Abstract
Insider threats, as one of the pressing challenges that threaten an organization’s information assets, usually result in considerable losses to the business. It is necessary to explore the key human factors that enterprise information security management should focus on preventing to reduce the probability of insider threats effectively. This paper first puts forward the improved Human Factors Analysis and Classification System (IHFACS) based on actual enterprise management. Then, the enterprise internal threat risk assessment model is constructed using the Bayesian network, expert evaluation, and fuzzy set theory. Forty-three classic insider threat cases from China, the United States, and Israel during 2009–2021 are selected as samples. Then, reasoning and sensitivity analysis recognizes the top 10 most critical human factors of the accident and the most likely causal chain of unsafe acts. The result shows that the most unsafe behavior was not assessing employees’ familiarity with the company’s internal security policies. In addition, improving the organizational impact of information security can effectively reduce internal threats and promote the sustainable development of enterprises.
1. Introduction
With the development of information management technologies, such as the Internet and mobile applications, the information security problems faced by enterprises have become increasingly serious, and information security risks have penetrated into all aspects of enterprise operation and management. alit is well-know that every company has internal sensitive data types, such as business plans, core technology, customer information data, and intellectual property. Therefore, an attack on an organization’s primary technical information may result in significant losses. The main sources of security threats for businesses today are insiders with access to sensitive data and systems—both malicious insiders and careless insiders []. IBM X-Force Threat Intelligence Index [] showed that insider attacks were the most common type of cyberattack in 2017, around 60%. The 2020 Insider Threat Report [] finds that almost all organizations feel vulnerable to insider attacks (95%), and 68% feel moderate to highly vulnerable to insider attacks. In addition, there are numerous causes of insider information security incidents, with human factors (HFs) dominating [].
1.1. Insider Threat Definition
What is a definition of an insider threat? First, an insider has been legitimately empowered with the right to access or use organizational assets. Assets may involve privileged accounts, core technical data, and other sensitive information. Alternatively, as commonly stated, an insider includes an employee (current or former), trusted business partner, or subcontractor []. Additionally, an insider threat was defined as: “intentional or unintentional activities by an insider cause damage to the organization’s assets and/or negatively affect the confidentiality, integrity, or availability of the organization’s information or information systems [].”
1.2. Insider Threat Incidents
Malicious or unintentional actions by insiders can cause equal harm to their organizations, leaking and deleting confidential internal data, or even giving external attackers an opportunity. Recently, a few internal accidents caused the company substantial financial loss and operational risk, which have aroused widespread concern. For example, an insider attack accident happened in a company at JD on 18 June 2021. This accident was caused by an intern programmer who maliciously deleted the project R&D database, causing delays in the project. In September 2017, a Wells Fargo employee mistakenly sent an email that compromised the information of 50,000 customers due to carelessness []. The Bank of Bahrain went bankrupt after a serious internal security incident caused by an employee error that resulted in a loss of $1.4 billion []. It can be seen from these examples that there are two main types of insider threats: intentional and malicious insider threats. The “unintentional insider threats” of human negligence and inadequate preparation, often the least detectable types of insider threats, may pose a more serious risk than the former []. In short, insider threats are essentially related to “human” factors []. The prevention and control of HFs can have a beneficial effect on decreasing insider threats in the enterprise.
This study aims to construct a human-causal analysis model of insider threats in an organization to gain insight into the various insecure behaviors and their influencing factors that lead to information security incidents within an organization. This paper will give important references for identifying what make insider threats in organizations happen and how to mitigate them more effectively.
The remainder of this paper is organized as follows: current research on insider threats examines various detection and preventive techniques in Section 2. Section 3 presents a hybrid model that integrates fuzzy set theory (FST), expert judgment, and an improved Human Factors Analysis and Classification System (IHFACS) into Bayesian networks (BN), called IHFACS-BN. Section 4 presents the application of the hybrid model in analyzing the key HFs that lead to insider threats in the enterprise and provides constructive comments based on the model’s inference results. Section 5 concludes the research and advises future studies. Finally, future work is presented in Section 6. Figure 1 depicts the organizational structure of this article.
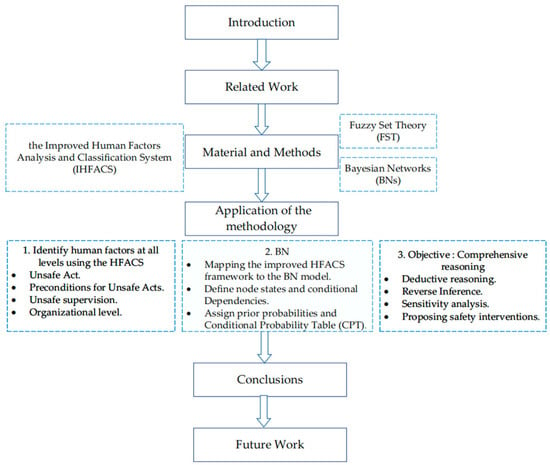
Figure 1.
Article outline.
2. Related Work
In recent years, the academic community has paid considerable attention to insider threats, and experts and scholars have proposed different solutions for insider threats in network information security. These methods can be separated into two primary categories: detection and prevention.
2.1. Detection Methods
Insider threat detection approaches are mainly technical and non-technical. Traditional insider threat detection techniques rely primarily on machine learning [], user commands [], and biometrics [], with security events, such as Trojans and viruses, serving as the primary detection objects. With the diversification of insider attackers and attack methods, traditional threat detection techniques have long failed to meet the demand. Insider threat discovery methods are primarily used to detect insider threats through the finding of behavioral traces of insider users and constructing related insider user behavior models. As a result, current insider threat detection approaches are based on aberrant behavior and formal modeling [].
