Abstract
Adaptor signature is a variant of digital signatures and useful for fair excheng in financial applications such as cryptocurrencies, to name a few, off-chain transaction protocols, atomic swaps and other privacy-enhancing mechanisms. However, similar to normal digital signatures, an adaptor signature also suffers from the loss of the secret key and single-point failure, which is insufficient in practice. In this paper, we address this constraint by introducing two new concepts as enhancements: multi-adaptor signatures and threshold adaptor signatures. First, we propose the formal security models for multi-adaptor signature and threshold adaptor signature. Then, we present specific schemes for these two primitives based on the commonly used blockchain signature scheme Schnorr and the post-quantum signature scheme Dilithium, respectively. Furthermore, we provide security proofs for these four schemes. Finally, we demonstrate interesting applications for blockchains, such as oracle-based conditional payment and n to n atomic swap.
1. Introduction
Due to its decentralized, anonymous, traceable, and transparent nature, blockchain has extensive applications. However, existing blockchain applications, such as cryptocurrencies, face challenges like poor scalability and low throughput. Addressing these issues, payment channel networks (PCNs) [1,2] establish channels on-chain, enabling numerous off-chain transactions between users. This reduces on-chain transaction volume, increases transaction throughput, and lowers on-chain costs. As a crucial technology for building PCNs in blockchains, adapter signatures [3] serve as important building block in addressing issues such as poor scalability and low throughput.
An adaptor signature is a cryptographic primitive that enables a signer to create a pre-signature under its secret key, adaptable into a valid signature by a publisher possessing a specific secret value. If the finalized signature becomes public, the signer can extract the secret value employed by the publisher. In blockchain applications, adapter signatures can be utilized in atomic swap [4], enabling two parties to proceed cross-chain fair exchange.
Adaptor signatures can be viewed as an extension of digital signatures to address the lack of mutual trust. Aside from key generation, signing and verification algorithms, there is a stage called pre-signing, where a pre-signing algorithm produces a pre-signature, which can be verified by a pre-signature verification algorithm. To convert a pre-signature into a normal signature, an adaptation algorithm and evidence extraction algorithm come into place. Adaptor signatures possess two distinct capabilities, i.e., authorization and evidence extraction, achieved by the integration of hard relations. Currently, motivated by blockchains, many works proposed adaptor signature schemes based on Schnorr signatures [3,5] and ECDSA signatures [3,6]. Additionally, for long-term security, there is also work [7] that provided adaptor signatures based on lattice signatures.
In an adaptor signature system, only a single signer is considered, which is often insufficient in many scenarios. We consider the following two instances:
- In cryptocurrency transactions, the loss of the secrete key of the signer can lead to significant financial losses. If we extend the adaptor signatures to a threshold setting, called the threshold adaptor signature scheme, the loss of a single secret key share does not compromise the security of the system.
- In blockchain-based crowdfunding scenarios, transactions require the consent of every stakeholder. This needs the extension of adaptor signatures into multi-setting, ensuring that a valid signature can only be generated when all stakeholders agree on the transaction.
As we can see, adaptor signatures are not suitable for the above scenarios that require multi-signers, and basic multi-party signatures lack the features of adaptor signatures. Therefore, this paper focuses on multi/threshold adaptor signatures. In the case of -threshold adaptor signatures, out of n secret key share holders need to participate to generate a valid signature. Moreover, multi-adaptor signatures require the participation of all secret key share holders in the signing protocol.
1.1. Our Results and Technical Overview
In this paper, we formally study multi-adaptor signatures and threshold adaptor signatures. Our contributions are three-fold:
Formal Models. We proposed a formal model for the multi-adaptor signature and threshold adaptor signature with one witness holder, n signers , and public verifiers.
A multi-adaptor signature scheme consists of one interactive protocol MSign and six non-interactive algorithms. The system works as follows:
- To start, the witness holder provides a statement Y, and each signer will invoke the MKGen algorithm to generate its public-secret key pair .
- Next, given Y and a message m to be signed, the n signers jointly run the MSign protocol to generate a pre-signature for m, then employ the KAgg algorithm to generate an aggregated key using .
- Then, using and Y, the witness holder can verify the validity of by invoking the algorithm. If is valid, the witness holder can further utilize the witness y (of the statement Y such that , where denotes a binary relation provided as a public parameter) to transform into a signature .
- Any verifier can use MVerify to verify the validity of .
- From and , all signers can obtain the witness y through the algorithm.
For a threshold adaptor signature scheme , which differs from in terms of the key generation algorithm (TKGen), the signing protocol (TSign) and the public key aggregation algorithm (KAgg). At the end of each execution instance of the protocol TKGen, each signer obtains a secret key share along with the corresponding public key . Given the statement Y and a message m, any (out of n) signers can jointly generate a valid pre-signature using their secret key shares and the public key by running the protocol TSign. Since all signers use a common , the KAgg algorithm for aggregating public keys in is not required in .
Our security definitions continue the security requirements of adaptor signature pre-signature adaptability and witness extractability. Pre-signature adaptability ensures that any valid pre-signature specific to Y can be completed into a valid signature using. Witness extractability guarantees that a valid tuple for a tuple can be used to extract a corresponding witness y. In addition, we provide definitions of unforgeability for and , respectively. For , we require that in a signing protocol involving n signers, even if the adversary corrupts of them, it should still be unable to forge a valid pre-signature. Unlike , for the unforgeability of -, it needs that fewer than signers should not be able to generate a valid pre-signature. The adversary, who can corrupt at most t signers, is allowed to participate in the key generation protocol, but still, it should be unable to forge a pre-signature that can be verified.
Schemes. We construct and - schemes based on Schnorr, which is the commonly used signature scheme in blockchain to meet the diverse application requirements. Additionally, considering the long-term security and the post-quantum signature standards established by NIST, we also construct and - based on Dilithium. We also provide security proofs for our schemes, demonstrating that the schemes satisfy pre-signature adaptability, witness extractability, and unforgeability.
