Abstract
In traditional power networks, security protection models primarily rely on perimeter-based defenses, utilizing firewalls, virtual private networks (VPNs), and identity authentication to block external threats. However, once a node within the power system is compromised, attackers can exploit it as a pivot to launch lateral movement attacks from within the system, posing serious threats to the core operations of the power grid. To address the increasingly complex cybersecurity landscape, this paper proposes a security defense approach that integrates an improved trust evaluation model based on the Practical Byzantine Fault Tolerance (PBFT) algorithm with a zero-trust architecture, leveraging the structural and functional symmetry among network nodes. The PBFT algorithm’s fault tolerance and consensus mechanisms are leveraged to ensure dynamic trust scoring across multiple nodes. This approach guarantees that each node has an equal role in the system’s operations, maintaining fairness and security across the network. Furthermore, the primary node in the PBFT consensus process is redefined as the arbitration node in the zero-trust framework, and faulty nodes can be automatically replaced through the view change protocol, thereby mitigating the centralization risk inherent in traditional zero-trust models. Experimental results demonstrate that the proposed approach achieves high accuracy and robustness in defending against both internal and external attacks in power network scenarios, highlighting the role of symmetry in enhancing secure and balanced system operations.
1. Introduction
1.1. Research Background
The communication network of modern power systems operates in an open and highly interconnected environment, serving as a critical foundation for the secure and stable operation of smart grids. However, as digitalization and interconnectivity increase, power communication networks face escalating cybersecurity threats. Attacks originating both externally and internally can disrupt data transmission, interfere with control commands, or even trigger cascading failures within the power grid, leading to severe economic and social consequences []. In particular, internal node compromise and lateral movement attacks have emerged as major challenges, as they can bypass traditional perimeter defenses and directly threaten the core of the power system. Therefore, establishing a dynamic, fine-grained, and adaptive trust evaluation mechanism has become an urgent necessity for ensuring power system security in complex environments.
1.2. Research Problem
Traditional network defense mechanisms primarily rely on static boundary protections, such as firewalls, virtual private networks (VPNs), and identity authentication. While these methods effectively block known external threats, they fail to identify and respond to insider threats and stealthy lateral movements once an internal node is compromised []. The core problem addressed in this paper is how to enable power communication networks to perform dynamic, distributed, and trustworthy identity verification and access control so that trust decisions can adaptively evolve according to the real-time security state of the system.
1.3. Research Status
Recent studies have explored various approaches to enhance cybersecurity in power systems. For example, reinforcement learning-based adaptive defense mechanisms have been proposed to identify and mitigate cyberattacks []; adversarial machine learning has been introduced to enhance intrusion detection systems []; and blockchain technology has been leveraged for DDoS detection and secure data sharing in IoT-based energy systems []. In the field of smart grids, blockchain and zero trust have been combined to improve resilience and reliability through decentralized authentication and smart contracts [,]. Meanwhile, the Practical Byzantine Fault Tolerance (PBFT) algorithm has been recognized as a robust consensus mechanism in distributed systems, capable of maintaining operational consistency even in the presence of faulty or malicious nodes [,,].
1.4. Problems and Gaps in Existing Research
Despite the progress achieved, several critical limitations remain in existing research.
- Most trust management models for power communication networks are static and fail to adapt to dynamic threat conditions. When internal nodes are compromised and used as pivot points for lateral attacks, existing models cannot dynamically reassess trustworthiness or isolate malicious nodes in time [,].
- Current defense methods are effective against external intrusions but lack the capability to detect pivot intrusions, disguised nodes, and coordinated internal attacks. Once an attacker manipulates trust scores or forges node identities, the system may misjudge the node as trustworthy, leading to trust hijacking and expanded attack propagation []. These gaps highlight the need for a distributed, self-adaptive, and continuously verified trust evaluation mechanism that can jointly defend against both internal and external threats.
1.5. Research Objective and Scope
To address the above issues, this paper proposes an improved trust evaluation model that integrates the PBFT consensus mechanism with the Zero Trust Architecture (ZTA). The proposed model leverages PBFT’s fault tolerance and consensus feedback mechanisms to achieve dynamic trust assessment in multi-node environments. The primary node in the PBFT process is redefined as the adjudicating node in the ZTA framework, and the view change protocol is used to automatically replace faulty or compromised nodes, mitigating centralization risks. Furthermore, the PBFT-ZT model enforces fine-grained access control and dynamic authorization for both internal and external communications within power systems, adhering to the principle of least privilege. An improved trust evaluation model is developed based on the PBFT consensus process, ensuring consensus and accurate trust scoring even with up to one-third faulty or malicious nodes, while adopting the attribute-based access control (ABAC) concept [] to enhance dynamic authorization consistency within the Zero Trust Architecture. The study’s objective is to enhance the reliability, adaptability, and resilience of power network defense systems under complex and evolving cyber threats. Experimental results verify the proposed model’s effectiveness in achieving higher accuracy and robustness against both internal and external attacks.
