Abstract
A covert communication scheme is designed for pinching antenna (PA)-enabled integrated sensing and communication (ISAC) systems. The base station (BS) emits sensing signals to detect the potential eavesdropper while opportunistically performing covert multicast transmissions. To enhance covertness, the inherent power uncertainty of the sensing signals is exploited to confuse eavesdroppers, thereby creating protective coverage for the legitimate transmission. For the considered systems, we design an alternating optimization framework to iteratively optimize the baseband, beamforming, and PA positionson the two waveguides, in which successive convex approximation and particle swarm optimization methods are introduced. Simulated results confirm that the proposed scheme achieves the highest covert communication rates with different numbers of multicast users compared to benchmark methods. Furthermore, increasing the transmit power and the number of PAs can further improve the covertness performance.
1. Introduction
To address the requirements of new applications such as autonomous driving and the metaverse, Integrated Sensing and Communications (ISAC) has become a prominent research topic [1]. In ISAC systems, wireless communications and radar sensing share the same spectrum and hardware infrastructure, enabling more efficient and cost-effective system designs [2].
Because of the openness and broadcasting nature of ISAC systems, confidential information encoded in the waveform is vulnerable to interception and eavesdropping. This risk is particularly prominent when the sensing target is a malicious node that may eavesdrop on legitimate transmissions. There has been some research studying covert communication [3] in ISAC, ensuring an extremely low interception probability [4,5,6,7,8,9] and hiding communications behavior, which naturally prevents confidential information from being intercepted. Reference [4] proposes a covert beamforming design framework to maximize the mutual information of radar, ensuring covert transmission. Reference [5] exploits dual-functional artificial noise with diverse power to confuse the eavesdropper and sense the targets simultaneously. The authors of [6] maximized the minimum data rate achievable by legitimate users, with constraints on the total transmit power, covert communication requirements for multiple wardens, and a minimum SNR threshold for each target to be detected. Reference [7] employs a reconfigurable intelligent surface (RIS) technique to dynamically control the wireless propagation environment by adjusting the incoming signals, thereby enhancing desired signals and suppressing unwanted reflections to improve covert communication performance. The authors of [8] proposed an active RIS-assisted covert communication system based on NOMA-ISAC and enhanced the covert rate through joint optimization of both transmission and reflection beamforming. Additionally, reference [9] proposes a joint beamforming and Unmanned Aerial Vehicle (UAV) trajectory design to enhance covertness in an ISAC system.
An enabling technique such as the use of Pinching Antennas (PAs) [10,11,12] is introduced in an ISAC system. The deposition of dielectric particles at designated locations on a dielectric waveguide enables the activation of PAs to generate controlled electromagnetic radiation fields, thereby defining specific communication zones [13]. These advantages of PAs have motivated some works to explore PA system (PASS) integrated with ISAC [14,15,16,17]. Reference [14] derives the Cramér–Rao Lower Bound (CRLB) for PASS-ISAC systems, demonstrating significant CRLB reduction compared to traditional systems. Reference [15] addresses the joint optimization of the communication rate and radar performance by developing a maximum-entropy reinforcement learning technique. Reference [16] maximizes sensing power under communication constraints for systems with single-transmit and single-receive waveguides. Reference [17] further characterizes the performance boundary using communication and sensing rates as metrics.
These pioneering works show the superiority of integrating PAs with ISAC for high-efficiency transmission. Additionally, the potential of PAs to enhance transmission security has gradually drawn attention. As shown in Table 1, a small number of studies have begun to use PAs to achieve physical-layer security (PLS) [18,19,20] and covert communication (CC) [21] in a system without ISAC. However, PA-enabled ISAC covert communications remain a research gap. Unlike PLS [18,19,20], we noticed that the integration of PAs and ISAC will bring about the dual promotion of covert communications: On the one hand, unlike PLS, which safeguards communication security at the information level, covert communication ensures that communication signals remain undetected at the signal level. This fundamental distinction leads to differences in optimization objectives, performance metrics, and other key aspects when designing PA systems [22,23]. On the other hand, the integration of PAs and ISAC will bring about the dual promotion on covert communications: (1) ISAC leverages its sensing capability to provide eavesdropper location information, thereby facilitating covert beamforming. Meanwhile, PAs can be dynamically repositioned to increase echo signal energy, further improving covert communication effectiveness. (2) PAs can move along the waveguide over tens of meters, enabling repositioning to the nearest receiver and creating reliable Line-of-Sight (LoS) links. (3) PAs significantly reduce both system complexity and implementation costs compared to relay- or UAV-assisted covert communication. PAs eliminate the need for predefined relay protocols, complex trajectory planning, and expensive hardware, relying instead on low-cost dielectric waveguides and power amplifiers.