The anomaly-based threat detection method mainly relies on big data and artificial intelligence technology to classify how users behave, then determine if there is any abnormal behavior that could be an insider threat. The approach may efficiently detect threats posed by unidentified patterns. Currently, it is the most used way. Lane et al. devised two methods based on instance learning and the hidden Markov model to solve this problem. The goal was to create a model of how system users typically work and find abnormal conditions as long-term deviations from expected behavior patterns. Both methods can identify anomalies well enough for low-level “focus of attention” detectors in multi-layer security systems, but they are not good enough for comprehensive security solutions []. Happa et al. modeled normal employee behavior using Gaussian mixture models with likelihood and criterion scores as anomaly detection metrics and incorporated pertinent expert knowledge, thereby improving the detection accuracy []. With the development of neural networks, deep learning techniques for analyzing the behavior of users and entities have become widespread for detecting insider threats. Zhang et al. proposed an insider threat detection model based on LSTM-Attention that takes full advantage of the LSTM (Long Short-term Memory) network and Attention to handle long sequences but also considers the unique characteristics of insiders []. Haq et al. developed two DL (Deep Learning) hybrid LSTM models integrated with Word2vec LSTM GLoVe (Global Vectors for Word Representation) LSTM and compared the performance of these models to detect insider threats with state-of-the-art ML (Machine Learning) models. It was found that ML-based models outperformed the DL-based ones []. Several studies have also begun to apply Feedforward Neural Networks [] and Recurrent Neural Networks [] to develop a new automatic anomaly detection method.
Insider threat detection methods based on anomalous behavior rely heavily on the accuracy and comprehensiveness of data acquisition and require a large amount of existing insider behavior data, which limits them. Applying non-technical detection methods (e.g., psychological, sociological) is also beneficial for reducing insider threats when there are few or no sample data available. However, the former can determine users’ psychological states from their network or host use, and the latter can infer malicious motives from their social performance [].
2.2. Prevention Methods
We found that most research has focused on using technology to “detect” threats rather than “prevent” them, so most enterprise cybersecurity programs tend to take a “detection-centric” approach to protection. The approaches for detecting insider threats described in the preceding section suffer from some drawbacks: they are inefficient and take a long time to discover and detect. Some research is theoretical and cannot be applied universally within organizations. Moreover, the primary limitation of a detection-centric approach to security is that it is inherently reactive, acting only on threats that have been identified. A prevention-centric approach tries to stop insider attacks before they happen. As many cybersecurity threats result from human error or a lack of awareness, Rajamäki et al. proposed a proactive and resilient education framework to develop corresponding cybersecurity education and training programs for different categories of employees []. Chowdhury et al. [] proposed a framework for enterprise network security training based on learning theory and the Delphi method.
When security technology cannot protect an organization from insider threats, the human element is usually the weakest link in the information security chain []. The current situation in enterprise security preparedness is that the human element is usually the most vulnerable part of the information security chain when the use of security technology fails to protect the organization from insider threats. Thus, human factors are receiving increasing attention. Although frameworks and assessment models for insider threats containing HFs have been proposed in the literature, they lack systematicity and relevance.
Effective accident prevention requires incorporating HFs into accident analysis models [,]. This study uses the HFACS model [], which Shapell and Wiegmann developed to study HFs in accidents based on the Swiss cheese model by analyzing a large amount of aviation accident data. Due to its effective evaluation framework, content integrity, and practicability, the model has been applied in different fields, such as coal mines, maritime transport, and laboratory explosions [,,]. Considering that insider threats are distinct from general safety incidents, this paper proposes an IHFACS framework for insider threat assessment items, adapted from the frameworks in the “Related Studies” section. At the same time, a hybrid model for insider threat HFs analysis is constructed based on BN. The hybrid model is then used to identify high-frequency human causes of insider threats and the causal relationships among HFs at each level to provide a reference for preventing insider threats and further reducing hazards and losses. The main novelties of this study are summarized as follows:
- An IHFACS framework is proposed to be applied to the HFs analysis of insider enterprise threats.
- An IHFACS-BN model is used to assess the risk of insecure behavior within the enterprise.
- HFACS, expert knowledge, the triangular fuzzy number estimation probability method, the Noisy-OR gate model, and BN are integrated into this model.
- BN-based reasoning identifies key risk factors and the interdependence of HFs at different and the same levels.
- Compared with traditional accident analysis methods, this method focuses more on the explicit and implicit correlations between HFs.
3. Material and Methods
This section outlines the methodology used to develop the IHFACS-BN model. The model was developed using the HFACS framework, expert assessment method, triangular fuzzy number estimation probability method, and BN to comprehensively identify the risk factors of inside-the-business threats. To achieve better analysis results, the hybrid model combines qualitative and quantitative analysis methods.
3.1. IHFACS
It is well known that HFACS is a widespread and popular framework for human error analysis []. According to the HFACS model, “primary causes cause accidents, and potential causes cause primary causes,” where the primary causes are analyzed at four levels: “unsafe human behavior, potential factors refer to the preconditions of unsafe behavior, unsafe supervision, and organizational influence” []. Figure 2 [] shows that the primary causes are analyzed at four levels: “unsafe human behavior; potential factors referring to the preconditions of unsafe behavior; unsafe supervision; and organizational influence.” The HFACS model is highly flexible and adaptable to industry-specific characteristics []. In this paper, we examined the literature on insider threat, investigated the current state of information security management in enterprises, and conducted a thorough examination of insider threat survey reports. We found that insider threats are high-risk, hidden, and multiple; the types of enterprises, security management policies, and employee quality vary. It makes the risk transmission process strongly coupled, ambiguous, and dynamic. Therefore, the HFs classification of the original HFACS framework is not fully applicable to insider enterprise threats. For example, the original HFACS framework focuses on the lack of inadequate supervision of crew members in aviation accidents at the unsafe supervision level, while enterprise network security protection uses computer technology to monitor user behavior characteristics in real time. In light of the preceding, this paper revises some of the HFs of the HFACS model by collecting and analyzing data on security incidents and referencing relevant studies. In addition, experts in this field hold a safety meeting to investigate the root of incidents and briefly describe the HFs professionally. Finally, the IHFACS model for insider threat analysis in enterprises is developed.
