Abstract
This paper studies the design of dual-mode resilient event-triggered control strategy for Markov jump cyber–physical systems (MJCPSs) under denial-of-service (DoS) attacks. Firstly, a novel resilient event-triggering scheme dependent on the DoS signal is developed to select the corresponding control protocol based on the current network quality of services. Particularly, the potential relationship between the triggering signal and system mode under DoS attacks is discussed, aiming to eliminate both Zeno behavior and singular triggering behavior by calculating the minimum and maximum data update rates. Then, we design an event-based dual-mode security controller to ensure that the closed-loop system has stochastic stability and good robust performance under DoS attacks. By constructing a Lyapunov–Krasovskii functional which depends on the lower and upper bounds of time delay, sufficient conditions for the existence of dual-mode security controller gains and resilient triggering parameters are presented with the LMI form. Finally, simulation results show that the proposed security control strategy has good robustness against DoS attacks.
1. Introduction
With the rapid development of artificial intelligence and other technologies, cyber–physical systems (CPSs) that can highly integrate computation, communication, and control have emerged and been widely used in critical infrastructures, such as smart grids [1], intelligent transportation [2], industrial internet [3], and so on. In essence, CPSs are a class of complex networked control systems with a cyclic feedback mechanism, and the ubiquitous interconnection features make the openness increasingly enhanced [4]. This means that the deep interaction between the information world and physical plant has achieved global autonomy and collaboration. However, the influence of cyber security threats and physical safety issues has brought great challenges to the integrated protection of CPSs. Once the security defense mechanism deployed on the information layer fails, malicious adversaries can covertly invade the information systems, causing CPS-induced failures to spread rapidly in the communication media, thereby making the serious non-contact damage to the physical process. Since physical systems operate in a relatively isolated environment, there is a lack of in-depth understanding of external network threats and internal security vulnerabilities [5]. Thus, it is of great value to design advanced security control strategies to ensure the safe operation of plants in an unreliable network environment. Recently, security issues for CPSs have attracted widespread attention, such as intrusion identification [6,7,8], secure state estimation [9,10,11], stability analysis [12,13,14,15], and resilient control [16,17,18,19].
In CPSs, malicious attackers have developed various remote intrusion modes by destroying the security requirements of physical systems, such as denial-of-service (DoS) attacks, false data injection (FDI) attacks, and deception attacks [20], where DoS attacks force system service interruption by occupying the limited communication bandwidth. In addition, DoS attacks do not need to acquire any prior system knowledge, which implies that DoS attacks can be easily launched without regard for privacy protection [21]. In this attack scenario, the abnormal behaviors caused by DoS attacks can be quickly perceived. However, the access to control and measurement signals will be lost, making it impossible to effectively deal with this attack behavior. Thus, it is necessary to develop an advanced security control strategy with robustness and intrusion tolerance to ensure that CPSs can operate smoothly in a degraded manner under DoS attacks. The authors in [12] have proposed the concept of “resilient control” to characterize the basic ability of CPSs to defend against DoS attacks. In [13], the authors developed an observer-based security control strategy for linear CPSs with multiple parallel transmission channels. The maximum operational duty cycle tolerated by CPSs under DoS attacks was obtained. To ensure both steady-state accuracy and transient security, the authors in [22] designed an active security control policy, where DoS attacks are assumed to occur in both control and measurement channels. The relationship between the resilience and communication bandwidth was studied in [23], where the bit rate condition under DoS attacks depends on the attack parameters and system matrices. The issue of secure consensus for interconnected CPSs under DoS attacks was discussed in [24,25,26,27,28], where the authors in [25] developed a time-varying resilient control scheme to ensure the secure consensus of the agent team. In [28], the authors discussed the co-design of the fault detection algorithm and consensus control protocol for interconnected CPSs under hidden DoS attacks. Since CPSs are susceptible to environmental mutations or random failures of physical components, they may consist of multiple subsystems with different structures and parameters. However, the above achievements are research on the security of deterministic CPSs, ignoring the research on CPSs with random jumps under cyber attacks.
Generally, it is difficult for the system to obtain measurement or control signals in a continuous manner. In order to overcome persistent communication, many sampled-data control policies based on a time-triggered communication mechanism have been widely investigated, see [29,30,31,32]. However, due to the limited communication bandwidth, this implies that the time-triggered sampling strategies can generate unnecessary consumption and computing resources. Consequently, the oversampling problem needs to be eliminated. As an effective solution to alleviate the communication burden, the event-triggered mechanism (ETM) regarded as “on-demand communication” was reported in [33,34,35,36,37], where the authors in [33] proposed a co-design method for the resilient event-triggered control (ETC) strategy to tolerate DoS attacks as much as possible. To obtain a higher communication efficiency, a novel switching-like ETC strategy for continuous CPSs was developed in [34] to balance the desired communication rate and security performance. In [35], a fully distributed secure cooperative control protocol for CPSs was developed to guarantee asymptotic consensus against distributed DoS attacks from multiple adversaries. The authors in [36] formulated a stochastic ETC scheme to overcome the stochastic DoS attacks by fully using the dynamic features of communication in the open network. Particularly, CPSs are vulnerable to environmental mutations or random failures of physical components, resulting in their potential to be composed of multiple subsystems with different structures and parameters. Therefore, it is necessary to develop appropriate security control strategies to ensure that jump CPSs still have an acceptable level of operation under cyber attacks. In addition, the authors in [37] developed a finite-time ETC strategy for nonlinear semi-Markov jump CPS to quickly defend against FDI attacks in finite time. Note that most ETC schemes adjust their event-triggering parameters in advance to counter the negative impact of DoS attacks on data transmission. This indicates that the traditional strategies have certain limitations when dealing with unpredictable DoS jamming attacks. Recently, the impact of DoS attacks was transformed into the uncertainty in triggering rule reported in [38], which plays a positive role in solving the mentioned problem.
However, very few works are available to solve similar topics for stochastic CPSs under DoS attacks and Markovian switching, to our knowledge. These facts inspire us to proceed with the present work.
This paper proposes a novel dual-mode resilient event-triggered control strategy for MJCPSs under DoS attacks. The salient contributions are as follows:
- (1)
- A novel resilient event-triggering rule that relies on DoS signals is designed to select corresponding control strategies on demand based on the current network service quality.
- (2)
- By analyzing the inner relationship between the system mode and the triggering instant under DoS attacks, the minimum and maximum inter-execution intervals are calculated to avoid Zeno behavior and singular triggering.
