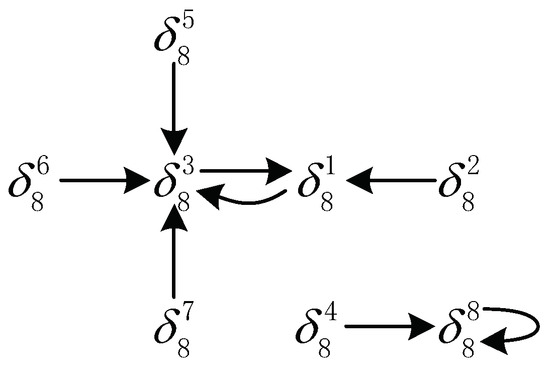
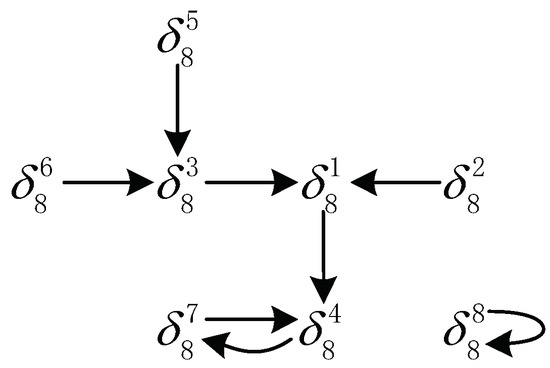
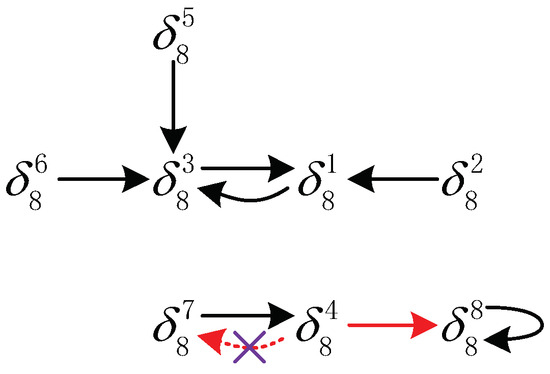
Abstract
This paper develops a parameter tuning method for solving the set restabilization problem of perturbed Boolean control networks (BCNs). First, the absorbable attractor, which we previously proposed, is recalled. Based on the relationship between attractors, a necessary and sufficient restabilizability criterion is derived. This criterion is used to check whether a perturbed BCN can be stabilized to the original target set by modifying the least number of parameters to the old controller. Furthermore, a constructive method for fine-tuning the old controller is provided if the criterion condition derived above is satisfied. Compared with the existing relevant results, ours have clear advantages, since they can address the set restabilization problem of BCNs subject to multi-column function perturbations, which has not been solved yet. Finally, two examples are employed to show the effectiveness and advantages of our results.
1. Introduction
The Boolean network (BN), proposed by Kauffman in 1969, is a simple logical dynamic system. It is commonly used to study genetic regulatory networks [1], cryptography [2], games [3], and so on. A BN consists of a set of nodes, each with two states. These nodes are connected with each other through logical rules. In addition, a BN with external inputs is called a Boolean control network (BCN). It should also be investigated as in control theory, because the goal of systems biology is to design therapy strategies in the treatment of some diseases, for example, cancer. To achieve the goal, gene intervention was proposed, whose main idea is to perturb some genes and then facilitates the gene regulatory network to evolve to a set of desired states from an unhealthy state. BNs and BCNs may seem simple, but they possess complex dynamic characteristics. Many problems related to practical biology can be effectively studied in such a Boolean form [4], which prompts researchers to explore BNs and BCNs.
In the past two decades, there has been a lot of research on BNs and BCNs. The stability and stabilization of BCNs has always been a research hotspot. For example, Cheng et al. gave basic definitions for the stability of BNs and the stabilization of BCNs in [5], and provided stability criteria and stabilization design methods. Li et al. pioneered a design method for state feedback controller of BCNs in [6]. Tian et al. proposed a design method with relatively low complexity for open control in [7]. The output feedback stabilization of BCNs was studied in [8], and a specific controller design method was provided. The simultaneous stabilization for a set of BCNs was investigated in [9]. Lin et al. discussed the stabilization of constrained BCNs [10]. These results are all about how to design a controller to stabilize a BCN to a fixed point. Later, some scholars directed their attention to set stability and set stabilization of BCNs [11,12,13,14,15,16], since in some cases, the interest lies in whether a BCN can be stabilized to a given target set, rather than a single point. A typical application of set stabilization is the synchronization design of a collection of interconnected systems; see Examples 1, 2, and 3 in [11].
