Abstract
The Internet of Medical Things (IoMT) is a network of healthcare devices such as wearables, diagnostic equipment, and implantable devices, which are linked to the internet and can communicate with one another. Blockchain (BC) technology can design a secure, decentralized system to store and share medical data in an IoMT-based intelligent healthcare system. Patient records were stored in a tamper-proof and decentralized way using BC, which provides high privacy and security for the patients. Furthermore, BC enables efficient and secure sharing of healthcare data between patients and health professionals, enhancing healthcare quality. Therefore, in this paper, we develop an IoMT with a blockchain-based smart healthcare system using encryption with an optimal deep learning (BSHS-EODL) model. The presented BSHS-EODL method allows BC-assisted secured image transmission and diagnoses models for the IoMT environment. The proposed method includes data classification, data collection, and image encryption. Initially, the IoMT devices enable data collection processes, and the gathered images are stored in BC for security. Then, image encryption is applied for data encryption, and its key generation method can be performed via the dingo optimization algorithm (DOA). Finally, the BSHS-EODL technique performs disease diagnosis comprising SqueezeNet, Bayesian optimization (BO) based parameter tuning, and voting extreme learning machine (VELM). A comprehensive set of simulation analyses on medical datasets highlights the betterment of the BSHS-EODL method over existing techniques with a maximum accuracy of 98.51%, whereas the existing methods such as DBN, YOLO-GC, ResNet, VGG-19, and CDNN models have lower accuracies of 94.15%, 94.24%, 96.19%, 91.19%, and 95.29% respectively.
1. Introduction
Smart healthcare is the advancement of conventional healthcare with advanced internet technologies. It incorporates various technologies to render real-time health-relevant data collected from patients utilizing smart wearable devices and detection of health problems in real time from the collected data [1]. The Internet of Medical Things (IoMT) plays a crucial role in the medical field to increase electronic devices’ throughput, precision, and consistency. Due to the outbreak of the coronavirus pandemic, visiting a doctor becomes a high risk for a person with small problems [2]. With the help of IoMT devices, it becomes easy to monitor health records daily, and preventive measures can be taken on our own. An IoMT-based smart healthcare system refers to a collection of several smart medical devices linked within the network over the internet [3]. Analysis can be done by making use of proper AI-based data transformation and interpretation methods after getting the medical dataset. However, easy access to healthcare applications and services has increased the risks and vulnerabilities that hinder smart healthcare systems’ performance. Also, many more heterogeneous devices collect data that differ in formats and size, making it a challenge to manage the data in the healthcare repositories and secure it from attackers who seek to profit from the data [4]. Therefore, smart healthcare schemes are prone to several security risks and threats, such as network attacks, software and hardware-based attacks, and system-level attacks, which put the lives of patients at risk.
Developing technologies, namely blockchain (BC), were utilized for providing cutting-edge solutions in several settings [5], one among them being the healthcare sector. BC technology is used in the medical field to guarantee the security of patient reports and rationalise data sharing amongst pharmaceutical companies, health care providers, and labs [6]. In the medical world, applications (apps) built on BC technology can detect significant and even hazardous errors [7]. Thus, it is capable of enhancing the openness, efficacy, and safety of the systems to exchange healthcare data in the medical field. Medical institutions are aided by BC technology to obtain insight and enhance medical record analysis. Then, the healthcare support system demands a new processing method with delay-sensitive monitoring which should be smart and managed stably [8].
Deep learning (DL) related medical diagnosis in the IoMT signifies the use of machine learning (ML) and artificial intelligence (AI) approaches to examine medical datasets collected from different devices connected to the internet, namely medical equipment and wearable devices [9]. It enhances the precision level of diagnostic decisions, helps identify trends and patterns in patient data, and enables efficient and more personalized healthcare delivery [10]. Simultaneously, hyperparameter tuning of the DL models becomes essential to improve the overall classification performance. Since trial-and-error hyperparameter selection is a challenging task, metaheuristic optimization techniques are used. In addition, image encryption schemes can be used to securely transmit healthcare data in the IoMT encryption. Furthermore, the key generation process is critical to the security of an encryption algorithm, as the strength of the key directly impacts the security of the encrypted data. Therefore, it is important to use strong and secure key generation methods and to properly manage and protect the keys.
This article develops an IoMT with a blockchain-based smart healthcare system using encryption with an optimal deep learning (BSHS-EODL) model. The presented BSHS-EODL technique comprises a few processes: data collection, image encryption, and data classification. Initially, the IoMT devices enable data collection processes, and the gathered images are stored in BC for security. Then, image encryption is employed to encrypt the data, and its key generation process is performed via the dingo optimization algorithm (DOA). Finally, the BSHS-EODL technique performs disease diagnosis comprising SqueezeNet, Bayesian optimization (BO) based parameter tuning, and voting extreme learning machine (VELM). A comprehensive set of simulation analyses is performed on medical datasets.
