Abstract
Frequent data sharing in Vehicular Ad Hoc Networks (VANETs) necessitates a robust foundation of secure access control to ensure data security. Existing ciphertext-policy attribute-based encryption schemes are constrained by the performance bottleneck of a single attribute authority. Furthermore, although many schemes adopt outsourced decryption, the verifiability of the decryption results is not guaranteed. Therefore, this paper proposes a Symmetrically Verifiable Outsourced Decryption Data Sharing Scheme with Privacy-Preserving for VANETs (VODDS). To balance the computational overhead across multiple authorities, VODDS introduces a distributed key distribution mechanism that organizes them into groups. Within each group, the key distribution credential is generated through a Group Key Agreement, with each round secured by a Byzantine consensus mechanism to achieve a balance between security and efficiency. User identities are converted into anonymous representations via hashing for embedding into the attribute keys. Furthermore, blockchain technology is used to record a hash commitment for the verification ciphertext. This enables the user to verify the outsourced result through a smart contract, which performs a symmetrical verification by matching the user’s locally computed hash against the on-chain record. Moreover, VODDS employs a linear secret sharing scheme to achieve policy hiding. We provide security analysis under the q-parallel Bilinear Diffie–Hellman Exponent and Decisional Diffie–Hellman assumptions, which proves the security of VODDS. In addition, VODDS exhibits higher efficiency compared to related schemes in the performance evaluation.
1. Introduction
Benefiting from the growing demand for wireless data exchange in transportation environments, Vehicular Ad Hoc Networks (VANETs) have attracted increasing attention []. As an emerging technology, VANETs enable vehicles to share information with other entities (e.g., vehicles, pedestrians, infrastructure) []. To ensure the security of shared data (e.g., vehicle speed, energy consumption, road conditions, weather), data encryption is essential [,,].
Frequent data sharing in Vehicular Ad Hoc Networks (VANETs) demands robust and flexible cryptographic solutions. Traditional encryption schemes are often limited by single- or coarse-grained data sharing models. In contrast, Ciphertext-Policy Attribute-Based Encryption (CP-ABE) empowers data owners to define flexible access policies over encrypted data []. In CP-ABE, user decryption keys are bound to sets of attributes, and a ciphertext can only be decrypted if the user’s attributes satisfy the policy embedded within it. This fine-grained access control mechanism makes CP-ABE particularly suitable for the complex access control requirements of VANETs.
Nevertheless, a limitation of some CP-ABE schemes [,,,] is their reliance on a single Attribute Authority (AA) for key distribution. This centralized approach inevitably creates a performance bottleneck in large-scale VANET environments. Therefore, schemes with multiple attribute authorities have been designed. In these schemes [,,], the authority for distributing attribute keys is delegated to specific AAs, which then operate independently. However, when certain attributes are popular and common, the corresponding keys are requested at a high frequency. This inevitably imposes a heavy computational overhead on the AA managing those attributes.
In addition, the storage of ciphertexts generated by CP-ABE encryption in VANETs is a significant challenge [,,]. In recent years, cloud storage has been employed to store these massive ciphertexts. Then vehicles download the ciphertexts from the cloud and decrypt them locally []. However, this approach introduces substantial communication and computational overhead for data users, making it unfeasible for resource-constrained individuals and thereby hindering wide deployment.
To ensure secure data sharing and alleviate the user-side computational burden in VANETs, several outsourced decryption schemes have been proposed [,,]. In such schemes, most decryption computations are offloaded to a cloud server. The user can then recover the data by performing only a lightweight operation on the result returned by the server. However, in this cloud-centric outsourcing model [], the user must first send a request to the remote cloud and wait for a response. Subsequently, the user must submit the keys and parameters required for partial decryption. Only after receiving these essential components does the cloud perform the partial decryption and return the result to the user. This process involves multiple rounds of long-distance interaction, incurring substantial communication overhead and latency.
Due to the uncertainty of outsourced decryption, verification of outsourced decryption results is necessary. The schemes in [,] adopt a ciphertext-verification mechanism, in which the user compares a verification ciphertext with the outsourced decryption result and then decides whether to perform local decryption based on this comparison. However, integrity verification for the verification ciphertext has not yet been achieved. Concurrently, ciphertexts are vulnerable to malicious tampering, making integrity verification a critical challenge. Therefore, there is a pressing need for a cloud-based CP-ABE scheme that supports edge-assisted outsourced decryption to reduce user-side cost and provides a comprehensive verification mechanism for outsourced results to ensure their reliability.
Motivated by the problems of single-point performance bottlenecks in multi-authority key distribution, insufficient privacy protection, and the lack of reliable verification of outsourced decryption, we present our proposed scheme. The main contributions of this paper are summarized as follows:
- (1)
- We propose a Symmetrically Verifiable Outsourced Decryption Data Sharing Scheme with Privacy-Preserving for VANETs (VODDS). In VODDS, AAs are partitioned into groups, and a PBFT-style Byzantine protocol is introduced during the in-group negotiation of key-distribution credentials. This mechanism spreads computation across authorities while tolerating partial faults. Users derive hash-based pseudonyms that bind to attribute keys for key extraction, and access policies are concealed via an LSSS-based construction to protect private information.
- (2)
- VODDS leverages blockchain and smart contracts to enable a symmetrically verifiable outsourced decryption. A hash of the verification ciphertext, generated during encryption, is stored on the blockchain as a commitment. During verification, the smart contract performs a symmetric check by matching the hash computed by the user from the returned result against the on-chain commitment. This process reliably detects incorrect or tampered outsourced decryption results, establishing a trust anchor for secure data sharing.
- (3)
- We conduct a rigorous security analysis and a detailed performance evaluation of VODDS. The scheme’s security is formally proven under the q-parallel BDHE and DDH assumptions, complemented by an informal analysis; additionally, a comprehensive performance evaluation from both theoretical and experimental perspectives demonstrates its high efficiency through comparisons with existing schemes in terms of functionality, storage, and computational overhead.
The outline of this paper is as follows. Section 2 reviews the related work, and Section 3 introduces the preliminaries. Section 4 formulates the problem by presenting the system model, security model, and a formal definition of VODDS. The specific construction of VODDS is detailed in Section 5, followed by its security analysis in Section 6. Section 7 presents the performance evaluation. Finally, Section 8 concludes the paper and discusses future work.
2. Related Work
2.1. CP-ABE
Originally proposed by Sahai and Waters [], the concept of ABE enables fine-grained access control to improve the efficiency of data sharing, and extensive research has subsequently been carried out on this basis. Goyal et al. [] first introduced the concept of CP-ABE, which associates access policies with ciphertexts to achieve secure and flexible access control of outsourced data. Cheung and Newport [] later presented the first provably secure CP-ABE scheme in the standard model, whose security is based on the Decisional Bilinear Diffie–Hellman (DBDH) assumption, where access policies are expressed by simple AND gates. This work attracted much attention due to its improved encryption efficiency and suitability for complex application scenarios such as cloud storage. Subsequently, Bethencourt et al. [] proposed a CP-ABE scheme that employs a tree-based access structure, where access policies are represented as trees, attributes as nodes, and the branching structure encodes access control logic. Guo et al. [] proposed an offline/online encryption technique for CP-ABE, which allows users to pre-compute some ciphertext components in advance, thereby reducing online computation and offering effective support for resource constrained entities.
