Abstract
Accurately evaluating the vulnerability of prefabricated components in prefabricated buildings is the basis of scientific management of its supply chain. Thus, a novel vulnerability evaluation method for the suppliers of prefabricated components in the context of prefabricated buildings was proposed in this study. First, a vulnerability evaluation index system was identified and constructed by the pressure–state–response (PSR) model. With the clear logic and strong applicability of PSR, this system, including 18 indexes, was easy to understand and exhibited strong practicability. The weights were then determined via the multiplicative analytic hierarchy process with the expansion of a probabilistic language terminology set (PLTS). PLTS could describe decision information more comprehensively, so the evaluation result is more scientific. Subsequently, the probability of the vulnerability level was superimposed in a parallel bottom-to-top method via the controlled interval and memory (CIM) models, and these were extended by the PLTS. This set handled the uncertain information in the decision-making process more efficiently and accurately, and finally determined the vulnerability distribution. Ultimately, the probability of each vulnerability level was determined by combining the weight information. The reconstruction and resettlement housing construction project of urban shanty towns in the Taohua South Road Community in Xihu District, Nanchang City, was selected as a case study. The case study proves the effectiveness of this method, which has higher resolution and is more convenient for managers to make decisions.
1. Introduction
Rapid urbanization and the growing environmental awareness in China have led to the increasing adoption of prefabricated buildings as efficient and environmentally friendly building technology [1]. According to the 14th Five-Year Construction Development Plan issued by the Ministry of Housing and Urban-Rural Development of China, prefabricated buildings are predicted to comprise more than 30% of new buildings. In prefabricated buildings, problems may arise, including an insufficient production capacity or supply capacity of suppliers, inadequate quality control, and imperfect supply chain management. These challenges can lead to delays during construction, quality problems, and increased costs, which can negatively affect the sustainability of the entire project construction and operation [2,3].
The supplier management of prefabricated components in prefabricated buildings refers to the standardized management and supervision of prefabricated component suppliers in prefabricated buildings to ensure that their product quality, delivery time, and safety meet the standards. At present, supply chain management has been successfully applied in food management [4], e-commerce [5], wine management [6], urban logistics systems [7], and other fields.
Vulnerability research is a systematic analysis of systems, networks, or programs to identify, classify, and evaluate security weaknesses or defects that may cause damage to the system. Uncertainty research in supplier management has gradually refined vulnerability research from traditional risk research [8]. Compared with risk research, vulnerability research focuses more on the internal nature of the system, more deeply analyzes suppliers, and provides more targeted risk management and coping strategies for related enterprises [9,10]. Vulnerability research explores system vulnerability characteristics to predict and reduce the risk of system interference. Vulnerability assessment helps managers to identify potential risks and threats in order to conduct effective preventive and coping measures. The supply interruption of prefabricated components is the vulnerability that this paper focuses on evaluating. The significance of this study lies in the offering of a novel supplier vulnerability evaluation method, providing scientific decision support for the supplier management of prefabricated components in buildings, as well as improving the sustainability and competitiveness of prefabricated construction.
Prefabricated buildings have gained traction among researchers, drawing significant attention. However, research on the evaluation of prefabricated component suppliers remains limited, and targeted research on the concept of “vulnerability” of prefabricated component suppliers is lacking. Studies on prefabricated component suppliers predominantly encompass the broader subject, with limited research conducted from the perspective of vulnerability. Zhu and Liu [11] focused on the risk management of prefabricated building supply by using the risk breakdown structure method. This approach was intended to identify the risk factors of the supply chain in prefabricated buildings. Liu et al. [2] proposed an evaluation system of supplier management maturity on the basis of five dimensions: procurement process, operational efficiency, relationship coordination, strategic adjustment, and corporate social responsibility. From the perspective of an owner’s procurement, Wang et al. [12] investigated the owner’s perspective of owner’s procurement by establishing an elastic supplier evaluation model for prefabricated components with the following three dimensions being considered: main evaluation criteria, enterprise flexibility and service, and green buildings. Song et al. [13] established the supplier evaluation index for prefabricated building components with the following five dimensions being considered: economy, quality, transportation, long-term cooperation, and aftersales. Jiang et al. [14] studied and analyzed the factors that hinder the growth of prefabricated buildings in China, and determined that risk is the main factor hindering the development of prefabricated buildings. However, risk has rarely been the focus of research. This scarcity justifies the importance of refining risk research and the suitability of vulnerability research as the research topic.
Vulnerability research has recently drawn wide interest and has been applied in various fields. Aleksic et al. [15] established a project vulnerability assessment model for the planning stage of a project prior to its implementation, providing a key direction for the follow-up management of the project. Karagiorgos et al. [16] analyzed the physical vulnerability and social vulnerability of mountain torrents, which can be used as a reference for the management strategy of mountain torrents. He et al. [17] conducted an ecological vulnerability assessment in China and identified the ecologically fragile areas, providing effective guidance for ecological protection and environmental management. Xu et al. [18] introduced the concept of vulnerability in the context of subway network systems. Their study focused on urban rail transit systems and classified vulnerability into three categories: station vulnerability, network vulnerability, and social vulnerability. Zhang et al. [19] proposed the concept of bike-sharing system vulnerability, and developed corresponding analysis techniques related to bike-sharing systems. Vulnerability research has been successfully applied in various fields, offering advantages such as sensitivity and applicability. Therefore, this study introduces vulnerability in the field of supplier evaluation for prefabricated components in prefabricated buildings. It analyzes the potential risks and problems faced by suppliers, reveals the weak links and fragile factors in the system, and predicts their effect on prefabricated building projects.
Traditional system evaluation methods include the fuzzy comprehensive evaluation method (FCEM) [20], grey relational analysis method (GRAM) [21], and the fault tree analysis (FTA) method [22], among others. The vulnerability evaluation of prefabricated component suppliers in prefabricated buildings is a relatively new research direction, and researchers have limited access to relevant information. In the fuzzy comprehensive evaluation method, the accurate determination of the membership function presents a challenge, potentially influencing the precision of the final evaluation results. The grey relational analysis assumes that the factors exhibit a linear and independent relationship, which may not always hold true in vulnerability research [21]. FTA modeling is complicated, and it typically assumes that failure has only one primary cause, which may not always hold true in vulnerability research [22]. By contrast, controlled interval and memory (CIM) models can effectively handle the fuzziness and correlation of risk factors, rendering them suitable for assessing the complexities of vulnerability factors and fuzzy evaluation in prefabricated component suppliers for prefabricated buildings. CIM models have been proven to be effective in risk assessment across various complex fields. In the study by Tian et al. [23], the risk factors for expressway investment exhibited multilevel structures, multiple factors, fuzzy evaluation, and randomness. Through using the CIM model, Tian determined the probability of risks at all levels in the risk assessment of expressway investment, verifying the feasibility of the project and presenting insights for project-related investment decisions. Zhang et al. [24] used the CIM model for the cost risk assessment of large hydropower projects, as well as for measuring the corresponding probability distribution. The study provided valuable information through which to enhance cost control measures.
The traditional CIM method often relies on an evaluation set to obtain the probability distribution of index risk [25]. This technique requires experts to precisely assess the risk level, which is based on the elements in the evaluation set and may not fully adhere to real-world scenarios. In this study, the CIM method was extended to a probabilistic language information environment. This extension considers the possibility of hesitation, ambiguity, and lack of knowledge (of the experts), rendering it preferable for actual decision-making situations. The glossary of probabilistic language was introduced in 2016 by Pang et al. [26], and the theory can be traced back to fuzzy sets [27] at the earliest stage. The probability language terminology set (PLTS) can be used to represent the language evaluation of decision makers at all levels, with indecision and uncertainty considered in the decision-making process [28]. In addition, the PLTS conforms to the natural expression habits of people in daily life, enhancing the relevance and practicality of decision makers. In recent years, numerous research findings have emphasized the good expandability of the probability language terminology set. Wu et al. [29] applied multiplication multi-objective optimization by ratio analysis by using the expanded probability language terminology set in karaoke TV brand selection, effectively demonstrating the efficacy of the method. Similarly, on the basis of the expansion of the probability language terminology set, Wang et al. [30] employed the grey relational projection method for hospital construction site selection. Lin et al. [31] used the TOmada de Decisão Iterativa Multicritério (TODIM) with an expanded set of probabilistic language terms to evaluate the Internet of Things platform, and then verified the advantages of this approach by comparative analysis. In addition, the technique for order preference by similarity to an ideal solution (TOPSIS), analytic hierarchy process (AHP), and VlseKriterijumska Optimizacija I Kompromisno Resenje (VIKOR) methods when based on the expansion of the probabilistic language terminology set have also been successfully used [32,33].