On the other hand, the actual system is inevitably disturbed by its surrounding environment. This may lead to changes in the structural parameters of the system. In particular, the impact of immeasurable variables or gene mutation on the gene regulatory network cannot be ignored. So the robustness of BCNs is particularly important, and many excellent research results have been reported, for example, refs. [17,18,19,20,21,22,23,24,25,26,27,28,29]. Most of these results are about the influence of perturbations on BNs [17,18,19,20,21,22,23,24,25] and robust stabilization of perturbed BCNs [20,26,27,28,29]. It is worth pointing out that the designed controllers are robust, but the robustness is limited. In other words, when some sensitive parameters in a BCN change slightly, the perturbed BCN may become unstable if it is still under the old controller. The simplest solution to this problem is to redesign the controller. However, a completely new controller can easily cause serious oscillation at the beginning of the system response. Therefore, it is significant to investigate how to deal with the restabilization problem of perturbed systems. Unfortunately, there are few papers in this respect. Recently, Li et al. have proposed an effective algorithm in [30] to modify the old state feedback controller, such that the unstable closed-loop system, due to disturbances, can be stabilized back to the original state. The pity is that the algorithm, as the authors said, can only deal with the single column function perturbation problem, but cannot solve the perturbation problem of multiple columns. Hou et al. developed a fine-tuning method in [31] to solve the multi-column function perturbation problem. Regrettably, it cannot be directly applied to the set restabilization problem. The above information is summarized in Table 1.

Table 1.
Summary of research on the stability and stabilization of perturbed BCNs.
Under the background, this paper tries to investigate the set restabilization of BCNs subjected to multi-column function perturbations. The main contributions are summarized as follows:
- An algorithm for calculating absorbable attractors is provided, where absorbable attractors play a key role in our method.
- For the perturbed BCNs, a method is developed to solve the set restabilization problem of BCNs subject to multi-column function perturbations, which has not been settled yet. This method has a wider scope of application, since most results in the existing literature are mainly about restabilization to a singleton, which is a special case of set restabilization.
The remaining part of our paper is arranged as follows. Some preliminary knowledge is introduced in Section 2. The main results are provided in Section 3. These results include some concepts, a set restabilizability criterion, and three algorithms. Section 4 gives two illustrative examples, and Section 5 offers a conclusion.
2. Materials and Methods
For the sake of convenience, some symbol explanations are given first.
- .
- represents the set , where denotes the ith column of the identity matrix.
- stands for the matrix , called a logical matrix.
- and express the ith column and ith row of a matrix L, respectively.
- () is the set of logical (real) matrices.
- is the set of matrices with all entries in .
The semi-tensor product (STP) is the main mathematical tool. We recall its definition and a basic property [32].
- For two matrices and , the STP of A and B iswhere r is the least common multiple of n and p; ⊗ is the Kronecker product of matrices.
- The logical matrixcalled a power-reducing matrix, satisfies .
Remark 1.
The STP is a natural extension of ordinary matrix multiplication, since it has the same basic properties as the ordinary matrix multiplication. In particular, STP is the ordinary matrix multiplication when . The operational symbol ⋉ is usually omitted for simplicity in this paper.
As we know, all entries of a Boolean matrix are in . Now, Boolean addition ⊕ and Boolean product ⊙ of two Boolean matrices and are recalled.
- When and , .
- When , , where .
Consider a BCN
and a state feedback controller
where , are state variables; , are control inputs; and are logical functions.
We replace 1 and 0 with and , respectively. The symbols and are also used to represent the vector forms of corresponding logical variables, if no confusion arises. Define and . According to STP techniques [32], it is easy to obtain the algebraic form of (1)–(2):
where and are called the structure matrix of (3) and state feedback matrix of (4), respectively. Due to the equivalence between (1)–(2) and (3)–(4), we only study (3)–(4) to highlight our method hereafter.
Definition 1.
Definition 2
([11]). A set is an invariant subset of the closed-loop system (5), if for any initial state , we have . And the union of all of the invariant subsets contained in is called the largest invariant subset contained in , denoted by .
