Abstract
With the development and popularization of Intelligent Transportation Systems (ITS), Vehicle Ad-Hoc Networks (VANETs) have attracted extensive attention as a key technology. In order to achieve real-time monitoring, VANET technology enables vehicles to collect real-time traffic updates through information collection devices and transmit this information to Roadside Units (RSUs), which are processed and integrated by an information processing center. However, high vehicle density leads to a conflict between minimizing the interval for vehicles to send Basic Safety Messages (BSMs) to RSUs and the limited communication resources of VANETs. To address this issue, we propose a MAC protocol based on the 802.11 CSMA/CA mechanism with the Preemptive-Resume Priority scheme. The arbitration device provides preemptive service to data packets with higher priority levels, thereby reducing data transmission delay. Moreover, queuing theory is employed to calculate the total delay for vehicles to send BSMs to a drone receiver, minimizing the BSM transmission interval and achieving minimal delay to meet safety driving requirements. The effectiveness and superiority of this mechanism and algorithm are demonstrated through simulation experiments.
1. Introduction
1.1. Preliminaries
In recent years, with the in-depth research and gradual popularization of autonomous driving technology, modern intelligent transportation systems (ITS) have become a focus of attention for governments, industry, and academia. Vehicle-to-vehicle (V2V) communication, as a core component of ITS, causes technical difficulties and challenges in the entire system. Each vehicle is equipped with a wireless interface called an On-Board Unit (OBU). The traditional method is that vehicles exchange and collect vehicle information and road condition information through the OBU and hand it over to the Road Side Unit (RSU) to complete communication between vehicles and infrastructure (V2I) [1]. The RSU then sends the information to the information processing center for data processing and integration. This leads to various challenges in Vehicular Ad hoc Networks (VANET). The communication coverage of VANETs is limited by the direct communication capability between vehicles and RSUs, which is further affected by factors such as terrain, buildings, and other obstacles. Consequently, certain regions or specific conditions may experience suboptimal communication quality or even a complete lack of continuous communication. Vehicles within VANETs are required to exchange a significant volume of data, encompassing crucial information such as location details, traffic status, event reports, and more [2]. Nevertheless, the data transfer speed in VANETs tends to be relatively slow due to the mobility of vehicles and the constrained transmission bandwidth. Consequently, this may result in increased communication latency and delayed data updates [3]. Ensuring the utmost reliability of vehicle data in VANETs is crucial for facilitating safety applications and enabling well-informed decision-making processes. However, ensuring data reliability presents certain challenges, such as signal attenuation, interference, and packet loss. These factors can undermine the reliability of data transmission. Unprocessed unreliable data can have detrimental effects, leading to erroneous decision-making or the dissemination of inaccurate traffic information [4]. However, the development of Unmanned Aerial Vehicle (UAV) technology has led to the replacement of RSUs by UAVs, which have become a topic of great interest for operators. UAVs, with their advantages of flexible deployment and wide coverage, offer faster transmission rates and can meet the demands of increasing user numbers and application messages. Compared to static relay stations, UAVs have a higher cost–performance ratio and economic efficiency due to their mobility, wide coverage, and low operation and maintenance costs [5]. Furthermore, UAVs can easily return to the air for inspection and maintenance, further reducing operational and maintenance costs. Low-altitude UAVs can fly in the air, free from the constraints of ground obstacles, providing a wider communication coverage range, filling the “blind spots” in communication between vehicles, and potentially offering better communication channels due to the existence of short-range line-of-sight (LOS) links [6]. Moreover, UAVs can expand network coverage and enhance network connectivity in various environments [7].
In VANETs, messages are characterized by their immediacy and time sensitivity, necessitating the timely transmission of messages from the source vehicle to the destination within a constrained time frame, while placing high demands on low latency. This requirement becomes particularly stringent in light of the advancements in autonomous driving technologies. Data packets that fail to meet the time constraints are discarded, leading to data loss [8]. In general, the vehicular networking domain follows the standardized framework established by the Society of Automotive Engineers (SAE) known as the J2735 standard [9]. At the heart of this standard lies the Basic Safety Message (BSM), thus making BSM messages the primary focus of discussion in this study. Vehicles periodically transmit BSM messages that encompass fundamental vehicle information, including position, speed, and acceleration. Given the time-critical nature and substantial volume of BSM messages, effectively managing network traffic load and mitigating congestion have emerged as pivotal research areas [10]. Furthermore, in situations where UAV resources are constrained or cost considerations come into play, multiple vehicles may require shared access to these resources. Consequently, the allocation of resources needs to be prioritized based on the urgency and importance of the demands to ensure their efficient utilization [11]. In particular, in emergency scenarios like traffic accidents or urgent rescue operations, specific vehicles may require expedited communication and assistance. Through the establishment of priority levels, it becomes feasible to guarantee prompt responsiveness and preferential allocation of resources to address these critical circumstances [12].
In the case of limited resources, constructing an appropriate Media Access Control (MAC) layer protocol is an important method for effectively managing network traffic load and alleviating congestion. The most popular media access control protocol used for wireless local area networks in the context of vehicular networks is IEEE 802.11P Distributed Coordination Function (DCF) [13]. It employs the Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) protocol with binary exponential backoff. DCF defines two channel access methods: basic access and the Request-to-Send/Clear-to-Send (RTS/CTS) mechanism. DCF not only plays a crucial role in new standards like IEEE 802.11e for enhanced Quality of Service (QoS), but it has also been widely implemented in various wireless test beds and simulation packages for wireless multi-hop self-organizing networks. Its low complexity has been widely recognized. Therefore, making reasonable improvements to this MAC layer protocol can provide a significant solution and innovation point for optimizing network architecture and addressing network congestion issues.
Moreover, when considering safety aspects, it has been shown that higher vehicle speeds on highways correlate with increased accident rates [14]. This insight offers a viable approach for establishing a priority criterion based on vehicle speed. In comparison to other metrics such as vehicle type or communication needs, vehicle speed is readily obtainable and can be promptly updated, enabling real-time reflection of the vehicle’s present motion state [15]. By prioritizing vehicles according to their speed, efficient resource allocation can be achieved. In general, vehicles traveling at lower speeds tend to have relatively lower requirements for real-time communication [16] as they can maintain a considerable distance from neighboring vehicles for a longer duration. Conversely, vehicles traveling at higher speeds necessitate timely communication support to promptly adjust their driving states and effectively respond to sudden situations. The prioritization of vehicles based on speed can further be leveraged for traffic flow control and coordination purposes. During instances of road congestion, the prioritization of faster-moving vehicles as a high priority can facilitate UAVs in providing real-time traffic feedback and route suggestions to enable these vehicles to avoid congested regions or opt for quicker routes [17]. This approach can potentially alleviate traffic congestion and enhance overall traffic efficiency.
1.2. Contributions
This paper primarily focuses on the information partitioning aspect, specifically centered around BSMs. The main contribution of this study is the proposal of a criterion for prioritizing vehicle speeds and the utilization of UAV assistance within the context of VANETs to provide services on unidirectional highways. Regarding priority partitioning, this paper presents an innovative preemptive approach and designs a MAC layer protocol based on the CSMA/CA protocol of 802.11P. Furthermore, this work incorporates queuing theory to calculate delays and control the feedback of information quantities. The key contributions of this paper can be summarized as follows:
- Based on the ground VANET system, a model is established, and vehicles are divided into different groups based on their speed ranges as priorities. The signal-to-noise ratio (SNR) and delay of the uplink transmission are calculated according to the relative position and angle between the vehicle and UAV.
- A MAC layer protocol with preemptive priority and an arbiter is designed based on the CSMA/CA protocol of 802.11P, and the MAC layer delay is calculated accordingly.
- A Preemptive-Resume Priority M/G/1 queue analysis is proposed for this model, which provides the average waiting time and average packet transmission delay for each class of packets. The time interval for sending BSM within the coverage range of the UAV by the vehicles is also calculated.
The remaining parts of this paper are as follows: Section 2 introduces recent research results in this field. Section 3 describes the network model and presents the main assumptions of the proposed model. Section 4 provides the calculation method for performance metrics. Section 5 conducts numerical simulations and analyzes the results. Section 6 concludes this paper.
