Abstract
The Internet of Things (IoT) and 5G networks play important roles in the latest systems for managing and monitoring various types of data. These 5G based IoT environments collect various data in real-time using micro-sensors as IoT things devices and sends the collected data to a server for further processing. In this scenario, a secure authentication and key agreement scheme is needed to ensure privacy when exchanging data between IoT nodes and the server. Recently, Cao et al. in “LSAA: A lightweight and secure access authentication scheme for both UE and mMTC devices in 5G networks” presented a new authentication scheme to protect user privacy. They contend that their scheme not only prevents various protocol attacks, but also achieves mutual authentication, session key security, unlinkability, and perfect forward/backward secrecy. This paper demonstrates critical security weaknesses of their scheme using informal and formal (mathemati) analysis: it does not prevent a single point of failure and impersonation attacks. Further, their proposed scheme does not achieve mutual authentication and correctness of security assumptions, and we perform simulation analysis using a formal verification tool to its security flaws. To ensure attack resilience, we put forward some solutions that can assist constructing more secure and efficient access authentication scheme for 5G networks.
1. Introduction
The radical development of the Internet of Things (IoT) and 5G networks in the present day has made security a demanding requirement for providing various services such as smart-healthcare, smart-home, smart-industries, etc., securely. Many IoT things devices are deployed in IoT environments to make it easy to manage and process huge real-time data to provide convenient services to the users of the 5G network. It is for this reason that 5G and IoT technology have an important role in the life of human beings because it helps in managing real-time data and to improve the quality of life of people [1]. In this situation, the exchange of data must be secure and reliable, made available only to the legitimate entities while keeping them away from the reach of malicious adversaries. IoT and mobile devices generally store secret parameters during the registration phase and then use it to authenticate among legal entities. If these devices are compromised, it can cause serious security problems because the devices have collected various data related with users such as voice, health, location, finance, etc. [2]. Therefore, research for privacy-preserving scheme is needed to ensure user and data privacy, which consider the possibility that user devices are compromised.
The results of several research works have been proposed for ensuring user privacy in IoT [3,4,5,6,7,8]. In 2016, to enhance user privacy for IoT, Park et al. proposed three factor based authentication scheme using elliptic curve cryptosystem (ECC) [3]. However, in 2017, Moon et al. [4] and Wang et al. [5] demonstrated that Park et al.’s scheme does not prevent impersonation and offilne dictionary attacks, and then they proposed a enhanced authentication and key agreement scheme to ensure secure communications in IoT environments. We et al. [6] also proposed a provable and secure user authentication scheme to resolve the common challenges and ensure the essential security properties of IoT. In 2018, Wazid et al. [7] proposed a secure user authentication with key agreement scheme for generic IoT networks. In 2019, Adavoudi-Jolfaei et al. [8] presented a lightweight three factor authentication scheme for providing access control between different groups. However, all the above-mentioned research works still have security weaknesses and do not consider the practical IoT environments.
Recently, Cao et al. [9] proposed a lightweight and secure access authentication scheme to guarantee security and privacy in 5G based IoT environments. However, this paper points out that Cao et al.’s scheme is not secure against a single point of failure and impersonation attacks. Since the secret parameters are stored as plaintext in devices, an adversary can, not only obtain public parameters but also easily get secret parameters stored in physical devices in their threat model. To resolve these security flaws, several studies [10,11,12] indicated that storing the secret parameters as plaintext is a major security weakness and it must be masked using a hash function and XOR operation. Further, we suggest a possible solution to ensure attack resilience.
The remainder of this paper is organized as follows. First, we present a review and cryptanalysis of Cao et al.’s scheme in Section 2 and Section 3. Afterward, we present a solution to ensure attack resilience and improved security in Section 4. Finally, we present a conclusion of this paper in Section 5.
1.1. Motivation and Contribution
The main purpose of this paper is to demonstrate the major security weaknesses of the LSAA scheme proposed by Cao in et al. [9]. In their scheme, an adversary can easily impersonate a legitimate user and generate a session key among entities. Therefore, we note that Cao et al.’s scheme is not secure against some attacks using informal and formal (mathematical) security analysis and does not meet essential security requirements in their threat model. We also perform the formal verification analysis using automated validation of internet security protocols and applications (AVISPA) [13] to demonstrate its security flaws, and is unsuitable for deployment in a public network. Further, we propose a solution for resolving these security weaknesses and to improve the overall security level.
1.2. Threat Model
In Cao et al.’s scheme, they adopt the Dolev-Yao (DY) threat model [14] to evaluate the security of the protocols. According to this model, an adversary can intercept, eavesdrop, insert, delete, and modify all messages transmitted between the communicating entities including user equipment (UE), machine-type communication (MTC) devices, and serving network (SN) because they communicate over a public (insecure) channel. The key generation center (KGC) is a fully trusted entity because it generates and manages the secret key for UEs and MTC devices (MDs). However, UEs and MDs are not physically protected and an adversary can obtain the data in the memory of UEs and MDs using power analysis attack [10,15,16].
2. Review of Cao et al.’s Scheme
This section succinctly reviews Cao et al.’s [9] scheme and discusses the threat model that can be used to perform cryptanalysis of their scheme. This scheme consists of four phases: system setup, registration, authentication and key agreement between UE and SN, and group access authentication and key agreement between massive MDs and SN. The notations used in this paper are presented in Table 1.