2.2. Access Policy Hiding
As an important part of CP-ABE, the security of access policies is necessary. Boneh and Waters [] proposed a CP-ABE scheme for hidden vector encryption, which hides the field names in the attribute vector to achieve anonymity. Nishide et al. [] proposed a partial policy hiding scheme in CP-ABE, where attribute values are defined as secret values hidden in the access structure, but their AND gates structure limits the expression of access policies. In the scheme proposed by Hao et al. [], the randomization technology is used to completely hide the attribute information in the access policy, and a fuzzy attribute localization mechanism based on garbled bloom filter is developed to help the authorized receiver efficiently locate its attributes and successfully decrypt the ciphertext. LSSS [] provides a more expressive framework for representing access policies. A Poly-ABE scheme was proposed by Xue et al. [], which uses LSSS expressing access policy and combines hidden vector encryption to achieve secure access control in multi-energy systems. Zhao et al. [] proposes a CP-ABE scheme for VANETs that uses LSSS to express access policies and uses fog nodes to participate in the encryption process.
2.3. Outsourced Decryption of CP-ABE
The purpose of outsourced decryption is to reduce the computational burden on the user’s side. Green et al. [] have long proposed an ABE scheme that supports outsourced decryption, which provides a transformation key to perform outsourced decryption in the cloud, reducing the user’s decryption overhead. Immediately afterwards, Li et al. [] applied outsourced decryption to CP-ABE, and access control-related decryption operations were offloaded to a third party in their work. Guo et al. [] put forward an outsourced decryption scheme applied in VANETs that uses validation ciphertext to help users confirm the correctness of partial decryption results. Ge et al. [] proposed a verifiable outsourced decryption scheme and used smart contracts to improve the claim mechanism against the outsourced decryption party. Wang et al. [] proposed a cloud-assisted partial decryption CP-ABE solution in which the cloud is assigned to perform partial decryption but cannot fully decrypt data because it does not have a user identity. Chen et al. [] proposed an outsourced decryption plan to introduce smart contracts, which also formulated a reward and punishment mechanism for outsourced decryption parties.
2.4. Multi-Authority CP-ABE
The multi-authority [] setting distributes the key distribution authority to AAs, which can distribute keys to users more efficiently than the single-authority setting. Ghorbel et al. [] proposed an attribute-based cryptographic scheme for access management in cloud services using blockchain. Belguith et al. [] proposed a CP-ABE scheme that relies on multi-attribute authority, which considers anti-collusion attacks. The decentralized CP-ABE scheme proposed by Zhang et al. [] implements an adaptive and secure single-round distributed key generation protocol. Ren et al. [] utilized blockchain nodes that act as trusted proxy entities to generate and distribute key fragments. In the proposal proposed by Lin et al. [], load balancing of authorization in distributed systems is achieved based on the characteristic of multi-authority. Their specific nodes are equipped with cryptographic reverse firewalls to prevent information leakage.
3. Preliminaries
This section introduces the background knowledge used in VODDS, including the bilinear map, group key agreement, the Byzantine Agreement, and the Decisional q-parallel BDHE assumption. The descriptions of key symbols are summarized in Table 1.

Table 1.
Symbols and their meanings.
3.1. Bilinear Map
Let and be multiplicative cyclic groups of prime order p. A bilinear map can be defined, with g denoting a generator of . The map e satisfies the following properties:
- (1)
- : For all and , it holds that .
- (2)
- -: which ensures that the map is not trivially constant.
- (3)
- : There exists an efficient algorithm to compute for any .
3.2. Group Key Agreement
Building upon the Group Key Agreement (GKA) protocol [], we organize AAs into groups based on the attributes they manage. For each attribute, the corresponding AAs form a group responsible for issuing user-related keys, and the generation of key distribution certificate is participated by all AA collaborators within the group. The construction of the AAs grouping mechanism based on GKA is described as the following matrix.
Our single-round GKA protocol is described as follows.
: When the system is initialized, is used as input and outputs the common parameter set .
: Take as a set of group members, and correspondingly, their identities .
: generates its own public key and broadcasts its own signature line:
for , is the signature of to , and ◯ represents is not public.
: The group public key is:
: can calculate its key distribution certificate from the corresponding column of the matrix:
3.3. Byzantine Agreement
In distributed systems, Byzantine Agreement refers to protocols that enable nodes to reach a collective decision, even when a subset of nodes fails or behaves arbitrarily. A Byzantine Agreement protocol must satisfy the following properties:
- (1)
- : All honest nodes must output the same value.
- (2)
- : If all honest nodes propose the same value v, then any honest node’s output must be v.
- (3)
- : The protocol remains secure and functional as long as no more than t nodes exhibit arbitrary faulty behavior, where and n is the total number of nodes.
VODDS employs the Byzantine Agreement during the initialization of AA groups to ensure that each AA is reliably authenticated by all other members. This approach aims to enhance the reliability of the distributed key distribution process.
3.4. Decisional q-Parallel BDHE Assumption
Let be a bilinear group pair of prime order p, with generator and bilinear map . Let q be a polynomial in the security parameter .
The challenger samples random elements and provides the following challenge tuple to the adversary:
Additionally, the adversary receives an element , which is either: (real case), or (random case). The adversary’s goal, in the Decisional q-parallel BDHE problem, is to distinguish which of the two cases holds.
Definition: An adversary has advantage in solving the Decisional q-parallel BDHE problem if:
where is a random element.
We say the Decisional q-parallel BDHE Assumption [] holds if for any probabilistic polynomial-time (PPT) adversary , the advantage is negligible in the security parameter .
4. Problems Formulation
4.1. System Model
As shown in Figure 1, we employ blockchain technology to store the hash value of the verification ciphertext alongside the blinded keys generated prior to data encryption and upload, while cloud servers are responsible for the long-term storage of users’ encrypted data. The VODDS framework involves six entities: (1) Trusted Authority (TA); (2) AA; (3) Cloud Storage Server (CSS); (4) Road Side Unit (RSU); (5) Data Owner (DO); and (6) Data User (DU). The roles of these entities are described as follows.

Figure 1.
System model of VODDS.
- (1)
- : TA is the fully trusted administrator of the system, responsible for system initialization and user registration with aa. In addition, TA also assists in constructing the AAs attribute group.
- (2)
- : AAs are registered by TA authentication and are responsible for issuing attribute keys to users. They are semi-trusted, meaning they are “honest-but-curious”. While they execute assigned tasks honestly, they may attempt to extract private information from user identities or abuse their permissions by distributing keys to unauthorized users. Unlike most multi-AA key distribution schemes, in which each AA manages a different attribute or attribute set, VODDS assigns frequently used attributes to be jointly managed by multiple AAs. These AAs form a management group for the corresponding attribute. In addition, the allocation of the group is not static, and we support AA to join and exit a certain attribute group. Upon receiving a user request, AA generates attribute key for the user using the key distribution credential obtained from the group.
- (3)
- : CSS stores the ciphertext uploaded by the user for a long time and sends the ciphertext in response to the RSU’s request. CSS does not store authentication ciphertext in our scenario. They are semi-credible.
- (4)
- : RSUs are communication facilities deployed on the side of the road, honest but curious. They are responsible for receiving decryption requests from users and providing outsourced decryption.
- (5)
- : DO are the initiators of data sharing and gain legal status by registering with TAs. After obtaining the data collected by the vehicle’s sensors, DO can develop an access policy to encrypt the data to be shared and upload it to CSS.
- (6)
- : The DU is the recipient of data sharing and also must register with the TA. A DU may be a vehicle, a pedestrian, or an infrastructure node. The DU requests services from the RSU. Upon receiving the outsourced decryption results provided by the RSU, the DU verifies them through a verification mechanism. Ultimately, the DU can perform the decryption operation independently.
