Abstract
Security has always been an important aspect of wireless communications. Aiming at further improve the security of wireless communication and how to prevent eavesdropping, this paper proposes a constellation encryption design based on chaotic sequence and the RSA algorithm. The core idea of this method is to effectively combine both chaotic sequences and RSA, and then to generate large number of encrypted sequences with high security. The specific method is to first use the asymmetric RSA algorithm to transmit the system parameters, then to use the initial value sensitivity of the chaotic sequence to generate the secret sequence, and finally to use the secret sequence to encrypt the original sequence. Simulations show that the proposed algorithm further improves the security of satellite communications without increasing the complexity of the original system.
1. Introduction
Because satellite communication has many advantages, such as long communication distance, small restrictions and flexible signal configuration, it is widely used in communication broadcasting, secure communication, positioning, navigation and other fields [1,2,3,4,5,6]. However, since the essence of satellite communication is wireless communication, the main problem is that communication signals are easily exposed to illegal interceptors in the process of wireless transmission, and the rapid improvement of computer data processing capabilities now means that the anti-interception ability of communication signals has improved. It is easy to cause potential security risks, especially in the field of military communications. If the concealment and security of the communication process cannot be guaranteed, it is possible to miss opportunities on the battlefield. Therefore, how todesign according to the characteristics of wireless communication is more secure. It is an urgent problem of wireless communication that needs to be solved in the future [7,8,9,10,11,12,13].
Low intercept probability communication is a comprehensive physical layer of wireless security technology, which guarantees the security of wireless communication from three levels: 1. Signal concealment to prevent communication signals from being discovered; 2. Feature hiding to prevent communication signal features from being extracted; 3. Information concealment to prevent communication information from being eavesdropped [14,15,16].
In Ref. [17], in order to improve the security of the physical layer, a novel chaotic technique was designed to make the symbol period change according to the behavior of the chaotic spreading sequence during communication. Ref. [18] proposed a new symbol-level constellation shift scheme based on phase ambiguity, so that the encrypted symbols are still on the ideal constellation points. However, the computational complexity still needs to be improved. The constellation is also mapped using digital chaos, adding a dynamic radius and phase offset to the standard constellation diagram [19], thus providing a high level of security during data transmission. However, under low signal-to-noise ratio conditions, it will affect the transmission’s reliability. Ref. [20] designed a fast, dual-polarization frequency hopping system and applied virtual polarization technology to satellite communication to enhance the secure transmission of the physical layer. In Ref. [21], a scheme based on constellation rotation and weighted fractional Fourier transform was proposed, so that the processed signal resembles a Gaussian distribution, which is not easy to detect. Additionally, the constellation points are also distorted to ensure strong confidentiality. Ref. [22] proposed a multiple encryption scheme, scrambled the already modulated symbols, and distributed them independently on the complex plane. Additionally, the dynamic parameters of the constellation shift were generated by 3-D hyper-digital chaos. Combining two asymmetric encryption algorithms, RSA (Rivest-Shamir-Adleman) and ECC (Ellipse Curve Ctyptography), generates a new hybrid key generation, which enhances the key strength in Ref. [23]. In Ref. [24], a six-dimensional model for generating chaotic sequences was first constructed, and encrypted sequences were generated according to the principles of the RSA asymmetric algorithm. In order to achieve better confidentiality of satellite communications and to improve the ability to resist interception, many methods have emerged at the level of physical layer encryption, but there are certain shortcomings in terms of high computational complexity, low reliability at low signal-to-noise ratios, and specific requirements for certain parameters. We found that chaos-based wireless secure communication systems and some algorithms in cryptography are widely used. This provided us with new ideas and methods. This paper combines the advantages of the algorithm so that it will not affect the judgment performance of the system and this further increases the interception resistance of the communication signal during transmission. The contributions made in this article are summarized below:
The contributions of this work are summarized as follows:
- The parameters transmitted by the asymmetric RSA algorithm directly affect the generation of the chaotic sequence, which increases the flexibility and security of the chaotic sequence as a secret sequence.
- The constellation encryption is directly performed using the secret sequence, so that the points on the constellation are not in the real position. In this process, the amplitude and phase of the constellation are not processed so that a better demodulation signal performance can be achieved, even under the conditions of a low signal-to-noise ratio.
