Abstract
This study examines the evolving use of social software to combat online disinformation by investigating Weibo users’ attitudes toward IP location disclosure as a measure of transparency and trustworthiness. We analyzed 49,579 posts (April 2022 to May 2023) from Weibo users about IP location disclosure, categorized the topics using LDA topic modeling within the frameworks of communication privacy management, the networked public sphere, and digital democracy, and conducted sentiment analysis. We constructed separate semantic networks for positive and negative terms to examine co-occurrence patterns. The results show that Weibo users are generally negative about this policy, as IP location may reveal personally identifiable information about individuals involved in discussions of online social/political events. Mandatory transparency, while intended to enhance accountability, functions as a mandatory visibility regime that reshapes privacy boundaries and undermines inclusive deliberation. The findings contribute to the exploration of the impact of government-mandatory information privacy disclosure policies on the implementation of platform functionality, as well as changes in user sentiment, information behavior, and components of social media discourse.
1. Introduction
The introduction of IP location disclosure on Weibo is driven by social events pushing for policies and regulations, intended to promote the platform in establishing a better communication order during special periods and to facilitate public monitoring of public interests. This function was initially tested and implemented on Weibo in March 2022. Weibo posts mentioning keywords such as Russia, Ukraine, and Kyiv would be displayed in their publishing location as sensitive to reduce the spread of fake news on social media platforms. In the following months, the feature gradually expanded to other major Chinese social media platforms such as Xiaohongshu (RED) and Douban. On 27 June 2022, the Cyberspace Administration of China (CAC) issued the Provisions on the Administration of Internet User Account Information, requiring that, starting from 1 August 2022, all online platforms publicly display users’ IP location attribution on their account pages. This regulatory shift also builds upon the Personal Information Protection Law of the People’s Republic of China (PIPL), which came into force in 2021. The PIPL defines personal information as data related to an identified or identifiable natural person, excluding anonymized information. Although IP locations are not explicitly mentioned, most legal interpretations treat them as personal information, similar to the General Data Protection Regulation (GDPR), because they can be used alone or in combination with other data to identify users.
Transparency tools have the potential to curb anonymity abuses and facilitate traceability and verification [1,2], but mandatory disclosure in highly regulated digital environments also exacerbates issues around privacy anxiety [3,4,5], geographic discrimination [6,7,8], and user self-censorship [9,10,11,12]. Understanding how users respond to these changes, particularly in terms of sentiment expression and topic engagement, is critical to assessing the broader implications of platform governance and digital identity disclosure [13,14].
Social media platforms provide a convenient medium for information acquisition and exchange [15,16] and are crucial for public opinion formation and sentiment expression [17,18]. As a social media platform with more than 500 million monthly active users and a coverage rate of more than 54.9% of Chinese Internet users [19], Weibo functions both as a primary venue for sharing personal experiences and perspectives on social issues [20,21] and as a platform for concentrating policy attention and piloting regulatory interventions [22,23]. By requiring each post to display the user’s IP location at the time of posting, Weibo not only redraws the users’ social graphs but also reconstructs the everyday management of privacy boundaries, forcing users to renegotiate their privacy rules [24].
A typical post displays the username, timestamp, content, and engagement metrics, followed by a vertically threaded comment section. The “IP attribution” label appears under the username in both posts and comments, indicating a province-level (e.g., Guangdong, Hebei) or municipality-level city (e.g., Shanghai, Beijing). To assist readers unfamiliar with the platform’s layout, Figure 1 virtually illustrates the interface of a Weibo post and comment thread, highlighting where the IP location label (e.g., Posted from: Beijing) appears under each username. Although the IP locations disclosed by the platform are limited to relatively coarse levels (e.g., mainland users are shown by province, municipalities like Beijing/Shanghai by city, and overseas users by country), users do not always interpret this change in terms of the probability of precise location. Instead, they perceive it as a shift in visibility, signifying a weakening of their power to control their identity. For instance, users whose IPs appear to originate from foreign countries or regions are often more likely to face identity scrutiny and labeling [25,26]. Users leverage geographic tags as clues to assess others’ credibility or political stance. Such judgments usually have little to do with the individual’s actual identity or intentions. Individuals from economically underdeveloped provinces or disaster-prone regions frequently endure prejudiced speculation and online discrimination [27,28,29].
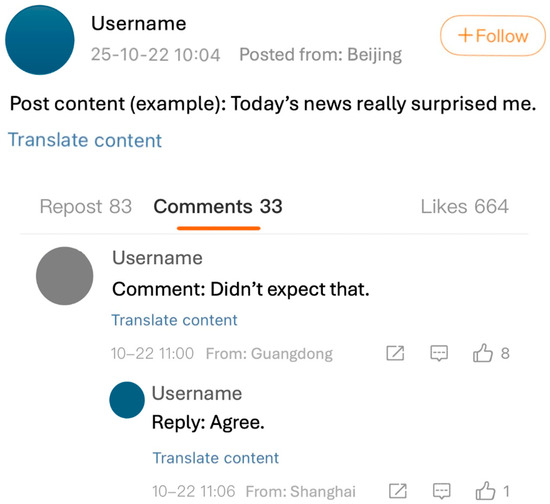
Figure 1.
Illustrative interface of a Weibo post and its comment thread.
According to the theory of Communication Privacy Management (CPM), when platform-mandated disclosures conflict with previously negotiated expectations of anonymity or contextual confidentiality, they trigger boundary turbulence, leading to confusion and renegotiation of the boundaries of information ownership, permissible use, and dissemination [30,31,32].
To analyze this phenomenon in depth, we develop a triadic framework, as illustrated in Figure 2. First, CPM emphasizes the dialectic between voluntary disclosure and privacy boundaries maintenance, explaining the boundary turbulence that users experience when forced to share geographic information. We analyze signals of boundary turbulence through sentiment analysis, exploring the extremes and trends of public sentiment towards IP location disclosure.
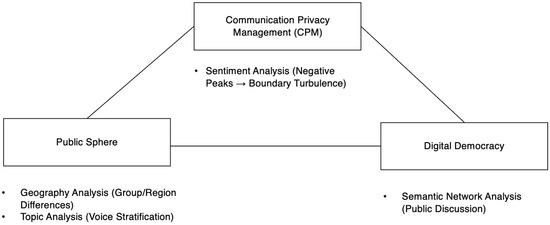
Figure 2.
Conceptual framework.
Second, Habermas’s networked public sphere [33] and Benkler’s economy of visibility [34] focus on how transparency tools reshape the field of public discourse: mandatory IP labels may stratify discursive authority according to geographic origin, valuing the voices of credible regions and marginalizing other groups [35,36,37]. In addition to group and regional differences, we combine sentiment distribution with topic modeling to explore the uneven distribution of public sentiment and IP location-related discourse topics, as well as the resulting voice stratification [38,39].
Finally, we situate these dynamics within the discourse of digital democracy. Although the digital democracy framework provides a valuable lens for understanding public discourse, its application in China’s social media context requires acknowledging certain limitations. Unlike Western contexts that emphasize civic participation and institutional pluralism, platforms like Weibo in China operate within a hybrid governance structure that intertwines state regulation, platform self-governance, and user engagement. Consequently, the manifestation of digital citizenship and public discourse is often constrained by policy logic and algorithmic moderation, prompting users to adjust their expression strategies and engage in self-censorship accordingly. Using semantic network analysis, we explore how identity transparency contributes to digital civic engagement and simultaneously creates new risks by exposing users [40,41,42].
Previous information disclosure initiatives on social media platforms have emphasized users’ commercial value. Users’ autonomous information disclosure behaviors, driven by intrinsic and extrinsic motivations, are often associated with incentives for platforms and merchants [43,44], such as fulfilling the platform’s needs for consumer information collection [45], marketing [46], and precise advertising placement [47].
Additionally, users’ socialization preferences influence their levels of information disclosure. Users pursuing visibility or relational capital tend to disclose more personal or contextual details to attract online discussion and engagement. In contrast, users who are risk-averse, privacy-sensitive, or less socially motivated tend to limit disclosure to a controlled audience or minimize information in necessary contexts [48,49]. While substantial research has been conducted on voluntary online identity disclosure, empirical research on mandatory IP location disclosure in highly regulated environments remains scarce. To address this gap, we pose three research questions (RQs):
- RQ1: What latent thematic structures emerge within discourse surrounding IP-based location labels?
- RQ2: How does sentiment distribution vary across these themes?
- RQ3: Under mandatory IP display, how do the networks of positive versus negative keywords differ?
We employ sentiment analysis, topic modeling, and semantic network analysis to (a) examine users’ sentiment distributions regarding the impacts of IP location disclosure, (b) identify related social topics in platform discussions, and (c) extract and correlate keywords from user-generated content classified as positive or negative, culminating in network visualization. Addressing these questions advances understanding of how governance policies interact with users’ privacy boundary management, thereby shaping emotional responses and the configuration of the digital public sphere.
2. Literature Review
This section adopts an integrative thematic literature review. It aims to synthesize theoretical perspectives on identity transparency and digital governance in social media. The review is organized into three main strands: (1) privacy and boundary management theories, which explain how individuals negotiate information disclosure; (2) digital democracy and networked publics, which situate IP disclosure within the dynamics of online participation and visibility; and (3) platform governance and censorship, which address how technological and policy architectures shape information flow and legitimacy. Together, these strands provide a multidimensional foundation for analyzing the impacts of mandatory IP location disclosure in the Chinese social media context.
2.1. Identity Transparency and Privacy Theories
Identity transparency on social media refers to platform-driven disclosure of users’ offline or online identity attributes (e.g., location, demographics, or verification status), typically justified by enhancements to credibility [50,51,52], accountability [53,54], and prevention of misrepresentation [55,56]. CPM theory views privacy as a dynamic boundary system negotiated between information owners and co-owners [57,58]. Individuals view privacy as a system of boundary governance: negotiated rules determine what information can be disclosed and what must be retained [59,60,61]. When platforms can unilaterally externalize contextual information, previously stable rules of anonymity, audience stratification, and contextual confidentiality are disrupted, creating boundary turbulence [30,62,63]. This turbulence manifests itself in users’ attempts to recalibrate their disclosure strategies (e.g., linguistic self-censorship, shifting sensitive discussions to private channels) or in stronger disputes over perceptions of information ownership infringement [10,64].
