Abstract
Health information systems (HISs) have immense value for healthcare institutions, as they provide secure storage, efficient retrieval, insightful analysis, seamless exchange, and collaborative sharing of patient health information. HISs are implemented to meet patient needs, as well as to ensure the security and privacy of medical data, including confidentiality, integrity, and availability, which are necessary to achieve high-quality healthcare services. This systematic literature review identifies various technologies and methods currently employed to enhance the security and privacy of medical data within HISs. Various technologies have been utilized to enhance the security and privacy of healthcare information, such as the IoT, blockchain, mobile health applications, cloud computing, and combined technologies. This study also identifies three key security aspects, namely, secure access control, data sharing, and data storage, and discusses the challenges faced in each aspect that must be enhanced to ensure the security and privacy of patient information in HISs.
1. Introduction
Described as comprehensive, technology-based systems, health information systems (HISs) are designed to manage and organize health data and information. These systems assist healthcare organizations in storing, retrieving, analyzing, and exchanging patient health information, thereby supporting clinical decision-making and enhancing patient care and outcomes. HISs typically include a range of software applications and tools for electronic health records (EHRs), health information exchange, clinical decision support (CDS), and administrative functions. These systems are versatile, being used in various settings such as hospitals, clinics, long-term care facilities, public health agencies, and even at home. HISs also play a pivotal role in enhancing data security and privacy, supporting compliance with regulations like the Health Insurance Portability and Accountability Act (HIPAA) [1].
The increase in digitalization of patient health information through electronic health records and personal health records has created new and serious threats to patient information security and privacy [2]. Medical data containing sensitive information about a patient’s health and personal life, including medical history, diagnoses, treatments, and personal identifying information, are vulnerable to breaches. Such breaches can lead to serious consequences, including identity theft, fraud, and medical malpractice [3]. The security of patient data encourages individuals to share their personal health information for current or future care [3]. Furthermore, if healthcare professionals cannot trust an organization to protect records, they may be reluctant to record all information collected from patients [4]. Therefore, it is essential that HISs are designed and implemented with privacy and security as core considerations [4]. This includes using secure technologies for storing and transmitting data, implementing access controls, and providing training to healthcare professionals on best practices for ensuring patient security and privacy. Moreover, ensuring the security and privacy of medical data, including confidentiality, integrity, and availability, is necessary to achieve high-quality healthcare services [3,4].
Table 1 provides an overview of the security and privacy technologies used in various HISs [3].

Table 1.
Overview of various health information systems.
Previous literature reviews have mainly focused on the use of a particular type of technology, such as blockchain and the Internet of Things (IoT) [5,6]. So far, most of these studies have not comprehensively explained and reviewed the various technologies for ensuring the privacy and security of medical data. Therefore, the literature review presented in this paper attempts to perform a comprehensive review to evaluate the security and privacy aspects of different technologies used in health information systems and to analyze their advantages, limitations, and future directions.
This literature review includes studies that utilize various technologies to enhance the security and privacy of healthcare information. These technologies can be analyzed from three security aspects, namely, secure access control, secure data sharing, and secure data storage. To address data security and privacy, these technologies provide different secure schemes, such as secure frameworks, secure authentication protocols, privacy-preserving infrastructures, data storage, and access control models [7,8].
In this literature review, four current technologies are evaluated, namely, mobile health applications, the IoT, blockchain, and cloud computing, along with other methods that employ a combination of technologies. It should be noted that mobile applications and the IoT are different because they serve different purposes and have various characteristics, such as distinct features and functionalities, different access points, diverse operating systems, and varied threats, including different security and privacy risks and required security countermeasures. For instance, mobile devices may require additional encryption or multi-factor authentication for access to sensitive health information, while IoT devices may require additional controls to ensure the privacy and security of the data they collect and transmit.
2. Background
Security in the context of medical data and health information refers to the protection of sensitive patient information from unauthorized access, use, or disclosure. It encompasses various measures to safeguard the confidentiality, integrity, and availability of health data [9]. Privacy, on the other hand, is a specific aspect of security that focuses on enforcing rules regarding how private information is stored and shared. Medical data privacy is important because it ensures that patients have control over who can access their health information and how it is used. This helps to maintain confidentiality and prevent the unauthorized use or disclosure of medical data, which can lead to identity theft, discrimination, and other negative consequences [9].
Therefore, attempts to create policies and regulations have been developed in various countries. For example, the Health Insurance Portability and Accountability Act (HIPAA) of 1996 consists of federal laws that protect the privacy and security of health information in the U.S. These rules ensure that individuals have rights over their health information, and they require specific protections to safeguard electronic health information [10]. All companies operating in the healthcare industry in the U.S. must comply with HIPAA regulations. This includes healthcare providers, health plans, healthcare clearinghouses, and their business associates. The HIPAA provides a comprehensive set of guidelines for ensuring the privacy and security of health information [3]. The key guidelines comprise a security rule, privacy rule, breach notification rule, and enforcement rule. The security rule outlines the security standards to protect electronic protected health information (ePHI). It includes administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI. The privacy rule establishes national standards for protecting individuals’ medical records and other personal health information. It governs the use and disclosure of PHI and grants a patient their rights over their own health information. In the event of a breach involving unsecured PHI, entities that comply with the HIPAA are required to notify affected individuals, the Secretary of Health and Human Services, and, in some cases, the media. Enforcement rules outline procedures for investigating complaints and the penalties for non-compliance with HIPAA regulations [3,11].
Accordingly, the privacy and security of HISs are crucial to ensure the confidentiality of a patient’s personal information and to prevent potential security breaches that may compromise the integrity of the data. Additionally, access control tools and extensive training are essential for securing patient information and protecting confidentiality [10]. The organization and implementation of security and privacy in HISs can vary significantly depending on the country and the type of provider or user. This variation is primarily due to differences in legal frameworks, cultural attitudes toward privacy, technological infrastructure, and the specific needs of healthcare providers and users. For example, the European Union’s General Data Protection Regulation (GDPR) is one of the most comprehensive and stringent privacy laws, impacting how companies worldwide handle the data of EU citizens [12]. In contrast, the United States has a more sector-specific approach, with laws like the HIPAA for healthcare data and the Children’s Online Privacy Protection Act (COPPA) for protecting data for children. On the other hand, Australia’s approach to health information privacy is outlined in the Privacy Act 1988, which includes the Australian Privacy Principles (APPs) [12]. These principles cover a broader spectrum of personal information compared to the U.S.’s HIPAA and apply to a wider range of entities, including all private health service providers [12].
In the context of HISs, approval and control of whether rules, requirements, and guidelines are followed, including the conducting of audits and inspections, are overseen by various regulatory bodies and government agencies. For instance, the HIPAA sets standards for the storage, sharing, and management of health information, and the Office of the Inspector General is involved in enforcing compliance through audits and investigations [13]. Furthermore, validation of HISs increasingly includes aspects of security and privacy. This is essential given the sensitive nature of health data and the evolving cybersecurity threat landscape. Modern validation methodologies for e-health systems focus on ensuring that security and privacy policies are effectively integrated and compliant with relevant regulations and standards. These methodologies typically involve a combination of technological advancements, adherence to legal frameworks, and the application of best practices in data security and privacy management. The goal is to ensure the confidentiality, integrity, and availability of health data throughout its lifecycle, from collection to storage and processing. The validation process often includes rigorous testing and assessment of security measures, privacy protocols, and compliance with laws like the HIPAA in the U.S. or the GDPR in the EU. This approach is crucial to safeguarding patient data against unauthorized access, breaches, and other security incidents [13].
