Abstract
In the digital era, almost every system is connected to a digital platform to enhance efficiency. Although life is thus improved, security issues remain important, especially in the healthcare sector. The privacy and security of healthcare records is paramount; data leakage is socially unacceptable. Therefore, technology that protects data but does not compromise efficiency is essential. Blockchain technology has gained increasing attention as it ensures transparency, trust, privacy, and security. However, the critical factors affecting efficiency require further study. Here, we define the critical factors that affect blockchain implementation in the healthcare industry. We extracted such factors from the literature and from experts, then used interpretive structural modeling to define the interrelationships among these factors and classify them according to driving and dependence forces. This identified key drivers of the desired objectives. Regulatory clarity and governance (F2), immature technology (F3), high investment cost (F6), blockchain developers (F9), and trust among stakeholders (F12) are key factors to consider when seeking to implement blockchain technology in healthcare. Our analysis will allow managers to understand the requirements for successful implementation.
1. Introduction
Recently, blockchain (BC) technology has attracted increasing attention from industry and academia. BC technology allows users to preserve, certify, and synchronize the contents of a transaction ledger, which are available to multiple users. Transactions are decentralized; the data are not controlled by a third party. Within the system, transactions are timestamped in a ledger; data modifications/alterations are generally impossible without changing the ledger. Figure 1 shows the key components of a BC.
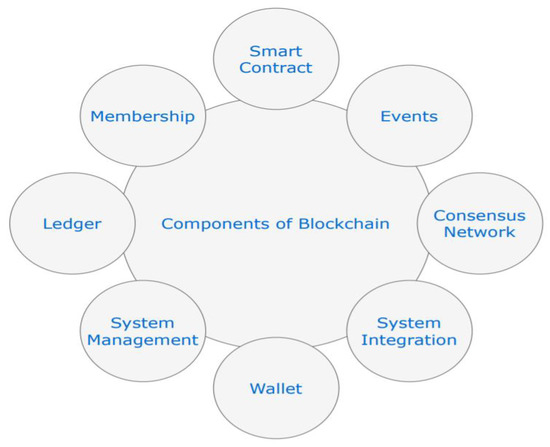
Figure 1.
Components of a BC.
BC technology ensures that trust and security are maintained during any transaction [1,2]. The healthcare, financial, and educational industries perceive the advantages afforded. Figure 2 describes the working principles of a BC.
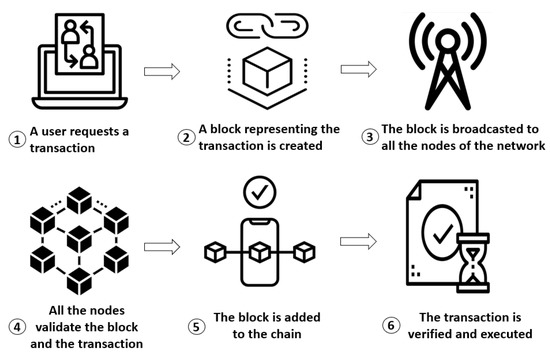
Figure 2.
Principles of a BC: a step-by-step flowchart.
As BC technology reduces fraudulent activity and protects privacy, healthcare providers would like to implement it [3]. Breaches of healthcare data are increasing rapidly; in 2017, the number of people affected exceeded 300 records; from 2010 to 2017, this number rose to 37 million records [4,5]. There are growing concerns regarding healthcare data sharing, secure data storage, and data ownership, as digitization becomes the norm [3]. A BC ensures transparency, security, and speed during data storage and distribution; it also solves the security, privacy, and integrity issues that arise in the field of healthcare technology [6,7,8,9]. A BC is decentralized, thus eliminating the accuracy and security concerns associated with dependence on a central authority. BC technology is inter-operator-based, ensuring a high standard of data exchange among healthcare associates. This boosts innovation, coordination among associates, market competition, and care quality [10,11,12,13].
In the past (when no BC was available), healthcare data interoperability among different institutions was categorized as push, pull, and view. In the push model, data transfer is possible between two providers; no third provider has access. For example, data transfer is possible between departments within the same hospital; however, data cannot be accessed by a different hospital, regardless of patient transfer to the other hospital. In the push model, it is very difficult to ensure data integrity during transfer. During a pull, one provider informally seeks data from another provider; there is no standardized audit trail. For example, an orthopedic surgeon can informally ask a cardiologist for information. During a view, one provider sees the record of another provider. For example, a surgeon can access an X-ray taken in the emergency department. The security approaches are not based on the relationship that exists between a patient and a provider; thus, they are largely ad hoc. The relevant policies are also subject to the laws of the local and federal governments.
A BC-based model for a healthcare market creates a new dimension by considering the safety of data integrity and the use of standardized formal contracts for data accession. When an electronic health record (EHR) (which stores data from multiple workers) is accessed, it is difficult to determine the identity of the person who performed a task and when the work was performed. BC timestamps all work and identify the worker; the data are also distributed to all participating nodes. If a modification or update appears in any node, this is distributed to all nodes and is thus visible systemwide. Data integrity is maintained without the need for human intervention [14]. Although BC affords many benefits, it has never been implemented in real-time healthcare. Adoption is inevitable.
Our literature review revealed only limited empirical evidence for BC use, despite its many possible benefits [15]. Very few studies have investigated the benefits, deficits, and functionalities of BC technology [16,17,18,19]. Most studies have sought to explain how BC works and to determine its current real-world implementation status [20]. However, critical factors affecting BC implementation in healthcare have not been addressed; knowledge of these factors is essential. Thus, we sought to identify these factors. Our findings can remove the confusion associated with real-time BC implementation. We offer a better understanding of the challenges imposed by implementation of BC technology in healthcare and the factors affecting such implementation. Our objectives are:
- (1)
- To identify factors that critically impact the implementation of BC technology in the healthcare industry;
- (2)
- To build a structured framework that depicts the interrelationships among such factors;
- (3)
- To define the motivation and reliance powers of such factors.
Based on past works and the opinions of experts in BC technology, we define 13 factors that greatly affect the implementation of such technology in healthcare. We used interpretive structural modeling (ISM) to explore the relationships among such factors. We performed Matrice d’Impact Croise’s Multiplication Appliquée a UN Classement (MICMAC) analysis to define the motivation and reliance powers of the factors. We sought to encourage industries that wish to implement BC technology.
The remainder of this paper is organized as follows. The literature regarding applications of BC technology in healthcare is reviewed in Section 2. Section 3 describes the methods used to achieve our research objectives. The research approach is discussed in Section 4. Managerial implications are discussed in Section 5. Practical implications are discussed in Section 6. The outcomes are summarized and conclusions are drawn in Section 7.
