Abstract
CHAM is a family of lightweight block ciphers designed for resource-constrained environments like IoT devices and embedded systems, which require low power consumption and high performance. Despite numerous cryptanalytic evaluations, the security of CHAM remains robust. Differential–linear cryptanalysis, a method that combines two of the strongest attack methods on block ciphers—differential cryptanalysis and linear cryptanalysis—has been successfully applied to many block ciphers. This study introduces the first concrete differential–linear approximations of CHAM, marking a significant advancement in the cryptanalysis of this cipher family. Utilizing a Boolean satisfiability problem framework, we present a 46-round differential–linear approximation of CHAM-64/128 with a correlation of and a 58-round approximation for CHAM-128/128 and CHAM-128/256 with correlations of and , respectively. These findings significantly exceed the designers’ expectations for differential–linear approximations using CHAM. Furthermore, the 46-round differential–linear approximation of CHAM-64/128 is the best distinguisher of CHAM-64/128 to date in a single-key attack model. Notably, our findings do not threaten the security of CHAM but provide deeper insights into its cryptanalytic resistance.
1. Introduction
CHAM is a family of lightweight block ciphers designed for resource-constrained environments, such as Internet of Things (IoT) devices, embedded systems, and other applications where both low power consumption and high performance are crucial. It was introduced by Koo et al. [1] and further revised by Roh et al. [2] to increase the numbers of rounds (note that only the numbers of rounds were changed, without changing the other structures). CHAM is based on a four-branch generalized Feistel structure and consists of ARX operations (modular addition , bitwise rotation , and bitwise XOR ). There are three ciphers, CHAM-64/128, CHAM-128/128, and CHAM-128/256, where the first number denotes the block size in bits and the second number denotes the key size in bits. For example, CHAM-64/128 has a 64-bit block size and a 128-bit key size, while CHAM-128/256 features a 128-bit block and a 256-bit key. Notably, CHAM is one of the ciphers that can be implemented with the smallest hardware area.
Several cryptanalytic results using CHAM have been published, including differential cryptanalysis [3,4], linear cryptanalysis [5], integral cryptanalysis [6], meet-in-the-middle type attacks [7,8], and impossible differential cryptanalysis [9]. Despite these analyses, the security of CHAM remains unthreatened due to its sufficient security margin.
Two important statistical techniques in the cryptanalysis of block ciphers are differential cryptanalysis, introduced by Biham and Shamir [10], and linear cryptanalysis, introduced by Matsui [11]. These techniques have been used to mount the best-known attacks on numerous block ciphers [12,13,14,15]. Consequently, resistance to these two cryptanalytic techniques, particularly the non-existence of high-probability differential characteristics or high-bias linear approximations spanning many rounds of the cipher, has become a crucial criterion in block cipher design.
The initial step in differential cryptanalysis is to search for high-probability differential characteristics, while in linear cryptanalysis, it is to search for high-correlation linear approximations. Over the last decade, a major focus has been on developing efficient methods to automatically search for these distinguishers (differential characteristics and linear approximations) [14,16,17,18,19,20]. Notable works in this area have significantly expanded the search space that can be explored within a practical time, thereby increasing our confidence in a cipher’s resistance against differential cryptanalysis and linear cryptanalysis.
For some block ciphers, it is relatively easy to find high-probability differential characteristics and high-correlation linear approximations within a few rounds. However, as the number of rounds increases, the effectiveness of both differential and linear cryptanalysis decreases. While it might seem that preventing long differential characteristics and linear approximations would suffice to make a block cipher immune to these attacks, short characteristics and approximations can also be exploited to break the cipher. The first cryptanalytic technique to demonstrate this was differential–linear cryptanalysis, introduced by Langford and Hellman in 1994 [21]. This technique combines differential cryptanalysis and linear cryptanalysis, leveraging their individual strengths over a few rounds to mount more effective attacks over many rounds. Differential–linear cryptanalysis has been used to evaluate the security of many block ciphers, including IDEA [22], COCONUT98 [23], Serpent [24,25], CTC2 [25], ICEPOLE [26,27], Chaskey [28,29], ChaCha [29], LEA [30], SPECK [30], and others. However, no concrete differential–linear approximations for CHAM have been reported until now. Currently, the only information we have is the expectation set by the designers of CHAM that differential–linear approximations would not exist beyond a certain number of rounds.
In differential–linear cryptanalysis, a crucial initial step is identifying differential–linear approximations (denoted by ) with high correlations. The development of automated searches for these approximations has remained virtually stagnant for nearly 20 years. Researchers typically identify differential–linear approximations using a three-stage process: (1) experimentally verifying short differential–linear approximations, denoted by ; (2) searching for short differential characteristics (denoted by ) and linear approximations (denoted by ); and (3) concatenating these three short distinguishers (differential characteristics and linear approximations) into a long differential–linear approximation . Due to the lack of an efficient method for searching for the short differential–linear approximations of , the practical search space for a difference is severely constrained to linear masks, , with a Hamming weight of 1 or 2. This persistent limitation weakens confidence in a cipher’s resistance to differential–linear cryptanalysis.
Recently, two methods have been proposed to automatically find the differential–linear approximation of the ARX cipher. One is based on mixed-integer linear programming (MILP) and mixed-integer quadratic constraint programming (MIQCP) techniques [31], and the other is based on a Boolean satisfiability problem [30]. The primary objective of this study is to provide the first concrete differential–linear approximations of CHAM, one of the ARX ciphers, by utilizing the latter framework.
1.1. Our Contributions
This paper gives the first concrete differential–linear approximations of CHAM. To the best of our knowledge, the security analysis of CHAM against differential–linear cryptanalysis has only been provided by its designers. However, they did not present concrete differential–linear approximations. They only provided upper bounds on the maximum numbers of rounds for which they expected differential–linear approximations to exist. This was achieved by using the known maximum probabilities of the differential characteristics and the known maximum correlations of the linear characteristics for short rounds. Furthermore, their analysis did not consider the differential–linear connectivity table (DLCT) and focused solely on the direct combination of differential characteristics and linear approximations.
Specifically, we present a 46-round differential–linear approximation with a correlation of for CHAM-64/128. This differential–linear approximation demonstrates that a differential–linear approximation can indeed cover significantly more rounds than anticipated by the designers of CHAM. Additionally, this approximation serves as a distinguisher for the longest rounds within the single-key attack model. The previous best distinguisher in the single-key model was the 40-round differential [7]. If we take the multi-key model into account, the 47-round related-key differential characteristic is the best distinguisher [2].
Furthermore, we introduce a 58-round differential–linear approximation with correlations of and for CHAM-128/128 and CHAM-128/256, respectively. Although this does not serve as a distinguisher for the longest rounds, it nevertheless illustrates that a differential–linear approximation can span more rounds than anticipated by the designers of CHAM. Note that the best distinguisher in the single-key model is the 67-round differential [2].
Table 1 provides a summary of our differential–linear approximation results compared to existing distinguishers for CHAM.

Table 1.
Summary of distinguishers of CHAM.
1.2. Paper Organization
The outline of the paper is as follows. In Section 2, we provide basic definitions and notations, introduce differential–linear approximations, Boolean satisfiability problems, and SAT solvers, and describe CHAM. We review the method proposed by Chen et al. for searching for differential–linear approximations of ARX block ciphers in Section 3. Section 4 presents our results: the first differential–linear approximations of CHAM. Finally, Section 5 concludes this paper and proposes further studies.
2. Preliminaries
2.1. Basic Definitions and Notations
Given a vector , denotes the j-th bit of x, where is the least significant bit. Let us denote as the vector , such that and for and . Let denote , where , and . The inner product of two vectors x and y in is defined as .
The correlation of a Boolean function over a set is defined as follows:
For a vectorial Boolean function , a set , an n-bit input mask , and an m-bit output mask , the (linear) correlation of f with respect to the set and the mask pair, denoted by , is defined to be the correlation of a Boolean function over the set S as follows:
We call the pair the linear approximation of f over S. When , we call it the linear approximation of f.
Example 1.

Let be a vectorial Boolean function. The function f maps the input x to an output , as given in hexadecimal notation in Table 2. (The function f is the 4-bit to 4-bit S-box of PRESENT [32].) Let and . Then, the linear correlation of f with respect to the set and the mask pair is as follows:

Table 2.
The vectorial Boolean function f.
2.2. Differential–Linear Approximation
The initial approach developed by Langford and Hellman [21] involved splitting the targeted cipher E into two sub-ciphers, and , such that , and combining a differential characteristic for with a linear approximation for to form an attack on the entire cipher E. Thanks to the differential–linear connectivity table concept introduced by Bar-On et al. [27], the differential–linear attack strategy has evolved to divide the cipher E into three sub-ciphers, , , and , such that instead of two (Figure 1).
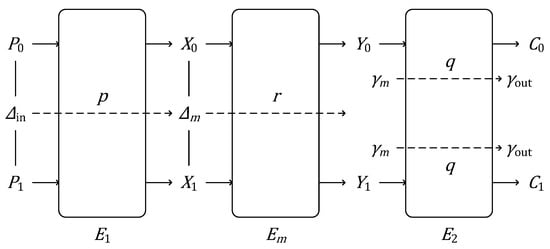
Figure 1.
The structure of a differential–linear approximation.
Suppose that the differential characteristic for , , holds with a probability p, the linear approximation for , , has a correlation of q, and the differential–linear approximation for , , has a correlation of r:
where S represents the set of samples used to calculate the correlation. Note that when involves round keys, the correlation r is estimated using N samples and M random keys. This is achieved by computing an empirical value with a random key and repeating the process M times. The final value of r is determined as the median (or mean) of the M obtained values [27,30,33]. Subsequently, the total correlation of the differential–linear approximation is estimated as follows:
2.3. Boolean Satisfiability Problem and SAT Solver
The Boolean satisfiability problem involves determining whether a given Boolean formula can be satisfied by any interpretation. In other words, it aims to ascertain if the variables in the formula can be assigned values of TRUE or FALSE in a consistent manner that results in the formula being evaluated as TRUE. If such an assignment is possible, the formula is said to be satisfiable. Conversely, if no such assignment exists, the formula is unsatisfiable, indicating that the formula is evaluated as FALSE for all potential variable assignments.
Example 2.

Consider the Boolean formula . To determine if this formula is satisfiable, we can construct the following truth table (see Table 3). The formula is satisfiable because there are combinations of P, Q, and R (specifically, and ) that make the formula true.

Table 3.
The truth table of .
The Boolean satisfiability problem is known to fall into the category of NP-complete problems, which means that currently, only algorithms with exponential worst-case complexity can solve it. Despite this complexity, there is ongoing research and development aimed at creating efficient and scalable algorithms to address it.
In this paper, we use two well-known SAT solvers, CryptoMiniSat by M. Soos et al. [34] and CaDiCaL by Biere [35], to search for differential–linear approximations of CHAM. CryptoMiniSat is recognized for its efficiency, scalability, and suitability for cryptographic applications. It supports multi-threaded operations and XOR clauses, making it highly versatile. On the other hand, CaDiCaL is designed with simplicity, performance, and lightweight architecture in mind, excelling in situations where these attributes are paramount. Both solvers bring unique strengths to the table, contributing to the continuous efforts to develop robust solutions for the Boolean satisfiability problem.