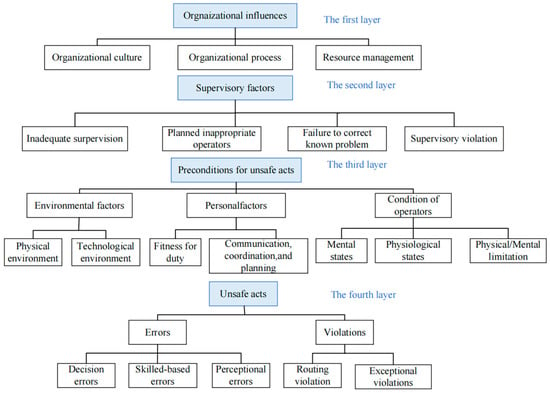
Figure 2.
HFACS framework.
3.2. Fuzzy Bayesian Network (FBN)
3.2.1. Fuzzy Theory and Expert Elicitation
It is well known that, as a scientific consensus, the expert judgment method can be utilized to judge the identified HFs significantly. Analytic Hierarchy Process (AHP) has a strong ability to deal with complex decision-making problems [,,]. However, because of the subjectivity of qualitative criteria, experts are commonly reluctant to express their opinions clearly and intuitively. Due to this, Laarhoven proposed this method, using fuzzy triangular numbers to calculate [], and extended the AHP. A combination of FST and subjective opinion help raters more effectively estimate the impact rate of identified each HF [,].
In fuzzy judgment, the expert language is quantified as TFN by the affiliation degree function. According to the definition of fuzzy number, the adopted TFN is denoted as A = (a, m, b), and the affiliation degree function of TFN [] can be expressed as follows:
In Formula (1), A denotes the fuzzy set on the specified universe x, μA(x) denotes the membership function of x to the fuzzy set A, and m denotes the mean value of the fuzzy number A, where a and b denote the upper and lower bounds of TFNs. In fuzzy judgment, the membership function is used to convert the qualitative linguistic expression of experts into fuzzy triangular numbers. When making preference judgments for pairs of elements in a group, as in AHP, the number of elements in a set should be limited to seven plus or minus two []. As a result, five linguistic variables are introduced: VL, L, M, H, and VH. The judgment results of TFNs are qualitatively described in Table 1.

Table 1.
Judgment of triangular fuzzy numbers.
The weight factor is used to represent the quality of experts in order to ensure the reliability of experts’ subjective evaluations. The experts’ abilities are primarily evaluated based on four aspects (Sn, n = 1,2,3,4): working years, education level, age, and professional positions, combined with the company’s internal information security management practices. Depending on the background of the invited experts, the composite score of the ith expert can be obtained by Equation (2) using the scoring rules in Table 2. Then, the respective weights () are determined according to the following Formulas (3) for five experts in different enterprise security fields.

Table 2.
Weighting scores of experts.
After obtaining the corresponding fuzzy numbers for the linguistic variables of the experts, the opinions of different experts are aggregated according to the linear joint prior method, namely:
In this formula: Pj is the aggregated fuzzy number of nodes, is the weight of experts, qij is the language evaluation of node j given by expert i, is the number of experts, n is the number of nodes.
In FST, the defuzzification process produces quantifiable results. Then, the method of Mean area method (MAM) can be used to get the fuzzy value of the node (N*), as the following Formula (5):
In this paper, the prior probability of each node can be obtained by converting N* into probability of an impact rate (PIR) using the Formulas (6) and (7) [].
3.2.2. BN
BN is a probabilistic reasoning-based graphical network with functions such as causal analysis, bidirectional reasoning, and prediction. Due to its ability to better simulate human thought processes, BN has become an increasingly popular modeling technology in network security, such as information security risk assessment and intelligent grid security [,]. Moreover, it has recently been used to study insider threats in models [,]. Therefore, we introduce a BN model to this study since its causal relationship is very suitable for the study and application of risk problems.
BN is usually composed of two parts: BN structure and BN parameters. (1) The structure of BN is also called a directed acyclic graph (DAG), which is mainly a qualitative analysis of the BN, consisting of nodes representing each event and directed edges connecting each node, as shown in Figure 3. There are three main types of nodes: target nodes, intermediate nodes, and evidence nodes. (2) The parameter of BN is also called the Conditional Probability Table (CPT), a quantitative analysis of BN that represents the strength of connections between network nodes. BN can be expressed as:
where (V, M) is a DAG with n nodes, M is the direct edge of these nodes, P is the CPT of each node and X = {X1, X2,..., Xn} is a set of random variables. The JPD (joint probability distribution) of BN is:
where, represents the parent node of Xi. In addition, this study will combine Noisy-OR gate model and expert judgment to implement CPT.