4.2. Security Model
The security of the VODDS scheme is under a comprehensive threat model that considers the following potential adversaries:
- Collusion DU: Multiple data users may collude by pooling their attribute keys in an attempt to access data that none of them could individually decrypt.
- Semi-Trusted AAs: A subset of AAs may be malicious and refuse to reach a consensus with other legitimate AAs during the credential generation process.
- Semi-Trusted CSS and RSU: The CSS and RSU are considered “honest-but-curious.” They will execute the protocol faithfully but may try to learn additional information from the ciphertexts or intermediate results they process.
Based on the above threat model, we present the formal security models for ciphertext semantic security and leak-free distributed key distribution.
1) Ciphertext Semantic Security: In the context of the selective model, the original ciphertext generated by this method is deemed to achieve semantic security if the adversary s advantage in the corresponding game is proven to be negligible.
Init: chooses an access structure . Each row of is mapped to an attribute by . The attribute set is defined as . Finally sends to challenger .
Setup: Prior to this phase, submitted a portion of the corrupted collection to . runs the algorithm, takes as input, and then transmits the generated public parameters to , while retaining the master secret key secretly. For each attribute authority , if , only its attribute public key is revealed to . Otherwise, if , both the attribute public key and the corresponding secret key are revealed to .
Query Phase 1: is allowed to issue multiple private key queries. For each query, it submits an attribute set S and a user identity to the challenger. The challenger checks whether S satisfies the challenge access structure . If it does not satisfy the structure, the challenger proceeds to generate the corresponding private key by running the KeyGen algorithm and returns it to the adversary. Otherwise, the query is rejected.
Challenge Phase: Two equal-length messages, and , are submitted by . randomly flips a coin , and encrypts under the access structure , then sends the ciphertext to .
Query Phase 2: This stage is identical to Query Phase 1. may continue to submit attribute sets S associated with a user identity in order to obtain the corresponding private keys. These sets must also not satisfy the challenge access structure.
Guess phase: outputs a guess of .
The advantage of in outputting rightly is:
If no PPT adversary can win the game with non-negligible advantage, then the VODDS scheme is IND-sCPA secure.
2) Leak-Free Distributed Key Distribution: Inspired by Zhang et al. [], our distributed key extraction process takes into account information security in the key distribution process.
Leak-free is defined as a game between a challenger and an attacker . first submits the identity and attribute set. In the case of setting 0, entrusts a third party to independently execute the initialization and key generation algorithm, and in the case of 1, uses the identity and attribute set to interact with AA to obtain the real attribute key. selects a bit , executes the algorithm, returns the key to . Then, output guess b, its advantage is defined as:
If no PPT attacker can pass the game with the above advantages, then the distributed key distribution is leak-free.
4.3. Formal Definition of VODDS
In this section, we present the formal definition of VODDS. VODDS mainly includes the following ten algorithms.
: This algorithm is executed by the TA. On input the security parameter , it generates the public parameters and the master secret key .
: This AA registration algorithm is performed by the TA. It takes the public parameters as input and outputs the private key and public key for .
: This algorithm is executed by the TA. It takes the public parameters as input and outputs the user’s unique identifier , secret value , as well as the user’s public key .
: This process is coordinated by the TA with the participation of AAs in group . It takes as input , an attribute , a set of secret keys and identifiers . The TA first computes the group private key . Then, the AAs execute a Byzantine consensus protocol where each generates a partial signature for a claimant . Finally, the TA converts and aggregates these signatures to produce the final credential for each .
: This algorithm is executed by . It takes as input the public parameters , the user’s hashed identity , the user’s attribute set , the group secret key , the authority’s identifier , and the group size z. For each attribute assigned to this AA, it selects a random tag and random values , then computes the user’s attribute secret key which includes components , , , , and for each attribute , the components , , and .
: This algorithm is executed by the data owner. It takes as input an access structure and the user’s secret value . It randomly selects a secret and computes a vector . For each row i of M, it computes and generates the partial ciphertext containing , , , and .
: This algorithm is executed by the data owner. It takes as input the public parameters , the partial ciphertext , the message m, and the user’s secret value . It computes the main ciphertext , generates the integrity verification code , and computes additional ciphertext components containing and for each row i, and . The final ciphertext is uploaded to the CSS.
: This algorithm is executed by the data user. It takes as input the public parameters and ciphertext components , . It randomly selects and transforms the ciphertext by computing and where all components are scaled by in the exponent. It then generates the correctness verification ciphertext , uploads to the blockchain, and sends the transformed ciphertext to the CSS.
: This algorithm is executed by the RSU. It takes as input the transformed ciphertext and the user’s attribute key . The RSU first computes the set of matching attributes I between the user’s attributes and the access policy, and calculates secret sharing coefficients . It then performs a series of pairing operations to compute intermediate values Q, R, S, T, and D, ultimately deriving and . Finally, the RSU returns the transformed ciphertext to the data user.
: This algorithm is executed by the data user. It takes as input the transformed ciphertext and the user’s secret value v. The user first computes a hash value and submits it to the smart contract for verification. If the verification passes, the contract returns , which the user decrypts to obtain . Finally, the user recovers the message by computing .
5. Specific Construction of VODDS
In this section, inspired by the work of Zheng et al. [], we propose to decouple the storage of verification ciphertexts from the encrypted data directly uploaded to the Cloud Storage Server (CSS). To this end, a blockchain is deployed to store hashes of verification ciphertexts generated by DOs, enabling secure and verifiable outsourced decryption. Furthermore, to prevent unauthorized data injection or tampering, we employ smart contracts to regulate all data-writing operations on the blockchain. The overall construction process of the VODDS scheme is shown in Figure 2, and the implementation mechanism of each stage will be described in detail below.
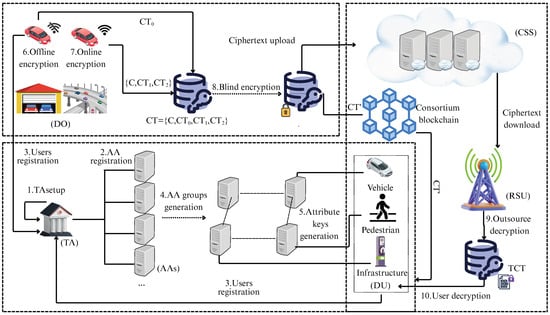
Figure 2.
Architecture and workflow of VODDS.
5.1. System Initialization
1) : Given a security parameter , let g be a generator of the group , and let p be the order of multiplicative cyclic groups and . Given a bilinear mapping and a hash function . Randomly select . Finally, exposes the parameters and keeps private.
2) : Let n denote the total number of AAs. Upon registration with the TA, each is assigned a unique identifier , which is publicly known. Then, randomly selects a secret value as its private key: . The corresponding public key is computed as .
3) : Each user registers with the and obtains a unique identifier . Then, the computes a secret value for the user. The user’s public key is defined as .
4) : First, let m denote the number of attributes in the system. For any attribute , the TA assigns appropriate AAs to manage , thereby forming an attribute group , where z is the number of members in . The TA then computes the group private key as , where . The corresponding group public key is .
Within the group, each member derives a signature through the BLS-based consensus protocol. Any attribute authority that intends to distribute a key for users must obtain identity signatures from other members in the group.
We introduce the Byzantine consensus mechanism in the process of signature. Concretely, we instantiate the above BLS consensus as a PBFT-style five-phase protocol with a per-request timestamp that binds the distribution instance. Let be the AA group for attribute , where each holds secret and public key . For the claimant with public identifier , define . The consensus process is shown in Figure 3.

Figure 3.
Consensus mechanism for AAs group.
