Abstract
The increasing adoption of electric vehicles (EVs) and the integration of 5G/6G networks are driving the demand for secure, intelligent, and interoperable charging infrastructure within the Internet of Vehicles (IoV) ecosystem. Electric Vehicle Charging Stations (EVCS) face growing cyber–physical threats, including spoofing, data injection, and firmware tampering, risking user privacy, grid stability, and EVCS reliability. While artificial intelligence (AI), blockchain, and cryptography have been applied in cybersecurity, comprehensive solutions tailored to EVCS challenges, such as real-time threat mitigation and scalability, are often lacking. This paper addresses these critical cybersecurity gaps by presenting a comprehensive overview of novel strategies for enhancing EVCS security through the Internet of Digital Twins (IoDT) technology. The primary objective is to evaluate advanced frameworks that synergize digital twins with artificial intelligence, blockchain, and quantum-resistant cryptography. Through systematic literature analysis, global threat assessments, and review of international standards, this study identifies key attack vectors and their impacts on EVCS. Key findings demonstrate that digital twin-driven solutions facilitate real-time monitoring, anomaly detection, predictive threat mitigation, and secure system governance. This review offers actionable insights for researchers, industry stakeholders, and policymakers to strengthen the cybersecurity and resilience of next-generation electric mobility infrastructure, addressing challenges like scalability and implementation barriers.
1. Introduction
The increasing global emphasis on sustainable and low-carbon transportation systems has significantly amplified the focus on electric vehicles (EVs), a phenomenon that is swiftly altering the dynamics of mobility and energy sectors []. This transition is driven by pressing environmental needs, including the reduction in greenhouse gas emissions, the improvement of urban air quality, and the decreased reliance on fossil fuels []. EVs, when powered by renewable energy sources, offer a promising avenue for achieving net-zero emissions within the transportation sector []. However, as the adoption of EVs continues to rise, there is an essential requirement for a scalable, reliable, and intelligent charging infrastructure to accommodate the needs of millions of vehicles effectively.
This infrastructure must not only ensure the efficient delivery of energy but also protect the integrity, confidentiality, and availability of its services amidst the growing challenges posed by cybersecurity threats. Modern electric vehicle charging stations (EVCS) have transcended their previous status as isolated hardware units, evolving into advanced cyber–physical systems that function within the expansive Internet of Vehicles (IoV) framework []. These systems utilize bidirectional energy flow, including vehicle-to-grid (V2G) technology, cloud-based analytics, and advanced wireless communication technologies such as 5G and emerging 6G networks, to facilitate real-time interaction with grid operators, EV owners, and third-party service providers [,]. Although these technological advancements significantly enhance the functionality, interoperability, and user experience of EVCS, they concurrently render the infrastructure susceptible to intricate and potentially severe cyber–physical vulnerabilities.
There is an increasing body of evidence indicating the heightened vulnerability of EVCS to malicious cyber activities []. Attacks such as spoofing [], false data injection [], man-in-the-middle (MitM) [], ransomware [], denial-of-service (DoS) [], and firmware tampering [] have demonstrated the capacity to compromise charging session integrity, mislead grid operators, extract sensitive consumer data, and even destabilize local energy distribution networks [,]. The integration of EVs into the power grid via V2G considerably broadens the potential attack surface, which can compromise charging session integrity, mislead grid operators, extract sensitive consumer data, or destabilize local energy networks [].
In 5G/6G environments, the inherent risks are intensified by features such as ultra-low latency, high device density, and distributed edge computing. These characteristics necessitate the development and deployment of advanced and adaptive security mechanisms to effectively address the associated challenges []. In the face of these emerging challenges, Digital Twin (DT) technology has emerged as a transformative concept with the potential to redefine cybersecurity approaches within cyber–physical infrastructures such as EVCS. A DT is a high-fidelity, real-time virtual model of a physical system that maintains synchronization with its physical counterpart through continuous data exchange, as illustrated in Figure 1 [].
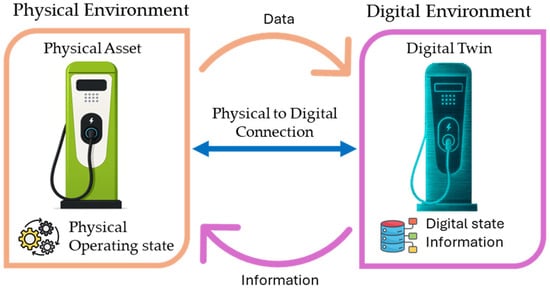
Figure 1.
Schematic model of an EV charging station digital twins.
Originally developed for applications in aerospace and manufacturing, DTs are now being reconceptualized for the protection of critical infrastructure. Recent studies show DTs’ real-world impact on securing EVCS. Coppolino et al. [] used FIWARE and Security Information and Event Management (SIEM) tools in Kropa, Slovenia, to monitor a smart grid with EVCS, catching data tampering in real-time charging sessions, while authors in [] applied deep reinforcement learning to correct compromised EVCS control signals instantly. Similarly, Galkin et al. [] simulated Open Charge Point Protocol (OCPP)-based systems for virtual commissioning, spotting protocol vulnerabilities before deployment. These applications highlight DTs’ ability to enhance monitoring, detect anomalies, and test security measures in controlled environments. By facilitating continuous monitoring, anomaly detection, failure prediction, and control optimization, DTs can function as intelligent sentinels, actively safeguarding EVCS against both established and emerging threats [,].
When integrated into EVCS and enhanced with Artificial Intelligence (AI), blockchain-based integrity assurance, and quantum-resistant cryptography, DTs facilitate an unparalleled degree of situational awareness and operational resilience []. For instance, conducting real-time analyses of anticipated versus actual system behaviors can identify anomalies that may signal zero-day attacks. Additionally, DTs can serve as experimental platforms for simulating attack scenarios and validating incident response strategies without jeopardizing the physical infrastructure []. Despite the conceptual promise and early pilot implementations, the deployment of DTs in EVCS cybersecurity remains fragmented and underexplored. Existing research tends to focus on isolated domains such as cryptographic enhancements [], intrusion detection systems [], or communication protocol hardening without integrating these into a comprehensive, system-wide framework supported by DTs.
A significant gap persists in the literature regarding the intersection of DTs with established standards such as ISO 15118 [] and OCPP 2.0.1 [], as well as with the regulatory frameworks and technological ecosystems that govern EV charging infrastructure. Few studies have systematically examined how these elements can jointly strengthen EVCS security against both current and emerging cyber threats. This review addresses that gap by providing a comprehensive, multidisciplinary synthesis of DTs in EVCS cybersecurity. Whereas earlier studies have tended to isolate specific technologies or focus on narrow vulnerabilities, this work integrates technical, policy, ethical, and economic perspectives into a unified analysis of system resilience.
Unlike Aljohani and Almutairi [], whose 2024 survey examined protocol vulnerabilities without establishing linkages to DT synthesis or 5G/6G threat modeling, and unlike Qureshi et al. [], and Mun et al. [], whose 2025 reviews addressed DTs in manufacturing and other critical infrastructure settings without incorporating EVCS-specific integration or cyber–physical risk considerations, this framework adopts a holistic approach. It presents a structured DT architecture, validates it through real-world pilot studies [], and aligns it with pertinent international standards. The review’s distinctive contributions include systematic mapping of 5G/6G-driven cyber–physical risks in EVCS environments; a comprehensive evaluation of DT applications for real-time monitoring and attack simulation; and synthesis of actionable recommendations for scalable, standards-compliant DT frameworks that address persistent gaps in interoperability, data protection, and cost-effectiveness.
In summary, this review makes the following three major contributions:
- Examines EVCS, emphasizing the advantages of 5G/6G connectivity while identifying new cyber–physical attack risks across control, communication, and power interfaces.
- Outlines DTs’ applications for EVCS cybersecurity, covering real-time monitoring, anomaly detection, attack simulation, and predictive response, using AI, blockchain, and cryptography, and reviews case studies validating these approaches.
- Evaluates cybersecurity standards (ISO 15118-20, OCPP 2.0.1, NIST IR 8356) for DTs’ deployment, highlighting gaps in interoperability, data protection, and cost-effectiveness, and suggests research priorities for scalable, resilient DT frameworks.
To provide readers with a clear overview of the paper’s structure and facilitate navigation through the complex topics covered, a roadmap figure is presented in Figure 2, illustrating the flow of information from EVCS architecture and vulnerabilities through DT fundamentals, implementation strategies, standards compliance, and future research directions.
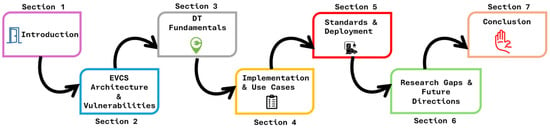
Figure 2.
Research roadmap and organizational structure of the review paper.
The review paper is organized to offer a thorough evaluation of Digital Twins (DTs) in augmenting the cybersecurity of Electric Vehicle Charging Stations (EVCS). It commences with an analysis of EVCS architecture and its cyber vulnerabilities, detailing components such as EVs, Charging Station Management Systems (CSMS), and grid interfaces, while emphasizing the advantages of 5G/6G technologies and the associated cybersecurity risks in both physical and communication layers. This is followed by an introduction to the foundational aspects of DTs for EVCS security, encompassing their structure, underlying technologies, and their role in replicating EVCS operations, alongside methodologies for real-time cybersecurity anomaly detection and attack simulation. The paper then investigates practical use cases and simulation tools for DT implementation, concentrating on applications such as monitoring, threat detection, firmware validation, and automated response, as well as simulation platforms for testing security in EVCS deployments.
Subsequently, it addresses standards, privacy, and deployment considerations, discussing policies, data privacy, encryption, regulatory compliance, and economic factors such as cost, integration, and interoperability that influence DT deployment. The paper also identifies research gaps and future directions, highlighting limitations in scaling and securing DTs for EVCS and advocating for further exploration into twin coordination with Vehicle-to-Grid (V2G) systems, real-time threat intelligence, and standardized frameworks. Finally, it concludes by summarizing the benefits of DTs for EVCS cybersecurity and providing practical recommendations for researchers, operators, and policymakers to ensure safe and scalable adoption.
Methodology
This review employs a systematic methodology to evaluate digital twin applications in EVCS cybersecurity within 5G/6G ecosystems. A three-phase approach was used:
- Literature acquisition from Web of science, IEEE Xplore, Elsevier, and SpringerLink (2020–2025), yielding 284 relevant studies from 772 records.
- Content analysis using a matrix framework to assess technological focus, EVCS layers, and cybersecurity functionalities.
- Thematic synthesis to identify gaps and propose a digital twin framework. Search terms included “digital twin,” “EVCS cybersecurity,” and “5G/6G”.
Inclusion criteria prioritized peer-reviewed studies with technical depth, simulations, or regulatory insights. This entire process is summarized in a flow diagram in Figure 3 below.
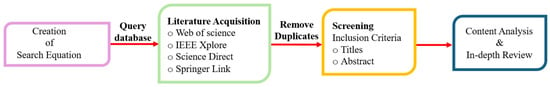
Figure 3.
Literature retrieval process.
2. EV Charging Infrastructure and Threat Landscape in 5G/6G Environments
Modern EV charging ecosystems comprise four critical components: EVs, EVCS, Charging Station Management Systems (CSMS), and Grid Interfaces, each contributing to an interconnected and potentially vulnerable infrastructure, as shown in Figure 4 [].
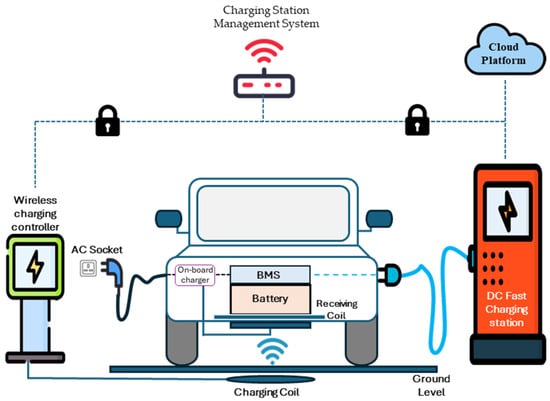
Figure 4.
Diagram showing how EV, EVCS, CSMS, and grid connections work together.
Electric Vehicles serve as highly sophisticated nodes with embedded subsystems such as Battery Management Systems (BMS), Telematics Control Units (TCUs), Infotainment Modules, and Over-the-Air (OTA) update capabilities [,]. These subsystems are integral to managing energy, ensuring connectivity, and facilitating user interaction. Nonetheless, they also introduce a range of cyber risks []. BMS units, for example, utilize proprietary algorithms to optimize the process of charging and discharging. However, these systems may be vulnerable to exploitation if adequate authentication protocols are not implemented [].
Similarly, TCUs and infotainment systems establish continuous communication pathways with external networks, thereby heightening susceptibility to spoofing, data injection, and unauthorized access []. Moreover, the integration of V2G systems supports the bidirectional flow of electricity, which requires stringent encryption and authentication protocols to protect against potential grid tampering [,].
EVCS have transitioned from merely serving as passive power dispensers to becoming sophisticated edge computing platforms. These platforms are now equipped with features such as contactless payment systems, dynamic load balancing, and cryptographic authentication []. Nevertheless, the enhancement of their computational and communication abilities broadens the cyber–physical attack surface. Vulnerabilities in Plug and Charge (PnC) implementations, particularly those conforming to ISO 15118, have been observed due to inconsistent cryptographic enforcement across vendors [,]. Ultra-fast charging stations with integrated cooling systems and local energy storage further complicate the threat profile by incorporating additional sensors and control logic that require protection []. CSMS platforms function as orchestration layers that manage authentication, billing, diagnostics, and energy optimization across a distributed network of EVCS []. The implementation of a hybrid cloud-edge architecture within CSMS operations raises concerns regarding data synchronization, Application Programming Interface (API) integrity, and role-based access control [].
Furthermore, the integration with fleet management systems and third-party applications through open APIs heightens the risk of data breaches and subsequent service disruptions in the event of a security breach []. Grid interface components, including smart transformers, advanced metering infrastructure (AMI), and virtual power plant (VPP) systems, enable bidirectional data and power flows between the grid and charging infrastructure []. These components utilize real-time data analytics and communication protocols to optimize grid load management and implement demand response operations. Nevertheless, their digital interfaces render them susceptible to cyber threats, which, if exploited, could result in grid instability, energy theft, or extensive service disruptions. The integration of 5G and emerging 6G networks into EV charging infrastructure facilitates enhanced connectivity, increased bandwidth, and advanced computational intelligence. The concept of network slicing within 5G/6G technology allows for the logical separation of services, providing dedicated bandwidth and customized security policies [].
This approach enables the prioritization of essential services, such as authentication and energy management, while effectively segregating them from general-purpose traffic []. Despite advancements, the implementation of slice-specific security protocols remains inconsistent among operators, thereby increasing the risk of cross-slice attacks. Multi-access Edge Computing (MEC) enhances the responsiveness and resilience of EVCS by relocating computation and analytics closer to the source of data generation []. This approach mitigates latency and ensures operational continuity during instances of cloud disconnection. Nevertheless, the distributed architecture of MEC introduces novel trust boundaries, thereby necessitating advanced strategies for hardware protection, anomaly detection, and decentralized identity verification.
In densely populated urban environments, the scalability of MEC must be judiciously balanced with resource constraints that may limit security monitoring capabilities. The advent of 6G technologies, including Terahertz (THz) communication, integrated sensing, and centimeter-level positioning, is expected to further augment the precision and intelligence of EV charging operations []. These technologies support applications ranging from immersive maintenance interfaces to real-time tamper detection.
However, they also introduce novel attack vectors, particularly at the physical layer, which will require new forms of lightweight cryptographic protection and adaptive security frameworks. The cyber–physical interface of EV charging infrastructure encompasses multiple communication layers and protocols. At the physical and transport layers, Controller Area Network (CAN) buses [,] and Automotive Ethernet [] are commonly used to transmit data within vehicles and between EVs and charging stations.
This supports real-time control, diagnostics, and power management functions. These protocols, while efficient, often lack robust security features such as encryption and mutual authentication, making them susceptible to spoofing, injection, and side-channel attacks. Middleware and application layer protocols such as Message Queuing Telemetry Transport (MQTT), Advanced Message Queuing Protocol (AMQP), and Constrained Application Protocol (CoAP) enable structured messaging and efficient data exchange between charging system components and external platforms [,]. Protocols like Open Charge Point Protocol (OCPP) [] and ISO 15118 standardize the communication between EVCS and CSMS, offering features such as Transport Layer Security (TLS) encryption and certificate-based authentication [,,]. However, real-world deployments frequently suffer from implementation flaws such as certificate mismanagement and fallback to insecure versions, undermining their theoretical security guarantees.
In grid integration, protocols such as Open Automated Demand Response (OpenADR), IEC 61850, and IEEE 2030.5 enable energy-aware control of EVCS based on real-time grid conditions [,]. These standards support demand-side management, frequency regulation, and distributed energy resource coordination, but introduce complexity in parsing and execution, particularly on constrained edge devices. The interoperability of these protocols, while essential for seamless system operation, introduces attack surfaces if authentication and authorization procedures are inconsistently enforced across platforms [,,]. The infrastructure for EV charging is susceptible to a diverse array of threat vectors encompassing software, hardware, and human interfaces. DoS attacks [] can render chargers inoperable, potentially paralyzing fleets or critical infrastructure. MitM attacks [] target communication sessions to intercept or manipulate sensitive data, particularly in protocols lacking mutual TLS enforcement. Firmware manipulation, which includes actions such as false data injection, backdoor insertion, and update interception, poses a substantial risk of enduring compromise.
This threat is particularly acute in devices that do not incorporate secure boot protocols and integrity verification measures []. User-facing components such as mobile applications, payment interfaces, and public display terminals are frequently targeted through social engineering and phishing campaigns [,]. Poor input validation and session handling in these systems can lead to data breaches and financial fraud []. At the physical layer, cable tampering, connector spoofing, and device substitution can bypass digital protection if hardware integrity checks are absent or ineffective []. As illustrated in Figure 5, the EVCS threat landscape encompasses diverse vectors that extend across cyber, physical, and communication domains, with prevalent examples including spoofing, DoS, and firmware manipulation. Mapping these attack pathways to specific system components such as the EV, central system management server, grid interface, and communication protocols provides a structured basis for evaluating severity and likelihood, thereby enabling the prioritization of countermeasures within a layered defense strategy.
