Abstract
In today’s scenario, image watermarking has been an integral part in various multimedia applications. Watermarking is the approach for adding additional information to the existing image to protect the data from modification and to provide data integrity. Frequency transform domain techniques are complex and costly and degrade the quality of the image due to less embedding of bits. The proposed work utilize the original DCT method with some modifications and applies this method on frequency bands of DWT. Furthermore, the output is used in combination with a pixel modification method for embedding and extraction. The proposed outcome is the improvement of performance achieved in terms of time, imperceptibility, and robustness.
1. Introduction
Image processing is a part of signal processing that takes an input image, processes it, and then generates the required output image or generates an image that satisfies certain characteristics or features. The authenticity of content is also very much important. During the digital processing of an image, content should not be modified or copied. Different techniques are used for providing authenticity of content such as encryption, cryptography, digital signatures, and steganography [1]. However, each has its disadvantages. For example, if an image has been modified then a digital signature can detect that modification, but a digital signature cannot detect the region where it is modified. Encryption does not provide ownership of content.
One way of providing authentication, copyright protection, or ownership identification is to use an image watermarking technique [2]. The original image and desired watermark or logo are embedded using different algorithms. Extraction is a process that usually works in a reverse manner to embedding.
With the rapid growth of the Internet and digital multimedia techniques, digital content can be easily copied and can be modified [3,4]. So as to resolve the illegal use of content and for the protection of ownership of content [5], the security of a watermark can be used.
The watermarking procedure is shown in Figure 1. It comprises of four steps as watermark generation, embedding, attacks, and extraction. Even if an attacker rotates a host image by some degree, the watermark should not be extracted or visible to that person.

Figure 1.
A basic model of a watermarking system.
The basic process of Watermarking is shown in Figure 2. Due to different types of attacks such as rotation, translation, filtering, adding noise, compression [6] etc., security through watermarking is of prime concern. Techniques in the frequency transform domain are mainly used in copyrights [7]. However, more bits cannot be embedded, as the quality is degraded. Figure 3 shows a visible watermarked image. Techniques of frequency domains are combined with pixel modification techniques in parallel, but they are time-consuming, complex, are not resistant [8] to different types of attacks, and mainly capacity is reduced.
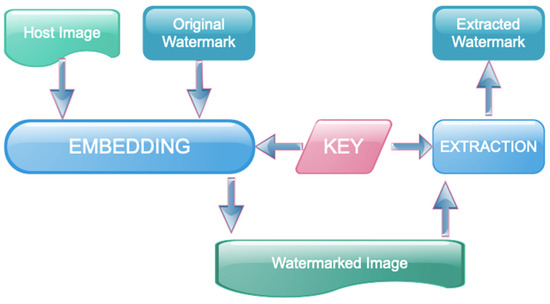
Figure 2.
Block diagram of the watermarking process.

Figure 3.
An example of a visible watermarked image [9].
In watermarking, the most important feature is to provide strong robustness, security, and capacity [10]. Watermarking techniques in spatial and frequency transform domains [11] must be resistant to different types of attacks. For example, one image is used as important evidence in a legal or medical case [12]. If someone has made minor changes in that image that cannot be easily detected by human [13] eyes using software such as Photoshop, then this modification will create major changes in such cases. In the event of the images being affected by uncertainties and inaccuracies that affect the overall scenario, fuzzy preprocessing [14,15] is required. Figure 4 shows the classification of Watermarking Techniques based on the type of attacks [16].
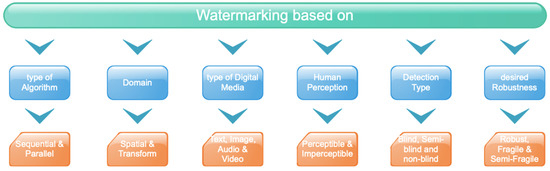
Figure 4.
Classification of watermarking techniques [16].
This approach proposes a solution that makes modifications to the basic method, and combines that modified method with existing methods that generate an algorithm for embedding and extraction. Different attacks are then applied for measuring performance [9]. The main objective of this work is to propose a modification to basic methods, and to generate a new solution that creates a new algorithm for embedding and extraction by using a hybrid method with modification [17,18]. The results are then compared with the previous existing solutions to differentiate the performance of the proposed method and the existing solutions.
The scope of this study involves the complete implementation of modifications in basic DCT methods and combinations of DWT, modified techniques with pixel modification that eliminate the use of DCT for finding DC components directly in spatial domains, and analyses of the performance.
2. Literature Review
Literature related to various techniques on image watermarking for providing copyright control and ownership identification is discussed in this section.