Our and - schemes with Schnorr are based on the multi-signature in [8] and the threshold signature in [9], respectively. Our and - schemes with Dilithium are based on the multi-signature and signature from [10]. Our schemes maintain the key generation processes of the original schemes with slight modifications to their signing protocols, introducing a statement in the commitment generation. Correspondingly, the pre-verify algorithm pVerify also involves the statement.
Applications. We present an application of multi-adaptor signature, an n to n atomic swap. In contrast to the atomic swap implemented with basic adaptor signatures, this approach effectively prevents economic losses resulting from the loss of a single secret key. For threshold adaptor signatures, we present an application in oracle-based conditional payment. The security of threshold adaptor signature ensures that a single malicious oracle cannot disrupt the payments. In addition, the payer retains the right to know that oracles are transferring funds to the payee. Furthermore, threshold and multi-adaptor signatures can also be applied to electronic voting and cross-chain crowdfunding, respectively.
1.2. Related Work
Due to the application advantages of adaptor signatures, Malavolta et al. [2] constructed an anonymous multi-hop lock protocol based on adaptor signatures and then build a secure payment channel network. Thyagarajan et al. [11] provided an efficient instantiation of a two-party general atomic swap protocol based on ECDSA/Schnorr adaptor signatures. Aumayr et al. [3] utilized adaptor signatures to build a generalized channels structure on a script-limited blockchain, enabling secure off-chain execution and enhancing blockchain scalability.
Threshold signature was first proposed by Desmedt and Frankel [12], and they gave a threshold signature scheme based on the RSA assumption. Motivated by blockchains, efficient threshold Schnorr/ECDSA signature [9,13,14,15,16] received much attention lately. For post-quantum threshold signature, Bendlin et al. [17] proposed a lattice-based -threshold signature based on Peikert hash-and-sign signature. Damgrd et al. [10] presented a lattice-based -threshold signature by implementing Dilithium-G in a multiparty setting. Multi-signature schemes enable a group of signers possessed an own secret/public key pair to produce a single signature on a message m. A number of modern and practical multi-signature schemes [18,19,20,21,22] are proposed based on Schnorr.
Organization of the Rest of the Paper. In Section 2, we give the preliminary. We give a model for multi-adaptor signature and thresho1d adaptor signature in Section 3 and Section 4, respectively. We also give specific schemes for the new primitives. In Section 5, we discuss two applications of multi and thresho1d adaptor signature.
2. Preliminary
We now revisit adaptor signatures as presented in [23]. An adaptor signature scheme (w.r.t a hard relation R) can be described as follows:
- KGen(): on input a security parameter , the randomized algorithm outputs the secret key and public key . In short, .
- pSign(): on input , a message and a statement , the randomized algorithm outputs a pre-signature . In short, pSign().
- pVerify(): on input , , and , the deterministic algorithm outputs a bit . In short, .
- Adapt(): on input and a witness y, this deterministic algorithm outputs a signature . In short, .
- Verify: on input m, and , this deterministic algorithm outputs a bit which equals 1 if and only if is a valid signature on m under . In short, .
- Ext: on input , and , this deterministic algorithm outputs y such that , or ⊥. In short, .
An adaptor signature scheme should satisfy pre-signature correctness, and a secure adaptor signature scheme should satisfy pre-signature adaptability, unforgeablity and witness extractability.
3. Multi Adaptor Signature
Here, we propose a formal model for multi-adaptor signature and the corresponding security requirements. We construct two secure multi-adaptor signature schemes based on Schnorr and Dilithium, respectively.
3.1. Syntax
Definition 1.

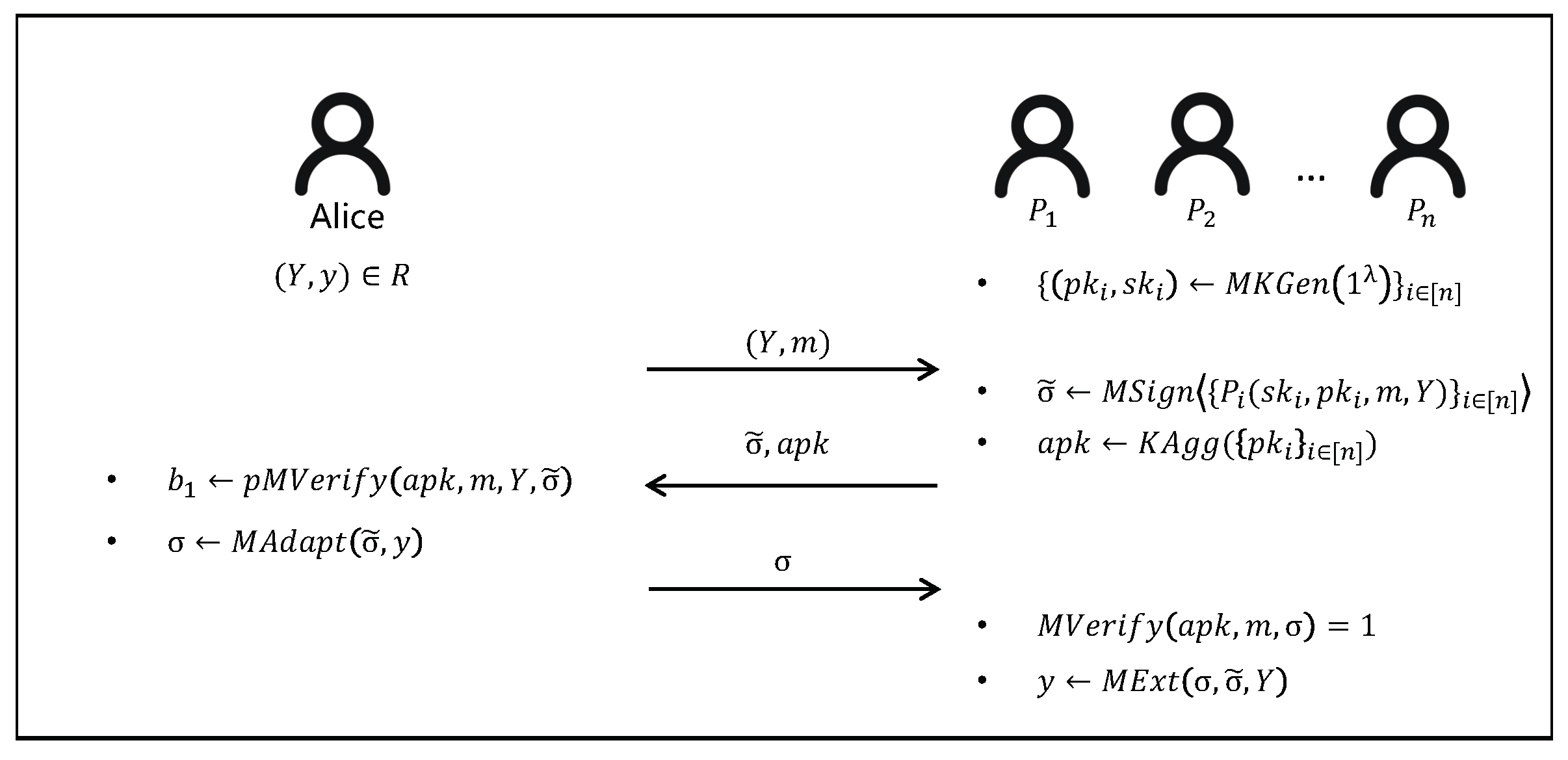
A multi-adaptor signature scheme (w.r.t a hard relationR) = (MKGen, MSign, KAgg, pMVerify, MAdapt, MVerify, MExt) consists of the following polynomial time protocol and algorithms, we also give a flowchart of multi-adaptor signature scheme in Figure 1.