- Using the secret sequence to directly encrypt the constellation, the obtained constellation diagram has the same shape as the unencrypted constellation diagram, so the illegal receiver cannot observe the constellation encryption from the constellation diagram, which improves the interception resistance of the satellite communication.
This paper proposes a constellation encryption design method, based on chaotic sequence and the RSA algorithm, that further improves the security of satellite communication. The remainder of this paper is as follows: Section 2 theoretically introduces the typical Logistic chaotic map and the RSA algorithm. Next, the design ideas and specific design steps of the proposed method are discussed in Section 3. Section 4 mainly provides a series of performance simulations on the design method of constellation encryption to verify the feasibility of the proposed design method. The last section draws conclusions from the prior discussion and experimental results.
2. Theoretical Content
2.1. Typical Chaotic Map
Logistic chaos is a mapping relationship of a typical chaotic sequence. As chaotic sequences have initial value sensitivity and parameter sensitivity, they are widely used in various encryption processes. Its mathematical formula is expressed as follows:
where µ is the system parameter, and the value range is . is the initial value, and the range of the values is (0,1). The bifurcation diagram of Logistic chaos is shown in Figure 1.
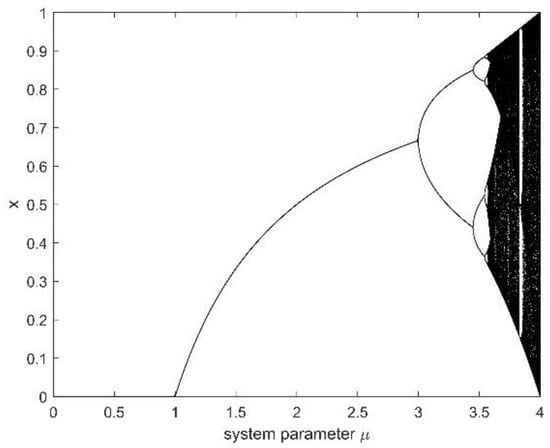
Figure 1.
Bifurcation diagram.
2.2. RSA Algorithm
2.2.1. The Process of RSA Algorithm
- (1)
- Arbitrarily choose two different prime numbers p and q to calculate the product , .
- (2)
- An integer e is arbitrarily selected, which must satisfy and , and the integer e is used as the encryption key.
- (3)
- Determine the decryption key d and satisfy .
- (4)
- The integers n and e are made public, and d is kept secret.
- (5)
- Encrypt plaintext m (m is an integer) into ciphertext c, use public key (n,e) for encryption, and encrypt algorithm .
- (6)
- Decrypt ciphertext c into plaintext m, use private key (n,d) for decryption, and decrypt algorithm (provided in Appendix A).
2.2.2. Security of RSA Algorithm
It is known, from the above steps, that a total of six numbers are involved, namely p, q, n, , e, and d. The public key uses two (n,e). The remaining four numbers are not public and the most critical is d.
Thus, consider whether to derive d, given the known public key (n,e)?
First step:
. e and need to be known.
Second step:
. p and q need to be known.
Third step:
. n needs to be factored.
Therefore, it can be concluded from the above analysis that if n can be factorized, d can be calculated, which means that the private key is cracked. The security of RSA depends on the factorization of large numbers, but whether it is equivalent to the factorization of large numbers has not been proven. The factorization of large numbers is a very difficult thing, and no other effective methods have been, found except for brute force.
3. The Proposed Design Method
3.1. Design Thinking
The chaotic sequence is iteratively generated by the deterministic equation, so that the receiver can reproduce the exact same sequence under the condition of mastering the parameters. At the same time, chaotic sequences are often used in the encryption process because they are sensitive to initial conditions and control parameters, and because they can generate a large number of different sequences. However, due to the influence of calculation accuracy, periodic characteristics will appear, which will have a great impact on the security of the communication system.
The RSA algorithm is often used in asymmetric encryption. It has a pair of public key and private key, and has the advantage of high cracking difficulty. Butthe secrecy strength of the RSA algorithm increases with the length of its key. Butthe longer the key, the longer it takes to encrypt and decrypt.