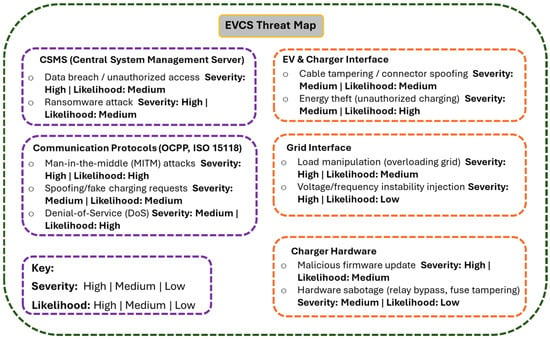
Figure 5.
EVCS threat map.
Table 1, Table 2, Table 3 and Table 4 synthesize key studies on cyberattacks and countermeasures in EV charging infrastructure, highlighting authors, methodologies, and findings across distinct threat domains. Table 1 presents solutions for authentication and privacy, tackling unauthorized access and man-in-the-middle attacks through techniques like blockchain, biometric authentication, and lightweight cryptography. These studies explore secure key establishments for V2G, energy harvesting in dynamic wireless charging, and bandwidth identification, all tailored to the constraints of EV charging systems, limited processing power, real-time operation, and bandwidth limitations. The novelty lies in customizing lightweight, privacy-preserving mechanisms to resist threats such as desynchronization, replay, and Sybil attacks within a constrained environment.

Table 1.
EVCS Authentication and Privacy Protocols.

Table 2.
AI/ML-Based Intrusion and Anomaly Detection Systems.

Table 3.
Blockchain for Enhanced EVCS Security and Trust.

Table 4.
Cyber–physical Attacks on EVCS and Corresponding Mitigation Strategies.
Table 2 focuses on AI- and ML-based intrusion detection systems that identify threats like denial-of-service and other cyber–physical anomalies. Approaches include deep neural networks, Long Short-Term Memory (LSTM) architecture, and edge-based detection of oscillatory load attacks. These systems analyze real-time system metrics to flag abnormal behavior and mitigate evolving threats. Notably, several studies incorporate complex datasets like CICEVCS2024 and apply transfer learning to improve adaptability across different EVCS contexts. The emphasis is on building smart, self-improving detection systems that keep pace with dynamic, cross-platform threat landscapes.
Table 3 explores blockchain technologies applied to EVCS, using frameworks such as Byzantine Fault Tolerance and Hyperledger Fabric to secure data integrity and transaction trust. These methods prevent fraud, false data injection, and man-in-the-middle attacks, supporting critical functions like payment processing and energy trading. By leveraging consortium blockchains and smart contracts, these studies address issues like double-spending, Sybil attacks, and congestion in decentralized networks. The innovation lies in adapting general blockchain principles to the specific operational and scalability demands of EV infrastructure.
Table 4 examines cyber–physical attacks and proposed mitigation strategies, including multi-layered authentication and Moving Target Defense. Studies analyze attacks exploiting public EVCS data, coordinated switching attempts, and vulnerabilities in EVCS management systems. Defenses include TCWGAN-based forecasting and multi-source control schemes to counter false data injection, malicious operating modes, and Distributed Denial-of-Service (DDoS) attacks.
The key contribution is in modeling complex and evolving attack vectors, such as time-varying DDoS, and embedding robust, EVCS-specific defenses into grid and V2G systems.
Comparative Evaluation of AI Models for EVCS Cybersecurity
The studies in Table 2 leverage various AI models for intrusion and anomaly detection in EVCS, including Deep Neural Networks (DNN) [], Long Short-Term Memory (LSTM) [], Convolutional Neural Networks (CNN) [], and Generative Adversarial Networks (GAN) variants like GAN-Gated Recurrent Unit (GRU), GAN-LSTM, and GAN-CNN []. Each model offers distinct strengths and weaknesses depending on the characteristics of EVCS data, such as time-series telemetry, high-dimensional sensor inputs, and dynamic network traffic patterns, understanding their suitability is critical for effective deployment in EVCS cybersecurity. DNNs excel in processing high-dimensional, non-sequential data, making them suitable for detecting complex patterns in EVCS metrics like voltage, current, and network traffic [,]. Their strength lies in handling large datasets and generalizing across diverse attack types, such as DoS and cyber–physical attacks [,,]. However, DNNs require substantial computational resources and labeled training data, which can be a bottleneck in resource-constrained edge devices typical in EVCS deployments []. Overfitting is also a risk if training data lacks diversity, potentially missing novel attack vectors [].
The LSTM models are tailored for sequential data, ideal for EVCS time-series data like power flow or communication logs [,]. They capture temporal dependencies, making them effective for detecting anomalies in charging patterns or oscillatory load attacks [,]. Their memory cells allow retention of long-term patterns, which is useful for identifying gradual attack escalations []. However, LSTMs are computationally intensive and sensitive to hyperparameter tuning, which can complicate real-time implementation in EVCS environments with strict latency requirements []. Convolutional Neural Networks (CNN), particularly Convolutional LSTM variants, combine spatial and temporal feature extraction, making them effective for detecting oscillatory load attacks or spatially correlated anomalies in EVCS networks [].
CNNs reduce computational complexity compared to LSTMs by leveraging convolutional layers, suitable for edge-based detection []. However, they may struggle with long-term dependencies in highly dynamic EVCS data and require careful preprocessing to align with spatial data structures []. The GAN variants, such as GAN-GRU, GAN-LSTM, and GAN-CNN, are used for predictive tasks like remaining useful life (RUL) estimation and anomaly detection [,].
GANs generate synthetic attack scenarios, enhancing training data diversity and improving detection of rare or zero-day attacks []. Their ability to model complex distributions is valuable for EVCS data with non-linear patterns []. However, GANs are prone to training instability and require significant computational resources, limiting their practicality in real-time EVCS applications []. Their reliance on Unsupervised learning also risks generating false positives if not carefully tuned [].
In the context of EVCS, data characteristics like real-time telemetry, high-noise levels, and dynamic network interactions favor models that balance computational efficiency with temporal sensitivity []. LSTM and Convolutional LSTM are particularly effective for time-series anomaly detection, while DNN suits broader pattern recognition across diverse metrics [,,]. GAN variants are promising for simulating rare attack scenarios but need optimization for edge deployment []. Future work should focus on hybrid models combining LSTM temporal strengths with CNN’s efficiency or lightweight GAN frameworks to address EVCS-specific constraints like low latency and limited edge computing power [,,].
To delineate these attributes systematically, Table 5 compares key AI models, including methodology, benchmarks such as dataset, accuracy and gaps, building on Table 2’s studies.

Table 5.
Comparative Attributes of AI Models for EVCS Intrusion Detection.
3. Digital Twins Foundations for EVCS Security
The IoDT signifies a transformative advancement in the design, monitoring, and safeguarding of complex cyber–physical systems, including EVCS []. DTs are defined as dynamic, digital models of physical assets or processes, which remain in constant alignment with their physical counterparts by integrating real-time data []. In the early 2000 s, Dr. Michael Grieves at the University of Michigan laid the groundwork for the concept of DTs. This foundational idea was later implemented by NASA to enhance simulation and diagnostic capabilities within aerospace systems []. Since then, the development of DTs has rapidly progressed due to advancements in artificial intelligence (AI), cloud infrastructure, and the extensive deployment of Internet of Things (IoT) technologies [,]. Today, DTs offer real-time operational insights, predictive analytics, and proactive control mechanisms, capabilities that are especially crucial in the cybersecurity landscape of EVCS [].
The success of DT systems in safeguarding the cybersecurity of EVCS is fundamentally dependent on achieving precise synchronization between the physical infrastructure and its digital model. This synchronization is facilitated by distributed sensor networks that gather comprehensive telemetry data, including parameters such as voltage, current, temperature, network latency, and usage patterns [].
These inputs are utilized to create multi-domain models that encompass not only physical behaviors, such as electrical, mechanical, and thermal, but also the digital interactions within communication and control layers. By merging real-time data with historical trends, DTs enhance situational awareness and predictive capabilities. In the realm of EVCS, this modeling aids in the early detection of anomalous power flows, compromised communication channels, or unauthorized access attempts, thereby bolstering robust cybersecurity postures [].
Digital Twin systems for EVCS are generally organized into layered architecture, facilitating modular design and seamless integration into various operational environments. At the foundational level is the physical layer, which comprises EVCS hardware, power conversion units, control modules, and sensing devices [].
Situated above the physical layer is the communication layer, which facilitates the exchange of data between internal modules and external interfaces by employing secure and standardized protocols []. The logical or data processing layer integrates AI-driven modules designed for state estimation, anomaly detection, behavior prediction, and system optimization []. Additional components may encompass visualization dashboards, rule-based mechanisms for the enforcement of cybersecurity protocols, and middleware that facilitates interaction with grid operators and external systems [].
The layered architecture of the EVCS digital ecosystem ensures resilience, flexibility, and security. In environments where cybersecurity is a critical concern, DTs function as continuous monitoring agents and analytical engines, capable of detecting and mitigating cyber threats in real time. Through cross-domain modeling, DTs identify vulnerabilities that arise from the interaction between physical processes, control logic, and communication protocol vulnerabilities that traditional, siloed assessments may overlook []. DTs serve as a virtual platform for testing and enhancing security measures by replicating attack vectors such as false data injection, protocol spoofing, firmware manipulation, and DoS scenarios []. Moreover, DTs maintain comprehensive event logs, which facilitate forensic investigations and compliance reporting following incidents [].
As illustrated in Figure 6, the operational flow of cybersecurity-focused DTs encompasses monitoring, anomaly detection, threat simulation, and response pathways, which are distributed across EVCS components. This flow begins with continuous monitoring, where IoT sensors collect real-time data from EVCS components like charging ports, power converters, and communication interfaces [].
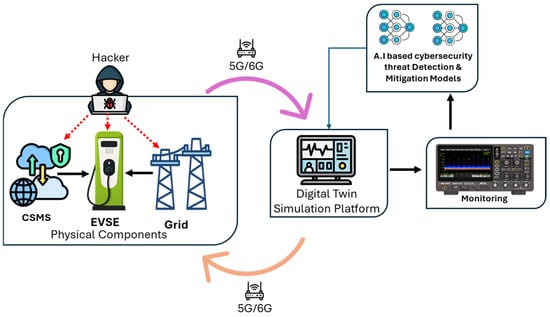
Figure 6.
Digital twins’ security flow for EVCS environments.
These sensors feed metrics such as current fluctuations, packet loss rates, or unauthorized access attempts into the DTs data processing layer []. Anomaly detection then employs AI algorithms, such as unsupervised clustering or statistical modeling, to identify deviations from normal operational patterns []. For instance, an unexpected spike in power draw or irregular network traffic could signal a potential cyberattack []. Threat simulation, a critical component, involves the DTs replicating attack scenarios, like injecting false data into control systems or simulating a denial-of-service attack, to test system resilience and refine mitigation strategies without risking the physical infrastructure []. Response pathways are activated when anomalies or threats are confirmed, leveraging predefined rules and AI-driven decisions to isolate compromised components, reroute power flows, or alert grid operators []. This closed-loop process ensures rapid detection and mitigation, maintaining EVCS integrity across its physical and digital domains.
As illustrated in Figure 6, the operational flow of cybersecurity-focused DTs encompasses monitoring, anomaly detection, threat simulation, and response pathways distributed across EVCS components. This visualization captures the closed-loop process of data collection, analysis, and mitigation across digital and physical domains. To further clarify how digital twins mitigate specific cyber threats in EVCS environments, the main DT-based solutions are summarized in Table 6 below.

Table 6.
DT Solutions to Key EVCS Security Threats.
The implementation of DTS capabilities in the cybersecurity of EVCS is supported by a combination of well-established and novel technologies. The IoT-based sensor arrays constitute the core of data acquisition, capturing a comprehensive array of environmental and operational metrics at the edge []. Edge computing platforms enhance system responsiveness by performing data processing tasks locally. This approach reduces reliance on centralized systems and facilitates real-time threat mitigation []. Cloud infrastructures offer scalable computing and storage capabilities that are crucial for analyzing historical data, training models, and synchronizing across networks.
Additionally, the use of microservices and containerization supports the modular deployment and lifecycle management of Digital Twin components []. The integration of AI techniques, such as supervised learning for identifying known attack patterns and unsupervised clustering for detecting anomalies, enhances the ability of digital twins to adapt to evolving cyber threats []. Collectively, these technologies provide a solid foundation for the implementation of DTs that satisfy the stringent security requirements of contemporary, interconnected EVCS environments.
However, the effectiveness of these technological components ultimately depends on how well they perform operationally. Technical performance in DT-driven EVCS cybersecurity relies on three interdependent factors: synchronization fidelity between digital and physical systems, model accuracy in representing operational states, and communication latency in threat response mechanisms []. Degradation in any of these dimensions amplifies vulnerabilities, particularly in 5G/6G network environments where high-speed data exchange is fundamental to security operations [].
Synchronization is maintained through the continuous IoT sensor data streams described above, enabling real-time anomaly detection []. However, this continuous exchange creates attack surfaces vulnerable to man-in-the-middle attacks and data tampering []. Studies of cyber–physical systems demonstrate that desynchronization can delay threat mitigation by 20–50% in smart grid infrastructures []. When DT’s lose synchronization with physical energy systems, they fail to detect fraudulent data injection attacks, reducing the effectiveness of grid destabilization countermeasures [].
Model fidelity directly influences the threat simulation accuracy of the AI techniques integrated into the DT architecture []. High-fidelity models employing CNN/LSTM hybrid architectures have achieved 93% detection accuracy for advanced persistent threats in IoT environments []. Conversely, models trained on synthetic datasets that inadequately capture operational complexity exhibit reduced generalizability []. In dynamic EVCS scenarios, low-fidelity models can increase false negative rates by up to 15%, allowing genuine threats to evade detection [,].
Communication latency presents critical constraints for the edge–cloud architecture discussed previously, particularly during handoffs in distributed deployments []. Ultra-reliable low-latency communication protocols must maintain latency below 50 ms to prevent exploitation through denial-of-service attacks []. When additional verification layers such as blockchain consensus mechanisms introduce overhead, latency can increase to 100–200 ms, compromising the responsiveness essential for vehicle-to-grid stability [,].
These performance requirements necessitate careful protocol selection that balances model fidelity with operational speed []. Industrial IoT pilot deployments have demonstrated that this balance is achievable through lightweight architectures, though successful implementation requires systematic optimization across all three performance dimensions [,].
4. Simulation Tools for Digital Twins Implementation
Digital Twins in EVCS function through a stratified architecture that enables synchronized interaction between physical components and their digital representations. As depicted in Figure 7, the physical layer encompasses hardware components such as EVCS, sensors, and connected EVs.
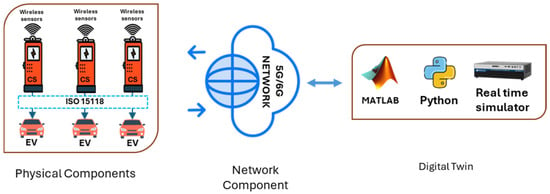
Figure 7.
Conceptual framework of Digital Twin architecture adapted for EVCS cybersecurity.
The data layer records sensor inputs, telemetry, and time-series metrics pertaining to system status []. The modeling layer performs real-time simulations, conducts cybersecurity analyses, and facilitates predictive diagnostics []. The service layer integrates tools for decision-making that are grounded in machine learning and artificial intelligence, whereas the visualization layer conveys actionable intelligence via dashboard interfaces []. These layers work together seamlessly to oversee charging operations, detect threats, and autonomously initiate corrective actions in a secure manner. Real-time system monitoring is a fundamental application of DTS technology in EVCS. DTs continuously monitor operational metrics such as voltage, current, temperature, state-of-charge (SoC), and power quality.
These data streams are visualized through 2D or 3D interfaces, offering infrastructure operators high-resolution situational awareness []. Prior to implementing software patches or backend updates, stakeholders may employ DT environments to simulate their potential effects on EVCS within a controlled, sandboxed virtual setting [].
Prominent programming and numerical computing platforms, such as MATLAB/Simulink, Python-based frameworks, and Modelica [], and Julia [] offer robust modeling capabilities for power flow analysis, communication behavior emulation, and cyber-attack scenario validation.
Python is widely used for DTs implementation in EVCS cybersecurity due to its flexibility, extensive libraries, and open-source nature, but it differs from tools like MATLAB/Simulink, Modelica, and Julia in capability and outcome []. Python frameworks such as OpenModelica, SimPy, or custom environments with libraries like NumPy, SciPy, and TensorFlow enable high-fidelity modeling of EVCS components, including power flows, communication protocols, and AI-driven anomaly detection []. Its strength lies in rapid prototyping and machine learning integration for real-time threat analysis, but it requires significant customization to match the precision of domain-specific tools [].
MATLAB/Simulink, with toolboxes for power systems and control, offers robust support for EVCS simulations and seamless hardware-in-the-loop (HIL) integration, reducing development time for cyber–physical models []. Its proprietary nature and licensing costs around $1015–$4090 per year, contrast with Python’s accessibility [,].
Modelica excels in multi-physics modeling, capturing EVCS thermal and electrical dynamics, but its steeper learning curve slows implementation compared to Python’s syntax [,]. Julia, optimized for numerical performance, handles large-scale simulations faster than Python in some cases but lacks mature libraries for EVCS applications [].
Outcomes are generally consistent across tools for well-defined DTs tasks, such as replicating EVCS behavior or anomaly detection, when models are accurately parameterized [,]. However, tool-specific differences arise in computational efficiency and integration. Python’s flexibility suits experimental setups and diverse data sources, but it may lag in real-time performance for 5G/6G environments compared to Julia or MATLAB’s solvers [,,]. Validation against standards like ISO 15118 or OCPP 2.0.1 shows comparable accuracy, though MATLAB’s compliance templates streamline regulatory alignment []. For resource-constrained teams, Python’s low cost and community support often outweigh specialized tools, but outcomes depend on expertise in tailoring Python to EVCS requirements [].
