Research on Image Steganography Based on Sudoku Matrix
Abstract
1. Introduction
2. Research Status
3. Research Methods
3.1. Research Plan
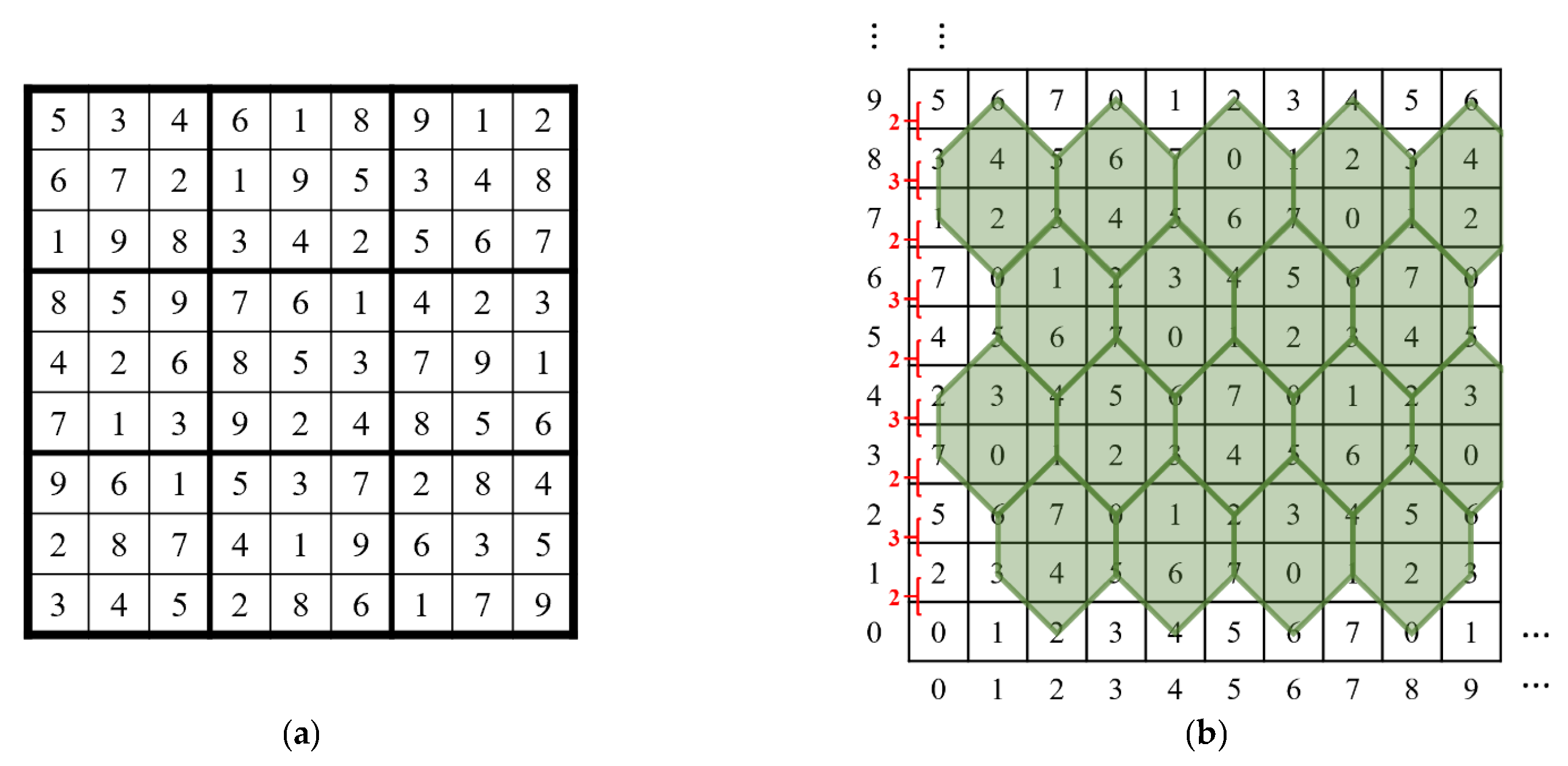
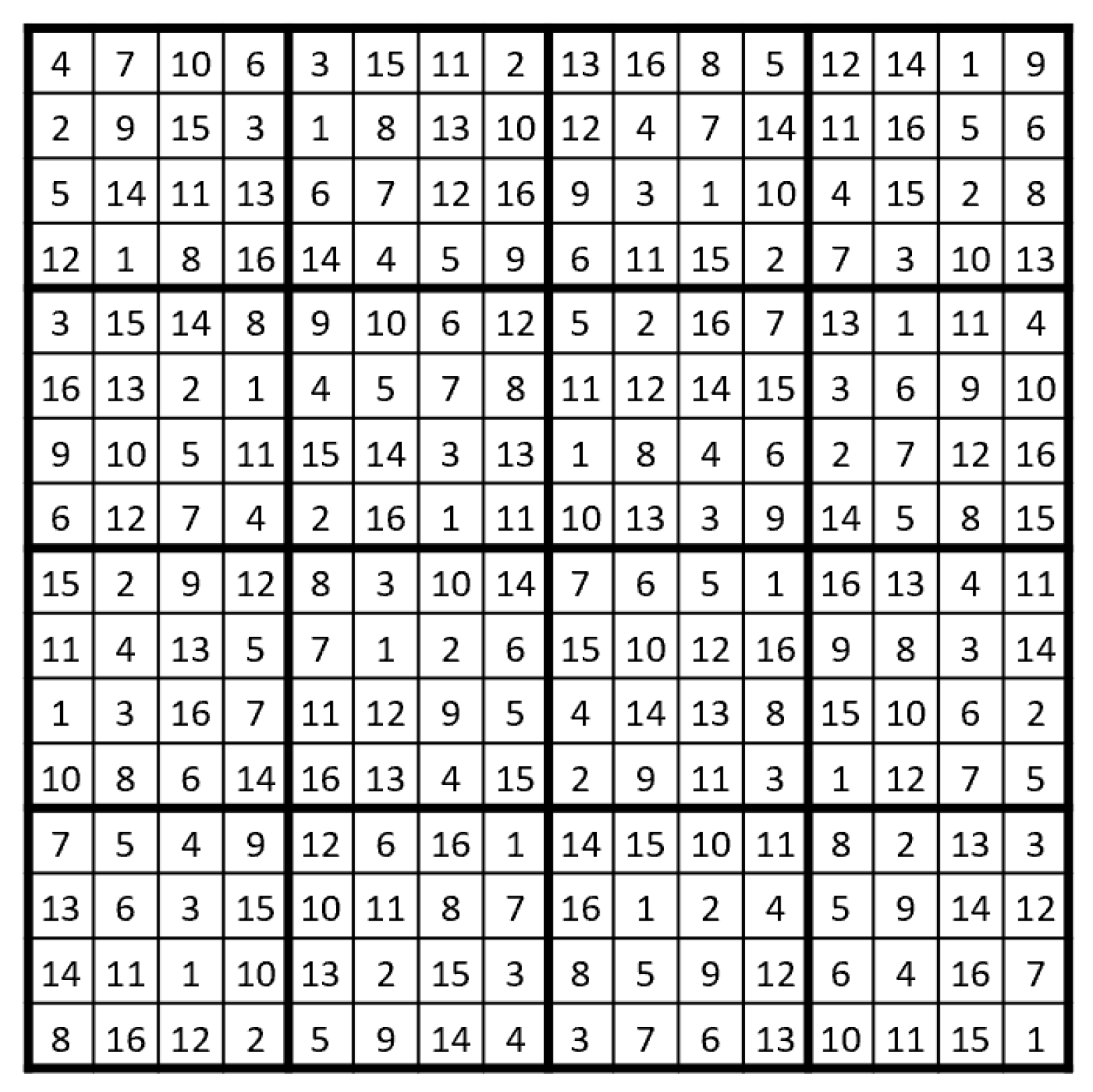