2. Related Works
Regarding UAV-assisted VANETs, a model was introduced in [18] to estimate the probability of line-of-sight propagation in air-to-ground wireless communication across different urban environments. This model integrates building distribution, terrain, and other environmental parameters while accounting for signal attenuation, scattering, and multipath propagation. In [19], the authors put forward an aerial-to-ground path loss model based on the probability model of LOS using UAVs. They further provided a methodology for determining the optimal height and angle of the UAV based on this model. Moreover, Ref. [20] introduced the integration of UAV assistance to enhance the connectivity and support services in urban vehicle VANETs. By leveraging UAVs as mobile base stations, communication among vehicles can be enhanced, thereby facilitating the provision of additional services. In [21], the authors introduced a routing approach that leverages UAVs for connectivity and traffic density perception. By employing UAVs as relay nodes, the Connected and Reliable UAV-assisted Vehicular (CRUV) network can dynamically select the most suitable routing path, thereby improving the efficiency and reliability of data transmission within vehicular self-organizing networks. Ref. [22] introduces a methodology that leverages UAVs to provide services for highway VANETs and distributed antenna systems. Through the deployment of UAVs, the communication quality between vehicles can be enhanced, resulting in wider network coverage and stronger signal gain. Ref. [23] introduces a traffic service solution aimed at minimizing latency in multi-tier UAV networks. By taking into account the hierarchical structure, connectivity, and data transmission demands of the UAV network, this scheme optimizes traffic routing and scheduling strategies to effectively reduce latency and ensure the provision of reliable traffic services.
There are currently two methods available to tackle the congestion traffic control problem in BSM transmission. The first approach involves regulating the BSM generation frequency. In [24], the LIMERIC algorithm is proposed, which actively monitors the real-time congestion status of the network and dynamically adjusts the message rate according to the prevailing network conditions. This algorithm demonstrates notable improvements in system throughput and latency reduction, thereby better satisfying the communication demands of the Dedicated Short-Range Communications (DSRC) system. Ref. [25] presents a congestion control technique that utilizes power or rate adaptation. By dynamically adjusting the transmission power or transfer rate of vehicle nodes in response to the prevailing network congestion level, this approach endeavors to optimize the utilization of network resources and mitigate congestion. In [26], the authors propose a distributed algorithm design approach called DRCV, which leverages collaboration and information exchange among vehicle nodes to achieve efficient utilization of network resources and congestion control. The second approach to tackle congestion traffic control issues in BSM transmission involves power control, which regulates the transmission power of BSM. However, due to the influence of interference and path loss among vehicle nodes, distributed power control algorithms may experience anomalies during practical implementations [27]. To overcome these challenges, the authors proposed an enhanced algorithm that leverages signal strength measurement and collaboration among vehicle nodes. By dynamically adjusting the transmission power of nodes, this algorithm endeavors to improve system performance and mitigate interference. Ref. [28] presents a novel approach that involves real-time monitoring and analysis of vehicle status and the communication environment. This method enables the dynamic adjustment of communication parameters and route selection to optimize the overall communication performance. By continuously adapting to changing conditions, this approach aims to enhance the efficiency and effectiveness of communication in vehicular networks.
Significant progress has been made in the performance analysis of 802.11P, and Bianchi [29] proposed the well-known Markov chain model for 802.11 DCF under saturated conditions. Using the Markov chain model, extensive research has been conducted on the performance of 802.11 DCF under saturated conditions [30]. Shao et al. [31] proposed an improved MAC protocol to address communication issues in VANETs. This protocol supports data transmission with multiple priorities and employs p-persistent techniques to manage media access, thereby enhancing network efficiency and performance. In [32], the authors developed a throughput analysis model for the modified protocol and discussed how to optimize network performance through access control. By analyzing throughput and access control, this paper provides valuable insights for understanding and optimizing the performance of IEEE 802.11a networks. The application of queuing theory as a mathematical foundation for this protocol is also of great research significance. In [33], the signal transfer function of the generalized state transition graph was derived to describe the probability distribution of the MAC layer service time, and the M/G/1/K and M/M/1/K models were used to characterize the 802.11 MAC layer. Through these improvements, the protocol’s throughput can be enhanced, latency can be reduced, and network stability and reliability can be improved. The FPMDC-MAC [34] protocol algorithm is a notable contribution in the field of VANETs, specifically focusing on the MAC layer. This algorithm introduces a fuzzy logic-based priority assignment mechanism to ensure the efficient transmission of important information. Additionally, it incorporates a cooperative MAC protocol to facilitate communication coordination among vehicles, thereby improving data transmission efficiency. By modifying the 802.11p protocol and incorporating a priority scheme, FPMDC-MAC demonstrates significant enhancements over the existing protocol. In a related study by Wang [35], an improvement approach for enhancing the performance of the IEEE 802.11p/bd MAC protocol is presented. This approach utilizes a 2-D Markov chain model and queuing theory to construct the model, which shares similar methodologies with our research. However, it does not incorporate priority-related schemes, which constitutes a distinct advantage of our work. In [36], Yang proposed a hybrid MAC protocol based on priority, which combines slot allocation with a carrier sense multiple access (CSMA) mechanism. By incorporating priority assignment and dynamic slot allocation strategies, this protocol achieves fair sharing and efficient utilization of network resources among vehicles with different priorities. The paper also provided detailed deployment schemes for unmanned aerial vehicles, demonstrating that the protocol effectively improves network throughput, latency, and reliability while ensuring fair sharing and balanced resource utilization among vehicles with different priorities. In [37], the author Linn aimed to design a conflict-free cooperative MAC protocol to address the issue of heterogeneous collisions in VANETs caused by differences in vehicle speeds, communication ranges, and data transmission requirements. The protocol utilizes a cooperation mechanism among vehicles by dividing neighboring vehicles into multiple groups, where only one vehicle in each group is allowed to transmit data, while others act as relay nodes for data forwarding. This approach enables vehicles with different speeds and communication ranges to share network resources, reducing the probabilities of heterogeneous collisions and packet loss, thus improving network performance and stability. Ref. [38] introduced a repetition-based cooperative broadcasting scheme to enhance the reliability and efficiency of message delivery in VANETs and mitigate the adverse effects of fading on message transmission. In this scheme, vehicles within the communication range form a cooperative group and collaborate to forward broadcast messages. Cooperation is achieved through the utilization of repetition techniques, where each vehicle retransmits the received message multiple times to increase the likelihood of successful message reception by other vehicles.
In [39], a priority-based communication scheme for V2V communication is presented, which is realized in VANETS utilizing the IEEE 802.11p standard. This scheme focuses on enhancing the QoS mechanism and incorporates priority scheduling techniques to optimize communication efficiency and minimize latency. By assigning different priorities to various types of data and vehicles, the proposed scheme aims to prioritize critical information and improve the overall performance of vehicular communication systems. Ref. [40] presented a novel priority-based approach for emergency data dissemination in urban environments. This method is specifically designed to facilitate the swift propagation of critical information during emergency situations. By leveraging prioritization techniques, the proposed method enhances the speed and reliability of data delivery, ensuring that emergency data reach relevant entities promptly. This approach holds great potential for improving emergency response systems and enhancing the overall efficiency of urban communication networks. In [41], the authors propose a V2V emergency data transmission scheme based on TCP protocol and priority queue technology in VANETs. This scheme utilizes stable connections and priority queue techniques to achieve fast transmission of emergency data. Moreover, it incorporates mechanisms such as traffic control and congestion control to ensure the stability and reliability of the transmission. Ref. [42] presents a novel dynamic resource allocation algorithm for optimizing the utilization of limited UAV and spectrum resources. The proposed algorithm takes into account both the communication demands of vehicles and the current network conditions. By considering factors such as vehicle-specific communication requirements and energy constraints, the algorithm intelligently allocates UAV resources to ensure efficient resource utilization. This approach holds significant potential for enhancing the overall performance and effectiveness of UAV-assisted communication systems in scenarios with limited resources.
Our work is based on the computational model of drone-assisted vehicular networks proposed in papers [18,19]. Furthermore, Refs. [20,21,22,23] provide strong evidence that supports the superiority and effectiveness of drones as relay nodes in vehicular networks. Currently, there are two main approaches to address the BSM traffic congestion control problem we are interested in: one is by adjusting the generation frequency, as discussed in Refs. [24,25,26] and the other is power control, as explored in Refs. [27,28]. Our proposed solution focuses on designing a MAC layer protocol that minimizes latency through preemptive priority and queuing theory and subsequently adjusts the generation frequency. The limitations of Refs. [24,25] lie in their focus on real-time congestion monitoring and optimizing network utilization efficiency without modifying the MAC layer or providing system-wide optimization. While real-time congestion monitoring is an effective method, it does not solve the fundamental problem. On the other hand, Ref. [26] mainly emphasizes vehicle-to-vehicle communication, overlooking the auxiliary role of drones or road test units. Our research centers around designing a MAC layer protocol to adjust the 802.11P protocol in vehicular networks, incorporating key aspects such as Markov chain modeling, queuing theory, and priority design. Unlike Refs. [29,30,31,32,33,34,35,36,37,38,39,40,41], our work comprehensively considers these three aspects, which we believe will lead to better results.
To present a comprehensive comparison, we summarize the related work, its shortcomings, and our proposed solution in Table 1. This table will allow readers to gain a clear understanding of the existing research landscape and how our approach stands out in addressing the identified limitations.

