Abstract
Massive machine type communications or internet of things (IoT) over wireless systems have invoked attention in terms of security problems, especially for multi-input multi-output (MIMO) schemes. In this paper, we propose efficient physical layer security (PLS) enhancing methods for space-time block coding (STBC), as well as spatial multiplexing (SM) schemes. The proposed methods pre-distort the transmit signals by using the phase information of the legitimate MIMO channel, and, as a result, the illegal eavesdropper cannot extract any information. The proposed predistortion for the STBC schemes is done so that the channel matrix at the receiver is a real-valued one, which results in full-rate and full-diversity gain for more than two transmit antennae. Therefore, compared to the conventional schemes, the proposed scheme eventually leads to the higher performance gain and lower detection complexity in addition to the high security protection. By extending the principle of the proposed method for STBC, a predistortion scheme is also proposed for SM by using the phase information of the column space of the channel matrix. The simulation results investigated in this paper reveal that the proposed methods can achieve enhanced error rate performances, as well as high security protection.
1. Introduction
The multi-input multi-output (MIMO) scheme is one of the most representative technologies in modern wireless communication systems, including wireless LAN as well as 4G to beyond 5G systems. To date, most of the physical layer technologies for MIMO systems have prioritized performance and capacity issues over security protection. However, dramatically increasing traffic demands, especially of machine-type communications, require more secure communication for privacy protection. Therefore, a number of studies have emphasized the importance of physical layer security (PLS) schemes for modern wireless communication systems [1,2], and there have been many proposals concentrating on the signal design for MIMO systems [3,4,5,6,7,8,9,10,11].
Techniques to add artificial noise (AN) have been considered as an effective means to protect the legitimate channel [3,4,5,6,7,8]. A typical design principle of AN is to make it orthogonal to the legitimate channel, so that it can be null to the legitimate receiver, while serving as interference to the illegal receiver [3]. Then, this idea of adding AN was applied to spatial modulation and space time block coding (STBC) schemes in [4,5,6,7,8], respectively, for PLS. However, adding AN obviously requires additional energy, which decreases the energy efficiency. Because of this, a recent study proposed the idea of adding artificial interference (AI), which can be considered as the channel dependent re-distribution of signal power, and this, therefore, accomplishes security protection without requiring any additional energy [9]. All of these ideas of adding AN or AI utilize the addition or re-distribution of channel-dependent power at the transmitter, which results in a seriously high peak-to-average power ratio (PAPR) problem.
To avoid the high PAPR problem, ideas that involve distorting the phase of the complex signal have been proposed [10,11]. For example, a phase rotation method has been applied to the STBC schemes to enhance secrecy [10], but the randomness of the phase distortion to the eavesdropper is only guaranteed by the additional secret key exchange between the legitimate transmitter and receiver. Meanwhile, a phase rotation technique was applied to the spatial modulation scheme to increase secrecy performance without risking any PAPR problem [11]. In these schemes, the secrecy protection capability is limited by the number of antennae and the modulation order employed.
In this paper, we propose novel secrecy enhancing methods for MIMO schemes. We consider that full-rate orthogonal STBC (O-STBC) schemes exist for instances employing more than two transmit antennae when real-numbered signals are used [12]. The proposed scheme first forms a full-rate non-orthogonal STBC encoding matrix, and then applies signal distortion for PLS in such a way as to make the channel matrix at the receiver fully orthogonal. Therefore, we can have a full-rate encoding matrix at the transmitter and a fully orthogonal channel matrix at the receiver. In addition to high secrecy protection, this leads to high performance gain due to higher diversity gain than the conventional methods. By extending this to the spatial multiplexing (SM) MIMO scheme, we design a new predistortion scheme.
The main contributions of this paper compared to the conventional schemes can be summarized as follows:
- Compared to the conventional AN or AI-aided schemes [3,4,5,6,7,8,9], the proposed methods distort the phase of the transmit signal, and they therefore avoid the PAPR problem and do not require additional energy for AN.
- Compared to the conventional phase-distortion based schemes [10,11], the proposed methods do not require an additional secret key exchange and have no limit on the secrecy protection capability.
- Compared to the conventional STBC schemes [12,13,14,15], the proposed scheme not only provides better bit error rate (BER) performance at the same rate (or can achieve the same performance at a higher rate), but it can also achieve high security protection. In addition, the complexity of the detection process can be reduced due to the use of the real-numbered channel matrix.
