Abstract
With the development in wireless communication and low-power device, users can receive various useful services such as electric vehicle (EV) charging, smart building, and smart home services at anytime and anywhere in smart grid (SG) environments. The SG devices send demand of electricity to the remote control center and utility center (UC) to use energy services, and UCs handle it for distributing electricity efficiently. However, in SG environments, the transmitted messages are vulnerable to various attacks because information related to electricity is transmitted over an insecure channel. Thus, secure authentication and key agreement are essential to provide secure energy services for legitimate users. In 2019, Kumar et al. presented a secure authentication protocol for demand response management in the SG system. However, we demonstrate that their protocol is insecure against masquerade, the SG device stolen, and session key disclosure attacks and does not ensure secure mutual authentication. Thus, we propose a privacy-preserving lightweight authentication protocol for demand response management in the SG environments to address the security shortcomings of Kumar et al.’s protocol. The proposed protocol withstands various attacks and ensures secure mutual authentication and anonymity. We also evaluated the security features of the proposed scheme using informal security analysis and proved the session key security of proposed scheme using the ROR model. Furthermore, we showed that the proposed protocol achieves secure mutual authentication between the SG devices and the UC using Burrows–Abadi–Needham (BAN) logic analysis. We also demonstrated that our authentication protocol prevents man-in-the-middle and replay attacks utilizing AVISPA simulation tool and compared the performance analysis with other existing protocols. Therefore, the proposed scheme provides superior safety and efficiency other than existing related protocols and can be suitable for practical SG environments.
1. Introduction
In the past few years, with the advances of information and communication technologies, users can easily access any service provided in various smart grid (SG) environments, including smart home, smart building, vehicle-to-grid (V2G) and advanced metering infrastructure (AMI) [1,2,3,4]. In particular, smart grid using smart device has attracted growing attention from the academia, industries, and researchers. The SG device (sensing device, smart meter, etc.) is one of the core components, which collects various information (electricity consumption, payment, address, etc.) and transfers it to utility centers (power provider, power distributor, etc.) to provide secure, reliable, and efficient power distribution. According to the report of the U.S. Department of Energy (DoE), since 1988, electricity demand has risen by almost 30%. However, the transmission capacity of electricity has only increased by 15% [5]. Therefore, demand-response management has become an important issue to ensure reliable supply of electricity.
In SG environments, the SG devices are deployed in industries, smart buildings, smart homes, etc. and collect many data in real-time, transferring electricity demands to energy generators. However, energy generators cannot efficiently handle these demands because the data collected by SG devices is very large and is difficult to handle it. To address these problems and maintain the efficient stability of supply, utility centers (UCs) analyze the data collected by SG devices and control fault detection, dynamic pricing, load balancing, leakage power, and demand-response [6]. However, the data transmitted between the UC and the SG devices can be tampered, injected, deleted, and forged by a malicious adversary because they are transmitted over an insecure channel [7]. The result of these situations can generate energy imbalances and gaps between energy demand and response. Therefore, authentication and key agreement mechanisms have become essential security requirements for smooth functioning of the SG operations with respect to demand response and data analytics. The security requirements for the SG system are summarized as follows:
- Secure and efficient authentication and key agreement protocols are essential to ensure secure communication and privacy.
- The proposed authentication and key agreement protocol must withstand various attacks such as replay, masquerade, and off-line identity guessing attacks.
- Authentication and key agreement protocol should consider SG device limitations with respect to power consumption, communication bandwidth, and memory.
In general, for power consumption feedback purposes, a SG relies heavily on the usage of a smart metering infrastructure. For instance, the data of SG device is useful for load forecasting, demand response management, and real-time pricing. However, the recording and transmission of power consumption data may cause serious privacy issues. If fine-grained power consumption data of the SG device is exposed, it can reveal the private information of consumers related to their daily routines or the appliances in the house. In addition, the computation and communication resources at the consumer’s side in the SG environments are usually very limited. Therefore, secure and efficient authentication mechanisms for preserving user privacy with low computational costs are essential in resource-constrained SG environments.
In 2019, Kumar et al. [6] proposed an elliptic curve cryptography (ECC)-based authentication protocol for demand response management in SG system. Kumar et al. claimed that their scheme can prevent various attacks. However, this paper shows that their scheme cannot withstand various attacks, including SG device stolen, session key disclosure, and masquerade attacks and cannot ensure secure mutual authentication. Furthermore, their scheme [6] is not suitable for resource-limited smart devices because it uses ECC with high computation and communication overheads. Therefore, we propose a privacy-preserving lightweight authentication scheme for demand response management in SG environments, considering an efficiency of SG devices and improving security level.
1.1. Adversary Model
We adopted the widely known Dolev–Yao (DY) threat model [8] to evaluate the safety of proposed protocol. According to the DY model, a malicious attacker can intercept, delete, modify, and insert the transmitted data over insecure channel. In addition to the capabilities of these attackers, the specific assumptions of the threat model are as follows:
- A malicious adversary can steal or obtain the SG device of a legal user and can extract secret parameters stored in the SG device utilizing power-analysis [9,10]. We also assume that a malicious adversary is able to capture as many SG device as possible.
- A malicious adversary may attempt various attacks, including masquerade, man-in-the-middle (MITM), session key disclosure, and replay attacks [11,12].
- Trusted authority (TA) and UCs are assumed to be fully trusted and semi-trusted entities, respectively, and cannot be compromised by a malicious adversary.
1.2. Contributions
The detailed contributions in this paper are summarized as follows:
