Abstract
As an essential cryptological element, symmetric-key block ciphers have long been utilized to offer information security. Even though they were created to provide data confidentiality, their adaptability grants them to be utilized in the creation of various cryptological techniques, including message authentication protocols, hash functions, and stream cryptograms. MARS is a symmetric shared-key block cryptosystem that supports 128-bit blocks and keys with sizes ranging from 128 to 448 bits. The cryptographic cores of MARS come in a variety of rounds, each constructed to take benefit of the robust outcomes in order to enhance security and performance over earlier ciphers. The MARS cipher is given a new function in this work that uses the operations ROT, XOR, NOP, INV, hash 512, Quotient, and MOD for improving the technique of the cipher. The goal of our modification is attaining a superior confusion level whilst retaining the MARS cryptosystem’s differential and linearity aspects.
1. Introduction
Cryptography is a modern encryption technology made up of a variety of mathematical processes requiring the application of formulas and algorithms. It was created to safeguard the confidentiality of military and diplomatic communications. A new market for cryptographic products has emerged as information technology and encryption science have advanced rapidly [1]. While the internet is currently being utilized to speed up the movement of huge amounts of critical and valuable data, these data must be protected from unauthorized access due to the internet’s multiple attack vectors [2]. To secure data from illegal access, many data protection techniques are used, including masking, watermarking, and encryption. Effective security technology is required to protect consumers’ sensitive digital data [3].
Cryptography is one of the most widely used and trusted methods of protecting digital data in computer and communication networks. Many various image encrypting systems, such as RSA, the International Data Encryption Algorithm, and the Data Encryption Standard, have been proposed to achieve this objective. However, owing to a variety of inherent image properties, such as increased redundancy and data capacity, which have been problematic for conventional encryption, such conventional systems do not appear to be optimal for image applications. Furthermore, numerous encryption algorithms necessitate additional operations on compressed image data, necessitating a lengthy computation time and a large amount of computational power.
Network security is to defend networks and their applications from intrusions while preserving the availability, confidentiality, and integrity of data. We take into account a variety of elements in our innovative system. (1) Confidentiality: In order to make information confidential, it is updated in a way that makes it impossible for an attacker to deduce the information. Through the use of encryption methods, it is accomplished. (2) Authentication: In order for a pair of interacting entities to prove their identification, the authentication component of security services is necessary. In essence, the authentication service works to verify the identity by ensuring that a secret is shared by all parties involved. (3) Integrity: Data integrity refers to the necessity for assurance that only authorized parties can change the message. The message is safeguarded from being altered by the attacker by being encrypted to some extent.
This article introduces a new modified MARS cryptosystem based on a new S-box generation and Niho exponent. Images were not encrypted using the MARS technique because the repeated letters in the plaintext would result in a non-flat histogram graphic. However, we can encrypt images in our newly modified Mars system, circumventing the MARS cryptosystem’s weak areas. The following list highlights the paper’s significant contributions:
- The novel system uses the SHA-512 algorithm to generate a secret key used in S-box generation to ensure that the S-box was totally dependent on every bit in the secret key.
- The subkeys generation is modified by using the Niho exponent, which is subset of Boolean bent functions. This base property of bent functions is used for protecting ciphers against linear cryptanalysis.
- After each cipher block, different rotations for S-boxes are selected based on the hashed key’s array to overcome the letter repetition problem.
- The ciphertext is mainly diffused after encrypting every plaintext block with the bitwise exclusive-OR operation so we guarantee that the ciphertext mix together.
- We perform an “image diffusion” step that makes randomization in the image so that if one pixel changes, it will have a large effect on the output of the diffusion step.
The entire algorithm is tested for image and text to attain a satisfactory level of security by the performance analysis test to improve the security level. The main innovation points of this paper are:
- Overcoming the letter repetition problem (this problem will cause the histogram to not be flat).
- Making high randomization in the image so that if one pixel will change so it will affect the whole image, and if we encrypt the same image with one pixel change it will cause a different ciphertext to be obtained.
- Making a generation of subkeys robust against linear and differential attacks by using the Niho exponent function.
The article is planned as follows: Section 2 presents the related work, Section 3 reviews a brief explanation for the MARS system, and Section 4 discusses the proposed algorithm, while Section 5 delivers numerical simulation results. Section 6 examines the proposed scheme’s performance. This article is concluded in Section 7.
2. Related Work
In 2007, The MARS method was subjected to diffusion analysis using first order SAC and higher order strict avalanche criteria in this work. The findings provide valuable information into the MARS spreading behavior and it can be used to develop novel encryption techniques [4]. In the year 2013, [5] Ahmed H. et al. suggested a Metamorphic-Enhanced MARS Cipher that improves on the MARS cipher by incorporating high confusion while keeping the linear and differential diffusion criteria intact. The encrypted key is used to generate the sub-keys after the user key has been encrypted. The meta-MARS encryption function is built using the MARS encryption cipher’s four low-level operations. The operation selection bits can be any two sub-key sequential bits. In the same year [6], Mansoor E.et al. published a study in which they offered a detailed examination of symmetric block encryption methods based on various factors. The main goal was to examine the performance of the most popular symmetric key algorithms in terms of authentication, flexibility, reliability, robustness, scalability, and security, as well as to highlight the major flaws of the algorithms in question, making the strengths and limitations of each algorithm transparent for application. Moataz M. et al. published a metamorphic-enhanced function in 2014 [7] that is used before and after the cipher process to improve the MARS cipher process, with plaintext as an input to the meta-MARS function. The metamorphic function uses four logical-level operations to encrypt the text before and after the ciphering process. These operations include XOR, INV, ROR, and NOP. In [8], different bitmap pictures are encrypted with RC6 and MARS; Yi Yi Aung et al. introduced in this paper visual inspection and various encryption techniques that are used to assess the quality of the encrypted images. Later, Nian Li et al. [9] addressed several research challenges related to Niho exponents and reviewed some recent advances in the application of Niho exponents in this study. Where Niho exponents were also used to discuss some unresolved problems in the areas of sequence design, coding theory and cryptography. Lately in 2021, Alibek N. et al [10] published an unbiased analysis of the most popular and widely used data encryption methods. The ability to protect data from various attacks, as well as the amount of time it takes to encrypt data, are the major characteristics that distinguish encryption algorithms. The most widely used symmetric encryption algorithms, such as DES, 3DES, Blowfish, MARS, and AES, were compared. Recently in 2022 [11], Qian LIU employed over finite fields with even characteristic two modules of permutation polynomials using Niho exponents. The algorithms employed in [5,7] were not used for image encryption, as they did not offer a solution to the repetition issue that prevents the histogram from being flat; moreover, they did not offer any changes to the key generation process. Subkeys for the MARS cryptosystem that have prolonged runs of ones or zeros could make MARS vulnerable to effective assaults [12]. When using round keys for multiplication, the two least significant bits are always set to one. Thus, regardless of the subkey, there are always two inputs that remain unchanged during the multiplication process, and there are also two outputs that remain fixed. MARS can be broken in 21 out of 32 rounds using a meet-in-the-middle attack that John Kelsey and Bruce Schneier published in 2004 [13]. In order to overcome these drawbacks of earlier systems, the authors proposed a novel algorithm for image encryption.
3. Background Review
3.1. The Niho Exponent
The bent function class is a subset of Boolean functions that achieve the highest level of nonlinearity attainable. These functions are essential in cryptology and coding theory [14]. As a result, the presence of bent functions is a well-known issue. When it comes to the polynomial form, monomial bent functions of the type:
are being investigated by [15] and the whole monomial bent functions are identified if n ≤ 20. After achieving this point, the community began to focus on the binomial bent functions of the following type [16]:
Let be a Boolean function such that for a given positive integer s and for some [17]. Functions of this form are called monomial functions. The exponent s is said to be a bent exponent if there exists such that is bent [18]. In order for to be bent, the following two conditions should be satisfied [19]:
- (1)
- (2)
- or
Proven by computer experiments that there is no other exponent s for [20]. These bent functions are analyzed in [21], where conditions of the existence of bent functions are provided for certain parameter values n, k, s1, and s2. [22].
Binomial Bent Functions
Over the years, monomial bent functions have been thoroughly researched [23], and all bent exponents for n 20 have been determined. Finding a new exponent s for n > 20 is extremely difficult because the search primarily relies on computer experiments, hence Equation (1) does not belong to any of the structures. As a consequence, the community began searching for bent functions containing multi tracing terms, with binomial functions as the first step. Ref. [24] made the first investigations in identifying binomial bent functions, demonstrating that Equation (2) is bent with Niho exponents s1 and s2. Consider that a Niho exponent is a positive integer s (generally considered modulo ) as well as is a Niho power function if the constraint of to is linear, or in other terms for certain j < n. Dobbertin et al. explored the bent property of binomials with the next Equation (3) and came up with the following bent Niho exponents
where satisfying and , and where m is even.
