Abstract
Designing a secure construction has always been a fascinating area for the researchers in the field of symmetric key cryptography. This research aimed to make contributions to the design of secure block cipher in the ideal cipher model whose underlying primitive is a family of to random permutations indexed by secret key. Our target construction of a secure block ciphers denoted as is built on a simple XOR operation and two block cipher invocations, under the assumptions that the block cipher in use is a pseudorandom permutation. One out of these two block cipher invocations produce a subkey that is derived from the secret key. It has been accepted that at least two block cipher invocations with XOR operations are required to achieve beyond birthday bound security. In this paper, we investigated the instances with the advanced proof technique and efficient block cipher constructions that bypass the birthday-bound up to provable security was achieved. Our study provided new insights to the block cipher that is beyond birthday bound security.
1. Introduction
A block cipher encryption design is called beyond birthday bound (BBB) secure if the proven upper bound on the adversarial advantage is meaningful even if an adversary can process more than data blocks, where is the size of the block of a block cipher. The first time, Iwata proposed a BBB encryption mode cipher-based encryption (CENC) [1]. This was nonce based construction providing a solution through the invocation of more than one block cipher and simple XOR operation and achieved security against all nonce respecting adversaries. Later on, Iwata proved CENC construction based on mirror theory technique [2], and achieved optimal security [3]. Bhattacharya and Nandi also gave the BBB security of CENC by analyzing the security bound of variable output length using the chi-squared method.
1.1. Pseudorandom Permutation and Pseudorandom Function with BBB
The conventional approach for designing the cryptography primitives based on symmetric cipher is to behave as a perfectly random function. The vast majority, in this case, is an encryption scheme [4], MAC encryption schemes [5,6], and authenticated encryption schemes [7], following this paradigm via pseudorandom functions (PRF). Patarin suggested the construction of permutation sum and proved that a variant of single permutation indistinguishable from a random function up to BBB [8]. In 2003, Patarin gave the result security [9], like so, in 2005, achieved up to this security bound [10,11]. However, the PRF provides a solution for increasing the use of cryptography in a real-world application. The pseudorandom permutation (PRP) is the leading building block of the cryptographic design in spite of PRF [12,13,14,15]. If a block cipher is directly implemented as a PRF, which will have provable security limit birthday bound with a large block, this is often acceptable. But it is not acceptable in practice with a lightweight block cipher, which has relatively small block sizes. The PRF can be replaced by a PRP up to birthday bound queries [16,17,18,19]. Moreover, if the block size of a block cipher is large enough, then the security loss is sometimes acceptable. Whatever, there are many scenarios, such as lightweight applications, whose numbers have grown tremendously before some years that require higher security bound [20,21,22,23,24,25,26]. In recent years, various constructions have been proposed that achieve BBB security against more than queries. We could categorize these constructions into XOR permutations based and truncation based. The XOR permutations is popular for BBB construction by taking the XOR of more than one independent PRP [20].
This construction was analyzed by Lucks [21]. The single key variant of this construction provides the security up to queries [27]. After that, Patarin revised this construction and improved the security bound up to [28]. Later on, the results were generated by more than two independent PRP with XOR operation [29]. Dai et al. [30] using the chi-squared method verified the security of XOR construction, but the original proof was provided by Bhattacharya and Nandi [31]. The XOR construction is acceptable for encryption, but it is not usable for authentication, because domain size is required to extend. This can be solved through hashing the message, but the XOR construction needs some precise combination with a double block hash function [32,33,34]. The truncation based solution was presented by Hall et al. [17]. Later on, it was proved that truncating permutation has security bound up to queries [35]. Stam also derived these results in a non-cryptographic context [27]. Recently, another construction was proposed, which is known as Encrypted Davies Meyer (EDM) introduced by Cogliati and Seurin [36].
There are two independent permutations and it behaves like random function up to [36]. Afterward, Dai et al. [30] achieved using the chi-squared method. Now, a novel construction EDMD improved the security up to by using mirror theory technique, which has almost an optimal security [37].
