A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications
Abstract
:1. Introduction
- We propose a secure and efficient multi-factor authentication algorithm for mobile money applications where PIN, OTP, and biometric fingerprints authenticate users. It also authorizes mobile money withdrawal by scanning the fingerprints of the mobile money users and the secure QR code of the mobile money agent that contains the unique mobile money agent code.
- We present the different ways of securing user authentication credentials such as PIN and OTP using SHA-256, biometric fingerprint by FIDO services that use the public-key cryptography technique (RSA), and a QR code and records in the databases by Fernet encryption.
- We design and implement the proposed secure and efficient multi-factor authentication algorithm for mobile money applications by developing G-MoMo application prototypes to prove that the algorithm is feasible and provides a higher degree of security.
- We present a comparative security and performance analysis of our proposed algorithm.
2. Related Work
2.1. Studies Related to Mobile Money Systems
2.2. Problem Statement
2.3. Technologies
- ▪
- Personal Identification Number (PIN)
- ▪
- One-Time Password (OTP)
- ▪
- Quick Response (QR) Code
- ▪
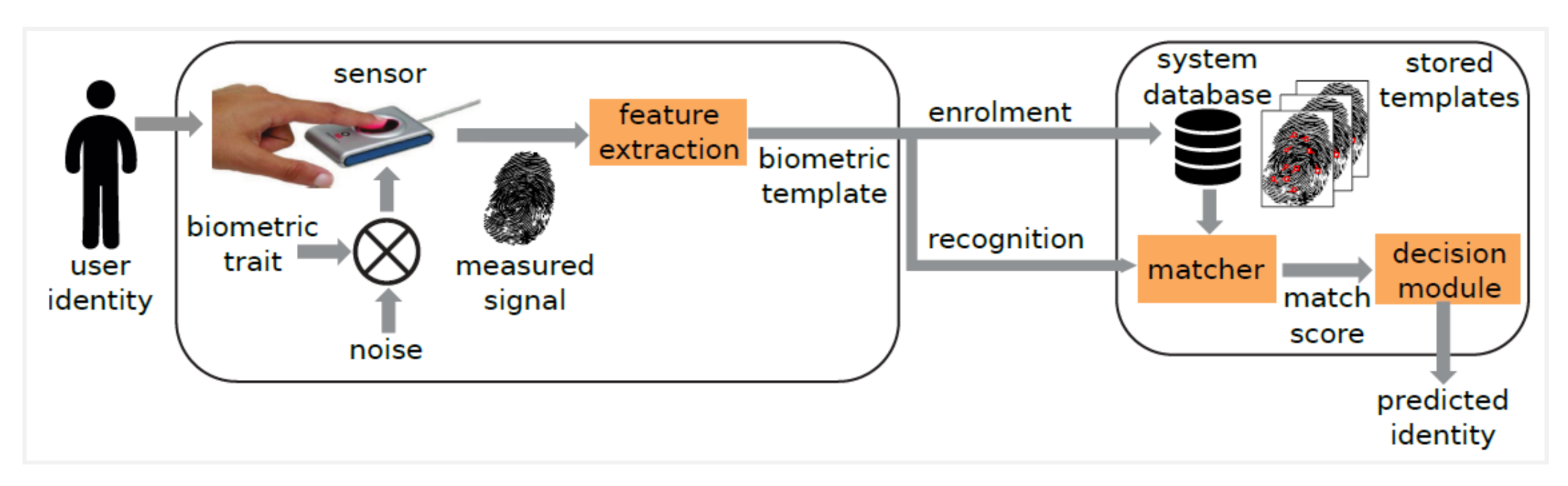
- Biometric Fingerprint
- ▪
- Secure Hashing Algorithm-256 (SHA-256)
- ▪
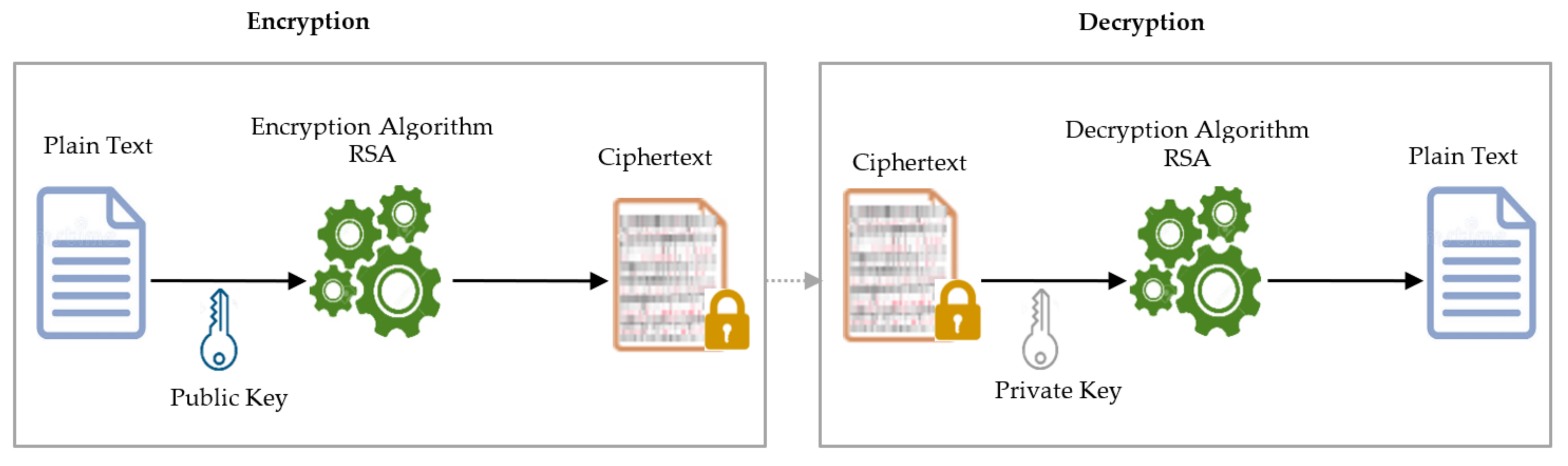
- Fast IDentity Online (FIDO)
- Fernet Encryption
3. Proposed Algorithm
- 1.
- Enrolment Phase
- Step 1. The mobile money must capture the ’s , i.e., .
- Step 2. The mobile money then verifies the provided by the . If the is wrong, the has three (3) attempts; otherwise, the information is saved in the .
- Step 3. The must complete the registration process by entering a five-digit and re-enter the five-digit .
- Step 4. If the five-digit entered and the re-entered do not match, the is required to enter the correct mobile money PIN; otherwise, it is hashed using the SHA-256, and saved in the .
- Step 5. The must use the fingerprint sensor to scan their . If the is successfully captured, the creates a new pair unique to the and ’s account. The is encrypted using RSA, sent to the and saved in a Keystore. The and the are encrypted using RSA, and stored in the under cryptographic Keystore and , respectively.
- Step 6. The stores and sends to the and .
- Step 7. The checks whether the or exists. If yes, the is requested to enter a new and for the registration; otherwise, the and records are encrypted using the Fernet, i.e., , save it in the and , and a notification for successful registration is displayed to the .
Algorithm 1 Enrolment Phase Input:, START 1 . 2 for () { 3 if ) then 4 in the 5 , } 6 if () AND ()) then 7 Hash the using SHA-256, and save in the . 8 else 9 Enter a valid 10 end if 11 Retrieve the biometric fingerprint feature, and pairs are created, i.e., .
is encrypted using RSA, sent to the and saved in a Keystore.
The and the are encrypted using RSA, , and stored in the under cryptographic Keystore and .12 The stores and sends to the and . 13 The checks whether the and exists. If yes, the is requested to enter a new and for the registration, else, the and records are encrypted using the Fernet, i.e., ; save it in the and
A notification for successful registration is displayed to the .14 else 15 Invalid user data 16 end if 17 18 Return STOP
- 2.