At the empirical level, CPM has been applied to multiple types of social media scenarios. First, adolescent and family contexts: De Wolf [65] distinguishes between “personal” and ‘interpersonal’ privacy management and suggests that “networked frustration” (i.e., a sense of powerlessness over the individual’s control over the flow of information) can reinforce adolescents’ efforts to negotiate interpersonal boundaries, especially when sharing personal information or sexually explicit material with parents, thus extending the explanatory power of CPM to multi-actor collaboration. Second, in human-algorithmic interactions, Craig and Child [66] identify multiple privacy disorders triggered by recommender systems and their recalibration strategies, demonstrating how opaque and biased algorithmic inferences can spawn new boundary negotiations, raising concerns over fairness, accountability, and discrimination in automated decision-making [67,68,69]. Third, gender-oriented differences in boundary management. Gender significantly moderates the association between privacy concerns and self-disclosure: women report higher privacy concerns, adopt stricter disclosure boundaries, and exhibit stronger boundary turbulence in mandatory disclosure contexts [70].
Finally, digital identity research indicates that mandatory transparency reinforces regional or socio-political categories, which in turn affects stigma, trustworthiness, and discrimination structures [71,72,73,74]. These studies suggest that platform-imposed identity transparency is not a neutral mechanism for enhancing authenticity, but rather a governance intervention that reconfigures privacy rulemaking, sentiment responses, and collaborative relationships among actors.
2.2. Digital Democracy and Networked Publics
Mandatory IP location disclosure intersects with discussions of digital democracy and networked publics. First, from Habermas’s ideal of the public sphere, democratic discourse relies on inclusive participation and rational-critical debate [33]. However, when each statement is attached to geographic information, the credibility of the discourse can be stratified by IP location labels: voices from institutional or mainstream regions are amplified by algorithms and user preferences [75,76,77] while expressions from diaspora, peripheral, or politically sensitive regions may be questioned, ignored, or even stigmatized [78,79,80,81,82].
Second, from the perspectives of the visibility economy [33] and the networked public sphere [34], IP location disclosure serves more than assisting platform content governance and misinformation reduction. The economy of visibility considers that platforms allocate users’ attention through interface design and algorithms [83,84,85], and that the location and visibility of various information elements are a form of resource allocation [86], in which case IP location disclosure, as a new and visible element, attracts more far-reaching attention and discussion on public social media platforms. The networked public sphere, on the other hand, reveals how public discourse is shaped under the dual mediation of technological architecture and policy logic [87,88,89]. Under these twofold mechanisms, IP location both provides algorithms and users with cues to quickly assess the credibility of information sources and may also contribute to the exclusion of specific groups due to geographical stereotypes and discrimination. This dynamic aligns with Yu and Margolin’s [29] concept of topic territoriality, which argues that revealing identity cues, such as IP location, turns conversational spaces into “territories” claimed and patrolled by perceived in-groups. As a result, out-group participants tend to withdraw, leading to topic homogeneity and reduced intergroup deliberation within networked publics.
Third, from the perspective of digital citizenship [90,91], transparency based on identity labeling has a dual effect. On the one hand, it reduces uncertainty about the source of information to a certain extent, enhances accountability, and improves the efficiency of collaboration [92,93,94]. Weibo initially introduced IP location disclosure to address the proliferation of misinformation in discussions of social events. Disclosing the actual IP location helps identify potential firsthand witnesses more quickly, thereby speeding up the correction of rumors. On the other hand, as the mechanism becomes normalized and extended, it may also trigger a chilling effect: vulnerable or high-risk groups may choose to remain silent for fear of being fleshed out, reported, or cyberbullied, thus limiting the plurality of the networked public space [95,96,97].
2.3. Platform Governance and Censorship
Platform governance studies usually define platforms as governance entities that regulate information flow and user behavior through technological architectures, policy tools, and implementation practices [98,99,100] In this vein, IP location disclosure is a soft governance technique embedded in content auditing, authenticity verification, and the labeling of digital identities, rather than complex governance initiatives such as post deletion and account blocking [101,102]. Between these extremes lies a form of semi-hard governance, typified by practices such as shadow banning, which restrict visibility and participation without explicitly removing content [103,104].
Based on the governance goal of combating misinformation, the platform allocates part of the credibility assessment to the user, so that the user assumes responsibility for authenticating “self/others” content, which reduces the cost of front-end auditing and manual verification [105,106]. Platforms increasingly rely on distributed accountability mechanisms that integrate user participation, algorithmic moderation, and third-party fact-checking systems. While these systems aim to enhance informational integrity, they also raise debates over bias, transparency, and procedural legitimacy [107]. Complementing these platform-level studies, Jin, Guo, and Lu [25] provide cross-national evidence indicating that public support for digital surveillance policies largely depends on political trust and cultural context. Citizens in high-trust societies are more likely to perceive surveillance as a protective mechanism, whereas those in low-trust societies are more likely to view it as coercive.
At the level of algorithmic governance, when digital labels and specific content are used as characteristic variables for credibility, risk, or authenticity assessment, they directly affect the probability of exposure and visibility of the content [83,108]; and algorithms, guided by existing training data and policy thresholds, may institutionalize established suspicions or downgrading of specific groups, replicating and expanding the original structural inequality [109]. Empirical evidence from Guo, Li, and Yang [110] further demonstrates that Weibo’s IP location disclosure, intended to promote civility and accountability, paradoxically increased location-based incivility. Geolocation served as an ideological cue that intensified intergroup conflicts, suggesting that such “soft governance” features may reproduce polarization rather than foster civil discourse.
Existing disclosure research focuses on voluntary disclosure in the context of business personalization [111,112]. Yet, there is a lack of systematic empirical evidence on public perceptions and discussions of mandatory disclosure in the context of public governance and democracy. Based on this gap, this paper examines how users narrate the legitimacy of platform governance, negotiate privacy boundaries under mandatory transparency, and perceive and express censorship risks through sentiment analysis, topic modeling, and semantic network analysis to assess whether IP location disclosure is internalized as a protective governance measure that contributes to the enhancement of information governance on platforms, or whether it is resisted as a measure that reinforces the inequality of rights between platforms and users.
3. Methodology
Given the introduction of IP location disclosure as a new mandatory information disclosure measure and the social platform’s display function, users’ sentiment representation, information provision, communication behaviors, expression methods, and discussion topics are likely to change. Therefore, this research focuses on users’ postings on IP locations in Weibo to address the following three research questions. Figure 3 illustrates the methodology framework developed to address the research questions. After the data of posting and forwarding contents of Weibo users are collected by using web crawlers and then data preprocessing, topic analysis based on LDA topic modeling is performed to explore the results of sentiment analysis of Weibo users’ attitudes about IP location disclosure, then conduct semantic network analysis of the keywords identified as positive and negative sentiments, as well as visualized and presented, respectively.
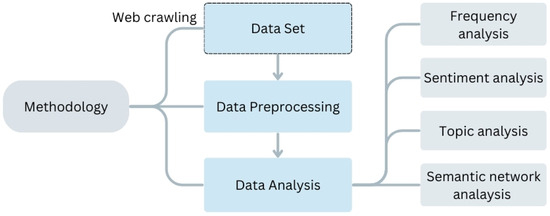
Figure 3.
Methodology framework.
3.1. Data Collection
To collect a large amount of data, this research used web crawlers to gather a corpus of web pages indexed by search engines [113]. Data was collected using a Python 3.11.3-based web crawler with advanced search capabilities. We used a combination of keywords, including IP location, IP display, and IP address, to retrieve relevant public Weibo posts. The data collection period was from 29 April 2022 to 26 May 2023. The start date marks the launch of Weibo’s mandatory IP location display initiative, and the one-year period ensures sufficient time to capture users’ reactions and discussion patterns. We initially collected 73,216 posts and, after filtering, retained 49,579 for analysis.
3.2. Data Preprocessing
In the data preprocessing stage, we preprocessed the corpus to improve accuracy and analytic usability. As shown in Figure 4, we first removed duplicate and reposted posts. Duplicates were identified by comparing post IDs and exact text strings, and reposts automatically generated by Weibo’s forward function were excluded to avoid redundancy. After this step, 64,870 posts remained.
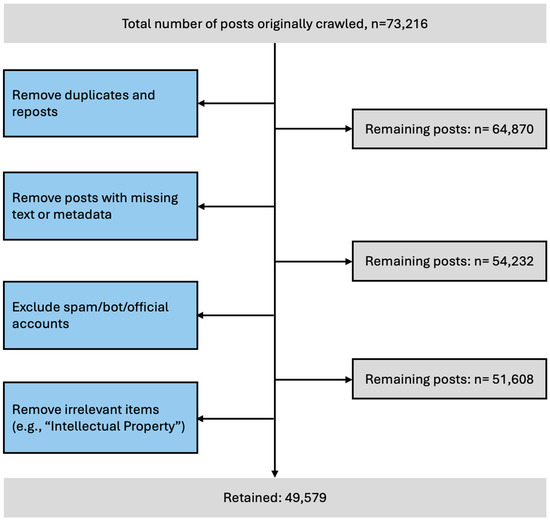
Figure 4.
Data filtering process for Weibo posts.
Second, we removed posts with missing or incomplete text, such as those containing only URLs, mentions, hashtags, or emoji symbols without substantive content. After this step, 54,232 posts remained.
Third, User accounts were filtered based on platform metadata to focus on individual users and reduce institutional or automated content. Official accounts with Weibo verification badges for government, media, or organizations (blue or gold V) were removed. Suspected spam or bot accounts were deleted if they posted more than 200 times per day for three days, had a follower-to-following ratio below 0.01, and had fewer than 50 followers. Private and individual accounts without verification badges and with moderate posting activity (≤50 posts per day) were retained, as they better reflected personal opinions [114]. Verified celebrity or influencer accounts were retained only when the IP address was visible; accounts without IP information were excluded from IP-based analyses. After this step, 51,608 posts remained.
Last, posts were considered irrelevant if they did not explicitly mention or discuss the IP location disclosure feature. Although Intellectual Property is a widely discussed topic on Chinese social media, it is unrelated to Internet Protocol (IP), which was the focus of this study. These irrelevant posts were identified using keyword comparison and manual review of ambiguous items, resulting in 49,579 posts retained for further processing.