This paper is organized as follows. Following this introduction, Section 2 reviews the related works. After presenting the concept of PLS schemes with AN and AI, the concept of O-STBC for real-numbered signals is introduced. Section 3 describes the proposed scheme. Section 4 presents the simulation results and discussions, and finally, Section 5 draws the conclusion.
Notation: Bold lower and upper case letters represent vectors and matrices, respectively. and represent the transpose and Hermitian transpose of a matrix , respectively. For a column vector, a, diag(a) returns a square diagonal matrix with the elements of vector a on the main diagonal. For a modulated signal, x denotes a real-numbered signal while z denotes a complex-numbered signal. and denote the absolute value and conjugate of a complex number z, respectively.
2. Related Works
2.1. Adding AN to STBC MIMO Schemes for Secrecy Enhancing
We consider a multi-input-single-output (MISO) wiretap channel, which includes a transmitter Alice with transmit antennae, a legitimate receiver Bob, and a passive eavesdropper Eve. Let and respectively denote the channel state information (CSI) vectors of Bob and Eve, where and represent the complex channel gains for the k-th transmit antenna from Alice to Bob and Eve, respectively. The perfect CSI is assumed to be available at both Bob and Eve, but Alice only shares the CSI with Bob. It is also assumed that the channel states of and are independent of each other. For the purpose of employing AN [7], the Alamouti scheme is adopted with the following encoding matrix, [13],
where and are the signals transmitted during the two symbol periods. Prior to transmission, Alice adds the following AN, , to :
where is the complex Gaussian AN with zero-mean and unit variance and s are the coefficients of the for the i-th time slot at the k-th antenna, which are designed to be nulled at Bob. Therefore, one of the possible coefficients sets can be , , , and [7].
Then, Alice transmits and the received signal vectors at Bob and Eve during the two symbol periods, and can, respectively, be expressed by:
where and are additive white Gaussian noise (AWGN) vectors at Bob and Eve, respectively. Since the AN is designed to be nulled out at Bob, Bob received as if Alice transmitted without any AN. Meanwhile, since the channel gains and are independent of each other, Eve cannot retrieve any signal due to uncancelled .
Because this method requires additional energy for AN, a new method was proposed that does not require any additional energy for secrecy protection. The idea of this proposed method is to utilize the quasi-orthogonal STBC (QO-STBC) scheme with linear detection capability, called linear decoding QO-STBC (LD-QO-STBC) [15], and to re-allocate the signal power across the transmission time and antennae [9].
2.2. O-STBC for Real-Numbered Signals
Even though the full-rate O-STBC scheme for complex-numbered signals only exists for the two transmit antennae system [13], it is well known that it can be designed for more than two transmit antennae for real-numbered signals, such as pulse-amplitude modulation (PAM) [12]. The encoding matrices of the full-rate O-STBC schemes for p time periods and transmit antennae, of size , can be found in the literature [12]; here we provide the following examples for and 8:
where are real-numbered signals. It is clear that the s in (4) and (5) are orthogonal matrices. In addition, they achieve the full rate, i.e., , because they are constituted by the transmit signal vector with p symbols over p time periods. Therefore, they can offer the full-diversity of due to the orthogonality as well as full-rate [12].
Assuming the signal vector is transmitted using via transmit antennae, the received signal vector can be expressed as:
where is the complex channel gain from the k-th transmit antenna to the receiver and is an AWGN vector. Then, the above (6) can be equivalently expressed by:
where is a complex-numbered channel matrix and is therefore not an orthogonal matrix. For example, the corresponding to the encoding matrix, of (4) can be given by:
Even though the above with complex elements does not have full-orthogonality, a linear decoding can be performed for real number signal detection as follows:
where is the estimated result of . This is because the diagonal elements of the Gram matrix, , are pure real numbers, while the off-diagonal elements are pure imaginary numbers which do not affect the real number signal detection.
3. The Proposed Methods
3.1. Secrecy Enhancement for STBC Schemes
Motivated by the fact that a full-rate O-STBC scheme can be achieved for real-numbered signal transmission through the use of more than two transmit antennae [12], we propose an efficient PLS scheme for STBC.