- Authentication Phase
- Step 1. The mobile money must enter their five-digit during the authentication phase to . Note that the can only attempt the authentication three (3) times.
- Step 2. The sends to the for validation.
- Step 3. The checks if the match. If they do not match, the transaction is terminated; otherwise, is generated and sent to the mobile money via SMS, and the copy of the sent is hashed using the SHA-256, and stored in the .
- Step 4. The is requested to enter the received . Note that the is valid for only 60 s.
- Step 5. When the mobile money enters the and does not match with the copy stored in the , i.e., , the transaction is terminated. Otherwise, the is required to scan the for recognition using the .
- Step 6. Once the scans the and it matches the , the protected resource informs the FIDO server component of the server-side application, which sends a challenge to the ’s . The FIDO authenticator (i.e., ) locally verifies the ’s identity based on the by generating a key pair and comparing the with the copy stored under the Keystore in the The are compared with the copy stored in the ’s under the cryptographic Keystore and respectively.
- Step 7. If the pairs do not match, the authentication will be terminated. Otherwise, the is authenticated and can now perform transactions.
Algorithm 2 Authentication Phase Input: START 1 . 2 for () { 3 if ) then 4 Request for the generation of 5 Send to the
Hash the sent using the SHA-256, and store in the6 Display the for the to read. 7 else 8 Invalid and transaction terminated 9 end if 10 . 11 if ) then 12 Scan the for recognition using the 13 else 14 Invalid and transaction terminated 15 end if 16 using the fingerprint sensor. 12 if ) then 13 pair are created. The is decrypted, , and compared with . The are also decrypted, and and compared with and , respectively.
if AND thenThe is authenticated successfully and can proceed to transaction. else Invalid end if 14 else 15 Invalid and transaction terminated end if 18 19 Return STOP
- 3.
- Transaction Phase
- Step 1. The mobile money begins the money withdrawal transaction by signing in to the application by entering their , , and .
- Step 2. If the , , and match, the is logged in, and the system displays the available the mobile money has.