- (3)
- Based on the LMI method and Lyapunov stability theory, sufficient conditions for the existence of security controller gains and resilient triggering parameters are given in the form of concise LMIs simultaneously.
The outline of this paper is organized as follows. Section 2 presents preliminaries and problem formulation. In Section 3, stability analysis under resilient event-triggered rule and DoS attacks is investigated in detail. The dual-mode security controller is designed in Section 4. In Section 5, a simulation example is presented to illustrate the effectiveness of the proposed method. Finally, Section 6 summarizes this paper.
2. Preliminaries and Problem Formulation
2.1. System Framework
Consider MJCPSs defined on a complete probability space , whose dynamics can be captured by
where , , and are the system state, control input, and regulated output variables, respectively. represents an exogenous disturbance belonging to . , , , , and denote known matrices of compatible dimensions.
Let represent a right-continuous Markov process taking values in a finite set , whose stationary mode transition rate matrix (TRM) can be given by
where , , and TRs from i to j satisfy two conditions, that is, if then ; otherwise, for any .
On the other hand, Figure 1 presents an advanced event-based control architecture for MJCPSs subject to energy-limited DoS attacks, where the virtual sensor system determined by a novel resilient event-triggered rule is developed to alleviate the heavy communication burden generated by using traditional sampled-data schemes, see refs. [29,30,31] and the references therein. For clarity, let represent the sampled error, then we review a general event-triggered scheme mentioned in [38] as follows:
where is a given triggering parameter, and are the unknown weighting matrices to be designed, and denotes the triggering sequence determined by (3). In this way, the control input applied to the control layer in the absence of DoS attacks can be described as
where denotes the unknown control gain to be designed. Notice that the packets are transmitted on the sensor–controller (S-C) and controller–actuator (C-A) channels over the open and secure communication networks, respectively. This means that the S-C channel is vulnerable to remote intrusion by malicious attackers. From the perspective of system control performance, malicious intrusion on the S-C channel may cause information mismatch between the S-C and C-A channels. That is, the actuator may maintain historical control actions for a long time, which is enough to pose a serious threat to physical security. In order to ensure safe operation in an unreliable network environment, we will redesign an improved resilient event-triggered scheme and related security control protocol for MJCPSs in the sequel.
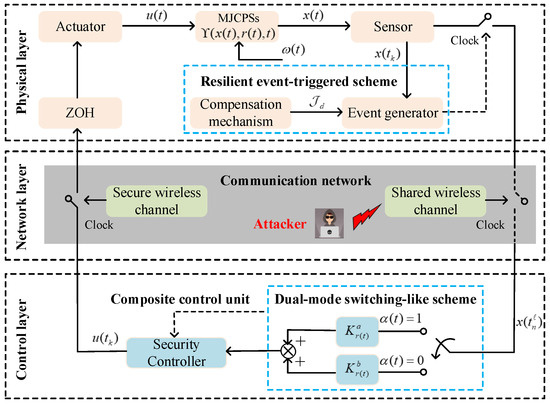
Figure 1.
Control architecture of MJCPSs under DoS attacks.
2.2. Dual-Mode Security Control Scheme
In general, the purpose of designing event-based data update strategy is to improve communication utilization. However, the malicious attackers always launch DoS attacks on the S-C channel covertly to destroy information interaction. This will inevitably lead to the accumulation of actual error between the historical update state and the current operation state such that the event-triggered condition is violated for a long time because the state error cannot be reset to zero. These facts motivates us to design a resilience margin for the event-triggered condition (3), which aims to be more robust against DoS attacks. From this, for any aperiodic interval , let be the n DoS active interval shown in Figure 2, where represents an injected DoS sequence. Then, for any , we define
and
as the union and relative complement of DoS subintervals over interval , respectively. Clearly, once the intermittent DoS attacks are successfully launched over a shared communication network, certain packets determined by the event-triggered rule (3) will be lost during the transmission. This implies that these criteria for stability analysis and controller synthesis presented in [24,25,27] may no longer be valid. Moreover, these packets that cannot be updated successfully are also considered redundant. In this case, we need to develop an improved event-triggered rule with a resilience margin according to (3). Firstly, the actual state error caused by DoS attacks can be defined as
where denotes a successful transmission sequence during the interval . Note that holds if DoS attacks do not exist; otherwise, DoS attacks cause an additional state error that can degrade security performance, i.e., holds. Then, a novel event-triggered rule with a resilience margin can be designed as
where represents the latest update instant when DoS attacks are no longer injected, denotes an unknown constant to be calculated, is the performance compensation for condition (3), and is the maximum resilience margin. Furthermore, is a Dirac measure used to describe DoS on/off properties, and its mathematical expectation can be characterized as
where is a positive scalar. In this way, we can design a novel dual-mode security controller under the resilient event-triggered rule (8) as follows:
where denotes a given regulated parameters, and represent the unknown control gains without or with DoS attacks, respectively. Let denote the time delay, then the control protocol (10) can be further rewritten as
where and denote the minimum and maximum time delays, respectively.
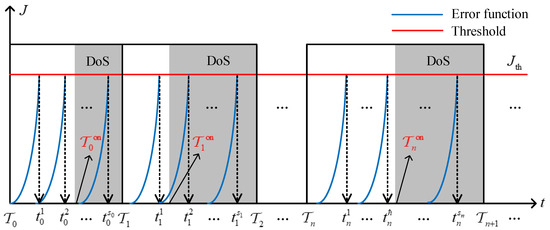
Figure 2.
Evolution of update data in the presence of DoS attacks.
In view of the designed resilient event-triggered rule (8) and dual-mode security control protocol (11), the resulting closed-loop systems can be described as
where , , and
In general, malicious attackers can launch three different types of DoS attacks on the CPS communication network, including periodic DoS attacks, stochastic DoS attacks, and time-constrained DoS attacks as shown in Figure 3. From the perspective of attack concealment, we consider time-constrained DoS attacks, whose properties can be characterized by frequency and duration.
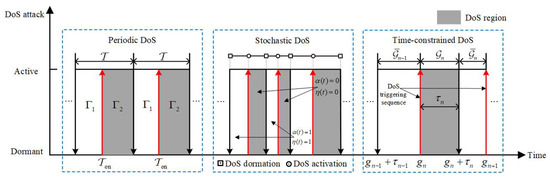
Figure 3.
Typical DoS attack models.
Assumption A1
(DoS Frequency [12]). There exist scalars and such that
for any .
