Abstract
Around a third of the world’s surface area is covered with forests. This is about 4–5 billion hectares of land. We are losing an additional 3 million hectares of forest cover each year than we did in 2001. Hence, researchers worldwide have been working on the identification and prevention of forest fires more aggressively. The wireless sensor network technology for forest fire detection was established as a result of the shortcomings of standard forest fire detection techniques in real time. This paper proposes an energy-aware Internet of Things (IoT) based Wireless Sensor Network (WSN) model with an efficient clustering and routing technique for forest fire detection. The proposed model is named Energy Efficient Routing Protocol (EERP). The model decreases the energy utilization in sensor nodes by minimizing idle listening in cluster heads. EERP also minimizes the transmission of redundant data by allowing only the sensor nodes close to an event to report the event. Furthermore, the model ensures that sensor nodes with low energy levels do not become cluster heads. EERP uses multi-hop routes to send data from source nodes to the Base Station. The performance of EERP is compared with that of some existing Medium Access Control (MAC) protocols in various scenarios. The simulation results prove that the proposed model reduces energy consumption in sensor nodes significantly.
1. Introduction
A wireless sensor network (WSN) is a network of wireless sensor devices that work in a coordinated way and communicate their readings to a base station. Each device is powered by a battery with a limited energy supply [1]. Furthermore, these devices have low computation power, and limited sensing and transmission range. The energy stored in the battery of a node determines the lifespan of the node. The stored energy is used for various node operations such as sensing, processing, and communication. The batteries in sensor nodes are small and usually cannot be replaced or recharged. There are various energy harvesting methods, but they cannot eliminate the need for energy management. Hence, the most challenging job is the organization of the limited battery power by using energy-efficient hardware and software protocols for WSNs [2]. Some of the popular applications of WSNs are surveillance in the military, remote patient monitoring in healthcare, measurement of environmental temperature, humidity, and air pressure, crop monitoring in agriculture, monitoring machines in industries, etc. [3]. The following are the design challenges in WSNs: energy conservation, scalability, localization, security, routing, etc. As sensor nodes are standalone devices that completely depend on their batteries to carry out all activities, many researchers have been working on energy-efficient clustering and routing techniques to reduce energy consumption in sensor nodes. In the work proposed in [4], the authors assessed each node’s centrality, energy surplus, and temperature to choose the best cluster head. In [5], the authors proposed a priority-based energy-efficient routing protocol for low-power and lossy networks.
The Internet of Things (IoT) is largely dependent on WSNs. Sensors continuously monitor the environment in IoT-based WSNs and alert the base station (BS) immediately if any event is detected. An IoT-based WSN also has a gateway to upload the collected data in IoT Cloud. The BS itself can work as the gateway in some deployments. The data stored in the IoT Cloud can be remotely accessed by users whenever they want. Some of the implementations of IoT-based WSNs are water quality monitoring [6], air pollution monitoring [7,8,9], smart agriculture [10,11], health and environments [12,13], smart irrigation [14], smart cities and smart buildings [15,16,17,18], smart wearables [19,20], etc.
Forests are one of the most significant and necessary resources on our earth. They purify the air we breathe and the water we drink, avoid corrosion and maintain the balance on earth. However, our forests are rapidly disappearing because of the forest fires caused by man as well as nature. Forest fires affect the safety of human habitation and destroy natural resources [21]. In 1971, a forest fire in Kure, Wester Honshu, Japan, destroyed 340 hectares of forest land. By the middle of 1997, the smoke and haze from forest fires in Indonesia had spread to neighbouring countries such as Malaysia and Singapore. In 1987, the black dragon fire started in China, and 18 million acres of land were affected. Bandipur National Park in India’s Karnataka state experienced widespread forest fires in February 2019. The intensity of a forest fire depends on the number of trees in the proximity, and thirsty wood and leaf litter that serve as fuel for the fire. These components are explosive and produce the perfect condition for starting the fire [22].
Recently, researchers have proposed many energy-aware WSN models to detect forest fires. In E-RARP proposed in [23], sensor nodes are randomly deployed in the forest. High residual energy sensor nodes are elected as Cluster Heads (CH). Each CH uses Time Division Multiple Access (TDMA) techniques to collect the data from its members and send them to the Base Station (BS). In FLS [24], the authors used temperature, smoke, light, humidity, and distance as inputs to their fire detection system. The objective of the model proposed in [25] is to determine the behaviour of the fire. The WSN model is used to measure the weather conditions around an active fire. In FireWxNet [26], the authors discussed the important aspects of modelling forest fires based on the FireWeather Index (FWI) System. The model proposed in the work uses a WSN for the early detection of forest fires. In the work proposed in [27], the authors used mixed learning techniques and Unmanned Aerial Vehicles (UAV) to detect forest fires early.
The clustering and/or routing techniques used in many recent forest fire detection models are not very energy-efficient. Many fire detection models do not use any clustering technique for data collection. Moreover, many of them do not use multi-hop paths for sending data packets to the sink node. The proposed model uses an energy-efficient clustering and routing technique for collecting data and sending them to the BS. The main contributions of the paper are highlighted below.
- This paper discusses a TDMA-based MAC protocol named Energy Efficient Routing Protocol (EERP) that uses energy-efficient clustering and routing algorithms. EERP employs a novel CH selection mechanism to ensure that all CHs are uniformly distributed in the network. To communicate with the CHs in the network, the BS creates multi-hop paths. So, the CHs do not have to communicate with the BS using high-power signals (long-range transmissions) that are energy exhaustive. To ensure that the load is distributed evenly across all the nodes in the network, an efficient CH rotation mechanism is also used.
- EERP considers three important parameters to do its job - Distance to the Event (DE), Threshold Energy (TE), and Verification Period (VP). The DE (predefined value in meters) ensures that only the nodes in the proximity of an event report it. The sensor nodes located more than DE meters away from the event do not report the event to their CHs. The TE value ensures that sensor nodes with low energy levels do not become CHs. The VP is a small time duration in each slot in which a CH checks the medium for any signal from the slot owner. The VP contributes to reducing idle listening in CHs.
- The proposed model assumes that the target area (forest area) is composed of small sub-areas or grids. In each grid, one CH is appointed to collect data from the rest of the nodes in the grid. These data are sent to the BS via one of the multi-hop routes established during the cluster formation phase. As WSNs are usually deployed to monitor very large forest areas, single-hop transmissions to the BS can be very costly.
- In the result section, the performance of EERP is compared with that of some existing energy-efficient TDMA-based MAC protocols. The simulation results prove that the proposed model performs better in reducing the energy consumption in sensor nodes and extending the lifetime of WSNs.