These platforms facilitate high-resolution time-domain simulations, enable co-simulation with real-time systems, and allow integration with machine learning toolkits, thereby serving as indispensable tools for proactive cybersecurity validation. The choice of a suitable simulation environment depends on the specific EVCS component being assessed, the required level of fidelity, and the complexity of integration with live operational data streams. This mitigates operational risk and facilitates adherence to standards such as ISO/SAE 21434 and NIST SP 800-82 [,]. A DTS can effectively replicate the response of a charging unit when subjected to a compromised firmware injection.
This capability allows developers to scrutinize unauthorized behaviors, simulate command failures, and evaluate the risks associated with data exfiltration. Such anticipatory testing empowers stakeholders to confirm the system’s resilience without subjecting the actual system to potential exploitation []. Another vital application is threat emulation and attack simulation [], DTs are capable of modeling sophisticated cyberattacks such as DoS, spoofing, false data injection (FDI), and advanced persistent threats (APTs) [,]. By integrating historical attack signatures and behavioral models into the DTs analytics engine, infrastructure providers can effectively simulate malicious activities, evaluate the proliferation of cyber threats, and assess the efficacy of layered security measures [].
Beyond passive detection, digital twins play a crucial role in facilitating real-time cybersecurity mitigation. By juxtaposing real-time operational data with established models of anticipated behavior, DTs can identify anomalies with a high degree of precision []. Upon detection of abnormal behaviors, such as unexpected handshake failures, irregular voltage oscillations, or backend command delays, they can initiate automated responses []. These measures may involve isolating affected components, executing firmware rollbacks, deploying over-the-air configuration updates, or issuing alerts to system operators.
This automated response loop significantly reduces the mean time to detect and respond, which is particularly crucial in ultra-dense urban charging networks or highway supercharging corridors []. The efficacy of DTS based cybersecurity is fundamentally reliant on the communication stack that facilitates system coordination. Figure 8 presents a comparative analysis of prominent industry entities that provide platforms for the development of cybersecurity detection and mitigation strategies.
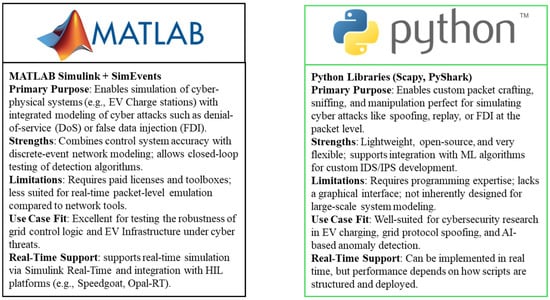
Figure 8.
Platforms for developing and testing cybersecurity detection and mitigation strategies.
The EVCS operates on a sophisticated protocol suite that encompasses the physical, transport, and application layers. Intra-vehicle communication is facilitated by the Controller Area Network (CAN) bus and Automotive Ethernet, while secure messaging between electric vehicles, charging stations, and backend servers is enabled by protocols such as TCP/IP, ISO 15118, OCPP, Message Queuing Telemetry Transport (MQTT), and Open Platform Communications Unified Architecture (OPC UA) []. DTs facilitate the simulation of these layered interactions, enabling developers to evaluate protocol compliance, packet sequencing, timing delays, and the resilience of security handshakes under diverse load conditions []. The integration with 5G and the emerging 6G networks facilitates further advancements through the implementation of network slicing, ultra-reliable low-latency communications (URLLC), and multi-access edge computing (MEC).
These technologies enable the localization of DT operations and threat detection, thereby allowing for a more rapid response to localized anomalies while maintaining the integrity of the global system []. In addition, DTs significantly enhance the processes of virtual commissioning and interoperability testing []. Prior to the implementation of new charging systems or the expansion to additional sites, operators can employ DTs to simulate deployment conditions, network topology, and environmental variability.
This pre-deployment modeling ensures compliance with standards such as OCPP 2.0.1 or ISO 15118 Plug and Charge and mitigates integration risks with utility backends or fleet management platforms []. This simulation capability is also applicable to V2G environments, where the bidirectional flow of energy and data introduces novel control logic and synchronization challenges. DTs are particularly well-suited to modeling and optimizing these complexities []. The realization of these capabilities is facilitated by a growing ecosystem of commercial DT platforms specifically designed for the energy and mobility sectors. Companies such as Opal-RT, RTDS, Typhoon HIL, and Speedgoat have emerged as prominent technology providers in the development and deployment of DT frameworks for EVCS.
Their platforms are equipped to manage real-time data streaming, model-based system design, hardware-in-the-loop (HIL) testing, and seamless edge–cloud integration capabilities, which are crucial for high-fidelity simulation of cyber–physical systems operating under 5G/6G connectivity. Figure 9 illustrates the architecture and operational focus of these platforms, demonstrating how each vendor supports different aspects of DTS-enabled cybersecurity pipelines, such as co-simulation, protocol fuzzing, or electromagnetic interference testing.
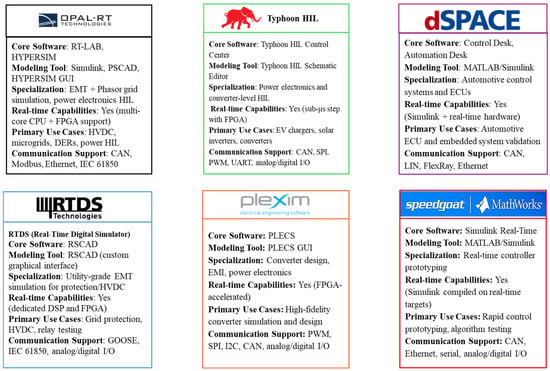
Figure 9.
Functional overview of industry-leading DTS simulation and HIL platforms for EVCS cybersecurity (Opal-RT, RTDS, Typhoon HIL, Speedgoat).
Table 7 provides a comparative summary of platform specifications, simulation software, and use cases in smart mobility and EV infrastructure. Together, these resources offer practitioners a reference framework for selecting and deploying DTs tailored to advanced EVCS security applications.

Table 7.
Comparative summary of DTS-enabled simulation platforms, technical specifications, cybersecurity features, and EVCS application domains.
Performance Metrics and Evaluation Criteria
DTs enhance EVCS cybersecurity through real-time monitoring, anomaly detection, and automated response mechanisms. To assess their effectiveness, specific performance metrics and evaluation criteria are essential. These metrics provide a quantitative basis for evaluating DTs performance in detecting and mitigating cyber threats, ensuring they meet the operational demands of 5G/6G-enabled EVCS environments.
- I.
- Detection Accuracy: This metric measures the proportion of correctly identified cyber threats, such as false data injections or denial-of-service attacks, against the total number of incidents []. Studies using AI-driven DTs, such as those employing deep neural networks, report detection accuracies ranging from 85% to 98% for known attack patterns in controlled EVCS simulations [,,,]. Accuracy varies based on training data quality and the complexity of attack vectors, with unsupervised learning models showing slightly lower performance for zero-day threats [].
- II.
- False Positive Rate: The false positive rate indicates the frequency of benign behaviors incorrectly flagged as threats []. High false positive rates can erode operator trust and disrupt EVCS operations. Current DTs implementations, particularly those using convolutional LSTM models, achieve false positive rates as low as 2% to 5% in urban charging networks [,]. These rates improve when DTs integrate historical data and real-time telemetry to refine anomaly detection algorithms.
- III.
- Latency: Latency measures the time from threat detection to response initiation []. In 5G/6G environments, DTs leveraging multi-access edge computing achieve response latencies of 10 to 50 milliseconds for localized anomaly detection []. This low latency is critical for ultra-dense charging networks, where rapid response prevents cascading failures []. Cloud-based DTs, however, may experience latencies up to 200 milliseconds due to data transmission overhead, highlighting the advantage of edge-based processing [].
- IV.
- Scalability Metrics: Scalability of DTs for Electric Vehicle Charging Stations (EVCS) is assessed by their capacity to manage an increasing number of EVCS units without compromising performance, such as detection accuracy or latency []. Simulations conducted using platforms like MATLAB/Simulink have shown that DTs can effectively handle up to 10,000 charging stations while maintaining stable performance, achieving detection accuracy above 90% and latency below 100 milliseconds when deployed across distributed edge nodes []. Beyond this scale, synchronization challenges may lead to a latency increase of approximately 20% to 30% due to higher computational and communication demands [].
- V.
- Resource Utilization: Effective DTs for Electric Vehicle Charging Stations (EVCS) must balance computational demands with resource constraints to ensure efficient operation. Edge-based DTs, such as those deployed on platforms like NVIDIA Jetson, typically consume between 50 and 100 watts per unit, depending on the workload and hardware configuration []. Cloud-based analytics for real-time processing of EVCS data require approximately 0.5 to 2 GB of RAM per charging station to handle tasks like monitoring and optimization [,]. Optimizing resource utilization is critical for cost-effective deployment, particularly in large-scale urban environments where scalability and energy efficiency are paramount [,].
These metrics were derived from case studies and simulations, such as those conducted with Opal-RT and Typhoon HIL platforms, which validate DTs performance under diverse attack scenarios []. For instance, DTs simulating a spoofing attack on an ISO 15118-compliant EVCS achieved a detection accuracy of 92% with a false positive rate of 3% and a response latency of 30 milliseconds []. Such evaluations ensure that DTs not only detect threats but also maintain operational efficiency and reliability. Future research should focus on standardizing these metrics across DTs platforms to enable consistent performance comparisons and guide practical deployments in large-scale energy networks [].
Recent pilot projects validate the effectiveness of DT simulation tools in enhancing cybersecurity for EVCS. The CyberTWIN-EV project, led by AESIN in the UK, integrated DT platforms with cybersecurity assessment tools to simulate cyberattacks such as DoS and MITM attacks on EV charging infrastructure []. The project deployed vehicle and grid-based intrusion detection systems (IDS) to identify anomalies and log them to a Mobility Security Operations Centre (MSoC), demonstrating the viability of digital twin environments for validating cybersecurity resilience in EV-grid interactions [].
Similarly, Trialog’s 2024 demonstration utilized digital twins with the Eclipse Ditto platform to simulate EV charging stations within their TriLab innovation laboratory []. This proof-of-concept enabled testing of software changes and interoperability scenarios without requiring physical charging infrastructure []. The case studies highlight the strong predictive power and practical advantages of DT applications in EVCS. These findings affirm strategic value of integrating DT technology into EVCS systems.
5. Standards, Privacy and Financial Feasibility
The integration of DTs technology into EVCS enhances operational visibility, predictive analytics, and cybersecurity by utilizing real-time data. Nevertheless, it presents substantial challenges concerning privacy, encryption, regulatory compliance, and cost [].
For effective deployment, it is imperative to adhere to standards such as ISO 15118, OCPP 2.0.1, and GDPR, while addressing deficiencies in synchronization, authentication, and data integrity []. Privacy-preserving techniques and robust encryption are essential for safeguarding sensitive information. Economic considerations, including capital expenditures (CAPEX), operational expenditures (OPEX), and return on investment (ROI), significantly impact adoption. Additionally, interoperability challenges within diverse EVCS environments also play a crucial role []. Addressing these challenges necessitates the implementation of coordinated standards as discussed below.
5.1. Compliance with Technical Standards
To ensure interoperability, security, and scalability, DTs-enabled EVCS must adhere to industry standards such as ISO 15118 [], OCPP 2.0.1 [], IEEE 2030.5 [], and NIST IR 8356 []. These standards provide frameworks for secure communication, data management, and system integration:
- I.
- ISO 15118: This standard establishes the framework for V2G communication, outlining the protocols necessary for the secure transmission of data between EVs and charging stations []. Transport Layer Security (TLS) is employed to facilitate encrypted communications, while digital certificates are utilized for authentication. This, when employed by DTs, can securely process data related to charging sessions []. Ensuring compliance with data protection laws is vital for DTs systems to sustain trust in V2G interactions, particularly when dealing with bidirectional charging scenarios.
- II.
- OCPP 2.0.1: The Open Charge Point Protocol (OCPP) 2.0.1 significantly enhances communication between chargers and backend systems by incorporating advanced security features, including support for TLS 1.3 and secure firmware updates []. DTs that implement OCPP 2.0.1 are capable of securely transmitting telemetry data to cloud-based twins, effectively reducing the potential for eavesdropping or data tampering.
- III.
- IEEE 2030.5: This communication standard helps utilities, distributed energy resources (DERs), and grid-connected devices like EV chargers share data safely and efficiently. It uses the Internet Protocol (IP) to control DERs from a distance and allows two-way communication to keep the grid stable. The standard ensures smart grids work well together by combining digital technologies with DERs and grid management systems [,,]. It requires the establishment of rigorous cybersecurity strategies, such as mutual authentication and encryption, to ensure the protection of data exchanges within EVCS ecosystems.
- IV.
- NIST IR 8356: The incident report (IR) from the National Institute of Standards and Technology (NIST) on DTs cybersecurity offers a risk-based framework for the protection of DTs systems. It underscores the importance of continuous monitoring, threat modeling, and incident response strategies to mitigate vulnerabilities in DTS-enabled EVCS []. Adherence to NIST IR 8356 guarantees that DTs systems maintain resilience against the evolving landscape of cyber threats, including data breaches and DoS attacks.
Failure to adhere to these standards may result in interoperability complications, expose security weaknesses, and lead to regulatory sanctions, thereby threatening the scalability and reliability of DT-enabled electric vehicle charging systems (DTs-enabled EVCS).
5.2. Technical Safeguards for Privacy and Data Protection
The incorporation of DTs technologies into EVCS presents notable challenges and responsibilities concerning data privacy and cybersecurity.
These systems are required to function within a multifaceted regulatory framework that encompasses various jurisdictions, including the General Data Protection Regulation (GDPR) of the European Union, the California Consumer Privacy Act (CCPA), and the Network and Information Security Directive 2 (NIS2) for critical infrastructure in Europe [,,]. These frameworks enforce stringent requirements concerning data handling, user consent, and system-level security practices. For example, the GDPR specifies essential user rights in Articles 15 to 21, including the rights to access, rectification, erasure (the “right to be forgotten”), and objection to automated decision-making, all of which must be integrated into the technical architecture of DTs platforms [].
Concurrently, the CCPA emphasizes transparency and consumer control over personal data, whereas the NIS2 classifies EVCS as critical infrastructure, necessitating increased resilience against cyber threats and service interruptions. These systems routinely collect, transmit, and process data across various legal jurisdictions, thereby necessitating compliance with data protection laws that span a fragmented array of regulatory frameworks []. This challenge is particularly acute in emerging markets, where regulatory frameworks specific to digital transformation technologies are frequently underdeveloped or entirely absent. Consequently, implementing entities must adopt anticipatory compliance strategies that align with internationally recognized standards and best practices to ensure lawful and ethical data governance.
5.3. Privacy by Design and System Architecture
Deploying DTs on a large scale involves handling vast amounts of sensitive and personally identifiable data, such as vehicle location, battery state-of-charge (SoC), consumption patterns, and user billing information [,]. This scenario requires a system architecture that embodies the principles of privacy by design and security by default. These core principles highlight the necessity of embedding data protection mechanisms throughout the system, from edge-level devices and sensor arrays to cloud-based analytics and user-facing visualization platforms [,].
A fundamental component of this approach is the implementation of user-centric consent management frameworks. These systems must provide users with transparent information regarding data collection and processing purposes, such as predictive maintenance, billing optimization, grid balancing, and data sharing practices []. In alignment with the stipulations of GDPR and CCPA, it is imperative that users are granted the capability to opt out of non-essential data processing, access their personal information, request its deletion, and contest profiling practices. The implementation of dynamic consent models, which facilitate real-time adjustments to user consent, has been shown to bolster user trust and participation [].
In accordance with privacy by design principles, the adoption of data minimization and purpose limitation is vital for ensuring responsible data governance in DTs-enabled EVCS. These principles require that only data necessary for fundamental system operations, such as routing, billing, or charging optimization, be collected and processed []. For instance, real-time location data essential for operational efficiency can be anonymized following initial processing to reduce the risks associated with prolonged user tracking. Furthermore, it is imperative to establish well-defined data retention policies that impose temporal constraints on data storage and usage, in accordance with the GDPR’s accountability and proportionality requirements [].
5.4. Cryptographic Protections and Access Control
The protection of sensitive data necessitates the implementation of robust encryption protocols and access control mechanisms.
Data in transit should be secured using TLS 1.3, which provides forward secrecy and minimizes handshake overhead [], while data at rest must employ encryption standards such as AES-256. Implementing Role-Based Access Control (RBAC) is essential for regulating access to sensitive datasets. By assigning permissions according to predefined roles, RBAC effectively minimizes the risk of internal misuse [,]. Furthermore, advanced techniques for privacy-preserving computation are crucial, particularly within federated and decentralized DTs environments. Prominent methods include:
- I.
- k-Anonymity: Ensures that individual user records cannot be uniquely identified by aggregating datasets []. This method proves highly effective in concealing electric vehicle (EV) charging patterns for regional grid analysis.
- II.
- Homomorphic Encryption: Facilitates the processing of encrypted data without the need for decryption, thereby enabling secure cloud-based analytics while maintaining the confidentiality of the data [].
- III.
- Secure Multi-Party Computation (SMPC): This process enables collaborative computation among various stakeholders, including utilities, regulators, and Original Equipment Manufacturers (OEMs), while ensuring that raw data inputs remain confidential [].
These strategies facilitate the continued functionality of DTs systems while effectively minimizing the potential for unauthorized access or inference attacks.
5.5. Risk Assessment and Continuous Monitoring
To ensure privacy and security throughout the digital transformation lifecycle, it is imperative to conduct Privacy Impact Assessments (PIAs) on a regular basis []. These assessments, in accordance with the accountability principle of the GDPR and the ISO/IEC 27701 standard for Privacy Information Management Systems (PIMS), are designed to identify, evaluate, and mitigate privacy risks in dynamic system configurations [].