Definition 3
([11]). A set is a control invariant subset of BCN (3), if for any initial state , there is a control sequence , such that . And the union of all of the control invariant subsets contained in is called the largest control invariant subset contained in , denoted by .
Remark 2.
As we know, the union of (control) invariant subsets is still a (control) invariant subset. So () is also a (control) invariant subset. From Lemma 4 of [11], BCN (3) is -stabilizable if and only if it is -stabilizable. Refer to [11] for more about the largest invariant subset and the largest control invariant subset.
When BCN (1) is seriously perturbed, there may be a logical function with a bit error or multiple bit errors in its truth table. Correspondingly, we call this phenomenon a one-bit function perturbation and a multibit function perturbation, respectively. These bit perturbations lead to changes in the columns of the structure matrix L. Such column changes are called column perturbations. Specifically, if only one column changes, we call it a single column function perturbation; otherwise, it is said to be a multi-column function perturbation.
Example 1.

Consider the following BCN:
whose truth table is shown in Table 2. Assume that BCN (6) is perturbed, which causes to change from 0 to 1 (this is a one-bit function perturbation). Correspondingly, changes from to (it is a single column function perturbation). If the value 0 of also changes and turns into 1 (accordingly, changes from to ), then BCN (6) suffers from a multi-bit perturbation.

Table 2.
Truth table of logical functions and in (6).
The target set is always denoted by in this paper. It is assumed that BCN (3) is stabilized to by an appropriate controller (4). That is, the closed-loop system (5) is -stable. If BCN (1) is seriously disturbed and its structure matrix L changes into another matrix , then BCN (3) becomes
and the closed-loop system (5) turns into
At this time, the perturbed closed-loop system (8) may no longer be -stable. In practical engineering, in order to avoid large oscillations in the system response, engineers usually tune parameters of the old controller as little as possible, rather than redesign a new controller to stabilize the perturbed system back to the original target set. The adjustment process is called parameter fine-tuning.
Our main purpose is to develop a method which can be used to check whether the perturbed and unstable closed-loop system (8) can be stabilized back to the original target set , through a fine-tuning technique. In addition, a specific parameter fine-tuning technique should be proposed.
3. Results
When the perturbed closed-loop system (8) is not stable within , we analyze its -restabilization from the following two problems.
- . How do we tune the old controller when ?
- . How do we tune the old controller when there are attractors not contained in the target set ?
Remark 3.
As we know, . So if , then . The purpose of handling Problem 1 is just to increase the likelihood of solving Problem 2, since Problem 2 is the main issue we need to solve in -restabilization of the perturbed system (8).
3.1. Modification for the Largest Invariant Subset
For the perturbed BCN (7), as we mentioned earlier, -stabilizability is equivalent to -stabilizability. Therefore, if BCN (7) is -stabilizable, the largest control invariant subset must be nonempty.
Assumption 1.
For BCN (7), the largest control invariant subset is nonempty.
Under Assumption 1, we use Proposition 2 given in [11] to calculate of BCN (7). Now we further provide an algorithm to implement as the largest invariant subset of the closed-loop system by modifying columns of G.
Remark 4.
For any state in , there may be several different control signals u, such that the next state of BCN (7) is still in , namely . In this case, we adopt the principle of modifying the parameters as little as possible, which can be seen from Step 1 of Algorithm 1. Specifically, if the control signal , given by the old controller (7), is one of the above feasible control signals, we keep the ith column of G unchanged. In this way, while implementing as the largest invariant subset of the new closed-loop system, we minimize the number of parameter modifications of G.
| Algorithm 1 The feedback matrix G can be modified by the following steps to make equal to the largest invariant subset of the new closed-loop system. |
|
3.2. Modification for Unstable Attractors
Let the feedback matrix G be modified into by Algorithm 1. Then, the old controller (4) changes into
and the closed-loop system (8) becomes
whose largest invariant subset is equal to .
The closed-loop system (10) is still not stable within , since the system (10) has attractors not included in . Let all such attractors be given as follows:
where
For any , we define its attraction domain as
Before giving our main theorem, an important concept is recalled.
Definition 4
([31]). 1. Assume that and are attractors of the closed-loop system (10). If there is a state and an integer satisfying , such that , then is said to be an absorbable attractor of by one step, and we denote it as .