Figure 1.
The flowchart of the multi adaptor signature.
- MKGen: on input a security parameter λ as input, this randomized algorithm returns the private signing key and public verification key . In short, .
- MSign: This probabilistic protocol is jointly ran by n signing players which generates a pre-signature . ’s input is a statement , a message , his private signing key and public key generated in MKGen. The protocol is allowed to abort. In short, .
- KAgg: on input , this deterministic algorithm outputs an aggregated public key . In short, .
- pMVerify: on input a message , an aggregated public key , a statement and a pre-signature , this deterministic algorithm outputs a bit . In short, .
- MAdapt: on input a pre-signature and a witness y, this deterministic algorithm outputs a signature σ. In short, .
- MVerify: on input an aggregated public key , a message m and a signature σ, this deterministic algorithm outputs a bit which equals 1 if and only if σ is a valid signature on m under . In short, .
- MExt: on input a signature σ, a pre-signature and a statement , this deterministic algorithm outputs a witness y such that , or ⊥. In short, .
Correctness. A multi-adaptor signature scheme should also satisfy pre-signature correctness.
Definition 2.
A multi-adaptor signature satisfies pre-signature correctness, if for all , generated by MKGen, , generated by MSign, , , and , the following holds:
3.2. Security Definitions
A multi-adaptor signature scheme is secure if it satisfies pre-signature adaptability, unforgeablity and witness extractability. We denote Q as the transcript of the interactions between adversary and ,. is a signing oracle that for an input message , , returns a valid public- verifiable signature , and is a pre-signing oracle that returns a corresponding pre-signature . The formal definition of these properties are as follows.
Definition 3.
A multi-adaptor signature satisfies pre-signature adaptability, if for all and , aggregated public key , and pre-signatures ; once we have that , then the following holds:
Without loss of generality, we assume there is a single honest player . The unforgeablity and witness extractability can be described as follows.
Definition 4.
A multi-adaptor signature satisfies unforgeable, if for any PPT adversary , its advantage in the following experiment
is negligible in λ.
Definition 5.
A multi-adaptor signature is witness extractable, if for any PPT adversary , its advantage in the following experiment
is negligible in λ.
3.3. Multi Adaptor Signature Based on Schnorr
Considering a p order cyclic group denoted as with generator g, the discrete logarithm problem in is hard. We consider the hard relation and denote the hash functions , and from to . The scheme =(S.MKGen, S.MSign, S.KAgg, S.pMVerify, S.MAdapt, S.MVerify, S.MExt) can be described as follows:
- –
- .Each signer samples a random and computes , then generates the secret key and public key .
- –
- .Given a message m and a statement , for each , each signer generates random and computes . It then outputs and broadcasts the v nonces . After receiving the nonces from others, each player computes for each and outputs . Each player computes , where , and . Then, each signer computes , , and . Broadcast . After receiving all form all players, computes . The signature of m is .
- –
- .Given , the algorithm computes , where , and . The aggregated public key is .
- –
- .Given an aggregated public key , a message m, a statement and an adaptor signature , the algorithm computes and accepts the adaptor signature if .
- –
- .Given an adaptor signature and a witness y, the algorithm outputs the signature , where .
- –
- .Given a message m, an aggregated public key , and a signature , the verifier computes and accepts the signature if .
- –
- .Given an adaptor signature , a signature and a statement , the algorithm can return the witness .
Theorem 1.
S.MASIGR = (S.MKGen, S.MSign, S.KAgg, S.pMVerify, S.MAdapt, S.MVerify, S.MExt) is a secure multi-adaptor signature.
Proof.
As we can see, the scheme satisfies pre-signature correctness. We now show that satisfies pre-signature adaptable, unforgeablity and witness extractable.
Pre-signature adaptability. Assume holds, such that . For , . It direct implies with , with and . Therefore, the vaild pre-signature can be adapted in a vaild signature.