In the proposed scheme, we first form a non-orthogonal full-rate encoding matrix for complex-numbered signals by inserting complex signals into . Then, the proposed scheme transforms the encoding matrix using a phase distortion matrix which represents the null space of the phase of the channel gain. During the transmission, the channel phase will be nulled out, and eventually only the amplitude component of the channel gain will arrive at the receiver. Therefore, we can have a full orthogonal real-numbered channel matrix at the receiver. Even though the encoding matrix with complex numbered signals is not orthogonal, the proposed scheme can achieve performance equivalent to that of the scheme with full-rate and full-diversity. It can also achieve high secrecy protection.
Here, we detail the operational principle of the proposed scheme. At the transmitter, Alice first generates a complex signal vector for p time periods and constructs a non-orthogonal encoding matrix by inserting complex signals into . For example, the following can be found for a system with four transmit antennae.
Note that keeps full-rate but is not orthogonal.
Next, the transmitting signals are predistorted so as to null out the phase of the channel gain. To this end, we form a phase-distorting vector, , as follows:
where represents the phase of . The next step is to determine the encoding matrix with the predistortion capability, , as follows:
where is the k-th column vector of . Note that multiplying to will lead to nulling of the phase of the complex channel gain for at Bob.
Finally, the received signal vector at Bob for p time periods can be represented by:
because and . Further, can be equivalently expressed by using a channel matrix as follows:
where the channel matrix results in a real-numbered orthogonal matrix. For example, when we apply the of (10), the corresponding results in:
Because the is a real-numbered matrix and has full-orthogonality, the complex signal detection at Bob can be easily performed by multiplying the transpose of . This will eliminate any complex inversion operation of the matrix, and it will lead to the following simple real-numbered matrix multiplication to obtain the recovered signal at Bob, :
Note that the Gram matrix in (16), , is a diagonal matrix, and thus there is no interference term for signal detection.
On the other hand, the received signal at Eve can be represented by:
Because contains distortion factors that cannot be nulled out at Eve, the non-diagonal Gram matrix of Eve results in signal detection that cannot be performed properly. Although we have shown the example of a system, the proposed idea can be applied to obtained from for systems with more than two transmit antennae.
3.2. Secrecy Enhancement for Spatial Multiplexing
We consider a wiretap SM MIMO system with transmit antennae at Alice as well as receive antennae at Bob and Eve, respectively. In this system, Alice transmits spatially multiplexed complex signal vector via the antennae for each time period. Then, is transmitted through the channel matrices of and at Bob and Eve, respectively, where and respectively denote the k-th column vectors of and . We propose a new PLS scheme for this environment.
By considering that the k-th signal component of , will be transmitted through to Bob, the proposed PLS scheme applies phase distortion to by using the sum of the channel phases of . For this purpose, the phase distorting vector, , is first found as follows:
where
and and are the complex channel gain from the k-th transmit antenna to the i-th receive antenna and its phase, respectively.
Next, the pre-distorted signal vector at Alice, , can be found as follows:
Then, the received signal at Bob can be represented by:
where the resulting channel matrix can be represented by:
Therefore, the signal detection can be achieved by using various well known detection methods, as follows:
where is a detection matrix, e.g., for zero forcing (ZF) detection and for minimum mean square error (MMSE) detection, where is the noise variance and is the identity matrix. On the other hand, the received signal at Eve is represented by:
As in the previous case for STBC schemes, contains -dependent distortion, and as a result, Eve cannot retrieve any information on the signal.
4. Simulation Results
We estimate the performance simulation results of the proposed schemes over a Rayleigh fading environment in comparison to the conventional STBC and SM schemes. In the simulations, we assume that the power of the modulation symbols was normalized to one. Figure 1 shows a comparison of the signal constellation change in the QPSK modulation scheme, when PLS schemes are applied for STBC schemes. If AN or AI is used to enhance secrecy [7,9], the amplitude of the signal varies greatly, which will lead to a high PAPR problem at the transmitter. On the other hand, due to its phase distortion characteristics, the proposed scheme maintains constant amplitude value, and it will therefore not suffer from a high PAPR problem.