2. Related Works
This section is divided into two subsections. Past works regarding applications of BC in healthcare are covered in the first subsection. The second subsection discusses critical factors influencing BC implementation in healthcare.
2.1. Past Studies Regarding Applications of BC in Healthcare
BC use in healthcare scenarios has focused on smart healthcare management, user-oriented medical research, and prevention of drug counterfeiting. In terms of healthcare management, health networks allow medical experts to obtain detailed information regarding current patient status (described in the reports of physicians or healthcare centers, as well as various studies). Analysis of medical records creates an ecosystem that transparently reduces the merit costs of patient records. Moreover, medical experts can monitor the treatment activities of stakeholders, such as physicians and healthcare centers. These systems facilitate insurance claim settling if insurance companies are permitted (by patients) to access data. As healthcare records are increasingly stored digitally, security elements must be incorporated in such digital systems. Any digital platform must be scalable and adaptable, thus capable of handling large numbers of records and adaptable to many types of changes [21]. One practical solution is Live Interactive FramE (LIFE), which ensures that all media streaming in a healthcare domain are appropriately secured with minimal video quality loss during immersive applications [22].
In the context of user-oriented medical research, several authors have focused on the workings and structures of health banks; these studies have led to major breakthroughs in medical research. A company may accumulate data from wearable devices and may provide a user platform for data storage and management. The stored medical data facilitate high-quality research by trusted organizations. Patients are not financially compensated for their data.
In terms of preventing drug counterfeiting, various authors have shown that the typical counterfeiting level today ranges from approximately 10% to 30% in developed countries. Counterfeiting is not confined to lifestyle medicines or drugs; it can include drugs that treat major medical issues, such as cardiovascular diseases. Recently, the Hyperledger research network described how drug counterfeiting could be reduced by timestamping. This problem could be addressed using a BC: all data have an address based on the stored information, thereby preventing drug counterfeiting [23].
Other authors [24] identified a simple but very robust BC system for patient data storage by the healthcare sector. The system encourages the storage of all data (beginning at birth), including lipid profile data yielded by wearable devices and magnetic resonance imaging information. All information is stored in a data lake, which facilitates simple querying, advanced analytics, and machine learning. This is a simple form of data warehousing; the stored materials include documents, images, .pdf files, and key values. The BC of each user serves as an index catalog containing a unique identification number, an encrypted link to the health record stored in the lake, and a timestamp that shows all data modifications. The user enjoys robust access control and can allow or restrict access using an audit log that shows every visit to the data repository. Such systems will greatly aid medical professionals (ranging from students to doctors) and governmental agencies. The data shared from the lake are tagged with the unique patient identification numbers, are up-to-date and accurate, and can be used for longitudinal healthcare research.
Electronic records contain data from wearable devices, medical records, and/or medical imaging; all are private. Cloud storage in a central regulatory database may be associated with data leakage; unauthorized data transfer can be avoided by enabling a BC architecture wherein a user or a patient has full control over data access by third parties (expert consultants or medical researchers). BC use in healthcare will aid in the development of a consensus system that verifies the appropriateness of prescribed medication [25].
As healthcare data are very sensitive, the type of BC to be used is critical. One report [26] discussed the various types of BC available, their bases, and their uses in terms of maintenance, validation, and storage of medical data. Out-of-the-box consortium BCs were considered optimal; both the node owner and miners control access. A consensus can be determined regarding the optimal number of validations imparted by a healthcare provider, a clinic, or an insurance company; the stored data are thus very accurate.
Although BC implementation in the healthcare sector is vital, this has not yet happened. It is essential to define factors that would aid implementation. This is the topic of the next subsection.
2.2. Crucial Factors Affecting Implementation of BC in Healthcare
Here, we review works regarding crucial factors that affect BC implementation in healthcare. Ekblaw et al. [14] regarded data security and privacy assurance as a major concern. Although BC data are safely stored, Shi et al. [27] presumed that healthcare data in a public database would be vulnerable to statistical attack. Thus, frequent encryption key changes would be required, increasing key storage costs. To address this problem, Zhao et al. [28] developed a smart key recovery scheme based on a body sensor network. In this system, there is no need for a stored encryption key. If a key must be recovered, it is retrieved by the body sensor network.
Khan et al. [29] stated that medical data interoperability was another key barrier; medical data must be communicated, shared, and used by employing various information communication technologies. Although creation of data interoperability has been discussed by several authors [11,30], its implementation remains a major concern.
Agarwal and Prabakaran [31] presumed that data fragmentation could compromise EHRs. Thus, there is a need to meticulously maintain EHRs [32]. Errors compromise diagnosis and patient safety [33]. Data unavailability is unacceptable, thus posing a problem when implementing BC technology. The compatibility of existing information with BC technology is also critical; incompatibility reduces system performance. Incompatible information technology interfaces [23] greatly slow the system. The deployment and maintenance of dedicated technology are essential components [34].
Regulation plays a major role in healthcare; lives are at stake [1]. Schwerin [35] questioned the compatibility of BC with general data protection regulations. BC must protect consumer rights according to law [36]. Trust is a critical consideration when using BC; data are decentralized, transparent, and uploaded [37]. Illegal bitcoin activities have compromised trust in the technology [38]. However, in the healthcare sector, the technology can never be completely trusted due to the demand for healthcare data privacy [39,40,41,42]. Regulators have stated that a key issue preventing large-scale implementation of BC technology is the lack of standardization. Only a few well-known infrastructures are available [38]. Different countries seek to apply BC in various manners. For example, Estonia wishes to use BC to award e-residency to new citizens [43]. Other countries seek to use BC for transparent taxation and other social needs [44]. Standardization is urgently required [45].
The creativity and intricacy of BC increase adoption costs. Furthermore, there are few service providers, which leads to increasing costs [38]. As BC implementation reduces transaction costs [46], the initial costs may be worthwhile. However, the technology may not be suitable for small- and medium-size industries that lack workers with skills to manage the system [38]. There is a need for more skilled operators.
BC became well-known due to bitcoin, but disagreements are increasing in the bitcoin community due to frequent code forking, supporting the notion that the technology is immature [47]. Many technical limitations remain [38].
Scalability is essential for robust system performance. In its present form, the network of a public BC is comparatively expensive and slow and thus difficult to adopt at a large scale. However, new scaling techniques such as plasma chains, lightning networks, zk-snarks, and state channels enhance performance and scalability (both in and out of the healthcare context) [1].