- We demonstrate that Kumar et al.’s protocol cannot withstand various attacks such as masquerade, SG devices stolen, and session key disclosure attacks. We also show that their protocol does not ensure secure mutual authentication.
- We present a privacy-preserving lightweight authentication protocol for the SG system using pseudo-identity and secret parameter to enhance the security weaknesses of Kumar et al.’s protocol. The proposed protocol can withstand against masquerade, session key disclosure, replay, and MITM attacks, as well as achieve secure mutual authentication and anonymity. Thus, the proposed protocol is more secure and efficient than Kumar et al.’s protocol because it utilizes only hash and XOR operations.
- We performed the widely known Burrows–Abadi–Needham (BAN) logic analysis [13] to prove that the proposed scheme provides secure mutual authentication. We utilized informal security analysis to prove the safety of the proposed protocol against potential attacks and also proved the session key security of proposed scheme utilizing ROR model [14].
- We performed formal security analysis utilizing the widely adopted Automated Validation of Internet Security Protocols and Applications (AVISPA) tool to evaluate that the proposed scheme is secure against replay and MITM attacks. Moreover, we present the performance analysis of the proposed protocol with existing protocols.
1.3. Organization
The rest of the article is organized as follows. Section 2 presents related works that discuss the SG environments and then Section 3 presents system model for the SG environments. In Section 4 and Section 5, we review of Kumar et al.’s scheme and analyze its security problems. In Section 6, we present a privacy-preserving lightweight authentication protocol for demand response management in SG environments to address the security shortcomings of Kumar et al.’s scheme and enhance efficiency. In Section 7, we perform the security analysis of the proposed scheme utilizing informal and formal analysis. Section 8 evaluates the security and performance features of the proposed scheme compared with existing schemes. Finally, we summarize the conclusion in Section 9.
2. Related Works
Many authentication and key agreement schemes for various environments have been presented over the last few years to ensure security and privacy of users [15,16,17]. In 2014, Rottondi et al. [15] presented the security and privacy scheme in V2G communication. In 2016, Jiang et al. [16] presented an ECC-based three-factor authentication scheme for e-health cloud to ensure privacy of health information. In 2016, Wan et al. [17] presented an efficient privacy-preserving scheme in the SG environments to provide secure communication and guarantee user’s anonymity.
Recently, SG has attracted much attention from academia, research institutes, industry, and government [18,19]. In 2016, Tsai and Lo [20] presented identity-based encryption and signature key distribution protocol for the SG. However, in 2016, Odelu et al. [21] showed that Tsai and Lo’s scheme [20] does not protect against ephemeral secret leakage attack and cannot ensure the privacy of smart meter. To resolve security drawbacks of Tsai and Lo’s scheme, Odelu et al. [21] presented a secure authentication key agreement scheme for SG. In 2015, Doh et al. [22] proposed a secure authentication scheme between smart meter and the utility system to manage information of power consumption. In 2016, Saxena et al. [23] presented an authentication scheme for SG, which performs secure user authentication for SG to provide protection against various attacks. In 2016, He et al. [24] presented ECC based lightweight anonymous key distribution scheme for SG and it was more efficient than Tsai and Lo’s scheme [20]. In 2017, Wazid et al. [25] presented secure three-factor remote user authentication scheme for renewable energy in SG system to enhance security level. In 2019, Kumar et al. [6] presented ECC-based authentication protocol for demand response management in SG system. However, as shown below, their scheme cannot prevent a variety of attacks such as SG device stolen, masquerade, and session key disclosure attacks, and it cannot ensure secure mutual authentication. Thus, we present a privacy-preserving lightweight authentication protocol for demand response management in the SG environments to address security problems of Kumar et al.’s scheme.
3. System Model
This section introduces the demand response management for the SG network model. This network model comprises two entities: a SG device and an UC, as shown in Figure 1. A SG device collects electricity data and provides efficient power management services. An UC manages monitoring data, including electricity consumption, load forecasting, demand response, real-time pricing, etc. The UC collects these data and estimates a total electricity capacity of a SG device in the power grid. However, as SG devices are deployed within the SG fields, the recording and transmission of power consumption data may cause serious privacy issues. A SG device usually sends sensitive power consumption reports via communication channel in the SG environments. A malicious adversary can intercept such reports to invade the privacy of users. For instance, it is easy to notice that inhabitants are at home or not by checking the power usage. In addition, privacy-sensitive data, such as usage of appliances, can be released to adversaries [26,27]. Consequently, privacy of users could be violated and sensitive data of users could be used for criminal purposes. Therefore, privacy-preserving authentication protocol in the SG environments should be supported.
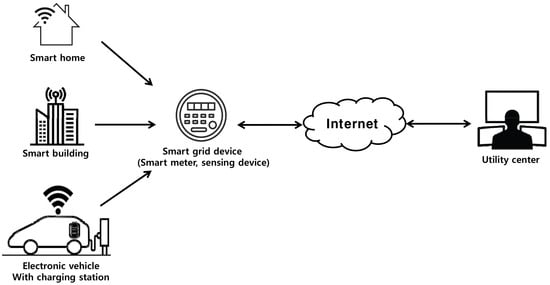
Figure 1.
Network model for smart grid environments.
Figure 2 introduces the authentication process of the proposed scheme in the SG environments to provide user privacy, including daily routines and electricity consumption habits. The proposed scheme comprises three parties: trust authority (TA), SG device, and UC. The SG device and the UC first register their identities to TA, and then TA issues credential information for the SG device and the UC. After that, the SG device and the UC perform mutual authentication. After authentication, the SG device and the UC use the session key to exchange power consumption reports and feedbacks, and so on. Consequently, they can communicate safely through the secure channel established by the session key. The meaning of the communication session involves identifying devices in the network and authorizing what each device should carry out in the network. The maintenance of communication session in the proposed scheme may change monthly or yearly, depending on security requirements.
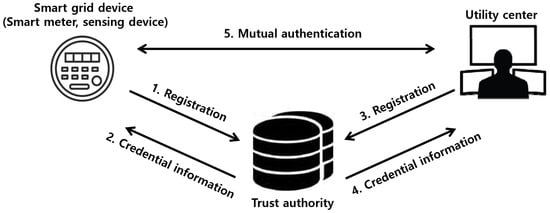
Figure 2.
Authentication process of the proposed scheme in smart grid environments.
4. Review of Kumar et al.’s Protocol
This section reviews Kumar et al.’s authentication protocol for SG system. Kumar et al.’s scheme is comprised of five phases: SG device registration, UC registration, authentication, dynamic SG device addition, and dynamic UC additions. Table 1 summarizes the notation used in the protocol.