Therefore, the current study seeks to use the CIM method with a probabilistic language extension to perform the vulnerability evaluation of prefabricated component suppliers. The primary contributions of this study are as follows: (1) Contrary to previous risk-based research results, this study shifts its perspective from risk to the vulnerability evaluation of prefabricated component suppliers. By analyzing supplier vulnerability, this study sheds light on the susceptibility of suppliers to external shocks. This change in perspective entails a closer examination of the vulnerabilities that suppliers may encounter, allowing for the refinement of risks and providing a basis for more accurate supplier management decision making. (2) The comprehensive, understandable, and operable index system in this study for evaluating the vulnerability of the suppliers of prefabricated components provides a solid theoretical basis for further research in related fields. Notably, no academic research on the vulnerability of the suppliers of prefabricated components has thus far been conducted. (3) Considering the particularity and complexity posed by the vulnerability research of prefabricated component suppliers, this study introduces the parallel response model of CIM and extends it to the probabilistic language environment. This model retains the inherent advantages of the CIM method in handling complex information while integrating the probabilistic language environment. Experts can more flexibly express different language evaluations, assign varying weights to language evaluations, and consider the intricacies and uncertainties of their thinking. Consequently, the evaluation process becomes more scientifically sound, yielding more accurate and reliable evaluation results. (4) This study reveals that the state of prefabricated component suppliers exerts the most significant effect on vulnerability, which is a key factor in supplier management. This finding shows that the attributes of the supplier encompass not only their capabilities, but are also key to measuring their vulnerability. These attributes represent two facets of competitiveness, and it also provides a scientific reference for the supplier management of prefabricated components.
The remaining sections of this paper are organized as follows: Section 2 describes, in detail, the vulnerability evaluation index system of prefabricated construction suppliers that is proposed in this study. Section 3 introduces the vulnerability evaluation model for prefabricated building suppliers. Section 4 presents a case study on the reconstruction and resettlement housing construction project of urban shanty towns in Taohua South Road Community, Xihu District, Nanchang City. Section 5 compares the proposed model with the classical CIM model, and analyzes the influence of different PLTS standardization methods on the evaluation results. In Section 6, the research content is summarized, and future research directions for this study are outlined.
2. The Vulnerability Evaluation Index System
2.1. Analysis of Influencing Factors
Accurate identification of influencing factors is the basis of scientific evaluation [34]. The vulnerability of prefabricated components suppliers in prefabricated buildings refers to the extent of irreversible losses caused by the potential risks and unfavorable factors in such projects. With respect to the capabilities of suppliers, vulnerability can also be viewed as a measure of supplier resistance to adverse conditions, such as external pressure or internal interference.
The pressure–state–response (PSR) model is one of the most widely used methods to evaluate the index system [35]. PSR model emphasizes the analysis from three levels: pressure (external pressure, threat or change borne by the system), state (current state or health degree of the system), and response (response or countermeasures made by the system to external pressure), which helps to fully understand the causes and effects of system vulnerability [36]. According to the PSR model, vulnerability management becomes a dynamic process, which can constantly adjust the response measures according to the actual situation and improve the system’s ability to adapt to changes.
In the current study, the pressure index reflects the external or internal pressure factors faced by suppliers, the status index indicates the capabilities of prefabricated component suppliers, and the response index denotes the coping strategies made by suppliers to deal with the pressure factors.
When the PSR model is applied to this study, there is a causal relationship and interaction among pressure, state, and response.
- (1)
- Pressure → state. This represents the direct influence of external pressure on the state of supply chain system of prefabricated buildings.
- (2)
- State → response. This refers to the response of the manager or the system itself caused by the change of the state of the assembled building supply chain system. When the adverse changes in the system state are identified, managers will formulate and implement corresponding strategies and measures to deal with them, aiming at restoring or improving the system state.
- (3)
- Response → stress. This means that the response measures taken by managers can affect and change the original stress.
- (4)
- Cyclic interaction: there is not only a direct linear relationship between these, but also a cyclic feedback. The response often changes the pressure, which further affects the state and forms a dynamic cycle.
Stress index elements can be summarized as follows:
- (1)
- Market competition. The escalation of market competition has increased the pressure on enterprises, compelling them to continuously improve their competitiveness. This involves adapting to changes in market demand and seeking innovation and differentiation [11,37].
- (2)
- Supply chain instability. Both unpredictable material supply and unreliable partnerships can directly lead to supply chain interruptions [2,13].
- (3)
- Market demand. The drastic fluctuation of market demand can lead to unstable order quantities, presenting challenges in production adjustment [14,38].
- (4)
- Policy changes. The level of state support for prefabricated buildings can directly affect all aspects of prefabricated building construction and supply enterprises [39].
- (5)
- Technological progress. Prefabricated building construction is currently in its early stages. The rapid technological progress in this industry can potentially subject suppliers to competitive pressure, market share decline, and customer loss, as well as increases in the vulnerability of suppliers [2].
The elements of state indicators can be summarized as follows:
- (1)
- Financial status. The financial status of prefabricated building construction suppliers directly reflects whether an enterprise can withstand unexpected adverse events [2,37].
- (2)
- Technical ability. The higher the technical level of suppliers, the larger the pool of skilled technicians, and the stronger the stable supply and high-quality production capacity of prefabricated buildings [2,40].
- (3)
- Production capacity. A well-designed production scheme can not only optimize the production process and improve production efficiency, but it can also be a significant manifestation of enterprise competitiveness [13,41].
- (4)
- Supply capacity. Prefabricated building components usually have large sizes and weights, requiring special transportation and handling. Thus, the transportation capacity of suppliers for large components is related to their delivery reliability, transportation cost, and market competitiveness [11,13].
The response index elements are divided into the following:
- (1)
- Emergency preparedness. A complete emergency plan can enable suppliers to respond to emergencies more quickly and effectively, as well as help to reduce production interruptions and business losses, thus decreasing vulnerability [42].
- (2)
- Supply management. Effective inventory management becomes crucial for suppliers facing external pressure. It directly affects the reliability and stability of the supply chain and serves as a key factor in helping overcome difficulties and successfully navigate through difficulties [37,41].
- (3)
- Market diversification. Suppliers with business distribution in multiple markets can better cope with the changes or instability of a certain market, and this can also reduce the vulnerability of suppliers [11,43].
- (4)
- Innovative ability. Suppliers exhibiting strong innovation capabilities can constantly introduce new products, services, or solutions that align with evolving market demands. This can help with sustaining a competitive advantage, thus reducing the vulnerability of suppliers [11,13].
2.2. Proposed Indicator System
Based on the identification results of the evaluation indexes in Section 2.1, the vulnerability evaluation index system of prefabricated components suppliers in prefabricated buildings was established (Table 1).

Table 1.
The proposed indicator system.
refers to the competitive pressure faced by the supply chain in the current market environment. relates to the continuity and reliability of raw material supply in the supply chain. measures the stability of long-term cooperative relations. refers to the change of market demand for construction products, and high demand fluctuation may lead to difficulties in supply chain planning and operation. is the government’s policy orientation and support for prefabricated buildings. refers to the speed and flexibility of the supply chain to adopt new technologies.
relates to the financial soundness and robustness of the supply chain. refers to the liquidity of funds in the supply chain, and sufficient liquidity is conducive to smooth operation. refers to the overall technical capacity of the supply chain. refers to the experience accumulated by the team in performing technical tasks. refers to the supply chain’s arrangement of future orders and production. means that maintaining high-quality products is a key factor for the success of the supply chain. means that the transportation capacity of large components is very important for the smooth supply chain in prefabricated buildings.
refers to whether the supply chain has a complete response to possible interruptions and shocks. means that the supply chain can still maintain operation when the material supply is unstable. means that multiple supply channels can reduce the risk of a single supplier. means that the diversification of components can increase the ability of supply chain to adapt to different needs. means that continuous R&D investment will help to enhance the long-term competitiveness of the supply chain.