We use a PBFT-style consensus inside with at most f Byzantine members and . Let the current view be v with primary p. A request is:
we write for message X signed by (BLS). Nodes log tuples with sequence number n.
Request: The claimant sends to the primary. The primary checks the signature and that is unused.
Pre-Prepare: If valid, the primary chooses n and multicasts:
A replica accepts this if (1) the sender is the current primary, (2) , (3) not previously used, (4) is fresh. Upon acceptance it records .
Prepare: Each accepting replica broadcasts:
Let . A node is prepared for when it has one valid PRE_PREPARE and at least Q matching PREPARE messages from distinct members. At this point each honest computes its claimant-bound partial signature:
and keeps it pending finalization.
Commit: Nodes then broadcast:
When a node collects at least Q matching COMMIT messages for , the request is decided (finalized). Each honest releases to .
Reply: The claimant accepts success after receiving valid responses from at least Q distinct members.
For each signature received by , the TA performs the transformation as follows: . Then, TA aggregates the signatures to generate ’s proof . After obtaining the certificate, the attribute authority can independently distribute attribute keys to users.
5) : For a user , let . The user’s attribute set is denoted as , where t is the number of attributes held by the user. For each attribute , an is selected to generate the attribute key of for the user. A value is chosen as the tag used during attribute key distribution. Additionally, random values are chosen. The attribute key corresponding to is:
5.2. Data Uploads
1) : Given the public parameters , an access structure is specified, where M is an matrix and maps each row i to an attribute . Randomly select , and define a vector to embed the secret s. Let denote the i-th row of M, then compute For each row i, compute a blinding value , and generate ciphertext components as:
2) : In this stage, the data owner performs the following operations. First, compute ciphertext Then, generate the integrity verification ciphertext Next, compute the ciphertext component :
Finally, is obtained and uploaded to CSS.
3) : The DU randomly chooses , then compute convert ciphertext as follows:
Finally, generate the correctness verification ciphertext . Upload to the blockchain and to CSS.
5.3. Data Download
1) : At this stage, the RSU obtains the attribute key of user and downloads the ciphertext from the CSS to perform outsourced decryption. Let the intersection between the user’s possessed attributes and the row-mapped attributes of the access structure matrix M be defined as Compute coefficients such that: where is the i-th row of the access matrix M. Then, the secret value s is defined as
For each , the RSU obtains the number of AAs in group , the global constant , and the public identifiers of each . Next, transform the ciphertext component:
Then the RSU calculate:
Finally, the RSU returns to the DU.
2) : As the RSU is an entity requiring vigilance, users must verify the decryption results returned by the RSU prior to decryption. This verification encompasses validating the correctness of parameters B and D, as well as confirming the integrity of parameter .
First, DU calculates a hash value h based on the acquired , which is described as:
Then, the DU submits h to the smart contract, which performs a symmetrical matching against the on-chain commitment. If a match is found, it indicates that , . Next, the smart contract returns , and the user decrypts it with to obtain . Finally, combined with user private (Here is the private holding value of the user that obtains the attribute key, and is the private holding value of , for clarity, note that, we explain: and are the same user) the user computes:
6. Security Analysis
6.1. IND-sCPA Security
Theorem 1.
Under the Decisional q-parallel BDHE Assumption, no PPT adversary can win the game with a non-negligible advantage. Therefore, the proposed VODDS scheme achieves IND-sCPA security.
Proof.
Assume, for contradiction, that a PPT adversary wins the selective IND-sCPA game with advantage . We construct a simulator and build an adversarial game that proves that also has a non-negligible advantage in breaking the q-parallel BDHE Assumption thanks to the non-negligible advantages of . In the construction, is given:
where T is either (real) or a random element (random). Its goal is to decide which case holds.
1) Init: commits to a target access structure with and . records the attribute rows for each attribute x.
2) Setup: picks and defines . So is implicit. For every attribute x it programs a hash oracle as:
where . For every AAk: If corrupted, choose , set and leak to . else, choose , set (keep secret). Finally, publish the simulated public parameters:
3) Key Query Phase 1: For every attribute set S queried by with , returns a user secret key: it uses genuine keys for corrupted AAs and TA components, and simulates honest-AA components with the programmed . Collusion resistance (user-specific factors ) prevents combining different keys to satisfy the policy.
4) Challenge: submits . picks and . Then, Message is calculated to:
Next, build , where and . Construct other ciphertext components, for each row i, set consistent with the public keys (BDHE bases appear inside terms). Last, send to .
5) Key Query Phase 2: Identical to Phase 1 (queries still must miss the policy).
6) Guess: outputs . answers:
The overall advantage of tackling the Decisional q-parallel BDHE Assumption is:
As shown in the result, if a PPT adversary could win the IND-sCPA security game with non-negligible advantage , then the simulator would be able to solve the Decisional q-parallel BDHE problem with the same advantage.However, the q-parallel BDHE Assumption is believed to be hard. Therefore, according to Theorem 1, our proposed scheme achieves IND-sCPA security. □
6.2. Leak-Freeness of the Distributed Key Extraction
Inspired by [], we conduct a security analysis of the distributed key extraction process based on the decisional Diffie–Hellman assumption.
Theorem 2
(Leak–Freeness). Under the decisional Diffie–Hellman assumption in the scheme’s bilinear groups, the multi-authority CP-ABE key-generation process is leak-free. Specifically, for any PPT adversary , the advantage is negligible.
Proof.
Let denote the public parameters, the public tag bound to user , the set of public keys visible to , and the transcript of all messages in the key-generation session. For , let denote the random variable equal to the view of in Game , and let be the event that outputs the bit “Real” in . We write for a negligible function in (namely, for every polynomial p there exists N such that for all ). Different occurrences of may denote different negligible functions, their sum is still negligible.
The leak-freeness advantage is defined as:
In the Real experiment, there is no extra trusted third party beyond the TA. In the Ideal experiment, the behaviors of the TA and the AAs are abstracted by an ideal functionality that, on input , returns a correctly distributed and nothing else. The simulator is PPT and has black-box access to this functionality (equivalently, the master secrets); it answers ’s queries and fabricates a transcript consistent with by replacing any blinded group element of the form with an independent uniform element in the prime-order group, simulating honest AAs’ BLS shares as for fresh , and recomputing all deterministic fields from public data and , while maintaining a consistency table keyed by to ensure identical answers across repeated queries.
Game (Real protocol). All authorities run the genuine key-generation protocol with . The adversary’s view is . By definition:
Game (Uniformizing random blindings). In , every term of the form (where r is sampled uniformly from ) is replaced by an independent uniform element of the prime-order group . Since adding a fixed permutes , the exponent is uniform in , hence is uniform in . Therefore the replacement preserves the joint distribution of , and:
Game (Simulating BLS signature shares). For each honest AA, the BLS share that appears in is replaced by where is chosen independently and uniformly from (H hashes to and is the AA’s secret exponent). If a PPT distinguisher could tell the real shares from these simulated ones (given the corresponding public information), one would obtain a PPT algorithm that breaks the standard security of BLS-type signatures, which relies on Diffie–Hellman–type assumptions in bilinear groups (e.g., q-SDH). By a standard hybrid argument over all honest shares:
Game (Simulator with master secrets). A simulator that knows all master secrets computes directly and fabricates a transcript consistent with : deterministic components are recomputed from public data and . Blinded components are resampled uniformly in as in and BLS shares follow the distribution enforced in . Consequently:
Game (Ideal world). The simulator outputs only , omitting the transcript. There exists a PPT re-simulation procedure which, given , reconstructs a transcript that is computationally indistinguishable from in : blinded parts are independent uniforms and the remaining parts are determined by public inputs and . Hence removing the transcript changes the adversary’s success probability by at most a negligible amount:
Combining the bounds by the triangle inequality yields:
Since is the Real experiment and is the Ideal experiment, we obtain:
namely, the protocol leaks no information. □
6.3. Collusion Resistance
The proposed VODDS scheme is resistant to collusion attacks, including both user collusion and AA collusion, under standard cryptographic assumptions.