Although BC is newer than the Internet of Things (IoT), cloud computing, and artificial intelligence (AI), the IoT exhibits many security issues. BC has greatly improved IoT applications, restoring trust [48]. The use of AI in healthcare affords excellent accuracy and precision, facilitating rapid decision-making. In the current coronavirus disease 2019 era, AI-based decisions categorize patients within a few minutes, greatly aiding clinicians. However, privacy remains important; patients fear that their data may be misplaced during AI analysis in the cloud. Prior to BC, cloud security was enhanced using specific applications [49,50,51]. After BC integration, data can be stored securely. As each transaction is recorded, patients can easily identify where the data are used. All involved groups experience benefits [52]. The integration of BC into the cloud resolves issues regarding location-based storage and analysis, while guaranteeing security [53]. BC must be integrated with more recent cutting-edge technologies. All industries accept that modern technology will render them smarter, but safety concerns remain. BC is already safe; the addition of other technologies can render it safer, faster, energy-saving, and cheaper [54,55,56].
3. Solutions
We first identified critical factors affecting BC introduction; we reviewed past works and sought 15 expert opinions (inputs to structured self-interaction matrices (SSIMs)). These opinions were collected during a workshop concerning digital technology in the healthcare sector held at KIIT University, Bhubaneswar, India, in 2020. The 15 experts included nine senior medical practitioners with at least 10 years of experience in reputable hospitals with digital platforms hosting patient records and managing medicine supplies, as well as six academics with at least 10 years of research experience in BC (all academics were at or above professor/associate professor level in their medical colleges/universities). There was no limit on the number of experts that had completed S exploring remanufacturing and green campus operations (Singhal et al., 2020 [57], Gholami et al., 2020 [58]); 10 had completed SIMs concerning researcher selection (Nilashi et al., 2019 [59]). Our 15 experts were thus adequate. Next, ISM was used to develop a baseline model of associations among critical factors, and MICMAC analysis was performed to group the factors. ISM seeks to determine relationships among factors identified through literature review or expert opinion as an issue or a problem (Jharkharia and Shankar 2005 [60], Ravi and Shankar 2005 [61], Raj and Attri 2011 [62]). ISM techniques include brainstorming, nominal group techniques, and face-to-face interviews, yielding expert views regarding how to develop a contextual relationship among selected key factors (Ravi et al., 2005 [63], Barve et al., 2007 [64], Hasan et al., 2007 [65], Raj et al., 2007 [66]). Here, we addressed the complex barriers to BC implementation in healthcare. Factors determined through a literature review were reviewed by experts. No limit was imposed on the number of factors (Singhal et al., 2020 [57], Nayak et al., 2019 [67]). Table 1 lists the 13 factors identified and Table 2 lists the ISM steps. The flowchart of the solution (i.e., research framework and sequential steps) is shown in Figure 3. The critical dimensions of BC in healthcare commences with SIM completion and concludes with MICMAC policy recommendations. A strong correlation is evident between the ISM model and the critical factors identified.

Table 1.
Numbers of factors evaluated in various reports.

Table 2.
ISM steps.
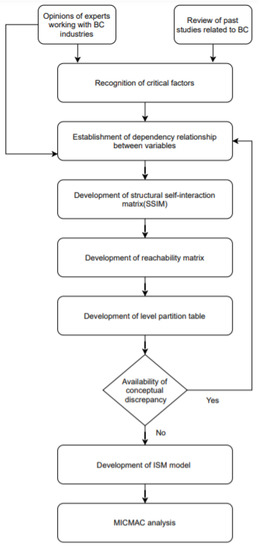
Figure 3.
Flowchart of solution methodology.
3.1. Data Collection
We reviewed all BC papers in Web of Science and Scopus in terms of critical factors influencing the adoption of BC in healthcare. With assistance from experts, we selected the 13 factors listed in Table 3.

Table 3.
Factors affecting the implementation of BC in healthcare.
3.2. ISM
ISM is old and widely used by researchers in knowledge management, energy conservation, supplier selection, and green supply chain management; it is also used by strategic decisionmakers in various organizations [72,73,74]. ISM seeks to recognize/construct associations between factors affecting decision-making when a particular problem arises, then to solve the problem by considering the driving and dependency powers of each factor [75]. The framework features associations among factors, as identified by experts [76]. Fewer experts are required, compared with structural equation modeling or the Delphi method. ISM nonetheless builds models that solve decision-making problems [77,78]. Table 4 lists the various applications of ISM. Modeling proceeds as follows: (1) recognition of relevant factors based on past studies and expert opinion; (2) development of an SSIM and then a reachability matrix; (3) creation of a partition level table using a reachability matrix; (4) characterization of relationships among various factors; and (5) identification of uncertainties and consequent modifications.

Table 4.
Applications of ISM.
3.2.1. The SSIM
The SSIMs completed by experts served as the ISM inputs. The contextual relationships among the 13 factors were determined by the majority opinions of the 15 experts expressed in a brainstorming session conducted during a 2020 workshop. The contextual relationships were finalized after considering the nature of each problem, the objective, and the majority opinion concerning the relationships between factors. The contextual association between two elements (i and j) is represented in one of four manners: (a) if i influences j, this is represented by “V”; (b) if j influences i, this is represented by “A”; (c) if i and j influence each other, this is represented by “X”; and (d) if i and j are independent, this is represented by “O”. For example, the interoperability of electronic health records F10 (IEH) influences the BC developers F9 (BD); the symbol used is V. Compatibility with other IT systems F5 (CIT) influences high investment cost F6 (HIC); the symbol used is A. The interoperability of electronic health records F10 (IEH) and privacy and security of storage data F7 (PSD) interact; the symbol used is X. Scalability and accessibility F8 (SA) has no relationship with data unavailability F1 (DU); the symbol used is O. The SSIM summary is presented in Table 5. The reachability matrix associated with the SSIMs is addressed below.

Table 5.
SSIM summary.
3.2.2. Reachability Matrix
The four SSIM representations, V, A, X, and O, were replaced by 1 or 0 in a reachability matrix, as follows: (a) the symbol “V” in the (i, j) position of the SSIM matrix is substituted by 1 and 0 in the (i, j) and (j, i) positions of the reachability matrix; (b) the symbol “A” in the (i, j) position of the SSIM matrix is substituted by 0 and 1 in the (i, j) and (j, i) positions of the reachability matrix; (c) the symbol “X” in the (i, j) position of the SSIM matrix is substituted by 1 in both the (i, j) and (j, i) positions of the reachability matrix; and (d) the symbol “O” in the (i, j) position in the SSIM matrix is substituted by 0 in both the (i, j) and (j, i) positions of the reachability matrix. Next, the transitivity of the reachability matrix was checked. Transitivity means that if factor F1 influences F2 and F2 influences F3, then F1 impacts F3. If the position (i, j) of F1 impacts F3, the value becomes 1. The driving power (DVP) of a factor is calculated by adding all values in the accommodating row and the dependence power (DNP) is calculated by adding all values in the accommodating column. After considering transitivity, the final version of the reachability matrix is shown in Table 6. The subsequent step (i.e., partition of different levels) uses the reachability matrix.