3. The Proposed Vulnerability Evaluation Model
3.1. Introduction to PLTS
PLTS is a set of terms and concepts used to describe and analyze the probabilistic nature of language models. PLTS can help to quantify and deal with the uncertainties and diversity in language generation and understanding.
- (1)
- Definition of the probability term set:Let be a given language set. The set of probabilistic language terms is then defined as follows [26]:where is a linguistic term in , is the probability that the linguistic term occurs, and is the number of terms contained in this probabilistic linguistic term set.
- (2)
- Standardization of the probability language terminology set:Since the introduction of the term set of probabilistic language, numerous standardized methods have been proposed [26,44,45]. However, not a single method has thus far been generally recognized by academic circles. The present study adopts the standardization method proposed by Pang [26]:Given a PLTS and , then the relevant PLTS is defined as follows [26]:where .In order to improve the universality of the model proposed in this paper, the most classic PLTS standardization method was selected. In Section 5.2 of this manuscript, the influence of different normalization methods on the results will be discussed in detail.
- (3)
- Constructing the decision matrix of the probability language terminology set:
- Let be a group of experts, with as the th expert. The expert weight vector is and . Suppose that each expert uses PLTS to evaluate the attribute , and the is the evaluation result of the attribute by the expert . These results are aggregated into a probabilistic language evaluation matrix [29]:where represents the total number of secondary indicators, denotes the total number of experts.
- The expert collective evaluation of the secondary indicator is the following [46]:where is the weight of in .
3.2. The PLTS-MAHP for Weight Calculation
On the basis of introducing PLTS in Section 3.1, this section introduces an improved multiplicative analytic hierarchy process (MAHP) method based on PLTS for weight calculation.
The MAHP, which was proposed by Lootsma in 1993 [47], is an effective weight determination technique based on a pairwise comparison standard matrix. It addresses the shortcomings of the analytic hierarchy process (AHP) in terms of weight scale, order preservation, and weight synthesis. Through using the multiplication equation, MAHP is transitive and eliminates the need for consistency checks [48]. Thus, the MAHP extended under a probabilistic language environment was used in this study. The concrete steps of the extended MAHP are as follows:
- (1)
- Establishing the language terminology set .
- (2)
- Inviting the expert to use PLTS to evaluate the relative importance between the attributes and . The expert collects evaluation information to form a paired comparison matrix [29]:
- (3)
- Through using Equation (4) to aggregate the pairwise comparison matrices provided by all experts , we obtain the following [49]:
- (4)
- The weight relation between attributes and is determined based on the MAHP method [47] to satisfy the following:where .In accordance with the logarithmic least square method, the weight can be obtained as follows:
- (5)
- After normalization, the weight of the attribute is expressed as per the following:
3.3. The PLTS-CIM for Vulnerability Assessment
On the basis of introducing PLTS in Section 3.1, this section introduces an improved CIM method based on PLTS for vulnerability assessment.
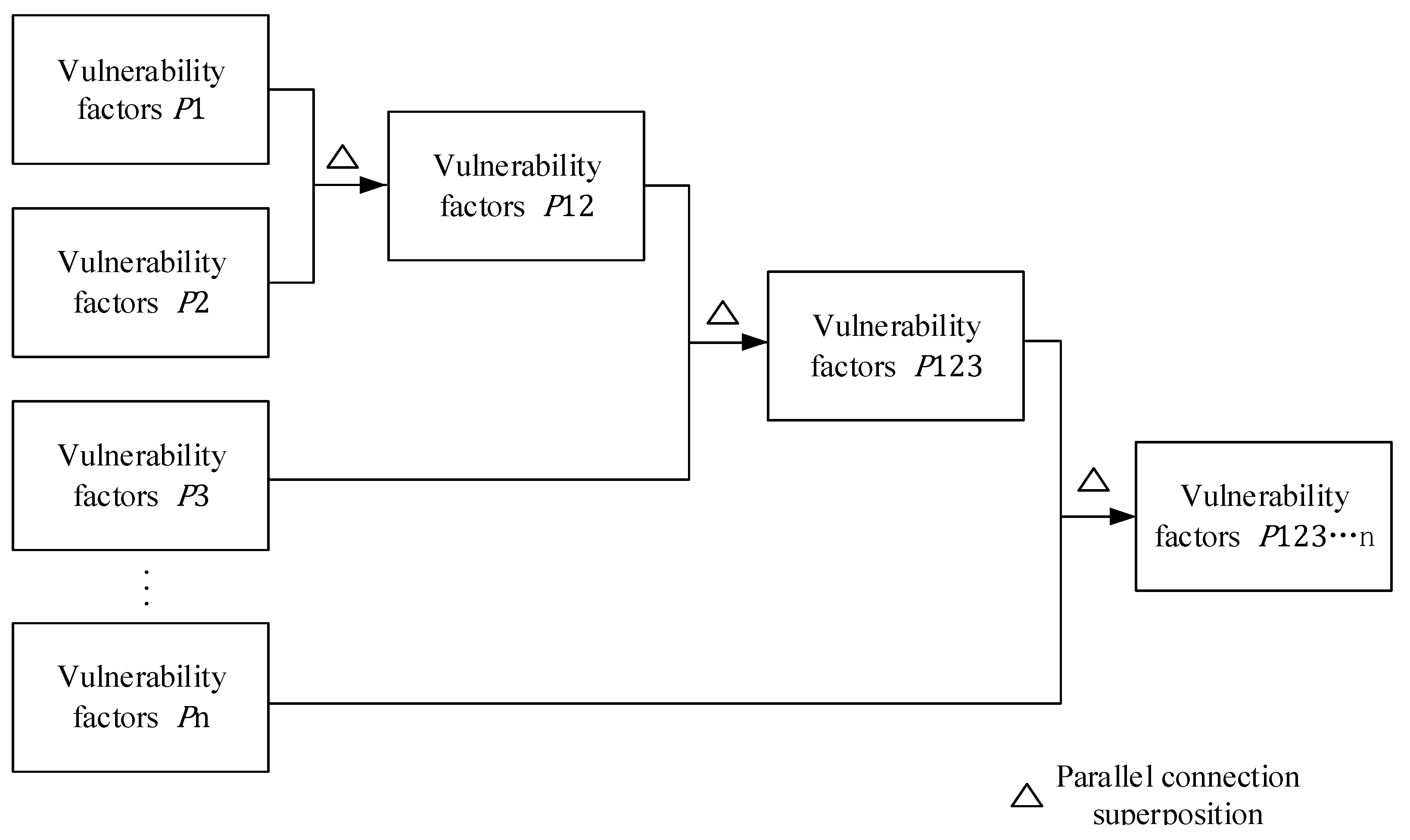
The CIM model uses a histogram to represent the probability distribution of variables. It determines the final probability of each vulnerability level in the upper layer by superimposing the calculation results of the former variable with the latter variable and circularly superimposing them. Based on the correlation and independence between variables, the CIM model can be categorized into a series response model and a parallel response model. This classification shares similarities with concepts in physics. The vulnerability of prefabricated subcontractors adheres to the law that any influencing factor in the parallel response model can affect vulnerability; thus, the vulnerability factors at the same level are substituted into the model in a parallel relationship. This process determines the probability distribution of their risk levels. The parallel superposition model is shown in Figure 1.
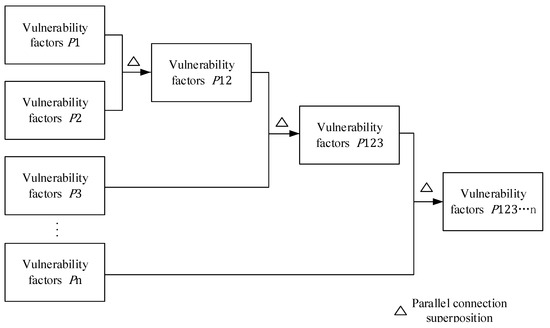
Figure 1.