The idea of the design method we proposed is that the digitally modulated signal shows several fixed points on the constellation diagram. Such a fixed modulation method makes the communication parameters of the transmitted signal easy to decipher, which brings great challenges to wireless link transmission communication. Taking this as a starting point, chaotic sequences are used to scramble the constellation points, so that the points on the original constellation map lose their original physical significance, and achieve the purpose of physical layer encryption. The essence is to use the chaotic sequence to remap the constellation points according to certain rules, and the parameters generated by the chaotic sequence use the RSA algorithm, that is, combinethe advantages of the above two and avoid, their defects as much as possible.
The specific method is: we use the public key and the key to encrypt and decrypt the information at the sender and receiver, respectively. For partners, the rules and public keys for information encryption can be obtained. After the receiving end receives the signal, first demodulate it, then use the key and pre-agreed rules to decrypt it, and then continue to process the signal, the flowchart is shown in Figure 2 For non-cooperating parties, the difficulty of intercepting information comes from three aspects: First, there is no encryption rule; Second, it is unclear which chaotic map to use and the specific parameters; and Third, it is difficult to know how to solve the key.
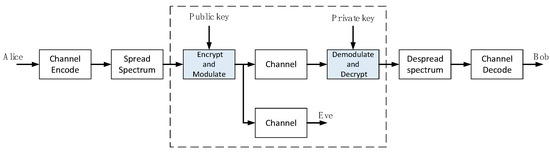
Figure 2.
Block diagram of the encrypted communication system.
The model we designed provides a set of constellation encryption flowcharts, in which both communicating parties have a lot of choice for the chaotic sequence used in encryption, and the parameters of the RSA algorithm can also be adjusted in real time, so the model has a strong flexibility, which further improves the anti-interception ability of information. At the same time, the simplicity of the entire model does not increase the computational complexity and does not reduce the reliability of communication under low signal-to-noise ratios. However, there are also some flaws, namely, the model is mainly designed for the sender and receiver, the channel only uses Gaussian white noise for scrambling, the whole process does not involve the synchronization of the transmit and receive time of the public key and the key and target signal, and the does not consider how to ensure that the ciphertext is not lost and distorted.
3.2. Specific Design Steps
The following section shows the complete block diagram and provides a detailed analysis of the encryption at the sender and decryption at the receiver.
3.2.1. Sender Encryption Steps
First, the sender part is displayed and analyzed, and the encryption block diagram of the sender is shown in Figure 3.
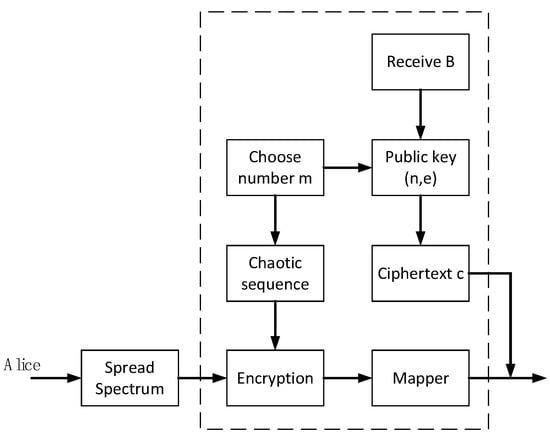
Figure 3.
Transmitter encryption block diagram.
- A.
The sender generates a chaotic sequence by , where a represents the starting point and b represents the initial value and the length of the sequence. For example, , where , , , , the meaning represented is: A’s ASCII code is 65, C’s ASCII code is 67. First, take an initial value of 0.55 and start iterating to generate the sequence, counting from the 65th bit of the sequence until the sequence length reaches 5500, then obtaining . Then, take the initial value of 0.84 to start generating the sequence, counting from the 67th bit of the sequence, until the sequence length reaches 8400, and get , for the rest, generate the encryption sequence according to this rule. The specific process is shown in Figure 4.
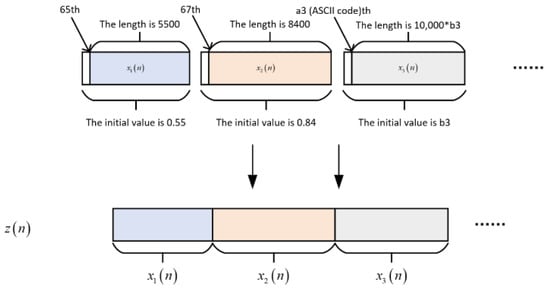
Figure 4.