Table 1.
Notation used in this paper.
2.1. System Setup Phase
This phase is performed by KGC to setup the system parameters. The KGC generates a large prime number p and three variables (, , and ) for registered MDs, UEs, and SNs, where indicates that a is uniformly random and selected from the range . Then, KGC selects one-way hash functions and and broadcasts public parameters including , and .
2.2. Registration Phase
In this phase, SN and UE register themselves with the KGC via a secure channel to access the system. SN and UE share the secret parameters with KGC during this phase. A detailed explanation of the process is presented as follows.
2.3. SN Registration
This process is performed by the KGC through a secure channel.
- (1)
- securely sends a unique identity to KGC.
- (2)
- After receiving , the KGC generates a master key for and computes mod p using Chebyshev polynomials. Then, KGC securely sends to and broadcasts ’s public key mod p and the unique identity .
2.4. Device Registration
2.4.1. UE Registration
- (1)
- The KGC generates a master key for and a variable , computes mod p, and then securely issues the smartcard (SC) to including , mod p, and . These values are secretly shared between and the KGC.
- (2)
- The KGC computes mod and sends it to for .
- (3)
- Finally, stores mod into a database for all registered UEs.
2.4.2. MD Registration
- (1)
- The KGC chooses MTC group leader , a master key , a variable , and then generates a master key , a variable for MTC group member .
- (2)
- The KGC computes mod p and mod p using Chebyshev polynomials. The KGC securely issues SC to including the unique ’s identity , the group identity GID, the shared secret mod p and mod p between and KGC.
- (3)
- Finally, the KGC computes mod and mod , and send it to . Then stores it into a database for MTC groups.
2.5. Authentication and Key Agreement Phase between UE and SN
This phase is mutual authentication and key agreement process between UE and SN, which is performed through a public channel. A detailed description of the process is presented as follows.
- (1)
- pre-computes mod p and mod p. Then, generates and computes mod p, mod mod p, mod mod p, mod mod mod . encrypts mod mod mod by the secret parameter and sends the access request including mod } to .
- (2)
- After receiving the access request, computes mod mod p and decrypt mod p, mod p. checks whether exist in a database, If it exist, verifies that mod is correct.
- (3)
- computes mod mod p and verifies that is correct. If is correct, generates and computes mod p, mod p, mod mod , mod mod .
- (4)
- computes the session key mod mod and sends authentication request encrypted with including mod mod .
- (5)
- On receiving the authentication request, decrypt and get the mod mod . Then, computes mod mod p and verify that is correct. If it is correct, computes the session key mod mod , mod p, mod and sends to
- (6)
- Finally, verifies that is correct. If it is correct, and authenticate and correctly establish the session key each other.
2.6. Group Access Authentication and Key Agreement Phase between Massive MDs and SN
This phase refers to the group access authentication and key agreement process between MDs and SN, which is performed through a public channel. The MTC group leader aggregates the group member ’s data and sends it to SN to authenticate between group members and SN. A detailed description of the process is presented as follows.
- (1)
- The MTC device precompute mod p, mod p, mod mod p, mod mod p.
- (2)
- selects and computes mod mod p, mod p, mod mod p. Then, encrypts mod mod mod by the secret parameter and sends the access request mod p, to .
- (3)
- After receiving the access request from , computes and mod mod mod mod mod mod ), where is function of the aggregating access request for group members, and sends the aggregation request , mod p, , to .
- (4)
- On receiving the aggregation request from , computes mod mod p, decrypts and obtains mod p and . Then, checks whether and GID are exist in a database, If they exist, verifies that mod and mod are correct.
- (5)
- computes mod mod p, mod mod p and verifies that is correct. If is correct, generates and computes mod p, mod p, mod mod , mod mod .
- (6)
- computes , , using Chinese remainder theorem (CRT). Then, get mod Z. Then, computes the session key mod mod p, , , , , , , , and sends the group authentication request mod mod to .