In the landscape of Health Information Systems (HISs), regulatory bodies such as the U.S. Food and Drug Administration (FDA) and the European Medicines Agency (EMA) play pivotal roles. These organizations are fundamental in establishing and enforcing standards that ensure the safety, efficacy, and privacy of health technologies. The FDA, in the United States, oversees the regulation of medical devices, which include software and hardware used in HISs. It sets forth guidelines that dictate how these technologies should be developed, tested, and implemented to protect patient data and ensure system integrity. Similarly, the EMA in the European Union performs an analogous function, focusing on the evaluation and supervision of medicinal products, thereby extending its influence to the technologies employed in healthcare settings across Europe [14].
These regulatory bodies also have a significant impact on how HIS technologies evolve and are adopted in healthcare practices. By setting stringent requirements for compliance, they influence the design and functionality of HIS technologies, prioritizing patient data security and privacy. Compliance with these regulations is not just a legal obligation but also a critical factor in gaining trust and acceptance among healthcare providers and patients. While these agencies primarily aim to protect public health, their guidelines also spur innovation, as developers and providers strive to create solutions that meet these rigorous standards without compromising on efficiency and user experience. Thus, the function and position of the FDA, EMA, and similar regulatory bodies are integral to the development and deployment of secure and privacy-compliant HIS technologies [14].
3. Materials and Methods
This systematic literature review followed the PRISMA guidelines [15], using an explicit and systematic search strategy and established inclusion and exclusion criteria. The search was conducted on five databases (Scopus, Web of Science, PubMed, Medline, and IEEE) to collect articles about the privacy and security of health information systems. During the querying phase, specific keywords were used to search for relevant articles. The search string used was (“medical date” OR “patient data” OR “health data”) AND (“privacy” OR “security” OR “data security”) AND (“health information systems” OR “information technology” OR “digital health” OR “health informatics”) with additional constraints: i.e., journal articles only, articles published in English, and articles published from 2002 to 2022.
As shown in Table 2, the search returned 1273 articles. All retrieved articles were imported to EndNote X20. At this stage, 559 duplicate references were removed, which left 714 papers for the initial screening process. During the initial screening stage, the titles and abstracts of all 714 research papers were assessed.

Table 2.
Study selection process.
The research team developed a set of criteria to determine article eligibility for this review. The primary inclusion criteria for this research are the following: (1) articles describing the privacy and security of medical data in health information systems and (2) articles about secure technologies or solutions for storing and exchanging medical data. Additionally, (1) literature reviews, (2) articles that provide general information or generic reports related to medical data without describing solutions or methods for ensuring the privacy of medical data, and (3) articles that published their methodology or design for studies that have not been completed yet were excluded.
From the data in Table 2, based on the inclusion and exclusion criteria, a further 514 articles were removed, leaving 116 articles for full-text review. After filtering and selection, 36 studies were included in this review. Figure 1 summarizes the inclusion and exclusion criteria and the steps of the proposed search using the PRISMA flow diagram.
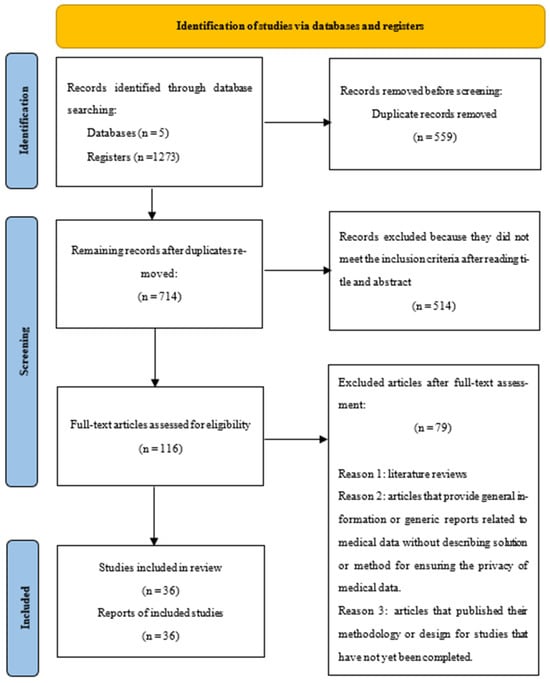
Figure 1.
PRISMA flow diagram of how the systematic literature review was conducted. The diagram is divided into three phases: identification, screening, and inclusion.
4. Results
Each article was assessed based on whether it identified and evaluated existing approaches used to enhance data privacy and security in HISs. This resulted in a total of 36 relevant articles being selected for this systematic review.
As shown in Table 3, the technologies used in HISs include mobile applications, the IoT, blockchain, cloud computing, and other technologies. Furthermore, the articles reviewed revealed three key security aspects, namely, secure access control, secure data sharing, and data storage. Table 4 provides the main characteristics of the studies included in this review, focusing on approaches used to enhance the security and privacy of medical data.

Table 3.
Technologies used in the included studies.

Table 4.
Characteristics of the studies included in this review.
4.1. Mobile Health Application
Mobile devices play an important role in the management of medical data in health information science. However, organizations must ensure that appropriate security and privacy measures are in place to protect sensitive information from unauthorized access or theft. These privacy and security measures align with the proposals of Ref. [7], who suggest threat modelling to identify potential threats and possible mitigations. By integrating security policies, defining sensitivity levels of form fields, and corresponding security mechanisms, data security can be catered to as early as the design phase. In addition, articles [8,16,17,18] implement secure models to strengthen the privacy and security of medical data within mHealth applications. These models aim to protect sensitive health information throughout its lifecycle, from collection and transmission to storage and access. For instance, Ref. [16] suggests a lightweight security framework for securing mHealth data collection systems, relying on lightweight and low-cost mechanisms to secure data exchanged with servers. These findings emphasize the importance of implementing strong encryption techniques for both data in transit and data at rest. This includes encrypting communication channels between devices and servers, as well as storing medical data on mobile devices and in the cloud [8]. For example, Ref. [8] proposes a scheme called an Efficient and Provable Secure Certificate-Based Combined Signature, Encryption, and Signcryption (CBCSES) scheme. This scheme not only provides encryption and signcryption but also offers an encryption or signature model when needed.
Moreover, mHealth applications can be designed using a secure framework for data collection, minimizing the risk of unauthorized access or theft of information. This contributes to securing the data exchanged with the server and includes key features such as tolerance to delays and lack of connectivity [7,16]. A previous study identified the need to use secure cloud storage for storing data, which can provide additional backup and security measures [17]. The system proposed in [17] offers salient features including efficient key management, privacy-preserving data storage and retrieval—particularly effective in emergency situations—and auditability to prevent misuse of health data. Furthermore, an approach presented in [18] utilized privacy-aware anomaly detection methods. These prioritize the security of health data by identifying abnormal patterns and ensuring the privacy of individual users, thus helping to maintain the confidentiality and integrity of sensitive health information [18].