2. Related Works
Almaiah et al. [11] present a DL framework based on BC that offers a dual level of security and privacy. Initially, a BC technique was modelled in which each participating entity was verified, validated, and registered by making use of a smart contract related enhanced proof-of-work to reach the target of privacy and security. Then, a DL approach including bidirectional long short-term memory (BLSTM) for a variational autoencoder (VAE) and intrusion detection systems for privacy were devised. Khan et al. [12] introduced BIoMT, a BC Hyperledger fabric-assisted consortium architecture which offers transparency, security, and integrity to health-oriented transactions and interchanges delicate medical data in serverless peer-to-peer (P2P) secured network settings. A consensus was devised and constituted to decrease rate of BC resource limitations on the IoMT.
In [13], suggesting a BC-based secured data management framework (BSDMF) for medical data related to the IoTs to exchange patients’ data securely and improve data accessibility and scalability. To assure data management and data transmission security among associated nodes, the IoMT-related security structure uses BC. In [14], this study evaluated offloading and scheduling issues for medical workflow in IoMT fog-cloud platforms. Thus, this study addressed the issue as an offloading and scheduling issue and developed deep reinforcement learning (DRL) as a Markov problem. This study designed an innovative DRL and BC-based system which contained multi-criteria offloading depending on DRL policies.
Lakhan et al. [15] developed an LSEOS method called lightweight secure efficient offloading scheduling. LSEOS has lightweight and secured offloading and scheduling methodologies whose offloading delay will be lesser compared to prevailing techniques. The end goal of LSEOS is to run the application over other nodes and diminish the delay and security threats in the mechanism. The metaheuristic LSEOS has the elements they are scheduling with neighbourhood search schemes, adaptive deadlines, and sorting. Kumar and Tripathi [16] offered an innovative contract-based consortium BC technique. The authors compiled interplanetary file systems (IPFS) and cluster nodes where smart contracts are deployable in the early phase. The IPFS cluster node assures the authentication and security of gadgets and even offers safe storage in IoMT based health care systems. Alqaralleh et al. [17] designed DL with BC-based secured image transmission and diagnosis system for the IoMT environment. The elliptic curve cryptography (ECC) was implemented in the initial stage, and then by combining grasshopper and fruit fly optimization (GO-FFO) system, ECC’s optimum key generation is taken. Finally, a method called a deep belief network (DBN) is applied to find the existence of disease. In [18], a novel secure authentication method utilizing ML was presented. To find the attack authentication and detection in an IoMT platform, this study applies ML and k-nearest neighbour (KNN) with smart contract (KNN-MLSC).
Uppal et al. [19] proposed an interplanetary file system (IPFS) enabled model for secure healthcare system. It enables the client to continuously upload the healthcare information gathered by IoT devices and to add to the BC transactions. The authors in [20] developed a BC based electronic medical records (EMR) management model for a smart healthcare system. The privacy of the healthcare data can be accomplished using BC technology. It offers off-chain storage for the records and assuring the authenticity and integrity of the health records. In [21], a new hybrid Elman Neural-based Blowfish BC approach has been introduced for the security of the healthcare data in the IoT environment. The Elman network offered continual monitoring to predict abnormal activities in the trained multimedia data. The authors in [22] developed a Lionized Golden Eagle based Homomorphic Elapid Security (LGE-HES) technique with blockchain in healthcare network. The blockchain provides the privacy of the medical images using hash operations.
Although several encryption techniques have been presented in the literature, security performance still needs to be improved. Since the images encompass a massive quantity of data, high redundancy rate, and increased correlation between neighboring pixels, classical encryption models cannot be used to resolve the requirements of the image encryption technique. Therefore, several approaches have been presented based on chaotic concepts, pixel swapping, etc. On the other hand, the continuous deepening of the DL model has resulted in the model overfitting issue. In addition, various hyperparameters have provided a substantial impact on the performance of the CNN model. In particular, the hyperparameters such as learning rate, batch size, and number of epochs are important to attain effectual outcome. As the trial-and-error technique for hyperparameter tuning is a challenging and erroneous procedure, a BO algorithm is used in this study.
3. The Proposed Model
In this paper, we develop a new BSHS-EODL method for secured medical image transmission and analysis in the IoMT environment. The presented BSHS-EODL technique enables BC assisted secured image communication and detection models for the IoMT environment. The proposed method includes data classification, data collection, and image encryption. At the initial stage, the IoMT devices enable data collection processes, and the gathered images are stored in BC for security. Once the images are gathered, they are encrypted using effective image encryption technique with a DOA based key generation process. Next, the encrypted image was securely transferred using BC technology. At the receiver end, the image decryption was implemented, and the disease diagnosis process was later. Figure 1 demonstrates the working process of the BSHS-EODL method.
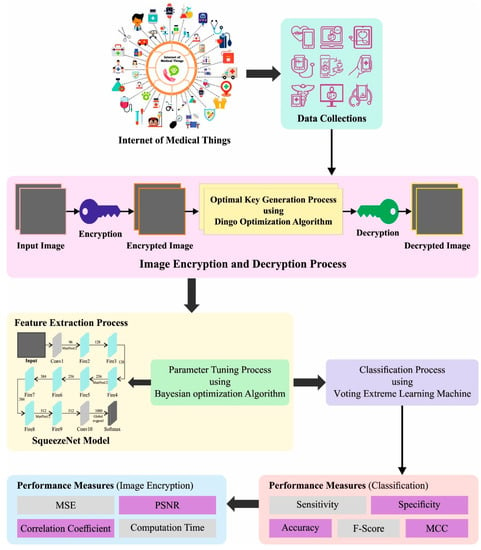
Figure 1.