Table 6.
Reachability matrix.
3.2.3. Level Partition
The antecedent and reachability sets for each element were developed based on the reachability matrix [83]. The reachability set contains the factors themselves and factors impacted by other factors, and the antecedent set consists of the factors themselves and factors impacting those factors. The intersection set is the group of elements common to the antecedent and reachability sets. The procedure was iterated; when the antecedent and reachability sets were equal, the top factor was identified. For example, level I is occupied by F13 due to the equality of the antecedent and reachability sets. Five iterations were performed when identifying the level of a factor. The level partition is shown in Table 7. All 13 factors are split into six levels. F2 occupies the sixth level and F13 occupies the first level; the other factors lie between these levels.

Table 7.
Level partition.
3.2.4. ISM
The ISM of Figure 4 was developed based on the digraph and level partition table. A digraph exemplifies the interrelationships among elements at edges and nodes. Digraphs remove the transitive relationships between elements. The ISM is extracted from the combinative information of the digraph [84].
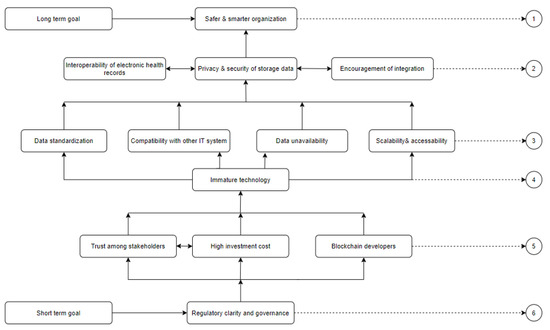
Figure 4.
The ISM.
3.3. MICMAC Analysis
MICMAC requires factor dependence and driving powers as inputs [85] and then categorizes the factors into four types (Figure 5). Autonomous variables (factors with weak dependence and driving powers) are shown in the first quadrant. Dependent variables (factors with strong dependence but weak driving powers) are shown in the second quadrant. Linkage variables (factors with strong dependence and driving powers) are shown in the third quadrant. Driving variables (factors with weak dependence powers but strong driving powers) appear in the fourth quadrant [66].
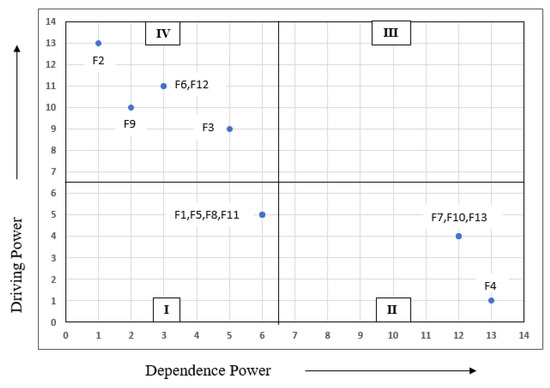
Figure 5.
MICMAC analysis.
4. Results and Discussion
We systematically analyzed and constructed the relationships among factors affecting the adoption of BC in healthcare. We derived factor dependence and driving powers through MICMAC analysis. We first identified 13 critical factors affecting the adoption of BC in healthcare (Table 1). Experts from academia and industry chose these factors. We used ISM to construct the model. The ISM split all factors into six levels. Regulatory clarity and governance (F2) (at the bottom of the hierarchy) was the key driver of BC adoption in healthcare. Daluwathumullagamage and Sims found that BC would ensure better corporate governance if development was accompanied by changes in regulatory frameworks [86]. Healthcare industries must encourage governments to regulate appropriately; BC use is essential. Level IV included trust among stakeholders (F12), high investment cost (F6), and BC developers (F9); all were strong drivers of adoption. Senior healthcare managers must enthusiastically adopt BC and consumers must understand the great benefits afforded by BC use. Gomez-Trujillo et al. emphasized that BC guarantees trust and transparency; if all individuals, industries, and other stakeholders maintain confidence in BC, long-term success is ensured [87]. Koster and Borgman found that BC adoption required the support of senior authorities and trust among partners [88]. Level IV contained only immature technology (F3), which strongly influenced BC adoption. BC is new, not standardized, and has seldom been implemented in governmental agencies. Compatibility issues affecting performance may arise [48,89]. Level III included data standardization (F11), compatibility with other IT systems (F5), data unavailability (F1), and scalability and accessibility (SA); all strongly influenced BC adoption. The technology remains immature, and therefore the above factors must all be upgraded to enhance performance in the healthcare sector [90]. Level II comprises interoperability of electronic health records (F10), privacy and security of storage (F7), and encouragement of integration (F13); all dynamically influence adoption. Finally, the factor at level I is affected by all other factors and thus exhibits the highest dependence power. Encouragement of integration is the key driver; BC can be combined with many cutting-edge technologies that render organizations more efficient and smarter [51,52,53]. Secure data storage makes organizations safer; this is one of our long-term healthcare objectives.
After MICMAC analysis, quadrant 4 hosted five factors with strong driving powers and quadrant 2 hosted four factors with strong dependence powers. Quadrant 3 was empty; there was no linkage variable. Quadrant 1 hosted four autonomous variables. Dependent variables comprised privacy and security of storage data (F7), interoperability of EHRs (F10), encouragement of integration (F13), and safer and smarter organizations (F4). MICMAC analysis revealed that regulatory clarity and governance (F2), immature technology (F3), high investment cost (F6), BC developers (F9), and trust among stakeholders (F12) exhibited strong driving powers and were thus the most important factors in terms of BC adoption in healthcare. Data unavailability (F1), compatibility with other IT systems (F5), scalability and accessibility (F8), and data standardization (F11) (autonomous variables) exhibited weaker dependences and driver powers, suggesting that they were less important than other factors. However, all identified factors affect the adoption of BC in healthcare.
We shared our analysis with stakeholders in healthcare industries. Surprisingly, many managers were unaware of many factors. We hope that our analysis will help them to prepare for successful BC adoption.
5. Managerial Implications
Our work will allow regulators, policymakers, governments, healthcare industrialists, and consumers to recognize the critical factors that affect BC incorporation in healthcare. Managers and decisionmakers should focus on the inputs and outputs of the ISM model. The inputs were based on a literature review and expert opinions. The outputs identify the interdependencies and the short- and long-term importances of various factors. The model will be implemented and tested in a cross-sectional manner in multiple industries.