The next step was to process the text content, which required removing duplicates and meaningless text noise. Additionally, Jieba in Python was used for Chinese word segmentation. Finally, we constructed, integrated, and refined stop-word lists and manually adjusted them based on data collection results and practical considerations.
3.3. Data Analysis
The term frequency-inverse document frequency (tf-idf) weighting method is used to determine the relevance of words in documents [115]. In this research project, the main keywords are weighted by tf-idf [116] for sentiment type determination and classification.
Latent Dirichlet Allocation (LDA) Topic Modeling is an unsupervised machine-learning technique [117] that does not require manual annotation. As a generative statistical model, it can reveal the underlying semantic structure in a large group of documents, showing the relationship between text and topics [118]. This research employed LDA topic modeling to classify and identify topics for corresponding topic sentiment analysis, exploring the primary scenarios of IP location disclosure on the Weibo platform and the distribution of user sentiment across different topics.
After sentiment annotation of the cleaned data and semantic web analysis, network visualization was performed by extracting words identified as positive or negative. By generating a keyword matrix and conducting network visualization, different narratives regarding IP location disclosure emerge, enabling a better understanding of the content and the specific considerations underlying users’ support and opposition.
4. Results and Discussion
4.1. Data Collection Result
Using “IP location” as the keyword and the time range from 29 April 2022, to 26 May 2023, Weibo public postings were crawled, yielding a total of 73,216 records. As shown in Table 1, the acquired data include Weibo content, publish time, username, IP location, and gender. After removing text noise and duplicates and completing data cleaning, a total of 49,579 items of data are available for analysis.

Table 1.
Example of collected Weibo data.
Since the implementation of the IP location disclosure function was constantly adjusted and improved during the initial period, the disclosure of different users was not the same, mainly due to (1) the initial display of IP location only in the comment section, which was gradually and comprehensively extended to the original Weibo posts and homepages of individual users; (2) users’ late upgrading version of Weibo; (3) different user’s account type. Occasionally, because celebrities’ real-name authentication accounts could turn off IP location disclosure before it became mandatory for all registered users, some user data in the IP location column may be empty.
Figure 5 illustrates the trend in public discussion of IP addresses. Peaks in postings correspond to policy milestones, such as the August 2022 entry into force of the “Regulations on the Management of Internet User Account Information” issued by the China Internet Network Information Center (CNNIC), which requires Internet accounts to fill in their real occupations and IP belongings to be disclosed, and the registration of accounts in some professional fields is required to provide verified materials. There was a notable decline in late October 2022, which may be associated with the public’s temporal shift in attention amid concurrent national events. However, the overall pattern shows sustained interest and discussion, particularly during the enforcement phase.
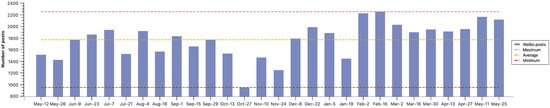
Figure 5.
Volume of posts about IP location on Weibo.
4.2. Sentiment Analysis
After calculating the sentiment scores of the texts and categorizing the sentiment tendencies based on the results, the overall sentiment analysis of the discussions related to IP location is performed. We used SnowNLP, a Chinese natural language processing toolkit, to analyze the sentiments. Each post received a score ranging from −50 (strongly negative) to +50 (strongly positive). Posts were classified as positive (>10), neutral (−10 to 10), or negative (<−10). Gender information was extracted from user profiles, which Weibo requires during registration. If no gender information was available, the post was marked as “unspecified” and excluded from gender-based comparisons.
To examine whether missing gender and location data introduced systematic bias, a chi-square test compared gender proportions between the complete and incomplete subsamples (complete group: 8919 males and 37,037 females; incomplete group: 730 males and 2893 females). The difference between the two groups was not statistically significant (χ2(1, N = 49,579) = 0.28, p = 0.60), indicating that data missingness was random with respect to gender distribution and thus unlikely to affect the study results.
Figure 6 juxtaposes the sentiment geo-heat map (left) with the geo-gender-sentiment Sankey diagram (right). In the geographic heat map, the dots represent provinces/overseas regions; the color is determined by the sentiment mean (darker green indicates more positive sentiment, darker red indicates more negative sentiment), and the size corresponds to the number of posts. The central region (Henan, Hubei, Hunan) shows the strongest negative tendency, while the eastern and overseas nodes have relatively flat sentiment.
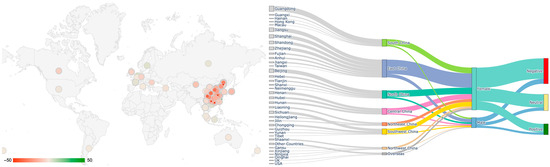
Figure 6.
Demographic sentiment analysis of Weibo IP location disclosure.
In the Sankey diagram, posts converge from the provinces (left) to the seven regions, then diverge by gender, and finally flow by sentiment category. The red negative streams are thickest in the East and Central regions. In conjunction with CPM theory, these deep red hotspots indicate areas of high border turbulence, where users are compelled to reassess their anonymity and contextual privacy rules in the face of the forced disclosure of geographic information. Regions such as the Northwest and Overseas are marginalized, indicating a clear stratification of discursive visibility and participation. Results from chi-square tests and effect size analyses indicate a highly imbalanced overall sentiment distribution (χ2 = 5372.3, p < 0.001), with negative posts (≈48%) far exceeding neutral (31%) and positive (21%) posts. Additionally, significant regional variations in posting volume were observed (χ2 ≈ 12,200, p < 0.001). Posts were highly concentrated in East China (33.7%), followed by North China (15.2%) and South China (13.6%).
Gender differences constitute a significant dimension of discursive stratification. A chi-square goodness-of-fit test indicated a highly significant gender imbalance in posting volume (χ2 = 38,821, p < 0.001). Female users accounted for approximately 80.6% of all posts, while male users accounted for 19.4%. This suggests that women were the dominant participants in the public discourse surrounding IP location disclosure. Prior research indicates that women have higher social media usage rates and activity levels than men [119] and also show higher concern for social issues [120,121]. Besides, women tend to have greater privacy concerns and a tendency to activate privacy settings [122,123], and this differential level of gender-oriented anxiety is because women tend to have a higher risk of being cyberbullied [124,125], together with the possibility of online threats translating into offline harassment [126].
Figure 7 presents the monthly distribution of sentiment tendencies from May 2022 to May 2023. The trajectory reveals how public attitudes toward IP location disclosure evolved during its rollout, reflecting both initial boundary turbulence and subsequent adaptation. In May 2022, when the feature was first introduced, negative sentiment sharply exceeded the average, while positive and neutral expressions were relatively suppressed. This phase aligns with the boundary turbulence concept, as characterized by the CPM theory, in which users’ original anonymity and contextual privacy rules are disrupted by the platform’s mandatory disclosures, compelling them to renegotiate the boundaries of their control over personal information [127].
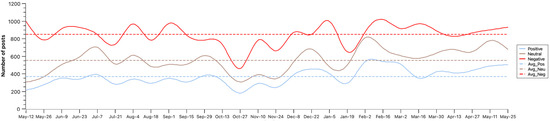
Figure 7.
Sentiment tendencies over time.
Negative sentiment rose again in August 2022, when the Cyberspace Administration of China (CAC) formally implemented mandatory IP attribution regulations, extending to real-name registration and IP display for professional accounts. Figure 8 shows that the interrupted time-series model revealed a significant change following the August 2022 CAC enforcement. Before enforcement, negative sentiment declined steadily (β = −0.036, p = 0.003), suggesting gradual adaptation to the IP disclosure feature. However, the enforcement was associated with a significant immediate increase (β = +0.082, p = 0.024) and a positive post-intervention slope (β = +0.032, p = 0.008), indicating that public discontent resurged after the policy was officially implemented.
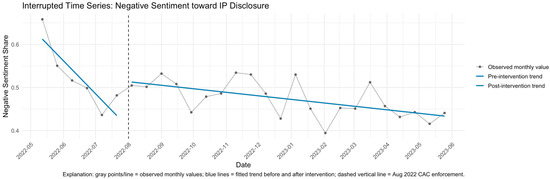
Figure 8.
Interrupted time-series analysis of negative sentiment toward IP location disclosure.
The Durbin–Watson statistic (DW = 2.03, p = 0.31) confirmed the absence of autocorrelation, suggesting a well-specified model. These results demonstrate that the CAC regulation induced both an immediate and a sustained increase in negative sentiment. The incident led to renewed questions about the strength and legitimacy of regulatory power. When platform governance policies exacerbate inequalities in discursive visibility, the public’s trust in the institutional process may be undermined [128,129].
Since October 2022, the sentiment trend has gradually stabilized, with the curves converging to the mean. In March 2023, there was a slight increase in positive sentiment and a decrease in negativity, indicating that users are gradually becoming accustomed to IP visibility and that this feature is entering the institutionalization and usage norm. However, this does not mean that the discourse environment has returned to neutrality: the structural regulation of visibility by platforms continues to shape the distribution of discourse, mainly because the mandatory disclosure emphasized by CPM has a profound impact on the management of users’ privacy boundaries and identities [58,130].
4.3. Topic Analysis
To further understand how Weibo users respond to mandatory IP location disclosure at the discourse level, we used LDA topic modeling and sentiment analysis to mine public opinion content in this study. As shown in Figure 9 and Figure 10, to determine the optimal number of topics, we trained a series of LDA models with K = 1 to K = 10. Model performance was evaluated using two standard metrics: (1) topic coherence (c_v), which measures the semantic consistency among high-probability words within a topic, and (2) log perplexity, which assesses the model’s predictive power. The coherence scores peaked at K = 7 (c_v = 0.4775), indicating the best topic interpretability, while the perplexity curve continued to decrease modestly. Therefore, we selected K = 7 as the optimal number of topics for subsequent analysis.
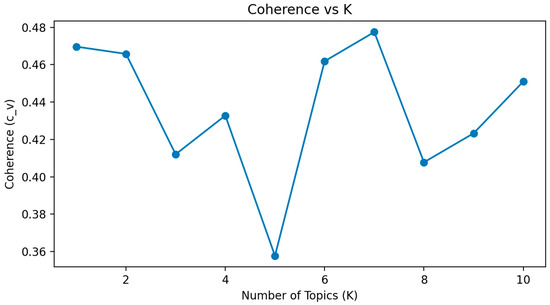
Figure 9.