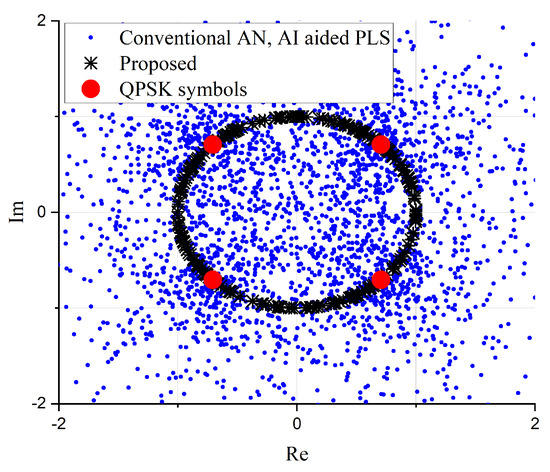
Figure 1.
Signal constellation comparison at the transmitter.
Figure 2 shows the BER performance comparison for various STBC schemes with QPSK modulation. Without any secrecy enhancing schemes, Bob and Eve are expected to achieve exactly the same BER performance. The conventional secrecy enhancing scheme with the Alamouti scheme can achieve excellent security protection by making the BER at Eve so bad that it is almost impossible for Eve to extract information [7]. However, this scheme involves sacrificing a power loss of 3 dB for AN to obtain high secrecy protection from Eve. We also note that these AN (or AI)-aided PLS schemes involve a trade-off between the power allocated to AN (or AI) and secrecy protection.
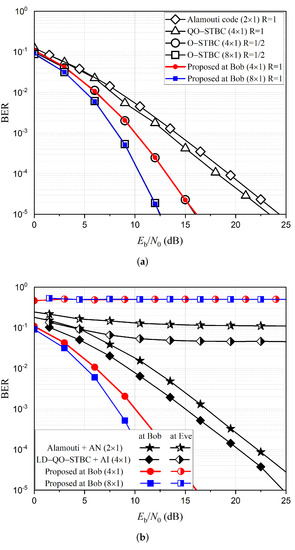
Figure 2.
BER performance comparison for various STBC schemes. (a) without PLS. (b) with PLS.
On the other hand, the proposed scheme maintains high secrecy protection, and it also achieves BER performance comparable to that of the conventional full-rate or full-diversity scheme without any additional power allocation. The BER performance of the proposed scheme shows exactly the same performance as the half rate O-STBC scheme, indicating that it achieves full diversity, even with . In addition, the BER performance at Eve with the proposed scheme shows that the proposed scheme does not allow any information leakage to Eve.
To evaluate the performance of the SM schemes, we use the 4 × 4 MIMO systems with QPSK and 16-QAM, respectively. Figure 3 shows the BER performance comparison with the ZF and MMSE detection schemes. As in the previous case, the conventional schemes without any secrecy enhancing capability lead to the same BER performance at Bob and Eve. The BER performance of the proposed scheme at Bob shows exactly the same performance as the conventional schemes, while the BER performance at Eve is highly deteriorated, indicating that it is almost impossible for Eve to properly extract information.
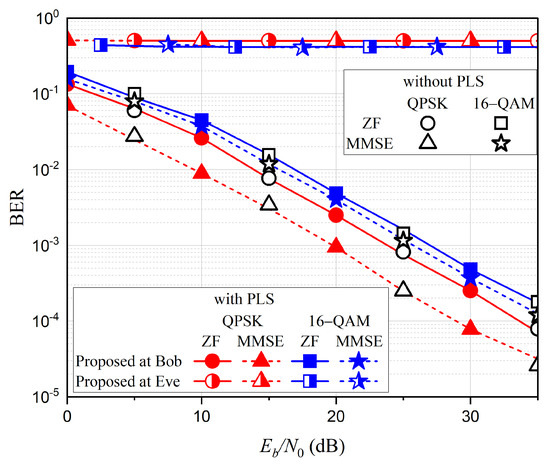
Figure 3.
BER performance comparison for various SM schemes.
We also investigate the influence of channel estimation error on BER performance. At this time, signals are transmitted through the channel with , where is an estimated channel gain, e is the estimation error, and is the variance of estimation error [16]. Figure 4 shows the BER performance changes for various STBC schemes according to . As can be seen in the figure, as increases, the proposed method for rate one STBC shows worse performance than the conventional O-STBC scheme with rate 1/2. This is because the phase distortion cannot be perfectly nulled out at the receiver in the proposed scheme, which results in a non-orthogonal channel matrix. Nevertheless, the proposed scheme still shows better performance than the conventional QO-STBC scheme with the same rate, and it also provides high security protection. On the other hand, Figure 5 shows the proposed method for SM achieves the same performance behavior as the conventional schemes. The results confirm that the proposed methods are not particularly vulnerable to channel estimation error relative to other conventional methods.