1.6. Paper Structure
The remainder of this paper is organized as follows. Section 2 introduces the overall system architecture, detailing the integration of the improved PBFT-based trust evaluation model with the zero-trust framework and the corresponding adjudicator node selection strategy. Section 3 presents the simulation experiments, which include trust value evaluation, node selection, and dynamic access control verification, and analyzes the experimental results, discussing the system performance in terms of trust convergence, latency, and defense robustness. Finally, Section 4 concludes the paper and outlines future research directions.
2. System Architecture
2.1. Framework Overview
In traditional power networks, internal threats can pose serious risks when a compromised node is exploited for lateral movement attacks. Current research still primarily relies on static or centralized trust allocation mechanisms, which, to some extent, limits the system’s self-adaptive capabilities and introduces the risk of single points of failure. To address these issues, this paper proposes a security model that integrates a zero-trust architecture with a dynamic trust evaluation mechanism based on PBFT. This framework combines the zero-trust principle of “no node is trusted by default” with the fault tolerance and consensus capabilities of the PBFT algorithm. Unlike traditional PBFT implementations that rely on a fixed primary node, the proposed model redefines the primary node as an arbitration node, enabling automatic replacement of abnormal nodes upon fault detection. This approach reduces centralization risks and achieves symmetrical distribution of node responsibilities. The design aims to provide a more flexible and reliable trust foundation for distributed systems operating in adversarial environments. To address this issue, the proposed framework integrates an improved PBFT-based trust evaluation model with a zero-trust architecture, leveraging the structural and functional symmetry among network nodes. This symmetry ensures that all nodes participate equally in trust scoring and consensus processes and that faulty or compromised nodes can be dynamically replaced without centralized control, thereby enhancing the system’s robustness and fairness in defending against both internal and external attacks.
As shown in Figure 1, each access request from an access subject is first submitted to the current adjudication node. The adjudication node plays a crucial role in decision-making within the system. It is responsible for reviewing access requests, determining whether a request can be granted based on the trust score, and forwarding the decision to the appropriate entity. It acts as a central point of control in the zero-trust architecture. The policy engine then calls the trust evaluation model to assess the current access request. The trust evaluation model dynamically updates the node’s trust value by comprehensively considering the access subject’s current device status, historical performance, and consensus feedback from the current round, and returns the trust value to the policy engine. Based on predefined access control rules, the policy engine determines whether to authorize the current access request and returns the result to the adjudication node. The adjudication node forwards trusted requests to the access object, while untrusted requests are intercepted to prevent further access to the object’s resources. Moreover, when the term of the adjudication node ends or a failure occurs, the adjudication node selection model calls the trust evaluation model to obtain the trust values of all devices in the current consensus network and elects a new adjudication node for the current round according to the selection strategy to complete the replacement process. This process fully reflects the symmetry in node responsibilities and decision-making: each node has the opportunity to participate in adjudication, and faulty nodes can be replaced on an equal basis, effectively avoiding centralization of the adjudication node and single-point failures, while enhancing fairness and robustness in defending against both internal and external attacks.
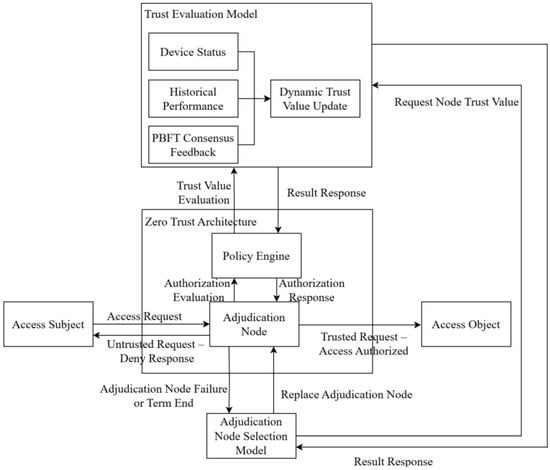
Figure 1.
PBFT-ZTM Algorithm Model.
2.2. Improved Trust Evaluation Model Based on PBFT
The architecture of the trust evaluation model is shown in Figure 2 and consists of four components: the Hardware Resource Scoring Model, the Node Status Evaluation Model, the PBFT Consensus Feedback Model, and the Trust Evaluation Model. The Hardware Resource Scoring Model is primarily responsible for monitoring key resource metrics of devices within the consensus network, including memory, CPU, bandwidth, and disk storage. In the PBFT Consensus Feedback Model, both adjudicator nodes and authentication nodes within the consensus network evaluate each access request initiated by the requesting entity. Based on the authentication outcomes, the model assigns corresponding trust score rewards or penalties to authentication nodes, adjudicator nodes, and the requesting entity. For legitimate access requests, the Trust Evaluation Model grants trust rewards to authentication nodes that successfully participate in the verification process and to requesting entities with a history of normal behavior []. If an authentication node fails to respond or issues a forged request, it is penalized with a trust deduction proportional to the severity of the event type []. In the case of malicious access attempts, trust score rewards are granted to nodes that successfully contribute to detecting the malicious behavior, while the requesting entity responsible for the malicious action receives a trust penalty. The Node Status Evaluation Module dynamically updates the status of each node based on its hardware resources and historical behavioral performance.