3.1.1. Design of Magic Matrices
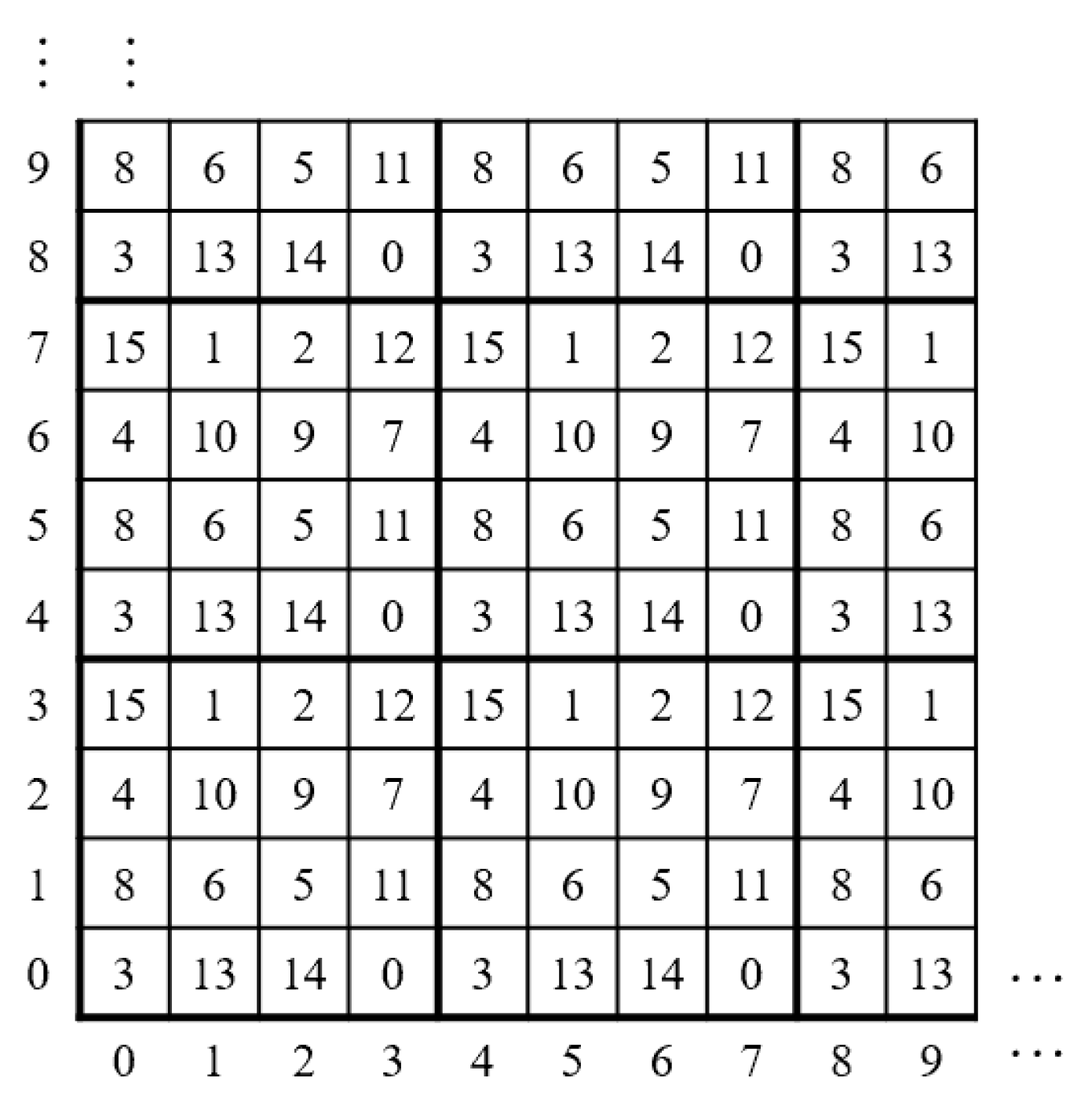
- 16 × 16 Sudoku matrix
- 2.
