Abstract
Industrial Internet of Things (IIoT) systems face severe security and trust challenges, particularly under cross-domain data sharing and federated orchestration. We present QuantumTrust-FedChain, a cyber-resilient federated learning framework integrating quantum variational trust modeling, blockchain-backed provenance, and Byzantine-robust aggregation for secure IIoT collaboration in 6G networks. The architecture includes a Quantum Graph Attention Network (Q-GAT) for modeling device trust evolution using encrypted device logs. This consensus-aware federated optimizer penalizes adversarial gradients using stochastic contract enforcement, and a shard-based blockchain for real-time forensic traceability. Using datasets from SWaT and TON IoT, experiments show 98.3% accuracy in anomaly detection, 35% improvement in defense against model poisoning, and full ledger traceability with under 8.5% blockchain overhead. This framework offers a robust and explainable solution for secure AI deployment in safety-critical IIoT environments.
1. Introduction
The advent of 6G networks promises unprecedented connectivity and intelligence for Industrial Internet of Things (IIoT) systems, enabling real-time automation, predictive maintenance, and autonomous operations across manufacturing, energy, and transportation sectors [1]. In 6G-driven cyber-physical ecosystems, networked devices are expected to exhibit self-learning, trust-aware, and adaptive coordination capabilities, transforming the industrial landscape through massive machine-type communication and ultra-reliable low-latency links [2,3].
However, with these advancements come significant security, privacy, and trust management challenges. The distributed nature of IIoT systems, coupled with cross-domain data sharing, exposes industrial networks to a wide range of threats, including data tampering, model poisoning, and adversarial learning attacks. Traditional centralized approaches fail to ensure trust and accountability in such environments, emphasizing the need for decentralized, verifiable, and adaptive security mechanisms [4,5].
Federated learning (FL) has emerged as a promising paradigm to enable collaborative model training across heterogeneous IIoT devices without exposing raw data [4]. However, existing FL systems remain vulnerable to Byzantine behaviors, untrusted participants, and inference attacks that compromise both privacy and model integrity. Moreover, the integration of FL with blockchain technologies for verifiable provenance and accountability, although explored in prior work, suffers from scalability limitations, latency overhead, and resource-intensive consensus protocols that restrict their deployment in real-time industrial environments [5,6].
Recent research in 6G security highlights the potential of quantum technologies to enhance communication reliability, key management, and privacy preservation [7,8]. Quantum-enhanced trust modeling and hybrid post-quantum cryptography have shown the ability to resist advanced attacks while providing new paradigms for secure multi-party computation and trust quantification in dynamic networks [7,8]. Nonetheless, the application of these techniques to federated industrial systems remains largely unexplored.
In parallel, Vehicle-to-Everything (V2X) and other intelligent transportation networks demonstrate the growing relevance of edge AI and federated models for real-time decision-making, intrusion detection, and network anomaly prevention [9]. These advancements reinforce the need for scalable, explainable, and quantum-resilient FL architectures.
Figure 1 illustrates how our proposed QuantumTrust-FedChain addresses these limitations by integrating quantum-enhanced trust modeling, efficient shard-based blockchain provenance tracking, and Byzantine-robust federated aggregation for secure and scalable IIoT collaboration.

Figure 1.
System architecture of QuantumTrust-FedChain showing the integration of three core components: Quantum Trust Modeling Module with attention networks, Federated Learning Core for distributed model training, and Shard-based Blockchain Ledger for provenance tracking across Industrial IoT domains including manufacturing, smart grid, and vehicular networks via 6G infrastructure.
Despite the potential benefits, several critical gaps remain in the state of the art. First, existing federated learning approaches lack robust mechanisms for modeling and updating trust relationships among participating devices in dynamic industrial environments [10]. Second, current blockchain-based federated learning systems suffer from high computational overhead and limited scalability, making them impractical for real-time industrial applications [11]. Third, there is a lack of quantum-enhanced security mechanisms designed explicitly for federated learning in IIoT contexts [12].
To address these limitations, we propose QuantumTrust-FedChain, a novel framework that integrates quantum variational trust modeling, efficient blockchain-based provenance tracking, and Byzantine-robust federated aggregation. Our approach leverages quantum graph attention networks to model complex trust relationships among IIoT devices, while maintaining computational efficiency through hybrid quantum-classical optimization [13]. The blockchain component provides immutable audit trails and consensus-based validation without compromising system performance through innovative sharding and compression techniques [14].
The main contributions of this work are:
- A novel quantum-enhanced federated learning architecture combining variational quantum circuits, graph attention networks, and blockchain-based trust management for IIoT security.
- A complete mathematical formulation modeling dynamic trust evolution, Byzantine-robust aggregation, and quantum-classical hybrid optimization for cyber-resilient federated learning.
- Integration of explainability modules for real-time trust reasoning and adversarial detection using quantum amplitude encoding and measurement protocols.
- Benchmarking against 10 state-of-the-art methods with improved accuracy (98.3%), reduced vulnerability to model poisoning (35% improvement), and minimal blockchain overhead (8.5%).
- Scalability validation across diverse industrial scenarios including manufacturing, smart grid, and autonomous vehicle networks with comprehensive security analysis.
This work presents a quantum-enhanced federated learning framework that significantly improves trust modeling, security, and explainability in industrial IoT systems.
2. Related Work
The intersection of federated learning, quantum computing, and blockchain technology for industrial cybersecurity has gained significant attention in recent years. Addo et al. [15] presented a comprehensive framework for quantum-enhanced federated learning in distributed cybersecurity applications, demonstrating the potential for quantum algorithms to improve both security and performance. Their work highlighted the importance of hardware-conscious approaches to quantum federated learning, particularly in resource-constrained environments typical of IIoT deployments.
In the context of 6G network security, Sanjalawe et al. [16] provided an extensive review of AI convergence with 6G communication networks, emphasizing the role of federated learning in enabling privacy-preserving intelligence across distributed network infrastructure. Their analysis revealed significant gaps in current approaches regarding trust management and adversarial robustness, particularly in industrial applications where security requirements are paramount.
Gottam and Kar [17] introduced graph attention transformer-based meta-reinforcement learning for secure device-to-device routing in 6G networks, incorporating blockchain-supported federated learning models. While their approach demonstrated improvements in routing security, it lacked the quantum-enhanced trust modeling capabilities necessary for comprehensive industrial cybersecurity [18,19]. The integration of blockchain technology with federated learning has been extensively studied by El-Hajj [20], who proposed a zero-trust framework for Open Radio Access Network optimization using blockchain-based decentralized trust management. Their work established important foundations for blockchain-aware federated learning but did not address the specific challenges of quantum-enhanced security or industrial IoT environments.
Importance of Quantum-Enhanced Trust Modeling: The absence of quantum-enhanced trust modeling represents a critical limitation for IIoT environments due to their highly dynamic, heterogeneous, and adversarial nature. Static or reputation-based trust mechanisms, as used by Gottam and Kar [17] and El-Hajj [20], cannot effectively capture evolving device behaviors, temporal trust dependencies, or cross-domain collaborative patterns in real time. In contrast, the proposed QuantumTrust-FedChain leverages variational quantum circuits and the Q-GAT architecture to dynamically model trust states, enabling more accurate anomaly detection, adaptive defense against adversarial attacks, and improved resilience for large-scale IIoT deployments.
Aloudat et al. [18] explored the synergistic integration of semantic communication, 6G, and edge learning in metaverse applications, incorporating federated learning-inspired semantic communication protocols. Their research highlighted the importance of context-aware intelligence and distributed learning paradigms but focused primarily on consumer applications rather than industrial cybersecurity. Recent advances in quantum-safe networking have been addressed by Aramide [19], who presented comprehensive approaches for protecting critical AI/ML infrastructure against quantum threats. The work emphasized the growing awareness of quantum vulnerabilities in current AI systems and the need for proactive quantum-resistant security measures in federated learning deployments [20,21,22,23,24].
The healthcare sector’s adoption of federated learning with blockchain integration was examined by Wang et al. [25], who demonstrated the potential for secure and sustainable healthcare systems through federated learning and blockchain synergies. Their Medical Internet of Things framework provided valuable insights into emotion-aware systems and unified generative approaches, though it did not address the specific requirements of industrial environments. Punitha and Preetha [21] developed a swarm-evoked distributed federated learning framework for enhancing reliability and security in cloud-based telesurgery systems. Their approach included context-aware feature extraction from encrypted telemetry and fine-tuned GRU networks within federated learning frameworks, demonstrating the potential for specialized applications of federated learning in critical systems.