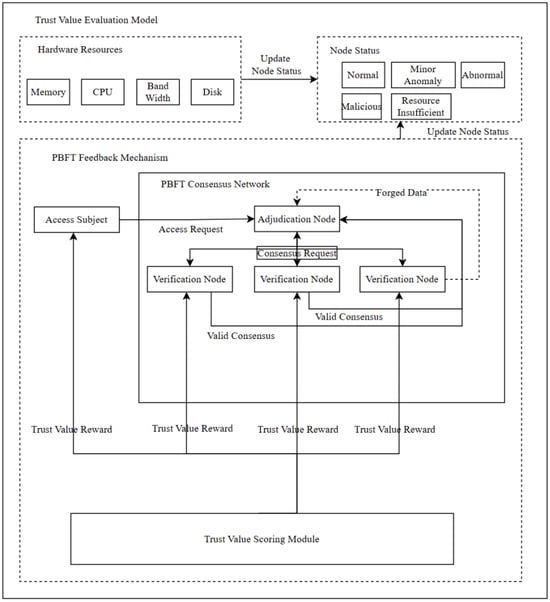
Figure 2.
Architecture of the Trust Evaluation Model.
To evaluate trust, the system first assigns each node an initial trust score. This score is updated based on two factors: the node’s past behavior (whether it has behaved as expected) and its current performance (whether it is functioning properly in the present). If a node behaves well, it earns a reward; if it misbehaves, it receives a penalty. Finally, the computed trust score is compared against a predefined threshold to determine whether the node is considered trustworthy. This evaluation provides a theoretical foundation for adjudicator node selection as well as for making access control decisions within the subsequent Zero Trust Architecture.
2.2.1. Initialization of Node Trust Value
Since newly joined nodes have not yet participated in any consensus activities, their behavioral characteristics remain undefined. These nodes are classified as floating nodes within the cluster and are assigned an initial trust value of 0.5.
2.2.2. Dynamic Update of Node Trust Value
Dynamically updating a node’s trust value by integrating its historical performance with its current state is an effective trust management mechanism. This approach allows the trust value to reflect not only the node’s long-term behavioral trends but also its real-time operational status, thereby enabling continuous monitoring and adaptive adjustment of node trustworthiness.
- Historical Performance:The trust value is updated based on the node’s historical performance. The shorter the time interval between each successful consensus participation, the greater the historical impact on the trust score; conversely, longer intervals reduce the influence of historical behavior. This relationship is described as follows:where represents the time weighting function. represents the consensus time interval. A baseline of 20 ms is used as the reference: if a node has not participated in consensus within 20 ms, its trust value at time i will continuously decay. In contrast, nodes that frequently participate in consensus within the 20 ms threshold will experience rapid trust accumulation. The parameter serves as the adjustment factor for historical influence—larger values of result in a faster decay of the historical impact.
- Trust Value Update: The key to updating the trust value based on a node’s performance in the current consensus round lies in the introduction of positive reward and negative penalty mechanisms, which enable the quantitative assessment of node behavior [].Positive Reward Mechanism: When a node correctly broadcasts information and efficiently participates in the consensus process, the system grants a positive trust incentive to the node. The positive reward mechanism is described as follows:where represent the current trust value of the node, and denote the magnitude of the reward. is the reward weighting coefficient for the i-th consensus round. Initially, the trust reward is relatively large to allow low-trust nodes to accumulate trust more quickly. As the number of consensus rounds increases, the reward magnitude gradually decreases, slowing the growth of high trust nodes. This mechanism enhances the overall stability of trust within the system. The reward weighting coefficient is described as follows:Negative Penalty Mechanism: When a node exhibits abnormal behavior such as failing to respond within a timeout period, broadcasting forged information, or participating in malicious attacks—the system reduces its trust value based on a penalty factor that reflects the severity of the behavior. This mechanism enables a rapid decline in the trustworthiness of malicious nodes, preventing them from exerting prolonged influence on the system. The penalty mechanism is described as follows:represent the current trust value of the node, and represent the trust value from the previous consensus round, indicates the magnitude of the penalty, while is the penalty weighting coefficient for the i-th consensus round. When a node has a high trust value, any detected malicious behavior results in more severe penalties, preventing high-trust nodes from leveraging their credibility to carry out malicious attacks. Conversely, low-trust nodes receive relatively lighter penalties for the same behavior.The penalty weighting coefficient is described as follows:
- Current Status and Trust Value Update: A node’s status directly determines both the credibility of its contribution to the system and the level of threat it may pose. In this paper, the definition of node status is provided in Table 1:
 Table 1. Node Status and Causes.The impact of different current node statuses on the trust value is described as follows:where represent the current trust value of the node, represent the trust value from the previous consensus round, C Represents the value range of penalty magnitude [−1, 0].
Table 1. Node Status and Causes.The impact of different current node statuses on the trust value is described as follows:where represent the current trust value of the node, represent the trust value from the previous consensus round, C Represents the value range of penalty magnitude [−1, 0]. - Trust Value Update: By integrating the node current status and historical performance, the trust value is updated according to the following description.