Sequence generation diagram.
The entire iterative process uses the Logistic mapping function, as shown in the following formula:
- B.
The encrypted sequence generated above is XORed with the information sequence to obtain an encrypted sequence, which is then modulated and transmitted.
- C.
The sender also needs to encrypt to m with the public key published by the receiver and needs to send the encrypted ciphertext c to the receiver.
3.2.2. Receiver Encryption Steps
Secondly, the receiving end part is displayed and analyzed, and the encryption block diagram of the sending end is shown in Figure 5.
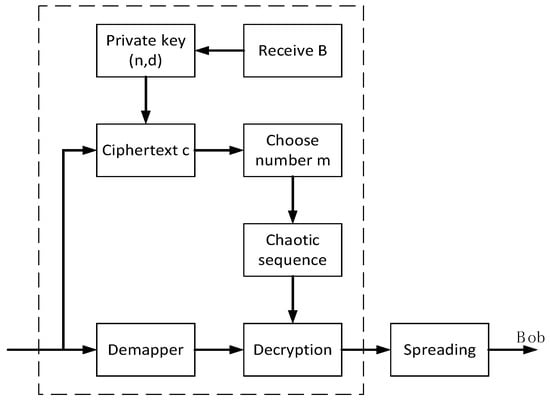
Figure 5.
Block diagram of receiver encryption.
- A.
The receiver first uses the RSA algorithm to generate a pair of public key (n,e) and secret key (n,d), and sends the public key.
- B.
The receiver uses the key to decrypt the received ciphertext c and obtains m.
- C.
The encrypted sequence z(n) is generated in the same manner as step A on the sender side.
- D.
After demodulating the received signal, the information is decrypted with the encrypted sequence to obtain the original information.
4. Experimental Simulation 7
4.1. Initial Value Sensitivity
Extreme sensitivity to the system’s initial conditions is the main dynamic characteristic of chaotic systems. Sensitivity refers to the fact that even a very small difference in initial values will result in two different sequences as the number of iterations increases. The chaotic system has good security performance because the small change in the initial value is difficult to estimate.
The trajectories of the real-valued mapping points generated by the iteration of the Logistic chaotic map and the simulation results are shown in Figure 6a,b, respectively. Their system parameters are all four and the number of iterations is 70.
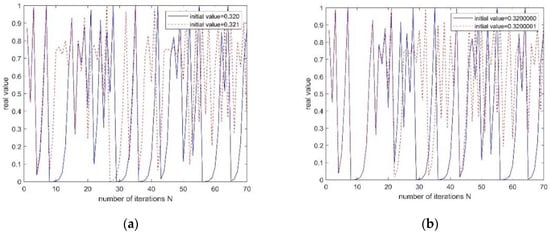
Figure 6.
The simulation curve of the initial value sensitivity of the chaotic sequence, in which (a) the initial value of the system is 0.320 and 0.321 and (b) are 0.3200000 and 0.3200001.
As can be seen from the above Figure 6a, when the initial value is 103 orders of magnitude different, the two trajectories are irrelevant after only eight iterations. Figure 6b further shows that it only takes about 21 iterations to iterate two irrelevant trajectories, even when the initial values differ by an order of magnitude of 107. This shows that the information of the initial value state of the orbit is rapidly lost with the separation of the system orbit, which shows the long-term unpredictability of the system orbit. Therefore, the initial value sensitivity of the chaotic sequence makes the chaotic system have excellent security performance.
4.2. Chaos of System Parameters
Lyapunov exponent is a typical analysis method to judge whether a system has chaotic characteristics and the degree of chaos.
The Lyapunov exponent refers to the two orbits that are not close to each other at the beginning of the phase space. With the continuous advancement of time, the average rate of change of exponential convergence or divergence is used to quantitatively describe the degree of separation of the chaotic system between the orbits of the local system. Its calculation formula is as follows:
Obviously, , so when , the mapping converges at a certain point; when , the mapping performs periodic motion; when , the mapping is in a chaotic state. The specific diagram is shown in Figure 7.
