Abstract
Cybersecurity has become a critical concern in the automotive sector, where the increasing connectivity and complexity of modern vehicles—particularly in the context of autonomous driving—have significantly expanded the attack surface. In response to these challenges, this paper presents the Welcome To The Machine (WTTM) framework, developed to support proactive and structured cyber risk management throughout the entire vehicle lifecycle. Specifically tailored to the automotive domain, the framework encompasses four core actions: detection, analysis, response, and remediation. A central element of WTTM is the WTTM Questionnaire, designed to assess the organizational cybersecurity maturity of automotive manufacturers and suppliers. The questionnaire addresses six key areas: Governance, Risk Management, Concept and Design, Security Requirements, Validation and Testing, and Supply Chain. This paper focuses on the development and validation of WTTM-Q. Statistical validation was performed using responses from 43 participants, demonstrating high internal consistency (Cronbach’s alpha > 0.70) and strong construct validity (CFI = 0.94, RMSEA = 0.061). A supervised classifier (XGBoost), trained on 115 hypothetical response configurations, was employed to predict a priori risk classes, achieving 78% accuracy and a ROC AUC of 0.84. The WTTM framework, supported by a Vehicle Security Operations Center, provides a scalable, standards-aligned solution for enhancing cybersecurity in the automotive industry.
1. Introduction
Modern vehicles are rapidly evolving into complex, software-defined systems with extensive and continuous connectivity to the external environment. This transformation—driven by the integration of real-time navigation, predictive maintenance, and advanced driver assistance systems—has significantly expanded the vehicle’s attack surface and introduced new cybersecurity risks. These risks go beyond unauthorized access to sensitive user data—such as geolocation, usage patterns, and lifestyle habits—and extend to critical safety concerns. A successful cyberattack can compromise onboard systems and potentially endanger passengers, pedestrians, cyclists, and other road users. These threats become particularly critical in the context of autonomous driving, where safety is intrinsically linked to software integrity and system resilience.
In response to these challenges, the automotive cybersecurity field has matured from early foundational work—based on attack trees and qualitative checklists [1,2]—to the development of more structured, quantitative methodologies. Prominent frameworks such as EVITA and HEAVENS have introduced formalized approaches to risk analysis and component certification, blending qualitative insights with robust quantitative metrics [3,4]. At the same time, taxonomies have been proposed to classify cyberattacks in intra-vehicle and V2X (vehicle-to-everything) communication contexts [5,6,7], supporting more systematic threat identification and mitigation. This methodological evolution is complemented by regulatory advancements: the ISO/SAE 21434:2021 standard now defines engineering requirements for cybersecurity risk management across the entire vehicle lifecycle, emphasizing structured threat modeling and secure-by-design development practices [3]. Similarly, the UNECE WP.29 regulation (UN R155/R156) mandates that manufacturers implement a Cybersecurity Management System (CSMS) and comply with secure software update procedures to obtain type approval [4].
Despite these advances, the automotive sector still faces challenges arising from increasingly complex supply chains and uneven levels of cybersecurity maturity across organizations. To bridge these gaps, recent research has introduced a variety of practical tools—including self-assessment questionnaires, operational checklists, and structured evaluation metrics—to support risk analysis and organizational readiness. Notably, Eskandarian et al. proposed a framework using structured questionnaires for cybersecurity vulnerability assessment [8,9], while other contributions have demonstrated how automated penetration testing and quantitative metrics can improve software robustness [10,11]. Guidelines issued by the NHTSA [12] and recent sector-wide surveys [13] further highlight the importance of integrating self-assessment mechanisms and resilience strategies from the design phase through to ongoing auditing and system maintenance.
In this context, this paper presents WTTM (“Welcome To The Machine”), an innovative and comprehensive framework developed to address emerging cybersecurity challenges in connected vehicles. WTTM is designed to support OEMs, suppliers, and system integrators in aligning with international standards such as ISO/SAE 21434 and WP.29, while fostering a proactive “security by design” culture tailored to the specific needs of the automotive domain. The framework—developed through European R&D funding—is based on a modular and scalable architecture and is organized into four sequential phases: (1) requirements analysis; (2) development of a multi-level cyber risk framework compliant with the TARA methodology outlined in ISO/SAE 21434; (3) validation through laboratory and real-vehicle testing; and (4) full integration, including over-the-air updates, security event management, and technical documentation to support certification and regulatory compliance.
At the core of WTTM is the WTTM Questionnaire (WTTM-Q), a structured assessment tool for evaluating cybersecurity maturity across six key domains: Governance, Risk Management, Concept and Design, Security Requirements, Validation and Testing, and Supply Chain. The questionnaire’s results are processed by a dedicated computational engine using supervised machine learning algorithms to estimate risk levels and identify priority intervention areas.
The aim of this article is to describe the WTTM methodological framework, with particular emphasis on the design, validation, and performance of the WTTM-Q. Following a critical review of the current state of the art and existing tools, we detail the questionnaire’s structure, data analysis methodology, and results of its experimental validation. The paper concludes by discussing the framework’s practical benefits, applicability, and future development prospects within the evolving landscape of automotive cybersecurity.
2. State of Art in Automotive Cybersecurity
The increasing interconnection and complexity of modern vehicles have made a structured and systematic approach to cybersecurity in the automotive sector essential. In recent years, the literature has documented the emergence of numerous frameworks and methodologies aimed at countering cyber threats, reflecting a growing focus on safeguarding both sensitive data and the physical safety of passengers and pedestrians—particularly in the context of autonomous vehicles.
