Abstract
The proliferation of Digital Twins (DTs) across industries like manufacturing, healthcare, and logistics is leading to the formation of complex ecosystems where heterogeneous DTs must cooperate. In such environments, establishing trust becomes paramount. However, trust in DTs remains an under-investigated problem, with current research predominantly focused on security and privacy, which are prerequisites but not sole constituents of trust. This paper presents a comprehensive framework for analyzing and enhancing the trustworthiness of Digital Twins. First, we propose a novel five-layer symmetrical reference architecture (Asset, Synchronization, Data, Application, Integration) that models physical and digital twins as peers, improving reusability and maintainability. Using this architecture as a foundation, we then develop a multi-dimensional taxonomy to categorize DT trust issues from three critical perspectives: (1) an architectural perspective, which identifies and maps trust issues (e.g., model accuracy, data latency, application usability) to specific layers and behavioral attributes like conformance and dependability; (2) a massive twinning perspective, which explores emergent challenges in ecosystems of cooperating DTs, such as relationship complexity and data management; and (3) a stakeholder perspective, which addresses the need for both qualitative and quantitative trust assurances. Our analysis reveals that trust is a composite property requiring a holistic approach beyond conventional security. The paper concludes by synthesizing these perspectives into a unified view of DT trust and outlining critical open challenges and future research directions, providing a foundational roadmap for developing truly trustworthy Digital Twin systems.
1. Introduction
With the rapid growth of the Metaverse, companies are using Digital Twins (DTs) to create a virtual world for their customers and employees. Hence, DTs are becoming the next breakthrough in digitization [,,], which have gained significant traction recently with applications across domains according to recent state-of-the-art reviews in agriculture [], automotive [], manufacturing [], construction [] and healthcare []. DTs are virtual copies of systems that are built through the fusion of high-fidelity system models and data [,]. According to Grieves and Vickers [], a DT can be defined as “a set of virtual information constructs that fully describes a potential or actual physical manufactured product from the micro atomic level to the macro geometrical level. At its optimum, any information that could be obtained from inspecting a physically manufactured product can be obtained from its Digital Twin”. Grieves [] characterized them as having three distinct spaces, namely, physical, communication, and digital. In the physical space, the real space contains the actual system or process and operational technology infrastructure for capturing and manipulating it (i.e., sensors and actuators). The digital space houses a high-fidelity digital replica of the physical system or process, which is able to simulate all aspects of it. The communication space allows for communication between the digital and physical spaces. Communication mode between the physical and virtual entities differentiates between a DT, digital shadow, and digital model. In DTs, bi-directional real-time data flow exists between the physical entity and the digital entity. In a digital shadow [], one-way real-time data flows from the physical entity to the digital entity. In a digital model [,], no data flow occurs between the entities. These spaces and all their services were further detailed and presented in a layered reference architecture for DTs proposed in [], where Alam et al. [] identified four main functional layers: (i) data dissemination and acquisition, (ii) data management and synchronization, (iii) data modeling and additional services, and (iv) data visualization and accessibility.
DTs can be used to improve the monitoring, performance, efficiency, and reliability of physical entities or systems by enabling real-time data analysis and feedback []. For example, DTs can be used in conjunction with augmented reality and virtual reality technologies to provide immersive and interactive experiences in virtual environments, which allow for rich visualization of the physical entity []. Also, Machine Learning (ML) and Artificial Intelligence (AI) can be used to predict potential problems before they occur and to support decision-making through insights based on behavioral analysis and simulations []. Additionally, DT is a platform for connecting physical infrastructure by providing a platform with common services for collaboration, data sharing, and visualization [].
The future significance of DTs is evident due to their application in everyday life. It continues to grow rapidly because of the breakthroughs in its enabling technologies, including but not limited to IoT, AI, and Big Data. For example, recent advances in wireless communication technology, such as WiFi 6/7 and 5G/6G, have richer experiences for DT because of the increased bandwidth and reliability []. Current projections for the DTs market estimate that its market is expected to reach $48.2 billion by 2026 and $1.3 trillion by 2030.
The rapid increase in the adoption of DT technology across all fields will inevitably lead to ecosystems of DTs forming, where heterogeneous DTs created and maintained by many stakeholders will need to cooperate and share data to realize stakeholder goals [,]. This requires trust relationships to be established between the stakeholders and DTs and between the different DTs []. Despite its importance [,], it remains an under-investigated problem without any concrete trust models for DTs. Recent reviews [,,,] show that from a technical perspective, most of the work is focused on security, safety, and privacy, which is not enough for trust assurance []. From a non-technical perspective (i.e., stakeholder trust), Trauer et al. [] presented a trust framework based on a literature review and an interview study with seven recommendations to improve stakeholder trust in DTs. Furthermore, the trust problem is encompassing [], and DTs are inherently complex [], which requires modeling from different perspectives []. Therefore, we attempt to characterize the potential trust issues of DTs from three different perspectives: trust issues in a single DT, trust issues for cooperating DTs, and trust issues for stakeholders and their DTs. In sharp contrast to the survey articles found in the literature, our main contributions in this article can be summarized as follows:
- Proposal of a five-layer reference architecture for DTs.
- Taxonomy and categorization of DT trust issues from three perspectives: architectural, massive twinning, and stakeholders.
- A parametric analysis of trust issues and their mapping to possible solutions for DT.
- Future directions highlighting possible solutions for open DT trust problems.
Based on that, the rest of this paper is organized as follows: Section 2 presents background about trust as well as related work. Section 3 presents our proposed reference architecture and an illustration of how it is used to build the architecture for a DT for a logistics hub. Section 5 discusses the trust issues and recommendations for improving the trustworthiness from an architectural perspective based on our proposed reference architecture. Then, Section 6 discusses the concept of massive twinning and its trust issues and recommendations. After that, Section 7 discusses stakeholder trust in the DT system and how it can be improved. Section 8 presents a discussion of our architecture and findings. Finally, Section 9 concludes and envisions future directions.
2. Background and Related Work
2.1. Trust Background
Trust is the belief or confidence that one has in another person, organization, or system to act in a reliable, honest, and competent manner []. Trust involves taking a leap of faith based on past experiences, reputation, or other factors, with the expectation that the person, organization, or system will act in a predictable and consistent manner. In the context of cooperating systems, it is the degree of confidence or belief that the systems will collaborate for a common purpose in a reliable, honest, and competent manner, according to their intended functions and ethical principles, and in coordination with humans and other systems [].
Trustworthiness, on the other hand, refers to the degree to which a system is perceived to be trustworthy. It is a measure of the reliability, honesty, and competence of the system, and is based on past experiences and reputation. It is a key factor in establishing and maintaining trust, and it has several attributes. According to [,], trustworthiness has 14 attributes, which we classify as either behavioral or non-behavioral. These attributes are summarized in Figure 1.
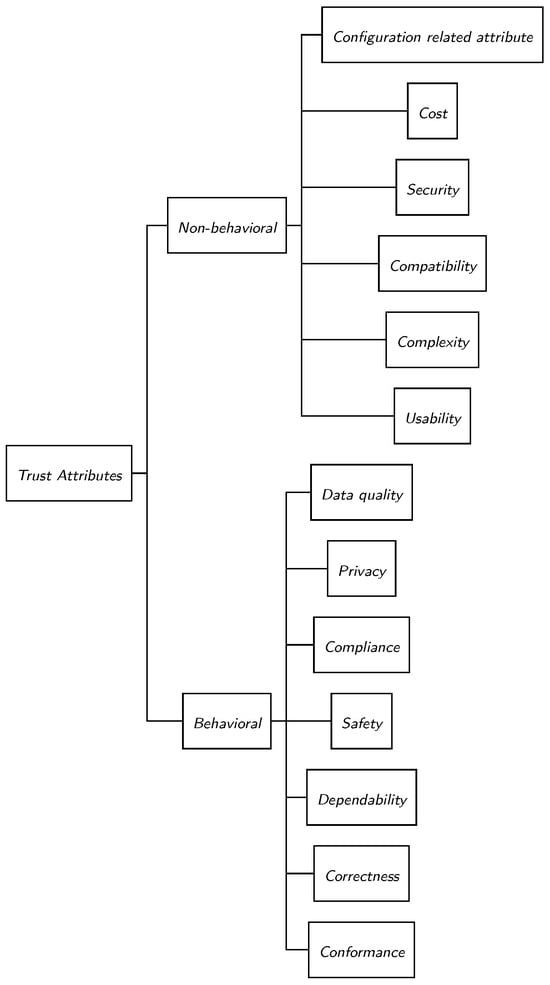
Figure 1.
Hierarchical taxonomy of behavioral and non-behavioral trust properties.