2.4. The Block Cipher CHAM
CHAM, consisting of ARX operations (modular addition , bitwise rotation , and bitwise XOR ), is a family of block ciphers with a four-branch generalized Feistel structure. Each cipher in this family is denoted as CHAM-n/k, where n represents the block size in bits and k represents the key size in bits. Table 4 lists the ciphers in this family and their parameters. Here, w denotes the bit length of a branch (word) and represents the number of rounds.

Table 4.
The block cipher CHAM parameters.
By applying iterations of the key-dependent round function, CHAM-n/k encrypts an n-bit plaintext of four w-bit words to an n-bit ciphertext of four w-bit words. For a round key , the i-th round function of CHAM is defined as follows:
where and when i is even and and when i is odd. The round function of CHAM is depicted in Figure 2.
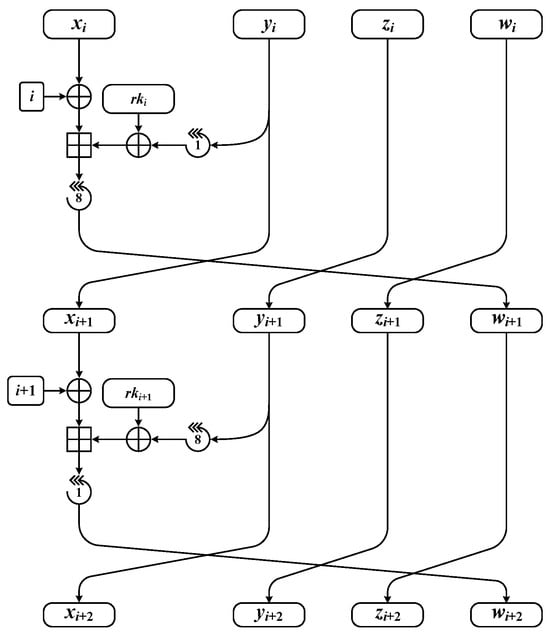
Figure 2.
The round function of CHAM.
The CHAM key schedules generate round keys for a given key of w-bit words . The round keys are generated by the following:
where . The value is the i-th round key for .
3. Searching for Differential–Linear Approximations
In this section, we briefly review the method proposed by Chen et al. for finding differential–linear approximations of block ciphers [30]. The core idea of Chen et al.’s method involves generating new differential–linear approximations by XORing known approximations, aiming to create approximations with high correlations. Their motivation is based on an intuitive understanding of correlations, leading to the conclusion that combining high-correlation approximations is likely to result in another effective approximation. Although this hypothesis relies on an assumption of independence that may not always be valid, it has been supported by experimental results.
We first introduce two concepts, strong unbalanced bit and weak unbalanced bit.
Definition 1
([30]). Consider an n-bit block cipher, an n-bit difference Δ, and a threshold c. The i-th ciphertext bit, where , is called a strong unbalanced bit if the absolute correlation of the differential–linear approximation exceeds c, where . If this condition is not met, the bit is called a weak unbalanced bit.
Suppose that two sub-ciphers, and and a difference are given. Based on the heuristic conclusion, a meet-in-the-middle search algorithm to search for differential–linear approximations is proposed. The algorithm works as follows. We first search for a set of strong unbalanced bits, , for a sub-cipher , a difference , and a threshold. Next, we search for linear approximations of a sub-cipher under the conditions that if for . Finally, for each returned linear approximation of , we compute the experimental correlation of the differential–linear approximation. We add the approximation to a list if the correlation is greater than or equal to the threshold. See Algorithm 1 for the detailed steps.
| Algorithm 1 [30] Searching for using the meet-in-the-middle method |
|
4. Differential–Linear Approximations of CHAM
This section presents the first differential–linear approximations of CHAM. We will denote , , and as the numbers of rounds covered by , , and , respectively. We first search for a differential–linear approximation and a linear approximation using Algorithm 1. Following this, we prepend a differential characteristic . Given the computational infeasibility of testing all the differences , we confine our investigation to cases where takes the form for (1-bit differences) or for (2-bit differences).
4.1. Differential–Linear Approximation of CHAM-64/128
This subsection presents the first differential–linear approximation of CHAM-64/128. A 46-round differential–linear approximation of CHAM-64/128 with a correlation of is found using Algorithm 1 by setting , , and (see Table 5). This approximation is composed of the following:

Table 5.
A 46-round differential–linear approximation of CHAM-64/128.
- A six-round differential characteristic with an output difference of and a probability of (note that this is optimal, as there is no six-round differential characteristic with a higher probability for this output difference; see Table 6);
 Table 6. An optimal 6-round differential characteristic of CHAM-64/128 with an output difference of .
Table 6. An optimal 6-round differential characteristic of CHAM-64/128 with an output difference of . - A 26-round differential–linear approximation with a correlation of . This value is the median of 200 experimental correlations, each derived from plaintext–ciphertext pairs. (The average and standard deviation of the 200 correlations are and , respectively. The 95% and 99% confidence intervals are , and , respectively.)
- A 14-round linear approximation with a correlation of (Note that this is also optimal, as there is no 14-round linear approximation with a higher correlation; see Table 7).
 Table 7. An optimal 14-round linear approximation of CHAM-64/128 with a correlation of .
Table 7. An optimal 14-round linear approximation of CHAM-64/128 with a correlation of .
This approximation represents the most effective distinguisher for CHAM-64/128 found to date in a single-key attack model, significantly exceeding the designers’ expectations for differential–linear approximations of CHAM-64/128.
As mentioned earlier, for each 1-bit and 2-bit difference, the set of strong unbalanced bits for the 26-round is determined using the threshold and pseudo plaintext–ciphertext pairs. These results are summarized in Table A1 provided in Appendix A.
4.2. Differential–Linear Approximation of CHAM-128/128 and CHAM-128/256
This subsection presents the first differential–linear approximation of CHAM-128/128 and CHAM-128/256. A 58-round differential–linear approximation with correlations of for CHAM-128/128 and for CHAM-128/256 is found using Algorithm 1 by setting , , and (see Table 8). This approximation is composed of the following:

Table 8.
A 58-round differential–linear approximation of CHAM-128/128 and CHAM-128/256.
- A 10-round differential characteristic with an output difference of and a probability of (Note that this is optimal, as there is no 10-round differential characteristic with a higher probability for this output difference. See Table 9);
 Table 9. An optimal 10-round differential characteristic of CHAM-128/128 and CHAM-128/256 with an output difference of .
Table 9. An optimal 10-round differential characteristic of CHAM-128/128 and CHAM-128/256 with an output difference of . - A 32-round differential–linear approximation with correlations of for CHAM-128/128 and for CHAM-128/256 (These values are the medians of 100 experimental correlations, each derived from plaintext–ciphertext pairs. (For CHAM-128/128, the average and standard deviation of the 100 correlations are and , respectively. The 95% and 99% confidence intervals are , and , respectively. For CHAM-128/256, the average and standard deviation of the 100 correlations are and , respectively. The 95% and 99% confidence intervals are , and , respectively).
- A 16-round linear approximation with a correlation of (note that this is also optimal, as there is no 16-round linear approximation with a higher correlation; see Table 10).
 Table 10. An optimal 16-round linear approximation of CHAM-128/128 and CHAM-128/256 with a correlation of .
Table 10. An optimal 16-round linear approximation of CHAM-128/128 and CHAM-128/256 with a correlation of .
Although this approximation is not the best distinguisher for CHAM-128/128 and CHAM-128/256, it stands as the first concrete differential–linear approximation. Remarkably, it surpasses the designers’ expectations for differential–linear approximations of CHAM-128/128 and CHAM-128/256.
As mentioned earlier, for each 1-bit and 2-bit difference, the set of strong unbalanced bits for the 32-round is determined using the threshold and pseudo plaintext–ciphertext pairs. These results are summarized in Table A2 and Table A3 provided in Appendix A.
5. Conclusions
In this work, we presented the first concrete differential–linear approximations of CHAM. We found a 46-round differential–linear approximation of CHAM-64/128 with a correlation of and a 58-round approximation for CHAM-128/128 and CHAM-128/256 with correlations of and , respectively. These are not only the first known concrete differential–linear approximations of CHAM, but they also have much longer rounds than the designers anticipated. Despite these findings, CHAM remains secure due to its sufficient security margin.
Further research is needed to better understand the differential–linear approximations and differential–linear cryptanalysis of ARX-based block ciphers, including CHAM. We anticipate that the following studies are necessary:
- mounting differential–linear attacks on CHAM using known differential–linear approximations,
- calculating more exact correlations of the differential–linear approximations, and
- developing more efficient and effective methods for finding differential–linear approximations.
Funding
This work was supported by an Institute of Information & communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (No. 2021-0-00046, Development of next-generation cryptosystem to improve security and usability of national information system).
Data Availability Statement
The data are contained within this article.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A. Experimental Results

Table A1.
Strong unbalanced bits for 26-round CHAM-64/128 with a threshold of .
Table A1.
Strong unbalanced bits for 26-round CHAM-64/128 with a threshold of .