Table 1.
Comparison of Other Papers and Our Work.
The main objective of our research is to address the congestion traffic control problem in BSM transmission. Unlike existing research, we focus on the specific needs of vehicles for BSM transmission. Specifically, we adjust the frequency of BSM generation so that faster-moving vehicles can transmit safety information at shorter intervals, thereby meeting their higher safety standards. In addition, we improve the 802.11P-based DCF protocol by combining it with a preemptive priority M/G/1 queue mathematical model. According to this protocol as the MAC layer protocol of the link, we perform uplink data transmission and allocate resources based on delay as the primary performance indicator in resource-constrained scenarios. This approach ensures that vehicles with higher priorities receive a greater share of resources to meet their shorter transmission interval requirements and better meet the needs of safe driving. Through extensive experimental validation, we demonstrate the effectiveness of our proposed method in controlling congested traffic and improving overall system performance.
3. System Model
In our analysis, we consider a single-directional highway segment based on UAVs with a length of D. We need to consider the following situation: As shown in Figure 1, represents the reference point where vehicles arrive. The network consists of N vehicles (index ) and M UAVs (index ). The UAVs have a communication range that covers the entire road segment, with the distribution parameter following a uniform distribution. Given the limited availability of communication resources in UAV and VANET communications, ensuring real-time monitoring of vehicle safety conditions and road conditions becomes a critical challenge. It is essential to transmit BSM information at the shortest possible intervals to meet these requirements. However, this can result in resource constraints and insufficient timeliness, leading to potential safety hazards caused by an overwhelming number of BSMs. Consequently, there is a need to prioritize vehicles and their transmitted data packets. This paper will focus on prioritizing vehicles based on speed ranges and give particular attention to BSM information.
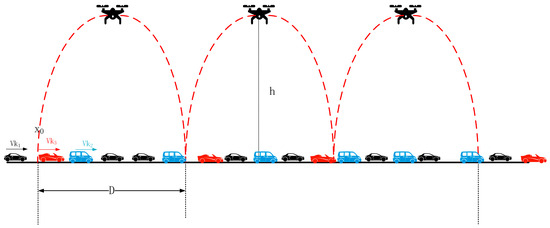
Figure 1.
Vehicle-to-Vehicle Communication Model.
The process can be divided into two steps: (1) classifying vehicles and their transmitted information based on their speed and designing a MAC layer protocol to schedule and queue the transmitted information; (2) using the 802.11p protocol, vehicles transmit the required messages through the MAC layer scheduling process and send them to the UAVs via the uplink. The following provides a detailed explanation.
For convenience, the significant notations and variables used in the analysis procedure are summarized in Table 2.

Table 2.
Notions used in the proposed analytical model.
3.1. Ground-Bound Vehicular Traffic Model
This paper assumes that the considered segment D represents a low- to moderate-density free-flow ground transportation system. Such a transportation system has been widely applied in the literature. The macroscopic free-flow traffic model used in this study is based on Ref. [43].
Because the communication range of UAVs under the V2I scenario in a highway depends on multiple factors, including the frequency, power, antenna gain of its communication system, as well as environmental conditions, the communication range can vary from several hundred meters to several kilometers based on different UAV communication systems and specific configurations. Additionally, assuming a constant velocity can help study the worst-case scenario in V2I. Therefore, we assume that after each vehicle k reaches position , its velocity remains unchanged at the speed at position until it exits the communication range of the UAV, .
We assume that the number of vehicles follows a Poisson distribution, and the vehicle density is . The premise of our study is that the vehicle density is not high, as in the case of high vehicle density, and it is highly likely to find multiple vehicle-UAV paths for connection, which does not align with our design approach. We focus on the worst-case scenario, aiming to minimize the number of paths. In this scenario, each time a vehicle enters the communication range of a UAV, it needs to be processed individually.
Additionally, we assume that the VANET includes a location service, such as Hierarchical Location Service (HLS) or Geographic Location Service (GLS), and the information related to the location service is included in the header of the transmitted data packets.
We divide a time window into several equal intervals . Since the traffic flow follows a Poisson random process with the parameter , the arrival time of vehicles is also a random variable denoted as and follows an exponential distribution with the parameter . Assuming that there is one vehicle arriving at the entrance point in each time interval , the average value and probability density function (pdf) [44] of the vehicle arrival time can be written as follows:
The speed at point is a continuous random variable, represented by for the mean value and for the standard deviation. The probability density function (pdf) of follows a truncated normal distribution [45].
In addition, , and the time for a vehicle to pass through is denoted as .
3.2. UAV-Assisted Vehicular Channel Model
The task of utilizing UAVs as intermediate relay bridges to facilitate the construction of VANET networks for enabling communication between two vehicles that are not within direct range of each other has been extensively studied in previous research papers. However, this specific scenario is not the focus of this paper. Instead, this paper primarily focuses on studying the connections formed within the communication range of a UAV. Each UAV categorizes and prioritizes all vehicles within its coverage area based on their speeds. By calculating the total delay, performing comparisons, and making optimal allocations, this paper aims to provide a detailed explanation. The relationship between drones and vehicles’ positions is as shown in Figure 2.
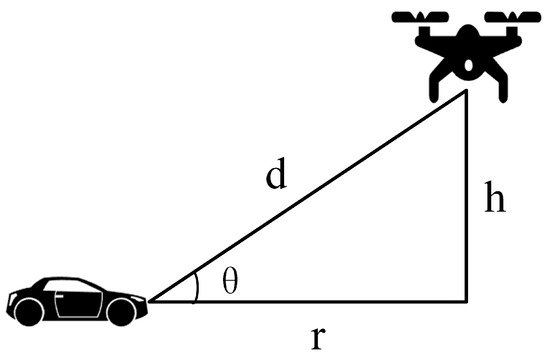
Figure 2.
Vehicle–UAV Position Relationship Diagram.
The speed of each vehicle is gathered at location and remains constant until it exits the communication range of the UAV. At any given time, a vehicle establishes an uplink connection with the UAV. To ensure that the UAV can receive signals from each vehicle and obtain signal strength, this model is considered to be composed of both LoS and NLoS links [22]. Depending on the UAV’s position and flight altitude, these links will have different probabilities. The vehicle K’s position is defined as , while the UAV’s position is , and must be optimized to satisfy QoS constraints. As shown in Figure 2, according to the Euclidean distance, the distance d between vehicle k and UAV u can be written as:
Assuming negligible values are ignored and considered as 0, the probabilities of LoS and NLoS links corresponding to the UAV are as follows:
where and are constants determined by the environment and carrier frequency, is the elevation angle, and =. Thus, the path loss expressions for LoS and NLoS links can be derived as follows:
where, represents the path loss exponent, and and are determined by the environment and represent the average additional loss for free space propagation in LoS and NLoS connections, respectively. denotes the speed of light, and represents the carrier frequency. Therefore, we can obtain the average path loss and the average channel gain as follows:
Thus, we can derive the SNR received by the UAV u from the vehicle at its current position as follows:
where is the transmission power of vehicle k, represents co-channel interference, denotes Gaussian white noise, and W is the bandwidth. According to the model, to achieve effective data transmission between the UAV and the vehicles, it is necessary to maximize the end-to-end rate while minimizing latency and power consumption.
3.3. The MAC Layer Communication Protocol
In densely populated traffic areas, such as congested urban roads or highways, vehicles often accumulate a substantial volume of safety information. As per the J2735 standard established by the Society of Automotive Engineers (SAE) in the United States [9], the increased number of vehicles leads to a significant rise in the frequency of BSMs received by UAVs per second. Consequently, important safety information may be discarded due to large transmission intervals, resulting in delayed or inadequate updates that compromise timeliness. This situation poses significant safety hazards. To mitigate such concerns, we have implemented a prioritization scheme for vehicles and their messages, enabling the prioritized validation and transmission of critical safety information. The subsequent section outlines the design of our MAC layer protocol.
In this study, due to vehicles entering the UAV communication range as a Poisson process and each vehicle transmitting fixed-sized data packets of bits at any given time, we adopt an M/G/1 queue model. Taking into account the priority categories, we assume there are r priority levels. Vehicles and their transmitted data packets of priority level i arrive according to a Poisson process with arrival rate , with specific values obtained from Section 3.1. It is worth noting that the adopted priority mechanism in this study is Preemptive-Resume Priority [46], meaning that high-priority customers interrupt the service of low-priority customers. Upon interruption, a checkpoint is set, and the interrupted data enter the Shunts for storage. The service time of the lower-priority customer resumes at the checkpoint. For a customer of priority level i, due to the preemption rule, there are no lower-priority customers appearing ahead of them in their queue, i.e., . The following provides a detailed explanation of the priority setting.