2.1.1. Trust Attributes: Behavioral
Attributes in this category are measured based on the behavior of the system. The attributes in this category are Correctness, Safety, Performance, Compliance, Dependability, Privacy, and Data quality. Correctness refers to the conformance of the behavior of the system to its formal specification []. It can be verified and validated using several techniques, such as testing and formal methods []. Safety is an attribute that describes how well the system prevents harm to its users, assets, and environment in case of hazards and threats []. Performance is an attribute that measures how well the system provides its functionality and achieves its goals [,]. Several metrics could be used to measure the performance of a system, such as throughput and latency []. Compliance covers a wide range of areas [], and it is an attribute that describes the degree to which the system adheres to laws, regulations, and industry standards. For example, a system that stores data in non-standard formats or uses non-standard processing methods is less trustworthy. Dependability is a complex attribute that describes several behavioral aspects of a system. A dependable system executes predictably and functions as intended. It encompasses several quality attributes of a system, including accuracy, availability, fault tolerance, flexibility, reliability, and scalability [,]. It can be measured based on runtime metrics such as failure rate and mean time to failure []. Privacy refers to the protection of sensitive information by allowing stakeholders/users to control how data is collected, used, and stored []. Data quality attribute measures the quality of the data in terms of its validity, timeliness, and integrity [].
These attributes apply to most computer systems, but they become more important in the context of DTs because of the critical nature of the systems they are made for. For example, the trustworthiness of DTs by human beings must be continually assessed based on these attributes []. On the other hand, conformance is a DT-specific trustworthiness attribute that measures how well a DT reflects its physical twin in terms of behavior [].
2.1.2. Trust Attributes: Non-Behavioral
Attributes in this category are not measured based on the behavior of the system; rather, they are quantitatively or qualitatively measured based on aspects such as design or operation. Attributes in this category are Usability, Complexity, Compatibility, Security, Cost, and Configuration-related attributes. Usability is a subjective attribute that measures the ease with which a system can be operated []. Complexity is an attribute that measures the intricacy, inter-connectivity, and heterogeneity of the system’s components and its data [,]. Compatibility is an attribute that measures the ease with which the system can integrate with other systems []. Security refers to the ability of the system to protect itself and its data from attacks and misuse [,]. It can be measured by looking at qualitative aspects of the system, including Accountability, Traceability, Confidentiality, Integrity, and Non-Repudiation. Cost is an attribute that quantifies the trustworthiness of the system based on the investment to make it trustworthy []. For example, investing in the certifying processes can be utilized to build and make the system more trustworthy []. Configuration-related attributes measure the degree of completeness and customizability of a system. In general, the more complete and customizable a system is, the more trustworthy it becomes [].
Most of the attributes in this category measure fundamental aspects of the system that are prerequisites for a trustworthy system []. For example, an unsecure system is untrustworthy regardless of the other attributes, because security is a prerequisite for trustworthiness [].
2.2. Related Work
Several reviews were published recently [,,,,,,] that cover many aspects of DTs from concept to implementation. Furthermore, other recent reviews that focus mainly on enabling technologies and challenges in DTs were also published in [,,,,]. These reviews show that cybersecurity-related research in DTs has been mainly focused on security and privacy. Thus, the literature on building trustworthy DTs is scarce; however, the concept of trustworthiness has been explored in other contexts, such as IoT [] and Cyber Physical Systems [], which could be leveraged in building DTs. The rest of this section discusses recent developments in cybersecurity and trust for DTs.
2.2.1. Recent Advances in Security for DTs
Alcaraz et al. [] presented a comprehensive survey of security threats for DTs. They analyze the current state of the DT paradigm and its enabling technologies and identify its operational requirements. Then, it classifies the security threats based on these operational requirements. The reviews in [,] discuss blockchain-based DTs and the role blockchain technology plays in their security. Examples of blockchain use in DTs can be found in [,], where blockchain is used to manage DT data. Hasan et al. [] proposed a blockchain-based approach for creating DTs, which can provide secure and trusted traceability, accessibility, and immutability of data and transactions involved in the creation process of DTs. It uses the InterPlanetary File System to host all the data resulting from all interactions.
2.2.2. Recent Advances in Trust for DTs
Rivera et al. [] proposed a maturity model for the development and sophistication of DTs, from blueprint to cooperating DTs. Also, it proposes a framework that identifies five technical enablers for achieving autonomic and cooperative DTs, highlighting the importance of trust and how it can be integrated into their framework. The authors in [] proposed a trust and security analyzer for cooperating DTs based on six criteria: security, resilience, reliability, uncertainty, dependability, and goal analysis. Bonney et al. [] proposed the use of a crystal-box workflow to improve trust and transparency in a DT. The proposed workflow contextualizes the information of the DT to the user by allowing them to inspect how the data is acquired, processed, and used by the DT without being able to modify it. The workflow was demonstrated using an open-source digital platform using a case study of a scaled three-storey structure, which showed how data is generated and processed, and how DT information is contextualized for the user. Trauer et al. [] proposed a framework to help practitioners create trust in DTs, which consists of three main components: stakeholders, user stories, and solution elements. Solution elements are the recommendations and measures to increase trust in DTs, such as explaining the twin properly, creating a common incentive, ensuring IP protection and IT security, proving the quality, ensuring a uniform environment, and documenting thoroughly. The framework is based on a literature review, a market study, and an interview study with 10 experts from various industries. It was evaluated by 12 experts, who found it to be generally useful and applicable.
3. Digital Twins Architecture
3.1. Overview
DTs are complex systems that require a deep understanding of both the physical asset or system being replicated and the technology used to create the virtual replica. A DT is a virtual representation of a physical asset or system that is used to simulate and predict its behavior in real-time. This requires a significant amount of data to be gathered from the physical asset or system, which is then used to create a digital model. The data can come from various sources, such as sensors, cameras, and other monitoring devices []. The complexity of DTs is further compounded by the need for advanced analytics, modeling, and simulation capabilities. The data gathered from the physical asset or system needs to be analyzed and processed to create an accurate digital model that can be used for simulations and predictions. This requires expertise in data analytics and artificial intelligence []. Furthermore, DTs can generate a tremendous amount of data, which can be overwhelming to manage and analyze. The data needs to be stored, processed, and analyzed in real time, which requires robust data management and analysis capabilities. The management of DTs also requires continuous updates and maintenance to ensure their accuracy and relevance []. Reference architectures are essential for DTs, as they provide a standardized framework for designing and implementing these technologies. A reference architecture is a standardized blueprint that outlines the key components, functionalities, and interactions required for a particular technology or system. In the case of DTs, a reference architecture provides a standardized approach for building and managing virtual replicas of physical assets or systems. In this work, we propose a reference architecture and use it to highlight the DTs’ trust issues in terms of the components of the architecture. This section discusses the details of our proposed architecture and presents an application for constructing the DT of a logistics hub.
The proposed architecture is shown in Figure 2, which depicts the twins as almost identical in terms of components and functionality. It is a layered architecture where each layer is present in both twins, with some differences in terms of the included functionality in some layers between them. It has five layers: asset layer, synchronization layer, data layer, application layer, and integration layer. The rest of this section is dedicated to describing the functionality of each layer, the physical twin, and its digital counterpart.
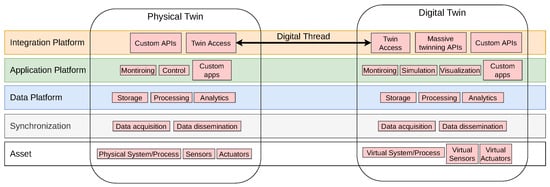
Figure 2.
Proposed architecture for digital twins.
3.2. Asset Layer
The asset layer includes the physical system/process on the physical twin and its digital replica on the DT. On the physical side, it can include a wide range of entities, such as machines, equipment, sensors, and devices, as well as the environment in which they operate. These entities generate data that is collected and used to create and enhance a digital replica on the DT. The digital replica can be modeled using different techniques depending on the complexity, available data, and analysis purpose [].
The most common modeling techniques [,] include first principles models, data-driven models, and hybrid models. First principles models are based on physical laws and equations that govern the behavior of the physical system, making them reliable but computationally demanding. Data-driven models use ML and statistical methods to learn from the data collected from the physical system, making them flexible but requiring a lot of data and validation. Hybrid models combine both first principles and data-driven approaches to leverage the strengths and overcome the limitations of each method, achieving high accuracy and efficiency but requiring a lot of coordination between different modeling techniques.
3.3. Synchronization Layer
The synchronization layer serves as a middleware that abstracts the complexity of data delivery from the asset and data layers, within the physical and DTs. It provides a platform for managing the communication and integration of the asset layer and the data layer, with the following key functionalities:
- Data collection: Collects data from the assets and devices in the system. This includes data from sensors, cameras, and other monitoring devices.
- Data filtering and processing: Provides filtering and processing facilities for the data between the two layers. This can help to reduce the volume of data that needs to be processed at the destination, improving the performance and scalability of the system.
- Data transmission: Reliably transmits the data from the asset layer to the data layer and vice versa.
- Interoperability and integration: Provides a common platform for integrating and enabling communication between different heterogeneous devices and systems. This reduces the complexity and cost of integration and improves the interoperability of the system.
- Security: Provides security features such as authentication, access control, encryption, and traceability and accountability to protect the data flow in both directions.
- Fault tolerance and resilience: Implements Logic to detect and recover from communication failures or other faults that may occur during data transmission. This can help to ensure the robustness and reliability of the DT system, even in the presence of unexpected events or failures.