Table 1.
Notations.
4.1. Smart Grid Device Registration Process
The SG device is called , where n is the number of to be deployed initially in SG system. The must register with to receive any services, where n is the number of the SG devices. A trusted authority chooses a and calculates and , where is the registration timestamp of the SG device. After that, the pre-loads the data into memory before deployment in SG system. Figure 3 describes the SG device registration process of Kumar et al.’s protocol.
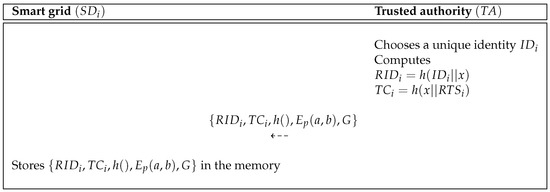
Figure 3.
Smart grid device registration process of Kumar et al.’s scheme.
4.2. Utility Center Registration Process
The utility center must register with to deploy the SG environments. The is called , where k is the number of to be deployed initially in SG system. chooses an identity and calculates and , where is the registration timestamp of the UC. Finally, the pre-loads the data into memory before deployment in SG system. Figure 4 describes the UC registration process of Kumar et al.’s protocol.

Figure 4.
Utility center registration process of Kumar et al.’s scheme.
4.3. Authentication Process
The main goal of this process is to negotiate a session key between and . Therefore, the and must authenticate each other. Figure 5 describes the authentication process of Kumar et al.’s protocol. The detailed process is described below.