Table 1.
Comparison of related works.
Motivated by the aforementioned observation, we focus on leveraging these advantages for covert communication. We investigate a waveguide multiplexing-based PA-assisted ISAC multicast covert communication system design. In this system, the BS is connected to two dielectric waveguides, transmitting both multicast communication signals and sensing signals to detect the eavesdropper while exploiting the power uncertainty of sensing signals to further confuse the eavesdropper. The main innovations and research contributions are summarized as follows:
- A waveguide multiplexing-based PA-assisted ISAC multicast covert communication system is proposed, where the BS connects to two dielectric waveguides, each embedded with multiple pinching antennas (PAs). Beyond transmitting multicast signals, the BS simultaneously emits sensing signals to detect a potential eavesdropper. The sensing signal also serves as artificial noise to interfere with the eavesdropper. Furthermore, the inherent power uncertainty of sensing signals is exploited to confuse the eavesdropper, thereby enhancing the covertness for legitimate users.
- Considering the eavesdropper adaptive detection threshold adjustment, we derive the minimum detection error probability (DEP). We formulate the problem in terms of maximizing the lowest achievable covert rate to guarantee a minimum quality of service for every user while satisfying both sensing illumination power requirements and covertness constraints, and an alternating optimization (AO) algorithm is designed, which iteratively optimizes the baseband beamforming through successive convex approximation (SCA) and PA positions on both waveguides through particle swarm optimization (PSO) methods.
- Simulated results show that the covert communication rate declines as the number of users increases; however, the proposed approach achieves the highest covert communication rates compared to benchmark schemes. When the sensing illumination power requirement increases, more BS power is allocated to sensing, leading to reduced covert communication rates.
2. System Model
As illustrated in Figure 1, we consider the covert communications in a PA-assisted ISAC system, where a BS multicasts to M single-antenna legitimate users while sensing an illegitimate eavesdropper. The BS is linked to two dielectric waveguides, each of length L, with one waveguide dedicated to the communication signal and the other to sending the sensing signal. Each waveguide is outfitted with N pinching antennas, represented by the set expressed as . For the p-th waveguide, the location of the n-th pinching antenna is formulated as in a three-dimensional coordinate system, where corresponds waveguide 1 and corresponds to waveguide 2. The coordinate of the m-th communication user is . Similarly, the eavesdropper is located at . The BS intends to transmit covert information to the legitimate single-antenna users through downlink transmission in the presence of the eavesdropper. In addition to this legitimate transmission, the single-antenna eavesdropper aims to detect the covert transmission activities.
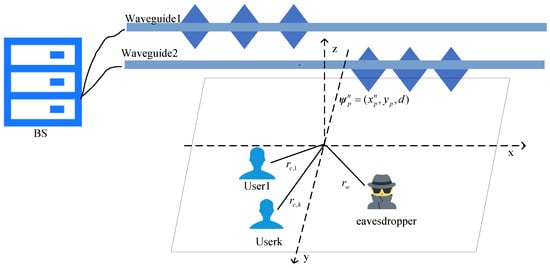
Figure 1.
PA-assisted ISAC multicast covert communication system.
As illustrated in Figure 2, the sensing signal not only detects the eavesdropper but also acts as the shelter to create uncertainty at the eavesdropper. The transmit power of the sensing signal () is uniformly distributed over the interval of , i.e.,
where and correspond to the minimum and the maximum of the sensing signal’s total transmit power. We assume the eavesdropper knows the distribution of but cannot obtain its instantaneous power value. This ambiguity prevents the eavesdropper from distinguishing whether fluctuations in received signal power originate from active covert transmissions or natural variations in . Besides assisting in covert signal transmission between the BS and legitimate users (ensuring low detection probability at the eavesdropper), the sensing signal also serves to enhance sensing functionality.
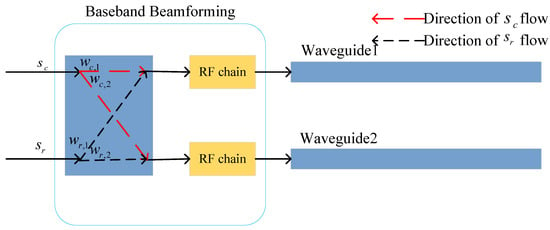
Figure 2.
