Modified Advanced Encryption Standard Algorithm for Information Security
Abstract
1. Introduction
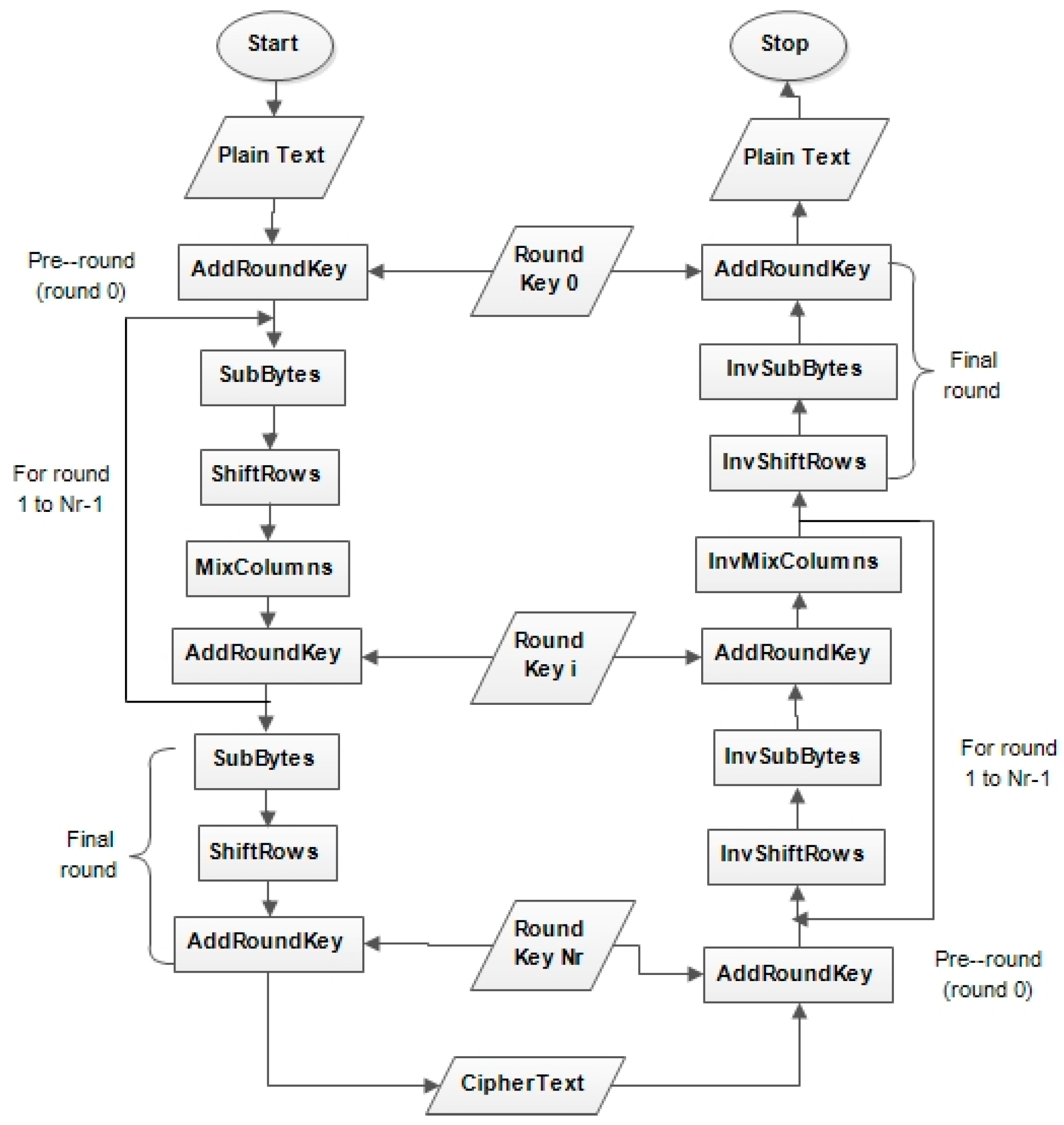
2. Existing AES Algorithm
- (i)
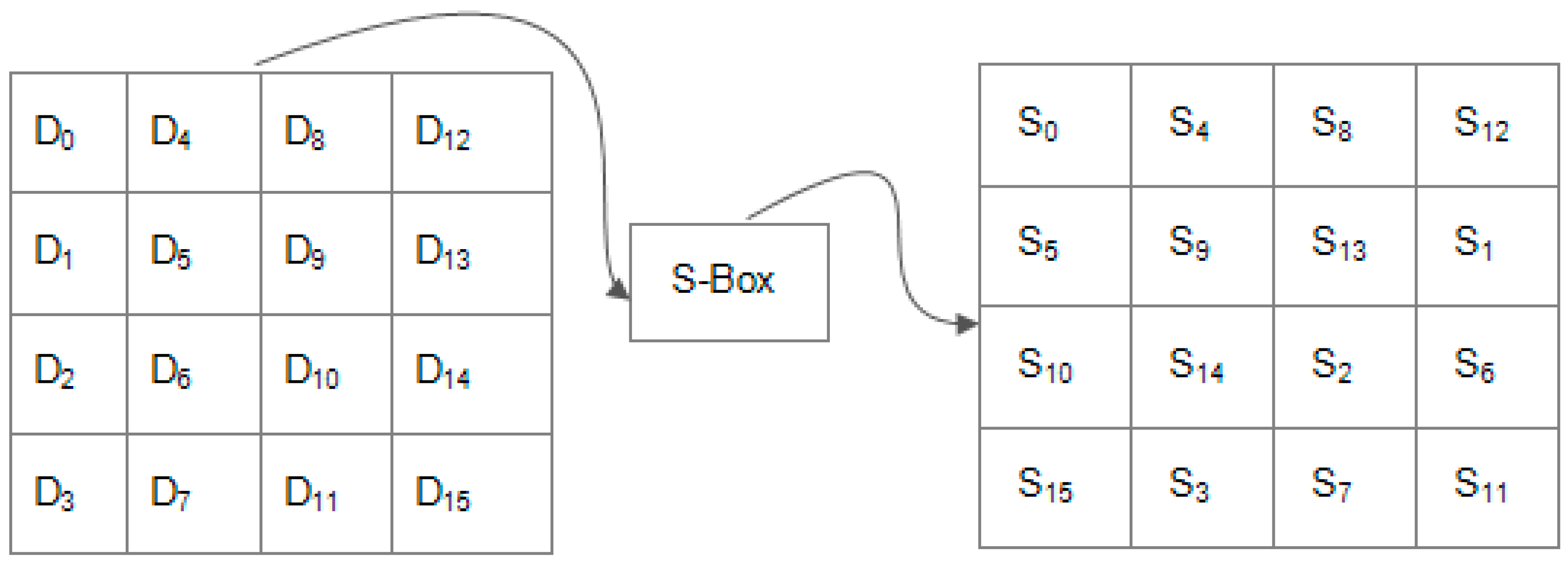
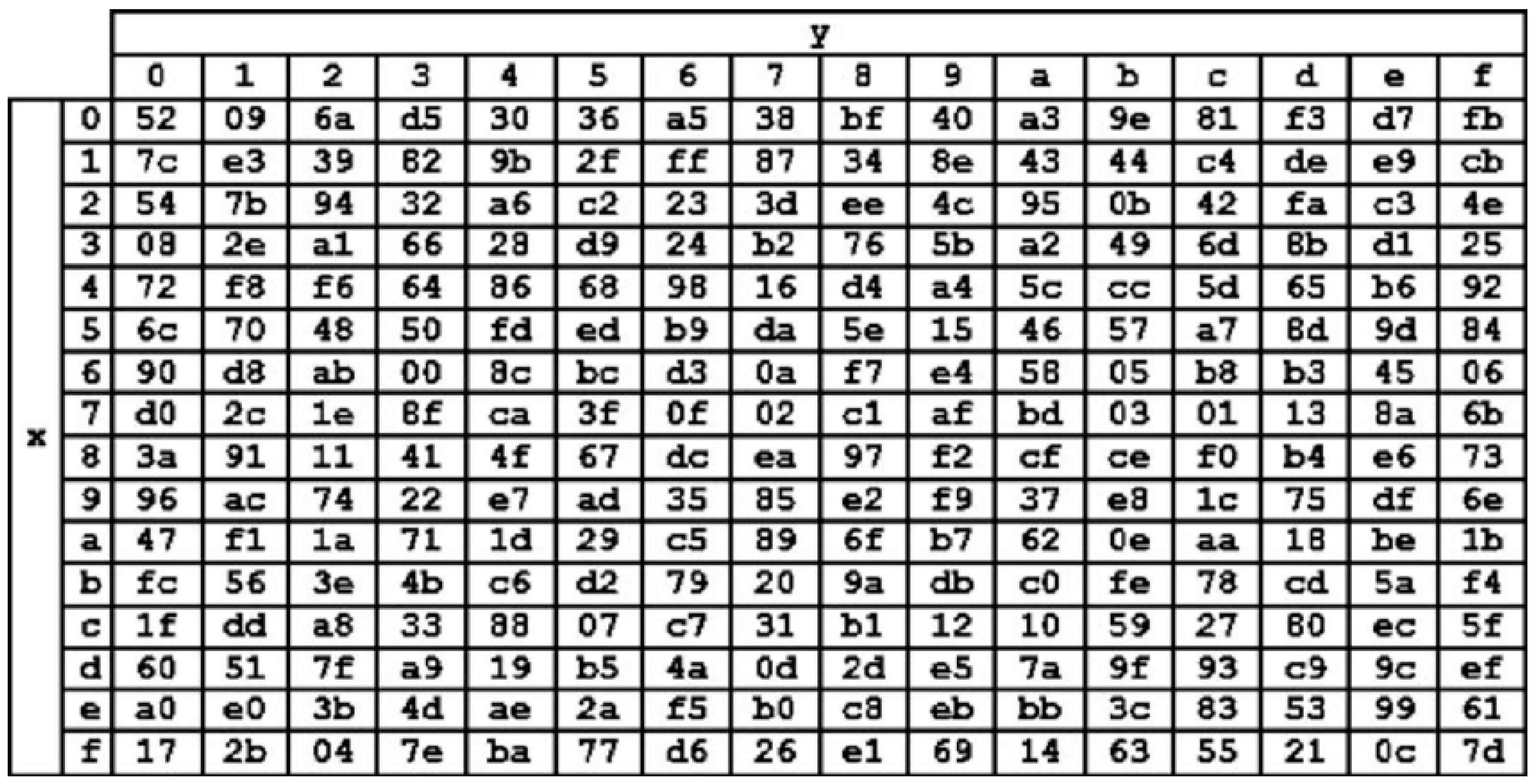
- SubBytes Transformation: as shown in Figure 2, SubBytes transformation is the only non-linear and invertible byte transformation that replaces each byte of the input data block (D0, …, D15) by the row (first 4-bits) and column (second 4-bits) of a 16 × 16 Substitution Box (S-Box). The S-Box, as shown in Figure 3, has special mathematical properties that ensure that changes in individual state bits propagate quickly across the cipher text, which introduces confusion. Inverse substitution table (InvS-Box) is used during decryption to undo the effect of the SubBytes transformation.