Coherence vs. Number of Topics (K).
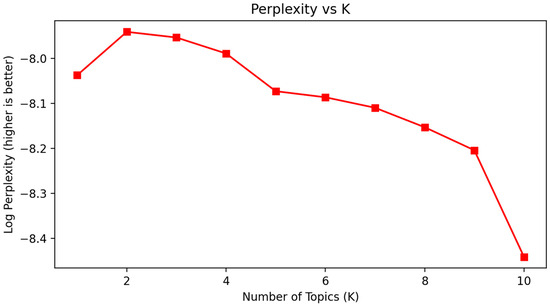
Figure 10.
Perplexity vs. Number of Topics (K).
By comparing the coherence and interpretability scores, seven topics were selected (as shown in Table 2), covering a wide range of content from macro-political issues to micro-daily life, namely: (1) Display and Change of Location, (2) Global Political and Controversial Affairs, (3) Social Issues in the Chinese Context, (4) Traveling, (5) Internet, (6) Social Network, and (7) Daily Life Posts. These seven topics reflect not only users’ everyday conversations but also their interpretive responses to the implementation of the IP-location disclosure policy. Topics related to international politics and domestic social affairs (Topics 2 and 3) indicate that users often perceive IP attribution as connected to broader governance mechanisms, including the regulation of online expression and the visibility of regional identity. Discussions focused on platform infrastructure and functions (Topics 5 and 6) highlight concerns about changes in the dynamics of online participation, such as perceived shifts in accountability, identity management, and content visibility.

Table 2.
Topic classification result.
Figure 11 shows that negative sentiment dominates for all six topics, except for the travel-related topic (Topic 4). Among them, negative sentiment is significantly higher than positive and neutral for topics related to politics (Topic 2), domestic controversial events (Topic 3), and content related to platform governance (Topics 5 and 6), reflecting users’ anxiety, mistrust, and antipathy towards the intersection of digital infrastructure and social control. Topic 1 (Display and Change of Location) centers on users’ experiences with the technical functionality of the new feature, including display errors and location mismatches. The prevalence of dissatisfaction within this topic points to users’ concerns about the reliability of the policy implementation and its implications for self-presentation and privacy management. In contrast, Topics 4 (Traveling) and 7 (Daily Life Posts) are more loosely connected to the policy itself and exhibit more neutral or positive sentiment, reflecting routine social sharing less affected by regulatory concerns. Together, these thematic and affective patterns suggest that user sentiment toward the policy encompasses a range of perspectives, from pragmatic concerns about technical performance and usability to more reflective considerations of transparency, identity, and the evolving relationship between users and platform governance.
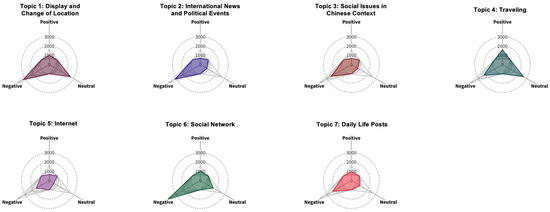
Figure 11.
Sentiment tendency distribution for each topic.
Figure 12 presents the relationship between text distribution (i.e., the distribution of keywords across the text) and sentiment mean, which is overall negatively correlated. The hotter the discussion of a topic, the lower its sentiment mean. It is worth noting that Topic 1, which deals with territorial display itself (e.g., display errors, modification failures, etc.), also shows a negative tendency, indicating users’ strong dissatisfaction with the decline in the ability of self-disclosure, which is a response to the failure of negotiating the right to privacy. The description of the social network environment in Topic 6 further expresses concerns about labeling, geographic discrimination, and human searches, revealing how platforms’ visibility algorithms expose users to potential cyberattacks.
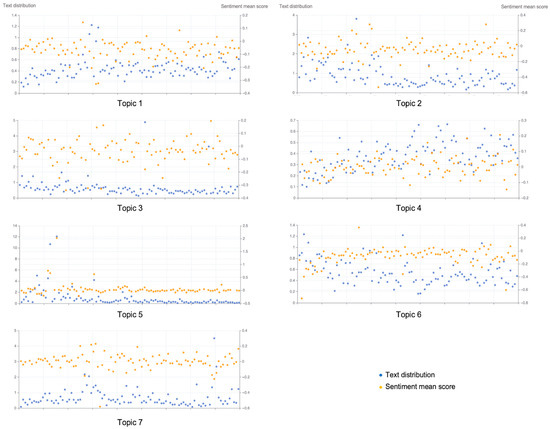
Figure 12.
Text distribution and sentiment mean score of each topic.
4.4. Semantic Network Analysis
To uncover the underlying structure of users’ attitudes toward IP location disclosure, we performed semantic network analysis by separating keywords tagged with positive and negative sentiment. Figure 13 and Figure 14 visualize the co-occurrence patterns in these two affective categories.
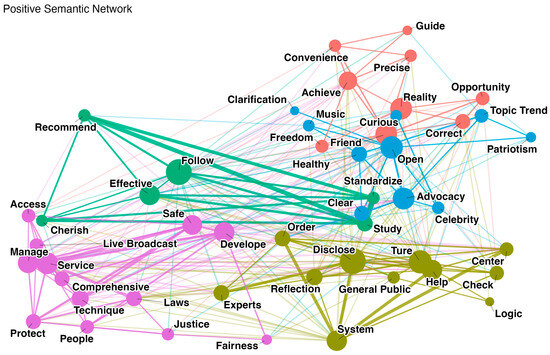
Figure 13.
Network visualization of words identified as positive sentiment.
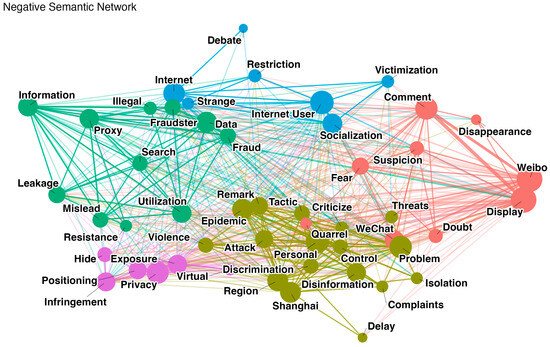
Figure 14.
Network visualization of words identified as negative sentiment.
The semantic network analyses for the positive and negative corpora were conducted independently. TF-IDF weighting was used both to filter out low-information or overly frequent words and to compute pairwise correlations between word TF-IDF vectors across documents, which served as edge weights.
The co-occurrence window was defined at the document level: two words were considered co-occurring if they appeared in the same Weibo post. Pairwise Pearson correlations between TF-IDF vectors were calculated to form a symmetric word–word correlation matrix, and only edges with |r| ≥ 0.40 were retained. The resulting matrix was converted into a weighted undirected graph G = (V, E). Semantic communities were detected using the Leiden algorithm (resolution = 1.15) to balance modular clarity and granularity. Visualization employed a compact force-directed layout with mild community attraction (α = 0.37, iterations = 3, scale = 0.95), allowing nodes within the same community to cluster while preserving overall structural balance.
In the positive sentiment network (Figure 13), five coherent semantic clusters can be identified, centering on institutional governance, technological functionality, civic participation, personal empowerment, and information order. Frequent co-occurrences of terms such as “standardize,” “clear,” “safe,” “effective,” and “system” indicate that users generally regard IP location disclosure as a governance measure that enhances transparency, credibility, and information security. Clusters including “laws,” “justice,” and “fairness” reflect users’ expectations that the policy will strengthen institutional accountability and procedural order, while keywords such as “study,” “advocacy,” and “public” point to an emerging civic awareness of information governance. Meanwhile, terms such as “follow,” “recommend,” and “service” highlight users’ recognition of the platform’s technical reliability and service efficiency.
Specifically, users perceive this feature as a positive step for the platform to enhance information transparency, risk management, and technological legitimacy. Platforms are expected to play a role in clarifying misunderstandings, ensuring security, and improving communication efficiency in the complex information ecosystem. This perception is closely related to platform governance legitimacy in digital democracy theory [131], reflecting users’ identification with governance mechanisms that have clear rules, credible mechanisms, and effective enforcement [132].
In the negative sentiment network (Figure 14), five semantic clusters can be identified. These clusters indicate that users’ concerns about IP policies extend beyond narrow technical privacy issues, reflecting broader insecurities and distrust toward governance mechanisms. For instance, the clustering of “privacy” with terms like “exposure,” “infringement,” and “positioning” reveals users’ anxieties about being forced into visibility and the erosion of personal boundaries. Simultaneously, the co-occurrence of terms like “display,” “region,” “discrimination,” “attack,” and “control” reflects users’ fears of being categorized, judged, or even excluded based on their geographic identity. Other clusters focus on questioning platform intentions (e.g., “mislead,” “utilization,” “tactic”) and skepticism toward network environments and governance effectiveness (e.g., “fraud,” “proxy,” “illegal,” “leakage”). Overall, this semantic network visualizes users’ multidimensional risk perceptions triggered by mandatory IP disclosure.
This semantic network structure reveals that when users perceive governance technologies as weakening rather than protecting individual agency, the platform’s normative legitimacy slips into functional coercion. Mandatory information disclosure prevents users from engaging in critical or sensitive discussions, weakening the participatory basis of digital democracy [133,134].
Although political factors inevitably shape online discourse in China, this study does not directly analyze state-level control or censorship dynamics. Instead, it focuses on the meso level of digital governance, examining how platform mechanisms of transparency and legitimacy are interpreted and emotionally responded to by users in everyday online interactions.
5. Discussion and Suggestions
On Chinese social media, IP-location disclosure has swiftly spread from Weibo to other platforms, transforming the display of geographic information into a new obligation for users. This study used “IP location” as a keyword and applied text mining, sentiment analysis, topic modeling, and semantic network analysis to reveal how this feature, under the combined lenses of CPM theory, the networked public sphere, and digital democracy, provokes complex user reactions and reshapes public discourse.