Assumption A2
(DoS Duration [12]). There exist scalars and such that
for any .
2.3. Control Objective
For MJCPSs under DoS attacks, the control objective of this article is to develop the advanced resilient event-triggered rule and dual-mode security control protocol, which aims to ensure the safe operation of physical system in an unreliable network environment. Some useful definitions are given as follows.
Definition 1
([38]). For any initial condition , MJCPSs (1) can be said to be stochastically stable if they have a positive parameter such that
Definition 2
([38]). Given a positive parameter , MJCPSs (1) can be considered stochastically stable and to have an disturbance attenuation level γ if this condition is met:
Definition 3
([13]). The transmission sequence is said to have a finite update rate if there are two positive scalars and such that
where and are the minimum and maximum update rates, respectively.
Remark 1.
Generally, DoS behaviors launched by malicious attackers have a certain concealment, which makes it difficult for defenders to predict attack intentions. Under such an unreliable communication network, the packets to be updated determined by ETM may be lost during the transmission, thereby reducing the security performance of the physical system. To defend against DoS attacks, several popular resilient ETC strategies have been proposed, which can adjust the triggering parameters online or in advance according to changes in the system state, see [34,35,39,40,41,42] and the references therein. However, the invisibility of DoS attacks makes it difficult to adjust triggering parameters in real time, which leads to certain limitations of such methods. In contrast, setting a certain resilience margin for ETM to cope with the transmission failures caused by DoS attacks can break through the barriers of traditional control schemes. In addition, the triggering parameters do not need to be adjusted depending on whether DoS attacks occur. Hence, the method of designing a reasonable resilience margin for ETM in a unified framework may facilitate system analysis under DoS attacks.
Remark 2.
The control behavior in response to DoS attacks can be divided into two cases: one is to force the control signal to zero as mentioned in [12,13], and the other is to maintain the historical control input by using a zero-order holder (ZOH), see [34,38] and the references therein. Obviously, the former is an extremely conservative way to defend against DoS attacks because the controlled system may be in an open-loop unstable status for a long time. Conversely, the latter allows the physical system to obtain relatively satisfactory security performance in a degraded manner. That is, it can be concluded that the second way is more suitable as the core idea of the intrusion tolerance control scheme. On this basis, we can design a DoS-based dual-mode security controller by introducing a Dirac measure [43], which is independent of the system mode . The composite control scheme that includes two different control protocols is similar to hybrid control, but both protocols cannot take effect simultaneously. It should be noted that the event-triggered rules corresponding to the above control protocols are selected based on whether DoS attacks occur.
3. Stability Analysis under Resilient Event-Triggered Rule and DoS Attacks
3.1. Stability Criterion
Firstly, the primary goal of this subsection is to find the stability criteria for MJCPSs (1) under resilient event-triggered rule (8) and DoS attack. Then, we perform a comprehensive feasibility analysis on condition (8) to demonstrate the theoretical validity.
Theorem 1.
Given positive scalars σ, α, , , and γ, , and the dual-mode security controller gains and . Under the proposed resilient event-triggered rule (8), MJCPSs (1) are stochastically stable in the presence of intermittent DoS attacks and have an disturbance attenuation level γ if there exist the positive definite matrices , , , ,, , , , , and the real matrix such that the following conditions are satisfied:
where ,
with
Proof.
Firstly, consider a stochastic Lyapunov–Krasovskii functional as follows:
where
For , let be the weak infinitesimal generator, which is computed along the state trajectory of MJCPSs (1) as
where is defined in Theorem 1. For clarity, let represent the augmented vector. Then, in view of the mathematical nature of , one can obtain that
where , , and . By virtue of the Jessen’s inequality, the integral terms in (19) are calculated as
where and are defined in Theorem 1, respectively.
Combining condition (14), it follows from (16)–(22) that
where
with and other parameters, which are given in Theorem 1.
Then, we will show that MJCPSs (1) have an disturbance attenuation level for any non-zero . Define . Based on Definition 2, it can be derived that
where , , and
which implies that is established. In this way, we obtain that , where . From this, we can conclude that MJCPSs (1) are stochastically stable and have an disturbance attenuation level .
Finally, based on the developed resilient event-triggered rule (8), it follows from condition (24) that
where and is given in condition (13). By Schur’s complement lemma, it is concluded that the objective term in (25) is equivalent to in (13). Thus, it is derived that , where . This implies that is established, where represents the decay rate and represents the maximum eigenvalue of . From this, we can obtain that
where . Then, it follows from condition (26) that
which implies that
where and is the minimum eigenvalue of . In this case, it can be concluded that is bounded by . Meanwhile, the maximum performance loss induced by DoS attacks is calculated as , where . This completes the proof. □
3.2. Feasibility Criterion
In this subsection, the main objective is to find the minimum update rate, which aims to avoid Zeno behavior with an unlimited number of transmission instants in a finite time period. The maximum downtime of (8) under DoS attacks is calculated.
Theorem 2.
For the closed-loop MJCPSs (12) with resilient event-triggered rule (8) and dual-mode security controller (10), Zeno behavior is strictly excluded if the inter-execution interval , is greater than or equal to
where
with , , , , , , , , , , , , , , , , , , , , and , σ, ϖ, , and represent the given positive parameters. Moreover, the maximum downtime caused by DoS attacks can be calculated as with , , , , , , , , , , and .
Proof.
See the Appendix A. □
Remark 3.
In view of the proposed resilient event-triggered rule (8), the purpose is to characterize two possible data update policies generated by intermittent DoS attacks through random variable , where and represent dormant and active DoS attacks, respectively. Here, the existence of makes the triggering threshold when greater than that when . This implies that a higher triggering threshold may determine fewer packets to be transmitted. Note that it is quite possible to transmit a large number of packets in a short period of time because of an inappropriate event-triggered rule. Therefore, regardless of whether the triggering threshold is low or high, Zeno behavior needs to be strictly avoided. Moreover, the exogenous disturbance can direct the trajectory of in the resilient event-triggered rule (8). In order to prevent the influence of the disturbance signal on the estimation of , it is necessary to develop an improved triggering inequality when discussing the feasibility of resilient event-triggered rule (8).
Remark 4.