2.2.3. Definition of Node Trust Threshold
The node trust threshold is defined in Table 2. Different types of behavior have corresponding impacts on a node’s trust value. When a node’s trust value falls below 0.2, it is classified as an untrustworthy node. Such nodes are excluded from future selection as adjudicator nodes within the cluster, and their access requests to other nodes will not be verified, thereby preventing them from obtaining service responses from the target resources. Nodes with trust values in the range of 0.2 to 0.5 are defined as floating nodes, whose behavioral characteristics remain unclear. The threshold values of 0.2 and 0.5 were selected after testing various configurations to optimize the trade-off between sensitivity and specificity in detecting untrustworthy nodes. This was based on observed system performance under different network conditions and attack scenarios. Nodes with trust values in the range of 0.5 to 1 are considered honest nodes. Only nodes that consistently align with the behavior of the majority across multiple consensus rounds are marked as honest. Compared to others, nodes with higher trust scores are granted greater access privileges and a higher probability of being selected as adjudicator nodes [].

Table 2.
Node Trust Threshold.
The decision to include a penalty mechanism for malicious behaviors like response denial or information forgery is grounded in the observed impact these attacks have on system stability. Penalty factors were calibrated based on simulation results to prevent undue influence from compromised nodes. While the proposed model demonstrates efficacy in a simulated environment, its scalability to real-world, large-scale power networks remains a consideration. Preliminary analysis suggests that the computational complexity is manageable within the parameters of modern power grid systems, but further work will focus on optimizing the algorithm for larger node networks.
2.3. Adjudicator Node Selection Strategy in Zero Trust Architecture
In the PBFT consensus algorithm, the view change protocol is a critical mechanism for handling primary node failures or Byzantine behaviors []. This protocol ensures that the system can continue operating and maintain consensus reliability when the primary node becomes unavailable or behaves abnormally. However, the traditional PBFT algorithm relies primarily on a round-robin mechanism for primary node election, which presents several limitations:
- Lack of historical behavior and reputation consideration: Nodes with poor performance or malicious behavior may still be elected as primary nodes, leading to frequent primary replacements and reduced overall system efficiency.
- Absence of trust score filtering: Without using trust values as a selection criterion, the system is less capable of filtering out malicious nodes during the election process. Such nodes may more easily enter the core consensus process, potentially disrupting system operations.
- Unreliable node selection in consecutive view changes: If unreliable nodes are repeatedly selected in successive view changes, the system may suffer from prolonged performance degradation or frequent view transitions, negatively impacting business continuity and response stability.
To address these issues, this paper proposes a trust score–based improvement to the primary node selection strategy. In the improved election process, the node’s trust score is introduced as a weighted metric. Nodes with higher trust values are given priority in the candidate pool, while nodes with trust scores below a predefined threshold are automatically excluded from the primary node election. The improved election workflow is illustrated in Figure 3.
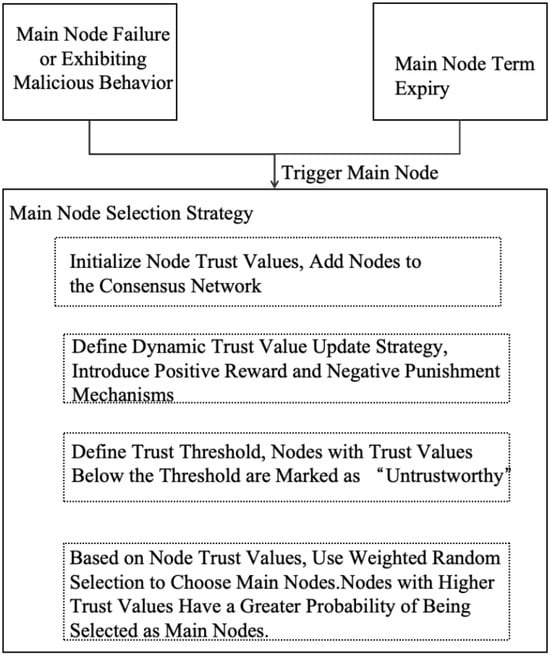
Figure 3.
Improved Primary Node Selection Strategy Based on Node Trust Value.
The probability of a node being selected as an adjudicator node is calculated as shown in Equation (8), where Ti represents the trust value of node i, and Pi denotes the probability of node i being selected as an adjudicator node.
3. Simulation Experiments
3.1. Experimental Environment
To evaluate the effectiveness of the proposed model, this paper conducted simulation-based comparative experiments. The experimental environment configuration is shown in Table 3.

Table 3.
Experimental Environment Configuration.
3.2. Trust Value Evaluation Experiments
A total of six devices were configured to participate in the experimental comparison, spanning twenty-six rounds of consensus. In each round, devices were evaluated based on trust-related factors, which include consensus time interval, resource utilization, and abnormal behavior events. Where Table 4 presents the consensus time interval of each device in every round. Table 5 shows the overall resource utilization of each device across different rounds. Table 6 details the abnormal events associated with each device in each round.

Table 4.
Consensus Time Interval of Devices in Different Consensus Rounds (Unit: milliseconds).

Table 5.
Resource Utilization of Devices Across Different Consensus Rounds.