Moreover, continuous cybersecurity monitoring, as delineated in NIST IR 8356, is crucial for identifying vulnerabilities such as unauthorized access attempts, malware intrusions, or anomalous data behavior []. To ensure the long-term sustainability and scalability of DTs-enabled electric vehicle charging systems, a comprehensive, multi-faceted strategy is necessary, integrating legal, technical, and ethical dimensions. Adherence to international standards such as ISO 15118, OCPP 2.0.1, IEEE 2030.5, and NIST IR 8356 are essential for facilitating interoperability, secure communication, and maintaining system integrity.
In conjunction with compliance with GDPR, CCPA, and NIS2 regulations, these technical safeguards establish a robust framework for ensuring user privacy and data protection. By integrating privacy by design principles, employing advanced cryptographic techniques, and implementing comprehensive risk governance mechanisms, stakeholders can enhance trust, achieve regulatory compliance, and advance technological maturity within the evolving context of DTs-enabled electric vehicle charging infrastructure.
5.6. Financial Feasibility of Digital Twin Implementation
The incorporation of DTs technology into EVCS, particularly within 5G/6G-enabled smart mobility networks, presents significant potential for advancing cybersecurity. By facilitating real-time system monitoring, predictive diagnostics, and automated threat response, DTs offer a proactive defense mechanism against a broad range of cyber–physical threats []. The capabilities are further enhanced by the low-latency and high-throughput communication features of next-generation wireless networks, such as Ultra-Reliable Low Latency Communications (URLLC) and MEC within the framework of 5G/6G standards [].
Nevertheless, the integration of DTs architecture within EVCS ecosystems presents a variety of cost-related complexities that require thorough assessment. These costs encompass several technological layers as discussed below:
- I.
- The physical layer encompasses investments in instrumentation, embedded control modules, edge computing devices, and HIL simulation units.
- II.
- The data layer includes investments in gateways that comply with protocols such as OCPP 2.0.1 and ISO 15118, secure communication interfaces, and high-bandwidth network subscriptions.
- III.
- The modeling and control layer demands the integration of real-time simulation platforms, such as MATLAB/Simulink or RSCAD, alongside system optimization engines to refine performance tuning.
- IV.
- The implementation of the AI layer entails substantial expenses associated with the development of data pipelines, the training of models, the orchestration of federated learning, and the continuous monitoring for model drift and bias.
Each layer greatly affects the total Capital Expenditure (CAPEX) and Operational Expenditure (OPEX) of the DTs-enhanced EVCS setup. These financial factors are very important in large city projects, where growth, compatibility, and following global standards must be balanced with budget limits. So, while adding digital technologies improves strength, automation, and risk control, it also requires careful cost planning to keep it economically sustainable in the long run.
To assess the economic viability of DTS-based cybersecurity solutions for EVCS, a cost–benefit analysis compared to conventional approaches is crucial. Conventional EVCS cybersecurity, utilizing firewalls, intrusion detection systems, and periodic updates, requires lower initial CAPEX of $10,000–$50,000 per site and OPEX of $5000–$15,000 annually for maintenance and monitoring []. However, their reactive nature leads to significant indirect costs from cyber incidents, such as data breaches costing around $200,000–$1 million per incident or service disruptions affecting grid stability and user trust [,]. In contrast, DTs-based solutions demand higher CAPEX, ranging from $30,000–$600,000 per site, including sensors costing approximately $50–$765 [], edge computing devices ranging $120–$249 [], HIL platforms costing $20,000–$500,000 [,,], and network subscriptions estimated at $5000–$50,000 []. The modeling and AI layers further elevate costs, with total CAPEX for a mid-sized urban deployment covering 10–50 chargers reaching $200,000–$1.5 million and OPEX of $50,000–$150,000 annually for cloud services, AI retraining, and personnel [,,,].
Despite higher costs, DTs offer substantial benefits through enhanced security and efficiency. Real-time anomaly detection and predictive diagnostics reduce successful attacks by 60–80%, avoiding losses of $120,000–$800,000 per incident and cutting downtime costs by 10–20% costing $10,000–$50,000 per hour for large networks [,,]. DTs also save 5–15% on electricity costs $10,000–$30,000 annually per high-traffic site, achieving ROI within 3–5 years for a 50-charger network, compared to 5–7 years for conventional systems []. While conventional approaches struggle with scalability in 5G/6G environments and zero-day threats, DTs provide modular scalability and automated responses, reducing labor costs by 20–30% value at $15,000–$25,000 per site []. Although small-scale or rural deployments may find DTs costs prohibitive, phased adoption and policy incentives like grants could offset CAPEX and enhance user trust and regulatory compliance while accelerating secure EVCS deployment.
5.7. Physical Layer Costs
At the physical layer, the architecture of EVCS is dependent on a range of hardware components essential for real-time monitoring and control.
These components include voltage and current sensors, thermal monitoring devices, and embedded control modules, which are typically integrated into the EVCS.
The cost of instrumentation per EVCS unit varies considerably, ranging from approximately $50 to $765, contingent upon the complexity and precision of the sensing technologies employed []. In addition to sensing hardware, edge computing platforms such as the NVIDIA Jetson and Raspberry Pi are commonly employed to enable local data processing. These devices are priced at approximately $249 and $120, respectively, with the price differences reflecting variations in computational capabilities and memory configurations [,]. Furthermore, for the advanced testing and real-time validation of EVCS operations, HIL simulation systems, including platforms such as Opal-RT and Typhoon HIL, are essential. These systems facilitate high-fidelity simulation environments and are available at a wide price range of $20,000 to $500,000, contingent upon system specifications, scalability, and the degree of Multiphysics integration required [,].
5.8. Data Layer Costs
At the data layer, DTs-enabled EVCSs depend on effective telemetry management, which is facilitated by standard communication protocols such as the Controller Area Network (CAN), OCPP 2.0.1, and ISO 15118. These protocols ensure secure, real-time data exchange between the EVCS, backend servers, and grid management systems []. To ensure protocol interoperability and maintain data integrity, specialized communication gateways are implemented at the charger level. The unit costs of these gateways range from approximately $164.70 to $1190, contingent upon factors such as processing capacity, embedded encryption features, and compatibility with multi-protocol operations []. As EVCS networks progress towards enhanced scalability and responsiveness, the connectivity infrastructure emerges as a fundamental aspect of performance. The incorporation of 5G/6G technologies, particularly those utilizing URLLC and MEC, significantly improves communication latency and throughput, thereby facilitating time-sensitive telemetry and security operations [].
5.9. Modeling and Simulation Layer Costs
At the modeling layer, real-time simulations are performed to mimic the dynamic behavior of EVCS under various operating conditions. This capability is essential for virtual commissioning, control logic validation, and testing cyber–physical resilience. Industry-standard simulation environments like MATLAB/Simulink and RSCAD are frequently used for these purposes. MATLAB/Simulink provides a wide array of toolboxes specifically designed for power systems and embedded control, with commercial licenses typically costing between $5000 and $15,000 per seat, depending on the configuration and toolbox selection [].
RSCAD, designed specifically for integration with Real-Time Digital Simulator (RTDS) hardware, facilitates high-fidelity electromagnetic transient simulations in real-time settings. When bundled with RTDS hardware, the licensing costs for RSCAD typically range from $25,000 to over $500,000. These costs vary based on the size of the simulation rack, the number of nodes, and the inclusion of advanced modules like GTNET and GTFPGA for communication and hardware interfacing [].
While Python-based frameworks such as OpenModelica, SimPy, or custom-built co-simulation environments offer the advantage of open-source flexibility, they generally necessitate substantial customization and development time. This requirement often leads to increased personnel costs and prolonged integration cycles [].
Furthermore, the utilization of cloud-based GPU resources for AI-enhanced simulations or federated modeling incur operational costs ranging from $0.35 to $2.48 per hour.
These expenses are contingent upon computational requirements, the complexity of the simulations, storage needs, and the necessity for continuous uptime []. Notwithstanding the associated cost implications, the modeling layer confers significant strategic advantages. By facilitating high-fidelity simulations within controlled digital environments, organizations can mitigate commissioning risks, substitute costly field testing with virtual validation, and expedite deployment timelines while ensuring adherence to safety and performance standards [].
5.10. AI and Analytics Layer Costs
In the context of AI, DTs-enabled EVCSs employ advanced computational models to enhance predictive analytics, detect anomalies, and optimize adaptive control strategies. This layer plays a pivotal role in enabling proactive system diagnostics and the early identification of threats, both of which are crucial for maintaining the performance and security of modern smart mobility infrastructure []. The initial capital investment required for the implementation of artificial intelligence capabilities encompasses the establishment of robust data pipelines. This process typically incurs costs ranging from $100,000 to $300,000, which include data ingestion, cleaning, labeling, and integration across diverse sources [].
In the implementation of federated learning architectures and reinforcement learning agents, particularly within decentralized environments that emphasize edge privacy and control coordination, additional costs ranging from $50,000 to $100,000 are frequently incurred []. Operational expenditures are sustained throughout the lifecycle of AI models, particularly concerning model retraining, bias mitigation, and drift detection. These activities are crucial for ensuring model accuracy, fairness, and adherence to regulatory standards in dynamic environments []. Despite the considerable costs associated with setup and maintenance, the implementation of an AI layer yields substantial improvements in operational efficiency.
This results in quantifiable labor savings and enhanced resilience for operators of smart cities and managers of electric vehicle fleets []. Financial feasibility, evaluated through CAPEX, OPEX, and ROI, indicates that while the initial investments are substantial, the long-term economic and security advantages substantiate the integration. Ultimately, a strategic, standards-aligned implementation of DTs in EVCS ensures a scalable, secure, and economically viable infrastructure for the future of electric mobility. To contextualize the implementation challenges and opportunities associated with DTs in EVCS, it is imperative to examine the intersection of technical standards, data privacy regulations, and financial considerations. Table 8 presents a synthesized review of the key aspects influencing the adoption and scalability of DTs-enabled EVCS, highlighting the relevant regulatory frameworks, implementation challenges, and recommended mitigation strategies.

Table 8.
Review of Standards, Privacy, and Financial Feasibility for DTs-Enabled EVCS.
5.11. Energy Consumption and Environmental Impact
The deployment of DT systems in EVCS introduces significant energy consumption considerations due to the computational and communication demands of maintaining real-time synchronization between physical and digital components. Frequent edge–cloud synchronization, enabled by 5G/6G networks, requires substantial data transmission and processing, which can consume considerable energy []. Edge computing platforms, such as NVIDIA Jetson or Raspberry Pi, used for local data processing, typically draw 5–20 watts per unit, depending on workload and configuration []. Cloud-based servers, often employed for complex simulations and AI model training, can consume hundreds of watts per server, with large-scale data centers potentially requiring megawatts of power for continuous operation [].
The high-frequency data exchanges in 5G/6G environments, particularly with Ultra-Reliable Low Latency Communications (URLLC), further amplify energy usage due to the power demands of high-speed, low-latency network infrastructure []. This energy consumption directly impacts the environmental footprint of DTs-enabled EVCS, particularly in regions that are reliant on fossil fuel-based energy sources. The carbon emissions associated with powering edge devices, cloud servers, and network infrastructure can undermine the sustainability goals of smart mobility systems, which aim to reduce greenhouse gas emissions through EV adoption.
For instance, a typical cloud data center can emit approximately 0.4–0.6 kg of CO2 per kWh of electricity consumed, depending on the energy mix [,]. In urban environments with dense EVCS deployments, the cumulative energy demand of DT systems can be substantial, potentially offsetting the environmental benefits of EVs if not powered by renewable energy sources [,]. To mitigate these impacts, energy-efficient strategies must be integrated into DTS implementations.
Utilizing renewable energy sources, such as solar or wind power, for edge and cloud computing operations can significantly reduce carbon emissions [].
Energy-efficient hardware, such as low-power edge devices and optimized server architectures, can further minimize energy consumption []. Adaptive synchronization protocols that dynamically adjust data exchange frequency based on operational needs can reduce unnecessary energy usage while maintaining system performance []. Additionally, leveraging open-source simulation frameworks like OpenModelica can lower computational demands compared to resource-intensive commercial platforms like MATLAB/Simulink, provided they meet performance requirements []. These measures are critical to aligning DTs-enabled EVCS with the environmental objectives of sustainable mobility, ensuring that cybersecurity enhancements do not come at the expense of increased carbon footprints.
6. Research Gaps and Future Directions
This review identifies significant research gaps across technical, operational, and governance dimensions. The identified gaps span multiple interconnected domains, each presenting distinct challenges that must be addressed to fully exploit DTs-enabled EVCS cybersecurity.
These gaps highlight fundamental limitations in current methodologies and emphasize areas where innovative research is essential for effective deployment.
6.1. Research Gaps
6.1.1. Security and Trust Deficiencies
Critical security vulnerability persists in the protection of DT systems throughout their operational lifecycle. Current research inadequately addresses vulnerabilities that span the phases of model development, deployment, runtime operation, and decommissioning, thereby leaving EVCS susceptible to sophisticated supply chain attacks, model poisoning during development, and unauthorized modifications during deployment. The absence of comprehensive security frameworks specifically tailored for DTs architecture creates significant exposure points that adversaries can exploit to compromise the entire security posture of EVCS infrastructure. Notably, existing research overlooks a fundamental vulnerability inherent in DTs-based security systems. The DTs themselves represent high-value attack targets that can be compromised to undermine the entire security architecture. This situation creates what is termed the “guardian paradox,” wherein the security monitoring and protection system becomes the primary attack vector for sophisticated adversaries.
Attackers can compromise DTs’ integrity to provide false security assessments, manipulate DTs outputs to mask ongoing physical attacks, exploit DTs privileges for unauthorized access to critical systems, or launch denial-of-service attacks against the DTs infrastructure itself. The compromise of DTs systems poses significant risks, as it can grant attackers legitimate credentials and trusted access to critical infrastructure while simultaneously obscuring ongoing attacks from operators. The integration of DTs with V2G, Vehicle-to-Everything (V2X), and smart grid systems results in complex interdependencies that substantially increase the cyber–physical attack surface. Current threat modeling methodologies inadequately address the cascading vulnerabilities that emerge from these cross-domain interactions, particularly in scenarios involving coordinated multi-vector attacks that exploit the trusted relationships between systems.
The interconnected nature of these systems implies that a compromise in one domain can swiftly propagate across others, potentially causing extensive disruption to both transportation and energy infrastructure.
Furthermore, the forthcoming quantum computing revolution presents long-term cryptographic challenges that current DTs implementations are ill-equipped to manage. The cryptographic foundations underpinning DTs security architectures face obsolescence as quantum computing capabilities progress, yet research lacks practical implementations of post-quantum cryptographic algorithms that are optimized for the resource-constrained nature of EVCS devices while maintaining the real-time performance requirements essential for effective DTs operations.
6.1.2. AI and Machine Learning Limitations
AI-driven IoDT systems encounter substantial challenges in differentiating between legitimate operational evolution and adversarial manipulation. As EVCS environments naturally evolve over time, the AI models that power DTs systems experience model drift, which can diminish their efficacy in threat detection and system optimization. Current drift detection mechanisms lack the sophistication required to manage the highly dynamic nature of 5G/6G network traffic patterns while concurrently identifying subtle adversarial manipulations intended to gradually degrade system performance.
This challenge is particularly pronounced in environments where attackers may employ sophisticated techniques to incrementally introduce model drift, rendering detection extremely difficult using conventional approaches. Federated learning, while offering promising capabilities for collaborative threat intelligence sharing across distributed IoDTs networks, introduces significant security vulnerabilities that current research has not adequately addressed. Existing federated learning approaches are vulnerable to model poisoning attacks, where malicious participants can corrupt the global model, inference attacks that can extract sensitive information from model updates, and data leakage that can compromise privacy. The safety-critical nature of EVCS environments necessitates robust privacy-preserving federated learning frameworks that can maintain security effectiveness while enabling beneficial collaboration among DTs operators.
The opacity of many AI models employed in DT systems creates additional challenges for security analysis and regulatory compliance. The black-box nature of deep learning models complicates the ability of security analysts to understand decision-making processes, validate security responses, and provide the transparency required for regulatory compliance in critical infrastructure applications. Research in explainable AI techniques specifically tailored for DTs security applications remains insufficient, particularly for approaches that can provide interpretable insights without compromising the effectiveness of security mechanisms.
6.1.3. Standards and Interoperability Deficiencies
Current cybersecurity standards, such as ISO 15118, OCPP 2.0.1, and NIST IR 8356, were formulated without consideration of DTs architecture, resulting in substantial deficiencies in authentication, authorization, and data integrity requirements specific to DT deployments within EVCS environments. These shortcomings in the standards leave organizations without explicit guidance for implementing DTs security controls, achieving regulatory compliance, and ensuring interoperability across various vendor implementations.
The lack of DTs-specific security standards generates uncertainty in the marketplace and hinders the development of consistent security practices across the industry. The diverse nature of EVCS vendor ecosystems, coupled with their proprietary DTs implementations, presents significant interoperability challenges that compromise the efficacy of coordinated security responses.
In the absence of standardized APIs, data formats, and communication protocols for seamless DT integration across various vendor platforms, the scalability and effectiveness of DT-enabled security solutions are markedly constrained.
This lack of interoperability hinders the realization of comprehensive threat intelligence sharing and coordinated incident response capabilities, which are crucial for safeguarding large-scale EVCS deployments.
6.1.4. Privacy and Governance Challenges
Existing privacy-preserving techniques, despite their theoretical robustness, introduce computational overhead that restricts their practical application in real-time IoDTs operations. Techniques such as homomorphic encryption and secure multi-party computation demand significant computational resources, which may not be accessible in edge computing environments where numerous DTs functions must be executed. There is a notable gap in research concerning lightweight privacy-preserving algorithms that are specifically optimized for the resource constraints and performance demands of edge-deployed DTs systems, while also ensuring compliance with evolving privacy regulations, including GDPR, CCPA, and emerging frameworks.
Current consent management frameworks are inadequate for the dynamic and continuous data collection requirements inherent in DTs system operations. Users necessitate granular control over the utilization of their data within DTs systems; however, existing frameworks fail to accommodate the real-time decision-making requirements and adaptive data usage patterns that are characteristic of effective DTs implementations. The development of adaptive consent mechanisms that provide users with meaningful control while maintaining system functionality represents a significant research challenge that must be addressed to facilitate widespread adoption of DT.