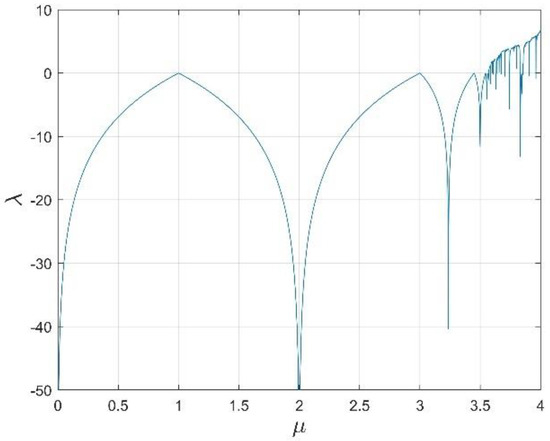
Figure 7.
Graph of the exponential relationship.
Figure 7 is a graph of the Lyapunov exponent under Logistic mapping conditions. It can be seen from the figure that, when µ = 1, µ = 3, = 0, the Logistic mapping chaotic system at this time is in a periodic state. When , there are system parameters greater than zero, that is, the logistic map has system parameters in a chaotic state. Combined with the bifurcation diagram in Figure 1, the system parameter is selected to be four, so that the mapping is in a chaotic state and traverses the entire value range, thereby increasing the confidentiality of the sequence.
4.3. Constellation Diagram Comparison before and after Encryption
Attack methods such as modulation identification for digital modulation will cause security risks in the communication process. By changing the shape of the constellation diagram, the purpose of the physical layer encryption is achieved, thereby ensuring the security of the system.
Common constellation encryption methods, such as phase rotation, amplitude adjustment, or a combination of the two methods, are used here to conduct simulation experiments with Binary Phase Shift Keying (BPSK) as an example. The time domain expression of the BPSK signal is:
In the simulation, the chaotic sequence is used as the random phase key and random amplitude key, and the shape of the constellation diagram is affected by encrypting the original sequence. Figure 8 is the simulation result of only encrypting the BPSK constellation diagram by using the random phase key. It can be seen from the diagram that the constellation points are all distributed on a circle with a radius of one. Under the condition of the same signal-to-noise ratio, the size of the selected phase interval is related to the bit error performance of the system.
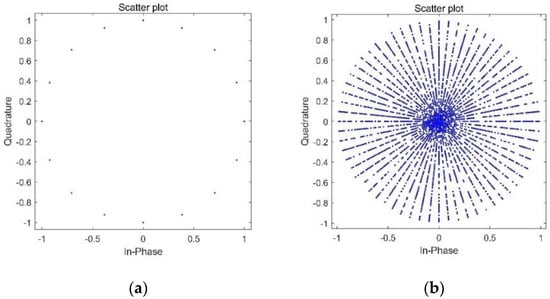
Figure 8.
BPSK constellation encryption algorithm. (a) Phase rotation and (b) rotation and amplitude adjustment.
Figure 9 is the simulation result of encrypting the BPSK constellation diagram using the random phase key and the random amplitude key at the same time. It can be seen that the constellation points of the encrypted constellation diagram are evenly distributed in a circle with a radius of about one, because the constellation the shape of the graph is further unrecognizable, so the illegal interceptor cannot obtain communication parameters through attack methods, such as constellation diagram clustering identification, which greatly improves the security of the communication process.
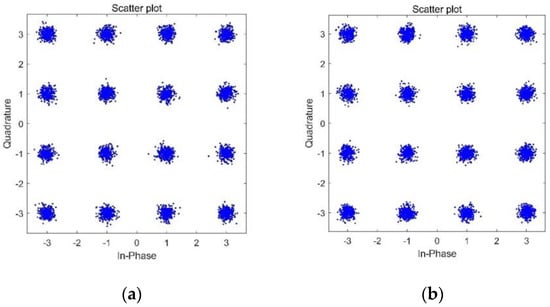
Figure 9.
Constellation diagram of 16QAM modulation of SNR = 15 dB, in which (a) is the unencrypted constellation diagram and (b) is the encrypted constellation diagram.
The constellation map encryption method, based on the random transformation of phase and amplitude, makes the distribution of constellation points random, and the cracking cost of the digital modulation link at the illegal receiver is greatly increased, so the security of the communication process is greatly improved. However, it also has some defects. This method cannot guarantee the judgment performance of the legitimate communication receiver, and even has a negative impact. The fundamental reason is that the closer the constellation point is to the center of the circle, the easier it is to be interfered with by noise in the process of passing through the transmission channel, which will lead to difficulty in the receiver’s decision, and then will increase the bit error rate of the decision.