- (1)
- Resistance to User Collusion
Each user is assigned a unique identity and a secret value , both generated by TA during registration. The user’s public key is computed as , and the attribute secret keys include components such as:
which embed both and in the exponent. These values ensure that each user’s keys are uniquely bound to their identity and cannot be reused or recombined across users. Even if several users share their keys in an attempt to satisfy an access policy collectively, the cryptographic binding to and makes such efforts ineffective. The attribute key components are not interoperable due to their user-specific structures, and thus the scheme inherently prevents collusion among users. This property holds under the hardness assumptions of the discrete logarithm and bilinear pairing problems.
- (2)
- Resistance to AA Collusion
To prevent collusion among AAs, the scheme introduces an Group Key Agreement mechanism to organize AAs into groups based on the attributes they manage. For each attribute group, the participating AAs jointly generate the group public key, and collaboratively distribute attribute credentials. Each AA contributes a partial signature on the attribute identifier , and the full credential is constructed by aggregating these signatures:
where denotes the group private key, which is never reconstructed explicitly. Furthermore, the signature generation follows a Byzantine Agreement protocol that ensures consistency and fault tolerance within each AA group. Under this protocol, a credential is only accepted if it is confirmed by a quorum of honest AAs. The Byzantine consensus guarantees that the system remains secure even when up to AAs behave maliciously, where n is the total number of AAs in the group.
Since the signature generation requires participation from a majority of honest AAs, no subset of malicious or colluding AAs can forge valid credentials without authorization. Moreover, each AA’s private key is tied to its identity, and cannot be simulated or substituted by others.
Therefore, the proposed VODDS scheme achieves strong resistance to both user collusion and AA collusion attacks.
7. Performance Evaluation
7.1. Functional Comparison
In this section, we compare the proposed scheme with schemes [,,,,,,]. As shown in Table 2, we analyze the schemes from eight aspects: privacy protection, multi-authority, distributed key distribution, access structure, anti-collusion for AAs, anti-collusion for DU, verifiability of outsourced decryption, and verifiability of ciphertext integrity. In the table, “✓” indicates support for the feature, “×” indicates no support, and “−” indicates either a single-AA architecture or that the scheme does not involve an AA setup.

Table 2.
Functional comparison.
Apart from the schemes in [,] and VODDS, the remaining schemes risk privacy leakage by exposing user identity or access policy. VODDS achieves privacy by encrypting user identities during distributed key distribution and employing an LSSS-based policy-hiding. Multi-authority is supported by most schemes, except for the single-AA architectures in [,,] and the non-AA scheme in []. Consequently, AA collusion is not applicable to these four schemes, while it is actively supported in all others except [,], which lack this feature. Distributed key distribution is a distinctive feature, implemented only in [] and VODDS. Regarding access structures, all schemes employ LSSS except [], which uses a Tree structure. Resistance to user collusion is universally supported except in [,]. Verifiable outsourced decryption is another key differentiator; it is only supported in [,,], and our work. Finally, VODDS is the sole one that provides reliable verification of ciphertext integrity.
7.2. Experimental Environment
To comprehensively evaluate the performance of VODDS against the advanced schemes [,,,,,,,], we conducted simulation tests to measure the computation overhead of each stage. The experiments were implemented in Java using the JPBC library, and the execution time of the main operations at each stage was recorded. Performance comparison charts were then plotted based on the results. The experimental environment is configured with an AMD Ryzen 7 7745HX @ 3.60 GHz CPU (Advanced Micro Devices, Inc., Santa Clara, CA, USA), Windows 11 Pro 24H2 (64 bit) operating system, and IntelliJ IDEA 2024.1.2 as the development platform. A Type A symmetric prime-order bilinear group was used, with curve parameters set to a 512-bit prime, resulting in bits and bits. Each experimental result was averaged over 1000 independent runs to ensure stability and accuracy. Since the initialization phase is a single process, we only give the comparison on the table. We conducted a detailed comparison and test of the scheme’s encryption overhead, decryption overhead, key generation overhead and total overhead. In addition, since we have introduced the blockchain to the verification mechanism of outsourced decryption, we have experimentally tested the hash value of verifying ciphertext and the packaging and on-chain delay of blinded keys, blockchain throughput, and blinded key retrieval and download delay to express the performance of our blockchain.
The detailed configuration of our experimental environment is summarized in Table 3.

Table 3.
Experimental Environment Configuration.
Our experiments focus on functional correctness and core costs, namely storage and computation overhead comparisons, and the performance of the blockchain and the PBFT consensus. This isolates the cryptographic and protocol costs that dominate the design space and establishes a fair, reproducible baseline across schemes.
In VODDS, the number of communication rounds (for example, between the DU and the RSU, and when interacting with the blockchain) is kept as small as possible, and RSUs are placed close to the DU side. In real deployments, authorities in the same group can also be placed by geographic or network proximity to further reduce the network latency of group key agreement, which is flexible.
In our permissioned blockchain architecture, gas is used for accounting, and the cost of writing a commitment (a 32-byte hash plus minimal metadata) is negligible. Overall, while wide-area latency and gas pricing may introduce additional overhead in practice, our measurements show moderate per-event delay for commitment and lookup and predictable consensus scalability, supporting the applicability of our design.
7.3. Storage and Computation Overhead Comparison
This subsection compares VODDS to schemes [,,,,,] in terms of storage and computational overhead. The symbols used in the overhead expressions are defined in Table 4. A detailed comparison is separately summarized in Table 5 and Table 6.

Table 4.
Notation for storage and computation overhead.

Table 5.
Storage overhead comparison.

Table 6.
Computation overhead comparison.
Table 5 compares the storage overhead of different schemes across three phases: system setup, key generation, and ciphertext size. The results indicate that the storage overhead of VODDS is comparable to most existing approaches. For instance, in the setup phase, our overhead of is within a similar range to other multi-authority schemes like [,]. Similarly, the private key and ciphertext sizes in VODDS remain competitive. It is worth noting that VODDS achieves a more comprehensive functionality and, as will be shown in the subsequent computation overhead comparison, also demonstrates superior performance.
Table 6 presents a comparative analysis of the computational overhead across different cryptographic phases. The results demonstrate that VODDS achieves highly competitive performance, particularly in the critical phases of encryption and decryption. For encryption, our overhead of is lower than that of several comparable schemes [,,]. More notably, our decryption overhead of only is significantly more efficient than others, especially those requiring multiple pairing operations (e.g., [,,]). This efficiency gain stems from our streamlined verification and decryption process. The slightly higher overhead in our setup phase, attributed to the distributed key generation and system initialization, is a one-time overhead that is justified by the enhanced security and functionality it enables.
From encryption to ciphertext storage and subsequent outsourced decryption, it is necessary to convert ciphertext or key to protect user privacy and data security. Table 7 compares the transformation overhead of our solution with existing schemes. The results demonstrate that VODDS incurs a transformation overhead of , which depends linearly on the complexity of the access policy. In contrast, other schemes involve more costly operations, such as bilinear pairings in [,], or a higher number of exponentiations in []. This comparison clearly shows that our approach achieves a significant reduction in transformation overhead, contributing to the overall efficiency of the data sharing process.

Table 7.