3.2. Description of the MARS Cryptosystem
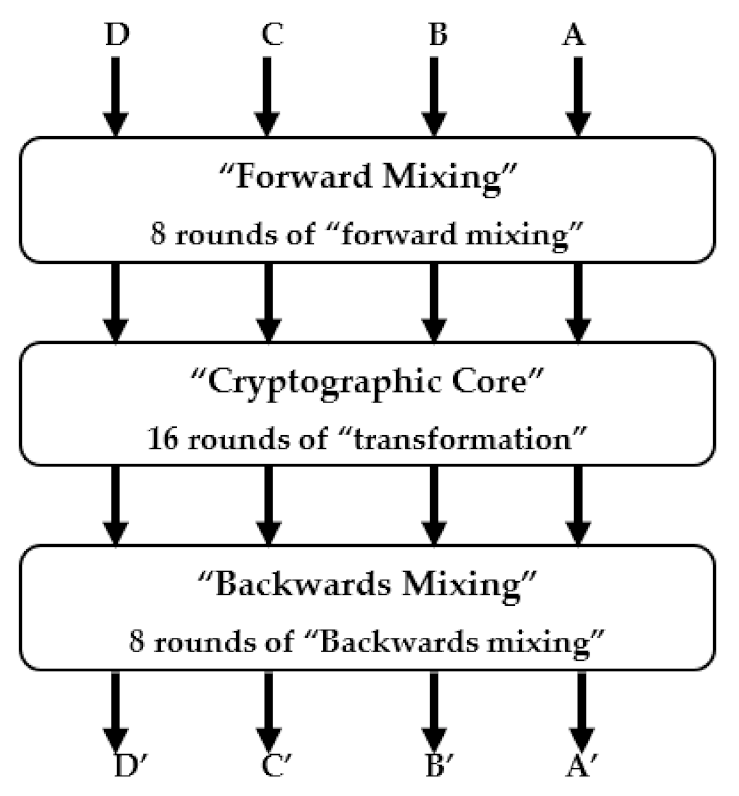
MARS is a shared-key block cipher with a 128-bit block size and a 128-bit key size. It was created to satisfy and exceed the specifications for a shared-key encryption standard. It generates 4/32-bit decrypted words of data named A’, B’, C’, and D’. [25] from 4/32-bit plaintext words of data named A, B, C, and D. All internal operations are conducted on 32-bit words, making the cipher word-oriented. MARS is a three-phase Feistel network of type three. Figure 1 shows a 16-round “cryptographic core” phase wrapped up within a double layer of eight rounds of forward/backwards mixing.
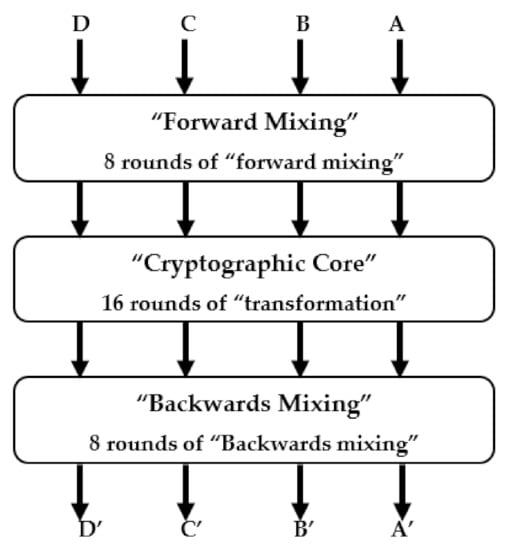
Figure 1.
High-level structure of MARS encryption procedure.
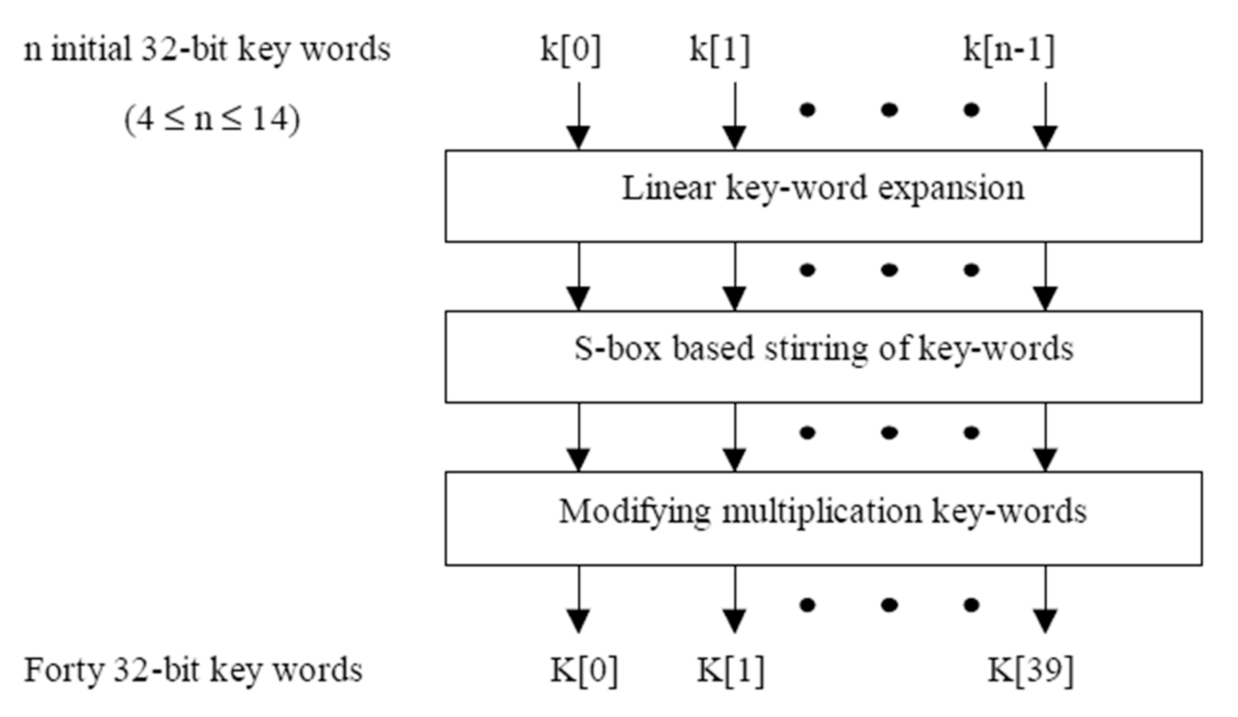
MARS allows user keys ranging in length from 4 to 14 words (128 to 448 bits). For the encoding procedure, MARS employs key expansion technique for expanding the key of the user into a key array K[] comprised of 40 words, as shown in Figure 2. Three steps make up the essential expansion process. The first phase is linear expansion, which employs a simple linear transform to expand the original user-supplied key to forty 32 bits. While the second phase utilizes “S-box based key stirring,” which uses a type 1 Feistel structure to stir the extended key. In a multiplication keyword modification step, the keywords utilized in the ciphering/deciphering processes of multiplying are examined. MARS likewise uses a table of a single S-box with bit words 512-32. This S-box is also utilized in the process of the key expansion. The S-box is split up into two tables, each with 256 entries: S0 and S1.
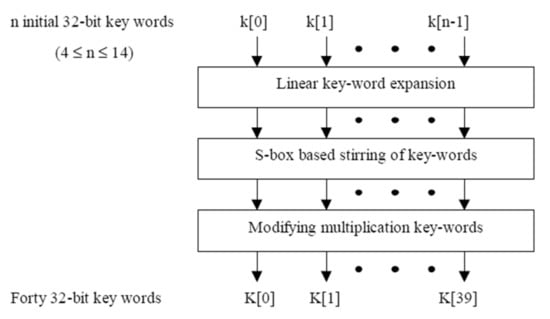
Figure 2.
MARS’ key expansion process.
The MARS Framework
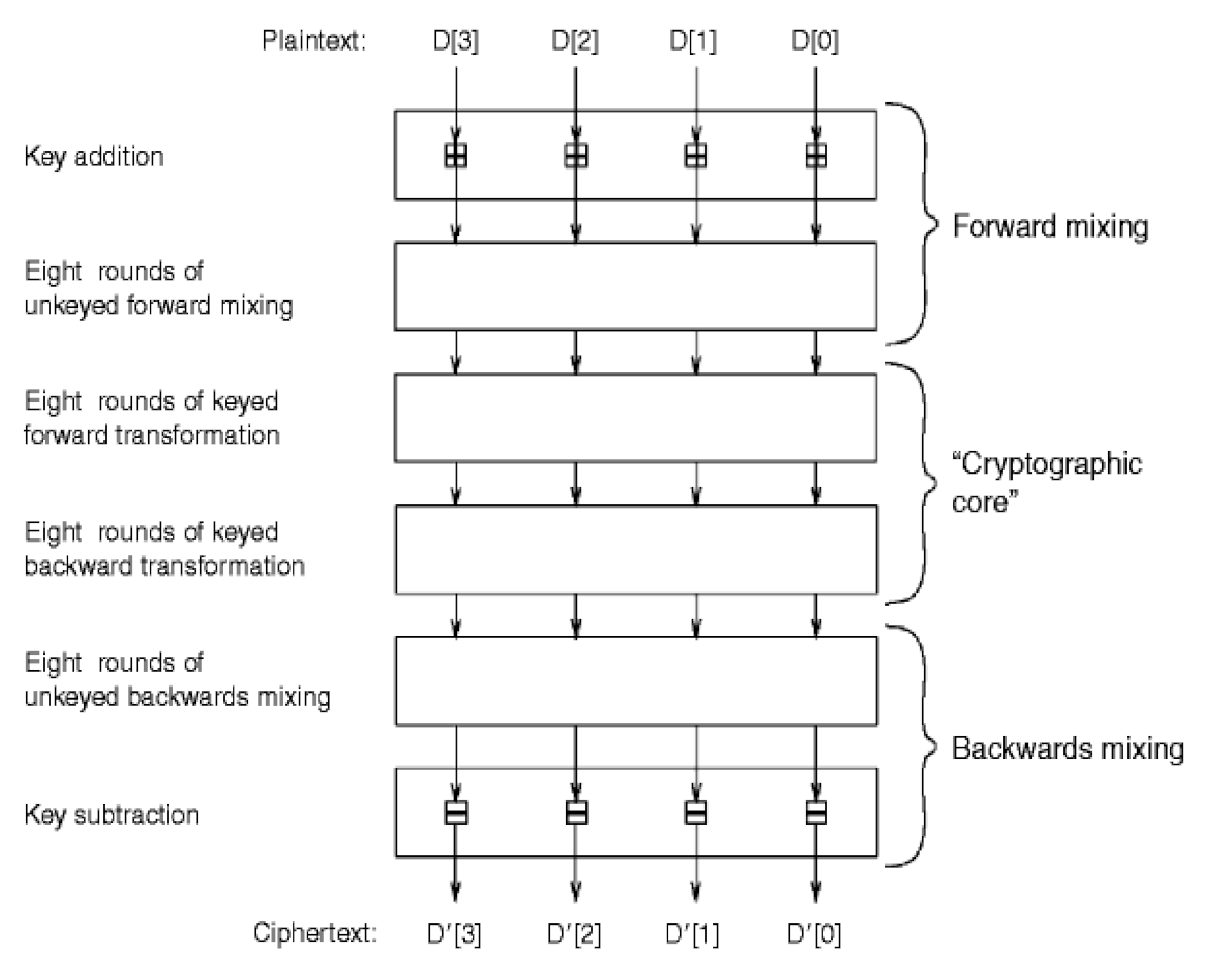
Figure 3 shows the six levels that a plaintext block should pass through to produce an encrypted block [13]. These levels are as follows:
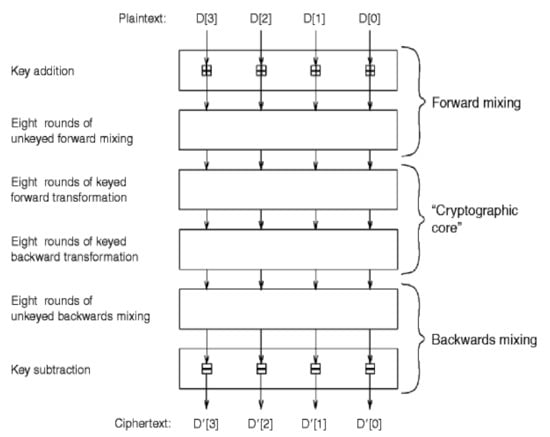
Figure 3.