Two independent keys are required for EDMD. The single key setting is significant for higher security bound and efficient construction, which was also performed in our construction. Anyways, this construction secures up to . Cogliati and Seurin also extended the EDMD construction called encrypted Wegman carter with davies meyer (EWCDM), which is nonce based BBB secure.
where, is a universal hash function, denote the nonce, and denote the message, which has an arbitrary length. The EWCDM achieved up to MAC queries when it has nonce respecting setting. The use of internal state values of EWCDM construction makes their security analysis formally inapplicable [37]. Mennink presented the rationale relying on the EWCDM function, and simplified versions of the conversion method applied to the advanced encryption scheme (AES) [38]. The main proposal of AES-PRF, the AES with a feed forward of the middle state, achieved almost no optimal security. This construction was applied to GCM and GCM-SIV, and how it entails the significant security improvements was discussed. A little while back, Mennink presented a heuristic study to build BBB secure from public random permutation, showing that a single permutation call could not be secured BBB [39].
The above discussion shows that what to be tackled in PRF for BBB and where the goal is to build PRF, so that it is indistinguishable from a truly random function. However, our study aimed to build block cipher in the ideal cipher model, under the assumption that the block cipher is a PRP out of PRF, achieving full security. Moreover, the sum of even mansour (SoEM) construction achieves BBB up to , that is built from two randomly drawn keys and two independent permutations; if either keys or permutations are identical, then there is a birthday bound attack.
1.2. Our Construction
In this paper, we focused on a block cipher design based on a single key, which achieved BBB up to security. The main motivation is by the scenarios where the block cipher only has block size of and [40]. The target construction of block cipher depicted in Figure 1, defined as , consists of two block cipher invocations and additional simple XOR operation. Furthermore, a heuristic approach is carried out to examine the instances of and, at last, efficient construction is successfully found. In detail, the first invoke of block cipher produces a subkey from the secret key such that , , and . The second invoke of a block cipher encrypt and decrypt the plaintext and ciphertext respectively, with a key or . However, we stress that the first block cipher invocation is precomputing and storing the subkey . Thus, our design only requires one invocation of a block cipher for encryption and decryption when the subkey is precomputed and stored. We have designed this construction in the ideal cipher model that has the main advantage of provable security up to . The previously available block cipher has maximum provable security up to . From the efficiency point of view, previous constructions required more than one key, block cipher invocations [20,36], and universal hash function invocations; in the absence of these, their efficiency needed to be increased. The minimum number of block cipher invocation with a single key is good for efficiency. Our design requires just a single secret key and one block cipher invocation for encryption and decryption when the subkey is precomputed and stored.
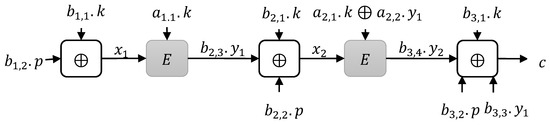
Figure 1.
2. Preliminaries
2.1. Notations
The denotes the set of bit strings of length . We denote the bitwise addition , where . The is the assignment of to the variable . The denotes the uniform random selection of from . The denotes the number of elements in . Let and denotes the multiplication of and , if then it is equal to , and if then equals to 0. The block cipher denotes as where is a plaintext/message space, is the key space. Throughout the paper, we have fixed . Let and denote the encryption and decryption, respectively, with a secret key . Let involves and . Sometimes, we denote as , as , and as and respectively. The are the input and output tuple of such that . The input-output tuple of is denoted as such that . Let denote the set of all permutations on . The function is said to be an if randomly selected that is . Similarly, we define these notations, , and respectively.
2.2. Security Definition
A computationally unbounded distinguisher is an algorithm that has adaptive access to an oracle and outputs a . Let the two oracles and have the same interface, we can get the distinguishing advantage of as follows.
A block cipher with a key space and message space is a mapping such that for all key . The is a permutation over . We denote for . The distinguisher is having query access to : is either with or . The is an underlying block cipher. The advantage of distinguisher in distinguishing and is defined as.
Throughout this paper, we considered information as theoretical with computationally unbounded distinguishers sorely limited by the number of queries to the oracle. Overall, maximum is taken by distinguisher that makes at most queries to its .
2.3. H-Coefficient Technique
Central to our proof is a H-Coefficient technique presented by Patarin [8,41]. As mentioned above, we considered the information as theoretical, with computationally unbounded distinguisher . Thus, we always assumed that distinguisher is deterministic without the loss of generality. Let distinguisher interacts with and . The interaction of with its oracles are recorded in a view . The is the probability distribution of when distinguisher interacts with . The is the set of all attainable views when interacting with , which is . The H-Coefficient technique states as follows:
Let . Consider a partition set of attainable view such that:
Then, the distinguishing advantage satisfies
The core idea of the H-coefficient technique is: a large number of views are almost equally likely in both oracles (real worlds and the ideal world), and the odd ones occur with a small probability. Note that the partitioning of into and views is directly reflected in the terms and in the bound: if is too large, will , whereas if is too large, will become .