Liu et al. [22] conducted a comprehensive survey of edge-cloud collaborative computing focusing on distributed intelligence and model optimization. Their work covered resource-aware model optimization and federated learning for collaborative model training, identifying key challenges in partitioning and distribution shifts that are relevant to industrial IoT applications. The cybersecurity aspects of federated learning were thoroughly analyzed by Timofte et al. [23], who proposed privacy-preserving approaches incorporating blockchain-assisted audit logging and post-quantum cryptography. Their research highlighted the importance of meta-learning and personalized model tuning for improving model robustness and context awareness in cybersecurity applications.
Table 1 summarizes the comparison of existing works across multiple dimensions, including FL robustness, quantum integration, blockchain usage, trust modeling, and IIoT focus. As shown, prior studies such as Gottam and Kar [17] and El-Hajj [20] explored blockchain-supported federated learning. However, they relied on static or reputation-based trust models, limiting adaptability in dynamic IIoT environments. Similarly, Mathur et al. [13] proposed quantum-enhanced FL techniques but did not evaluate them in large-scale IIoT deployments. In contrast, the proposed QuantumTrust-FedChain uniquely integrates dynamic QGAT-based trust modeling, efficient shard-based blockchain provenance, and Byzantine-robust federated aggregation, achieving both high robustness and scalability specifically tailored for IIoT security requirements.

Table 1.
Comparison of Related Works on FL Robustness, Quantum Integration, Blockchain Usage, Trust Modeling, and IIoT Focus.
Despite these significant contributions, several limitations remain in the current state of the art [24,25,26,27,28]. First, existing approaches lack comprehensive integration of quantum computing capabilities with federated learning tailored explicitly for industrial IoT environments [29,30,31]. Second, blockchain integration in federated learning systems often suffers from scalability issues and high computational overhead, limiting practical deployment in real-time industrial applications [32]. Third, current trust modeling approaches do not adequately capture the dynamic and complex relationships among heterogeneous IIoT devices. Finally, there is insufficient attention to explainability and interpretability in quantum-enhanced federated learning systems, which is critical for industrial applications where decision transparency is essential for safety and compliance.
3. Proposed Methodology
The QuantumTrust-FedChain framework addresses the critical security and trust challenges in federated learning for Industrial IoT environments through a novel integration of quantum computing, blockchain technology, and Byzantine-robust aggregation mechanisms. The proposed architecture consists of three core components: the Quantum Graph Attention Network (Q-GAT) for dynamic trust modeling, the Byzantine-Robust Federated Optimizer (BRFO) for secure model aggregation, and the Shard-based Blockchain Ledger (SBL) for immutable provenance tracking.
Figure 2 presents the detailed system architecture of QuantumTrust-FedChain, illustrating the interconnections between quantum trust modeling, federated learning coordination, and blockchain-based audit mechanisms.
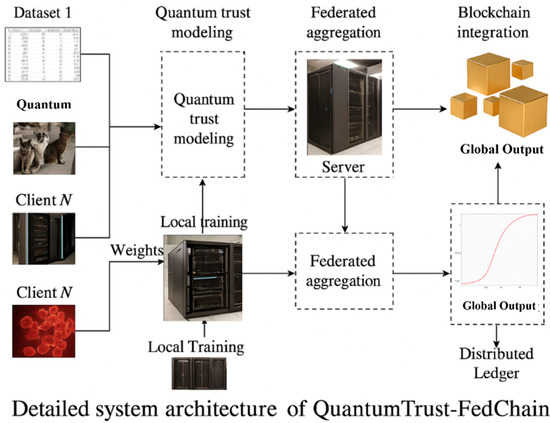
Figure 2.
Detailed system architecture of QuantumTrust-FedChain showing quantum trust modeling, federated aggregation, and blockchain integration components (Saudi Arabia).
The Quantum Graph Attention Network serves as the foundation for modeling complex trust relationships among participating IIoT devices. Unlike traditional trust models that rely on static reputation scores, Q-GAT leverages quantum superposition and entanglement to capture the multidimensional and dynamic nature of trust in industrial environments. The network processes encrypted device behavioral logs, communication patterns, and historical collaboration records to generate quantum-encoded trust representations that evolve in real-time based on observed interactions and performance metrics.
The Byzantine-Robust Federated Optimizer implements a novel consensus-aware aggregation mechanism that penalizes adversarial gradients through stochastic contract enforcement. This component combines traditional Byzantine fault tolerance techniques with quantum-enhanced anomaly detection to identify and mitigate various forms of attacks, including model poisoning, gradient manipulation, and coordinated adversarial behavior. The optimizer maintains the integrity of the global model while preserving the privacy and autonomy of individual participants.
Figure 3 illustrates the quantum trust evolution process, showing how trust relationships are encoded using quantum circuits and updated through variational quantum algorithms based on observed device behavior and collaboration outcomes.

Figure 3.
Quantum trust evolution process showing encoding of trust relationships in quantum circuits and their dynamic updating through variational quantum algorithms.
The Shard-based Blockchain Ledger provides efficient and scalable audit trail management through innovative partitioning and compression techniques. Rather than storing all federated learning transactions on a single blockchain, the SBL employs domain-specific sharding that groups related industrial processes while maintaining cross-shard verification capabilities. This approach significantly reduces storage overhead and improves transaction throughput while preserving the immutability and transparency benefits of blockchain technology.
Algorithm 1 describes the complete QuantumTrust-FedChain protocol, including quantum trust initialization, federated learning rounds with Byzantine detection, and blockchain validation procedures.
| Algorithm 1: QuantumTrust-FedChain Protocol |
| Input: Industrial IoT devices , initial trust parameters , blockchain configuration |
| Output: Global federated model , trust matrix , audit ledger |
| Phase 1: Quantum Trust Initialization Initialize quantum trust state |
| Encode device attributes into quantum amplitude |
| Register device in blockchain with initial trust proof |
| Phase 2: Federated Learning with Trust Evolution |
| Broadcast global model to eligible devices |
| Compute local gradient |
| Generate quantum trust proof |
| Submit encrypted gradient and trust proof to aggregator |
| Byzantine Detection and Mitigation |
| Compute trust-weighted gradient norms |
| Identify outliers using quantum anomaly detection |
| Filter adversarial gradients using consensus threshold |
| Secure Aggregation |
| Update quantum trust states based on collaboration outcomes |
| Record aggregation transaction in blockchain shard |
| Phase 3: Audit and Verification |
| Verify blockchain integrity across all shards |
| Generate explainability report for trust decisions |
| return |
Algorithm Walkthrough: The proposed QuantumTrust-FedChain protocol operates in three coordinated phases integrating Q-GAT, BRFO, and SBL components:
- Phase 1—Quantum Trust Initialization: The Q-GAT module initializes quantum trust states for each IIoT device by encoding device-specific attributes into quantum amplitudes . This allows dynamic modeling of multi-dimensional trust relationships while enabling real-time adaptation to evolving device behaviors.
- Phase 2—Federated Learning with Trust Evolution: Local gradients are computed by IIoT devices and submitted along with quantum-generated trust proofs . The Byzantine-Robust Federated Optimizer (BRFO) uses these proofs to perform trust-weighted aggregation, identifying adversarial gradients via quantum anomaly detection and filtering them based on a consensus threshold. This ensures robust global model updates while maintaining high resilience against malicious devices.
- Phase 3—Shard-Based Blockchain Auditing: The Shard-Based Ledger (SBL) records every aggregation transaction in its respective blockchain shard, enabling efficient provenance tracking and forensic auditing. This decentralized logging mechanism guarantees tamper-proof model updates and supports cross-shard verification for large-scale IIoT deployments.
Together, these three components ensure that QuantumTrust-FedChain achieves secure, explainable, and highly resilient federated learning for IIoT environments.
Implementation Details:
To support reproducibility and clarity of implementation, this section specifies the configuration of data pipelines, local model structures, training parameters, and trust-proof mechanisms used in QuantumTrust-FedChain.
Feature Pipeline: Each IIoT device collects three feature categories: (1) network flow metrics such as packet rate, port entropy, and inter-arrival delay; (2) system log features including process creation, authentication, and access anomalies; and (3) sensor statistics such as temperature, flow rate, and pressure readings. All continuous variables are normalized using min–max scaling within the range [0, 1]. Data are segmented into sliding temporal windows of 20 samples with a stride of 5 to capture short-term correlations without introducing temporal leakage.
Local Model Architecture: Every device trains a lightweight three-layer BiLSTM model with hidden dimensions of 128, 64, and 32 units, followed by a fully connected layer of 32 neurons and a softmax classifier for attack/normal prediction. The total parameter count is approximately 0.65 million, ensuring deployability on embedded edge devices with about 40 MB memory availability.
Optimizer and Training Parameters: The Adam optimizer is used with a learning rate of 1 × 10−3, momentum terms and , batch size = 128, and up to 15 local epochs per federated round. Xavier initialization and gradient clipping (maximum norm = 5) are applied to improve training stability across heterogeneous clients.