The cipher’s high-level structure.
- a.
- Pre-Whitening Level: The plaintext’s words have 128 bits of key material modulo 232 added to them.
- b.
- Forward Mixing Level: An unkeyed mixing procedure consisting of eight rounds utilizing the MARS S-box extensively.
- c.
- Forward Core Level: A keyed unbalanced Feistel encryption of eight rounds, which resists cryptanalytic assault by combining S-box lookups, data-dependent rotations, multiplications, xors, and additions.
- d.
- Backward Core Level: A keyed unbalanced Feistel encryption of eight rounds, which resists cryptanalytic assault by combining S-box lookups, data-dependent rotations, multiplications, xors, and additions.
- e.
- Backward Mixing Level: An unkeyed mixing operation of eight rounds utilizing the MARS S-box extensively.
- f.
- Post-Whitening Level: A key material of 128bits have been withdrew from the block’s words modulo 232.
4. Proposed Cryptosystem:
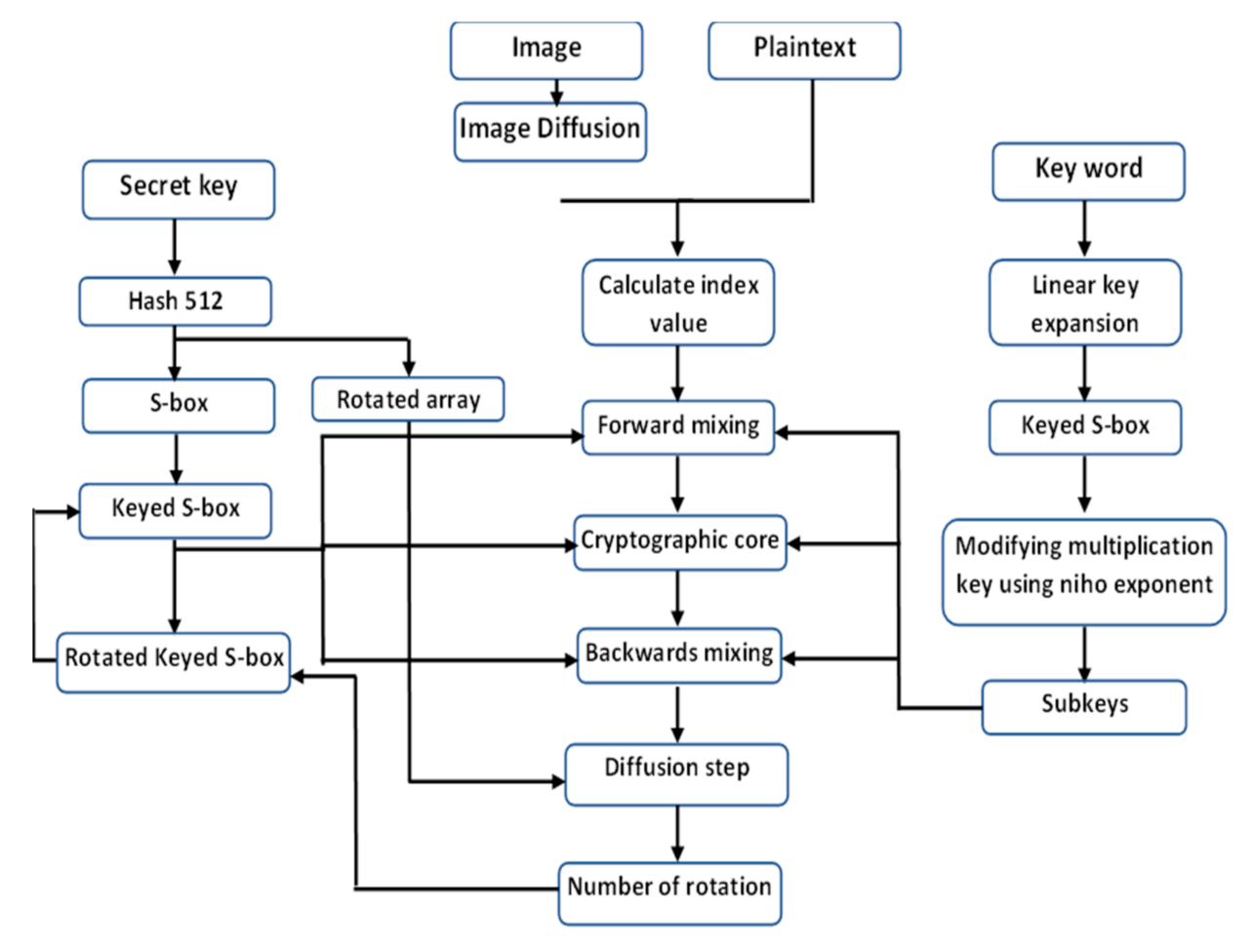
An innovative method is introduced to eliminate the pixel correlations, increase the value of entropy, and accelerate the avalanche effect. Plaintext and image encryption are both possible with the improved MARS. Figure 4 depicts the suggested encryption scheme’s flow chart. Table 1 shows a list of mathematical symbols used in the paper. Furthermore, Table 2 demonstrates a list of abbreviations.
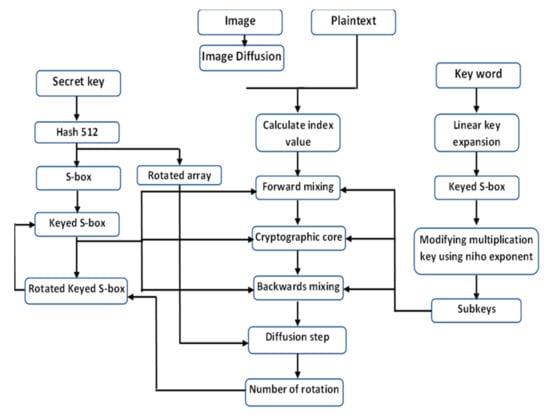
Figure 4.
The flow chart of the proposed encryption scheme.

Table 1.
List of mathematical symbols.

Table 2.
List of abbreviations.
In our new system, the key expansion process is the same as MARS except the part of the mask to modify the multiplication subkeys. We modified it by using the Niho exponent. In our novel scheme, we intend to establish a strong relationship between S-box and the user key.
We modify the S-box used in the MARS system by mixing it with the secret key. The encryption process for our novel scheme has the same encryption steps as MARS. We modify the S-box part to get different rotations after every step. In addition, we introduce the image diffusion step at the beginning of the encryption scheme and after the forward mixing, cryptographic core, and backward mixing to ensure that by changing one pixel it will affect a significant change for the whole image. Finally, we use the Xor operation to merge the whole ciphertext with each other to make a strong relation between the plaintext and the ciphertext, as if only one pixel changes, the ciphertext will totally change.
4.1. Proposed Keyed S Box
In our novel scheme, we intend to establish a strong relationship between the S-box and the user key, as well as a strong association between rounds and the S-box by making each round have a distinct S-box, so that even if we duplicate the plaintext, we will obtain a distinctive ciphertext. The following is a description of the operating procedure:
Step 1: Using the “SHA3-512” algorithm to produce 512 bits of the secret key.
Step 2: Expanding the hashed key to a 512-word array by rotating the hashed key by the number 17. We use the number 17 because it cannot be divided by 512; as a result, we guarantee that the array cannot be repeated.
Step 3: Merging the expanded hashed key with S-box by XOR operation.
Step 4: We calculate the values of “the rotated array” using the hashed key values, which will cause the S-boxes to rotate with different values. After encrypting each message’s block, we rotate the S-box, S-box1, and S-box2 using the values in the “rotated array.” As a result, while encrypting another block of message, we will have a new arrangement for S-box, S-box1, and S-box2, resulting in a strong relationship between the ciphertext and key because we will have different ciphertext even if we enter the same block of data.
4.2. Key Expansion Process
In our new system, the key expansion process is the same as MARS except the part of the mask to modify the multiplication subkeys. The material of the original key is first duplicated into a 15-word temporary table T[], proceeded by the number of words n, then zeroes. We did this by establishing:
The following method is then performed four times, with each iteration computing the expansion key’s next ten words:
- The subsequent linear function is utilized to transform the array T[]:
- The array T[] is then stirred via four rounds of Feistel networks of type 1. We replicate the process four times in total.
- Later, ten words are taken from T[], then rearranged into the extended key array’s following ten words, K[]. This is accomplished by establishingand using the relation:where satisfying and , and where m is even equal.
- We choose secret value and calculate the secret value Then we convert the expanded key array into the polynomial array and applied it into the relationwhere:After we execute the trace function, we convert the function back into the binary array.
- Finally, we partition the function into subkeys.