First, our findings indicate that introducing a new platform feature can significantly alter the online environment. From a CPM perspective, mandatory disclosure directly disrupts users’ negotiated privacy boundaries: each time a platform update or policy rollout occurs, spikes in negative sentiment signal boundary turbulence, indicating that users must recalibrate their rules for what to make public versus what to keep hidden. Although the policy aims for transparency and accountability, it has triggered heightened privacy concerns and social pressures, leading users to feel under surveillance, restrict self-disclosure of personal information [28], engage in self-censorship, and adopt depoliticized expressions [27]. Topic classification and sentiment distribution further demonstrate that when IP location becomes salient in discussions of significant events (e.g., epidemic, international affairs), its overall effect is adverse, shifting the course of debate and intensifying public emotional volatility.
Our findings also resonate with research on social network formation and homophily, which suggests that users tend to form ties based on shared identities or contextual cues [135,136,137,138,139]. Building on studies of peer influence and identity-based clustering [140,141,142,143], IP-based visibility can be seen as facilitating the emergence of micro-level peer networks that reinforce collective sentiment patterns. Such alignment amplifies emotional contagion and polarization [26,144], indicating that mandatory disclosure not only personalizes accountability but also reshapes relational boundaries and the social topology of online publics.
Second, through the lens of the networked public sphere, geographic labeling produces clear stratification of voices: discussion volume and visibility for central regions and female users are amplified, while peripheral areas and minority groups fall silent or become stigmatized. Because users, platforms, and government policy do not share symmetrical rights and responsibilities, discourse on IP disclosure is dominated by negative sentiment. Users who are forced to relinquish privacy find that the platform and regulators, expected to safeguard their security, have failed to do so, instead spawning more discriminatory and hostile speech [145,146].
Ultimately, the digital democracy perspective requires consideration of the impact of technological interventions on the legitimacy of public discourse. Allowing users to censor the validity and authenticity of speech based on the user’s IP location to circumvent the spread of fake news and misinformation is not considered the right direction for platforms to improve their regulatory mechanisms. Platform initiatives to regulate speech impact people’s self-expression [147,148]. As users understand the platform’s content management mechanisms and systems for moderating information flow, they begin to engage in anti-censorship and self-censorship [149], e.g., by processing text to circumvent sensitive keywords (utilizing abbreviations, code words, other languages, emojis, etc.) for greater expression freedom.
Similarly to textual content-based management, users have corresponding responses and self-protection methods for implementing IP location disclosure, such as enabling the global proxy mode of the Virtual Private Network (VPN) to conceal their actual location when posting. In the future, it can be further explored that variable relationships among the transparency of government information regulatory mechanisms [150,151], the extent of individual privacy information disclosure [152], the public’s trust toward government [153], and users’ online information behavior [154].
Based on the findings and results, it is suggested that researchers focus on whether there is a correlation between the functional architecture and the transparency of the social media platform itself, users’ usage habits, and the platform’s expression environment, to establish corresponding theoretical models and conduct empirical studies. In addition, researchers can focus on the relationship between users’ willingness to disclose personal information and their sentiment expressions, for example, whether excessive information disclosure and newly added identity labels affect users’ willingness, and the impact of expression. Our results indicate that the percentage of negative sentiment (47.93%) is significantly higher than that of positive sentiment (20.76%) in posts related to IP location. Still, sentiment scores differ across topics; for example, the positive sentiment for tourism-related topics is higher. In contrast, topics related to international disputes and social affairs exhibit higher negative sentiment. Thus, the influence of users’ sentiment performance and discussion topics should be further explored.
Furthermore, future research may also revisit the evolving meaning of anonymity in the contemporary Internet era. Once considered a defining feature of online interaction, anonymity is increasingly being replaced by transparency and traceability of identity. The shift reflected in Weibo’s IP location policy raises broader questions about how digital platforms balance accountability, privacy, and the legitimacy of participation.
6. Conclusions, Limitations, and Future Work
By crawling Weibo data from 28 April 2022 to 26 May 2023, this research conducted a sentiment analysis of discussions on IP location disclosure. Results indicated that Weibo posts involving IP location have become the new trend, discussion habit, and personal label of social networks, mainly associated with the display and change of IP location, the connection with issues in social events, the way the Internet and social media platforms are used, and the daily postings of individuals, etc. Sentiment analysis results indicated that disclosing IP location generally elicited more negative sentiment than positive sentiment. After network visualization of keywords identified as having positive or negative sentiment, the corresponding associations and co-occurrences were explored. Positive sentiment was associated with safe and orderly contexts, while negative sentiment was related to information disclosure and privacy issues, adverse social events, and cyberbullying.
The original intention of IP location disclosure as a mandatory government information policy was to create a more objective, rational, and authentic online speech environment during special periods (such as the Russo-Ukrainian War and COVID-19), making an optimistic assumption about the correlation between the trustworthiness of online speeches and the transparency of the information-providing subject. However, in the actual application process, the user’s IP location when speaking has become a new element of personal attack. In addition, when people are more likely to comment on news and publish political opinions online about international affairs, the location of people becomes one factor others may consider in assessing their political stance.
The limitation of this research is the limited exploration of user attributes and the lack of a deep dive into the connection with specific real-world social events. In future work, based on sentiment analysis results and the information on users’ IP locations and genders collected in the data, research should explore the concerned aspects and contributing factors of users’ privacy anxiety from the perspectives of user psychology and attributes. Additionally, it is possible to examine users’ sentiment tendencies on social platforms that disclose IP locations. By cross-referencing with Weibo, to study the social platforms with different functional attributes and focuses, such as Xiaohongshu, which focuses on life and experience sharing, and Douban, which has thematic groups that differentiate and aggregate people, discover the differences and similarities between their users’ opinions on IP location disclosure, and discuss the impact of IP this feature on their speaking environments and usage habits [155,156].
Author Contributions
Conceptualization, Y.L., Z.X. and D.K.W.C.; Methodology, Y.L., Z.X., D.K.W.C. and E.K.; Software, Y.L.; Validation, Z.X., D.K.W.C. and E.K.; Formal analysis, Y.L. and Z.X.; Investigation, Y.L.; Resources, D.K.W.C.; Data curation, Y.L.; Writing—original draft, Y.L.; Writing—review & editing, D.K.W.C. and E.K.; Visualization, Y.L.; Supervision, D.K.W.C.; Project administration, D.K.W.C. and E.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
The ethics committee of the Faculty of Education, The University of Hong Kong, approved this research.
Informed Consent Statement
Not required.
Data Availability Statement
Data are available on reasonable request to the first author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ray, R.K.; Chowdhury, F.R.; Hasan, M.R. Blockchain applications in retail cybersecurity: Enhancing supply chain integrity, secure transactions, and data protection. J. Bus. Manag. Stud. 2024, 6, 206. [Google Scholar] [CrossRef]
- Seneviratne, O.; Kagal, L. Enabling privacy through transparency. In Proceedings of the 2014 Twelfth Annual International Conference on Privacy, Security and Trust, Toronto, ON, Canada, 23–24 July 2014; pp. 121–128. [Google Scholar]
- Chaudhuri, R.; Chatterjee, S.; Vrontis, D. Antecedents of privacy concerns and online information disclosure: Moderating role of government regulation. EuroMed J. Bus. 2023, 18, 467–486. [Google Scholar] [CrossRef]
- Esmark Jones, C.L.; Stevens, J.L.; Noble, S.M.; Breazeale, M.J. Panic attack: How illegitimate invasions of privacy cause consumer anxiety and dissatisfaction. J. Public Policy Mark. 2020, 39, 334–352. [Google Scholar] [CrossRef]
- Tang, J.; Akram, U.; Shi, W. Why people need privacy? The role of privacy fatigue in app users’ intention to disclose privacy: Based on personality traits. J. Enterp. Inf. Manag. 2021, 34, 1097–1120. [Google Scholar] [CrossRef]
- Acquisti, A.; Fong, C. An experiment in hiring discrimination via online social networks. Manag. Sci. 2020, 66, 1005–1024. [Google Scholar] [CrossRef]
- Leung, E.; Verriest, A. Does location matter for disclosure? Evidence from geographic segments. J. Bus. Financ. Account. 2019, 46, 541–568. [Google Scholar] [CrossRef]
- Zhang, C. Ethical review of compulsory display of user IP addresses on multiple network platforms. J. Soc. Sci. Humanit. Lit. 2024, 7, 113–117. [Google Scholar]
- Celuch, M.; Oksa, R.; Ellonen, N.; Oksanen, A. Self-censorship among online harassment targets: The role of support at work, harassment characteristics, and the target’s public visibility. Inf. Commun. Soc. 2024, 27, 2171–2190. [Google Scholar] [CrossRef]
- Kim, J.; Zo, H. Am I watching or being watched? Exploring the selective disclosure paradox in users’ self-censorship to dataveillance awareness in video recommender systems. Telemat. Inform. 2025, 98, 102253. [Google Scholar] [CrossRef]
- Warner, M.; Wang, V. Self-censorship in social networking sites (SNSs)—Privacy concerns, privacy awareness, perceived vulnerability and information management. J. Inf. Commun. Ethics Soc. 2019, 17, 375–394. [Google Scholar] [CrossRef]
- Zhong, Z.J.; Wang, T.; Huang, M. Does the Great Firewall cause self-censorship? The effects of perceived internet regulation and the justification of regulation. Internet Res. 2017, 27, 974–990. [Google Scholar] [CrossRef]
- Feher, K. Digital identity and the online self: Footprint strategies—An exploratory and comparative research study. J. Inf. Sci. 2021, 47, 192–205. [Google Scholar] [CrossRef]
- McCarthy, S.; Rowan, W.; Mahony, C.; Vergne, A. The dark side of digitalization and social media platform governance: A citizen engagement study. Internet Res. 2023, 33, 2172–2204. [Google Scholar] [CrossRef]
- Azzaakiyyah, H.K. The Impact of Social Media Use on Social Interaction in Contemporary Society. Technol. Soc. Perspect. 2023, 1, 1–9. [Google Scholar] [CrossRef]
- Mai, J.E. Big data privacy: The datafication of personal information. Inf. Soc. 2016, 32, 192–199. [Google Scholar] [CrossRef]
- Boon-Itt, S.; Skunkan, Y. Public perception of the COVID-19 pandemic on Twitter: Sentiment analysis and topic modeling study. JMIR Public Health Surveill. 2020, 6, e21978. [Google Scholar] [CrossRef] [PubMed]
- Leppert, K.; Saliterer, I.; Korać, S. The role of emotions for citizen engagement via social media—A study of police departments using Twitter. Gov. Inf. Q. 2022, 39, 101686. [Google Scholar] [CrossRef]
- China Internet Network Information Center. The 51st Statistical Report on China’s Internet Development. 2023. Available online: https://cnnic.cn/NMediaFile/2023/0322/MAIN16794576367190GBA2HA1KQ.pdf (accessed on 13 March 2023).