The remaining sections of the article are arranged as follows. Section 2 discusses some generic purpose WSN models, designed to extend the lifetime of WSNs. This section also discusses some recently proposed models, designed specifically for forest fire detection. Section 3 describes the working of the proposed model in detail. Section 4 compares the performance of the proposed model with that of some existing TDMA-based MAC protocols in different scenarios. In Section 5, we do a comprehensive comparative analysis of all the protocols simulated in Section 4. Section 6 concludes the paper and highlights the modifications that can be done to enhance the performance of the model.
2. Related Work
In this section, we first discuss some basic WSN models, designed to maximize the lifetime of WSNs. Next, we discuss some recently proposed WSN models, designed specifically to detect forest fires.
LEACH [28] is a self-organizing, adaptable clustering protocol for WSNs that uses a cluster head rotation technique to distribute energy load uniformly among the network’s sensors. Sensor nodes in the target area form groups called clusters, with one node performing as the cluster head of the cluster. LEACH incorporates a random CH rotation scheme, spreading the load across multiple sensors rather than continuously draining the power from a single sensor. An elected CH broadcasts an advertisement packet to inform the neighbouring non-CH nodes about its selection. A non-CH node sends a join request message to the CH from which the strongest advertisement signal was received. After cluster formation, the CH broadcasts a transmission schedule in its cluster to allocate each cluster member one data slot in a frame. A cluster member can transmit only in its own slot. It keeps its radio OFF in the other slots. The CH collects data from all the cluster members and sends an aggregate packet to the BS directly.
The following protocols are the successors of LEACH that made modifications to LEACH. LEACH- C [29] is a clustering protocol in which the BS takes all the following decisions– selection of CHs, formation of clusters, and dissemination of data across the network. The first protocol that uses the SPINS protocol [30] to add security features to LEACH is SLEACH [31]. This protocol employs simple cryptographic methods for WSNs. Q-LEACH [32] is a quadrant-based routing protocol that combines the characteristics of the LEACH protocol and the Q-DIR [33] routing algorithms. LEACH-B [34] uses an innovative technique for the formation of clusters and the selection of CHs in the network. By allowing the CHs to interact with the BS via multi-hop routes, multi-hop LEACH [35] increases the network performance in terms of energy conservation.
In MG-LEACH [36], nodes are divided into groups based on their locations, and the number of groups depends on the density of the nodes. The BS creates these groups during the deployment of the nodes. This step is an additional step called the Set Building Phase. The other two phases called Setup Phase and Steady State Phase are similar to LEACH. In BEE-MAC [37], the cluster formation process is also the same as in LEACH. Each CH broadcasts a TDMA plan during the announcement phase to allocate control slots to its members. A source node broadcasts a control packet in its control slot to claim one or more data slots. To know which data slots are available, a source node keeps its radio ON continuously from the beginning of the control period till its control slot.
In ES-MAC [38], the cluster formation process is the same as in LEACH. ES-MAC introduces a small time duration called the Verification Period (VP) at the beginning of each slot. In this time duration, a CH checks the medium for any signal from the slot owner. If the CH does not receive any signal from the slot owner during this period, it turns its radio OFF till the beginning of the next slot. The VP ensures that idle listening in CHs is minimized. EE-MAC [39] uses four important parameters to minimize unnecessary energy consumption in sensor nodes and distribute the overall load uniformly among them. The Residual Energy (RE) of each node is compared with a TE value to decide if the node can participate in the CH selection process. A predefined value called the Proximity Threshold (PT) ensures that CHs are not located too close to each other in the network. Another parameter called the Maximum Cluster Size (MCS) puts a limit on the maximum size of clusters in the network. EE-MAC also uses the VP like ES-MAC to reduce idle listening in CHs.
LEC-MAC [40] uses five parameters to do its job. A PT value is used to distribute CHs in the network uniformly. The PT value ensures that no region in the target area is crowded with CHs. An MCS value is used to prevent clusters from growing too big. A TE value is used to ensure that low-energy nodes do not become CHs. If the RE of a node is less than the TE, it is not allowed to participate in the CH selection process. A DE value is used to minimize the transmission of redundant data. Sensor nodes located more than DE meters away from the event are not allowed to report the event. A VP is also used, such as ES-MAC and EE-MAC, to reduce idle listening in CHs.
Recently, many researchers have developed very efficient WSN models for forest fire detection. In the work discussed in [41], the authors proposed a system called the Forest Fires Surveillance System (FFSS) to monitor forest fires. This system includes a WSN, a middleware, and a web application. Each node in the WSN is equipped with a thermometer, a humidity sensor, and a smoke detector. The middleware receives the data from the gateway and processes them. The web application provides a GUI to view the information. The WSN architecture discussed in [22], consists of sensor nodes, a router (gateway), and a monitoring host/phone. The sensor nodes collect information on environmental parameters such as humidity, air temperature, atmospheric pressure, wind speed, wind direction, etc. The data are sent to the CH of the cluster. The CH aggregates the data collected from all the sensor nodes and sends it to the Network Coordinator. The network coordinator sends the data to the gateway. The gateway forwards the data to the monitoring host.
In [42], the authors demonstrated how a wireless sensor network can be used to keep track of forest fires. The design uses MICA motes that have GPS devices attached to them. The objective here is to measure the temperature, relative humidity, and barometric pressure in the vicinity of the fire. In [43], the authors used the Sliding Window Skylines technique in sensor networks to detect forest fires. Basically, the authors worked on how to avoid unnecessary communication by using a novel data suppression method. The work in [44] used a Location Aided Routing approach to detect forest fires. The novel routing algorithm considers three factors: length of the route between nodes, temperature recorded, and count of packets in node buffers. EEFFL proposed in [45] divides the forest area into three zones: High Active Zone, Medium Active Zone, and Low Active Zone. The model uses a greedy forwarding approach to send data to the BS. Sensors in the high active zone send data to the BS continuously. Sensors in the medium active zone send data to the BS periodically. Sensors from the low active zone avoid transmitting data to the BS.
In [46], the authors proposed a hierarchical routing algorithm for fog-enabled sensor networks. The ordinary sensor nodes and the CHs work only to forward the data packets. The routing decisions are taken solely by the fog nodes as they are more powerful in terms of storage, processing, and computation. In the work discussed in [47], the authors proposed a comprehensive framework for the early detection of forest fires, taking into consideration the energy consumption in sensor nodes. The framework modifies the strategies of sensor deployment, clustering, and routing, to respond to forest fires quickly.
Table 1 compares the WSN models discussed above based on some parameters. The parameter ‘Cluster Formation’ denotes whether the model supports cluster formation. The parameter ‘Slot Allocation’ denotes whether sensor nodes select slots for themselves or slots are allocated by the CH. The parameter ‘Communication Technique’ denotes whether the communications are single-hop or multi-hop. The parameter ‘Energy Consumption’ represents the average energy consumption in sensor nodes based on factors such as cluster formation, communication techniques, and the number of control packets exchanged. The parameter ‘Application’ represents the application area of the proposed WSN model.