4.2. IoT
The Internet of Things (IoT) has the potential to transform healthcare by enabling data collection and exchange from various devices and sensors. IoT devices feature built-in security measures, including encryption and authentication, to protect data in transit and storage while ensuring access is restricted to authorized parties [28].
IoT devices can store and organize medical data, simplifying access and analysis for healthcare professionals [19]. A new shared, agnostic, and permissioned decentralized data layer enhances data availability. This architecture has been implemented in a real-world Internet of Medical Things (IoMT) application [19], effectively handling sensitive data by preserving privacy and ensuring data availability without third-party reliance. Additionally, the IoT enhances data security and privacy through encryption, robust authentication, and access control, ensuring that sensitive health data are accessible only to authorized parties, thereby making unauthorized access more challenging [20,21,22,23,24].
It is important to note that IoT applications in healthcare offer cost reduction and efficiency benefits. These applications streamline operations, minimize errors and waste, and reduce system costs [21]. The focus in [21] was on avoiding the key escrow problem and establishing a new session key between servers and personal digital assistants (PDAs) for future communication, enhancing cost-effectiveness, and security against various attacks. Remote monitoring contributes to shorter hospital stays and fewer readmissions, improving treatment outcomes and reducing healthcare costs [21,25]. Furthermore, Ref. [25] discusses using an edge server to compute data authenticators to verify data integrity, significantly reducing computational costs and the management burden on third-party verifiers.
4.3. Blockchain
Extensive research has established that blockchain technology offers a secure, transparent, and tamper-proof method for storing and sharing medical data, which is crucial for maintaining patient privacy and security within HISs. Operating on a decentralized network, blockchain technology lacks a central authority controlling the data. This approach mitigates the risk of a single point of failure or a single entity accessing sensitive information, addressing potential security issues inherent in centralized storage systems [28]. Additionally, Ref. [28] discovered that blockchain technology can overcome challenges related to interoperability, security, confidentiality, privacy protection, and secure storage. Similarly, Ref. [27] integrated two decentralized technologies, the Solid ecosystem and blockchain, using solidity-based smart contracts to resolve security issues, thereby providing a secure, patient-centric design for complex, developing electronic health record (EHR) data exchange.
Blockchain technology can also create secure private networks for sharing sensitive medical data (transferred and distributed) exclusively among authorized parties [33,49]. For example, Ref. [33] proposes a permissioned blockchain-based system for EHR data sharing and integration, employing public key infrastructure-based asymmetric encryption and digital signatures to secure EHR data. This system ensures patient privacy protection and adheres to healthcare data management requirements, including the access control policy specified by the patient. Similarly, Ref. [32] introduced a privacy-preserving medical data-sharing scheme that balances the need for privacy with the necessity of data sharing. This perspective aligns with Ref. [49], who utilized a blockchain-based secure data sharing mechanism for the safe uploading and sharing of health data. The study by Ref. [31] developed a blockchain-based system with a secure data storage architecture to tackle cybersecurity storage challenges, employing private data collection to ensure privacy and decentralizing nodes in the network to prevent storage complications. This method also addresses other security challenges typically associated with centralized systems. Furthermore, blockchain technology enables the creation of smart contracts that automate data sharing under predefined conditions, ensuring that data are only shared with authorized parties. In line with this, Ref. [30] developed an access control framework based on smart contracts, which is built on a distributed ledger (blockchain), to secure the sharing of electronic medical records among various entities in the smart healthcare system.
In the context of blockchain applications in HISs, patient autonomy is a central theme, allowing individuals to have ownership and control over their personal health data. This empowerment is crucial, yet it poses challenges, particularly when patients are cognitively impaired or unable to manage their data. In such cases, the use of advanced directives or legally authorized representatives could be integrated into blockchain systems to ensure responsible data management [26]. Moreover, blockchain’s decentralized nature and cryptographic techniques provide robust security for health data [27]. However, challenges arise in maintaining consistent permissions, especially in emergency situations where swift access to patient data is crucial. Smart contracts and cryptographic keys within blockchain networks can be employed to manage permissions seamlessly, ensuring healthcare professionals have necessary access while maintaining patient privacy and data integrity [30].
Furthermore, the legal implications of using blockchain in HISs under different jurisdictions, such as the potential access by the U.S. government to cloud-stored data under U.S. law, raise significant privacy concerns. While blockchain offers many benefits for healthcare data security, its integration into existing healthcare systems must be approached with caution, ensuring adherence to regulations like the HIPAA and addressing potential privacy issues related to decentralized data storage. This necessitates a careful balance between technological innovation and compliance with legal and regulatory standards.
4.4. Cloud Computing
Cloud computing offers multiple advantages for ensuring the security and privacy of medical data in HISs. By adopting cloud-based solutions, healthcare organizations benefit from strong security controls, encryption, access controls, redundancy, and compliance certifications, all aimed at safeguarding patient data. The findings of this review indicate that cloud computing providers can implement robust access control mechanisms. These include multi-factor authentication and role-based access control, ensuring that only authorized personnel can access sensitive medical data, thereby enhancing security measures [36,38].
Moreover, cloud computing can be more cost-effective compared to maintaining an on-premises IT infrastructure. This efficiency comes from eliminating the need for expensive hardware and software, allowing healthcare organizations to reduce costs and improve their overall financial performance [36]. Cloud computing also guarantees data recovery following a disaster, further bolstering data security and privacy [17,37]. For instance, a study by Ref. [37] describes a secure encryption algorithm (SE) combined with fragmentation and dispersion for storage. This method is designed to protect data even if both the key and the public fragment of EHR data on clouds are compromised. This aligns with other research demonstrating that storing EHR in the cloud significantly enhances security and protects patient information from unauthorized access [50].
4.5. Other Technologies
In addition to the technologies mentioned earlier, several studies have examined methods that employ a variety of technologies to enhance the security and privacy of medical data. Table 5 presents an overview of these technologies.

Table 5.
Overview of other technologies used in HISs.
The study by Ref. [48] developed a hybrid security solution using the Spring Framework, services for sensitive data (TSD) as a service platform, and Hypertext Transfer Protocol (HTTP) security methods. This solution provides secure hosting and operation of application services, as well as the collection, storage, processing, and provisioning of data. The results demonstrate that the adopted digital solution effectively protects APIs and personal health data. Another study by Ref. [41] presents a new hash-based BBS (HBBS) pseudo-random bit generator to ensure the integrity and security of data, making it suitable for smart health applications and telemedicine. This study also proposes an encryption technique aimed at achieving robust security during the transmission of medical data. Furthermore, Ref. [44] introduces a secure and lightweight approach using fewer elliptic curve cryptography (ECC) operations and a physically unclonable function (PUF), improving security and efficiency with lower computational and communication costs. The study by Ref. [45] proposes a privacy-preserving encryption approach that incorporates an innovative data collection protocol. This method involves dividing patient data into three parts and storing them across three data servers to maintain privacy.