The encryption algorithm proposed in this paper uses the secret key sequence to map the real constellation points, so that the encrypted constellation points no longer have the meaning of traditional constellation points. For the collaborator, the encrypted constellation point can be decrypted using the same chaotic sequence as the sender and the encryption rules of this algorithm, so that it is in the real position, and then the signal is subsequently processed.
As can be seen from Figure 9, there is no difference in the shape of the constellation diagram before and after encryption. The advantage of this is that the communication interceptor can determine the modulation method used by the sender through the constellation diagram identification or even machine learning, butabt they could not observe any trace of encryption from the constellation map.
4.4. System Reliability
In order to verify the feasibility of the algorithm, we used the proposed constellation encryption algorithm to simulate QPSK and 16QAM modulation and obtained the variation curve of the bit error rate under different signal-to-noise ratios, as shown in Figure 10:
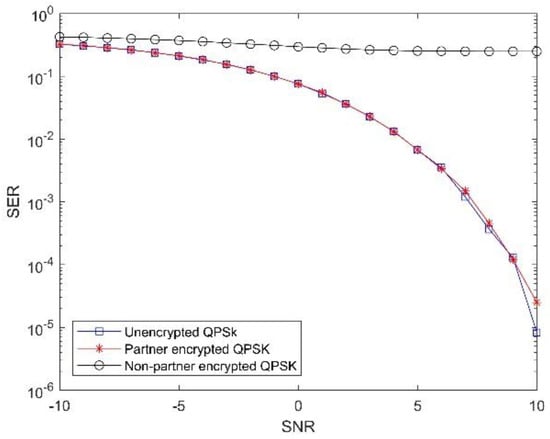
Figure 10.
Simulation diagram of the bit error rate of QPSK scrambled constellation encryption algorithm.
It can be seen from Figure 10 and Figure 11 that, under the condition of using the scrambled constellation encryption algorithm, if the communication receiver uses the traditional method to make judgments, even if the signal-to-noise ratio continues to increase, the bit error rate of QPSK will slowly decrease, but will eventually settle at around 0.25, and the bit error rate of 16QAM will gradually approach one.
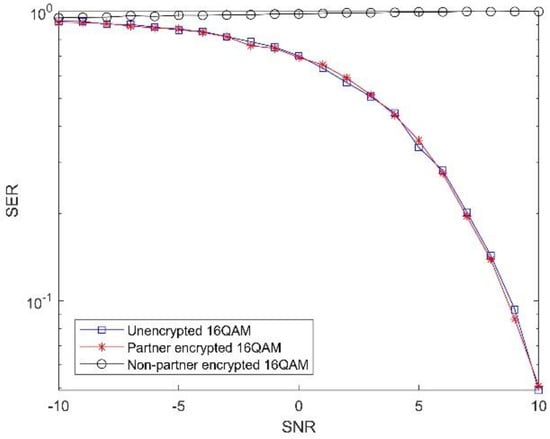
Figure 11.
Simulation diagram of the bit error rate of 16QAM scrambling constellation encryption algorithm.
This is because the illegal receiver can only judge that it is a traditional modulation through constellation identification. Therefore, even if the sender knows that the sender may have adopted a certain constellation scrambling algorithm, it cannot be effectively cracked. After using the corresponding demodulation judgment method, the bit error rate of the legitimate receiver is much lower than that of the illegal receiver. Simultaneous simulations show that the proposed encryption algorithm has almost the same bit error rate as the non-encrypted algorithm, so the proposed algorithm will not deteriorate the bit error rate performance.
5. Conclusions
This paper proposes a constellation encryption design based on chaotic sequence and the RSA algorithm. The method uses the parameters transmitted by the RSA algorithm to generate chaotic sequences, and then uses the chaotic sequences to make the modulation constellation points inconsistent with the original meaning, which further improves the security of satellite communication without increasing the complexity of the original system. After simulation analysis and verification, the bit error rate of the non-cooperating party will be greatly improved, and at the same time, it will not affect the receiving performance of the cooperating party, so this algorithm has good confidentiality performance and ensures the communication security of the system. Therefore, it is suitable for satellite security communication.