Figure 5.
Authentication process of Kumar et al.’s scheme.
- Step 1:
- chooses a random number and generates a current timestamp . After that, computes and and sends authentication request message to the over insecure channel.
- Step 2:
- After receiving the message, checks , where is maximum transmission delay bound and is current timestamp. If the condition is valid, computes utilizing the corresponding of stored in the database.
- Step 3:
- then generates timestamp and a random number , and calculates , , the session key shared with as , and . After that, sends the authentication message to the over insecure channel.
- Step 4:
- After receiving the message, checks condition . If it is correct, further calculates , and session key shared with as , . If the condition , aborts communication. Otherwise, generates a timestamp and calculates . After that, sends acknowledgment message to the over insecure channel.
- Step 5:
- After receiving the message, checks the condition . If the condition is valid, computes and checks if holds. If the condition is valid, and store the common session key .
4.4. Dynamic Smart Grid Device Addition Process
The main goal of this process is adding a new SG device to provide flexibility in the system and the detailed processes are shown below.
- Step 1:
- Trusted authority selects an identity and calculates and .
- Step 2:
- After that, the pre-loads the data in the memory before it is deployed.
- Step 3:
- sends data for to all over secure channel. The needs to broadcast messages to the deployed regarding deployment of the so that and deployed can establish a common session key after mutual authentication.
4.5. Dynamic Utility Center Addition Process
The main goal of this process is same as the one in Section 4.4 from the point of view of UC and the detailed processes are shown below.
- Step 1:
- The selects a identity and calculates and .
- Step 2:
- then pre-loads the data in the memory before it is deployed.
- Step 3:
- If a is already deployment prior to , pre-loads into the memory of .
After finishing this process, broadcasts a completion statement to all entities and is successfully registered in SG environments.
5. Cryptanalysis of Kumar et al.’s Protocol
This section demonstrates the security drawbacks of Kumar et al.’s protocol, including SG device stolen, masquerade, and session key disclosure attacks, as well as mutual authentication.
5.1. Masquerade Attack
We assume that a malicious adversary can obtain the SG device of legal user and intercept information transmitted in open channel, and then may attempt to masquerade . According to Section 1.1, can extract secret information using power analysis attack. Finally, performs the masquerade attack as below:
- Step 1:
- generates a random number and calculates , . After that, sends message to over insecure channel.
- Step 2:
- After receiving the message from , checks . If the condition is valid, calculates and generates a timestamp . then selects a random number and computes , , , , and . After that, sends the message to .
- Step 3:
- After receiving the message from , checks condition . If the condition is valid, computes , , and . Then, generates a timestamp and computes . After that, sends message to over insecure channel.
- Step 4:
- After receiving the message from , checks condition . If the condition is valid, calculates and checks if holds. If the condition is valid, and store session key .
Therefore, can successfully generate a session key between and and send a legitimate authentication request message. Consequently, we show that Kumar et al.’s protocol does not withstand masquerade attack.
5.2. Smart Grid Device Stolen Attack
Kumar et al. claimed that their scheme could withstand SG device stolen attack because a malicious attacker cannot calculate the correct and without knowing secret key x of the . However, according to Section 5.1, we demonstrate that successfully impersonates legitimate user and calculates the session key. Therefore, Kumar et al.’s protocol is insecure against SG device stolen attack.
5.3. Session Key Disclosure Attack
In Kumar et al.’s scheme, they claimed that their scheme was secure against session key disclosure attack, although the secret numbers u and v are compromised to . According to the Kumar et al’s scheme, cannot obtain session key because does not know parameters and . However, in Section 5.1, we demonstrate that can successfully generate session key using parameters obtained from SG devices of a legitimate user. Therefore, once a SG device is compromised, all its previous communications will be breached. Furthermore, since the malicious attacker can capture as many SG devices as possible, the can obtain the session key of other SG devices. As a result, Kumar et al.’s protocol cannot defend against session key disclosure attack.
5.4. Mutual Authentication
Kumar et al. showed that their scheme could achieve secure mutual authentication between and . However, according to Section 5.1, can successfully compute authentication request message and response message . Consequently, Kumar et al.’s scheme does not achieve secure mutual authentication.
6. Proposed Scheme
This section proposes a privacy-preserving lightweight authentication scheme for demand response management in the SG environment to overcome various security drawbacks of Kumar et al.’s protocol [6]. In our scheme, the general data flow of the SG system model in public channel is the same as Kumar et al.’s scheme [6]. The proposed scheme is composed of seven process: pre-deployment, SG registration, UC registration, authentication, dynamic SG device addition, and dynamic UC addition.
6.1. Pre-Deployment Process
In this section, the SG devices and must register with before its deployment in SG environments. firstly selects unique identities and of and , respectively. Then, stores the credential information in the memory of and stores the credential information in the database of prior to its deployment in the SG environments.
6.2. Smart Grid Device Registration Process
The must register with trusted authority to receive the power management services. Figure 6 describes the SG device registration process of proposed scheme and the steps of this process are given below.
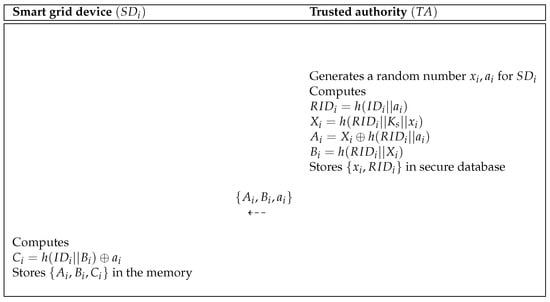
Figure 6.
Smart grid device registration process of the proposed scheme.
- Step 1:
- generates a random number for . After that, computes , , , and and stores in secure database. Finally, sends to .
- Step 2:
- After receiving the message, computes and stores in the memory.
6.3. Utility Center Registration Process
The must register with in order to provide power management services. Figure 7 describes the UC registration process of proposed scheme and the steps of this process are given below.
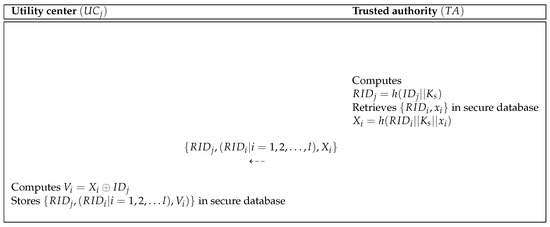
Figure 7.
Utility center registration process of the proposed scheme.
- Step 1:
- computes and retrieves in secure database. Then, computes and sends to .
- Step 2:
- After receiving the message, computes and stores in the database.
6.4. Authentication Process
In authentication process, the proposed scheme provides the user’s privacy by using pseudo-identity and secret parameters in the SG environments. Before the starting session, request an authentication request to in order to ensure secure communication and establish the session key . Figure 8 describes the authentication process of proposed scheme and the steps of this process are given below.