The author in [19] proposed a hybrid watermarking technique by combining two methods of frequency transform domains i.e., DWT–DCT, which will provide high robustness, provide authentication [20], and compare the results with a cox additive algorithm [21]. This work uses a hybrid watermarking method (DWT–DCT) which per-forms two-level, three level, and four-level DWT followed by respective DCT on host images.
A CDMA digital image watermark is proposed [18], which uses wavelet trans-form, is tested in different color spaces, and detects that the RGB color space is more effective for watermark embedding and extraction.
According to [22], high robustness can be provided by using a technique that is based on a hybrid domain. The watermark is embedded in spatial and transform do-mains in parallel, which provides high robustness and resistance to both image processing and geometric attacks.
In [23], authors presented a method that split the data into two parts for frequency and spatial insertion, based on user preference and data importance, which enhances the performance and embeds the important part in the frequency domain and rest in the spatial domain. First, they have separated the watermark into two parts and insert them into the spatial domain to obtain their spatial coefficients [24]. Next, they have transformed the first part of watermark Hs by applying DCT to obtain DCT coefficients. They have inserted the second part of the watermark into DCT coefficients [23]. Lastly, they have applied IDCT to obtain marked images. The splitting of data doubles the protection, and for more security we can make splitting even more com-plex. The disadvantages of using DCT, are, however, there. A comparative analysis of some of the existing methodologies and their attacks is depicted in Table 1.

Table 1.
Comparison of existing methods with mathematical terms.
Comparison of Existing Methods
All of the methods described above have their advantages and disadvantages. The main aim of watermarking is to provide strong robustness. None of the above techniques provide a solution for finding DC components [20] without applying DCT. None of the techniques of both the domain and their combinational methods provide a complete solution that provides strong robustness against different types of attacks.
3. Proposed Methodology
Different types of methods are used in both domains for image watermarking: Different types of methods are used in both domains for image watermarking: modification of pixel values, LSB-based method, DWT-based watermarking, DCT based watermarking, SVD based watermarking, DWT-DCT-SVD based watermarking, parallel watermarking, etc. A common problem of all of these methods is that they are not resistant to all types of geometric and image processing attacks. Another problem is that these techniques require applying DCT to find DC components.
Hence, the solution to this is a mechanism which makes modifications in a basic method, and eliminates the use of DCT to find DC components. It then applies this modified method to existing methods of DWT, and then according to the new method, modifies DC and changes the pixel values in the watermark according to the modified DC; then, it replaces those watermark bits in the DC components of the host image. Figure 5 shows the workflow for the proposed methodology.
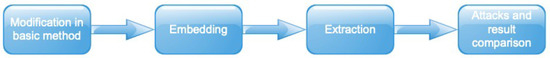
Figure 5.
Proposed workflow.
Step I: Modification in the basic method.
The modification in the basic DCT approach is conducted by applying the modification of the LH band of the DWT method. The frequency band is modified with the updated DC values, then further processing is done. The modification of DC components is shown in Figure 6. The embedding and extraction process of modified DC coefficients is depicted in Table 2 and Table 3 respectively.
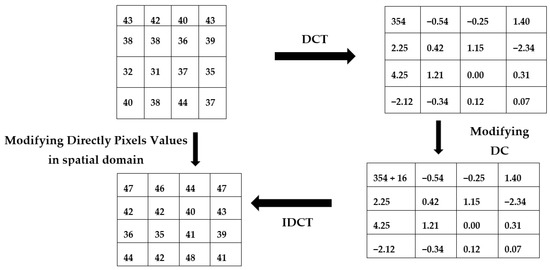
Figure 6.
Relation between DC and Spatial Domain.

Table 2.
Calculation of DC Coefficient.

Table 3.
Modified DC Coefficient.
Step II: Algorithm 1 shows the embeddign process of modified DC coeffiieients.
| Algorithm 1: Embedding Algorithm |
| Step 1—Apply Arnold Transform on the watermarked image. Step 2—Apply DWT up to two levels on the host image and take the LH band. Step 3—Apply DWT up to two levels on the watermark image and take the LL band of the watermark image to embed into the LH band. Step 4—Divide the LH band into 4 × 4 bands. Step 5—Find the DC coefficient c (0,0) of each block by summing up the pixels values of a particular block. Step 6—According to the watermark information, find the magnitudes as: If w = 0 T1 = −0.5∆, T2 = 1.5∆ If w = 1 T1 = 0.5∆, T2 = 1.5∆ where ∆ = block size = 4 Step 7—Find the quantization step as C1 and C2 using T1 and T2 as: C1 = αk∆ + T1 C2 = αk∆ + T2 where α = constant value Step 8—Modify the DC coefficient c’s of each block for embedding in the DC coefficient as follows: c’ (0,0) = C2 if abs c(0,0) − c2 < abs c(0,0) − c1 =C1 else Step 9—Find difference M as: M = c’i, j (0, 0) − ci, j (0, 0) Step 10—Add M/4 to each pixel block in the watermark and then replace the particular block’s DC’s value with these values for embedding. Step 11—Repeat steps 5–10 until all blocks are processed and DC‘s are modified and embedded. |
Step III: Algorithm 2 shows the extraction process of the modified DC coefficients embedded in the watermark.