4.3. Encryption Process
In our new system, the encryption process is the same as the MARS cryptosystem; however, we add a few steps that make the whole ciphertext depend on itself and on the secret key, which implies that, by changing one bit in the plaintext or the secret key, it will cause a changeover for the whole ciphertext. The encryption process is shown in Figure 5 and is described as follows:
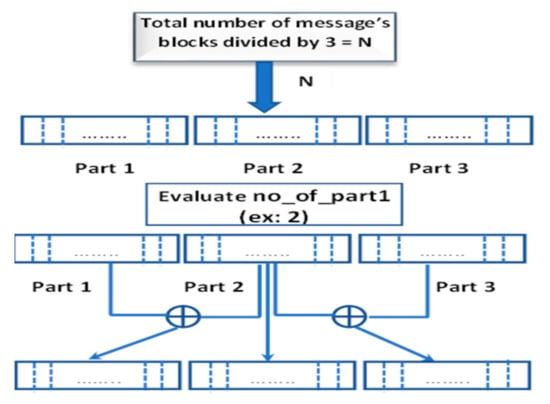
Figure 5.
The encryption process.
At the first step: Before we make the forward mixing rounds, we calculate the index factor that we use to rotate the S-box. We set the initial value of the index factor (index) to zero. After we encrypt the first sub-block from the plaintext, the index factor (index) will increase by one. The value of the index factor is the address of the element that is located in the rotated array. This element will cause the S-box to rotate left by its value; then, we increase the number of (index) by one and we get the address of another element located in the rotated array. This element will cause the S-box1 to rotate left by its value. Finally, we increase the number of (index) by one and we get the address of the element located in the rotated array. This number will cause the S-box2 to rotate left by its value. This step will be repeated for the two other phases.
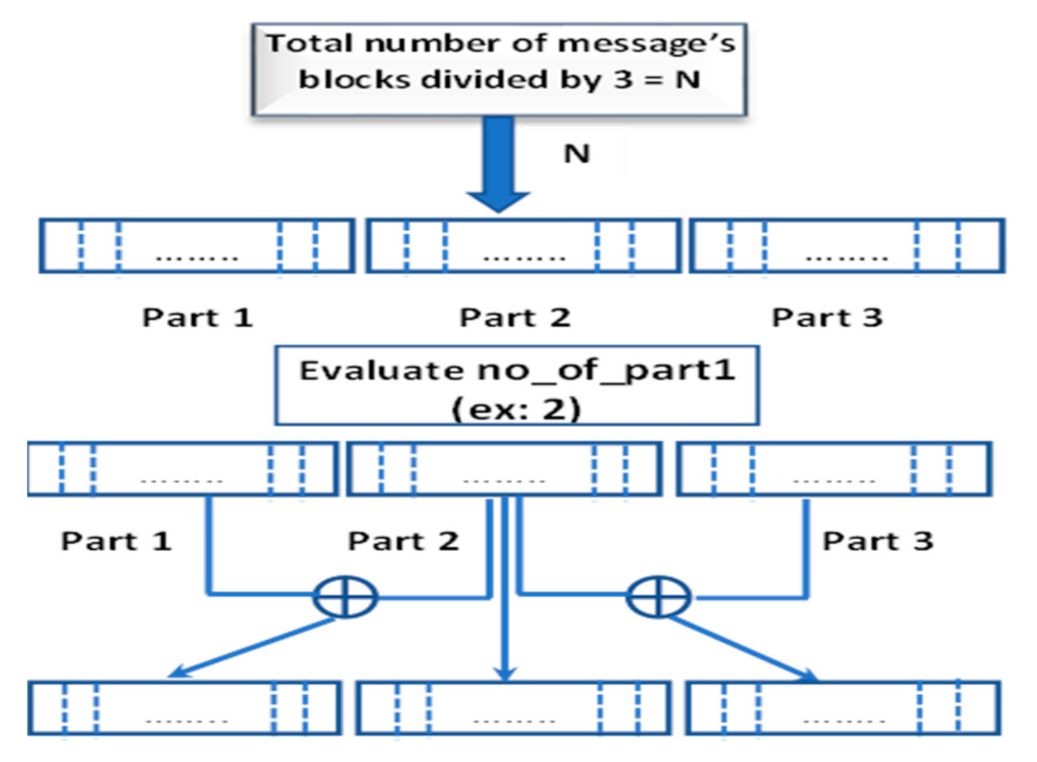
At the second step: We divide the ciphertext into three parts of blocks, we first evaluate the number of sub-blocks in each part by dividing the total number of the message’s blocks by three.
Then, we evaluate the number of the parts that XORed with the other two parts {in this step we depend on index factor (index)}.
no_of_part1 = Mod [index,3]
Final step: Mixing the chosen part, which is determined by the index factor (index) with the other two parts.
4.4. Image Diffusion
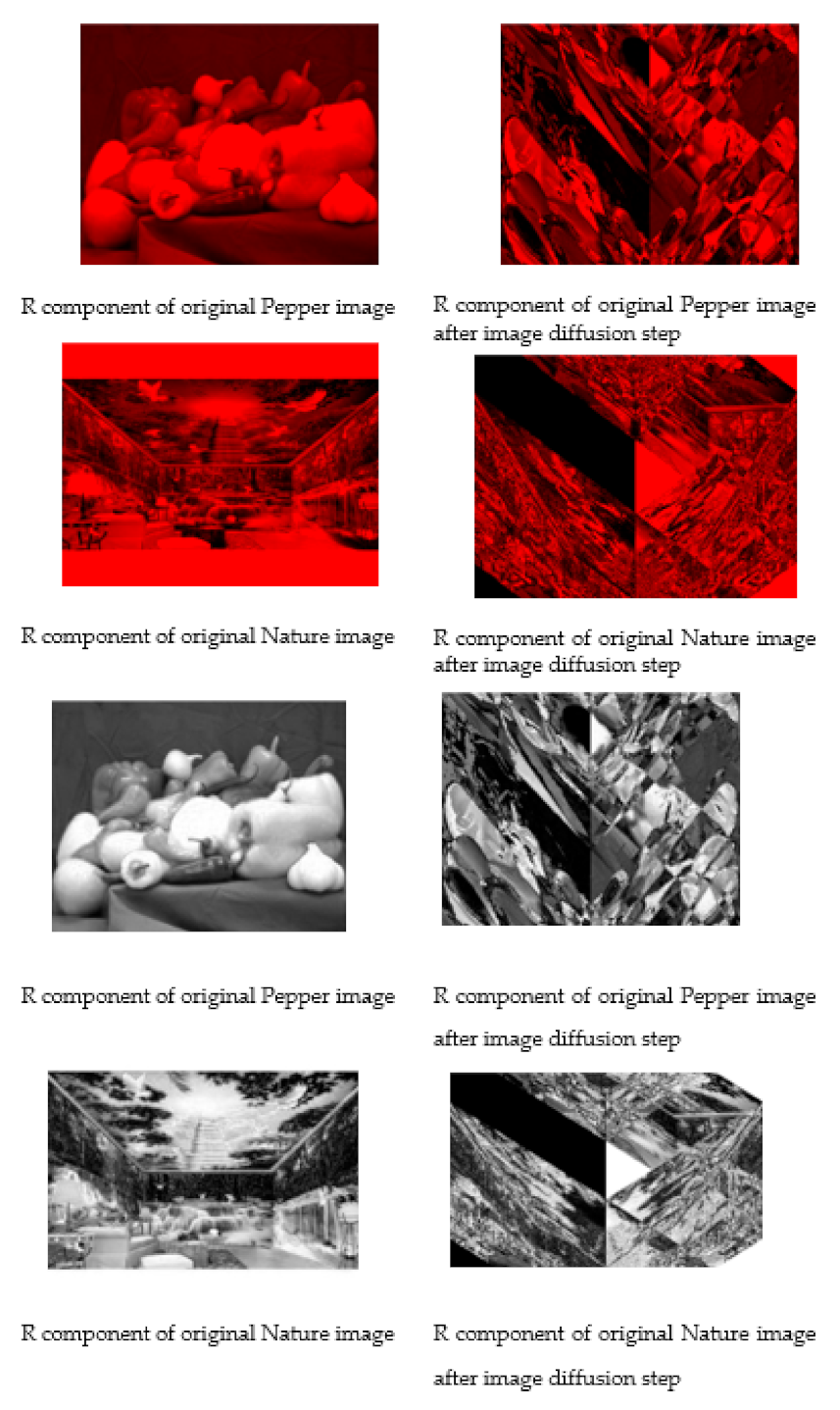
R, G, and B are the three primary components of any colorful image. In order to obtain better randomness, we perform “image diffusion”. In this step, we use simple operations “Xoring and rotate left”. We perform the following program for every component:
These steps will be performed after forward mixing, cryptographic core, and backward mixing. Figure 6 illustrates how the image diffusion step makes randomization in the image.

Figure 6.
Image diffusion.
4.5. Decryption Process
In our novel scheme, its decryption process is the inverse of the encryption process, and the decryption code is similar to the encryption code, so the novel scheme is secure against chosen ciphertext attacks as against chosen plaintext attacks. For the image diffusion step also, its decryption code is the same as the encryption code because we only use XOR operations. The S-box in the decryption process will be rotated to the right by the same manner as in the encryption process to get the same values in each step.
5. Simulation Results
Wolfram Mathematica 13 has been used to simulate and test the novel MARS approach that has been proposed. The tremendous mathematical and computational capabilities of the Wolfram Language are fully integrated with the built-in support for programmatic and interactive image encryption. The simulated environment was created using an Intel Core i5 processor running at 2.7 GHz, 8 GB of memory, and Windows 10.
