A Blockchain-Based Incentive Mechanism for Sharing Cyber Threat Intelligence
Abstract
1. Introduction
- (1)
- Employing evolutionary game theory to analyze and derive corresponding incentive strategies that can curb the free-riding behavior of participating members in threat intelligence sharing, so that the free-riding members eventually choose to participate in the sharing or withdraw from the platform under the effect of the incentive mechanism.
- (2)
- The incentive mechanism is deployed into smart contracts that run in the trusted environment of blockchain to dynamically regulate the incentive strategy. The decentralization and tamper-proof characteristics of blockchain solve the lack of trust among the sharing members and no longer require the participation of trusted third parties, thereby realizing the secure and efficient sharing of cyber threat intelligence.
2. Related Work
2.1. Cyber Threat Intelligence Sharing
2.2. Blockchain Technology
2.3. Shared Incentive Mechanism
3. The Sharing Incentive Mechanism Construction
3.1. Sharing Strategy Assumptions
- The threat intelligence sharing platform has a defined size in terms of the number of members; each member is a finite rational participant. Specifically, the set of shared members on this platform is defined as: ; the strategy set for each member of the sharing group is , where . The Cartesian product of the pure strategy sets of each party in the game, which is the strategy space , consists of all possible combinations of pure strategies;
- In the initial stage of the game, participating member chooses to share threat intelligence with probability and chooses not to share threat intelligence with probability , i.e., ;
- Members who participate in sharing cyber threat intelligence can obtain shared benefits ; represents the scaling factor of defense benefits. The shared gain involves virtual points and reputation level enhancement granted by the sharing platform. Because the sharing platform is based on blockchain smart contracts, the virtual points are non-tamperable and have credible execution efficiency to address the issue of trust that members have with the sharing platform. Additionally, if other members also share, through complementary threat intelligence (thus breaking the information island and taking proactive defense), additional defense benefits can be obtained by participants when other members share information;
- Cyber threat intelligence is highly time-sensitive and account members who are inactive for a long time (e.g., more than the set time of one month) should be punished with points; the number of points for punishment is expressed by ;
- In order to mark the contributions and historical reputation of the shared members, we introduce an account level to distinguish different shared members. Members with higher levels will receive higher sharing profits. and , respectively, represent the cost coefficient and cost-balancing parameter. In order to prevent accounts with from pouring spam into the platform without any cost, we introduce a cost coefficient , which is computed as . When , it reaches the account level that balances the publishing cost and publishing incentive, which is the cost-neutral account level. For example, when , the cost coefficient is greater than 1 before the member account level r reaches level 4, which means that the cost of publishing threatening intelligence at this time is greater than the profit;
- The initial points of each member are . When appears in the dynamic regulation process, the new member with needs to incur a cost to release threat intelligence. At this time, the initial points can help the new member release threat intelligence to obtain a promotion of account level. Of course, if the new member is inactive for a long time after joining, they will be punished with points , which also encourages new members to share network threat intelligence as soon as possible after joining.
- To be able to actively regulate the sharing participation degree of the platform, a dynamic parameter is introduced, whose positive and negative values represent the cost and benefit, respectively. When the sharing benefit is not enough to stimulate members to participate in sharing, members generally share negatively and can be encouraged to carry out sharing by giving extra points; the value of is set to be less than zero at this time. When the sharing degree of the platform is too high and the quality of the platform threat intelligence decreases (causing the inflation of points), it will affect the willingness of high-ranking members to share high-value information and it will be necessary to charge a cost for sharing; the value of is set to be greater than zero at this time;
- is the stock benefit scaling factor when both sides of the game choose not to participate in sharing. Although the participating members share negatively, the platform stock of cyber threat intelligence can still bring some gains to the participating members, which is denoted by .