- (ii)
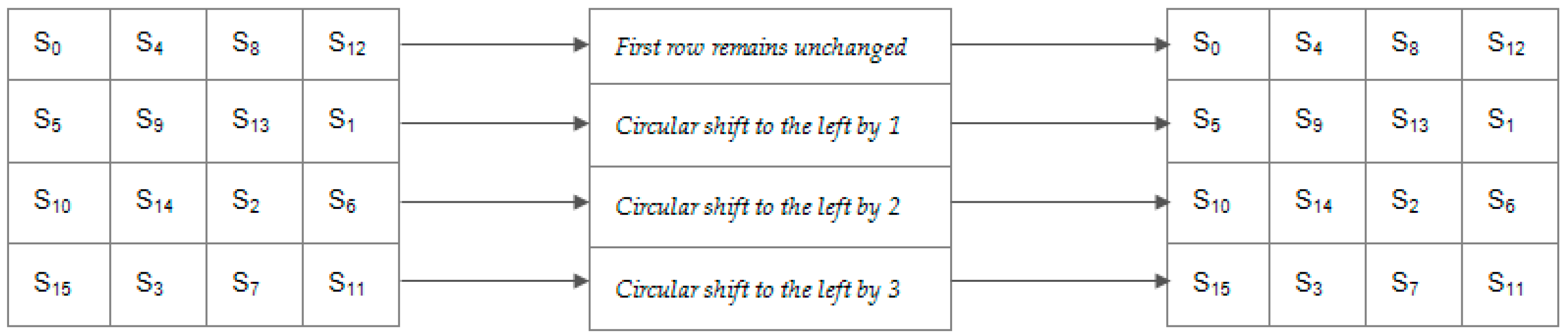
- ShiftRows Transformation: This manipulates the rows of the state by using a certain offset to shift the bytes in each row, as shown in Figure 4. This is carried out to ensure that the columns of the state are not independently encrypted. During this operation, the first row remains unchanged, while one-byte, two-byte, and three-byte circular shift operation is performed on the second, third, and fourth rows, respectively. For the decryption process, the first row remains unchanged, while the other rows are shifted to the right based on the same offset used to shift them to the left during encryption process
- (iii)