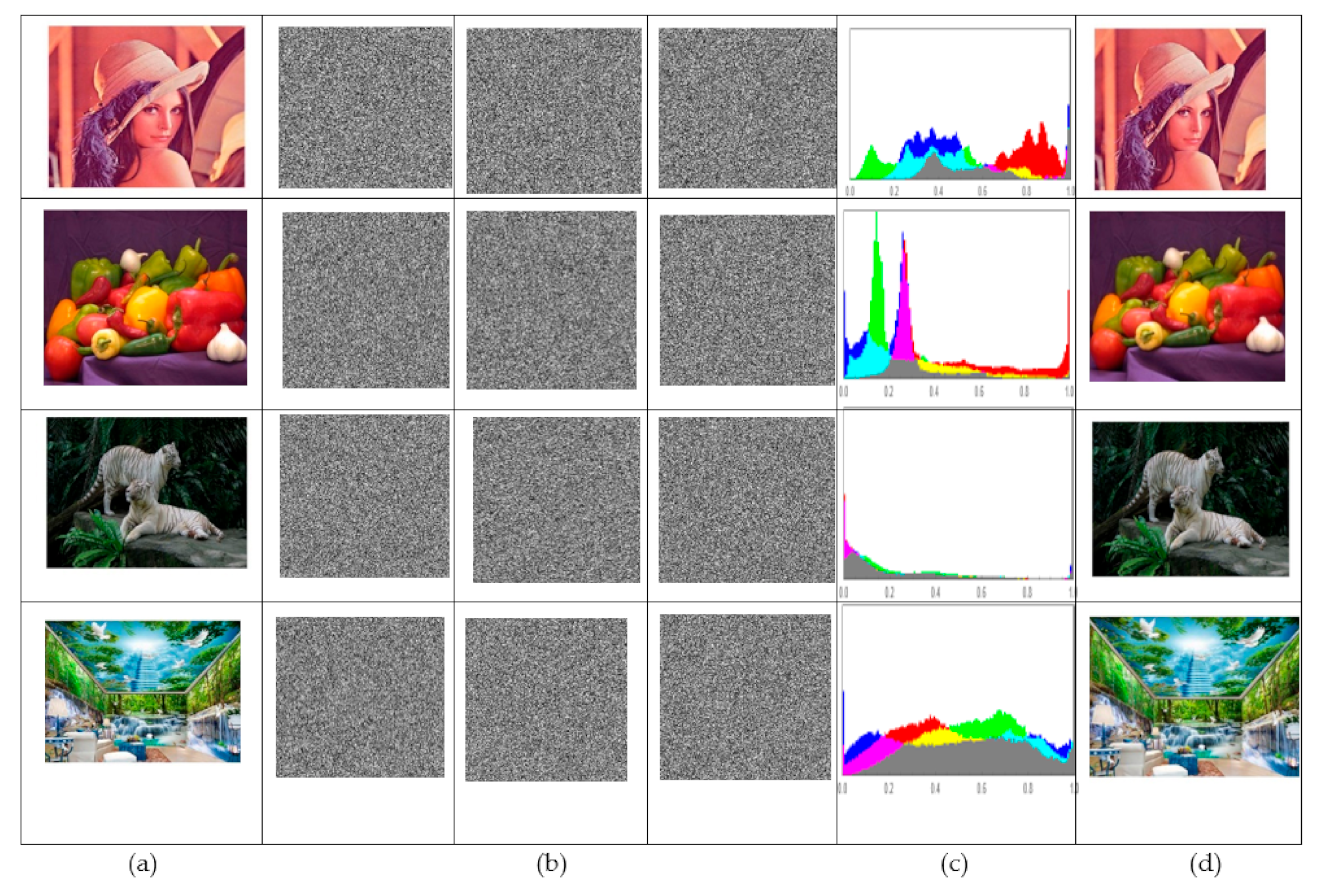
The algorithm is applied to the images of Lena, Pepper, Tigers, and Nature. The suggested symmetric encryption and decryption system is implemented using the ‘Mathematica 13’ program. Figure 7a shows the original plain images with a size of 512 × 512 pixels. The components “RGB” of the matching cipher image are created using the encryption procedure, as shown in Figure 7b. Then, using the proper secret key, we decrypted the cipher image in Figure 7b to obtain the perfectly reconstructed image in Figure 7d. Figure 7c shows the histograms of the plain images. The pattern of the cipher image is noise-like and unrelated to the original plain image, as shown in the Figures. The image that was retrieved is flawlessly restored.
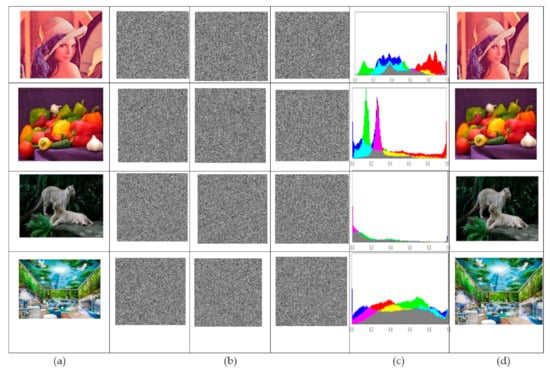
Figure 7.
Histograms of colored plain images. (a) Original Plain images. (b) Cipher images. (c) Histograms of original plain images. (d) Decrypted plain images.
6. Performance and Security Analysis
6.1. For Plaintext
6.1.1. Avalanche Effect
The avalanche effect is the changing in the number of bits in the cipher text as one bit of the plaintext or one bit of the secret key changes. Any encryption technique should have the property that a smear change in the plaintext or key would yield a major change in the ciphertext [26]. If the modifications are minor, this could minimize the size of the plaintext or key space that needs to be searched, making cryptanalysis much easier. The avalanche effect can be determined as follows:
In this case, we take four plaintexts, where two of them are normal messages while the other ones are of a repeated letter “e”. The effect of avalanche is computed by toggling one bit from everyone in different positions. Then, we compute the avalanche effect by toggling the user’s key in various positions. After computing the avalanche effects as indicated in Table 3, the following results have been obtained:

Table 3.
The effect of avalanche.
6.1.2. Language Statistics
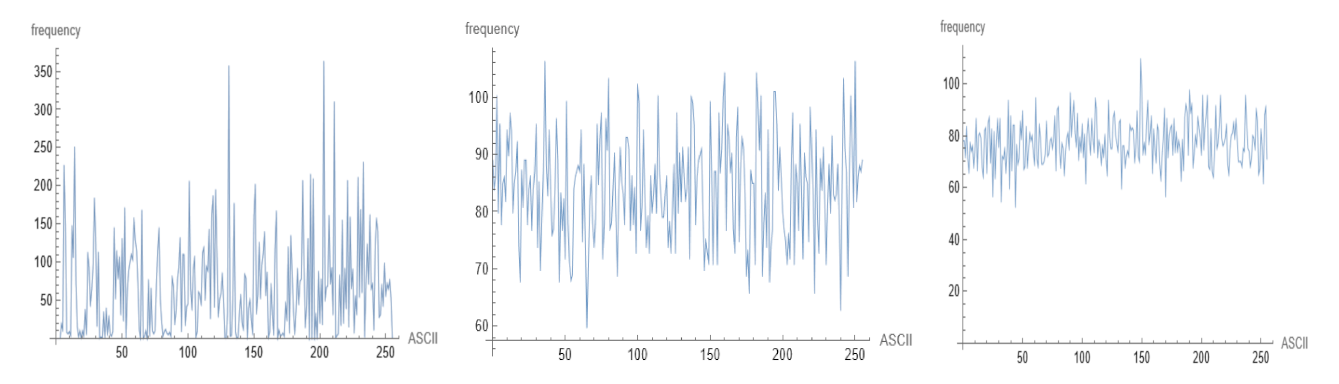
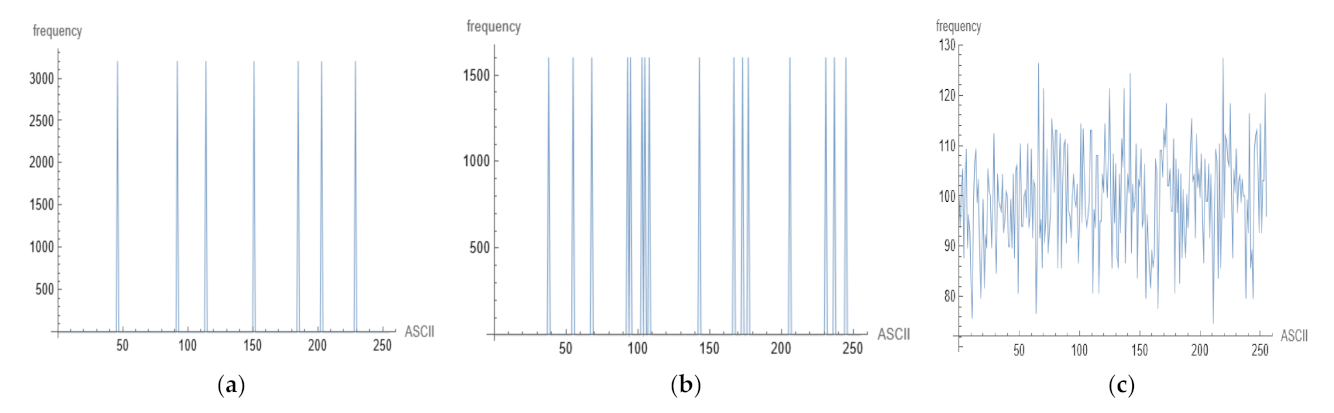
Entropy is a statistical metric that determines how much information is created on average for each letter in a text. The amount of limitation placed on a text in the language due to its statistical nature is measured by redundancy. Shannon proposed a new method for estimating a language’s entropy and redundancy. If the ciphertext of a cryptosystem has a flat distribution, it is deemed unbreakable against statistical examination. Figure 8 depicts the statistics of the plaintext for the utilized file, MARS ciphertext statistics, and the strength of the new suggested system.
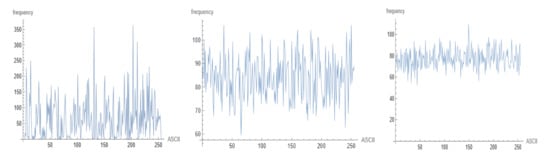
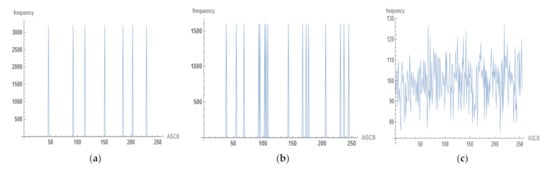
Figure 8.