3.2. Sharing Strategy Analysis
3.3. Threat Intelligence Sharing Incentives
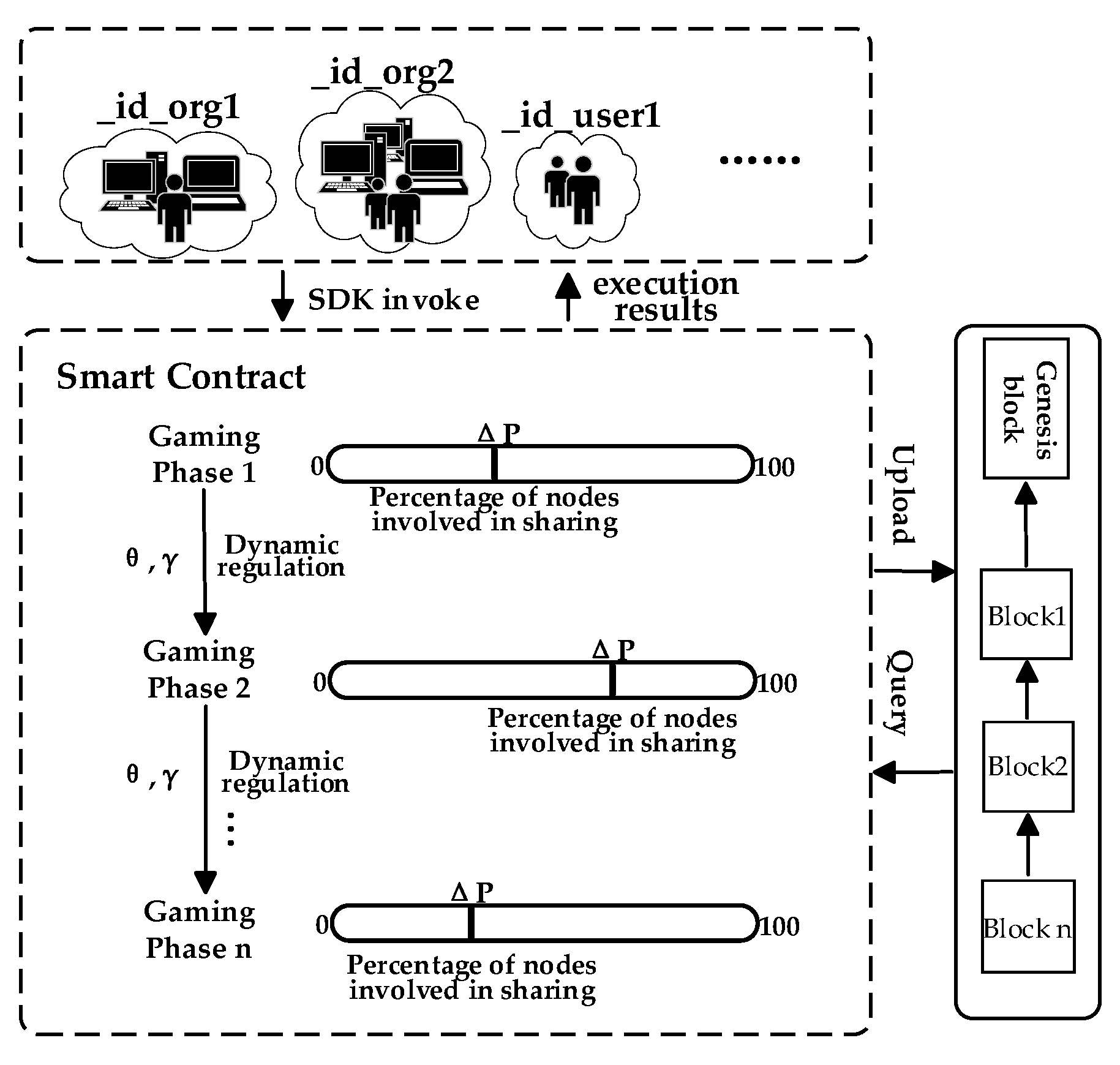
4. Threat Intelligence Sharing Incentive Smart Contracts
4.1. Smart Contract Algorithm
| Algorithm 1 shared game mechanism |
| Input: |
| Parameters of the incentive strategy for the strategy case one condition |
| Output: |
| Threat intelligence sharing feedback, i.e., incentives or costs |
| 1: function SGM(_id, parameters of the first strategy) |
| 2: cert_data = load_certificate(signcert) //Get certificates |
| 3: Validate(cert_data) //Calibration certificate |
| 4: if true then //Authentication passed |
| 5: R = getUserInformation.rank //Node account level |
| 6: S_last = getPreviousparameter.s //cost-balancing parameter S |
| 7: T = getPreviousparameter.t //Shared saturation time |
| 8: S_new = N/T |
| 9: P = ParticipateSharingCnt //UsersCnt |
| 10: if P < P* then |
| 11: feedback = IncentiveReward //This is motivation at this moment |
| 12: else if P > SaturationRate then |
| 13: k = k + 1 //Gaming rounds self-added |
| 14: ParticipateSharingCnt = 0 |
| 15: end if |
| 16: feedback = Cost //This is cost at this moment |
| 17: return feedback |
| 18: end if |
| 19: end function |
| Algorithm 2 negative shared punishment |
| Input: |
| Node certificate,signcert //Node identity certificate |
| Node account rank,rank //Node account level |
| Integral count,Count //Nodes points |