- (7)
- decrypts mod p, computes mod mod p and mod mod p, and verifies mod .
- (8)
- If it is correct, computes mod mod p, , , , , , , , mod p, mod p and sends to .
- (9)
- On receiving the from the group members, computes and sends it to .
- (10)
- Finally, checks correctness of and authenticates with .
3. Security Weaknesses of Cao et al.’s Scheme
In this section, we demonstrate that Cao et al.’s scheme is vulnerable to MD and UE impersonation attacks as well as a single point of failure. Further, we also show that Cao et al.’s scheme does not achieve secure mutual authentication and session key security, which is a necessary security requirement for authentication and key agreement scheme.
3.1. Formal Security Analysis
We prove that Cao et al.’s scheme does not achieve the session key security using Real-or-Random (ROR) model [17] which is broadly accepted formal proof [18,19,20]. We first present the basic concept of ROR model, and then perform the formal security analysis through this proof.
- Participants We denote and as the instance and of UE and SN, respectively.
- Accepted state After exchanging the last messages, the oracle moves to an accepted state. When all the messages are concatenated in order, a current session identifier of is defined.
- Partnering When and are in the shared same and the accepted state, and then complete mutual authentication and key agreement, and are defined as partners.
- Freshness To perform the ROR proof, the instances (, ) are considered fresh if the session key between UE and SN is not compromised to attacker A at present.
- Attacker Under the threat model of Cao et al. [9], an A has a complete control over the communication network. A also access to the queries presented in Table 2 to break the security of Cao et al.’s scheme.
 Table 2. Queries and descriptions.
Table 2. Queries and descriptions. - Semantic Security Under the this model, A attempt to find an instance’s correct session key from a random nonce. A has to utilize the ROR queries, and then guesses a bit c. When A correctly find a bit c, A win the game ans destroy the semantic security of protocol. We define that is event of winning the game by A and is advantage in breaking the session key of Cao et al.’s scheme P.
- Random Oracle In Cao et al.’s scheme, all participants can utilize a random oracle which is a one-way hash function H.
Here, we prove that Cao et al.’s scheme does not achieve the session key security by the following Definition 1 and Theorem 1.
Definition 1.
Chaotic Map-based Discrete Logarithm Problem (CMDLP): Given x and y, it is computationally hard to find integer i such that mod .
Theorem 1.
Suppose that A is an adversary running in a polynomial time t against LASS and is the advantage of A in breaking the session key security of Cao et al.’s scheme. Then,
where , , and denote the number of queries, is a one-way hash function H, and is the breaking advantage of CMDLP by A, respectively.
We define the following games with the event in which A wins the game . The formal proofs using ROR model are below:
- Game : This game is a direct attack by A against the protocol. The c is first randomly selected at the beginning of this game and its winning advantage is:
- Game : This game is an eavesdropping attack by A which A can control the all the exchanged messages using query. After that, A executes the query to find whether its output is a correct or a random value. In Cao et al.’s scheme, UE and SN exchange the session key which is computed by mod mod and mod mod . If A want to correctly guess it, A must break the difficulty of solving CMDLP. However, A should get the temporary private key of UE and SN from the . It is computationally hard to find the temporary private key because the ’s security is based on the difficulty of solving CMDLP. Thus, and are indistinguishable. Then,
- Game : Finally, A performs the final attack and tries to impersonate the legal UE and SN using , and some queries. A execute the query, and then extract the values and stored in the memory of UE and SN. A successfully break the session key security using the obtained private key because A can properly proceed the authentication and key agreement phase without solving the CMDLP. Therefore, and are distinguishable. Then,