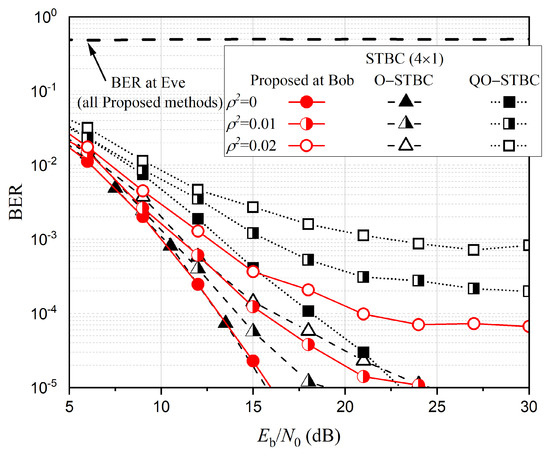
Figure 4.
BER performance comparison of various STBC schemes with channel estimation error.
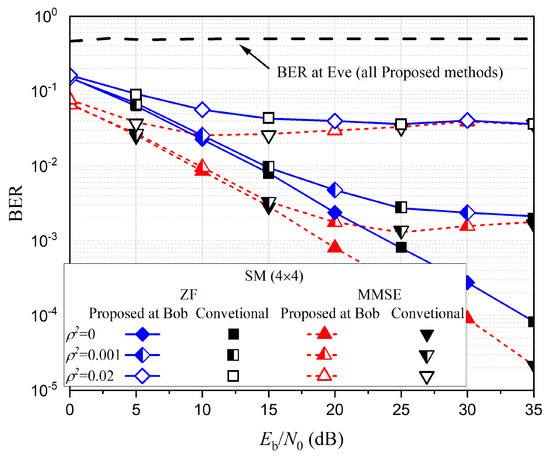
Figure 5.
BER performance comparison of various SM schemes with channel estimation error.
To compare a security capability of PLS schemes, the secrecy capacity has usually been investigated in the previous studies [3,9,17]. Here we first present the equations for the secrecy capacities of the proposed and conventional PLS schemes. The secrecy capacity can be defined as follows:
where and are the capacities at Bob and Eve, respectively. For conventional AN (or AI)-aided schemes [7,9], the capacity at Bob, can be represented as:
where represents the variance of AWGN at Bob. On the other hand, Eve suffers from the noise effect of uncanceled as well as AWGN, that is,
and thus, should be treated as noise in addition to AWGN. The capacity at Eve for AN (or AI)-aided schemes, , can be estimated as follows:
where represents the variance of AWGN at Eve.
In the case of the proposed method, the detector at Eve cannot discriminate signal components inside in (17), since the signal is distorted by unknown phase information at Alice. That is,
and thus there is no pure signal component inside . Therefore, the capacities at Bob and Eve for the proposed method can be represented as follows:
This eventually leads to of 0, and this can be confirmed from the BER simulation results shown in Figure 2b. The result shows that BER at Eve is 0.5 regardless of signal to noise ratio (SNR) values, showing no information leakage to Eve.
We evaluate the capacities of various PLS schemes by using the above derived equations, and Figure 6 presents the capacity comparisons of PLS schemes at Bob and Eve. Since the proposed method does not consume any additional power for PLS, the capacity of the proposed method at Bob accomplishes the highest, while the capacity of the proposed method at Eve is the lowest that is always zero. The capacity of the existing AN method at Bob shows about 3 dB power loss compared to the proposed method because of the power consumption for AN. On the other hand, the existing AI method barely consumes extra energy, and thus it achieves almost the same capacity as the proposed method at Bob. Nevertheless, Eve also can accomplish better capacity performance with the AI method since the energy consumed for AI is much less than that for AN. This can also be confirmed in Figure 2b, where the BER performance of the AI method is better than that of AN, at Eve.