Managers will be interested in the outcomes; they should prepare the resources for successful implementation. Managers must offer staff workshops and training regarding BC and its benefits. Existing educational institutes and special training schools may be involved. Managers must be careful when sharing information; a competitive advantage must not be lost. Petersson and Baur [91] emphasized that an organization is not required to reorganize its business model during BC integration. Furthermore, BC is possible in a traditional system; a new system is unnecessary. During organizational preparation, knowledge of the technical aspects will be helpful.
All organizations must now adopt cutting-edge BC technology. Its basic features include smart contracts, privacy, and data security; it is easy to switch to new (improved) future platforms. Existing open-source platforms are expensive if they are expected to serve as proprietorial infrastructure [92]. Organizations should implement BC technology immediately; the “wait-and-see” period is over. Early acceptance of the technology will afford competitive advantages [93].
6. Practical Implications
Healthcare decisionmakers must implement BC to protect the privacy of healthcare data. Such privacy supports the implementation of AI and federated learning, which enhance organizational efficiency. Kumar et al. [52] used BC technology for data authentication, allowing efficient use of AI and federated learning. In the era of coronavirus disease 2019, cutting-edge AI can rapidly identify an infection and is applicable worldwide; this could be combined with BC technology. With increasing data digitization, the need for privacy increases, along with the desire for societal betterment. BC technology can serve as the foundation of the required systems.
7. Conclusions
In our digital age, it is essential to protect healthcare data, but appropriate technology is lacking. BC technology can achieve the desired objectives. AI and federated learning enhance efficiency. BC systems would improve greatly if organizations were to successfully implement the technology. Large organizations (e.g., NVIDIA) have commenced research regarding AI and federated learning, motivated by societal betterment.
Here, we recognized 13 factors that influence successful BC implementation in the healthcare industry. We used ISM to divide these 13 factors into six levels. An inappropriate regulatory environment greatly hinders BC adoption in the healthcare industry. Firms are reluctant to adopt this intricate and immature technology. Compatibility, investment cost, and security concerns are equally important. Our work has the following strengths. First, no similar formal study has appeared. Second, we have highlighted the key obstacles hindering the implementation of BC technology and have proposed methods to eliminate them. We offer useful tips for specialists in cutting-edge technology. BC will greatly advance organization in our digital era. Nonetheless, this study had the following limitations. First, we evaluated only a few critical factors emphasized in the literature. Second, as this technology is emerging, there are few skilled experts; we canvassed only 15.
In the future, we plan to validate the results obtained after implementing BC technology and to combine the findings with AI and federated learning to create a useful, real-time generalized model. As previously suggested, and as reinforced by current demand, reliable security solutions must be integrated into all digital platforms and must be capable of adaptation to new environments [94,95]. We will seek BC technology that is secure across all applications. We will share the corresponding implementations in future articles. We will also perform cross-sectional studies to identify factors that can enhance the impact (i.e., strength) of BC implementation. Finally, we suggest that others could implement our approach in their diverse sectors by combining longitudinal and cross-sectional studies. We hope that our work may serve as a reference. It should be shared and may aid other industries.
Author Contributions
Conceptualization, S.A. and S.T.; methodology, S.A. and S.T.; validation, S.A., M.-I.J. and H.-C.K.; formal analysis, S.A., M.-I.J. and H.-C.K.; data curation, S.A. and S.T.; writing—original draft preparation, S.A.; writing—review and editing, S.A. and S.T.; supervision, H.-C.K.; project administration, H.-C.K.; funding acquisition, H.-C.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF), supported by the Ministry of Science, ICT & Future Planning (NRF2017R1D1A3B04032905).
Informed Consent Statement
All the participants gave their consent to participate in this study.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Katuwal, G.J.; Pandey, S.; Hennessey, M.; Lamichhane, B. Applications of blockchain in healthcare: Current landscape & challenges. arXiv 2018, arXiv:1812.02776. [Google Scholar]
- Zhang, P.; Schmidt, D.C.; White, J.; Lenz, G. Blockchain technology use cases in healthcare. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2018; Volume 111, pp. 1–41. [Google Scholar]
- Meinert, E.; Alturkistani, A.; Foley, K.A.; Osama, T.; Car, J.; Majeed, A.; Van Velthoven, M.; Wells, G.; Brindley, D. Blockchain implementation in health care: Protocol for a systematic review. JMIR Res. Protoc. 2019, 8, e10994. [Google Scholar] [CrossRef]
- Talesh, S.A. Data breach, privacy, and cyber insurance: How insurance companies act as “compliance managers” for businesses. Law Soc. Inq. 2018, 43, 417–440. [Google Scholar] [CrossRef]
- McCoy, T.H.; Perlis, R.H. Temporal trends and characteristics of reportable health data breaches, 2010–2017. JAMA 2018, 320, 1282–1284. [Google Scholar] [CrossRef] [PubMed]
- Yaeger, K.; Martini, M.; Rasouli, J.; Costa, A. Emerging blockchain technology solutions for modern healthcare infrastructure. J. Sci. Innov. Med. 2019, 2. [Google Scholar] [CrossRef]
- Khezr, S.; Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain technology in healthcare: A comprehensive review and directions for future research. Appl. Sci. 2019, 9, 1736. [Google Scholar] [CrossRef]
- McGhin, T.; Choo, K.K.R.; Liu, C.Z.; He, D. Blockchain in healthcare applications: Research challenges and opportunities. J. Netw. Comput. Appl. 2019, 135, 62–75. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Park, J.H.; Park, J.H. Blockchain security in cloud computing: Use cases, challenges, and solutions. Symmetry 2017, 9, 164. [Google Scholar] [CrossRef]