After finishing all the games (, A tries to correctly find the c using query. Therefore,
Then, we obtain the final result by multiplying 2 both sides of (7):
Finally, we can remove the probability in Equation (8) because we break the session key security without solving the CMDLP. Therefore, we prove that Cao et al.’s scheme does not achieves the session key security using this formal proof.
3.2. Informal Security Analysis
We demonstrate that Cao et al.’s scheme does not resist impersonation attacks and single point of failure, and also does not ensure secure mutual authentication using informal analysis.
3.2.1. UE Impersonation Attack
During UE registration phase, the UE receives SC , mod p, from KGC. According to Section 1.2, Cao et al. present the threat model and analyze security of the proposed scheme using their threat model. However, if a malicious attacker A compromise the UE and extracts the data stored in the UE’s memory, A can successfully generate the access request mod } and the response message because the secret data of the UE’s memory is directly stored without employing any cryptographic method. Further, A can also generate the session key . Therefore, their scheme is vulnerable to UE impersonation attacks and a detailed description of the processed involved in this attack is shown in Figure 1.
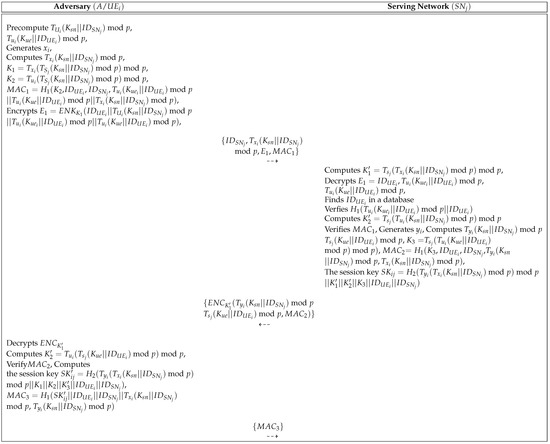
Figure 1.
UE impersonation attack in Cao et al.’s scheme.
3.2.2. MD Impersonation Attack
In the MTC device (MD) registration phase, the MD received SC = mod p, mod p} from KGC, where , GID, mod p, mod p are the unique ’s identity, the group identity GID, the shared secret between and KGC, respectively. When an adversary A obtains the and extracts these secret parameters, A can not only access the serving network but also generate the session key between and . Hence, Cao et al.’s scheme does not prevent MD impersonation attack and for a detailed description of the processes involved in this phase, please refer to [9].
3.2.3. Secure Mutual Authentication
According to Section 3.2.1 and Section 3.2.2, an adversary A can easily access the system proposed by Cao et al.’s scheme and authenticate among entities. Additionally, A can generate the session key between UE/SN and MTD devices/SN. Thus, their scheme does not achieve secure mutual authentication.
3.2.4. Single Point of Failure
In Cao et al.’s scheme, the MTC group leader collects the access request of the group member and aggregates it. Afterward, sends the aggregation messages of an access request to serving network . However, if node is compromised, off-line or break down, the access request of massive MTC nodes cannot be delivered to . It limits the security and the performance of the proposed system. Therefore, Cao et al.’s scheme does not offer resistance against a single point of failure attack because the massive MTC nodes cannot be able to access the service when does not work.
3.2.5. Correctness of Security Assumption
Cao et al. presented a threat model to analyze the security of the scheme, and then claimed that their scheme is secure against various attacks on the presented threat model. However, we demonstrate that Cao et al.’s scheme is vulnerable to the above-mentioned attacks using their threat model and that they did not consider all potential attacks. Thus, we suggest a solution to alleviate the said security flaws in Section 4.
3.3. Simulation Analysis Using AVISPA Tool
This section perform the formal simulation analyis uisng AVISPA tool which is a widely-accepted validation tool for proving security of cryptographic protocols [13,21]. AVISPA verifies that cryptograhpic protocols is secure against replay and man-in-the-middle attacks. It uses a high-level protocols specification language (HLPSL) [22] to construct the security features of the protocols. There are four back-ends models [23]: “constraint logic-based attack searcher (CL-AtSE)”, “on the fly model checker (OFMC)”, “SAT-based model checker (SATMC)”, and “tree automata based on protocol analyzer (TA4SP)”. The constructed HLPSL code is converted to a intermediate format (IF) using a translator “HLPSL2IF”, and then it is utilized for four back-ends to prove security. Finally, the output presents results of security analysis. This process is presented in Figure 2 and the detailed description of HLPLS can be found in [21,22].