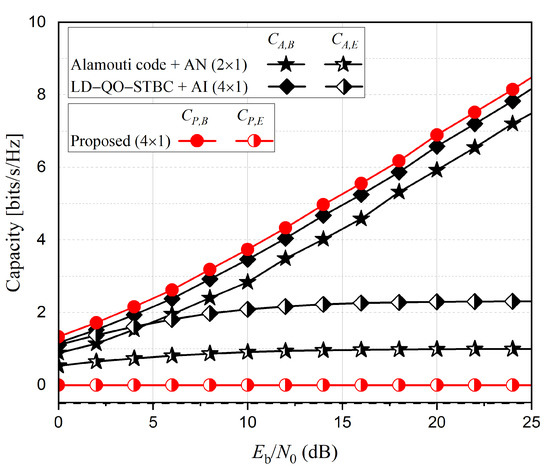
Figure 6.
Capacity comparison of various PLS schemes at Bob and Eve.
Figure 7 shows the secrecy capacity comparison of the proposed and AN (or AI)-aided PLS schemes. It reveals that the secrecy capacity of the proposed method shows the best performance due to the best and worst capacities at Bob and Eve, respectively, as shown in Figure 6. On the other hand, the conventional AN scheme should sacrifice secrecy capacity due to additional power consumption. We note that the AN method achieves better secrecy capacity than the AI method. This is because the difference in capacities between Bob and Eve is smaller in the AI method compared to that in the AN method.
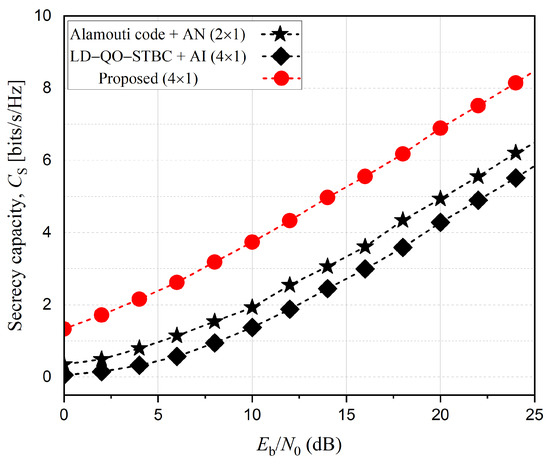
Figure 7.
Secrecy capacity comparison of various PLS schemes.
5. Conclusions and Discussion
This paper proposed efficient PLS schemes for STBC and SM-based MIMO systems. Compared to the conventional AN-based PLS scheme, the proposed schemes neither require additional power nor have a PAPR problem, because they distort the phase of the complex signals. The performance simulation results showed that, in addition to high security protection, the proposed scheme for the STBC-based MIMO system achieves BER performance approximating those of the conventional schemes with full rate or full orthogonality. The proposed scheme for the SM-based MIMO system also showed almost no information leakage to the illegal eavesdropper.
The proposed scheme requires accurate CSI at both the transmitter and the receiver, which may not be the common assumption for the STBC-based MIMO systems. The future work should focus on other alternative methods which do not require CSI at the transmitter, by considering STBC as a transmit diversity technique. In addition, we investigated the effect of CSI estimation error by using a commonly used model, but the estimation error accumulation effect may impact further on the performance of the proposed SM-based MIMO scheme. Hence, future work should focus on detailed investigation on the effect of imperfect channel information, leading to more efficient PLS schemes.