| Input Difference | # | Strong Unbalanced Bits |
|---|---|---|
| 10 | 20, 27, 34, 35, 36, 37, 44, 53, 58, 60 | |
| 8 | 21, 35, 36, 37, 38, 45, 54, 59 | |
| 11 | 22, 29, 36, 37, 38, 39, 46, 55, 59, 60, 62 | |
| 8 | 23, 38, 39, 40, 47, 56, 61, 63 | |
| 8 | 24, 32, 39, 40, 41, 55, 57, 62 | |
| 8 | 25, 33, 40, 41, 42, 49, 58, 63 | |
| 7 | 26, 33, 34, 41, 42, 43, 59 | |
| 6 | 27, 35, 42, 43, 44, 60 | |
| 10 | 4, 27, 28, 35, 36, 43, 44, 45, 52, 59 | |
| 8 | 29, 36, 37, 44, 45, 46, 51, 62 | |
| 10 | 14, 21, 30, 38, 44, 45, 46, 47, 52, 63 | |
| 12 | 0, 15, 22, 31, 32, 39, 45, 46, 47, 48, 53, 55 | |
| 13 | 0, 15, 16, 23, 32, 33, 40, 46, 47, 49, 54, 56, 63 | |
| 11 | 0, 17, 24, 32, 33, 34, 41, 47, 50, 55, 57 | |
| 11 | 1, 18, 25, 27, 32, 33, 34, 35, 42, 51, 56 | |
| 10 | 19, 26, 33, 34, 35, 36, 43, 52, 57, 59 | |
| 6 | 35, 36, 52, 53, 59, 60 | |
| 9 | 14, 36, 37, 44, 52, 53, 54, 60, 61 | |
| 8 | 15, 38, 45, 53, 54, 55, 61, 62 | |
| 7 | 39, 46, 54, 55, 56, 62, 63 | |
| 8 | 1, 40, 47, 48, 55, 56, 57, 63 | |
| 7 | 2, 32, 41, 49, 56, 57, 58 | |
| 7 | 3, 33, 42, 50, 57, 58, 59 | |
| 7 | 4, 34, 43, 51, 58, 59, 60 | |
| 6 | 35, 44, 52, 59, 60, 61 | |
| 7 | 36, 45, 53, 59, 60, 61, 62 | |
| 6 | 46, 53, 54, 61, 62, 63 | |
| 6 | 47, 48, 54, 55, 62, 63 | |
| 5 | 32, 48, 49, 56, 63 | |
| 5 | 33, 49, 50, 56, 57 | |
| 7 | 33, 34, 49, 50, 51, 57, 58 | |
| 7 | 12, 34, 35, 50, 51, 52, 59 | |
| 2 | 52, 59 | |
| 1 | 53 | |
| 3 | 31, 54, 61 | |
| 1 | 55 | |
| 2 | 1, 56 | |
| 2 | 18, 57 | |
| 2 | 3, 58 | |
| 3 | 35, 44, 59 | |
| 1 | 60 | |
| 2 | 52, 61 | |
| 4 | 23, 46, 53, 62 | |
| 4 | 32, 47, 54, 63 | |
| 6 | 25, 32, 47, 48, 55, 63 | |
| 4 | 26, 32, 49, 56 | |
| 6 | 27, 33, 35, 50, 57, 59 | |
| 1 | 51 | |
| 10 | 12, 20, 27, 28, 29, 34, 36, 45, 51, 58 | |
| 13 | 4, 13, 21, 27, 28, 29, 30, 35, 37, 46, 51, 52, 59 | |
| 11 | 14, 22, 29, 30, 31, 36, 47, 52, 53, 59, 60 | |
| 8 | 15, 16, 23, 31, 32, 53, 54, 61 | |
| 9 | 0, 16, 17, 24, 31, 33, 54, 55, 62 | |
| 10 | 1, 17, 18, 25, 32, 34, 41, 55, 56, 63 | |
| 9 | 2, 17, 18, 19, 26, 35, 48, 56, 57 | |
| 10 | 3, 18, 19, 20, 27, 36, 43, 49, 57, 58 | |
| 9 | 4, 20, 21, 27, 28, 35, 44, 50, 59 | |
| 7 | 5, 21, 22, 29, 51, 59, 60 | |
| 10 | 6, 22, 23, 29, 30, 44, 46, 52, 60, 61 | |
| 11 | 7, 14, 22, 23, 24, 31, 45, 53, 60, 61, 62 | |
| 12 | 8, 15, 16, 23, 24, 25, 32, 41, 46, 54, 62, 63 | |
| 13 | 0, 9, 17, 24, 25, 26, 33, 42, 47, 48, 54, 55, 63 | |
| 11 | 1, 10, 18, 25, 26, 27, 32, 34, 43, 49, 56 | |
| 14 | 2, 11, 19, 26, 27, 28, 33, 35, 44, 49, 50, 56, 57, 59 | |
| 3 | 35, 36, 37 | |
| 5 | 36, 37, 38, 45, 59 | |
| 4 | 38, 39, 46, 55 | |
| 4 | 39, 40, 47, 63 | |
| 5 | 24, 32, 40, 41, 57 | |
| 4 | 25, 33, 41, 42 | |
| 4 | 34, 42, 43, 59 | |
| 4 | 27, 35, 43, 44 | |
| 4 | 28, 36, 44, 45 | |
| 5 | 29, 37, 44, 45, 46 | |
| 6 | 30, 38, 45, 46, 47, 63 | |
| 5 | 31, 32, 46, 47, 55 | |
| 6 | 32, 33, 40, 47, 49, 54 | |
| 8 | 17, 32, 33, 34, 41, 47, 55, 57 | |
| 4 | 33, 34, 35, 51 | |
| 3 | 35, 36, 52 | |
| 4 | 36, 52, 53, 60 | |
| 3 | 53, 54, 61 | |
| 4 | 38, 54, 55, 62 | |
| 3 | 55, 56, 63 | |
| 5 | 1, 48, 55, 56, 57 | |
| 3 | 49, 57, 58 | |
| 6 | 33, 42, 50, 57, 58, 59 | |
| 2 | 59, 60 | |
| 4 | 52, 59, 60, 61 | |
| 4 | 45, 53, 61, 62 | |
| 4 | 46, 54, 62, 63 | |
| 4 | 47, 48, 55, 63 | |
| 5 | 32, 48, 49, 56, 63 | |
| 4 | 33, 49, 50, 57 | |
| 5 | 34, 49, 50, 51, 58 | |
| 0 | - | |
| 0 | - | |
| 0 | - | |
| 0 | - | |
| 1 | 55 | |
| 1 | 56 | |
| 1 | 57 | |
| 0 | - | |
| 1 | 59 | |
| 1 | 60 | |
| 1 | 61 | |
| 1 | 62 | |
| 1 | 63 | |
| 1 | 48 | |
| 2 | 49, 56 | |
| 1 | 27 | |
| 13 | 3, 4, 5, 12, 21, 28, 34, 43, 51, 57, 58, 59, 60 | |
| 8 | 20, 27, 28, 29, 36, 45, 51, 58 | |
| 7 | 21, 29, 30, 35, 46, 52, 59 | |
| 8 | 14, 22, 30, 31, 36, 47, 53, 60 | |
| 6 | 15, 16, 23, 31, 54, 61 | |
| 7 | 0, 16, 17, 24, 33, 55, 62 | |
| 9 | 1, 17, 18, 25, 34, 41, 55, 56, 63 | |
| 8 | 2, 18, 19, 26, 35, 48, 56, 57 | |
| 8 | 3, 19, 20, 27, 36, 49, 57, 58 | |
| 6 | 4, 20, 21, 28, 44, 59 | |
| 6 | 21, 22, 29, 51, 59, 60 | |
| 9 | 6, 22, 23, 30, 44, 46, 52, 60, 61 | |
| 7 | 23, 24, 31, 45, 53, 61, 62 | |
| 10 | 16, 23, 24, 25, 32, 41, 46, 54, 62, 63 | |
| 8 | 17, 25, 26, 33, 42, 47, 48, 55 | |
| 11 | 1, 10, 18, 25, 26, 27, 32, 34, 43, 49, 56 |

Table A2.
Strong unbalanced bits for 32-round CHAM-128/128 with a threshold of .
Table A2.
Strong unbalanced bits for 32-round CHAM-128/128 with a threshold of .
| Input Difference | # | Strong Unbalanced Bits |
|---|---|---|
| 17 | 4, 5, 44, 55, 77, 83, 84, 87, 88, 95, 96, 109, 110, 117, 122, 123, 124 | |
| 17 | 5, 6, 45, 56, 64, 78, 84, 85, 88, 89, 97, 111, 117, 118, 123, 124, 125 | |
| 19 | 6, 7, 39, 46, 57, 65, 79, 85, 86, 89, 90, 98, 105, 112, 118, 119, 124, 125, 126 | |
| 18 | 1, 8, 40, 47, 58, 66, 80, 86, 87, 90, 91, 99, 113, 119, 120, 125, 126, 127 | |
| 20 | 2, 8, 9, 41, 48, 59, 67, 74, 81, 87, 88, 91, 92, 96, 100, 114, 120, 121, 126, 127 | |
| 20 | 3, 9, 10, 49, 60, 68, 75, 82, 88, 89, 92, 93, 96, 97, 101, 108, 115, 121, 122, 127 | |
| 19 | 4, 10, 11, 61, 69, 76, 83, 89, 90, 93, 94, 96, 97, 98, 102, 109, 116, 122, 123 | |
| 19 | 5, 11, 12, 51, 62, 70, 77, 84, 90, 91, 94, 95, 97, 98, 99, 103, 117, 123, 124 | |
| 19 | 6, 12, 13, 52, 63, 64, 71, 78, 85, 91, 92, 95, 98, 99, 100, 104, 118, 124, 125 | |
| 18 | 13, 14, 32, 53, 64, 65, 72, 79, 86, 92, 93, 99, 100, 101, 105, 119, 125, 126 | |
| 21 | 1, 8, 14, 15, 33, 54, 65, 66, 73, 80, 87, 93, 94, 99, 100, 101, 102, 106, 120, 126, 127 | |
| 23 | 2, 9, 15, 16, 34, 41, 55, 66, 67, 74, 81, 88, 94, 95, 96, 100, 101, 102, 103, 107, 114, 121, 127 | |
| 23 | 3, 10, 16, 17, 35, 56, 64, 67, 68, 75, 82, 89, 95, 96, 97, 101, 102, 103, 104, 108, 115, 121, 122 | |
| 21 | 4, 11, 17, 18, 36, 57, 64, 65, 68, 69, 76, 83, 90, 97, 98, 103, 104, 105, 109, 122, 123 | |
| 21 | 5, 12, 18, 19, 37, 58, 65, 66, 69, 70, 77, 84, 91, 98, 99, 104, 105, 106, 117, 123, 124 | |
| 19 | 13, 19, 20, 38, 59, 66, 67, 70, 71, 78, 92, 99, 100, 105, 106, 107, 111, 124, 125 | |
| 17 | 14, 20, 21, 39, 60, 67, 68, 72, 79, 93, 100, 101, 106, 107, 108, 125, 126 | |
| 18 | 15, 21, 22, 40, 61, 68, 69, 72, 73, 80, 94, 101, 102, 107, 108, 109, 126, 127 | |
| 19 | 16, 22, 23, 41, 62, 69, 70, 73, 74, 81, 95, 96, 102, 103, 108, 109, 110, 114, 127 | |
| 21 | 17, 23, 24, 42, 63, 64, 70, 71, 74, 75, 82, 96, 97, 103, 104, 108, 109, 110, 111, 115, 122 | |
| 20 | 18, 24, 25, 32, 43, 65, 71, 72, 75, 76, 83, 97, 98, 104, 105, 109, 110, 111, 112, 116 | |