Figure 8.
Authentication process of the proposed scheme.
- Step 1:
- computes , , , and . Then, checks whether . If the condition is valid, generates a random nonce and computes , , and . After that, sends authentication request message to over insecure channel.
- Step 2:
- After receiving the message from , retrieves in database and calculates , , and . Then, retrieves corresponding in database and checks whether . If the condition is valid, calculates and checks whether . If the condition is correct, generates a random nonce and computes , , and . Finally, sends authentication message to over insecure channel.
- Step 3:
- After receiving the message from , computes , , , and . After that, checks whether . If the condition is correct, the and achieve mutual authentication successfully.
6.5. Dynamic Smart Grid Device Addition Process
When new SG device wants to register with the SG environments, the following steps must be performed and detailed steps are as follows. The main goal of this process is adding a new SG device to provide flexibility in SG environments. The detailed steps of this process are given below.
- Step 1:
- First, chooses a new to the over secure channel. After receiving the message, sends to the over secure channel. Then, generates a random number .
- Step 2:
- After that, computes , , , and . Finally, stores in secure database and sends its to the over secure channel.
- Step 3:
- After receiving the message, computes and stores in the memory.
6.6. Dynamic Utility Center Addition Process
The following steps are required to deploy new and the detailed steps are given below.
- Step 1:
- The chooses a new and sends to over secure channel. After receiving the message, sends to the over secure channel. After that, computes and retrieves in the database.
- Step 2:
- Then, computes and sends to the .
- Step 3:
- After receiving the message, computes and stores in secure database.
7. Security Analysis
In this phase, we demonstrate that the proposed scheme has the ability to resist various attacks using informal security analysis and the formal security verification tool Automated Validation of Internet Security Protocols and Applications (AVISAP). We also analyze that our proposed scheme provides session key security and secure mutual authentication using Real-or-Random (ROR) model [14] and Burrows–Abadi–Needham (BAN) logic [13]. ROR model, BAN logic, and AVISPA analysis techniques are also widely accepted to evaluate the security of protocol.
7.1. Informal Security Analysis
We performed informal security analysis to demonstrate the safety of the proposed scheme. Our protocol can defend against various attacks such as session key disclosure, SG device stolen, masquerade, and replay attacks, as well as ensure secure mutual authentication and anonymity.
7.1.1. Masquerade Attack
According to Section 1.1, a malicious adversary can obtain SG device of legitimate user and can intercept transmitted data over insecure channel. If tries impersonate a legitimate user, must correctly generate an authentication request and response messages. However, cannot generate the authentication request message and authentication message without the correct random nonces and . Furthermore, cannot generate a session key because secret parameter is not available to . Therefore, the proposed scheme is secure against masquerade attack.
7.1.2. Smart Grid Device Stolen Attack
We assume that a malicious adversary obtains SG device of a legitimate user and extracts secret information stored in the memory using power analysis attack [9]. However, cannot obtain sensitive information of a legitimate user because all information stored in the memory is masked by XOR operation and hash function. Therefore, our protocol prevents SG device stolen attack because cannot know the user’s real identity , , and secret parameter .
7.1.3. Replay Attack
Our protocol withstands replay attack because all transmitted messages are changed in every session. Assuming that tries to impersonate legal user by resending information transmitted in a previous authentication process, cannot use the previous messages because and check whether and , respectively. Thus, our protocol is secure against replay attack.
7.1.4. Session key disclosure attack
In the proposed scheme, cannot calculate because cannot compute authentication request message without knowing random nonce and secret parameter . Therefore, our protocol can withstand session key disclosure attack.
7.1.5. Insider attack
This type of attack happens when the administrator of authentication server exploits data stored in the database to legalize his authentication process on behalf of the user. Even if it is assumed that a malicious adversary can obtain stored in memory of , cannot obtain sensitive information such as user’s real identity and without knowing random nonce and . Thus, our protocol is secure against insider attack.
7.1.6. Mutual Authentication
After receiving the authentication request message from the , checks whether . If is valid, authenticates successfully. After receiving the authentication message from the , also checks whether , and then authenticates . Therefore, our protocol ensures secure mutual authentication between and because cannot generate correct authentication messages.
7.1.7. Anonymity
does not obtain a legitimate user’s real identity because it is masked by one-way hash function and XOR operation such as . Therefore, our protocol ensures anonymity because cannot know the user’s real identity without random nonce and .
7.2. Security Features
In Table 2, we evaluate the security features of the proposed scheme with existing schemes [6,20,21,28]. The schemes in [20,28] cannot withstand session key disclosure attack and those in [20,21,28] provide dynamic node addition phase. The scheme in [6] cannot withstand various types of attacks and cannot ensure secure mutual authentication and anonymity. Consequently, the proposed scheme ensures better security functionality than all previous schemes.

Table 2.
A comparative summary: security features.
7.3. Formal Security Analysis Using BAN Logic
We performed BAN logic [13] analysis to verify that our protocol provides secure mutual authentication. Table 3 shows the notation used for BAN logic analysis and we then defines the goals, idealized forms, and assumptions before performing BAN logic analysis.