PA-assisted ISAC multicast covert communication architecture based on waveguide multiplexing.
2.1. Transmission Scheme
Let denote the multicast communication, where . The precoded signal can be expressed as . The precoded symbol is then up-converted through the radio frequency (RF) chain and introduced to the waveguide at position . In the p-th waveguide, the controllable intra-waveguide phase shift for the input signal at N PAs is denoted by
where represents the power-scaling factor of the n-th PA. To simplify the analysis, we assume equal power allocation among N PAs, i.e., , where denotes the radiation coefficient of PAs. The phase shift introduced to the n-th PA by feed point can be given by
where refers the guided wavelength in the waveguide, denotes the guided wavenumber, represents the guided wavelength, and denotes the effective refractive index of the waveguide [9]. The channel responses within the two waveguides can be modeled as follows:
For the considered high-frequency regime, the LoS-dominant model is widely used to approximate the the free-space channel. Let denote the channel vector between the p-th waveguide and user m. The resultant free-space channel vector is given by
where each element is expressed as follows:
where , c is the speed of light, with as the carrier frequency and as the free-space wavenumber. Moreover, denotes the Euclidean distance from the n-th PA on the p-th waveguide to user m. The BS transmits sensing signals to confuse the eavesdropper when detecting covert data transmission. The sensing signal is defined as , which satisfies , where represents the symbol index. Let denote the hypothesis that the BS is not transmitting private data to the communication users and denote the hypothesis that covert transmission is ongoing. Under , the BS transmits only the sensing signal () with the normalized covariance matrix () to the eavesdropper, aiming to both sense the target and confuse the eavesdropper. Under , in addition to , the BS transmits the covert communication signal () to the legitimate users. We use to denote the corresponding transmit beamforming vector. We assume that the sensing signal is independent of the information symbols (). Therefore, from the eavesdropper’s perspective, the transmitted signal is
2.2. Covert Communications
During covert communication, under , the received signal at communication user m is
where represents additive white Gaussian noise (AWGN) affecting user m with zero mean and variance (). Since follows a uniform distribution, . Thus, the covert communication rate at user m is
Under , the signal received by the communication user is given by
Although under , the received signal is irreducible noise, due to the randomness of , this noise can actually be exploited to assist in covert communication between the BS and users and simultaneously sense communication users, reducing overhead without CSI feedback.
On the other hand, the eavesdropper attempts to detect covert communication by a Neyman–Pearson test of the received signal (). The received signal at the eavesdropper is expressed as follows:
where is AWGN at the eavesdropper with zero mean and variance (). The eavesdropper uses the average received power (i.e., ) as the test statistic with the following decision rule:
where is the detection threshold and and represent the binary decisions favoring and , respectively. For , the average received power at the eavesdropper is given by
The detection error probability () at the eavesdropper is expressed as follows:
where represents the total error probability and is the missed detection probability. Furthermore, is the false-alarm probability.
where , . When , the minimum value of is . In this case, covert communication cannot be achieved. When , the eavesdropper’s DEP is given by
When , , so is a monotonically decreasing function. When , , so is a monotonically increasing function. Therefore, when lies in the interval of , DEP is the minimum, i.e.,
It should be noted that to realize covert communication, the covertness constraint condition () must be satisfied. The covertness constraint conditions of and can be respectively derived as follows:
The left-hand sides of inequalities (19) and (20) are equal, while the right-hand side of inequality (20) is the right-hand side of inequality (19) multiplied by an additional . Due to , if inequality (20) holds, inequality (19) must necessarily hold; thus, inequality (19) can be omitted.
2.3. Sensing Metric
We use illumination power [16] as a performance metric. Since the sensing signal follows a uniform distribution, the expected received illumination power at the target is given by
3. Problem Formulation and Solution
In covert communication, BS maximizes the minimum covert communication rate among all multicast users while hiding legitimate transmissions from the eavesdropper by increasing its total error probability. The optimization problem can be formulated as follows:
where , , and represents the total power budget. The power constraint (22d) ensures the total power budget. (22c) is the covertness constraint, with typically set to a small value to guarantee transmission covertness. (22b) represents the sensing illumination power constraint. (22e) is the normalization constraint for the sensing signal beamforming matrix. (22f) specifies the minimum spacing () between adjacent PAs. (22g) defines the feasible region for PA positions on the waveguide. (22h) and (22i) are the rank-1 constraints.