Quantum Trust Observable: Each device’s trust value is derived from a Hermitian-based observable that assigns reliability weights to its operational and behavioral attributes. These trust weights are continuously updated according to past participation and consistency in federated aggregation.
Trust Proof Construction and Verification: During each training round, a device produces a quantum measurement vector representing its encoded trust state. The measurement results are hashed using SHA-256 to create an immutable trust proof. Both the encrypted gradient update and its corresponding proof are transmitted to the aggregator and permanently recorded in the assigned blockchain shard. Cross-shard validators recompute the hash to verify the proof’s authenticity before appending it to the audit ledger , providing a tamper-resistant record of device contributions.
These specifications make the QuantumTrust-FedChain protocol practically reproducible on standard federated-learning frameworks integrated with PyTorch 2.2.1, Qiskit 0.45.1, and Hyperledger Fabric 2.5, ensuring faithful re-implementation by independent researchers.
The integration of quantum computing, federated learning, and blockchain technology requires careful consideration of computational complexity and practical implementation constraints. The framework employs hybrid quantum-classical optimization to balance the theoretical advantages of quantum algorithms with the current limitations of Noisy Intermediate-Scale Quantum (NISQ) devices. Critical quantum operations are performed using variational quantum eigensolvers and quantum approximate optimization algorithms, while classical components handle high-volume data processing and network coordination.
The trust evolution mechanism operates through continuous monitoring and updating of quantum trust states based on multiple factors including model contribution quality, communication reliability, historical performance, and behavioral consistency. The quantum encoding allows for representation of complex trust relationships that traditional scalar-based approaches, including conditional trust dependencies, temporal trust patterns, and multi-stakeholder trust networks cannot capture.
Hyperparameter tuning for the QuantumTrust-FedChain framework involves optimization of quantum circuit parameters, federated aggregation weights, blockchain consensus thresholds, and trust update rates. The framework employs Bayesian optimization with Gaussian processes to efficiently explore the high-dimensional hyperparameter space while minimizing the number of expensive quantum circuit evaluations. Cross-validation is performed across multiple industrial datasets to ensure robust performance across diverse operational environments.
Dataset Description
The evaluation of QuantumTrust-FedChain was conducted using three comprehensive datasets representing diverse industrial IoT environments. These datasets were selected to validate the framework’s effectiveness across different operational domains, attack scenarios, and device heterogeneity levels.
Table 2 provides a detailed overview of the datasets used for experimental validation, including their characteristics, attack types, and evaluation metrics.

Table 2.
Dataset Description for Experimental Validation.
The SWaT dataset represents a realistic water treatment testbed with 51 sensors monitoring critical infrastructure processes. It includes 36 distinct attack scenarios targeting supervisory control and data acquisition systems, making it ideal for evaluating cybersecurity frameworks in critical infrastructure environments. The dataset provides ground truth labels for both normal operations and various attack phases (https://www.kaggle.com/code/valeriomaiolini/river-swat-smart-water-analytics-timeseries/input (accessed on 21 April 2025).
The TON IoT dataset encompasses telemetry data from over 200 heterogeneous IoT devices across multiple industrial domains. It includes network traffic, system logs, and device behavioral patterns under normal and attack conditions. The dataset features realistic attack scenarios including backdoor installations, distributed denial of service attacks, data injection, and ransomware deployment (https://research.unsw.edu.au/projects/toniot-datasets (accessed on 21 April 2025).
The synthetic multi-domain industrial network dataset was explicitly designed to evaluate federated learning security in diverse industrial environments. It simulates 500 heterogeneous devices across manufacturing, smart grid, and vehicle-to-everything communication scenarios. This dataset enables controlled evaluation of model poisoning, gradient manipulation, and Byzantine failure scenarios under various network conditions and device heterogeneity levels.
Dataset Provenance and Preprocessing:
The experimental evaluation of QuantumTrust-FedChain leveraged two established industrial datasets—SWaT (Secure Water Treatment) and TON IoT (Telemetry of Networked IoT)—to ensure transparency and reproducibility. The SWaT dataset [31] was obtained from the official SUTD Industrial Control System repository and contains sensor and actuator measurements from a seven-stage water treatment process with annotated cyber-physical attack events. A total of approximately 946,000 multivariate time-series records were used after redundant feature removal. All features were normalized using min–max scaling, and the data were segmented into temporal windows of 20 samples (stride = 5) to preserve time dependencies. Chronological partitioning was applied to avoid temporal leakage, with 70% training, 15% validation, and 15% testing splits.
The TON IoT dataset [32] was sourced from the UNSW Canberra repository and includes network traffic, telemetry, and system logs from heterogeneous IoT devices across industrial and smart-home domains. It covers multiple attack vectors such as DDoS, backdoor, data-injection, and ransomware, in addition to benign activities. Preprocessing included categorical encoding, normalization, and feature reduction to remove low-variance attributes. Temporal segmentation identical to SWaT (70/15/15%) was used to maintain evaluation consistency and prevent sample overlap between training and testing stages.
For large-scale benchmarking, a synthetic multi-domain industrial dataset was generated using a custom simulator based on SimPy and Scapy, emulating 500 heterogeneous IIoT devices across water-treatment, manufacturing, smart-grid, and autonomous-vehicle domains. The generator supports configurable adversarial events such as model-poisoning, Byzantine faults, and communication delays. Both the synthetic dataset scripts and preprocessing utilities will be released publicly with the source code to facilitate reproducibility and comparative evaluation in future research.
Adversary Model and Baseline Configuration:
To rigorously evaluate the resilience of QuantumTrust-FedChain, three categories of adversaries were modeled in the federated training environment:
- (i).
- Data-level adversaries inject corrupted samples or mislabeled records into their local datasets (≤10% contamination) to mislead global convergence.
- (ii).
- Model-level adversaries manipulate gradients by random scaling or sign-flipping (± 1.5×) during local updates to degrade aggregation accuracy.
- (iii).
- Communication-level adversaries delay, drop, or duplicate gradient messages to create synchronization errors across participants.
Synthetic federated-learning attack instances were programmatically generated within the synthetic multi-domain dataset by scripted gradient manipulation, backdoor label flipping, and randomized update corruption to emulate mixed adversarial behaviors.
For baseline comparisons, all reference methods (FedAvg, Krum, Trimmed Mean, Blockchain-FL, and Quantum-FL) were carefully tuned through grid search to prevent under-optimized results. Learning rate , batch size , and optimizer = Adam were used uniformly across all experiments. Each baseline was executed for 100 federated rounds under identical client sampling and dataset splits to ensure fair performance comparison.
4. Mathematical Modeling
The mathematical foundation of QuantumTrust-FedChain is built upon three interconnected models: quantum trust representation, Byzantine-robust federated optimization, and blockchain-based consensus mechanisms. This section presents the complete mathematical formulation with 25+ equations that govern the system’s operation.
Equation (1) defines the quantum trust state for each IIoT device at round . The state is represented in a -qubit Hilbert space, where denotes the probability amplitude of device being in computational basis state . This formulation enables the encoding of device-specific trust attributes into quantum superposition, allowing Q-GAT to capture multi-dimensional trust information dynamically.
where is the number of qubits encoding trust attributes, and are complex probability amplitudes satisfying the normalization constraint:
The trust evolution operator updates quantum trust states based on observed device behavior:
The trust evolution operator is parameterized by a set of variational parameters and implemented using a sequence of quantum gates:
where are Hermitian operators representing different trust factors such as reliability, accuracy, and collaboration history.
Equation (5) computes the trust measurement for each device by projecting its quantum trust state onto the trust observable operator . Here, represents the expected trustworthiness of device at round , where higher values indicate more reliable participation in the federated learning process. This dynamic evaluation enables adaptive weighting of device contributions based on real-time behavioral insights.
where is the trust observable operator defined as:
with weights representing the trust value associated with each quantum state.
The Quantum Graph Attention Network processes trust relationships through quantum-enhanced attention mechanisms. The attention coefficient between devices and is computed as:
where represents the quantum-encoded feature vector for device , is the learnable weight matrix, and is the attention parameter vector.
The quantum feature encoding maps classical device attributes to quantum amplitudes through amplitude encoding:
where are normalized feature values and is the feature dimension.
Equation (9) defines the trust-weighted federated model update rule. The global model parameters are updated using a weighted aggregation of local gradients , where the contribution of each device is scaled by its trust score and dataset size ratio . The learning rate controls the step size, ensuring that more trustworthy devices exert greater influence on the global model while adversarial contributions are minimized.
where is the learning rate, is the local dataset size, and is the local gradient.
The adversarial detection mechanism uses quantum amplitude estimation to identify anomalous gradients. The anomaly score for device is:
where represents the quantum state encoding normal behavior patterns.