Table 3.
Notations used for BAN logic.
7.3.1. BAN Logic Rule
The rules of BAN logic are as follows.
- Message meaning rule:
- Nonce verification rule:
- Jurisdiction rule:
- Freshness rule:
- Belief rule:
7.3.2. Goals
The goals for BAN logic analysis are as follows.
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
7.3.3. Idealized Forms
The idealized forms are formulated as follows:
- :
- :
- :
- :
7.3.4. Assumptions
We define initial assumptions to perform the BAN logic analysis.
- :
- :
- :
- :
- :
- :
- :
- :
7.3.5. Proof Using BAN Logic
We performed the BAN logic analysis for our protocol and the detailed proofs are below.
- Step 1:
- According to , we obtain
- Step 2:
- Using the message meaning rule with and , we can obtain
- Step 3:
- Using the freshness rule with , we can obtain
- Step 4:
- From the nonce verification rule with and , we can obtain
- Step 5:
- Using the belief rule with , we can obtain
- Step 6:
- Because of , from the and we can obtain
- Step 7:
- From the jurisdiction rule with and we can obtain
- Step 8:
- According to , we can obtain
- Step 9:
- Using the message meaning rule with and , we can obtain
- Step 10:
- Using the freshness rule with , we can obtain
- Step 11:
- Using the nonce verification rule with and , we can obtain
- Step 12:
- Using the belief rule with , we can obtain
- Step 13:
- Because of , from the and we can obtain
- Step 14:
- Using the jurisdiction rule with and we can obtain
Based on Goals 1–4, we proved that proposed protocol ensures secure mutual authentication between and .
7.4. Formal Security Analysis Using ROR Model
ROR model [14] is the formal security analysis to verify session key (SK) security of protocol from active/passive attacker . We first discuss the ROR model before performing the proof of SK security for the proposed protocol.
In our protocol, there are two participants SG device and UC , where and are instances of and of , respectively. Table 4 defines queries for ROR model to perform security analysis, including , , , , and queries. is also a random oracle, which is a collision-resistant hash function. We uses Zipf’s law [29] to prove SK security of the proposed protocol, which has been widely applied to verify recent authentication schemes [30,31].

Table 4.
Queries of ROR model.
Theorem 1.
If denotes the advantage function of a malicious attacker in violating SK security of the proposed authentication scheme, then
where , and are the number of query, the number of query, and the range space of the hash function , respectively, and s and C are the Zipf’s parameters [29].
Proof.
Similarly, we adopt the proof as presented in [32,33]. A sequence of four games is denoted by , where are defined for demonstrating the SK security of the proposed authentication scheme. We denote that is the probability a malicious attacker wins the game . The detailed descriptions of these four games are shown in Game 0–3. □
- Game: This game is the initial game in which selects the random bit c. In addition, this game denotes actual attack of for the protocol and c is guessed at the beginning of . According to this game, we can get,
- Game: This game denotes that performs an eavesdropping attack, in which it intercepts all transmitted messages and during authentication process utilizing query. Once the game ends, sends and queries. The output of the and queries decide if obtains random numbers and shared session key between and . To derive , needs secret information , , and . Thus, and are indistinguishable because the winning probability of is not increased. We then get,
- Game: In this game, the and queries are simulated. This game is modeled as an active attack, in which a malicious attacker eavesdrops all transmitted messages and during authentication process. All transmitted messages in authentication process are protected by utilizing the collision-resistant one-way hash function . In addition, random numbers and are used in the messages and . However, and are not derived from all transmitted messages due to the collision-resistant one-way hash function . makes and sends query, and then we can get the result using birthday paradox.
- Game: In this the final game, the query is simulated. Hence, a malicious attacker can extract the credential informations from memory of the SG device using power-analysis attack. Note that , and . It is computationally infeasible for to derive identity of correctly via the queries without ’s master key and secret parameter . As a result, and are indistinguishable if identity guessing attack is not implemented. Consequently, utilizing Zipf’s law [29], we can get the result as below:As all the games are executed, can only guess the exact bit c. Thus, we can get as below:Using Equations (1), (2), and (5), we can get the result as below:Using Equations (4)–(6), we obtain the result utilizing the triangular inequality as below:Finally, we obtain the required result by multiplying both sides of Equation (7) by a factor of 2.
7.5. Formal Security Analysis Using AVISPA
AVISPA is a widely used simulation tool for checking whether authentication protocol is secure against replay and MITM attacks. To perform AVISPA simulation, the session and environment of security protocol must be defined using the High-Level Protocol Specification Language (HLPSL). We define three basic roles in HLPSL implementation for the proposed protocol: the SG device , the utility server , and the trusted authority . The and are shown in Figure 9.

Figure 9.
Role specification of environment and session.
7.5.1. Detailed Specification of Roles
First, receives the initial messages and makes a state value from 0 to 1. generates a random number , calculates , and then sends a registration request message to over secure channel and changes the state value from 1 to 2. In transition 2, receives the secret parameters from over secure channel. In login and authentication process, generates a random number and computes an authentication request message . Then, sends to utility center and updates the state value from 2 to 3. In the last transition, receives a authentication message from the , computes the session key , and declares a request function , which means that denotes a strong authentication factor. As a result, authenticates successfully. The specification of a SG device () is shown in Figure 10. In Figure 11 and Figure 12, the role specifications of and are similarly defined with .

Figure 10.
Role specification of smart grid device.

Figure 11.
Role specification of utility center.