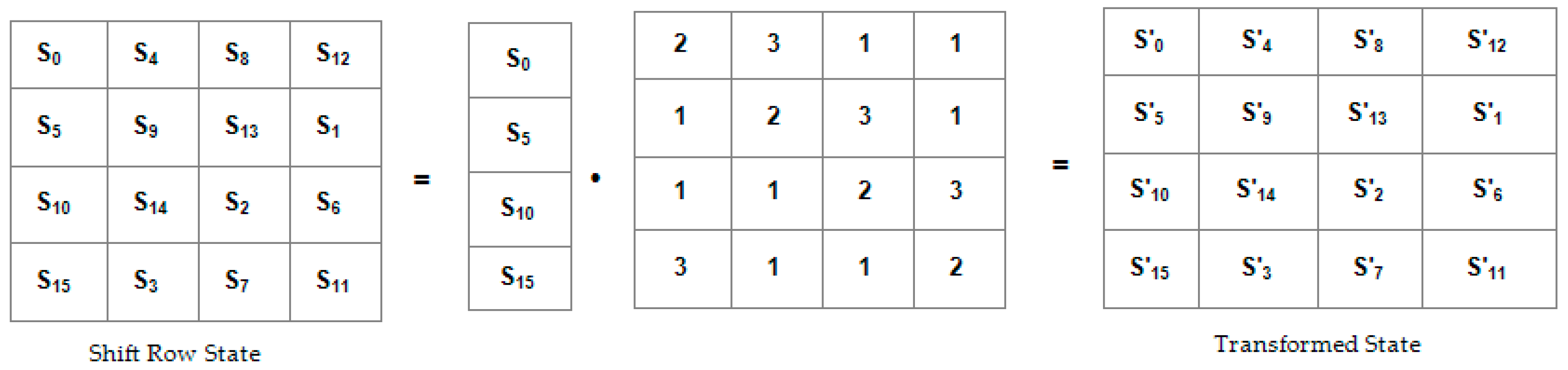
- MixColumns Transformation: This is a linear diffusion process that sees the columns of the state as coefficients of polynomial of order x7. It manipulates all the columns of the state by carrying out multiplication and addition operation on their bytes. Exclusive OR (XOR) is used for the addition operation while modulo is used for the multiplication operation. As shown in Figure 5, each column of the state obtained from shiftrow transformation is multiplied by a mixing matrix to obtain the transformed matrix. With this manipulation, the initial setting of the cipher text is changed, such that no bytes look similar. Inverse MixColumns is used to undo this transformation during the decryption process.