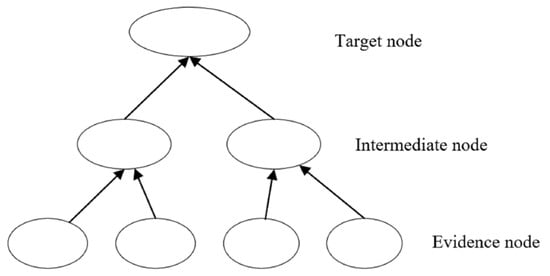
Figure 3.
Directed acyclic graph.
4. Application of the Methodology
4.1. Application of HFACS Framework
To identify as many contributing factors to the insider threat as possible, we first compiled insider threat incidents from 2009 to 2021 in various countries using Weibo, Baidu, and the existing literature. We filtered the collected data to identify enterprise security incidents in which unsafe acts were the leading cause. This paper compiles 43 enterprise insider threat incidents in China and other nations (including the United States and Israel) between 2009 and 2021. Then, based on the direct and indirect causes in the incident reports and concerning related studies [,,,,,], the HFs of insider enterprise threats were categorized and aggregated according to the item categories of the IHFACS model. Second, a workshop on information security within enterprises was held to compensate for the dearth of sample data, with the participation of experts in the field, such as senior project supervisors, network management managers, and IT engineers from various businesses. The improved HFACS model adheres to the four levels of the original HFACS framework; only specific subcategories were revised. Finally, these failures were classified into four levels based on the HFACS model: organizational influence (N = 12), unsafe supervision failures (N = 13), preconditions for unsafe acts (N = 8), and unsafe acts (N = 9). It can be seen that unsafe supervision and organizational failure contribute to insider threats most frequently. Table 3 lists the IHFACS contributory failures, along with their compliance and specific manifestations.

Table 3.
Symbols and descriptions of HFs in the IHFACS.
4.2. Establishment of Interdependencies for the Identified HFs
For mapping the IHFACS model into BN, the identified HFs are transformed into a hierarchy of nodes in BN. In the traditional HFACS framework, it is generally considered that the relationship between the four levels is that the upper level influences the lower level. The bottom layer (unsafe behavior) directly determines the occurrence of the accident. It often ignores the connections between different levels and within the same level. In practice, we find that this interaction relationship has an important impact on the occurrence of insider threats.
This study proposes two hypotheses as a result. The first is that the higher-level HFs in IHFACS would influence the lower-level HFs, and the second is that HFs at the same level could influence one another. First, the human factors of 43 insider threat events were classified and counted using the established IHFACS model. The frequency of HFs was then calculated, followed by the probability of the layers interacting. For example, when A11 occurs, the frequency of C12 is 18, and the proportion of its total frequency (20) is 0.9, indicating that A11 and C12 have a 0.9 correlation value. We establish the threshold value at 0.8. Experts score (0–1) the association between upper and lower levels with each same-level factor according to IHFACS and get the association probability by weighted average. Two sets of association probabilities were derived after expert scoring and statistical analysis of case data. There are three scenarios to consider.
Scenario 1: When the case’s association probability exceeds the threshold value, the factors are deemed highly associated regardless of whether the expert’s scoring value for the group of factors is greater than or less than the threshold value. An edge links two nodes together.
Scenario 2: When the case data count a set of factors whose association values are all less than the threshold and the expert scores for that set of factors are also less than the threshold, this means that the pair of factors does not hold in both hypotheses and is not considered.
Scenario 3: When the calculated association value for the case is less than the threshold and the expert’s scoring value for the group of factors’ association is greater than the threshold, factor weighting is necessary to determine the analysis. The calculation is weighted with a ratio of 0.8:0.2. For example, the statistical value of 20% and the expert’s score of 80% can be weighted independently. If the weighted value is less than the threshold value, the group of factors is deemed irrelevant or insufficient and is not considered. The graphical structure of BN is built according to the IHFACS hierarchy by connecting nodes between the upper and lower levels of HFACS and within the same level with edges, as shown in Figure 4. All directed edges connecting nodes in the model of Figure 4 are shown in Table A1.
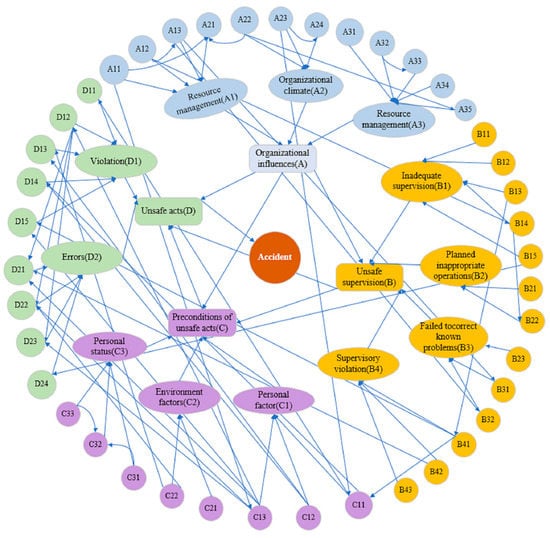
Figure 4.
Mapping identified HFs in IHFACS to BN.
4.3. Bayesian Network Assignment
In BN of the information security incident risk, the state of each node is considered to have two states. “Yes” means it has an impact on the occurrence of the accident, and “No” means it has no impact on the accident. The next step is determining the nodes’ prior probabilities and CPTs. Due to the relatively general statistics of insider threat events, some qualitative influencing factors cannot be obtained through statistical data. Therefore, this paper adopts fuzzy, expert elicitation, and Noisy-OR gate model to obtain the prior probability of the evidence nodes and CPTs for intermediate nodes. For this purpose, a method of scoring rules is established to calculate the competence of each expert and assign their respective weights. The contents of the expert rating scale are in Table 2, and the expert weights are shown in Table 4. Table 5 summarizes all expert opinions on the likelihood of HFs failures, and corresponding defuzzified aggregated and PIR values.