- Zhang, P.; Walker, M.A.; White, J.; Schmidt, D.C.; Lenz, G. Metrics for assessing blockchain-based healthcare decentralized apps. In Proceedings of the 2017 IEEE 19th International Conference on e-Health Networking, Applications and Services (Healthcom), Dalian, China, 12–15 October 2017; pp. 1–4. [Google Scholar]
- Ahram, T.; Sargolzaei, A.; Sargolzaei, S.; Daniels, J.; Amaba, B. Blockchain technology innovations. In Proceedings of the 2017 IEEE Technology & Engineering Management Conference (TEMSCON), Santa Clara, CA, USA, 8–10 June 2017; pp. 137–141. [Google Scholar]
- Kuo, T.T.; Zavaleta Rojas, H.; Ohno-Machado, L. Comparison of blockchain platforms: A systematic review and healthcare examples. J. Am. Med. Inform. Assoc. 2019, 26, 462–478. [Google Scholar] [CrossRef]
- Ekblaw, A.; Azaria, A.; Halamka, J.D.; Lippman, A. A Case Study for Blockchain in Healthcare: “MedRec” prototype for electronic health records and medical research data. In Proceedings of the IEEE Open & Big Data Conference, Vienna, Austria, 22–24 August 2016; Volume 13, p. 13. [Google Scholar]
- Batubara, F.R.; Ubacht, J.; Janssen, M. Challenges of blockchain technology adoption for e-government: A systematic literature review. In Proceedings of the 19th Annual International Conference on Digital Government Research: Governance in the Data Age, Delft, The Netherlands, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Ali, O.; Ally, M.; Dwivedi, Y. The state of play of blockchain technology in the financial services sector: A systematic literature review. Int. J. Inf. Manag. 2020, 54, 102199. [Google Scholar] [CrossRef]
- Alketbi, A.; Nasir, Q.; Talib, M.A. Blockchain for government services—Use cases, security benefits and challenges. In Proceedings of the 2018 15th Learning and Technology Conference (L&T), Jeddah, Saudi Arabia, 25–26 February 2018; pp. 112–119. [Google Scholar]
- Lindman, J.; Rossi, M.; Tuunainen, V.K. Opportunities and risks of blockchain technologies in payments—A research agenda. In Proceedings of the 50th Hawaii International Conference on System Sciences, Hilton Waikoloa Village, HI, USA, 4–7 January 2017; pp. 1533–1542. [Google Scholar]
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Tama, B.A.; Kweka, B.J.; Park, Y.; Rhee, K.H. A critical review of blockchain and its current applications. In Proceedings of the 2017 International Conference on Electrical Engineering and Computer Science (ICECOS), Palembang, Indonesia, 22–23 August 2017; pp. 109–113. [Google Scholar]
- Antón, P.; Munoz, A.; Mana, A.; Koshutanski, H. Security-enhanced ambient assisted living supporting school activities during hospitalisation. J. Ambient Intell. Humaniz. Comput. 2012, 3, 177–192. [Google Scholar] [CrossRef]
- Antón, P.; Maña, A.; Muñoz, A.; Koshutanski, H. An immersive view approach by secure interactive multimedia proof-of-concept implementation. Multimed. Tools Appl. 2015, 74, 8401–8420. [Google Scholar] [CrossRef]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on E-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; pp. 1–3. [Google Scholar]
- Linn, L.A.; Koo, M.B. Blockchain for health data and its potential use in health it and health care related research. In ONC/NIST Use of Blockchain for Healthcare and Research Workshop. Gaithersburg, Maryland, United States: ONC/NIST; NIST: Gaithersburg, MD, USA, 2016; pp. 1–10. [Google Scholar]
- Joshi, A.P.; Han, M.; Wang, Y. A survey on security and privacy issues of blockchain technology. Math. Found. Comput. 2018, 1, 121. [Google Scholar] [CrossRef]
- Alhadhrami, Z.; Alghfeli, S.; Alghfeli, M.; Abedlla, J.A.; Shuaib, K. Introducing blockchains for healthcare. In Proceedings of the 2017 International Conference on Electrical and Computing Technologies and Applications (ICECTA), Ras Al Khaimah, United Arab Emirates, 21–23 November 2017; pp. 1–4. [Google Scholar]
- Shi, S.; He, D.; Li, L.; Kumar, N.; Khan, M.K.; Choo, K.K.R. Applications of blockchain in ensuring the security and privacy of electronic health record systems: A survey. Comput. Secur. 2020, 97, 101966. [Google Scholar] [CrossRef] [PubMed]
- Zhao, H.; Zhang, Y.; Peng, Y.; Xu, R. Lightweight backup and efficient recovery scheme for health blockchain keys. In Proceedings of the 2017 IEEE 13th International Symposium on Autonomous Decentralized System (ISADS), Bangkok, Thailand, 22–24 March 2017; pp. 229–234. [Google Scholar]
- Khan, F.A.; Asif, M.; Ahmad, A.; Alharbi, M.; Aljuaid, H. Blockchain technology, improvement suggestions, security challenges on smart grid and its application in healthcare for sustainable development. Sustain. Cities Soc. 2020, 55, 102018. [Google Scholar] [CrossRef]
- Zhang, P.; White, J.; Schmidt, D.C.; Lenz, G. Applying software patterns to address interoperability in blockchain-based healthcare apps. arXiv 2017, arXiv:1706.03700. [Google Scholar]
- Agrawal, R.; Prabakaran, S. Big data in digital healthcare: Lessons learnt and recommendations for general practice. Heredity 2020, 124, 525–534. [Google Scholar] [CrossRef]
- Kruse, C.S.; Kothman, K.; Anerobi, K.; Abanaka, L. Adoption factors of the electronic health record: A systematic review. JMIR Med. Inform. 2016, 4, e19. [Google Scholar] [CrossRef]
- Tanner, C.; Gans, D.; White, J.; Nath, R.; Pohl, J. Electronic health records and patient safety: Co-occurrence of early EHR implementation with patient safety practices in primary care settings. Appl. Clin. Inform. 2015, 6, 136. [Google Scholar]
- Randall, D.; Goel, P.; Abujamra, R. Blockchain applications and use cases in health information technology. J. Health Med. Inform. 2017, 8, 8–11. [Google Scholar] [CrossRef]
- Schwerin, S. Blockchain and privacy protection in the case of the european general data protection regulation (GDPR): A delphi study. J. Br. Blockchain Assoc. 2018, 1, 3554. [Google Scholar] [CrossRef]
- Abramova, S.; Böhme, R. Perceived Benefit and Risk as Multidimensional Determinants of Bitcoin Use: A Quantitative Exploratory Study; ICIS: Dublin, Ireland, 2016. [Google Scholar]
- Sas, C.; Khairuddin, I.E. Design for trust: An exploration of the challenges and opportunities of bitcoin users. In Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems, Denver, CO, USA, 6–11 May 2017; pp. 6499–6510. [Google Scholar]
- Sadhya, V.; Sadhya, H. Barriers to Adoption of Blockchain Technology. Available online: https://aisel.aisnet.org/amcis2018/AdoptionDiff/Presentations/20/ (accessed on 27 February 2021).