Figure 12.
Role specification of trusted authority.
7.5.2. Results of AVISPA Analysis
We utilized CL-based Attack Searcher (CL-AtSe) and On-the-fly-Model-Checker (OFMC) back-ends to the verify security of our protocol. The HLPSL code was translated into intermediate format, and then converted to output format using the back-ends. Figure 13 shows the results of simulation using two back-ends. The result of CL-AtSe back-end shows that two states were analyzed and the translation time was 0.10 s. The result of OFMC back-end shows it visited node 1040 nodes with nine plies depth. According to the results of simulation, the proposed protocol is secure against replay and MITM attacks.
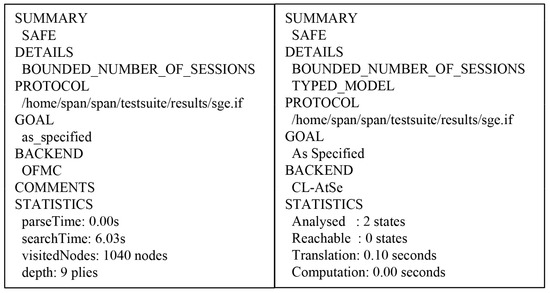
Figure 13.
AVISPA simulation result using OFMC and CL-AtSe.
8. Performance Analysis
This section compares performances and security feature of proposed scheme with existing schemes [6,20,21,28].
8.1. Computation Overhead
We compared the computation costs of the proposed scheme with existing schemes [6,20,21,28]. We define the parameters based on the work of Kumar et al.’s scheme [6]. , , , , , , , and denote public key certificate verification, public key certificate generation, one-way hash function, symmetric encryption/decryption, modular exponentiation, multiplication, ECC point addition, ECC point multiplication, and bilinear pairing, respectively. Based on the works in [21,34], we present the execution time for various cryptographic operations in Table 5 and assume {, } is negligible because it requires very low execution time. We also assume and .

Table 5.
Various cryptographic operations based on execution time [21,34].
In authentication process, total computation overheads of proposed scheme and Kumar et al.’s scheme are and , respectively. Based on the works in [21,34], the total computational overheads of our scheme is 0.011 s and 0.05 ms, which is implemented on HiPerSmart card and Pentium IV platform, respectively. Therefore, we provide better efficiency than existing schemes because our protocol utilizes only hash function and XOR operation. Table 6 shows the analysis result of computation overhead compared to existing schemes.

Table 6.
A comparative summary: computation overheads.
8.2. Communication Overhead
We first define that timestamp, identity, hash, random number, and ECC cryptosystem are 32, 160, 160, 160, and 320 bits, respectively. In our protocol, transmitted messages and require (160 + 160 + 160 =) 480 and (160 + 160 + 160 =) 480 bits, respectively. As a result, the proposed scheme has more efficient than related schemes [6,20,21,28] because the total communication overhead of proposed protocol is very low compared with the others. Table 7 shows the analysis result of communication overhead compared to existing schemes.

Table 7.
A comparative summary: communication overheads.
8.3. Storage Overhead
We first define that identity, hash, timestamp, random number, and public key cryptosystem are 20, 20, 4, 20, and 40 bytes, respectively. In our protocol, stored messages and require (20 + 20 + 20 =) 60 and (20 + 20 + 20 =) 60 bytes, respectively. Although the proposed scheme storage overhead of somewhat higher than Kumar et al.’s scheme, it provides better efficiency and security than the other related schemes [6,20,21,28]. Table 8 shows the analysis result of storage overhead compared to existing schemes.