- Step 3. If the is greater than or equals to 5000 and the mobile money wants to withdraw money, they can enter an less than or equal to the available .
- Step 4. The system then requests the to scan their using the fingerprint sensor.
- Step 5. If the scanned matches, the system requests the to scan the secure of the mobile money using the smart scanner for confirmation purposes.
- Step 6. If the scanned secure matches, the system displays a successful withdrawal message seeking the to collect money from the mobile money .
Algorithm 3 Transaction Phase—Withdraw Money Input: START 1 2 for () { 3 if ) then 4 The user is successfully logged in, and the system checks for the available 5 else 6 Invalid Login Credentials 7 end if 8 9 Return 10 if () then 11 Enter the to withdraw 12 else 13 Insufficient 14 end if 15 16 if () then 17 Scan 18 using the fingerprint sensor 19 if then 20 pair is created. The is decrypted, and compared with . The are also decrypted, and and compared with and , respectively. 21 then 22 Scan the ’s secure for confirmation 23 using the Smart Scanner 24 if then 25 Withdraw money from ’s account 26 Update the remaining 27 Display successful money withdrawn message 28 else 29 Invalid 30 end if 31 else 32 Invalid 33 end if 34 else 35 Invalid 36 end if 37 else 38 Insufficient 39 end if STOP
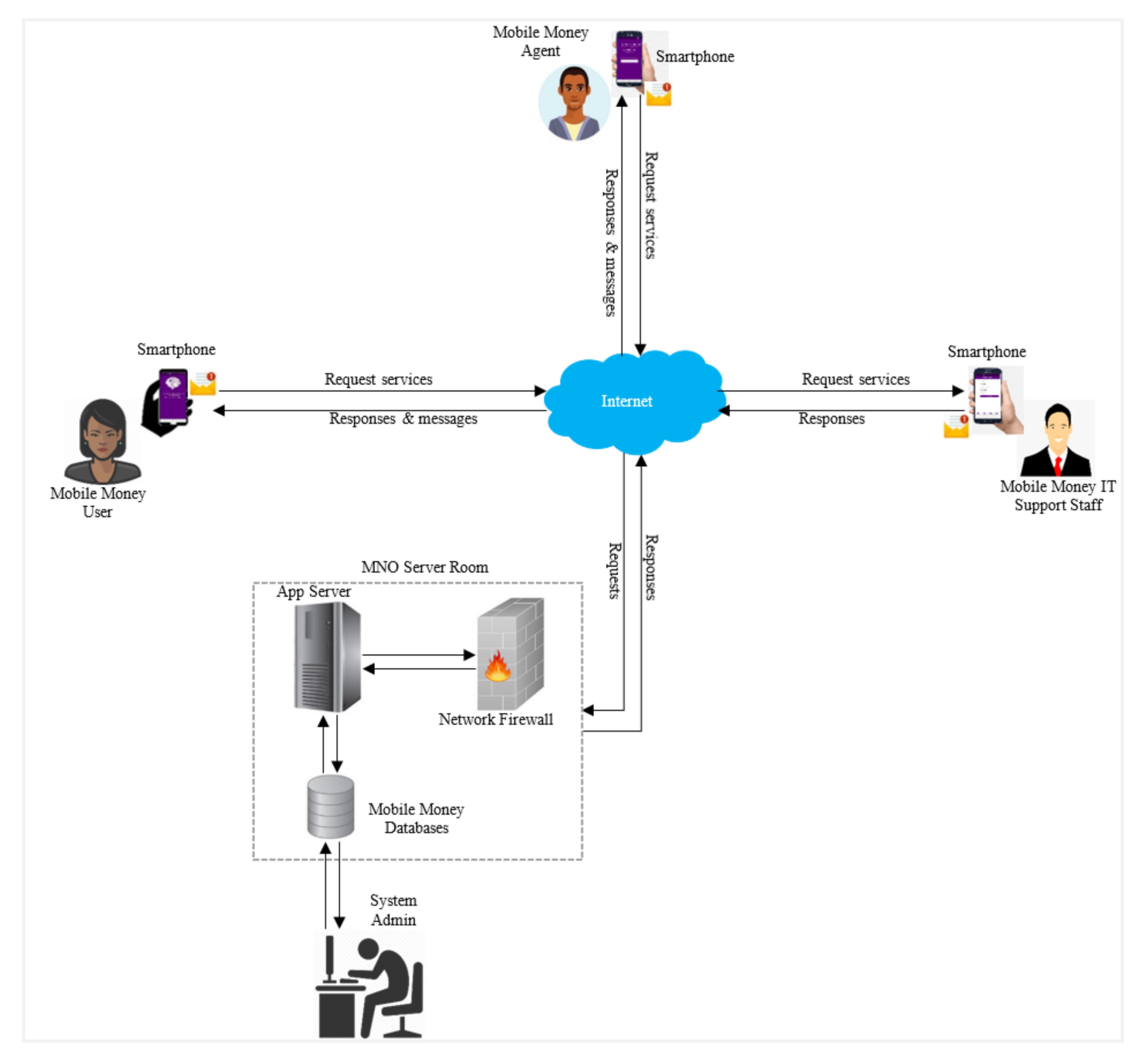
System Architecture
4. System Implementation
4.1. Software Development Tools
- ○
- Vue JS Framework
- ○
- Python
- ○
- MySQL
- ○
- Twilio programmable SMS
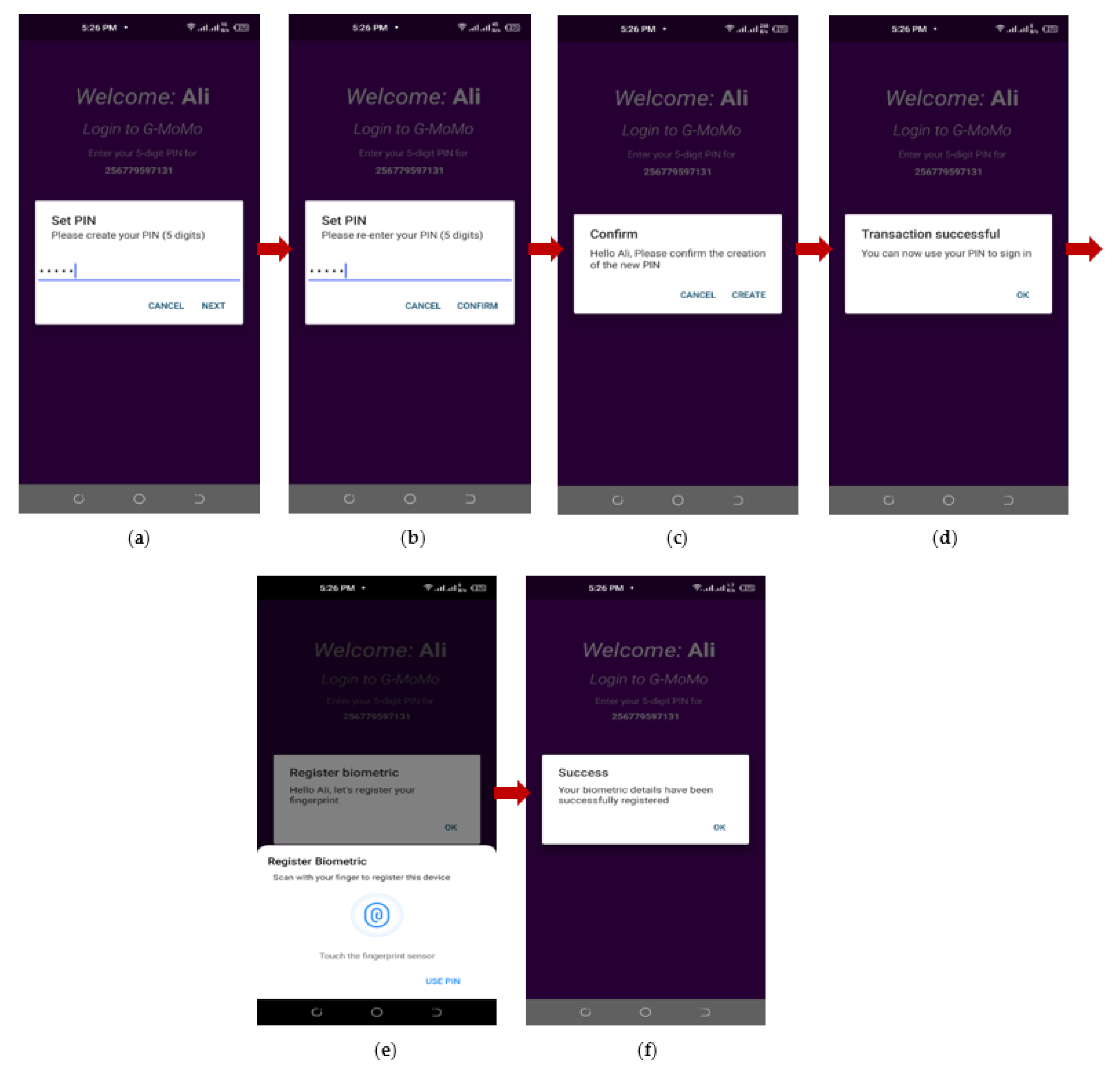
4.2. Implementation of the G-MoMo Applications Prototypes
- (a)
- Mobile Money Customer Registration
- (b)
- Mobile Money Customer Authentication Process
- (c)
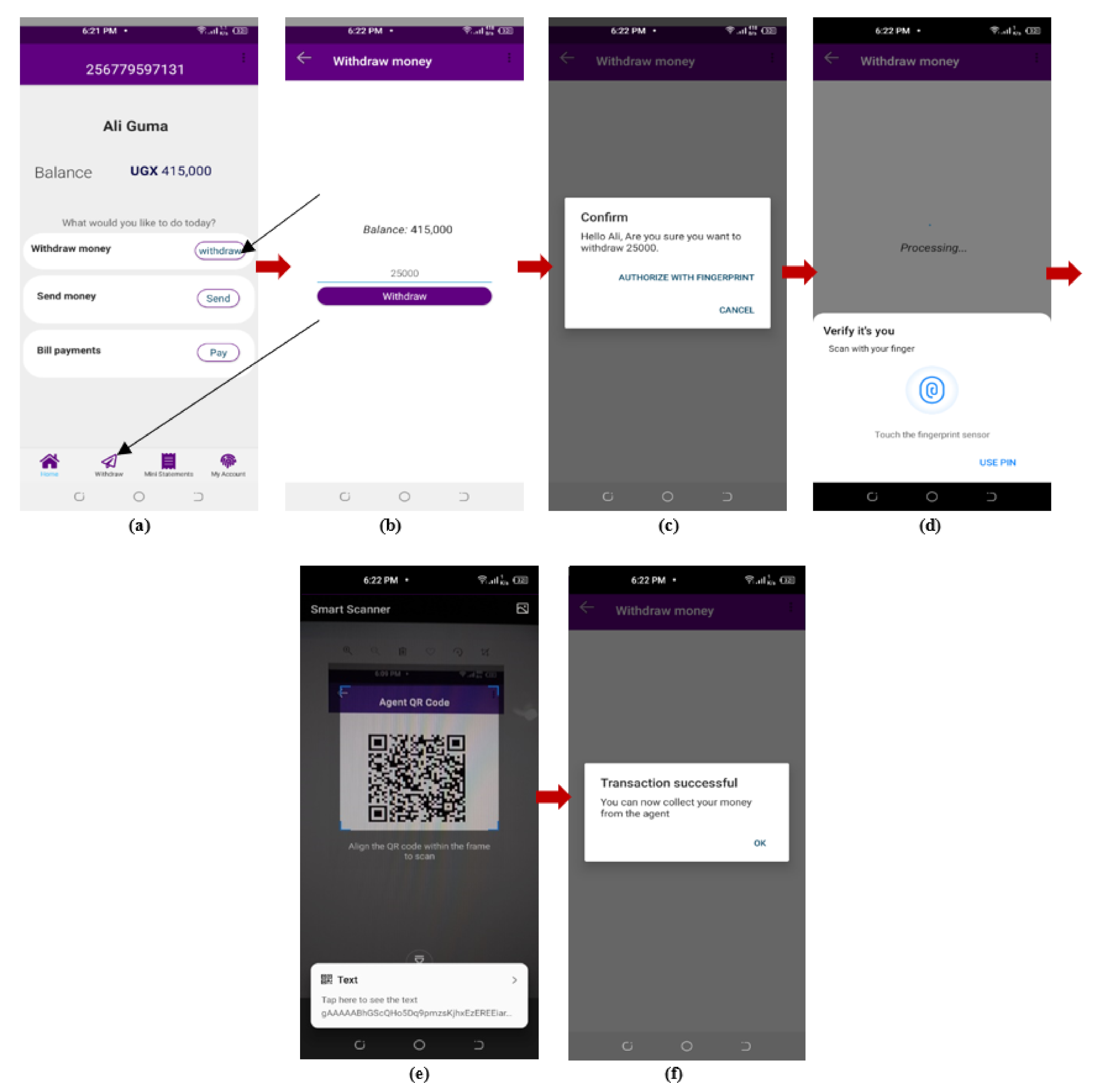
- Money Withdrawal
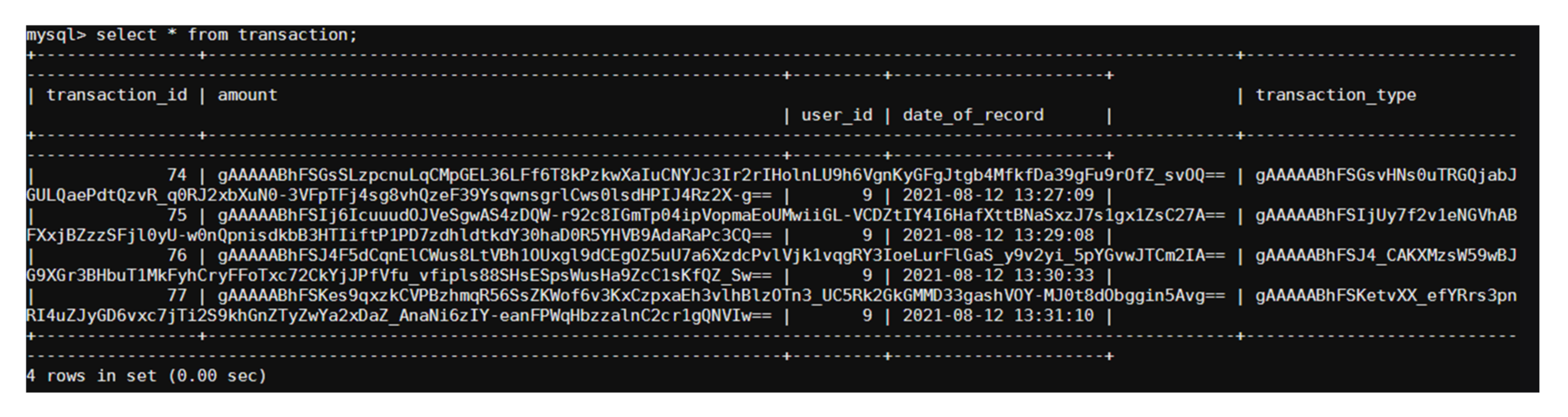
- (d)
- Encrypted Records in the Tables
5. Security Analysis
- ⇨
- Provides secure and efficient authentication: The proposed multi-factor authentication algorithm uses a PIN, OTP, and biometric fingerprint. The security of the PIN and OTP are ensured by SHA-256 and the biometric fingerprint by FIDO, which provides secure and robust authentication [14,17,46,62,63,65,68,69,70,71]. Besides, using a mobile money agent’s secure QR code in authorizing money withdrawal guarantees authenticity [81,83].