- Jia, L.; Han, X. Tracing Weibo (2009–2019): The commercial dissolution of public communication and changing politics. Internet Hist. 2020, 4, 304–332. [Google Scholar] [CrossRef]
- Kong, D.; Chen, A.; Zhang, J.; Xiang, X.; Lou, W.V.; Kwok, T.; Wu, B. Public discourse and sentiment toward dementia on Chinese Social Media: Machine learning analysis of Weibo Posts. J. Med. Internet Res. 2022, 24, e39805. [Google Scholar] [CrossRef]
- Qiu, S.; Gao, X.; Yue, W.; Zhang, Q. Government-led and internet-empowered citizen participation in China’s policymaking: A case study of the Shanghai 2035 Master Plan. Gov. Inf. Q. 2023, 40, 101806. [Google Scholar] [CrossRef]
- Sun, T.; Zhao, Q. Delegated censorship: The dynamic, layered, and multistage information control regime in China. Politics Soc. 2022, 50, 191–221. [Google Scholar] [CrossRef]
- Hildén, J. Am I my IP address’s keeper? Revisiting the boundaries of information privacy. Inf. Soc. 2017, 33, 159–171. [Google Scholar] [CrossRef]
- Jin, J.; Guo, Y.; Lu, J. Comparing public support for digital surveillance policies in 50 countries. Soc. Sci. Q. 2024, 105, 1600–1615. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, D. Who joins which network, and why? Soc. Netw. Anal. Min. 2023, 13, 127. [Google Scholar] [CrossRef]
- Li, J.; Luo, Y.; Yuan, Q. Uncovering the impact of IP location display on user behavior in China’s social platforms: A policy-driven analysis. Telecommun. Policy 2025, 49, 102978. [Google Scholar] [CrossRef]
- Liu, Y.L.; Wu, Y.; Li, C.; Song, C.; Hsu, W.Y. Does displaying one’s IP location influence users’ privacy behavior on social media? Evidence from China’s Weibo. Telecommun. Policy 2024, 48, 102759. [Google Scholar] [CrossRef]
- Yu, C.; Margolin, D. Topic territoriality and the cost of civility: Examining the impact of IP address disclosure on Weibo. J. Comput. Mediat. Commun. 2024, 29, zmae018. [Google Scholar] [CrossRef]
- DeGroot, J.M.; Vik, T.A. “We were not prepared to tell people yet”: Confidentiality breaches and boundary turbulence on Facebook. Comput. Hum. Behav. 2017, 70, 351–359. [Google Scholar] [CrossRef]
- Petronio, S.; Child, J.T. Conceptualization and operationalization: Utility of communication privacy management theory. Curr. Opin. Psychol. 2020, 31, 76–82. [Google Scholar] [CrossRef]
- Smith, S.A.; Brunner, S.R. To reveal or conceal: Using communication privacy management theory to understand disclosures in the workplace. Manag. Commun. Q. 2017, 31, 429–446. [Google Scholar] [CrossRef]
- Habermas, J. The Structural Transformation of the Public Sphere: An Inquiry into a Category of Bourgeois Society; MIT Press: Cambridge, MA, USA, 1991. [Google Scholar]
- Benkler, Y. The Wealth of Networks: How Social Production Transforms Markets and Freedom; Yale University Press: New Haven, CT, USA; London, UK, 2006. [Google Scholar]
- Bertot, J.C.; Jaeger, P.T.; Grimes, J.M. Using ICTs to create a culture of transparency: E-government and social media as openness and anti-corruption tools for societies. Gov. Inf. Q. 2010, 27, 264–271. [Google Scholar] [CrossRef]
- Papacharissi, Z. The virtual sphere: The internet as a public sphere. New Media Soc. 2002, 4, 9–27. [Google Scholar] [CrossRef]
- Vos, T.P.; Craft, S. The discursive construction of journalistic transparency. J. Stud. 2017, 18, 1505–1522. [Google Scholar] [CrossRef]
- Ørmen, J. Not so distinct after all: Assessing social stratification of news users on the web. J. Stud. 2019, 20, 1653–1670. [Google Scholar] [CrossRef]
- Willekens, M.; Siongers, J.; Lievens, J. Social stratification and social media disengagement. The effect of economic, cultural and social capital on reasons for non-use of social media platforms. Poetics 2022, 95, 101708. [Google Scholar] [CrossRef]
- Hutchings, S.C. Uncovering the uncoverers: Identity, performativity and representation in counter-disinformation discourse. Cult. Stud. 2025, 39, 546–573. [Google Scholar] [CrossRef]
- Riedl, M.J.; Lukito, J.; Woolley, S.C. Political influencers on social media: An introduction. Soc. Media Soc. 2023, 9, 20563051231177938. [Google Scholar] [CrossRef]
- Tim, Y.; Pan, S.L.; Bahri, S.; Fauzi, A. Digitally enabled crime-fighting communities: Harnessing the boundary spanning competence of social media for civic engagement. Inf. Manag. 2017, 54, 177–188. [Google Scholar] [CrossRef]
- Kuerbis, B.; Mueller, M. Exploring the role of data enclosure in the digital political economy. Telecommun. Policy 2023, 47, 102599. [Google Scholar] [CrossRef]
- Shibchurn, J.; Yan, X. Information disclosure on social networking sites: An intrinsic-extrinsic motivation perspective. Comput. Hum. Behav. 2015, 44, 103–117. [Google Scholar] [CrossRef]
- Kolotylo-Kulkarni, M.; Xia, W.; Dhillon, G. Information disclosure in e-commerce: A systematic review and agenda for future research. J. Bus. Res. 2021, 126, 221–238. [Google Scholar] [CrossRef]
- Blankespoor, E.; deHaan, E.; Marinovic, I. Disclosure processing costs, investors’ information choice, and equity market outcomes: A review. J. Account. Econ. 2020, 70, 101344. [Google Scholar] [CrossRef]
- Ryu, S.; Park, Y.N. How consumers cope with location-based advertising (LBA) and personal information disclosure: The mediating role of persuasion knowledge, perceived benefits and harms, and attitudes toward LBA. Comput. Hum. Behav. 2020, 112, 106450. [Google Scholar] [CrossRef]
- Knijnenburg, B.P.; Kobsa, A.; Jin, H. Dimensionality of information disclosure behavior. Int. J. Hum. Comput. Stud. 2013, 71, 1144–1162. [Google Scholar] [CrossRef]
- Towner, E.; Grint, J.; Levy, T.; Blakemore, S.J.; Tomova, L. Revealing the self in a digital world: A systematic review of adolescent online and offline self-disclosure. Curr. Opin. Psychol. 2022, 45, 101309. [Google Scholar] [CrossRef]
- Curry, A.L.; Stroud, N.J. The effects of journalistic transparency on credibility assessments and engagement intentions. Journalism 2021, 22, 901–918. [Google Scholar] [CrossRef]
- Veltri, G.A.; Lupiáñez-Villanueva, F.; Folkvord, F.; Theben, A.; Gaskell, G. The impact of online platform transparency of information on consumers’ choices. Behav. Public Policy 2023, 7, 55–82. [Google Scholar] [CrossRef]
- Yang, J.; Battocchio, A.F. Effects of transparent brand communication on perceived brand authenticity and consumer responses. J. Prod. Brand Manag. 2021, 30, 1176–1193. [Google Scholar] [CrossRef]
- Dumont, G.E. Transparency or accountability? The purpose of online technologies for nonprofits. Int. Rev. Public Adm. 2013, 18, 7–29. [Google Scholar] [CrossRef]
- Ramírez, Y.; Tejada, Á. Digital transparency and public accountability in Spanish universities in online media. J. Intellect. Cap. 2019, 20, 701–732. [Google Scholar] [CrossRef]
- Singhal, A.; Neveditsin, N.; Tanveer, H.; Mago, V. Toward fairness, accountability, transparency, and ethics in AI for social media and health care: Scoping review. JMIR Med. Inform. 2024, 12, e50048. [Google Scholar] [CrossRef]
- Vandervorst, F.; Verbeke, W.; Verdonck, T. Data misrepresentation detection for insurance underwriting fraud prevention. Decis. Support Syst. 2022, 159, 113798. [Google Scholar] [CrossRef]
- Bélanger, F.; James, T.L. A theory of multilevel information privacy management for the digital era. Inf. Syst. Res. 2020, 31, 510–536. [Google Scholar] [CrossRef]
- Meng, X. From Interpersonal Privacy to Human—Technological Privacy: Communication Privacy Management Theory Revisited. Tech. Commun. 2024, 71, 72–88. [Google Scholar] [CrossRef]
- De Wolf, R.; Willaert, K.; Pierson, J. Managing privacy boundaries together: Exploring individual and group privacy management strategies in Facebook. Comput. Hum. Behav. 2014, 35, 444–454. [Google Scholar] [CrossRef]
- Martin, K. Understanding privacy online: Development of a social contract approach to privacy. J. Bus. Ethics 2016, 137, 551–569. [Google Scholar] [CrossRef]
- Stanton, J.M.; Stam, K.R. Information technology, privacy, and power within organizations: A view from boundary theory and social exchange perspectives. Surveill. Soc. 2003, 1, 152–190. [Google Scholar] [CrossRef]
- Acquisti, A.; Brandimarte, L.; Loewenstein, G. Privacy and human behavior in the information age. In The Cambridge Handbook of Consumer Privacy; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar]
- Aloia, L.S. The emotional, behavioral, and cognitive experience of boundary turbulence. Commun. Stud. 2018, 69, 180–195. [Google Scholar] [CrossRef]
- Mansour, A.; Francke, H. Collective privacy management practices: A study of privacy strategies and risks in a private Facebook group. Proc. ACM Hum. Comput. Interact. 2021, 5, 1–27. [Google Scholar] [CrossRef]
- De Wolf, R. Contextualizing how teens manage personal and interpersonal privacy on social media. New Media Soc. 2020, 22, 1058–1075. [Google Scholar] [CrossRef]
- Craig, M.J.; Child, J.T. What’s Mine Is (Not) Yours: A CPM Analysis of Privacy Breakdowns and Recalibration Practices in the Social Media Algorithm Context. 2024, Preprint. Available online: https://osf.io/preprints/socarxiv/mqckr (accessed on 24 October 2025).