| Last shared time,last_time //Last shared time |
| Output: |
| new_count //Updated node points |
| 1: function NSP(signcert, rank, Count,last_time) |
| 2: setClock() //Set the clock to trigger automatically |
| 3: time = new Date() //Current time |
| 4: for id in id_list do |
| 5: info = getUserInfo(id) //Get node information |
| 6: if time − last_time > T then |
| 7: u = (time − last_time) − T |
| 8: new_count = count − u |
| 9: else |
| 10: u = 0 |
| 11: new_count = count − u |
| 12: end if |
| 13: return new_count |
| 14: end for |
| 15: end function |
4.2. Smart Contracts Deployment
5. Experiment Analysis
5.1. ESS Validation Analysis
5.2. Incentive Validation Analysis
5.3. Comparative Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- van Haastrecht, M.; Golpur, G.; Tzismadia, G.; Kab, R.; Priboi, C.; David, D.; Racataian, A.; Baumgartner, L.; Fricker, S.; Ruiz, J.F. A Shared Cyber Threat Intelligence Solution for SMEs (vol 10, 2913, 2021). Electronics 2022, 11, 349. [Google Scholar] [CrossRef]
- Cha, J.; Singh, S.K.; Pan, Y.; Park, J.H. Blockchain-based cyber threat intelligence system architecture for sustainable computing. Sustainability 2020, 12, 6401. [Google Scholar] [CrossRef]
- Brown, R.; Lee, R.M. The Evolution of Cyber Threat Intelligence (cti): 2019 Sans Cti Survey. SANS Institute. 2019. Available online: https://www.sans.org/white-papers/38790/ (accessed on 12 July 2021).