- ⇨
- Provides data confidentiality: The proposed algorithm offers confidentiality by hashing PIN and OTP using SHA-256, securing the biometric fingerprint by FIDO that uses the RSA encryption algorithm, and Fernet encryption to secure the mobile money agent code and the records in the databases. At the same time, FIDO helps secure communication channels between the application server and the mobile money IT support staff, agent, and user using RSA. It helps to secure authentication credentials from being intercepted by attackers [21,46,63,65,66,93]. Furthermore, using Fernet encryption to secure QR codes in G-MoMo applications ensures data confidentiality [46,78].
- ⇨
- Provides data integrity: The G-MoMo applications database records are protected using Fernet encryption. Likewise, the authentication credentials, such as PIN and OTP, are secured using SHA-256, and a biometric fingerprint using FIDO, which makes it difficult for the adversaries to modify or alter and insert new data and read their content both in storage and in transit, hence maintaining the integrity of the data [21,46,65]. Moreover, implementing secure QR codes in G-MoMo applications where the mobile money agent’s serial number is encrypted using Fernet encryption to generate a mobile money agent code, which is then encoded in a QR code for the user to scan during money withdrawal, helps protect data integrity [46,78].
- ⇨
- Ensures non-repudiation: During mobile money registration, the IT support staff, agents, and users avail their biodata, phone number, SIM serial number, PIN, and biometric fingerprint. The phone numbers uniquely identify the subscriber. When OTP is sent to the user’s phone number during authentication, he should not deny receiving the sent OTP because a copy of the sent OTP is saved in the user’s table, linked to the phone number. Likewise, a phone number ensures that no mobile money user can deny performing transaction(s) since every transaction is traced [21,65,66,93]. Still, using a secure QR code to store the mobile money agent code that the mobile money customer scans during mobile money withdrawal helps to ensure non-repudiation by the mobile money agent [46].
- ⇨
- Ensures anonymity: Multi-factor authentication ensures user anonymity by entering a unique PIN and biometric fingerprints that uniquely identify them. There is no physical contact between mobile money agents and users and the mobile money service provider in mobile payments. Therefore, only the mobile money payment gateway has records that can trace and identify them [46,65,66].
- ⇨
- Ensures privacy: The biometric fingerprint is protected using FIDO that uses RSA to protect public/private key pairs and biometric templates. The database records are also secured with Fernet encryption, thus protecting the credentials and transaction privacy and the privacy of the mobile money IT support staff, agents, and users [21,63,73]. In addition, the use of a secure QR code to store an encrypted mobile money agent code helps to ensure privacy [74].
- ⇨
- Prevention of shoulder-surfing attacks: The current 2FA for mobile money uses only PIN and SIM to authenticate users, which is insufficient to provide strong security. Therefore, this approach is vulnerable to shoulder-surfing attacks because the PINs are entered when they are unmasked. However, using multiple identifiers, such as PIN, OTP, biometric fingerprint, and a secure QR code, in the proposed algorithm helps to prevent shoulder-surfing attacks [13,20,23,46].
- ⇨
- Prevention of social engineering attacks: Social engineering is a typical security challenge in mobile money where attackers persuade mobile money agents and users by calling them to reveal their mobile money PINs. This security challenge is solved in the proposed algorithm by implementing multi-factor authentication where users have to avail multiple identifiers such as PIN, OTP, and biometric fingerprint to verify them. Even if the attackers obtain the PIN, it will not be easy to guess the next OTP since it is generated randomly and only valid for 60 s. It is also challenging to get the biometric fingerprints because it is secured using FIDO, where public/private key pairs are generated. The private key and biometric templates are kept in the user’s smartphone and the public key in the FIDO database.
- ⇨
- Prevention of phishing attack: A phishing attack is where adversaries disguise themselves as the staff of the mobile money service provider by sending messages or voice calls to mobile money agents and users requesting them to avail their mobile money PINs. Once they succeed in obtaining the user’s PIN, they can perform fraudulent transactions. The proposed algorithm solves this problem by implementing multi-factor authentication using a PIN, OTP, and biometric fingerprint. The OTP is random and unique and only valid for 60 s. The biometric fingerprint is secured using FIDO that uses RSA to generate public/private key pairs. The generated public key is encrypted and sent to the online FIDO database associated with the user’s mobile money account and saved in a Keystore. The private key and biometric templates are encrypted and stored in the smartphone’s cryptographic Keystore and smartphone [20,62,68,69,70,71]. Moreover, integrating a secure QR code in mobile money agent authorization helps prevent phishing attacks [77].
- ⇨
- Prevention of PIN-guessing attack: The current 2FA scheme for mobile money uses four- or five-digit PINs to authenticate users, making it easy for the attacker to guess because of their simplicity. This attack is mitigated in the proposed algorithm using additional authentication factors such as OTP and biometric fingerprint. The OTP sent to users is four digits and is randomly generated, making it difficult for the attacker to guess the next OTP. Besides, the OTP is hashed using SHA-256 and encrypted using Fernet before saving it in the database. Furthermore, biometric fingerprints are secured using FIDO that uses RSA, making it complicated for the adversaries to guess the public and private keys used. The biometric template is encrypted and stored in the user’s smartphone [20].
- ⇨
- Prevention of brute-force attack: Attackers are familiar with PIN-based authentication systems, and most of the PINs used are easy to crack. Therefore, even if the PIN and OTP are cracked, it becomes difficult to break the FIDO system because it uses RSA to encrypt public/private key pairs and biometric templates. The encrypted private key and biometric template are stored in the user’s smartphone, and the encrypted public key is stored in the FIDO database. Similarly, the secure QR code to store the encrypted mobile money agent code that the customer scans to confirm mobile money withdrawal helps prevent brute-force attacks [20,46].