As shown in Figure 3, all devices are located inside the UAV for operation. The frame-header Checker (referred to as Checker in the diagram) is responsible for checking the header of the message packets received from the vehicles on the uplink, determining whether to accept them and dividing them into segments based on the vehicle’s speed (included in the packet header). Buffer-A, Buffer-B, and Buffer-C represent three buffers that receive data packets from different priority levels and wait for instructions from the Arbiter. The Arbiter is responsible for scheduling the transmission order on the output link and accessing the outgoing packets. It has Shunts B and Shunts C buffers that store the remaining data packets of interrupted low and medium priority levels due to the Preemptive-Resume Priority rule.
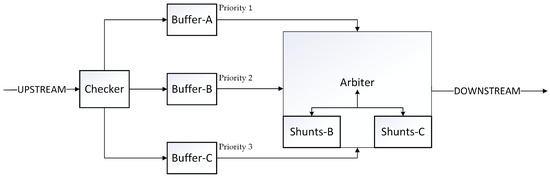
Figure 3.
Basic Structure Diagram of the MAC Layer Protocol.
The information enters the frame-header Checker from vehicles on the Up Stream and the message priority is determined. The information transmitted by vehicles in the high-speed section enters Buffer-A as high-priority, while that transmitted by vehicles in the medium-speed section enters Buffer-B as medium-priority and that transmitted by vehicles in the low-speed section enters buffer Buffer-C as low-priority. The Arbiter is responsible for scheduling the transmission order on the output link and accessing the outgoing packets. If a medium-priority packet is interrupted by a high-priority packet, a breakpoint is set, and the remaining packets are transferred to Shunts B. If a low-priority packet is interrupted by a high- or medium-priority packet, a breakpoint is set and the remaining packets are transferred to Shunts C. We assume that the time it takes for packets to be transmitted to the buffer is negligible [47].
The protocol defines the mechanism for bandwidth allocation and packet scheduling. Assuming that the number of packets is negligible and that each buffer has an infinite capacity, the Arbiter can simply schedule the packets based on the following priority order (from highest to lowest). The packet scheduling is based on considerations of timeliness since the unmanned vehicle has a limited capacity to process messages within a given time period. Therefore, the protocol prioritizes the processing of data packets from vehicles in the high-speed section. Here is the specific priority order:
- Packets from Buffer-A
- Packets from Buffer-B
- Packets from Buffer-C
In this order, the Arbiter will allocate resources and schedule packet transmission accordingly.
As shown in Figure 4, the queue currently contains one data packet with priority 2 and two data packets with priority 3. At this moment, when a data packet with priority 1 arrives, it interrupts the queue and is prioritized for processing.
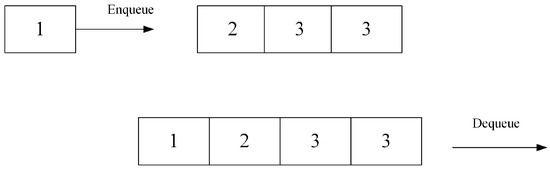
Figure 4.
Max Priority Queue.
The following is a description of the protocol steps for the Preemptive-Resume Priority 802.11 CSMA/CA [48] with an arbiter in this article; the flowchart is shown in Figure 5.
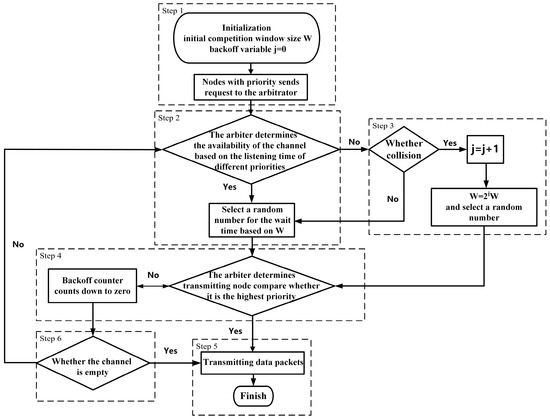
Figure 5.
Protocol Flowchart.
Step 1: Initialization
Each node determines its own priority and sets reasonable initial contention window sizes, maximum backoff times, and an arbiter node to coordinate the priority transmission order between nodes and the preemptive interruption (including the buffer).
Step 2: Contention Stage
- When a node is ready to send data, it first sends requests to the Arbiter and carries its priority information.
- The Arbiter sets different listening times for different priorities brought by each node (shorter for higher priority, and so on, defined as High Distributed inter-frame space (HDIFS), Middle Distributed inter-frame space (MDIFS), and Low Distributed inter-frame space (LDIFS)). If the channel is idle during the listening time, the contention channel stage is entered; otherwise, the backoff mechanism is triggered.
Step 3: Backoff Mechanism
This article employs the backoff mechanism of IEEE 802.11 standard DCF, which uses a binary exponential backoff method with a backoff time range of (0, ). represents the current backoff stage, and represents the corresponding contention window size. is equal to 2 to the power of J, where m is the maximum backoff stage specified in the 802.11 standard, and W is the initial contention window size (as set in step 1). The backoff counter takes a value of and decreases by one for every time slot when the channel is idle; otherwise, it remains unchanged. If a collision occurs (i.e., multiple nodes have the same priority or the Arbiter indicates preemption is allowed, causing these nodes to potentially send data simultaneously), the contention window of the colliding nodes doubles to reduce the collision probability. The node enters the contention phase when the backoff counter countdown ends; otherwise, it continues to wait and updates the counter.
Step 4: Contention Channel
After the backoff counter of a node reaches zero, the node sends another request to the Arbiter. The Arbiter evaluates the priority of the node and considers other ongoing transmissions to determine the next node for data transmission. If the current node has the highest priority or the Arbiter indicates that the node can preempt, the node immediately sends the data. Otherwise, the node continues to wait.
Step 5: Data Transmission
Nodes that obtain permission from the Arbiter start transmitting data. Other nodes temporarily stop sending data and continue to monitor the channel state upon detecting channel occupancy.
Step 6: Channel Release
Upon completion of data transmission, the node releases the channel and notifies the Arbiter that the channel is idle, allowing other nodes to contend for the channel.
In summary, in this scenario, we need to consider the following aspects:
Reasonable selection of UAV altitude and communication range.
Considering the transmission time from vehicles to UAVs, calculate the MAC layer service time. The queuing time is calculated using the designed UAV MAC layer protocol. Calculate the expressions for latency and rate, and based on this, calculate the BSM transmission interval.
Based on the parameter definition of the objective function, obtain a solution that is in line with practical considerations and simulate its implementation.
4. Problem Formulation and Performance Metrics
Based on the model and various performance metrics proposed in the previous section, we divide this section into four parts:
- Calculate the uplink transmission latency between the UAV and each vehicle based on the UAV-Assisted Vehicular Channel Model from the previous section.
- Calculate the overall MAC layer service time based on the uplink transmission latency and the MAC protocol.
- Calculate the queuing time and overall system dwell time based on the Preemptive-Resume Priority rule and service time.
- Calculate the BSM transmission interval for vehicles within the UAV coverage area based on the system dwell time.
- Next, we will introduce these three parts separately. Let T denote the total communication delay between vehicles and the UAV.
4.1. UAV Communication Latency
As shown in Figure 1, vehicles arrive at location and randomly establish communication links with the UAV within its communication range. Let us assume that all vehicles transmit data packets of the same size, denoted as bits. Let T represent the total communication delay between vehicles and the UAV. The specific calculation expressions are described below.
4.1.1. UAV Uplink Communication Latency
In order to derive the channel characteristics between vehicle k and the UAV, we consider an uplink P-NOMA network where vehicles encode their data packets through superposition coding and transmit them to the UAV over a shared channel. At the UAV, the data packets are relayed using a Decode-and-Forward (DF) protocol. According to the channel characteristics model provided by the UAV-Assisted Vehicular Channel Model and based on the Shannon–Hartley formula, the transmission rate of vehicles in the G2A channel is obtained as:
where is a constant representing the total available bandwidth of the uplink path, and can be obtained from Equation [11] in the previous section. Based on the transmission rate, we can determine the time required to transmit a data packet of size as:
4.1.2. UAV MAC Layer Service Delay
In this paper, we only consider the access mechanism. Furthermore, we have the following assumptions: (1) The network consists of r competing stations, where r is the number of priority levels. (2) Since vehicles follow a Poisson arrival model and each vehicle sends a message containing only one data packet of the same size bits, the arrival of data packets at the MAC layer also follows a Poisson process with the same arrival rate as the vehicle arrival rate . (3) It is assumed that the probability P of collision occurring in transmission from a station is constant and independent of the transmission history.