2. Let and be two attractors of (10), where . If there is a different attractor satisfying , such that , then is said to be an absorbable attractor of by s steps, and we denote it as . When the number of steps s does not need to be emphasized, is usually written as , and is simply called an absorbable attractor of . For consistency of notation, we define .
Remark 5.
According to item 1 of Definition 4, we know that for any attractor , if , then can be broken and , including , becomes a new part of by replacing with . Similarly, for any , the attractor can be cut off and becomes a part of by modifying s columns of .
In the following, we give a method for checking whether an attractor is absorbable into another attractor . For convenience, let
We first split into pieces
where , .
Compute
Next, for any set , we define a -dimensional Boolean vector V. Specifically, if , then the kth element of V is 1; else, it is 0.
Proposition 1.
Let and be two vector representations corresponding to attractor and attraction domain , respectively, where is also an attractor of system (10). if and only if .
Proof.
, if and only if there must exist an element at the same position in and , both equal to 1. We let . Then, equivalently, there is a block in , say , such that . In other words, there is a positive integer k, such that , which shows that the state and integer satisfy item 1 of Definition 4. Therefore, . □
It is easy to compute by directly using Proposition 1. Now we present an algorithm for calculating .
From Remark 5, it is easy to find that if holds for all attractors , then the system (10) can be stabilized to (of course, also to the original target subset ) through the appropriate modification to , where can be calculated by using Algorithm 2. Based on this discovery, we give the main theorem.
| Algorithm 2 Let all attractors that are not contained in be given in (11). Assume that , have been obtained. Then, can be calculated by the following steps. |
|
Theorem 1.
Assume that the system (10) has p attractors not included in , and these attractors are given in (11). The system (10) can be stabilized to by making modifications to p columns of , if and only if
where is the largest invariant subset of (10) in . Moreover, if (15) holds, p is the minimum number of columns to be modified to stabilize (10) to .
Proof.
(Necessity) We prove it by using reduction to absurdity. It is assumed that (15) is not true. In other words, there is an attractor that does not belong to .
We know that the system (10) can be stabilized to by modifying . Denote the modification result of by . Then, (10) becomes
which is -stable.
From Lemma 3 of [11], the closed-loop system (16) is also -stable. Now let us take a state from as the initial state. According to Definition 1, there must be a positive integer T, such that
where .
It is noted that
and
Combining (17), (18), and (19), we have
It implies , where k is a nonnegative integer and satisfies . This contradicts our assumption.
(Sufficiency) First, we split into pieces as (12) and (13). From (12) and (13), it is easy to obtain
and
For any , , we consider it in two cases. When , from item 1 of Definition 4, there exists a state and an integer satisfying , such that . Then, is broken by replacing with , and , including , becomes a new part of .
When , according to item 2 of Definition 4, there is a different attractor satisfying , such that . Then, there exists a state and an integer satisfying , such that . We replace with .
In this way, we let the feedback matrix be finally modified into . Then, the closed-loop system (10) turns into
We denote the largest invariant subset of (20) in by . It is easy to find that
Next, we show that the closed-loop system (20) is -stable. We take any point as the initial state. If , the conclusion is a direct result. Otherwise, let and . According to the design method of , there is a state , such that and
where is a different attractor. Then, the front part of the state trajectory of (20) is
where , .
In the following, we use mathematical induction to prove that for the above s, the closed-loop system (20) is convergent to .
When , from the analysis provided above, the state trajectory of (20) must be convergent to . Assume that it is true for the case of . Let us consider the case of , namely .
From (21), we obtain
where is a distinct attractor satisfying . It follows that the state trajectory of (20) is convergent to in accordance with the assumption. Then, the system (20) is -stable, equivalently -stable.
Finally, every attractor in (11) has to be broken to ensure the convergence of the state trajectory to . Hence, the number of modified columns in is no less than p. It implies that p is the minimum number of columns to be modified. □
Remark 6.
1. Under Assumption 1, -stabilizability of the perturbed system (8) is equivalent to that of the system (10), so Theorem 1 provides a necessary and sufficient criterion for -stabilizability of (8).
2. The proof process of Sufficiency in Theorem 1 provides a constructive method for tuning the controller (9). And when the condition (15) is met, only the minimum number of columns in need to be modified.