- Double-layer magic matrix
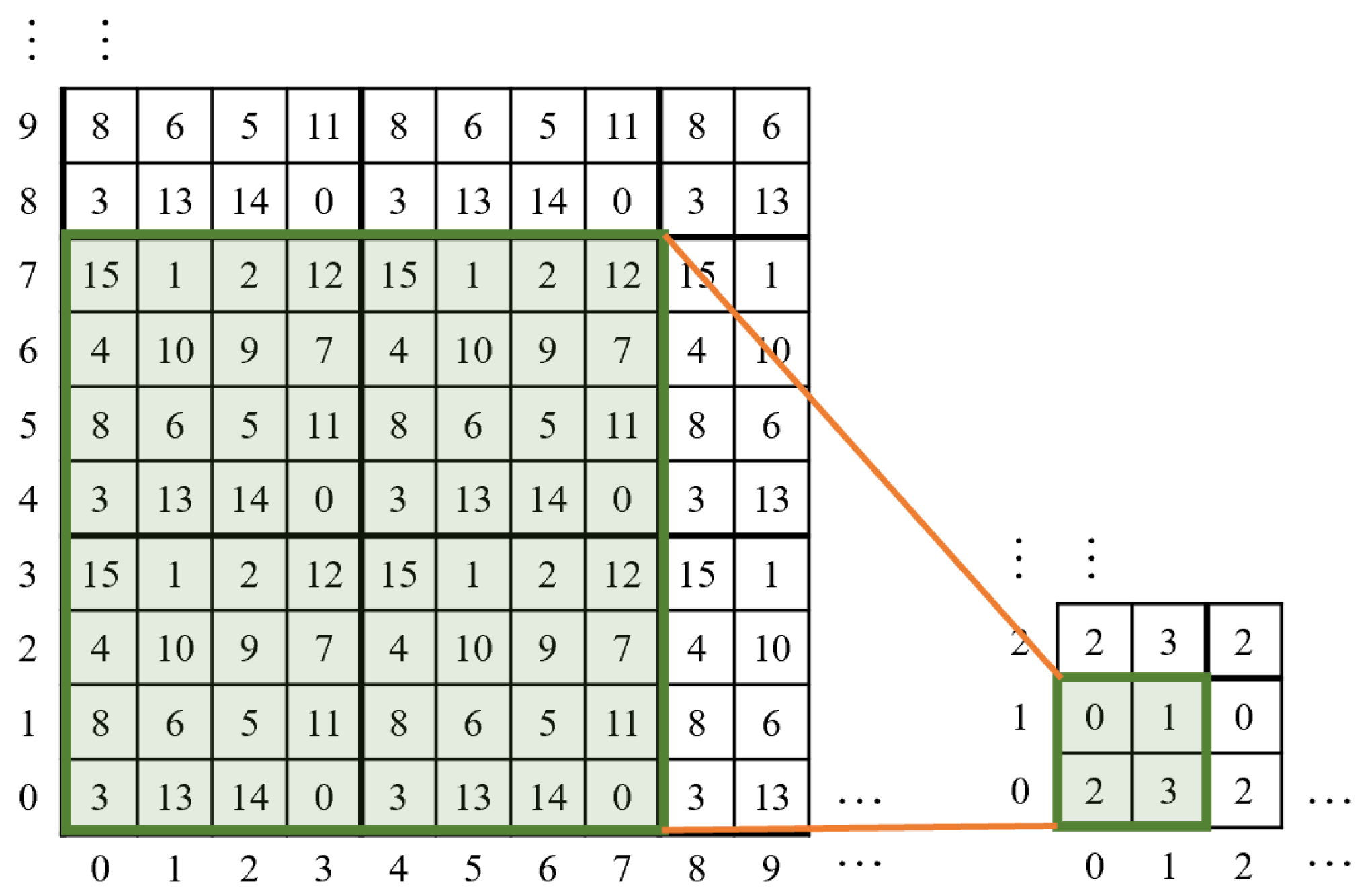
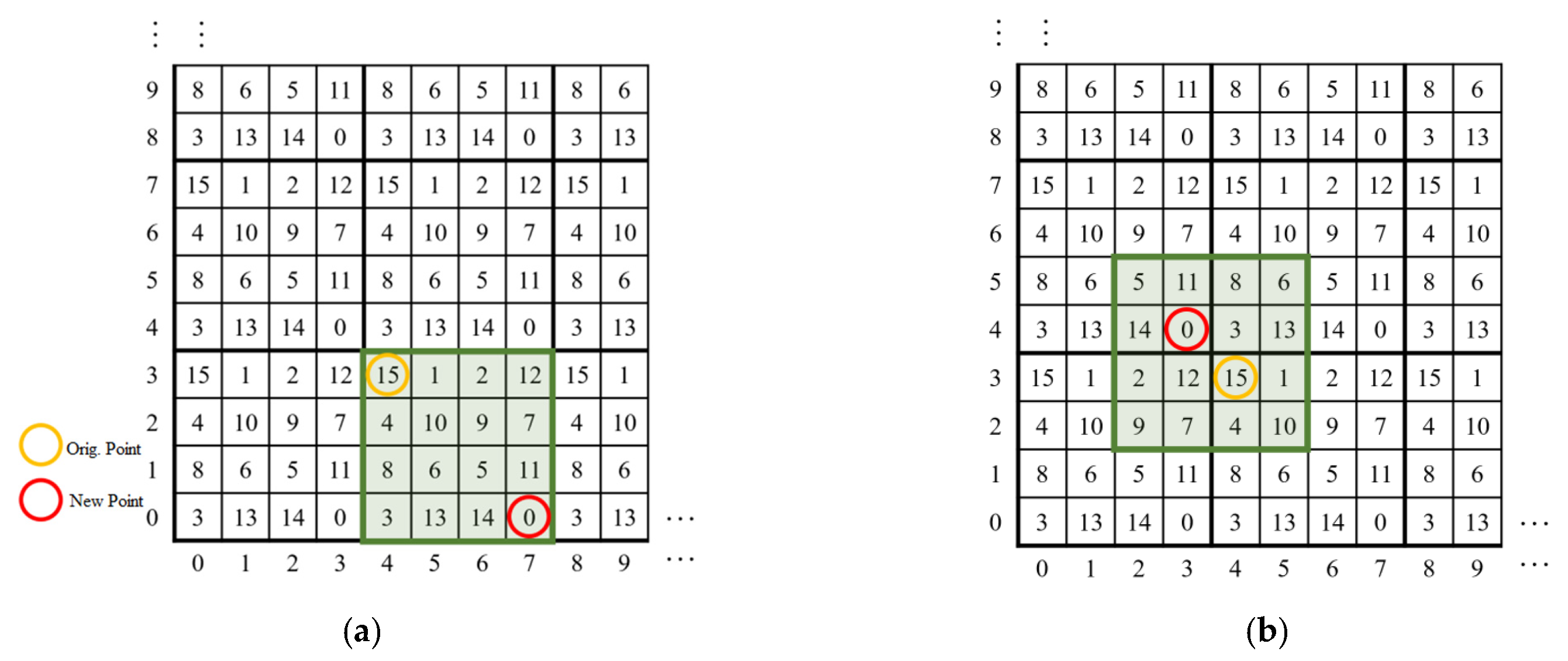
3.1.2. Determination of Traversal Area
3.2. Evaluation Methods
- Visual effect
- 2.
- Embedding rate (ER)
- 3.
- Peak signal-to-noise ratio (PSNR)
4. Experimental Analysis
4.1. Turtle Shell Magic Matrix-Based Image Steganography
4.2. 4 × 4 Magic Matrix-Based Image Steganography
4.3. 4-2 Double-Layer Magic Matrix-Based Image Steganography
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Petitcolas, F.A.P.; Anderson, R.J.; Kuhn, M.G. Information hiding-a survey. Proc. IEEE 1999, 87, 1062–1078. [Google Scholar] [CrossRef]
- Sreejith, R.; Senthil, S. A novel tree based method for data hiding and integrity in medical images. In Proceedings of the IEEE International Conference on Electrical, Instrumentation and Communication Engineering (ICEICE), Karur, India, 27–28 April 2017; pp. 1–4. [Google Scholar]
- Bender, W.; Gruhl, D.; Morimoto, N. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Chang, C.C.; Lin, C.C.; Tseng, C.S. Reversible hiding in DCT-based compressed images. Inf. Sci. 2007, 177, 2768–2786. [Google Scholar] [CrossRef]
- Lu, T.C.; Leng, H.S. Reversible dual-image-based hiding scheme using block folding technique. Symmetry 2017, 9, 223. [Google Scholar] [CrossRef]
- Liu, W.L.; Leng, H.S.; Huang, C.K. A block-based division reversible data hiding method in encrypted images. Symmetry 2017, 9, 308. [Google Scholar] [CrossRef]
- Lin, C.C.; Shiu, P.F. High capacity data hiding scheme for DCT-based images. J. Inf. Hiding Multimed. Signal Process. 2010, 1, 220–240. [Google Scholar]
- Abdelwahab, A.A.; Hassaan, L.A. A discrete wavelet transform based technique for image data hiding. In Proceedings of the 2008 National Radio Science Conference, Tanta, Egypt, 18–20 March 2008; pp. 1–9. [Google Scholar]
- Liu, H.; Liu, J.; Huang, J. A robust DWT-based blind data hiding algorithm. In Proceedings of the IEEE International Symposium on Circuits & Systems, Phoenix-Scottsdale, AZ, USA, 26–29 May 2002; Volume 2, p. II. [Google Scholar]