Unforgeability. If ∃ adversary corrupts at most signing players can forge a valid confirmer signature, an efficient adversary can be constructed that can break the security of multi-signature scheme in [8]. For setup, generates , and sends to . When queries on message , interacts with its own challenger to obtain a transcript and gives to . When queries on message , obtains a transcript and gives to . When outputs a forged signature on a message , can provide a valid signature of scheme in [8].
Witness extractability. If ∃ adversary corrupts at most signing players can forge a valid confirmer signature, an efficient adversary can be constructed that can break the unforgeability of scheme in [8] or break the hardness of the relation R. When makes signing queries works as described in unforgeability. If ’s forgery , can use to extract the witness and break the hardness of the relation R. Otherwise, forge a valid signature that satisfies , which also a valid signature of multi-signature scheme in [8]. □
3.4. Multi Adaptor Signature Based on Dilithium
For a random matrix , we consider the hard relation . We denote : and COM=(CKGen, Commit, Open) a homomorphic commitment. The scheme D.MASIGR=(D.MKGen, D.MSign, D.KAgg, D.pMVerify, D.MAdapt, D.MVerify, D.MExt) can be described as follows:
- –
- .Given a random matrix , each signer samples and computes , where . The secret key and the public key .
- –
- .Given a message m, a list of public keys and a statement , each player samples , computes , with , and broadcasts . After receiving for all and a random , sets , derives a challenge and computes a signature share . Then, runs the rejection sampling on input , broadcasts with probability ; otherwise broadcasts Restart. If some player broadcast Restart, restart from sampling ; otherwise derives a per-user challenge , reconstructs then checks and . If the check fails for some j, broadcasts Abort; otherwise, computes and . The signature of m is .
- –
- .The aggregated public key is .
- –
- .Given an aggregated public key , a message m, an adaptor signature , and statement , the algorithm derives a per-user challenge and reconstruct . Then, outputs if and .
- –
- .Given an adaptor signature , and a witness , the algorithm outputs the signature , where and .
- –
- .Given a message m, a signature , aggregated public key , the algorithm derives a per-user challenge and reconstruct . Then, outputs if and .
- –
- .Given an adaptor signature , a signature , the algorithm can return as the witness .
Theorem 2.
D.MASIGR = (D.MKGen, S.MSign, D.KAgg, D.pMVerify, D.MAdapt, D.MVerify, D.MExt) is a secure multi-adaptor signature.
Proof.
We now show satisfies pre-signature adaptability, unforgeablity and witness extractability. □
Pre-signature adaptability. If , which means . For valid pair , we can obtain . It direct implies with , with , and . Therefore, the vaild pre-signature can be adapted into a vaild signature.
Unforgeability and witness extractability. The proof is subsumed by the unforgeability and witness extractability proof of . If adversary breaks the unforgeability or witness extractability of , an efficient adversary can be constructed that can break the unforgeability of scheme in [10] or the hardness of the relation R.
4. Threshold Adaptor Signature
In this section, we present a formal model for threshold adaptor signatures and construct two secure schemes based on Schnorr and Dilithium, respectively.
4.1. Syntax
Definition 6.
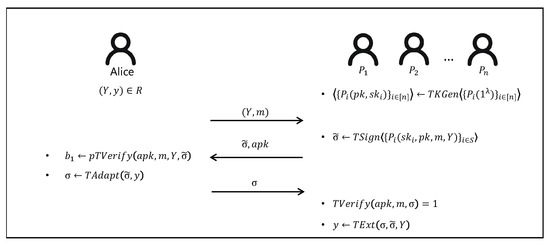
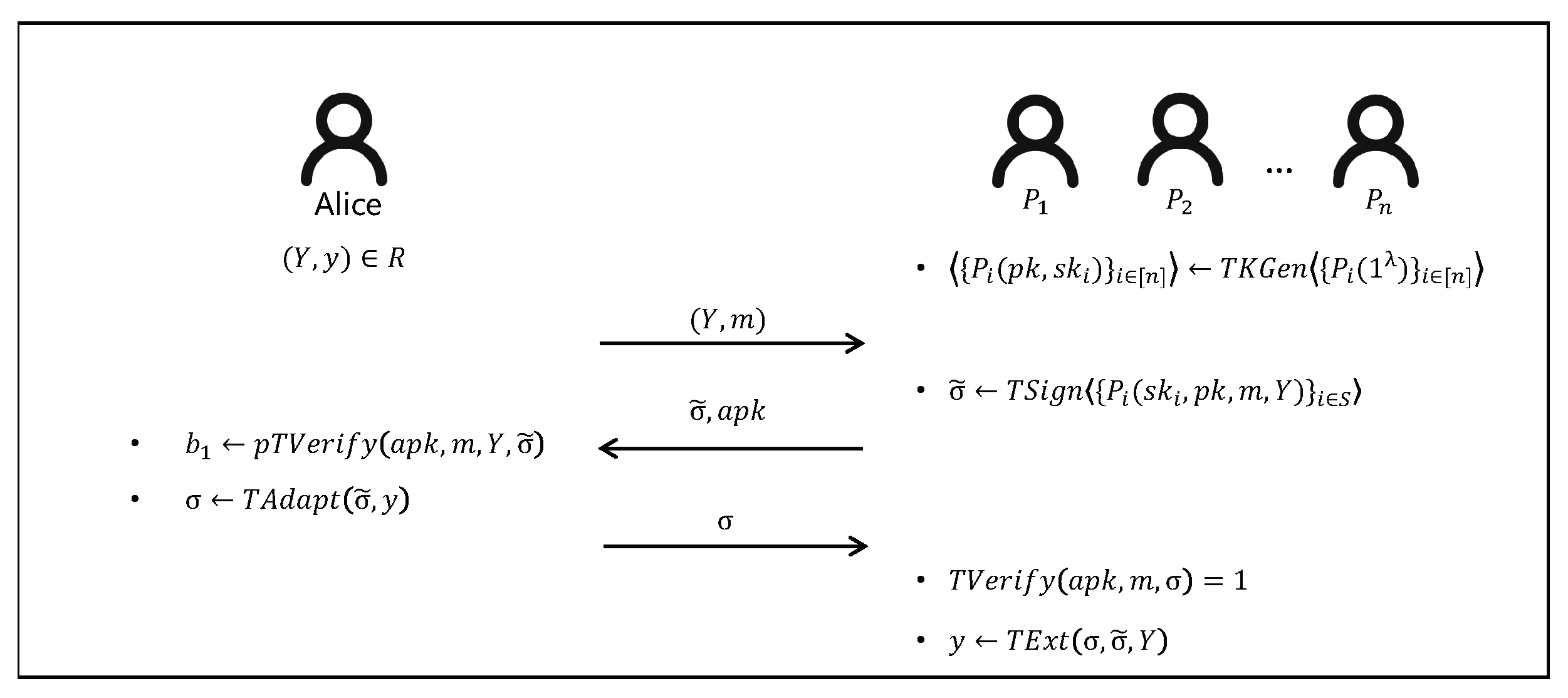
A -threshold adaptor signature scheme (w.r.t a hard relation R) can be described as follows, and we also give a flowchart of multi-adaptor signature scheme in Figure 2.