- ⇨
- Resistance to replay attacks: In the current 2FA scheme for mobile money, the adversaries delay or replay the authentication process several times to allow mobile money agents and users to enter their mobile money PIN several times until the attacker gets hold of the PIN. In the proposed algorithm, the researchers implemented a multi-factor authentication scheme where users must enter multiple identifiers, such as PIN, OTP, and biometric fingerprint, to verify themselves, which helps prevent replay attacks. In addition, the PIN and OTP are secured using SHA-256 and biometric fingerprints by FIDO, where the public/private key pair and biometric templates are encrypted using RSA, and the mobile money agent code stored in the QR code is secured by Fernet encryption. Protecting the authentication identifiers makes it difficult for the adversaries to perform replay attacks [62,66,68,69,70,71,93].
- ⇨
- Resistance to insider attacks: Insider attacks are perpetrated by the employees and former employees of the mobile money service providers since they have inside information about the mobile money systems and access to mobile money agents and users’ PIN and transaction data. They take advantage of being within the organization to perform fraudulent transactions at the expense of users. The proposed algorithm mitigates this attack by using Fernet encryption to secure records in the database [66,73].
- ⇨
- Resistance to impersonation attacks: This attack is easy because attackers are familiar with the current 2FA scheme for mobile money. In the proposed algorithm, impersonation attacks are mitigated by (1) registering and identifying users with their phone number since no two persons will have the same phone number and (2) implementing multi-factor authentication involving PIN, OTP, and biometric fingerprints. Additionally, we secure the authentication identifiers, such as PIN and OTP, using SHA-256, biometric fingerprint by FIDO, a QR code, and records in the database using Fernet encryption [23,66].
- ⇨
- Resistance to identity fraud: The current 2FA scheme for mobile money is prone to identity fraud. However, this threat model is mitigated in the proposed algorithm by implementing a solid and robust multi-factor authentication scheme using the PIN, OTP, biometric fingerprint, and secure QR [13,19,21,46]. Moreover, protecting the authentication identifiers, such as PIN and OTP, using SHA-256, biometric fingerprint by FIDO, a QR code, and records in the database using Fernet encryption helps to mitigate identity fraud [23,66].
- ⇨
- Resistance to man-in-the-middle (MITM) attack: With the current 2FA scheme for mobile money, attackers can intercept communication between mobile money agents, users, systems, and banks. Attackers secretly steal the authentication credentials, such as a PIN or personal transaction information, spy on the user, or interrupt communications. This attack is prevented in the proposed algorithm by securing the PIN and OTP using SHA-256, biometric fingerprint by FIDO, QR code, and records in the database by Fernet encryption [20,62,68,69,70,71,93]. Likewise, the authentication identifiers, such as PIN and OTP, and public keys are hashed and encrypted before transmitting them online.
6. Performance Analysis
6.1. Communication Overhead
6.2. Computational Cost
7. Comparison with Other Related Works
7.1. Security Features
7.2. Performance Comparisons
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hendershott, T.; Zhang, X.; Zhao, J.L.; Zheng, Z. FinTech as a Game Changer: Overview of Research Frontiers. Inf. Syst. Res. 2021, 32, 1–17. [Google Scholar] [CrossRef]
- Barbu, C.M.; Florea, D.L.; Dabija, D.-C.; Constantin, M.; Barbu, R. Customer Experience in Fintech. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 1415–1433. [Google Scholar] [CrossRef]
- Dharmadasa, P.D.C.S. “Fintech Services” and the Future of Financial Intermediation: A Review. Sri Lanka J. Econ. Res. 2021, 8, 21–38. [Google Scholar] [CrossRef]
- Langley, P.; Leyshon, A. The Platform Political Economy of FinTech: Reintermediation, Consolidation and Capitalisation. New Polit. Econ. 2020, 26, 376–388. [Google Scholar] [CrossRef]
- Lu, B.; Hao, S.; Pinedo, M.; Xu, Y. Frontiers in Service Science: Fintech Operations—An Overview of Recent Developments and Future Research Directions. Serv. Sci. 2021, 13, 19–35. [Google Scholar] [CrossRef]
- Cornelli, G.; Frost, J.; Gambacorta, L.; Rau, R.; Wardrop, R.; Ziegler, T. Fintech and Big Tech Credit: What Explains the Rise of Digital Lending? CESifo Forum 2021, 22, 30–34. [Google Scholar]
- Sharma, Y. Mobile Payments Market—Global Opportunity Analysis and Industry Forecast, 2014–2022. 2017. Available online: www.alliedmarketresearch.com/mobile-payments-market (accessed on 10 May 2020).
- Jakhiya, M.; Bishnoi, M.M.; Purohit, H. Emergence and growth of mobile money in modern India: A study on the effect of mobile money. In Proceedings of the 2020 Advances in Science and Engineering Technology International Conferences (ASET), Dubai, United Arab Emirates, 4 February–9 April 2020; pp. 1–10. [Google Scholar]
- Ali, G.; Dida, M.A.; Sam, A.E. Evaluation of key security issues associated with mobile money systems in Uganda. Information 2020, 11, 309. [Google Scholar] [CrossRef]
- Egami, H.; Matsumoto, T. Mobile money use and healthcare utilization: Evidence from rural Uganda. Sustainability 2020, 12, 3741. [Google Scholar] [CrossRef]
- Ali, G.; Dida, M.A.; Sam, A.E. Two-factor authentication scheme for mobile money: A review of threat models and countermeasures. Future Internet 2020, 12, 160. [Google Scholar] [CrossRef]
- Basigie, A.; Mtaho, L. Securing Mobile Money Services in Tanzania: A Case of Vodacom M-Pesa. Int. J. Comput. Sci. Netw. Solut. 2014, 2, 1–11. [Google Scholar]
- Mtaho, B.A. Improving Mobile Money Security with Two-Factor Authentication. Int. J. Comput. Appl. 2015, 109, 9–15. [Google Scholar]
- Mega, B. Framework for Improved Security on Usage of Mobile Money Application Based on Iris Biometric Authentication Method in Tanzania. Master’s Thesis, The University of Dodoma, Dodoma, Tanzania, 2020. [Google Scholar]
- Islam, I.; Munim, K.M.; Islam, M.N.; Karim, M.M. A proposed secure mobile money transfer system for SME in Bangladesh: An industry 4.0 perspective. In Proceedings of the 2019 International Conference on Sustainable Technologies for Industry 4.0 (STI), Dhaka, Bangladesh, 24–25 December 2019; pp. 1–6. [Google Scholar]
- Chetalam, J.L. Enhancing Security of MPesa Transactions by Use of Voice Biometrics. Master’s Thesis, The United States International University—Africa, Nairobi, Kenya, 2018. [Google Scholar]
- Osman, F.; Nakanishi, H. High Correctness Mobile Money Authentication System. Int. J. Psychosoc. Rehabil. 2020, 24, 3544–3556. [Google Scholar] [CrossRef]
- Okpara, O.S.; Bekaroo, G. Cam-Wallet: Fingerprint-based authentication in M-wallets using embedded cameras. In Proceedings of the 2017 IEEE International Conference on Environment and Electrical Engineering and 2017 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I & CPS Europe), Milan, Italy, 6–9 June 2017; pp. 1–5. [Google Scholar]