Table 1.
Comparison table.
3. Proposed Model
In the proposed model, the target area (forest area) is assumed to be divided into n equal-sized grids. All the sensor nodes are homogeneous and equipped with temperature sensors and global positioning systems (GPS). The sensor nodes are randomly deployed in the target area. Each node is capable of transmitting directly to the BS by varying its transmission power. The BS is located outside of the target area and is fully aware of the dimensions of the grids. The sensor nodes send data packets to the BS periodically. The BS sends the data collected from the sensor nodes to an IoT cloud. The data can be accessed by the registered Fire Stations. If an event (fire breakout) is detected, it is immediately reported by the sensor nodes to the BS. In this case, the data are immediately sent to the IoT Cloud, and thereafter, to the local fire station.
The proposed model is divided into two phases: (i) Setup and (ii) Steady-State. During the setup phase, the BS selects CHs and establishes multi-hop communication paths with them. During the steady-state phase, the data collected by the sensor nodes are sent to the IoT Cloud.
3.1. Setup Phase
At the beginning of the setup phase, each sensor node sends an information message (SNinf) to the BS. This message SNinf consists of SNid, SNre, and SNgn, where SNid represents the sensor node ID, SNre represents the residual energy of the node, and SNgn represents the grid number of the node. The BS compares the residual energy of each sensor node with a predefined threshold called Threshold Energy (TE). If the residual energy in a node is greater than the TE, it is eligible to participate in the CH selection procedure. If a node’s residual energy is less than the TE, it cannot participate in the CH selection process. The BS chooses the node with the highest residual energy as the CH among all the eligible nodes in a grid. The BS then broadcasts a message BSsel to inform all sensor nodes about the newly selected CHs. The message contains SNid and SNgn of each selected CH. Here, SNid represents the ID of the appointed CH and SNgn represents the grid number of the CH.
Each ordinary node sends a join request (JOIN_REQ) message to its CH. An ordinary node identifies its CH from the grid number of the CH, which matches the grid number of the node. Each JOIN-REQ message consists of SNid and SNgn of the requesting node. A CH accepts all the requesting nodes as its members. After a time-out period, the BS broadcasts a message (BSfrm) to inform all the nodes in the target area about the frame size and structure. The BS then broadcasts a schedule (BSsch) for the selected CHs. For each pair of sending and receiving devices, this message contains SNid of the sending CH, SNid of the receiving CH (or BSid of the BS), and SNslot which denotes the slot number in which the sender can send data to the receiver. Next, each CH broadcasts the intra-cluster schedule (CHsch) in its cluster. The message contains SNid and SNslot for each cluster member, where SNid represents the ID of the cluster member and SNslot represents the slot allocated to the member in the frame.
A sample network architecture is presented in Figure 1. The target area is split into nine grids (clusters). Each cluster consists of four or five nodes. The CHs are represented by sensor nodes inside red rectangular boxes. The clusters are numbered 1 through 9 from left to right then top to bottom. The first cluster consists of five nodes numbered 1 through 5, and node 3 is the CH. The second cluster consists of four nodes numbered 6 through 9, and node 9 is the CH. Similarly, every other cluster contains some sensor nodes, one of which is appointed as the CH.
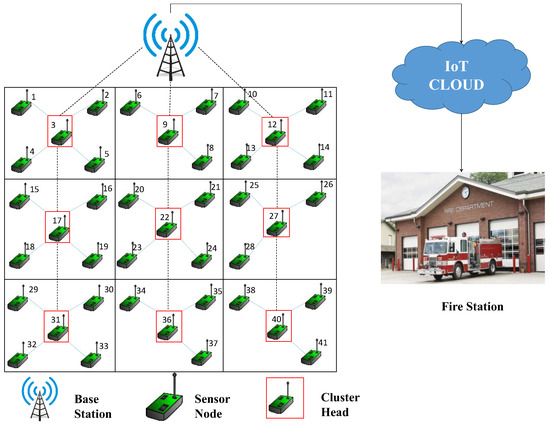
Figure 1.
The network architecture in the Proposed Model.
A frame is divided into two parts, namely intra-cluster communication period and inter-cluster communication period. In the intra-cluster communication period, sensor nodes send data to their CHs in the allocated time slots. In the inter-cluster communication period, a CH sends data to its upstream CH or the BS. The frame size is determined by the BS. A sample frame structure is shown in Figure 2. The frame structure is related to the network presented in Figure 1. The number of ordinary nodes in the largest cluster determines the number of slots in the intra-cluster communication period. The number of slots in the inter-cluster communication period depends on the number of clusters in a column and the number of clusters in a row in the network architecture. In the frame shown in Figure 2, there are four slots in the intra-cluster communication period and five slots in the inter-cluster communication period.
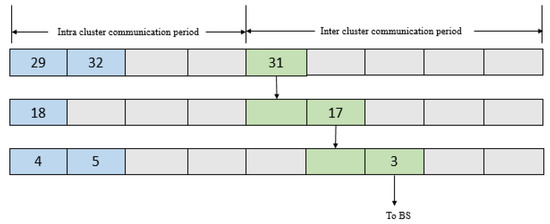
Figure 2.
Intra-cluster and Inter-cluster communication periods in a frame.
To depict the multi-hop data transmission, we consider a scenario where data are transmitted from CH-31 to the BS via CH-17 and CH-3. It can be seen in Figure 2 that the ordinary sensor nodes SN-29 and SN-32 in cluster 7 (CL-7) transmit their data to CH-31 in the first slot and second slot respectively in the intra-cluster communication period. The other two slots (coloured grey) in the intra-cluster communication are left unused. Similarly, SN-18 in CL-4 sends data to CH-17 in the first slot of the intra-cluster communication period (three unused slots shown in grey). Furthermore, SN-4 and SN-5 in CL-1 send data to CH-3 in the first slot and second slot respectively in the intra-cluster communication period (two unused slots shown in grey). The data collected by CH-31 are sent to CH-17 in the first slot of the inter-cluster communication period. The data collected by CH-17 are sent to CH-3 in the second slot of the inter-cluster communication period. The data collected by CH-3 are eventually sent to the BS in the third slot of the inter-cluster communication period. The fourth and fifth slots (shown in grey) are used by CH-9 and CH-12 respectively to send data to the BS. These slots are not unused, but they have been shown in grey as they are not used in the multi-hop transmission from CH-31 to the BS. Figure 3 shows the flowchart of the setup phase of the proposed model and Algorithm 1 shows the steps in the setup phase of the proposed model.