| 18 | 19, 26, 33, 44, 66, 72, 73, 76, 77, 84, 98, 99, 105, 106, 111, 112, 113, 117 | |
| 20 | 26, 27, 34, 45, 67, 73, 74, 77, 78, 85, 92, 99, 100, 106, 107, 112, 113, 114, 118, 125 | |
| 13 | 28, 35, 68, 74, 75, 78, 79, 86, 101, 108, 113, 114, 115 | |
| 19 | 28, 29, 36, 47, 69, 75, 76, 79, 80, 87, 94, 101, 102, 108, 109, 114, 115, 116, 127 | |
| 18 | 16, 29, 30, 37, 70, 76, 77, 80, 81, 88, 102, 103, 109, 110, 115, 116, 117, 121 | |
| 23 | 17, 30, 31, 38, 49, 64, 71, 76, 77, 78, 80, 81, 82, 89, 97, 103, 104, 111, 115, 116, 117, 118, 122 | |
| 22 | 0, 18, 31, 39, 50, 65, 72, 77, 78, 79, 82, 83, 90, 98, 104, 105, 111, 112, 117, 118, 119, 123 | |
| 21 | 0, 1, 19, 40, 51, 66, 73, 78, 79, 80, 83, 84, 91, 99, 105, 106, 113, 118, 119, 120, 124 | |
| 23 | 1, 2, 20, 27, 41, 52, 67, 74, 79, 80, 81, 84, 85, 92, 100, 106, 107, 113, 114, 119, 120, 121, 125 | |
| 26 | 2, 3, 21, 28, 35, 42, 53, 60, 68, 75, 80, 81, 82, 85, 86, 93, 101, 107, 108, 114, 115, 119, 120, 121, 122, 126 | |
| 21 | 3, 4, 36, 43, 54, 61, 69, 76, 82, 83, 86, 87, 94, 108, 109, 115, 116, 121, 122, 123, 127 | |
| 10 | 36, 37, 62, 69, 76, 87, 109, 115, 116, 120 | |
| 9 | 30, 37, 38, 63, 77, 88, 117, 121, 122 | |
| 11 | 31, 32, 38, 39, 57, 78, 89, 111, 117, 118, 122 | |
| 10 | 0, 33, 39, 40, 58, 79, 90, 118, 119, 123 | |
| 12 | 1, 34, 40, 41, 59, 80, 91, 99, 113, 119, 120, 124 | |
| 12 | 2, 35, 41, 42, 60, 81, 92, 100, 114, 120, 121, 125 | |
| 12 | 3, 36, 43, 61, 82, 93, 115, 121, 122, 125, 126, 127 | |
| 11 | 4, 37, 43, 44, 62, 83, 94, 122, 123, 126, 127 | |
| 10 | 5, 38, 44, 45, 63, 84, 95, 96, 123, 124 | |
| 11 | 6, 32, 39, 45, 46, 64, 85, 97, 98, 124, 125 | |
| 10 | 33, 40, 47, 65, 86, 98, 99, 119, 125, 126 | |
| 12 | 34, 41, 47, 48, 66, 80, 98, 99, 100, 120, 126, 127 | |
| 10 | 9, 35, 49, 67, 88, 96, 99, 100, 121, 127 | |
| 11 | 10, 36, 43, 50, 68, 89, 96, 97, 100, 101, 122 | |
| 12 | 11, 37, 44, 51, 69, 90, 97, 98, 102, 103, 109, 123 | |
| 10 | 12, 38, 45, 52, 70, 91, 98, 99, 103, 124 | |
| 9 | 13, 39, 53, 92, 99, 100, 104, 105, 125 | |
| 9 | 14, 40, 53, 54, 72, 100, 101, 105, 126 | |
| 10 | 15, 41, 55, 73, 94, 101, 102, 105, 106, 127 | |
| 9 | 16, 55, 56, 74, 95, 96, 102, 103, 107 | |
| 10 | 17, 43, 57, 64, 75, 97, 103, 104, 108, 115 | |
| 12 | 18, 44, 51, 57, 58, 65, 76, 98, 104, 105, 108, 109 | |
| 10 | 19, 45, 59, 66, 77, 99, 105, 106, 109, 110 | |
| 10 | 20, 53, 59, 60, 67, 78, 100, 106, 107, 111 | |
| 6 | 21, 61, 79, 101, 108, 112 | |
| 9 | 22, 61, 62, 69, 80, 102, 108, 109, 113 | |
| 9 | 62, 63, 70, 81, 103, 109, 110, 114, 115 | |
| 7 | 24, 32, 63, 82, 104, 111, 115 | |
| 9 | 33, 72, 83, 105, 111, 112, 115, 116, 117 | |
| 8 | 33, 34, 59, 73, 84, 106, 113, 117 | |
| 9 | 27, 35, 53, 60, 74, 85, 114, 118, 119 | |
| 12 | 28, 35, 36, 54, 61, 75, 86, 108, 114, 115, 119, 126 | |
| 5 | 61, 68, 69, 108, 119 | |
| 5 | 62, 69, 70, 109, 120 | |
| 7 | 63, 64, 70, 71, 103, 110, 121 | |
| 6 | 32, 65, 72, 104, 111, 122 | |
| 7 | 33, 66, 72, 73, 105, 112, 123 | |
| 6 | 34, 67, 73, 74, 113, 124 | |
| 6 | 35, 68, 74, 75, 114, 125 | |
| 6 | 36, 69, 75, 76, 115, 126 | |
| 7 | 37, 70, 76, 77, 109, 116, 127 | |
| 6 | 38, 64, 77, 78, 96, 117 | |
| 7 | 39, 65, 72, 78, 79, 97, 118 | |
| 8 | 40, 66, 73, 79, 80, 98, 105, 119 | |
| 7 | 41, 67, 74, 80, 81, 99, 120 | |
| 5 | 75, 81, 82, 100, 121 | |
| 8 | 43, 69, 76, 82, 83, 101, 115, 122 | |
| 6 | 44, 77, 83, 84, 102, 123 | |
| 6 | 45, 78, 84, 85, 103, 124 | |
| 5 | 79, 85, 86, 104, 125 | |
| 6 | 47, 80, 86, 87, 105, 126 | |
| 5 | 81, 87, 88, 106, 127 | |
| 5 | 82, 88, 89, 96, 107 | |
| 4 | 89, 90, 97, 108 | |
| 4 | 90, 91, 98, 109 | |
| 2 | 92, 99 | |
| 5 | 53, 92, 93, 100, 111 | |
| 2 | 94, 101 | |
| 6 | 55, 81, 94, 95, 102, 113 | |
| 6 | 56, 64, 82, 95, 103, 114 | |
| 6 | 57, 64, 65, 83, 104, 115 | |
| 7 | 58, 65, 66, 84, 98, 105, 116 | |
| 9 | 59, 66, 67, 85, 92, 99, 106, 117, 124 | |
| 7 | 60, 67, 68, 100, 107, 118, 125 | |
| 21 | 20, 31, 32, 59, 60, 66, 67, 68, 72, 86, 93, 99, 100, 101, 107, 108, 117, 118, 119, 125, 126 | |
| 22 | 0, 21, 33, 60, 61, 67, 68, 69, 73, 87, 94, 100, 101, 102, 108, 109, 118, 119, 120, 125, 126, 127 | |
| 21 | 1, 22, 34, 61, 62, 68, 69, 70, 74, 88, 95, 96, 102, 103, 108, 109, 110, 119, 120, 121, 127 | |
| 20 | 2, 35, 63, 64, 69, 70, 71, 75, 89, 96, 97, 103, 104, 109, 110, 111, 115, 120, 121, 122 | |
| 19 | 3, 32, 36, 63, 65, 70, 71, 72, 76, 90, 97, 98, 104, 105, 111, 112, 121, 122, 123 | |
| 20 | 4, 33, 37, 65, 66, 71, 72, 73, 77, 91, 98, 99, 105, 106, 111, 112, 113, 122, 123, 124 | |
| 21 | 5, 33, 34, 38, 59, 67, 72, 73, 74, 78, 92, 99, 100, 105, 106, 107, 113, 114, 123, 124, 125 | |
| 22 | 6, 27, 34, 35, 39, 60, 68, 73, 74, 75, 79, 86, 93, 100, 101, 107, 108, 114, 115, 124, 125, 126 | |
| 20 | 28, 35, 36, 40, 61, 69, 74, 75, 76, 80, 94, 101, 102, 108, 109, 115, 116, 125, 126, 127 | |
| 20 | 36, 37, 41, 62, 69, 70, 75, 76, 77, 95, 96, 102, 103, 109, 110, 115, 116, 117, 126, 127 | |
| 24 | 9, 30, 37, 38, 41, 42, 63, 64, 70, 71, 76, 77, 78, 82, 96, 97, 103, 104, 109, 110, 111, 117, 118, 127 | |
| 21 | 10, 32, 38, 39, 43, 65, 72, 77, 78, 79, 83, 96, 97, 98, 104, 105, 111, 112, 117, 118, 119 | |
| 25 | 0, 11, 33, 39, 40, 44, 65, 66, 73, 77, 78, 79, 80, 84, 97, 98, 99, 104, 105, 106, 112, 113, 119, 120, 124 | |
| 27 | 1, 12, 34, 40, 41, 45, 66, 67, 73, 74, 78, 79, 80, 81, 85, 92, 98, 99, 100, 105, 106, 107, 113, 114, 119, 120, 121 | |
| 23 | 2, 13, 35, 41, 42, 46, 67, 68, 74, 75, 80, 81, 82, 86, 99, 100, 101, 107, 108, 114, 115, 121, 122 | |
| 22 | 3, 14, 36, 43, 47, 69, 75, 76, 81, 82, 83, 100, 101, 102, 108, 109, 115, 116, 121, 122, 123, 127 | |
| 22 | 4, 15, 37, 43, 44, 48, 70, 76, 77, 82, 83, 84, 101, 102, 103, 109, 110, 116, 117, 122, 123, 124 | |
| 21 | 5, 16, 38, 44, 45, 49, 71, 77, 78, 83, 84, 85, 102, 103, 104, 111, 117, 118, 123, 124, 125 | |
| 22 | 6, 17, 39, 45, 46, 50, 72, 78, 79, 84, 85, 86, 103, 104, 105, 111, 112, 118, 119, 124, 125, 126 | |
| 20 | 18, 40, 47, 51, 73, 79, 80, 85, 86, 87, 104, 105, 106, 112, 113, 119, 120, 125, 126, 127 | |
| 22 | 19, 41, 48, 52, 74, 80, 81, 86, 87, 88, 92, 96, 100, 105, 106, 107, 113, 114, 120, 121, 126, 127 | |
| 18 | 9, 20, 49, 53, 75, 82, 87, 88, 89, 96, 97, 106, 107, 108, 114, 115, 121, 122 | |
| 21 | 10, 21, 50, 53, 54, 76, 82, 83, 88, 89, 90, 94, 97, 98, 107, 108, 109, 115, 116, 122, 123 | |
| 20 | 11, 22, 44, 51, 55, 77, 84, 89, 90, 91, 97, 98, 99, 108, 109, 110, 116, 117, 123, 124 | |
| 19 | 12, 23, 45, 52, 56, 78, 85, 90, 91, 92, 99, 100, 109, 110, 111, 117, 118, 124, 125 | |