Schematic of the CIM parallel superposition model.
The evaluation steps of the traditional CIM model are as follows:
(1) Establish a vulnerability evaluation set = {extreme risk, high risk, moderate risk, low risk, extremely low risk}, and invite experts to assign scores for the vulnerability elements of secondary indicators to obtain preliminary data.
(2) The probability of the element under the vulnerability level can be expressed as . represents the vulnerability grade, where is extremely dangerous, is high risk, and is extremely low risk; is the number of experts scoring under vulnerability level , and is the total number of experts.
(3) Calculate the vulnerability distribution of each element layer by layer by using the parallel response model. The probability calculation equation for the vulnerability level after and are connected in parallel is as follows:
where is the probability of the element under the vulnerability level , and is the probability of the element .
(4) Based on the calculated vulnerability probability distribution value of each element, the vulnerability distribution of all elements under each upper-level element is gradually computed after parallel connection [50]. The vulnerability probability at all levels is then calculated by combining the weight information of upper-level elements:
where is the number of upper elements; is the probability of the th upper layer element under the vulnerability level ; and is the weight of the th upper element.
The evaluation steps of the CIM model, based on the expansion of the probability language terminology set, are as follows:
(1) Establish PLTS
Researchers can construct PLTS according to the characteristics of the research object. This paper provides a suggested five-level PLTS, i.e., . is extremely dangerous, is highly dangerous, is moderately dangerous, is slightly dangerous, and is extremely slightly dangerous.
(2) Invite an expert to evaluate the language of the element . Then, the evaluation results are as follows:
In this study, the language terms with a probability of 0 in PLTS are retained.
(3) Collect the evaluation information of each expert and assemble it into a probabilistic language evaluation matrix :
where represents the total number of secondary indicators, and denotes the total number of experts.
(4) In accordance with Equation (4), the expert evaluation of the secondary indicator can be summarized as follows:
(5) Standardize the collective evaluation
If , the PLTS is defined as follows:
where .
(6) Collect the standardized expert evaluation matrix :
(7) Calculate the vulnerability grade probability of each element layer by layer via the parallel response model. The vulnerability distribution of and after parallel connection is as follows:
(8) In accordance with Equation (18), gradually calculate the vulnerability distribution of all elements connected in parallel under each upper element and obtain the vulnerability distribution of the upper elements:
(9) By combining the weight information of the upper elements, the total probability of each vulnerability level is calculated:
where ; is the number of upper elements; is the probability that is the language term of the th upper-level element; and is the weight of the th upper element.
3.4. Realization Method of the Proposed Model
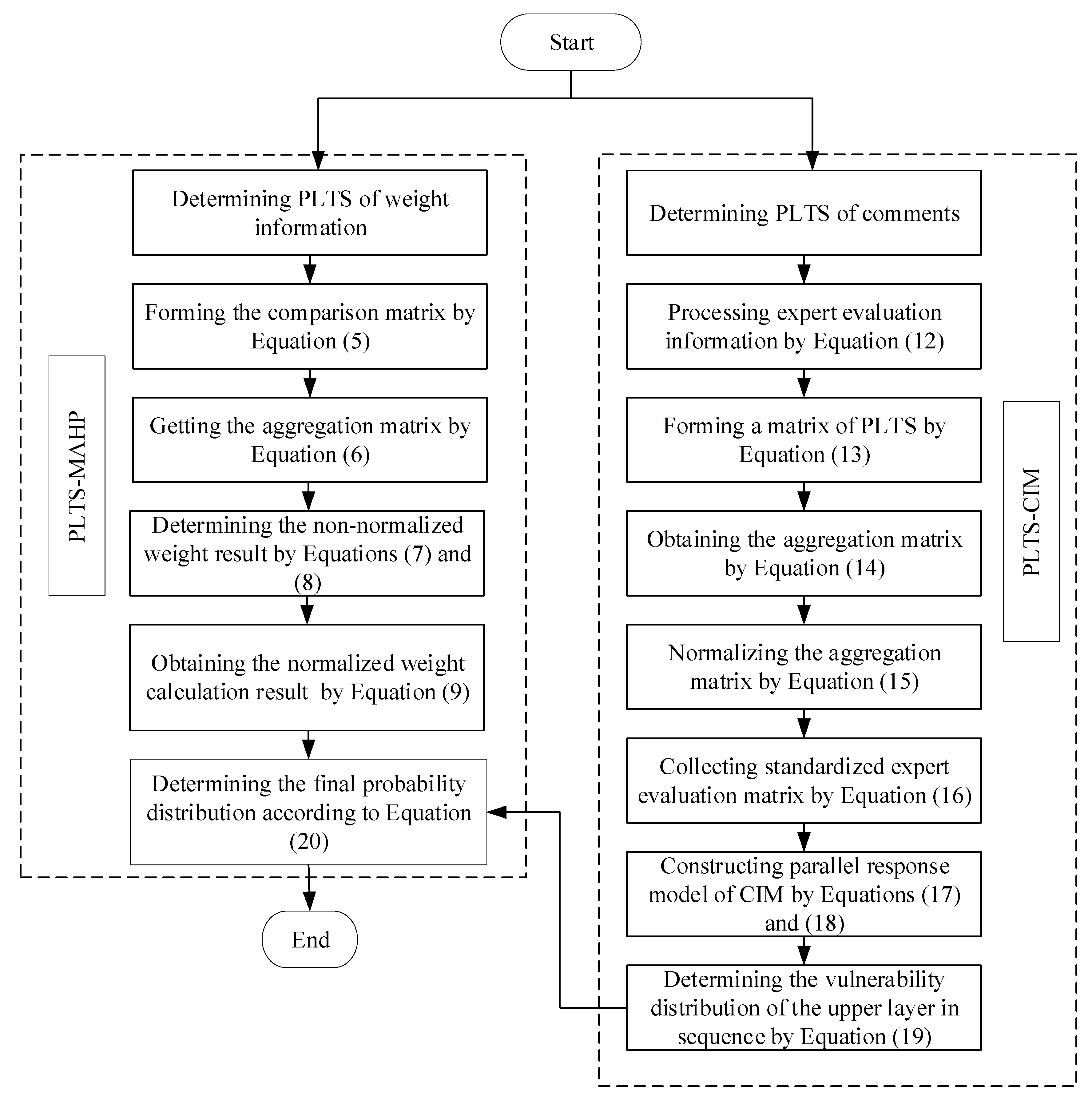
Vulnerability assessment is a typical multi-criteria decision making (MCDM) problem [51]. Referring to the general research paradigm of MCDM, the flow chart of the model proposed in this paper is shown in Figure 2.
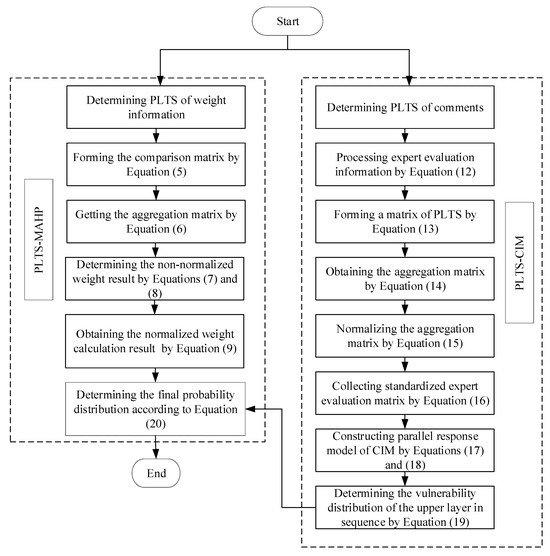
Figure 2.
Flowchart of vulnerability assessment.
According to Figure 2, the detailed implementation steps of the proposed model are as follows.
Step 1. Collecting weight information and evaluation information based on PLTS.
According to the management purpose and case characteristics, managers set up a reasonable set of language terms, collecting enough information of experts on the importance of indicators and case evaluation by means of expert interviews and questionnaires.