Table 6.
Abnormal Events of Devices Across Different Consensus Rounds.
From Round 1 to Round 20, all nodes participated in the consensus process normally, and the consensus time intervals remained within 20 ms. During this period, the system’s resource utilization showed a gradual upward trend. Between Round 20 and Round 25, Devices 1, 2, 3, and 6 continued to participate in consensus stably. However, some devices occasionally exhibited consensus time intervals exceeding 20 ms.
As shown in Table 5, the resource utilization of Devices 1 through 6 gradually increased during the consensus process. By Round 23, the resource utilization of Device 1 reached the 80% threshold, after which its response capability began to decline. In contrast, the other devices maintained resource utilization levels below the threshold and continued to participate in the consensus process normally.
As shown in Table 6, during Rounds 20 to 25, Devices 4 and 5 experienced abnormal events such as network jitter and refused responses. In Round 26, Devices 1 to 5 maintained the same experimental configuration as in the previous round, whereas Device 6, which had previously been operating normally, was subjected to an external attack, resulting in a container escape incident. The experimental results, illustrated in Figure 4, show that during Rounds 1 to 20, the trust values of all devices increased steadily, indicating a high level of trust earned through consistent and reliable operation. Subsequently, during Rounds 21 to 25, the trust values of Devices 4 and 5 declined continuously due to abnormal behavior. Among them, Device 5 experienced a steeper drop in trust value due to the higher severity weighting of its anomalies. Additionally, in Round 23, Device 1 exceeded the 80% resource utilization threshold, triggering a status change to resource-deficient, which led to a rapid decline in its trust value. By Round 26, Device 6 suffered an external attack resulting in a container escape, causing its trust value to drop to zero, further confirming the phenomenon of trust collapse following an external compromise.
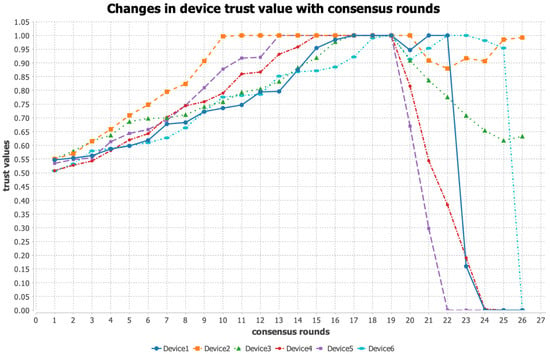
Figure 4.
Graph of device trust value changes over consensus rounds.
3.3. Adjudicator Node Selection Experiments
The traditional PBFT adjudicator node selection algorithm adopts a round-robin approach, where the current view number modulo the total number of nodes determines the primary node. This mechanism ensures that all nodes participate in consensus fairly and deterministically, with each node taking turns to serve as the adjudicator. In any given consensus round, only one adjudicator node is selected, with a selection probability of 1, while all other nodes have a probability of 0. To intuitively illustrate changes in node status, this experiment involved six devices participating in 30 rounds of consensus, with a primary node election occurring in each round. For Rounds 1 to 26, the consensus intervals, resource utilization, and abnormal events of each device are shown in Figure 4. In the final four rounds, the status of all devices remained consistent with that of Round 26. The experimental results are presented in Figure 5.
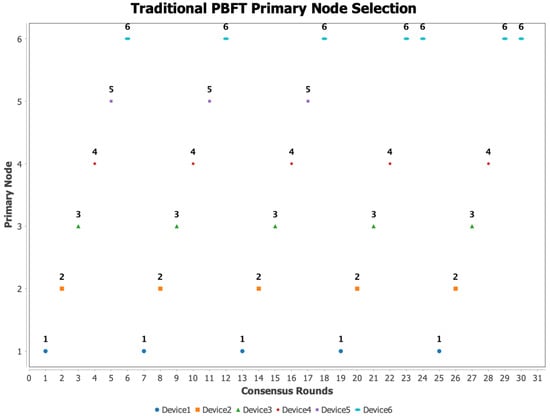
Figure 5.
The selection of adjudication nodes in the traditional PBFT algorithm.