Note that the unreasonable event-triggered rules may also lead to singular triggering, which is another abnormal behavior that cannot transmit for a long time after a successful transmission attempt. By solving the maximum inter-execution interval between two consecutive transmissions, it is concluded that singular triggering can be avoided to guarantee the validity of the developed event-triggered rules. Due to intermittent DoS attacks, a large number of packets cannot be transmitted within the active DoS subintervals. Thus, it is necessary to characterize the maximum downtime between two adjacent successful updates to estimate the impact of intermittent DoS attacks on control performance. However, few results discuss this critical issue, and it is difficult to obtain an explicit representation for the maximum downtime caused by DoS attacks. Furthermore, similar to the procedures for avoiding Zeno behavior, we also study the potential impact of disturbance signal on calculating the maximum downtime.
4. Design of Dual-Mode Security Controller under Resilient Event-Triggered Rule
In this section, inspired by the theoretical results of stability analysis under the resilient event-triggered rule (8), we present a design procedure of the proposed dual-mode security control protocol. The following results illustrate the stated objectives.
Theorem 3.
Given positive scalars σ, α, , , γ, , there is a dual-mode security controller (10) such that MJCPSs (1) are stochastically stable in the presence of intermittent DoS signal and have an disturbance attenuation level γ, if there are positive definite matrices , , , , , , , , , and real matrices , , and with appropriate dimensions such that the following conditions are satisfied:
where , ,
and the remaining parameters are defined in Theorem 1. Then, the gains of the dual-mode security controller can be computed as
Proof.
Firstly, define the following new variables as , , , , , , , , , and . Then, based on the proof of Theorem 1, it can be seen that only the parameters , , and in (13) can affect the solution of security control gains and . To characterize an explicit form of control gains, the left-hand inequality in (13) can be transformed into
where
and .
Then, by post- and pre-multiplying both sides of (33) with and its transpose, we obtain
where , , , , and are defined in Theorem 3. Next, the nonlinear terms and in condition (34) are further rewritten as as , respectively. Substituting the resulting inequalities into (34), it is concluded that the left-hand inequality in (30) is established.
In a similar way, by post-multiplying and pre-multiplying both sides of the right-hand inequality in condition (13) with and its transpose, then we obtain the conclusion that the right-hand inequality in (30) is true. In addition, it follows from (14) that
which can be equivalent to
and
where and are given in Theorem 3. According to the Schur complement lemma, it can be deduced that
where
5. Simulation Example
In this section, a simulation example is given to demonstrate the effectiveness of the event-based dual-mode security control strategy under DoS attacks.
As shown in Figure 4, we consider a Pulse-Width Modulation (PWM)-driven boost converter borrowed from [44], which can be captured by
where L, C and R denote the inductance, capacitance and load resistance, respectively. and represent the terminal voltage and source voltage of the capacitor, respectively. is the current through the inductance. is a switching signal controlled by a PWM-driven boost converter. Here, as a typical circuit system, the role of using a PWM-driven boost converter is to obtain higher voltage. Let be the system state, then the differential Equation (40) is further rewritten as , , where the system parameters are and . Selecting , , and , all parameters can be listed as follows: Mode 1:
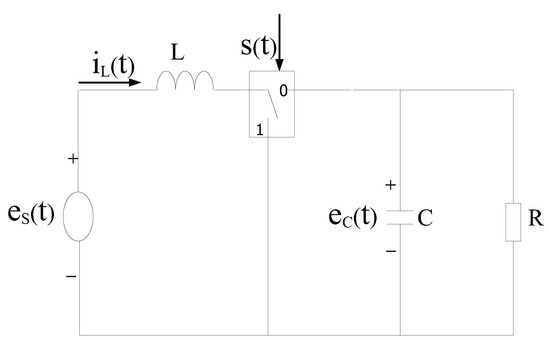
Figure 4.
PWM-driven boost converter.
Mode 2:
and . Without loss of generality, the transition rate matrix is given as
and the exogenous disturbance signal is assumed to be . According to Theorem 3, the given constants are selected as , , , , , , and . Then, the security controller gains and weighting matrices can be calculated as
Under the initial state , Figure 5 presents the state trajectories by using the proposed dual-mode security controller (10) when DoS attacks are not injected over the shared communication network. The time evolution of the regulated output and actual state error without DoS attacks are shown in Figure 6 and Figure 7, respectively. Obviously, by using the developed dual-mode security controller (10), the closed-loop MJCPSs (12) achieve stochastic stability and have good robustness. In Figure 8, we show the event-triggered instants determined by the resilient event-triggered condition (8) in the absence of DoS attacks, in which the number of successful transmissions is 67. From this, the average transmission period is calculated as . Note that the proposed resilient event-triggered rule (8) is equivalent to the static event-triggered rule when DoS attacks do not occur. Once malicious attackers inject DoS attacks into the communication network, Figure 9 provides schematic diagrams of DoS attacks and system modes, where and represent the active and dormant DoS intervals, respectively. Then, based on the different values of , DoS attacks can be divided into two types, namely low-intensity and high-intensity DoS attacks. Assume that the upper bound of performance loss caused by low-intensity DoS attacks is . In this case, Figure 10 shows the state response under the proposed dual-mode event-triggered security controller (10). Figure 11 presents the event-triggered instants determined by the resilient event-triggered condition (8) under low-intensity DoS attacks, where the number of the successful transmissions is 21. From this, the average transmission period is calculated as . Compared with the situation without DoS attacks, the system state can only converge to a bounded range when the time approaches infinity, indicating that DoS attacks caused a serious negative impact on the system performance. Although the event triggering interval does not exceed the maximum inter-execution interval calculated in Theorem 2, the controller remains in an unreleased state for a long time. On the other hand, assume that the upper bound of performance loss caused by low-intensity DoS attacks is . In this case, Figure 12 shows the state response under the proposed dual-mode event-triggered security controller (10). Compared with the above two situations, it can be seen that the system state cannot converge to zero when the time tends to infinity. This means that high-intensity DoS attacks can cause irreversible damage to the control performance of the system. Figure 13 shows the triggering instant and transmission sequence under high-intensity DoS attacks, where the number of the successful transmissions is 13 and the average transmission period is calculated as . From this, it can be seen that once the event-triggering interval exceeds the maximum allowable inter-execution interval , the system will completely lose control performance due to the controller not being updated for a long time. This means that the proposed event dual-mode event-triggered security controller (10) can ensure the safe and stable operation of the system under a specific DoS attack intensity.