6.1.5. Economic and Implementation Barriers
While the technical advantages of IoDTs enabled EVCS cybersecurity are increasingly apparent, there remains a lack of comprehensive cost–benefit analysis frameworks that sufficiently consider capital expenditures, operational expenses, and the value of risk mitigation. This analytical deficiency hinders informed decision-making by infrastructure operators and policymakers, who require clear economic justification for investments in DTs.
The complexity involved in quantifying security benefits, particularly in terms of avoided losses and enhanced operational efficiency, poses challenges in constructing persuasive business cases for DTs adoption. Current research notably lacks systematic methodologies for phased DTs deployment, which would allow organizations to incrementally adopt capabilities while managing costs and operational risks. Organizations require clear implementation of roadmaps that facilitate a gradual transition from traditional security approaches to DTs-enabled systems, without compromising operational continuity or introducing unacceptable risks during transition periods.
6.1.6. Technical Limitations of Digital Twins
DTs significantly bolster the cybersecurity of EVCS but are limited by technical challenges. Synchronization delays, often due to 5G/6G network latency or resource-constrained edge devices, can impede real-time threat detection, especially in dense urban areas with numerous charging stations where millisecond-scale delays may miss critical security events. Model drift, caused by hardware degradation or shifting grid dynamics, further undermines the DTs ability to detect subtle cyberattacks without continuous recalibration. Resource-limited edge devices struggle to support real-time modeling and AI-driven threat detection, forcing trade-offs between security and computational efficiency, while data update delays from intermittent connectivity or overloaded cloud infrastructure create vulnerabilities that attackers can exploit.
These limitations introduce new attack surfaces, making DTs both an asset and a potential liability. Application Programming Interface (API) hijacking can compromise data exchanges between DTs, EVCS, or backend systems, potentially disrupting charging operations or grid stability, especially if protocols like OCPP 2.0.1 lack robust authentication. Data poisoning, where attackers manipulate inputs like voltage or battery metrics, can mislead DTs into misinterpreting system states, risking grid instability by mimicking demand surges. Model spoofing, a more severe threat, allows attackers to manipulate DTs logic to conceal malicious activities like firmware tampering. To counter these risks, robust API encryption, continuous authentication, advanced anomaly detection using time-series analysis and unsupervised learning, blockchain-based model versioning, and low-latency protocols with lightweight AI are essential to ensure DTs enhance EVCS cybersecurity effectively.
6.2. Future Research Directions
Addressing the identified research gaps requires a systematic approach that prioritizes foundational security mechanisms while building toward comprehensive, scalable solutions. The proposed research directions are organized to address immediate security concerns while establishing the technical foundations necessary for long-term success.
6.2.1. Scalable and Resilient DTs Architectures
Future research endeavors should prioritize the creation of adaptive synchronization protocols that harness the potential of emerging 6G technologies, including Terahertz communication and integrated sensing. These protocols should enable dynamic fidelity adjustments by assessing system criticality and threat levels in real-time. It is essential for these protocols to incorporate context-aware algorithms that can respond to varying network conditions and security requirements, as well as hierarchical synchronization strategies tailored for multi-tier EVCS deployments. Establishing Quality-of-Service frameworks to prioritize essential DTs synchronization tasks based on operational needs is also crucial. Energy-efficient synchronization techniques are particularly vital for battery-limited edge devices participating in DTs networks.
Another significant research direction involves distributed DTs orchestration, which requires the development of coordination frameworks to manage multiple DTs across expansive EVCS networks. Blockchain-based consensus mechanisms offer promising solutions for managing DTS state and ensuring integrity, while hierarchical control architectures can provide centralized oversight with decentralized execution. Additionally, there is a need for advanced load balancing and resource allocation algorithms specifically designed for distributed DTs workloads, along with robust fault tolerance and recovery mechanisms to address DTs network failures and partitioning scenarios without compromising security.
6.2.2. Advanced Security and Trust Mechanisms
The protection of DTs against targeted attacks requires dedicated research into comprehensive integrity assurance frameworks that can detect, prevent, and respond to attacks against the DTs infrastructure itself. It is imperative to develop multi-layered DTs health monitoring and integrity verification systems to continuously evaluate the trustworthiness of DTs.
Concurrently, backup and recovery mechanisms should be established to facilitate the swift restoration of compromised DTs instances, thereby minimizing service disruptions. Strategies for DTS isolation and containment are crucial to prevent lateral movement from compromised twins to other system components.
Additionally, multi-IoDTs validation mechanisms can offer consensus-based verification for critical security decisions. The need for attack attribution and forensic capabilities specifically tailored to DTs-targeted incidents is an emerging area of research, as traditional forensic methods may prove inadequate for analyzing attacks on DT infrastructure.
The deployment of honeypot DTs implementations can yield valuable intelligence regarding attacker techniques and intentions, while also serving as early warning systems for sophisticated attacks on production DTs infrastructure. Zero-trust security architecture specifically designed for digital DTs-enabled EVCS environments must integrate continuous authentication and authorization mechanisms for all DTs components and users. Furthermore, they should employ behavioral analytics for real-time DTS integrity verification and anomaly detection, as well as micro-segmentation strategies to isolate critical DTs functions and data flows.
Dynamic trust scoring mechanisms, based on DTs performance metrics, security assessments, and threat intelligence, can facilitate adaptive security posture management that automatically responds to evolving threat conditions. Immediate research attention is required for quantum-resistant security implementations to prepare DTs systems for the post-quantum era.
It is imperative to develop lightweight lattice-based and hash-based cryptographic algorithms optimized specifically for DTs operations, alongside hybrid classical-quantum approaches that ensure security during transition periods. The integration of quantum key distribution with emerging 6G sensing capabilities presents promising avenues for achieving quantum-safe communications, while performance benchmarking of post-quantum algorithms in real-time DTs operations will be crucial for practical deployment decisions.
6.2.3. Intelligent AI and Machine Learning Systems
Self-adaptive DTs intelligence systems, which are capable of continuous learning and adaptation while ensuring security, represent a significant research frontier. Advanced drift detection algorithms that integrate time-series analysis with unsupervised learning methodologies can effectively differentiate between legitimate operational evolution and adversarial manipulation. Concurrently, self-healing mechanisms facilitate automatic model recalibration and optimization without the need for human intervention. The development of adversarial training techniques specifically tailored for robust anomaly detection under attack conditions is imperative, alongside multi-modal learning approaches that can synthesize diverse EVCS data sources for comprehensive threat detection. Continual learning frameworks that adapt to evolving threat landscapes without succumbing to catastrophic forgetting of previously learned threats constitute a critical research challenge.
These systems must sustain their effectiveness against known threats while continuously updating their capabilities to address emerging attack vectors and novel threat patterns. Secure federated learning networks necessitate advanced privacy-preserving mechanisms that enable collaborative learning while safeguarding against sophisticated attacks. Differential privacy mechanisms with quantified privacy guarantees must be developed for federated model training, while secure aggregation protocols resistant to model poisoning and inference attacks are essential for maintaining the integrity of collaborative learning processes.
Cross-validation frameworks for distributed threat intelligence sharing can facilitate beneficial cooperation among DTs operators, while Byzantine fault-tolerant federated learning algorithms provide resilience against adversarial participants within the learning network.
6.2.4. Standardization and Interoperability Frameworks
The formulation of DTs-native security standards tailored for EVCS applications constitutes a critical research imperative. It is essential to establish authentication and authorization protocols for the comprehensive management of the DTs lifecycle, alongside standardized mechanisms for data integrity and provenance verification that can monitor DTs model and data lineage throughout the system lifecycle. Standardized APIs for secure DTs interoperability across various vendors and platforms are crucial for facilitating the ecosystem-wide collaboration necessary for effective cybersecurity.
Concrete priorities include developing standardized DT testbeds for EVCS, such as cyber–physical platforms integrating OCPP/ISO 15118 with HIL simulations to replicate 5G/6G threats, enabling reproducible benchmarking of resilience metrics like MTTR under FDIA scenarios. Resilience benchmarking frameworks should quantify DT performance in V2G contexts via multi-physics models assessing grid stability under cascading attacks, targeting 90%+ recovery rates. For cross-border deployments, data-sharing frameworks compliant with GDPR/NIS2 must incorporate federated DT learning to secure energy flow data across EU grids, mitigating sovereignty risks in renewable integration.
Furthermore, compliance frameworks for multi-jurisdictional DTS deployments must address the intricate regulatory landscape governing the protection of critical infrastructure. Research into cross-domain integration protocols is required to develop secure mechanisms for DTs interaction across V2G, V2X, and smart grid ecosystems. Network slicing strategies can isolate critical EVCS functions while enabling essential cross-domain interactions, and grid-aware security protocols must ensure system stability during cyber incidents. Interoperable threat intelligence sharing frameworks across domain boundaries can enhance overall security effectiveness, while coordinated incident response protocols for cross-domain attacks ensure a rapid and effective response to sophisticated threats that span multiple infrastructure domains.
6.2.5. Privacy by Design and Regulatory Alignment
Lightweight privacy preservation techniques optimized for real-time DTs operations necessitate focused scholarly investigation. It is imperative to develop edge-optimized homomorphic encryption algorithms that minimize computational overhead; alongside secure multi-party computation protocols specifically designed for distributed DTS analytics. Privacy-preserving synthetic data generation techniques can facilitate DTs training and testing without compromising sensitive information, while dynamic anonymization approaches for continuous data streams must accommodate varying sensitivity levels and regulatory requirements.
Adaptive governance frameworks, capable of managing the complex regulatory landscape surrounding DTs deployments, must incorporate dynamic consent management systems that provide real-time user control and transparency. Automated compliance monitoring and reporting mechanisms can alleviate administrative burdens while ensuring adherence to regulatory requirements across multiple jurisdictions. Cross-jurisdictional data governance frameworks are particularly crucial for international EVCS networks that must comply with diverse privacy and security regulations.
6.2.6. Practical Implementation and Validation
Comprehensive pilot deployment studies are crucial for validating DTs frameworks in real-world environments and demonstrating their practical efficacy. Large-scale urban EVCS testbeds, encompassing thousands of charging stations across diverse operational conditions, can yield valuable insights into scalability limitations and performance characteristics. Longitudinal studies evaluating DTs performance under varying threat scenarios and system loads are essential for understanding long-term reliability and effectiveness. Establishing industry-academia collaboration ecosystems is imperative to expedite the transition from research to practical deployment.
The joint development of open-source DTs platforms for EVCS cybersecurity can provide common foundations for innovation, while standardized benchmarking frameworks enable objective comparison of different DTs security solutions. Knowledge transfer programs can accelerate DTs adoption in industry, while public–private partnerships provide the resources necessary for large-scale DTs infrastructure development.
7. Conclusions
This review examines the integration of DTs technology with 5G/6G networks to enhance cybersecurity in EVCS. It underscores DTs as a robust defense mechanism within cyber–physical systems. Key points include the following:
- I.
- DTs enhance security through real-time monitoring, predictive diagnostics, and threat mitigation, yet they remain susceptible to manipulation, necessitating robust integrity assurance, secure model versioning, and trust frameworks.
- II.
- Features such as Ultra-Reliable Low-Latency Communications (URLLC), Multi-access Edge Computing (MEC), and network slicing facilitate scalable DTs architecture; however, challenges persist in distributed computing, synchronization, and security across large-scale EVCS.
- III.
- AI-driven anomaly detection, blockchain-based trust, and quantum-resistant encryption demonstrate potential but are insufficient in real-world EVCS settings.
- IV.
- The lack of standardization, AI model drift, DTs lifecycle management, economic feasibility, and compliance with privacy regulations present significant obstacles, necessitating interdisciplinary research and DTs-native security protocols.
- V.
- Clear cost–benefit models and return on investment (ROI) are essential to incentivize infrastructure operators to adopt DTs-based cybersecurity solutions.
- VI.
- Privacy-by-design, user consent mechanisms, and legal harmonization are critical for compliance, trust, and sustainability, particularly as Vehicle-to-Grid (V2G), Vehicle-to-Home (V2H), and Vehicle-to-Everything (V2X) technologies increase cyber risks.
The integration of DTs technology significantly enhances EVCS cybersecurity, but its energy consumption and environmental impact must be carefully managed to align with the sustainability goals of smart mobility. By prioritizing renewable energy sources, energy-efficient hardware, and adaptive synchronization protocols, DTs-enabled EVCS can achieve robust security without compromising environmental objectives. The review concludes that fully developed and responsibly deployed DTs technology is crucial for a secure, intelligent, and resilient EVCS ecosystem, requiring urgent collaboration among academia, industry, and policymakers. Addressing concrete challenges, including the development of open-source DT testbeds for scalable EVCS validation, the establishment of resilience benchmarks for V2G systems under zero-day threats, and the creation of harmonized cross-border frameworks for secure data flows, will accelerate the realization of resilient and interoperable infrastructure networks.
Author Contributions
Conceptualization, E.F.M. and M.H.A.; methodology, E.F.M. and M.H.A.; software, E.F.M. and M.H.A.; validation, M.H.A.; formal analysis, E.F.M.; investigation, E.F.M.; resources, E.F.M. and M.H.A.; data curation, E.F.M.; writing—original draft preparation, E.F.M.; writing—review and editing, M.H.A.; visualization, E.F.M.; supervision, M.H.A.; project administration, M.H.A.; funding acquisition, M.H.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Udendhran, R.; Mohan, T.R.; Babu, R.; Uthra, R.A.; Anupama, C.G.; Selvakumarasamy, S.; Dinesh, G.; Mukhopadhyay, M.; Saraswat, V.; Chakraborty, P. Transitioning to sustainable E-vehicle systems-Global perspectives on the challenges, policies, and opportunities. J. Hazard. Mater. Adv. 2025, 17, 100619. [Google Scholar] [CrossRef]
- Tilly, N.; Yigitcanlar, T.; Degirmenci, K.; Paz, A. How sustainable is electric vehicle adoption? Insights from a PRISMA review. Sustain. Cities Soc. 2024, 117, 105950. [Google Scholar] [CrossRef]
- Timilsina, R.R.; Zhang, J.; Rahut, D.B.; Patradool, K.; Sonobe, T. Global drive toward net-zero emissions and sustainability via electric vehicles: An integrative critical review. Energy Ecol. Env. 2025, 10, 125–144. [Google Scholar] [CrossRef]
- Acharige, S.S.G.; Haque, M.E.; Arif, M.T.; Hosseinzadeh, N.; Hasan, K.N.; Oo, A.M.T. Review of Electric Vehicle Charging Technologies, Standards, Architectures, and Converter Configurations. IEEE Access 2023, 11, 41218–41255. [Google Scholar] [CrossRef]
- Hamdare, S.; Kaiwartya, O.; Aljaidi, M.; Jugran, M.; Cao, Y.; Kumar, S.; Mahmud, M.; Brown, D.; Lloret, J. Cybersecurity Risk Analysis of Electric Vehicles Charging Stations. Sensors 2023, 23, 6716. [Google Scholar] [CrossRef] [PubMed]
- Singh, A.R.; Vishnuram, P.; Alagarsamy, S.; Bajaj, M.; Blazek, V.; Damaj, I.; Rathore, R.S.; Al-Wesabi, F.N.; Othman, K.M. Electric vehicle charging technologies, infrastructure expansion, grid integration strategies, and their role in promoting sustainable e-mobility. Alex. Eng. J. 2024, 105, 300–330. [Google Scholar] [CrossRef]
- Tanyıldız, H.; Batur Şahin, C.; Batur Dinler, Ö.; Migdady, H.; Saleem, K.; Smerat, A.; Gandomi, A.H.; Abualigah, L.M. Detection of cyber attacks in electric vehicle charging systems using a remaining useful life generative adversarial network. Sci. Rep. 2025, 15, 10092. [Google Scholar] [CrossRef]
- Stichow, A.; Rempel, P. Securing Electric Vehicle Charging Stations: A Critical Analysis of Authentication Vulnerabilities. In Proceedings of the 32nd IEEE International Requirements Engineering Conference Workshops, REW 2024, Reykjavik, Iceland, 24–25 June 2024; pp. 231–240. [Google Scholar] [CrossRef]
- Acharya, S.; Mieth, R.; Karri, R.; Dvorkin, Y. False data injection attacks on data markets for electric vehicle charging stations. Adv. Appl. Energy 2022, 7, 100098. [Google Scholar] [CrossRef]
- Rubio, J.E.; Alcaraz, C.; Lopez, J. Addressing Security in OCPP: Protection Against Man-in-The-Middle Attacks. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security, NTMS 2018, Paris, France, 26–28 February 2018; Volume 2018, pp. 1–5. [Google Scholar] [CrossRef]
- Basnet, M.; Poudyal, S.; Ali, M.H.; Dasgupta, D. Ransomware detection using deep learning in the SCADA system of electric vehicle charging station. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Conference—Latin America, ISGT Latin America 2021, Lima, Peru, 15–17 September 2021. [Google Scholar] [CrossRef]
- Aljohani, T.; Almutairi, A. Modeling time-varying wide-scale distributed denial of service attacks on electric vehicle charging Stations. Ain Shams Eng. J. 2024, 15, 102860. [Google Scholar] [CrossRef]
- AbdelrahemLastname, M.; Aldweesh, A. Blockchain-Based Secure Firmware Updates for Electric Vehicle Charging Stations in Web of Things Environments. World Electr. Veh. J. 2025, 16, 226. [Google Scholar] [CrossRef]
- Aljohani, T.; Almutairi, A. A comprehensive survey of cyberattacks on EVs: Research domains, attacks, defensive mechanisms, and verification methods. Def. Technol. 2024, 42, 31–58. [Google Scholar] [CrossRef]
- Sasi, T.; Lashkari, A.H.; Lu, R.; Xiong, P.; Iqbal, S. A comprehensive survey on IoT attacks: Taxonomy, detection mechanisms and challenges. J. Inf. Intell. 2024, 2, 455–513. [Google Scholar] [CrossRef]
- Mazumder, M.; Debbarma, S. EV Charging Stations with a Provision of V2G and Voltage Support in a Distribution Network. IEEE Syst. J. 2021, 15, 662–671. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Friha, O.; Kantarci, B.; Tihanyi, N.; Cordeiro, L.; Debbah, M.; Hamouda, D.; Al-Hawawreh, M.; Choo, K.-K.R. Edge Learning for 6G-Enabled Internet of Things: A Comprehensive Survey of Vulnerabilities, Datasets, and Defenses. IEEE Commun. Surv. Tutor. 2023, 25, 2654–2713. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Suman, R. Digital Twin applications toward Industry 4.0: A Review. Cogn. Robot. 2023, 3, 71–92. [Google Scholar] [CrossRef]
- Coppolino, L.; Nardone, R.; Petruolo, A.; Romano, L.; Souvent, A. Exploiting Digital Twin technology for Cybersecurity Monitoring in Smart Grids. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023. [Google Scholar] [CrossRef]
- El Mariachet, J.; Tan, S.; Basnet, M.; Ali, M.H. Deep Reinforcement Learning-Driven Mitigation of Adverse Effects of Cyber-Attacks on Electric Vehicle Charging Station. Energies 2023, 16, 7296. [Google Scholar] [CrossRef]
- Galkin, N.; Yang, C.W.; Vyatkin, V. Automatic Generation of Charging Point’s Digital Twin for Virtual Commissioning of Their Automation Systems. IEEE Open J. Ind. Electron. Soc. 2023, 4, 14–26. [Google Scholar] [CrossRef]
- Ali, M.; Kaddoum, G.; Li, W.T.; Yuen, C.; Tariq, M.; Poor, H.V. A Smart Digital Twin Enabled Security Framework for Vehicle-to-Grid Cyber-Physical Systems. IEEE Trans. Inf. Forensics Secur. 2023, 18, 5258–5271. [Google Scholar] [CrossRef]
- Yu, J.U.; Cho, K.S.; Park, S.W.; Son, S.Y. Digital Twin System Framework and Implementation for Grid-Integrated Electric Vehicles. Energies 2024, 17, 6249. [Google Scholar] [CrossRef]
- Suhail, S.; Malik, S.U.R.; Jurdak, R.; Hussain, R.; Matulevičius, R.; Svetinovic, D. Towards situational aware cyber-physical systems: A security-enhancing use case of blockchain-based digital twins. Comput. Ind. 2022, 141, 103699. [Google Scholar] [CrossRef]
- Mchirgui, N.; Quadar, N.; Kraiem, H.; Lakhssassi, A. The Applications and Challenges of Digital Twin Technology in Smart Grids: A Comprehensive Review. Appl. Sci. 2024, 14, 10933. [Google Scholar] [CrossRef]
- Qureshi, A.R.; Asensio, A.; Imran, M.; Garcia, J.; Masip-Bruin, X. A survey on security enhancing Digital Twins: Models, applications and tools. Comput. Commun. 2025, 238, 108158. [Google Scholar] [CrossRef]
- Afaqui, M.S.; Gangopadhyay, A.; El-Hajj, M. Leveraging Digital Twins and Intrusion Detection Systems for Enhanced Security in IoT-Based Smart City Infrastructures. Electronics 2024, 13, 3941. [Google Scholar] [CrossRef]
- Santos, J.B.; Francisco, A.M.B.; Cabrita, C.; Monteiro, J.; Pacheco, A.; Cardoso, P.J.S. Development and Implementation of a Smart Charging System for Electric Vehicles Based on the ISO 15118 Standard. Energies 2024, 17, 3045. [Google Scholar] [CrossRef]
- Raghav, R.H.; Veshnu, G.; Kumar, S.D.; Pillai, A.S. Establishing communication between EV-EVSE-CSMS based on IEC61851-1 and OCPP 2.0.1 Standard. In Proceedings of the 2023 14th International Conference on Computing Communication and Networking Technologies, ICCCNT 2023, Delhi, India, 6–8 July 2023. [Google Scholar] [CrossRef]
- Mun, H.; Han, K.; Damiani, E.; Yeun, H.K.; Kim, T.-Y.; Martino, L.; Yeun, C.Y. A Comprehensive Survey on Digital Twin: Focusing on Security Threats and Requirements. IEEE Access 2025, 13, 73362–73390. [Google Scholar] [CrossRef]
- Attaran, M.; Celik, B.G. Digital Twin: Benefits, use cases, challenges, and opportunities. Decis. Anal. J. 2023, 6, 100165. [Google Scholar] [CrossRef]
- Kumar, P.; Channi, H.K.; Kumar, R.; Rajiv, A.; Kumari, B.; Singh, G.; Singh, S.; Dyab, I.F.; Lozanović, J. A comprehensive review of vehicle-to-grid integration in electric vehicles: Powering the future. Energy Convers. Manag. X 2025, 25, 100864. [Google Scholar] [CrossRef]
- Waseem, M.; Ahmad, M.; Parveen, A.; Suhaib, M. Battery technologies and functionality of battery management system for EVs: Current status, key challenges, and future prospectives. J. Power Sources 2023, 580, 233349. [Google Scholar] [CrossRef]
- Design Flaws and Security Considerations for Telematics and Infotainment Systems—IEEE Cybersecurity. Available online: https://cybersecurity.ieee.org/blog/2017/05/30/design-flaws-and-security-considerations-for-telematics-and-infotainment-systems/ (accessed on 19 May 2025).