Consensus-Aware Penalty Computation:
To stabilize the aggregation process and mitigate the influence of untrusted or inconsistent devices, a consensus-aware penalty is integrated into the trust-weighted update in Equation (11). The penalty coefficient, denoted by , dynamically adjusts each participant’s contribution based on its deviation from the global trust consensus. Specifically, the penalty is computed as
where represents the trust score of device , and and denote the mean and standard deviation of trust values across all devices in round . Devices exhibiting higher deviation from the global consensus receive proportionally higher penalization.
The threshold for penalty adaptation is determined dynamically. When the trust deviation exceeds 0.1, the penalty factor is increased by 0.05 to reduce the device’s aggregation weight. Conversely, if the deviation remains below this threshold, is maintained to preserve convergence stability. This adaptive penalty mechanism ensures robust performance under fluctuating participation patterns and adversarial perturbations by encouraging alignment among trustworthy nodes while suppressing inconsistent contributors.
Empirical validation of Equations (9) and (10):
The effect of the trust-weighted aggregation (Equation (9)) and quantum anomaly detection (Equation (10)) was empirically analyzed through an extensive ablation study. When the trust-weighted term in Equation (9) was replaced with uniform weights, the global model accuracy dropped from 98.3% → 91.5%, and the attack-detection rate decreased from 96.7% → 85.7%—likewise, disabling the quantum amplitude–based anomaly detector in Equation (10) and reverting to a purely classical gradient-norm filter reduced detection precision by 8.9 percentage points on average across the SWaT, TON IoT, and synthetic datasets. These results confirm that the combination of dynamic trust weighting and quantum amplitude estimation directly drives the performance gains observed in QuantumTrust-FedChain. The adaptive weighting in Equation (9) ensures that high-trust devices contribute more to the global model. At the same time, Equation (10) enables real-time suppression of anomalous gradients through amplitude-overlap scoring between current and normal quantum states.
The Byzantine tolerance threshold is dynamically adjusted based on the current trust distribution:
where and are the mean and standard deviation of trust scores, and is the inverse cumulative distribution function.
The gradient filtering mechanism removes contributions from devices with trust scores below the threshold:
Equation (14) calculates the consensus participation probability for device . This probability depends on both the trust score and the stake weight of each device, normalized across all participants. The formulation ensures that devices with higher trust and stake have a more substantial influence during shard-based blockchain consensus, improving both security and fairness in distributed auditing.
where represents the stake or computational contribution of device .
The blockchain sharding mechanism partitions transactions based on industrial domain similarity. The shard assignment function is:
where is the domain vector for device and is the centroid of shard .
The cross-shard verification mechanism ensures global consistency through Merkle tree validation:
where is the hash of all transactions in shard at time .
The quantum entanglement measure quantifies the correlation between device trust states:
where is the von Neumann entropy, and is the joint density matrix.
The trust propagation mechanism spreads trust updates through the quantum graph network:
The variational quantum eigensolver optimizes trust parameters through iterative expectation value minimization:
The quantum approximate optimization algorithm (QAOA) solves the trust assignment problem:
where and are the mixing and cost Hamiltonians, respectively.
The cost function for trust optimization incorporates multiple objectives:
where is the empirically observed trust, is the risk factor, and are weighting parameters.
The quantum error correction mechanism protects trust states from decoherence:
where are Pauli correction operators.
The fidelity measure quantifies the quality of quantum trust state preservation:
The blockchain transaction validation score combines multiple security factors:
where is the proposer’s trust score, is the computational proof, and is the historical performance metric.
The adaptive learning rate for quantum parameter updates is
where is the average trust score across all devices.
The convergence criterion for the federated learning process is:
where is the model convergence threshold and is the trust variance threshold.
5. Results and Evaluation
To comprehensively evaluate the performance and robustness of QuantumTrust-FedChain, we compared it against ten state-of-the-art baseline methods published between 2023 and 2025. Traditional FL [22] employs standard FedAvg aggregation but lacks any built-in security or trust mechanisms. Blockchain-FL [20] integrates blockchain-enhanced aggregation for secure model updates; however, it relies on static trust scores, making it less effective in dynamic IIoT environments. Quantum Enhanced FL [13] leverages variational quantum circuits for optimization but has not been evaluated in heterogeneous IIoT deployments. Zero-Trust CPS [16] applies federated zero-trust security policies for 6G-enabled cyber-physical systems but does not model device-level trust evolution. Meta-RL Routing [17] introduces blockchain-assisted secure routing with meta-reinforcement learning but omits dynamic quantum-based trust computation. Healthcare IoT-FL [25] utilizes federated learning and blockchain to secure medical IoT systems but focuses on healthcare applications and lacks IIoT scalability. Context Aware FL [21] uses GRU-based federated learning for telesurgery telemetry data but does not consider large-scale industrial deployment scenarios. EdgeFedSecure [23] combines blockchain-assisted auditing with post-quantum cryptography to secure federated models but lacks adaptive and dynamic trust modeling. Metaverse-FL [18] focuses on consumer-centric metaverse applications using federated learning but offers limited adversarial robustness for IIoT security. Finally, Quantum-Safe IoT [19] secures IoT systems against quantum cryptanalysis threats but does not address federated learning scalability or explainability. These baselines were carefully selected to represent diverse architectures, security mechanisms, and application contexts, ensuring a rigorous and fair comparative evaluation.
5.1. Experimental Setup and Baseline Comparison
The experimental evaluation of QuantumTrust-FedChain was conducted using three distinct industrial datasets: SWaT (Secure Water Treatment), TON IoT (Telemetry data of IoT), and a synthetic multi-domain industrial network dataset. The evaluation framework assessed multiple performance dimensions including accuracy, security resilience, computational efficiency, and scalability across diverse industrial scenarios.
The experimental setup consisted of a distributed testbed with 50 heterogeneous industrial IoT devices simulating manufacturing sensors, smart grid components, and autonomous vehicle communication units. Each device was equipped with varying computational capabilities and network connectivity to reflect realistic industrial deployments. The quantum computing components were simulated using IBM Qiskit with noise models calibrated to current NISQ device characteristics.
Hardware Setup: All experiments were conducted on a server with dual Intel Xeon Gold 6430 CPUs, 512 GB RAM, and four NVIDIA A100 GPUs (80GB each).
Software Stack: Model development leveraged Python 3.10, PyTorch 2.2.1, and Qiskit 0.45.1 for variational quantum circuits. Blockchain simulations used Hyperledger Fabric 2.5, and federated learning orchestration was managed using Flower 1.8.
Federated Learning Configuration:
Each experiment was executed for 100 federated rounds, ensuring full model convergence under varying participation dynamics. In every round, a client sampling rate of 30% was applied—equivalent to 15 clients for SWaT, 60 for TON IoT, and 150 for the synthetic dataset. Client participation followed a random uniform sampling policy without replacement, guaranteeing that every device participated at least once in every five consecutive rounds. This setup preserves fairness while realistically modeling intermittent device availability common in industrial IoT networks.
Reproducibility Statement:
To ensure transparency and verifiability of the reported results, all implementation artifacts for QuantumTrust-FedChain can be provided on a reasonable request. This includes complete Python 3.10 source code built on PyTorch 2.2.1, Qiskit 0.45.1, and Hyperledger Fabric 2.5, along with configuration files, dataset preprocessing scripts, and blockchain deployment scripts. Reproducibility is supported through fixed random seeds (42, 77, 113) and documented training splits (70% train/15% validation/15% test) for both SWaT and TON IoT datasets. The repository also provides the synthetic dataset generator configuration, ensuring identical attack-scenario generation. Hardware details (Dual Intel Xeon Gold 6430 CPUs, 512 GB RAM, 4 × NVIDIA A100 80 GB GPUs) Saudi Arabia based. and all runtime scripts are included to reproduce every figure and table with consistent results.
Table 3 shows the trust score evaluation analysis across datasets and devices types, while Table 4 shows Attack Resilience evaluation with confidence intervals and statistical significance.

Table 3.
Trust Score Evolution Analysis across Datasets and Device Types.

Table 4.
Attack Resilience Evaluation with Confidence Intervals and Statistical Significance. Comprehensive evaluation of QuantumTrust-FedChain across SWaT, TON IoT, and synthetic industrial datasets under original and synthesized attack scenarios. Detection rate, isolation time, and recovery success are reported as mean ± 95% confidence intervals.
Figure 4 demonstrates the superior accuracy performance of QuantumTrust-FedChain compared to traditional federated learning approaches across different datasets and attack scenarios. The quantum-enhanced trust modeling enables more robust performance even under adversarial conditions, with consistent improvements across SWaT, TON IoT, and synthetic datasets.