| Algorithm 2: Extraction Algorithm |
| Step 1—Apply DWT up to two levels on the watermarked image. Step 2—Find the DC coefficient c (0, 0) of each block by summing up the pixels values of a particular block. Step 3—Using quantization steps ∆, compute w’ (i, j): w’ (i, j) = mod (ceil((c(0,0))/∆),α) Step 4—Extract the watermark by applying an Inverse Arnold Transform. |
Step IV: Attacks and Result Comparison.
The attacks are performed on the host image, and then the original and modified values are calculated. Then, a comparative analysis is done. The complete methodology of embedding, extraction, attack and result comparison is shown in Figure 7.
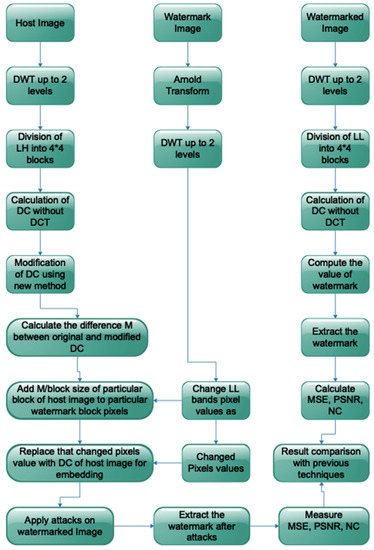
Figure 7.
Proposed embedding, extraction algorithms, attacks, and result comparisons.
4. Experimental Results
Here, the first modification in basic technique is conducted in the following way. The DC component is directly realized in the spatial domain, which eliminates the use of DCT and IDCT for embedding in the DC component. The MATLAB simulation of modified DC component is shown in Figure 8.
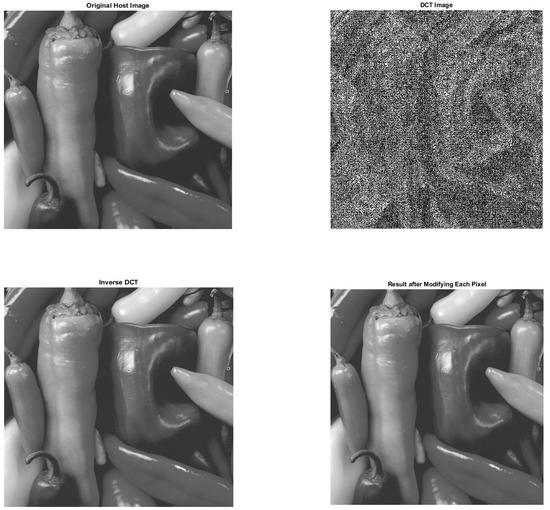
Figure 8.
Modification based on DCT.
Table 2 and Table 3 shows the calculation of DC component for the Block Image and the final resultant image.
4.1. Embedding and Extraction of 512 × 512-Host Image and 64 × 64 Watermark
The following Figure 9 show the result of the embedding and extraction of the watermark.
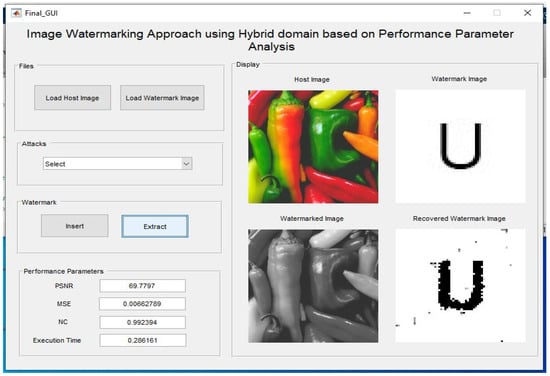
Figure 9.
Embedding and extraction using the proposed method for a host image of size 512 × 512 and watermark of size 64 × 64.
Extraction of watermark after applying different types of attacks such as scaling, cropping, adaptive filtering, salt and pepper noise, Gaussian noise, sharpening, etc. is shown in the following figures.
In the Figure 10, the watermarked image is scaled and then the watermark is extracted for checking performance against scaling attacks.