Figure 2.
The Process of AVISPA Simulation.
3.3.1. HLPLS Specifications
Before the beginning of simulation proof, all the phases of Cao et al.’s scheme are defined through the HLPLS. We then have tested it under two scenarios (UE-SN and MD-SN), considering UE-SN and MD-SN authentication phases.
Scenario 1. UE-SN Authentication: In scenario 1, there are three basic roles (SN, UE, KGC) and the HLPSL descriptions of each role are shown in Figure 3, Figure 4 and Figure 5, respectively. The session and environment are defind in Figure 6.

Figure 3.
Scenario 1: HLPSL description of SN role.

Figure 4.
Scenario 1: HLPSL description of UE role.

Figure 5.
Scenario 1: HLPSL description of KGC role.

Figure 6.
Scenario 1: HLPSL description of session and environment.
Scenario 2. MD-SN Authentication: In scenario 2, there are four basic roles (SN, MD, MD, KGC) and the HLPSL descriptions of each role are shown in Figure 7, Figure 8, Figure 9 and Figure 10, respectively. The session and environment are defined in Figure 11.

Figure 7.
Scenario 2: HLPSL description of SN role.

Figure 8.
Scenario 2: HLPSL description of MD role.

Figure 9.
Scenario 2: HLPSL description of MD role.

Figure 10.
Scenario 2: HLPSL description of KGC role.

Figure 11.
Scenario 2: HLPSL description of session and environment.
3.3.2. Simulation Results
To demonstrate that Cao et al.’s scheme is not secure against replay and man-in-the-middle attacks, we simulated the OMFC and CL-AtSe using the pre-defined HLPLS of scenario 1 and 2.
Simulation Result of Scenario 1: Under the OFMC back-ends, the search depth is 3 when 3 nodes have been searched in 0.8 s. Under the CL-AtSe, the translation time is 0.05 s and 2 states are analyzed.
Simulation Result of Scenario 2: Under the OFMC back-ends, the search depth is 3 when 3 nodes have been searched in 0.2 s. Under the CL-AtSe, the translation time is 0.02 s and 2 states are analyzed.
Figure 12 and Figure 13 and present the results of OFMC and CL-AtSe back-ends, which presents “UNSAFE”. Therefore, the scenario 1 and 2 are not secure against replay and man-in-the-middle attacks.

Figure 12.
Simulation result of Scenario 1.