Author Contributions
Conceptualization, methodology, and writing—original draft preparation, M.Q. and Q.J.; writing—review and editing, M.Q. and B.B.; supervision, J.Z. and C.J. All authors have read and agreed to the published version of the manuscript.
Funding
The work is supported by the National Natural Science Foundation of China (grant No.62171468).
Data Availability Statement
The authors claim that the data used in this article are provided by our simulations and the data used to support the findings of this study are available from the corresponding author upon request.
Conflicts of Interest
The authors declare that they no conflicts of interest.
Appendix A
Prove: When the encryption algorithm is , the decryption algorithm is .
Assuming that the proof holds, then we have
Obtained from Equation (A1)
It can be seen from Equation (A3), and set its quotient as, then
It can be obtained from Equations (A2) and (A4)
Expand the left side of Equation (A5)
From Equation (A6), except for the first term, the rest of the terms contain the factor, so Equation (A5) can be simplified as
During the encryption process, it is known
Let the quotient be h, we can get
From Equations (A7) and (A9) we can get
Therefore, to prove that the hypothesis holds, it is only necessary to prove that Equation (A9) holds.
The following is divided into two cases to discuss and prove.
① if m and n are coprime, and m < n.
According to Euler’s theorem, we can get
Multiply the exponents on both sides of Equation (A11) simultaneously to get
Processing with Equation (A6), we can get
Multiplying both sides of Equation (A13) by m, we can get
Therefore, when m and n are mutually prime, the proof is complete.
② if m and n are not coprime, and m < n.
Assume, m = l × p and n = p × q.
Therefore, necessarily m and q coprime, we can get
And according to Euler’s theorem, we can get
Since q is a prime number, we can get
Multiplying the left side of Equation (A17) by , we get
also because
Available
Substitute Equation (A9) into the above equation to get
Multiplying both sides of the equation by m, we get
Substitute the assumptions into
And because n = p × q, you can get
Substitute Equation (A9) into the above equation, we can get
Therefore
Therefore, if m and n are not mutually prime, the proof is complete.
References
- Gao, Y.; Ao, H.; Zhou, Q.; Feng, Z.; Zhou, W.; Li, Y.; Li, X. Modeling of satellite communication systems design with physical layer security. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 1680–1683. [Google Scholar] [CrossRef]
- Yuxuan, G.; Yue, L.; Penghui, S. Research Status of Typical Satellite Communication Systems. In Proceedings of the 2021 19th International Conference on Optical Communications and Networks (ICOCN), Qufu, China, 23–27 August 2021; pp. 1–3. [Google Scholar] [CrossRef]
- You, L.; Li, K.-X.; Wang, J.; Gao, X.; Xia, X.-G.; Ottersten, B. Massive MIMO Transmission for LEO Satellite Communications. IEEE J. Sel. Areas Commun. 2020, 38, 1851–1865. [Google Scholar] [CrossRef]
- Hou, Y.; Chen, Y.; Wang, Z.; Xiang, H. Research on Dynamic Assignment of Satellite Communication Tasks Based on GA Algorithm. In Proceedings of the 2020 IEEE 5th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 12–14 June 2020; pp. 1052–1055. [Google Scholar] [CrossRef]
- Wei, L.; Mingfeng, L.; Yanyan, H. A high reliable satellite communication for emergency communications. In Proceedings of the IET International Conference on Communication Technology and Application (ICCTA 2011), Beijing, China, 14–16 October 2011; pp. 811–814. [Google Scholar] [CrossRef]
- Saunders, C. The role of small satellites in military communications. In Proceedings of the IET Seminar on Military Satellite Communications 2013 (Milsatcoms 2013), London, UK, 14 June 2013; pp. 1–13. [Google Scholar] [CrossRef]