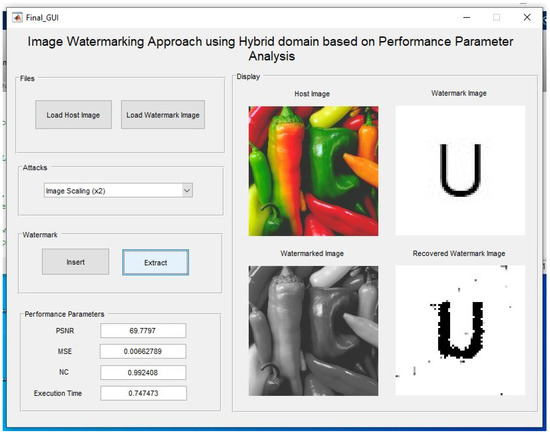
Figure 10.
Image scaling attack and extraction of watermark after scaling of watermarked image.
The Figure 11 demonstrate the first watermarked image is cropped from four corners, and then using the proposed extraction algorithm the watermark is extracted after the cropping attack.
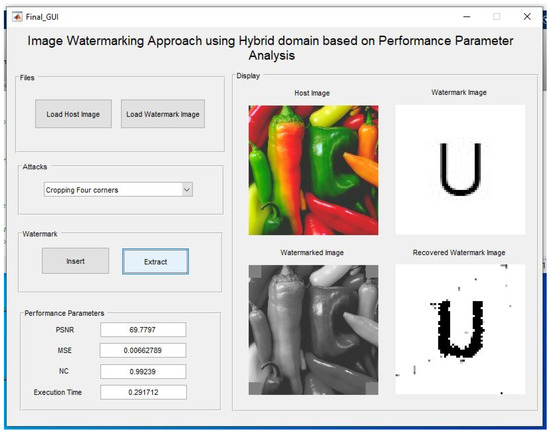
Figure 11.
Cropping attack and extraction of watermark after cropping a watermarked image.
Here, the Figure 12 demonstrates the image-filtering attack is applied on the watermarked image, then the watermark is extracted using the proposed method with high NC.
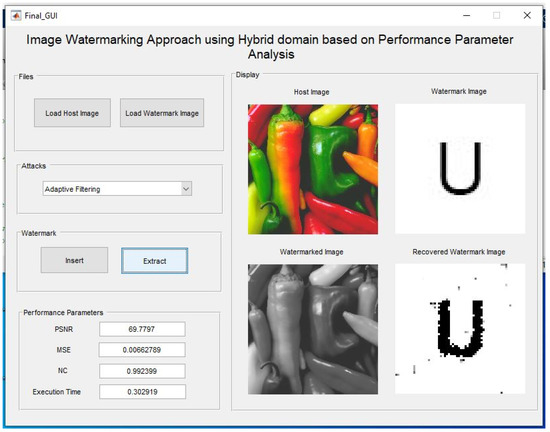
Figure 12.
Adaptive filtering attack and extraction of watermark after filtering the watermarked image.
In the Figure 13, the salt and pepper noise is added, and the watermark is extracted by using the proposed method. Comparison is conducted for original and extracted watermarks for measuring normalized correlation. The Table 4 below shows the comparison of extracted watermark from different attacks and the original watermark of size 64 × 64.
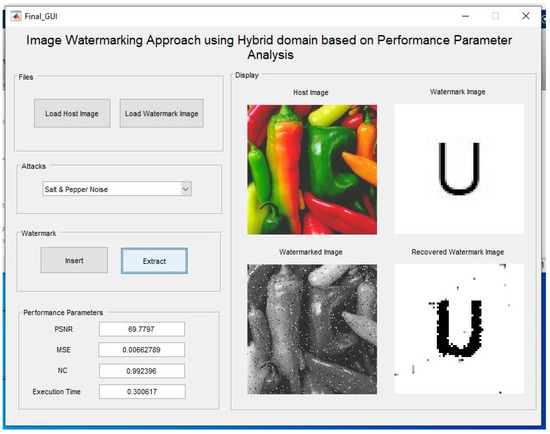
Figure 13.
Salt and pepper noise on the watermarked image and extraction of the watermark after adding noise.

Table 4.
Comparison of extracted watermark with original watermark of size 64 × 64.
4.2. Embedding and Extraction for a Real-Time Host Image Size of 1200 × 1200
For measuring the capacity, different resolution images are used. Different attacks are applied on watermarked images, and then the watermark is extracted after applying the attacks. The different attacks are histogram equalization, Gaussian noise, sharpening, etc. The following Figure 14 show the embedding of a watermark in the real-time image using the proposed method.