| Algorithm 1: Pseudo-code for Setup-phase |
| 1: Input: Sensor nodes deployed in target area 2: Output: Formation of clusters in target area 3: N= number of CHs/grids 4: n= number of cluster nodes 5: m= number of nodes in the target area 6: i = 0, j = 0, k = 0, l = 0, c = 0 7: for i = 1 to m 8: each node sends INF message to BS 9: end for 10: for i = 1 to N 11: for j = 1 to n 12: if (RE > UT) 13: node can participate in CH selection procedure 14: c = c + 1 15: else 16: node will become an ordinary node 17: end if 18: end for 19: end for 20: for i = 1 to N 21: for k = 1 to c 22: if (RE = max(RE)) 23: node appointed as CH 24: else 25: node will become ordinary node 26: end if 27: end for 28: end for 29: for i = 1 to m 30: each node receives CH selection message from BS 31: end for 32: for i = 1 to n−1 33: each ordinary node sends JOIN_REQ message to its CH 34: end for 35: for i = 1 to m 36: each node receives frame information message from BS 37: end for 38: for i = 1 to m 39: each node receives schedule message from BS 40: end for 41: for i = 1 to n−11 42: each ordinary node receives schedule message from its CH 43: end for |
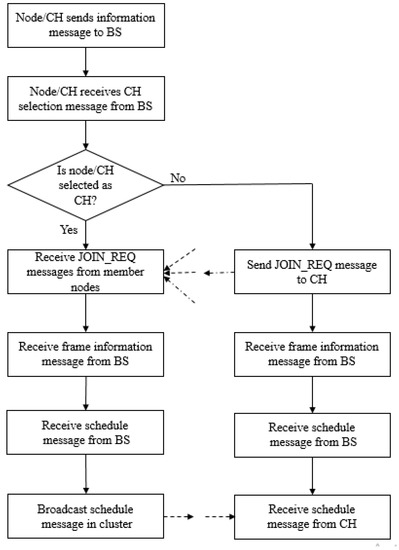
Figure 3.
Setup Phase in Proposed Model.
3.2. Steady-State Phase
The Steady-State phase consists of multiple frames, each of which is divided into a number of slots. Each slot is allocated to one member node in the cluster. A member can send data only in its own slot. It keeps its radio OFF in all other slots in a frame. At the start of each slot, a CH turns its radio ON for a very short duration called the Verification Period (VP). If the CH does not hear from the slot owner (member node that owns the slot) during the VP, it turns its radio OFF immediately after the VP. If the CH hears from the slot owner during the VP, it keeps its radio ON for the entire duration of the slot. The VP aids in reducing idle listening in CHs. The proposed model uses another parameter called Distance-to-Event (DE) which aids in reducing the transmission of redundant data. The DE (predefined in meters) ensures that only nodes in the proximity of an event report it to their CHs. If a node is more than DE metres away from the event, it will not report the event to its CH. Figure 4 shows how verification periods are arranged in a frame. Figure 5 shows the flowchart of the steady-state phase in the proposed model.
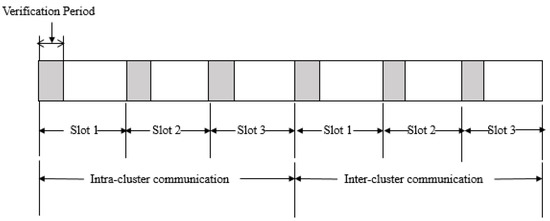
Figure 4.
Verification Periods in a Frame.
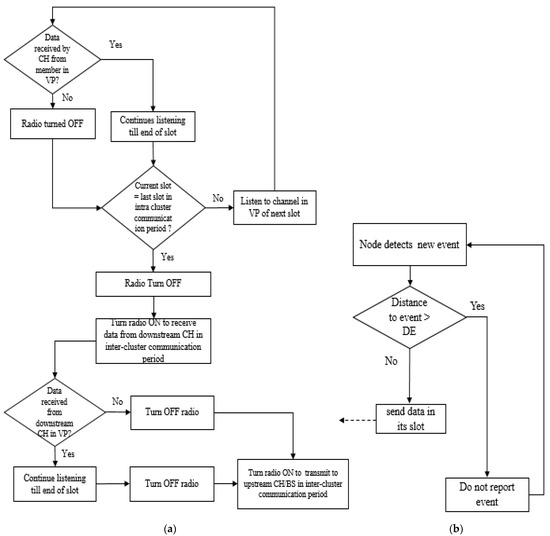
Figure 5.
Steady-State Phase in Proposed Model: (a) Functioning of CH and (b) Functioning of member node.
After gathering information from the source nodes, the CH forwards the aggregated data to its upstream CH or the BS (if the CH belongs to one of the clusters in the first row in the network architecture). After a predefined number of frames, the next round begins. In the setup phase of the first round, all sensor nodes send information messages (SNinf) to the BS. However, in the setup phase of all other rounds, CHs send information messages (CHinf) to the BS. This CHinf message contains the following information for all the members in the cluster (including the CH itself) - SNid and SNre. Based on this information, the BS can decide whether the current CH can continue to function as the CH of the cluster or whether a new node should be appointed as the CH. A new node is appointed as the CH when the residual energy of the current CH is less than the threshold energy. As member nodes are not directly involved in sending information messages, a significant amount of energy is saved in the setup phase of all other rounds.
Algorithm 2 shows the steps in the steady-state phase of the proposed model. Figure 6 shows the functioning of the BS in a complete round. Figure 7 represents a scenario to show the real-time application of the proposed model. In the given scenario, a fire breakout is detected by SN-41 in CL-9. The node sends the information to CH-40, and CH-40 communicates the message to the BS via CH-27 and CH-12. The BS sends the information to the IoT Cloud, which is then immediately sent to the local fire station. The path of data transmission is shown in a red dotted line from CH-40 to the BS and a red solid line from the BS to the local fire station.
| Algorithm 2: Pseudo-Code for Steady-State Phase |
| 1: Input: Clusters formed in Setup Phase 2: Output: Data Transmission to the IoT Cloud 3: N = total number of clusters 4: n = total nodes in a cluster 5: i = 0, j = 0, s = no of slots 6: Node detects a new event 7: If (distance to event > DE) 8: do not report the event 9: else 10: report event in its slot 11: end if 12: for i = 1 to s 13: if (CH receives data from its member in VP) 14: continue listening till the end of the slot 15: else 16: turn radio OFF 17: end if 18: end for 19: for i = 1 to s 20: if (Current slot = last time slot for intra-cluster communication) 21: wait to receive data from downstream CH in the inter-cluster communication period 22: else 23: listen to channel in VP of next slot 24: end if 25: end for 26: if (Data is received from downstream CH in VP) 27: Continue listening till the end of the slot 28: else 29: Turn off radio 30: end for 31: for i = 1 to N 32: CH sends aggregate data to its upstream CH /BS 33: end for |
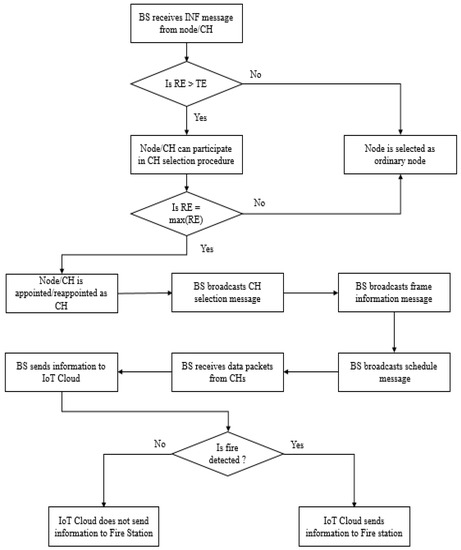
Figure 6.