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Yaqoob, S.; Khan, M.M.; Talib, R.; Butt, A.D.; Saleem, S.; Arif, F.; Nadeem, A. Use of blockchain in healthcare: A systematic literature review. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 644–653. [Google Scholar] [CrossRef]
- Esmaeilzadeh, P.; Mirzaei, T. The potential of blockchain technology for health information exchange: Experimental study from patients’ perspectives. J. Med. Internet Res. 2019, 21, e14184. [Google Scholar] [CrossRef]
- Pandey, P.; Litoriya, R. Implementing healthcare services on a large scale: Challenges and remedies based on blockchain technology. Health Policy Technol. 2020, 9, 69–78. [Google Scholar] [CrossRef]
- Sullivan, C.; Burger, E. E-residency and blockchain. Comput. Law Secur. Rev. 2017, 33, 470–481. [Google Scholar] [CrossRef]
- Pokrovskaia, N.N. Tax, financial and social regulatory mechanisms within the knowledge-driven economy. Blockchain algorithms and fog computing for the efficient regulation. In Proceedings of the 2017 XX IEEE International Conference on Soft Computing and Measurements (SCM), IEEE, St. Petersburg, Russia, 24–26 May 2017; pp. 709–712. [Google Scholar]
- Ølnes, S.; Ubacht, J.; Janssen, M. Blockchain in government: Benefits and implications of distributed ledger technology for information sharing. Gov. Inf. Q. 2017, 34, 355–364. [Google Scholar] [CrossRef]
- Thakre, A.; Thabtah, F.; Shahamiri, S.R.; Hammoud, S. A novel block chain technology publication model proposal. Appl. Comput. Inform. 2019. [Google Scholar] [CrossRef]
- Andersen, J.V.; Bogusz, C.I. Patterns of Self-Organising in the Bitcoin Online Community: Code Forking as Organising in Digital Infrastructure. In Proceedings of the International Conference on Information Systems (ICIS 2017), Seoul, Korea, 10–13 December 2017. [Google Scholar]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Waller, A.; Sandy, I.; Power, E.; Aivaloglou, E.; Skianis, C.; Muñoz, A.; Maña, A. Policy based management for security in cloud computing. In FTRA International Conference on Secure and Trust Computing, Data Management, and Application; Springer: Berlin/Heidelberg, Germany, 2011; pp. 130–137. [Google Scholar]
- Muñoz, A.; Maña, A.; González, J. Dynamic Security Properties Monitoring Architecture for Cloud Computing. In Security Engineering for Cloud Computing: Approaches and Tools; IGI Global: Hershey, PA, USA, 2013; pp. 1–18. [Google Scholar]
- Muñoz, A.; Gonzalez, J.; Maña, A. A performance-oriented monitoring system for security properties in cloud computing applications. Comput. J. 2012, 55, 979–994. [Google Scholar] [CrossRef]
- Kumar, R.; Khan, A.A.; Zhang, S.; Wang, W.; Abuidris, Y.; Amin, W.; Kumar, J. Blockchain-federated-learning and deep learning models for covid-19 detection using ct imaging. arXiv 2020, arXiv:2007.06537. [Google Scholar]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Integration of blockchain and cloud of things: Architecture, applications and challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2521–2549. [Google Scholar] [CrossRef]
- Kshetri, N. Blockchain’s roles in strengthening cybersecurity and protecting privacy. Telecommun. Policy 2017, 41, 1027–1038. [Google Scholar] [CrossRef]
- Sun, M.; Zhang, J. Research on the application of block chain big data platform in the construction of new smart city for low carbon emission and green environment. Comput. Commun. 2020, 149, 332–342. [Google Scholar] [CrossRef]
- Shen, C.; Pena-Mora, F. Blockchain for cities—a systematic literature review. IEEE Access 2018, 6, 76787–76819. [Google Scholar] [CrossRef]
- Singhal, D.; Tripathy, S.; Jena, S.K. Remanufacturing for the circular economy: Study and evaluation of critical factors. Resour. Conserv. Recycl. 2020, 156, 104681. [Google Scholar] [CrossRef]
- Gholami, H.; Bachok, M.F.; Saman, M.Z.M.; Streimikiene, D.; Sharif, S.; Zakuan, N. An ISM Approach for the Barrier Analysis in Implementing Green Campus Operations: Towards Higher Education Sustainability. Sustainability 2020, 12, 363. [Google Scholar] [CrossRef]
- Nilashi, M.; Dalvi, M.; Ibrahim, O.; Zamani, M.; Ramayah, T. An interpretive structural modelling of the features influencing researchers’ selection of reference management software. J. Librariansh. Inf. Sci. 2019, 51, 34–46. [Google Scholar] [CrossRef]
- Jharkharia, S.; Shankar, R. IT-enablement of supply chains: Understanding the barriers. J. Enterp. Inf. Manag. 2005, 18, 11–27. [Google Scholar] [CrossRef]
- Ravi, V.; Shankar, R. Analysis of interactions among the barriers of reverse logistics. Technol. Forecast. Soc. Chang. 2005, 72, 1011–1029. [Google Scholar] [CrossRef]
- Raj, T.; Attri, R. Identification and modelling of barriers in the implementation of TQM. Int. J. Product. Qual. Manag. 2011, 8, 153–179. [Google Scholar] [CrossRef]
- Ravi, V.; Shankar, R.; Tiwari, M.K. Productivity improvement of a computer hardware supply chain. Int. J. Product. Perform. Manag. 2005, 54, 239–255. [Google Scholar] [CrossRef]
- Barve, A.; Kanda, A.; Shankar, R. Analysis of interaction among the barriers of third party logistics. Int. J. Agil. Syst. Manag. 2007, 2, 109–129. [Google Scholar] [CrossRef]
- Hasan, M.A.; Shankar, R.; Sarkis, J. A study of barriers to agile manufacturing. Int. J. Agil. Syst. Manag. 2007, 2, 1–22. [Google Scholar] [CrossRef]
- Raj, T.; Shankar, R.; Suhaib, M. An ISM approach for modelling the enablers of flexible manufacturing system: The case for India. Int. J. Prod. Res. 2008, 46, 6883–6912. [Google Scholar] [CrossRef]
- Nayak, S.; Tripathy, S.; Dash, A. Non-technical skill development strategy to enhance safety performance of railway system: An interpretive structural modelling approach. Int. J. Bus. Excell. 2019, 19, 168–188. [Google Scholar] [CrossRef]
- Ahmad, M.; Tang, X.W.; Qiu, J.N.; Ahmad, F. Interpretive structural modeling and MICMAC analysis for identifying and benchmarking significant factors of seismic soil liquefaction. Appl. Sci. 2019, 9, 233. [Google Scholar] [CrossRef]