The difficulty in solving problem (22) is the joint optimization of baseband beamforming variables and PA positions, which is tightly coupled and complex. To overcome this challenge, we design an alternating optimization framework to decouple the original problem into two subproblems. An iterative procedure is employed to solve these subproblems successively, utilizing both PSO and SCA techniques.
3.1. Pinching Antenna Position Optimization
Given fixed and , the original problem (22) can be transformed into the following form:
We employ the PSO algorithm to address this challenging problem. First, we introduce a particle swarm comprising q individuals. The position of the n-th PA along waveguide 1 (waveguide 2) is given by (), as shown below:
To comply with constraint (22g), all initial values () are set within the interval of . Accordingly, the initial velocity is defined as follows:
Following [25], the i-th particle updates its position according to its own historical best position () and the global best position of the entire swarm (). The equation for iterative updates is formulated as follows:
where l represents the iteration index and represents the inertia weight, which balances global and local search. A higher promotes exploration at the expense of individual refinement, while a lower value has the converse effect. To improve performance, decreases linearly during within the range of , with the update step size expressed as . Coefficients and are learning factors. Random variables and are distributed between 0 and 1, introducing randomness to enhance search diversity and prevent premature convergence. After each position update, a boundary check ensures particles remain within , ensuring continuous satisfaction of constraint (22f).
The fitness evaluation for each particle during every iteration is performed using the unconstrained problem (23). Given the position (), the minimum user secrecy rate can be derived from (9) and denoted as . In addition, to ensure the constraints of problem (23), the penalty coefficient () is introduced into the fitness function, which is updated as follows:
where is the penalty term; is the penalty factor; and is used to count the total number of times that the current PA position violates the constraints of problem (23), as given by the following formula:
where k denotes the indicator function. If the condition inside the parentheses holds, it is equal to 1; otherwise, it is equal to 0. As the fitness of each particle is evaluated, both their individual and collective best positions undergo iterative refinement until convergence is achieved.
3.2. Baseband Beamforming Optimization
Given the PA positions, the original problem degenerates into a traditional beamforming problem. At this time, this sub-problem is expressed as a semidefinite programming (SDP) problem:
To solve problem (30), we introduce an auxiliary variable and restate the problem as follows:
where denotes the minimum covert communication rate among all multicast users. By relaxing problem (31) through the omission of the rank-one constraints, we can directly solve it while ensuring the solution’s alignment with the original problem [26]. The proof is provided in Appendix A. Applying the SCA method to , the local point obtained at the j-th iteration is given by
Problem (31) can be transformed into the following form:
Now, problem (33) can be directly solved by CVX.
Convergence: In problem (23), the objective value is non-decreasing due to the retention of globally optimal positions. Similarly, the SCA applied to problem (30) ensures a non-decreasing objective across iterations. Given that problem (22) is a constrained optimization with an upper-bounded objective function, the sequence of objective values generated by the algorithm is guaranteed to converge, leading to eventual termination.
Complexity: The computational cost has two components. The PSO stage requires operations, where denotes the maximum iteration count, I is the population size, and M is the number of waveguides. Meanwhile, solving problem (33) demands computations, with I being the number of SCA iterations. Thus, the computational complexity amounts to [27].
4. Numerical Result
We evaluate the performance of the proposed PA-assisted ISAC multicast covert communication system in this section. We consider a three-dimensional topological network setting. The length of the two dielectrics is 5 m. The carrier frequency is GHz. The height of the waveguide is m, dBm. . . The y-axis coordinates of the two waveguides are and . Additionally, we consider (Hybrid Beamforming (HB) [28,29] and Fully Digital Beamforming (FDB)) [30,31] benchmark schemes:
(1) HB: This configuration employs a base station with two radio frequency (RF) chains positioned at [−L/2, 0, d]. Each RF chain is connected to N conventional antennas. Covert transmission is realized by leveraging sensing signals in conjunction with hybrid beamforming techniques.
(2) FDB: The BS is equipped with RF chains, along with antennas, each matched to one RF chain placed at [−L/2, 0, d]. By incorporating a sensing signal and adopting a fully digital beamforming architecture, the covert performance is effectively enhanced.