Working process of BSHS-EODL approach.
3.1. Image Encryption
In this work, image encryption method takes place to secure medical images. The image encryption procedure mostly comprises key selection, chaotic sequence pre-processing, diffusion, block scrambling, confusion, and expansion [23]. The chaotic sequence pre-processing makes the sequence more arbitrary. Block scrambling has been separated, as intra- and inter-block scrambling decrease the correlation and offer optimum protection against statistical attack. The expansion stage enhances arbitrary numbers to novel images towards all the encryption and thus gains a distinct ciphertext image that is optimally prepared to resist chosen plaintext attack. Diffusion and confusion complicate the connection amongst ciphertext and keys, which make it complex for adversaries to decrypt a ciphertext image and that improves the resistance of such scenarios.
- Key Selection
Optimizing values , and created by the DOA technique can be utilized as the keys for 2-D logistic maps. For avoiding transient impact, the first 200 points can be discarded and generate 2 chaotic sequences that are of length
- Chaotic Sequence Preprocessing
The 2 chaotic sequences can be pre-processed based on Equation (1).
whereas and implies the chaotic sequences pre-processed sequence, whereas .
- Image Scrambling
The 16 sub-blocks of similar sizes can be separated by the new image , and the remaining numbers of sequences are acquired for composing a sequences . The acquired integer sequence was sorted, and inter-block scrambling was attained based on Equation (2).
Sequences and refer to the collection of sequence values from the mid sequences and , correspondingly and a novel sequence was created based on Equation (3). All the sub-blocks were disordered times by intra-block scrambling established to process the novel disordered sixteen sub-blocks.
Finally, the 16 sub-blocks can be combined with procedure image
- Image Expansion
The and are 2 random matrices created, whereas the sizes of and are 4 and , correspondingly. Develop image based on the system for forming an expanded image
- Confusion and Diffusion
The chaotic scheme comprises two stages: diffusion and confusion. Confusion seeks to obscure and confound the relationships among key and the cipher images. Diffusion aims to obscure the relationships among the cipher and plain images by making it as convoluted. Principally, the swapping operation on the rows and the columns was performed for the realization of the confusion effects. Primarily, compute the novel row index utilizing , followed by related row with row indexes .
Secondly, the parameters are computed utilizing .
Thirdly, accomplish a bitwise XOR function on the expansion image with parameters
If , then
At the fourth stage, swap the th and th row of for obtaining
In the fifth, the first and last columns of can be computed to obtain
At the sixth stage, the other columns of and can be computed.
The diffusion and confusion of columns are related to the row, but that sequence was utilized rather than sequence . The particular computation process was projected in Algorithm 1.
| Algorithm 1: Column confusion and diffusion |
| Input: Image and pre-processed chaotic sequence Output: Image for to , , , if then end if if then , else if , , end if , , for , , end for end for |
3.2. Key Generation Process
The DOA is used for an effective key generation process. The DOA is a metaheuristic approach stimulated by the hunting behaviours of dingo. DOA is chosen for key generation due to its following advantages: high convergence, robust, global optimization, a smaller number of parameters, simplicity, and highly versatile. This strategy includes scavenging nature, attack by persecution, and assembling procedures [24]. Australian dingo dogs are in danger of extermination. Consequently, the survival rate of dingo is regarded in the DOA. The mathematical expression of DOA is given in the following. In general, dingoes meet in groups during hunting. They then find the prey location and surround it using the following equation:
In Equation (10), represents the new prey location of the searching agent, denotes the random integer generated within 2, , where SizePop indicates overall dingo population size. shows the subset of search agent where denotes the randomly generated dingo population, specifies the existing search agent, signifies the best possible searching agent attained from prior iteration, and is a consistently produced arbitrary number within [−2, 2]. Typically, dingoes hunt tiny prey and chase it till it gets caught. These characteristics are expressed as follows:
In Equation (11), describes the movement of the dingo, shows existing search agents, means best possible search agent obtained from the previous iteration, represents randomly produced numbers from the interval 1 to the size of maximal of the search agent, and shows the selected search agent, where .
Scavenger is characterized as a dingo finding meat to eat if they get a random walk in the habitat.
In Equation (12), denotes the dingo progress, has equivalent value as in Equation (12), represents the randomly generated number within [1, max_size of searching agent] interval, indicates the selected search agent, denotes the existing search agent, where , and signifies the arbitrarily created binary number. Finally, the survival rate of the dingoes is expressed as follows:
In Equation (13), and correspondingly represent poor and optimum fitness values in the present round. signifies existing fitness value of - searching agent. The survival vector in Equation (13) encompasses the normalizing fitness value within . Equation (14) is used for attaining lower survival rate.
In Equation (14), represents that search agent with minimal survival rate is upgraded. In addition, and denote the randomly produced numbers within [1, max_size of searching agent] interval, specifies best possible searching agent accomplished from previous iteration, and showing binary number of agents, with and , describes , selected searching agent, indicates the best possible searching agent accomplished from previous iteration, and shows the randomly generated number.