3. Construction Limitations
In this section, we will discuss the construction limitations of secure block cipher in the ideal cipher model, which is built on dedicated block cipher invocations and simple XOR operation. The operation has efficiency benefits. The target construction is denoted as and is built on block cipher invocations. Let denote the underlying block cipher with block size and . key size. Let p, , and denote the plaintext, ciphertext, and key, respectively, where all have size. Let and be variable of being or , where and . The encryption of is shown in Algorithm 1. The target construction is depicted in Figure 1. In detail, this is a graphical view from which we would acquire the resultant block cipher construction. Moreover, all the block cipher invocations are involved in the computation of the ciphertext . The ciphertext must be invertible and efficiently decrypted from plaintext and key . There are some limitations for to achieve our goal:
The plaintext should be involved in exactly one operation. The involves in XOR operation, which gives and corresponding . So, both outputs ( and ) are called plaintext dependent variable. On the other side, if a variable is used to compute another variable which depends on , then and corresponding would also be plaintext dependent variable. So, we cannot use plaintext dependent variable to produce any or , otherwise, constructions will not be efficient.
There should be at most one plaintext dependent variable produced from the XOR operation. Otherwise, the decryption process cannot efficiently decrypt because there is more than one variable.
If we summarize and satisfy the above limitations, then can be an efficient block cipher construction. Moreover, an additional condition is also necessary for efficiency and security. Our goal is to achieve () . The target construction is important to achieve the goal. Nowadays, and block cipher is utilized in various applications of different block sizes, such as and . In some environments, the block size of block ciphers can be even shorter. Thus, block cipher construction with a simply birthday bound security may not be suitable for various applications. Therefore, another construction which provide higher security is definitely necessary. Particularly, for application design, a block cipher with full security is surely an interesting research . Our second goal is the efficiency, we invoke two block cipher because minimum number of block cipher invocation led to concern about high efficiency. It is well known that block cipher invocations are much more time consuming than XOR operation. So, the efficiency reduces due to a number of block cipher invocation. But, besides this, we aimed to achieve perfect efficiency under the condition of no security sacrifices, i.e., eliminating the unnecessary input variables. In fact, this is also a reason in our target construction having simple XOR operation and only necessary input variables. Algorithm 1 is shown as follow:
| Algorithm 1 |
| input: |
| Output: |
|
In order to achieve the above goals among the instances of target construction, we adopted a heuristic approach. For the instances of , we invoked only two block cipher to achieve provable security because for instances of had most security. Thus, at least two block cipher invocations are required to bypass the birthday bound barrier.
We continued to examine the instances of and would not analyze the instances unless investigated all the instances of and none of them achieve security. In fact, if some instances of achieves security, then there is no need to examine the other instances of . To follow the above strategy, we analyzed the target construction and found 32 instances with provable security.
3.1. Instances
According to the previous discussion, the plaintext should be involved in exactly one XOR operation. There should be, at most, one plaintext dependent variable produced from the XOR operation. Otherwise, the decryption process cannot efficiently decrypt because there exists more than one variable. The plaintext dependent variable cannot be used to produce any key-value; otherwise, constructions will not be efficient. Following this strategy, we divided instances into three types on the basis of when plaintext is XOR to compute and respectively.
- Type 1 instances: when is XOR to compute
- Type 2 instances: when is XOR to compute
- Type 3 instances: when is XOR to compute
3.1.1. Type 1 Instances
According to the above limitation, the cannot be used to produce key value, so, . The plaintext should be involved in exactly one XOR operation, so, and . We set , which is the first block cipher invocation, and set which is second block cipher invocation. If , it means two block ciphers’ invocations are parallel, and these instances are involved in type 2. It also shows that and are plaintext variables. Then, we set because is already used as a plaintext dependent variable. All of these simplified constructions of type 1 are shown in Figure 2. We examined the instances of type 1, and ciphertext is computed as follows.
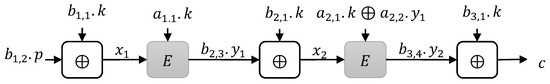
Figure 2.