Within this evolving landscape, the development of taxonomies for cyberattack classification represents a significant advancement. Kour and Anwar proposed distinct taxonomies for intra-vehicle and vehicle-to-everything (V2X) environments, facilitating the implementation of targeted defense strategies [12,13]. At the same time, regulatory frameworks such as ISO/SAE 21434 and the ENISA guidelines have gained traction, alongside the widespread use of checklists and self-assessment tools for vulnerability detection [14,15]. Recent studies suggest that structured questionnaires and penetration testing activities can significantly improve system resilience [16,17]. Nevertheless, there is ongoing debate about the adequacy of current standards in supporting a dynamic, multi-domain approach that spans the entire vehicle lifecycle. While self-assessment tools contribute to security management, further development is needed to address complex and interdependent threat scenarios.
In response to these challenges, the WTTM framework introduces a modular methodology organized into four phases—from requirements gathering to questionnaire design—providing a systematic, standards-compliant solution tailored to the practical needs of the automotive industry. The WTTM framework builds on the strengths and limitations of existing models, specifically addressing current gaps related to organizational maturity assessment and adaptability across diverse automotive contexts.
2.1. Comparison of Major Cybersecurity Frameworks for Automotive
Cybersecurity assessment in the automotive sector is currently supported by a wide array of frameworks, each offering specific advantages and presenting distinct limitations. Selecting the most appropriate framework requires a careful evaluation of several criteria, including scope of application, ease of implementation, regulatory alignment, scalability, and adaptability to industry needs.
Among the most widely adopted standards is ISO/SAE 21434, which serves as a global benchmark for automotive cybersecurity. This standard provides comprehensive guidelines for risk management throughout the entire vehicle lifecycle, encompassing design, production, and post-production phases. Its strengths lie in its standardized and holistic approach, as well as its alignment with regulatory initiatives such as UNECE WP.29. However, ISO/SAE 21434 also poses significant challenges: its implementation can be resource-intensive, requiring strong organizational alignment and the adoption of new processes and tools. As a result, smaller manufacturers or suppliers with limited resources may struggle to fully comply with its requirements [14].
The EVITA (Enhanced Vehicle Intrusion Test Architecture) framework represents one of the earliest efforts to develop a security model specifically for automotive applications. Based on attack tree analysis, it was designed to support secure hardware and software architectures, particularly in embedded systems. EVITA provides a rigorous methodology for identifying and mitigating vulnerabilities and remains relevant for in-vehicle networks and control units. Nevertheless, its applicability is limited: it is primarily tailored to mid-sized and heavy vehicles and does not comprehensively address modern connectivity paradigms such as vehicle-to-everything (V2X) communication [18,19].
The TARA (Threat Analysis and Risk Assessment) methodology is recognized for its proactive approach to threat modeling. It enables stakeholders to anticipate cybersecurity risks from the early stages of system design through deployment. TARA is especially valuable for organizations that prioritize systematic, forward-looking risk mitigation strategies. However, the methodology can be challenging to implement, particularly for small and medium-sized enterprises. It demands specialized expertise in threat modeling and often requires the development of dedicated tools and risk catalogs, increasing the overall operational burden [14].
ICVTest focuses on black-box penetration testing for intelligent and connected vehicles. It simulates real-world cyberattacks without prior knowledge of the system under test, making it effective for identifying exploitable vulnerabilities. This framework is especially useful for evaluating the robustness of cybersecurity defenses under realistic conditions. Its primary limitation, however, lies in its inability to detect threats that require system-level knowledge. Consequently, ICVTest is most effective when used in conjunction with other assessment methods that incorporate internal architectural insights [14].
Finally, the Holistic Framework for Proactive Risk Identification introduces an integrated perspective by incorporating technical, market, and supply chain dimensions. It supports comprehensive risk management by contextualizing cybersecurity within broader organizational and economic environments. This framework is particularly well-suited to large OEMs and Tier-1 suppliers operating in global markets. Nevertheless, its complexity and extensive data requirements may create implementation barriers for less mature organizations. Moreover, its adoption may require significant investments in specialized tools and personnel capable of interpreting the multi-domain insights it generates [15].
Recent studies have emphasized the growing importance of digital forensics in automotive cybersecurity. Strandberg et al. (2023) provide a systematic review of challenges and technical solutions for in-vehicle forensic data acquisition and preservation [16]. Meanwhile, Cantelli-Forti et al. (2025) offer insights from real-world investigations involving the Event and Voyage Data Recorders (EDR/VDR), outlining practical considerations for data integrity, access control, and evidence admissibility [17]. These works highlight the critical role of forensic readiness in ensuring post-incident analysis, particularly within legal and regulatory frameworks.
2.2. Frameworks Analysis
Taken together, these frameworks reveal a common trend: the growing need to adopt structured, modular, and integrated approaches that address the entire lifecycle of connected vehicles. Although existing frameworks differ in scope and feasibility, their interoperability and ongoing evolution are critical to effectively responding to the dynamic landscape of automotive cyber threats. The literature increasingly underscores the importance of balancing comprehensiveness with practicality, advocating for solutions that are adaptable to diverse organizational contexts and capable of evolving alongside technological advancements.
Within this evolving scenario, the WTTM framework contributes by offering a modular solution tailored to the specific demands of the automotive industry. Built upon a layered attack surface model and aligned with ISO/SAE 21434, WTTM incorporates tools such as the WTTM-Q to assess organizational maturity and cybersecurity risk posture. Its emphasis on automation, scalability, and proactive monitoring positions it as a promising approach—particularly for embedding security considerations into the early stages of system design and strategic decision-making. As such, WTTM enhances the existing landscape by addressing gaps left by other frameworks, with a focus on usability, adaptability, and actionable insights.
3. Materials and Methods
Within this context, the WTTM framework was developed to provide a structured and technologically advanced solution for cyber risk management in connected vehicles. Its foundation lies in a multi-layered attack surface classification model (Figure 1), which is organized into four distinct layers.