- (iv)
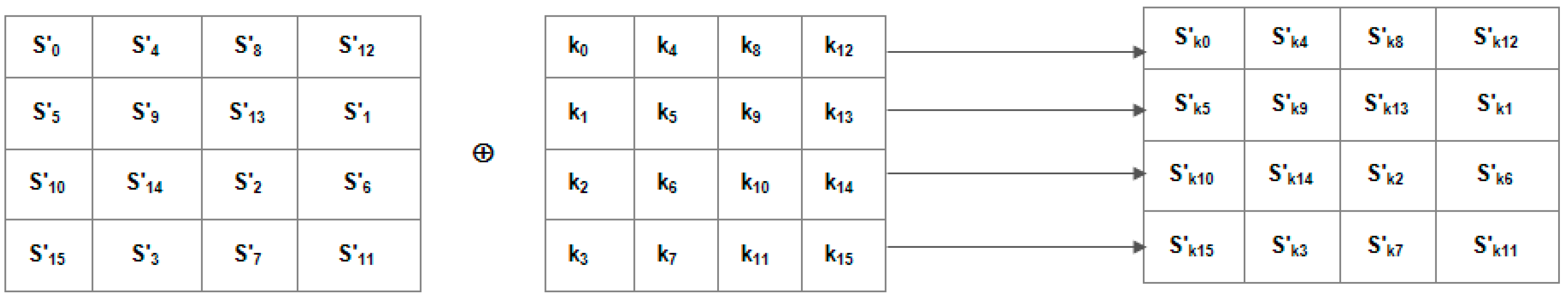
- AddRoundKey Transformation: This is the last transformation that will be done for each round. As shown in Figure 6, an addition operation between the bytes of the transformed state and the round key is carried out while using XOR.
3. Related Works
4. Proposed Methodology
4.1. Modified SubBytes Transformation
| S= | S 0,0 | S 0,1 | S 0,2 | S 0,3 | and K = | K0,0 | K0,1 | K0,2 | K0,3 |
| S 1,0 | S 1,1 | S 1,2 | S 1,3 | K1,0 | K1,1 | K1,2 | K1,3 | ||
| S 2,0 | S 2,1 | S 2,2 | S 2,3 | K2,0 | K2,1 | K2,2 | K2,3 | ||
| S 3,0 | S 3,1 | S 3,2 | S 3,3 | K3,0 | K3,1 | K3,2 | K3,3 |
| S ’ = | S 0,0 ⨁ Key0 | S 0,1 ⨁ Key0 | S 0,2 ⨁ Key0 | S 0,3 ⨁ Key0 |
| S 1,0 ⨁ Key1 | S 1,1 ⨁ Key1 | S 1,2 ⨁ Key1 | S 1,3 ⨁ Key1 | |
| S 2,0 ⨁ Key2 | S 2,1 ⨁ Key2 | S 2,2 ⨁ Key2 | S 2,3 ⨁ Key2 | |
| S 3,0 ⨁ Key3 | S 3,1 ⨁ Key3 | S 3,2 ⨁ Key3 | S 3,3 ⨁ Key3 |
| S′= | S’0,0 | S’0,1 | S’0,2 | S’0,3 |
| S’1,0 | S’1,1 | S’1,2 | S’1,3 | |
| S’2,0 | S’2,1 | S’2,2 | S’2,3 | |
| S’3,0 | S’3,1 | S’3,2 | S’3,3 |
4.2. Modified Inverse SubBytes Transformation
| S ’ = | S’0,0 | S’0,1 | S’0,2 | S’0,3 |
| S’1,0 | S’1,1 | S’1,2 | S’1,3 | |
| S’2,0 | S’2,1 | S’2,2 | S’2,3 | |
| S’3,0 | S’3,1 | S’3,2 | S’3,3 |
| S = | S’ 0,0 ⨁ Key0 | S’ 0,1 ⨁ Key0 | S’ 0,2 ⨁ Key0 | S’ 0,3 ⨁ Key0 |
| S’ 1,0 ⨁ Key1 | S’ 1,1 ⨁ Key1 | S’ 1,2 ⨁ Key1 | S’ 1,3 ⨁ Key1 | |
| S’ 2,0 ⨁ Key2 | S’ 2,1 ⨁ Key2 | S’ 2,2 ⨁ Key2 | S’ 2,3 ⨁ Key2 | |
| S’ 3,0 ⨁ Key3 | S’ 3,1 ⨁ Key3 | S’ 3,2 ⨁ Key3 | S’ 3,3 ⨁ Key3 |
| S = | S0,0 | S0,1 | S0,2 | S0,3 |
| S1,0 | S1,1 | S1,2 | S1,3 | |
| S2,0 | S2,1 | S2,2 | S2,3 | |
| S3,0 | S3,1 | S3,2 | S3,3 |
4.3. Modified ShiftRows Transformation
| S= | S 0,0 | S 0,1 | S 0,2 | S 0,3 | and K = | K0,0 | K0,1 | K0,2 | K0,3 |