Table 4.
Weights of employed experts.

Table 5.
Expert opinions for HFs, defuzzify aggregated, and probability value.
In this BN model, the conditional probability table of only one D1(“violation”) node requires 25 = 32 CPTs. The amount of data required is too large. In order to reduce the required data, the Noisy-OR gate model is introduced to estimate the CPT in this study. In the BN based on the Noisy-OR gate model, each variable has only two states, that is, “yes” and “no,” and each variable is independent of the other []. Meanwhile, only one variable Ai is enough to cause the result Y to appear when the other variables do not. Only Ai is “yes”, and the other parent nodes is “no.” The probability expression of the occurrence of node Y is as in Equation (10), and then CPTs for the child node Y are calculated using Equation (11).
4.4. Inverse Reasoning (IR) and Sensitivity Analysis (SA)
The FBN model inputs the prior model and CPTs to make it simulated and run in the GeNIe 2.3 Academic program and get the risk probability inference result of accidents. Deductive reasoning is one of the unique and specific characteristics of BN, which can reason regarding HFs that are not fully reflected in accident investigation reports, thereby improving accident investigation reports and contributing to future accident prevention. According to the reverse inference rule of BN, the calculation result is obtained, and the probability that the accident state is “yes” is set to 100%. As shown in Figure 5, the sum of the four probabilities of organizational influences (A), unsafe supervision (B), preconditions of unsafe acts (C), and unsafe acts (D) is significantly greater than 1, demonstrating the existence of interactions within all four HFACS levels and among their peers. Notably, the probability of unsafe behavior is the largest, followed by the premise of unsafe behavior. Continue to infer the reverse, assuming that the probability of bad conditions for accidents A, B, and C is 100%, the results show that the probability of unsafe behavior is as high as 99%, and A13 has the highest probability in parent nodes. The most likely cause-and-effect chain leading to unsafe behaviors is A13→A1→A→D. The most likely causal chain that leads to unsafe behavior begins with a flawed security detection system, then passes to poor resource management and organizational influences.
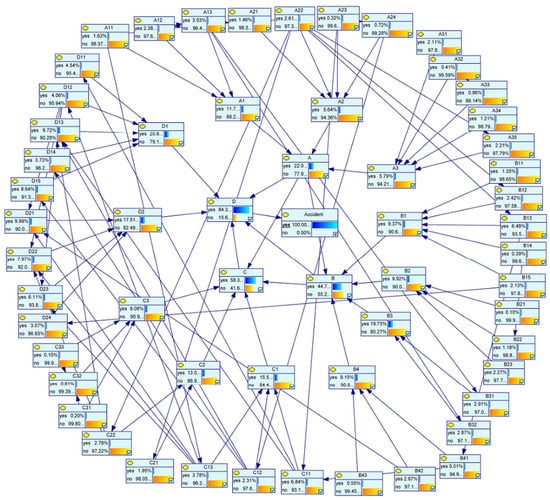
Figure 5.
Insider threat risk diagnostic inference results.
Sensitivity analysis is used to determine the degree of influence of each factor on insider threat incidents. In Figure 6, the darker the node’s color, the more sensitive the node is. The most sensitive events are A22, A11, A23, A24, C13, A13, A12, B13, D12, C12, and C11. Among them, the top five contributing root events are “managers don’t pay enough attention to internal security organization (A22),” “insufficient safety education and training (A11),” “lack of humanistic care for employees who are inclined to leave (A23),” “enterprise talent mobility is large (A24),” and “competence (C13).” Moreover, it is worth noting that the largest proportion (60%) of the accident occurrence comes from organizational influences (A) among the top 10 contributing HFs (Table 6).
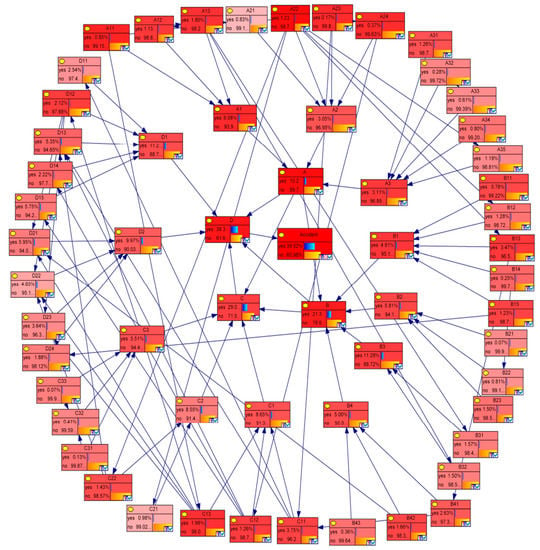
Figure 6.
Sensitivity analysis results.

Table 6.
Top 10 riskiest factors in insider threats.
4.5. Suggestions for Enterprise Information Security Management
- (1)
- For the most fundamental factor of imperfect security detection systems, enterprises, especially SMEs, should pay attention to their investment in insider threat detection technology and promptly update detection tools to strengthen database security management. Suggestions for the prevention of internal threats are made for key causal factors.
- (2)
- At the organizational impact A level, enterprises should focus on preventing insider threats, setting up an internal information security management department, and establishing a sound internal attack emergency response mechanism. In addition, continuous information security awareness training and education are crucial to enterprise security management.