3. The purpose of modifying into is to increase the possibility of solving Problem 2, since . In other words, if those attractors of the perturbed closed-loop system (8), not included in , all belong to , then we can use our fine-tuning method to directly modify G without calculating the largest invariant subset ; , G).
4. Theorem 1 has a wider scope of application. As we know, most results at present are mainly about restabilization to a single state. However, such a restabilization problem is a special case of the set restabilization (specifically, when the target set is a singleton). In addition, Theorem 1 is not only applicable to single column function perturbation problem of BCNs, but also to the multi-column function perturbation problem that has not been settled yet in [30].
5. Since the dimension of system (5) is , Theorem 1 is of exponential complexity. To some extent, it limits the application of this method in large-scale systems.
3.3. Parameter Adjustment Algorithm
Combining the results of Section 3.1 and Section 3.2 together, we provide an algorithm for fine tuning the parameters of the old state feedback matrix G in (8).
Remark 7.
1. It can be determined in Steps 1 and 2 whether the perturbed system (8) can be restabilized to . The specific fine-tuning process for parameters is implemented in Step 3.
2. As analyzed in Remark 4, the number of parameters that need to be modified is as little as possible in handling Problem 1. In addition, Theorem 1 shows that as long as condition (15) is met, we only need to modify the least number of columns in . Therefore, our method always follows the principle of minimizing the number of modified columns in G.
In order to better understand Algorithm 3, a flowchart is provided in Figure 1. Through Algorithm 3, the matrix is modified into . Then, we obtain the final new controller
which can stabilize the perturbed BCN (7) within .
| Algorithm 3 The closed-loop system (5) is -stable. Assume that BCN (3) is perturbed, its structure matrix L becomes , and the new closed-loop system (8) has p attractors that are not contained in and are given as in (11). Then, under Assumption A1, the problem of fine-tuning the old controller can be solved to restabilize BCN (8) to by the following steps. |
|
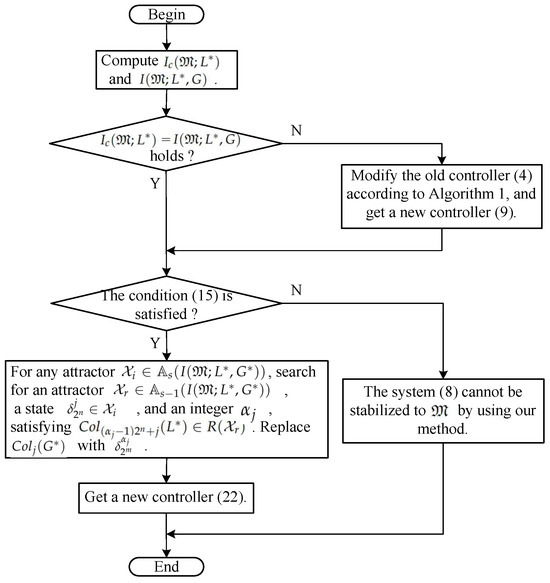
Figure 1.
Flowchart of Algorithm 3.
4. Discussion
In the following, we demonstrate how to deal with the set restabilization problem of a perturbed BCN through two examples.
Example 2.
Consider a simplified model of the lac operon in Escherichia coli, whose stabilization problem has been discussed in [9,12,33].
where the state variables , , and stand for lac mRNA, lactose in high concentrations, and lactose in medium concentrations, respectively; the inputs , , and represent extracellular glucose, high extracellular lactose, and medium extracellular lactose, respectively.
We utilize the vector form of logical variables to set and . Then, it is easy to obtain the algebraic form of BCN (23):
where
Just like in [12], the target set is taken as
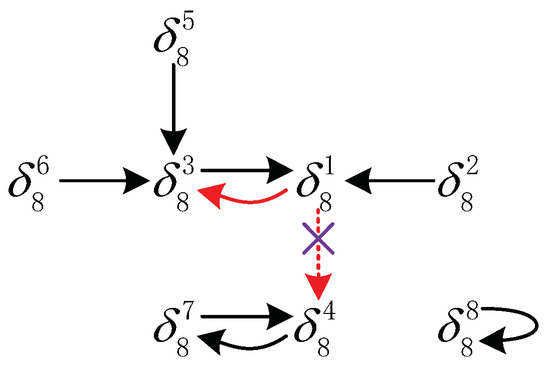
The state transition diagram of (26) is given in Figure 2. Obviously, the closed-loop system (26) is -stable.