| S 1,0 | S 1,1 | S 1,2 | S 1,3 | K1,0 | K1,1 | K1,2 | K1,3 | ||
| S 2,0 | S 2,1 | S 2,2 | S 2,3 | K2,0 | K2,1 | K2,2 | K2,3 | ||
| S 3,0 | S 3,1 | S 3,2 | S 3,3 | K3,0 | K3,1 | K3,2 | K3,3 |
- Step 1: Each row (Rowi) of the state matrix was added to the corresponding row in the round key matrix using XOR to obtain a 4-byte vector called State-Key (SKey) vector.
- Step 2: The four-byte of the State-Key vector are then XORed together to obtain an 8-bit value called the Rank Value (RVal).
- Step 3: The eight-bit Rank Value (RVali) is then stored in corresponding Rowi of the state matrix.
- Step 4: Steps 1–3 will be repeated for the remaining rows Row1 to Row3
- Step 5: Attach Rank Number (RNo) to the Rank Values obtained in Step 3 above for each of the rows of the state (Row0 to Row3) in ascending order with the minimum rank value having 1 as the rank number while the maximum rank value has 4 as the Rank Number.
| S = | 4D | 87 | F2 | 97 | and K = | 11 | 55 | 75 | A1 |
| EC | 6E | 4C | 90 | 1F | 44 | 53 | CA | ||
| 4A | C3 | 46 | E7 | 83 | E6 | 90 | 3D | ||
| 8C | D8 | 95 | A6 | D4 | 31 | 77 | 9F |
| S = | 4D | 87 | F2 | 97 | S’ = | 4D | 87 | F2 | 97 |
| EC | 6E | 4C | 90 | 4C | 90 | EC | 6E | ||
| 4A | C3 | 46 | E7 | E7 | 4A | C3 | 46 | ||
| 8C | D8 | 95 | A6 | D8 | 95 | A6 | 8C |
4.4. Modified Inverse ShiftRows Transformation
4.5. Evaluating the Performance of the Modified AES
5. Results and Discussion
5.1. Measuring the Avalanche Effect
5.1.1. Avalanche Effect with a Short Plain Text File
5.1.2. Avalanche Effect with a 0.5 mb Text File
5.2. Measuring the Execution Time
- (i)
- 4.00 GB Random Access Memory (RAM).
- (ii)
- 500 GB Hard Disk Drive (HDD).
- (iii)
- Intel(R) Core i3 Processor clocking @ 2.27 GHz Dual Core.
- (iv)
- A 64 bit Microsoft Windows 10 Pro Operating System.