The set of keys is preferred by considering the “fitness function” as a max key using peak signal-to-noise ratio (PSNR) for scrambling and unscrambling data from medical images. With the help of hybrid optimization, the organization has been developed, and it is given in the following:
3.3. Blockchain Technology
The proposed BSHS-EODL technique used BC technology for secure data transmission in the medical field. A BC is distributed data where a novel time-stamped transaction is grouped and appended to a hash-chain of blocks [25]. The BSHS-EODL technique comprises a data processing section, application server for data transmission and reception, BC enabled decentralized databases, application programming interface (API) management element, and data analytics unit. A few processes which take place in the system are Create_Patient_Data, Grant_Access_ToHCP, and Revoke_Access. The structured data of the patient gets saved in the classical dataset and the unstructured data gets stored in the data warehouse. The encrypted data gets saved in the distributed BC using preferrable smart contract. After the storage of data in the allotted BC, BSHS-EODL technique uses VELM classifier for classification process. The medical image is loaded into the decentralized BC, and the BSHS-EODL technique can be employed to the data fetched from the decentralized network. The BSHS-EODL technique operates in the following way. Ethereum BC network can be employed for patient data distribution. Each individual actor carries out various activities in the network and has access to the data for which they received access. The patients can generate the information and commit the transaction. When the transactions are committed in the BC, the altered transaction is dispersed over the Internet, verifying that each data existing in the network can be accessed by every actor in the network and cannot be changed by unintentional persons. The medical personnel can access the data only when the respective user provides access permissions. Healthcare professionals can access the patient data and perform disease diagnostic processes. If the healthcare professional receives a request from the patient, they can accept it and send a request to access the data to the specific person. Upon the acceptance of the request, they investigate the medical data for disease detection purposes.
3.4. Disease Classification Model
In this work, the BSHS-EODL technique performs disease diagnosis comprising SqueezeNet, BO based parameter tuning, and VELM.
3.4.1. Feature Extraction Using SqueezeNet
To produce feature vectors, the SqueezeNet model is used in this work. SqueezeNet is a small, efficient deep neural network structure [26]. It is intended to be faster and smaller than other architectures while accomplishing higher accuracy on image classification tasks. SqueezeNet exploits a technique named “squeeze-and-excitation” to decrease the parameter count in the network, enabling it to be more effective in terms of memory and computational requirements. It was specifically designed for use on embedded and mobile devices. The SqueezeNet architecture comprises a series of layers, including the following:
- Pooling layers, decrease the spatial dimension of the feature maps.
- The input layer takes in the image dataset.
- A sequence of FC layers categorises the image based on the extracted features through the convolution layer.
- A sequence of convolutional layers extracts features from the image. This layer uses “fire modules” that comprise the “expand” layer with a larger number of filters, followed by “squeeze” layer with smaller number of filters. This enables the network to maintain fewer parameters while still extracting relevant features from the image.
The architecture also includes a dropout layer and a softmax layer. Dropout is a regularization technique that prevents overfitting by randomly dropping out some neurons during training. The softmax layer creates a probability distribution over the feasible classes used to classify the image. The SqueezeNet architecture is designed to be small and efficient, with a total of only 1.2 million parameters. This makes it better suited for use on embedded and mobile devices with limited computational resources.
Here, the BO is utilized for the hyperparameter selection of SqueezeNet. A probabilistic method of the objective function called the surrogate function can be created using BO technique [27]. Bayes’ Theorem is the core of BO technique and computes the conditional probability of event given another event ,
Bayes’ theorem is capable of being adjusted by neglecting the marginal probability from the conditional probability for optimization problem using Equation (17):
A new version of Bayes’ theorem is given as follows:
The conditional probability is a function that estimates the objective function and is utilized for sampling the searching space. The searching space in these problems is the SqueezeNet hyperparameter. BO algorithm, as an informed search technique, can be differentiated by using an acquisition function that exploits the posterior for sampling the searching area and selecting the succeeding sample to evaluate the objective function. In this study, the objective function can be denoted as a Gaussian method with the Matern 5/2 kernel. At first, random samples from the search space are exploited for determining the objective function at these samples. The assessments and samples are gathered in a consecutive way, which leads to a sequence of data points , where denotes the number of samples. The set defines the likelihood, and prior function can be described as follows:
The posterior is updated afterwards with the evaluation of prior and probability. The acquisition function, , is enhanced over the Gaussian algorithm for selecting the subsequent sample , which can be represented as follows:
In this study, the acquisition function can be executed by the expected improvement algorithm, as defined below.
In Equation (21), indicates the value of objective function for the better sample, denotes the expectation operator, and shows the better sample location in the search range. Then, the sample selected can be assessed by the objective function, and these processes are repeated until the objective function attains its least or minimum objective within the given run time.