Additionally, Ref. [46] designed several secure and privacy-preserving subprotocols to ensure privacy in an e-healthcare system, adopting a secure greedy algorithm for query performance and min-heap technology to enhance efficiency. The method in [47] offers an architecture that improves the reliability of data exchange between healthcare personnel by providing a security layer that supports accountability through context-aware services, enabling appropriate data access for users. Ref. [40] proposes a secure method for preserving privacy in healthcare data, specifically for disease prediction in modern healthcare systems. This system uses cryptography during data transfer and allows authorized healthcare staff to securely access patient data for disease prediction using a herding genetic algorithm-based deep learning neural network. Ref. [43] suggests a secure, expressive, and efficient access control scheme with immediate attribute/user revocation in collaborative e-health systems, based on the ordered binary decision diagram (OBDD) access structure. It binds user keys to user identities, therefore creating resistance to collusion attacks. Additionally, Ref. [39] highlights a model based on a multi-agent system comprising various intelligent agents such as a user interface agent, authentication agent, connection establishment agent, and connection management agent. This model provides effective and secure e-health security services, facilitating ease of use and effective communication between users and e-service providers.
Various studies have demonstrated the relationship between secure solutions for storing and sharing sensitive health information and ensuring the security and privacy of data in HISs. For instance, Ref. [42] proposed a secure scheme using a decentralized federated learning-based convolutional neural network, private and public interplanetary file systems (IPFS), a consortium blockchain network, and smart contracts. This scheme is ideal for promoting a secure and privacy-friendly environment for data sharing. In a study by Ref. [49], a framework for 5G-secure smart healthcare monitoring (5GSS) was employed for fast and accurate identification of context-aware health situations, along with a blockchain-based secure data sharing mechanism and low-latency services for emergent patients.
5. Discussion
In this systematic literature review, the articles on data privacy and security for HISs that were reviewed focused on various technologies, such as the IoT, blockchain, mHealth applications, and cloud computing. This section first discusses the challenges and future directions of these technologies in relation to HISs. From this, three fundamentally distinct security aspects could be identified, namely, secure access control, data sharing, and data storage within HISs. These aspects will be discussed in the subsequent subsections.
5.1. Challenges and Future Directions of the Technologies Used in HISs
5.1.1. Mobile Health Applications
In the realm of mHealth applications, the privacy and security of medical data can be significantly enhanced through the use of robust encryption techniques. These techniques are crucial in preventing unauthorized access and are resistant to various attacks. Consequently, even if unauthorized individuals gain access to the data, it remains indecipherable without the appropriate decryption keys [7]. These findings are in line with those reported in [51], which also emphasized the need for efficient measures to mitigate privacy and security risks in mHealth. This highlights the significance of encryption in safeguarding data against breaches.
A challenge identified in this review is the lack of adequate backup mechanisms in many mHealth applications. Some applications do not have sufficient data backup and recovery systems, which poses a challenge in restoring data following a security breach or other data loss events. The article by Ref. [52] underscores the essential need for comprehensive data backup and recovery mechanisms in mHealth applications and points out the potential vulnerabilities in many current applications. This concern is echoed in [53].
Therefore, the development of a framework for ensuring the privacy and security of data in mHealth applications should encompass strategies aimed at minimizing risks. Such strategies include employing strong encryption techniques to prevent unauthorized access, implementing comprehensive data backup and recovery mechanisms, ensuring secure storage, and maintaining clarity and ease of use for the end-user.
5.1.2. IoT
Many IoT devices used in healthcare are not designed with security as a primary concern, and often feature weak password mechanisms or other vulnerabilities that are susceptible to exploitation by attackers [54]. Additionally, these devices and systems frequently collect and transmit substantial amounts of personal and medical data, presenting risks of unauthorized access, use, or disclosure [21,25]. This concern aligns with the findings of Ref. [55], that underscore the necessity of a secure and resilient operating environment for critical IoT systems in healthcare to mitigate potential threats. Consequently, addressing these security vulnerabilities is imperative for the healthcare sector to ensure patient safety and system integrity [56].
To bridge these gaps and overcome limitations, the healthcare sector should adopt appropriate technical and organizational measures for data protection, implement effective authentication mechanisms, and deploy security protocols alongside privacy-preserving solutions for tracking, monitoring, and analytics. Furthermore, research that focuses on designing IoT devices with standardized protocols to address the interoperability and standardization challenges in IoT and healthcare systems is essential [57].
5.1.3. Blockchain
Besides the significant benefits of using blockchain technology to control access to sensitive medical information [58], achieving complete data privacy and confidentiality in healthcare systems remains a considerable challenge that must be addressed effectively [49]. These findings align with Ref. [59], who suggests that blockchain-based health systems must establish robust mechanisms to protect patient data and ensure privacy. Other concerns include the scalability of blockchain technology and the management of shared healthcare records, which can affect their capacity to ensure the security and privacy of health information [60]. Additionally, the processing speed and capacity of blockchain systems may not be sufficient for the demands of real-time healthcare data management [32], which is a concern that was also raised in other studies [61,62].
Considering this, further research and development focusing on enhancing the scalability and performance of blockchain networks, strengthening measures for data privacy and confidentiality, addressing interoperability challenges, and considering the societal and security implications of blockchain-based health systems, is required.
5.1.4. Cloud Computing
One of the findings of this review is the security concerns associated with cloud computing. Cloud computing systems are vulnerable to hacking and data breaches, potentially exposing sensitive medical information to unauthorized parties [35]. This concern aligns with findings from Ref. [63], who indicate that healthcare organizations are hesitant to adopt cloud computing due to concerns over patient information confidentiality, privacy, and service costs. Ensuring the security of patient data and compliance with regulations such as the HIPAA and GDPR remain a significant challenge in cloud-based HISs [64].
The potential exposure of sensitive health information and the need for robust backup and disaster recovery mechanisms are significant areas of concern for healthcare organizations [63]. Medical institutions may have limited control over the security and privacy of their data when utilizing cloud computing systems, and they often depend on the security measures implemented by the cloud provider [17,37]. This finding is consistent with [64], highlighting the challenges in maintaining control over data, which also encompasses issues related to data interception and ownership in cloud computing.
Based on this analysis, while cloud computing offers numerous benefits for healthcare, such as improved collaboration, cost savings, and scalability, it also presents critical limitations and challenges. Overcoming security concerns, ensuring data privacy and confidentiality, and addressing the reluctance to adopt cloud technology are essential for the successful implementation of cloud computing in healthcare. These are crucial issues for future research. Furthermore, data protection methods should be designed to suit real-world clinical settings [37].
5.2. Secure Access Control
Numerous articles have emphasized the importance of secure access control as a vital component of HISs, regardless of the technology used. This is essential to ensuring the privacy and security of sensitive patient data. Secure access control is instrumental in preventing data breaches by regulating access to sensitive patient data. This approach effectively reduces the risk of data theft, cyberattacks, and other security threats [21,30,35,39,41,43]. Moreover, it ensures that only authorized individuals can access sensitive patient information, thereby protecting patient privacy and preventing unauthorized access to information that can be exploited for malicious purposes [23,38,39,40,44]. Implementing secure access controls is crucial in preventing data breaches, which can be both costly and damaging to healthcare organizations. By restricting access to sensitive data, the likelihood of data breaches can significantly be minimized. Most studies suggest that secure access control not only reduces communication and computational costs but also enhances security [21,30,35]. From an efficiency standpoint, some articles highlight that certain systems are effective for real-time healthcare systems [30,35,44], while others suggest that certain models, particularly those based on agent-based systems, provide effective and secure e-health security services [39].