5.3. Comparative Analysis of Computed Results with Existing Works
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Christiana, A.O.; Adeshola, G.Q.; Oluwatobi, A.N. Implementation of Textual Information Encryption using 128, 192 and 256 Bits Advanced Encryption Standard Algorithm. Ann. Comput. Sci. Ser. 2017, 15, 153–159. [Google Scholar]
- Iyer, S.C.; Sedamkar, R.; Gupta, S. A Novel Idea on Multimedia Encryption Using Hybrid Crypto Approach. Procedia Comput. Sci. 2016, 79, 293–298. [Google Scholar] [CrossRef]
- Mahendra, L.I.; Santoso, Y.K.; Shidik, G.F. Enhanced AES using MAC Address for Cloud. In Proceedings of the 2017 International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 7–8 October 2017; pp. 66–71. [Google Scholar]
- Kundi, D.-S.; Aziz, A.; Ikram, N. A high performance ST-Box based unified AES encryption/decryption architecture on FPGA. Microprocess. Microsyst. 2015, 41, 1–10. [Google Scholar] [CrossRef]
- Mestiri, H.; Kahri, F.; Bouallegue, B.; Machhout, M. A high-speed AES design resistant to fault injection attacks. Microprocess. Microsyst. 2016, 41, 47–55. [Google Scholar] [CrossRef]
- Mathur, N.; Bansode, R. AES Based Text Encryption Using 12 Rounds with Dynamic Key Selection. Procedia Comput. Sci. 2016, 79, 1036–1043. [Google Scholar] [CrossRef]
- Gérault, D.; Lafourcade, P.; Minier, M.; Solnon, C. Revisiting AES related-key differential attacks with constraint programming. Inf. Process. Lett. 2018, 139, 24–29. [Google Scholar] [CrossRef]
- Zodpe, H.; Sapkal, A. An Efficient AES Implementation using FPGA with Enhanced Security Features. J. King Saud Univ. Eng. Sci. 2018, in press. [Google Scholar] [CrossRef]
- Pradhan, R.; Gupta, A.; Jaiswal, M. An Enhanced AES algorithm using cascading method on 400 bits key size used in enhancing the safety of next generation Internet of things (IOT). In Proceedings of the 2017 IEEE International Conference on Computing, Communication and Automation (ICCCA), London, UK, 5–6 May 2017. [Google Scholar]
- Selimis, G.N.; Kakarountas, A.P.; Fournaris, A.P.; Milidonis, A.; Koufopavlou, O. A Low Power Design for Sbox Cryptographic Primitive of Advanced Encryption Standard for Mobile End-Users. J. Low Power Electron. 2007, 3, 327–336. [Google Scholar] [CrossRef]
- Gamido, H.V.; Sison, A.M.; Medina, R.P. Implementation of Modified AES as Image Encryption Scheme. Indones. J. Electr. Eng. Inform. (IJEEI) 2018, 6, 301–308. [Google Scholar] [CrossRef]
- Saha, R.; Geetha, G.; Kumar, G.; Kim, T.-H. RK-AES: An Improved Version of AES Using a New Key Generation Process with Random Keys. Secur. Commun. Netw. 2018, 2018, 1–11. [Google Scholar] [CrossRef]
- Kumar, P.; Rana, S.B. Development of modified AES algorithm for data security. Optik 2016, 127, 2341–2345. [Google Scholar] [CrossRef]
- Vaidehi, M.; Rabi, B.J. Enhanced MixColumn Design for AES Encryption. Indian J. Sci. Technol. 2015, 8, 1–7. [Google Scholar] [CrossRef]
- Reyes, E.M.D.L. Modified AES Cipher Round and Key Schedule. In Proceedings of the 2018 International Conference on Intelligent Informatics and Biomedical Sciences (ICIIBMS), Bangkok, Thailand, 21–24 October 2018. [Google Scholar]
- Chowdhury, A.R.; Mahmud, J.; Raihan, A.; Kamal, M.; Hamid, A. MAES: Modified Advanced Encryption Standard for Resource Constraint Environments. In Proceedings of the IEEE Sensors Applications Symposium (SAS), Seoul, Korea, 12–14 March 2018; pp. 2–7. [Google Scholar]
- Talirongan, H.; Sison, A.M.; Medina, R.P. Modified Advanced Encryption Standard using Butterfly Effect. In Proceedings of the 2018 IEEE 10th International Conference on Humanoid, Nanotechnology, Information Technology, Communication and Control., Environment and Management (HNICEM), Baguio City, Philippines, 29 November–2 December 2018; pp. 1–6. [Google Scholar]
- Nejad, F.H.; Sabah, S.; Jam, A.J. Analysis of avalanche effect on advance encryption standard by using dynamic S-Box depends on rounds keys. In Proceedings of the 2014 International Conference on Computational Science and Technology (ICCST), Sabah, Malaysia, 27–28 August 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–5. [Google Scholar]