During the first 20 rounds of election, all devices operated stably with no abnormal behavior. Each node took turns serving as the adjudicator according to the PBFT round-robin mechanism, sequentially assuming consensus responsibilities. This phase highlights PBFT’s fair leader election principle, ensuring that all nodes have equal opportunities to lead the consensus process, thereby enhancing the decentralization of the system. However, starting from Round 21, the experimental results gradually revealed the limitations of the traditional PBFT adjudicator node selection algorithm. From Round 22, Device 1 exceeded the 80% resource utilization threshold. Since the traditional selection logic does not account for computational resource consumption, Device 1 continued to be selected as the primary node despite being close to a performance bottleneck. Under high-load conditions, this may lead to slower transaction processing and increased message latency, thus compromising consensus stability. In addition, Device 4 began to experience frequent network jitter from Round 20 onward. When selected as the adjudicator, this instability resulted in packet loss and communication delays, further prolonging the time required to reach consensus. In certain scenarios, such fluctuations could frequently trigger the view change mechanism, increasing system complexity and the risk of latency. Device 5 exhibited a refused response anomaly in Round 20. Since PBFT lacks a built-in mechanism for proactively detecting malicious nodes, it relies solely on timeout strategies to passively handle such issues. As a result, the system eventually skipped Device 5 and selected Device 6 as the adjudicator. However, this process incurred additional communication overhead, negatively impacting overall system efficiency. After Round 26, Device 6 was compromised by an external attacker, losing its trusted status and becoming a pivot for system intrusion. Nevertheless, the PBFT algorithm, which lacks intrusion detection and security assessment capabilities, continued to select Device 6 as the adjudicator based on the round-robin logic, thereby exposing the system to serious security threats. In contrast to the traditional PBFT selection mechanism, the trust value–based adjudicator node selection strategy dynamically evaluates the trustworthiness of each node in every round and calculates the probability of being selected accordingly. Nodes with higher trust values are more likely to be selected as adjudicators, while other nodes still retain non-zero selection probabilities. This avoids permanently excluding nodes due to short-term anomalies and improves the system’s robustness and fault tolerance. Based on the trust value variations across rounds described in Section 3, the probability curves for each node being selected as adjudicator in each round are shown in Figure 6.
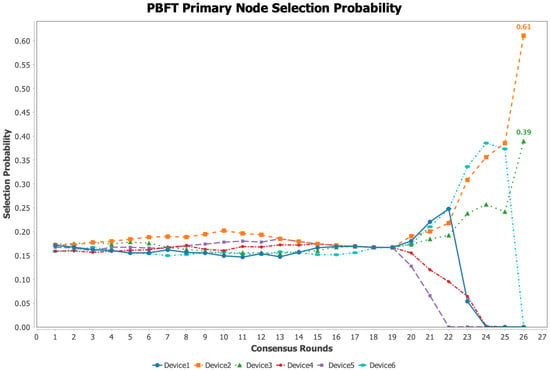
Figure 6.
Adjudication node selection probability based on trust value.
During the first 20 rounds of consensus, all devices operated stably with no abnormal events. As a result, the selection probabilities for each node were relatively uniform, maintaining around 20%. Unlike the traditional PBFT algorithm, after Round 20, Device 4 and Device 5 began to exhibit network jitter and response timeouts, leading to reduced stability. Consequently, their probability of being selected as adjudicator nodes dropped significantly, indicating that the system proactively adjusted to avoid assigning consensus responsibilities to unstable nodes, thereby mitigating potential disruptions. At the same time, other devices assumed a greater portion of the adjudication workload, with their selection probabilities increasing accordingly. After Round 23, due to Device 1 exceeding the 80% resource utilization threshold, its probability of being selected as an adjudicator dropped substantially. This effectively reduced the adjudication burden on high-load devices, allowing the system to prioritize devices with greater stability and available computing resources. Device 5, having remained in an abnormal state over an extended period, saw its trust value gradually drop to zero. Starting from Round 23, it was no longer eligible to be selected as an adjudicator node, thereby preventing it from continuing to interfere with the consensus process. In Round 26, Device 6 was compromised by an external attacker, resulting in its trust value being reduced to zero. The system consequently excluded it from the adjudicator node selection process, thus preventing a compromised node from being elected and containing the potential spread of security threats throughout the network.
3.4. Access Control Experiments in Zero Trust Architecture
Zero trust architecture dynamically adjusts access control policies based on the principle of least privilege by continuously evaluating the trust status of access subjects (devices, users, or processes), effectively improving system security and preventing unauthorized access. In this section’s experiment, the changes in access permissions of devices under different trust values are further evaluated. This experiment revolves around three core permission levels: log query access control, data access permission, and full control permission. Different trust thresholds are set for each permission level: when the trust value is higher than 0.2, the device is allowed to query logs of other nodes in the power system; when the device’s trust value is higher than 0.5, the device can access business data of other nodes in the power system, ensuring that business data will not be read or tampered with by low-trust devices; devices with trust values higher than 0.8 are granted full access control permissions. The initial data settings of this experiment are shown in Table 7, where T represents consensus rounds, C represents trust value, and R represents the number of requests. Based on the experimental data in Section 3.2, the device trust values are set according to each consensus round. In the experiment, devices 1 to 6 successively initiate log query, data query, and full access control requests to other device nodes in the power system. To simulate the differentiated behavior of devices in actual operation, we set different request counts for each device, namely 50 times, 100 times, 200 times, 250 times, 300 times, and 350 times. The log query access control experimental results are shown in Figure 7. In the first 21 rounds of consensus, the log query permissions of all devices remained stable, and the number of allowed accesses remained within the set threshold. However, in the consensus rounds from 21 to 25, due to network jitter and refusal to respond anomalies in devices 4 and 5, respectively, as well as the system load of device 1 exceeding 80%, the trust values of these nodes gradually declined. When the trust value falls below the set threshold, the adjudication system automatically refuses to grant the corresponding access control permissions. By the 23rd round of consensus, the trust values of device 1, device 4, and device 5 had dropped to 0.1598, 0.1906, and 0, respectively. Since the trust values did not meet the minimum authorization standard, the adjudication system refused to grant the minimum permissions to the above nodes.