Figure 3 demonstrates the convergence of the proposed scheme. It can be observed that all schemes converge to a stable covert rate, ensuring overall convergence in solving the joint optimization problem constructed in this paper. Additionally, a larger covert constraint factor and a greater number of antennas enhance covert performance. This is because a larger covert constraint factor results in a looser covert constraint and more antennas provide more degrees of freedom.
| Algorithm 1: Two-Stage Alternating Optimization Algorithm. |
|
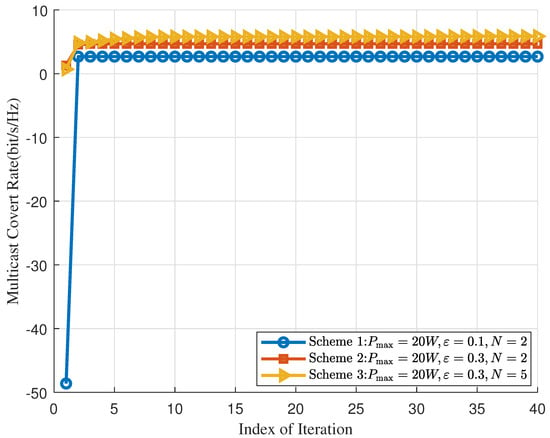
Figure 3.
Convergence behavior of the Algorithm 1.
Figure 4 shows the impact of transmit power on multicast covert rates. Both PASS and the two benchmark schemes exhibit increasing multicast covert rates as the base station’s total power increases. Under all conditions, PA significantly outperforms benchmark schemes due to the strong LoS link, with this performance gain becoming more pronounced as transmit power rises. In comparison with conventional antenna architectures, PASS achieves remarkable gains, owing to its advantages in combating large-scale path loss. Our proposed method achieves the highest covert communication rate. This outcome is anticipated, as the PASS framework effectively harnesses the reconfigurability of PAs to enhance system performance while fully exploiting the advanced signal processing capabilities available at the baseband, thereby yielding superior covert communication rates. FDB consistently surpasses HB, indicating that it provides an excellent balance between performance and system complexity. The physical advantages of FDB over HB lie in two key aspects. Firstly, FDB has more RF chains than HB. This gives FDB considerably more beamforming degrees of freedom for more flexible and precise signal manipulation. Secondly, FDB performs fully digital beamforming, enabling high-precision amplitude and phase control in the digital domain, whereas HB’s hybrid architecture involves analog components with limited precision. These features allow FDB to achieve better covert performance through more accurate signal shaping and power distribution.
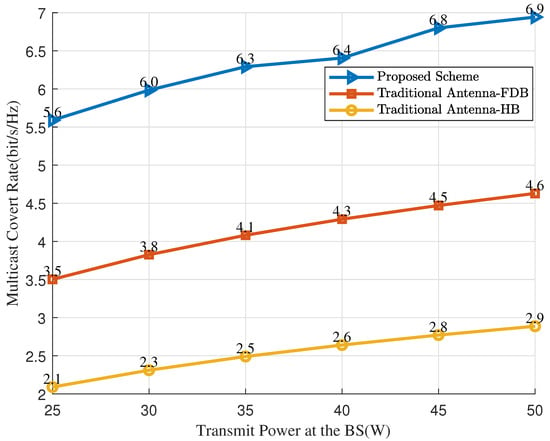
Figure 4.
The multicast covert rate versus the transmit power.
Figure 5 illustrates the relationship between the covert communication rate and the number of PAs. The covert rate improves with increasing N. This enhancement occurs because a larger N offers extra degrees of freedom to enhance covert performance. However, the distance between the PAs and the communication users is observed to increase with the height of the dielectric waveguide, consequently reducing the covert communication rate as height increases.
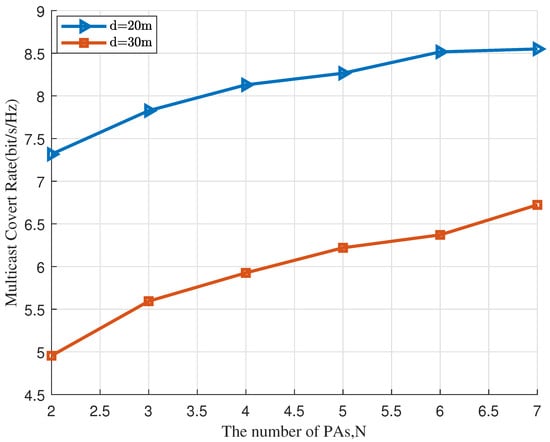
Figure 5.
The multicast covert rate versus the number of PAs (N).