- Kalaiselvi, K.; Kumar, A. Enhanced AES cryptosystem by using genetic algorithm and neural network in S-box. In Proceedings of the 2016 IEEE International Conference on Current Trends in Advanced Computing (ICCTAC), Bangalore, India, 10–11 March 2016; pp. 1–6. [Google Scholar]
- Fathi, M.H.; Sekhavat, Y.A.; Toughi, S. An image encryption scheme based on elliptic curve pseudo random and Advanced Encryption System. Signal. Process. 2017, 141, 217–227. [Google Scholar]
- D’Souza, F.J.; Panchal, D. Advanced encryption standard (AES) security enhancement using hybrid approach. In Proceedings of the 2017 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017. [Google Scholar]
- Hoomod, H.K.; Zewayr, M.H. Image Encryption Using Modified AES with Bio-Chaotic. Int. J. Adv. Sci. Res. Eng. (IJASRE) 2016, 02, 8–31. [Google Scholar]
- Phyu, P.M.; Khin, M.L. New Analysis Methods on Strict Avalanche Criterion of S-Boxes. Int. J. Math. Comput. Sci. 2008, II, 899–903. [Google Scholar]
- Castro, J.C.; Sezneca, A.; Izquierdo, A.; Ribagorda, A. The Strict Avalanche Criterion Randomness Test. Math. Comput. Simul. 2005, 68, 1–7. [Google Scholar] [CrossRef]
- Deshmukh, P.; Kolhe, V. Modified AES based algorithm for MPEG video encryption. In Proceedings of the International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, India, 27–28 February 2014; pp. 1–5. [Google Scholar]
- Sadiq, A.T.; Faisal, F.H. Modification of AES algorithm based on Extended Key and Plain Text. J. Adv. Comput. Sci. Technol. Res. 2015, 5, 104–112. [Google Scholar]
- Anukirti; Jayaswal, V. Modified AES Algorithm Integrating IBDP (Image Block Displacement Procedure) for Data Encryption. Int. J. Comput. Appl. 2018, 179, 5–9. [Google Scholar]
- Kawle, P.; Hiwase, A.; Bagde, G.; Tekam, E.; Kalbande, R. Modified Advanced Encryption Standard. Int. J. Soft Comput. Eng. (IJSCE) 2014, 4, 21–23. [Google Scholar]
- Lakshmi, R.; Mohan, H.S. Implementation and performance analysis of modified AES Algorithm with key-dependent dynamic s-box and key multiplication. Int. J. Math. Comput. Appl. Res. (IJMCAR) 2015, 5, 1–10. [Google Scholar]
- Yan, J.; Chen, F. An Improved AES Key Expansion Algorithm. In Proceedings of the 2016 International Conference on Electrical, Mechanical and Industrial Engineering, Phuket, Thailand, 24–25 April 2016; pp. 113–116. [Google Scholar]
- Jammu, A.; Harjinder, S. Improved AES for Data Security in E-Health. Int. J. of Adv. Res. in Comput. Sci. 2017, 8, 2016–2020. [Google Scholar]
- Mamun, A.A.; Rahman, S.S.M.; Shaon, T.A.; Hossain, M. Security Analysis of AES and Enhancing its Security by Modifying S-Box with an Additional Byte. Int. J. Comput. Netw. Commun. 2017, 9, 69–88. [Google Scholar] [CrossRef]
- Singh, A. A New Approach to Enhance Avalanche Effect in Aes to Improve Computer Security. Inf. Technol. Softw. Eng. 2015, 5, 1–5. [Google Scholar] [CrossRef]
- Kamali, S.H.; Shakerian, R.; Hedayati, M.; Rahmani, M. A new modified version of Advanced Encryption Standard based algorithm for image encryption. In Proceedings of the 2010 International Conference on Electronics and Information Engineering, Kyoto, Japan, 1–3 August 2010. [Google Scholar]
| S/No | Rank Number (RNo) | No. of Byte Position to Shift (RNo-1) |
|---|---|---|
| 1 | 1 | 0 |
| 2 | 2 | 1 |
| 3 | 3 | 2 |
| 4 | 4 | 3 |
| S/No | RVals | Value (Hex) | Value (Dec) | RNos | State Row No |
|---|---|---|---|---|---|
| 1 | RVal0 | 3F | 63 | 1 | 0 |
| 2 | RVal1 | 9C | 156 | 3 | 1 |
| 3 | RVal2 | E0 | 224 | 4 | 2 |
| 4 | RVal3 | 6A | 106 | 2 | 3 |
| AES Name | Secret Key (Plain) | Secret Key (Hex) | Cipher Text (Hex) | Avalanche Effect |
|---|---|---|---|---|
| Conventional AES | dKro9Wahme#dHrn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 72 6E 37 | 83 4A A0 CB 25 78 FD FB 5D 14 24 BD 32 CD E0 00 | 0.5078125 (50.78123%) |
| dKro9Wahme#dHsn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 73 6E 37 | BB 87 74 9F 78 20 28 D8 40 1D DE 6C F7 41 3A E7 | ||