Instances with one block cipher Invocation of type 1.
We would show that any instance that makes only one block cipher invocation of type 1 construction could not achieve security. Let be a block cipher, shown in Figure 3. We showed that there exists a distinguisher that can distinguish any such block cipher from using at most queries.
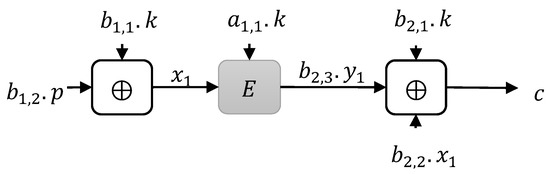
Figure 3.
Type 1: One Block cipher invocation.
● When and .
In this case, we can see the input or output of is not related to or . When , then distinguisher selects arbitrary and to get and . If the event occurs, then output is 1; otherwise, it is 0. The success probability of is 1 when interacts with . The results are similar for .
● When and .
In this case, we can see the input or output of is independent of the key. When , the distinguisher selects arbitrary and to get and then, it puts and to get and . If the event occurs, then output is 1, otherwise 0.
The success probability of is 1 when interacts with . Similar is the case for .
● When .
In this case, there exists a distinguisher , distinguishing the oracle from the ideal world oracle with some probability. The distinguisher makes queries and operates as follows. For , the distinguisher selects arbitrary to get . If for all queries and its indices , then output 1, otherwise output 0.
At the end of type 1 instances, we can conclude that the plaintext added in the first operation and the output value after the first invocation of block cipher are included in second block cipher invocation as a key that is a , so the advantage of the adversary is at most around birthday bound.
3.1.2. Type 2 Instances
Following the construction limitations, set . The plaintext should be involved in exactly one operation, so, and We set that is, the first block cipher invocation, and thus, we set that is, second block cipher invocation. It also shows that and are not plaintext dependent variables. All of these simplified constructions of type 1 are depicted in Figure 4. Here, we examined the type 2 instances. For these instances, we computed ciphertext as follows.
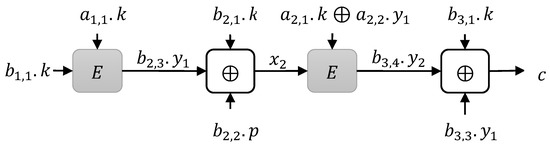
Figure 4.
The first block cipher invocation is . Throughout all the instances of type 2, we call as a subkey that is obtained from the secret key for those instances with . However, the computation from to is and always holds and respectively. Moreover, for any plaintext and ciphertext pair and the adversary knows the internal variable differences and . Therefore, according to the above constraint, we can find some conditions on the type 2 instances to achieve .
● When .
If then it means . Adversary makes a query to to get and the first block cipher invocation kicks off. Then, the instances are based on only a single block cipher invocation in the adversary view. As we discussed in the previous sections, when , the construction achieves security up to birthday bound.
● When .
If then adversary regards and . So, the instance gives essentially one step of [42].
● When .
If then , i.e., the adversary knows and can control the value. A distinguisher is launched and fixes two distinct and . The distinguisher queries to and gets ciphertext and and stores respectively. The makes a query for and receives and , respectively, and matches to stored . The distinguisher recovers For any plaintext-ciphertext pair and the distinguisher can compute (such that ) and and query and to recovering and , respectively. So, the output of distinguisher is 1 if , otherwise, compute 0. When interacting with then the output of distinguisher is 1 until it recovers . Thus, the success probability is .
● When .
This has a similar analysis which is presented above, where the adversary knows and has control over the value of and he fixes the ciphertext and and queries to .
● When .
If it has , which is denoted by and . Thus, the adversary knows and can control . A distinguisher is launched and gives queries to and receives and and stores respectively. Moreover, sends distinct queries to and receives and respectively, and stores . Then, he matches and . The can compute and for any plaintext-ciphertext and receive from . Moreover, the distinguisher just needs to make some extra queries. Thus, the success probability is trivially .
● When .
This is also having a similar analysis as shown above.
Putting all the above properties of type 2 instances together, we got 32 instances, denoted by and depicted in Figure 5. We investigated these constructions and found provable security. We used the H-Coefficient technique for proof, which is discussed in Section 4.