Functioning of the BS in a complete round.
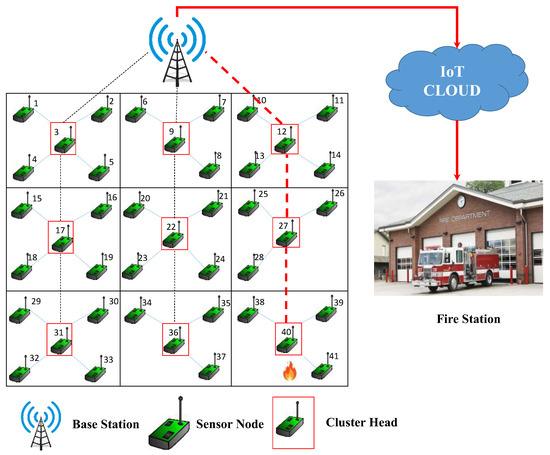
Figure 7.
Real-time application of Proposed Model.
4. Simulation Results
The python programming language is used for the simulations. As in LEACH, the simulations employ the First Order Radio Model. The parameters used in the simulations are mentioned in Table 2. Here, Elec represents the amount of power required to operate the circuitry of a transmitter or receiver. The term Eidle denotes energy spent in the idle mode. To indicate the amount of power used by the transmit amplifier, we use the symbol Eamp.

Table 2.
: Simulation Parameters.
4.1. Scenario 1
In Scenario 1, 100 sensor nodes are deployed in a 100 × 100 m2, and the number of CHs is 16. Figure 8. shows the results of the first simulation. Figure 9 represents the round numbers in which the First Node (FN) and Last Node (LN) die in each protocol.
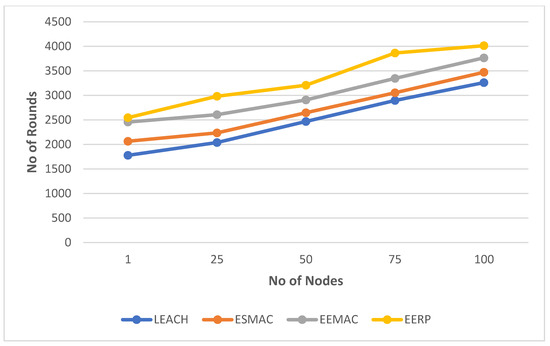
Figure 8.
Simulation results in Scenario 1.
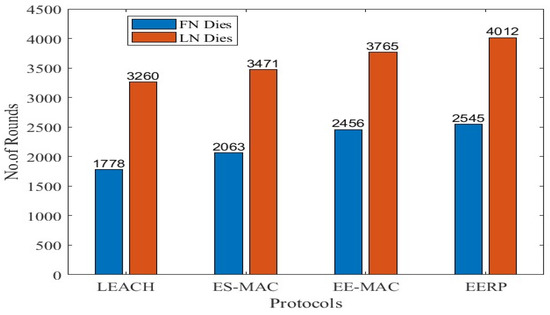
Figure 9.
FN and LN deaths in Scenario 1.
4.2. Scenario 2
In scenario 2, 200 nodes are deployed in a 100 × 100 m2 area, and the number of CHs is 16. Figure 10 displays the simulation results in the second scenario. Figure 11 represents the round numbers in which the FN and LN die in each protocol.
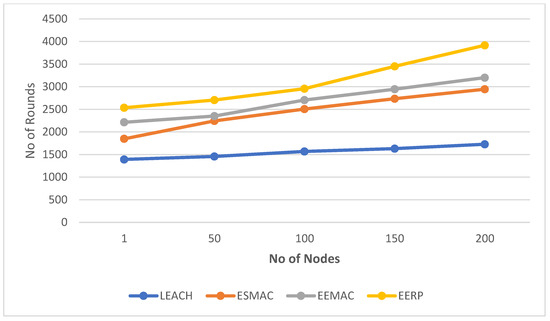
Figure 10.
Simulation result in Scenario 2.
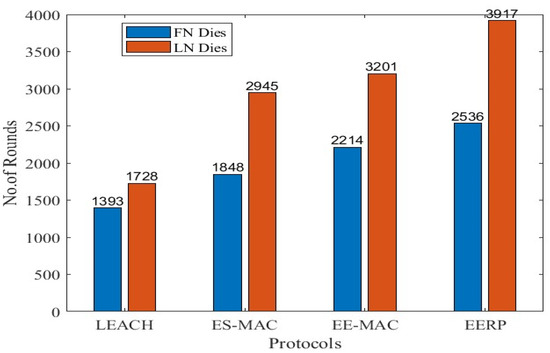
Figure 11.
FN and LN deaths in Scenario 2.
4.3. Scenario 3
The third scenario involves the deployment of 100 nodes in a 50 × 50m2 area with 16 CHs in the target area. The outcomes of the simulations can be seen in Figure 12. Figure 13 represents the round numbers in which the FN and LN die in each protocol.
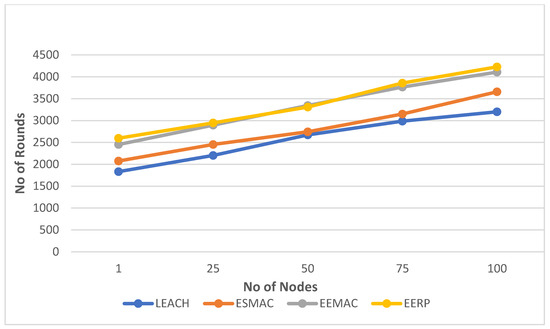
Figure 12.
Simulation result in Scenario 3.
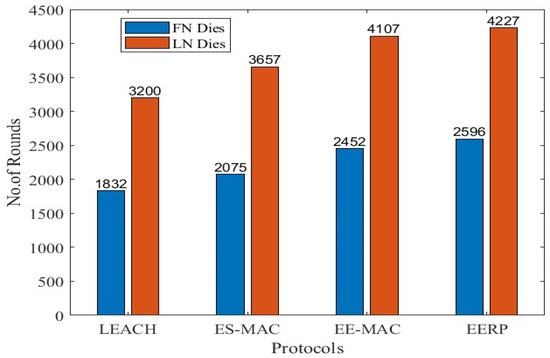
Figure 13.