- Binns, R. Algorithmic accountability and public reason. Philos. Technol. 2018, 31, 543–556. [Google Scholar] [CrossRef] [PubMed]
- Mittelstadt, B.D.; Allo, P.; Taddeo, M.; Wachter, S.; Floridi, L. The ethics of algorithms: Mapping the debate. Big Data Soc. 2016, 3, 2053951716679679. [Google Scholar] [CrossRef]
- Selbst, A.D.; Boyd, D.; Friedler, S.A.; Venkatasubramanian, S.; Vertesi, J. Fairness and abstraction in sociotechnical systems. In Proceedings of the Conference on Fairness, Accountability, and Transparency, Atlanta, GA, USA, 29–31 January 2019; pp. 59–68. [Google Scholar]
- Zhang, R.; Fu, J.S. Privacy management and self-disclosure on social network sites: The moderating effects of stress and gender. J. Comput. Mediat. Commun. 2020, 25, 236–251. [Google Scholar] [CrossRef]
- Anand, N.; Brass, I. Responsible innovation for digital identity systems. Data Policy 2021, 3, e35. [Google Scholar] [CrossRef]
- Dollar, C.B.; Tietjen, G. Living as socially marked individuals: Two stories on stigma and its consequences. Humanit. Soc. 2023, 47, 3–28. [Google Scholar] [CrossRef]
- Sedlmeir, J.; Smethurst, R.; Rieger, A.; Fridgen, G. Digital identities and verifiable credentials. Bus. Inf. Syst. Eng. 2021, 63, 603–613. [Google Scholar] [CrossRef]
- Windley, P.J. Digital Identity: Unmasking Identity Management Architecture (IMA); O’Reilly Media, Inc.: Sebastopol, CA, USA, 2005. [Google Scholar]
- Das, R.; Wong, Y.N.; Jones, R.; Jackson, P.J. How do we speak about algorithms and algorithmic media futures? Using vignettes and scenarios in a citizen council on data-driven media personalisation. New Media Soc. 2024, 27, 3931–3949. [Google Scholar] [CrossRef]
- Head, A.J.; Fister, B.; MacMillan, M. Information Literacy in the Age of Algorithms: Student Experiences with News and Information, and the Need for Change. Proj. Inf. Lit. 2020, 55. Available online: https://eric.ed.gov/?id=ED605109 (accessed on 26 October 2025).
- Shen, H.; DeVos, A.; Eslami, M.; Holstein, K. Everyday algorithm auditing: Understanding the power of everyday users in surfacing harmful algorithmic behaviors. Proc. ACM Hum. Comput. Interact. 2021, 5, 1–29. [Google Scholar] [CrossRef]
- Bhandari, N.B. Diaspora and cultural identity: A conceptual review. J. Political Sci. 2021, 21, 100–108. [Google Scholar] [CrossRef]
- Ferguson, C.J. Does the internet make the world worse? Depression, aggression and polarization in the social media age. Bull. Sci. Technol. Soc. 2021, 41, 116–135. [Google Scholar] [CrossRef]
- Lindell, J.; Mikkelsen Båge, E. Disconnecting from digital news: News avoidance and the ignored role of social class. Journalism 2023, 24, 1980–1997. [Google Scholar] [CrossRef]
- Muhammed, T.S.; Mathew, S.K. The disaster of misinformation: A review of research in social media. Int. J. Data Sci. Anal. 2022, 13, 271–285. [Google Scholar] [CrossRef]
- Turel, O.; Osatuyi, B. Biased credibility and sharing of fake news on social media: Considering peer context and self-objectivity state. In Fake News on the Internet; Routledge: Abingdon, UK, 2023; pp. 39–66. [Google Scholar]
- Cini, L. How algorithms are reshaping the exploitation of labour-power: Insights into the process of labour invisibilization in the platform economy. Theory Soc. 2023, 52, 885–911. [Google Scholar] [CrossRef]
- Duffy, B.E.; Meisner, C. Platform governance at the margins: Social media creators’ experiences with algorithmic (in)visibility. Media Cult. Soc. 2023, 45, 285–304. [Google Scholar] [CrossRef]
- O’Reilly, T.; Strauss, I.; Mazzucato, M. Algorithmic attention rents: A theory of digital platform market power. Data Policy 2024, 6, e6. [Google Scholar] [CrossRef]
- Piffari, C.; Lagorio, A.; Pinto, R. The role of information visibility on healthcare resource network performance: An agent-based simulation approach. J. Oper. Res. Soc. 2025, 76, 1019–1033. [Google Scholar] [CrossRef]
- O’Mahony, P. Habermas and the public sphere: Rethinking a key theoretical concept. Eur. J. Soc. Theory 2021, 24, 485–506. [Google Scholar] [CrossRef]
- Vachhani, S.J. Networked feminism in a digital age—Mobilizing vulnerability and reconfiguring feminist politics in digital activism. Gend. Work. Organ. 2024, 31, 1031–1048. [Google Scholar] [CrossRef]
- Viader Guerrero, J. Beyond the digital public sphere: Towards a political ontology of algorithmic technologies. Philos. Technol. 2024, 37, 102. [Google Scholar] [CrossRef]
- Calzada, I. Emerging digital citizenship regimes: Pandemic, algorithmic, liquid, metropolitan, and stateless citizenships. Citizsh. Stud. 2023, 27, 160–188. [Google Scholar] [CrossRef]
- Matheus, R.; Faber, R.; Ismagilova, E.; Janssen, M. Digital transparency and the usefulness for open government. Int. J. Inf. Manag. 2023, 73, 102690. [Google Scholar] [CrossRef]
- Saldanha, D.M.F.; Dias, C.N.; Guillaumon, S. Transparency and accountability in digital public services: Learning from the Brazilian cases. Gov. Inf. Q. 2022, 39, 101680. [Google Scholar] [CrossRef]
- Sharma, S.; Kar, A.K.; Gupta, M.P.; Dwivedi, Y.K.; Janssen, M. Digital citizen empowerment: A systematic literature review of theories and development models. Inf. Technol. Dev. 2022, 28, 660–687. [Google Scholar] [CrossRef]
- Zhao, B.; Cheng, S.; Schiff, K.J.; Kim, Y. Digital transparency and citizen participation: Evidence from the online crowdsourcing platform of the City of Sacramento. Gov. Inf. Q. 2023, 40, 101868. [Google Scholar] [CrossRef]
- Büchi, M.; Festic, N.; Latzer, M. The chilling effects of digital dataveillance: A theoretical model and an empirical research agenda. Big Data Soc. 2022, 9, 20539517211065368. [Google Scholar] [CrossRef]
- Strycharz, J.; Segijn, C.M. Ethical side-effect of dataveillance in advertising: Impact of data collection, trust, privacy concerns and regulatory differences on chilling effects. J. Bus. Res. 2024, 173, 114490. [Google Scholar] [CrossRef]
- Stubenvoll, M.; Binder, A. Is knowledge power? Testing whether knowledge affects chilling effects and privacy-protective behaviors using browser histories. Comput. Hum. Behav. 2024, 150, 107949. [Google Scholar] [CrossRef]
- Chen, L.; Tong, T.W.; Tang, S.; Han, N. Governance and design of digital platforms: A review and future research directions on a meta-organization. J. Manag. 2022, 48, 147–184. [Google Scholar] [CrossRef]
- Gong, Y.; Li, X. Designing boundary resources in digital government platforms for collaborative service innovation. Gov. Inf. Q. 2023, 40, 101777. [Google Scholar] [CrossRef]
- Mao, Z.; Wu, J.; Qiao, Y.; Yao, H. Government data governance framework based on a data middle platform. Aslib J. Inf. Manag. 2022, 74, 289–310. [Google Scholar] [CrossRef]
- Doshi, A.R.; Schmidt, W. Soft governance across digital platforms using transparency. Strategy Sci. 2024, 9, 185–204. [Google Scholar] [CrossRef]
- Giorgino, M.C.; Barnabè, F. Hard and soft governance mechanisms for large projects. A historical perspective. J. Manag. Hist. 2025, 31, 285–313. [Google Scholar] [CrossRef]
- Balendra, S. Free Speech in the Puzzle of Content Regulation; Springer: Berlin/Heidelberg, Germany, 2024. [Google Scholar]
- Gorwa, R. The Politics of Platform Regulation: How Governments Shape Online Content Moderation; Oxford University Press: Oxford, UK, 2024. [Google Scholar]
- Cobbe, J. Algorithmic censorship by social platforms: Power and resistance. Philos. Technol. 2021, 34, 739–766. [Google Scholar] [CrossRef]
- Cusumano, M.A.; Gawer, A.; Yoffie, D.B. Can self-regulation save digital platforms? Ind. Corp. Chang. 2021, 30, 1259–1285. [Google Scholar] [CrossRef]
- Gosztonyi, G. Censorship from Plato to Social Media. In The Complexity of Social Media’s Content Regulation and Moderation Practices; Springer Nature: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Kuroda, Y.; Yamamoto, G.; Kuroda, T. Identifying undefined risks: A risk model and a privacy risk identification measure in the privacy impact assessment process. Inf. Soc. 2024, 40, 202–214. [Google Scholar] [CrossRef]
- Zajko, M. Artificial intelligence, algorithms, and social inequality: Sociological contributions to contemporary debates. Sociol. Compass 2022, 16, e12962. [Google Scholar] [CrossRef]
- Guo, Y.; Li, Y.; Yang, T. Civilizing social media: The effect of geolocation on the incivility of news comments. New Media Soc. 2025, 27, 2996–3016. [Google Scholar] [CrossRef]
- Cloarec, J.; Meyer-Waarden, L.; Munzel, A. Transformative privacy calculus: Conceptualizing the personalization-privacy paradox on social media. Psychol. Mark. 2024, 41, 1574–1596. [Google Scholar] [CrossRef]
- Zeng, F.; Ye, Q.; Li, J.; Yang, Z. Does self-disclosure matter? A dynamic two-stage perspective for the personalization-privacy paradox. J. Bus. Res. 2021, 124, 667–675. [Google Scholar] [CrossRef]