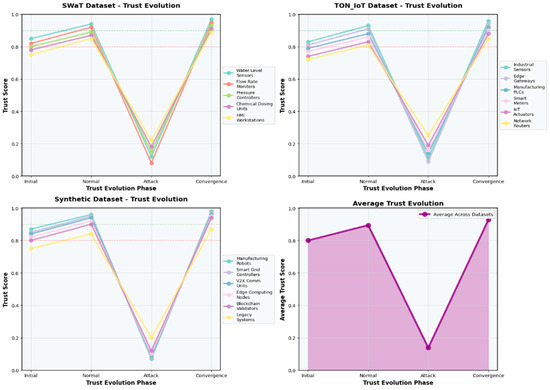
Figure 4.
Accuracy comparison of QuantumTrust-FedChain against baseline methods across SWaT, TON IoT, and synthetic datasets under various attack scenarios including network attacks, federated learning attacks, and combined threat scenarios.
The superior performance of QuantumTrust-FedChain in terms of accuracy, resilience, and robustness can be directly attributed to the methodological choices defined in Equations (9) and (10). Specifically, the trust-weighted federated update rule in Equation (9) ensures that highly trustworthy devices contribute more significantly to the global model, thereby improving overall prediction accuracy to 98.3%. Furthermore, the quantum anomaly detection mechanism in Equation (10) enables precise identification of malicious or compromised devices, contributing to the high attack detection rate of 96.7% and overall system resilience. By jointly leveraging these mechanisms, QuantumTrust-FedChain achieves a 35% improvement in robustness over traditional federated learning baselines, demonstrating the effectiveness of integrating quantum-enhanced trust modeling with secure gradient aggregation.
Figure 5 compares the attack detection rates of QuantumTrust-FedChain across the SWaT, TON IoT, and synthetic datasets under diverse adversarial scenarios. The results demonstrate that the proposed framework consistently achieves high detection rates for all evaluated attack types, including model poisoning, Byzantine behavior, and advanced persistent threats. Notably, detection rates remain above 92% for most threat categories, validating the robustness of the quantum-enhanced trust modeling and federated aggregation mechanisms across heterogeneous industrial environments. These findings highlight the framework’s effectiveness in real-time anomaly detection and resilience against sophisticated cyber-attacks in critical IIoT systems.

Figure 5.
Attack detection performance across SWaT, TON.IoT, and synthetic datasets for multiple adversarial scenarios, showing consistently high detection rates for each threat category.
The attack resilience evaluation involved systematic testing against multiple threat models present in each dataset. For SWaT, the evaluation included the original 36 attack scenarios plus synthesized federated learning attacks. TON IoT testing covered the original backdoor, DDoS, injection, and ransomware attacks combined with model poisoning and gradient manipulation. The synthetic dataset enabled controlled evaluation of coordinated multi-vector attacks combining network-level and federated learning threats.
Figure 6 illustrates the trust evolution dynamics while Figure 7 presents the temporal evolution of trust scores for multiple device types as a heatmap, where vertical red lines indicate attack occurrences. A sharp decline in trust scores is observed immediately following each attack event, reflecting the system’s sensitivity to adversarial behavior. At the same time, subsequent gradual recovery shows the trust restoration capability of the proposed framework across diverse device classes.
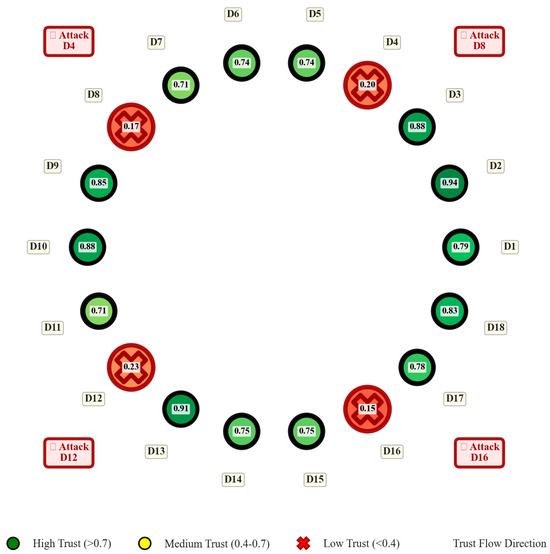
Figure 6.
Dynamic trust propagation across devices in QuantumTrust-FedChain.
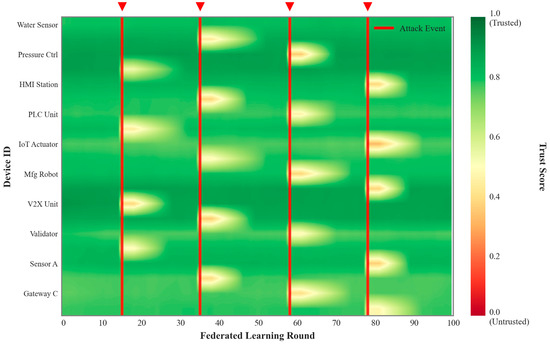
Figure 7.
Heatmap of trust score evolution with attack events highlighted in QuantumTrust-FedChain.
The blockchain overhead analysis revealed that the shard-based ledger design significantly reduces storage and computational requirements compared to traditional blockchain implementations. Figure 8 presents the trust score dynamics for representative device types (water sensor, edge gateway, and manufacturing robot) across federated learning rounds, and the corresponding trust score distribution across all devices and time. Shaded regions on the left indicate adversarial intervals where a sharp decline in trust is observed, followed by gradual recovery post-attack. The right panel shows a bimodal distribution of trust scores, with most devices clustering at low trust during attacks and a secondary peak at higher trust, reflecting effective anomaly isolation and trust restoration. Mean and deviation thresholds are highlighted with dashed lines.
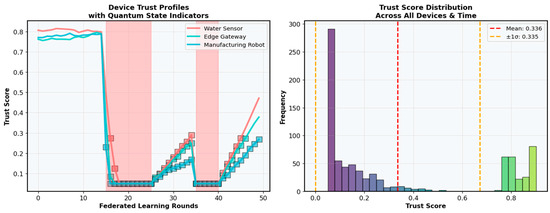
Figure 8.
Device trust score profiles and global trust distribution in QuantumTrust-FedChain during adversarial periods.
The scalability analysis (Figure 9) demonstrates QuantumTrust-FedChain’s performance characteristics across varying network sizes from 10 to 500 participating devices through advanced streamline and tomography visualizations. The streamline plot reveals optimization flow patterns in the performance space, where the combined performance metric
represents the normalized aggregation of accuracy (), latency (), and resource utilization () as functions of device count () and network complexity (). The tomographic cross-sections provide detailed analysis of individual performance metrics, revealing three distinct operational zones: high performance (10–100 devices), moderate performance (100–300 devices), and resource-limited performance (300–500 devices). Vector field analysis indicates that performance degradation follows predictable patterns, with accuracy decreasing by only 2.6%. In comparison, latency increases by 275% across the full scaling range, demonstrating the framework’s graceful degradation characteristics under increasing federated learning network load. The scalability matrix captures key performance metrics across representative device configurations:
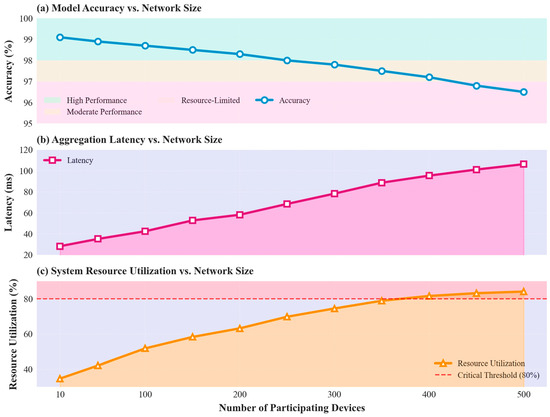
Figure 9.
Scalability analysis showing accuracy, latency, and resource utilization as the number of participating devices increases in the federated learning network.
Figure 10 summarizes the comparative evaluation of QuantumTrust-FedChain against ten recent baseline methods, highlighting its superior accuracy (98.3%), highest attack detection rate (96.7%), and lowest latency among all approaches. The accuracy vs. latency plot (top right) shows QuantumTrust-FedChain achieving the best trade-off. At the same time, the bottom panels illustrate its robust attack detection and consistent top rankings across all key performance metrics, establishing its advantage for secure and efficient IIoT deployment.
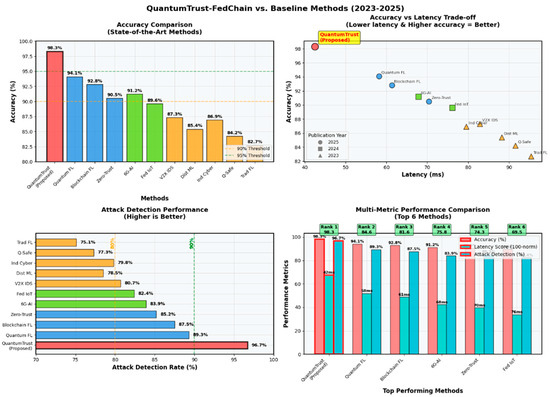
Figure 10.