In this paper, the probability of a station sending in a random time slot is defined as . The relationship formula between and P is derived from a generalized Markov chain model [19]. In this paper, a Monte Carlo algorithm is used to calculate the probability of collision for each priority level. The value of P depends on the arrival rate, and the value of P for lower priority levels should be added to the value of P for higher priority levels (because priority level 1 will only have effective collisions with priority level 1, while priority level 3 will have effective collisions with priority levels 1, 2, and 3). The specific process is as shown in Algorithm 1:
| Algorithm 1: Proposed algorithm for Packet Channel Collision Probability. |
| Input: arrival rate array, num packet array, window size array, number of priorities, number of iterations Initialize: num collisions = array of size num priorities initialized with zeros Output: collision probability array for each priority Begin: for iter = 1 to num iterations do arrival times = generate arrival times (arrival rates, num packets) for i = 1 to num priorities do for j = 1 to num packets[i] do if check collision (arrival times, i, j, window sizes) then num collisions[i] = num collisions[i] + 1 end if end for end for end for collision probabilities = calculate collision probabilities (num collisions, num packets, num iterations) End |
This algorithm is used to calculate the collision probability (P) for different priority levels and scenarios, and then this information can be utilized for subsequent calculations.
Let denote the backoff stage and denote the corresponding contention window size,. W represents the initial window size, typically defined as 15 or 31 according to the 802.11P protocol. m denotes the maximum backoff stage defined by the 802.11P protocol. represents the value of the backoff counter at time t, and represents the backoff stage of the node at time t.
In this paper, we assume a constant collision probability P that is independent of the transmission history, allowing us to discretize the two-dimensional stochastic process for Markov chain modeling. Due to the impact of factors such as vehicle speed and road conditions, the packet arrival rate in this paper is limited, resulting in an unsaturated condition. When the buffer is empty, the backoff counter is not activated. Therefore, to represent this condition, we introduce states to indicate an empty buffer. It should be noted that we assume that if no collision occurs, a packet will either be successfully transmitted or reach the maximum retry limit and be discarded, without considering other reasons for transmission failure. Let denote the probability of no packet arrival within a time slot, which depends on the slot size and the packet arrival rate. The mentioned virtual slot size refers to the average interval between two consecutive decrements of the backoff timer. Therefore, we build a discrete-time Markov chain model based on the two-dimensional stochastic process , where the combination of backoff stage and backoff counter value represents the state of a node. The collision probability P and current state are used to determine the transition to the next state. This approach allows us to analyze and derive performance metrics for the system. The modified generalized Markov chain model is shown in the Figure 6.
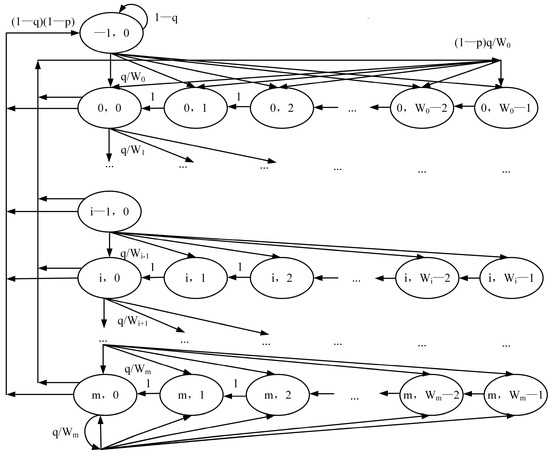
Figure 6.
Markov Chain Model.
The transition probabilities of the generalized Markov chain are as follows:
Let denote the stationary distribution of the chain. According to the regularity of the chain, we can express it as follows:
By imposing the normalization condition, we can obtain:
Then, the transmission probability of the user in a random time slot is defined as τ, and transmission starts when the backoff counter is 0. τ can be obtained by the following formula:
The actual time slot interval for a station is determined by the algorithm and specific parameters in different priority scenarios.
represents the probability of detecting a busy channel due to successful transmissions from other stations, and represents the probability of the channel being idle. and can be calculated using the following equation.
represents the duration of a successful transmission, represents the duration of detecting channel busyness due to collisions, and represents the duration of an idle system time slot. and can be obtained using the following equation:
Note that in this article, different priority levels have different Distributed inter-frame space (DIFS) values (HDIFS, MDIFS, and LDIFS), which means that the time slot duration () for each priority level is also different. Additionally, is the transmission rate obtained in the previous section, and we define . This article takes the average values of variables and for all vehicles in each priority level.
In practice, the duration of a station’s collision () depends on whether the station participated in the collision or observed it. However, since the 802.11 standard does not have an ACK timeout specification, this article assumes that . Therefore, the actual time interval can be simplified as follows:
The probability of no packet arrival within a time slot interval 1 − q can be written as:
The average MAC layer delay can be expressed as [30]:
In the equation, m represents the maximum backoff stage specified by the 802.11 standard, and W represents the initial contention window size. It is important to note that the variable varies for each priority level.
4.2. UAV Queuing Delay
In this section, we will focus on studying queuing delay, which is an important component of overall latency. It can be defined as the time taken for a packet to reach the transmission buffer and is dependent on the number of users multiplexed on the same wireless resource [46]. Due to vehicle arrivals following a Poisson process and assuming each vehicle sends a data packet of size , arrivals are exponentially distributed in this paper. Even under relatively low loads, queuing delay can occur due to sudden changes in incoming traffic. To measure the performance of the queue, we define the utility ratio (the probability that all servers are busy). As is a probability and needs to satisfy the requirement of queue stability, its range should be between 0 and 1.
Since the arrival time and service time of packets are independent, and the arrival process in the MAC layer’s arrival area and buffer area is also a Poisson process (refer to Section 3.3), based on the standard queuing theory, the packet queuing model for UAV MAC layer can be regarded as a Preemptive-Resume Priority M/G/1 model.
In the following calculations, we have different delay expressions for each priority. In this paper, we use the following symbols: represents the average queuing time for priority i, and represent the average service time and remaining service time for priority i. is the second moment of the average service time for priority i, derived from the formula . represents the variance of the distribution for that priority, which is exponential distribution in this case. denotes the average arrival rate for priority i, and represents the system utilization for priority i. The formula for . As mentioned earlier in this paper, the number of priorities in this model is r = 3. The value of is obtained from the upstream communication delay and its MAC layer delay. is constant.
The queuing delay is the time span from when a packet enters the buffer and waits in the channel allocation queue until it starts to be transmitted. According to Little’s Law and the Pollaczek–Khintchine (P-K) formula, we can obtain the average waiting time for the highest priority as follows:
where the remaining service time is obtained from the following formula:
It is evident that the remaining waiting time for different priorities will be different due to the effect of preemptive rules. Customers with higher priority enter the system without having to wait for customers with lower priority to be served. They are immediately interrupted, and the interruption point is set.
For the second priority, we need to consider the associated workload of customers with the same and higher priority who are already in the system when this customer enters, as well as the workload generated by higher priority customers who may arrive during the waiting time. Therefore, can be calculated using the following formula:
For all priorities, the derivation is similar, and the average waiting time in the buffer can be expressed as follows:
where i is the priority level, ranging from 1 to r.
This paper selects two representative cases for illustration, as follows:
As shown in Figure 7, for Scenario 1, is selected, where the vehicle with the slowest speed segment has the highest arrival rate and the largest number of vehicles. For Scenario 2, is selected, where the vehicle with the highest speed segment has the highest arrival rate and the largest number of vehicles. The remaining scenarios, as they are not representative, are not discussed in this paper.
Figure 7.
Simulated Figure for Scenario 1 and 2 Data Packet Arrival Order.
In our system, we define as the average communication delay between each vehicle within the coverage range of the UAV across different priority levels.
According to the equation , we can obtain the relationship between system utilization rate as follows:
By substituting Equation (30), we can rearrange the equation as follows:
4.3. Expression for Total Delay
For a preemptive MAC layer protocol, the expression for the overall delay, which is the average dwell time, is as follows:
4.4. BSM Transmission Interval
According to the model in Section 3.1, the expected passing time of vehicles in each speed segment is calculated based on the average velocity of vehicles in that segment. Let be the expectation of the passing time, which can be expressed as . Then, the expected BSM transmission interval for each priority level, denoted as , is given by the following equation:
where represents the number of vehicles in priority level i, and the minimum time interval for BSM transmission for vehicles in priority level i is denoted as:
4.5. Minimization of BSM Transmission Interval Problem
In the limited case of UAV, we aim to maximize the frequency of BSM transmissions as much as possible. This approach improves safety. Therefore, we need to discuss the problem of minimizing the BSM transmission interval. Based on Equation (39), minimizing the BSM transmission interval can be understood as minimizing the overall delay for each priority level. An optimization problem with an objective function and constraints can be formulated as follows:
As derived from Equation (39), the above minimization problem can be obtained from the following minimization problem:
where i is the set priority level.