- Chang, C.C.; Wu, W.C. Hiding secret data adaptively in vector quantization index tables. IEE Proc.-Vis. Image Signal Process. 2006, 153, 889–897. [Google Scholar] [CrossRef]
- Hu, Y.C. High-capacity image hiding scheme based on vector quantization. Pattern Recognit. 2006, 39, 1715–1724. [Google Scholar] [CrossRef]
- Chang, C.C.; Kieu, T.D.; Wu, W.C. A lossless data embedding technique by joint neighboring coding. Pattern Recognit. 2009, 42, 1597–1603. [Google Scholar] [CrossRef]
- Pizzolante, R.; Carpentieri, B.; Castiglione, A. The AVQ algorithm: Watermarking and compression performances. In Proceedings of the 2011 Third International Conference on Intelligent Networking and Collaborative Systems, Fukuoka, Japan, 30 November–2 December 2011; pp. 698–702. [Google Scholar]
- Wang, R.Z.; Lin, C.F.; Lin, J.C. Image hiding by optimal LSB substitution and genetic algorithm. Pattern Recognit. 2001, 34, 671–683. [Google Scholar] [CrossRef]
- Mielikainen, J. LSB matching revisited. IEEE Signal Process. Lett. 2006, 13, 285–287. [Google Scholar] [CrossRef]
- Ker, A.D. Improved detection of LSB steganography in grayscale images. In International Workshop on Information Hiding; Springer: Berlin/Heidelberg, Germany, 2004; pp. 97–115. [Google Scholar]
- Sahu, A.K.; Swain, G. A novel n-rightmost bit replacement image steganography technique. 3D Res. 2019, 10, 2. [Google Scholar] [CrossRef]
- Sahu, A.K.; Swain, G. A novel multi stego-image based data hiding method for gray scale image. Pertanika J. Sci. Technol. 2019, 27, 753–768. [Google Scholar]
- Sahu, A.K.; Swain, G.; Babu, E.S. Digital image steganography using bit flipping. Cybern. Inf. Technol. 2018, 18, 69–80. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, S. Efficient steganographic embedding by exploiting modification direction. IEEE Commun. Lett. 2006, 10, 781–783. [Google Scholar] [CrossRef]
- Kim, H.J.; Kim, C.; Choi, Y. Improved modification direction methods. Comput. Math. Appl. 2010, 60, 319–325. [Google Scholar] [CrossRef]
- Liu, Y.; Chang, C.C.; Huang, P.C.; Hsu, C.Y. Efficient Information Hiding Based on Theory of Numbers. Symmetry 2018, 10, 19. [Google Scholar] [CrossRef]