- Paul, B.; Sarker, A.; Abhi, S.H.; Das, S.K.; Ali, M.F.; Islam, M.M.; Islam, M.R.; Moyeen, S.I.; Badal, M.F.R.; Ahamed, M.H. Potential smart grid vulnerabilities to cyber attacks: Current threats and existing mitigation strategies. Heliyon 2024, 10, e37980. [Google Scholar] [CrossRef]
- Munusamy, N.; Vairavasundaram, I. AI and Machine Learning in V2G technology: A review of bi-directional converters, charging systems, and control strategies for smart grid integration. e-Prime—Adv. Electr. Eng. Electron. Energy 2024, 10, 100856. [Google Scholar] [CrossRef]
- Silva, E.; Freitas, T.; Yasmin, R.; Shoker, A.; Esteves-Verissimo, P. EVOLVE: A Value-Added Services Platform for Electric Vehicle Charging Stations. 2025. Available online: https://arxiv.org/pdf/2503.18687v1 (accessed on 19 May 2025).
- Kilic, A. Secure and convenience charging communication between electric vehicle and charging station with plug and charge. Electr. Power Syst. Res. 2025, 241, 111371. [Google Scholar] [CrossRef]
- Johnson, J.; Berg, T.; Anderson, B.; Wright, B. Review of Electric Vehicle Charger Cybersecurity Vulnerabilities, Potential Impacts, and Defenses. Energies 2022, 15, 3931. [Google Scholar] [CrossRef]
- Ravindran, M.A.; Nallathambi, K.; Vishnuram, P.; Rathore, R.S.; Bajaj, M.; Rida, I.; Alkhayyat, A. A Novel Technological Review on Fast Charging Infrastructure for Electrical Vehicles: Challenges, Solutions, and Future Research Directions. Alex. Eng. J. 2023, 82, 260–290. [Google Scholar] [CrossRef]
- Chowdhury, A.; Shafin, S.S.; Masum, S.; Kamruzzaman, J.; Dong, S. Secure Electric Vehicle Charging Infrastructure in Smart Cities: A Blockchain-Based Smart Contract Approach. Smart Cities 2025, 8, 33. [Google Scholar] [CrossRef]
- Masood, A.; Lakew, D.S.; Cho, S. Security and Privacy Challenges in Connected Vehicular Cloud Computing. IEEE Commun. Surv. Tutor. 2020, 22, 2725–2764. [Google Scholar] [CrossRef]
- Sadaf, M.; Iqbal, Z.; Javed, A.R.; Saba, I.; Krichen, M.; Majeed, S.; Raza, A. Connected and Automated Vehicles: Infrastructure, Applications, Security, Critical Challenges, and Future Aspects. Technologies 2023, 11, 117. [Google Scholar] [CrossRef]
- Joseph, A.; Balachandra, P. Smart Grid to Energy Internet: A Systematic Review of Transitioning Electricity Systems. IEEE Access 2020, 8, 215787–215805. [Google Scholar] [CrossRef]
- Basnet, M.; Ali, M.H. Exploring cybersecurity issues in 5G enabled electric vehicle charging station with deep learning. IET Gener. Transm. Distrib. 2021, 15, 3435–3449. [Google Scholar] [CrossRef]
- Siddiky, M.N.A.; Rahman, M.E.; Uzzal, M.S.; Kabir, H.M.D. A Comprehensive Exploration of 6G Wireless Communication Technologies. Computers 2025, 14, 15. [Google Scholar] [CrossRef]
- Jahandar, S.; Shayea, I.; Gures, E.; El-Saleh, A.A.; Ergen, M.; Alnakhli, M. Handover decision with multi-access edge computing in 6G networks: A survey. Results Eng. 2025, 25, 103934. [Google Scholar] [CrossRef]
- Acharya, S.; Dvorkin, Y.; Pandzic, H.; Karri, R. Cybersecurity of Smart Electric Vehicle Charging: A Power Grid Perspective. IEEE Access 2020, 8, 214434–214453. [Google Scholar] [CrossRef]
- Hank, P.; Vermesan, O.; Müller, S.; Van Den Keybus, J. Automotive ethernet: In-vehicle networking and smart mobility. In Proceedings of the Design, Automation and Test in Europe, DATE, Grenoble, France, 18–22 March 2013; pp. 1735–1739. [Google Scholar] [CrossRef]
- Seoane, V.; Garcia-Rubio, C.; Almenares, F.; Campo, C. Performance evaluation of CoAP and MQTT with security support for IoT environments. Comput. Netw. 2021, 197, 108338. [Google Scholar] [CrossRef]
- Arbab-Zavar, B.; Palacios-Garcia, E.J.; Vasquez, J.C.; Guerrero, J.M. Message Queuing Telemetry Transport Communication Infrastructure for Grid-Connected AC Microgrids Management. Energies 2021, 14, 5610. [Google Scholar] [CrossRef]
- Cullen, G.; Kirchner, S.R. OCPP Interoperability: A Unified Future of Charging. World Electr. Veh. J. 2024, 15, 191. [Google Scholar] [CrossRef]
- Garofalaki, Z.; Kosmanos, D.; Moschoyiannis, S.; Kallergis, D.; Douligeris, C. Electric Vehicle Charging: A Survey on the Security Issues and Challenges of the Open Charge Point Protocol (OCPP). IEEE Commun. Surv. Tutor. 2022, 24, 1504–1533. [Google Scholar] [CrossRef]
- Nguyen, L.-H.; Nguyen, V.-L.; Hwang, R.-H.; Kuo, J.-J.; Chen, Y.-W.; Huang, C.-C.; Pan, P.-I. Towards Secured Smart Grid 2.0: Exploring Security Threats, Protection Models, and Challenges. IEEE Commun. Surv. Tutor. 2024, 27, 2581–2620. [Google Scholar] [CrossRef]
- Hossain, M.S.; Rodine, C.; Tsiropoulou, E.E. A Blockchain and PKI-Based Secure Vehicle-to-Vehicle Energy-Trading Protocol. Energies 2024, 17, 4245. [Google Scholar] [CrossRef]
- Venkatesan, M.; Narayanamoorthi, R.; Kacor, P.; Vrzala, M. Bidirectional wireless power transfer: Bridging electric vehicles and the grid through converter analysis, coil topologies, and communication protocol review. Results Eng. 2025, 25, 103803. [Google Scholar] [CrossRef]
- Neaimeh, M.; Andersen, P.B. Mind the gap- open communication protocols for vehicle grid integration. Energy Inform. 2020, 3, 1. [Google Scholar] [CrossRef]
- Skarga-Bandurova, I.; Kotsiuba, I.; Biloborodova, T. Cyber Security of Electric Vehicle Charging Infrastructure: Open Issues and Recommendations. In Proceedings of the 2022 IEEE International Conference on Big Data, Big Data 2022, Osaka, Japan, 17–20 December 2022; pp. 3099–3106. [Google Scholar] [CrossRef]
- Vailoces, G.; Keith, A.; Almehmadi, A.; El-Khatib, K. Securing the electric vehicle charging infrastructure: An in-depth analysis of vulnerabilities and countermeasures. In Proceedings of the DIVANet 2023—Proceedings of the International ACM Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications, Montreal, QC, Canada, 30 October–3 November 2023; pp. 31–38. [Google Scholar] [CrossRef]
- Kim, Y.; Hakak, S.; Ghorbani, A. Detecting Distributed Denial-of-Service (DDoS) attacks that generate false authentications on Electric Vehicle (EV) charging infrastructure. Comput. Secur. 2024, 144, 103989. [Google Scholar] [CrossRef]
- Wu, X.; Li, G.; Zhou, J. A Lightweight Secure Management Scheme for Energy Harvesting Dynamic Wireless Charging System. IEEE Access 2020, 8, 224729–224740. [Google Scholar] [CrossRef]
- Irshad, A.; Usman, M.; Chaudhry, S.A.; Naqvi, H.; Shafiq, M. A Provably Secure and Efficient Authenticated Key Agreement Scheme for Energy Internet-Based Vehicle-to-Grid Technology Framework. IEEE Trans. Ind. Appl. 2020, 56, 4425–4435. [Google Scholar] [CrossRef]
- Bansal, G.; Naren, N.; Chamola, V.; Sikdar, B.; Kumar, N.; Guizani, M. Lightweight Mutual Authentication Protocol for V2G Using Physical Unclonable Function. IEEE Trans. Veh. Technol. 2020, 69, 7234–7246. [Google Scholar] [CrossRef]
- Baza, M.; Amer, R.; Rasheed, A.; Srivastava, G.; Mahmoud, M.; Alasmary, W. A blockchain-based energy trading scheme for electric vehicles. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications and Networking Conference, CCNC 2021, Las Vegas, NV, USA, 9–12 January 2021. [Google Scholar] [CrossRef]
- Hataba, M.; Sherif, A.; Elsersy, M.; Nabil, M.; Mahmoud, M.; Almotairi, K.H. Privacy-Preserving Biometric-based Authentication Scheme for Electric Vehicles Charging System. In Proceedings of the 2021 3rd IEEE Middle East and North Africa COMMunications Conference, MENACOMM 2021, Agadir, Morocco, 3–5 December 2021; pp. 86–91. [Google Scholar] [CrossRef]
- Babu, P.R.; Amin, R.; Reddy, A.G.; Das, A.K.; Susilo, W.; Park, Y.H. Robust Authentication Protocol for Dynamic Charging System of Electric Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 11338–11351. [Google Scholar] [CrossRef]
- Roman, L.F.A.; de Lira Gondim, P. Authentication protocol built from a chaotic cryptosystem for a fog and cloud-based CWD-WPT charging station. In Proceedings of the 2021 International Wireless Communications and Mobile Computing, IWCMC 2021, Harbin City, China, 28 June–2 July 2021; pp. 370–375. [Google Scholar] [CrossRef]
- Parameswarath, R.P.; Abhishek, N.V.; Sikdar, B. PREVENT: A Mechanism for Preventing Message Tampering Attacks in Electric Vehicle Networks. In Proceedings of the IEEE Vehicular Technology Conference, Florence, Italy, 20–23 June 2023; Volume 2023. [Google Scholar] [CrossRef]
- Basnet, M.; Ali, M.H. Deep learning-based intrusion detection system for electric vehicle charging station. In Proceedings of the 2020 2nd International Conference on Smart Power and Internet Energy Systems, SPIES 2020, Bangkok, Thailand, 15–18 September 2020; pp. 408–413. [Google Scholar] [CrossRef]
- ElKashlan, M.; Aslan, H.; Elsayed, M.S.; Jurcut, A.D.; Azer, M.A. Intrusion Detection for Electric Vehicle Charging Systems (EVCS). Algorithms 2023, 16, 75. [Google Scholar] [CrossRef]
- Anli, Y.A.; Ciplak, Z.; Sakaliuzun, M.; Izgu, S.Z.; Yildiz, K. DDoS detection in electric vehicle charging stations: A deep learning perspective via CICEV2023 dataset. Internet Things 2024, 28, 101343. [Google Scholar] [CrossRef]
- Warraich, Z.S.; Morsi, W.G. Early detection of cyber–physical attacks on fast charging stations using machine learning considering vehicle-to-grid operation in microgrids. Sustain. Energy Grids Netw. 2023, 34, 101027. [Google Scholar] [CrossRef]
- Sarieddine, K.; Sayed, M.A.; Torabi, S.; Atallah, R.; Assi, C. Edge-based detection and localization of adversarial oscillatory load attacks orchestrated by compromised EV charging stations. Int. J. Electr. Power Energy Syst. 2024, 156, 109735. [Google Scholar] [CrossRef]
- Almadhor, A.; Alsubai, S.; Bouazzi, I.; Karovič, V.; Davidekova, M.; Al Hejaili, A.; Sampedro, G. Transfer learning for securing electric vehicle charging infrastructure from cyber-physical attacks. Sci. Rep. 2025, 15, 9331. [Google Scholar] [CrossRef]
- Buedi, E.D.; Ghorbani, A.A.; Dadkhah, S.; Ferreira, R.L. Enhancing EV Charging Station Security Using a Multi-dimensional Dataset: CICEVSE2024. In Data and Applications Security and Privacy XXXVIII.; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2024; Volume 14901, pp. 171–190. [Google Scholar] [CrossRef]
- Khan, O.G.M.; Elghitani, F.; Youssef, A.; Salama, M.; El-Saadany, E.F. Real-Time Congestion-Aware Charging Station Assignment Model for EVs. IEEE Internet Things J. 2024, 11, 11723–11736. [Google Scholar] [CrossRef]
- Sheikh, A.; Kamuni, V.; Urooj, A.; Wagh, S.; Singh, N.; Patel, D. Secured Energy Trading Using Byzantine-Based Blockchain Consensus. IEEE Access 2020, 8, 8554–8571. [Google Scholar] [CrossRef]
- Khalid, R.; Malik, M.W.; Alghamdi, T.A.; Javaid, N. A consortium blockchain based energy trading scheme for Electric Vehicles in smart cities. J. Inf. Secur. Appl. 2021, 63, 102998. [Google Scholar] [CrossRef]
- Xu, C.; Wu, H.; Liu, H.; Li, X.; Liu, L.; Wang, P. An Intelligent Scheduling Access Privacy Protection Model of Electric Vehicle Based on 5G-V2X. Sci. Program. 2021, 2021, 1198794. [Google Scholar] [CrossRef]
- Kabir, M.E.; Ghafouri, M.; Moussa, B.; Assi, C. A Two-Stage Protection Method for Detection and Mitigation of Coordinated EVSE Switching Attacks. IEEE Trans. Smart Grid 2021, 12, 4377–4388. [Google Scholar] [CrossRef]
- Liu, W.; Li, L.; Li, X. Power System Forced Oscillation Caused by Malicious Mode Attack via Coordinated Charging. In Proceedings of the I and CPS Asia 2022–2022 IEEE IAS Industrial and Commercial Power System Asia, Shanghai, China, 8–11 July 2022; pp. 1838–1844. [Google Scholar] [CrossRef]
- Zhou, Y.; Xu, H.; Liu, W.; Li, Y. Malicious mode attack on electric vehicle coordinated charging and its defense strategy. Sustain. Energy Grids Netw. 2024, 39, 101440. [Google Scholar] [CrossRef]
- Gupta, K.; Panigrahi, B.K.; Joshi, A.; Paul, K. Demonstration of denial of charging attack on electric vehicle charging infrastructure and its consequences. Int. J. Crit. Infrastruct. Prot. 2024, 46, 100693. [Google Scholar] [CrossRef]
- Jeong, S.I.; Choi, D.H. Electric Vehicle User Data-Induced Cyber Attack on Electric Vehicle Charging Station. IEEE Access 2022, 10, 55856–55867. [Google Scholar] [CrossRef]
- Gandhi, K.; Morsi, W.G. Impact of the Open Charge Point Protocol Between the Electric Vehicle and the Fast Charging Station on the Cybersecurity of the Smart Grid. In Proceedings of the Canadian Conference on Electrical and Computer Engineering, Halifax, NS, Canada, 18–20 September 2022; Volume 2022, pp. 235–240. [Google Scholar] [CrossRef]
- Mu, H.; Pang, A.; Jiang, C.; Yang, W.; Zhao, Q. Defense against false data injection attacks on the electric vehicle charging stations data markets. Eng. Appl. Artif. Intell. 2025, 154, 110983. [Google Scholar] [CrossRef]
- Elhussini, H.; Assi, C.; Ghrayeb, A.; Atallah, R. A Tale of Two Entities. ACM Trans. Internet Things 2021, 2, 8. [Google Scholar] [CrossRef]
- Sayed, M.A.; Atallah, R.; Assi, C.; Debbabi, M. Electric vehicle attack impact on power grid operation. Int. J. Electr. Power Energy Syst. 2022, 137, 107784. [Google Scholar] [CrossRef]
- Pourmirza, Z.; Walker, S. Electric Vehicle Charging Station: Cyber Security Challenges and Perspective. In Proceedings of the 2021 9th IEEE International Conference on Smart Energy Grid Engineering, SEGE 2021, Oshawa, ON, Canada, 11–13 August 2021; pp. 111–116. [Google Scholar] [CrossRef]
- Nasr, T.; Torabi, S.; Bou-Harb, E.; Fachkha, C.; Assi, C. Power jacking your station: In-depth security analysis of electric vehicle charging station management systems. Comput. Secur. 2022, 112, 102511. [Google Scholar] [CrossRef]
- Ahalawat, A.; Adepu, S.; Gardiner, J. Security Threats in Electric Vehicle Charging. In Proceedings of the 2022 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids, SmartGridComm 2022, Singapore, 25–28 October 2022; pp. 399–404. [Google Scholar] [CrossRef]
- Shirvani, S.; Baseri, Y.; Ghorbani, A. Evaluation Framework for Electric Vehicle Security Risk Assessment. IEEE Trans. Intell. Transp. Syst. 2024, 25, 33–56. [Google Scholar] [CrossRef]
- Kilichev, D.; Turimov, D.; Kim, W. Next–Generation Intrusion Detection for IoT EVCS: Integrating CNN, LSTM, and GRU Models. Mathematics 2024, 12, 571. [Google Scholar] [CrossRef]
- Monikandan, A.S.; Chellaswamy, C.; Geetha, T.S.; Sivaraju, S.S. Optimized Convolutional Neural Network-Based Capacity Expansion Framework for Electric Vehicle Charging Station. Int. Trans. Electr. Energy Syst. 2022, 2022, 2915910. [Google Scholar] [CrossRef]
- Shafee, A.A.; Mahmoud, M.M.E.A.; Srivastava, G.; Fouda, M.M.; Alsabaan, M.; Ibrahem, M.I. Detection of Distributed Denial of Charge (DDoC) Attacks Using Deep Neural Networks with Vector Embedding. IEEE Access 2023, 11, 75381–75397. [Google Scholar] [CrossRef]
- Adcock, B.; Brugiapaglia, S.; Dexter, N.; Moraga, S. Deep Neural Networks Are Effective At Learning High-Dimensional Hilbert-Valued Functions From Limited Data. Proc. Mach. Learn. Res. 2020, 145, 1–36. Available online: https://arxiv.org/pdf/2012.06081 (accessed on 3 August 2025).