It should be noted that the number of experts should be appropriate; too few experts are difficult to obtain comprehensive data, and too many experts often make the calculation too large. Approximately 5 or 7 is the recommended number of experts. If the expert information is collected by questionnaire, the result of consistency test should be acceptable.
Step 2. Calculating the weight of each index.
Equation (5) was used to aggregate the expert evaluation information and to form the pairwise comparison matrix . This was the beginning of weight calculation.
By using Equation (6), all pairwise comparison matrices provided by the experts were aggregated into the probability preference matrix .
By substituting into the Equations (7) or (8), the normalized weights were achieved for the secondary index. In addition, the normalized weights for the primary index were obtained by bringing the weight results of the secondary index into Equation (9).
Step 3. Determining the probability distribution of vulnerability level.
Equation (12) was a tool to process the information of experts’ evaluation of cases. Equation (13) was used to form the probability linguistic evaluation matrix . The expert evaluation of the secondary indicator was obtained by Equation (14). Equation (16) was engaged to collect the standardized expert evaluation matrix .
Equations (17) and (18) were used to solve the vulnerability distribution of and after parallel connection. Equation (19) was employed to the vulnerability distribution of the upper elements .
Bring the primary index weights and obtained in the Step 2 into Equation (20), and the final probability distribution was obtained. Obviously, the maximum probability distribution was the final solution.
4. Case Studies
4.1. Project Overview and Data Sources
The reconstruction and resettlement housing construction project of urban shanty towns in the Taohua South Road Community in Xihu District, Nanchang City covers an area of approximately 32,000 m2, with a total construction area of around 137,000 m2, including an aboveground construction area of about 103,000 m2, and an underground construction area of around 34,000 m2. The high-rise residential buildings in this project all adopt an assembled structure system, with a total construction area of 85,629.9 m3, and a volume of PC components of approximately 14,000 m3. The construction unit shall be given a capital subsidy of 50 RMB/m2, and the maximum subsidy for a single project shall not exceed 2 million RMB.
Nanchang City is actively promoting the large-scale development of prefabricated buildings, with more than ten component suppliers being involved in this industry. As a result, the market competition for this project is relatively intense, and the supply of components is stable due to strong government policy support. The selected supplier for evaluation in this study is the Changsha Yuanda Company, which is one of the largest prefabricated building suppliers in China and has extensive engineering experience.
The main reasons for choosing Changsha Yuanda Company in this paper are as follows. (1) Market position. Changsha Yuanda Company has a high market share and influence in the assembled construction industry in China. Assessing its supply chain vulnerability would provide important information about the supply chain of the whole industry. (2) Supply chain scale. This company’s prefabricated building supply chain is larger and therefore more complex. Evaluating a responsible supply chain is more conducive to revealing the potential risks and problems that may exist in it, and providing corresponding improvement and management suggestions. (3) Feasibility. This company participated in the construction of the case object. The authors could obtain the supply chain data and information of Changsha Yuanda Company completely. This makes the corresponding evaluation work more feasible. Obviously, reliable and sufficient engineering data is the basis of accurate evaluation. (4) Industry representativeness. Changsha Yuanda Company, as one of the leaders in the assembled construction industry in China, has a good industry representation in its supply chain. By evaluating the fragility of its supply chain, it can represent the supply chain situation of the whole prefabricated construction industry to a certain extent.
This study adopted a questionnaire survey and expert interviews to collect the necessary research data. The basic information on the five invited experts is shown in Table 2.

Table 2.
Basic information on the five experts.
According to Table 2, all five experts had undergraduate and above education in the field of civil engineering, with an average work experience of 17.8 years. All engineers held the title of senior engineer and have been involved in the supply chain management of five or more prefabricated projects. These findings indicate that the five experts possessed extensive engineering experience and solid professional knowledge. Therefore, based on the composition of the experts, it can be preliminarily concluded that the research data obtained through the questionnaire survey and expert interviews in this study are valid. Furthermore, the reliability and validity of the questionnaire survey results in this study have been tested and verified, further confirming the effectiveness of the research data [52,53].
It is worth mentioning that these experts are also invited to discuss their opinions and suggestions on the index system. All five experts agree that the index system proposed in this paper is complete and comprehensive in the case study. This preliminarily proves that the index system proposed in this paper is complete and comprehensive.
4.2. Weight Calculation Based on the PLTS-MAHP
(1) Establishing the PLST of weight information:
This manuscript establishes the weighted information for PLST based on the characteristics of the research subject, as shown in Table 3.

Table 3.
PLST of the weight information.
(2) Formation of the pairwise comparison matrix :
Due to space limitations, this section only provides detailed weight calculation results for three primary indicators based on PLTS-MAHP. Experts were invited to use the PLTS in Table 3 to assess the relative importance between the primary indicators. Equation (5) was used to aggregate the expert evaluation information and to form the pairwise comparison matrix .
(3) Formation of probability preference matrix:
By using Equation (6), all pairwise comparison matrices provided by the experts were aggregated into the probability preference matrix :
(4) Calculation of indicator weights:
By substituting into Equation (8), the normalized weights were obtained as . By applying Equation (9) for normalization, the weight information for the primary indicators was calculated as ω = (0.369, 0.416, 0.215).
Through using a similar approach, the calculation results for all indicator weights could be obtained, as shown in Table 4.

Table 4.
Calculation results of weights based on the PLTS-MAHP.
In the primary indicators, the state indicator () had the highest weight. The construction management of prefabricated buildings heavily relies on suppliers consistently providing components. Factors such as the supplier’s production capacity, resource condition, supply chain management, and coordination directly affect the stability of component supply. If the supplier’s own state is unstable and they are unable to provide components in a timely manner, it will result in supply instability or interruption, leading to project delays and uncertainty in the construction of prefabricated buildings. Therefore, it is reasonable that has the highest weight. These research findings are highly consistent with the comprehensive results of predecessors, which enhances the persuasive power of this article [54]. However, the research subject of that manuscript is industrial buildings, whereas the present article is about ordinary residential buildings.
In the secondary indicators, the degree of policy support () had the highest weight at 0.0775. Currently, the prosperity of the prefabricated building market in China primarily depends on measures such as tax relief, subsidies, and the priority approval of projects, which is provided by various levels of the Chinese government. Clearly, any changes in the intensity of these policy supports will have a significant impact on the prefabricated building market. Therefore, the vulnerability of supplier evaluation to policy support level was found to be the greatest, which is reasonable.
Combined with the actual situation of the case, we suggest that managers consider the following aspects to ensure the effective support of policies for the supply chain of prefabricated buildings: (1) Formulate long-term clear and stable policy guidance and support measures to enhance the development confidence and investment willingness of enterprises. (2) Improve the provision of financial subsidies, tax relief and other incentives. (3) Promote the formulation and implementation of industry standards and norms, ensure the quality of products and services, and promote healthy and orderly competition. (4) Encourage public–private partnership (PPP) to invest in infrastructure and projects in prefabricated buildings.
Financial stability () ranks second in terms of weight. The financial stability of prefabricated building component suppliers directly reflects their operational capability and stability. If a supplier faces issues such as funding shortages, debt pressures, or financial risks, it may lead to a disruption in the capital chain and the inability to complete component orders smoothly. Therefore, the financial condition has a significant impact on the vulnerability of suppliers.
Market demand fluctuation () ranks third in terms of weight. This indicates that market demand fluctuations are an important indicator but have a slightly smaller impact on the vulnerability of suppliers compared to the previous two. The possible reason for this, is that the demand for the prefabricated building market in China still shows a clear upward trend, and any potential market fluctuations would be relatively short-term impacts.
Based on the above analysis, the weight calculation results based on the PLTS-MAHP are reasonable and interpretable.
4.3. Vulnerability Assessment Based on the PLTS-CIM
(1) Establishing PLST for evaluating comment information:
Due to the uncertainty in the occurrence probability of vulnerability factors for prefabricated building component suppliers, this study invited five experts to quantitatively assess the vulnerability of 18 secondary indicators of the PC supplier based on a set of probability linguistic terms. The set of linguistic terms was defined as , where is extremely risky, is highly risky, is moderately risky, is slightly risky, and is extremely slightly risky.