This study has identified secure access control as being critical for ensuring the privacy and security of medical data. However, several challenges exist in implementing secure access control in HISs. HISs typically involve multiple levels of access control, including user authentication, authorization, and audit logging. Managing and configuring these controls can be complex, with a risk of misconfiguration or loopholes that can lead to security breaches. Additionally, HISs are often intricate and may involve various systems handling large volumes of data and users. Consequently, integrating different systems and ensuring that they all have the necessary access controls is challenging. Furthermore, there are numerous regulations and standards, such as the HIPAA, HITECH, and GDPR, which must be adhered to in the healthcare industry [10].
When integrating blockchain and cloud computing to facilitate decentralized access control, healthcare organizations must adopt a comprehensive and proactive strategy for securing access to HISs. This strategy may include implementing multi-factor authentication, encryption, and user training and awareness programs, along with conducting regular security audits and assessments. Furthermore, healthcare organizations should stay informed about the latest security best practices and emerging threats, adjusting their access controls as necessary.
According to the literature, several limitations are associated with providing secure access control. Technical limitations pertain to the technical infrastructure of HISs, such as vulnerabilities in software or hardware, potentially compromising system security and permitting unauthorized access to sensitive data. Human factors also pose a threat, as employees might intentionally or unintentionally misuse sensitive patient data, leading to data breaches or other security incidents.
Addressing the identified weaknesses in secure access control of HISs requires a multifaceted approach to effectively enhance security and protect sensitive patient data. A key strategy is the strengthening of the technical infrastructure. This involves regular updates and patches to both software and hardware components of HISs, which help fix vulnerabilities and enhance a system’s overall security. Another crucial aspect is the enhancement of employee training and awareness. Implementing comprehensive training programs focused on data security and privacy practices increases employees’ awareness of potential risks. This education is vital for reducing the likelihood of data breaches resulting from human error or misuse. Further fortification of HIS security includes implementing advanced authentication mechanisms, such as multi-factor authentication. This significant step, coupled with regular audits of access, will ensures that only authorized personnel access sensitive patient data, thereby minimizing the risk of unauthorized breaches. Additionally, conducting regular system audits and security assessments is indispensable. These periodic reviews assist in identifying and mitigating potential threats to HISs. Continuous monitoring and assessment of the security landscape allow proactive addressing of potential vulnerabilities. By focusing on these critical areas—upgrading technical infrastructure, enhancing employee awareness and training, implementing robust authentication processes, and conducting regular security audits—the security of HISs can significantly be improved. This comprehensive approach reduces the likelihood of unauthorized access and strengthens the protection of patient data.
5.3. Secure Data Sharing
Another aspect of security discussed in the literature is the facilitation of secure data sharing in HISs. One method for achieving secure data sharing involves utilizing decentralized solutions [19,29,32,33,34]. Implementing lightweight and cost-effective mechanisms can enhance efficiency by minimizing time and resource consumption, thereby reducing expenses for healthcare organizations [24,29,46]. Other approaches offer secure data sharing by enabling a centralized system, which is simpler to monitor and secure compared to multiple disparate systems [16,17,20,21,33,35]. Studies, such as [33], demonstrate that secure and trustworthy data sharing empowers patients to manage their own data, including having complete control over sharing permissions. Furthermore, Ref. [37] introduces a data sharing system from a user-centric perspective, which not only improves medical treatment but also safeguards individual safety and privacy.
Based on analysis, achieving secure data sharing in HISs is a complex and ongoing process that demands constant vigilance. However, implementing robust authentication and authorization mechanisms is challenging, particularly in large healthcare organizations with multiple systems and databases. A further challenge arises from the fact that HISs often operate across various technologies and standards, complicating data exchange and potentially leading to incomplete patient records, thus hindering secure information sharing. One significant challenge for healthcare organizations is to prevent data breaches, which can lead to the theft or exposure of sensitive patient data. Protective measures may include firewalls, intrusion detection systems, and other security protocols. Additionally, HIS staff must be thoroughly trained and made aware of the importance of data privacy and security. They should understand the risks associated with data breaches and be educated on prevention strategies.
Previous studies on secure data sharing in HISs highlight its essential role in enhancing patient care but also point out several limitations that must be addressed. A primary limitation is the lack of interoperability, which hampers data sharing across different systems. This can create barriers to secure health information sharing, leading to incomplete patient records, especially when patients receive care from multiple providers or organizations. Another critical limitation is the vulnerability of HISs to cybersecurity attacks and technical failures due to their complex technical infrastructure. These incidents can compromise the confidentiality, integrity, and availability of sensitive health information. Furthermore, regulatory and legal barriers can prevent data sharing between different healthcare providers and organizations, limiting the benefits of data sharing in healthcare outcomes. Technical constraints also pose significant challenges to secure data sharing. Some HISs may lack the capacity for large-scale data sharing or the necessary security features to safeguard data during transmission. Additionally, most schemes for secure data sharing are not designed with real-world clinical settings in mind. Finally, the lack of standardization in HISs can impede the accuracy and consistency of shared data, further complicating the secure sharing process.
In response to the challenges encountered in secure data exchange within HISs, several principal recommendations have been identified as best practices. First, there is an increasing agreement on the need to enhance interoperability. This involves developing and adopting standardized protocols and formats, which are essential for enabling smooth data transfer across various HIS platforms. Equally critical is the strengthening of cybersecurity measures. To protect HISs against cyber threats and technical mishaps, the implementation of advanced security protocols is crucial. In conjunction, regular security audits and system updates are necessary to ensure robust defenses against potential cyberattacks. Another key aspect is addressing the regulatory and legal barriers that impede efficient data sharing. A coordinated effort to harmonize regulations can facilitate data exchange across different jurisdictions while ensuring secure and compliant operations. Improving the technical infrastructure of HISs is also a priority. This includes upgrading systems to not only support large-scale data sharing but also to integrate enhanced security features for data protection. These upgrades are necessary to meet the growing demands and complexities of modern healthcare data management. Additionally, the design of secure data sharing systems should consider the practical needs and workflows of real-world clinical settings. Customizing these systems to integrate seamlessly into the daily operations of healthcare providers is essential for their effective adoption and use. Finally, the standardization of data is vital. Promoting and implementing uniform standards in data recording and sharing is crucial to ensuring accuracy and consistency across different systems. This uniformity is key to improving the quality of patient care while maintaining the integrity and privacy of health data.