- Nayak, S.; Tripathy, S.; Dash, A. Role of non technical skill in human factor engineering: A crucial safety issue in Indian Railway. Int. J. Syst. Assur. Eng. Manag. 2018, 9, 1120–1136. [Google Scholar] [CrossRef]
- Aich, S.; Tripathy, S. An interpretive structural model of green supply chain management in Indian computer and its peripheral industries. Int. J. Procure. Manag. 2014, 7, 239–256. [Google Scholar] [CrossRef]
- Tripathy, S.; Sahu, S.; Ray, P.K. Interpretive structural modelling for critical success factors of R&D performance in Indian manufacturing firms. J. Model. Manag. 2013, 8, 212–240. [Google Scholar]
- Lim, M.K.; Tseng, M.L.; Tan, K.H.; Bui, T.D. Knowledge management in sustainable supply chain management: Improving performance through an interpretive structural modelling approach. J. Clean. Prod. 2017, 162, 806–816. [Google Scholar] [CrossRef]
- Saxena, J.P.; Vrat, P. Scenario building: A critical study of energy conservation in the Indian cement industry. Technol. Forecast. Soc. Chang. 1992, 41, 121–146. [Google Scholar] [CrossRef]
- Girubha, J.; Vinodh, S.; Vimal, K.E.K. Application of interpretative structural modelling integrated multi criteria decision making methods for sustainable supplier selection. J. Model. Manag. 2016, 11, 358–388. [Google Scholar] [CrossRef]
- Diabat, A.; Govindan, K. An analysis of the drivers affecting the implementation of green supply chain management. Resour. Conserv. Recycl. 2011, 55, 659–667. [Google Scholar] [CrossRef]
- Mangla, S.K.; Luthra, S.; Mishra, N.; Singh, A.; Rana, N.P.; Dora, M.; Dwivedi, Y. Barriers to effective circular supply chain management in a developing country context. Prod. Plan. Control 2018, 29, 551–569. [Google Scholar] [CrossRef]
- Chakraborty, K.; Mondal, S.; Mukherjee, K. Critical analysis of enablers and barriers in extension of useful life of automotive products through remanufacturing. J. Clean. Prod. 2019, 227, 1117–1135. [Google Scholar]
- Kim, Y.; Park, Y.; Song, G. Interpretive Structural Modeling in the Adoption of IoT Services. KSII Trans. Internet Inf. Syst. 2019, 13. [Google Scholar] [CrossRef]
- Rana, N.P.; Dwivedi, Y.K.; Hughes, D.L. Analysis of Challenges for Blockchain Adoption within the Indian Public Sector: An Interpretive Structural Modelling Approach. Inf. Technol. People 2021. [Google Scholar] [CrossRef]
- Sharma, M.G.; Kumar, S. The Implication of Blockchain as a Disruptive Technology for Construction Industry. IIM Kozhikode Soc. Manag. Rev. 2020, 9, 177–188. [Google Scholar] [CrossRef]
- Kamble, S.S.; Gunasekaran, A.; Sharma, R. Modeling the blockchain enabled traceability in agriculture supply chain. Int. J. Inf. Manag. 2020, 52, 101967. [Google Scholar] [CrossRef]
- Patri, R.; Suresh, M. Factors influencing lean implementation in healthcare organizations: An ISM approach. Int. J. Healthc. Manag. 2018, 11, 25–37. [Google Scholar] [CrossRef]
- Bhosale, V.A.; Kant, R. An integrated ISM fuzzy MICMAC approach for modelling the supply chain knowledge flow enablers. Int. J. Prod. Res. 2016, 54, 7374–7399. [Google Scholar] [CrossRef]
- Sushil, S. Interpreting the interpretive structural model. Glob. J. Flex. Syst. Manag. 2012, 13, 87–106. [Google Scholar] [CrossRef]
- Sivaprakasam, R.; Selladurai, V.; Sasikumar, P. Implementation of interpretive structural modelling methodology as a strategic decision making tool in a Green Supply Chain Context. Ann. Oper. Res. 2015, 233, 423–448. [Google Scholar] [CrossRef]
- Jayasuriya Daluwathumullagamage, D.; Sims, A. Blockchain-Enabled Corporate Governance and Regulation. Int. J. Financ. Stud. 2020, 8, 36. [Google Scholar] [CrossRef]
- Gomez-Trujillo, A.M.; Velez-Ocampo, J.; Gonzalez-Perez, M.A. Trust, Transparency, and Technology: Blockchain and Its Relevance in the Context of the 2030 Agenda. In The Palgrave Handbook of Corporate Sustainability in the Digital Era; Palgrave Macmillan: Cham, Switzerland, 2021; pp. 561–580. [Google Scholar]
- Koster, F.; Borgman, H. New Kid on The Block! Understanding Blockchain Adoption in the Public Sector. In Proceedings of the 53rd Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2020. [Google Scholar]
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Hasselgren, A.; Kralevska, K.; Gligoroski, D.; Pedersen, S.A.; Faxvaag, A. Blockchain in healthcare and health sciences—A scoping review. Int. J. Med. Inform. 2020, 134, 104040. [Google Scholar] [CrossRef] [PubMed]
- Petersson, E.; Baur, K. Impacts of Blockchain Technology on Supply Chain Collaboration: A Study on the Use of Blockchain Technology in Supply Chains and How It Influences Supply Chain Collaboration. Available online: https://www.diva-portal.org/smash/get/diva2:1215210/FULLTEXT01.pdf (accessed on 19 March 2019).
- Satyavolu, P.; Herridge, M. Blockchain in Manufacturing: Enhancing Trust, Cutting … (n.d.). Available online: https://www.cognizant.com/whitepapers/blockchain-in-manufacturing-enhancing-trust-cuttingcosts-and-lubricating-processes-across-the-value-chain-codex3239.pdf (accessed on 18 January 2021).
- Choi, D.; Chung, C.Y.; Seyha, T.; Young, J. Factors Affecting Organizations’ Resistance to the Adoption of Blockchain Technology in Supply Networks. Sustainability 2020, 12, 8882. [Google Scholar] [CrossRef]
- Sánchez-Cid, F.; Mana, A.; Spanoudakis, G.; Kloukinas, C.; Serrano, D.; Munoz, A. Representation of security and dependability solutions. In Security and Dependability for Ambient Intelligence; Springer: Boston, MA, USA, 2009; pp. 69–95. [Google Scholar]
- Serrano, D.; Ruíz, J.F.; Muñoz, A.; Maña, A.; Armenteros, A.; Crespo, B.G.N. Development of applications based on security patterns. In Proceedings of the 2009 Second International Conference on Dependability, IEEE, Athens, Greece, 18–23 June 2009; pp. 111–116. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).