Now, let us suppose that the BCN (24) is perturbed. And the 39th, 49th, 57th, and 60th columns of L are changed into , , , and , respectively. Then, (24) becomes
where
Correspondingly, the closed-loop system (26) turns into
We plot the state transition diagram of the perturbed closed-loop system (28) in Figure 3. From this figure, we find that there is an attractor
which is not contained in . Therefore, the perturbed BCN (27) is not -stable if still under the old controller (25).
In the following, we use Algorithm 3 to deal with the -restabilization problem of (27). First, through calculation, we have
Obviously, . So we need to tune the controller (25) to implement as the largest invariant subset of the closed-loop system. We divide into eight blocks
where , .
Because
and
we set
That is to say, the first column of G should be modified from to . Then, we obtain a new controller
Putting (29) into (27), we have
It is directly verified that the largest invariant subset equals . Figure 4 is its state transition diagram.

Similarly, due to
then . It implies that the condition (15) is satisfied. Furthermore, according to Algorithm 3, we modify the fourth column of to . So the final controller is
Remark 8.
Example 2 shows how to fine-tune the old controller to realize -stabilization of the BCN (27) subject to a multi-column function perturbation. It is noted that such a set restabilization problem has not been solved in the current literature.
Example 3.
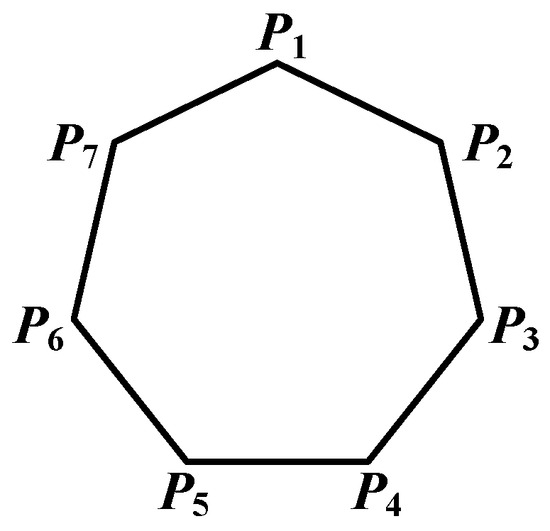

Consider a networked evolutionary game, which has seven players . The network graph is shown in Figure 6. The fundamental game is the Prisoner’s Dilemma [20] and its payoff bimatrix is given in Table 3. The strategy updating rule adopts unconditional imitation with fixed priority [3]. Each player chooses strategy “defect” or “cooperate”, denoted by 1 and 2, respectively. In this model, and are two pseudo-players with the same aim of achieving cooperation among all players.

Figure 6.
Network graph.

Table 3.
Payoff bimatrix for Prisoner’s Dilemma.
We denote the strategies of and at time step t by and , respectively, and express the strategy of as , . Using the techniques provided in [3], we can obtain the algebraic form of the above model:
where and
It is assumed that and are perturbed to and , respectively. That is, the structure matrix L changes into
The target set here is a singleton (“cooperate”. cooperate”. cooperate”. cooperate”. cooperate”. cooperate”. cooperate”), whose algebraic form is . Since the closed-loop system (35) has two fixed points and , then the perturbed networked evolutionary game (34) is unstable if still under the old controller (33).
Remark 9.
5. Conclusions
This paper has proposed a fine-tuning technique to restabilize perturbed BCNs to their target set. A restabilizability criterion was derived and a parameter tuning algorithm was developed. Compared with the existing results, ours have obvious advantages. They are not only applicable to the multi-column function perturbation problem, but can also address the set restabilization of perturbed BCNs, which is a more general stabilization problem.
However, as analyzed in item 5 of Remark 6, Theorem 1 is of exponential complexity, which is the weakness of our method. Seeking a way to effectively reduce the computational complexity of this method is our future research work. One possible solution is to refer to the aggregation algorithm. Firstly, consider and calculate the connected subnetworks separately, and then integrate the parameter tuning problem of the entire network through coupling relationships.