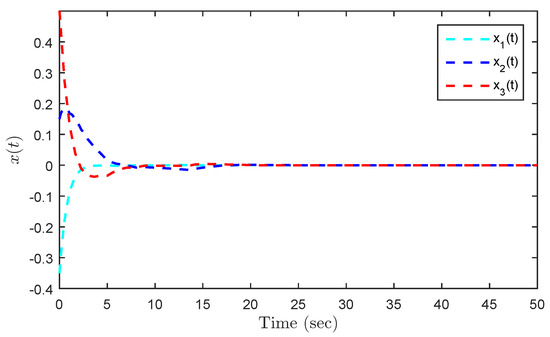
Figure 5.
State responses without DoS attacks.
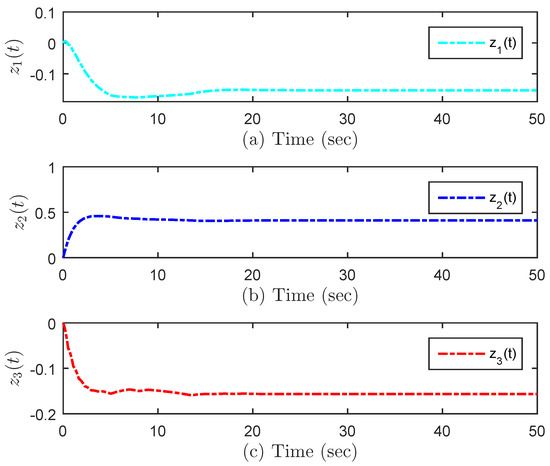
Figure 6.
Evolution of the regulated output without DoS attacks.
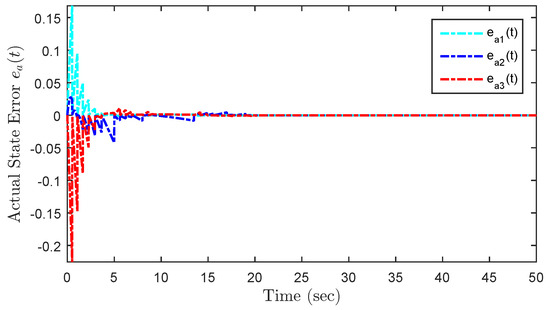
Figure 7.
Evolution of the actual state error without DoS attacks.
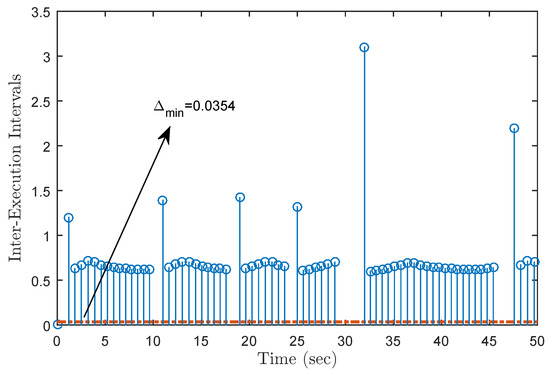
Figure 8.
Update instants without DoS attacks.
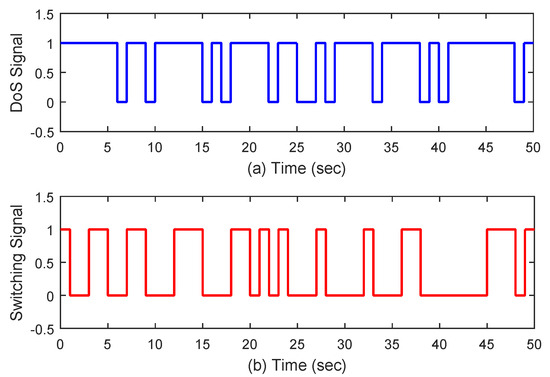
Figure 9.
Top: (a) DoS signal. Bottom: (b) Switching signal.
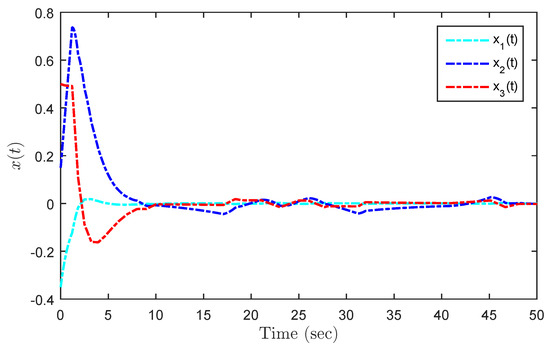
Figure 10.
State responses under DoS attacks with .
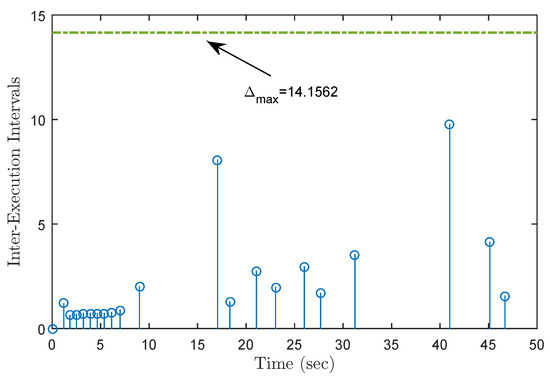
Figure 11.
Update instants under DoS attacks with .
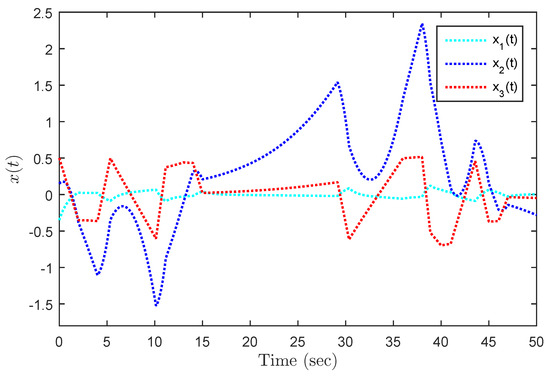
Figure 12.
State responses under DoS attacks with .
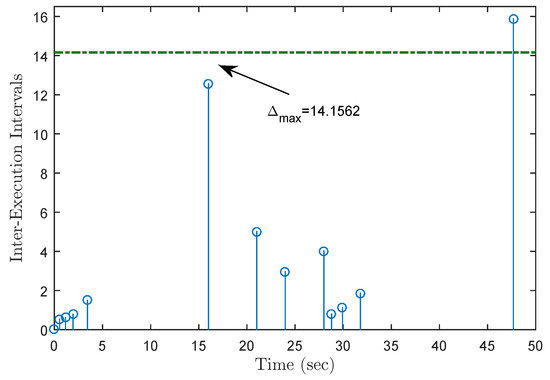
Figure 13.