(2) Constructing the probability linguistic evaluation matrix:
A questionnaire survey method was used to collect the experts’ evaluations of each secondary indicator. The probability linguistic evaluation matrix was then formulated:
(3) Assuming that the expert weights of the five experts in this study were consistent, the aggregated expert assessment matrix can be obtained based on Equation (13):
(4) Solving for vulnerability distribution:
By using Equations (17) and (18), the superimposed vulnerability distributions for Market competition intensity () and Material supply stability () can be obtained as follows:
The detailed calculation process of Equation (29) can be found in Table 5.

Table 5.
Superimposed probability for vulnerability levels of and .
Similarly, the superimposed vulnerability distribution for all secondary indicators can be calculated. Based on this, the vulnerability distribution for each primary indicator can be calculated (refer to Table 6).

Table 6.
Vulnerability distribution of primary indicators.
Based on the weight information obtained in Section 4.2, the probability distribution of the vulnerability levels for prefabricated component suppliers in modular construction can be determined, as shown in Table 7.

Table 7.
Probability distribution of the vulnerability levels.
According to Table 7, the vulnerability level of the supplier falls between and , and is closer to . Through an investigation into the component supply process for this project, it was found that the supplier was able to deliver the required prefabricated components on time, ensuring the stability of the supply chain. They had sufficient production capacity and resources to meet project demands, thus avoiding issues of over reliance on a single supplier or supply difficulties. Quality inspections conducted on site showed that the provided prefabricated components by this supplier were stable in quality and complied with relevant building standards and regulations. Furthermore, during the construction of the case project, there were three instances of design changes requiring urgent adjustments. The supplier was able to flexibly adapt their component production and supply with the help of their professional technical team and engineers. Therefore, the evaluation results presented in this article are consistent with the actual conditions of the project, and it could be considered that the index system constructed in this paper is complete and comprehensive.
5. Discussions
5.1. Comparison of Computational Performance with Classical CIM
In order to highlight the superiority of the proposed model, this paper compares it with the computational principles of the traditional CIM method. According to the classical CIM method, a re-survey should be conducted; as such, the same five experts were invited back to quantitatively assess the risk of the 18 secondary indicators based on the risk evaluation set {extremely dangerous, highly dangerous, moderately dangerous, slightly dangerous, and extremely slightly dangerous}.
To avoid the influence of weight calculation on the discussion in this section, the classical CIM model also adopts the weight information calculated in Section 4.2 of this paper. The distribution of the supplier’s secondary indicator risks is shown in Table 8.

Table 8.
Vulnerability distribution for secondary indicators based on the classical CIM model.
With the combination of weight information for the secondary indicators, the total probability distribution of vulnerability levels for prefabricated component suppliers in modular construction can be obtained and showed in Table 9.

Table 9.
Vulnerability distribution of primary indicators under the classical CIM method.
By incorporating the weightings of the three primary indicators and the calculation results from Table 9, the evaluation results of the project based on the traditional CIM method can be determined. The probabilities for the five vulnerability levels are as follows: 0.0022, 0.0164, 0.0565, 0.4274, and 0.4975, respectively. Consequently, the evaluation result based on the traditional CIM method falls between the categories of “low risk” and “very low risk”, leaning towards the latter.
When comparing the aforementioned evaluation results with those obtained from the PLTS-CIM method, it becomes apparent that the outcomes of both algorithms were remarkably similar. However, the evaluation results derived from the PLTS-CIM approach offered certain advantages. Firstly, in contrast to the classical CIM method, the results yielded by the PLTS-CIM approach exhibited a higher resolution. Under the classical CIM model, the probabilities for “low risk” and “very low risk” are 0.4274 and 0.4975, respectively, with a mere difference of 0.0701 (equivalent to a 14.09% variation) between them. Conversely, under the PLTS-CIM, the probabilities for “low risk” and “very low risk” amount to 0.411 and 0.5026, respectively, thus showing a significance difference of 0.0916 (corresponding to an 18.23% variation). Enhanced resolution in the evaluation results can effectively diminish the possibility of misjudgment on the part of management personnel.
Secondly, in comparison with the classical CIM method, the evaluation results based on the PLTS-CIM approach are more distinct. In the PLTS-CIM, the probability of falling into the category of “very low risk” is 0.5026, surpassing the 50% threshold. Furthermore, the probabilities of encountering “high risk”, “moderate risk”, and “low risk” are substantially lower in the PLTS-CIM than in the traditional CIM. This discrepancy can be attributed to the fact that PLTS expansion enables the CIM model to provide a more elaborate description of expert opinions, thereby leading to more focused evaluation results. Evidently, more prominent evaluation results can effectively minimize the likelihood of misjudgment by management personnel.
5.2. Influence of Different PLTS Standardization Methods on Evaluation Results
Different normalization methods for PLTS can potentially affect the performance evaluation of the proposed model in this study. In order to evaluate this impact, we analyze two additional recently developed normalization methods for PLTS [26,44,45]. It should be emphasized that only the standardization methods are different, and other calculation processes are exactly the same.
Normalization Method 1 was proposed by Pang et al. [26]. It is widely used and considered a classic method in the relevant field, and it is also the method selected in this study. This method uniformly distributes the value of among the probabilities:
Normalization Method 2 was introduced by Zhang et al. [55]. Its calculation equation is as follows:
where , and is the number of different language terms in the language term set .
Normalization Method 3, proposed by Song and Li [45], is an improvement on Method 1 of normalization.
Rule 1: If language term is not found in the , there is no need to find it in the normalized PLTS.
Rule 2: If , then is allocated to certain language terms in according to the following rules:
(1) Optimistic attitude: is allocated to the largest binary language term in , which corresponds to the largest index.
(2) Pessimistic attitude: is evenly allocated among the smallest binary language terms in L(p), which correspond to the smallest indexes.
(3) Neutral attitude: is evenly allocated, as proposed by Pang et al. [26] in the Normalization Method 1.
The three different normalization methods use the same PLTS information, with slight variations in the PLTS normalization process. Their results are shown in Table 10.

Table 10.
Calculation results based on three different normalization algorithms.
As can be seen from Table 10, the calculation results of the three normalization methods are especially close. This shows that it is reasonable to choose the most classical normalization algorithm in this paper.
Compared with the other two algorithms, the result of Normalization Method 2 is more optimistic—even more optimistic than the result of optimism in Normalization Method 3. In Normalization Method 3, with the change in managers’ attitude from optimism to pessimism, the probability of being at the level increases. However, even if the manager is very pessimistic, the probability that the project is at the level is still the largest. That is to say, in this case, the attitude of managers will not affect the final evaluation results.
To summarize, considering the calculation performance and amount of calculation, this paper suggests that managers adopt classical standardization methods. Of course, this conclusion needs more engineering cases to prove this assertion.
6. Conclusions
To accurately evaluate the vulnerability of prefabricated components in prefabricated buildings, this study proposes a novel vulnerability evaluation index system and evaluation model for prefabricated construction suppliers. Building upon the PSR model, this research delves into the external or internal pressure factors faced by suppliers, their current status or situation, and their actions or strategies in response to pressure factors. Combining these aspects with literature research, this study developed an evaluation index system with 18 indicators. The vulnerability of suppliers was analyzed from both macro and micro perspectives. The influence of external factors and internal details such as capabilities, resources, and management were considered. The proposed index system is easy to comprehend, is practical, and provides valuable insights or effective vulnerability assessment. In addition, this study used the multiplicative AHP with an extended probability language terminology set to obtain weight information. Based on this, it introduced the CIM model with an extended PLTS to evaluate the vulnerability of prefabricated building suppliers in the reconstruction and resettlement housing project of urban shanty towns in the Taohua South Road Community, Xihu District, Nanchang City. Case studies show that state is the most important primary indicator. The degree of policy support, financial stability, and market demand fluctuation are the most important secondary indicator indicators. Managers can manage important indicators to improve efficiency. The probability that the vulnerability assessment result of this project is low risk is set at 0.411, and the probability of extremely low risk is set at 0.5026. The conclusions of these cases are essentially consistent with engineering practice. Compared with the traditional CIM model, the expert decision information of this method is more scientific and comprehensive, resulting in more objective and effective outcomes through data analysis. The PLTS standardization method has little influence on the evaluation results of this case.