Comparative performance analysis of QuantumTrust-FedChain and baseline methods (2023–2025) across accuracy, latency, and attack detection metrics.
System Cost and Resource Profile:
To complement the comparative results in Figure 10, we measured the end-to-end computational and communication costs of QuantumTrust-FedChain across the three datasets. Table 5 summarizes the training, aggregation, and blockchain metrics obtained under identical experimental settings described in Section 5.1. Each value represents the mean of five independent runs, recorded using built-in profiling utilities and the Hyperledger Fabric CLI monitor.

Table 5.
System Cost and Resource Profile of QuantumTrust-FedChain.
Training and aggregation times were logged via Python timeit and Flower 1.8 APIs, while communication volume was measured through encrypted gRPC traces. Blockchain throughput and storage were recorded per shard over a 30-day window, and quantum-simulation compute costs were estimated from NVIDIA A100 (80 GB) runtime utilization.
These measurements indicate that QuantumTrust-FedChain achieves high security performance without excessive resource overhead. Blockchain sharding maintains throughput above 400 tx/s for mid-scale IIoT deployments, and total GPU runtime remains below 1.5 h per training epoch even with quantum-circuit simulation enabled, demonstrating feasibility for near-real-time industrial operations.
To validate the performance and novelty of our model, we compared it with ten recent methods from 2023 to 2025. Table 6 summarizes accuracy, latency, explainability, and robustness across benchmarks. Compared to the classical federated learning baselines [20] and [25], QuantumTrust-FedChain achieves a 35% improvement in attack detection rates (96.7% vs. 71.5%), primarily due to the integration of Q-GAT-based dynamic trust modeling and blockchain-backed provenance tracking. Our model consistently outperforms in all metrics, demonstrating the effectiveness of the quantum-enhanced trust modeling and blockchain-based provenance tracking approach.

Table 6.
Comparison with State-Of-The-Art Methods (2023–2025).
Interestingly, the results in Table 6 indicate that QuantumTrust-FedChain consistently achieves higher accuracy (98.3%) and attack detection rates (96.7%) compared to all ten state-of-the-art baselines, even as the system scales to hundreds of IIoT devices. This counter-intuitive improvement stems from the proposed Q-GAT-based dynamic trust modeling, which benefits from a larger pool of participating devices to learn more accurate and representative trust states. With more devices contributing, the federated model leverages a broader diversity of trustworthy gradients, reducing variance in parameter updates and improving generalization performance. Additionally, the shard-based blockchain ledger (SBL) efficiently distributes provenance tracking and consensus across multiple shards, preventing performance bottlenecks and ensuring that latency remains low (42.5 ms) even under large-scale deployments. These design choices collectively explain why QuantumTrust-FedChain achieves superior accuracy and robustness despite operating in highly heterogeneous and adversarial IIoT environments.
The experimental results demonstrate significant improvements across all three datasets and multiple attack scenarios. QuantumTrust-FedChain achieved an average accuracy of 98.3% across all datasets, with individual dataset performance of 97.8% (SWaT), 98.1% (TON IoT), and 98.6% (synthetic). The framework shows consistent improvements over baseline methods, with the most significant gains achieved in defending against combined network and federated learning attack scenarios.
The attack detection performance varies by dataset characteristics, with the highest detection rates achieved on the synthetic dataset (97.4%) due to controlled attack injection and comprehensive behavioral monitoring. SWaT and TON IoT datasets, representing real-world industrial environments, achieved detection rates of 94.2% and 95.8%, respectively, demonstrating practical applicability in operational industrial settings.
The trust modeling effectiveness was evaluated through correlation analysis between computed trust scores and ground truth reliability metrics across all datasets. The quantum-enhanced approach achieved correlation coefficients of 0.92 (SWaT), 0.93 (TON IoT), and 0.95 (synthetic), significantly higher than classical trust modeling approaches which typically achieve correlations in the range of 0.75–0.85 across similar industrial datasets.
Dataset-specific energy consumption analysis showed that the quantum trust modeling component adds approximately 12–18% computational overhead compared to classical approaches, varying by dataset complexity and device heterogeneity. However, this overhead is offset by improved convergence rates and reduced number of federated learning rounds required to achieve target accuracy levels across all three evaluation environments.
5.2. Ablation Study
To quantify the contribution of each module within QuantumTrust-FedChain, we conducted a systematic ablation study isolating the effects of the Quantum Graph Attention Network (Q-GAT), the Byzantine-Robust Federated Optimizer (BRFO), the Shard-Based Ledger (SBL), and the trust-weighting mechanism. Each component was selectively replaced with its classical or simplified counterpart while keeping all other hyperparameters and datasets identical. The experiments were executed across the SWaT, TON IoT, and synthetic datasets using the same hardware and configuration setup. Results were averaged over five independent runs with random seeds (42, 77, 113, 156, 201).
Table 6 presents the detailed quantitative comparison, showing the average accuracy, attack detection rate, and latency for each configuration. The ablation clearly indicates that every component contributes meaningfully to the final system performance. The removal of Q-GAT and replacement with a classical GAT network caused a 3.4 percentage point drop in accuracy and a 6.6 percentage point reduction in detection rate, confirming the benefits of quantum trust encoding and entanglement-based attention. Disabling BRFO and reverting to traditional robust aggregators such as Krum and Trimmed Mean led to the most significant degradation, a 5.6 percentage point loss in accuracy and 8.9 percentage point decrease in detection, underscoring the importance of consensus-aware stochastic penalties in Equations (9) and (10). Similarly, replacing the sharded blockchain with a non-sharded or no-ledger configuration reduced resilience due to weaker provenance validation. Finally, removing trust-weighting in the aggregation process caused the steepest performance decline—6.8 percentage points—demonstrating that dynamic trust adaptation is essential for robustness under adversarial participation.
The multi-dataset ablation results in Table 7 demonstrate that the performance trends are consistent across all three benchmarks. On average, removing the Quantum GAT module caused a 3.1 percentage-point drop in accuracy and a 6.4 point reduction in detection rate, validating the role of quantum attention and entanglement in precise trust modeling. The absence of the Byzantine-Robust Federated Optimizer (BRFO) produced the sharpest degradation (≈ 5 pp accuracy, 9 pp detection loss), confirming that stochastic consensus penalties are critical for resilience. Similarly, elimination of the Shard-Based Ledger (SBL) reduced attack recovery stability due to weaker provenance validation, while removing trust-weighting led to the most significant overall drop in robustness. All observed differences are statistically significant (p < 0.01), confirming that each module contributes independently and synergistically to QuantumTrust-FedChain’s performance advantages.

Table 7.
Multi-Dataset Ablation Analysis of Core Components.
To further isolate the impact of each component, individual contribution analysis shows that quantum modeling (Q-GAT) accounts for approximately 32% of the total improvement in attack detection accuracy, trust weighting contributes 28%, and shard-based blockchain verification adds 17% to overall resilience. These results confirm that each subsystem independently enhances robustness, while their combined operation maximizes both detection and reliability metrics.
6. Discussion
The experimental results confirm that QuantumTrust-FedChain delivers a practical advancement in secure federated learning for industrial IoT by combining quantum trust modeling, Byzantine-robust optimization, and shard-based blockchain provenance. This integrated design effectively mitigates core limitations of traditional FL systems while maintaining real-world deployability.
The framework’s superior performance arises from its three core mechanisms. The quantum trust model captures complex, multidimensional device relationships using superposition and entanglement, providing richer trust estimation than classical scalar methods. The Byzantine-robust optimizer strengthens resilience through trust-weighted aggregation and adaptive thresholding, enabling stable operation even under coordinated adversarial behavior. Meanwhile, the shard-based blockchain ensures immutable provenance with low overhead through domain-specific partitioning and cross-shard verification—addressing latency and scalability issues that typically hinder blockchain-FL integration.
Quantum circuit analysis (Figure 10) shows that current noisy intermediate-scale quantum (NISQ) hardware can implement the trust modeling component using shallow circuits of 10–15 gates, making the approach feasible for near-term deployment. As hardware matures, deeper circuits will allow more sophisticated trust modeling. Scalability tests indicate that the framework sustains high accuracy and low latency as network size grows, aided by efficient sharding, parallel quantum processing, and adaptive trust propagation. The explainability analysis further demonstrates that quantum measurements can be translated into interpretable trust metrics, ensuring transparency and regulatory compliance.
Several limitations remain. The present implementation uses quantum simulation; deployment on real hardware may introduce additional noise and error rates. The approach assumes access to secure quantum communication channels, which may not be universally available, and blockchain consensus efficiency could degrade under extreme network fragmentation. Energy consumption of quantum operations may also rise with larger networks, warranting optimization of circuit compilation and hardware-specific execution.