Author Contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work. Conceptualization, Y.H. and H.T.; Data curation, Y.H.; Formal analysis, H.T.; Funding acquisition, H.T.; Investigation, Y.H.; Methodology, Y.H.; Resources, Y.H. and H.T.; Validation, Y.H. and H.T.; Writing—original draft, Y.H.; Writing—review and editing, H.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported by the National Key R&D Program of China (no. 2021YFB3203202), the Chongqing Nature Science Foundation (no. cstc2020jcyj-msxmX0708), and the Technology Innovation and Application Demonstration Project of Chongqing (no. cstc2018jszx-cyzdX0152).
Data Availability Statement
The original contributions presented in the study are included in the article. Further inquiries can be directed to the corresponding authors.
Conflicts of Interest
The authors declare no conflicts of interest.
Nomenclature
| Sets | |
| Set of all n dimensional real vectors | |
| Set of dimensional real matrices | |
| Set of dimensional logical matrices | |
| Set of dimensional matrices with all entries in | |
| Set of all columns in | |
| Target set | |
| Largest invariant subset contained in | |
| Largest control invariant subset contained in | |
| Set of all absorbable attractors of attractor by s steps | |
| Set of n players | |
| Notations | |
| dimensional identity matrix | |
| ith column of a matrix L | |
| ith row of a matrix L | |
| ith column of | |
| dimensional logical matrix | |
| Least common multiplier of n and p | |
| ⊗ | Kronecker product |
| ⋉ | STP |
| Power-reducing matrix | |
| ⊕ | Boolean addition |
| ⊙ | Boolean product |
| Attraction domain of an attractor | |
| Acronyms | |
| BN | Boolean network |
| BCN | Boolean control network |
| STP | Semi-tensor product |
References
- Kauffman, S. Metabolic stability and epigenesis in randomly constructed genetic net. J. Theor. Biol. 1969, 22, 437–467. [Google Scholar] [CrossRef] [PubMed]
- Zong, Y.; Dong, L.; Lu, X. Entropy Model of Rosin Autonomous Boolean Network DigitalTrue Random Number Generator. Electronics 2024, 13, 1140. [Google Scholar] [CrossRef]
- Cheng, D.; He, F.; Qi, H.; Xu, T. Modeling, analysis and control of networked evolutionary game. IEEE Trans. Autom. Control 2015, 60, 2402–2415. [Google Scholar] [CrossRef]
- Shmulevich, I.; Dougherty, E.; Zhang, W. From Boolean to probabilistic Boolean networks as models of genetic regulatory network. Proc. IEEE 2002, 90, 1778–1792. [Google Scholar] [CrossRef]
- Cheng, D.; Qi, H.; Li, Z.; Liu, J. Stability and stabilization of Boolean network. Int. J. Robust Nonlinear Control 2011, 21, 134–156. [Google Scholar] [CrossRef]
- Li, R.; Yang, M.; Chu, T. State feedback stabilization for Boolean control network. IEEE Trans. Autom. Control 2013, 58, 1853–1857. [Google Scholar] [CrossRef]
- Tian, H.; Zhang, H.; Wang, Z.; Hou, Y. Stabilization of k-valued logical control networks by open-Cloop control via the reverse transfer method. Automatica 2017, 83, 387–390. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y. Output feedback stabilization control design for Boolean control network. Automatica 2013, 49, 3641–3645. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y.; Liu, Z. Simultaneous stabilization for a set of Boolean control network. Syst. Control. Lett. 2013, 62, 1168–1174. [Google Scholar] [CrossRef]
- Lin, L.; Cao, J.; Abdel-Aty, M.; Al-Juboori, U. Topological Structure, Reachability, and Stabilization of Constrained Boolean Control Networks via Event-Triggered Control. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 3565–3574. [Google Scholar] [CrossRef]
- Guo, Y.; Wang, P.; Gui, W.; Yang, C. Set stability and set stabilization of Boolean control networks based on invariant subset. Automatica 2015, 61, 106–112. [Google Scholar] [CrossRef]
- Li, F.; Tang, Y. Set stabilization for switched Boolean control network. Automatica 2017, 78, 223–230. [Google Scholar] [CrossRef]