- (3)
- Talent is the core resource for an enterprise’s sustainable and healthy development. The loss of high-level talents can easily lead to the leakage of the enterprise’s commercial secrets and core technologies. Focusing on humanistic care for employees is one of the most important ways to retain talent. In addition, it is building an early warning mechanism for high-level talent loss to prevent it before it happens.
5. Conclusions
To identify and rank the most highly contributing HFs in insider threats, this paper proposes a hybrid model based on FST, BN, and IHFACS. The model facilitated the identification, characterization, and ranking of human factors from the perspective of accident causation. Deficiencies in resource management (e.g., A11, A12, and A13), poor organizational climate, technical detection vulnerabilities, and bad personal factors were the most critical root events related to the occurrence of insider threats. At the same time, behavior violation was the most important unsafe behavior leading to accidents, among which the factor with the most significant influence is “employees’ familiarity with the company’s internal safety policy/low level of mastery of safety skills” (D12).
The study’s most striking finding was that organizational influence is the primary contributor to the top 10 basic events. In addition, the study discovered that HFs influencing different levels of insider threat have an influential relationship not only between factors at the next level associated with the previous level, but also between factors across levels and within the same level. The most likely causal chain for the occurrence of insecure behaviors was: “Inadequate detection system deployment and system access control settings→resource management failure→organizational management failure→insecure behaviors.”
Despite the lack of available datasets to compare our methods, the results of other insider threat studies could be used to corroborate each other. Elmrabit et al. [] proposed a BN-based insider threat risk prediction model, which predicts that cases with the highest likelihood of insider threats are due to a high level of risk in human factors, including capabilities, opportunities, and motivation. Small companies pay less attention to insider threats, invest less in technical factors, and have lower detection levels. Furthermore, inadequate occupational safety training, which leads to insufficient safety awareness among employees and predisposes them to unsafe behaviors, is an essential human factor prevalent in insider threats []. These were consistent with the results of this study.
Insider threat is one of the toughest challenges to the sustainable development of enterprises currently, and the insider threat risk assessment model proposed in this study has certain application value. Based on the obtained results, more reasonable control measures and improvement suggestions are put forward for the internal risk prevention of the enterprise.
6. Future Work
This paper has some limitations. Since insider threat incidents are corporate scandals, many security incident investigation reports are not publicly available, making the sample size of cases in this paper small. At the same time, because subjective factor data mostly involves personal privacy and corporate secrets, it is more difficult to obtain than objective factor data. Although the integration of expert judgment and fuzzy theory is used to solve the problem of insufficient historical data and help risk assessment overcome possible ambiguity, the reasoning process and results of the study are largely related to the completeness of the cases and the expertise of the expert group.
In our future work, we will design privacy and secret filtering protection mechanisms to ensure the threat pattern data is based on the user’s or enterprise’s concerns in response to the problem of difficult access to some data. Through this approach, we can collect as many different security events as possible within the enterprise to expand the sample size. Based on these data, we plan to incorporate machine learning into the BN model in order to improve the model’s accuracy and credibility in risk assessment.
Author Contributions
Conceptualization, Y.W.; methodology, M.Z.; validation, M.Z.; formal analysis, M.Z.; investigation, M.Z.; resources, C.D.; data curation, C.D.; writing—original draft preparation, M.Z.; writing—review and editing, C.D. and Y.W.; funding acquisition, Y.W. and C.D. All authors have read and agreed to the published version of the manuscript.
Funding
This paper is supported by Philosophy and Social Science Foundation Youth Project of Hunan Province of China, grant number 19YBQ093, the Scientific research project of Education Department, grant number 20C1625, and the Special Funds for Student Innovation and Entrepreneurship Training Program, grant number S202010555082. The funders had no role in study design, data collection and analysis, decision to publish, or preparation of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
We sincerely thank all the experts who participated in this research information security conference and Krista Chen for their contribution to this work.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A

Table A1.
All directed edges connecting nodes in the model.
Table A1.
All directed edges connecting nodes in the model.
| A11→A1 | B22→B2 | D14→D1 | A23→ C11 | C22→D22 |
| A12→A1 | B23→B2 | D15→D1 | A24→ C12 | C31→C32 |
| A13→A1 | B31→B3 | D21→D2 | A32→A33 | C33→C32 |
| A21→A2 | B32→B3 | D22→D2 | B13→B41 | D12→D21 |
| A22→A2 | B41→B4 | D23→D2 | B14→B22 | D12→D22 |
| A23→A2 | B42→B4 | D24→D2 | B15→D24 | D12→D23 |
| A24→A2 | B43→B4 | A11→A21 | B41→C11 | A1→A |
| A31→A3 | C11→C1 | A11→C13 | B42→D21 | A2→A |
| A32→A3 | C12→C1 | A12→A13 | C11→D11 | A3→A |
| A33→A3 | C13→C1 | A13→B31 | C11→D13 | B1→B |
| A34→A3 | C21→C2 | A13→B32 | C12→D13 | B2→B |
| A35→A3 | C22→C2 | A22→A12 | C12→D14 | B3→B |
| B11→B1 | C31→C3 | A22→A35 | C12→D15 | B4→B |
| B12→B1 | C32→C3 | A22→B12 | C13→D12 | C1→C |
| B13→B1 | C33→C3 | A22→ B13 | C13→D21 | C2→C |
| B14→B1 | D11→D1 | A22→ C21 | C13→D22 | C3→C |
| B15→B1 | D12→D1 | A22→ C22 | C13→D23 | D1→D |
| B21→B2 | D13→D1 | A23→A24 | C22→D13 | D2→D |
References
- Wong, W.P.; Tan, H.C.; Tan, K.H.; Tseng, M.L. Human factors in information leakage: Mitigation strategies for information sharing integrity. Ind. Manag. Data Syst. 2019, 119, 1242–1267. [Google Scholar] [CrossRef]
- Lee, C.; Iesiev, A.; Usher, M.; Harz, D.; McMillen, D. IBM X-Force Threat Intelligence Index. Available online: www.ibm.com/legal/copytrade.shtml (accessed on 20 March 2022).