- Kumar, S.; Gupta, M. A review of focused crawling schemes for search engine. In Smart Trends in Computing and Communications: Proceedings of SmartCom 2020; Springer: Singapore, 2021; pp. 311–317. [Google Scholar] [CrossRef]
- Zhang, B.; Lin, J.; Luo, M.; Zeng, C.; Feng, J.; Zhou, M.; Deng, F. Changes in public sentiment under the background of major emergencies—Taking the Shanghai epidemic as an example. Int. J. Environ. Res. Public Health 2022, 19, 12594. [Google Scholar] [CrossRef]
- Qaiser, S.; Ali, R. Text mining: Use of TF-IDF to examine the relevance of words to documents. Int. J. Comput. Appl. 2018, 181, 25–29. [Google Scholar] [CrossRef]
- Kim, S.W.; Gil, J.M. Research paper classification systems based on TF-IDF and LDA schemes. Hum. Centric Comput. Inf. Sci. 2019, 9, 30. [Google Scholar] [CrossRef]
- Farkhod, A.; Abdusalomov, A.; Makhmudov, F.; Cho, Y.I. LDA-based topic modeling sentiment analysis using topic/document/sentence (TDS) model. Appl. Sci. 2021, 11, 11091. [Google Scholar] [CrossRef]
- Jelodar, H.; Wang, Y.; Yuan, C.; Feng, X.; Jiang, X.; Li, Y.; Zhao, L. Latent Dirichlet allocation (LDA) and topic modeling: Models, applications, a survey. Multimed. Tools Appl. 2019, 78, 15169–15211. [Google Scholar] [CrossRef]
- Su, W.; Han, X.; Yu, H.; Wu, Y.; Potenza, M.N. Do men become addicted to internet gaming and women to social media? A meta-analysis examining gender-related differences in specific internet addiction. Comput. Hum. Behav. 2020, 113, 106480. [Google Scholar] [CrossRef]
- Salter, M. Privates in the online public: Sex(ting) and reputation on social media. New Media Soc. 2016, 18, 2723–2739. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, Y.; Shen, X.L.; Wang, N.; Zhang, X.; Wu, Y. Understanding the trust building mechanisms in social media: Regulatory effectiveness, trust transfer, and gender difference. Aslib J. Inf. Manag. 2018, 70, 498–517. [Google Scholar] [CrossRef]
- Bhave, D.P.; Teo, L.H.; Dalal, R.S. Privacy at work: A review and a research agenda for a contested terrain. J. Manag. 2020, 46, 127–164. [Google Scholar] [CrossRef]
- Pieters, W. Beyond individual-centric privacy: Information technology in social systems. Inf. Soc. 2017, 33, 271–281. [Google Scholar] [CrossRef]
- McLean, L.; Griffiths, M.D. Female gamers’ experience of online harassment and social support in online gaming: A qualitative study. Int. J. Ment. Health Addict. 2019, 17, 970–994. [Google Scholar] [CrossRef]
- Navarro, R. Gender issues and cyberbullying in children and adolescents: From gender differences to gender identity measures. In Cyberbullying Across the Globe: Gender, Family, and Mental Health; Springer Nature: Berlin/Heidelberg, Germany, 2016; pp. 35–61. [Google Scholar]
- Backe, E.L.; Lilleston, P.; McCleary-Sills, J. Networked individuals, gendered violence: A literature review of cyberviolence. Violence Gend. 2018, 5, 135–146. [Google Scholar] [CrossRef]
- Kar, R.B.; Yu, X. The Contractual Death and Rebirth of Privacy. Harv. J. Law Technol. 2024, 38. [Google Scholar] [CrossRef]
- Haggart, B.; Keller, C.I. Democratic legitimacy in global platform governance. Telecommun. Policy 2021, 45, 102152. [Google Scholar] [CrossRef]
- Moss, G. Digital Regulation and Questions of Legitimacy. Policy Internet 2025, 17, e433. [Google Scholar] [CrossRef]
- Xiao, Y. Transparency and privacy on social media: Privacy policies for enhancing users’ control on social media. Int. J. Hum. Comput. Interact. 2025, 1–20. [Google Scholar] [CrossRef]
- Berg, S.; Hofmann, J. Digital democracy. Internet Policy Rev. 2021, 10, 1–23. [Google Scholar] [CrossRef]
- Ghadge, N. Enhancing Identity Management: Best Practices for Governance and Administration. Comput. Sci. Inf. Technol. 2024, 219–228. [Google Scholar] [CrossRef]
- Mikhaylovskaya, A. Enhancing deliberation with digital democratic innovations. Philos. Technol. 2024, 37, 3. [Google Scholar] [CrossRef]
- Rattanasevee, P.; Akarapattananukul, Y.; Chirawut, Y. Direct democracy in the digital age: Opportunities, challenges, and new approaches. Humanit. Soc. Sci. Commun. 2024, 11, 1681. [Google Scholar] [CrossRef]
- Mayer, A.; Puller, S.L. The old boy (and girl) network: Social network formation on university campuses. J. Public Econ. 2008, 92, 329–347. [Google Scholar] [CrossRef]
- Lewis, K.; Kaufman, J.; Gonzalez, M.; Wimmer, A.; Christakis, N. Tastes, ties, and time: A new social network dataset using Facebook.com. Soc. Netw. 2008, 30, 330–342. [Google Scholar] [CrossRef]
- Red, V.; Kelsic, E.D.; Mucha, P.J.; Porter, M.A. Comparing community structure to characteristics in online collegiate social networks. SIAM Rev. 2011, 53, 526–543. [Google Scholar] [CrossRef]
- Smirnov, I.; Thurner, S. Formation of homophily in academic performance: Students change their friends rather than performance. PLoS ONE 2017, 12, e0183473. [Google Scholar] [CrossRef]
- Wimmer, A.; Lewis, K. Beyond and below racial homophily: ERG models of a friendship network documented on Facebook. Am. J. Sociol. 2010, 116, 583–642. [Google Scholar] [CrossRef] [PubMed]
- Eisenberg, D.; Golberstein, E.; Whitlock, J.L. Peer effects on risky behaviors: New evidence from college roommate assignments. J. Health Econ. 2014, 33, 126–138. [Google Scholar] [CrossRef]
- Xu, D. Acculturational homophily. Econ. Educ. Rev. 2017, 59, 29–42. [Google Scholar] [CrossRef]
- Hofstra, B.; Corten, R.; van Tubergen, F. Beyond the core: Who has larger social networks? Soc. Forces 2021, 99, 1274–1305. [Google Scholar] [CrossRef]
- Michelman, V.; Price, J.; Zimmerman, S.D. Old boys’ clubs and upward mobility among the educational elite. Q. J. Econ. 2022, 137, 845–909. [Google Scholar] [CrossRef]
- Kneeland, M.K.; Kleinbaum, A.M. Rewiring the organizational network: Corporate offsites and network tie formation. Strateg. Manag. J. 2025, 46, 209–241. [Google Scholar] [CrossRef]
- Grygiel, J.; Brown, N. Are social media companies motivated to be good corporate citizens? Examination of the connection between corporate social responsibility and social media safety. Telecommun. Policy 2019, 43, 445–460. [Google Scholar] [CrossRef]
- Pick, J.B.; Koohikamali, M.; Dunaway-Perez, J. Management and mitigation of location privacy violations: Case study analysis of US local governments. Inf. Soc. 2022, 38, 147–164. [Google Scholar] [CrossRef]
- Park, M.S.; Shin, J.K.; Ju, Y. A taxonomy of social networking site users: Social surveillance and self-surveillance perspective. Psychol. Mark. 2015, 32, 601–610. [Google Scholar] [CrossRef]
- Shane-Simpson, C.; Manago, A.; Gaggi, N.; Gillespie-Lynch, K. Why do college students prefer Facebook, Twitter, or Instagram? Site affordances, tensions between privacy and self-expression, and implications for social capital. Comput. Hum. Behav. 2018, 86, 276–288. [Google Scholar] [CrossRef]
- Chen, X.; Xie, J.; Wang, Z.; Shen, B.; Zhou, Z. How We Express Ourselves Freely: Censorship, Self-censorship, and Anti-censorship on a Chinese Social Media. In International Conference on Information; Springer Nature: Cham, Switzerland, 2023; pp. 93–108. [Google Scholar]
- Jacoby, G.; Liu, M.; Wang, Y.; Wu, Z.; Zhang, Y. Corporate governance, external control, and environmental information transparency: Evidence from emerging markets. J. Int. Financ. Mark. Inst. Money 2019, 58, 269–283. [Google Scholar] [CrossRef]
- Urman, A.; Makhortykh, M. How transparent are transparency reports? Comparative analysis of transparency reporting across online platforms. Telecommun. Policy 2023, 47, 102477. [Google Scholar] [CrossRef]
- Rossi, J. What rules the Internet? A study of the troubled relation between Web standards and legal instruments in the field of privacy. Telecommun. Policy 2021, 45, 102143. [Google Scholar] [CrossRef]
- Sibley, C.G.; Greaves, L.M.; Satherley, N.; Wilson, M.S.; Overall, N.C.; Lee, C.H.; Milojev, P.; Bulbulia, J.; Osborne, D.; Milfont, T.L.; et al. Effects of the COVID-19 pandemic and nationwide lockdown on trust, attitudes toward government, and well-being. Am. Psychol. 2020, 75, 618. [Google Scholar] [CrossRef]
- Barth, S.; de Jong, M.D.; Junger, M.; Hartel, P.H.; Roppelt, J.C. Putting the privacy paradox to the test: Online privacy and security behaviors among users with technical knowledge, privacy awareness, and financial resources. Telemat. Inform. 2019, 41, 55–69. [Google Scholar] [CrossRef]
- Shin, D.; Kee, K.F.; Shin, E.Y. Algorithm awareness: Why user awareness is critical for personal privacy in the adoption of algorithmic platforms? Int. J. Inf. Manag. 2022, 65, 102494. [Google Scholar] [CrossRef]
- Stark, L. The emotional context of information privacy. Inf. Soc. 2016, 32, 14–27. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).