Figure 13.
Simulation result of Scenario 2.
4. Security Fixes
In Cao et al.’s scheme [9], the major security issues is that the secret parameters are stored in a smartcard (SC) or memory of devices without applying any cryptographic method. An adversary can easily extract and obtain the secret parameters using power analysis because of this problem. It makes the scheme vulnerable to a single point of failure, UE impersonation, MD impersonation attacks, inability to achieve secure mutual authentication and to exhibit a wrong threat model. These major security issues are discussed in Section 3.
In the last decades, several authentication and key agreement protocols have been designed to ensure user and data privacy. These protocols store the secret parameters in the memory of devices such as UE, micro-sensor, smartcard, etc., which use it to authenticate and establish the session key between entities. Like other studies, Cao et al. proposed the LSAA scheme using the same approach. However, according to Cao et al.’s threat model, we assume that an adversary can easily compromise the physical IoT devices and extract the sensitive data stored in the memory of the devices. Although Cao et al. realized that an adversary can easily compromise IoT devices, they did not consider these problems in the design of their proposed protocol.
Herein, we suggest the necessary guidelines to mitigate the security weaknesses of the Cao et al.’s scheme.
- Fix 1.
- In the registration phase of Cao et al.’s scheme, the KGC should not issue the secret parameters as plaintext to prevent stolen device attacks. The UE and MD should store the secret parameters in encrypted form using XOR operation and a hash function.
- Fix 2.
- The LSAA scheme adopts the two-factor authentication technique using smartcard and secret parameters. However, the LSAA scheme does not verify whether UE and MD are from a legitimate entity that has the same security as the one-factor authentication scheme. Thus, the UE and MD need to ensure that the user is a legitimate user using a password or biometrics to improve the security level. We suggest the three-factor authentication with biometrics using a fuzzy extractor [24]
- Fix 3.
- In the Cao et al.’s scheme, the KGC selects only one MTC group leader per group and this leads to a single point of failure attack. The KGC recodes the group leader list and related parameters in a blockchain to ensure that all members can freely access the leader of other groups. This prevents the issue of a single point of failure attack because the group members can freely access other group leaders when there is a problem with its group leader.
In these suggested solutions, the UE, and MD impersonation attacks can be mitigated and we do not assert that our suggested solutions are perfect against the above-mentioned security issues. However, it will definitely improve the security of the system and increase the attack complexity for an adversary.
Cao et al. did well by designing a novel group access authentication scheme in 5G networks. However, they would have looked at their scheme from various angles. Bringing improvements in a field of study is a difference in the individual approaches of researchers. Surely, this paper will bring about awareness of the need to design a secure and efficient authentication scheme for IoT environments.
5. Conclusions
This paper refers to “LSAA: A lightweight and secure access authentication scheme for both UE and mMTC devices in 5G networks”. We demonstrated that Cao et al.’s scheme is vulnerable to single point of failure and impersonation attacks, does not provide secure mutual authentication, and does not meet the security requirement of their proposed threat model. Moreover, we prove that their scheme does not achieve the session key security using formal (mathematics) analysis, and perform the simulation test using AVISPA tool to demonstrate their security weakneeses. The above-mentioned security flaws make Cao et al. scheme inappropriate and impractical to utilize. Thus, we suggested ways of improving the security level which can lead to a more secure and efficient scheme for 5G based IoT environments.
Author Contributions
Conceptualization, K.P.; methodology, K.P.; validation, K.P.; formal analysis, K.P.; writing—original draft preparation, K.P.; writing—review and editing, Y.P.; supervision, Y.P.; project administration, Y.P. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Electronics and Telecommunications Research Institute (ETRI) grant funded by the Korean government [22ZR1330, Research on Intelligent Cyber Security and Trust Infra].