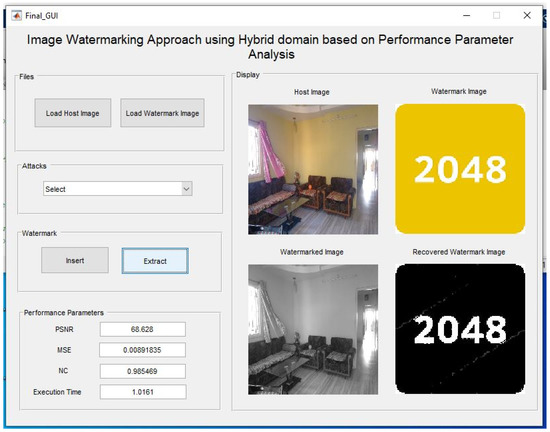
Figure 14.
Embedding and Extraction using the proposed method for a real-time host image of size 1200 × 1200.
Here, in the Figure 15 first histogram equalization attack is applied on a watermarked image and the watermark is extracted using the proposed method, as shown in the figure.
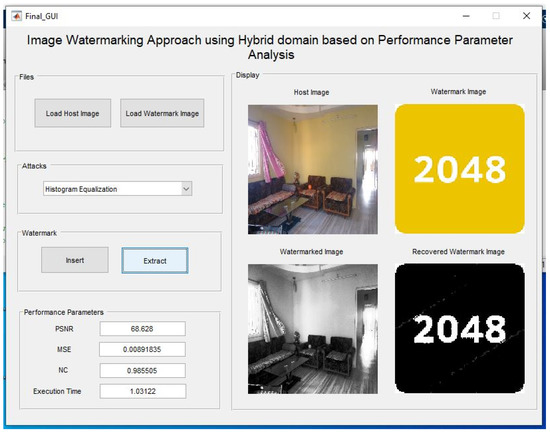
Figure 15.
Applying histogram equalization on the watermarked image and extraction of it.
In the Figure 16, Gaussian noise is added and the watermark is extracted after adding noise.
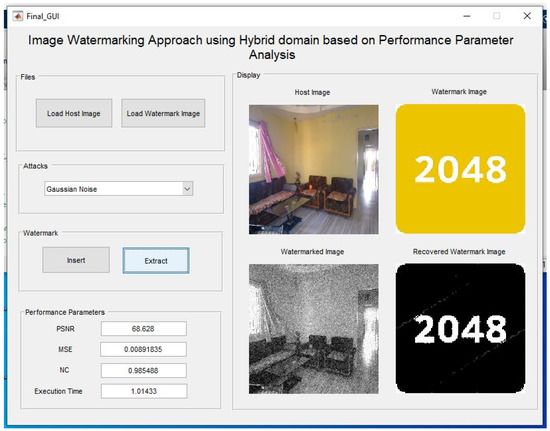
Figure 16.
Adding Gaussian noise, and extraction after adding noise.
In the Figure 17, the watermarked image is sharpened and then the watermark is extracted using the extraction method.
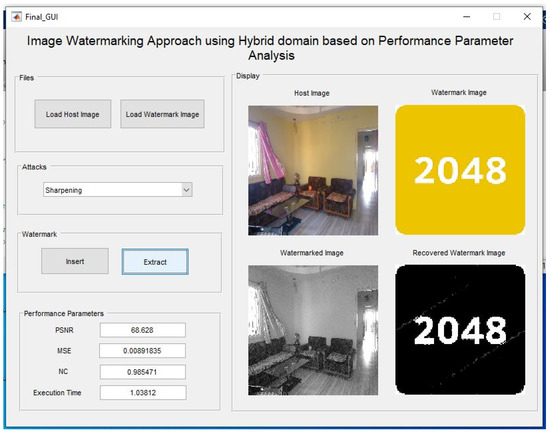
Figure 17.
Sharpened watermarked image and extraction after sharpening of the watermarked image.
The following Table 5 compares the extracted watermark with the original watermark, for checking the similarity and for measuring normalized correlation.

Table 5.
Comparison of extracted watermark with original watermark of size 128 × 128.
5. Results Analysis
Performance of execution of the proposed work is one of the criteria that needs to be considered. In this implementation, an image with a size of 512 × 512 and a watermark with a size of 64 × 64 is considered, and in another case, real-time images of sizes 1200 × 1200 and 128 × 128 are taken as input images for embedding algorithms. The maximum size of the image that can be taken is up to 1200 × 1200, and the watermark size is goes up to 256 × 256 bits.
The first total execution time for embedding and extraction with attacks and without attacks is measured as shown in the following Table 6:

Table 6.
Execution time comparison.