5.4. Secure Data Storage
Various studies have discussed the importance of secure data storage in HISs for ensuring data privacy and security. An analysis of these studies reveals that implementing secure data storage can be cost-effective in the long run, as it reduces the risk of costly data breaches for healthcare organizations [8,25]. Another significant finding is that utilizing decentralized solutions helps address potential security issues through solidity-based smart contracts [26,31,36]. It is also noted that secure data storage ensures patient data confidentiality, allowing only authorized personnel access [7,18,41,45,48]. This practice helps prevent data breaches and unauthorized access to sensitive health information [20,28,31]. As indicated in the literature, secure data storage builds trust between patients and healthcare providers. Patients are more inclined to trust providers who take their data’s security and privacy seriously, potentially leading to better patient outcomes and higher satisfaction [17,22]. Additionally, secure data storage maintains the integrity of patient data by preventing tampering or alteration, ensuring data accuracy and reliability, which is critical for making important medical decisions [65]. Overall, secure data storage is essential for maintaining patient data privacy and security, and healthcare organizations that prioritize it can benefit from improved compliance, reduced costs, and increased trust.
In general, secure data storage in HISs requires a comprehensive approach that addresses key challenges to ensure the confidentiality, integrity, and availability of patient data. This involves implementing stringent user authentication and authorization protocols, ensuring that storage data are accessed only by authorized personnel. Furthermore, employing a multi-layered security approach that includes firewalls, encryption, and intrusion detection systems can further strengthen data storage security against a wide array of cyber threats. Maintaining the accuracy and completeness of patient data is critical for effective patient care and medical decision-making, so utilizing reliable protocols for data verification and validation can support data integrity. Additionally, implementing data backup and recovery mechanisms can help mitigate the risk of data loss. Addressing these recommendations will significantly improve the security and reliability of data storage within HISs.
These improvements are not only beneficial for the protection of data but also play a pivotal role in enhancing the overall quality of patient care.
6. Limitations
The literature review presented here has a few limitations. Initially, only papers published in English were included, thereby excluding articles reported in other languages. Furthermore, the review was restricted to journal articles to ensure its quality. Consequently, other types of publications, such as conference papers, books, white papers, and organizational reports, were not considered. This exclusion may have resulted in missing additional insights that could have been valuable for this review. Therefore, it is possible that some security issues not mentioned in the selected articles were overlooked.
7. Conclusions
This study systematically reviews the literature on health information systems (HISs) in relation to medical data privacy and security. It contributes to existing research by identifying various related technologies and addressing security and privacy aspects. This study highlights the necessity for a secure HIS that not only meets organizational objectives but also ensures the protection of patient data. HISs offer significant benefits to healthcare organizations in terms of storing, retrieving, analyzing, exchanging, and sharing patient health information. These systems must both serve the needs of patients and health practitioners, while safeguarding the security and privacy of medical data. Therefore, HISs must be designed and implemented with privacy and security as primary considerations. This involves employing secure technologies for data storage and sharing, enforcing access controls to restrict data viewing or modification, and educating healthcare professionals on best practices for patient data privacy and security.
In conclusion, this review has explored the significant advancements and challenges in the realm of health information systems (HISs), focusing on key technologies such as blockchain, mobile health applications, cloud computing, and secure data sharing and storage. As we look toward the future of HISs, it is important to consider the evolving landscape of health data management frameworks. In this context, openEHR emerges as a noteworthy framework. While not the primary focus of this review, openEHR’s approach to standardized data models and archetypes for electronic health records presents potential synergies with the technologies discussed. Its emphasis on interoperability, security, and patient-centered data management aligns with the broader objectives of enhancing HISs. Future research could beneficially explore the integration of openEHR with current technologies to address the evolving needs of healthcare systems, ensuring a comprehensive and secure approach to managing health information. The continuous evolution of HISs requires adaptable and forward-thinking solutions, and openEHR represents a key area for future exploration and development in this field.
Author Contributions
Conceptualization, methodology, analysis P.S., E.V.-G. and Y.-W.C.; formal analysis, P.S.; investigation, P.S.; writing—original draft preparation, P.S.; writing—review and editing, E.V.-G. and Y.-W.C.; supervision, E.V.-G. and Y.-W.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Yusof, M.M.; Papazafeiropoulou, A.; Paul, R.J.; Stergioulas, L.K. Investigating Evaluation Frameworks for Health Information Systems. Int. J. Med. Inform. 2008, 77, 377–385. [Google Scholar] [CrossRef] [PubMed]
- Vora, J.; Italiya, P.; Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M.S.; Hsiao, K.F. Ensuring Privacy and Security in E-Health Records. In Proceedings of the International Conference on Computer, Information and Telecommunication Systems (CITS), Colmar, France, 11–13 July 2018. [Google Scholar]
- Mbonihankuye, S.; Nkunzimana, A.; Ndagijimana, A. Healthcare Data Security Technology: HIPAA Compliance. Wirel. Commun. Mob. Comput. 2019, 2019, 1927495. [Google Scholar] [CrossRef]
- Qayyum, A.; Qadir, J.; Bilal, M.; Al-Fuqaha, A. Secure and Robust Machine Learning for Healthcare: A Survey. IEEE Rev. Biomed. Eng. 2020, 14, 156–180. [Google Scholar] [CrossRef] [PubMed]