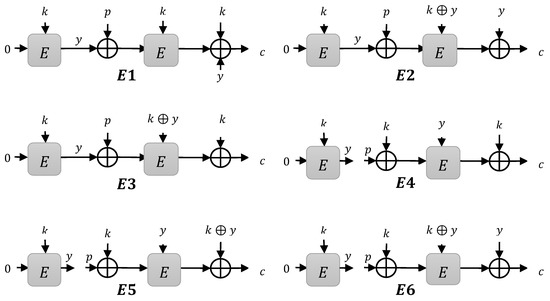
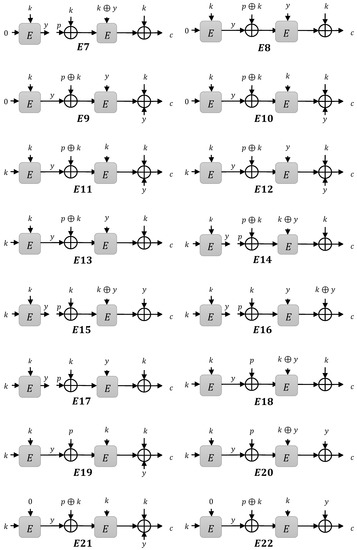
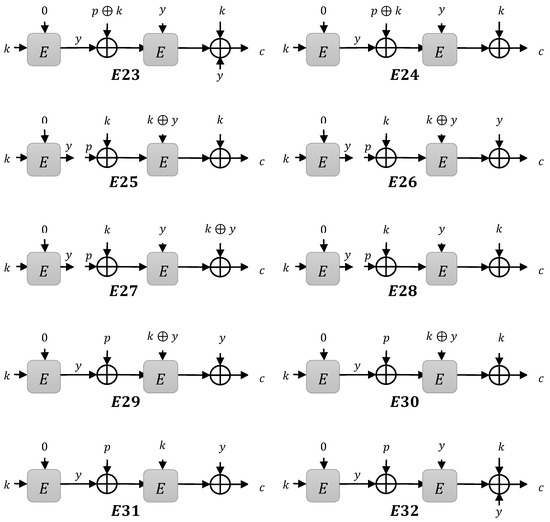
Figure 5.
The efficient construction: the internal variable is referred to as a subkey for these constructions.
3.1.3. Type 3 Instances
When is to compute , then , , and The constructions of type 3 are depicted in Figure 6. In this construction, it could be seen that and are linearly related, and distinguisher can distinguish by only two queries to with distinct plaintext and verifying . Hence, the discussion of type 3 instances is omitted here.

Figure 6.
4. Security Proof
Let is any instance, and is an underlying block cipher. Let there be any distinguisher that has access to oracles and either with or . The distinguisher is computationally unbounded and deterministic, making queries when interacting with and . We defined distinguisher queries to and as and respectively: and do not contain duplicate queries. When distinguisher interacts with and the queries response are and respectively. The is the view denoting the transcripts, and in the end, the distinguisher obtains a view . The distinguisher based on the computes its decision bit. Accordingly, the decision probability distribution of distinguisher relies on the probability distribution of . The and are the probability distribution on when interacts with and respectively. We used as an attainable view when interacts with , which is and . The main goal of the proof is to disclose the subkey and secret key after interacting with and . In as ,, we chose and got corresponding subkey by querying . The distinguisher can easily derive query response of invocations for each query response in . The query responses of a block cipher for each view is divided into three tables. The first one consists of a single query response of block cipher : . The second table consists of the other queries’ responses of block cipher derived from : . The last table consists of all queries’ responses from : .
4.1. Bad Events
if there are following queries: , and such that the following condition holds: there exists in table and in table such that = where then causes bad event.
4.2.
According to our construction, we gave here the exact definition of which also ensures the . The does not cause bad event. Here, we defined the of only due to the limited space. At least, one event defines the if it exists.
- (a)
- such that ;
- (b)
- such that ;
- (c)
- and such that
- (d)
- and such that
The subkey and secret are uniformly selected at random from a size of at least . We get
Thus, we get
Let and using above values, we get
4.3. Ratio for
First of all, . The is a random variable that is defined on the probability space of all possible underlying block cipher and all possible secret key . The probability space of is denoted as . Correspondingly, the is equal to . In , an element getting along with is taken, if gives exactly the same responses for all queries. The is defined as all the elements in compatible with .