Algorithm 2 provides the process of minimizing the BSM transmission interval.
| Algorithm 2: Proposed algorithm for Transmit Interval of BSM minimization |
| Initialize: set the number of priority levels r End for End |
5. Numerical Results
In this paper, we idealize the definition of a message to contain only one packet, which can be adjusted in size as bits. Multiple packets contained within a message can be treated as one large packet. In this paper, the packet size is set to 10,240 bits.
To evaluate the effectiveness of the above expression, we conducted simulation experiments on MATLAB. In the simulation, the set parameters are shown in the following table, where the G2A link delay is based on Table 3 and referenced from the literature [19].

Table 3.
G2A Link Delay Parameter Table.
The MAC layer and queuing delay are based on Table 4, referenced from the literature [48].

Table 4.
MAC Layer and Queuing Delay Parameter Table.
Furthermore, this paper defines the number of priority levels r as 3. The control frame rate is . The DIFS for each priority level is defined as . The vehicle speed range is defined as ; .
Analysis of Delay and Processed Packet Volume under Different Arrival Rates
For scenario 1, we selected and defined the collision probability P based on the number of vehicles or messages, where a higher number of messages corresponds to a higher probability of packet collisions, .
For scenario 2, we selected and defined the collision probability P based on the number of vehicles or messages, considering the case where higher priority packets need to take into account the presence of low priority packets in effective collisions, .
According to Figure 8a, the model follows a Poisson distribution, and it shows the number of vehicles in different speed ranges under the condition of .
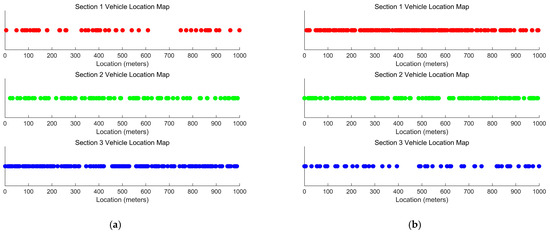
Figure 8.
Scenario 1 and 2 Vehicle Location MAP. (a) Scenario 1 and (b) scenario 2.
According to Figure 8b, the model follows a Poisson distribution, and it shows the number of vehicles in different speed ranges under the condition of .
According to the simulation and Figure 9a, the average speed in different speed ranges is . The average passage time in different speed ranges is .
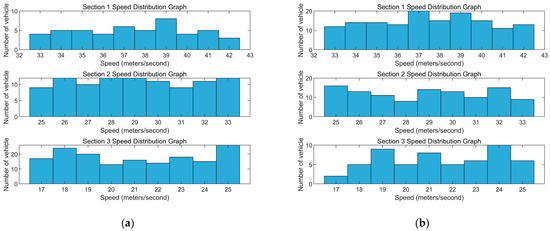
Figure 9.
Scenario 1 and 2 Speed Distribution Graph. (a) Scenario 1 and (b) scenario 2.
According to Figure 9b, it can be observed that the difference between scenarios 1 and 2 lies in the varying arrival rates, which in turn lead to different numbers of vehicles. However, there is not much impact on the average values of different vehicle speeds or the average passage times. the average speed in different speed ranges is . The average passage time in different speed ranges is .
The specific data in Figure 10a are as follows: , . Figure 10a shows that due to the low number of vehicles in the higher priority segment (Priority 1) and the smaller collision probability P at the stations, the vehicles in the higher speed range can send data packets with little waiting time and have shorter processing times compared to other speed ranges. This finding aligns with the real-world scenario. On the other hand, for the medium and lower speed ranges corresponding to Priority 2 and 3, the delay increases. Vehicles in the lower speed range need to wait for some time before sending data packets. This matches the initial design intention of this study.
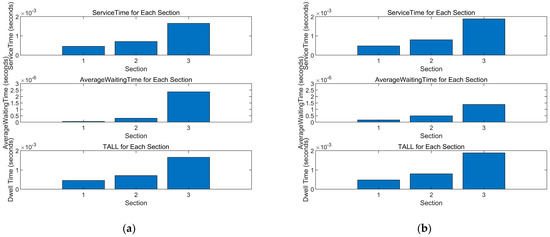
Figure 10.
Scenario 1 and 2 Delay Maps of Vehicles in Different Speed Ranges. (a) Scenario 1 and (b) scenario 2.
The specific data in Figure 10b are as follows: . Comparing scenario 1, it can be observed that due to the increased arrival rate in the higher speed range, there is an increase in the number of vehicles and thus, an increase in the number of sent data packets. As a result, the average service time, average waiting time, and total delay for Priority 1 also increase compared to scenario 1. Additionally, the medium and lower speed ranges also experience an increase in delay due to the need to avoid the data packets from the higher speed range. This observation aligns with the requirements of this study.
The specific data in Figure 11a are as follows: . The vehicles in speed range 3, which represents the slowest speed, have a longer travel time within the UAV coverage area. However, due to their longer transmission or queuing time, the time interval between sending BSMs for these vehicles is longer compared to other speed ranges, and it shows an increasing trend.
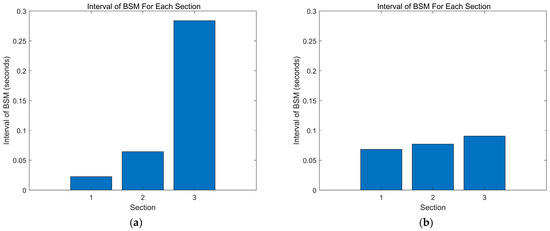
Figure 11.
Scenario 1 and 2 Interval of BSM For Each Section. (a) Scenario 1 and (b) scenario 2.
The specific data in Figure 11b are as follows: . Compared with scenario 1, it can be observed that due to the increased number of vehicles and thus, an increase in the number of high-priority data packets in the higher speed range, the time interval between sending BSMs increases in scenario 2. This is reasonable since more vehicles result in more data packets, which increases collision probability and thus, increases service and waiting times in the queue, leading to longer time intervals between packet transmissions.
However, as shown in Figure 11a,b, for the medium and lower speed ranges, the delay time in the queue does not decrease but increases when the arrival rate and the number of vehicles and data packets decrease compared to scenario 1. Additionally, due to the reduced number of vehicles, there are fewer BSM data packets, resulting in similar time intervals between packet transmissions for Priority 2 compared to scenario 1 (as the arrival rate for Priority 2 remains unchanged), and shorter time intervals for Priority 3 but still higher than those for Priorities 1 and 2.
Figure 12a,b demonstrates the practicality of the preemptive priority assignment scheme and MAC layer protocol design adopted in this paper by comparing preemptive and commonly used non-preemptive priority assignment schemes. Compared to non-preemptive schemes, preemptive schemes are more effective in managing and scheduling tasks in highly competitive resource environments, improving system responsiveness and throughput. By assigning different priorities to tasks, preemptive schemes can ensure that high-priority tasks are executed in a timely manner, thereby meeting the requirements of applications with higher real-time performance demands. Additionally, it is worth noting that based on the data, the preemptive scheme reduces latency compared to the non-preemptive high-priority scheme by 8.17% and overall system by 24.92%. In terms of frequency, the preemptive scheme is 23.55% stronger than the non-preemptive scheme. Therefore, the preemptive priority assignment scheme and MAC layer protocol design adopted in this paper are very useful and can effectively improve system performance and network transmission quality, meeting the requirements of different application scenarios.
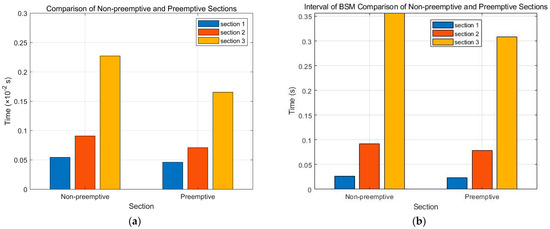
Figure 12.
Comparison of Non-preemptive and Preemptive Sections. (a) Delay and (b) interval of BSM.
As shown in Figure 13a, this study compares the preemptive priority allocation scheme employed in this paper with the priority-based MAC layer modification scheme proposed in reference [34], demonstrating the practicality of the priority allocation scheme and MAC layer protocol design utilized in this work. Compared to reference [34], our proposed scheme exhibits significant advantages in terms of overall system delay performance, achieving a 68.8% higher overall efficiency. This further validates the novelty and effectiveness of our approach. By introducing a priority allocation mechanism, our proposed scheme better meets the real-time and reliability requirements of different types of data in vehicular communication, thereby enhancing system performance and efficiency. This positions our paper as a valuable point of comparison and provides beneficial insights for research and practice in the field of vehicular networking.