- Agbo, C.C.; QMahmoud, H.; Eklund, J.M. Blockchain Technology in Healthcare: A Systematic Review. Healthcare 2019, 7, 56. [Google Scholar] [CrossRef] [PubMed]
- Mohamad Jawad, H.H.; Bin Hassan, Z.; Zaidan, B.B.; Mohammed Jawad, F.H.; Mohamed Jawad, D.H.; Alredany, W.H.D. A Systematic Literature Review of Enabling IoT in Healthcare: Motivations, Challenges, and Recommendations. Electronics 2022, 11, 3223. [Google Scholar] [CrossRef]
- Katarahweire, M.; Bainomugisha, E.; Mughal, K.A.; Ngubiri, J. Form-based security in mobile health data collection systems. Secur. Priv. 2021, 4, e155. [Google Scholar] [CrossRef]
- Ullah, I.; Amin, N.U.; Khan, M.A.; Khattak, H.; Kumari, S. An Efficient and Provable Secure Certificate-Based Combined Signature, Encryption and Signcryption Scheme for Internet of Things (IoT) in Mobile Health (M-Health) System. J. Med. Syst. 2020, 45, 4. [Google Scholar] [CrossRef]
- Keshta, I.; Odeh, A. Security and privacy of electronic health records: Concerns and challenges. Egypt. Inform. J. 2021, 22, 177–183. [Google Scholar] [CrossRef]
- Harman, L.B.; Flite, C.A.; Bond, K. Electronic Health Records: Privacy, Confidentiality, and Security. Am. Med. Assoc. J. Ethics 2012, 14, 712–719. [Google Scholar]
- Basil, N.N.; Solomon, A.; Chukwuyem, E.; Ekokobe, F. Health Records Database and Inherent Security Concerns: A Review of the Literature. Cureus 2022, 14, e30168. [Google Scholar] [CrossRef]
- Fathima Shah, W. Preserving Privacy and Security: A Comparative Study of Health Data Regulations—GDPR vs. HIPAA. Int. J. Res. Appl. Sci. Eng. Technol. 2023, 11. [Google Scholar] [CrossRef]
- Amato, F.; Casola, V.; Cozzolino, G.; De Benedictis, A.; Mazzocca, N.; Moscato, F. A Security and Privacy Validation Methodology for e-Health Systems. ACM Trans. Multimed. Comput. Commun. Appl. 2021, 17. [Google Scholar] [CrossRef]
- Joppi, R.; Bertele, V.; Vannini, T.; Garattini, S.; Banzi, R. Food and Drug Administration vs European Medicines Agency: Review times and clinical evidence on novel drugs at the time of approval. Br. J. Clin. Pharmacol. 2020, 86, 170–174. [Google Scholar] [CrossRef]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G.; The PRISMA Group. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. PLoS Med. 2009, 6, e1000097. [Google Scholar] [CrossRef]
- Simplicio, M.A.; Iwaya, L.H.; Barros, B.M.; Carvalho, T.C.; Näslund, M. SecourHealth: A Delay-Tolerant Security Framework for Mobile Health Data Collection. IEEE J. Biomed. Health Inform. 2015, 19, 761–772. [Google Scholar] [CrossRef]
- Tong, Y.; Sun, J.; Chow, S.S.; Li, P. Cloud-Assisted Mobile-Access of Health Data With Privacy and Auditability. IEEE J. Biomed. Health Inform. 2014, 18, 419–429. [Google Scholar] [CrossRef]
- Xie, Y.; Zhang, K.; Kou, H.; Mokarram, M.J. Private anomaly detection of student health conditions based on wearable sensors in mobile cloud computing. J. Cloud Comput. 2022, 11. [Google Scholar] [CrossRef] [PubMed]
- Bigini, G.; Lattanzi, E. Toward the InterPlanetary Health Layer for the Internet of Medical Things With Distributed Ledgers and Storages. IEEE Access 2022, 10, 82883–82895. [Google Scholar] [CrossRef]
- Kong, F.; Zhou, Y.; Xia, B.; Pan, L.; Zhu, L. A Security Reputation Model for IoT Health Data Using S-AlexNet and Dynamic Game Theory in Cloud Computing Environment. IEEE Access 2019, 7, 161822–161830. [Google Scholar] [CrossRef]
- Agrahari, A.K.; Varma, S.; Venkatesan, S. Two factor authentication protocol for IoT based healthcare monitoring system. J. Ambient Intell. Humaniz. Comput. 2023, 14, 16081–16098. [Google Scholar] [CrossRef]
- Ullah, F.; Ullah, I.; Khan, A.; Uddin, M.I.; Alyami, H.; Alosaimi, W. Enabling Clustering for Privacy-Aware Data Dissemination Based on Medical Healthcare-IoTs (MH-IoTs) for Wireless Body Area Network. J. Healthc. Eng. 2020, 2020, 8824907. [Google Scholar] [CrossRef]
- Shreya, S.; Chatterjee, K.; Singh, A. A smart secure healthcare monitoring system with Internet of Medical Things. Comput. Electr. Eng. 2022, 101, 107969. [Google Scholar] [CrossRef]
- Bashir, A.; Mir, A.H. Lightweight Secure MQTT for Mobility Enabled e-health Internet of Things. Int. Arab. J. Inf. Technol. 2021, 18, 773–781. [Google Scholar] [CrossRef]
- Ding, R.; Zhong, H.; Ma, J.; Liu, X.; Ning, J. Lightweight Privacy-Preserving Identity-Based Verifiable IoT-Based Health Storage System. IEEE Internet Things J. 2019, 6, 8393–8405. [Google Scholar] [CrossRef]
- Yongjoh, S.; So-In, C.; Kompunt, P.; Muneesawang, P.; Morien, R.I. Development of an Internet-of-Healthcare System Using Blockchain. IEEE Access 2021, 9, 113017–113031. [Google Scholar] [CrossRef]
- Ghayvat, H.; Sharma, M.; Gope, P.; Sharma, P.K. SHARIF: Solid Pod-Based Secured Healthcare Information Storage and Exchange Solution in Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 5609–5618. [Google Scholar] [CrossRef]
- Arul, R.; Al-Otaibi, Y.D.; Alnumay, W.S.; Tariq, U.; Shoaib, U.; Piran, M.J. Multi-modal secure healthcare data dissemination framework using blockchain in IoMT. Pers. Ubiquitous Comput. 2021. [Google Scholar] [CrossRef]
- Khan, A.A.; Wagan, A.A.; Laghari, A.A.; Gilal, A.R.; Aziz, I.A.; Talpur, B.A. BIoMT: A State-of-the-Art Consortium Serverless Network Architecture for Healthcare System Using Blockchain Smart Contracts. IEEE Access 2022, 10, 78887–78898. [Google Scholar] [CrossRef]
- Saini, A.; Zhu, Q.; Singh, N.; Xiang, Y.; Gao, L.; Zhang, Y. A Smart-Contract-Based Access Control Framework for Cloud Smart Healthcare System. IEEE Internet Things J. 2021, 8, 5914–5925. [Google Scholar] [CrossRef]
- Mnyawi, R.; Kombe, C.; Sam, A.; Nyambo, D. Blockchain-based Data Storage Security Architecture for e-Health Care Systems: A Case of Government of Tanzania Hospital Management Information System. Int. J. Comput. Sci. Netw. Secur. 2022, 22, 364–374. [Google Scholar]
- Xu, G.; Qi, C.; Dong, W.; Gong, L.; Liu, S.; Chen, S.; Liu, J.; Zheng, X. A Privacy-Preserving Medical Data Sharing Scheme Based on Blockchain. IEEE J. Biomed. Health Inform. 2022, 27, 698–709. [Google Scholar] [CrossRef]
- Dubovitskaya, A.; Baig, F.; Xu, Z.; Shukla, R.; Zambani, P.S.; Swaminathan, A.; Jahangir, M.M.; Chowdhry, K.; Lachhani, R.; Idnani, N.; et al. ACTION-EHR: Patient-Centric Blockchain-Based Electronic Health Record Data Management for Cancer Care. J. Med. Internet Res. 2020, 22, e13598. [Google Scholar] [CrossRef]