Ciphertext transformation overhead comparison.
Figure 4a shows the key generation overhead of VODDS compared with the other six schemes. The number of attributes showed a clear positive correlation with the time overhead. Although the binding of attribute groups in our scheme introduces some computational overhead, its performance remains superior to that of schemes [,,]. Scheme [] key generation uses simple public parameters and a single-attribute authoritative private key as inputs, and the operation is lightweight. Scheme [] has the highest overhead overhead due to the Group-KeyGen algorithm and the key transformation interaction of multiple entities. Within a multi-authority architecture, the key generation overhead of our scheme is competitive.
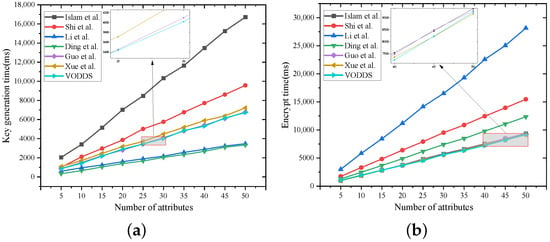
Figure 4.
VODDS’s performance: (a) Key generation performance; (b) Encryption performance [,,,,,].
As shown in Figure 4b, the overhead of our solution is comparable to that of [,,]. When the number of attributes reaches 40, however, the overhead of our solution is only 7242.518 ms, which is the lowest among all schemes. It is worth noting that our solution employs an offline/online encryption strategy, whereas [,] rely on conventional encryption. In contrast, the scheme in [] requires collaborative encryption between the DU and ESP and introduces a large number of ciphertext components, resulting in relatively high computational overhead.
As an important part of the outsourced decryption or ciphertext storage architecture, the transformation of ciphertext or keys will also bring certain computational overhead. Based on Table 2, we perform a performance comparison with schemes [,,,]. As shown in Figure 5a, the scheme [] requires exponential encryption of each ciphertext component at the RSU end and storing the result in the cloud, which leads to high overhead. Our solution only converts some ciphertext components related to user privacy and decryption security, thereby maintaining a relatively low computational overhead.

Figure 5.
VODDS’s performance: (a) Ciphertext transformation performance; (b) Decryption performance [,,,,,,,].
For the comparison of decryption overhead, Figure 5b shows that, due to the use of outsourced decryption and a complete verification mechanism, the decryption overhead for our users remains lightweight. The scheme in [] employs simpler bilinear exponentiation and approximation operations to restore the plaintext; however, our verification mechanism offers stronger reliability. In [], the computational overhead introduced by decryption operations associated with the access policy is positively correlated with the number of attributes, which imposes a significant computational burden on the user.
In Figure 6, we present a comprehensive experimental comparison of the three key stages of the CP-ABE scheme: encryption, decryption, and key generation. In terms of total overhead, VODDS demonstrates a clear advantage. When the number of attributes ranges from 40 to 50, VODDS reduces the delay by approximately 500 ms compared with [,]. Overall, in all the given attribute number test points, VODDS consistently outperforms outstanding performance relative to the other schemes.
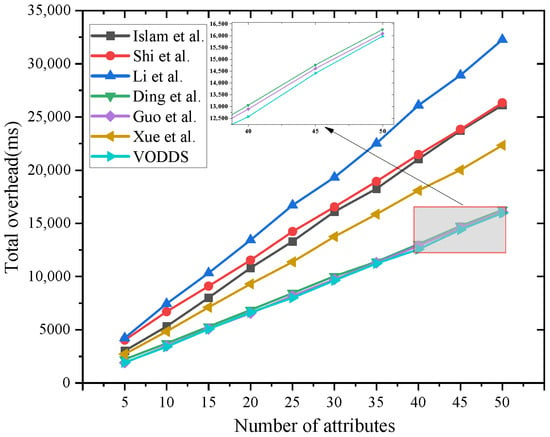
Figure 6.
Comparison of total performance [,,,,,].
In addition to the above work, we evaluate the performance of the blockchain layer that records and verifies decryption commitments. In our architecture, the DO computes and , and writes one on-chain commitment per decryption event (a 32-byte hash plus metadata) on an Ethereum-compatible, permissioned blockchain. When the DU receives the outsourced decryption result, it computes , submits to the smart contract to retrieve , and then completes the local verification/decryption upon receiving the on-chain response. We measure three metrics that directly affect this workflow: write throughput, confirmation latency for the commitment write, and key-retrieval latency for the DU lookup. Under our parameter settings (permissioned deployment with deterministic block generation), the write cost for one commitment is approximately 45,000 gas and the latency to confirm that write is about 150–200 ms; the key-retrieval latency ranges from 90 ms to 140 ms as the number of participating nodes increases from 1 to 25. Figure 7 shows how performance scales with the number of nodes: write throughput decreases gradually from about 870 transactions/s to about 770 transactions/s, while both the confirmation latency and the key-retrieval latency increase steadily (approximately 150→200 ms and 90→140 ms, respectively). These results indicate that, although additional nodes introduce communication and synchronization overhead—as expected—the system preserves relatively high throughput and keeps per-event delays in an acceptable range for VANET-scale data sharing.
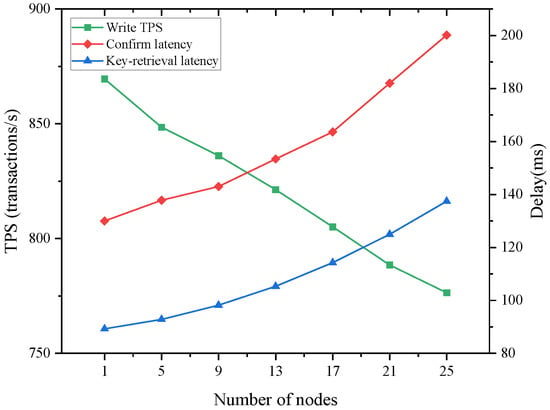
Figure 7.
Blockchain performance.
To bootstrap each attribute group we run a PBFT-style Byzantine consensus when issuing the claimant’s group certificate. This provides strong consistency and fault tolerance for the key-distribution credentials and, in turn, underpins the security of the subsequent cryptographic workflow. We further evaluated the practical cost of this consensus by varying the number of attribute authorities and measuring network-wide communication and cumulative computation per decided round. As shown in Figure 8, communication grows predictably with the number of attribute authorities: from about 4.9 KB when there are 4 authorities to about 286 KB when there are 31 authorities. The cumulative computation exhibits a similar trend, rising from 92 ms to about 3.4 s across all nodes. These results match the quadratic profile expected from PBFT’s all-to-all Prepare/Commit phases and show that the overhead remains moderate for the group sizes we target, while providing the robustness needed for secure key distribution in VODDS.
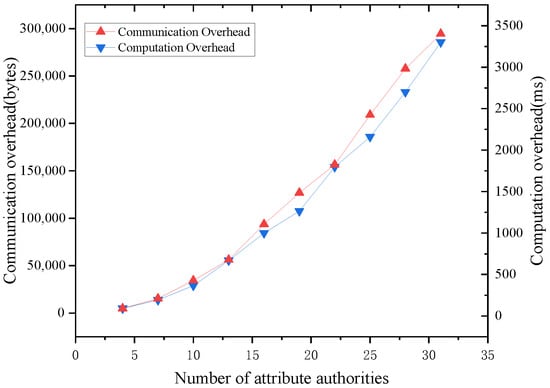
Figure 8.
Overhead of the PBFT consensus.