- Chang, C.C.; Chou, Y.C.; Kieu, T.D. An information hiding scheme using Sudoku. In Proceedings of the 2008 3rd International Conference on Innovative Computing Information and Control, Dalian, China, 18–20 June 2008; p. 17. [Google Scholar]
- Hong, W.; Chen, T.S.; Shiu, C.W. A minimal Euclidean distance searching technique for Sudoku steganography. In Proceedings of the 2008 International Symposium on Information Science and Engineering, Shanghai, China, 20–22 December 2008; Volume 1, pp. 515–518. [Google Scholar]
- Kieu, T.D.; Wang, Z.H.; Chang, C.C. A Sudoku Based Wet Paper Hiding Scheme. Int. J. Smart Home 2011, 3, 1–12. [Google Scholar]
- Chang, C.C.; Liu, Y.; Nguyen, T.S. A novel turtle shell based scheme for data hiding. In Proceedings of the 2014 Tenth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kitakyushu, Japan, 27–29 August 2014; pp. 89–93. [Google Scholar]
- Liu, Y.; Chang, C.C.; Nguyen, T.S. High capacity turtle shell-based data hiding. IET Image Process. 2016, 10, 130–137. [Google Scholar] [CrossRef]
- Jin, Q.; Li, Z.; Chang, C.C. Minimizing Turtle-Shell Matrix Based Stego Image Distortion Using Particle Swarm Optimization. IJ Netw. Secur. 2017, 19, 154–162. [Google Scholar]
- Liu, L.; Chang, C.C.; Wang, A. Data hiding based on extended turtle shell matrix construction method. Multimed. Tools Appl. 2017, 76, 12233–12250. [Google Scholar] [CrossRef]
- Xie, X.Z.; Lin, C.C.; Chang, C.C. Data hiding based on a two-layer turtle shell matrix. Symmetry 2018, 10, 47. [Google Scholar] [CrossRef]
- He, M.; Liu, Y.; Chang, C.C. A mini-Sudoku matrix-based data embedding scheme with high payload. IEEE Access 2019, 7, 141414–141425. [Google Scholar] [CrossRef]
- Horng, J.H.; Xu, S.; Chang, C.C. An Efficient Data-Hiding Scheme Based on Multidimensional Mini-SuDoKu. Sensors 2020, 20, 2739. [Google Scholar] [CrossRef]
- Chen, W.; Chang, C.C.; Weng, S. Multi-Layer Mini-Sudoku Based High-Capacity Data Hiding Method. IEEE Access 2020, 8, 69256–69267. [Google Scholar] [CrossRef]
- USC-SIPI Image Database. Available online: http://sipi.usc.edu/database/ (accessed on 13 December 2020).