Plaintext statistics (a) Plaint text statistics and repeated letters in plaintext, (b) Statistics of MARS, and (c) Statistics of proposed system.
6.1.3. NIST Statistical Suite
NIST has developed a set of 16 tests to ensure that binary sequences generated by random or pseudorandom number generators are indeed random, which can be utilized for a variety of applications such as cryptography, modelling, and simulations. The tests are focused on applications that require randomization for cryptographic purposes, such as keying material creation. The tests are described in detail in the NIST Special Publication (SP) 800-22, A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications [27]. Table 4 shows the average results of the statistical tests for the suggested system and MARS algorithm.

Table 4.
The average values of the statistical tests for the proposed system and MARS algorithm.
6.2. For Image
The security analysis of the proposed encryption technique with R, G, and B components will be discussed in this section.
6.2.1. Key Space
The ability of cryptography to resist brute force assaults enhances with an increasing key space. As our suggested algorithm employs a 448-bit key, the number of permissible secret key permutations is 2448 for R, G, and B individually, it made it extremely hard to be cracked whilst employing a brute force assault.
6.2.2. Key Sensitivity
Two aspects of key sensitivity can be assessed: First aspect, while encoding the same plaintext image using slightly different keys, the ciphertext image will be completely different, as assessed by the ciphertext image’s changing rate t. Second aspect, even though the discrepancy between the erroneous and right keys is negligible, the image decoded from the wrong key contains no information about the plaintext image.
For the first aspect, we compute:
For the second aspect:
The hypothetical values for Diff1, Diff3 and Diff2, Diff4 in the case of dual arbitrary images are 99.6094% and 33.3328%, correspondingly. Table 5 shows that the computed results of Diff1, Diff2, Diff3, and Diff4 for R, G, and B components for images.

Table 5.
The computed key sensitivity results.
6.2.3. Histogram Analysis
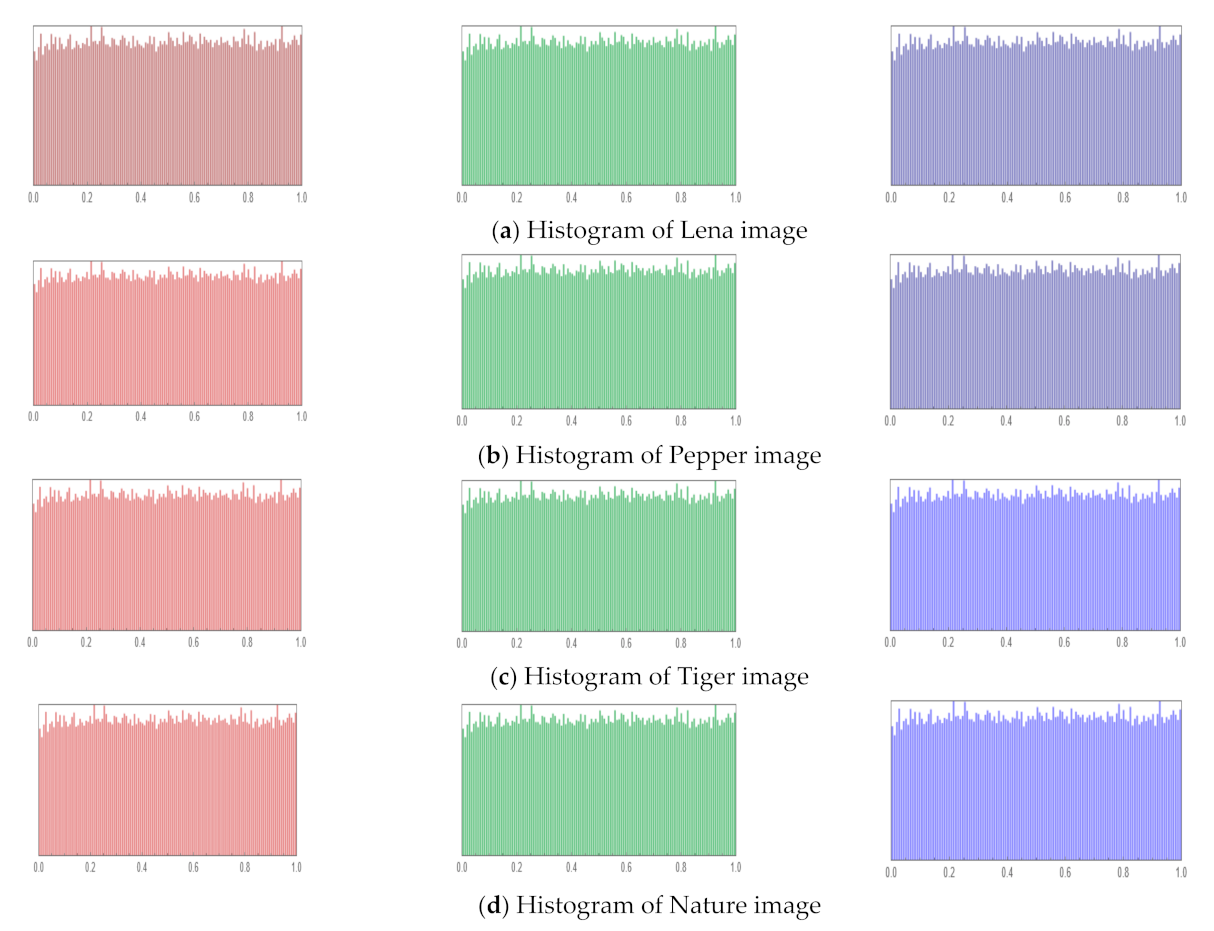
The way that an image’s pixel values are distributed is represented by the histogram. The histogram values in an encrypted image should have a uniform distribution, making it difficult for the attacker to discover anything about the image. The uniform distribution of pixel values in a coded image demonstrates the applicability of the proposed encryption approach. Figure 9 shows the encrypted images’ histograms.
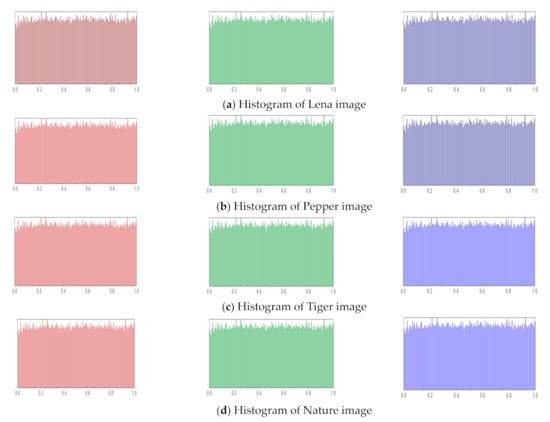
Figure 9.
The encrypted images’ histograms.
6.2.4. Pixel Correlation Analysis
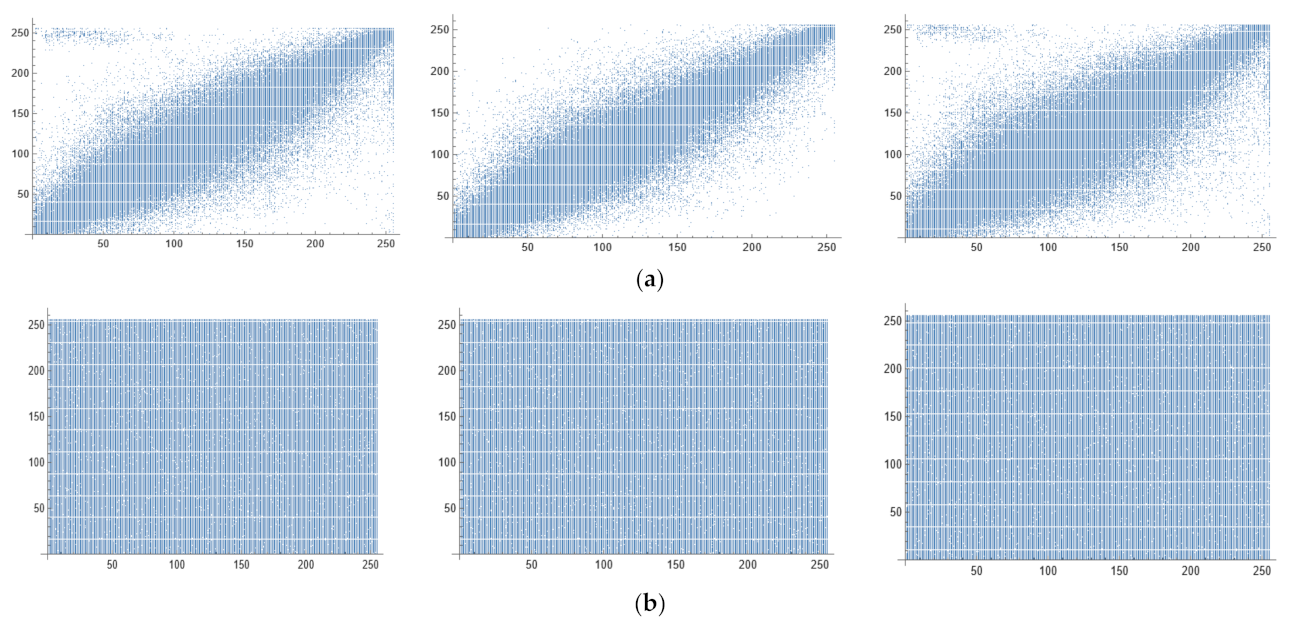
The Nature image has a strong correlation amongst every pixel along with its neighboring pixels, denoting minor variance for the value across the stated image. Among the objectives for a ciphered image is a lessening correlation amongst the adjoining pixels; lessening the correlation strengthens the encoding effect, leading to system overall security enhancement. Horizontal, vertical, and diagonal pixels are the most prevalent types of correlation. Table 6 lists the various correlation coefficients of the cipher image. Figure 10 depicts the relationship between the Nature image and its cipher. Plain image correlation is high and near to one. The correlation of the cipher images, on the other hand, is low and close to zero, indicating that the encrypted pixels in the encrypted images are valued and distributed randomly [28].