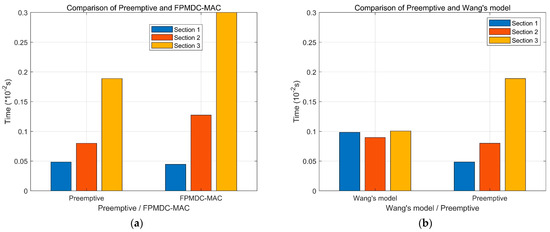
Figure 13.
Comparison of Other Models and Preemptive Models. (a) With FPMDC-MAC and (b) with Wang’s Model.
As depicted in Figure 13b, this study presents a comparison between our proposed scheme and a paper published in the Sensor journal under MDPI [35]. Both studies focus on modifying the 802.11P protocol using queuing theory and 2D Markov models. However, our proposed scheme incorporates a priority allocation mechanism, which enhances the timeliness of high-priority vehicles and significantly improves the overall system performance. Additionally, our proposed scheme better caters to the communication requirements of different vehicles, optimizing system performance and efficiency. Comparative analysis reveals that our proposed scheme outperforms the approach presented in paper [35], resulting in a 22.7% higher overall system efficiency. This further validates the novelty and practicality of our proposed scheme, offering valuable insights for research and applications within the vehicular networking domain.
This finding suggests that the priority classification in this study achieves the expected results of prioritizing higher priority vehicles, i.e., those in the higher speed range, to use limited resources, and allows for speed limiting measures to be taken for these vehicles to ensure normal UAV operation. The small change in numbers is mainly due to the limited number of data packets and vehicles and insufficient arrival rate parameters, which is in line with realistic scenarios [49,50].
- Congestion: In situations with high vehicle arrival rates, the number of vehicles on the road may exceed the road capacity, leading to congestion. This can cause traffic jams and reduce vehicle speeds. When the arrival rate approaches or exceeds the road capacity, vehicle speeds often significantly decrease.
- Traffic safety: On highways, vehicle speeds may be limited to maintain safe distances and prevent accidents. If the vehicle arrival rate increases but the road capacity cannot accommodate it, traffic management authorities may take measures to restrict vehicle speeds to ensure safety.
- Road infrastructure and design: Road structures, signs, speed limits, and other factors can affect vehicle speeds. Even if the arrival rate increases, if the road design and facilities do not support high-speed travel, vehicle speeds may still be limited.
These aspects will be further explored and addressed in subsequent research.
6. Conclusions
In this paper, we proposed an algorithm based on UAV-assisted VANETs for prioritizing data transmission and interaction between vehicles and UAVs, considering the speed of the moving vehicles. This algorithm was used to allocate limited wireless communication resources and ensure priority for the transmission of safety-critical information, such as traffic information. To achieve this, we designed an improved 802.11 CSMA/CA MAC layer access protocol equipped with an arbitrator. Additionally, we established a preemptive M/G/1 queuing theory model based on this network and calculated the data delay. By prioritizing the transmission requirements of the highest-priority moving vehicles in safety-related information transmission, we addressed the problem of minimizing total delay. We further transformed the problem of minimizing total delay within the same UAV coverage area into a problem of minimizing BSM transmission intervals. Finally, through simulation experiments, we validated the effectiveness of the proposed method in this paper. The simulation results demonstrated that under different arrival rates, this mechanism could reduce the transmission intervals for high-speed vehicles, thereby improving the efficiency of information transmission for high-speed driving vehicles and meeting the network performance requirements of safety driving applications in intelligent transportation systems.
At the time of this research, certain limitations existed in our work. First, this paper only considered the uplink transmission from vehicles to the relay portion; the downlink transmission from the relay back to the user vehicles will be investigated in future studies. Second, our research focused primarily on the V2I communication mode, but future work is needed to incorporate V2V communication for further expansion. Additionally, it is important to note that our simulation results are numerical solutions, and therefore, future studies will involve utilizing other simulation software to conduct further research and validate the practical implications of our findings. In order to further enhance our research, we plan to address these limitations and conduct a more comprehensive exploration in future studies.
Author Contributions
Conceptualization, J.L., T.H. and W.G.; Methodology, T.H.; Validation, J.L., T.H., W.G. and X.L.; Formal analysis, J.L. and T.H.; Investigation, T.H.; Writing—review and editing, J.L. and T.H.; Supervision, J.L., W.G. and X.L.; Project administration, J.L. and X.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was funded by the Beijing Municipal Education Commission (KM202310011002) and the General Program of Educational Teaching Reform Research Project at the Beijing Technology and Business University (jg225210).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Acknowledgments
We would like to thank the anonymous reviewers for their valuable and insightful comments.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Li, P.; Liu, Q.; Huang, C.H.; Wang, J.H.; Jia, X.H. Delay-bounded Minimal Cost Placement of Roadside Units in Vehicular Ad hoc Networks. In Proceedings of the IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 6589–6594. [Google Scholar]
- Padiya, P.; Vidhate, A.; Vasappanavara, R. Cluster-based combined hybrid relay vehicle selection approach for improving performance and reliability in vehicular ad hoc networks. Int. J. Commun. Netw. Distrib. Syst. 2023, 29, 532–554. [Google Scholar] [CrossRef]
- Khurana, M.; Krishna, C.R. MIMO-based Spatial Diversity Scheme in VANET Scenario. In Proceedings of the 2015 1st International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 4–5 September 2015; pp. 257–261. [Google Scholar]
- Yuan, Z.Y.; Wei, D.; Zhu, J.Q.; Hou, Y.J.; Li, M.; Sun, T. A Dynamic Multi-path Routing for VANET. In Proceedings of the International Conference on Automation, Mechanical and Electrical Engineering (AMEE), Phuket, Thailand, 26–27 July 2015; pp. 766–773. [Google Scholar]
- Seliem, H.; Ahmed, M.H.; Shahidi, R.; Shehata, M.S. Delay Analysis for Drone-Based Vehicular Ad-Hoc Networks. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017. [Google Scholar]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless Communications with Unmanned Aerial Vehicles: Opportunities and Challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Bupe, P.; Haddad, R.; Rios-Gutierrez, F. Relief and Emergency Communication Network Based on an Autonomous Decentralized UAV Clustering Network. In Proceedings of the IEEE Southeastcon, Fort Lauderdale, FL, USA, 9–12 April 2015. [Google Scholar]
- Mu’azu, A.A.; Tang, L.J.; Hasbullah, H.; Lawal, I.A.; Shah, P.A. Real-Time Massage Differentiation with Priority Data Service Flows in VANET. In Proceedings of the 2014 International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 3–5 June 2014. [Google Scholar]
- J2735_201603; Dedicated Short-Range Communications (DSRC) Message Set Dictionary. SAE International: Warrendale, PA, USA, 2016.