It should be noted that the synchronization layer acts as a middleware specifically to abstract and manage the real-time, bidirectional data flow between the asset and data layers, thereby simplifying their respective functions by handling core communication tasks such as data collection, filtering, transmission, interoperability, security, and fault tolerance. This layer relieves the asset and data layers from needing to embed these complex, low-level communication details. This separation of concerns allows (a) the asset layer to focus solely on generating or consuming data and (b) the data layer to specialize in storage and analytics. This is done without each being burdened by the intricacies of reliable, secure, and efficient data delivery. This design enhances modularity, reduces system complexity, and improves overall maintainability.
3.4. Data Layer
The data layer implements data-related functionality, which includes processing, storage, and analytics. Both twins implement these functionalities, but the data layer is richer and more complex on the DT side. This is because the DT stores its own data and that of its physical counterpart, and it is intended to provide more services (e.g., simulation) that require more complex systems. More specifically, it provides the following functions:
- Data storage: Provides a storage mechanism for all collected and computed data, which can be in different formats such as structured, semi-structured, and unstructured data. It can also use different database technologies, such as relational databases, NoSQL databases, and time-series databases, depending on the type of data and the requirements of the DT application.
- Data processing and analytics: Provides facilities for processing and analyzing stored data, generating insights and predictions about the underlying assets. This involves using various techniques such as statistical analysis, ML, and artificial intelligence algorithms to identify patterns and relationships in the data.
- Data access: Provides a platform for accessing and querying the stored data, which includes providing APIs and other interfaces for accessing the data, as well as providing tools for data visualization and analysis.
- Data security: Ensures the security and privacy of the stored data. This includes implementing access control mechanisms, data encryption, and other security features to prevent unauthorized access and data breaches []. This also includes data governance policies, data retention policies, and data anonymization policies, which ensure that the data is used appropriately.
- Data backup and recovery: Ensures that the data stored is protected from data loss or corruption. This involves implementing data replication, mirroring, and backup processes to create redundant copies. Also, it involves testing and validating the backup and recovery processes to ensure their reliability and effectiveness in the event of a data loss or corruption.
- Model validation and verification (V&V) and accreditation: Involves checking that a DT model accurately represents the physical system under specified conditions, while Model Accreditation involves certifying that a DT model is suitable for a specific purpose or application. There are several methods and challenges for conducting V&V and accreditation of DTs, including continuous V&V, hybrid V&V, and a hybrid framework. Continuous V&V involves performing it throughout the lifecycle of a DT, while the hybrid framework combines different V&V techniques for evaluating different aspects of a DT model. The hybrid framework establishes a systematic approach for conducting V&V and Accreditation of DTs. It is based on clear definitions, criteria, metrics, and documentation to facilitate communication and collaboration among different stakeholders.
3.5. Application Layer
The application layer implements a platform where applications can be developed to allow users and stakeholders to interact with the underlying assets using graphical user interfaces. However, it provides the following core functionality:
- Monitoring and control: Allows users to monitor the underlying control assets in real time.
- Simulation and modeling: Allows users to simulate the behavior of the physical twin under different conditions, which can be performed based on real-time data or historical data, depending on the requirements of the DT application.
- Analysis and optimization: Allows users to analyze the data and optimize the performance of the physical system, which can be performed using various techniques such as statistical analysis, ML, and AI algorithms.
- Reporting and visualization: Allows users to generate reports and visualize the data in various formats, such as charts, graphs, and tables, which can be customized based on the user’s requirements and preferences.
Some applications are implemented on both twins (e.g., control and monitoring), while others are usually only implemented on the DT (e.g., visualization).
3.6. Integration Layer
The integration layer is a platform that allows stakeholders to define services and interfaces, which allow their twins to communicate with external systems. It provides the core functionality of synchronizing the physical twin to its digital counterpart through the twin access component, which handles data ingestion, protocol translation, and real-time state updates. Another component that could be included in this layer is a massive twinning component that allows DTs of different systems to cooperate, creating a network of interoperable digital models.
This interoperability is the key to unlocking system-of-systems intelligence. By enabling DTs to leverage existing cloud-based systems and services, the integration layer facilitates the creation of richer, composite services. For instance, a DT from a logistics network can share data with a DT from a manufacturing plant, allowing for dynamic, just-in-time part delivery and production rescheduling.
Ultimately, this layer acts as the central nervous system for the entire DT ecosystem. It not only ensures seamless data flow but also manages security, access control, and governance across all connected twins and external services, transforming isolated digital models into a cohesive, intelligent, and actionable enterprise asset.
3.7. Enhancing Trust Through Symmetrical Design
While we propose a five-layer symmetrical reference architecture as a key novelty, the true novelty lies not in the layer names themselves, but in the symmetrical peer-to-peer design that models the physical and digital twins with identical layered structures (Asset, Synchronization, Data, Application, Integration), treating them as functional equals rather than subsuming the physical twin within the DT. This approach fundamentally enhances reusability, maintainability, and testability by enabling parallel development and clearer integration pathways, as demonstrated in the logistics hub example. The proposed symmetrical architecture directly enhances trust by establishing a transparent and consistent framework. Both the physical and digital twins are structured as identical, peer-level entities, which simplifies the mapping of specific trust attributes such as conformance, data quality, and dependability. This is done to discrete layers, thereby clarifying accountability and vulnerability points. The uniform structure enables independent verification and validation of each twin, as their parallel compositions allow for direct behavioral comparison and anomaly detection, fostering greater confidence in their alignment. Ultimately, the design’s inherent clarity and modularity not only improve maintainability but also systematically reinforce trustworthiness by making the system’s operations more interpretable, testable, and verifiable at every layer.
4. Illustrative and Comparative Study
4.1. Illustrative Example
This example describes the construction of a DT of a logistics hub using our proposed architecture. A logistics hub is a central location where goods are received, sorted, stored, and distributed to their final destinations. The environment of a logistics hub is typically a large warehouse or distribution center, where a variety of technologies are used to manage the movement of goods.
A logistics hub is a complex facility that comprises several components, including receiving and shipping areas, storage areas, material handling systems, inventory management systems, transportation management systems, office and administrative areas, and security and safety systems. These components work together to ensure that goods are moved and stored efficiently and effectively. Material handling systems, such as conveyor belts and robotic arms, help to move goods around the facility, while inventory management and transportation management systems track the movement of goods from the warehouse to their final destination. Office and administrative areas allow staff to manage the movement of goods and coordinate with carriers, while security and safety systems ensure the safety of staff and goods.
Figure 3 shows where each of the components fits according to our architecture. For the physical twin, the asset layer contains the material handling, transportation, and inventory management systems, in addition to all other sensors and actuators (e.g., cameras, control terminals, etc.). At the synchronization layer, a dedicated IoT infrastructure that synchronizes the asset and data layers is introduced, such as message brokers, which completely decouple them. This greatly improves the maintainability at each layer, but more so for the asset layer, as broken assets are often replaced and new assets are introduced. The data layer stores, processes, and analyzes all data within the physical twin. The application layer contains applications that staff use to manage the facility, such as the warehouse management system. At the integration, custom APIs are defined to integrate the physical twin with local services and its DT.
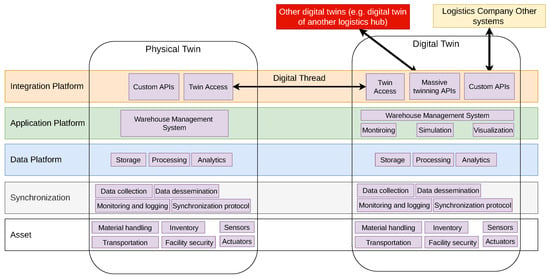
Figure 3.
Illustrative example for the architecture.
The DT has an identical structure and functionality to its physical counterpart. However, the DT has a more complex data, application, and integration layers because it provides more complex services. For example, it might provide predictive analysis at the data layer, simulation at the application layer, and integrations with other DTs and other systems owned by the same company (e.g., ERP systems). The architecture’s design, which explicitly supports bidirectional data flow and steering of the physical system, aligns with the definition of a DT rather than a Digital Shadow. The proposed five-layer architecture includes an Integration Layer that enables synchronization between the physical and DTs, and the Application Layer on the digital side supports simulations, optimizations, and control functions whose results are fed back to the physical asset via the Synchronization Layer. For instance, in the logistics hub example, the DT’s predictive analysis and simulation outcomes influence physical operations such as inventory management or material handling, enabling continuous optimization. Therefore, the system embodies a true DT by facilitating closed-loop control and real-time, bidirectional interaction.
4.2. Comparison with Existing Architectures
Existing architectures such as the ones described in [,], often envision the physical twin to have a different architecture from its DT. For example, the architecture [] presents the physical twin as a layer in the architecture of the DT, where a digital thread is introduced to connect it to the first layer in the DT. This greatly simplifies the development of the DT because all the integration with the physical twin is taken care of by the digital thread. However, it introduces several problems with it, as follows:
- The DT is fully dependent on the physical twin, because it is part of the architecture of the DT. This greatly impacts several quality attributes of the DT, such as testability, because the physical twin has to be present to test the DT. Also, flexibility and scalability are impacted, as it is unclear how to connect multiple DTs to the same physical counterpart.