Figure 2.
The flowchart of threshold adaptor signature.
- TKGen: this probabilistic protocol is jointly run by n signing players which takes a security parameter λ as public input. The private output of each signing player is a signing secret key share , and the public output is the corresponding signing public key . The protocol is allowed to abort. In short, .
- TSign: this probabilistic protocol is jointly run by a subset with to generate a pre-signature . Each player ’s private input is his secret key share , while the public input consists of , m and . The protocol is also allowed to abort. In short, .
- pTVerify: on input a public key , a statement , a message and a pre-signature , this deterministic algorithm outputs a bit . In short, .
- TAdapt: on input a pre-signature and a witness y, this deterministic algorithm outputs a signature σ. In short, .
- TVerify: on input a public key , a message m and a signature σ, this deterministic algorithm outputs a bit which equals 1 if σ is a valid signature. In short, .
- TExt: on input a signature σ, a statement and a pre-signature , this deterministic algorithm outputs a witness y such that , or ⊥. In short, .
Correctness. A threshold adaptor signature should satisfy pre-signature correctness.
Definition 7.
A threshold adaptor signature satisfies pre-signature correctness, if for all , , generated by TKGen, , generated by TSign, , and , the following holds:
4.2. Security Definitions
A secure threshold adaptor signature scheme should satisfy pre-signature adaptable, unforgeable and witness extractable. We denote Q as the transcript containing all the interactions between adversary and , , . When a malicious adversary corrupts at most t signing players query and , it can obtain the views of the protocols TKGen and TSign on input messages which the adversary adaptively chose, respectively. is a pre-signing oracle that for a message , , returns a corresponding pre-signature .
Definition 8.
A threshold adaptor signature is pre-signature adaptable, if for all , , and , once we have that , then the following holds:
Definition 9.
A threshold adaptor signature satisfies unforgeable, if for any PPT adversary , its advantage in the following experiment
is negligible in λ.
Definition 10.
A threshold adaptor signature is witness extractable, if for any PPT adversary , its advantage in the following experiment
is negligible in λ.
4.3. Threshold Adaptor Signature Based on Schnorr
Consider a p order cyclic group denoted as with generator g, and the discrete logarithm problem in is hard. We consider the hard relation and denote as a random oracle. The scheme =(S.TKGen, S.TSign, S.pTVerify, S.TAdapt, S.TVerify, S.TExt) can be described as follows:
- –
- .Each player , performs Pedersen distributed key generation protocol. After the protocol, each holds a value that is their secret signing share and a public key .
- –
- .Let be the set of players participating in the signing protocol. Each player can use S to determine the Lagrangian coefficients . Let be hash functions whose outputs are in .Each signing player samples single-use nonces , computes commitments , then broadcasts . When given a message m and a statement , creates the set B, where B is the ordered list of tuples . Then, computes the set of values , the group commitment , the challenge , and . securely deletes from their local storage. broadcasts . After received , from other players, checks the consistency of each . If no check fails, the signature of m is , where .
- –
- .Parse as , and as , respectively, then compute and . Output 1 if and only if ; otherwise, output 0.
- –
- .Given an adaptor signature and a witness y, the algorithm outputs the signature , where .
- –
- .Parse as , and as , respectively, then compute and . Output 1 if and only if ; otherwise, output 0.
- –
- .Given an adaptor signature , a signature and a statement, the algorithm can return the witness .
Theorem 3.
=(S.TKGen, S.TSign, S.pTVerify, S.TAdapt, S.TVerify, S.TExt) is a secure threshold adaptor signature.
Proof.
The proof is subsumed by the security proof of with the only distinction that we need to provide a reduction to the scheme in [9] instead of scheme in [8] for unforgeability and witness extractability. If ∃ adversary can break the unforgeability or witness extractability of , an efficient adversary can be constructed that can break the unforgeability of scheme in [9]. □
4.4. Threshold Adaptor Signature Based on Dilithium
For a random matrix , we consider the hard relation . We denote and as a homomorphic commitment and : , , as random oracles. The scheme =(D.TKGen, D.TSign, D.pTVerify, D.TAdapt, D.TVerify, D.TExt) can be described as follows.
- –
- .Each player samples a random matrix share and generates a commitment , broadcasts . After receiving for all , broadcasts . After receiving for all , checks . If the check fails for some j, broadcasts Abort; otherwise computes and sets . samples and computes , respectively, generates a random oracle commitment , then broadcasts . After receiving for all , broadcasts . After receiving for all , check . If the check fails for some j, broadcasts Abort; otherwise, the public key , and ’s secret key is .