Based on the research results of this paper, the future research directions in this field are as follows. (1) The vulnerability evaluation index system of prefabricated building suppliers will be continuously enriched and improved from the perspective of stakeholders or the whole life cycle. (2) According to the characteristics of vulnerability assessment of prefabricated building suppliers, more standardized methods of probabilistic language terms set will be proposed. (3) Meta-heuristic optimization algorithms (particle swarm optimization algorithm [56], genetic algorithm [57], and so on), artificial neural networks, or data mining algorithms will be considered to evaluate the vulnerability of prefabricated building suppliers.
Author Contributions
Conceptualization, X.W. and H.P.; methodology, X.W. and H.W.; software, H.W.; formal analysis, X.W.; investigation, X.W. and H.P.; data curation, X.W. and H.P.; writing—original draft preparation, X.W. and H.W.; writing—review and editing, X.W. and H.P.; project administration, Z.H.; funding acquisition, X.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Science and Technology R&D Project of China Construction Fourth Bureau (HX202212140002).
Data Availability Statement
The data are not publicly available due to privacy of cooperative unit. The case analysis data used to support the findings of this study are available from the corresponding author upon request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Li, C.Z.; Li, S.; Li, X.; Wu, H.; Xiao, B.; Tam, V.W.Y.; Asiedu-Kwakyewa, C. A Scientometric Review of Management of Prefabricated Construction from 2011–2021. Buildings 2022, 12, 1515. [Google Scholar] [CrossRef]
- Liu, K.N.; Su, Y.K.; Zhang, S.J. Evaluating Supplier Management Maturity in Prefabricated Construction Project-Survey Analysis in China. Sustainability 2018, 10, 3046. [Google Scholar] [CrossRef]
- Deep, S.; Gajendran, T.; Jefferies, M. Factors Influencing Power and Dependence for Collaboration among Construction Project Participants. J. Leg. Aff. Disput. Resolut. Eng. Constr. 2020, 12, 06520001. [Google Scholar] [CrossRef]
- Kechagias, E.P.; Gayialis, S.P.; Papadopoulos, G.A.; Papoutsis, G. An Ethereum-Based Distributed Application for Enhancing Food Supply Chain Traceability. Foods 2023, 12, 1220. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Yan, F.X.; Jia, F.; Chen, L.J. Building supply chain resilience through ambidexterity: An information processing perspective. Int. J. Logist.-Res. Appl. 2023, 26, 172–189. [Google Scholar] [CrossRef]
- Gayialis, S.P.; Kechagias, E.P.; Papadopoulos, G.A.; Kanakis, E. A Smart-Contract Enabled Blockchain Traceability System Against Wine Supply Chain Counterfeiting. In Proceedings of the IFIP WG 5.7 International Conference on Advances in Production Management Systems (APMS)-Smart Manufacturing and Logistics Systems-Turning Ideas into Action, Gyeongju, Republic of Korea, 25–29 September 2022; pp. 477–484. [Google Scholar]
- Gayialis, S.P.; Kechagias, E.P.; Konstantakopoulos, G.D. A city logistics system for freight transportation: Integrating information technology and operational research. Oper. Res. 2022, 22, 5953–5982. [Google Scholar] [CrossRef]
- Chen, Z.; Wang, X. Specific investment, supplier vulnerability and profit risks. J. Bus. Financ. Account. 2020, 47, 1215–1237. [Google Scholar] [CrossRef]
- Chen, Z.Q.; Wang, X.Q. Specific investment and supplier vulnerability. Econ. Lett. 2017, 151, 16–18. [Google Scholar] [CrossRef]
- Demirli, K.; Yimer, A.D. Fuzzy scheduling of a build-to-order supply chain. Int. J. Prod. Res. 2008, 46, 3931–3958. [Google Scholar] [CrossRef]
- Zhu, T.; Liu, G. A Novel Hybrid Methodology to Study the Risk Management of Prefabricated Building Supply Chains: An Outlook for Sustainability. Sustainability 2023, 15, 361. [Google Scholar] [CrossRef]
- Wang, Q.K.; Duan, H.L.; Shen, C.X. Selection and Evaluation of Component Suppliers Based on Resilience. In Proceedings of the ICCREM 2021: Challenges of the Construction Industry under the Pandemic, Beijing, China, 16–17 October 2021; pp. 425–437. [Google Scholar]
- Song, Y.H.; Wang, J.W.; Guo, F.; Lu, J.Q.; Liu, S. Research on Supplier Selection of Prefabricated Building Elements from the Perspective of Sustainable Development. Sustainability 2021, 13, 6080. [Google Scholar] [CrossRef]
- Jiang, L.; Li, Z.F.; Li, L.; Gao, Y.L. Constraints on the Promotion of Prefabricated Construction in China. Sustainability 2018, 10, 2516. [Google Scholar] [CrossRef]
- Aleksic, A.; Puskaric, H.; Tadic, D.; Stefanovic, M. Project management issues: Vulnerability management assessment. Kybernetes 2017, 46, 1171–1188. [Google Scholar] [CrossRef]
- Karagiorgos, K.; Thaler, T.; Huebl, J.; Maris, F.; Fuchs, S. Multi-vulnerability analysis for flash flood risk management. Nat. Hazards 2016, 82, S63–S87. [Google Scholar] [CrossRef]
- He, L.; Shen, J.; Zhang, Y. Ecological vulnerability assessment for ecological conservation and environmental management. J. Environ. Manag. 2018, 206, 1115–1125. [Google Scholar] [CrossRef] [PubMed]
- Xu, J.; Song, S.; Zhai, H.; Yuan, P.; Chen, M. A new analytical framework for network vulnerability on subway system. Concurr. Comput.-Pract. Exp. 2020, 32, e5508. [Google Scholar] [CrossRef]
- Zhang, L.; Xiao, Z.; Ren, S.; Qin, Z.; Goh, R.S.M.; Song, J. Measuring the vulnerability of bike-sharing system. Transp. Res. Part A-Policy Pract. 2022, 163, 353–369. [Google Scholar] [CrossRef]
- Dyckhoff, H.; Souren, R. Integrating multiple criteria decision analysis and production theory for performance evaluation: Framework and review. Eur. J. Oper. Res. 2022, 297, 795–816. [Google Scholar] [CrossRef]
- Miao, C.; Teng, J.; Wang, J.; Zhou, P. Population vulnerability assessment of geological disasters in China using CRITIC-GRA methods. Arab. J. Geosci. 2018, 11, 268. [Google Scholar] [CrossRef]
- Chodur, G.M.; Zhao, X.; Biehl, E.; Mitrani-Reiser, J.; Neff, R. Assessing food system vulnerabilities: A fault tree modeling approach. BMC Public Health 2018, 18, 817. [Google Scholar] [CrossRef]
- Tian, S.B.; Zhang, P.L.; Liu, T.X. Application of Controlled Intervals and Memory Model in Risk Evaluation of Expressway Investment. In Proceedings of the 5th International Conference on Innovation & Management, Vols I and II, Maastricht, The Netherlands, 10–11 December 2008; pp. 1696–1701. [Google Scholar]
- Zhang, N.M.; Luo, F.L.; Bi, L.; Hu, L.X. Cost Risk Assessment for Large Hydropower Project Based on the Probability Distribution. In Proceedings of the Advances in Hydrology and Hydraulic Engineering, PTS 1 and 2, Zhangjiajie, China, 10–12 August 2012; p. 1015. [Google Scholar]
- Kavikumar, R.; Sakthivel, R.; Kwon, O.M.; Kaviarasan, B. Faulty actuator-based control synthesis for interval type-2 fuzzy systems via memory state feedback approach. Int. J. Syst. Sci. 2020, 51, 2958–2981. [Google Scholar] [CrossRef]