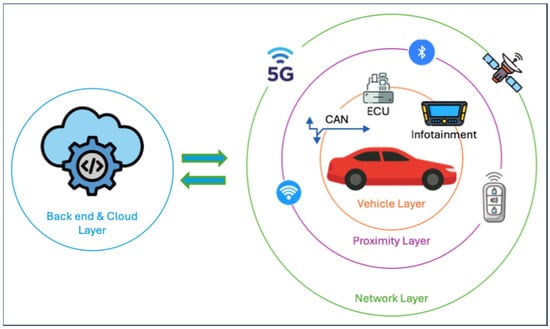
Figure 1.
Automotive attack surface.
The Vehicle Layer encompasses onboard physical components such as Electronic Control Units (ECUs), communication buses (e.g., CAN), telematics systems, infotainment units, sensors, and digital keys. The Proximity Layer includes short-range communication interfaces, such as Bluetooth, Wi-Fi, Vehicle-to-Vehicle (V2V), Vehicle-to-Infrastructure (V2I), and keyless entry systems. The Network Layer addresses external connectivity technologies, including LTE/5G, satellite links, mobile hotspots, and Intelligent Transportation System (ITS) infrastructure. Finally, the Backend and Cloud Layer focuses on interactions with public and private cloud services, OEM infrastructure, blockchain platforms, and third-party backend systems [20].
This layered classification facilitates a nuanced, context-aware analysis of the vehicle’s cyberattack surface, enabling the design of domain-specific defense strategies tailored to the characteristics and vulnerabilities of each layer.
3.1. Core Components of the WTTM Implementation
The implementation of the WTTM framework followed an iterative, modular approach, characterized by the progressive release of integrated software and hardware components. At the core of the system is a Cyber Risk Assessment Platform, designed to automate compliance with international standards—such as ISO/SAE 21434 and UNECE WP.29—and to automatically generate a Maturity Card, which provides a dynamic snapshot of the cybersecurity posture of a vehicle or fleet.
Complementing this is a predictive interactive dashboard (Figure 2), which offers real-time visualization of key security indicators, including a “cyber weather” index, layer-specific vulnerability metrics, and anomaly statuses. The dashboard supports advanced functionalities such as alerting, classification, and event tracking.
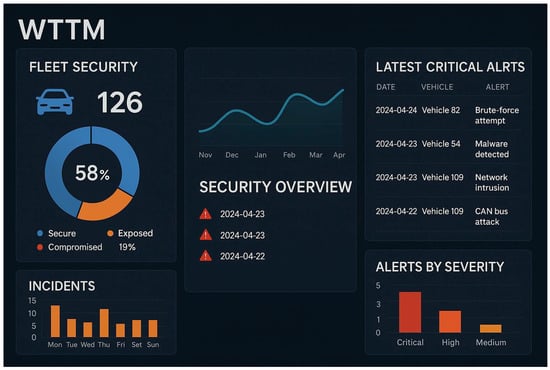
Figure 2.
WTTM dashboard.
Additionally, the platform delivers personalized improvement roadmaps, tailored to each client based on the results of the cybersecurity assessment and the Maturity Card analysis. For log analysis, anomaly detection, and event processing, the platform integrates advanced Security Information and Event Management (SIEM) tools, enhanced by machine learning and artificial intelligence capabilities.
3.2. Operational Backbone: The Vehicle Security Operations Center (V-SOC)
The Vehicle Security Operations Center (VSOC), developed as part of the WTTM framework, constitutes an advanced infrastructure for continuous security monitoring and incident response in connected vehicle environments. From an operational perspective, the VSOC is built on a scalable and modular architecture designed to process large volumes of data originating from vehicles and associated infrastructure.
Through integration with Original Equipment Manufacturer (OEM) cloud services, threat intelligence platforms, and Over-the-Air (OTA) update systems, the VSOC enables proactive cybersecurity management while ensuring compliance with international standards such as ISO/SAE 21434 (road vehicle cybersecurity) and the General Data Protection Regulation (GDPR).
3.2.1. Key Operational Aspects
At the core of the VSOC is an advanced predictive analytics and AI-driven detection system that leverages artificial intelligence and data mining techniques to proactively identify anomalies and emerging threats. By analyzing behavioral models and real-time vehicle telemetry, the platform establishes baseline operational patterns, enabling the high-precision detection of suspicious activities. A key innovation is the integration of digital twin technology, which generates virtual replicas of individual vehicles to support continuous security monitoring and the automated deployment of countermeasures upon threat detection.
The VSOC operates through a streamlined four-phase workflow. The first phase involves comprehensive detection capabilities, collecting telemetry data and security events from a wide range of sources, including Electronic Control Units (ECUs), backend services, and embedded vehicle sensors. In the second phase, this data undergoes rigorous analysis, during which VSOC security analysts leverage Security Information and Event Management (SIEM) systems in conjunction with advanced correlation engines to classify incidents and identify root causes—even in the case of sophisticated, multi-vector attacks.
Once a threat is confirmed, the third phase initiates immediate mitigation actions, including virtual patching and Over-the-Air (OTA) software updates to neutralize risks in real time. The final phase focuses on remediation, ensuring operational continuity by validating the effectiveness of countermeasures and restoring the vehicle to a secure, fully functional state.
The system’s automation framework employs Security Orchestration, Automation, and Response (SOAR) playbooks to standardize and accelerate incident response procedures. Its threat intelligence backbone incorporates real-time data feeds from specialized sources such as the Automotive Information Sharing and Analysis Center (Auto-ISAC). A particularly notable feature is the automated vulnerability management system, which monitors and resolves security gaps across the entire automotive supply chain. This includes automated ticketing and remediation workflows specifically designed to support Tier 2 suppliers and other critical stakeholders.