Similarly, is defined on the probability space of , underlying block cipher , and key . On defining and respectively, we have
is , that is the number of keys times, the number of block ciphers. We next computed and . We knew that the view contains the key value, that is, at the end of the interaction, it is disclosed to distinguisher . A set of input outputs of underlying block cipher are derived and separately stored in tables , and . The number of input-output of with the key value is denoted as and in and respectively, where . The denotes the number of queries to with key value. There is no collision between any two tables, so is good. Secondly, the distinguisher never makes duplicate queries. Therefore, all the inputs and outputs of in , and are distinct, showing that. The query response of in has or ( have and others ). On assuming , we got
From , we have
We can compute
Finally, we can compute
Thus, it gives a ratio for
Combining both 4.2 and 4.3,
Author Contributions
L.W. conceptualized the idea, Y.N. performed analysis, and both the authors wrote manuscript in coordination with each other.
Funding
National Nature Science Foundation of China, Youth Project.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Iwata, T. New Blockcipher Modes of Operation with Beyond the Birthday Bound Security. In International Workshop on Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2006; pp. 310–327. [Google Scholar]
- Patarin, J. Mirror theory and cryptography. Appl. Algebra Eng. Commun. Comput. 2017, 28, 321–338. [Google Scholar] [CrossRef]
- Iwata, T.; Mennink, B.; Vizár, D. Cenc is optimally secure. IACR Cryptol. ePrint Arch. 2016, 2016, 1087. [Google Scholar]
- Bellare, M.; Desai, A.; Jokipii, E.; Rogaway, P. A concrete security treatment of symmetric encryption. In Proceedings of the 38th Annual Symposium on Foundations of Computer Science, Miami Beach, FL, USA, 20–22 October 1997; pp. 394–403. [Google Scholar]
- Bellare, M.; Guérin, R.; Rogaway, P. Xor macs: New methods for message authentication using finite pseudorandom functions. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1995; pp. 15–28. [Google Scholar]
- Bernstein, D.J. How to stretch random functions: The security of protected counter sums. J. Cryptol. 1999, 12, 185–192. [Google Scholar] [CrossRef]
- McGrew, D.A.; Viega, J. The security and performance of the galois/counter mode (gcm) of operation. In International Conference on Cryptology in India; Springer: Berlin/Heidelberg, Germany, 2004; pp. 343–355. [Google Scholar]
- Patarin, J. A Proof of Security in O(2n) for the Xor of Two Random Permutations. In International Conference on Information Theoretic Security; Springer: Berlin/Heidelberg, Germany, 2008; pp. 232–248. [Google Scholar]
- Patarin, J. Luby-rackoff: 7 rounds are enough for 2n(1−ε) security. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2003; pp. 513–529. [Google Scholar]
- Patarin, J. On linear systems of equations with distinct variables and small block size. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2005; pp. 299–321. [Google Scholar]
- Patarin, J. Introduction to mirror theory: Analysis of systems of linear equalities and linear non equalities for cryptography. IACR Cryptol. ePrint Arch. 2010, 2010, 287. [Google Scholar]
- Daemen, J.; Rijmen, V. Rijndael/aes. Encycl. Cryptogr. Secur. 2005, 520–524. [Google Scholar] [CrossRef]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.; Seurin, Y.; Vikkelsoe, C. Present: An ultra-lightweight block cipher. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- De Canniere, C.; Dunkelman, O.; Knežević, M. Katan and ktantan—A family of small and efficient hardware-oriented block ciphers. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2009; pp. 272–288. [Google Scholar]
- Guo, J.; Peyrin, T.; Poschmann, A.; Robshaw, M. The led block cipher. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 326–341. [Google Scholar]
- Impagliazzo, R.; Rudich, S. Limits on the provable consequences of one-way permutations (invited talk). In Proceedings on Advances in Cryptology; Springer: Berlin/Heidelberg, Germany, 1990; pp. 8–26. [Google Scholar]
- Hall, C.; Wagner, D.; Kelsey, J.; Schneier, B. Building prfs from prps. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1998; pp. 370–389. [Google Scholar]
- Bellare, M.; Rogaway, P. The security of triple encryption and a framework for code-based game-playing proofs. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2006; pp. 409–426. [Google Scholar]