Table 6.
The different correlation coefficients of the R, G, and B cipher images.
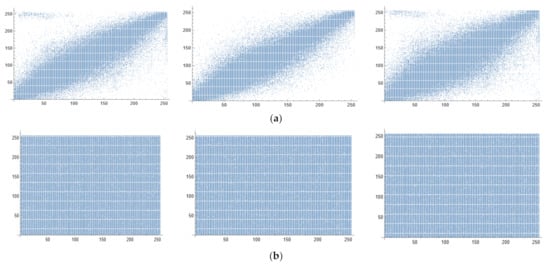
Figure 10.
The correlation for the Nature image and its cipher: (a) Relationship between neighboring pixels in horizontal, vertical, and diagonal directions of plain Nature image; (b) Relationship between neighboring pixels in horizontal, vertical, and diagonal directions of cipher Nature image.
6.2.5. Plaintext Sensitivity
The algorithm’s sensitivity towards plaintext signifies that a slight variation in plaintext results in enormous variation within ciphertext, which entails one of the cryptographic security analysis standards. The extent of plaintext sensitivity of image encryption approaches is measured experimentally using NPCR (number of pixels change rate) and UACI (unified average changing intensity). NPCR and UACI reflect the percentage and variation extent for a number of pixels in the ciphered image subsequent to random alteration of the pixel’s valuation in the original input image, respectively. The following are the formulas for calculating NPCR and UACI:
where W ∗ H stands for the image size, x (i, j) represents the pixel within the (i, j) coordinate related to the ciphered image correspondent to the original image, as well as x′ (i, j) denotes the pixel of the ciphertext image related to the variated plaintext image in the (i, j) coordinate. NPCR and UACI are anticipated to be valued at 99.6094 percent and 33.4635 percent, correspondingly. [29,30,31,32]. Four colored photos are selected to be tested for our suggested technique. Table 7 lists the NPCR and UACI tests valuation outputs.

Table 7.
NPCR and UACI listed output results.
6.2.6. Chi-Square Test
Figure 9 indicates that the ciphertext image’s histogram is distributed uniformly, withstands the statistical assaults, and is demonstrated using the chi-square test denoted as:
where denotes the true frequency for every pixel’s level, while e denotes the estimated one. The lower the value of the chi square, the greater the homogeneity and uniformity of the ciphertext images [33]. when the output value of chi square is below 295.25 for the confidence level a = 0.05, the test is declared as passed. Table 8 shows the value of the chi-square test in this research.

Table 8.
Chi-square test results.
6.2.7. PSNR Evaluation
The peak-signal-to-noise ratio (PSNR) can be utilized to determine an image’s quality. A strong image encryption algorithm should produce encrypted images having a low PSNR value. PSNR is calculated using the following formula:
Given that P(i, j) is the original image pixel value and c(i, j) is the encrypted image pixel value, than the mean square error (MSE) can be computed from the following equation:
In this article, the value of the PSNR test is demonstrated in Table 9.

Table 9.
Demonstrated values of PNSR and MSE.
6.2.8. Complexity Analysis
By using a big O notation to analyze the complexity of each operation required to encrypt or decode images, it is possible to determine the computational complexity of image encryption methods. The steps necessary to complete the encryption process are used to gauge the algorithm’s computational complexity. For a plain image with a size of M × N, the complexity time for the suggested algorithm is O ((M × N)/Bs), where Bs is the number of blocks in the image.
6.2.9. Comparison with Existing Methods
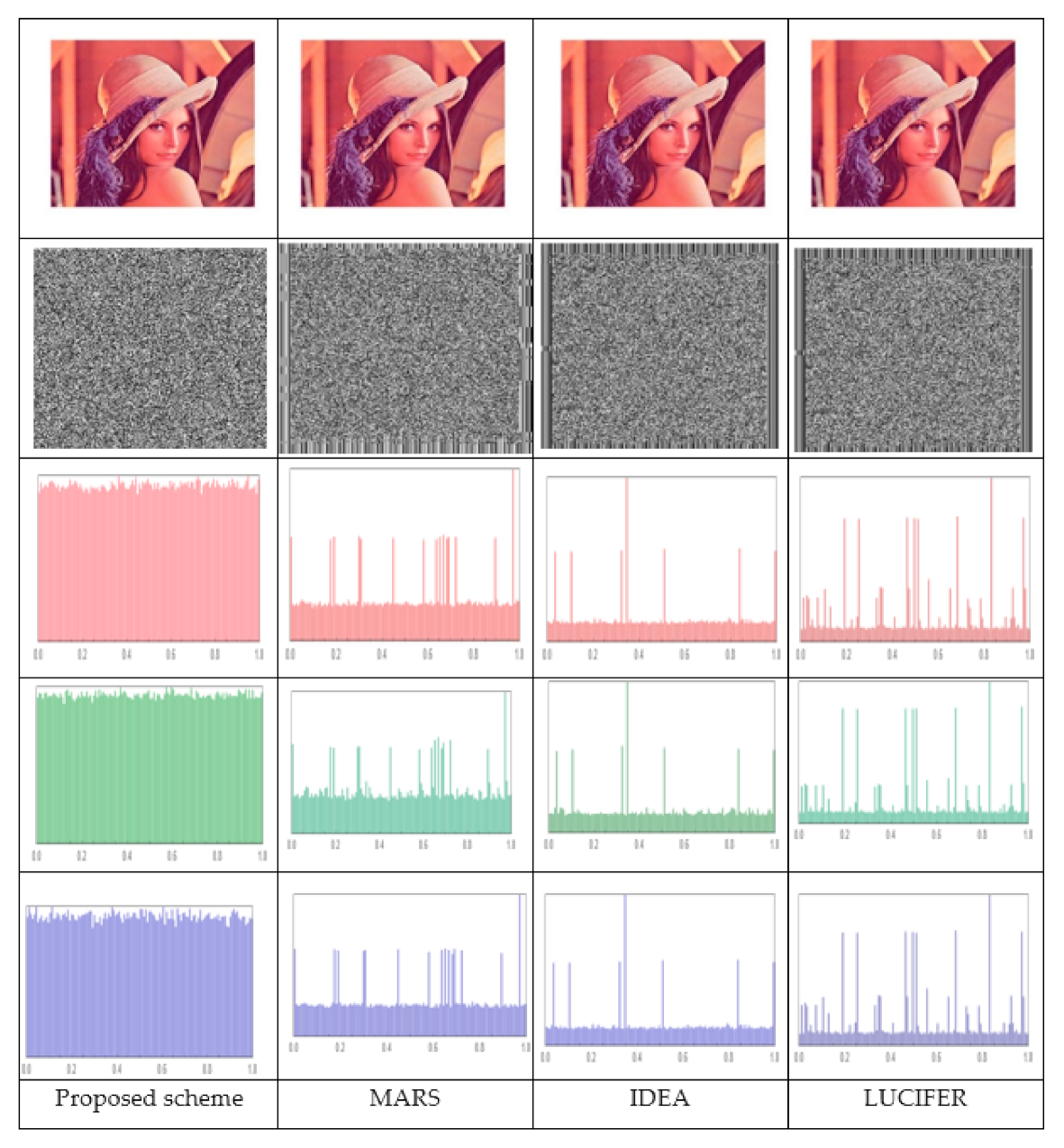
The suggested scheme is complemented with alternative methods, employing correlation analysis, entropy, NPCR, and UACI, and for the Lena image of size 512*512 in Table 10 comparing our system with other systems: MARS [13], IDEA [34], and LUCIFER [35]. Figure 11 shows histograms of plaintext Lena’s image and cipher image for the proposed scheme, MARS, IDEA, and LUCIFER concluding that, compared to the other systems, the histogram for the ciphered images in our suggested approach is the most uniformly distributed. These results imply that our cryptosystem has improved histogram assault resilience.

Table 10.
Comparative evaluation for new proposed scheme with MARS, IDEA, and LUCIFER cryptosystems.
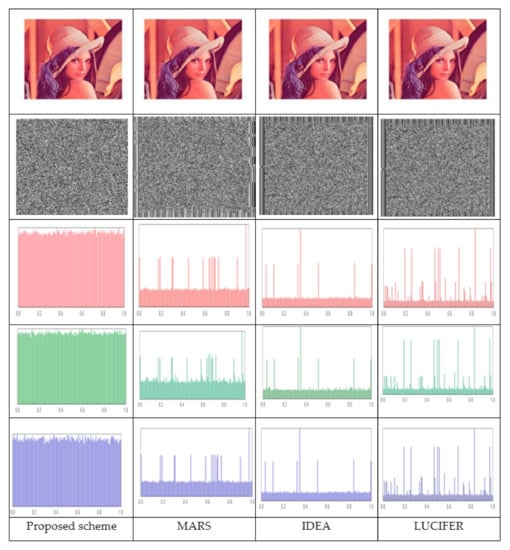
Figure 11.
Histograms of plaintext Lena’s image and cipher image for proposed scheme, MARS, IDEA, and LUCIFER.
7. Conclusions
A superior variant of MARS is offered in this article, a Niho function was added to the MARS cipher, and the subkeys generation was improved by using the Niho exponent, which is a subset of Boolean bent functions; this modification improved the ciphering procedure and achieved a higher level of confusion while retaining the MARS cipher’s linear and differential features. In addition, a strong relationship between S-box and the user key was established, as well as between rounds and S-box by making each round have a different S-box, so that even if we have repeated text, we will get distinct ciphertext. Additionally, we created a tight relationship between the ciphertext and the plaintext by splitting the ciphertext into smaller parts and Xoring them together to ensure that even if a single bit changes in the plaintext it will result in totally distinct ciphertext. It was discovered that MARS, LUCIFER, and IDEA had drawbacks when using images instead of text, including the histogram of the ciphertext, the correlation between the plain image and the cypher image, entropy, NPCR, and UACI.