- Riesco, R.; Larriva-Novo, X.; Villagrá, V.A. Cybersecurity threat intelligence knowledge exchange based on blockchain: Proposal of a new incentive model based on blockchain and Smart contracts to foster the cyber threat and risk intelligence exchange of information. Telecommun. Syst. 2020, 73, 259–288. [Google Scholar] [CrossRef]
- Lin, S.; Yin, J.; Pei, Q.; Wang, L.; Wang, Z. A Nested Incentive Scheme for Distributed File Sharing Systems. In Proceedings of the 2021 IEEE International Conference on Smart Internet of Things (SmartIoT), Jeju, Republic of Korea, 13–15 August 2021; pp. 60–65. [Google Scholar]
- Wagner, T.D.; Mahbub, K.; Palomar, E.; Abdallah, A.E. Cyber threat intelligence sharing: Survey and research directions. Comput. Secur. 2019, 87, 101589. [Google Scholar] [CrossRef]
- Tounsi, W.; Rais, H. A survey on technical threat intelligence in the age of sophisticated cyber attacks. Comput. Secur. 2018, 72, 212–233. [Google Scholar] [CrossRef]
- Sakellariou, G.; Fouliras, P.; Mavridis, I.; Sarigiannidis, P. A Reference Model for Cyber Threat Intelligence (CTI) Systems. Electronics 2022, 11, 1401. [Google Scholar] [CrossRef]
- Saxena, R.; Gayathri, E. Cyber threat intelligence challenges: Leveraging blockchain intelligence with possible solution. Mater. Today Proc. 2022, 51, 682–689. [Google Scholar] [CrossRef]
- Schlette, D.; Caselli, M.; Pernul, G. A comparative study on cyber threat intelligence: The security incident response perspective. IEEE Commun. Surv. Tutor. 2021, 23, 2525–2556. [Google Scholar] [CrossRef]
- Strom, B.E.; Applebaum, A.; Miller, D.P.; Nickels, K.C.; Pennington, A.G.; Thomas, C.B. Mitre att&ck: Design and philosophy. In Technical Report; The MITRE Corporation: Bedford, MA, USA, 2018. [Google Scholar]
- Lin, Y.; Liu, P.; Wang, H.; Wang, W.; Zhang, Y. Overview of Threat Intelligence Sharing and Exchange in Cybersecurity. J. Comput. Res. Dev. 2020, 57, 2052. [Google Scholar] [CrossRef]
- Amaro, L.J.B.; Azevedo, B.W.P.; de Mendonca, F.L.L.; Giozza, W.F.; Albuquerque, R.D.O.; Villalba, L.J.G. Methodological Framework to Collect, Process, Analyze and Visualize Cyber Threat Intelligence Data. Appl. Sci. 2022, 12, 1205. [Google Scholar] [CrossRef]
- Purohit, S.; Neupane, R.; Bhamidipati, N.R.; Vakkavanthula, V.; Wang, S.; Rockey, M.; Calyam, P. Cyber threat intelligence sharing for co-operative defense in multi-domain entities. IEEE Trans. Dependable Secur. Comput. 2022, 1–18. [Google Scholar] [CrossRef]
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where Is Current Research on Blockchain Technology?—A Systematic Review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef] [PubMed]
- Nakamoto, S. A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 3 April 2023).
- Sofia, D.; Lotrecchiano, N.; Trucillo, P.; Giuliano, A.; Terrone, L. Novel Air Pollution Measurement System Based on Ethereum Blockchain. J. Sens. Actuator Netw. 2020, 9, 49. [Google Scholar] [CrossRef]
- Aladhadh, S.; Alwabli, H.; Moulahi, T.; Al Asqah, M. BChainGuard: A New Framework for Cyberthreats Detection in Blockchain Using Machine Learning. Appl. Sci. 2022, 12, 12026. [Google Scholar] [CrossRef]
- Szabo, N. Smart contracts: Building blocks for digital markets. EXTROPY J. Transhumanist Thought 1996, 18, 28. [Google Scholar]
- Alabdulatif, A.; Al Asqah, M.; Moulahi, T.; Zidi, S. Leveraging Artificial Intelligence in Blockchain-Based E-Health for Safer Decision Making Framework. Appl. Sci. 2023, 13, 1035. [Google Scholar] [CrossRef]
- Liang, X.; Yan, Z.; Kantola, R. GAIMMO: A Grade-Driven Auction-Based Incentive Mechanism with Multiple Objectives for Crowdsourcing Managed by Blockchain. IEEE Internet Things J. 2022, 9, 17488–17502. [Google Scholar] [CrossRef]
- Ai, Z.; Liu, Y.; Wang, X. ABC: An auction-based blockchain consensus-incentive mechanism. In Proceedings of the 2020 IEEE 26th International Conference on Parallel and Distributed Systems (ICPADS), Hong Kong, China, 2–4 December 2020; pp. 609–616. [Google Scholar]
- Cheng, G.; Deng, S.; Xiang, Z.; Chen, Y.; Yin, J. An auction-based incentive mechanism with blockchain for iot collaboration. In Proceedings of the 2020 IEEE International Conference on Web Services (ICWS), Beijing, China, 19–23 October 2020; pp. 17–26. [Google Scholar]
- Ding, X.; Guo, J.; Li, D.; Wu, W. An incentive mechanism for building a secure blockchain-based internet of things. IEEE Trans. Netw. Sci. Eng. 2020, 8, 477–487. [Google Scholar] [CrossRef]
- Zhang, B.J.; Guo, K.W.; Hu, K. Research on Data Sharing Incentive Mechanism Based on Smart Contract. Comput. Eng. 2022, 48, 37–44. [Google Scholar] [CrossRef]
- Motepalli, S.; Jacobsen, H.-A. Reward mechanism for blockchains using evolutionary game theory. In Proceedings of the 2021 3rd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2021; pp. 217–224. [Google Scholar]
- Tanimoto, J. Fundamentals of Evolutionary Game Theory and Its Applications; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Herbert Gintis Game Theory Evolving: A Problem-Centered Introduction to Modeling Strategic Interaction; China Renmin University Press: Beijing, China, 2015.