- Sakhnini, J.; Khan, M.A.; Aljarf, A.; Alshammari, S.; Alghamdi, A.; Alshehri, M.; Alhaidari, F. A Generalizable Deep Neural Network Method for Detecting Attacks in Industrial Cyber-Physical Systems. IEEE Syst. J. 2023, 17, 5152–5160. [Google Scholar] [CrossRef]
- Sommer, C.; Hossain, M.J. Artificial Intelligence-driven optimization of V2G and charging point selection en-route: A systematic literature review. Energy Convers. Manag. X 2025, 26, 100978. [Google Scholar] [CrossRef]
- Talukder, M.A.; Islam, M.M.; Uddin, M.A.; Farhana, K.F.H.; Sultana, S.; Al Amin, S.A.; Moni, M.A. Machine learning-based network intrusion detection for big and imbalanced data using oversampling, stacking feature embedding and feature extraction. J. Big Data 2024, 11, 33. [Google Scholar] [CrossRef]
- Benfarhat, I.; Goh, V.; Siow, C.; Lee, I.; Sheraz, M.; Ngu, E.; Chuah, T. Advanced Temporal Convolutional Network Framework for Intrusion Detection in Electric Vehicle Charging Stations. IEEE Open J. Veh. Technol. 2025, 6, 1033–1050. [Google Scholar] [CrossRef]
- Zheng, J.; Zhu, J.; Xi, H. Short-term energy consumption prediction of electric vehicle charging station using attentional feature engineering and multi-sequence stacked Gated Recurrent Unit. Comput. Electr. Eng. 2023, 108, 108694. [Google Scholar] [CrossRef]
- Hussain, A.; Yadav, A.; Ravikumar, G. Anomaly Detection Using Bi-Directional Long Short-Term Memory Networks for Cyber-Physical Electric Vehicle Charging Stations. IEEE Trans. Ind. Cyber-Phys. Syst. 2024, 2, 508–518. [Google Scholar] [CrossRef]
- Muhuri, P.S.; Chatterjee, P.; Yuan, X.; Roy, K.; Esterline, A. Using a Long Short-Term Memory Recurrent Neural Network (LSTM-RNN) to Classify Network Attacks. Information 2020, 11, 243. [Google Scholar] [CrossRef]
- Motlagh, S.G.; Oladigbolu, J.; Li, L. A review on electric vehicle charging station operation considering market dynamics and grid interaction. Appl. Energy 2025, 392, 126058. [Google Scholar] [CrossRef]
- Hwang, I.C.; Kang, H.S. Anomaly Detection Based on a 3D Convolutional Neural Network Combining Convolutional Block Attention Module Using Merged Frames. Sensors 2023, 23, 9616. [Google Scholar] [CrossRef]
- Tian, J.; Liu, H.; Gan, W.; Zhou, Y.; Wang, N.; Ma, S. Short-term electric vehicle charging load forecasting based on TCN-LSTM network with comprehensive similar day identification. Appl. Energy 2025, 381, 125174. [Google Scholar] [CrossRef]
- Lim, W.; Yong, K.S.C.; Lau, B.T.; Tan, C.C.L. Future of generative adversarial networks (GAN) for anomaly detection in network security: A review. Comput. Secur. 2024, 139, 103733. [Google Scholar] [CrossRef]
- Zhang, T.; Peng, Q.; Zeng, S. Predicting EV Charging Demand in Renewable-Energy-Powered Grids Using Explainable Machine Learning. Sustainability 2025, 17, 4158. [Google Scholar] [CrossRef]
- Salehpour, M.J.; Hossain, M.J. Leveraging machine learning for efficient EV integration as mobile battery energy storage systems: Exploring strategic frameworks and incentives. J. Energy Storage 2024, 92, 112151. [Google Scholar] [CrossRef]
- Fatemeh, D.; Li, Y.; Firouz, B.A.; Abdallah, S. On TinyML and Cybersecurity: Electric Vehicle Charging Infrastructure Use Case. IEEE Access 2024, 12, 108703–108730. [Google Scholar] [CrossRef]
- Choi, K.; Yi, J.; Park, C.; Yoon, S. Deep Learning for Anomaly Detection in Time-Series Data: Review, Analysis, and Guidelines. IEEE Access 2021, 9, 120043–120065. [Google Scholar] [CrossRef]
- Duraj, A.; Szczepaniak, P.S.; Sadok, A. Detection of Anomalies in Data Streams Using the LSTM-CNN Model. Sensors 2025, 25, 1610. [Google Scholar] [CrossRef]
- Ao, S.I.; Fayek, H. Continual Deep Learning for Time Series Modeling. Sensors 2023, 23, 7167. [Google Scholar] [CrossRef] [PubMed]
- Tightiz, L.; Dang, L.M.; Yoo, J.; Padmanaban, S. A comprehensive review on AIoT applications for intelligent EV charging/discharging ecosystem. Energy Convers. Manag. X 2025, 27, 101088. [Google Scholar] [CrossRef]
- Benfarhat, I.; Goh, V.T.; Siow, C.L.; Sheraz, M.; Chuah, T.C. Temporal Convolutional Network Approach to Secure Open Charge Point Protocol (OCPP) in Electric Vehicle Charging. IEEE Access 2025, 13, 15272–15289. [Google Scholar] [CrossRef]
- Al-E’mari, S.; Sanjalawe, Y.; Allehyani, B.; Kurdi, G.; Makhadmeh, S.; Jaradat, A.; Hijazi, D. Forensic Analysis of Cyberattacks in Electric Vehicle Charging Systems Using Host-Level Data. Comput. Mater. Contin. 2025, 85, 3289–3320. [Google Scholar] [CrossRef]
- Mitikiri, S.B.; Srinivas, V.L.; Pal, M. Anomaly detection of adversarial cyber attacks on electric vehicle charging stations. e-Prime—Adv. Electr. Eng. Electron. Energy 2025, 11, 100911. [Google Scholar] [CrossRef]
- Aziz, A.; Schelén, O.; Bodin, U. Digital Twin as a Proxy for Industrial Cyber-Physical Systems. In Proceedings of the 2023 10th International Conference on Wireless Communication and Sensor Networks, Chengdu, China, 6–8 January 2023; pp. 85–92. [Google Scholar] [CrossRef]
- Abdelrahman, M.; Macatulad, E.; Lei, B.; Quintana, M.; Miller, C.; Biljecki, F. What is a Digital Twin anyway? Deriving the definition for the built environment from over 15,000 scientific publications. Build. Environ. 2025, 274, 112748. [Google Scholar] [CrossRef]
- Chen, H.; Shao, H.; Deng, X.; Wang, L.; Wang, X. Comprehensive Survey of the Landscape of Digital Twin Technologies and Their Diverse Applications. CMES—Comput. Model. Eng. Sci. 2023, 138, 125–165. [Google Scholar] [CrossRef]
- Das, O.; Zafar, M.H.; Sanfilippo, F.; Rudra, S.; Kolhe, M.L. Advancements in digital twin technology and machine learning for energy systems: A comprehensive review of applications in smart grids, renewable energy, and electric vehicle optimization. Energy Convers. Manag. X 2024, 24, 100715. [Google Scholar] [CrossRef]
- Alhumam, N.; Rahman, M.M.H.; Aljughaiman, A. A Comprehensive Review on Cybersecurity of Digital Twins Issues, Challenges, and Future Research Directions. IEEE Access 2025, 13, 45106–45124. [Google Scholar] [CrossRef]
- Purohit, S.; Govindarasu, M. FL-EVCS: Federated Learning based Anomaly Detection for EV Charging Ecosystem. In Proceedings of the International Conference on Computer Communications and Networks, ICCCN, Kailua-Kona, HI, USA, 29–31 July 2024. [Google Scholar] [CrossRef]
- Ibrahim, M.; Rjabtšikov, V.; Gilbert, R. Overview of Digital Twin Platforms for EV Applications. Sensors 2023, 23, 1414. [Google Scholar] [CrossRef] [PubMed]
- Dihan, M.S.; Akash, A.I.; Tasneem, Z.; Das, P.; Das, S.K.; Islam, M.R.; Islam, M.M.; Badal, F.R.; Ali, M.F.; Ahamed, M.H.; et al. Digital twin: Data exploration, architecture, implementation and future. Heliyon 2024, 10, e26503. [Google Scholar] [CrossRef] [PubMed]
- Bolat-Akça, B.; Bozkaya-Aras, E. Digital twin-assisted intelligent anomaly detection system for Internet of Things. Ad Hoc Netw. 2024, 158, 103484. [Google Scholar] [CrossRef]
- Homaei, M.; Mogollón-Gutiérrez, Ó.; Sancho, J.C.; Ávila, M.; Caro, A. A review of digital twins and their application in cybersecurity based on artificial intelligence. Artif. Intell. Rev. 2024, 57, 201. [Google Scholar] [CrossRef]
- Holmes, D.; Papathanasaki, M.; Maglaras, L.; Ferrag, M.A.; Nepal, S.; Janicke, H. Digital Twins and Cyber Security—Solution or challenge? In Proceedings of the 6th South-East Europe Design Automation, Computer Engineering, Computer Networks and Social Media Conference, SEEDA-CECNSM 2021, Preveza, Greece, 24–26 September 2021. [Google Scholar] [CrossRef]
- Allison, D.; Smith, P.; McLaughlin, K. Digital Twin-Enhanced Incident Response for Cyber-Physical Systems. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023. [Google Scholar] [CrossRef]
- Yalavarthy, U.R.S.; Kumar, N.B.; Babu, A.R.V.; Narasipuram, R.P.; Padmanaban, S. Digital twin technology in electric and self-navigating vehicles: Readiness, convergence, and future directions. Energy Convers. Manag. X 2025, 26, 100949. [Google Scholar] [CrossRef]
- Sai, A.M.V.V.; Wang, C.; Cai, Z.; Li, Y. Navigating the Digital Twin Network landscape: A survey on architecture, applications, privacy and security. High-Confid. Comput. 2024, 4, 100269. [Google Scholar] [CrossRef]
- Chen, S.; Bekar, E.T.; Bokrantz, J.; Skoogh, A. AI-enhanced digital twins in maintenance: Systematic review, industrial challenges, and bridging research–practice gaps. J. Manuf. Syst. 2025, 82, 678–699. [Google Scholar] [CrossRef]
- Itäpelto, T.; Elhajj, M.; van Sinderen, M. Digital twin application in lifecycle security of critical infrastructures: A systematic literature review. Int. J. Crit. Infrastruct. Prot. 2025, 50, 100783. [Google Scholar] [CrossRef]
- Wang, Q.; Li, Y.; Li, R. Integrating artificial intelligence in energy transition: A comprehensive review. Energy Strategy Rev. 2025, 57, 101600. [Google Scholar] [CrossRef]
- Costa, M.; Del Papa, G.; Costa, M.; Del Papa, G. Digital Twins for Intelligent Vehicle-to-Grid Systems: A Multi-Physics EV Model for AI-Based Energy Management. Appl. Sci. 2025, 15, 8214. [Google Scholar] [CrossRef]
- Allende, M.; López León, D.L.; Cerón, S.; Pareja, A.; Pacheco, E.; Leal, A.; Da Silva, M.; Pardo, A.; Jones, D.; Worrall, D.J. Quantum-resistance in blockchain networks. Sci. Rep. 2023, 13, 5664. [Google Scholar] [CrossRef] [PubMed]
- Deng, R.; Xiao, G.; Lu, R.; Liang, H.; Vasilakos, A.V. False data injection on state estimation in power systems-attacks, impacts, and defense: A survey. IEEE Trans. Industr. Inform. 2017, 13, 411–423. [Google Scholar] [CrossRef]
- Psaltis, D.; Ntouros, K.; Lekidis, A.; Brotsis, S.; Kolokotronis, N. Evaluating 5G-enabled EV Charging Infrastructure’s Resilience Through Stealthy Cyber-Attacks. In Proceedings of the 2025 IEEE International Conference on Cyber Security and Resilience, CSR 2025, Chania, Greece, 4–6 August 2025; pp. 923–928. [Google Scholar] [CrossRef]
- Ali, W.A.; Fanti, M.P.; Roccotelli, M.; Ranieri, L. A Review of Digital Twin Technology for Electric and Autonomous Vehicles. Appl. Sci. 2023, 13, 5871. [Google Scholar] [CrossRef]
- Subran, A.K.; Sankaran, S.; Sutraye, P.; Nishad, A.K. Threat Modeling and Attack Simulation of Charging Infrastructures in Electric Vehicles. In Proceedings of the 2024 15th International Conference on Computing Communication and Networking Technologies, ICCCNT 2024, Kamand, India, 24–28 June 2024. [Google Scholar] [CrossRef]
- Awouda, A.; Traini, E.; Bruno, G.; Chiabert, P. IoT-Based Framework for Digital Twins in the Industry 5.0 Era. Sensors 2024, 24, 594. [Google Scholar] [CrossRef]
- Andriulo, F.C.; Fiore, M.; Mongiello, M.; Traversa, E.; Zizzo, V. Edge Computing and Cloud Computing for Internet of Things: A Review. Informatics 2024, 11, 71. [Google Scholar] [CrossRef]
- Zhang, C.; Joshi, H.P.; Riley, G.F.; Wright, S.A. Towards a virtual network function research agenda: A systematic literature review of VNF design considerations. J. Netw. Comput. Appl. 2019, 146, 102417. [Google Scholar] [CrossRef]
- Mahboubi, A.; Luong, K.; Aboutorab, H.; Bui, H.T.; Jarrad, G.; Bahutair, M.; Camtepe, S.; Pogrebna, G.; Ahmed, E.; Barry, B.; et al. Evolving techniques in cyber threat hunting: A systematic review. J. Netw. Comput. Appl. 2024, 232, 104004. [Google Scholar] [CrossRef]
- Wakili, A.; Bakkali, S.; Ibrahim, I.A. A digital twin-enhanced cybersecurity framework for IoT in healthcare: Applications in industry 4.0. Telemat. Inform. Rep. 2025, 20, 100254. [Google Scholar] [CrossRef]
- Rouhani, S.H.; Su, C.L. Future cyber-resilient renewable and sustainable smart grids: A critical review from power system researchers’ perspective on emerging threats and solutions. Renew. Sustain. Energy Rev. 2026, 226, 116299. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Noura, H.N.; Salman, O.; Chahine, K. Toward Secure Smart Grid Systems: Risks, Threats, Challenges, and Future Directions. Future Internet 2025, 17, 318. [Google Scholar] [CrossRef]
- Rojek, I.; Marciniak, T.; Mikołajewski, D.; Rojek, I.; Marciniak, T.; Mikołajewski, D. Digital Twins in 3D Printing Processes Using Artificial Intelligence. Electronics 2024, 13, 3550. [Google Scholar] [CrossRef]
- Praveenkumar, K.; Balasm, Z.; Bharathi, P.; Premalatha, B.; Ataev, S.; Priya, P. Digital Twins Driven by Artificial Intelligence to Mitigate, Detect, and Simulate Virtual Space Cyber Threats. In Proceedings of the 2025 International Conference on Computational Innovations and Engineering Sustainability, ICCIES 2025, Coimbatore, India, 24–26 April 2025. [Google Scholar] [CrossRef]
- Iwanowski, M.; Olszewski, D.; Graniszewski, W.; Krupski, J.; Pelc, F. The Choice of Training Data and the Generalizability of Machine Learning Models for Network Intrusion Detection Systems. Appl. Sci. 2025, 15, 8466. [Google Scholar] [CrossRef]
- Abbass, W.; Abbas, N.; Majeed, U.; Nawaz, W.; Abbas, Q.; Farooqi, A.H. A Cyber Resilient Framework for V2X Enabled Roundabouts in Intelligent Transportation Systems. IEEE Access 2025, 13, 154775–154802. [Google Scholar] [CrossRef]