FN and LN deaths in Scenario 3.
4.4. Scenario 4
In the fourth scenario, there are 200 sensor nodes in a 50 × 50 m2 target area with 16 CHs. The outcomes of the simulations can be seen in Figure 14. Figure 15 represents the round numbers in which the FN and LN die in each protocol.
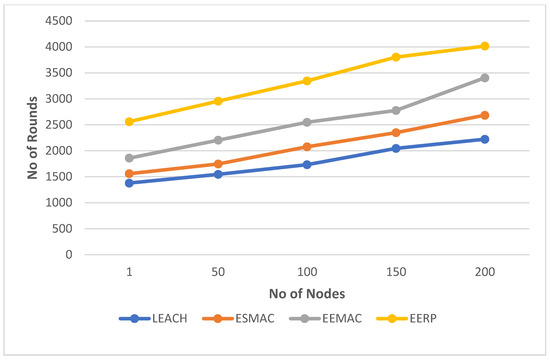
Figure 14.
Simulation result in Scenario 4.
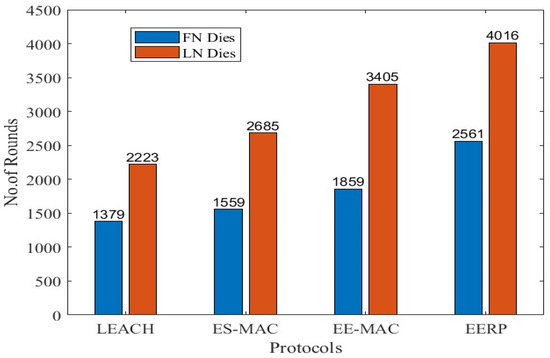
Figure 15.
FN and LN deaths in Scenario 4.
5. Comparative Analysis
This section presents the analysis of energy consumption in sensor nodes in all four protocols that were simulated. The analysis considers energy consumption due to sending/receiving control/data packets during the cluster formation process and the average energy spent in each frame of a protocol. Table 3 shows the comparison of the protocols based on their important characteristics.

Table 3.
Comparisons of Protocols.
5.1. Energy Consumption in LEACH
The amount of energy used by an ordinary sensor node is expressed by EON_LEACH and is computed as shown in Equation (1).
EON_LEACH = ERE_ADV + ESE_JOIN + ERE_SCH + ESE_DATA
The energy consumed by the node in receiving advertisement packets is denoted by ERE_ADV. The energy spent in sending a join request to the selected CH is denoted by ESE_JOIN. The term ERE_SCH denotes the energy spent in receiving the schedule from the CH. ESE_DATA represents the energy consumed by the node in transmitting data to the CH. ECH_LEACH indicates the energy consumed by a CH and is determined by using Equation (2).
ECH_LEACH = EBR_ADV + ERE_JOIN + EBR_SCH + ERE_DATA + ESE_DATA
The energy spent by the CH in broadcasting an advertisement packet is denoted by EBR_ADV. ERE_JOIN is the energy spent in receiving join-request packets from ordinary nodes. EBR_SCH represents the energy consumed by the CH in broadcasting the schedule in its cluster. ERE_DATA represents the energy consumed in receiving data from member nodes. ESE_DATA represents the energy consumed by the CH in sending data to the BS. The total energy spent in a cluster in a LEACH frame is denoted as ELEACH and is calculated using Equation (3). Here, n is the number of member nodes in the cluster.
ELEACH = n * EON_LEACH + ECH_LEACH
5.2. Energy Consumption in ES-MAC
In ES-MAC, the energy consumption in each ordinary sensor node is denoted by EON_ESMAC and is computed as shown in Equation (4). The energy spent by the CH is denoted by ECH_ESMAC and is calculated as shown in Equation (5).
EON_ESMAC = ERE_ADV + ESE_JOIN + ERE_SCH + ESE_DATA
ECH_ESMAC = EBR_ADV + ERE_JOIN + EBR_SCH + ERE_DATA + ESE_DATA
The total energy spent in a cluster in an ES-MAC frame is denoted by the symbol EESMAC, where n is the number of member nodes in the cluster.
EESMAC = n* EON_ESMAC + ECH_ESMAC
In LEACH, the CHs lose a significant amount of energy in idle listening. In ES-MAC, the Verification Period is used to reduce idle listening in CHs. Hence, ES-MAC reduces energy consumption in sensor nodes compared with LEACH.
5.3. Energy Consumption in EE-MAC
In EE-MAC, the energy consumed by an ordinary sensor node is denoted by EON_EEMAC and is computed as shown in Equation (7).
EON_EEMAC = ERE_ADV + ESE_JOIN + ERE_ACK + ERE_SCH + ESE_DATA
Here, ESE_JOIN denotes the energy spent in sending join-request messages to CHs. ERE_ACK is the energy spent by the ordinary node in receiving acknowledgement packets from CHs. ECH_EEMAC denotes the energy consumed by the CH and is calculated using Equation (8).
ECH_EEMAC = EBR_ADV + ERE_JOIN + EBR_ACK + EBR_SCH + ERE_DATA + ESE_DATA
EBR_ACK denotes the energy spent by the CH in broadcasting acknowledgement packets. The total energy spent in a cluster in an EE-MAC frame is denoted by EEEMAC and is calculated using Equation (9). Here, EAON_EEMAC denotes the energy spent by all the ordinary nodes in the cluster.
EEEMAC = EAON_EEMAC + ECH_EEMAC
EE-MAC saves more energy compared to LEACH and ES-MAC. EE-MAC uses four parameters to save energy. The RE of a node is compared with a TE value to decide if the node can participate in the CH selection process. The PT ensures that CHs are not located too close to each other in the network. The MCS puts a limit on the maximum size of clusters in the network. The VP aids in reducing idle listening in CHs.
5.4. Energy Consumption in EERP
In EERP, the energy spent by an ordinary node is represented by EON_EERP and is calculated as shown in Equation (10).
EON_EERP = ESE_INF + ERE_BS-SEL + ESE_JOIN + ERE_BS-FRM + ERE_BS-SCH + ERE_CH-SCH + ESE_DATA
Here, ESE_INF is the energy consumed in communicating the information message to the BS. ERE_BS-SEL is energy spent in receiving the CH selection message from BS. ESE_JOIN is the amount of energy spent in sending a JOIN_REQ message to its CH. ERE_BS-FRM represents the energy consumed in receiving frame information from BS. ERE_BS-SCH denotes the energy spent in receiving the inter-cluster communication schedule from BS. ERE_CH-SCH denotes the energy spent in receiving the intra-cluster communication schedule from CH. ESE_DATA denotes the energy spent in sending data to its CH. The energy consumed by the CH is denoted by ECH_EERP and is calculated by using Equation (11).