Update instants under DoS attacks with .
On the other hand, in order to further demonstrate the effectiveness of the proposed control strategy, we consider a DC motor-driven inverted pendulum systems, which is modeled in [45]. The system parameters are as follows:
and the other parameters remain unchanged. Then, the security controller gains and weighting matrices can be calculated as
Under the initial state , Figure 14 presents the state trajectories by using the proposed dual-mode security controller (10) when DoS attacks are not injected over the shared communication network. Similarly, assume that the upper bound of performance loss caused by low-intensity DoS attacks is . In this case, Figure 15 shows the state response under the proposed dual-mode event-triggered security controller (10), while Figure 16 shows the state response by using a general one. Therefore, it can prove the effectiveness of the dual-mode security controller proposed in this paper.
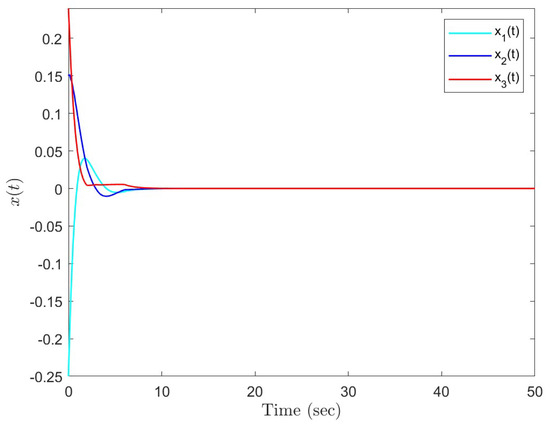
Figure 14.
State responses without DoS attacks.
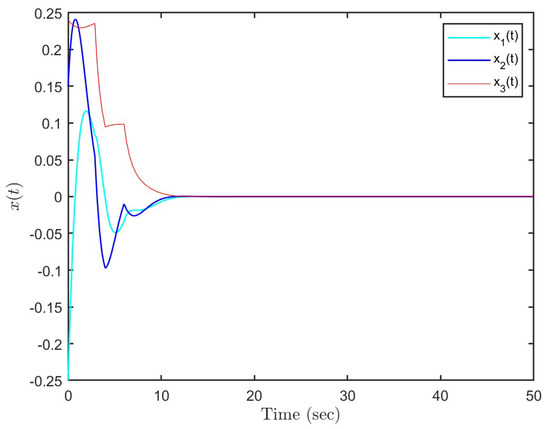
Figure 15.
State responses under DoS attacks with by using security controller.
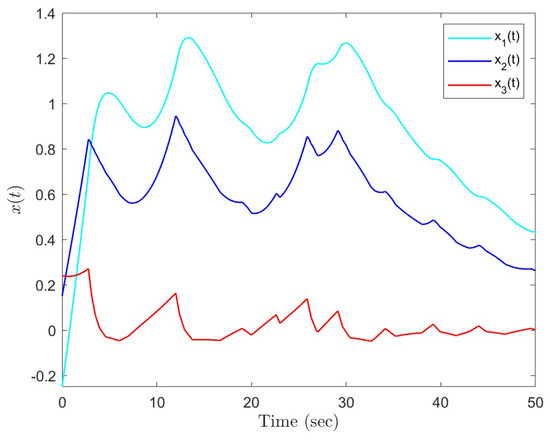
Figure 16.
State responses under DoS attacks with by using general controller.
6. Conclusions
This paper addressed the problem of dual-mode event-triggered control for MJCPSs under DoS attacks. A novel random event-triggering rule determined by DoS signal was developed to select appropriate control strategies as needed based on the current network service quality. Then, the relationship between triggering signals and system modes under DoS attacks was analyzed. By calculating the minimum and maximum inter-execution intervals, Zeno behavior and singular triggering can be avoided. On this basis, a mode-dependent event-triggered security was designed to ensure the stable operation of the system under DoS attacks. Finally, a new security control strategy was proposed to tolerate the packet loss caused by DoS attacks as much as possible. In our future work, we will focus on the problem of attack detection and resilient control of unmanned aerial vehicle systems under connectivity-preserved and connectivity-broken DoS attacks from a switching perspective.
Author Contributions
Conceptualization: M.G. Data curation: M.G. and H.X. Funding acquisition: M.G. and T.P. Investigation: H.X. and S.C. Software: M.G. and Z.L. Supervision: Z.L. Writing—original draft: M.G. Writing—review and editing: Z.L., M.G. and S.C. All authors have read and agreed to the published version of the manuscript.
Funding
The author(s) received funding from the Science and Technology Commission of Shanghai Municipality program (19510750200) for this research.
Conflicts of Interest
All authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Appendix A
Proof of the Theorem 2.
For any transmission interval determined by the general event-triggered rule (3), the following two cases are divided to explain the relationship between the jump signal and the triggering sequence , where represents the jump instant sequence.
Case I: No jump occurs during the interval , that is, is assumed to be established. Then, it follows from (7) that
As can be seen from the dual-mode security control protocol in (A1), due to the intermittent DoS attacks, two additional crucial points need to be considered in the following analysis.
- DoS attacks are not activated by malicious attackers. This indicates that and .
By virtue of (10), it can be derived from (A1) that
where , , , and are given in Theorem 2. Then, a virtual auxiliary variable satisfying needs to be introduced, aiming to constrain the change of . Thus, the analytical solution of can be governed by
Combined with the actual state error mentioned in (7), one can yield that
Based on the resilient event-triggered rule (8), it is concluded that and are established without DoS attacks, where and are given in Theorem 2. Then, we obtain , which is guaranteed by , where is a given constant. To calculate the minimum inter-execution interval , we need to discuss the inherent relationship between , , and . With the help of Young’s inequality, it can be further guaranteed by , where the forms of and consist of the parameters , , and . Combined with inequality (A4), one can yield
which is greater than or equal to in condition (29).
- DoS attacks are injected remotely by malicious attackers. This means that and .
Due to DoS attacks, condition (A2) needs to be rewritten as
where . Then, it follows from (A6) that , where is given in Theorem 2. Similarly, we define a virtual intermediate variable satisfying , whose solution can be calculated as
Substituting into (A7), we obtain . Meanwhile, it can be known from the resilient event-triggered rule (8) that is established when there are DoS attacks, where and are given scalars. Subsequently, we need to focus on the relationship between , , , , and . Based on Young’s inequality, it can be concluded that , where , , , , and are defined in Theorem 2. From this, one can yield
where and . This implies that the inter-execution interval is greater than or equal to defined in condition (29).