| 17 | 13, 24, 53, 57, 79, 86, 91, 92, 93, 100, 101, 111, 112, 118, 119, 125, 126 | |
| 18 | 14, 54, 58, 80, 87, 92, 93, 94, 100, 101, 102, 111, 112, 113, 119, 120, 126, 127 | |
| 20 | 15, 26, 55, 59, 67, 80, 81, 88, 93, 94, 95, 96, 101, 102, 103, 113, 114, 120, 121, 127 | |
| 22 | 16, 27, 55, 56, 59, 60, 64, 82, 89, 94, 95, 96, 97, 102, 103, 104, 108, 113, 114, 115, 121, 122 | |
| 21 | 17, 28, 57, 61, 64, 65, 69, 83, 90, 95, 97, 98, 103, 104, 105, 109, 114, 115, 116, 122, 123 | |
| 20 | 18, 29, 58, 62, 64, 65, 66, 70, 84, 91, 98, 99, 104, 105, 106, 115, 116, 117, 123, 124 | |
| 23 | 19, 30, 58, 59, 63, 65, 66, 67, 85, 92, 98, 99, 100, 105, 106, 107, 111, 116, 117, 118, 123, 124, 125 | |
| 9 | 5, 44, 83, 84, 88, 117, 122, 123, 124 | |
| 10 | 6, 78, 84, 85, 89, 111, 118, 123, 124, 125 | |
| 9 | 7, 79, 85, 86, 90, 119, 124, 125, 126 | |
| 11 | 8, 80, 86, 87, 91, 99, 113, 120, 125, 126, 127 | |
| 10 | 9, 59, 88, 92, 96, 100, 114, 121, 126, 127 | |
| 9 | 10, 88, 89, 93, 96, 97, 115, 122, 127 | |
| 9 | 11, 61, 69, 90, 94, 97, 98, 116, 123 | |
| 9 | 12, 62, 91, 95, 97, 98, 99, 117, 124 | |
| 10 | 12, 13, 63, 64, 92, 98, 99, 100, 118, 125 | |
| 11 | 13, 14, 65, 92, 93, 99, 100, 101, 119, 125, 126 | |
| 12 | 14, 15, 33, 65, 66, 94, 100, 101, 102, 120, 126, 127 | |
| 12 | 15, 16, 66, 67, 74, 94, 95, 96, 101, 102, 103, 121 | |
| 11 | 16, 17, 64, 68, 95, 97, 102, 103, 104, 108, 122 | |
| 10 | 18, 64, 65, 69, 98, 103, 104, 105, 109, 123 | |
| 10 | 19, 65, 66, 69, 70, 99, 104, 105, 106, 124 | |
| 9 | 20, 66, 67, 71, 100, 105, 106, 107, 125 | |
| 8 | 21, 68, 72, 101, 106, 107, 108, 126 | |
| 8 | 22, 69, 73, 80, 102, 108, 109, 127 | |
| 9 | 23, 69, 70, 74, 96, 103, 108, 109, 110 | |
| 10 | 24, 71, 74, 75, 97, 104, 109, 110, 111, 115 | |
| 7 | 25, 72, 76, 98, 105, 111, 112 | |
| 10 | 26, 44, 73, 77, 99, 106, 111, 112, 113, 117 | |
| 9 | 27, 73, 74, 77, 78, 100, 107, 113, 114 | |
| 8 | 28, 74, 75, 79, 101, 108, 114, 115 | |
| 9 | 29, 75, 76, 80, 102, 109, 114, 115, 116 | |
| 11 | 30, 70, 76, 77, 80, 81, 103, 110, 115, 116, 117 | |
| 11 | 31, 38, 77, 78, 81, 82, 104, 111, 116, 117, 118 | |
| 10 | 0, 78, 79, 82, 83, 105, 112, 117, 118, 119 | |
| 13 | 1, 40, 73, 79, 80, 83, 84, 106, 113, 118, 119, 120, 124 | |
| 18 | 1, 2, 41, 52, 74, 79, 80, 81, 84, 85, 92, 100, 107, 114, 119, 120, 121, 125 | |
| 13 | 2, 3, 53, 75, 81, 82, 85, 86, 108, 115, 120, 121, 122 | |
| 6 | 36, 76, 87, 109, 115, 116 | |
| 3 | 37, 116, 120 | |
| 3 | 38, 117, 121 | |
| 4 | 39, 78, 118, 122 | |
| 4 | 40, 79, 119, 123 | |
| 4 | 41, 80, 120, 124 | |
| 3 | 42, 121, 125 | |
| 3 | 43, 122, 126 | |
| 3 | 44, 123, 127 | |
| 2 | 45, 124 | |
| 3 | 46, 97, 125 | |
| 3 | 47, 98, 126 | |
| 3 | 48, 99, 127 | |
| 3 | 49, 96, 100 | |
| 3 | 50, 97, 101 | |
| 3 | 51, 98, 102 | |
| 3 | 52, 99, 103 | |
| 3 | 53, 100, 104 | |
| 3 | 54, 101, 105 | |
| 3 | 55, 102, 106 | |
| 4 | 56, 74, 103, 107 | |
| 4 | 57, 75, 104, 108 | |
| 4 | 58, 76, 105, 109 | |
| 8 | 19, 59, 66, 77, 99, 105, 106, 110 | |
| 2 | 60, 107 | |
| 2 | 61, 108 | |
| 3 | 62, 109, 113 | |
| 3 | 63, 110, 114 | |
| 4 | 32, 82, 111, 115 | |
| 3 | 33, 112, 116 | |
| 4 | 34, 84, 113, 117 | |
| 6 | 35, 60, 74, 85, 114, 118 | |
| 0 | - | |
| 1 | 69 | |
| 2 | 70, 109 | |
| 1 | 71 | |
| 2 | 72, 122 | |
| 1 | 73 | |
| 1 | 74 | |
| 2 | 75, 125 | |
| 1 | 76 | |
| 3 | 76, 77, 127 | |
| 2 | 77, 78 | |
| 3 | 78, 79, 97 | |
| 3 | 79, 80, 98 | |
| 3 | 80, 81, 99 | |
| 3 | 81, 82, 100 | |
| 2 | 82, 83 | |
| 1 | 84 | |
| 1 | 85 | |
| 1 | 86 | |
| 2 | 87, 105 | |
| 1 | 88 | |
| 1 | 89 | |
| 1 | 90 | |
| 1 | 91 | |
| 1 | 92 | |
| 1 | 93 | |
| 1 | 94 | |
| 1 | 95 | |
| 2 | 64, 114 | |
| 3 | 65, 104, 115 | |
| 4 | 65, 66, 105, 116 | |
| 4 | 59, 66, 67, 117 | |
| 27 | 13, 19, 20, 24, 53, 58, 59, 60, 66, 67, 68, 78, 79, 86, 92, 93, 99, 100, 105, 106, 107, 109, 110, 111, 117, 118, 125 | |
| 16 | 32, 60, 66, 67, 68, 86, 93, 100, 101, 107, 108, 117, 118, 119, 125, 126 | |
| 15 | 33, 61, 67, 68, 69, 87, 94, 101, 102, 108, 109, 119, 120, 126, 127 | |
| 15 | 34, 62, 69, 70, 88, 95, 96, 102, 103, 109, 110, 119, 120, 121, 127 | |
| 16 | 35, 63, 64, 69, 70, 71, 89, 96, 97, 103, 104, 110, 111, 120, 121, 122 | |
| 16 | 32, 36, 65, 70, 71, 72, 90, 97, 98, 104, 105, 111, 112, 121, 122, 123 | |
| 16 | 4, 33, 37, 66, 72, 73, 91, 98, 99, 105, 106, 112, 113, 122, 123, 124 | |
| 15 | 34, 38, 67, 73, 74, 92, 99, 100, 106, 107, 113, 114, 123, 124, 125 | |
| 15 | 35, 39, 68, 73, 74, 75, 93, 100, 101, 108, 114, 115, 124, 125, 126 | |
| 16 | 36, 40, 69, 74, 75, 76, 94, 101, 102, 108, 109, 115, 116, 125, 126, 127 | |
| 16 | 37, 41, 70, 75, 76, 77, 95, 96, 102, 103, 109, 110, 116, 117, 126, 127 | |
| 15 | 38, 42, 64, 71, 76, 77, 78, 96, 97, 103, 104, 111, 117, 118, 127 | |
| 17 | 10, 39, 43, 65, 72, 77, 78, 79, 96, 97, 98, 104, 105, 111, 112, 118, 119 | |
| 17 | 11, 40, 44, 66, 73, 78, 79, 80, 97, 98, 99, 105, 106, 112, 113, 119, 120 | |
| 17 | 12, 41, 45, 67, 74, 79, 80, 81, 98, 99, 100, 106, 107, 113, 114, 120, 121 | |
| 16 | 13, 42, 46, 68, 75, 80, 81, 82, 99, 100, 101, 108, 114, 115, 121, 122 | |
| 16 | 43, 47, 69, 76, 81, 82, 83, 100, 101, 102, 108, 109, 115, 116, 122, 123 | |
| 14 | 44, 70, 77, 82, 83, 84, 102, 103, 109, 110, 116, 117, 123, 124 | |
| 13 | 45, 49, 78, 83, 84, 85, 103, 104, 111, 117, 118, 124, 125 | |
| 15 | 46, 50, 72, 79, 84, 85, 86, 103, 104, 105, 112, 118, 119, 125, 126 | |
| 16 | 18, 47, 51, 73, 80, 85, 86, 87, 104, 105, 106, 113, 119, 120, 126, 127 | |
| 16 | 19, 48, 52, 74, 81, 86, 87, 88, 96, 105, 106, 107, 114, 120, 121, 127 | |
| 15 | 20, 49, 53, 75, 82, 87, 88, 89, 96, 97, 107, 108, 115, 121, 122 | |
| 16 | 21, 50, 54, 76, 83, 88, 89, 90, 97, 98, 108, 109, 115, 116, 122, 123 | |
| 17 | 22, 51, 55, 77, 84, 89, 90, 91, 98, 99, 108, 109, 110, 116, 117, 123, 124 | |
| 14 | 52, 78, 85, 91, 92, 99, 100, 109, 110, 111, 117, 118, 124, 125 | |
| 14 | 53, 57, 79, 86, 92, 93, 100, 101, 111, 112, 118, 119, 125, 126 | |
| 15 | 54, 58, 80, 87, 92, 93, 94, 101, 102, 112, 113, 119, 120, 126, 127 | |
| 16 | 15, 55, 59, 81, 88, 93, 94, 95, 96, 102, 103, 113, 114, 120, 121, 127 | |
| 16 | 16, 56, 60, 64, 82, 89, 94, 95, 96, 97, 103, 104, 114, 115, 121, 122 | |
| 15 | 57, 61, 64, 65, 83, 90, 95, 97, 98, 104, 105, 115, 116, 122, 123 | |
| 20 | 18, 29, 58, 62, 64, 65, 66, 70, 84, 91, 98, 99, 104, 105, 106, 115, 116, 117, 123, 124 |

Table A3.
Strong unbalanced bits for 32-round CHAM-128/256 with a threshold of .
Table A3.