- Cybersecurity Insiders. 2020 Insider Threat Report. Available online: https://www.cybersecurity-insiders.com (accessed on 20 March 2022).
- Suman, R.; Far, B.; Mohammed, E.; Nair, A.; Janbakhsh, S. Visualization of Server Log Data for Detecting Abnormal Behaviour. In Proceedings of the 2018 IEEE International Conference on Information Reuse and Integration (IRI), Salt Lake City, UT, USA, 6–9 July 2018; pp. 244–247. [Google Scholar] [CrossRef]
- Frank, L.; Justin, P.; Yung, M.; Paul, J. Positioning Your Organization to Respond to Insider Threats. IEEE Eng. Manag. Rev. 2019, 47, 75–83. [Google Scholar]
- Laycomb, W.R.; Nicoll, A. Insider threats to cloud computing: Directions for new research challenges. In Proceedings of the International Computer Software and Applications Conference, Izmir, Turkey, 16–20 July 2012; pp. 387–394. [Google Scholar] [CrossRef]
- Editorial Department of this Journal. Inventory: Major data leakage incidents at home and abroad in 2017. China Inf. Secur. 2018, 3, 62–68. [Google Scholar]
- Yang, Y. The revelation that insider threats cost billions of dollars. Inf. Secur. 2010, 24, 53. [Google Scholar]
- Buckley, O.; Nurse, J.R.; Legg, P.A.; Goldsmith, M.; Creese, S. Reflecting on the Ability of Enterprise Security Policy to Address Accidental Insider Threat. In Proceedings of the 2014 Workshop on Socio-Technical Aspects in Security and Trust, Vienna, Austria, 18 July 2014; pp. 8–15. [Google Scholar] [CrossRef]
- Goh, P. Humans as the weakest link in maintaining cybersecurity: Building cyber resilience in humans. In Introduction to Cyber Forensic Psychology: Understanding the Mind Of The Cyber Deviant Perpetrators; World Scientific: Singapore, 2021; pp. 287–305. Available online: 10.1142/9789811232411_0014 (accessed on 20 March 2022).
- Ye, X.; Hong, S.; Han, M. Feature Engineering Method Using Double-layer Hidden Markov Model for Insider Threat Detection. Int. J. Fuzzy Log. Intell. Syst. 2020, 20, 17–25. [Google Scholar] [CrossRef]
- Wu, C.; Shuai, J.; Long, T.; Yu, J. Research on User Abnormal Operation Detection Method Based on Linux Shell Command. Inf. Netw. Secur. 2021, 21, 31–38. [Google Scholar]
- Yao, H.; Wang, C.; Xu, Q.; Li, W. A distributed biometric authentication protocol based on homomorphic encryption. Comput. Res. Dev. 2019, 56, 2375–2383. [Google Scholar]
- Guo, S.Z.; Zhang, L.; Pan, Y.; Tao, W.; Bai, W.; Zheng, Q.B.; Liu, Y.; Pan, Z.S. A review of research on insider threat discovery detection methods. Data Acquis. Ration. 2022, 37, 488–501. [Google Scholar]
- Lane, T.; Brodley, C.E. An empirical study of two approaches to sequence learning for anomaly detection. Mach. Learn. 2003, 51, 73–107. [Google Scholar] [CrossRef]
- Happa, J. Insider-threat detection using gaussian mixture models and sensitivity profiles. Comput. Secur. 2018, 77, 838–859. [Google Scholar]
- Zhang, G.H.; Yan, F.R.; Zhang, D.W.; Liu, X.F. Insider Threat Detection Model Based on LSTM-Attention. Netinfo Security 2022, 22(2), 1–10. [Google Scholar] [CrossRef]
- Haq, M.A.; Khan, M.A.R.; Alshehri, M. Insider Threat Detection Based on NLP Word Embedding and Machine Learning. Intell. Autom. Soft Comput. 2022, 33, 619–635. [Google Scholar]
- Hu, T.; Niu, W.; Zhang, X.; Liu, X.; Lu, J.; Liu, Y. An Insider Threat Detection Approach Based on Mouse Dynamics and Deep Learning. Secur. Commun. Netw. 2019, 2019, 3898951. [Google Scholar] [CrossRef]
- Alshehri, A. Relational Deep Learning Detection with Multi-Sequence Representation for Insider Threats. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 758–765. [Google Scholar] [CrossRef]
- Theoharidou, M.; Kokolakis, S.; Karyda, M.; Kiountouzis, E. The insider threat to information systems and the effectiveness of ISO17799. Comput. Secur. 2005, 24, 472–484. [Google Scholar] [CrossRef]
- Rajamäki, J.; Nevmerzhitskaya, J.; Virág, C. Cybersecurity education and training in hospitals: Proactive resilience educational framework (Prosilience EF). In Proceedings of the 2018 IEEE Global Engineering Education Conference (EDUCON), Santa Cruz de Tenerife, Spain, 17–20 April 2018; pp. 2042–2046. [Google Scholar] [CrossRef]
- Chowdhury, N.; Katsikas, S.; Gkioulos, V. Modeling effective cybersecurity training frameworks: A delphi method-based study. Comput. Secur. 2022, 113, 102551. [Google Scholar] [CrossRef]
- Hadlington, L. Human factors in cybersecurity; examining the link between Internet addiction, impulsivity, attitudes towards cybersecurity, and risky cyber security behaviours. Heliyon 2017, 3, e00346. [Google Scholar] [CrossRef]