- –
- .Given a message m and a statement , each player samples and computes , with , and broadcasts . After receiving for all and a random , sets , derives a challenge and computes a signature share . Then, runs the rejection sampling on input , broadcasts with probability ; otherwise broadcasts Restart. If some player broadcast Restart, restart from sampling ; otherwise reconstructs then checks and . If the check fails for some j, broadcasts Abort; otherwise, computes and . The signature of m is .
- –
- .Given a public key , a message m, an adaptor signature , and statement , the algorithm derives a challenge and reconstructs . Then, outputs if and .
- –
- .Given an adaptor signature , and a witness , the algorithm outputs the signature , where and .
- –
- .Given a message m, a signature , a public key , the algorithm derives a challenge and reconstructs . Then, outputs if and .
- –
- .Given an adaptor signature , a signature , the algorithm can return as the witness .
Theorem 4.
=(D.TKGen, D.TSign, D.pTVerify, D.TAdapt, D.TVerify, D.TExt) is a secure threshold adaptor signature.
Proof.
The proof is subsumed by the security proof of , differing only in presenting a reduction to the scheme, instead of the multi-signature scheme in [10] for unforgeability and witness extractability. □
5. Application
In this section, we present further applications for multi-adaptor signature and threshold adaptor signature.
5.1. n to n Atomic Swap
When cryptographic assets from two different blockchain networks need to be exchanged, atomic swaps can be utilized. This technology allows two parties to securely and verifiably exchange without relying on third-party trust.
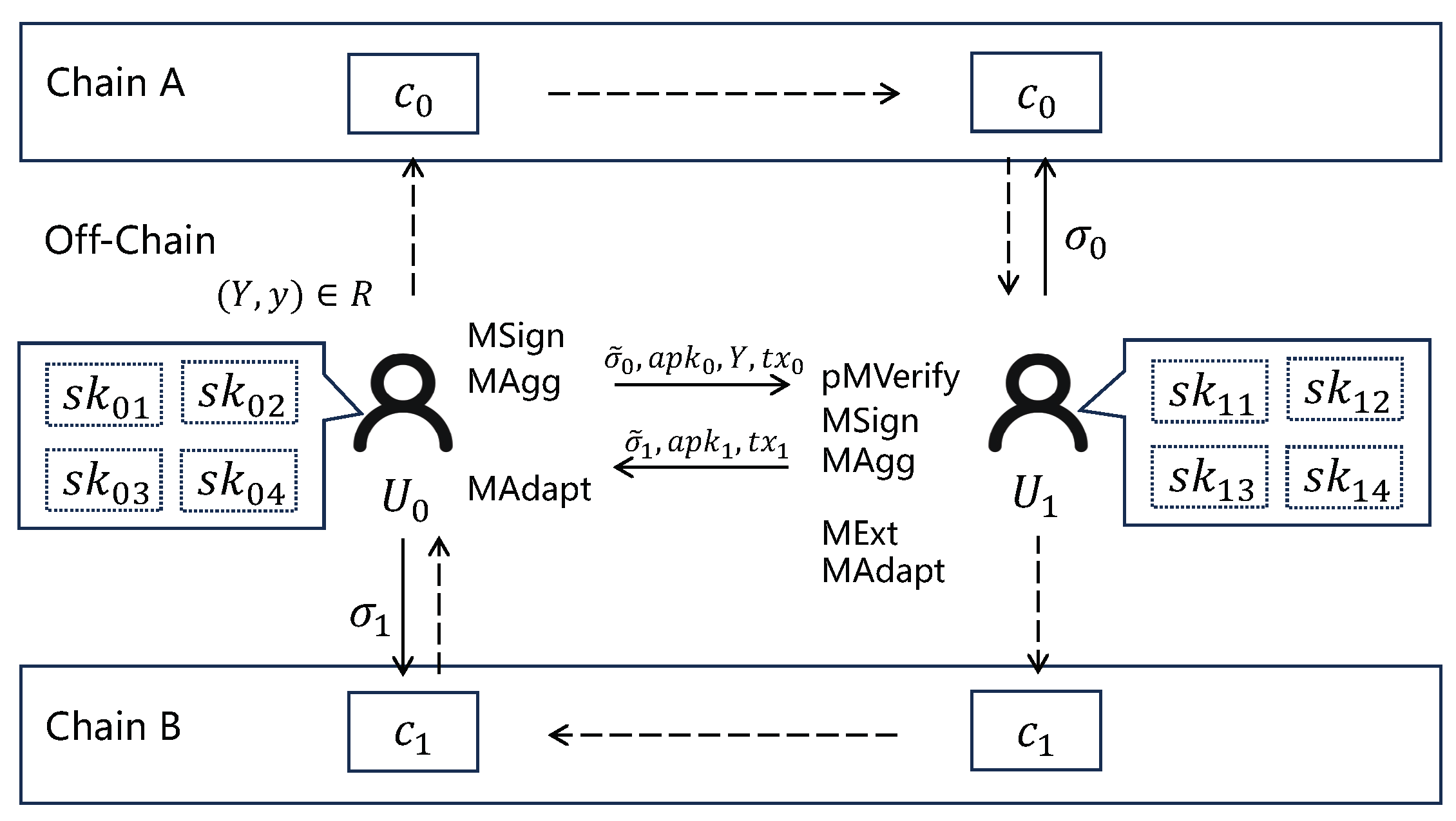
We have constructed an atomic swap system (Figure 3) using multi-adaptor signature, which includes two entities, the transacting parties and . To mitigate the risk of economic loss in the event of the loss of a single secret key holding a substantial amount, and can distribute cryptographic coins and their corresponding secret keys across n locations.
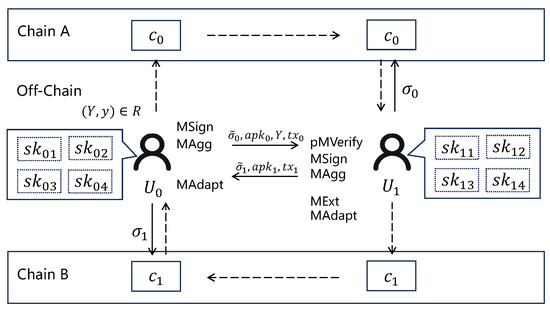
Figure 3.