- The architecture of the physical twin and the DT could be different. This makes the DT difficult to maintain, as developers look at different specifications when working with the twins.
- There is a clear distinction between the physical twin and the DT, because each DT depends on its physical twin. This simplifies finding the physical twin when its digital counterpart is compromised.
On the other hand, in our proposed architecture, the DT is an extended digital replica of the physical twin, and they both integrate through their integration layers. This solves the first problem because a given twin could be configured to connect to one or multiple twins by extending the twin access component. Furthermore, since both twins have the same architecture, perhaps with extended features on the digital side, maintaining both systems becomes simpler and cheaper because the components of the upper layers on the physical side are reused on the digital side. Finally, in our architecture, there is no clear distinction between the physical and DTs, because they are modeled like peers that can be connected at will.
5. Toward Trustworthy Digital Twins Architecture
5.1. Overview
Ensuring trust in DTs is critical for their effective use in decision-making and optimization. To integrate trust into our DT architecture, the potential trust issues need to be considered at each layer of our architecture. These trust issues affect the trust attributes that we discussed in Section 2.1. In this work, we focus on how the behavioral attributes are impacted by the trust issues at each layer. Table 1 presents a summary of these attributes.

Table 1.
Trust attributes considered at each layer.
5.2. Asset Layer
The asset layer has a physical side and a digital side, that represent each of the twins, respectively. All the trust attributes are impacted at this layer because of its sheer complexity, where interactions between humans, machines, and data are managed. The trust issues at this layer can be categorized into four categories, namely, safety-related issues, data-related issues, dependability-related issues, and digital model issues.
5.2.1. Safety Related Trust Issues
Safety is the ability to operate without risk of injury or harm to the system’s environment and its users, and it can be achieved by ensuring that there are no consequences on them []. Safety is a critical aspect of trustworthiness and a major concern in critical systems, because those could cause harm to the environment if they did not have designed-in safety mechanisms that mitigate potential risks to a tolerable level []. In addition to mitigating common issues and failures at design time [], this requires the behavior of the system to be monitored to detect potential issues at runtime and activate those safety mechanisms []. This highlights two major safety-related trust issues, namely, safety control effectiveness and behavior-based detection accuracy.
5.2.2. Data Related Trust Issues
There are three data-related trust issues, namely, data quality issues, data compliance issues, and data privacy issues. The quality of the data, according to [], is measured in terms of its integrity, reliability, timeliness, and validity. Data compliance issues are related to legal compliance, legal requirements of what data is collected and how it is collected, such as complying with the General Data Protection Regulation (GDPR). Privacy is defined as the protection of personal or sensitive information that is collected, processed, or transmitted by interconnected devices and systems []. It is a major concern for DTs in certain contexts (e.g., smart cities) because these technologies enable continuous sensing and data sharing, which may expose users’ identities, locations, preferences, or behaviors to unauthorized parties [].
5.2.3. Dependability Related Trust Issues
There are two dependability-related trust issues, namely, inconsistent performance and system failures. These occur as a result of poor practices during the lifecycle of the DT []. They are partially addressed during the development of the DT by improving its scalability, reliability, and resilience [,,]. Reliability is the ability of interconnected devices, systems, and applications to perform consistently and accurately in their environments []. Scalability means that a system can cope with the rising workload caused by the expansion of elements in the system during its functioning without compromising its efficiency [,]. Resilience is defined as the ability of a system to withstand cyber attacks, recover from failures, and maintain its functionality and security throughout its lifecycle [,]. Then, at run time, the behavior of the DT is monitored to detect potential scenarios that might lead to a failure or performance issues []. For example, during the operation of the DT, monitoring is imperative to anticipate unforeseen load based on the behavior of the system. Otherwise, the system may have inconsistent performance or fail.
5.2.4. Model Related Trust Issues
Model complexity is the degree of difficulty in understanding, designing, and managing a system that has many interrelated parts and behaviors []. It is a key challenge for trustworthiness in DTs because it increases uncertainty, variability, and unpredictability of the system []. It might also require more data, computation, and communication resources, which can introduce errors, biases, and vulnerabilities [,]. Atkinson et al. [] analyzed the current DT standards and architectures, and identified some of the sources of unnecessary accidental complexity. The work proposed new standards and architectures that could support the efficient implementation of DTs and their seamless integration with other systems. The work also suggested some best practices and guidelines for reducing complexity and enhancing quality in DTs. Composability is one way of managing complexity, and it is defined as the ability to combine digital elements into larger assemblies and models that can be reused and modified []. It can help improve trustworthiness at this layer by enabling interoperability, modularity, and flexibility. It can also facilitate verification and validation by allowing the reuse of existing components and models that have been tested and verified. Composing DTs to build more complex DTs is referred to as massive twinning, which introduces more trust issues [] that we discuss later.
Model accuracy is the degree to which the DT model reflects the reality and behavior of the physical system. It is a measure of how closely the model matches the actual system in terms of inputs, outputs, and dynamics. Accuracy can be improved through the use of verification and validation procedures [,]. Verification is the process of checking whether the model is correctly implemented according to its specifications. Validation is the process of checking whether the model is consistent with the observed data and phenomena. Verification and validation can help ensure that the model is reliable, accurate, and credible. Furthermore, according to [], the accuracy of the model changes over time because of the temporal aspect of the physical system, which naturally degrades over time. Tao et al. [] proposed a DT modeling theoretical system, which deconstructed and investigated the DT modeling from six aspects: model construction, model assembly, model fusion, model verification, model modification, and model management. Also, they presented a DT modeling framework based on the theoretical system, and applied it to a case study of an aircraft engine DT. This trust issue depends on the correctness and conformance attributes.
Model accuracy and conformance are indeed strengthened by explicitly linking them to the choice of digital model development approaches, as a failure in the underlying modeling method is a primary source of conformance risk. The fidelity with which a DT replicates its PT behavior is directly contingent upon whether the selected modeling paradigm is adequately suited to the system’s complexity, data availability, and required predictive capabilities. An inappropriate or poorly implemented model inherently introduces discrepancies between the predicted and actual behaviors of the physical asset, thereby directly undermining the DT’s conformance. Therefore, this causal relationship emphasizes that achieving high conformance is not merely an outcome of runtime synchronization but is fundamentally determined by the rigor and suitability of the initial model construction and its continuous validation.
5.3. Synchronization Layer
This layer in a DT architecture abstracts the complexity of data delivery from the asset and data layers. It serves as a bridge between the asset and data layers in the physical twin and the DT, which abstracts the data delivery logic from both layers. There are two major trust issues at this layer, data latency/loss and destination mismatch []. Data latency/loss occurs when data is delayed or not delivered to the destination, which can be due to network factors, such as network congestion or bandwidth limitations, or a fault in the synchronization system itself. This can lead to inconsistencies in the destination’s state, affecting its accuracy and reliability. On the other hand, destination mismatch occurs when data is delivered to the wrong destination, which can happen due to configuration errors, network issues, or compromise of the system itself. This can result in an inconsistent state at the intended and wrong destinations. These issues impact the correctness, dependability, and privacy trustworthiness attributes.
5.4. Data Layer
DTs are complex systems that generate and process large volumes of data, often in real-time, depending on the application and the complexity of the system. The purpose of this layer is to store and process all of this data. The physical and DTs also share the trust issues at this layer, although they become more pronounced in the latter because of its inherent complexity []. There are three main trust issues at this layer, namely, poor data platform dependability, data model complexity, and data storage and processing transparency.
Poor dependability of the data platform is a critical trust issue because the platform must be able to store big data, as the DT becomes more complex. This requires the platform to dynamically adjust to meet the needs of the DT. The complexity of the data model is another trust issue, which could lead to dependability and maintainability issues of the model and its applications []. This includes degrading performance, increasing the difficulty for developing and maintaining applications to leverage this data, and increasing the probability of bugs, which degrades the quality of the data []. This issue affects the dependability and data quality attributes.
Clarity and comprehensibility of how data is collected, stored, analyzed, and used is a critical and major trust issue at this layer. This is because the processing and storage of data affects the quality of the data, which is a key trustworthiness attribute []. For example, AI is used to analyze the data and provide insights, which heavily depend on the suitability of the model used [,,], and the repeatability and reliability of the results are contingent on the used AI techniques being explainable and verifiable [,]. These aspects become imperative in the context of critical systems []. This issue affects the compliance and data quality attributes.
5.5. Application Layer
This layer is an application platform that allows users to interact with and visualize assets through different applications. For example, CAD/ECAD (electronic computer-aided design) systems can be used to visualize and manipulate their geometric, physical, and behavioral aspects []. Furthermore, since these applications deal with complex and critical systems, it is important that they be easy to use. Therefore, a critical trust issue at this layer is the usability of those applications, and in that regard, the literature on software usability can be leveraged to objectively benchmark their usability as an attribute for computing trustworthiness [,]. Furthermore, the usability of the applications affects several behavioral trust attributes, including dependability, compliance, privacy, and data quality. Dependability is affected when the applications do not perform well (e.g., constantly crash). Compliance is affected if the applications collect data in such a way that they break the law, such as collecting data from minors in a smart city context. Privacy is affected when the applications leak data to unauthorized entities. Finally, data quality is affected when, for example, an application displays data with lower precision (e.g., by rounding or truncating numbers). This might compel the user to make an incorrect decision based on that low-quality data.