- Kim, H.J.; Kim, H.H.; Ku, H.; Yoo, K.D.; Lee, S.; Park, J.I.; Kim, H.J.; Kim, K.; Chung, M.K.; Lee, K.H.; et al. Smart Decentralization of Personal Health Records with Physician Apps and Helper Agents on Blockchain: Platform Design and Implementation Study. JMIR Med. Inform. 2021, 9, e26230. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Kim, M.; Yu, S.; Das, A.K.; Park, Y. Design of Secure Authentication Protocol for Cloud-Assisted Telecare Medical Information System Using Blockchain. IEEE Access 2020, 8, 192177–192191. [Google Scholar] [CrossRef]
- Shakil, K.A.; Zareen, F.J.; Alam, M.; Jabin, S. BAMHealthCloud: A biometric authentication and data management system for healthcare data in cloud. J. King Saud Univ.-Comput. Inf. Sci. 2020, 32, 57–64. [Google Scholar] [CrossRef]
- Qiu, H.; Qiu, M.; Liu, M.; Memmi, G. Secure Health Data Sharing for Medical Cyber-Physical Systems for the Healthcare 4.0. IEEE J. Biomed. Health Inform. 2020, 24, 2499–2505. [Google Scholar] [CrossRef] [PubMed]
- Son, J.; Kim, J.D.; Na, H.S.; Baik, D.K. Dynamic access control model for privacy preserving personalized healthcare in cloud environment. Technol. Health Care 2015, 24 (Suppl. S1), S123–S129. [Google Scholar] [CrossRef] [PubMed]
- Khan, F.; Reyad, O. Application of intelligent multi agent based systems for E-healthcare security. Inf. Sci. Lett. 2019, 8, 67–72. [Google Scholar]
- Padinjappurathu Gopalan, S.; Chowdhary, C.L.; Iwendi, C.; Farid, M.A.; Ramasamy, L.K. An Efficient and Privacy-Preserving Scheme for Disease Prediction in Modern Healthcare Systems. Sensors 2022, 22, 5574. [Google Scholar] [CrossRef] [PubMed]
- Reyad, O.; Karar, M.E. Secure CT-Image Encryption for COVID-19 Infections Using HBBS-Based Multiple Key-Streams. Arab. J. Sci. Eng. 2021, 46, 3581–3593. [Google Scholar] [CrossRef] [PubMed]
- Salim, M.M.; Park, J.H. Federated Learning-based secure Electronic Health Record sharing scheme in Medical Informatics. IEEE J. Biomed. Health Inform. 2022, 27, 617–624. [Google Scholar] [CrossRef] [PubMed]
- Edemacu, K.; Jang, B.; Kim, J.W. Collaborative Ehealth Privacy and Security: An Access Control With Attribute Revocation Based on OBDD Access Structure. IEEE J. Biomed. Health Inform. 2020, 24, 2960–2972. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Z.; Liu, W.; Ma, R.; Shirazi, S.H.; Xie, Y. Lightweight Healthcare Wireless Body Area Network Scheme With Amplified Security. IEEE Access 2021, 9, 125739–125752. [Google Scholar] [CrossRef]
- Yi, X.; Bouguettaya, A.; Georgakopoulos, D.; Song, A.; Willemson, J. Privacy Protection for Wireless Medical Sensor Data. IEEE Trans. Dependable Secur. Comput. 2016, 13, 369–380. [Google Scholar] [CrossRef]
- Zhang, M.; Chen, Y.; Susilo, W. PPO-CPQ: A Privacy-Preserving Optimization of Clinical Pathway Query for E-Healthcare Systems. IEEE Internet Things J. 2020, 7, 10660–10672. [Google Scholar] [CrossRef]
- Dzissah, D.A.; Lee, J.S.; Suzuki, H.; Nakamura, M.; Obi, T. Privacy Enhanced Healthcare Information Sharing System for Home-Based Care Environments. Healthc. Inform. Res. 2019, 25, 106–114. [Google Scholar] [CrossRef]
- Chatterjee, A.; Gerdes, M.W.; Khatiwada, P.; Prinz, A. SFTSDH: Applying Spring Security Framework With TSD-Based OAuth2 to Protect Microservice Architecture APIs. IEEE Access 2022, 10, 41914–41934. [Google Scholar] [CrossRef]
- Hu, J.; Liang, W.; Hosam, O.; Hsieh, M.Y.; Su, X. 5GSS: A framework for 5G-secure-smart healthcare monitoring. Connect. Sci. 2022, 34, 139–161. [Google Scholar] [CrossRef]
- Roehrs, A.; Da Costa, C.A.; da Rosa Righi, R.; De Oliveira, K.S.F. Personal Health Records: A Systematic Literature Review. J. Med. Internet Res. 2017, 19, e5876. [Google Scholar] [CrossRef]
- Mirza, A.B. Potential of Mobile Devices in New Zealand Healthcare. In Masters of Engineering in Software; Massey University: Albany, Auckland, New Zealand, May 2008. [Google Scholar]
- Dogtown Media. Data Backup and Disaster Recovery Strategies for Healthcare App Data Storage. Available online: https://www.dogtownmedia.com/data-backup-and-disaster-recovery-strategies-for-healthcare-app-data-storage/ (accessed on 12 January 2024).
- Arora, S.; Yttri, J.; Nilse, W. Privacy and Security in Mobile Health (mHealth) Research. Alcohol. Res. 2014, 36, 143–151. [Google Scholar]
- Elhoseny, M.; Thilakarathne, N.N.; Alghamdi, M.I.; Mahendran, R.K.; Gardezi, A.A.; Weerasinghe, H.; Welhenge, A. Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions. Sustainability 2021, 13, 11645. [Google Scholar] [CrossRef]
- Thapa, S.; Bello, A.; Maurushat, A.; Farid, F. Security Risks and User Perception towards Adopting Wearable Internet of Medical Things. Int. J. Environ. Res. Public Health 2023, 20, 5519. [Google Scholar] [CrossRef] [PubMed]
- Tandon, R.; Cupta, P.K. Security and Privacy Challenges in Healthcare Using Internet of Things. In IoT-Based Data Analytics for the Healthcare Industry; Singh, S.K., Singh, R.S., Pandey, A.K., Udmale, S.S., Chaudhary, A., Eds.; Academic Press: London, UK, 2021; pp. 149–165. [Google Scholar]
- Kelly, J.T.; Campbell, K.L.; Gong, E.; Scuffham, P. The Internet of Things: Impact and Implications for Health Care Delivery. J. Med. Internet Res. 2020, 22, e20135. [Google Scholar] [CrossRef] [PubMed]
- Yinka, O.T.; Haw, S.C.; Yap, T.T.V.; Subramaniam, S. Improving the data access control using blockchain for healthcare domain. F1000 Res. 2021, 10, 901. [Google Scholar] [CrossRef]
- Kiania, K.; Jameii, S.M.; Rahmani, A.M. Blockchain-based privacy and security preserving in electronic health: A systematic review. Multimed. Tools Appl. 2023, 82, 28493–28519. [Google Scholar] [CrossRef] [PubMed]
- Sanka, A.I.; Cheung, R.C.C. A systematic review of blockchain scalability: Issues, solutions, analysis and future research. J. Netw. Comput. Appl. 2021, 195, 103232. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy for Healthcare Blockchains. IEEE Trans. Serv. Comput. 2022, 15, 3668–3686. [Google Scholar] [CrossRef]
- Ghosh, P.K.; Chakraborty, A.; Hasan, M.; Rashid, K.; Siddique, A.H. Blockchain Application in Healthcare Systems: A Review. Systems 2023, 11, 38. [Google Scholar] [CrossRef]
- Mehrtak, M.; SeyedAlinaghi, S.; MohsseniPour, M.; Noori, T.; Karimi, A.; Shamsabadi, A.; Heydari, M.; Barzegary, A.; Mirzapour, P.; Soleymanzadeh, M.; et al. Security challenges and solutions using healthcare cloud computing. J. Med. Life 2021, 14, 448. [Google Scholar] [CrossRef]
- AI-Issa, Y.; Ottom, M.A.; Tamrawi, A. eHealth Cloud Security Challenges: A Survey. J. Healthc. Eng. 2019, 2019, 7516035. [Google Scholar]
- Attarian, R.; Hashemi, S. An anonymity communication protocol for security and privacy of clients in IoT-based mobile health transactions. Comput. Netw. 2021, 190, 107976. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).