The atomic swap system with multi adaptor signature.
- Setup: publicly discloses statement Y, and both and invoke algorithm MKGen to generate their keys and for their participation in this transaction.
- Locking Assets: The exchanging parties use a time-lock to restrict the pending currencies, with the time-lock primarily granting sufficient time to complete the exchange. That also prevents from withdrawing their currency after withdrawing ’s currency.
- Generating Transactions: utilizes MSign to generate a pre-signature for the exchange transaction (i.e., transferring to ) based on statement Y, and invokes MAgg to generate an aggregated key , then sends to . After verifies by pMVerify, generate the aggregated key and pre-signature for the exchange transaction base on Y, where is that transferring to , then sends to .
- Broadcasting Transactions: verifies and adapts the into a complete signature value using MAdapt, then broadcasts to obtain . Based on and , can extract witness y using MExt, then adapts into a complete signature value . broadcasts to obtain the .
Henceforth, n to n atomic swaps are able to be processed in batches simultaneously.
5.2. Oracle-Based Conditional Payment
Oracle-based conditional payments are a financial mechanism or smart contract arrangement that relies on external data oracles to trigger and execute a payment or transaction when specific conditions are met. The conditions can be anything that can be determined or verified by external data, such as the outcome of a sports event, weather conditions, stock prices, or any other event. These conditional payments are commonly used in blockchain and smart contract environments to automate financial agreements based on real-world events or data.
For example, Alice and Bob bet on a sports match. Alice bets USD 30 on team C, with the USD 30 held in escrow by oracles until the end of the game. Oracles serve as an intermediary layer connecting the blockchain with the real world. Once the match results are disclosed, oracles fetch the outcome from external data sources and execute payments based on the results. In the event that team C loses the match, oracles will transfer the USD 30 from Alice’s account to Bob’s account.
We now give an oracle-based conditional payment system using threshold adaptor signature and verifiable time signature. The system consists of a payer (A), a payee (B), and a set of oracles ( utilized as watchtowers.
- Setup: A publishes its statement Y, and each oracle , runs the key generation protocol TKGen to generate and its own secret key .
- Escrowing funds: oracles generate a verifiable time signature and send it to A, ensuring that A can redeem its funds after time T if the predefined conditions have yet to be fulfilled. Once A receives the verifiable time signature and checks its validity, A sends its signature to the oracles, which claims that the funds are escrowed in the address , then check its validity.
- Condition monitoring: The oracles continuously monitor to determine whether the predefined conditions are met.
- Payment execution: When the conditions are met before time T, the oracles automatically execute the payment as per the agreed terms. oracles collectively perform TASIG to generate a pre-signature and send it to A. A calls TpVerify to verify , and for the valid , A uses its witness y and invokes TAdapt, transforming it into a signature that can be publicly verified. After B receives the signature, B can publish the signature and miners utilize TVerify to verify the signature.
We can observe that the securities of the threshold adaptor signature ensure that a single malicious oracle cannot disrupt the payment. Additionally, A has the right to be informed that the funds are being transferred to the payee. Only when A adapts the pre-signature into a publicly verifiable signature can B complete the receipt of funds.
6. Conclusions
Adaptor signatures have lots of applications in cryptocurrencies and blockchain, but may encounter issues such as secret key loss and single-point failure. To address this, we introduce multi-adaptor signatures and threshold adaptor signatures. We propose their security models and give four schemes based on Schnorr and Dilithium, respectively. Finally, two interesting applications are present, demonstrating that multi-adaptor signature and threshold adaptor signature can prevent system disruptions caused by the loss of a single secret key. In the future, for long-term security and broader application scenarios, we will focus on lattice-based (t, n)-threshold adaptor signatures.
Author Contributions
Methodology, Y.J. and B.G.; Writing (original draft preparation), Y.J. and Y.X.; Writing (review and editing), R.Z. and Y.X. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Natural Science Foundation of China (Grant No. 62202458).
Data Availability Statement
Data supporting this study are included within the article.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| q | A prime number |
| The interval | |
| Boldface small letters (e.g., ) | Column vectors over and |
| Boldface capital letters (e.g., ) | Matrices |
| The concatenation of matrices and | |
| A polynomial ring for an irreducible monic polynomial , where N is a power of 2 | |
| A lattice in | |
| In an interactive protocol Pro between parties A and B, A’s (resp. B’s) input is (resp. ), where A’s (resp. B’s) output at the end of the execution is (resp. ). | |
| A protocol with all parties receive the same output y. | |
| An NP language and as the associated binary relation |
References
- Decker, C.; Wattenhofer, R. A fast and scalable payment network with bitcoin duplex micropayment channels. In Proceedings of the SSS 2015, Edmonton, AB, Canada, 18–21 August 2015; Springer: Cham, Switzerland, 2015; pp. 3–18. [Google Scholar] [CrossRef]
- Malavolta, G.; Moreno-Sanchez, P.; Schneidewind, C.; Kate, A.; Maffei, M. Anonymous multi-hop locks for blockchain scalability and interoperability. In Proceedings of the NDSS 2019, San Diego, CA, USA, 24–27 February 2019. [Google Scholar] [CrossRef]
- Aumayr, L.; Ersoy, O.; Erwig, A.; Faust, S.; Hostkov, K.; Maffei, M.; Moreno-Sanchez, P.; Riahi, S. Generalized channels from limited blockchain scripts and adaptor signatures. In Proceedings of the ASIACRYPT 2021, Singapore, 6–10 December 2021; Springer: Cham, Switzerland, 2021; pp. 635–664. [Google Scholar] [CrossRef]
- Chaum, D.; Pedersen, T.P. Wallet Databases with Observers. In Proceedings of the CRYPTO 1992, Santa Barbara, CA, USA, 16–20 August 1992; Springer: Berlin/Heidelberg, Germany, 1993; pp. 89–105. [Google Scholar] [CrossRef]
- Erwig, A.; Faust, S.; Hostáková, K.; Maitra, M.; Riahi, S. Two-party adaptor signatures from identification schemes. In Proceedings of the PKC 2021, Virtual, 10–13 May 2021; Springer: Cham, Switzerland, 2021; pp. 451–480. [Google Scholar] [CrossRef]
- Moreno-Sanchez, P.; Kate, A. Scriptless Scripts with ECDSA. 2018. Available online: https://lists.linuxfoundation.org/pipermail/lightning-dev/attachments/20180426/fe978423/attachment-0001.pdf (accessed on 6 December 2023).