- Carpentieri, B.; Castiglione, A.; Santis, A.D.; Palmieri, F.; Pizzolante, R. One-pass lossless data hiding and compression of remote sensing data. Future Gener. Comput. Syst. 2019, 90, 222–239. [Google Scholar] [CrossRef]
- Kumar, R.; Jung, K.H. Enhanced pairwise IPVO-based reversible data hiding scheme using rhombus context. Inf. Sci. 2020, 536, 101–119. [Google Scholar] [CrossRef]

| Cover Image | Chang et al.′s Scheme (TDH) | Low-Com-Cost-2020 | Low-Com-Cost_TS | |||
|---|---|---|---|---|---|---|
| EC (bpp) | PSNR (dB) | EC (bpp) | PSNR (dB) | EC (bpp) | PSNR (dB) | |
| Airplane | 1.5 | 49.76 | 1.5 | 50.17 | 1.5 | 49.2 |
| Baboon | 1.5 | 49.76 | 1.5 | 50.17 | 1.5 | 49.2 |
| Boat | 1.5 | 49.76 | 1.5 | 50.17 | 1.5 | 49.24 |
| House | 1.5 | 49.75 | 1.5 | 50.17 | 1.5 | 49.2 |
| Paper | 1.5 | 49.76 | 1.5 | 50.17 | 1.5 | 49.2 |
| Average | 1.5 | 49.76 | 1.5 | 50.17 | 1.5 | 49.21 |
| Cover Image | ER (bpp) | PSNR (dB) | Hiding Duration | Extraction Duration |
|---|---|---|---|---|
| Baboon | 2 | 46.3651 | 0.0256 | 0.0121 |
| Paper | 2 | 46.3604 | 0.0282 | 0.0137 |
| Airplane | 2 | 46.3658 | 0.0266 | 0.0135 |
| House | 2 | 46.3583 | 0.0305 | 0.0128 |
| Avg | 2 | 46.3624 | 0.0277 | 0.0130 |
| Cover Image | ER (bpp) | PSNR (dB) | Hiding Duration | Extraction Duration |
|---|---|---|---|---|
| Airplane | 3 | 40.73 | 0.041 | 0.0188 |
| Baboon | 3 | 40.731 | 0.0417 | 0.0221 |
| Boat | 3 | 40.725 | 0.0419 | 0.0187 |
| House | 3 | 40.727 | 0.0429 | 0.0193 |
| Paper | 3 | 40.728 | 0.0421 | 0.0185 |
| Avg | 3 | 40.728 | 0.0419 | 0.0195 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hsiao, T.-C.; Liu, D.-X.; Chen, T.-L.; Chen, C.-C. Research on Image Steganography Based on Sudoku Matrix. Symmetry 2021, 13, 387. https://doi.org/10.3390/sym13030387
Hsiao T-C, Liu D-X, Chen T-L, Chen C-C. Research on Image Steganography Based on Sudoku Matrix. Symmetry. 2021; 13(3):387. https://doi.org/10.3390/sym13030387
Chicago/Turabian StyleHsiao, Tsung-Chih, Dong-Xu Liu, Tzer-Long Chen, and Chih-Cheng Chen. 2021. "Research on Image Steganography Based on Sudoku Matrix" Symmetry 13, no. 3: 387. https://doi.org/10.3390/sym13030387
APA StyleHsiao, T.-C., Liu, D.-X., Chen, T.-L., & Chen, C.-C. (2021). Research on Image Steganography Based on Sudoku Matrix. Symmetry, 13(3), 387. https://doi.org/10.3390/sym13030387