From Figure 18, it has been concluded that the proposed method can be executed in less time even with changing image size, with attacks and without attacks. The watermark is embedded and the mean square error is computed. Comparative analysis of Existing and Proposed methods is shown on the basis of PSNR and MSE in Table 7.
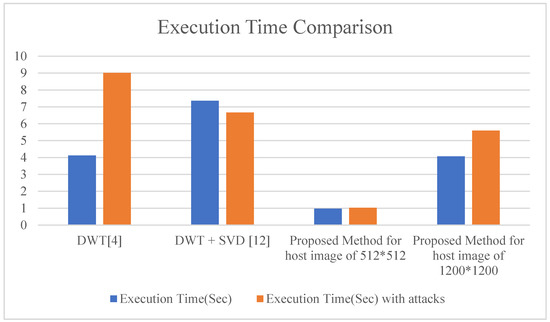
Figure 18.
Execution time comparison.

Table 7.
Results comparison of PSNR and MSE.
From Figure 19, it has been concluded that the PSNR is high. Acceptable Values of PSNR must be higher than 30 for better visibility. Therefore, in the proposed case, 69.77 is achieved.
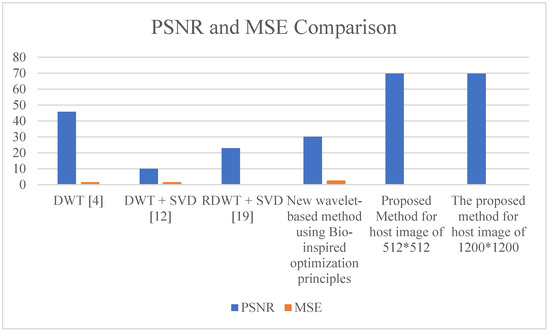
Figure 19.
PSNR and MSE comparisons.
Next, different types of attacks are applied such as scaling, cropping, adaptive filtering, salt and pepper noise, Gaussian noise, etc. on watermarked images, and the watermark is efficiently extracted. Normalized correlation is calculated for measuring the correlation. Comparison of existing and proposed method on the basis of NC value is done in Table 8.

Table 8.
Results comparison of NC for different types of attacks.
Figure 20, shows the different NC values for existing and proposed approaches. The acceptable value of NC should be near to one. The value of one means that the algorithm is very robust against different types of attacks. From the graph, the proposed method is concluded to be the best for all types of attacks. As the size of the host and water-mark image increase, the value of NC decreases, and time of execution also increases.
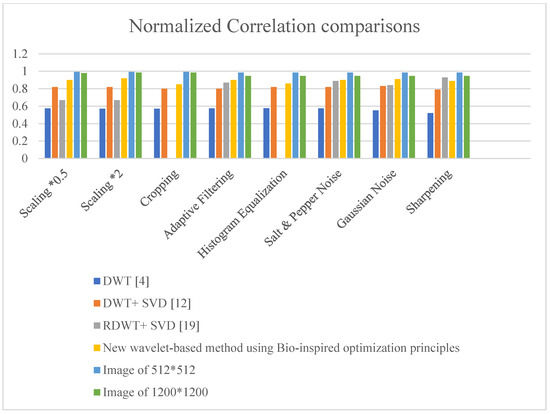
Figure 20.
Normalized correlation comparisons.
A Comparative analysis of proposed method with the existing one based on PSNR, MSE, Execution Time and NC value is done in Figure 21. In watermarking, high robustness and resistance to distortion are highly required. In the previous approaches, DWT has been extensively used for watermarking. However, in the LL band frequency, coefficients have high robustness but have a low resistance to distortion, which results in improper watermarking. In the proposed method, the DC coefficients are modified and then the watermarking is conducted in the spatial do-main, which results in both high robustness and higher resistance to distortion that improves the watermarking approach. The proposed method provides higher flexibility and good time–frequency representation. The disadvantages of using DCT are overcome by eliminating the use of DCT for finding DC, which enhances execution time and the mean square error. The proposed method can be used for different resolution images. As the size of the base image and watermark increases, robustness decreases and execution time and mean square errors increase; the peak signal to noise ratio will also increase.
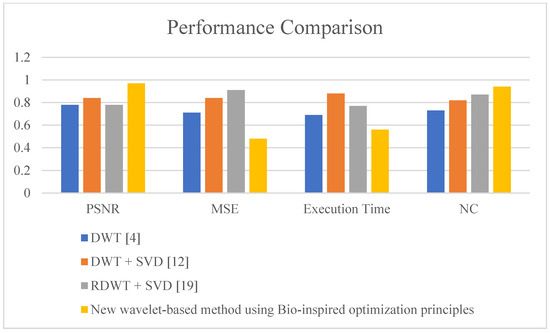
Figure 21.