3.2.2. Strategic Advantages and Compliance
The architecture of the VSOC ensures exceptional scalability through its cloud-native and hybrid design, capable of securing millions of connected vehicles simultaneously while maintaining strict compliance with leading industry standards, including ISO/SAE 21434 for automotive cybersecurity, UNECE Regulation No. 155, and the EU General Data Protection Regulation (GDPR).
Operational efficiency is continuously optimized through advanced analytics that shorten remediation timelines and support data-driven security enhancements. The platform has been initially tested through simulations and expert-reviewed scenarios to assess its resilience under representative attack conditions. The solution adheres to internationally recognized standards and frameworks, including:
- ISO/SAE 21434 (2021) for automotive cybersecurity engineering
- EU General Data Protection Regulation (GDPR 2016/679)
- UNECE R155 vehicle cybersecurity regulations
- Auto-ISAC threat intelligence frameworks
As a holistic cybersecurity solution, the VSOC platform represents the convergence of AI-powered analytics, intelligent automation, and strategic third-party integrations, establishing a future-proof foundation for secure, connected mobility ecosystems. Its ability to anticipate threats, automate responses, and maintain regulatory compliance makes it an indispensable tool for OEMs navigating the evolving landscape of automotive cybersecurity.
The following section introduces the WTTM Questionnaire, which serves as the entry point to the entire WTTM workflow by enabling systematic cybersecurity data collection and evaluation.
3.3. WTTM-Q Definition Process
To ensure compliance with emerging international standards—such as ISO/SAE 21434 and ISO 26262—the WTTM Questionnaire was developed. This instrument evaluates organizational maturity and regulatory alignment within the automotive sector across six critical lifecycle domains: Governance, Risk Management, Concept and Design, Security Requirements, Validation and Test, and Supply Chain.
These constructs were defined through an iterative development process involving domain experts, normative references, and a comparative analysis of established cybersecurity frameworks, including NIST, ENISA, and ISO/IEC 27001.
- The Governance domain assesses the presence and effectiveness of formal policies, defined roles and responsibilities, and cybersecurity training programs, ensuring alignment with applicable regulatory mandates.
- The Risk Management domain evaluates the organization’s capability to perform structured risk assessments using methodologies such as TARA (Threat Analysis and Risk Assessment) and HARA (Hazard Analysis and Risk Assessment), supporting a proactive cybersecurity posture.
- Within the Concept and Design domain, the questionnaire examines the early integration of safety and security considerations, including asset and hazard identification, secure development practices, and third-party component management.
- The Security Requirements domain verifies that design specifications are complete, traceable, and consistent with identified threats and system objectives.
- The Validation and Test domain focuses on the robustness of verification and validation activities, such as penetration testing, fault injection, post-production monitoring, and maintenance planning.
- Finally, the Supply Chain domain assesses security measures throughout the supplier ecosystem, including audit mechanisms, contractual obligations, and communication protocols with external vendors.
The full version of the questionnaire is provided in Appendix A.
3.4. Statistical Validation of the Questionnaire
The initial statistical validation of the WTTM-Q was conducted on a sample of 43 respondents selected through purposive sampling. Participants were industry professionals working in the automotive and embedded systems sectors, with direct experience in cybersecurity, functional safety, and compliance processes. Recruitment was carried out via professional networks, industry events, and direct outreach to partner organizations involved in safety-critical development projects. Respondents completed the questionnaire anonymously using an online survey platform, and consent to participate in the study was obtained.
To assess the internal consistency of the instrument, Cronbach’s alpha was calculated for each of the six domains, all of which exceeded the standard threshold of 0.70:
- Governance (α = 0.868)
- Risk Management (α = 0.887)
- Concept and Design (α = 0.848)
- Security Requirements (α = 0.829)
- Validation and Test (α = 0.877)
- Supply Chain (α = 0.819)
To evaluate the factor structure, a data-splitting strategy was employed to mitigate the risk of overfitting. The dataset was randomly divided into two independent subsamples: one used for Exploratory Factor Analysis (EFA, n = 22) and the other for Confirmatory Factor Analysis (CFA, n = 21). The EFA yielded good psychometric results, including a Kaiser–Meyer–Olkin (KMO) measure of 0.845 and a significant Bartlett’s test of sphericity (χ2(435) = 886.3, p < 0.001). Six factors were extracted, explaining 73.72% of the total variance, consistent with the conceptual domain structure defined in the questionnaire.
The CFA conducted on the second subsample demonstrated a good model fit:
- Comparative Fit Index (CFI) = 0.912
- Tucker–Lewis Index (TLI) = 0.892
- Root Mean Square Error of Approximation (RMSEA) = 0.064
These findings provide empirical support for the construct validity and reliability of the WTTM-Q, despite the small sample size. The application of a cross-validation approach through data-splitting enhances the credibility of the results and mitigates the limitations associated with using a single dataset for both EFA and CFA. To further assess the generalizability of the instrument, a synthetic dataset was also generated to simulate organizations with varying maturity levels. This dataset was subsequently used to train and test machine learning models for cybersecurity risk classification based on WTTM-Q input profiles.
4. Results
This section presents the outcomes of the automated cyber-risk classification task derived from responses to the WTTM-Q questionnaire. The goal was to assess the feasibility of replacing static scoring procedures with a data-driven model informed by expert judgment. The results are structured as follows: (i) dataset generation and expert labeling; (ii) model training and evaluation procedure; (iii) comparative analysis of classification algorithms; and (iv) performance of the final model.
4.1. Statistical Validation of the Questionnaire
To simulate diverse organizational maturity profiles and address the lack of publicly available automotive data, a synthetic dataset comprising 115 response configurations was created. Each configuration was constructed to represent realistic combinations of answers across the WTTM-Q dimensions. A panel of domain experts—comprising professionals in cybersecurity, systems engineering, and automotive safety—independently reviewed and labeled each profile based on their perceived risk level.