Table 7.
Access control experimental data based on trust value evolution.
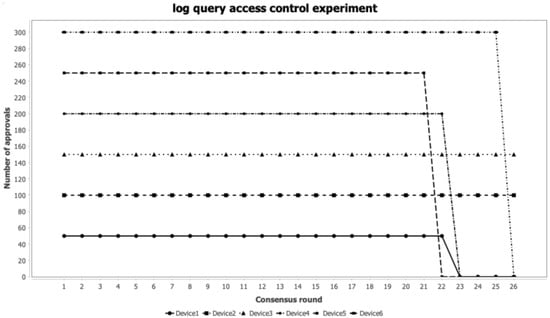
Figure 7.
Log query access control experiment.
From the results of the log query access control experiment, it can be seen that during the first 21 rounds of consensus, all devices maintained stable log query permissions, and the number of approvals remained within the set threshold. However, during the consensus process from Round 21 to Round 25, due to network jitter on Device 4, a refused response on Device 5, and Device 1 experiencing a system load exceeding 80%, the trust values of these nodes gradually declined. When the trust value fell below the specified threshold, the adjudication system automatically denied the corresponding access control permissions. By Round 23, the trust values of Device 1, Device 4, and Device 5 dropped to 0.15, 0.19, and 0, respectively. As their trust values did not meet the minimum authorization standard, the adjudication system refused to grant even the lowest level of permissions to the above nodes.
As shown in Figure 8, the results of the data access control experiment are generally similar in trend to those of the log query access control experiment, but the security threshold for data access control is higher, and permission changes are more sensitive. In the initial state, all devices had a trust value of 0.5, granting them data access control permission. During the first 20 rounds of consensus, as all devices actively participated in the consensus process, their trust values gradually increased, and all access requests were judged as trustworthy by the adjudication system, with no abnormal fluctuations observed. Subsequently, some devices experienced abnormal states, including high load, network anomalies, and failures, leading to a gradual decline in their trust values to below the 0.5 trust threshold. Once a device’s trust value fell below 0.5, the adjudication system automatically adjusted the access permissions and no longer allowed the device to access data from other nodes in order to prevent potential security threats.
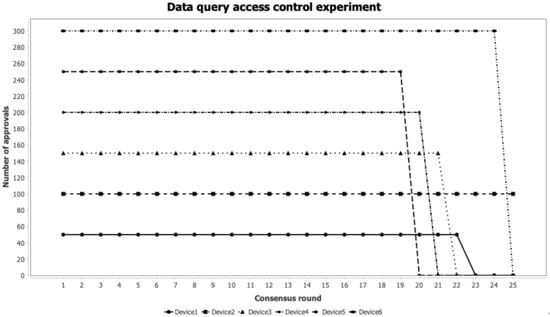
Figure 8.
Data query access control experiment.
The full access control experiment further raised the security level of access permissions, allowing only devices with trust values higher than 0.8 to obtain access control rights over other devices. As shown in Figure 9, during the initial stage, due to the strict access control policies of the zero trust architecture, all devices had relatively low trust values and did not meet the minimum standard for full access control. As a result, all access requests were intercepted by the adjudication system, and devices were unable to obtain control permissions over other nodes. As the number of consensus rounds increased, between Rounds 8 and 14, devices actively participated in consensus, and their trust values gradually increased, exceeding the security threshold for full access control. They were then granted high-level access to other nodes, and the system maintained an overall secure and trustworthy state. After Round 21, due to abnormal states in some nodes, the trust values of certain devices began to decline, triggering the dynamic access adjustment mechanism of the adjudication system. At this point, the system automatically revoked full access permissions for devices with trust values below 0.8 and either downgraded or completely denied their access rights.
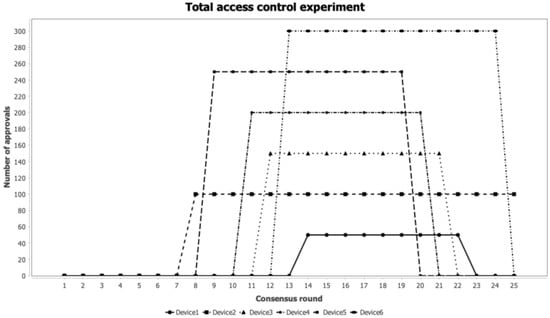
Figure 9.
Total access control experiment.
4. Conclusions
This paper proposes a security defense framework that integrates an improved Practical Byzantine Fault Tolerance (PBFT)-based trust evaluation model with a Zero Trust Architecture (ZTA) to address internal and external threats in power communication networks. By combining consensus-driven feedback with dynamic trust assessment, the proposed model enables decentralized and symmetric trust management among network nodes. Experimental results show that the framework effectively enhances real-time responsiveness, reduces the risk of single-point failure through automated adjudicator node replacement, and improves robustness under adversarial conditions.
The study demonstrates that incorporating consensus mechanisms into zero-trust models provides a reliable approach for adaptive and fine-grained security control in critical infrastructure systems. This integration offers practical insights for improving fairness, resilience, and automation in distributed network defense.