- Liu, R.; Lu, J.; Lou, J.; Alsaedi, A.; Alsaadi, F. Set stabilization of Boolean networks under pinning control strategy. Neurocomputing 2017, 260, 142–148. [Google Scholar] [CrossRef]
- Tian, H.; Hou, Y. State feedback design for set stabilization of probabilistic Boolean control network. J. Frankl. Inst. 2019, 356, 4358–4377. [Google Scholar] [CrossRef]
- Zhu, S.; Liu, Y.; Lou, J.; Lu, J.; Alsaadi, F. Sampled-Data State Feedback Control for the Set Stabilization of Boolean Control Network. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 1580–1589. [Google Scholar] [CrossRef]
- Jia, Y.; Wang, B.; Feng, J.; Cheng, D. Set Stabilization of Boolean Control Networks via Output-Feedback Controller. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 7527–7536. [Google Scholar] [CrossRef]
- Meng, M.; Feng, J. Function perturbations in Boolean networks with its application in a D. Melanogaster gene network. Eur. J. Control 2014, 20, 87–94. [Google Scholar] [CrossRef]
- Liu, Y.; Li, B.; Chen, H.; Cao, J. Function perturbations on singular Boolean network. Automatica 2017, 84, 36–42. [Google Scholar] [CrossRef]
- Wu, J.; Liu, Y.; Ruan, Q.; Lou, J. Robust stability of Switched Boolean Networks with function perturbation. Nonlinear Anal. Hybrid Syst. 2022, 46, 101216. [Google Scholar] [CrossRef]
- Yang, X.; Li, H. Reachability, controllability, and stabilization of Boolean control networks with stochastic function perturbation. IEEE Trans. Syst. Man Cybern. Syst. 2023, 53, 1198–1208. [Google Scholar] [CrossRef]
- Xiao, Y.; Dougherty, E. The impact of function perturbations in Boolean network. Bioinformatics 2007, 23, 1265–1273. [Google Scholar] [CrossRef] [PubMed]
- Qian, X.; Dougherty, E. Effect of function perturbation on the steady-state distribution of genetic regulatory networks: Optimal structural intervention. IEEE Trans. Signal Process. 2008, 56, 4966–4976. [Google Scholar] [CrossRef]
- Li, X.; Li, H.; Li, Y.; Yang, X. Function perturbation impact on stability in distribution of probabilistic Boolean network. Math. Comput. Simul. 2020, 177, 4358–4377. [Google Scholar] [CrossRef]
- Zhu, S.; Lu, J.; Huang, T.; Liu, Y. Output robustness of probabilistic Boolean control networks with respect to one-bit perturbation. IEEE Trans. Control Netw. Syst. 2020, 7, 1769–1777. [Google Scholar] [CrossRef]
- Li, L.; Zhang, A.; Lu, J. Robust set stability of probabilistic Boolean networks under general stochastic function perturbation. Inf. Sci. 2022, 582, 833–849. [Google Scholar] [CrossRef]
- Zhong, J.; Ho, D.; Lu, J.; Xu, W. Global robust stability and stabilization of Boolean network with disturbance. Automatica 2017, 84, 142–148. [Google Scholar] [CrossRef]
- Li, H.; Yang, X.; Wang, S. Robustness for stability and stabilization of Boolean networks with stochastic function perturbation. IEEE Trans. Autom. Control 2021, 66, 1231–1237. [Google Scholar] [CrossRef]
- Zhong, J.; Liu, Y.; Lu, J.; Gui, W. Pinning control for stabilization of Boolean networks under knock-out perturbation. IEEE Trans. Autom. Control 2022, 67, 1550–1557. [Google Scholar] [CrossRef]
- Campbell, C.; Albert, R. Stabilization of perturbed Boolean network attractors through compensatory interaction. BMC Syst. Biol. 2014, 53, 53. [Google Scholar] [CrossRef]
- Li, X.; Li, H.; Zhao, G. Function perturbation impact on feedback stabilization of Boolean control network. IEEE Trans. Neural Netw. Learn. Syst. 2019, 30, 2548–2554. [Google Scholar] [CrossRef]
- Hou, Y.; Tian, H.; Wang, C. Restabilization of perturbed Boolean control networks based on absorbable attractor. Asian J. Control 2024. [Google Scholar] [CrossRef]
- Cheng, D.; Qi, H.; Li, Z. Analysis and Control of Boolean Networks: A Semi-Tensor Product Approach; Springer: London, UK, 2011. [Google Scholar]
- Veliz-Cuba, A.; Stigler, B. Boolean models can explain bistability in the lac operon. J. Comput. Biol. 2011, 18, 783–794. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).