Overall performance comparison of the proposed method with existing methods.
6. Conclusions and Future Enhancement
In this work, different techniques of watermarking are described. Different types of attacks that affect the robustness of images have also been discussed. The presence of a watermark should not distort the quality of the original image. Lots of research has been conducted to design solutions for providing high imperceptibility, strong robustness, more security, and high capacity. In this work, the focus is on providing strong robustness and high capacity. Hence, a modification is conducted to basic technique, and then embedding is performed based on a combination of modified techniques with existing DWT techniques; then, this combined method is used with pixel modification techniques, which enhances the capacity, robustness and imperceptibility, and reduces the total execution time.
Four parameters are analyzed (i.e., MSE, PSNR, NC, time) which show performance improvement of the proposed method. In this system, DWT is combined with a modified method instead of SVD, RDWT, etc. The method can be used and the same approach can also be implemented for video watermarking.
Author Contributions
Conceptualization, R.S. and R.T.; methodology, R.S.; software, R.T.; validation, R.S., R.T., M.G., A.K.Y. and J.P.; formal analysis, M.G.; investigation, R.S. and M.G.; resources, R.T. and A.K.Y.; data curation, R.S. and R.T.; writing—original draft preparation, R.S. and R.T.; writing—review and editing, R.T., M.G. and J.P.; visualization, A.K.Y.; supervision, M.G. and J.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research is partially supported by the NSF Grant 2025682 at Tennessee Tech University.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| DCT | Discrete Cosine Transform |
| IDCT | Inverse Discrete Cosine Transform |
| DWT | Discrete Wavelet Transform |
| RDWT | Redundant Discrete Wavelet Transform |
| PSNR | Peak Signal to Noise Ratio |
| MSE | Mean Square Error |
| NC | Normalized Correlation |
| DC Component | Direct Current (Average of Pixel Values) |
| CDMA | Code Division Multiple Access |
| RGB | Red–Green–Blue |
| LSB | Least Significant Bit |
| SVD | Singular Value Decomposition |
| LL Band | Approximate image of the input image (Low-Frequency Sub band) |
| LH | Horizontal features of Original Image |
| HL | Vertical features of Original Image |
| HH | Diagonal features of Original Image |
References
- Mane, G.V.; Chiddarwar, G.G. Review Paper on Video Watermarking Techniques. Int. J. Sci. Res. Publ. 2013, 3, 1–5. [Google Scholar]
- Chen, T.P.C.; Chen, T. Progressive image watermarking. In Proceedings of the 2000 IEEE International Conference on Multimedia and Expo, New York, NY, USA, 30 July–2 August 2000; IEEE: Piscataway, NJ, USA, 2000; Volume 2, pp. 1025–1028. [Google Scholar]
- Lee, J.C. Analysis of attacks on common watermarking techniques. IEEE Electr. Comput. Eng. 2017, 1, 1–7. [Google Scholar]
- Khalili, M.; Asatryan, D. Color spaces effects on improved discrete wavelet transform-based digital image watermarking using Arnold transform map. IET Signal Process. 2013, 7, 177–187. [Google Scholar] [CrossRef]
- Kumar, N.; Kalpana, V. Novel Reversible Steganography Method using Dynamic Key Generation for Medical Images. Indian J. Sci. Technol. 2015, 8, 61–74. [Google Scholar] [CrossRef][Green Version]
- Islam, S.M.; Debnath, R.; Hossain, S.A. DWT Based Digital Watermarking Technique and its Robustness on Image Rotation, Scaling, JPEG compression, Cropping and Multiple Watermarking. In Proceedings of the 2007 International Conference on Information and Communication Technology, Dhaka, Bangladesh, 7–9 March 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 7–9. [Google Scholar]
- Liu, X. Fractional krawtchouk transforms with an application to image watermarking. IEEE Trans. Signal Process. 2017, 65, 1894–1908. [Google Scholar] [CrossRef]
- Srivastava, R.; Srivastava, P. A multimodal-based approach for face and unique mark based combination for confirmation of human. Int. J. Bus. Anal. 2019, 6, 16–28. [Google Scholar] [CrossRef]