3.4.2. Image Classification Using VELM Model
Finally, the classification of medical images is performed by the VELM model. The VELM was utilized as a classifier in this work. The VELM is a significant ML model which enhances classification accuracy while maintaining high processing speeds and robustness to noise and outliers in the input data. An ELM is a type of artificial neural network (ANN) with a single hidden layer (HL) [28]. Here, the weight that connects input to the HL and HL to biases are randomized. The weights between the output and HLs are computed by the Moore–Penrose inverse, making the training model faster. Several ELMs can be used for classification to increase detection accuracy. Each individual ELM is trained using similar data. In the process of detection, the sample is used for all the ELMs and output is computed. Based on the majority voting, the last output is computed. Assume, an ELM with activation functions and hidden neurons in HL. If there is training sample of the form , where and () then the output can be represented as
for, .
Where and denote the learning parameters of jth hidden neuron. indicates the weight vector that connects jth hidden neurons to output neurons. This can be represented as follows:
where,
The and parameters are randomly initialized for minimizing the error , where , that is independent of input dataset. The output weights can be expressed by finding the least square solution,
where the symbol characterizes the Moore–Penrose generalized inverse of matrix. It implies ELM is trained. In -ELM, - ELM is used. The equivalent number of hidden layers initialized this ELM. The learning parameter and of each ELM is initialized in a random fashion. Next, each ELM is trained on a similar dataset and the results are computed. In detection stage, a set of samples of the form is used for each ELM. The output or of every individual ELM is taken, and majority voting receives the last output. For every sample, a vector has been used for storing the class labels recognized by dissimilar ELMs. At first, is initialized to zero once an ELM output takes place; the value of equivalent location in can be raised by 1. For instance, assume output of is [1, 0] now become [1, 0]. Output of is again , then becomes . Output of is , then becomes . Once each output is reached, then the concluding output is evaluated.
4. Performance Validation
In this section, the experimental outcome of the BSHS-EODL technique is well studied on skin lesion images in the ISIC database. Figure 2 illustrates the sample images.
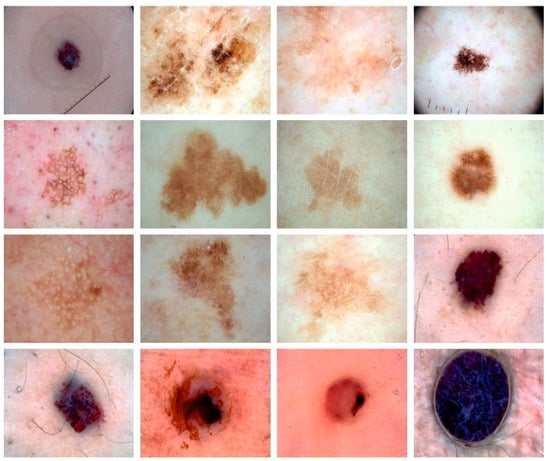
Figure 2.
Sample Images.
Figure 3 shows the histogram analysis of the BSHS-EODL technique. Figure 3a,b show the original images and their corresponding histogram images. Similarly, Figure 3c,d demonstrate the encrypted images and their respective histograms.
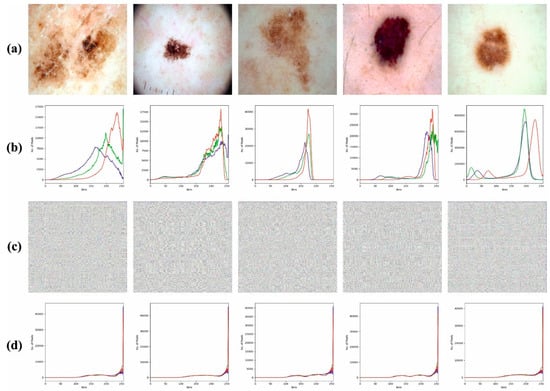
Figure 3.
(a) Original Images (b) Histogram of Original Images (c) Encrypted Images (d) Histogram of Encrypted Images.
Table 1 represents the comparative MSE and PSNR examination of the BSHS-EODL technique with existing techniques [17,29] on different images. The results indicate that the GWO and GO-PSO algorithms resulted in higher MSE values, while the GO-FFO and HOCE-ECC techniques led to considerable MSE values. However, the BSHS-EODL technique gains effective performance over other models with minimal MSE of 0.072, 0.057, 0.078, 0.102, and 0.071 under test images 1–5, respectively. The experimental outcomes indicate that the GWO and GO-PSO algorithms represented lower PSNR values than existing ones. Although the GO-FFO and HOCE-ECC models reach moderately improved PSNR values, the BSHS-EODL technique outperformed the existing models with a higher PSNR of 59.56 dB, 60.57 dB, 59.21 dB, 58.04 dB, and 59.62 dB under images 1–5 respectively.

Table 1.
MSE and PSNR analysis BSHS-EODL approach with other systems under varying images.
Table 2 shows a brief CC outcome of the BSHS-EODL system under several images. The experimental outcome stated that the GWO and GO-PSO algorithms represented lesser CC values over existing ones. However, the GO-FFO and HOCE-ECC models reach moderately enhanced CC values, and the BSHS-EODL approach outperformed the existing techniques with maximal CC of 99.42, 99.63, 99.21, 99.72, and 99.68 under images 1–5 correspondingly.

Table 2.