- Coneland, R.; Crespi, N. Wallet-on-wheels—Using a vehicle’s identity for secure mobile money. In Proceedings of the 2013 17th International Conference on Intelligence in Next Generation Networks (ICIN), Venice, Italy, 15–16 October 2013; pp. 102–109. [Google Scholar]
- Hassan, M.A.; Shukur, Z. A secure multi factor user authentication framework for electronic payment system. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021; pp. 1–6. [Google Scholar]
- Vincent, O.R.; Okediran, T.M.; Abayomi-Alli, A.A.; Adeniran, O.J. An Identity-Based Elliptic Curve Cryptography for Mobile Payment Security. SN Comput. Sci. 2020, 1, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Castle, S.; Pervaiz, F.; Weld, G.; Roesner, F.; Anderson, R. Let’s talk money: Evaluating the security challenges of mobile money in the developing world. In Proceedings of the 7th Annual Symposium on Computing for Development (ACM DEV’16), New York, NY, USA, 18–20 November 2016; pp. 1–10. [Google Scholar]
- Sharma, L.; Mathuria, M. Mobile banking transaction using fingerprint authentication. In Proceedings of the 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2018; pp. 1300–1305. [Google Scholar]
- Phipps, R.; Mare, S.; Ney, P.; Webster, J.; Heimerl, K. ThinSIM-based attacks on mobile money systems. In Proceedings of the COMPASS ’18: ACM SIGCAS Conference on Computing and Sustainable Societies (COMPASS), New York, NY, USA, 20–22 June 2018; pp. 1–11. [Google Scholar]
- Alhassan, N.S.; Yusuf, M.O.; Karmanje, A.R.; Alam, M. Salami attacks and their mitigation—An overview. In Proceedings of the 5th International Conference on Computing for Sustainable Global Development, New Delhi, India, 14–16 March 2018; pp. 4639–4642. [Google Scholar]
- Altwairqi, A.F.; AlZain, M.A.; Soh, B.; Masud, M.; Al-Amri, J. Four Most Famous Cyber Attacks for Financial Gains. Int. J. Eng. Adv. Technol. 2019, 9, 2131–2139. [Google Scholar]
- Binbeshr, F.; Mat Kiah, M.L.; Por, L.Y.; Zaidan, A.A. A systematic review of PIN-entry methods resistant to shoulder-surfing attacks. Comput. Secur. 2021, 101, 102–116. [Google Scholar] [CrossRef]
- AbouSteit, M.H.S.; Tammam, A.F.; Wahdan, A. A novel approach for generating one-time password with secure distribution. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 461–466. [Google Scholar]
- Anusha, N.; Sai, A.D.; Srikar, B. Locker security system using facial recognition and One Time Password (OTP). In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 812–815. [Google Scholar]
- Zadeh, M.J.; Barati, H. Security improvement in mobile baking using hybrid authentication. In Proceedings of the 3rd International Conference on Advances in Artificial Intelligence, Istanbul, Turkey, 26–28 October 2019; pp. 198–201. [Google Scholar]
- Iftikhar, J.; Hussain, S.; Mansoor, K.; Ali, Z.; Chaudhry, S.A. Symmetric-key multi-factor biometric authentication scheme. In Proceedings of the 2nd International Conference on Communication, Computing and Digital Systems (C-CODE), Islamabad, Pakistan, 6–7 March 2019; pp. 288–292. [Google Scholar]
- Devendra, S. The Significant Role of Smartphones in Improving Consumer’s Quality of Life. Int. J. Adv. Res. Innov. Ideas Educ. 2021, 7, 578–586. [Google Scholar]
- Shaik, C. Preventing Counterfeit Products using Cryptography, QR Code and Webservice. Comput. Sci. Eng. Int. J. 2021, 11, 1–11. [Google Scholar] [CrossRef]
- Kurniawan, I.; Sudaryanto, S.; Sukarno, H. The Shifting of or Code-Based Payment Method to Improve the Competitive Advantage (Ca) at Bank Jatim through Tam Model Approach. IOSR J. Bus. Manag. 2021, 23, 22–27. [Google Scholar]
- Sabri, P.N.A.A.; Abas, A.; Din, R. Enhancing Data Storage of or Code Using C3M Technique. Eur. J. Mol. Clin. Med. 2020, 7, 3805–3813. [Google Scholar]
- Cho, J.; Seo, G.W.; Lee, J.S.; Cho, H.K.; Kang, E.M.; Kim, J.; Chun, D.-I.; Yi, Y.; Won, S.H. The usefulness of the QR code in orthotic applications after orthopaedic surgery. Healthcare 2021, 9, 298. [Google Scholar] [CrossRef]
- Chou, G.J.; Wang, R.Z. The Nested QR Code. IEEE Signal Process. Lett. 2020, 27, 1230–1234. [Google Scholar] [CrossRef]
- Din, M.M.; Anwar, R.M.; Fazal, F.A. Asset tagging for library system-does QR relevant? In Proceedings of the International Conference on Applied and Practical Sciences ICAPS (2021), Kuala Lumpur, Malaysia, 18–19 February 2021; pp. 1–11. [Google Scholar]
- Onyinyechi, O.P.; Ifeanyi, O.A.; Nnabuchi, E.N.; Nwakaego, I.P. Enhanced Business Marketing for Small Scale Enterprises Via the Quick Response Code Technology. Frontiers 2021, 1, 7–13. [Google Scholar]
- Sun, L.; Liang, S.; Chen, P.; Chen, Y. Encrypted digital watermarking algorithm for quick response code using discrete cosine transform and singular value decomposition. Multimed. Tools Appl. 2021, 80, 10285–10300. [Google Scholar] [CrossRef]
- Suebtimrat, P.; Vonguai, R. An Investigation of Behavioral Intention Towards QR Code Payment in Bangkok, Thailand. J. Asian Financ. Econ. Bus. 2021, 8, 939–950. [Google Scholar]
- Kosim, K.P.; Legowo, N. Factors Affecting Consumer Intention on QR Payment of Mobile Banking: A Case Study in Indonesia. J. Asian Financ. Econ. Bus. 2021, 8, 391–401. [Google Scholar]
- Widaningsih, S.; Suheri, A. Design of Waste Management System Using QR Code for Effective Management in Wastebank. J. Phys. 2021, 1764, 1–6. [Google Scholar] [CrossRef]
- Chaveesuk, S.; Piyawat, N. Use of QR code technology in eastern Thailand: Entrepreneur perspective. Utopía Prax. Latinoam. 2021, 26, 76–88. [Google Scholar]
- Tao, Y.; Cai, F.; Zhan, G.; Zhong, H.; Zhou, Y.; Shen, S. Floating quick response code based on structural black color with the characteristic of privacy protection. Opt. Express 2021, 29, 1–11. [Google Scholar] [CrossRef]
- Ximenes, A.M.; Sukaridhoto, S.; Sudarsono, A.; Albaab, M.R.; Basri, H.; Yani, M.A.; Islam, E. Implementation QR code biometric authentication for online payment. In Proceedings of the 2019 International Electronics Symposium (IES), Surabaya, Indonesia, 27–28 September 2019; pp. 676–682. [Google Scholar]
- Dasgupta, D.; Roy, A.; Nag, A. Biometric authentication. In Advances in User Authentication; Infosys Science Foundation Series; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Priya, S.P. Biometrics and Fingerprint Payment Technology. Int. J. Adv. Res. Comput. Sci. Technol. 2017, 5, 114–118. [Google Scholar]
- Jain, A.K.; Nandakumar, K.; Ross, A. 50 years of biometric research: Accomplishments, challenges, and opportunities. Pattern Recognit. Lett. 2015, 79, 80–105. [Google Scholar] [CrossRef]
- Buciu, I.; Gacsadi, A. Biometrics Systems and Technologies: A survey. Int. J. Comput. Commun. Control 2016, 11, 315–330. [Google Scholar] [CrossRef] [Green Version]
- Faridah, Y.; Nasir, H.; Kushsairy, A.K.; Safie, S.I.; Khan, S.; Gunawan, T.S. Fingerprint Biometric Systems. Trends Bioinform. 2016, 9, 52–58. [Google Scholar] [CrossRef] [Green Version]
- Fingerprints. Biometric Technologies. 2017. Available online: https://www.fingerprints.com/asset/assets/downloads/fingerprints-biometric-technologies-whitepaper-2017-revb.pdf (accessed on 16 May 2021).