5.6. Integration Layer
This layer is an interface/API platform where APIs are deployed to allow the physical and DTs to synchronize and integrate with other systems. One of the trust concerns at this layer is usability, which refers to how well it exposes the underlying functionality in terms of ease of use [], which can be addressed through different techniques such as usability testing and surveys. Another issue is the trustworthiness of the DT from the perspective of the physical twin, which is introduced at this layer because of the synchronization of the twins, and vice versa. Each twin continuously analyzes the behavior of the other in an attempt to detect malicious behavior [,]. This analysis considers many properties, such as accuracy, to determine the trustworthiness of each of the entities by the other [,]. Usability at this layer has the same implications in terms of impact on trust attributes.
6. Trust from a Massive Twinning Perspective
Massive twinning [] is the concept of creating and maintaining a digital twin for almost every physical entity (such as humans, machines, or processes) in a networked scenario, and using these digital twins to provide data, insights, and control for various applications. Massive twinning is envisaged to be a key feature of 6G networks, as it can enable pervasive intelligent services in industrial and other domains. Massive twinning can also enhance the performance of emergent intelligence (EI) applications, which rely on the interaction among massive agents with simple logic to achieve complex behavior patterns. By migrating the data and logic from the physical agents to their digital twins on the edge server, massive twinning can reduce the traffic load and improve the reliability of EI applications.
Trust management in a massive twinning context refers to the ability of digital twins to establish and maintain trust relationships with other digital twins or human agents based on their behavior and reputation []. It is a key element that enables better decision-making and improved operational efficiency of digital twins []. It can also help enhance the resilience and adaptability of the cooperating digital twins by detecting and resolving any conflicts or anomalies that may occur [,]. The first trust issue is that this context is relationship complexity, because in massive twinning, the relationships between two DTs are not always symmetric. This asymmetry introduces a lot of complexity that renders most trust models that assume symmetry unusable (e.g., P2P trust models). Another trust issue is data management, because cooperating DTs share a lot of data that has to be stored in a tamper-proof way.
7. Trust from a Stakeholder Perspective
Stakeholder trust in a DT is the confidence they have in its design and behavior, which includes its relationships to other systems and stakeholders []. Furthermore, as adoption of DT technology increases, ecosystems will form where they cooperate and share data, possibly across domains (i.e., different organizations), which might result in conflicts of interest among stakeholders []. Hence, there is a need for mechanisms to assure stakeholders of the trustworthiness of their DT (i.e., its value and alignment with their goals). Recent literature indicates that two types of assurances could be provided to stakeholders:
- Qualitative trust assurance: Used to educate the stakeholder about the value of the DT and how it provides that value [,]. This is difficult to quantify [], but there are frameworks that have concrete recommendations of how to achieve that, such as []. Furthermore, educating the stakeholders about the behavior of the DT can be done through using modelling techniques (e.g., crystal-box and grey-box modelling) or examining the actual source code of the DT []. The main goal here is to provide transparency about the inner workings of the DT.
- Quantitative trust assurance: Used to provide stakeholders with concrete estimations of the conformance of the DT to its physical counterpart in terms of model and behavior [,]. This involves performing automated model validation and verification based on uncertainty quantification [], for which open-source tools such as UQpy [] exist. For behavioral estimations, usually ML-based approaches (supervised, semi-supervised, or unsupervised) are used to model the behavior of the PT and use that to estimate errors in the DT [].
Also, compliance with legal and regulatory requirements is another critical trust issue related to using DTs []. For example, DTs must comply with data protection laws such as the General Data Protection Regulation and the California Consumer Privacy Act when they rely on sensitive data, including personal data about individuals, which are designed to protect the privacy and security of personal data and give individuals control over how their data is collected, processed, and used.
The relationship between the behavioral trust attribute of Compliance and its role in stakeholder trust is complementary rather than redundant, as it addresses different facets of the same core concept. The behavioral attribute “Compliance” as defined in Section 2, describes the system’s operational characteristic of adhering to laws, regulations, and standards during its runtime execution, making it a measurable property of the system’s behavior. This attribute is contextualized within the stakeholder perspective, where compliance becomes a critical assurance mechanism; stakeholders require proof that the DT not only operates in a compliant manner (the behavioral aspect) but also that this operational compliance is explicitly aligned with and verifiable against specific legal and regulatory frameworks like GDPR. Thus, the behavioral attribute is the what (the system’s conformant conduct), while the stakeholder discussion is the why (building confidence by demonstrating that this conduct meets external legal obligations), creating a comprehensive link from technical operation to stakeholder value and risk mitigation.
It should be noted that a DT application (potentially) has many diverse stakeholders that may range from coders and developers, up to decision makers, up to policy makers. These figures may be spread across the organizational hierarchy; therefore, their interpretation of the subject may vary in a considerable way. This would lead to different needs from the perspective of “trust” in relation to a DT application.
8. Key Findings and Interpretations
In this paper, we have explored the trust issues of DTs from three different perspectives: architectural perspective, massive twinning perspective, and stakeholders’ perspective. We have not discussed any security issues in this paper, as security is a prerequisite for trust. Security refers to the protection of DTs from unauthorized access, modification, or damage, while trust refers to the confidence that DTs behave as expected and intended. Trust is built upon security, but also depends on other factors such as transparency, accountability, reliability, and fairness. Therefore, we focus on the trust challenges that go beyond security in the context of DTs. Also, security issues for DTs have been thoroughly explored in the literature [,].
Our proposed architecture facilitates the development of DTs because it uses functional layers that exist on both the physical and digital counterparts. In that way, the DT is presented as a digital version of the physical twin with extra functionality. For example, at the application layer, some of the same applications that exist on the physical twin could be deployed on the DT with DT-specific ones. This is a departure from the existing architectures in the literature, which present the physical twin as the “physical layer” in the architecture of the DT, such as [,,]. Furthermore, isolating the digital and physical assets into their own layer facilitates model validation and verification, as the process of synchronizing them to the data layer is delegated to a separate layer. Also, the synchronization between the twins happens through their respective integration layers, which gives each of them full control of their level of integration with their counterpart. Overall, the architecture maximizes reuse and improves maintainability, as both sides (digital and physical) have an identical structure.
From an architectural perspective, the trust issues at the asset layer revolve around the construction of the physical and digital assets, such as reliability and scalability. At the synchronization and integration layers, the trust issues are mainly communication trust issues, such as interoperability and performance. At the data layer, the complexity of the data models and transparency of AI algorithms are the most pronounced trust issues. At the application layer, application usability is the most pronounced trust issue, as it directly impacts the decisions (or lack thereof) taken by the stakeholders.
Trust issues in massive twinning are going to become more pronounced as DTs become more ubiquitous. These issues might seem similar to trust issues of peer-to-peer systems; however, in a massive twining context, the relationships between different DTs are much more complex and often asymmetrical. For example, in massive twinning, a single DT could be composed of several smaller DTs, which have relationships with each other and the one that encompasses all of them. However, it is currently not feasible to develop trust management solutions in this context because its security and privacy are under-investigated, and some of the enabling technologies are still not widely in use, such as 5G/6G networks [].
From the perspective of stakeholders, trust issues [] revolve around understanding the value of the DT and its methods. For example, they need to understand the internal processes of the DT and how these processes add value to them.
9. Conclusions and Future Work
This paper has presented a comprehensive exploration of behavioral trust in DTs, addressing a critical and under-investigated area as DT ecosystems become more complex and interconnected. Our work provides a structured foundation for understanding, analyzing, and enhancing the trustworthiness of DTs through three primary contributions.
First, we proposed a novel five-layer reference architecture for DTs, comprising Asset, Synchronization, Data, Application, and Integration layers. A key differentiator of this architecture is its symmetrical design, where both the physical and DTs are modeled as peers with identical layered structures. This approach facilitates greater reusability, maintainability, and a clearer conceptual model compared to existing architectures that often subsume the physical twin within the DT’s structure. The illustrative example of a logistics hub demonstrated the practical applicability of this architecture. Second, we developed a systematic taxonomy and analysis of DT trust issues from three distinct yet interconnected perspectives shown in Figure 4. The Architectural Perspective meticulously identifies and categorizes potential trust issues at each layer of our proposed architecture, mapping them to key behavioral trust attributes such as conformance, correctness, dependability, safety, compliance, privacy, and data quality. This layer-by-layer analysis provides a granular blueprint for developers to pinpoint and address trust vulnerabilities during the design and operation of a DT. The Massive Twinning Perspective examines the emergent trust challenges in scenarios where numerous DTs cooperate. This context introduces unique complexities, such as asymmetric relationships and sophisticated data management requirements, which render traditional symmetric trust models inadequate and call for new, dynamic trust management solutions. The Stakeholder Perspective highlights the importance of stakeholder confidence, distinguishing between qualitative assurances (e.g., transparency and value communication) and quantitative assurances (e.g., model conformance metrics and behavioral error estimation). This underscores that technical trustworthiness must be complemented by perceived trust to ensure widespread adoption.