CC analysis of BSHS-EODL approach with other techniques under varying images.
Table 3 represents the encryption outcomes of the BSHS-EODL method with existing models under the presence of attacks in terms of computation time (CT) and PSNR. The outcome inferred that the GWO and GO-PSO algorithms resulted in higher CT values, while the GO-FFO and HOCE-ECC approaches led to considerable CT values. The BSHS-EODL algorithm attains effectual performance over other systems with minimal CT of 0.20 s, 0.13 s, 0.16 s, 0.11 s, and 0.15 s under test images 1–5 correspondingly.

Table 3.
CT and PSNR outcome of BSHS-EODL approach with other techniques under varying images.
The experimental outcomes implied that the GWO and GO-PSO algorithms represented minimal PSNR values over existing ones. However, the GO-FFO and HOCE-ECC models reached moderately greater PSNR values, and the BSHS-EODL approach outperformed the existing approaches with enhanced PSNR of 59.21 dB, 60.17 dB, 58.80 dB, 57.71 dB, and 59.31 dB under images 1–5 correspondingly.
The classification performance of the BSHS-EODL technique can be tested on the ISIC 2017 Dataset, comprising 318 samples with seven classes, as defined in Table 4.

Table 4.
Details of dataset.
The confusion matrices of the BSHS-EODL method are investigated under distinct sizes of TRS and TSS in Figure 4. The results demonstrated that the BSHS-EODL technique properly recognizes the samples under every class.
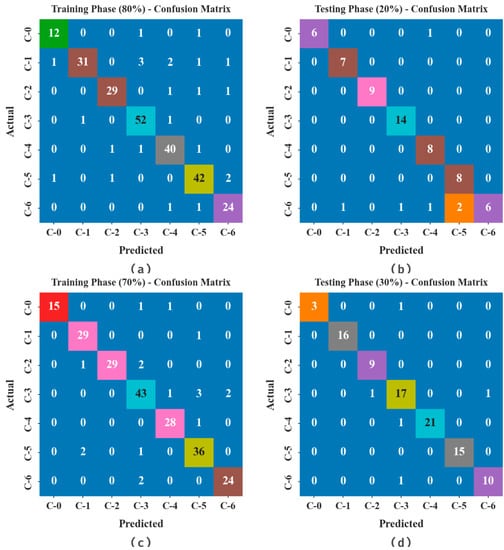
Figure 4.
Confusion matrices of BSHS-EODL approach (a,b) TRS/TSS of 80:20 and (c,d) TRS/TSS of 70:30.
In Table 5, the overall results of the BSHS-EODL technique are demonstrated. The results indicate that the BSHS-EODL technique properly classified the images under all classes. For instance, with 80% of TRS, the BSHS-EODL technique reaches average of 97.30%. In addition, with 20% of TSS, the BSHS-EODL approach attains average of 97.32%. Meanwhile, with 70% of TRS, the BSHS-EODL system attains average of 97.68%. Finally, with 30% of TSS, the BSHS-EODL algorithm obtains average of 98.51%.

Table 5.
Classifier outcome of BSHS-EODL approach with different metrics.
The training accuracy (TACY) and validation accuracy (VACY) of the BSHS-EODL method can be assessed in Figure 5. The figure inferred that the BSHS-EODL algorithm has demonstrated greater results with enhanced values of TACY and VACY. It can be noted that the BSHS-EODL system has obtained maximal TACY outcomes.
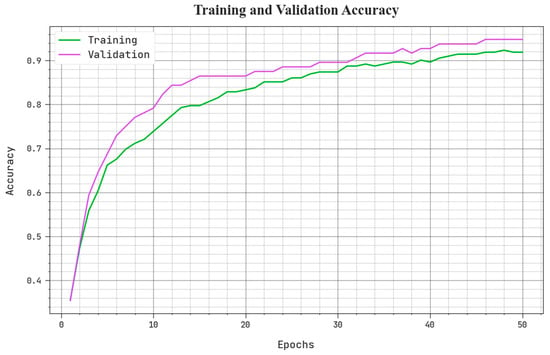
Figure 5.
TACY and VACY analysis of BSHS-EODL method.
The training loss (TLOS) and validation loss (VLOS) of the BSHS-EODL approach are tested in Figure 6. The figure stated that the BSHS-EODL approach has demonstrated higher performance with decreasing TLOS and VLOS. Evidently, the BSHS-EODL algorithm has resulted in lesser VLOS outcomes.
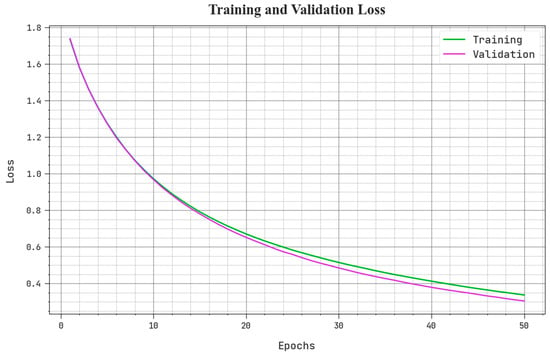
Figure 6.