Strong unbalanced bits for 32-round CHAM-128/256 with a threshold of .
| Input Difference | # | Strong Unbalanced Bits |
|---|---|---|
| 17 | 4, 5, 44, 55, 77, 83, 84, 87, 88, 95, 96, 109, 110, 117, 122, 123, 124 | |
| 17 | 5, 6, 45, 56, 64, 78, 84, 85, 88, 89, 97, 111, 117, 118, 123, 124, 125 | |
| 19 | 6, 7, 39, 46, 57, 65, 79, 85, 86, 89, 90, 98, 105, 112, 118, 119, 124, 125, 126 | |
| 18 | 1, 8, 40, 47, 58, 66, 80, 86, 87, 90, 91, 99, 113, 119, 120, 125, 126, 127 | |
| 20 | 2, 8, 9, 41, 48, 59, 67, 74, 81, 87, 88, 91, 92, 96, 100, 114, 120, 121, 126, 127 | |
| 19 | 3, 9, 10, 49, 60, 68, 82, 88, 89, 92, 93, 96, 97, 101, 108, 115, 121, 122, 127 | |
| 19 | 4, 10, 11, 61, 69, 76, 83, 89, 90, 93, 94, 96, 97, 98, 102, 109, 116, 122, 123 | |
| 19 | 5, 11, 12, 51, 62, 70, 77, 84, 90, 91, 94, 95, 97, 98, 99, 103, 117, 123, 124 | |
| 19 | 6, 12, 13, 52, 63, 64, 71, 78, 85, 91, 92, 95, 98, 99, 100, 104, 118, 124, 125 | |
| 19 | 0, 13, 14, 32, 53, 64, 65, 72, 79, 86, 92, 93, 99, 100, 101, 105, 119, 125, 126 | |
| 20 | 1, 8, 14, 15, 33, 54, 65, 66, 73, 80, 87, 93, 94, 100, 101, 102, 106, 120, 126, 127 | |
| 22 | 2, 9, 15, 16, 34, 55, 66, 67, 74, 81, 88, 94, 95, 96, 100, 101, 102, 103, 107, 114, 121, 127 | |
| 23 | 3, 10, 16, 17, 35, 56, 64, 67, 68, 75, 82, 89, 95, 96, 97, 101, 102, 103, 104, 108, 115, 121, 122 | |
| 21 | 4, 11, 17, 18, 36, 57, 64, 65, 68, 69, 76, 83, 90, 97, 98, 103, 104, 105, 109, 122, 123 | |
| 21 | 5, 12, 18, 19, 37, 58, 65, 66, 69, 70, 77, 84, 91, 98, 99, 104, 105, 106, 117, 123, 124 | |
| 19 | 13, 19, 20, 38, 59, 66, 67, 70, 71, 78, 92, 99, 100, 105, 106, 107, 111, 124, 125 | |
| 16 | 14, 20, 21, 39, 60, 67, 68, 72, 79, 100, 101, 106, 107, 108, 125, 126 | |
| 19 | 15, 21, 22, 40, 61, 68, 69, 72, 73, 80, 94, 101, 102, 107, 108, 109, 113, 126, 127 | |
| 19 | 16, 22, 23, 41, 62, 69, 70, 73, 74, 81, 95, 96, 102, 103, 108, 109, 110, 114, 127 | |
| 21 | 17, 23, 24, 42, 63, 64, 70, 71, 74, 75, 82, 96, 97, 103, 104, 108, 109, 110, 111, 115, 122 | |
| 20 | 18, 24, 25, 32, 43, 65, 71, 72, 75, 76, 83, 97, 98, 104, 105, 109, 110, 111, 112, 116 | |
| 19 | 19, 26, 33, 44, 66, 72, 73, 76, 77, 84, 98, 99, 105, 106, 111, 112, 113, 117, 124 | |
| 20 | 26, 27, 34, 45, 67, 73, 74, 77, 78, 85, 92, 99, 100, 106, 107, 112, 113, 114, 118, 125 | |
| 13 | 28, 35, 68, 74, 75, 78, 79, 86, 101, 108, 113, 114, 115 | |
| 19 | 28, 29, 36, 47, 69, 75, 76, 79, 80, 87, 94, 101, 102, 108, 109, 114, 115, 116, 127 | |
| 17 | 29, 30, 37, 70, 76, 77, 80, 81, 88, 102, 103, 109, 110, 115, 116, 117, 121 | |
| 23 | 17, 30, 31, 38, 49, 64, 71, 76, 77, 78, 80, 81, 82, 89, 97, 103, 104, 111, 115, 116, 117, 118, 122 | |
| 22 | 0, 18, 31, 39, 50, 65, 72, 77, 78, 79, 82, 83, 90, 98, 104, 105, 111, 112, 117, 118, 119, 123 | |
| 21 | 0, 1, 19, 40, 51, 66, 73, 78, 79, 80, 83, 84, 91, 99, 105, 106, 113, 118, 119, 120, 124 | |
| 23 | 1, 2, 20, 41, 52, 59, 67, 74, 79, 80, 81, 84, 85, 92, 100, 106, 107, 113, 114, 119, 120, 121, 125 | |
| 25 | 2, 3, 21, 28, 35, 42, 53, 60, 68, 75, 80, 81, 82, 85, 86, 93, 101, 108, 114, 115, 119, 120, 121, 122, 126 | |
| 21 | 3, 4, 36, 43, 54, 61, 69, 76, 82, 83, 86, 87, 94, 108, 109, 115, 116, 121, 122, 123, 127 | |
| 10 | 36, 37, 62, 69, 76, 87, 109, 115, 116, 120 | |
| 9 | 30, 37, 38, 63, 77, 88, 117, 121, 122 | |
| 11 | 31, 32, 38, 39, 57, 78, 89, 111, 117, 118, 122 | |
| 10 | 0, 33, 39, 40, 58, 79, 90, 118, 119, 123 | |
| 11 | 1, 34, 40, 41, 59, 80, 91, 113, 119, 120, 124 | |
| 12 | 2, 35, 41, 42, 60, 81, 92, 100, 114, 120, 121, 125 | |
| 12 | 3, 36, 43, 61, 82, 93, 115, 121, 122, 125, 126, 127 | |
| 10 | 4, 37, 43, 44, 62, 83, 94, 122, 123, 127 | |
| 10 | 5, 38, 44, 45, 63, 84, 95, 96, 123, 124 | |
| 11 | 6, 32, 39, 45, 46, 64, 85, 97, 98, 124, 125 | |
| 10 | 33, 40, 47, 65, 86, 98, 99, 119, 125, 126 | |
| 13 | 34, 41, 47, 48, 66, 80, 87, 98, 99, 100, 120, 126, 127 | |
| 10 | 9, 35, 49, 67, 88, 96, 99, 100, 121, 127 | |
| 11 | 10, 36, 43, 50, 68, 89, 96, 97, 100, 101, 122 | |
| 12 | 11, 37, 44, 51, 69, 90, 97, 98, 102, 103, 109, 123 | |
| 10 | 12, 38, 45, 52, 70, 91, 98, 99, 103, 124 | |
| 9 | 13, 39, 53, 92, 99, 100, 104, 105, 125 | |
| 9 | 14, 40, 53, 54, 72, 100, 101, 105, 126 | |
| 10 | 15, 41, 55, 73, 94, 101, 102, 105, 106, 127 | |
| 9 | 16, 55, 56, 74, 95, 96, 102, 103, 107 | |
| 10 | 17, 43, 57, 64, 75, 97, 103, 104, 108, 115 | |
| 11 | 18, 44, 57, 58, 65, 76, 98, 104, 105, 108, 109 | |
| 10 | 19, 45, 59, 66, 77, 99, 105, 106, 109, 110 | |
| 10 | 20, 53, 59, 60, 67, 78, 100, 106, 107, 111 | |
| 6 | 21, 61, 79, 101, 108, 112 | |
| 9 | 22, 61, 62, 69, 80, 102, 108, 109, 113 | |
| 9 | 62, 63, 70, 81, 103, 109, 110, 114, 115 | |
| 7 | 24, 32, 63, 82, 104, 111, 115 | |
| 10 | 33, 58, 72, 83, 105, 111, 112, 115, 116, 117 | |
| 8 | 33, 34, 59, 73, 84, 106, 113, 117 | |
| 8 | 35, 53, 60, 74, 85, 114, 118, 119 | |
| 12 | 28, 35, 36, 54, 61, 75, 86, 108, 114, 115, 119, 126 | |
| 5 | 61, 68, 69, 108, 119 | |
| 5 | 62, 69, 70, 109, 120 | |
| 7 | 63, 64, 70, 71, 103, 110, 121 | |
| 6 | 32, 65, 72, 104, 111, 122 | |
| 7 | 33, 66, 72, 73, 105, 112, 123 | |
| 6 | 34, 67, 73, 74, 113, 124 | |
| 6 | 35, 68, 74, 75, 114, 125 | |
| 6 | 36, 69, 75, 76, 115, 126 | |
| 7 | 37, 70, 76, 77, 109, 116, 127 | |
| 6 | 38, 64, 77, 78, 96, 117 | |
| 7 | 39, 65, 72, 78, 79, 97, 118 | |
| 7 | 40, 66, 73, 79, 80, 98, 119 | |
| 7 | 41, 67, 74, 80, 81, 99, 120 | |
| 5 | 75, 81, 82, 100, 121 | |
| 8 | 43, 69, 76, 82, 83, 101, 115, 122 | |
| 6 | 44, 77, 83, 84, 102, 123 | |
| 6 | 45, 78, 84, 85, 103, 124 | |
| 5 | 79, 85, 86, 104, 125 | |
| 6 | 47, 80, 86, 87, 105, 126 | |
| 5 | 81, 87, 88, 106, 127 | |
| 5 | 82, 88, 89, 96, 107 | |
| 4 | 89, 90, 97, 108 | |
| 4 | 90, 91, 98, 109 | |
| 2 | 92, 99 | |
| 5 | 53, 92, 93, 100, 111 | |
| 2 | 94, 101 | |
| 6 | 55, 81, 94, 95, 102, 113 | |
| 6 | 56, 64, 82, 95, 103, 114 | |
| 6 | 57, 64, 65, 83, 104, 115 | |
| 7 | 58, 65, 66, 84, 98, 105, 116 | |
| 9 | 59, 66, 67, 85, 92, 99, 106, 117, 124 | |
| 7 | 60, 67, 68, 100, 107, 118, 125 | |
| 21 | 20, 31, 32, 59, 60, 66, 67, 68, 72, 86, 93, 99, 100, 101, 107, 108, 117, 118, 119, 125, 126 | |
| 21 | 0, 21, 33, 61, 67, 68, 69, 73, 87, 94, 100, 101, 102, 108, 109, 118, 119, 120, 125, 126, 127 | |
| 21 | 1, 22, 34, 61, 62, 68, 69, 70, 74, 88, 95, 96, 102, 103, 108, 109, 110, 119, 120, 121, 127 | |
| 20 | 2, 35, 63, 64, 69, 70, 71, 75, 89, 96, 97, 103, 104, 109, 110, 111, 115, 120, 121, 122 | |
| 19 | 3, 32, 36, 63, 65, 70, 71, 72, 76, 90, 97, 98, 104, 105, 111, 112, 121, 122, 123 | |
| 19 | 4, 33, 37, 65, 66, 71, 72, 73, 77, 91, 98, 99, 105, 106, 112, 113, 122, 123, 124 | |
| 20 | 5, 33, 34, 38, 59, 67, 72, 73, 74, 78, 92, 99, 100, 106, 107, 113, 114, 123, 124, 125 | |
| 22 | 6, 27, 34, 35, 39, 60, 68, 73, 74, 75, 79, 86, 93, 100, 101, 107, 108, 114, 115, 124, 125, 126 | |
| 20 | 28, 35, 36, 40, 61, 69, 74, 75, 76, 80, 94, 101, 102, 108, 109, 115, 116, 125, 126, 127 | |
| 20 | 36, 37, 41, 62, 69, 70, 75, 76, 77, 95, 96, 102, 103, 109, 110, 115, 116, 117, 126, 127 | |
| 24 | 9, 30, 37, 38, 41, 42, 63, 64, 70, 71, 76, 77, 78, 82, 96, 97, 103, 104, 109, 110, 111, 117, 118, 127 | |
| 21 | 10, 32, 38, 39, 43, 65, 72, 77, 78, 79, 83, 96, 97, 98, 104, 105, 111, 112, 117, 118, 119 | |
| 24 | 0, 11, 33, 39, 40, 44, 65, 66, 73, 77, 78, 79, 80, 84, 97, 98, 99, 105, 106, 112, 113, 119, 120, 124 | |
| 27 | 1, 12, 34, 40, 41, 45, 66, 67, 73, 74, 78, 79, 80, 81, 85, 92, 98, 99, 100, 105, 106, 107, 113, 114, 119, 120, 121 | |
| 23 | 2, 13, 35, 41, 42, 46, 67, 68, 74, 75, 80, 81, 82, 86, 99, 100, 101, 107, 108, 114, 115, 121, 122 | |
| 22 | 3, 14, 36, 43, 47, 69, 75, 76, 81, 82, 83, 100, 101, 102, 108, 109, 115, 116, 121, 122, 123, 127 | |