- Chang, D.; Nandi, M. A short proof of the prp/prf switching lemma. IACR Cryptol. ePrint Arch. 2008, 2008, 78. [Google Scholar]
- Bellare, M.; Krovetz, T.; Rogaway, P. Luby-rackoff backwards: Increasing security by making block ciphers non-invertible. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1998; pp. 266–280. [Google Scholar]
- Lucks, S. The sum of prps is a secure prf. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2000; pp. 470–484. [Google Scholar]
- Lim, C.H.; Korkishko, T. Mcrypton–a lightweight block cipher for security of low-cost rfid tags and sensors. In International Workshop on Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2005; pp. 243–258. [Google Scholar]
- Wu, W.; Zhang, L. Lblock: A Lightweight Block Cipher; Springer: Berlin/Heidelberg, Germany, 2011; pp. 327–344. [Google Scholar]
- Borghoff, J.; Canteaut, A.; Güneysu, T.; Kavun, E.B.; Knezevic, M.; Knudsen, L.R.; Leander, G.; Nikov, V.; Paar, C.; Rechberger, C.; et al. Prince—A Low-Latency Block Cipher for Pervasive Computing App. Lications; Springer: Berlin/Heidelberg, Germany, 2012; pp. 208–225. [Google Scholar]
- Beaulieu, R.; Treatman-Clark, S.; Shors, D.; Weeks, B.; Smith, J.; Wingers, L. The simon and speck lightweight block ciphers. In Proceedings of the 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Beierle, C.; Jean, J.; Kölbl, S.; Leander, G.; Moradi, A.; Peyrin, T.; Sasaki, Y.; Sasdrich, P.; Sim, S.M. The skinny family of block ciphers and its low-latency variant mantis. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2016; pp. 123–153. [Google Scholar]
- Bellare, M.; Impagliazzo, R. A tool for obtaining tighter security analyses of pseudorandom function based constructions, with app. lications to prp to prf conversion. IACR Cryptol. ePrint Arch. 1999, 1999, 24. [Google Scholar]
- Patarin, J. Security in O(2n) for the xor of two random permutations\-proof with the standard h technique. IACR Cryptol. ePrint Arch. 2013, 2013, 368. [Google Scholar]
- Cogliati, B.; Lampe, R.; Patarin, J. The indistinguishability of the xor of $$ k $$ permutations. In International Workshop on Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2014; pp. 285–302. [Google Scholar]
- Dai, W.; Hoang, V.T.; Tessaro, S. Information-theoretic indistinguishability via the chi-squared method. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2017; pp. 497–523. [Google Scholar]
- Bhattacharya, S.; Nandi, M. Revisiting variable output length xor pseudorandom function. IACR Trans. Symmetric Cryptol. 2018, 2018, 314–335. [Google Scholar]
- Yasuda, K. A new variant of pmac: Beyond the birthday bound. In Annual Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2011; pp. 596–609. [Google Scholar]
- Datta, N.; Dutta, A.; Nandi, M.; Paul, G.; Zhang, L. Single key variant of PMAC_plus. IACR Trans. Symmetric Cryptol. 2017, 2017, 268–305. [Google Scholar]
- Naito, Y. Blockcipher-based macs: Beyond the birthday bound without message length. In International Conference on the Theory and App.lication of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2017; pp. 446–470. [Google Scholar]
- Gilboa, S.; Gueron, S. The advantage of truncated permutations. In International Symposium on Cyber Security Cryptography and Machine Learning; Springer: Berlin/Heidelberg, Germany, 2019; pp. 111–120. [Google Scholar]
- Cogliati, B.; Seurin, Y. Ewcdm: An efficient, beyond-birthday secure, nonce-misuse resistant mac. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2016; pp. 121–149. [Google Scholar]
- Mennink, B.; Neves, S. Encrypted davies-meyer and its dual: Towards optimal security using mirror theory. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2017; pp. 556–583. [Google Scholar]
- Mennink, B.; Neves, S. Optimal prfs from blockcipher designs. IACR Trans. Symmetric Cryptol. 2017, 228–252. [Google Scholar]
- Chen, Y.L.; Lambooij, E.; Mennink, B. How to build pseudorandom functions from public random permutations. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2019; pp. 266–293. [Google Scholar]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. Simon and speck: Block ciphers for the internet of things. IACR Cryptol. ePrint Arch. 2015, 2015, 585. [Google Scholar]
- Chen, S.; Steinberger, J. Tight security bounds for key-alternating ciphers. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2014; pp. 327–350. [Google Scholar]
- Even, S.; Mansour, Y. A construction of a cipher from a single pseudorandom permutation. J. Cryptol. 1997, 10, 151–161. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).