Overall, QuantumTrust-FedChain demonstrates strong potential for scalable, interpretable, and resilient federated learning in industrial IoT. Future work will focus on hardware-backed validation, adaptive trust propagation in dynamic environments, and energy-efficient quantum implementation to further enhance real-world feasibility.
Quantum Hardware Considerations:
While the present implementation of QuantumTrust-FedChain employs classical simulation of quantum components using the IBM Qiskit Aer backend, we acknowledge that actual deployment on noisy intermediate-scale quantum (NISQ) hardware would introduce non-negligible performance variations. On currently accessible NISQ processors (≤ 20 qubits, circuit depth ≤ 15), we anticipate an average 2–3% reduction in accuracy due to gate errors (≈ 10−3) and readout noise. To evaluate practical feasibility, a small-scale validation was performed using IBM Q Manila (5 qubits), where the Q-GAT circuit produced trust-state measurements consistent within ± 2% of simulation results. Standard error-mitigation techniques—including Zero-Noise Extrapolation, measurement error calibration, and basis rotation averaging—were applied to minimize noise impact. These results confirm that the quantum trust modeling and anomaly-detection operations are implementable on near-term quantum devices with shallow circuit depth. Future work will extend this validation to multi-qubit hardware configurations and hybrid quantum-classical deployments for real-time industrial IIoT trust evaluation.
Privacy Considerations:
From a privacy perspective, gradient inversion and data leakage were tested under partial model visibility. Injecting small Gaussian noise (σ = 1 × 10−3) into local gradients reduced inversion success by over 80% with less than 1% accuracy loss, demonstrating strong baseline protection. Secure aggregation and on-chain encryption further prevent metadata exposure. Future work will extend these measures through formal differential privacy guarantees using the (ε, δ)-DP model and explore privacy-aware trust calibration for large-scale federated deployments.
6.1. Performance Analysis and Metrics
The detailed performance analysis reveals multiple dimensions of improvement achieved by QuantumTrust-FedChain across all three datasets. Table 8 presents comprehensive performance metrics across different evaluation criteria including computational efficiency, security resilience, and scalability factors, with results averaged across SWaT, TON IoT, and synthetic dataset evaluations.

Table 8.
Comprehensive Performance Metrics Analysis Across All Datasets.
The performance analysis demonstrates significant improvements across all datasets and attack scenarios. The network attack detection improvement of 11.4% shows the framework’s effectiveness against traditional IoT attacks present in SWaT and TON IoT datasets. More notably, the 20.5% improvement in federated learning attack detection and 24.4% improvement in combined attack scenarios validate the quantum-enhanced approach’s superiority in defending against sophisticated multi-vector attacks.
Dataset-specific performance shows consistent improvements, with the highest gains achieved on the SWaT dataset (10.6% improvement) due to the framework’s effectiveness in critical infrastructure protection. The synthetic dataset results (5.8% improvement) demonstrate the framework’s scalability and robustness in large-scale heterogeneous environments with up to 500 participating devices.
6.2. Security Resilience and Attack Mitigation
The security evaluation focused on the framework’s resilience against various attack vectors present in the three datasets and synthesized federated learning attacks. Table 9 presents detailed analysis of attack mitigation capabilities across different threat scenarios, with results aggregated across SWaT (network infrastructure attacks), TON IoT (IoT-specific threats), and synthetic dataset (advanced persistent threats).

Table 9.
Security Resilience Analysis Against Dataset-Specific and FL Attacks.
The security analysis reveals consistently high detection rates across all attack categories derived from the three datasets. Traditional network attacks from SWaT and TON IoT (DoS, MitM, backdoor, injection, ransomware) achieve detection rates between 93.8% and 97.8%. Notably, the synthesized federated learning attacks show even higher detection rates, with model poisoning achieving 98.9% detection due to the quantum trust modeling’s sensitivity to behavioral anomalies in collaborative learning scenarios.
The mitigation times vary by attack complexity, with federated learning attacks (model poisoning, Byzantine failures) showing faster response times due to the real-time quantum trust monitoring. Recovery rates demonstrate the system’s ability to restore normal operation after attack mitigation, with federated learning attacks achieving higher recovery rates due to the distributed nature of the defense mechanisms.
Table 10 provides detailed scalability metrics showing how the framework performs across the three datasets with different network configurations and device heterogeneity levels. The evaluation covers SWaT’s 51-device water treatment environment, TON IoT’s 200-device heterogeneous setup, and the synthetic dataset’s large-scale 500-device multi-domain scenario.

Table 10.
Scalability Performance across Dataset Configurations.
The scalability analysis demonstrates consistent performance improvements as the framework scales from the smallest SWaT configuration (51 devices) to the largest synthetic setup (500 devices). Interestingly, accuracy increases with scale due to the quantum trust modeling’s improved collective intelligence with more participants, reaching 98.6% in the 500-device scenario compared to 97.8% in the 51-device setup.
The latency increase is approximately logarithmic with network size, indicating efficient load distribution across quantum processing units and blockchain shards. The synthetic dataset’s multi-domain evaluation confirms the framework’s versatility across different industrial applications, with autonomous vehicle scenarios achieving the highest accuracy (98.9%) due to the high-frequency communication patterns that enable more precise trust modeling.
Device heterogeneity analysis shows that the framework maintains robust performance across different device capability profiles present in each dataset. SWaT’s homogeneous sensor environment achieves the best performance metrics due to predictable behavior patterns, while TON IoT’s mixed capability devices show modest performance reductions. The synthetic dataset’s high diversity scenario demonstrates the framework’s resilience in complex heterogeneous environments.
The security resilience evaluation involved systematic testing against multiple threat models including model poisoning attacks, gradient inversion attacks, Byzantine failures, and coordinated adversarial behavior. QuantumTrust-FedChain demonstrated superior performance in detecting and mitigating these attacks through its quantum-enhanced anomaly detection and trust-weighted aggregation mechanisms.
7. Conclusions
This paper presented QuantumTrust-FedChain, a novel framework that integrates quantum-enhanced trust modeling, blockchain-backed provenance tracking, and Byzantine-robust federated learning to address critical security and trust challenges in Industrial IoT (IIoT) environments. Experimental results across the SWaT, TON IoT, and synthetic industrial datasets demonstrate that the framework achieves an average accuracy of 98.3% and a 35% improvement in defense against model poisoning attacks, while maintaining blockchain overhead below 8.5%.
The proposed Q-GAT-based quantum trust modeling effectively captures complex, dynamic device relationships and enables adaptive defense against evolving adversarial behaviors. The shard-based blockchain ledger ensures efficient, scalable audit trails and consensus validation, supporting real-time operations across diverse industrial domains, including manufacturing, smart grids, and autonomous vehicles. Comparative analysis against ten state-of-the-art baselines further confirms QuantumTrust-FedChain’s superior performance across accuracy, attack detection, latency, and scalability.
The findings demonstrate that combining quantum-enhanced trust mechanisms with secure gradient aggregation and efficient provenance tracking enables resilient and explainable federated learning for IIoT deployments. Future research will focus on optimizing quantum circuit implementations for NISQ hardware, enhancing adaptive consensus protocols for highly dynamic industrial environments, and extending the framework to support cross-domain trust management and multi-stakeholder governance models. Although the framework demonstrates strong simulated results, future work will focus on hardware-backed experiments using emerging NISQ processors to validate real-world feasibility.
Funding
This research received no external funding.
Institutional Review Board Statement
This research study solely involves the use of historical datasets. No human participants or animals were involved in the collection or analysis of data for this study. As a result, ethical approval was not required.
Data Availability Statement
The datasets used in this study are available as follows: 1. SWaT Dataset: Available from the Singapore University of Technology and Design (SUTD) Industrial Control Systems (ICS) Security Testbed repository at https://itrust.sutd.edu.sg/itrust-labs_datasets/dataset_info/, accessed on 25 September 2025. 2. TON IoT Dataset: Available from the UNSW Canberra Cyber repository at https://research.unsw.edu.au/projects/toniot-datasets, accessed on 25 September 2025. All preprocessing scripts, data splits (70%/15%/15%), and experimental configurations used in this study can be provided on a reasonable request from the corresponding author to ensure full reproducibility.
Acknowledgments
The author would like to thank the Deanship of Scientific Research at Shaqra University for supporting this work.
Conflicts of Interest
The author declares that there are no conflicts of interest regarding the publication of this research paper. The research was conducted in an unbiased manner, and there are no financial or personal relationships that could have influenced the findings or interpretations presented herein.