| Modified AES | dKro9Wahme#dHrn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 72 6E 37 | D6 BA 33 8A C3 61 3A 74 B5 FB EB A4 EA 97 B1 10 | 0.578125 (57.8125%) |
| dKro9Wahme#dHsn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 73 6E 37 | 5D 2D A4 39 11 04 95 C8 2E 17 D3 7F 5C 43 22 86 |
| AES Name | Secret Key | Plain Text | Plain Text (Hex) | Cipher Text (Hex) | Avalanche Effect |
|---|---|---|---|---|---|
| Conventional AES | dKro9Wahme#dHrn7 | I Love Unilorin! | 49 20 4C 6F 76 65 20 55 6E 69 6C 6F 72 69 6E 21 | 83 4A A0 CB 25 78 FD FB 5D 14 24 BD 32 CD E0 00 | 0.4921875 (49.21875%) |
| I Love Unimorin! | 49 20 4C 6F 76 65 20 55 6E 69 6D 6F 72 69 6E 21 | F2 96 36 B1 6A FA 68 D2 C4 4A DF 2D BA 64 CA A9 | |||
| Modified AES | I Love Unilorin! | 49 20 4C 6F 76 65 20 55 6E 69 6C 6F 72 69 6E 21 | D6 BA 33 8A C3 61 3A 74 B5 FB EB A4 EA 97 B1 10 | 0.5625 (56.25%) | |
| I Love Unimorin! | 49 20 4C 6F 76 65 20 55 6E 69 6D 6F 72 69 6E 21 | 6B CC 92 7D 1E C2 74 B4 E7 EB 7E 0A D1 CA 67 6F |
| AES Name | Secret Key (Plain) | Secret Key (Hex) | File Size | Avalanche Effect |
|---|---|---|---|---|
| Conventional AES | dKro9Wahme#dHrn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 72 6E 37 | 0.5 MB | 0.49973 (49.973%) |
| dKro9Wahme#dHsn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 73 6E 37 | |||
| Modified AES | dKro9Wahme#dHrn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 72 6E 37 | 0.5 MB | 0.563625 (56.3625%) |
| dKro9Wahme#dHsn7 | 64 4B 72 6F 39 57 61 68 6D 65 23 64 48 73 6E 37 |
| AES Name | Secret Key | File Size | Avalanche Effect |
|---|---|---|---|
| Conventional AES | dKro9Wahme#dHrn7 | 0.5 MB | 0.504715 (50.4715%) |
| Modified AES | dKro9Wahme#dHrn7 | 0.5 MB | 0.55735 (55.735%) |
| Plain Text Size | AES Name | Avrg. Encryption Time (ms) | Avrg. Decryption Time (ms) |
|---|---|---|---|
| 16 Byte | Conventional AES | 0.1215 | 0.1637 |
| Modified AES | 0.1658 | 0.1789 | |
| 32 Byte | Conventional AES | 0.2156 | 0.2232 |
| Modified AES | 0.2976 | 0.3114 | |
| 64 Byte | Conventional AES | 0.4154 | 0.3326 |
| Modified AES | 0.4564 | 0.4626 | |
| 128 Byte | Conventional AES | 0.4333 | 0.4076 |
| Modified AES | 0.6984 | 0.5911 | |
| 0.5 mb | Conventional AES | 1769.85 | 1684.17 |
| Modified AES | 2359.65 | 2269.32 |
| S/N | Author | Test Data | Execution Time | Difference (s) | |
|---|---|---|---|---|---|
| Conventional AES (s) | Modified AES (s) | ||||
| 1. | [11] | 256 × 256 image | 12.1760 | 11.4190 | 0.7570 |
| 2. | [16] | 16 bytes text file | 0.0113 | 0.2414 | −0.2301 |
| 3. | [24] | Three 256 × 256 coloured images | 86.5342 | 9.0000 | 77.5342 |
| 4. | [26] | 4.45MB image | 3.7390 | 3.6490 | 0.0900 |
| 5. | [27] | 128 × 128 image | 0.2330 | 0.0840 | 0.1490 |
| 6. | [28] | Image files | 41.4573 | 18.9419 | 22.5154 |
| 7. | [29] | 16 bytes text file | 1.9259 | 1.8749 | 0.0510 |
| 8. | [30] | Text File | 0.2467 | 0.2461 | 0.0006 |
| 9. | [31] | Text File | 0.6000 | 0.6010 | −0.0010 |
| 10. | [32] | Plain text | 6.2100 | 6.1700 | 0.0400 |
| 11. | [33] | 256 × 256 image of 192 KB | 6.4430 | 6.3490 | −0.0940 |
| Proposed Technique | 16 bytes text file | 0.0713 | 0.1723 | −0.1010 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abikoye, O.C.; Haruna, A.D.; Abubakar, A.; Akande, N.O.; Asani, E.O. Modified Advanced Encryption Standard Algorithm for Information Security. Symmetry 2019, 11, 1484. https://doi.org/10.3390/sym11121484
Abikoye OC, Haruna AD, Abubakar A, Akande NO, Asani EO. Modified Advanced Encryption Standard Algorithm for Information Security. Symmetry. 2019; 11(12):1484. https://doi.org/10.3390/sym11121484
Chicago/Turabian StyleAbikoye, Oluwakemi Christiana, Ahmad Dokoro Haruna, Abdullahi Abubakar, Noah Oluwatobi Akande, and Emmanuel Oluwatobi Asani. 2019. "Modified Advanced Encryption Standard Algorithm for Information Security" Symmetry 11, no. 12: 1484. https://doi.org/10.3390/sym11121484
APA StyleAbikoye, O. C., Haruna, A. D., Abubakar, A., Akande, N. O., & Asani, E. O. (2019). Modified Advanced Encryption Standard Algorithm for Information Security. Symmetry, 11(12), 1484. https://doi.org/10.3390/sym11121484