Table 8.
A comparative summary: storage overheads.
9. Conclusions
This study demonstrated that Kumar et al.’s scheme cannot defend against various potential attacks such as masquerade, SG device stolen, and session key disclosure attacks. We also showed that Kumar et al.’s scheme does not ensure mutual authentication. To overcome these security shortcomings of Kumar et al.’s scheme, we present a privacy-preserving lightweight authentication protocol for demand response management in the SG environments. Our protocol prevents against various attacks, including masquerade, replay, SG device stolen, and session key disclosure attacks and achieves secure mutual authentication and anonymity. We proved that our protocol ensures secure mutual authentication between and using BAN logic, and then we showed that the proposed protocol withstands various potential attacks using informal security analysis and ROR model. We also demonstrated that our scheme was secure against replay and MITM attacks using AVISPA simulation tool. Furthermore, we compared communication overheads, computation overheads, and storage overheads with existing schemes. Therefore, our protocol is applicable for practical SG environments because it is more secure and efficient than other existing schemes.
Author Contributions
Conceptualization, S.Y. and K.P.; Formal analysis, S.Y., K.P. and J.L.; Methodology, J.L., S.L. and B.C.; Software, J.L., S.L. and B.C.; Supervision, Y.P. (YoungHo Park) and Y.P. (YoHan Park); Validation, Y.P. (YoungHo Park) and Y.P. (YoHan Park); Writing—original draft, S.Y.; Writing—review & editing, Y.P. (YoungHo Park) and K.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2018R1D1A3B07050409) and in part by the Institute for Information & communications Technology Promotion (IITP) grant funded by the Korea government (MIST) (No. 2018-0-00312, Developing technologies to predict, detect, respond, and automatically diagnose security threats to automotive Ethernet-based vehicle).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Park, Y.H.; Park, Y.H. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Tonyali, S.; Akkaya, K.; Saputro, N.; Uluagac, A.S.; Nojoumian, M. Privacy–preserving protocols for secure and reliable data aggregation in IoT–enabled Smart Metering systems. Future Gener. Comput. Syst. 2018, 78, 547–557. [Google Scholar] [CrossRef]
- Braeken, A.; Kumar, P.; Martin, A. Efficient and Privacy-Preserving Data Aggregation and Dynamic Billing in Smart Grid Metering Networks. Energies 2018, 11, 2085. [Google Scholar] [CrossRef] [Green Version]
- Kumar, P.; Gurtov, A.; Sain, M.; Martin, A.; Ha, P.H. Lightweight authentication and key agreement for smart metering in smart energy networks. IEEE Trans. Smart Grid 2019, 10, 4349–4359. [Google Scholar] [CrossRef] [Green Version]
- Department of Energy. Exploring the Imperative of Revitalizing America’s Electric Infrastructure. February 2017. Available online: https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/DOE_SG_Book_Single_Pages.pdf (accessed on 3 February 2020).
- Kumar, N.; Aujla, G.S.; Das, A.K.; Conti, M. ECCAuth: Secure authentication protocol for demand response management in smart grid systems. IEEE Trans. Ind. Inform. 2019, 15, 6572–6582. [Google Scholar] [CrossRef]
- Desai, S.; Alhadad, R.; Chilamkurti, N.; Mahmood, A. A survey of privacy preserving schemes in IoE enabled smart grid advanced metering infrastructure. Clust. Comput. 2019, 22, 43–69. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology—CRYPTO; Lecture Notes in Computer Science; Springer: Santa Barbara, CA, USA, 1999; pp. 388–397. [Google Scholar]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2012, 51, 541–552. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.Y.; Yu, S.J.; Park, K.S.; Park, Y.H.; Park, Y.H. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [Green Version]
- Yu, S.J.; Park, K.S.; Park, Y.H. A secure lightweight three–factor authentication scheme for IoT in cloud computing environment. Sensors 2019, 19, 3598. [Google Scholar] [CrossRef] [Green Version]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; pp. 65–84.
- Rottondi, C.; Fontana, S.; Verticale, G. Enabling privacy in vehicle-to-grid interactions for battery recharging. Energies 2014, 7, 2780–2798. [Google Scholar] [CrossRef] [Green Version]
- Jiang, Q.; Khan, M.K.; Lu, X.; Ma, J.; He, D. A privacy preserving three–factor authentication protocol for e-Health clouds. J. Supercomput. 2016, 72, 3826–3849. [Google Scholar] [CrossRef]
- Wan, Z.; Zhu, W.T.; Wang, G. PRAC: Efficient privacy protection for vehicle-to-grid communications in the smart grid. Comput. Secur. 2016, 62, 246–256. [Google Scholar] [CrossRef]
- Jo, H.J.; Kim, I.S.; Lee, D.H. Efficient and privacy-preserving metering protocols for smart grid systems. IEEE Trans. Smart Grid 2016, 7, 1732–1742. [Google Scholar] [CrossRef]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H.; Kumari, S.; Li, X.; Sangaiahm, A.K. An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Future Gener. Comput. Syst. 2018, 81, 557–565. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. Secure anonymous key distribution scheme for smart grid. IEEE Trans. Smart Grid 2016, 7, 906–914. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Wazid, M.; Conti, M. Provably secure authenticated key agreement scheme for smart grid. IEEE Trans. Smart Grid 2016, 9, 1900–1910. [Google Scholar] [CrossRef]
- Doh, I.; Lim, J.; Chae, K. Secure authentication for structured smart grid system. In Proceedings of the International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS’15), Fukuoka, Japan, 8–10 July 2015; pp. 200–204. [Google Scholar]
- Saxena, N.; Choi, B.J.; Lu, R. Authentication and authorization scheme for various user roles and devices in smart grid. IEEE Trans. Inf. Forensics Secur. 2016, 11, 907–921. [Google Scholar] [CrossRef] [Green Version]
- He, D.; Wang, H.; Khan, M.K.; Wang, L. Lightweight anonymous key distribution scheme for smart grid using elliptic curve cryptography. IET Commun. 2016, 10, 1795–1802. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Rodrigues, J.P.C. Secure three-factor user authentication scheme for renewable energy based smart grid environment. IEEE Trans. Ind. Inform. 2017, 13, 3144–3153. [Google Scholar] [CrossRef]
- Weaver, K. A Perspective on How Smart Meters Invade Individual Privacy. 2014. Available online: https://skyvisionsolutions.files.wordpress.com/2014/08/utility-smart-meters-invade-privacy-22-aug-2014.pdf (accessed on 3 February 2020).
- Finster, S.; Baumgart, I. Privacy-aware smart metering: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1088–1101. [Google Scholar] [CrossRef]
- Wu, D.; Zhou, C. Fault-tolerant and scalable key management for smart grid. IEEE Trans. Smart Grid 2011, 2, 375–381. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Park, K.S.; Park, Y.H.; Park, Y.H.; Das, A.K. 2PAKEP: Provably secure and efficient two-party authenticated key exchange protocol for mobile environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Kumar, N.; Khan, M.K.; Choo, K.K.R.; Park, Y.H. Design of secure and lightweight authentication protocol for wearable devices environment. IEEE J. Biomed. Health Inform. 2018, 22, 1310–1322. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J. TCALAS: Temporal credential based anonymous lightweight authentication scheme for internet of drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Huang, S.S.; Tsai, T.T.; Ke, J.H. List-free id-based mutual authentication and key agreement protocol for multi-server architectures. IEEE Trans. Emerg. Top. Comput. 2016, 4, 102–112. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).