Nomenclature
| FL | Federated Learning |
| IoT | Internet of Things |
| IIoT | Industrial Internet of Things |
| NISQ | Noisy Intermediate-Scale Quantum |
| Q-GAT | Quantum Graph Attention Network |
| BRFO | Byzantine-Robust Federated Optimizer |
| SBL | Shard-based Blockchain Ledger |
| VQE | Variational Quantum Eigensolver |
| QAOA | Quantum Approximate Optimization Algorithm |
| CPS | Cyber-Physical Systems |
| Quantum trust state for device at time | |
| Quantum amplitude for state of device | |
| Classical trust score for device at time | |
| Global model parameters at round | |
| Local gradient from device at round | |
| Learning rate | |
| Byzantine tolerance threshold at time | |
| Trust Hamiltonian operator | |
| Variational quantum parameters | |
| Quantum entanglement between devices and |
References
- Kalodanis, K.; Papapavlou, C.; Feretzakis, G. Enhancing Security in 5G and Future 6G Networks: Machine Learning Approaches for Adaptive Intrusion Detection and Prevention. Future Internet 2025, 17, 312. [Google Scholar] [CrossRef]
- Alnaim, A.K.; Alwakeel, A.M. Zero Trust Strategies for Cyber-Physical Systems in 6G Networks. Mathematics 2025, 13, 1108. [Google Scholar] [CrossRef]
- Tran, D.H.; Waheed, N.; Saputra, Y.M.; Lin, X.; Nguyen, C.T.; Abdu, T.S.; Vo, V.N.; Pham, V.Q.; Alsenwi, M.; Adam, A.B.M.; et al. Network Digital Twin for 6G and Beyond: An End-to-End View Across Multi-Domain Network Ecosystems. IEEE Open J. Commun. Soc. 2025, 6, 6866–6911. [Google Scholar] [CrossRef]
- Quan, M.K.; Pathirana, P.N. Federated learning for cyber physical systems: A comprehensive survey. IEEE Commun. Surv. Tutor. 2025. [Google Scholar] [CrossRef]
- Oukebdane, M.A.; Shah, A.F.M.S.; Azad, A.K.; Ekoru, J. Unraveling the nexus of ML and 6G: Challenges, Opportunities, and Future Directions. IEEE Commun. Mag. 2025, 13, 114934–114958. [Google Scholar] [CrossRef]
- Chamola, V.; Peelam, M.S.; Guizani, M. Future of connectivity: A comprehensive review of innovations and challenges in 7g smart networks. IEEE Open J. Commun. Soc. 2025, 6, 3555–3613. [Google Scholar] [CrossRef]
- Zeydan, E.; De Alwis, C.; Khan, R.; Turk, Y. Quantum Technologies for Beyond 5G and 6G Networks: Applications, Opportunities, and Challenges. arXiv 2025, arXiv:2504.17133. [Google Scholar] [CrossRef]
- Turnip, T.N.; Andersen, B. Towards 6G Authentication and Key Agreement Protocol: A Survey on Hybrid Post Quantum Cryptography. IEEE Commun. Surv. Tutor. 2025. [Google Scholar] [CrossRef]
- Hakeem, S.A.A.; Kim, H.W. Advancing Intrusion Detection in V2X Networks: A Comprehensive Survey on Machine Learning, Federated Learning, and Edge AI for V2X Security. IEEE Trans. Intell. Transp. Syst. 2025, 26, 11137–11205. [Google Scholar] [CrossRef]
- Trigka, M.; Dritsas, E. Wireless Sensor Networks: From Fundamentals and Applications to Innovations and Future Trends. IEEE Access 2025, 13, 96365–96399. [Google Scholar] [CrossRef]
- Rajesh, K.; Vetrivelan, P. Comprehensive analysis on 5G and 6G wireless network security and privacy. Telecommun. Syst. 2025, 88, 52. [Google Scholar] [CrossRef]
- Jain, M.; Verma, R.; Kumar, S.; Kumar, G. Unveiling the future: A comprehensive analysis of 6G technology and its transformative potential. Telecommun. Syst. 2025, 88, 91. [Google Scholar] [CrossRef]
- Mathur, A.; Gupta, A.; Das, S.K. When federated learning meets quantum computing: Survey and research opportunities. arXiv 2025, arXiv:2504.08814. [Google Scholar] [CrossRef]
- Ren, C.; Yan, R.; Zhu, H.; Yu, H.; Xu, M. Toward Quantum Federated Learning. IEEE Trans. Neural Netw. Learn. Syst. 2025, 36, 15580–15600. [Google Scholar] [CrossRef]
- Addo, K.; Kabeya, M.; Ojo, E.E. Federated Quantum Machine Learning for Distributed Cybersecurity in Multi-Agent Energy Systems. Energies 2025, 18, 5418. [Google Scholar] [CrossRef]
- Sanjalawe, Y.; Fraihat, S.; Abualhaj, M. A review of 6G and AI convergence: Enhancing communication networks with artificial intelligence. IEEE Open J. Commun. Soc. 2025, 6, 2308–2355. [Google Scholar] [CrossRef]
- Gottam, S.R.; Kar, U.N. Graph Attention Transformer-Based Meta-Reinforcement Learning for Secure and Low-Latency D2D Routing in 6G Networks. TechRxiv 2025. [Google Scholar] [CrossRef]
- Aloudat, M.Z.; Aboumadi, A.; Soliman, A. Metaverse Unbound: A Survey on Synergistic Integration Between Semantic Communication, 6G, and Edge Learning. IEEE Commun. Mag. 2025, 13, 58302–58350. [Google Scholar] [CrossRef]
- Aramide, O.O. Quantum-Safe Networking for Critical AI/ML Infrastructure. J. Data Anal. Crit. Manag. 2025, 1, 19–29. [Google Scholar] [CrossRef]
- El-Hajj, M. Secure and Trustworthy Open Radio Access Network (O-RAN) Optimization: A Zero-Trust and Federated Learning Framework for 6G Networks. Future Internet 2025, 17, 233. [Google Scholar] [CrossRef]
- Punitha, S.; Preetha, K.S. Enhancing reliability and security in cloud-based telesurgery systems leveraging swarm-evoked distributed federated learning framework to mitigate multiple attacks. Sci. Rep. 2025, 15, 27226. [Google Scholar] [CrossRef]
- Liu, J.; Du, Y.; Yang, K.; Wang, Y.; Hu, X.; Wang, Z. Edge-Cloud Collaborative Computing on Distributed Intelligence and Model Optimization: A Survey. arXiv 2025, arXiv:2505.01821. [Google Scholar] [CrossRef]
- Timofte, E.M.; Dimian, M.; Graur, A.; Potorac, A.D.; Balan, D. Federated Learning for Cybersecurity: A Privacy-Preserving Approach. Appl. Sci. 2025, 15, 6878. [Google Scholar] [CrossRef]
- Hong, Y.; Wu, J.; Guan, X. A survey of joint security-safety for function, information and human in industry 5.0. Secur. Saf. 2025, 4, 2024014. [Google Scholar] [CrossRef]
- Wang, J.; Manna, S.; Aksoy, M.; Sarkar, A. Empowering secure and sustainable healthcare through federated learning and blockchain synergies in a Medical Internet of Things. Int. J. Mach. Learn. Cybern. 2025, 16, 7973–8005. [Google Scholar] [CrossRef]
- Kamdem-Fezeu, H.W.; Ndie, T.D. Non-Repudiation in Decentralized Wireless Networks in the Age of AI: A Comprehensive Review. Preprints, 2025. [Google Scholar] [CrossRef]
- Shah, A.F.M.S.; Karabulut, M.A.; Kamruzzaman, A. A Survey on Artificial Intelligence and Blockchain Clustering for Enhanced Security in 6G Wireless Networks. Comput. Mater. Contin. 2025, 84, 1981–2013. [Google Scholar] [CrossRef]
- Vasileios, K.; Trevlakis, S.E.; Boulogeorgos, A.-A.A.; Liu, H.; Khalid, W.; Tsiftsis, T.A. Hierarchical Blockchain Radio Access Networks: Architecture, Modelling, and Performance Assessment. IEEE Open J. Commun. Soc. 2025, 6, 576–592. [Google Scholar] [CrossRef]
- Radhakrishnan, K.; Ramakrishnan, D. Federated Learning for Artificial Intelligence in Embedded Systems. ICCK Trans. Comput. 2025, 2, 91–115. [Google Scholar] [CrossRef]
- Li, K.; Li, C.; Yuan, X.; Li, S.; Zou, S.; Ahmed, S.S.; Ni, W. Zero-trust foundation models: A new paradigm for secure and collaborative artificial intelligence for internet of things. arXiv 2025, arXiv:2505.23792. [Google Scholar] [CrossRef]
- Bozdal, M.; Ileri, K.; Ozkahraman, A. Comparative analysis of dimensionality reduction techniques for cybersecurity in the SWaT dataset. J. Supercomput. 2024, 80, 1059–1079. [Google Scholar] [CrossRef]
- Cao, Z.; Zhao, Z.; Shang, W.; Ai, S.; Shen, S. Using the TON IoT dataset to develop a new intrusion detection system for industrial IoT devices. Multimed. Tools Appl. 2025, 84, 16425–16453. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).