- Wang, J.; Liu, G.; Chen, Y.; Wang, S. Construction and Analysis of SHA-256 Compression Function Based on Chaos S-Box. IEEE Access 2021, 9, 61768–61777. [Google Scholar] [CrossRef]
- Zhang, Y.; He, Z.; Wan, M.; Zhan, M.; Zhang, M.; Peng, K.; Song, M.; Gu, H. A New Message Expansion Structure for Full Pipeline SHA-2. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 1553–1566. [Google Scholar] [CrossRef]
- Al-Odat, Z.; Abbas, A.; Khan, S.U. Randomness analyses of the secure hash algorithms, SHA-1, SHA-2 and modified SHA. In Proceedings of the 2019 International Conference on Frontiers of Information Technology (FIT), Islamabad, Pakistan, 16–18 December 2019; pp. 316–321. [Google Scholar]
- Nassr, D.I. Secure Hash Algorithm-2 formed on DNA. J. Egypt. Math. Soc. 2019, 27, 1–20. [Google Scholar] [CrossRef] [Green Version]
- Aradhana, S.; Ghosh, S.M. Review Paper on Secure Hash Algorithm with Its Variants. Int. J. Tech. Innov. Mod. Eng. Sci. 2017, 3, 43–48. [Google Scholar]
- Martino, R.; Cilardo, A. A Flexible Framework for Exploring, Evaluating, and Comparing SHA-2 Designs. IEEE Access 2019, 7, 72443–72456. [Google Scholar] [CrossRef]
- Martino, R.; Cilardo, A. Designing a SHA-256 processor for blockchain-based IoT applications. Internet Things 2020, 11, 1–13. [Google Scholar] [CrossRef]
- Sghaier, A.; Zeghid, M.; Massoud, C.; Machout, M. Design and implementation of low area/power elliptic curve digital signature hardware core. Electronics 2017, 6, 46. [Google Scholar] [CrossRef] [Green Version]
- Panos, C.; Malliaros, S.; Ntantogian, C.; Panou, A.; Xenakis, C. A Security Evaluation of FIDO’s UAF Protocol in Mobile and Embedded Devices. Commun. Comput. Inf. Sci. 2017, 766, 127–142. [Google Scholar]
- Feng, H.; Li, H.; Pan, X.; Zhao, Z.; Cactilab, T. A formal analysis of the FIDO UAF protocol. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium 2021, San Diego, CA, USA, 21–25 February 2021; pp. 1–15. [Google Scholar]
- Purnomo, A.T.; Gondokaryono, Y.S.; Kim, C.S. Mutual authentication in securing a mobile payment system using encrypted QR code based on Public Key Infrastructure. In Proceedings of the 2016 6th International Conference on System Engineering and Technology (ICSET), Bandung, Indonesia, 3–4 October 2016; pp. 194–198. [Google Scholar]
- Sharma, N.; Bohra, B. Enhancing online banking authentication using the hybrid cryptographic method. In Proceedings of the 2017 3rd International Conference on Computational Intelligence & Communication Technology (CICT), Ghaziabad, India, 9–10 February 2017; pp. 1–8. [Google Scholar]
- Hassan, M.A.; Shukur, Z.; Hasan, M.K. An efficient secure electronic payment system for e-commerce. Computers 2020, 9, 66. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G.P. Design of secure and efficient electronic payment system for mobile users. In International Conference on Mathematics and Computing; Springer: Singapore, 2017; Volume 1, pp. 34–43. [Google Scholar]
- Susanna, A.; David, S.; Kathrine, J.W.; Esther, A.G. Enhancing user authentication for mobile wallet using cryptographic algorithm. J. Adv. Res. Dyn. Control Syst. 2018, 10, 891–897. [Google Scholar]
- Kim, H.; Jung, Y.; Jun, M. A Study on Secure Mobile Payment Service for the Market Economy Revitalization. J. Korea Acad. Ind. Coop. Soc. 2017, 18, 41–48. [Google Scholar]
- Han, Z.; Yang, L.; Wang, S.; Mu, S.; Liu, Q. Efficient multi-factor two-server authenticated scheme under mobile cloud computing. Wirel. Commun. Mob. Comput. 2018, 2018, 1–14. [Google Scholar]
- Shin, Y. Review of the suitability to introduce new identity verification means in South Korea: Focused on Block Chain and FIDO. J. Converg. Inf. Technol. 2018, 8, 85–93. [Google Scholar]
- Canales, C. FIDO Alliance Overview. 2020. Available online: https://novugens.com/wp-content/uploads/2020/03/ID37-FIDO-Alliance-2.pdf (accessed on 2 April 2021).
- Singh, A.; Singh, C.; Mishra, S. Enhanced Honey Encryption Algorithm on e-mail with Increased Message Space. Int. J. Res. Eng. Sci. Manag. 2020, 3, 453–456. [Google Scholar]
- Dijesh, P.; SuvanamSasidhar, B.; Yellepeddi, V. Enhancement of e-commerce security through asymmetric key algorithm. Comput. Commun. 2020, 153, 125–134. [Google Scholar]
- Chang, Y.-Y.; Yan, S.-L.; Lin, P.-Z.; Zhong, H.-B.; Marescaux, J.; Su, J.-L.; Wang, M.-L.; Lee, P.-Y. A mobile medical QR-code authentication system and its automatic FICE image evaluation application. J. Appl. Res. Technol. 2015, 13, 220–229. [Google Scholar] [CrossRef]
- Asok, A.; Arun, G. QR Code Based Data Transmission in Mobile Devices Using AES Encryption. Int. J. Sci. Res. 2016, 5, 1116–1120. [Google Scholar]
- Mittra, P.; Rakesh, N. A desktop application of QR code for data security and authentication. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; pp. 1–5. [Google Scholar]
- Goel, N.; Sharma, A.; Goswami, S. A way to secure a QR code: SQR. In Proceedings of the 2017 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017; pp. 494–497. [Google Scholar]
- Husny, H.R.M.; Binti, N.A.N.; Nizar, N.A.; Abdullah, N.Y.; Ismail, W.H.W. Encrypted QR Code System. J. Comput. Technol. Creat. Content 2017, 2, 82–92. [Google Scholar]
- Soltani, M.; Bardsiri, A.K. Designing a Novel Hybrid Algorithm for QR-Code Images Encryption and Steganography. J. Comput. 2018, 13, 1075–1088. [Google Scholar] [CrossRef]
- Ghodke, A.V.; Dagade, R.V. Electronic secure vehicle verification system using advanced Digi-locker system. In Proceedings of the 2018 3rd International Conference for Convergence in Technology (I2CT), Pune, India, 6–8 April 2018; pp. 1–4. [Google Scholar]
- Arief, A.T.; Wirawan, W.; Suprapto, Y.K. Authentication of printed document using quick response (QR) code. In Proceedings of the 2019 International Seminar on Intelligent Technology and Its Applications (ISITIA), Surabaya, Indonesia, 28–29 August 2019; pp. 228–233. [Google Scholar]
- Wahsheh, H.A.M.; Luccio, F.L. Security and privacy of QR code applications: A comprehensive study, general guidelines and solutions. Information 2020, 11, 217. [Google Scholar] [CrossRef] [Green Version]
- Pramusinto, W.; Sartana, B.T.; Mulyati, S.; Amini, D.S. Implementation of AES-192 Cryptography and QR Code to Verify the Authenticity of Budi Luhur University Student Certificate. J. Pendidik. Teknol. Kejuru. 2020, 3, 209–215. [Google Scholar]
- Carter, R.A.; Anton, A.I.; Dagnino, A.; Williams, L. Evolving beyond requirements creep: A risk-based evolutionary prototyping model. In Proceedings of the Fifth IEEE International Symposium on Requirements Engineering, Toronto, ON, Canada, 27–31 August 2001; pp. 94–101. [Google Scholar]