Our new modified algorithm can withstand a variety of known assaults, statistical attacks, differential attacks, and high-speed performance, according to extensive experimentation and security analysis. The main points achieved in our proposed system is to overcome the letter repetition problem and make high randomization in the cipher image so that if one pixel will change it will affect whole cipher image and if we encrypt the same image with one pixel change it will cause different ciphertext to be obtained. Conclusively, in the case of changing the key size, it can be seen that it leads to a clear change in the subkeys and S-box generation, which causes strong confusion between the secret key and the ciphertext.
In the future, we will extend our proposed method with the help of the chaotic mapping function for improving robustness against a wide range of attacks. Moreover, we will try to make S-box generate dynamically when it is needed to reduce the space required.
Author Contributions
Conceptualization, F.A. and D.H.E.; methodology, F.A. and D.H.E.; software, F.A. and D.H.E.; validation, F.A. and D.H.E.; formal analysis, F.A. and D.H.E.; investigation, F.A. and D.H.E.; resources, F.A. and D.H.E.; data curation, F.A. and D.H.E.; writing—original draft preparation, F.A. and D.H.E.; writing—review and editing, F.A. and D.H.E.; visualization, F.A. and D.H.E.; supervision, F.A. and D.H.E.; project administration F.A. and D.H.E.; funding acquisition, D.H.E. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R238), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Data Availability Statement
Not applicable.
Acknowledgments
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R238), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Meyer, C.H. Cryptography-a state of the art review. In Proceedings of the VLSI and Computer Peripherals. COMPEURO 89, Hamburg, Germany, 8–12 May 1989; pp. 4/150–4/154. [Google Scholar] [CrossRef]
- Ahmed, H.E.-D.H.; Kalash, H.M.; Allah, O.S.F. Encryption quality analysis of the RC5 block Cipher algorithm for digital images. Opt. Eng. 2006, 45, 107003. [Google Scholar] [CrossRef]
- Li, S.; Zheng, X. Cryptanalysis of a chaotic image encryption method. In Proceedings of the 2002 IEEE International Symposium on Circuits and Systems (ISCAS), Scottsdale, AZ, USA, 26–29 May 2002; p. II. [Google Scholar] [CrossRef]
- Reddy, A.R. A Candidate Cipher for Advanced Encryption Algorithm and its Diffusion Strength. In Proceedings of the National Conference on Recent trends in Information Technology, Bangalore, India, 12 May 2007. [Google Scholar] [CrossRef]
- Helmy, A.; Saeb, M.; Mohamed, A.B. A Metamorphic-Enhanced MARS Block Cipher. Int. J. Comput. Sci. Commun. Secur. (IJCSCS) 2013, 3, 61–66. [Google Scholar]
- Ebrahim, M.; Khan, S.; Khalid, U.B. Symmetric Algorithm Survey: A Comparative Analysis. arXiv 2013, arXiv:1405.0398. [Google Scholar]
- Naguib, M.M.; Khater, H.; Mohamed, A.B. Improved Mars ciphering using a metamorphic-enhanced function. Int. J. Comput. Inf. Eng. 2014, 8, 7–10. [Google Scholar] [CrossRef]
- Aung, Y.Y.; Kyi, T.M.; Win, M.T. Security of Digital Images Using Cryptographic Algorithms. Int. J. Res. Innov. Appl. Sci. IJRIAS 2019, IV, 103–106. [Google Scholar]
- Li, N.; Zeng, X. A survey on the applications of Niho exponents. Cryptogr. Commun. 2019, 11, 509–548. [Google Scholar] [CrossRef]
- Nurgaliyev, A.; Wang, H. Comparative study of symmetric cryptographic algorithms. In Proceedings of the 2021 International Conference on Networking and Network Applications (NaNA), Lijiang, China, 29 October–1 November 2021; pp. 107–112. [Google Scholar] [CrossRef]
- Liu, Q. Two classes of permutation polynomials with Niho exponents over finite fields with even characteristic. Turk. J. Math. 2022, 46, 17. [Google Scholar] [CrossRef]
- Preneel, B.; Bosselaers, A.; Rijmen, V.; Rompay, B.V.; Granboulan, L.; Stern, J.; Murphy, S.; Dichtl, M.; Serf, P.; Biham, E.; et al. Comments by the NESSIE Project on the AES Finalists. 2000. Available online: https://www.researchgate.net/publication/2646004_Comments_by_the_NESSIE_Project_on_the_AES_Finalists (accessed on 28 April 2022).
- Kelsey, J.; Schneier, B. MARS Attacks! Preliminary Cryptanalysis of reduced-Round MARS Variants. In Proceedings of the Third AES Candidate Conference, New York, NY, USA, 13–14 April 2000; pp. 169–185. [Google Scholar]
- Dillon, J.F. Elementary Hadamard Difference Sets. Ph.D. Dissertation, University of Maryland, College Park, MD, USA, 1974. [Google Scholar] [CrossRef]
- Leander, N. Monomial bent functions. IEEE Trans. Inf. Theory 2006, 52, 738–743. [Google Scholar] [CrossRef]
- Canteaut, A.; Charpin, P.; Kyureghyan, G.M. A new class of monomial bent functions. Finite Fields Their Appl. 2008, 14, 221–241. [Google Scholar] [CrossRef]
- Charpin, P.; Gong, G. Hyperbent Functions, Kloosterman Sums, and Dickson Polynomials. IEEE Trans. Inf. Theory 2008, 54, 4230–4238. [Google Scholar] [CrossRef][Green Version]
- Mesnager, S. A new class of bent boolean functions in polynomial forms. In Proceedings of the International Workshop on Coding and Cryptograph WCC, Ullensvang, Norway, 10–15 May 2009; pp. 5–18. Available online: http://eprint.iacr.org/2008/512 (accessed on 16 April 2022).
- Mesnager, S. A new family of hyper-bent boolean functions in polynomial form. In Proceedings of the IMA 12th International Conference on Cryptography and Coding, IMACC, Cirencester, UK, 15–17 December 2009; Parker, M.G., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5921, pp. 402–417. [Google Scholar] [CrossRef]
- Mesnager, S. A new class of bent and hyper-bent Boolean functions in polynomial forms. Des. Codes Cryptogr. 2011, 59, 265–279. [Google Scholar] [CrossRef]
- Wang, B.; Tang, C.; Qi, Y.; Yang, Y.; Xu, M. A New Class of Hyper-bent Boolean Functions with Multiple Trace Terms. Report 2011/600. Cryptol. Eprint Arch. 2011. Available online: https://eprint.iacr.org/2011/600 (accessed on 22 April 2022).
- Wang, B.; Tang, C.; Qi, Y.; Yang, Y. A generalization of the class of hyper-bent Boolean functions in binomial forms. Report 2011/698. Cryptol. Eprint Arch. 2011. Available online: http://eprint.iacr.org/2011/698 (accessed on 10 May 2022).
- Mesnager, S.; Flori, J.-P. A note on hyper-bent functions via Dillon-like exponents. Report 2012/033. Cryptol. Eprint Arch. 2012. Available online: http://eprint.iacr.org/2012/033 (accessed on 10 May 2022).
- Dobbertin, H.; Canteaut, G.L.A.; Carlet, C.; Felke, P.; Gaborit, P. Construction of bent functions via Niho power functions. J. Combin. Theory Ser. A Vol. 2006, 113, 779–798. [Google Scholar] [CrossRef]
- Burwick, C.; Coppersmith, D.; D’Avignon, E.; Gennaro, R.; Halevi, S.; Jutla, C.; Matyas, S.M.; O’Connor, L.; Peyravian, M.; Safford, D.; et al. The MARS Encryption AlgorithmI. BM, 27 August 1999. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.35.5887 (accessed on 2 June 2022).
- Dewangan, C.P.; Agrawal, S.; Mandal, A.K.; Tiwari, A. Study of avalanche effect in AES using binary codes. In Proceedings of the 2012 IEEE International Conference on Advanced Communication Control and Computing Technologies (ICACCCT), Ramanathapuram, India, 23–25 August 2012; pp. 183–187. [Google Scholar] [CrossRef]
- Stoyanov, B.P. Pseudo-random bit generator based on chebyshev map. In Application of Mathematics in Technical and Natural Sciences; Todorov, M.D., Ed.; American Institute of Physics: College Park, MD, USA, 2013; Volume 1561, pp. 369–372. [Google Scholar] [CrossRef]
- Ghadirli, H.M.; Nodehi, A.; Enayatifar, R. An overview of encryption algorithms in color images. Signal Process. 2019, 164, 163–185. [Google Scholar] [CrossRef]
- Xu, X.; Feng, J. Research and Implementation of Image Encryption Algorithm Based on Zigzag Transformation and Inner Product Polarization Vector. In Proceedings of the 2010 IEEE International Conference on Granular Computing, San Jose, CA, USA, 14–16 August 2010; pp. 556–561. [Google Scholar] [CrossRef]
- Ahmad, J.; Larijani, H.; Emmanuel, R.; Mannion, M.; Qureshi, A. Secure Occupancy Monitoring System for IoT Using Lightweight Intertwining Logistic Map. In Proceedings of the 2018 10th Computer Science and Electronic Engineering (CEEC), Colchester, UK, 19–21 September 2018; pp. 208–213. [Google Scholar] [CrossRef]
- Ahmad, J.; Hwang, S.O. A secure image encryption scheme based on chaotic maps and affine transformation. Multimed Tools Appl. 2016, 75, 13951–13976. [Google Scholar] [CrossRef]
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. J. Sel. Areas Telecommun. 2011, 1, 31–38. [Google Scholar]
- Khanzadi, H.; Eshghi, M.; Borujeni, S.E. Image encryption using random bit sequence based on chaotic maps. Arab. J. Sci. Eng. 2014, 39, 1039–1047. [Google Scholar] [CrossRef]
- Chen, J.; Xue, D.; Lai, X. An analysis of international data encryption algorithm(IDEA) security against differential cryptanalysis. Wuhan Univ. J. Nat. Sci. 2008, 13, 697–701. [Google Scholar] [CrossRef]
- Sorkin, A. Lucifer, a cryptographic algorithm. Cryptologia 1984, 8, 22–42. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).