Figure 6 shows the relationship between the covert constraint and the covert rate. As increases, the covert constraint relaxes, and the covert rate increases monotonically. Compared to conventional antenna systems, PASS achieves significant performance gains by leveraging the mobility advantages of its antenna architecture. Among all benchmark schemes, the method proposed in this work attains the highest covert communication rate.
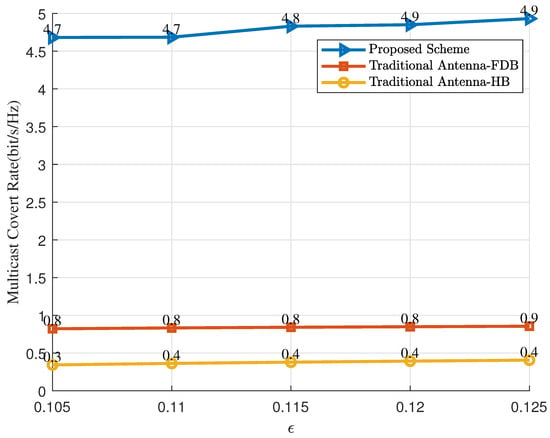
Figure 6.
The multicast covert rate versus the covert communication constraint ().
Figure 7 illustrates the relationship between the number of users and the multicast covert communication rate. The performance of all schemes decreases as the number of users increases. More users have to share limited system resources, and the main beam has to be widened to cover more dispersed user locations, resulting in a reduction in directional gain. However, the proposed scheme outperforms the comparative schemes, as the PAs provide an additional passive beamforming dimension, which, combined with the active beamforming at the base station, enables more precise beam control. As the number of users continues to increase, the beam becomes very wide, and the rate of decline slows down. At this point, further increasing the number of users causes the minimum rate to gradually approach a convergent lower bound.
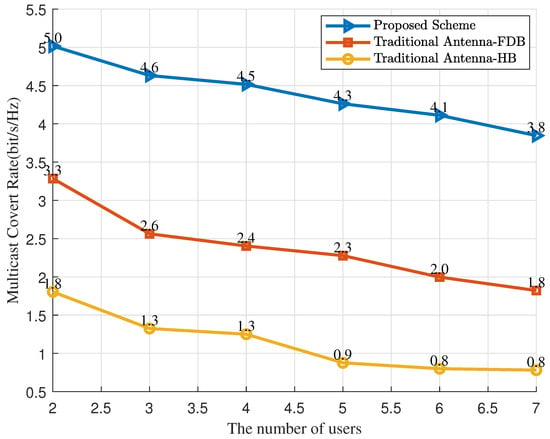
Figure 7.
The multicast covert rate versus the number of users.
5. Conclusions
We proposed a PA-assisted ISAC covert communication system with waveguide multiplexing, in which the uncertainty of sensing signal power is utilized to confuse the eavesdropper to further enhance the system’s covertness. For the considered system, we maximize the minimum covert communication rate among all multicast users through joint optimization of baseband beamforming variables and PA positions. To solve the non-convex problem, we first designed an AO framework; then, the SCA and PSO methods were employed to iteratively optimize the baseband beamforming and the positions of the parasitic antennas on the two waveguides. The simulation results showed that the proposed scheme achieved an average performance improvement of 368% for HB and 204% for FDB. Furthermore, increasing transmit power and the number of PAs can further improve the covertness performance.
Author Contributions
Software, Y.D.; Validation, Y.D.; Data curation, Y.D.; Writing—original draft, Y.D.; Writing—review & editing, B.H.; Visualization, Y.D.; Supervision, L.L., L.Y., Y.Z. and J.C.; Project administration, L.L., L.Y., Y.Z. and J.C.; Funding acquisition, L.L., L.Y., Y.Z. and J.C. All authors have read and agreed to the published version of the manuscript.
Funding
National Natural Science Foundation of China (62201421,62271368, 62371367, 62371354), the Key Research and Development Program of Shaanxi (2023-ZDLGY-50); supported by the Fundamental Research Funds for the Central Universities (QTZX23066), Shaanxi High-Level Talents Special Support Program, Innovation Capability Support Program of Shaanxi under Grant 2024ZC-KJXX-080.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding authors.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
For optimization variables and constraints (33b) and (33c), the Lagrangian is expressed as follows:
where , , and are dual variables.
For ,
For (using , ):
For (using ),
These conditions confirm that the optimal solution of problem (33) satisfies the KKT criteria.