- Zhang, W.Y. Game Theory and Intelligence Economics; Shanghai People’s Publishing House: Shanghai, China, 1990. [Google Scholar]
- Mohanta, B.K.; Panda, S.S.; Jena, D. An Overview of Smart Contract and Use Cases in Blockchain Technology. In Proceedings of the 2018 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Bengaluru, India, 10–12 July 2018; pp. 1–4. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Al-Ibrahim, O.; Mohaisen, A.; Kamhoua, C.; Kwiat, K.; Njilla, L. Beyond Free Riding: Quality of Indicators for Assessing Participation in Information Sharing for Threat Intelligence. arXiv 2017, arXiv:1702.00552. [Google Scholar] [CrossRef]






| Participating Node 1 | Participating Node 2 | |
|---|---|---|
| Shared | Unshared | |
| shared | ||
| unshared | ||
| Smart Contract | Language | Compiler Version | Gas Cost (gwei) | Run Time (ms) |
|---|---|---|---|---|
| SGM | Solidity | 0.8.13 | 244,520 | 765 |
| NSP | Solidity | 0.8.13 | 27,513 | 593 |
| Strategy Case 1 | 4 | 2 | 10 | 1 | 2 | 8 | 0.25 |
| Strategy Case 2 | 4 | 2 | 4 | 1 | 4 | 0.2 | 0.25 |
| Strategy Case 3 | 4 | 2 | 10 | 1 | 7 | 8 | 0.25 |
| Other Parameters | Other Parameters | ||
|---|---|---|---|
| Same as strategy case 1 | 0 | Same as strategy case 1 | −8 |
| 1 | −4 | ||
| 2 | 0 | ||
| 3 | 3 | ||
| 4 | 6 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ma, X.; Yu, D.; Du, Y.; Li, L.; Ni, W.; Lv, H. A Blockchain-Based Incentive Mechanism for Sharing Cyber Threat Intelligence. Electronics 2023, 12, 2454. https://doi.org/10.3390/electronics12112454
Ma X, Yu D, Du Y, Li L, Ni W, Lv H. A Blockchain-Based Incentive Mechanism for Sharing Cyber Threat Intelligence. Electronics. 2023; 12(11):2454. https://doi.org/10.3390/electronics12112454
Chicago/Turabian StyleMa, Xingbang, Dongsheng Yu, Yanhui Du, Lanting Li, Wenkai Ni, and Haibin Lv. 2023. "A Blockchain-Based Incentive Mechanism for Sharing Cyber Threat Intelligence" Electronics 12, no. 11: 2454. https://doi.org/10.3390/electronics12112454
APA StyleMa, X., Yu, D., Du, Y., Li, L., Ni, W., & Lv, H. (2023). A Blockchain-Based Incentive Mechanism for Sharing Cyber Threat Intelligence. Electronics, 12(11), 2454. https://doi.org/10.3390/electronics12112454