Labels were assigned as:
- 0 (Secure): configurations judged as adequate and compliant with industry standards;
- 1 (Vulnerable): configurations considered insufficient or indicative of elevated cybersecurity risk.
This labeled dataset was used as the foundation for supervised learning. Although the dataset was designed to represent diverse and realistic organizational profiles, we acknowledge that its synthetic nature may limit the external validity of the results. To mitigate potential labeling bias, all profiles were independently assessed by a multidisciplinary panel of experts, and consensus labels were used where possible. Future work will aim to validate the model on real organizational data, or alternatively, to expand the scenario set using advanced simulation techniques and domain-specific case studies.
4.2. Model Training and Evaluation Protocol
The dataset was randomly divided into a training set (80%) and a test set (20%), preserving label distribution through stratified sampling. To ensure model robustness and prevent overfitting, a 5-fold stratified cross-validation was performed on the training set. Final evaluation metrics were calculated on the unseen test set. Three supervised learning algorithms were considered for comparison:
- Logistic Regression (LR), for its simplicity and interpretability;
- Random Forest (RF), known for its robustness and ability to handle nonlinear relationships;
- Extreme Gradient Boosting (XGBoost), a state-of-the-art ensemble method combining efficiency and high predictive accuracy.
Each model was trained and evaluated using the same data splits and performance metrics. Table 1 summarizes the results obtained on the test set. As shown, XGBoost outperformed the other models across all evaluation metrics, offering the best balance between precision, recall, and overall discriminative capability. It was therefore selected as the final model for the automated classification task.

Table 1.
Performance comparison of classification algorithms.
These metrics confirm the model’s effectiveness, particularly in identifying high-risk (vulnerable) configurations. The recall of 0.82 is especially valuable in the context of cybersecurity, where failing to identify a vulnerability (false negatives) can have severe consequences. The precision of 0.75 suggests some conservative misclassification of secure organizations as vulnerable—an acceptable trade-off in preventive risk assessment.
Figure 3 provides a comprehensive overview of the performance of the final classification model (XGBoost). The confusion matrix on the left illustrates the model’s ability to correctly classify most configurations, with a high number of true positives (vulnerable profiles correctly identified) and true negatives (secure profiles correctly classified), and relatively few misclassifications. This balance reflects the model’s reliability in both detecting cybersecurity risks and avoiding unnecessary false alarms.
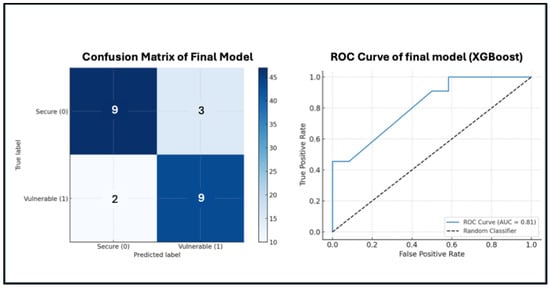
Figure 3.
Model performance metrics.
On the right, the ROC curve demonstrates the model’s discriminative capability, with an AUC of 0.84, indicating good performance in distinguishing between secure and vulnerable classes. The curve stays well above the diagonal baseline, confirming the classifier’s robustness and suitability for automated cyber-risk assessment in the automotive domain.
5. Discussion
The WTTM framework represents a significant advancement in addressing the escalating cybersecurity challenges faced by the automotive sector, particularly in the era of increasingly connected and autonomous vehicles. Its modular and scalable architecture, developed in alignment with international standards such as ISO/SAE 21434 and UNECE WP.29, supports a proactive risk management approach throughout the vehicle lifecycle, thereby promoting a “security by design” culture.
A central innovation of the WTTM framework is the integration of the WTTM-Q, an assessment tool developed through an iterative, expert-driven process and inspired by established frameworks including NIST and ISO/IEC 27001. The questionnaire is structured around six critical domains—Governance, Risk Management, Concept and Design, Security Requirements, Validation and Testing, and Supply Chain—and is designed to assess organizational maturity in terms of cybersecurity and functional safety.
The results of the statistical validation are promising. All constructs exhibited strong internal consistency, with Cronbach’s alpha values exceeding 0.70, and demonstrated high construct validity, as indicated by Confirmatory Factor Analysis (CFA) results (CFI = 0.94, RMSEA = 0.061). These metrics affirm the robustness and reliability of the questionnaire as a measurement instrument.
To transform qualitative assessments into a data-driven risk classification process, the framework incorporates a supervised machine learning classifier. A multidisciplinary panel of experts evaluated 115 hypotheticals but realistic response configurations, labeling them as either “Secure” or “Vulnerable.” Among the tested algorithms, Extreme Gradient Boosting (XGBoost) yielded the best performance, achieving an accuracy of 0.78, ROC AUC of 0.84, and recall of 0.82. These results underscore the model’s effectiveness in identifying high-risk organizational profiles. Although the precision (0.75) was slightly lower than the recall, this trade-off is deemed acceptable in cybersecurity contexts, where minimizing false negatives is a critical priority.
While the expert-generated dataset enables controlled evaluation and reflects plausible organizational conditions, it remains synthetic. Therefore, we acknowledge the limitations of this setup. To strengthen the external validity of the classifier, future work will:
- Validate the model on real-world organizational data, when accessible;
- Extend the dataset through advanced simulation techniques to increase scenario diversity;
- Apply cross-validation across broader population subsets to further ensure stability.
Despite these limitations, the current results provide a promising foundation for an automated, expert-informed, and adaptable cyber-risk assessment framework in the automotive sector.