- Agarwal, H.; Sen, D.; Raman, B.; Kankanhalli, M. Visible watermarking based on importance and just noticeable distortion of image regions. Multimed. Tools Appl. 2016, 75, 7605–7629. [Google Scholar] [CrossRef]
- Lin, S.D.; Chen, C.F. A Robust DCT-Based Watermarking for Copyright Protection. IEEE Trans. Consum. Electron. 2000, 8, 415–421. [Google Scholar] [CrossRef]
- Singh, A.K.; Sharma, N.; Dave, M.; Mohan, A. A novel technique for digital image watermarking in spatial domain. In Proceedings of the 2nd IEEE International Conference on Parallel, Distributed and Grid Computing, Solan, India, 30 April 2012. [Google Scholar]
- Wang, S. A novel DIBR 3D image watermarking algorithm resist to geometrical attacks. Chin. J. Electron. 2017, 26, 1184–1193. [Google Scholar] [CrossRef]
- Srivastava, R. Score-Level Multimodal Biometric Authentication of Humans Using Retina, Fingerprint, and Finger vein. IJAEC 2020, 11, 1–16. [Google Scholar]
- Versaci, M.; Morabito, F.C.; Angiulli, G. Adaptive Image Contrast Enhancement by Computing Distances into a 4-Dimensional Fuzzy Unit Hypercube. IEEE Access 2017, 5, 26922–26931. [Google Scholar] [CrossRef]
- Simi, V.R.; Edla, D.R.; Joseph, J.; Kuppili, V. Parameter-free fuzzy histogram equalization with illumination preserving characteristics dedicated for contrast enhancement of magnetic resonance images. Appl. Soft Comput. 2020, 93, 106364. [Google Scholar] [CrossRef]
- Asikuzzaman, M.; Alam, M.; Lambert, A.; Pickering, M. Imperceptible and Robust Blind Video Watermarking using Chrominance Embedding: A Set of Approaches in the DT CWT Domain. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1502–1517. [Google Scholar] [CrossRef]
- Budiman, G.; Novamizanti, L.; Iwut, I. Genetics algorithm optimization of DWT-DCT based image Watermarking. J. Phys. 2017, 795, 012–039. [Google Scholar] [CrossRef]
- Khan, A.; Siddiqa, A.; Munib, S.; Malik, S.A. A recent survey of reversible watermarking techniques. Inf. Sci. 2014, 279, 251–272. [Google Scholar] [CrossRef]
- Qingtang, S. Robust color image watermarking technique in the spatial domain. Soft Comput. 2018, 22, 91–106. [Google Scholar] [CrossRef]
- Surbhi, A.M.; Rajesh, K. A Survey on Image Watermarking Techniques. Int. J. Sci. Emerg. Technol. Latest Trends (IJSETT) 2014, 1, 22–26. [Google Scholar]
- Jia, S.L. A novel blind color images watermarking based on SVD. Elsevier Int. J. Light Electron Opt. 2014, 125, 2868–2874. [Google Scholar] [CrossRef]
- Anjum, S.R.; Verma, P. Performance evaluation of DWT based image watermarking using error correcting codes. Int. J. Advanc. Comput. Res. 2012, 2, 151–156. [Google Scholar]
- Devi, B.P.; Singh, K.M.; Roy, S. Dual Image Watermarking Scheme based on Singular Value Decomposition and Visual Cryptography in Discrete Wavelet Transform. Int. J. Comput. Appl. 2012, 50, 6–13. [Google Scholar]
- Ramalingam, M. A Steganography Approach over Video Images to Improve Security. Indian J. Sci. Technol. 2015, 8, 79–86. [Google Scholar] [CrossRef][Green Version]
- Chopra, D.; Gupta, P.; Sanjay, G.; Gupta, A. LSB Based Digital Watermarking Technique. Int. J. Appl. 2014, 3, 2319–4847. [Google Scholar]
- Shen, X.F.; Ma, X.H. A Watermarking Algorithm for Digital Image Based on DCT and SVD. In Proceedings of the Congress on Image and Signal Processing, Sanya, China, 27–30 May 2008. [Google Scholar]
- Cerkezi, L.; Çetinel, G. RDWT and SVD based secure digital image watermarking using ACM. In Proceedings of the 24th Signal Processing and Communication Application Conference (SIU), Zonguldak, Turkey, 16–19 May 2016. [Google Scholar]
- Chang, C.C.; Tsai, P.; Lin, C.C. SVD-based digital image watermarking scheme. Pattern Recognit. Lett. 2005, 26, 1577–1586. [Google Scholar] [CrossRef]
- Arora, S.M. A DWT-SVD based Robust Digital Watermarking for Digital Images. Procedia Comput. Sci. 2018, 132, 1441–1448. [Google Scholar]
- Joseph, A.; Anusudha, K. Robust watermarking based on DWT SVD. Int. J. Signal Image Process. 2013, 1, 147–164. [Google Scholar]
- Rahman, M. A dwt, dct and svd based watermarking technique to protect the image piracy. Int. J. Manag. Public Sect. Inform. Commun. Techn. (IJMPICT) 2013, 4, 1–12. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).