References
- Liu, F.; Masouros, C.; Petropulu, A.P.; Griffiths, H.; Hanzo, L. Joint Radar and Communication Design: Applications, State-of-the-Art, and the Road Ahead. IEEE Trans. Commun. 2020, 68, 3834–3862. [Google Scholar] [CrossRef]
- Liu, F.; Cui, Y.; Masouros, C.; Xu, J.; Han, T.X.; Eldar, Y.C.; Buzzi, S. Integrated Sensing and Communications: Toward Dual-Functional Wireless Networks for 6G and Beyond. IEEE J. Sel. Areas Commun. 2022, 40, 1728–1767. [Google Scholar] [CrossRef]
- Li, W.; Liao, J.; Qian, Y.; Zhou, X.; Lin, Y. A Wireless Covert Communication System: Antenna Coding and Achievable Rate Analysis. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 438–443. [Google Scholar] [CrossRef]
- Ma, S.; Sheng, H.; Yang, R.; Li, H.; Wu, Y.; Shen, C.; Al-Dhahir, N.; Li, S. Covert Beamforming Design for Integrated Radar Sensing and Communication Systems. IEEE Trans. Wirel. Commun. 2023, 22, 718–731. [Google Scholar] [CrossRef]
- Tang, R.; Yang, L.; Lv, L.; Zhang, Z.; Liu, Y.; Chen, J. Dual-Functional Artificial Noise (DFAN) Aided Robust Covert Communications in Integrated Sensing and Communications. IEEE Trans. Commun. 2025, 73, 1072–1086. [Google Scholar] [CrossRef]
- Ghosh, I.; Chattopadhyay, A.; Mishra, K.V.; Petropulu, A.P. Multicast with Multiple Wardens in IRS-Aided Covert DFRC System. In Proceedings of the ICASSP 2024—2024 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Seoul, Republic of Korea, 14–19 April 2024; pp. 12871–12875. [Google Scholar] [CrossRef]
- Liu, Z.; Li, X.; Zhang, H. Exploiting Active RIS for Covert Communication in mmWave ISAC with Finite Blocklength. In Proceedings of the 2024 IEEE 35th International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Valencia, Spain, 2–5 September 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, P.; Xiao, F.; Yang, L.; Tsiftsis, T.A.; Liu, H. Covert Beamforming Design for Active RIS-Assisted NOMA-ISAC Systems. In Proceedings of the 2023 IEEE Globecom Workshops (GC Wkshps), Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 1141–1146. [Google Scholar] [CrossRef]
- Deng, D.; Zhou, W.; Li, X.; da Costa, D.B.; Ng, D.W.K.; Nallanathan, A. Joint Beamforming and UAV Trajectory Optimization for Covert Communications in ISAC Networks. IEEE Trans. Wirel. Commun. 2025, 24, 1016–1030. [Google Scholar] [CrossRef]
- Ding, Z.; Schober, R.; Poor, H.V. Flexible-antenna systems: A pinching-antenna perspective. IEEE Trans. Commun. 2025, 73, 9236–9253. [Google Scholar] [CrossRef]
- Xu, Y.; Ding, Z.; Karagiannidis, G.K. Rate maximization for downlink pinching-antenna systems. IEEE Wirel. Commun. Lett. 2025, 14, 1431–1435. [Google Scholar] [CrossRef]
- Tegos, S.A.; Diamantoulakis, P.D.; Ding, Z.; Karagiannidis, G.K. Minimum Data Rate Maximization for Uplink Pinching-Antenna Systems. IEEE Wirel. Commun. Lett. 2025, 14, 1516–1520. [Google Scholar] [CrossRef]
- Ding, Z.; Poor, H.V. LoS Blockage in Pinching-Antenna Systems: Curse or Blessing? IEEE Wirel. Commun. Lett. 2025, 14, 2798–2802. [Google Scholar] [CrossRef]
- Ding, Z. Pinching-antenna assisted ISAC: A CRLB perspective. arXiv 2025, arXiv:2504.05792. [Google Scholar] [CrossRef]
- Qin, Y.; Fu, Y.; Zhang, H. Joint antenna position and transmit power optimization for pinching antenna-assisted ISAC systems. arXiv 2025, arXiv:2503.12872. [Google Scholar] [CrossRef]