Recent advances in adversarial machine learning—particularly in the domain of clean-label backdoor attacks—offer valuable insights that complement the WTTM framework. For instance, Zhao et al. in [21] introduced CBat, a clean-label attack on language models based on stylized input triggers, and CBatD, a defense mechanism that removes poisoned data by analyzing loss distributions and feature relevance. These works reveal how input manipulation and training dynamics can be leveraged to shape model outcomes, emphasizing the importance of both proactive and reactive approaches to system security.
In this light, WTTM distinguishes itself by operating on a different conceptual plane: rather than reacting to already compromised inputs, it leverages structured organizational self-assessment (via WTTM-Q) and predictive modeling to estimate latent vulnerabilities before they manifest operationally. This anticipatory, human-adaptive strategy complements traditional adversarial defenses and provides a broader, systemic view of cyber risk—particularly suited to complex socio-technical ecosystems such as automotive manufacturing and supply chains.
To further clarify the novelty and positioning of WTTM within the broader cybersecurity landscape, Table 2 provides a comparative summary of key characteristics across prominent risk assessment frameworks. While ISO/SAE 21434 offers strong regulatory grounding and HEAVENS brings TARA-based risk evaluation to the fore, these approaches typically rely on static methods, are limited in automation, and do not scale easily to organization-level self-assessments. EVITA and similar academic models remain mostly theoretical or tightly coupled to specific architectures. In contrast, WTTM integrates expert-informed organizational diagnostics with automated, data-driven classification, enabling scalable, adaptive, and domain-specific risk evaluation.

Table 2.
Comparative overview of automotive cybersecurity frameworks.
Another limitation of the current work concerns the comparative analysis between frameworks, which is mostly focused on qualitative aspects. To better highlight WTTM’s added value compared to established standards such as HEAVENS and TARA, future developments will enrich the comparative table with quantitative metrics derived from pilot projects, including average implementation time, estimated costs, and degree of automation achieved. These data will provide a stronger empirical foundation and clearly demonstrate the practical advantages of the framework.
Table 2 presents a comparative summary of widely adopted automotive cybersecurity frameworks alongside WTTM. While existing frameworks provide structured approaches to risk management, they are often manual, component-focused, or lack predictive modeling capabilities. In contrast, WTTM uniquely combines expert-driven assessments, machine learning, and supply chain awareness, offering a comprehensive and scalable solution for organizational cyber-risk evaluation.
Forensic Readiness and Regulatory Alignment
In line with its ambition to provide end-to-end lifecycle coverage, future iterations of the WTTM framework will integrate forensic readiness capabilities. These include mechanisms for secure, time-synchronized logging, cryptographic signing and hashing of log files, segregation of operational vs. evidentiary data, and role-based retrieval of forensic records. WTTM-Q will be extended to evaluate organizational preparedness in managing chain of custody, log retention policies, and controlled evidence access—in accordance with standards such as ISO/IEC 27037 (Guidelines for Evidence Handling) and ISO/IEC 27043 (Incident Investigation Principles). These enhancements aim to ensure legal defensibility, regulatory compliance, and effective post-incident attribution, particularly in coordination with Event Data Recorders (EDR) and DSSAD systems, which are increasingly required in jurisdictions such as the EU for vehicle categories M1 and N1.
The framework is further enhanced by the incorporation of a VSOC, which enables real-time system monitoring, AI-driven anomaly detection, and automated incident response through Security Orchestration, Automation, and Response (SOAR) playbooks. The integration of digital twin technology and an extended vulnerability management system spanning the entire supply chain further reinforces WTTM’s operational relevance and practical applicability.
Nevertheless, certain limitations must be acknowledged. The sample size used for questionnaire validation (n = 43) is relatively modest, and the predictive model’s effectiveness is contingent upon the quality and consistency of expert labeling. Furthermore, the dynamic and evolving nature of cyber threats necessitates periodic methodological and technical updates to ensure continued efficacy. A final challenge lies in the lack of global regulatory harmonization, which may hinder the consistent and widespread adoption of the WTTM framework across international contexts.
6. Conclusion and Future Works
The WTTM framework offers a comprehensive and standards-aligned solution for cyber-risk management in the automotive sector. By integrating structured self-assessment via the WTTM questionnaire, automated risk classification through the XGBoost algorithm, and real-time monitoring enabled by the VSOC, the framework facilitates a scalable, proactive, and adaptive approach to cybersecurity.
Its modular architecture supports phased implementation tailored to the specific technological, organizational, and regulatory requirements of diverse stakeholders, including original equipment manufacturers (OEMs), suppliers, and system integrators. In an environment marked by rapid technological advancement and increasingly sophisticated cyber threats, frameworks like WTTM are essential for preserving data integrity, functional safety, and user trust.
Several research directions are proposed to further enhance the framework’s efficacy. Expanding the dataset with a larger volume of real-world responses to the WTTM-Q would increase the generalizability and robustness of the classifier, enabling more precise risk assessments across a broader range of industrial scenarios. Moreover, incorporating real-time threat intelligence—such as dynamic feeds from platforms like Auto-ISAC—could substantially augment the VSOC’s predictive capabilities and responsiveness.
The deployment of AI-driven solutions for autonomous over-the-air (OTA) software updates represents a promising direction for automating vulnerability remediation. Additionally, comparative benchmarking against other established frameworks—such as EVITA, TARA, and ICVTest—in real-world, operational environments would provide empirical validation of WTTM’s relative effectiveness and maturity.
Another area of opportunity lies in the development of AI-assisted tools for automated regulatory compliance tracking, addressing standards such as ISO/SAE 21434, UNECE R155, and GDPR. These tools could streamline certification workflows and reduce the compliance burden on organizations operating in complex regulatory environments.