ECH_EERP = ESE_INF + ERE_BS-SEL + ERE_JOIN + ERE_BS-FRM + ERE_BS-SCH + EBR_CH-SCH + ERE_DATA + ESE_DATA
Here, EBR_CH-SCH is the energy consumed by the CH in broadcasting the schedule in its cluster. ESE_DATA is the energy spent in sending the data to its upstream CH or BS. EEERP denotes the total energy spent in the cluster in an EERP frame and is calculated by using Equation (12). Here, EAON_EERP denotes the energy spent by all the ordinary nodes in the cluster.
EEERP = EAON_EERP + ECH_EERP
The proposed model saves more energy compared to LEACH, ES-MAC, and EE-MAC. EERP considers three parameters to do its job. The TE is compared with the RE of a node to decide if it can be selected as the new CH. In the case of a CH, it is decided whether the CH can continue to function as the CH of the cluster. The DE ensures that only the nodes within the proximity of an event report the event. The VP ensures that idle listening in CHs is reduced.
6. Conclusion and Future Work
In this research, we propose an Energy Efficient Routing Protocol (EERP) which is a TDMA-based MAC protocol to extend the lifetime of IoT-based WSN systems used for forest fire detection. The model decreases the energy utilization in sensor nodes by minimizing idle listening in cluster heads. EERP also minimizes the transmission of redundant data by allowing only the sensor nodes close to an event to report the event. Furthermore, the model ensures that sensor nodes with low energy levels do not become cluster heads. EERP uses multi-hop routes to send data from source nodes to the Base Station. The performance of EERP is compared with that of some existing MAC protocols in various scenarios. The performance of the proposed model can be further enhanced by using soft computing techniques.
Author Contributions
Problem Identification, R.B.P. and K.D.; Methodology, R.B.P. and K.D.; Implementation, R.B.P.; Writing—Original Draft Preparation, R.B.P.; Writing—Review and Editing, K.D.; Supervision, K.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Acknowledgments
We thank VIT-AP University for helping us with the Article Processing Charge for publication of the article in Open Access.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Rawat, P.; Chauhan, S. Clustering protocols in wireless sensor network: A survey, classification, issues, and future directions. Comput. Sci. Rev. 2021, 40, 100396. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000; p. 10. [Google Scholar]
- Dionisis, K.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of wireless sensor networks: An up-to-date survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar]
- Ju, X. Energy-efficient routing sensing technology of wireless sensor networks based on Internet of Things. J. High Speed Netw. 2021, 27, 225–235. [Google Scholar] [CrossRef]
- Fatemeh, S.; Souri, A.; Baker, T.; al Ridhawi, I.; Aloqaily, M. PriNergy: A priority-based energy-efficient routing method for IoT systems. J. Supercomput. 2020, 76, 8609–8626. [Google Scholar]
- Zin, M.C.; Gopal, L.; Aung, Y.L. WSN-based reconfigurable water quality monitoring system in IoT environment. In Proceedings of the 2017 14th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), Phuket, Thailand, 27–30 June 2017; pp. 741–744. [Google Scholar]
- Santanu, M.; Nguyen, H.A.D.; Ha, Q.P. IoT-enabled wireless sensor networks for air pollution monitoring with extended fractional-order Kalman filtering. Sensors 2021, 21, 5313. [Google Scholar]
- Lo Sciuto, G. Air pollution effects on the intensity of received signal in 3G/4G mobile terminal. Int. J. Energy Environ. Eng. 2019, 10, 221–229. [Google Scholar] [CrossRef]
- Giacomo, C.; Sciuto, G.L.; Monforte, P.; Napoli, C. Cascade feed forward neural network-based model for air pollutants evaluation of single monitoring stations in urban areas. Int. J. Electron. Telecommun. 2015, 61, 327–332. [Google Scholar] [CrossRef]
- Khalid, H.; Din, I.U.; Almogren, A.; Islam, N. An energy efficient and secure IoT-based WSN framework: An application to smart agriculture. Sensors 2020, 20, 2081. [Google Scholar]
- Sushanth, G.; Sujatha, S. IOT based smart agriculture system. In Proceedings of the 2018 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2018; pp. 1–4. [Google Scholar]
- Maryam, S.; Sadeghi-Niaraki, A.; Choi, S.; Islam, S.M.R. Performance analysis of IoT-based health and environment WSN deployment. Sensors 2020, 20, 5923. [Google Scholar]
- Alamelu, J.V.; Mythili, A. Design of IoT based generic health care system. In Proceedings of the 2017 International Conference on Microelectronic Devices, Circuits and Systems (ICMDCS), Vellore, India, 10–12 August 2017; pp. 1–4. [Google Scholar]
- Sabrine, K.; el Houssaini, D.; Kammoun, I.; Kanoun, O. Precision irrigation: An IoT-enabled wireless sensor network for smart irrigation systems. In Women in Precision Agriculture; Springer: Cham, Switzerland, 2021; pp. 107–129. [Google Scholar]
- Rani, S.R.; Maheswar, G.R. Kanagachidambaresan; Integration of WSN and IoT for smart cities; Jayarajan, P., Ed.; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Khedr, A.M.; Osamy, W.; Ahmed, S.; Abdel-Aziz, S. Privacy preserving data mining approach for IoT based WSN in smart city. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 555–563. [Google Scholar] [CrossRef]
- Shao, X. Improved energy-efficient routing architecture for traffic management system using a hybrid meta-heuristic algorithm in Internet of vehicles. J. High Speed Netw. Prepr. 2022, 1–10. [Google Scholar] [CrossRef]
- Marek, K.; Bijok, T.; Sciuto, G.L. Design and Modeling of Intelligent Building Office and Thermal Comfort Based on Probabilistic Neural Network. SN Comput. Sci. 2022, 3, 485. [Google Scholar]
- Pedro, C.; Martinez, J.; Rodriguez-Molina, J.; Cuerva, A. Integration of wearable devices in a wireless sensor network for an E-health application. IEEE Wirel. Commun. 2013, 20, 38–49. [Google Scholar]
- Alduais, N.A.M.; Abdullah, I.; Jamil, A. An efficient data collection algorithm for wearable/mobile tracking system in IoT/WSN. In Proceedings of the 2018 Electrical Power, Electronics, Communications, Controls and Informatics Seminar (EECCIS), Batu, Indonesia, 9–11 October 2018; pp. 250–254. [Google Scholar]