TLOS and VLOS analysis of BSHS-EODL approach.
The extensive comparative study of the BSHS-EODL technique takes place in Table 6 [17,30]. The results highlighted that the VGG-19 model shows least performance, whereas the DBN and YOLO-GC techniques reported moderately similar outcomes. In comparison, the ResNet and CDNN models attain a reasonable performance.

Table 6.
Comparative outcome of BSHS-EODL method with other DL techniques.
However, the BSHS-EODL technique gains maximum classification performance with of 98.51%, of 92.98%, and of 99.11%. These outcomes ensured the betterment of the BSHS-EODL method over other existing techniques in the IoMT environment.
5. Conclusions
This article introduces a new BSHS-EODL technique for secure medical image transmission and analysis in the IoMT environment. The presented BSHS-EODL technique enables BC assisted secured image transmission and diagnosis models for the IoMT platform. The proposed method includes data classification, data collection, and image encryption. At the initial stage, the IoMT devices enable data collection processes, and the gathered images are stored in BC for security. Subsequently, image encryption is applied to encrypt the data and the key generation process is performed via the DOA. Finally, the BSHS-EODL technique performs disease diagnosis comprising SqueezeNet, BO based parameter tuning, and VELM. A comprehensive set of simulation analyses on medical datasets highlights the supremacy of the BSHS-EODL technique. In upcoming years, the performance of the proposed method can be tested on other disease diagnoses.
Author Contributions
Conceptualization, A.A.; Methodology, A.A.; Software, Y.M.A.; Validation, Y.M.A.; Formal analysis, Y.M.A.; Writing—original draft, A.A.; Writing—review & editing, Y.M.A.; Visualization, A.A.; Funding acquisition, A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research work is funded by the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia by the grant number RUP3-1.
Institutional Review Board Statement
This article does not contain any studies with human participants performed by any of the authors.
Data Availability Statement
Data sharing is not applicable to this article as no datasets were generated during the current study.
Acknowledgments
The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia, for funding this research work through project number RUP3-1.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
References
- Vaiyapuri, T.; Binbusayyis, A.; Varadarajan, V. Security, privacy and trust in IoMT enabled smart healthcare system: A systematic review of current and future trends. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 731–737. [Google Scholar] [CrossRef]
- Garg, N.; Wazid, M.; Das, A.K.; Singh, D.P.; Rodrigues, J.J.; Park, Y. BAKMP-IoMT: Design of blockchain enabled authenticated key management protocol for internet of medical things deployment. IEEE Access 2020, 8, 95956–95977. [Google Scholar] [CrossRef]
- Gul, M.J.; Rehman, A.; Paul, A.; Rho, S.; Riaz, R.; Kim, J. Blockchain expansion to secure assets with fog node on special duty. Soft Comput. 2020, 24, 15209–15221. [Google Scholar] [CrossRef]
- Kagita, M.K.; Thilakarathne, N.; Gadekallu, T.R.; Maddikunta, P.K.R. A review on security and privacy of internet of medical things. Intell. Internet Things Healthc. Ind. 2022, 171–187. [Google Scholar]
- Dai, H.N.; Imran, M.; Haider, N. Blockchain-enabled internet of medical things to combat COVID-19. IEEE Internet Things Mag. 2020, 3, 52–57. [Google Scholar] [CrossRef]
- Roshanzamir, M.; Darbandy, M.T.; Roshanzamir, M.; Alizadehsani, R.; Shoeibi, A.; Ahmadian, D. Swarm Intelligence in Internet of Medical Things. In Proceedings of the 2022 IEEE 10th Jubilee International Conference on Computational Cybernetics and Cyber-Medical Systems (ICCC), Reykjavík, Iceland, 6–9 July 2022; pp. 371–376. [Google Scholar]
- Razdan, S.; Sharma, S. Internet of medical things (IoMT): Overview, emerging technologies, and case studies. IETE Tech. Rev. 2022, 39, 775–788. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.; Mohanty, S.P. Fortified-chain: A blockchain-based framework for security and privacy-assured internet of medical things with effective access control. IEEE Internet Things J. 2021, 8, 11717–11731. [Google Scholar] [CrossRef]
- Dwivedi, R.; Mehrotra, D.; Chandra, S. Potential of Internet of Medical Things (IoMT) applications in building a smart healthcare system: A systematic review. J. Oral Biol. Craniofacial Res. 2022, 12, 302–318. [Google Scholar] [CrossRef]