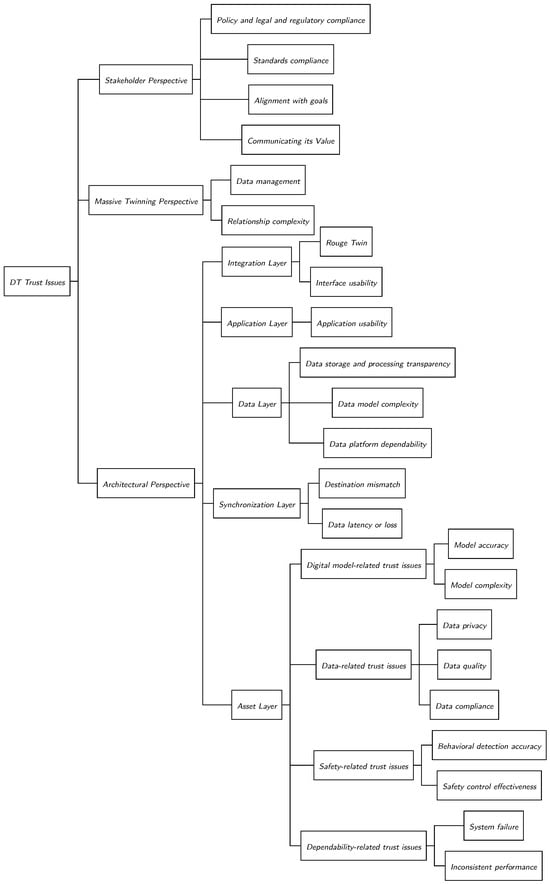
Figure 4.
DT trust issues from three different perspectives.
Finally, our parametric analysis and discussion synthesized these perspectives, clarifying that security, while a fundamental prerequisite, is not sufficient for trust. True trustworthiness in DTs is built upon a combination of robust architecture, reliable data, transparent processes, and usable interfaces, all of which must function cohesively across potentially massive and collaborative ecosystems.
Looking ahead, several promising directions emerge. The proposed taxonomy, while analytically rigorous, lacks empirical validation through quantitative metrics, formal verification, or implementation in a high-fidelity case study to demonstrate functional efficacy and performance overhead. Furthermore, the analysis of trust in massive twinning environments, while identifying critical challenges like asymmetric trust relationships and composability, does not provide a formal model or protocol for dynamic trust computation. The architectural discussion also omits a detailed treatment of the synchronization layer’s inherent trade-offs, such as the latency introduced by its decoupling middleware and the resulting impact on real-time conformance for safety-critical control loops, which are pivotal for assessing the practical trustworthiness of the proposed design.
Funding
The authors would like to acknowledge the support provided by the Interdisciplinary Research Center for Intelligent Secure Systems (IRC-ISS) and the Deanship of Scientific Research at King Fahd University of Petroleum & Minerals (KFUPM). This project is funded by IRC-ISS Grants #INSS2502 and #INSS2503.
Data Availability Statement
Data sharing is not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Alhazmi, T.; Azzedin, F.; Hammoudeh, M. MQTT Based Data Distribution Framework for Digital Twin Networks. In Proceedings of the 8th International Conference on Future Networks & Distributed Systems, Marakech, Morocco, 11–12 December 2024; pp. 1008–1013. [Google Scholar]
- Tao, F.; Zhang, H.; Liu, A.; Nee, A.Y. Digital twin in industry: State-of-the-art. IEEE Trans. Ind. Inform. 2018, 15, 2405–2415. [Google Scholar] [CrossRef]
- Guo, J.; Bilal, M.; Qiu, Y.; Qian, C.; Xu, X.; Raymond Choo, K.K. Survey on digital twins for Internet of Vehicles: Fundamentals, challenges, and opportunities. Digit. Commun. Netw. 2024, 10, 237–247. [Google Scholar] [CrossRef]
- Purcell, W.; Neubauer, T. Digital Twins in Agriculture: A State-of-the-art review. Smart Agric. Technol. 2023, 3, 100094. [Google Scholar] [CrossRef]
- Piromalis, D.; Kantaros, A. Digital Twins in the Automotive Industry: The Road toward Physical-Digital Convergence. Appl. Syst. Innov. 2022, 5, 65. [Google Scholar] [CrossRef]
- Leng, J.; Wang, D.; Shen, W.; Li, X.; Liu, Q.; Chen, X. Digital twins-based smart manufacturing system design in Industry 4.0: A review. J. Manuf. Syst. 2021, 60, 119–137. [Google Scholar] [CrossRef]
- Menassa, C.C. From BIM to digital twins: A systematic review of the evolution of intelligent building representations in the AEC-FM industry. J. Inf. Technol. Constr. 2021, 26, 58–83. [Google Scholar] [CrossRef]
- Alazab, M.; Khan, L.U.; Koppu, S.; Ramu, S.P.; Iyapparaja, M.; Boobalan, P.; Baker, T.; Maddikunta, P.K.R.; Gadekallu, T.R.; Aljuhani, A. Digital Twins for Healthcare 4.0-Recent Advances, Architecture, and Open Challenges. IEEE Consum. Electron. Mag. 2022, 12, 29–37. [Google Scholar] [CrossRef]
- Schleich, B.; Anwer, N.; Mathieu, L.; Wartzack, S. Shaping the digital twin for design and production engineering. CIRP Ann. 2017, 66, 141–144. [Google Scholar] [CrossRef]
- Wagg, D.; Worden, K.; Barthorpe, R.; Gardner, P. Digital twins: State-of-the-art and future directions for modeling and simulation in engineering dynamics applications. ASCE-ASME J. Risk Uncertain. Eng. Syst. Part B. 2020, 6, 030901. [Google Scholar] [CrossRef]
- Grieves, M.; Vickers, J. Digital twin: Mitigating unpredictable, undesirable emergent behavior in complex systems. In Transdisciplinary Perspectives on Complex Systems; Springer: Berlin/Heidelberg, Germany, 2017; pp. 85–113. [Google Scholar]
- Sepasgozar, S.M. Differentiating digital twin from digital shadow: Elucidating a paradigm shift to expedite a smart, sustainable built environment. Buildings 2021, 11, 151. [Google Scholar] [CrossRef]
- Alhazmi, T.; Azzedin, F.; Hassine, J.; Hammoudeh, M. Formal Specification and Executable Analysis of Digital Twin Systems Using Maude Rewriting Logic. Future Gener. Comput. Syst. 2025, 176, 108148. [Google Scholar]
- VanDerHorn, E.; Mahadevan, S. Digital Twin: Generalization, characterization and implementation. DEcision Support Syst. 2021, 145, 113524. [Google Scholar]
- Alam, K.M.; El Saddik, A. C2PS: A digital twin architecture reference model for the cloud-based cyber-physical systems. IEEE Access 2017, 5, 2050–2062. [Google Scholar]
- Alcaraz, C.; Lopez, J. Digital Twin: A Comprehensive Survey of Security Threats. IEEE Commun. Surv. Tutor. 2022, 24, 1475–1503. [Google Scholar]
- Kukushkin, K.; Ryabov, Y.; Borovkov, A. Digital Twins: A Systematic Literature Review Based on Data Analysis and Topic Modeling. Data 2022, 7, 173. [Google Scholar] [CrossRef]
- Opoku, D.G.J.; Perera, S.; Osei-Kyei, R.; Rashidi, M. Digital twin application in the construction industry: A literature review. J. Build. Eng. 2021, 40, 102726. [Google Scholar] [CrossRef]
- Jones, D.; Snider, C.; Nassehi, A.; Yon, J.; Hicks, B. Characterising the Digital Twin: A systematic literature review. CIRP J. Manuf. Sci. Technol. 2020, 29, 36–52. [Google Scholar] [CrossRef]
- Iraji, S.; Mogensen, P.; Ratasuk, R. Recent advances in M2M communications and Internet of Things (IoT). Int. J. Wirel. Inf. Netw. 2017, 24, 240–242. [Google Scholar] [CrossRef]
- Rosen, R.; Fischer, J.; Boschert, S. Next generation digital twin: An ecosystem for mechatronic systems? IFAC-Papersonline 2019, 52, 265–270. [Google Scholar]
- Eckert, C.; Isaksson, O.; Hallstedt, S.; Malmqvist, J.; Rönnbäck, A.Ö.; Panarotto, M. Industry trends to 2040. In Proceedings of the Design Society: International Conference on Engineering Design, Delft, The Netherlands, 5–8 August 2019; Volume 1, pp. 2121–2128. [Google Scholar]
- Rasheed, A.; San, O.; Kvamsdal, T. Digital twin: Values, challenges and enablers from a modeling perspective. IEEE Access 2020, 8, 21980–22012. [Google Scholar] [CrossRef]
- Trauer, J.; Mutschler, M.; Mörtl, M.; Zimmermann, M. Challenges in Implementing Digital Twins—A Survey. In Proceedings of the International Design Engineering Technical Conferences and Computers and Information in Engineering Conference, St. Louis, MO, USA, 14–17 August 2022; Volume 86212, p. V002T02A055. [Google Scholar]