Furthermore, the current version of WTTM does not yet implement modules for digital forensic readiness or support EDR/DSSAD interfaces. While these elements are essential for compliance with evolving regulations and for supporting post-incident investigations, their integration remains a target for future development. A key limitation concerns the delayed integration of forensic readiness: at present, the dedicated modules (e.g., EDR/DSSAD interfaces and secure, verifiable log collection mechanisms) have not been implemented or tested within the current framework. To overcome this issue, future developments of WTTM will include their earlier integration and experimental validation in real-world scenarios, ensuring full end-to-end lifecycle coverage and further strengthening regulatory compliance and post-incident investigation reliability. This limitation also affects the scope of the current assessment model (WTTM-Q), which will need to be extended to evaluate organizational capability in evidence capture, retention, and legal defensibility.
In conclusion, WTTM constitutes a novel and strategic contribution to the field of automotive cybersecurity. By bridging the gap between traditional risk assessment frameworks and intelligent, automated defense mechanisms, it offers a forward-looking, resilient approach aligned with both current industry needs and future technological trends. Ongoing work should prioritize enhancing the framework’s scalability, real-time adaptability, and integration with emerging technologies across the automotive ecosystem.
Future developments will focus on extending WTTM to support digital forensics and evidence handling in compliance with standards like ISO/IEC 27037 and 27043. This will include defining interfaces with EDR/DSSAD systems, implementing mechanisms for secure and auditable log collection, and enriching the WTTM-Q questionnaire with items that assess forensic readiness at both organizational and technical levels. Experimental validation of these additions on real-world incident data will be pursued in collaboration with industry partners.
Author Contributions
Conceptualization and methodology, E.P. and M.F. All authors have read and agreed to the published version of the manuscript.
Funding
This article is the result of dissemination activities related to the Welcome To The Machine project, funded under the Programma Regionale Abruzzo FESR 2021–2027—AVVISO 1.1.1.1: Sostegno a progetti di Ricerca e Innovazione delle imprese afferenti ai Domini tecnologici della Strategia Regionale di Specializzazione Intelligente RIS3 Abruzzo 21–27, CUP: C19J24000120007, with a non-repayable grant of EUR 560,000.00.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Conflicts of Interest
Author Enrico Picano and Massimo Fontana were employed by the company Vantea SMART SPA. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Correction Statement
This article has been republished with a minor correction to the Data Availability Statement. This change does not affect the scientific content of the article.
Appendix A. WTTM-Q
The WTTM-Q was developed as part of the WTTM framework to assess the cybersecurity and functional safety maturity of organizations operating within the automotive sector. The questionnaire is structured around six key domains derived from ISO/SAE 21434, ISO 26262, and relevant best practices: Governance, Risk Management, Concept and Design, Security Requirements, Validation and Testing, and Supply Chain. Each domain includes targeted items designed to investigate specific aspects of the organizational preparedness, awareness, process formalization, and policy enforcement. Responses are collected using a 5-point Likert scale that reflects the level of the implementation, documentation, and integration of the evaluated practices (see Table A1). The questionnaire supports structured self-assessment and serves as input for the supervised classification model used to estimate cybersecurity risk levels.
WTTM-Q Structure
- GovernancePolicies and Procedures
- Has a formal cybersecurity policy been established?
- Are there documented procedures for managing cybersecurity?
- Is there a formal functional safety policy?
- Are roles and responsibilities defined for security management?
- Is there a mandatory cybersecurity training plan?
- Is there a mandatory functional safety training plan?
- Are responsibilities defined at organizational, project, and product levels?
- Have these responsibilities been communicated to staff?
- Is there a plan for managing security anomalies?
Security Awareness- 10.
- Does staff receive specific cybersecurity training?
- 11.
- Is training provided for functional safety?
- 12.
- Are competency assessments conducted?
- 13.
- Is the effectiveness of the training measured?
- Risk Management
- Has a cybersecurity risk assessment been conducted?
- Is there a documented cyber risk register?
- Is functional risk re-evaluated in case of design changes?
- Has a HARA (Hazard Analysis and Risk Assessment) been performed?
- Is the TARA (Threat Analysis and Risk Assessment) updated periodically?
- Is there a register of hazards with corresponding ASIL levels?
- Concept and Design
- Have assets to be protected been identified and classified?
- Have hazards been identified and classified?
- Have cybersecurity objectives been defined?
- Have safety goals with ASIL levels been defined?
- Does the concept integrate safety and cybersecurity?
- Have combined fault/threat scenarios been analyzed?
- Is secure software development enforced?
- Is the security of third-party components managed?
- Is there a secure integration process for components?
- Security Requirements
- Are cyber requirements traceable to objectives?
- Are functional safety requirements traceable to safety goals?
- Does the design include measures against spoofing and DoS attacks?
- Does the design include fault tolerance features?
- Are supplied components evaluated for cyber compliance?
- Are supplied components evaluated for ASIL compliance?
- Validation and Testing
- Are penetration tests planned on critical components?
- Are fault injection tests planned?
- Is there a cybersecurity validation plan?
- Is there a functional safety validation plan?
- Are integrated tests (safety + cybersecurity) carried out?
- Are tamper-resistant controls implemented during production?
- Is functional safety verified during production?
- Are patch management plans in place?
- Are recall plans defined for security reasons?
- Is a phase-out plan (for safety and cyber) in place?
- Are there guidelines for TARA and HARA?
- Does the configuration address both safety and cybersecurity?
- Is a security-focused change management process active?
- Supply Chain
- Are suppliers evaluated for cybersecurity management?
- Are suppliers evaluated for functional safety management?
- Do specifications include cyber and safety requirements?
- Are annual supply chain audits conducted?
- Are audit results communicated to suppliers?

Table A1.
Likert scale for response evaluation.
Table A1.