- Lakhan, A.; Mohammed, M.A.; Elhoseny, M.; Alshehri, M.D.; Abdulkareem, K.H. Blockchain multi-objective optimization approach-enabled secure and cost-efficient scheduling for the Internet of Medical Things (IoMT) in fog-cloud system. Soft Comput. 2022, 26, 6429–6442. [Google Scholar] [CrossRef]
- Almaiah, M.A.; Ali, A.; Hajjej, F.; Pasha, M.F.; Alohali, M.A. A lightweight hybrid deep learning privacy preserving model for FC-based industrial internet of medical things. Sensors 2022, 22, 2112. [Google Scholar] [CrossRef]
- Khan, A.A.; Wagan, A.A.; Laghari, A.A.; Gilal, A.R.; Aziz, I.A.; Talpur, B.A. BIoMT: A state-of-the-art consortium serverless network architecture for healthcare system using blockchain smart contracts. IEEE Access 2022, 10, 78887–78898. [Google Scholar] [CrossRef]
- Abbas, A.; Alroobaea, R.; Krichen, M.; Rubaiee, S.; Vimal, S.; Almansour, F.M. Blockchain-assisted secured data management framework for health information analysis based on Internet of Medical Things. Pers. Ubiquitous Comput. 2021, 1–14. [Google Scholar] [CrossRef]
- Lakhan, A.; Mohammed, M.A.; Kozlov, S.; Rodrigues, J.J. Mobile-fog-cloud assisted deep reinforcement learning and blockchain-enable IoMT system for healthcare workflows. Trans. Emerg. Telecommun. Technol. 2021, e4363. [Google Scholar] [CrossRef]
- Lakhan, A.; Sodhro, A.H.; Majumdar, A.; Khuwuthyakorn, P.; Thinnukool, O. A lightweight secure adaptive approach for internet-of-medical-things healthcare applications in edge-cloud-based networks. Sensors 2022, 22, 2379. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Towards design and implementation of security and privacy framework for internet of medical things (iomt) by leveraging blockchain and ipfs technology. J. Supercomput. 2021, 77, 7916–7955. [Google Scholar] [CrossRef]
- Alqaralleh, B.A.; Vaiyapuri, T.; Parvathy, V.S.; Gupta, D.; Khanna, A.; Shankar, K. Blockchain-assisted secure image transmission and diagnosis model on Internet of Medical Things Environment. Pers. Ubiquitous Comput. 2021, 1–11. [Google Scholar] [CrossRef]
- Al-Otaibi, Y.D. K-nearest neighbour-based smart contract for internet of medical things security using blockchain. Comput. Electr. Eng. 2022, 101, 108129. [Google Scholar] [CrossRef]
- Uppal, S.; Kansekar, B.; Mini, S.; Tosh, D. HealthDote: A blockchain-based model for continuous health monitoring using interplanetary file system. Healthc. Anal. 2023, 3, 100175. [Google Scholar] [CrossRef]
- Zakzouk, A.; El-Sayed, A.; Hemdan, E.E.D. A blockchain-based electronic medical records management framework in smart healthcare infrastructure. Multimed. Tools Appl. 2023, 1–19. [Google Scholar] [CrossRef]
- Karthik, G.M.; Kalyana Kumar, A.S.; Karri, A.B.; Jagini, N.P. Deep intelligent blockchain technology for securing IoT-based healthcare multimedia data. Wirel. Netw. 2023, 1–13. [Google Scholar] [CrossRef]
- Miriam, H.; Doreen, D.; Dahiya, D.; Rene Robin, C.R. Secured Cyber Security Algorithm for Healthcare System Using Blockchain Technology. Intell. Autom. Soft Comput. 2023, 35, 1889–1906. [Google Scholar] [CrossRef]
- Hussain, M.; Iqbal, N.; Bashir, Z. A chaotic image encryption scheme based on multi-directional confusion and diffusion operations. J. Inf. Secur. Appl. 2022, 70, 103347. [Google Scholar] [CrossRef]
- Almazán-Covarrubias, J.H.; Peraza-Vázquez, H.; Peña-Delgado, A.F.; García-Vite, P.M. An improved Dingo optimization algorithm applied to SHE-PWM modulation strategy. Appl. Sci. 2022, 12, 992. [Google Scholar] [CrossRef]
- Maw, A.; Adepu, S.; Mathur, A. ICS-BlockOpS: Blockchain for operational data security in industrial control system. Pervasive Mob. Comput. 2019, 59, 101048. [Google Scholar] [CrossRef]
- Shafiee, M.J.; Li, F.; Chwyl, B.; Wong, A. Squishednets: Squishing squeezenet further for edge device scenarios via deep evolutionary synthesis. arXiv 2017, arXiv:1711.07459. [Google Scholar]
- Atteia, G.; Alhussan, A.A.; Samee, N.A. BO-ALLCNN: Bayesian-Based Optimized CNN for Acute Lymphoblastic Leukemia Detection in Microscopic Blood Smear Images. Sensors 2022, 22, 5520. [Google Scholar] [CrossRef]
- Kushwah, G.S.; Ranga, V. Voting extreme learning machine based distributed denial of service attack detection in cloud computing. J. Inf. Secur. Appl. 2020, 53, 102532. [Google Scholar] [CrossRef]
- Padmavathi, U.; Rajagopalan, N. Blockchain Enabled Emperor Penguin Optimizer Based Encryption Technique for Secure Image Management System. Wirel. Pers. Commun. 2022, 127, 2347–2364. [Google Scholar] [CrossRef]
- Yacin Sikkandar, M.; Alrasheadi, B.A.; Prakash, N.B.; Hemalakshmi, G.R.; Mohanarathinam, A.; Shankar, K. Deep learning based an automated skin lesion segmentation and intelligent classification model. J. Ambient Intell. Humaniz. Comput. 2021, 12, 3245–3255. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).