- Islam, R.; Abbassi, R.; Garaniya, V.; Khan, F. Determination of human error probabilities for the maintenance operations of marine engines. J. Ship Prod. Des. 2016, 32, 226–234. [Google Scholar] [CrossRef]
- Lu, J.; Liu, W.; Yu, K.; Zhou, L. The Dynamic Evolution Law of Coal Mine Workers’ Behavior Risk Based on Game Theory. Sustainability 2022, 14, 4015. [Google Scholar] [CrossRef]
- Wiegmann, D.; Shapprll, S. A Human Error Approach to Aviation Accident Analysis: The Human Factors Analysis and Classification System; Ashgate Press: London, UK, 2003; pp. 45–70. [Google Scholar]
- Ma, L.; Ma, X.; Xing, P.; Yu, F. A hybrid approach based on the HFACS-FBN for identifying and analysing human factors for fire and explosion accidents in the laboratory. J. Loss Prev. Process Ind. 2022, 75, 104675. [Google Scholar] [CrossRef]
- Xie, T.; Li, C.; Wei, Y.; Jiang, J.; Xie, R. Cross-domain integrating and reasoning spaces for offsite nuclear emergency response. Saf. Sci. 2016, 85, 99–116. [Google Scholar] [CrossRef]
- Emre, A. A marine accident analysing model to evaluate potential operational causes in cargo ships. Saf. Sci. 2017, 92, 17. [Google Scholar]
- Shappell, S.; Wiegmann, D. Applying Reason: The human factors analysis and classification system (HFACS). Hum. Factors Aerosp. Saf. 2001, 1, 59–86. [Google Scholar]
- Zarei, E.; Yazdi, M.; Abbassi, R.; Khan, F. A hybrid model for human factor analysis in process accidents: FBN-HFACS. J. Loss Prev. Process Ind. 2019, 57, 142–155. [Google Scholar] [CrossRef]
- Rostamabadi, A.; Jahangiri, M.; Zarei, E.; Kamalinia, M.; Alimohammadlou, M. A novel Fuzzy Bayesian Network approach for safety analysis of process systems: An application of HFACS and SHIPP methodology. J. Clean. Prod. 2020, 244, 118761. [Google Scholar] [CrossRef]
- Cao, C.; Liu, Y.; Tang, O.; Gao, X. A fuzzy bi-level optimization model for multi-period post-disaster relief distribution in sustainable humanitarian supply chains. Int. J. Prod. Econ. 2021, 235, 108081. [Google Scholar] [CrossRef]
- Qiao, W.; Liu, Y.; Ma, X.; Liu, Y. Human factors analysis for maritime accidents based on a dynamic fuzzy bayesian network. Risk Anal. 2020, 40, 957–980. [Google Scholar] [CrossRef]
- Laarhoven, P.; Pedrycz, W. A Fuzzy extension of saaty’s priority theory. Fuzzy Sets Syst. 1983, 11, 229–241. [Google Scholar] [CrossRef]
- Saaty, T.L. Why the magic number seven plus or minus two. Math. Comput. Model. 2003, 38, 233–244. [Google Scholar] [CrossRef]
- Fu, Y.; Wu, X. Information security risk assessment method based on Bayesian network. J. Wuhan Univ. 2006, 5, 631–634. [Google Scholar]
- Wadhawan, Y.; AlMajali, A.; Neuman, C. A comprehensive analysis of smart grid systems against cyber-physical attacks. Electronics 2018, 7, 249. [Google Scholar] [CrossRef]
- Greitzer, F.L.; Kangas, L.J.; Noonan, C.F.; Dalton, A.C.; Hohimer, R.E. Identifying at-risk employees: Modeling psychosocial precursors of potential insider threats. In Proceedings of the 2012 45th Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2012; pp. 2392–2401. [Google Scholar] [CrossRef]
- Alsowail, R.; Al-Shehari, T. A Multi-Tiered Framework for Insider Threat Prevention. Electronics 2021, 10, 1005. [Google Scholar] [CrossRef]
- Kim, J.; Lee, C.; Chang, H. The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth. Sustainability 2020, 12, 10639. [Google Scholar] [CrossRef]
- Hong, Y.; Furnell, S. Understanding cybersecurity behavioral habits: Insights from situational support. J. Inf. Secur. Appl. 2021, 57, 102710. [Google Scholar] [CrossRef]
- Reshmi, S. Multihand Administration with Intrusion Avoidance in Database System. Data Min. Knowl. Eng. 2010, 2. Available online: https://api.semanticscholar.org/CorpusID:168640234.
- Seo, S.; Kim, D. Study on Inside Threats Based on Analytic Hierarchy Process. Symmetry 2020, 12, 1255. [Google Scholar] [CrossRef]
- Hong, Y.; Furnell, S. Motivating information security policy compliance: Insights from perceived organizational formalization. J. Comput. Inf. Syst. 2022, 62, 19–28. [Google Scholar] [CrossRef]
- Onisko, A.; Druzdzel, M.; Wasyluk, H. Learning bayesian network parameters from small data sets: Application of noisy-or gates. Int. J. Approx. Reason. 2001, 27, 165–182. [Google Scholar] [CrossRef]
- Elmrabit, N.; Yang, S.; Yang, L.; Zhou, H. Insider threat risk prediction based on Bayesian network. Comput. Secur. 2020, 96, 101908. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).