Case II: Some jumps occur during the interval . This means that with .
Once there are some jumps during the interval , we need to divide it into a group of subintervals based on the jump instants. Furthermore, it can be seen from the above derivation that conditions (A2) and (A6) are satisfied regardless of whether DoS attacks are dormant or active. Since the jump signal , obeys a right-continuous Markov process, this indicates that either or can be satisfied for the first subinterval . Notice that is maintained within the transmission interval due to the effect of ZOH. In this case, no matter the subinterval, we can obtain and . Thus, the same conclusion can be drawn as in Case I. That is, conditions (A2) and (A6) always hold, where there exist some jumps during the transmission interval . In summary, the parameter determined by (A2) and (A6) is regarded as the minimum execution interval, implying that Zeno behavior can be avoided.
On the other hand, DoS attacks can cause a severe mismatch of information between S-C and C-A sides. Therefore, we need to calculate the maximum downtime, which is reflected by the maximum update interval between two successful transmission attempts subject to the resilient event-triggered rule (8). Firstly, before embarking on this study, it can be concluded from Case I and Case II that the presence or absence of jumps during each transmission interval has no effect on estimating . Next, if is satisfied, then we can derive , where is given in (A8) and the parameters , , , are defined in Theorem 2. In view of the accumulation of sampling errors caused by DoS attacks, a large number of packets from S-C side cannot be transmitted normally. Therefore, it is necessary to re-estimate over time period , . Intuitively, we need to discuss the internal relationship between the latest transmission instant and DoS initiation instant. From this, the estimation of during can be divided into the following three steps.
Step I: The latest transmission attempt occurs at , that is, , where and denote the latest transmission and DoS initiation instants, respectively. Then, we obtain that
where . Since there may be some abnormal event-triggered packets during , it follows from (A9) that
where , and is the maximum number of packet losses caused by DoS attacks during .
Step II: The latest transmission attempt occurs before , that is, is established. For , we can obtain
In a similar way, for the DoS active subinterval, can be further calculated as
Step III: Calculate the maximum update interval between two successful transmission attempts.
By comparing the magnitude of conditions (A10) and (A12), it can be found that the supermum of is characterized by condition (A10). Substituting the fact into condition (A10), it can be deduced that
where
, , and . Therefore, in order to ensure the safe operation under DoS attacks, the maximum downtime must be less than or equal to defined in Theorem 2. The proof is complete. □
References
- Mollah, M.B.; Zhao, J.; Niyato, D.; Lam, K.-Y.; Zhang, X.; Ghias, A.M.Y.M.; Koh, L.H.; Yang, L. Blockchain for Future Smart Grid: A Comprehensive Survey. IEEE Internet Things J. 2020, 8, 18–43. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-physical systems security—A survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef]
- Molnar, T.G.; Kiss, A.K.; Ames, A.D.; Orosz, G. Safety-Critical Control With Input Delay in Dynamic Environment. IEEE Trans. Control Syst. Technol. 2023, 31, 1507–1520. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Dorfler, F.; Bullo, F. Attack Detection and Identification in Cyber-Physical Systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Chang, V.; Hawash, H.; Chakrabortty, R.K.; Ryan, M. Deep-IFS: Intrusion Detection Approach for Industrial Internet of Things Traffic in Fog Environment. IEEE Trans. Ind. Inform. 2020, 17, 7704–7715. [Google Scholar] [CrossRef]
- Qaddoura, R.; Al-Zoubi, A.M.; Almomani, I.; Faris, H. A Multi-Stage Classification Approach for IoT Intrusion Detection Based on Clustering with Oversampling. Appl. Sci. 2021, 11, 3022. [Google Scholar] [CrossRef]
- Jovanov, I.; Pajic, M. Relaxing Integrity Requirements for Attack-Resilient Cyber-Physical Systems. IEEE Trans. Autom. Control 2019, 64, 4843–4858. [Google Scholar] [CrossRef]
- Ding, D.; Han, Q.-L.; Ge, X.; Wang, J. Secure State Estimation and Control of Cyber-Physical Systems: A Survey. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 176–190. [Google Scholar] [CrossRef]
- Incremona, G.P.; Rubagotti, M.; Tanelli, M.; Ferrara, A. A General Framework for Switched and Variable Gain Higher Order Sliding Mode Control. IEEE Trans. Autom. Control 2021, 66, 1718–1724. [Google Scholar] [CrossRef]
- De Persis, C.; Tesi, P. Input-to-State Stabilizing Control Under Denial-of-Service. IEEE Trans. Autom. Control 2015, 60, 2930–2944. [Google Scholar] [CrossRef]
- Lu, A.-Y.; Yang, G.-H. Input-to-State Stabilizing Control for Cyber-Physical Systems With Multiple Transmission Channels Under Denial of Service. IEEE Trans. Autom. Control 2018, 63, 1813–1820. [Google Scholar] [CrossRef]
- Lu, A.-Y.; Yang, G.-H. Stability Analysis for Cyber-Physical Systems Under Denial-of-Service Attacks. IEEE Trans. Cybern. 2021, 51, 5304–5313. [Google Scholar] [CrossRef]
- Umlauft, J.; Hirche, S. Feedback Linearization Based on Gaussian Processes With Event-Triggered Online Learning. IEEE Trans. Autom. Control 2020, 65, 4154–4169. [Google Scholar] [CrossRef]
- Doostmohammadian, M.; Meskin, N. Finite-Time Stability Under Denial of Service. IEEE Syst. J. 2021, 15, 1048–1055. [Google Scholar] [CrossRef]
- Tahoun, A.H.; Arafa, M. Secure control design for nonlinear cyber–physical systems under DoS, replay, and deception cyber-attacks with multiple transmission channels. ISA Trans. 2022, 128, 294–308. [Google Scholar] [CrossRef]