- Ogura, K.; Katto, J.; Takai, M. 7 BRAEVE: Stable and adaptive BSM rate control over IEEE802.11p vehicular networks. In Proceedings of the 2013 IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2013; pp. 745–748. [Google Scholar]
- Wang, Y.H.; He, Y.; Yu, F.R.; Lin, Q.Z.; Leung, V.C.M. Efficient Resource Allocation in Multi-UAV Assisted Vehicular Networks With Security Constraint and Attention Mechanism. IEEE Trans. Wirel. Commun. 2023, 22, 4802–4813. [Google Scholar] [CrossRef]
- Zhuang, K.; Xu, L.M.; Li, L.; Wang, L.; Fei, A.G. GA-MADDPG: A Demand-Aware UAV Network Adaptation Method for Joint Communication and Positioning in Emergency Scenarios. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Glasgow, UK, 26–29 March 2023. [Google Scholar]
- Andrianova, M.; Komarova, N.; Grudtsov, V.; Kuznetsov, E.; Kuznetsov, A. Amplified Detection of the Aptamer-Vanillin Complex with the Use of BSM DNA Polymerase. Sensors 2018, 18, 49. [Google Scholar] [CrossRef]
- Lu, F.Q.; Chen, X.W. Analyzing the Speed Dispersion Influence on Traffic Safety. In Proceedings of the 2009 International Conference on Measuring Technology and Mechatronics Automation, Zhangjiajie, China, 11–12 April 2009; pp. 482–485. [Google Scholar]
- Khan, M.J.; Chauhan, R.C.S.; Singh, I. Comparative Analysis of Full Duplex and Half Duplex Relay for High-Speed Vehicular Scenario. Wirel. Pers. Commun. 2022, 127, 3435–3448. [Google Scholar] [CrossRef]
- Nguyen, V.; Khoa, T.A.; Oo, T.Z.; Tran, N.H.; Hong, C.S.; Huh, E.N. Time Slot Utilization for Efficient Multi-Channel MAC Protocol in VANETs. Sensors 2018, 18, 3028. [Google Scholar] [CrossRef]
- Kumar, A.; Krishnamurthi, R.; Nayyar, A.; Luhach, A.K.; Khan, M.S.; Singh, A. A novel Software-Defined Drone Network (SDDN)-based collision avoidance strategies for on-road traffic monitoring and management. Veh. Commun. 2021, 28, 100313. [Google Scholar] [CrossRef]
- Feng, Q.X.; Tameh, E.K.; Nix, A.R.; McGeehan, J. Modelling the Likelihood of Line-of-Sight for Air-to-Ground Radio Propagation in Urban Environments. In Proceedings of the Global Telecommunications Conference, San Francisco, CA, USA, 27 November–1 December 2006. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Drone Small Cells in the Clouds: Design, Deployment and Performance Analysis. In Proceedings of the IEEE Global Communications Conference, San Diego, CA, USA, 6–10 December 2015. [Google Scholar]
- Oubbati, O.S.; Chaib, N.; Lakas, A.; Lorenz, P.; Rachedi, A. UAV-Assisted Supporting Services Connectivity in Urban VANETs. IEEE Trans. Veh. Technol. 2019, 68, 3944–3951. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Lakas, A.; Lagraa, N.; Yagoubi, M.B. CRUV: Connectivity-based Traffic Density Aware Routing using UAVs for VANETs. In Proceedings of the International Conference on Connected Vehicles and Expo, Shenzhen, China, 19–23 October 2015; pp. 68–73. [Google Scholar]
- Seliem, H.; Shahidi, R.; Ahmed, M.H.; Shehata, M.S. Drone-Based Highway-VANET and DAS Service. IEEE Access 2018, 6, 20125–20137. [Google Scholar] [CrossRef]
- Li, J.; Han, Y. A Traffic Service Scheme for Delay Minimization in Multi-Layer UAV Networks. IEEE Trans. Veh. Technol. 2018, 67, 5500–5504. [Google Scholar] [CrossRef]
- Bansal, G.; Kenney, J.B.; Rohrs, C.E. LIMERIC: A Linear Adaptive Message Rate Algorithm for DSRC Congestion Control. IEEE Trans. Veh. Technol. 2013, 62, 4182–4197. [Google Scholar] [CrossRef]
- Khorakhun, C.; Busche, H.; Rholing, H. Congestion control for VANETs based on power or rate adaptation. In Proceedings of the 5th International Workshop on Intelligent Transportation (WIT), Hamburg, Germany, 18–19 March 2008; pp. 33–43. [Google Scholar]
- Drigo, M.; Zhang, W.H.; Baldessari, R.; Le, L.; Festag, A.; Zorai, M. Distributed Rate Control Algorithm for VANETs (DRCV). In Proceedings of the Sixth ACM International Workshop on Vehicular Inter-Networking-VANET 2009, Beijing, China, 15–16 September 2009; pp. 119–120. [Google Scholar]
- Yoon, Y.; Kim, H. Resolving Distributed Power Control Anomaly in IEEE 802.11p WAVE. IEICE Trans. Commun. 2011, E94b, 290–292. [Google Scholar] [CrossRef]
- Huang, C.L.; Fallah, Y.P.; Sengupta, R.; Krishnan, H. Adaptive Intervehicle Communication Control for Cooperative Safety Systems. IEEE Netw. 2010, 24, 6–13. [Google Scholar] [CrossRef]
- Bianchi, G. Performance analysis, of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Chatzimisios, P.; Boucouvalas, A.C.; Vitsas, V. Packet delay analysis of IEEE 802.11 MAC protocol. Electron. Lett. 2003, 39, 1358–1359. [Google Scholar] [CrossRef]
- Shao, C.X.; Leng, S.P.; Zhang, Y.; Fu, H.R. A Multi-priority Supported P-Persistent MAC Protocol for Vehicular Ad Hoc Networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Paris, France, 1–4 April 2012; pp. 2532–2537. [Google Scholar]
- Ergen, M.; Varaiya, P. Throughput analysis and admission control for IEEE 802.11a. Mob. Netw. Appl. 2005, 10, 705–716. [Google Scholar] [CrossRef]
- Park, C.G.; Han, D.H.; Ahn, S.J. Performance analysis of MAC layer protocols in the IEEE 802.11 wireless LAN. Telecommun. Syst. 2006, 33, 233–253. [Google Scholar] [CrossRef]
- Manoj, M.; Sudhir, A.C. Fuzzy Based Prioritized Message Dissemination and Cooperative MAC Protocol for VANET. Wirel. Pers. Commun. 2023, 133, 1175–1198. [Google Scholar] [CrossRef]
- Wang, Y.; Shi, J.H.; Fang, Z.Y.; Chen, L.Y. A Novel Analytical Model for the IEEE 802.11p/bd Medium Access Control, with Consideration of the Capture Effect in the Internet of Vehicles. Sensors 2023, 23, 9589. [Google Scholar] [CrossRef]
- Yang, X.; Mao, Y.Q.; Xu, Q.; Wang, L. Priority-Based Hybrid MAC Protocol for VANET with UAV-Enabled Roadside Units. Wirel. Commun. Mob. Comput. 2022, 2022, 8697248. [Google Scholar] [CrossRef]
- Linn, N.N.; Liu, K.; Gao, Q. A Contention-Free Cooperative MAC Protocol for Eliminating Heterogenous Collisions in Vehicular Ad Hoc Networks. Sensors 2023, 23, 1033. [Google Scholar] [CrossRef] [PubMed]
- Yang, F.; Sun, Y.L.; Zou, S.; Luo, X.B. Repetition-Based Cooperative Broadcasting for Vehicular Ad Hoc Networks Under the Rayleigh Fading Channel. Appl. Sci. 2020, 10, 212. [Google Scholar] [CrossRef]
- Suthaputchakun, C.; Ganz, A. Priority based inter-vehicle communication in vehicular ad-hoc networks using IEEE 802.11e. In Proceedings of the IEEE 65th Vehicular Technology Conference, Dublin, Ireland, 22–25 April 2007; pp. 2595–2599. [Google Scholar]
- Ghorai, C.; Banerjee, I. A Novel Priority Based Exigent Data Diffusion Approach for Urban VANETs. In Proceedings of the 18th International Conference on Distributed Computing and Networking (ICDCN), Hyderabad, India, 5–7 January 2017. [Google Scholar]
- Mukhopadhyay, A.; Limitha, B.S.; Anusha, R.; Gowthami, V. TCP and Priority Queue based Emergency Data Transmission in VANETs. In Proceedings of the 2022 IEEE 3rd Global Conference for Advancement in Technology (GCAT), Bangalore, India, 7–9 October 2022; pp. 1–6. [Google Scholar]
- Qi, W.J.; Song, Q.Y.; Guo, L.; Jamalipour, A. Energy-Efficient Resource Allocation for UAV-Assisted Vehicular Networks with Spectrum Sharing. IEEE Trans. Veh. Technol. 2022, 71, 7691–7702. [Google Scholar] [CrossRef]
- Khabbaz, M.; Antoun, J.; Assi, C. Modeling and Performance Analysis of UAV-Assisted Vehicular Networks. IEEE Trans. Veh. Technol. 2019, 68, 8384–8396. [Google Scholar] [CrossRef]
- Prasad, H.; Li, Z.; Ben-Akiva, M. Analyzing time headway data for car-following behavior using mixture-of-exponentials distributions. Transp. Res. Part B Methodol. 2011, 45, 529–540. [Google Scholar]
- Khabbaz, M.J.; Fawaz, W.F.; Assi, C.M. Modeling and Delay Analysis of Intermittently Connected Roadside Communication Networks. IEEE Trans. Veh. Technol. 2012, 61, 2698–2706. [Google Scholar] [CrossRef]
- Adan, I.; Resing, J. Queueing Systems; Eindhoven University of Technology: Eindhoven, The Netherlands, 2015. [Google Scholar]
- Shi, G.; Fang, H.; Qu, J.; Zeng, L. Packet queueing delay in resilient packet ring network nodes. Tsinghua Sci. Technol. 2004, 9, 406–409. [Google Scholar]
- Xu, C.C.; Liu, K.Z.; Liu, G.; He, J.H. Accurate Queuing Analysis of IEEE 802.11 MAC Layer. In Proceedings of the IEEE GLOBECOM 2008-2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008. [Google Scholar]
- Jin, D.; Shi, F.; Song, J. A Traffic Flow Theory based Density Adopted Emergency Message Dissemination Scheme for Vehicular Ad Hoc Networks. In Proceedings of the 2015 International Conference on Information Networking (ICOIN), Siem Reap, Cambodia, 12–14 January 2015; pp. 57–62. [Google Scholar]
- Kononov, J.; Durso, C.; Reeves, D.; Allery, B.K. Relationship Between Traffic Density, Speed, and Safety and Its Implications for Setting Variable Speed Limits on Freeways. Transport. Res. Rec. 2012, 2280, 1–9. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).