8. Conclusions and Discussions
This paper presents VODDS, a symmetrically verifiable and privacy-preserving data sharing scheme for VANETs. Its main works are threefold: First, to address the single-point performance bottleneck in multi-authority systems, a distributed key distribution mechanism is introduced. This mechanism organizes attribute authorities into groups. Within each group, key distribution credentials are generated through a Group Key Agreement protocol, with each round secured by a Byzantine consensus. This approach effectively balances decentralized load balancing with robust security assurance. Second, the scheme implements a policy-hiding access control mechanism by leveraging the LSSS, which not only supports the flexible expression of complex access policies but also effectively conceals the policy information to protect user privacy. Third, a secure and reliable outsourced decryption framework is constructed based on blockchain and smart contracts. This framework records verification commitments on the blockchain and utilizes smart contracts for symmetrical verification—a process that symmetrically matches the outsourced decryption result against the on-chain commitment—thereby providing users with a trustworthy verification service for outsourced decryption in complex, low-latency vehicular environments. Security analysis demonstrates that VODDS achieves IND-sCPA security, leak-freeness, and collusion resistance. Finally, extensive performance evaluations and comparisons confirm the scheme’s superior efficiency and scalability.
In this paper, the term “symmetry” has a specific meaning. It refers to the structural equivalence between the verification ciphertext generated by the DO and the pseudo-verification ciphertext computed by the DU based on the outsourced decryption result. First, the DO creates a verification ciphertext and saves its hash on the blockchain. Then, the DU receives a result from the RSU and calculates a pseudo-verification ciphertext. The process is called symmetrical because if the RSU’s work is correct, the DU’s result will match the DO’s original in structure. The smart contract can then reliably compare these two values. It checks the DU’s result against the DO’s stored commitment. This is also the origin of the term “Symmetrically Verifiable Outsourced Decryption” in the title of this paper.
VODDS demonstrates strong theoretical suitability for VANETs that need frequent data sharing and flexible access control. Its practical efficiency in low-latency settings is achieved by offloading most decryption tasks to an outsourced mechanism. Nevertheless, some limitations require further investigation. Currently, the LSSS-based access structure in VODDS does not support dynamic policy updates. Implementing such updates would require the integration of mechanisms for proxy re-encryption, a process expected to introduce considerable overhead and latency. Moreover, the current design lacks a fully developed mechanism for tracing malicious users and attribute authorities.
We plan to augment VODDS with accountable anonymity via threshold openable group signatures. Users operate with unlinkable group signatures by default, so identities remain hidden in all honest interactions. Upon evidenced misbehavior, a quorum of independent trace authorities jointly executes an opening procedure to recover only the culprit’s enrollment identity with public verifiability. We will pair this with dynamic revocation such as accumulator-based blacklists and, where appropriate, verifiable encryption of identities under the same threshold escrow. This approach clarifies the inherent trade off: raising the opening threshold and using short-lived pseudonyms strengthens anonymity but slows or complicates tracing, whereas lowering the threshold and using longer-lived identifiers improves traceability and revocation efficiency but increases linkability risk.
In the near future, by incorporating support for dynamic policy updates and enhancing the traceability mechanism against malicious entities, VODDS is expected to be adopted in more complex and dynamic data-sharing scenarios, thereby broadening its practical applicability in intelligent transportation systems and beyond.
Author Contributions
Methodology, H.L. and J.L.; formal analysis, C.Y. and Q.L.; investigation, M.Q., H.L. and Q.L.; writing—original draft preparation, M.Q.; writing—review and editing, M.Q., C.Y., H.L. and Q.L.; project administration, J.L.; supervision, J.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Natural Science Foundation of Hunan Province, China, grant numbers 2025JJ60413, 2025JJ60924.
Data Availability Statement
Data are available on request, due to privacy and copyrights.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Cunha, F.; Villas, L.; Boukerche, A.; Maia, G.; Viana, A.; Mini, R.A.; Loureiro, A.A. Data communication in VANETs: Protocols, applications and challenges. Ad Hoc Netw. 2016, 44, 90–103. [Google Scholar] [CrossRef]
- Zhao, C.; Zhang, L.; Wu, Q.; Rezaeibagha, F. Publicly Accountable Data-Sharing Scheme Supporting Privacy Protection for Fog-Enabled VANETs. IEEE Trans. Veh. Technol. 2024, 73, 8487–8502. [Google Scholar] [CrossRef]
- Qu, F.; Wu, Z.; Wang, F.Y.; Cho, W. A Security and Privacy Review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2985–2996. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhang, X.; Xie, X.; Ding, Y.; Kumar, S. A verifiable hidden policy CP-ABE with decryption testing scheme and its application in VANET. Trans. Emerg. Telecommun. Technol. 2022, 33, e3785. [Google Scholar] [CrossRef]
- Lu, J.; Yu, C.; Qi, M.; Luo, H.; Tian, J.; Li, J. A Symmetry-Enhanced Secure and Traceable Data Sharing Model Based on Decentralized Information Flow Control for the End–Edge–Cloud Paradigm. Symmetry 2025, 17, 1771. [Google Scholar] [CrossRef]
- Xia, Y.; Liu, X.; Ou, J.; Ma, O. RLID-V: Reinforcement Learning-Based Information Dissemination Policy Generation in VANETs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 14151–14161. [Google Scholar] [CrossRef]
- Guo, Z.; Wang, G.; Li, Y.; Ni, J.; Du, R.; Wang, M. Accountable Attribute-Based Data-Sharing Scheme Based on Blockchain for Vehicular Ad Hoc Network. IEEE Internet Things J. 2023, 10, 7011–7026. [Google Scholar] [CrossRef]
- Islam, M.A.; Madria, S.K. Attribute-Based Encryption Scheme for Secure Multi-Group Data Sharing in Cloud. IEEE Trans. Serv. Comput. 2022, 15, 2158–2172. [Google Scholar] [CrossRef]
- Li, Z.; Li, W.; Jin, Z.; Zhang, H.; Wen, Q. An Efficient ABE Scheme With Verifiable Outsourced Encryption and Decryption. IEEE Access 2019, 7, 29023–29037. [Google Scholar] [CrossRef]
- Ding, S.; Li, C.; Li, H. A Novel Efficient Pairing-Free CP-ABE Based on Elliptic Curve Cryptography for IoT. IEEE Access 2018, 6, 27336–27345. [Google Scholar] [CrossRef]
- Li, H.; Pei, L.; Liao, D.; Chen, S.; Zhang, M.; Xu, D. FADB: A Fine-Grained Access Control Scheme for VANET Data Based on Blockchain. IEEE Access 2020, 8, 85190–85203. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, J.; Liu, Y.; Yang, X.; Qi, F.; Song, W. Privacy-Preserving Attribute-Based Access Control Scheme With Intrusion Detection and Policy Hiding for Data Sharing in VANET. IEEE Internet Things J. 2024, 11, 23348–23369. [Google Scholar] [CrossRef]