- Esgin, M.F.; Ersoy, O.; Erkin, Z. Post-quantum adaptor signatures and payment channel networks. In Proceedings of the European Symposium on Research in Computer Security, Guildford, UK, 14–18 September 2020; Springer: Cham, Switzerland, 2020; pp. 378–397. [Google Scholar] [CrossRef]
- Nick, J.; Ruffing, T.; Seurin, Y. MuSig2: Simple two-round Schnorr multi-signatures. In Proceedings of the CRYPTO 2021, Virtual, 16–20 August 2021; Springer: Cham, Switzerland, 2021; pp. 189–221. [Google Scholar] [CrossRef]
- Komlo, C.; Goldberg, I. FROST: Flexible round-optimized Schnorr threshold signatures. In Proceedings of the SAC 2020, Brno, Czech Republic, 30 March–3 April 2020; Springer: Cham, Switzerland, 2021; Volume 12804, pp. 34–65. [Google Scholar] [CrossRef]
- Damgrd, I.; Orlandi, C.; Takahashi, A.; Tibouchi, M. Two-round n-out-of-n and multi-signatures and trapdoor commitment from lattices. J. Cryptol. 2022, 35, 14. [Google Scholar] [CrossRef]
- Thyagarajan, S.A.; Malavolta, G.; Moreno-Sanchez, P. Universal atomic swaps: Secure exchange of coins across all blockchains. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–26 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1299–1316. [Google Scholar] [CrossRef]
- Desmedt, Y.; Frankel, Y. Shared generation of authenticators and signatures. In Proceedings of the CRYPTO 1991, Santa Barbara, CA, USA, 11–15 August 1991; Springer: Cham, Switzerland, 1991; Volume 576, pp. 457–469. [Google Scholar] [CrossRef]
- Gennaro, R.; Goldfeder, S. Fast multiparty threshold ECDSA with fast trustless setup. In Proceedings of the CCS 2018, Toronto, ON, Canada, 15–19 October 2018; pp. 1179–1194. [Google Scholar] [CrossRef]
- Castagnos, G.; Catalano, D.; Laguillaumie, F.; Savasta, F.; Tucker, I. Bandwidth-efficient threshold EC-DSA. In Proceedings of the PKC 2020, Edinburgh, UK, 4–7 May 2020; Springer: Cham, Switzerland, 2020; Volume 12111, pp. 266–296. [Google Scholar] [CrossRef]
- Canetti, R.; Gennaro, R.; Goldfeder, S.; Makriyannis, N.; Peled, U. UC non-interactive, proactive, threshold ECDSA with identifiable aborts. In Proceedings of the CCS 2020, Virtual, 9–13 November 2020; pp. 1769–1787. [Google Scholar] [CrossRef]
- Castagnos, G.; Catalano, D.; Laguillaumie, F.; Savasta, F.; Tucker, I. Bandwidth-efficient threshold EC-DSA revisited: Online/offline extensions, identifiable aborts proactive and adaptive security. Theor. Comput. Sci. 2023, 939, 78–104. [Google Scholar] [CrossRef]
- Bendlin, R.; Krehbiel, S.; Peikert, C. How to share a lattice trapdoor: Threshold protocols for signatures and (H) IBE. In Proceedings of the ACNS 2013, Banff, AB, Canada, 25–28 June 2013; Springer: Cham, Switzerland, 2013; Volume 7954, pp. 218–236. [Google Scholar] [CrossRef]
- Nicolosi, A.; Krohn, M.N.; Dodis, Y.; Mazieres, D. Proactive Two-Party Signatures for User Authentication. In Proceedings of the NDSS 2003, San Diego, CA, USA, 27 February–3 March 2003. [Google Scholar]
- Bellare, M.; Neven, G. Multi-signatures in the plain public-key model and a general forking lemma. In Proceedings of the CCS 2006, Alexandria, VA, USA, 30 October–3 November 2006; pp. 390–399. [Google Scholar]
- Bagherzandi, A.; Cheon, J.H.; Jarecki, S. Multisignatures secure under the discrete logarithm assumption and a generalized forking lemma. In Proceedings of the CCS 2008, Alexandria, VA, USA, 27–31 October 2008; pp. 449–458. [Google Scholar] [CrossRef]
- Ma, C.; Weng, J.; Li, Y.; Deng, R. Efficient discrete logarithm based multi-signature scheme in the plain public key model. Des. Codes Cryptogr. 2010, 54, 121–133. [Google Scholar] [CrossRef]
- Syta, E.; Tamas, I.; Visher, D.; Wolinsky, D.I.; Jovanovic, P.; Gasser, L.; Gailly, N.; Khoffi, I.; Ford, B. Keeping authorities “honest or bust” with decentralized witness cosigning. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 526–545. [Google Scholar] [CrossRef]
- Aumayr, L.; Ersoy, O.; Erwig, L.; Faust, S.; Hostkov, K.; Maffei, M.; Moreno-Sanchez, P.; Riahi, S. Generalized Bitcoin-Compatible Channels. Cryptology ePrint Archive, Report 2020/476. Available online: http://hdl.handle.net/20.500.12708/40215 (accessed on 6 December 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).