- Lu, A.-Y.; Yang, G.-H. Resilient Observer-Based Control for Cyber-Physical Systems With Multiple Transmission Channels Under Denial-of-Service. IEEE Trans. Cybern. 2020, 50, 4796–4807. [Google Scholar] [CrossRef]
- Li, Z.; Zhao, J. Resilient adaptive control of switched nonlinear cyber-physical systems under uncertain deception attacks. Inf. Sci. 2021, 543, 398–409. [Google Scholar] [CrossRef]
- Kim, S.; Park, K.-J.; Lu, C. A Survey on Network Security for Cyber–Physical Systems: From Threats to Resilient Design. IEEE Commun. Surv. Tutor. 2022, 24, 1534–1573. [Google Scholar] [CrossRef]
- Cosentino, F.; Oberhauser, H.; Abate, A. Grid-free computation of probabilistic safety with malliavin calculus. IEEE Trans. Autom. Control 2023, 68, 6369–6376. [Google Scholar] [CrossRef]
- Li, T.; Chen, B.; Yu, L.; Zhang, W.-A. Active Security Control Approach Against DoS Attacks in Cyber-Physical Systems. IEEE Trans. Autom. Control 2021, 66, 4303–4310. [Google Scholar] [CrossRef]
- Feng, S.; Cetinkaya, A.; Ishii, H.; Tesi, P.; Persis, C.D. Networked control under DoS attacks: Tradeoffs between resilience and data rate. IEEE Trans. Autom. Control 2020, 66, 460–467. [Google Scholar] [CrossRef]
- Feng, Z.; Wen, G.H.; Hu, G.Q. Distributed secure coordinated control for multiagent systems under strategic attacks. IEEE Trans. Cybern. 2017, 47, 1273–1284. [Google Scholar] [CrossRef]
- Senejohnny, D.; Tesi, P.; De Persis, C. A Jamming-Resilient Algorithm for Self-Triggered Network Coordination. IEEE Trans. Control Netw. Syst. 2018, 5, 981–990. [Google Scholar] [CrossRef]
- Yang, Y.; Xu, H.; Yue, D. Observer-Based Distributed Secure Consensus Control of a Class of Linear Multi-Agent Systems Subject to Random Attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2018, 66, 3089–3099. [Google Scholar] [CrossRef]
- Deng, C.; Wen, C. MAS-Based Distributed Resilient Control for a Class of Cyber-Physical Systems With Communication Delays Under DoS Attacks. IEEE Trans. Cybern. 2021, 51, 2347–2358. [Google Scholar] [CrossRef]
- Zhang, D.; Ye, Z.; Dong, X. Co-Design of Fault Detection and Consensus Control Protocol for Multi-Agent Systems Under Hidden DoS Attack. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 2158–2170. [Google Scholar] [CrossRef]
- Persis, C.D.; Tesi, P. Formulas for data-driven control: Stabilization, optimality, and robustness. IEEE Trans. Autom. Control 2020, 65, 909–924. [Google Scholar] [CrossRef]
- Gabriel, G.W.; Goncalves, T.R.; Geromel, J.C. Optimal and robust sampled-data control of Markov jump linear systems: A differential LMI approach. IEEE Trans. Autom. Control 2018, 63, 3054–3060. [Google Scholar] [CrossRef]
- Gunasekaran, N.; Joo, Y.H. Robust Sampled-data Fuzzy Control for Nonlinear Systems and Its Applications: Free-Weight Matrix Method. IEEE Trans. Fuzzy Syst. 2019, 27, 2130–2139. [Google Scholar] [CrossRef]
- De Persis, C.; Rotulo, M.; Tesi, P. Learning Controllers From Data via Approximate Nonlinearity Cancellation. IEEE Trans. Autom. Control 2023, 68, 6082–6097. [Google Scholar] [CrossRef]
- Amini, A.; Asif, A.; Mohammadi, A. Formation-containment control using dynamic event-triggering mechanism for multi-agent systems. IEEE/CAA J. Autom. Sin. 2020, 7, 1235–1248. [Google Scholar] [CrossRef]
- Peng, C.; Sun, H. Switching-Like Event-Triggered Control for Networked Control Systems Under Malicious Denial of Service Attacks. IEEE Trans. Autom. Control 2020, 65, 3943–3949. [Google Scholar] [CrossRef]
- Xu, W.; Hu, G.; Ho, D.W.C.; Feng, Z. Distributed Secure Cooperative Control Under Denial-of-Service Attacks From Multiple Adversaries. IEEE Trans. Cybern. 2020, 50, 3458–3467. [Google Scholar] [CrossRef]
- Peng, C.; Wu, J.; Tian, E. Stochastic Event-Triggered H∞ Control for Networked Systems Under Denial of Service Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 52, 4200–4210. [Google Scholar] [CrossRef]
- Qi, W.; Hou, Y.; Zong, G.; Ahn, C.K. Finite-Time Event-Triggered Control for Semi-Markovian Switching Cyber-Physical Systems With FDI Attacks and Applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 2665–2674. [Google Scholar] [CrossRef]
- Sun, H.; Peng, C.; Zhang, W.; Yang, T.; Wang, Z. Security-based resilient event-triggered control of networked control systems under denial of service attacks. J. Frankl. Inst. 2019, 356, 10277–10295. [Google Scholar] [CrossRef]
- Xu, Y.; Fang, M.; Shi, P.; Wu, Z.-G. Event-based secure consensus of multiagent systems against DoS attacks. IEEE Trans. Cybern. 2020, 50, 3468–3476. [Google Scholar] [CrossRef]
- Feng, Z.; Hu, G. Secure Cooperative Event-Triggered Control of Linear Multiagent Systems Under DoS Attacks. IEEE Trans. Control Syst. Technol. 2020, 28, 741–752. [Google Scholar] [CrossRef]
- Deng, C.; Wen, C. Distributed resilient observer-based fault-tolerant control for heterogeneous multiagent systems under actuator faults and DoS attacks. IEEE Trans. Control Netw. Syst. 2020, 7, 1308–1318. [Google Scholar] [CrossRef]
- Behera, A.K.; Bandyopadhyay, B. Robust sliding mode control: An event-triggering approach. IEEE Trans. Circuits Syst. II Express Briefs 2017, 64, 146–150. [Google Scholar] [CrossRef]
- Xiong, J.; Lam, J.; Shu, Z.; Mao, X. Stability Analysis of Continuous-Time Switched Systems With a Random Switching Signal. IEEE Trans. Autom. Control 2014, 59, 180–186. [Google Scholar] [CrossRef]
- Zhang, L.; Cui, N.; Liu, M.; Zhao, Y. Asynchronous filtering of discrete-time switched linear systems with average dwell time. IEEE Trans. Circuits Syst. Regul. Pap. 2011, 58, 1109–1118. [Google Scholar] [CrossRef]
- Lian, J.; Li, C.; Liu, D. Input-to-state stability for discrete-time nonlinear switched singular systems. IET Control Theory Appl. 2017, 11, 2893–2899. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).