- Zhang, Z.; Liu, Y.; He, B.; Chen, J. Integrated sensing and communications for pinching-antenna systems (PASS). arXiv 2025, arXiv:2504.07709. [Google Scholar] [CrossRef]
- Ouyang, C.; Wang, Z.; Zou, Y.; Liu, Y.; Ding, Z. ISAC Rate Region of Pinching-Antenna Systems. In Proceedings of the 2025 IEEE/CIC International Conference on Communications in China (ICCC Workshops), Shanghai, China, 10–13 August 2025; pp. 1–6. [Google Scholar] [CrossRef]
- Zhu, G.; Mu, X.; Guo, L.; Xu, S.; Liu, Y.; Al-Dhahir, N. Pinching-Antenna Systems (PASS)-enabled Secure Wireless Communications. IEEE Trans. Commun. 2025. [Google Scholar] [CrossRef]
- Sun, M.; Ouyang, C.; Wu, S.; Liu, Y. Physical layer security for pinching-antenna systems (PASS). arXiv 2025, arXiv:2503.09075. [Google Scholar] [CrossRef]
- Wang, K.; Ding, Z.; Al-Dhahir, N. Pinching-Antenna Systems for Physical Layer Security. IEEE Wirel. Commun. Lett. 2025. [Google Scholar] [CrossRef]
- Jiang, H.; Wang, Z.; Liu, Y. Pinching-antenna system (PASS) enhanced covert communications. arXiv 2025, arXiv:2504.10442. [Google Scholar] [CrossRef]
- Feng, R.; Li, Q.; Zhang, Q.; Qin, J. Robust Secure Beamforming in MISO Full-Duplex Two-Way Secure Communications. IEEE Trans. Veh. Technol. 2016, 65, 408–414. [Google Scholar] [CrossRef]
- Jin, Q.; Fan, L.; Lei, X.; Zhao, J.; Nallanathan, A. Covert Communication of Multi-Antenna AF Relaying Networks. IEEE Trans. Commun. 2025, 73, 5699–5714. [Google Scholar] [CrossRef]
- Su, N.; Liu, F.; Masouros, C. Sensing-Assisted Eavesdropper Estimation: An ISAC Breakthrough in Physical Layer Security. IEEE Trans. Wirel. Commun. 2024, 23, 3162–3174. [Google Scholar] [CrossRef]
- Shi, Y.; Eberhart, R. A modified particle swarm optimizer. In Proceedings of the 1998 IEEE International Conference on Evolutionary Computation Proceedings. IEEE World Congress on Computational Intelligence (Cat. No.98TH8360), Anchorage, AK, USA, 4–9 May 1998; pp. 69–73. [Google Scholar]
- Han, Y.; Li, N.; Liu, Y.; Zhang, T.; Tao, X. Artificial Noise Aided Secure NOMA Communications in STAR-RIS Networks. IEEE Wirel. Commun. Lett. 2022, 11, 1191–1195. [Google Scholar] [CrossRef]
- Feng, Y.; Chen, J.; Xue, X.; Wu, K.; Zhou, Y.; Yang, L. Max-Min Fair Beamforming for IRS-Aided Secure NOMA Systems. IEEE Commun. Lett. 2022, 26, 234–238. [Google Scholar] [CrossRef]
- Ci, W.; Qi, C. Finite-Resolution DACs Based Hybrid Beamforming Design for Covert Communications. In Proceedings of the GLOBECOM 2024—2024 IEEE Global Communications Conference, Cape Town, South Africa, 8–12 December 2024; pp. 4642–4647. [Google Scholar] [CrossRef]
- Zhu, Z.; You, B.; Li, Z.; Mu, J.; Yang, S.; Lee, I. Hybrid Beamforming and Sensing Design for Near-Field Covert Communication. In Proceedings of the ICC 2025—IEEE International Conference on Communications, Montreal, QC, Canada, 8–12 June 2025; pp. 2284–2289. [Google Scholar] [CrossRef]
- Gao, W.; Xie, Z.; Wang, Y.; Yao, Y.; Jiang, H.; Shu, F. Covert Beamforming Design for Holographic Integrated Sensing and Communication with Imperfect CSI. IEEE Internet Things J. 2025, 12, 48043–48059. [Google Scholar] [CrossRef]
- Jia, H.; Ma, L.; Chen, S.; Qin, D. Joint Secure and Covert Beamforming Design in Dual-Functional Radar-Communication Systems. In Proceedings of the 2024 IEEE International Conference on Communications Workshops (ICC Workshops), Denver, CO, USA, 9–13 June 2024; pp. 1213–1218. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).