Nevertheless, the current model mainly focuses on device-level trust evaluation, and the experiments were conducted in a controlled simulation environment. Future work will aim to extend trust evaluation to finer granularity—such as process- and request-level analysis—and incorporate proactive defense techniques like behavior prediction, honeypot deception, and dynamic resource isolation. These enhancements will further strengthen the framework’s adaptability and enable its application in large-scale, real-world power network environments.
Author Contributions
Conceptualization, methodology, validation, and writing, X.L., S.Y. (Sen Yang), J.X., L.L.; Conceptualization, Data curation, Formal analysis, W.L., S.Y. (Shengjie Yu); Supervision, funding acquisition, and review, S.L., Y.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by a Science and Technology Project funded by State Grid Jiangsu Electric Power Company (Project No. J2024089).
Data Availability Statement
All datasets are available in the mentioned references.
Acknowledgments
Our thanks to the above projects for their support.
Conflicts of Interest
Authors (Xiaoyun Liao, Sen Yang, Jun Xu, Li Liu) were employed by the company [STATE GRID TAIZHOU POWER SUPPLY COMPANY]. The authors declare that this study received funding from the State Grid Jiangsu Electric Power Company Science and Technology Project (Project No. J2024089). The funder had the following involvement with the study: study design, the writing of this article.
References
- Li, J.; Gu, C.; Xiang, Y.; Li, F. Edge-cloud computing systems for smart grid: State-of-the-art, architecture, and applications. J. Mod. Power Syst. Clean Energy 2022, 10, 805–817. [Google Scholar] [CrossRef]
- Wang, J.; Yan, Z.; Lan, J.; Bertino, E.; Pedrycz, W. TrustGuard: GNN-based robust and explainable trust evaluation with dynamicity support. IEEE Trans. Dependable Secure Comput. 2024, 21, 4433–4450. [Google Scholar] [CrossRef]
- Hammad, A.A.; Ahmed, S.R.; Abdul-Hussein, M.K.; Ahmed, M.R.; Majeed, D.A.; Algburi, S. Deep reinforcement learning for adaptive cyber defense in network security. In Proceedings of the 2024 Cognitive Models and Artificial Intelligence Conference, Dubai, United Arab Emirates, 15–17 March 2024; pp. 292–297. [Google Scholar]
- Khan, M.; Ghafoor, L. Adversarial machine learning in the context of network security: Challenges and solutions. J. Comput. Intell. Robot. 2024, 4, 51–63. [Google Scholar]
- Khan, Z.A.; Namin, A.S. A survey of DDoS attack detection techniques for IoT systems using Blockchain technology. Electronics 2022, 11, 3892. [Google Scholar] [CrossRef]
- Hajian, A.; Chang, H.C. A Blockchain-Based Smart Grid to Build Resilience Through Zero-Trust Cybersecurity; Springer International Publishing: Cham, Switzerland, 2022; pp. 1–19. [Google Scholar]
- Liu, T.; Ma, Y.; Jiang, H.; Wu, S.; Zuo, J.; Peng, T. Research on power grid security protection architecture based on zero trust. Elec. Power Inf. Commun. Technol. 2021, 19, 25–32. [Google Scholar]
- Sousa, J.; Bessani, A.; Vukolić, M. A byzantine fault-tolerant ordering service for the Hyperledger Fabric blockchain platform. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Luxembourg, 25–28 June 2018; pp. 51–58. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the Symposium on Operating Systems Design and Implementation (OSDI), New Orleans, LA, USA, 22–25 February 1999; pp. 173–186. [Google Scholar]
- Zhang, Y.; Gan, Y.; Li, C.; Deng, C.; Luo, Y. Primary node selection based on node reputation evaluation for PBFT in UAV-assisted MEC environment. Wirel. Netw. 2023, 29, 3515–3539. [Google Scholar] [CrossRef]
- Lv, P.; Sun, X.; Huang, H.; Qian, J.; Sun, C.; Dai, H. Dynamic trust continuous evaluation-based zero-trust access control for power grid cloud service. J. Phys. Conf. Ser. 2022, 2402, 012008. [Google Scholar] [CrossRef]
- Wang, R.; Li, C.; Zhang, K.; Tu, B. Zero-trust based dynamic access control for cloud computing. Cybersecurity 2025, 8, 12. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero trust architecture (ZTA): A comprehensive survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-based access control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Zhu, X.; Hu, X.; Zhu, W. RGPBFT: A reputation-based PBFT algorithm with node grouping strategy. Arab. J. Sci. Eng. 2025, 50, 11837–11850. [Google Scholar] [CrossRef]
- Gambo, M.L.; Almulhem, A. Zero trust architecture: A systematic literature review. arXiv 2025, arXiv:2503.11659. [Google Scholar]
- Huang, H.; Zhang, J.; Hu, J.; Fu, Y.; Qin, C. Research on distributed dynamic trusted access control based on security subsystem. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3306–3320. [Google Scholar] [CrossRef]
- Arun, G. Zero Trust Evolution: Advanced Architectures for Resilient Cloud-Native IAM Systems. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2025, 11, 679–685. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).