| 22 | 4, 15, 37, 43, 44, 48, 70, 76, 77, 82, 83, 84, 101, 102, 103, 109, 110, 116, 117, 122, 123, 124 | |
| 21 | 5, 16, 38, 44, 45, 49, 71, 77, 78, 83, 84, 85, 102, 103, 104, 111, 117, 118, 123, 124, 125 | |
| 22 | 6, 17, 39, 45, 46, 50, 72, 78, 79, 84, 85, 86, 103, 104, 105, 111, 112, 118, 119, 124, 125, 126 | |
| 20 | 18, 40, 47, 51, 73, 79, 80, 85, 86, 87, 104, 105, 106, 112, 113, 119, 120, 125, 126, 127 | |
| 22 | 19, 41, 48, 52, 74, 80, 81, 86, 87, 88, 92, 96, 100, 105, 106, 107, 113, 114, 120, 121, 126, 127 | |
| 17 | 20, 49, 53, 75, 82, 87, 88, 89, 96, 97, 106, 107, 108, 114, 115, 121, 122 | |
| 21 | 10, 21, 50, 53, 54, 76, 82, 83, 88, 89, 90, 94, 97, 98, 107, 108, 109, 115, 116, 122, 123 | |
| 21 | 11, 22, 44, 51, 55, 77, 84, 89, 90, 91, 97, 98, 99, 103, 108, 109, 110, 116, 117, 123, 124 | |
| 18 | 12, 23, 52, 56, 78, 85, 90, 91, 92, 99, 100, 109, 110, 111, 117, 118, 124, 125 | |
| 18 | 13, 24, 53, 57, 79, 86, 91, 92, 93, 99, 100, 101, 111, 112, 118, 119, 125, 126 | |
| 18 | 14, 54, 58, 80, 87, 92, 93, 94, 100, 101, 102, 111, 112, 113, 119, 120, 126, 127 | |
| 20 | 15, 26, 55, 59, 67, 80, 81, 88, 93, 94, 95, 96, 101, 102, 103, 113, 114, 120, 121, 127 | |
| 22 | 16, 27, 55, 56, 59, 60, 64, 82, 89, 94, 95, 96, 97, 102, 103, 104, 108, 113, 114, 115, 121, 122 | |
| 21 | 17, 28, 57, 61, 64, 65, 69, 83, 90, 95, 97, 98, 103, 104, 105, 109, 114, 115, 116, 122, 123 | |
| 20 | 18, 29, 58, 62, 64, 65, 66, 70, 84, 91, 98, 99, 104, 105, 106, 115, 116, 117, 123, 124 | |
| 23 | 19, 30, 58, 59, 63, 65, 66, 67, 85, 92, 98, 99, 100, 105, 106, 107, 111, 116, 117, 118, 123, 124, 125 | |
| 9 | 5, 44, 83, 84, 88, 117, 122, 123, 124 | |
| 10 | 6, 78, 84, 85, 89, 111, 118, 123, 124, 125 | |
| 9 | 7, 79, 85, 86, 90, 119, 124, 125, 126 | |
| 11 | 8, 80, 86, 87, 91, 99, 113, 120, 125, 126, 127 | |
| 10 | 9, 59, 88, 92, 96, 100, 114, 121, 126, 127 | |
| 9 | 10, 88, 89, 93, 96, 97, 115, 122, 127 | |
| 9 | 11, 61, 69, 90, 94, 97, 98, 116, 123 | |
| 9 | 12, 62, 91, 95, 97, 98, 99, 117, 124 | |
| 10 | 12, 13, 63, 64, 92, 98, 99, 100, 118, 125 | |
| 11 | 13, 14, 65, 92, 93, 99, 100, 101, 119, 125, 126 | |
| 12 | 14, 15, 33, 65, 66, 94, 100, 101, 102, 120, 126, 127 | |
| 12 | 15, 16, 66, 67, 74, 94, 95, 96, 101, 102, 103, 121 | |
| 11 | 16, 17, 64, 68, 95, 97, 102, 103, 104, 108, 122 | |
| 10 | 18, 64, 65, 69, 98, 103, 104, 105, 109, 123 | |
| 10 | 19, 65, 66, 69, 70, 99, 104, 105, 106, 124 | |
| 9 | 20, 66, 67, 71, 100, 105, 106, 107, 125 | |
| 8 | 21, 68, 72, 101, 106, 107, 108, 126 | |
| 9 | 21, 22, 69, 73, 80, 102, 108, 109, 127 | |
| 9 | 23, 69, 70, 74, 96, 103, 108, 109, 110 | |
| 10 | 24, 71, 74, 75, 97, 104, 109, 110, 111, 115 | |
| 7 | 25, 72, 76, 98, 105, 111, 112 | |
| 9 | 26, 73, 77, 99, 106, 111, 112, 113, 117 | |
| 9 | 27, 73, 74, 77, 78, 100, 107, 113, 114 | |
| 8 | 28, 74, 75, 79, 101, 108, 114, 115 | |
| 9 | 29, 75, 76, 80, 102, 109, 114, 115, 116 | |
| 11 | 30, 70, 76, 77, 80, 81, 103, 110, 115, 116, 117 | |
| 11 | 31, 38, 77, 78, 81, 82, 104, 111, 116, 117, 118 | |
| 10 | 0, 78, 79, 82, 83, 105, 112, 117, 118, 119 | |
| 13 | 1, 40, 73, 79, 80, 83, 84, 106, 113, 118, 119, 120, 124 | |
| 18 | 1, 2, 41, 52, 74, 79, 80, 81, 84, 85, 92, 100, 107, 114, 119, 120, 121, 125 | |
| 13 | 2, 3, 53, 75, 81, 82, 85, 86, 108, 115, 120, 121, 122 | |
| 6 | 36, 76, 87, 109, 115, 116 | |
| 4 | 37, 87, 116, 120 | |
| 3 | 38, 117, 121 | |
| 4 | 39, 78, 118, 122 | |
| 4 | 40, 79, 119, 123 | |
| 4 | 41, 80, 120, 124 | |
| 3 | 42, 121, 125 | |
| 3 | 43, 122, 126 | |
| 3 | 44, 123, 127 | |
| 2 | 45, 124 | |
| 3 | 46, 97, 125 | |
| 3 | 47, 98, 126 | |
| 3 | 48, 99, 127 | |
| 3 | 49, 96, 100 | |
| 3 | 50, 97, 101 | |
| 3 | 51, 98, 102 | |
| 3 | 52, 99, 103 | |
| 3 | 53, 100, 104 | |
| 3 | 54, 101, 105 | |
| 3 | 55, 102, 106 | |
| 4 | 56, 74, 103, 107 | |
| 4 | 57, 75, 104, 108 | |
| 4 | 58, 76, 105, 109 | |
| 8 | 19, 59, 66, 77, 99, 105, 106, 110 | |
| 2 | 60, 107 | |
| 2 | 61, 108 | |
| 3 | 62, 109, 113 | |
| 3 | 63, 110, 114 | |
| 4 | 32, 82, 111, 115 | |
| 3 | 33, 112, 116 | |
| 4 | 34, 84, 113, 117 | |
| 6 | 35, 60, 74, 85, 114, 118 | |
| 0 | - | |
| 1 | 69 | |
| 2 | 70, 109 | |
| 1 | 71 | |
| 2 | 72, 122 | |
| 1 | 73 | |
| 1 | 74 | |
| 2 | 75, 125 | |
| 2 | 76, 126 | |
| 3 | 76, 77, 127 | |
| 2 | 77, 78 | |
| 3 | 78, 79, 97 | |
| 3 | 79, 80, 98 | |
| 3 | 80, 81, 99 | |
| 3 | 81, 82, 100 | |
| 1 | 83 | |
| 1 | 84 | |
| 1 | 85 | |
| 1 | 86 | |
| 2 | 87, 105 | |
| 1 | 88 | |
| 1 | 89 | |
| 1 | 90 | |
| 1 | 91 | |
| 1 | 92 | |
| 1 | 93 | |
| 1 | 94 | |
| 1 | 95 | |
| 2 | 64, 114 | |
| 3 | 65, 104, 115 | |
| 4 | 65, 66, 105, 116 | |
| 4 | 59, 66, 67, 117 | |
| 27 | 13, 19, 20, 24, 53, 58, 59, 60, 66, 67, 68, 78, 79, 86, 92, 93, 99, 100, 105, 106, 107, 109, 110, 111, 117, 118, 125 | |
| 16 | 32, 60, 66, 67, 68, 86, 93, 100, 101, 107, 108, 117, 118, 119, 125, 126 | |
| 15 | 33, 61, 67, 68, 69, 94, 101, 102, 108, 109, 118, 119, 120, 126, 127 | |
| 15 | 34, 62, 69, 70, 88, 95, 96, 102, 103, 109, 110, 119, 120, 121, 127 | |
| 16 | 35, 63, 64, 69, 70, 71, 89, 96, 97, 103, 104, 110, 111, 120, 121, 122 | |
| 16 | 32, 36, 65, 70, 71, 72, 90, 97, 98, 104, 105, 111, 112, 121, 122, 123 | |
| 16 | 4, 33, 37, 66, 72, 73, 91, 98, 99, 105, 106, 112, 113, 122, 123, 124 | |
| 15 | 34, 38, 67, 73, 74, 92, 99, 100, 106, 107, 113, 114, 123, 124, 125 | |
| 15 | 35, 39, 68, 73, 74, 75, 93, 100, 101, 108, 114, 115, 124, 125, 126 | |
| 16 | 36, 40, 69, 74, 75, 76, 94, 101, 102, 108, 109, 115, 116, 125, 126, 127 | |
| 16 | 37, 41, 70, 75, 76, 77, 95, 96, 102, 103, 109, 110, 116, 117, 126, 127 | |
| 15 | 38, 42, 64, 71, 76, 77, 78, 96, 97, 103, 104, 111, 117, 118, 127 | |
| 17 | 10, 39, 43, 65, 72, 77, 78, 79, 96, 97, 98, 104, 105, 111, 112, 118, 119 | |
| 17 | 11, 40, 44, 66, 73, 78, 79, 80, 97, 98, 99, 105, 106, 112, 113, 119, 120 | |
| 17 | 12, 41, 45, 67, 74, 79, 80, 81, 98, 99, 100, 106, 107, 113, 114, 120, 121 | |
| 16 | 13, 42, 46, 68, 75, 80, 81, 82, 99, 100, 101, 108, 114, 115, 121, 122 | |
| 16 | 43, 47, 69, 76, 81, 82, 83, 100, 101, 102, 108, 109, 115, 116, 122, 123 | |
| 14 | 44, 70, 77, 82, 83, 84, 102, 103, 109, 110, 116, 117, 123, 124 | |
| 13 | 45, 49, 78, 83, 84, 85, 103, 104, 111, 117, 118, 124, 125 | |
| 15 | 46, 50, 72, 79, 84, 85, 86, 103, 104, 105, 112, 118, 119, 125, 126 | |
| 16 | 18, 47, 51, 73, 80, 85, 86, 87, 104, 105, 106, 113, 119, 120, 126, 127 | |
| 16 | 19, 48, 52, 74, 81, 86, 87, 88, 96, 105, 106, 107, 114, 120, 121, 127 | |
| 14 | 20, 49, 53, 75, 82, 88, 89, 96, 97, 107, 108, 115, 121, 122 | |
| 16 | 21, 50, 54, 76, 83, 88, 89, 90, 97, 98, 108, 109, 115, 116, 122, 123 | |
| 17 | 22, 51, 55, 77, 84, 89, 90, 91, 98, 99, 108, 109, 110, 116, 117, 123, 124 | |
| 14 | 52, 78, 85, 91, 92, 99, 100, 109, 110, 111, 117, 118, 124, 125 | |
| 14 | 53, 57, 79, 86, 92, 93, 100, 101, 111, 112, 118, 119, 125, 126 | |
| 15 | 54, 58, 80, 87, 92, 93, 94, 101, 102, 112, 113, 119, 120, 126, 127 | |
| 16 | 15, 55, 59, 81, 88, 93, 94, 95, 96, 102, 103, 113, 114, 120, 121, 127 | |
| 15 | 56, 60, 64, 82, 89, 94, 95, 96, 97, 103, 104, 114, 115, 121, 122 | |
| 15 | 57, 61, 64, 65, 83, 90, 95, 97, 98, 104, 105, 115, 116, 122, 123 | |
| 20 | 18, 29, 58, 62, 64, 65, 66, 70, 84, 91, 98, 99, 104, 105, 106, 115, 116, 117, 123, 124 |
References
- Koo, B.; Roh, D.; Kim, H.; Jung, Y.; Lee, D.G.; Kwon, D. CHAM: A family of lightweight block ciphers for resource-constrained devices. In Proceedings of the Information Security and Cryptology–ICISC 2017: 20th International Conference, Seoul, Republic of Korea, 29 November–1 December 2017; Revised Selected Papers 20. Springer: Cham, Switzerland, 2018; pp. 3–25. [Google Scholar]