- Wei, Z.; Li, J.; Wang, X.; Gao, C.Z. A Lightweight Privacy-Preserving Protocol for VANETs Based on Secure Outsourcing Computing. IEEE Access 2019, 7, 62785–62793. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. VANETs Cloud: Architecture, Applications, Challenges, and Issues. Arch. Comput. Methods Eng. 2021, 28, 1134–3060. [Google Scholar] [CrossRef]
- Miao, Y.; Li, F.; Li, X.; Ning, J.; Li, H.; Choo, K.K.R.; Deng, R.H. Verifiable Outsourced Attribute-Based Encryption Scheme for Cloud-Assisted Mobile E-Health System. IEEE Trans. Dependable Secur. Comput. 2024, 21, 1845–1862. [Google Scholar] [CrossRef]
- Safi, Q.G.K.; Luo, S.; Wei, C.; Pan, L.; Yan, G. Cloud-based security and privacy-aware information dissemination over ubiquitous VANETs. Comput. Stand. Interfaces 2018, 56, 107–115. [Google Scholar] [CrossRef]
- Lu, J.; Li, W.; Sun, J.; Xiao, R.; Liao, B. Secure and Real-Time Traceable Data Sharing in Cloud-Assisted IoT. IEEE Internet Things J. 2024, 11, 6521–6536. [Google Scholar] [CrossRef]
- Li, J.; Sha, F.; Zhang, Y.; Huang, X.; Shen, J. Verifiable outsourced decryption of attribute-based encryption with constant ciphertext length. Secur. Commun. Netw. 2017, 2017, 3596205. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy Identity-Based Encryption. In Advances in Cryptology—EUROCRYPT 2005, Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Cramer, R., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security (CCS ’06), Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar] [CrossRef]
- Cheung, L.; Newport, C. Provably secure ciphertext policy ABE. In Proceedings of the 14th ACM Conference on Computer and Communications Security (CCS ’07), Alexandria, VA, USA, 2 November–31 October 2007; pp. 456–465. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
- Guo, R.; Yang, G.; Shi, H.; Zhang, Y.; Zheng, D. O3-R-CP-ABE: An Efficient and Revocable Attribute-Based Encryption Scheme in the Cloud-Assisted IoMT System. IEEE Internet Things J. 2021, 8, 8949–8963. [Google Scholar] [CrossRef]
- Boneh, D.; Waters, B. Conjunctive, Subset, and Range Queries on Encrypted Data. In Theory of Cryptography, Proceedings of the 4th Theory of Cryptography Conference, TCC 2007, Amsterdam, The Netherlands, 21–24 February 2007; Vadhan, S.P., Ed.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 535–554. [Google Scholar]
- Nishide, T.; Yoneyama, K.; Ohta, K. Attribute-Based Encryption with Partially Hidden Encryptor-Specified Access Structures. In Applied Cryptography and Network Security, Proceedings of the 6th International Conference, ACNS 2008, New York, NY, USA, 3–6 June 2008; Bellovin, S.M., Gennaro, R., Keromytis, A., Yung, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 111–129. [Google Scholar]
- Hao, J.; Huang, C.; Ni, J.; Rong, H.; Xian, M.; Shen, X.S. Fine-grained data access control with attribute-hiding policy for cloud-based IoT. Comput. Netw. 2019, 153, 1–10. [Google Scholar] [CrossRef]
- Beimel, A. Secret-Sharing Schemes: A Survey. In Coding and Cryptology, Proceedings of the Third International Workshop, IWCC 2011, Qingdao, China, 30 May–3 June 2011; Chee, Y.M., Guo, Z., Ling, S., Shao, F., Tang, Y., Wang, H., Xing, C., Eds.; Spinger: Berlin/Heidelberg, Germany, 2011; pp. 11–46. [Google Scholar]
- Xue, J.; Shi, L.; Zhang, W.; Li, W.; Zhang, X.; Zhou, Y. Poly-ABE: A traceable and revocable fully hidden policy CP-ABE scheme for integrated demand response in multi-energy systems. J. Syst. Archit. 2023, 143, 102982. [Google Scholar] [CrossRef]
- Green, M.; Hohenberger, S.; Waters, B. Outsourcing the Decryption of ABE Ciphertexts. In Proceedings of the 20th USENIX Security Symposium (USENIX Security 11), San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Li, J.; Huang, X.; Li, J.; Chen, X.; Xiang, Y. Securely Outsourcing Attribute-Based Encryption with Checkability. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 2201–2210. [Google Scholar] [CrossRef]
- Ge, C.; Liu, Z.; Susilo, W.; Fang, L.; Wang, H. Attribute-Based Encryption With Reliable Outsourced Decryption in Cloud Computing Using Smart Contract. IEEE Trans. Dependable Secur. Comput. 2024, 21, 937–948. [Google Scholar] [CrossRef]
- Chen, L.; Xu, S.; Zhang, H.; Weng, J. Fair-and-Exculpable-Attribute-Based Searchable Encryption With Revocation and Verifiable Outsourced Decryption Using Smart Contract. IEEE Internet Things J. 2025, 12, 4302–4317. [Google Scholar] [CrossRef]
- Geng, Z.; Yanan, W.; Guojing, L.; Xueqing, W.; Kaiqiang, G.; Jiye, W. A Trusted Data Storage and Access Control Scheme for Power CPS Combining Blockchain and Attribute-Based Encryption. In Proceedings of the 2021 IEEE 21st International Conference on Communication Technology (ICCT), Tianjin, China, 13–16 October 2021; pp. 355–359. [Google Scholar] [CrossRef]
- Ghorbel, A.; Ghorbel, M.; Jmaiel, M. Accountable privacy preserving attribute-based access control for cloud services enforced using blockchain. Int. J. Inf. Secur. 2022, 21, 489–508. [Google Scholar] [CrossRef]
- Belguith, S.; Kaaniche, N.; Hammoudeh, M. Analysis of attribute-based cryptographic techniques and their application to protect cloud services. Trans. Emerg. Telecommun. Technol. 2022, 33, e3667. [Google Scholar] [CrossRef]
- Zhang, L.; Qiu, F.; Hao, F.; Kan, H. 1-Round Distributed Key Generation With Efficient Reconstruction Using Decentralized CP-ABE. IEEE Trans. Inf. Forensics Secur. 2022, 17, 894–907. [Google Scholar] [CrossRef]
- Ren, Z.; Yan, E.; Chen, T.; Yu, Y. Blockchain-based CP-ABE data sharing and privacy-preserving scheme using distributed KMS and zero-knowledge proof. J. King Saud Univ.-Comput. Inf. Sci. 2024, 36, 101969. [Google Scholar] [CrossRef]
- Lin, Y.; Xiong, H.; Su, H.; Yeh, K.H. Multi-Authority CP-ABE Scheme With Cryptographic Reverse Firewalls for Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2025, 26, 5348–5359. [Google Scholar] [CrossRef]
- Wu, Q.; Mu, Y.; Susilo, W.; Qin, B.; Domingo-Ferrer, J. Asymmetric Group Key Agreement. In Advances in Cryptology—EUROCRYPT 2009, Proceedings of the 28th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cologne, Germany, 26–30 April 2009; Joux, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 153–170. [Google Scholar]
- Waters, B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization. In Public Key Cryptography–PKC 2011, Proceedings of the 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Catalano, D., Fazio, N., Gennaro, R., Nicolosi, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Zhang, Y.; Li, J.; Yan, H. Constant Size Ciphertext Distributed CP-ABE Scheme With Privacy Protection and Fully Hiding Access Structure. IEEE Access 2019, 7, 47982–47990. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Xue, K.; Xue, Y.; Hong, J.; Li, W.; Yue, H.; Wei, D.S.L.; Hong, P. RAAC: Robust and Auditable Access Control With Multiple Attribute Authorities for Public Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2017, 12, 953–967. [Google Scholar] [CrossRef]
- Das, S.; Namasudra, S. Multiauthority CP-ABE-based Access Control Model for IoT-enabled Healthcare Infrastructure. IEEE Trans. Ind. Inform. 2023, 19, 821–829. [Google Scholar] [CrossRef]
- Wang, L.; Zhong, H.; Cui, J.; Zhang, J.; Wei, L.; Bolodurina, I.; He, D. Privacy-Preserving and Secure Distributed Data Sharing Scheme for VANETs. IEEE Trans. Mob. Comput. 2024, 23, 13882–13897. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).