Author Contributions
Conceptualization, H.L. and S.C.; methodology, H.L. and S.C.; validation, H.L. and S.K.; formal analysis, H.L.; investigation, H.L.; writing—original draft preparation, H.L.; writing—review and editing, S.K.; supervision, S.K.; project administration, S.K.; funding acquisition, S.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (NRF-2021R1A2C1003121).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| AI | artificial interference |
| AN | artificial noise |
| AWGN | additive white Gaussian noise |
| BER | bit error rate |
| CSI | channel state information |
| IoT | internet of things |
| LD-QO-STBC | linear decoding QO-STBC |
| MIMO | multi-input multi-output |
| MISO | multi-input-single-output |
| MMSE | minimum mean square error |
| O-STBC | orthogonal STBC |
| PAM | pulse-amplitude modulation |
| PAPR | peak-to-average power ratio |
| PLS | physical layer secrecy |
| QO-STBC | quasi-orthogonal STBC |
| SM | spatial multiplexing |
| SNR | signal to noise ratio |
| STBC | space-time block coding |
| ZF | zero forcing |
References
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.-K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef] [Green Version]
- Sanenga, A.; Mapunda, G.A.; Jacob, T.M.L.; Marata, L.; Basutli, B.; Chuma, J.M. An Overview of Key Technologies in Physical Layer Security. Entropy 2020, 22, 1261. [Google Scholar] [CrossRef] [PubMed]
- Negi, R.; Goel, S. Secret Communication using Artificial Noise. In Proceedings of the VTC-2005-Fall, 2005 IEEE 62nd Vehicular Technology Conference, Dallas, TX, USA, 28 September 2005. [Google Scholar]
- Yang, P.; Qiu, X.; Mu, F. Artificial Noise-Aided Secure Generalized Spatial Modulation for Multiuser Transmission. IEEE Wirel. Commun. Lett. 2020, 24, 2416–2420. [Google Scholar] [CrossRef]
- Shang, P.; Yu, W.; Zhang, K.; Jiang, X.-Q.; Kim, S. Secrecy Enhancing Scheme for Spatial Modulation Using Antenna Selection and Artificial Noise. Entropy 2019, 21, 626. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Allen, T.; Tajer, A.; Al-Dhahir, N. Secure Alamouti Multiple Access Channel Transmissions: Multiuser Transmission and Multi-Antenna Eavesdroppers. IEEE Wirel. Commun. Lett. 2019, 8, 1510–1513. [Google Scholar] [CrossRef]
- Shang, P.; Kim, S.; Jiang, X.-Q. Efficient Alamouti-Coded Spatial Modulation for Secrecy Enhancing. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 16–18 October 2019. [Google Scholar]
- Fakoorian, S.A.A.; Jafarkhani, H.; Swindlehurst, A.L. Secure space-time block coding via artificial noise alignment. In Proceedings of the 2011 Conference Record of the Forty Fifth Asilomar Conference on Signals, Systems and Computers (ASILOMAR), Montreal, CQ, Canada, 6–9 November 2011. [Google Scholar]
- Shang, P.; Lee, H.; Kim, S. Waveform Design for Space–Time Coded MIMO Systems with High Secrecy Protection. Electronics 2020, 9, 2003. [Google Scholar] [CrossRef]
- Allen, T.; Cheng, J.; Al-Dhahir, N. Secure Space-Time Block Coding without Transmitter CSI. IEEE Wirel. Commun. Lett. 2014, 3, 573–576. [Google Scholar] [CrossRef]
- Jiang, X.-Q.; Wen, M.; Hai, H.; Li, J.; Kim, S. Secrecy-Enhancing Scheme for Spatial Modulation. IEEE Commun. Lett. 2018, 22, 550–553. [Google Scholar] [CrossRef]
- Tarokh, V.; Jafarkhani, H.; Calderbank, A.R. Space-time block codes from orthogonal designs. IEEE Trans. Inform. Theory 1999, 45, 1456–1467. [Google Scholar] [CrossRef]
- Alamouti, S.M. A simple transmit diversity technique for wireless communications. IEEE J. Sel. Areas Commun. 1998, 16, 1451–1458. [Google Scholar] [CrossRef]
- Tirkkonen, O.; Boariu, A.; Hottinen, A. Minimal nonorthogonality rate 1 space-time block code for 3+ Tx antennas. In Proceeding of the 2000 IEEE Sixth International Symposium On Spread Spectrum Techniques and Applications, Parsippany, NJ, USA, 6–8 September 2000. [Google Scholar]
- Lee, Y.; Uh, M.; Chang, S. Comments and Corrections on “A Novel QO-STBC Scheme With Linear Decoding for Three and Four Transmit Antennas”. IEEE Commun. Lett. 2016, 20, 1908–1909. [Google Scholar] [CrossRef]
- Rezki, Z.; Khisti, A.; Alouini, M.-S. On the Secrecy Capacity of the Wiretap Channel with Imperfect Main Channel Estimation. IEEE Trans. Commun. 2014, 62, 3652–3664. [Google Scholar] [CrossRef] [Green Version]
- Oggier, F.; Hassbii, B. The secrecy capacity of the MIMO wiretap channel. IEEE Trans. Inf. Theory. 2011, 57, 4961–4972. [Google Scholar] [CrossRef] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).