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chettri, L.; Bera, R. A Comprehensive Survey on Internet of Things (IoT) Toward 5G Wireless Systems. IEEE Internet Things J. 2020, 7, 16. [Google Scholar] [CrossRef]
- Lopez-Ballester, J.; Pastor-Aparicio, A.; Felici-Castell, S.; Segura-Garcia, J.; Cobos, M. Enabling Real-Time Computation of Psycho-Acoustic Parameters in Acoustic Sensors Using Convolutional Neural Networks. IEEE Sens. J. 2020, 20, 11429. [Google Scholar] [CrossRef]
- Park, Y.; Park, Y. Three-Factor User Authentication and Key Agreement Using Elliptic Curve Cryptosystem in Wireless Sensor Networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Moon, J.; Lee, D.; Lee, Y.; Won, D. Improving Biometric-Based Authentication Schemes with Smart Card Revocation/Reissue for Wireless Sensor Networks. Sensors 2017, 17, 940. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wang, C.; Xu, G.; Sun, J. An Enhanced Three-Factor User Authentication Scheme Using Elliptic Curve Cryptosystem for Wireless Sensor Networks. Sensors 2017, 17, 2946. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A privacy-preserving and provable user authentication scheme for wireless sensor networks based on Internet of Things security. J. Ambient Intell. Hum. Comput. 2017, 8, 101–116. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Adavoudi-Jolfaei, A.; Ashouri-Talouki, M.; Aghili, S.F. Lightweight and anonymous three-factor authentication and access control scheme for real-time applications in wireless sensor networks. Peer-Peer Netw. Appl. 2019, 12, 43–59. [Google Scholar] [CrossRef]
- Cao, J.; Yan, Z.; Ma, R.; Zhang, Y.; Fu, Y.; Li, H. LSAA: A Lightweight and Secure Access Authentication Scheme for Both UE and mMTC Devices in 5G Networks. IEEE Internet Things J. 2020, 7, 5329. [Google Scholar] [CrossRef]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smartcard security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541. [Google Scholar] [CrossRef] [Green Version]
- Sureshkumar, V.; Amin, R.; Obaidat, M.S.; Karthikeyan, I. An enhanced mutual authentication and key establishment protocol for TMIS using chaotic map. J. Inf. Secur. Appl. 2020, 53, 102539. [Google Scholar] [CrossRef]
- Xiong, H.; Kang, Z.; Chen, J.; Tao, J.; Yuan, C.; Kumari, S. A novel multiserver authentication scheme using proxy resignature with scalability and strong user anonymity. IEEE Syst. J. 2020, 2, 2156. [Google Scholar] [CrossRef]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://people.irisa.fr/Thomas.Ge\net/span/ (accessed on 8 April 2022).
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198. [Google Scholar] [CrossRef]
- Eisenbarth, T.; Kasper, T.; Moradi, A.; Paar, C.; Salmasizadeh, M.; Shalmani, M.T.M. On the power of power analysis in the real world: A complete break of the KEELOQ code hopping scheme. In Advances in Cryptology–CRYPTO; Springer: Heidelberg, Germany, 17–21 August 2008; pp. 203–220. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology–CRYPTO; Springer: Heidelberg, Germany, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC’05), Lecture Notes in Computer Science (LNCS), Les Diablerets, Switzerland, 23–26 January 2005; pp. 65–84. [Google Scholar]
- Yu, S.; Lee, J.; Park, K.; Das, A.K.; Park, Y. IoV-SMAP: Secure and Efficient Message Authentication Protocol for IoV in Smart City Environment. IEEE Access 2020, 8, 167875. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Das, A.K.; Park, Y. BPPS: Blockchain-Enabled Privacy-Preserving Scheme for Demand-Response Management in Smart Grid Environments. IEEE Trans. Dependable Secur. Comput. 2022. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N.J. Anonymous Lightweight Chaotic Map-based Authenticated Key Agreement Protocol for Industrial Internet of Things. IEEE Internet Things J. 2020, 17, 1133. [Google Scholar] [CrossRef]
- Park, K.; Noh, S.; Lee, H.; Das, A.K.; Kim, M.; Park, Y.; Wazid, M. LAKS-NVT: Provably Secure and Lightweight Authentication and Key Agreement Scheme without Verification Table in Medical Internet of Things. IEEE Access 2020, 8, 119387. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project avispa. In Proceedings of the APPSEM 2005 Workshop, Tallinn, Finland, 13–15 September 2005; pp. 1–2. [Google Scholar]
- Vigano, L. Automated Security Protocol Analysis with the AVISPA Tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61. [Google Scholar] [CrossRef] [Green Version]
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. SIAM J. Comput. 2008, 38, 97. [Google Scholar] [CrossRef] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).