- Bersani, M.M.; Braghin, C.; Cortellessa, V.; Gargantini, A.; Grassi, V.; Presti, F.L.; Mirandola, R.; Pierantonio, A.; Riccobene, E.; Scandurra, P. Towards Trust-preserving Continuous Co-evolution of Digital Twins. In Proceedings of the 2022 IEEE 19th International Conference on Software Architecture Companion (ICSA-C), Honolulu, HI, USA, 12–15 March 2022; pp. 96–99. [Google Scholar]
- Sharma, A.; Kosasih, E.; Zhang, J.; Brintrup, A.; Calinescu, A. Digital twins: State of the art theory and practice, challenges, and open research questions. J. Ind. Inf. Integr. 2022, 30, 100383. [Google Scholar] [CrossRef]
- Botín-Sanabria, D.M.; Mihaita, A.S.; Peimbert-García, R.E.; Ramírez-Moreno, M.A.; Ramírez-Mendoza, R.A.; Lozoya-Santos, J.d.J. Digital twin technology challenges and applications: A comprehensive review. Remote Sens. 2022, 14, 1335. [Google Scholar] [CrossRef]
- Laplante, P. Trusting Digital Twins. Computer 2022, 55, 73–77. [Google Scholar] [CrossRef]
- Trauer, J.; Schweigert-Recksiek, S.; Schenk, T.; Baudisch, T.; Mörtl, M.; Zimmermann, M. A Digital Twin Trust Framework for Industrial Application. Proc. Des. Soc. 2022, 2, 293–302. [Google Scholar] [CrossRef]
- Stjepandić, J.; Sommer, M.; Stobrawa, S. Digital twin: Conclusion and future perspectives. In DigiTwin: An Approach for Production Process Optimization in a Built Environment; Springer: Cham, Switzerland, 2022; pp. 235–259. [Google Scholar]
- Wei, L.; Yang, Y.; Wu, J.; Long, C.; Li, B. Trust management for Internet of Things: A comprehensive study. IEEE Internet Things J. 2022, 9, 7664–7679. [Google Scholar] [CrossRef]
- Rein, A.; Rieke, R.; Jäger, M.; Kuntze, N.; Coppolino, L. Trust establishment in cooperating cyber-physical systems. In Proceedings of the Security of Industrial Control Systems and Cyber Physical Systems: First Workshop, CyberICS 2015, Vienna, Austria, 21–22 September 2015; Springer: Berlin/Heidelberg, Germany, 2016; pp. 31–47. [Google Scholar]
- Mohammadi, G. Trustworthy Cyber-Physical Systems; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Mohammadi, V.; Rahmani, A.M.; Darwesh, A.M.; Sahafi, A. Trust-based recommendation systems in Internet of Things: A systematic literature review. Hum.-Centric Comput. Inf. Sci. 2019, 9, 21. [Google Scholar] [CrossRef]
- Ly, K.; Sun, W.; Jin, Y. Emerging challenges in cyber-physical systems: A balance of performance, correctness, and security. In Proceedings of the 2016 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 498–502. [Google Scholar]
- Samir, K.; Khabbazi, M.; Maffei, A.; Onori, M.A. Key Performance Indicators in Cyber-Physical Production Systems. Procedia CIRP 2018, 72, 498–502. [Google Scholar] [CrossRef]
- Bhuiyan, M.Z.A.; Kuo, S.Y.; Lyons, D.; Shao, Z. Dependability in cyber-physical systems and applications. ACM Trans. -Cyber-Phys. Syst. 2018, 3, 1. [Google Scholar] [CrossRef]
- Miller, M.E.; Spatz, E. A unified view of a human digital twin. Hum.-Intell. Syst. Integr. 2022, 4, 23–33. [Google Scholar] [CrossRef]
- Azzedin, F.; Suwad, H.; Rahman, M.M. An Asset-Based Approach to Mitigate Zero-Day Ransomware Attacks. Comput. Mater. Contin. 2022, 73, 3003–3020. [Google Scholar] [CrossRef]
- Alyami, S.; Alharbi, R.; Azzedin, F. Fragmentation attacks and countermeasures on 6LoWPAN Internet of Things networks: Survey and simulation. Sensors 2022, 22, 9825. [Google Scholar] [CrossRef]
- Campos-Ferreira, A.E.; Lozoya-Santos, J.d.J.; Vargas-Martínez, A.; Mendoza, R.; Morales-Menéndez, R. Digital twin applications: A review. In Memorias del Congreso Nacional de Control Automático; Asociación de México de Control Automático: Puebla, Mexico, 2019; Volume 2, pp. 606–611. [Google Scholar]
- Harper, K.E.; Ganz, C.; Malakuti, S. Digital twin architecture and standards. IIC J. Innov. 2019, 12, 72–83. [Google Scholar]
- Juarez, M.G.; Botti, V.J.; Giret, A.S. Digital twins: Review and challenges. J. Comput. Inf. Sci. Eng. 2021, 21, 030802. [Google Scholar] [CrossRef]
- Singh, S.; Weeber, M.; Birke, K.P. Advancing digital twin implementation: A toolbox for modelling and simulation. Procedia CIRP 2021, 99, 567–572. [Google Scholar] [CrossRef]
- Ran, Y.; Zhou, X.; Lin, P.; Wen, Y.; Deng, R. A survey of predictive maintenance: Systems, purposes and approaches. arXiv 2019, arXiv:1912.07383. [Google Scholar]
- Lim, K.Y.H.; Zheng, P.; Chen, C.H. A state-of-the-art survey of Digital Twin: Techniques, engineering product lifecycle management and business innovation perspectives. J. Intell. Manuf. 2020, 31, 1313–1337. [Google Scholar] [CrossRef]
- Rathore, M.M.; Shah, S.A.; Shukla, D.; Bentafat, E.; Bakiras, S. The role of ai, machine learning, and big data in digital twinning: A systematic literature review, challenges, and opportunities. IEEE Access 2021, 9, 32030–32052. [Google Scholar] [CrossRef]
- Fuller, A.; Fan, Z.; Day, C.; Barlow, C. Digital twin: Enabling technologies, challenges and open research. IEEE Access 2020, 8, 108952–108971. [Google Scholar] [CrossRef]
- Suhail, S.; Hussain, R.; Jurdak, R.; Oracevic, A.; Salah, K.; Hong, C.S.; Matulevičius, R. Blockchain-based digital twins: Research trends, issues, and future challenges. ACM Comput. Surv. (Csur) 2022, 54, 1–34. [Google Scholar] [CrossRef]
- Raj, P. Empowering digital twins with blockchain. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2021; Volume 121, pp. 267–283. [Google Scholar]
- Suhail, S.; Hussain, R.; Jurdak, R.; Hong, C.S. Trustworthy digital twins in the industrial internet of things with blockchain. IEEE Internet Comput. 2021, 26, 58–67. [Google Scholar] [CrossRef]
- Putz, B.; Dietz, M.; Empl, P.; Pernul, G. Ethertwin: Blockchain-based secure digital twin information management. Inf. Process. Manag. 2021, 58, 102425. [Google Scholar] [CrossRef]
- Rivera, L.F.; Jiménez, M.; Villegas, N.M.; Tamura, G.; Müller, H.A. The forging of autonomic and cooperating digital twins. IEEE Internet Comput. 2021, 26, 41–49. [Google Scholar] [CrossRef]
- Kuruppuarachchi, P.; Rea, S.; McGibney, A. Trust and security analyzer for collaborative digital manufacturing ecosystems. In Proceedings of the International Symposium on Leveraging Applications of Formal Methods, Rhodes, Greece, 22–30 October 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 208–218. [Google Scholar]
- Bonney, M.S.; de Angelis, M.; Dal Borgo, M.; Wagg, D.J. Contextualisation of information in digital twin processes. Mech. Syst. Signal Process. 2023, 184, 109657. [Google Scholar] [CrossRef]
- Voas, J.; Mell, P.; Piroumian, V. Considerations for Digital Twin Technology and Emerging Standards. 2021. Available online: https://csrc.nist.gov/pubs/ir/8356/ipd (accessed on 1 November 2025).