- Liang, C.; Zhang, Q.; Ma, J.; Li, K. Research on neural network chaotic encryption algorithm in wireless network security communication. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 1–10. [Google Scholar] [CrossRef]
- Gao, Y.; Ao, H.; Feng, Z.; Zhou, W.; Hu, S.; Li, X. Modeling and Practise of Satellite Communication Systems Using Physical Layer Security: A Survey. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), Guangzhou, China, 21–24 July 2017; pp. 829–832. [Google Scholar] [CrossRef]
- Zheng, G.; Arapoglou, P.-D.; Ottersten, B. Physical Layer Security in Multibeam Satellite Systems. IEEE Trans. Wirel. Commun. 2012, 11, 852–863. [Google Scholar] [CrossRef]
- Li, W.; Mclernon, D.; Wong, K.-K.; Wang, S.; Lei, J.; Zaidi, S.A.R. Asymmetric Physical Layer Encryption for Wireless Communications. IEEE Access 2019, 7, 46959–46967. [Google Scholar] [CrossRef]
- Pfeiffer, J.; Fischer, R.F.H. Multilevel Coding for Physical-Layer Security. IEEE Trans. Commun. 2022, 70, 1999–2009. [Google Scholar] [CrossRef]
- Li, W.; Mclernon, D.; Lei, J.; Ghogho, M.; Zaidi, S.A.R.; Hui, H. Cryptographic Primitives and Design Frameworks of Physical Layer Encryption for Wireless Communications. IEEE Access 2019, 7, 63660–63673. [Google Scholar] [CrossRef]
- Hoseini, S.A.; Bouhafs, F.; den Hartog, F. A Practical Implementation of Physical Layer Security in Wireless Networks. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Xu, H.; Sun, L. Encryption Over the Air: Securing Two-Way Untrusted Relaying Systems Through Constellation Overlapping. IEEE Trans. Wirel. Commun. 2018, 17, 8268–8282. [Google Scholar] [CrossRef]
- Han, S.; Li, J.; Meng, W.; Guizani, M.; Sun, S. Challenges of Physical Layer Security in a Satellite-Terrestrial Network. IEEE Netw. 2022, 36, 98–104. [Google Scholar] [CrossRef]
- Quyen, N.X.; Duong, T.Q.; Vo, N.S.; Xie, Q.; Shu, L. Chaotic direct-sequence spread-spectrum with variable symbol period: A technique for enhancing physical layer security. Comput. Netw. 2016, 109, 4–12. [Google Scholar] [CrossRef]
- Sedaghatnejad, S.; Farhang, M. Detectability of Chaotic Direct-Sequence Spread-Spectrum Signals. IEEE Wirel. Commun. Lett. 2015, 4, 589–592. [Google Scholar] [CrossRef]
- Wang, X.; Li, Z.; Zhang, Q.; Pan, X.; Gao, R.; Xin, X.; Yao, H.; Tian, F.; Tian, Q.; Wang, Y. Chaotic physical layer encryption scheme based on phase ambiguity for a DMT system. Opt. Express 2022, 30, 14782–14797. [Google Scholar] [CrossRef] [PubMed]
- Sultan, A.; Yang, X.; Hajomer, A.A.E.; Hussain, S.B.; Hu, W. Dynamic QAM Mapping for Physical-Layer Security Using Digital Chaos. IEEE Access 2018, 6, 47199–47205. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, B.; Guo, D. Physical Layer Secure Transmission Based on Fast Dual Polarization Hopping in Fixed Satellite Communication. IEEE Access 2017, 5, 11782–11790. [Google Scholar] [CrossRef]
- Luo, Z.; Wang, H.; Zhou, K.; Lv, W. Combined Constellation Rotation With Weighted FRFT for Secure Transmission in Polarization Modulation Based Dual-Polarized Satellite Communications. IEEE Access 2017, 5, 27061–27073. [Google Scholar] [CrossRef]
- Sultan, A.; Yang, X.; Hajomer, A.A.E.; Hu, W. Chaotic Constellation Mapping for Physical-Layer Data Encryption in OFDM-PON. IEEE Photonics Technol. Lett. 2018, 30, 339–342. [Google Scholar] [CrossRef]
- Vidhya, E.; Sivabalan, S.; Rathipriya, R. Hybrid Key Generation for RSA and ECC. In Proceedings of the 2019 International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 15–16 November 2019; pp. 35–40. [Google Scholar] [CrossRef]
- Yue, P.; Guodong, L.; Jing, Z. Based on the Improved RSA Keys and Compound Chaotic System and Design of Audio Encryption Algorithm. In Proceedings of the 2016 International Conference on Smart City and Systems Engineering (ICSCSE), Hunan, China, 25–26 November 2016; pp. 197–201. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).