- Song, J.; Xie, H. Design and Implementation of a Vue. js-Based College Teaching System How to Work with This Template. Int. J. Emerg. Technol. Learn. 2019, 14, 59–69. [Google Scholar] [CrossRef] [Green Version]
- Yun, Q. Design and implementation of E-commerce platform based on Vue.js and MySQL. In Proceedings of the 3rd International Conference on Computer Engineering, Information Science & Application Technology (ICCIA 2019), Wuhan, China, 30–31 May 2019; pp. 449–454. [Google Scholar]
- Kyriakidis, A.; Maniatis, K.; You, E. The Majesty of Vue.js 2; Lean Publishing: Victoria, BC, Canada, 2017. [Google Scholar]
- Macrae, C. Vue.js: Up and Running—Building Accessible and Performant Web Apps; O’Reilly Media: Sebastopol, CA, USA, 2018. [Google Scholar]
- Vyas, H.A.; Virparia, P.V. Template-Based Transliteration of Braille Character to Gujarati Text—The Application. Rising Threat. Expert Appl. Solut. 2021, 1187, 437–446. [Google Scholar]
- Mpawe, N.M.; Mussa, A.D. A Web-based Monitoring and Evaluation System for Government Projects in Tanzania: The Case of Ministry of Health. Eng. Technol. Appl. Sci. Res. 2020, 10, 6109–6115. [Google Scholar]
- Sadeq, M.J.; Rayhan, K.S.; Akter, M.; Forhat, R.; Haque, R.; Akhtaruzzaman, M. Integration of blockchain and remote database access protocol-based database. In Proceedings of the Fifth International Congress on Information and Communication Technology, London, UK, 20–21 February 2020; pp. 533–539. [Google Scholar]
- Geetha, V.; Anbumani, V.; Selvi, T.; Sindhuja, C.S.; Vanathi, S. IoT based well-organized hostel power consumption and attendance administration system. In Proceedings of the International Virtual Conference on Robotics, Automation, Intelligent Systems and Energy (IVC RAISE 2020), Perundurai, India, 15 December 2020; pp. 1–9. [Google Scholar]
- Ray, S.; Biswas, G.P.; Dasgupta, M. Secure Multi-Purpose Mobile-Banking Using Elliptic Curve Cryptography. Wirel. Pers. Commun. 2016, 90, 1331–1354. [Google Scholar] [CrossRef]
- ElGhanam, E.; Ahmed, I.; Hassan, M.; Osman, A. Authentication and billing for dynamic wireless EV charging in an internet of electric vehicles. Future Internet 2021, 13, 257. [Google Scholar] [CrossRef]





| Symbols | Meaning |
|---|---|
| User | |
| User’s first name | |
| User’s last name | |
| SIM serial number | |
| Subscriber ID | |
| User’s phone number | |
| User’s PIN | |
| Re-entered PIN | |
| User’s OTP | |
| User’s biometric fingerprint | |
| Biometric template | |
| User’s public key | |
| User’s private key | |
| User’s smartphone | |
| User’s ID | |
| Smartphone ID | |
| One-way hash function—SHA-256 | |
| Fernet Encryption/Decryption with key u | |
| Public key Encryption/Decryption—RSA | |
| Main database | |
| FIDO database | |
| User’s electronic balance | |
| Agent | |
| Agent QR code | |
| Amount |
| Symbols | Meaning | Length (Bytes) |
|---|---|---|
| User | 8 | |
| User’s first name | 16 | |
| User’s last name | 16 | |
| SIM serial number | 16 | |
| Subscriber ID | 8 | |
| User’s phone number | 16 | |
| User’s PIN | 8 | |
| Re-entered PIN | 8 | |
| User’s OTP | 8 | |
| User’s biometric fingerprint | 16 | |
| Biometric template | 16 | |
| User’s public key | 32 | |
| User’s private key | 32 | |
| User’s smartphone | 8 | |
| User’s ID | 8 | |
| Smartphone ID | 8 | |
| One-way hash function—SHA-256 | 32 | |
| Fernet Encryption/Decryption with key u | 16 | |
| Public key Encryption/Decryption—RSA | 256 | |
| Main database | 256 | |
| FIDO database | 256 | |
| User’s electronic balance | 16 | |
| Agent | 8 | |
| Agent QR code | 16 | |
| Amount | 16 |
| Phase | Message Content | Message Size (Bytes) |
|---|---|---|
| Registration | 16 + 16 + 16 + 8 + 16 = 72 bytes | |
| {} | 8 + 8 = 16 bytes | |
| 40 + 32 + 8 + 8 = 88 bytes | ||
| 16 + 16 + 16 + 8 + 16 + 40 + 32 + 8 + 8 = 160 bytes | ||
| Authentication | 8 + 8 + 8 = 24 bytes | |
| 8 + 8 = 16 bytes | ||
| 8 + 8 + 8 = 24 bytes | ||
| } | 16 + 32 + 16 = 64 bytes | |
| 8 + 8 + 32 = 48 bytes | ||
| Transaction | } | 8 + 16 = 24 bytes |
| } | 8 + 16 = 24 bytes | |
| {} | 16 + 32 + 16 = 64 bytes | |
| 8 + 8 + 32 = 48 bytes | ||
| 8 + 16 = 24 bytes | ||
| 8 + 8 + 16 = 48 bytes |
| Proposed Algorithm | Authentication Phase | Transaction Phase (Cash Withdrawal) |
|---|---|---|
| Our Algorithm | ||
| [93] |
| S/No | Security Feature | [15] | [16] | [19] | [20] | [21] | [93] | Our Algorithm |
|---|---|---|---|---|---|---|---|---|
| 1 | Provides efficient authentication | No | Yes | No | No | No | No | Yes |
| 2 | Provides data confidentiality | No | No | No | No | Yes | Yes | Yes |
| 3 | Provides data integrity | No | No | No | No | Yes | No | Yes |
| 4 | Ensures non-repudiation | No | No | No | No | Yes | Yes | Yes |
| 5 | Ensures anonymity | No | No | No | No | No | No | Yes |
| 6 | Ensures privacy | No | No | No | No | Yes | No | Yes |
| 7 | Prevention of shoulder-surfing attacks | No | No | No | Yes | No | No | Yes |
| 8 | Prevention of social engineering | No | No | No | No | No | No | Yes |
| 9 | Prevention of phishing attack | No | No | No | Yes | No | No | Yes |
| 10 | Prevention of PIN-guessing attack | No | No | No | Yes | No | No | Yes |
| 11 | Prevention of brute-force attack | No | No | No | Yes | No | No | Yes |
| 12 | Resistance to replay attacks | No | No | No | No | No | Yes | Yes |
| 13 | Resistance to insider attacks | No | No | No | No | No | No | Yes |
| 14 | Resistance to impersonation attacks | Yes | Yes | No | No | No | No | Yes |
| 15 | Resistance to identity fraud | No | No | Yes | No | Yes | No | Yes |
| 16 | Resistance to a MITM attack | No | No | No | Yes | No | Yes | Yes |
| Proposed Algorithm | Authentication Phase | Transaction Phase (Cash Withdrawal) | Total |
|---|---|---|---|
| Our Algorithm | |||
| [93] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, G.; Dida, M.A.; Elikana Sam, A. A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications. Future Internet 2021, 13, 299. https://doi.org/10.3390/fi13120299
Ali G, Dida MA, Elikana Sam A. A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications. Future Internet. 2021; 13(12):299. https://doi.org/10.3390/fi13120299
Chicago/Turabian StyleAli, Guma, Mussa Ally Dida, and Anael Elikana Sam. 2021. "A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications" Future Internet 13, no. 12: 299. https://doi.org/10.3390/fi13120299
APA StyleAli, G., Dida, M. A., & Elikana Sam, A. (2021). A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications. Future Internet, 13(12), 299. https://doi.org/10.3390/fi13120299