- Muttashar, A.G.; Khalaf, O.I. An improved algorithm to fire detection in forest by using wireless sensor networks. Int. J. Civ. Eng. Technol. (IJCIET)-Scopus Index. 2018, 9, 369–377. [Google Scholar]
- Zhang, J.; Li, W.; Yin, Z.; Liu, S.; Guo, X. Forest fire detection system based on wireless sensor network. In Proceedings of the 2009 4th IEEE Conference on Industrial Electronics and Applications, Xi’an, China, 25–27 May 2009; pp. 520–523. [Google Scholar]
- Noureddine, M.; Nurellari, E.; El Alaoui, A.E. A novel energy-efficient and reliable ACO-based routing protocol for WSN-enabled forest fires detection. J. Ambient. Intell. Humaniz. Comput. 2022, 1–17. [Google Scholar]
- Pouya, B.; Uysal, S. Forest fire detection in wireless sensor network using fuzzy logic. In Proceedings of the 2013 Fifth International Conference on Computational Intelligence, Communication Systems and Networks, Madrid, Spain, 5–7 June 2013; pp. 83–87. [Google Scholar]
- Carl, H.; Han, R.; Seielstad, C.; Holbrook, S. FireWxNet: A multi-tiered portable wireless system for monitoring weather conditions in wildland fire environments. In Proceedings of the 4th International Conference on Mobile Systems, Applications and Services, Uppsala, Sweden, 19–22 June 2006; pp. 28–41. [Google Scholar]
- Mohamed, H.; Bagheri, M. Forest fire modeling and early detection using wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2009, 7, 169–224. [Google Scholar]
- Kasyap, V.L.; Sumathi, D.; Alluri, K.; Reddy Ch, P. Navod Thilakarathne, and R. Mahammad Shafi. Early detection of forest fire using mixed learning techniques and UAV. Comput. Intell. Neurosci. 2022, 2022. [Google Scholar] [CrossRef]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Shuo, S.; Liu, X.; Gu, X. An energy-efficiency Optimized LEACH-C for wireless sensor networks. In Proceedings of the 7th International Conference on Communications and Networking in China, Kunming, China, 8–10 August 2012; pp. 487–492. [Google Scholar]
- Adrian, P.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security protocols for sensor networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar]
- Wang, X.; Li-zhen, Y.; Ke-fei, C. Sleach: Secure low-energy adaptive clustering hierarchy protocol for wireless sensor networks. Wuhan University J. Nat. Sci. 2005, 10, 127–131. [Google Scholar]
- Basit, M.; Javaid, N.; Rehman, O.; Akbar, M.; Nadeem, Q.; Iqbal, A.; Ishfaq, M. Q-LEACH: A new routing protocol for WSNs. Procedia Comput. Sci. 2013, 19, 926–931. [Google Scholar]
- Yang, L.; Shang, F.; Long, Z.; Ren, Y. An energy efficient multiple-hop routing protocol for wireless sensor networks. In Proceedings of the 2008 First International Conference on Intelligent Networks and Intelligent Systems, Wuhan, China, 1–3 November 2008; pp. 147–150. [Google Scholar]
- Mu, T.; Tang, M. LEACH-B: An improved LEACH protocol for wireless sensor network. In Proceedings of the 2010 6th International Conference on Wireless Communications Networking and Mobile Computing (WiCOM), Chengdu, China, 23–25 September 2010; pp. 1–4. [Google Scholar]
- Seli, M.; Behera, P.K.; Sahoo, P.K.; Bisoy, S.K.; Hui, K.L.; Sain, M. Mobility Induced Multi-Hop LEACH Protocol in Heterogeneous Mobile Network. IEEE Access 2022, 10, 132895–132907. [Google Scholar]
- Hicham, O.; Lagraini, H.; Mouhsen, A.; Chhiba, M.; Tabyaoui, A. MG-leach: An enhanced leach protocol for wireless sensor network. Int. J. Electr. Comput. Eng. 2019, 9, 2088–8708. [Google Scholar]
- Kumar, D.; Singh, M.P. Bit-map-assisted energy-efficient MAC protocol for wireless sensor networks. Int. J. Adv. Sci. Technol. 2018, 119, 111–122. [Google Scholar]
- Kumar, D.; Singh, M.P.; Gupta, R. An energy saving medium access control protocol for wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 1435–1448. [Google Scholar]
- Rajeev, R.; Debasis, K.; Gupta, R.; Singh, M.P. Energy-Efficient Medium Access Control in Wireless Sensor Networks. Wirel. Pers. Commun. 2022, 122, 409–427. [Google Scholar]
- Babu, P.R.; Debasis, K. A Low Energy Consuming MAC Protocol for Wireless Sensor Networks. In Proceedings of the 2022 2nd International Conference on Artificial Intelligence and Signal Processing (AISP), Vijayawada, India, 12–14 February 2022; pp. 1–5. [Google Scholar]
- Byungrak, S.; Her, Y.; Kim, J. A design and implementation of forest-fires surveillance system based on wireless sensor networks for South Korea mountains. Int. J. Comput. Sci. Netw. Secur. 2006, 6, 124–130. [Google Scholar]
- Doolin, D.M.; Sitar, N. Wireless sensors for wildfire monitoring. In Smart Structures and Materials 2005: Sensors and Smart Structures Technologies for Civil, Mechanical, and Aerospace Systems; SPIE: Bellingham, WA, USA,, 2005; Volume 5765, pp. 477–484. [Google Scholar]
- Krešimir, P.; Belani, H.; Vuković, M. Early forest fire detection with sensor networks: Sliding window skylines approach. In Proceedings of the Knowledge-Based Intelligent Information and Engineering Systems: 12th International Conference, KES 2008, Proceedings, Part I 12. Zagreb, Croatia, 3–5 September 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 725–732. [Google Scholar]
- Al-Dhief, F.T.; Muniyandi, R.C.; Sabri, N.; Hamdan, M.; Latiff, N.M.A.; Albadr, M.A.A.; Khairi, M.H.H.; Hamzah, M.; Khan, S. Forest Fire Detection Using New Routing Protocol. Sensors 2022, 22, 7745. [Google Scholar] [CrossRef]
- Vikram, R.; Sinha, D.; De, D.; Das, A.K. EEFFL: Energy efficient data forwarding for forest fire detection using localization technique in wireless sensor network. Wirel. Netw. 2020, 26, 5177–5205. [Google Scholar] [CrossRef]
- Noureddine, M.; Khemiri-Kallel, S.; El Alaoui, A.E. Fog-assisted hierarchical data routing strategy for IoT-enabled WSN: Forest fire detection. Peer--Peer Netw. Appl. 2022, 15, 2307–2325. [Google Scholar]
- Emre, A.Y.; Korpeoglu, I.; Ulusoy, Ö. A framework for use of wireless sensor networks in forest fire detection and monitoring. Comput. Environ. Urban Syst. 2012, 36, 614–625. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).