- Roh, D.; Koo, B.; Jung, Y.; Jeong, I.W.; Lee, D.G.; Kwon, D.; Kim, W.H. Revised version of block cipher CHAM. In Proceedings of the Information Security and Cryptology–ICISC 2019: 22nd International Conference, Seoul, Republic of Korea, 4–6 December 2019; Revised Selected Papers 22. Springer: Cham, Switzerland, 2020; pp. 1–19. [Google Scholar]
- Huang, M.; Wang, L. Automatic Tool for Searching for Differential Characteristics in ARX Ciphers and Applications. In Progress in Cryptology—INDOCRYPT 2019; Hao, F., Ruj, S., Sen Gupta, S., Eds.; Springer: Cham, Switzerland, 2019; pp. 115–138. [Google Scholar]
- Roh, D. Validity of Differential Characteristics of ARX Block Ciphers. IEEE Access 2023, 11, 100672–100682. [Google Scholar] [CrossRef]
- Huang, M.; Wang, L. Automatic search for the linear (hull) characteristics of ARX ciphers: Applied to SPECK, SPARX, CHASKEY, and CHAM-64. Secur. Commun. Netw. 2020, 2020, 4898612. [Google Scholar] [CrossRef]
- Li, J.; Qiu, X.; Li, L.; Zhu, C.; Wu, X. New Integral distinguishers for I-Present™, TANGRAM and CHAM. In Proceedings of the 2022 7th IEEE International Conference on Data Science in Cyberspace (DSC), Guilin, China, 11–13 July 2022; pp. 548–555. [Google Scholar]
- Biryukov, A.; Teh, J.S.; Udovenko, A. Advancing the Meet-in-the-Filter Technique: Applications to CHAM and KATAN. In International Conference on Selected Areas in Cryptography; Springer: Cham, Switzerland, 2023. [Google Scholar]
- Zhang, K.; Lai, X.; Wang, L.; Guan, J.; Hu, B.; Wang, S.; Shi, T. Meet-in-the-middle attack with splice-and-cut technique and a general automatic framework. Des. Codes Cryptogr. 2023, 91, 2845–2878. [Google Scholar] [CrossRef]
- Ling, Q.; Cui, T.; Hu, H.; Gong, S.; He, Z.; Huang, J.; Xiao, J. Finding Impossible Differentials in ARX Ciphers under Weak Keys. IACR Trans. Symmetric Cryptol. 2024, 2024, 326–356. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Matsui, M. Linear Cryptanalysis Method for DES Cipher. In Advances in Cryptology—EUROCRYPT ’93; Helleseth, T., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; pp. 386–397. [Google Scholar]
- Biham, E.; Shamir, A. Differential Cryptanalysis of Feal and N-Hash. In Advances in Cryptology—EUROCRYPT ’91. EUROCRYPT 1991; Davies, D.W., Ed.; Springer: Berlin/Heidelberg, Germany, 1991; pp. 1–16. [Google Scholar]
- Etrog, J.; Robshaw, M.J.B. The Cryptanalysis of Reduced-Round SMS4. In Selected Areas in Cryptography, SAC 2008; Avanzi, R.M., Keliher, L., Sica, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 51–65. [Google Scholar]
- Song, L.; Huang, Z.; Yang, Q. Automatic Differential Analysis of ARX Block Ciphers with Application to SPECK and LEA. In Information Security and Privacy; Liu, J.K., Steinfeld, R., Eds.; Springer: Cham, Switzerland, 2016; pp. 379–394. [Google Scholar]
- Flórez-Gutiérrez, A.; Naya-Plasencia, M. Improving Key-Recovery in Linear Attacks: Application to 28-Round PRESENT. In Advances in Cryptology—EUROCRYPT 2020; Canteaut, A., Ishai, Y., Eds.; Springer: Cham, Switzerland, 2020; pp. 221–249. [Google Scholar]
- Mouha, N.; Wang, Q.; Gu, D.; Preneel, B. Differential and Linear Cryptanalysis Using Mixed-Integer Linear Programming. In Information Security and Cryptology; Wu, C.K., Yung, M., Lin, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 57–76. [Google Scholar]
- Mouha, N.; Preneel, B. Towards finding optimal differential characteristics for ARX: Application to Salsa20. Cryptol. Eprint Arch. 2013, 2013/328. [Google Scholar]
- Sun, S.; Hu, L.; Wang, P.; Qiao, K.; Ma, X.; Song, L. Automatic Security Evaluation and (Related-key) Differential Characteristic Search: Application to SIMON, PRESENT, LBlock, DES(L) and Other Bit-Oriented Block Ciphers. In Advances in Cryptology—ASIACRYPT 2014; Sarkar, P., Iwata, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; pp. 158–178. [Google Scholar]
- Liu, Y.; Wang, Q.; Rijmen, V. Automatic Search of Linear Trails in ARX with Applications to SPECK and Chaskey. In Applied Cryptography and Network Security; Manulis, M., Sadeghi, A.R., Schneider, S., Eds.; Springer: Cham, Switzerland, 2016; pp. 485–499. [Google Scholar]
- Sun, L.; Wang, W.; Wang, M. Accelerating the search of differential and linear characteristics with the SAT method. IACR Trans. Symmetric Cryptol. 2021, 2021, 269–315. [Google Scholar] [CrossRef]
- Langford, S.K.; Hellman, M.E. Differential-Linear Cryptanalysis. In Advances in Cryptology—CRYPTO ’94; Desmedt, Y.G., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; pp. 17–25. [Google Scholar]
- Hawkes, P. Differential-linear weak key classes of IDEA. In Advances in Cryptology—EUROCRYPT’98; Nyberg, K., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; pp. 112–126. [Google Scholar]
- Biham, E.; Dunkelman, O.; Keller, N. Enhancing Differential-Linear Cryptanalysis. In Advances in Cryptology—ASIACRYPT 2002; Zheng, Y., Ed.; Springer: Berlin/Heidelberg, Germany, 2002; pp. 254–266. [Google Scholar]
- Dunkelman, O.; Indesteege, S.; Keller, N. A Differential-Linear Attack on 12-Round Serpent. In Progress in Cryptology—INDOCRYPT 2008; Chowdhury, D.R., Rijmen, V., Das, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 308–321. [Google Scholar]
- Lu, J. A methodology for differential-linear cryptanalysis and its applications. Des. Codes Cryptogr. 2015, 77, 11–48. [Google Scholar] [CrossRef]
- Huang, T.; Tjuawinata, I.; Wu, H. Differential-Linear Cryptanalysis of ICEPOLE. In Fast Software Encryption; Leander, G., Ed.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 243–263. [Google Scholar]
- Bar-On, A.; Dunkelman, O.; Keller, N.; Weizman, A. DLCT: A New Tool for Differential-Linear Cryptanalysis. In Advances in Cryptology—EUROCRYPT 2019; Ishai, Y., Rijmen, V., Eds.; Springer: Cham, Switzerland, 2019; pp. 313–342. [Google Scholar]
- Leurent, G. Improved Differential-Linear Cryptanalysis of 7-Round Chaskey with Partitioning. In Advances in Cryptology—EUROCRYPT 2016; Fischlin, M., Coron, J.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 344–371. [Google Scholar]
- Beierle, C.; Leander, G.; Todo, Y. Improved Differential-Linear Attacks with Applications to ARX Ciphers. In Advances in Cryptology—CRYPTO 2020; Micciancio, D., Ristenpart, T., Eds.; Springer: Cham, Switzerland, 2020; pp. 329–358. [Google Scholar]
- Chen, Y.; Bao, Z.; Yu, H. Differential-Linear Approximation Semi-unconstrained Searching and Partition Tree: Application to LEA and Speck. In Advances in Cryptology—ASIACRYPT 2023; Guo, J., Steinfeld, R., Eds.; Springer: Singapore, 2023; pp. 223–255. [Google Scholar]
- Bellini, E.; Gerault, D.; Grados, J.; Makarim, R.H.; Peyrin, T. Fully Automated Differential-Linear Attacks Against ARX Ciphers. In Topics in Cryptology—CT-RSA 2023; Rosulek, M., Ed.; Springer: Cham, Switzerland, 2023; pp. 252–276. [Google Scholar]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An Ultra-Lightweight Block Cipher. In Cryptographic Hardware and Embedded Systems—CHES 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- Blondeau, C.; Leander, G.; Nyberg, K. Differential-linear cryptanalysis revisited. J. Cryptol. 2017, 30, 859–888. [Google Scholar] [CrossRef]
- Soos, M.; Nohl, K.; Castelluccia, C. Extending SAT solvers to cryptographic problems. In Theory and Applications of Satisfiability Testing; Springer: Berlin/Heidelberg, Germany, 2009; pp. 244–257. [Google Scholar]
- Biere, A. CaDiCaL at the SAT Race 2019. SAT RACE 2019, 2019, 8. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).