- Pang, Q.; Wang, H.; Xu, Z. Probabilistic linguistic linguistic term sets in multi-attribute group decision making. Inf. Sci. 2016, 369, 128–143. [Google Scholar] [CrossRef]
- Zadeh, L. Fuzzy sets. Inform. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Baral, C.; Gelfond, M.; Rushton, N. Probabilistic reasoning with answer sets. Theory Pract. Log. Program. 2009, 9, 57–144. [Google Scholar] [CrossRef]
- Wu, X.L.; Liao, H.C.; Xu, Z.S.; Hafezalkotob, A.; Herrera, F. Probabilistic Linguistic MULTIMOORA: A Multicriteria Decision Making Method Based on the Probabilistic Linguistic Expectation Function and the Improved Borda Rule. IEEE Trans. Fuzzy Syst. 2018, 26, 3688–3702. [Google Scholar] [CrossRef]
- Wang, S.Q.; Wei, G.W.; Wu, J.; Wei, C.; Guo, Y.F. Model for selection of hospital constructions with probabilistic linguistic GRP method. J. Intell. Fuzzy Syst. 2021, 40, 1245–1259. [Google Scholar] [CrossRef]
- Lin, M.; Huang, C.; Xu, Z.; Chen, R. Evaluating IoT Platforms Using Integrated Probabilistic Linguistic MCDM Method. IEEE Internet Things J. 2020, 7, 11195–11208. [Google Scholar] [CrossRef]
- Zhang, X.L.; Xing, X.M. Probabilistic Linguistic VIKOR Method to Evaluate Green Supply Chain Initiatives. Sustainability 2017, 9, 1231. [Google Scholar] [CrossRef]
- Xie, W.Y.; Xu, Z.S.; Ren, Z.L.; Wang, H. Probabilistic Linguistic Analytic Hierarchy Process and Its Application on the Performance Assessment of Xiongan New Area. Int. J. Inf. Technol. Decis. Mak. 2018, 17, 1693–1724. [Google Scholar] [CrossRef]
- Feng, Y.X.; Zhang, Z.F.; Tian, G.D.; Fathollahi-Fard, A.M.; Hao, N.N.; Li, Z.W.; Wang, W.J.; Tan, J.R. A Novel Hybrid Fuzzy Grey TOPSIS Method: Supplier Evaluation of a Collaborative Manufacturing Enterprise. Appl. Sci. 2019, 9, 3770. [Google Scholar] [CrossRef]
- Hughey, K.F.D.; Cullen, R.; Kerr, G.N.; Cook, A.J. Application of the pressure-state-response framework to perceptions reporting of the state of the New Zealand environment. J. Environ. Manag. 2004, 70, 85–93. [Google Scholar] [CrossRef] [PubMed]
- Ashraf, A.; Haroon, M.A.; Ahmad, S.; Abowarda, A.S.; Wei, C.Y.; Liu, X.H. Use of remote sensing-based pressure-state-response framework for the spatial ecosystem health assessment in Langfang, China. Environ. Sci. Pollut. Res. 2023, 30, 89395–89414. [Google Scholar] [CrossRef] [PubMed]
- Han, Y.H.; Skibniewski, M.J.; Wang, L.F. A Market Equilibrium Supply Chain Model for Supporting Self-Manufacturing or Outsourcing Decisions in Prefabricated Construction. Sustainability 2017, 9, 2069. [Google Scholar] [CrossRef]
- Akinwande, T.; Hui, E.C.M. Housing supply value chain in relation to housing the urban poor. Habitat Int. 2022, 130, 102687. [Google Scholar] [CrossRef]
- Han, Y.; Wang, L.; Kang, R. Influence of consumer preference and government subsidy on prefabricated building developer’s decision-making: A three-stage game model. J. Civ. Eng. Manag. 2023, 29, 35–49. [Google Scholar] [CrossRef]
- Deng, W.B.; Wang, H.J.; Yuan, Y. Research on Evaluation of Prefabricated Building Component Suppliers Based on Dominance-Based Rough Set Approach. In Proceedings of the 6th International Symposium on Project Management (ISPM2018), Chongqing, China, 21–23 July 2018; pp. 131–136. [Google Scholar]
- Wang, D.; Luo, J.Y.; Wang, Y.K. Multifactor uncertainty analysis of prefabricated building supply chain: Qualitative comparative analysis. Eng. Constr. Archit. Manag. 2022. [Google Scholar] [CrossRef]
- Luo, L.; Li, Y.; Wang, X.; Jin, X.; Qin, Z. Supply Chain Vulnerability in Prefabricated Building Projects and Digital Mitigation Technologies. IEEE Trans. Eng. Manag. 2023, 1–13. [Google Scholar] [CrossRef]
- Saeed, K.A.; Malhotra, M.K.; Abdinnour, S. How supply chain architecture and product architecture impact firm performance: An empirical examination. J. Purch. Supply Manag. 2019, 25, 40–52. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, Y.Q.; Gao, W.J.; Kuroki, S. Life Cycle Environmental and Cost Performance of Prefabricated Buildings. Sustainability 2020, 12, 2609. [Google Scholar] [CrossRef]
- Song, Y.M.; Li, G.X. A large-scale group decision-making with incomplete multi-granular probabilistic linguistic term sets and its application in sustainable supplier selection. J. Oper. Res. Soc. 2019, 70, 827–841. [Google Scholar] [CrossRef]
- Wu, X.L.; Liao, H.C. An approach to quality function deployment based on probabilistic linguistic term sets and ORESTE method for multi-expert multi-criteria decision making. Inf. Fusion 2018, 43, 13–26. [Google Scholar] [CrossRef]
- Lootsma, F.A. Scale sensitivity in the multiplicative AHP and SMART. J. Multi-Criteria Decis. Anal. 1993, 2, 87–110. [Google Scholar] [CrossRef]
- Triantaphyllou, E. Two new cases of rank reversals when the AHP and some of its additive variants are used that do not occur with the multiplicative AHP. J. Multi-Criteria Decis. Anal. 2001, 10, 11–25. [Google Scholar] [CrossRef]
- Lin, M.; Chen, Z.; Xu, Z.; Gou, X.; Herrera, F. Score function based on concentration degree for probabilistic linguistic term sets: An application to TOPSIS and VIKOR. Inf. Sci. 2021, 551, 270–290. [Google Scholar] [CrossRef]
- Garg, V.K.; Kumar, R.; Marcus, S.I. A probabilistic language formalism for stochastic discrete-event systems. IEEE Trans. Autom. Control 1999, 44, 280–293. [Google Scholar] [CrossRef]
- Stojcic, M.; Zavadskas, E.K.; Pamucar, D.; Stevic, Z.; Mardani, A. Application of MCDM Methods in Sustainability Engineering: A Literature Review 2008–2018. Symmetry 2019, 11, 350. [Google Scholar] [CrossRef]
- Muniz, J.; Fonseca-Pedrero, E. Ten steps for test development. Psicothema 2019, 31, 7–16. [Google Scholar] [CrossRef]
- Peters, D.M.; Fritz, S.L.; Krotish, D.E. Assessing the Reliability and Validity of a Shorter Walk Test Compared With the 10-Meter Walk Test for Measurements of Gait Speed in Healthy, Older Adults. J. Geriatr. Phys. Ther. 2013, 36, 24–30. [Google Scholar] [CrossRef]
- Ekanayake, E.; Shen, G.Q.P.; Kumaraswamy, M.M.; Owusu, E.K. Identifying supply chain vulnerabilities in industrialized construction: An overview. Int. J. Constr. Manag. 2022, 22, 1464–1477. [Google Scholar] [CrossRef]
- Zhang, X.L.; Liao, H.C.; Xu, B.; Xiong, M.F. A probabilistic linguistic-based deviation method for multi-expert qualitative decision making with aspirations. Appl. Soft Comput. 2020, 93, 106362. [Google Scholar] [CrossRef]
- Gad, A.G. Particle Swarm Optimization Algorithm and Its Applications: A Systematic Review. Arch. Comput. Methods Eng. 2022, 29, 2531–2561. [Google Scholar] [CrossRef]
- Alhijawi, B.; Awajan, A. Genetic algorithms: Theory, genetic operators, solutions, and applications. Evol. Intell. 2023. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).