Likert scale for response evaluation.
| Score | Description | Operational Meaning |
|---|---|---|
| 1 | No evidence | The practice is absent and not planned |
| 2 | Initial phase | Informal or pilot activity |
| 3 | Partially implemented | Ongoing activity with partial documentation |
| 4 | Fully implemented | Documented, traceable, and monitored practice |
| 5 | Best practice/optimized | Mature practice with continuous measurement and improvement |
Usage Notes—Each questionnaire item is intended to be answered by individuals with an adequate understanding of cybersecurity and safety processes within the organization. The results may be aggregated per domain or analyzed item by item to identify critical gaps, track organizational progress, or support automated classification processes within the WTTM framework.
References
- Chlup, S.; Christl, K.; Schmittner, C.; Shaaban, A.M.; Schauer, S.; Latzenhofer, M. THREATGET: Towards Automated Attack Tree Analysis for Automotive Cybersecurity. Information 2023, 14, 14. [Google Scholar] [CrossRef]
- Rahimi, N.; Mirhassani, M.; Schuelke-Leech, B.A. Enhancing Risk Assessment Models for Heavy Duty and Medium Duty Vehicles through Customization of the EVITA Framework. Preprint on Research Square, 31 December 2023. [Google Scholar] [CrossRef]
- Knight, A. Risk-Assessment Frameworks. In Hacking Connected Cars; Knight, A., Ed.; Wiley: Hoboken, NJ, USA, 2020. [Google Scholar] [CrossRef]
- Lautenbach, A.; Almgren, M.; Olovsson, T. Proposing HEAVENS 2.0—An Automotive Risk Assessment Model. In Proceedings of the 5th ACM Computer Science in Cars Symposium (CSCS’21), Ingolstadt, Germany, 30 November 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 1–12. [Google Scholar] [CrossRef]
- Good Practices for Security of Smart Cars. Available online: https://www.enisa.europa.eu/publications/smart-cars (accessed on 11 September 2025).
- Wolf, M.; Scheibel, M. A Systematic Approach to a Quantified Security Risk Analysis for Vehicular IT Systems. In Automotive-Safety & Security; Gesellschaft für Informatik e.V.: Bonn, Germany, 2012; pp. 195–210. [Google Scholar]
- Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef] [PubMed]
- Eskandarian, A.; Wu, C.; Sun, C. Research Advances and Challenges of Autonomous and Connected Ground Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 683–711. [Google Scholar] [CrossRef]
- Yang, D.; Sarma, N.J.S.; Hyland, M.F.; Jayakrishnan, R. Dynamic Modeling and Real-Time Management of a System of EV Fast-Charging Stations. Transp. Res. Part C Emerg. Technol. 2021, 128, 103186. [Google Scholar] [CrossRef]
- Kaur, K.; Kaddoum, G.; Zeadally, S. Blockchain-Based Cyber-Physical Security for Electrical Vehicle Aided Smart Grid Ecosystem. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5178–5189. [Google Scholar] [CrossRef]
- Lesi, V.; Jovanov, I.; Pajic, M. Network Scheduling for Secure Cyber-Physical Systems. In Proceedings of the 2017 IEEE Real-Time Systems Symposium (RTSS), Paris, France, 5–8 December 2017; pp. 45–55. [Google Scholar] [CrossRef]
- Tanaji, B.A.; Roychowdhury, S. A Survey of Cybersecurity Challenges and Mitigation Techniques for Connected and Autonomous Vehicles. IEEE Trans. Intell. Veh. 2024, 1–18. [Google Scholar] [CrossRef]
- Siddiqui, F.; Khan, R.; Tasdemir, S.Y.; Hui, H.; Sonigara, B.; Sezer, S.; McLaughlin, K. Cybersecurity Engineering: Bridging the Security Gaps in Advanced Automotive Systems and ISO/SAE 21434. In Proceedings of the 2023 IEEE 97th Vehicular Technology Conference (VTC2023-Spring), Florence, Italy, 20–23 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Karopoulos, G.; Kambourakis, G.; Chatzoglou, E.; Hernández-Ramos, J.L.; Kouliaridis, V. Demystifying In-Vehicle Intrusion Detection Systems: A Survey of Surveys and a Meta-Taxonomy. Electronics 2022, 11, 1072. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Strandberg, K.; Nowdehi, N.; Olovsson, T. A Systematic Literature Review on Automotive Digital Forensics: Challenges, Technical Solutions and Data Collection. IEEE Trans. Intell. Veh. 2023, 8, 1350–1367. [Google Scholar] [CrossRef]
- Cantelli-Forti, A.; Longo, G.; Oveis, A.H.; Russo, E. Insights from Field Experience: Digital Forensics of Event and Voyage Data Recorders in Transportation Systems Accident Investigation. Int. J. Inf. Secur. 2025, 24, 163. [Google Scholar] [CrossRef]
- Haddaji, A.; Ayed, S.; Chaari Fourati, L.; Merghem Boulahia, L. Investigation of Security Threat Datasets for Intra- and Inter-Vehicular Environments. Sensors 2024, 24, 3431. [Google Scholar] [CrossRef] [PubMed]
- Gularte, K.H.M.; da Costa, J.P.J.; Vargas, J.A.R.; da Silva, A.S.; Santos, G.A.; Wang, Y. Integrating Cybersecurity in V2X: A Review of Simulation Environments. IEEE Access 2024, 12, 177946–177985. [Google Scholar] [CrossRef]
- Pascale, F.; Adinolfi, E.A.; Coppola, S.; Santonicola, E. Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles. Electronics 2021, 10, 1765. [Google Scholar] [CrossRef]
- Zhao, S.; Tuan, L.A.; Fu, J.; Wen, J.; Luo, W. Exploring Clean Label Backdoor Attacks and Defense in Language Models. IEEE/ACM Trans. Audio Speech Lang. Process. 2024, 32, 3014–3024. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).