- Newrzella, S.R.; Franklin, D.W.; Haider, S. Three-dimension digital twin reference architecture model for functionality, dependability, and life cycle development across industries. IEEE Access 2022, 10, 95390–95410. [Google Scholar] [CrossRef]
- Thelen, A.; Zhang, X.; Fink, O.; Lu, Y.; Ghosh, S.; Youn, B.D.; Todd, M.D.; Mahadevan, S.; Hu, C.; Hu, Z. A comprehensive review of digital twin—Part 1: Modeling and twinning enabling technologies. Struct. Multidiscip. Optim. 2022, 65, 354. [Google Scholar] [CrossRef]
- Wunderlich, A.; Booth, K.; Santi, E. Hybrid analytical and data-driven modeling techniques for digital twin applications. In Proceedings of the 2021 IEEE Electric Ship Technologies Symposium (ESTS), Arlington, VA, USA, 3–6 August 2021; pp. 1–7. [Google Scholar]
- Azzedin, F. Mitigating denial of service attacks in RPL-based IoT environments: Trust-based approach. IEEE Access 2023, 11, 129077–129089. [Google Scholar] [CrossRef]
- Aheleroff, S.; Xu, X.; Zhong, R.Y.; Lu, Y. Digital twin as a service (DTaaS) in industry 4.0: An architecture reference model. Adv. Eng. Inform. 2021, 47, 101225. [Google Scholar] [CrossRef]
- Fang, L.; Shi, X.; Song, S.; Wang, X. Study on IIoT-based Safety Platform of Industrial Enterprises. In Proceedings of the 2022 Prognostics and Health Management Conference (PHM-2022 London), London, UK, 27–29 May 2022; IEEE: New York, NY, USA, 2022; pp. 415–419. [Google Scholar]
- Premalatha, J.; Rajasekar, V. Industrial Internet of Things Safety and Security. In Internet of Things; CRC Press: Boca Raton, FL, USA, 2020; pp. 135–152. [Google Scholar]
- Khan, W.Z.; Rehman, M.; Zangoti, H.M.; Afzal, M.K.; Armi, N.; Salah, K. Industrial internet of things: Recent advances, enabling technologies and open challenges. Comput. Electr. Eng. 2020, 81, 106522. [Google Scholar] [CrossRef]
- Bertino, E.; Sandhu, R.; Thuraisingham, B.; Ray, I.; Li, W.; Gupta, M.; Mittal, S. Security and Privacy for Emerging IoT and CPS Domains. In Proceedings of the Twelfth ACM Conference on Data and Application Security and Privacy, Baltimore, MD, USA, 24–27 April 2022; pp. 336–337. [Google Scholar]
- Moore, S.J.; Nugent, C.D.; Zhang, S.; Cleland, I. IoT reliability: A review leading to 5 key research directions. CCF Trans. Pervasive Comput. Interact. 2020, 2, 147–163. [Google Scholar] [CrossRef]
- Gajek, S.; Lees, M.; Jansen, C. IIoT and cyber-resilience: Could blockchain have thwarted the Stuxnet attack? AI Soc. 2021, 36, 725–735. [Google Scholar] [CrossRef]
- Gupta, A.; Christie, R.; Manjula, R. Scalability in internet of things: Features, techniques and research challenges. Int. J. Comput. Intell. Res. 2017, 13, 1617–1627. [Google Scholar]
- Xing, L. Reliability in Internet of Things: Current status and future perspectives. IEEE Internet Things J. 2020, 7, 6704–6721. [Google Scholar] [CrossRef]
- Ali, Z.H.; Ali, H.A.; Badawy, M.M. Internet of Things (IoT): Definitions, Challenges, and Recent Research Directions. Int. J. Comput. Appl. 2015, 128, 975–8887. [Google Scholar] [CrossRef]
- Al-Hejri, I.; Azzedin, F.; Almuhammadi, S.; Syed, N.F. Enabling Efficient Data Transmission in Wireless Sensor Networks-Based IoT Applications. Comput. Mater. Contin. 2024, 79, 4197–4218. [Google Scholar] [CrossRef]
- Attaran, M.; Celik, B.G. Digital Twin: Benefits, use cases, challenges, and opportunities. Decis. Anal. J. 2023, 6, 100165. [Google Scholar] [CrossRef]
- Atkinson, C.; Kühne, T. Taming the complexity of digital twins. IEEE Softw. 2021, 39, 27–32. [Google Scholar] [CrossRef]
- Lu, J.; Zheng, X.; Schweiger, L.; Kiritsis, D. A cognitive approach to manage the complexity of digital twin systems. In Smart Services Summit: Digital as an Enabler for Smart Service Business Development; Springer: Berlin/Heidelberg, Germany, 2021; pp. 105–115. [Google Scholar]
- Wang, B.T.; Burdon, M. Automating trustworthiness in digital twins. In Automating Cities; Springer: Berlin/Heidelberg, Germany, 2021; pp. 345–365. [Google Scholar]
- Ghaleb, M.; Azzedin, F. Trust-aware Fog-based IoT environments: Artificial reasoning approach. Appl. Sci. 2023, 13, 3665. [Google Scholar] [CrossRef]
- Wright, L.; Davidson, S. How to tell the difference between a model and a digital twin. Adv. Model. Simul. Eng. Sci. 2020, 7, 13. [Google Scholar] [CrossRef]
- Tao, F.; Xiao, B.; Qi, Q.; Cheng, J.; Ji, P. Digital twin modeling. J. Manuf. Syst. 2022, 64, 372–389. [Google Scholar] [CrossRef]
- Abbasi, M.A.; Memon, Z.A.; Durrani, N.M.; Haider, W.; Laeeq, K.; Mallah, G.A. A multi-layer trust-based middleware framework for handling interoperability issues in heterogeneous IoTs. Clust. Comput. 2021, 24, 2133–2160. [Google Scholar] [CrossRef]
- Huang, H.; Khan, L.; Zhou, S. Classified enhancement model for big data storage reliability based on Boolean satisfiability problem. Clust. Comput. 2020, 23, 483–492. [Google Scholar] [CrossRef]
- Hu, X.; Chu, L.; Pei, J.; Liu, W.; Bian, J. Model complexity of deep learning: A survey. Knowl. Inf. Syst. 2021, 63, 2585–2619. [Google Scholar] [CrossRef]
- Cronrath, C.; Aderiani, A.R.; Lennartson, B. Enhancing digital twins through reinforcement learning. In Proceedings of the 2019 IEEE 15th International Conference on Automation Science and Engineering (CASE), Vancouver, BC, Canada, 22–26 August 2019; pp. 293–298. [Google Scholar]
- Alcaraz, C.; Cazorla, L.; Fernandez, G. Context-awareness using anomaly-based detectors for smart grid domains. In Proceedings of the Risks and Security of Internet and Systems: 9th International Conference, CRiSIS 2014, Trento, Italy, 27–29 August 2014; Springer: Berlin/Heidelberg, Germany, 2015; pp. 17–34. [Google Scholar]
- Sagiroglu, S.; Sinanc, D. Big data: A review. In Proceedings of the 2013 International Conference on Collaboration Technologies and Systems (CTS), San Diego, CA, USA, 20–24 May 2013; pp. 42–47. [Google Scholar]
- Löcklin, A.; Müller, M.; Jung, T.; Jazdi, N.; White, D.; Weyrich, M. Digital twin for verification and validation of industrial automation systems—A survey. In Proceedings of the 2020 25th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Vienna, Austria, 8–11 September 2020; Volume 1, pp. 851–858. [Google Scholar]
- Rokka Chhetri, S.; Al Faruque, M.A. IoT-enabled living digital twin modeling. In Data-Driven Modeling of Cyber-Physical Systems Using Side-Channel Analysis; Springer: Cham, Switzerland, 2020; pp. 155–182. [Google Scholar]
- Bandi, A.; Heeler, P. Usability testing: A software engineering perspective. In Proceedings of the 2013 International Conference on Human Computer Interactions (ICHCI), Chennai, India, 23–24 August 2013; pp. 1–8. [Google Scholar]
- Boyes, H.; Watson, T. Digital twins: An analysis framework and open issues. Comput. Ind. 2022, 143, 103763. [Google Scholar] [CrossRef]
- Yuan, S.; Han, B.; Krummacker, D.; Schotten, H.D. Massive twinning to enhance emergent intelligence. In Proceedings of the 2022 IEEE Symposium on Computers and Communications (ISCC), Rhodes, Greece, 30 June–3 July 2022; pp. 1–4. [Google Scholar]
- Gardner, P.; Dal Borgo, M.; Ruffini, V.; Hughes, A.J.; Zhu, Y.; Wagg, D.J. Towards the development of an operational digital twin. Vibration 2020, 3, 235–265. [Google Scholar] [CrossRef]
- Olivier, A.; Giovanis, D.G.; Aakash, B.; Chauhan, M.; Vandanapu, L.; Shields, M.D. UQpy: A general purpose Python package and development environment for uncertainty quantification. J. Comput. Sci. 2020, 47, 101204. [Google Scholar] [CrossRef]
- Barricelli, B.R.; Casiraghi, E.; Gliozzo, J.; Petrini, A.; Valtolina, S. Human digital twin for fitness management. IEEE Access 2020, 8, 26637–26664. [Google Scholar] [CrossRef]
- Suhail, S.; Zeadally, S.; Jurdak, R.; Hussain, R.; Matulevičius, R.; Svetinovic, D. Security attacks and solutions for digital twins. arXiv 2022, arXiv:2202.12501. [Google Scholar]
- Redelinghuys, A.; Basson, A.H.; Kruger, K. A six-layer architecture for the digital twin: A manufacturing case study implementation. J. Intell. Manuf. 2020, 31, 1383–1402. [Google Scholar] [CrossRef]
- Azzedin, F.A. Trust Modeling and Its Applications for Peer-to-Peer Based Systems. Ph.D. Thesis, University of Manitoba, Winnipeg, MB, Canada, 2004. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).