- Mavikumbure, H.S.; Ali, M.H.; Aljohani, A.; Refaat, S.S.; Dmour, H.A.; Khan, M.A. Cy-Phy ADS: Cyber-Physical Anomaly Detection Framework for EV Charging Systems. IEEE Trans. Transp. Electrif. 2024, 10, 9904–9917. [Google Scholar] [CrossRef]
- Jayakrishna, N.; Prasanth, N. Detection of DDOS attacks in Vehicular Ad Hoc Networks using Ensemble Deep Learning Model and Optimization Technique. Results Eng. 2025, 27, 107022. [Google Scholar] [CrossRef]
- Chen, Y.; Lei, X.; Niu, S.; Jian, L. Trustworthy V2G scheduling and energy trading: A blockchain-based framework. eTransportation 2024, 22, 100376. [Google Scholar] [CrossRef]
- Mutahhar, A.; Khanzada, T.J.S.; Shahid, M.F.; Mutahhar, A.; Khanzada, T.J.S.; Shahid, M.F. Enhanced Scalability and Security in Blockchain-Based Transportation Systems for Mass Gatherings. Information 2025, 16, 641. [Google Scholar] [CrossRef]
- Tejada-Arango, D.A.; Kiviluoma, J.; Morales-España, G. Debunking the speed-fidelity trade-off: Speeding-up large-scale energy models while keeping fidelity. Int. J. Electr. Power Energy Syst. 2025, 168, 110674. [Google Scholar] [CrossRef]
- Govea, J.; Gutierrez, R.; Villegas-Ch, W. Use of granular computing for resource optimization in IoT networks. Front. Commun. Netw. 2025, 6, 1575120. [Google Scholar] [CrossRef]
- Almudayni, Z.; Soh, B.; Samra, H.; Li, A. Energy Inefficiency in IoT Networks: Causes, Impact, and a Strategic Framework for Sustainable Optimisation. Electronics 2025, 14, 159. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A.N. TON-IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Vidyalakshmi, G.; Gopikrishnan, S.; Boulila, W.; Koubaa, A.; Srivastava, G. Digital Twins and Cyber-Physical Systems: A New Frontier in Computer Modeling. CMES—Comput. Model. Eng. Sci. 2025, 143, 51–113. [Google Scholar] [CrossRef]
- Lalithadevi, B.; Krishnaveni, S. A Comprehensive Survey on Enhancing Digital Twin Security Systems with Explainable AI Techniques. In Proceedings of the 3rd International Conference on Intelligent Data Communication Technologies and Internet of Things, IDCIoT 2025, Bengaluru, India, 5–7 February 2025; pp. 535–542. [Google Scholar] [CrossRef]
- Li, X.; Niu, W.; Tian, H. Application of Digital Twin in Electric Vehicle Powertrain: A Review. World Electr. Veh. J. 2024, 15, 208. [Google Scholar] [CrossRef]
- Widl, E.; Cronbach, D.; Sorknæs, P.; Fitó, J.; Muschick, D.; Repetto, M.; Ramousse, J.; Ianakiev, A. Expert survey and classification of tools for modeling and simulating hybrid energy networks. Sustain. Energy Grids Netw. 2022, 32, 100913. [Google Scholar] [CrossRef]
- Plietzsch, A.; Kogler, R.; Auer, S.; Merino, J.; Gil-de Muro, A.; Liße, J.; Vogel, C.; Hellmann, F. PowerDynamics.jl—An experimentally validated open-source package for the dynamical analysis of power grids. SoftwareX 2022, 17, 100861. [Google Scholar] [CrossRef]
- Xie, J.; Wu, G.; Zhou, X.; Deng, S. Future perspectives on internet of vehicles resource management: Digital twin-enabled edge computing frameworks. J. Eng. Appl. Sci. 2025, 72, 119. [Google Scholar] [CrossRef]
- Balasubramanian, P.; Nazari, S.; Kholgh, D.K.; Mahmoodi, A.; Seby, J.; Kostakos, P. A cognitive platform for collecting cyber threat intelligence and real-time detection using cloud computing. Decis. Anal. J. 2025, 14, 100545. [Google Scholar] [CrossRef]
- Sadiq, M.; Islam, M.R.; Lipu, M.S.H.; Hannan, M.A.; Saad, M.H.M.; Islam, A.S.M.M.; Khan, M.S.H. Decentralized Model Predictive Control for Offshore Wind-Powered Seaport DC Microgrids With Electric Vehicle Stations. IEEE Trans. Ind. Appl. 2025, 61, 2258–2270. [Google Scholar] [CrossRef]
- Wulff, N.; Miorelli, F.; Gils, H.C.; Jochem, P. Vehicle Energy Consumption in Python (VencoPy): Presenting and Demonstrating an Open-Source Tool to Calculate Electric Vehicle Charging Flexibility. Energies 2021, 14, 4349. [Google Scholar] [CrossRef]
- Pricing and Licensing—MATLAB & Simulink. Available online: https://www.mathworks.com/pricing-licensing.html (accessed on 4 August 2025).
- Gurusamy, A.; Ashok, B.; Mason, B. Prediction of Electric Vehicle Driving Range and Performance Characteristics: A Review on Analytical Modeling Strategies With Its Influential Factors and Improvisation Techniques. IEEE Access 2023, 11, 131521–131548. [Google Scholar] [CrossRef]
- Berman, E.; Ginesin, J. The State of Julia for Scientific Machine Learning. 2024. Available online: https://arxiv.org/pdf/2410.10908v1 (accessed on 4 August 2025).
- Calvo-Bascones, P.; Voisin, A.; Do, P.; Sanz-Bobi, M.A. A collaborative network of digital twins for anomaly detection applications of complex systems. Snitch Digital Twin concept. Comput. Ind. 2023, 144, 103767. [Google Scholar] [CrossRef]
- Mahmud, K.; Town, G.E. A review of computer tools for modeling electric vehicle energy requirements and their impact on power distribution networks. Appl. Energy 2016, 172, 337–359. [Google Scholar] [CrossRef]
- Chrysostomou, D.; Torres, J.L.R.; Cremer, J.L. TensorConvolutionPlus: A python package for distribution system flexibility area estimation. SoftwareX 2025, 31, 102241. [Google Scholar] [CrossRef]
- Malekzadeh, M. Performance prediction and enhancement of 5G networks based on linear regression machine learning. EURASIP J. Wirel. Commun. Netw. 2023, 2023, 74. [Google Scholar] [CrossRef]
- Madhusudhanan, S.; Sivraj, P. Development of Communication Simulator for Electric Vehicle Charging following ISO 15118. In Proceedings of the 2022 IEEE North Karnataka Subsection Flagship International Conference, NKCon 2022, Vijaypur, India, 20–21 November 2022. [Google Scholar] [CrossRef]
- Jauhar, S.K.; Sethi, S.; Kamble, S.S.; Mathew, S.; Belhadi, A. Artificial intelligence and machine learning-based decision support system for forecasting electric vehicles’ power requirement. Technol. Forecast. Soc. Chang. 2024, 204, 123396. [Google Scholar] [CrossRef]
- Bongomin, O.; Mwape, M.C.; Mpofu, N.S.; Bahunde, B.K.; Kidega, R.; Mpungu, I.L.; Tumusiime, G.; Owino, C.; Goussongtogue, Y.M.; Yemane, A.; et al. Digital Twin technology advancing Industry 4.0 and Industry 5.0 across Sectors. Results Eng. 2025, 26, 105583. [Google Scholar] [CrossRef]
- Mendoza, M.A.T.; Soto, J.C.V.; Mauricio, J.M.; Maza, J.M.; Perez, M.A. Digital Twin Adaptive Remedial Action Scheme for Preventing Voltage Collapse. IEEE J. Emerg. Sel. Top. Ind. Electron. 2025, 6, 523–535. [Google Scholar] [CrossRef]
- Balta, E.C.; Pease, M.; Moyne, J.; Barton, K.; Tilbury, D.M. Digital Twin-Based Cyber-Attack Detection Framework for Cyber-Physical Manufacturing Systems. IEEE Trans. Autom. Sci. Eng. 2024, 21, 1695–1712. [Google Scholar] [CrossRef]
- Iyer, S.V.; Sangwan, K.S.; Dhiraj. Digital twin-based virtual commissioning for evaluation and validation of a reconfigurable process line. IET Collab. Intell. Manuf. 2024, 6, e12111. [Google Scholar] [CrossRef]
- Korotunov, S.; Tabunshchyk, G.; Arras, P. Utilization of a Digital Twin for an Electric Vehicles Smart Charging Station for Future Use with Engineering Students. In Artificial Intelligence and Online Engineering; Lecture Notes in Networks and Systems; Springer: Cham, Switzerland, 2023; Volume 524, pp. 233–240. [Google Scholar] [CrossRef]
- Yu, G.; Ye, X.; Xia, X.; Chen, Y.Q. Digital twin enabled transition towards the smart electric vehicle charging infrastructure: A review. Sustain. Cities Soc. 2024, 108, 105479. [Google Scholar] [CrossRef]
- Francisco, A.M.B.; Monteiro, J.; Cardoso, P.J.S. A Digital Twin of Charging Stations for Fleets of Electric Vehicles. IEEE Access 2023, 11, 125664–125683. [Google Scholar] [CrossRef]
- Li, G.; Luan, T.H.; Zheng, J.; Lai, C.; Zhang, K.; Yu, S. SECR: A Secure and Efficient Charging Reservation Scheme Based on Digital Twin in Vehicular Network. IEEE Internet Things J. 2024, 12, 10434–10452. [Google Scholar] [CrossRef]
- Kaleybar, H.J.; Brenna, M.; Castelli-Dezza, F.; Zaninelli, D. Sustainable MVDC Railway System Integrated with Renewable Energy Sources and EV Charging Station. In Proceedings of the 2022 IEEE Vehicle Power and Propulsion Conference, VPPC 2022, Merced, CA, USA, 1–4 November 2022. [Google Scholar] [CrossRef]
- Ahmed, M.; Pathan, A.S.K. False data injection attack (FDIA): An overview and new metrics for fair evaluation of its countermeasure. Complex Adapt. Syst. Model. 2020, 8, 4. [Google Scholar] [CrossRef]
- Tirulo, A.; Chauhan, S.; Shafie-khah, M. LLM-powered threat intelligence: Proactive detection of zero-day attacks in electric vehicle cyber-physical systems. Sustain. Energy Grids Netw. 2025, 43, 101877. [Google Scholar] [CrossRef]
- Rahman, M.M.; Chayan, M.M.H.; Mehrin, K.; Sultana, A.; Hamed, M.M. Explainable Deep Learning for Cyber Attack Detection in Electric Vehicle Charging Stations. In Proceedings of the 2024 11th International Conference on Networking, Systems and Security, NSysS 2024, Khulna Karak, Bangladesh, 19–21 December 2025; Volume 24, pp. 1–7. [Google Scholar] [CrossRef]
- Touré, A.; Imine, Y.; Semnont, A.; Delot, T.; Gallais, A. A framework for detecting zero-day exploits in network flows. Comput. Netw. 2024, 248, 110476. [Google Scholar] [CrossRef]
- Ma, S.; Flanigan, K.A.; Bergés, M. State-of-the-Art Review: The Use of Digital Twins to Support Artificial Intelligence-Guided Predictive Maintenance. 2024. Available online: https://www.researchgate.net/publication/390915833_Advancing_Cybersecurity_with_Digital_Twin_Technology (accessed on 4 August 2025).
- Pooyandeh, M.; Liu, H.; Sohn, I. Cybersecurity in Digital Twins of Electric Vehicle’s LIBs: Unveiling a Robust TTB-GA Attack. IEEE Trans. Intell. Transp. Syst. 2025, 26, 5360–5381. [Google Scholar] [CrossRef]
- Salim, M.M.; Camacho, D.; Park, J.H. Digital Twin and federated learning enabled cyberthreat detection system for IoT networks. Future Gener. Comput. Syst. 2024, 161, 701–713. [Google Scholar] [CrossRef]
- Tran-Dang, H.; Kim, D.S. Digital Twin-empowered intelligent computation offloading for edge computing in the era of 5G and beyond: A state-of-the-art survey. ICT Express 2025, 11, 167–180. [Google Scholar] [CrossRef]
- Dogra, A.; Jha, R.K.; Jain, S. A Survey on beyond 5G Network with the Advent of 6G: Architecture and Emerging Technologies. IEEE Access 2021, 9, 67512–67547. [Google Scholar] [CrossRef]
- Bellavista, P.; Bicocchi, N.; Fogli, M.; Giannelli, C.; Mamei, M.; Picone, M. Exploiting microservices and serverless for Digital Twins in the cloud-to-edge continuum. Future Gener. Comput. Syst. 2024, 157, 275–287. [Google Scholar] [CrossRef]
- Grieves, M.; Vickers, J. Digital twin: Mitigating unpredictable, undesirable emergent behavior in complex systems. In Transdisciplinary Perspectives on Complex Systems: New Findings and Approaches; Springer: Cham, Switzerland, 2016; pp. 85–113. [Google Scholar] [CrossRef]
- Lu, Y.; Liu, C.; Wang, K.I.K.; Huang, H.; Xu, X. Digital Twin-driven smart manufacturing: Connotation, reference model, applications and research issues. Robot. Comput. Integr. Manuf. 2020, 61, 101837. [Google Scholar] [CrossRef]
- Rasheed, A.; San, O.; Kvamsdal, T. Digital twin: Values, challenges and enablers from a modeling perspective. IEEE Access 2020, 8, 21980–22012. [Google Scholar] [CrossRef]
- Jetson Modules, Support, Ecosystem, and Lineup|NVIDIA Developer. Available online: https://developer.nvidia.com/embedded/jetson-modules (accessed on 4 August 2025).
- Jafari, M.; Kavousi-Fard, A.; Chen, T.; Karimi, M. A Review on Digital Twin Technology in Smart Grid, Transportation System and Smart City: Challenges and Future. IEEE Access 2023, 11, 17471–17484. [Google Scholar] [CrossRef]
- Onile, A.E.; Petlenkov, E.; Levron, Y.; Belikov, J. Smartgrid-based hybrid digital twins framework for demand side recommendation service provision in distributed power systems. Future Gener. Comput. Syst. 2024, 156, 142–156. [Google Scholar] [CrossRef]
- Al-Shetwi, A.Q.; Atawi, I.E.; El-Hameed, M.A.; Abuelrub, A. Digital Twin Technology for Renewable Energy, Smart Grids, Energy Storage and Vehicle-to-Grid Integration: Advancements, Applications, Key Players, Challenges and Future Perspectives in Modernising Sustainable Grids. IET Smart Grid 2025, 8, e70026. [Google Scholar] [CrossRef]
- Qi, Q.; Tao, F. Digital Twin and Big Data Towards Smart Manufacturing and Industry 4.0: 360 Degree Comparison. IEEE Access 2018, 6, 3585–3593. [Google Scholar] [CrossRef]
- Popławski, T.; Dudzik, S.; Szeląg, P. Forecasting of Energy Balance in Prosumer Micro-Installations Using Machine Learning Models. Energies 2023, 16, 6726. [Google Scholar] [CrossRef]
- Bastami, H.; Shakarami, M.R.; Doostizadeh, M. A non-hierarchical ATC framework for parallel scheduling of active distribution network with multiple autonomous microgrids. Int. J. Electr. Power Energy Syst. 2021, 133, 107293. [Google Scholar] [CrossRef]
- CYBERTWIN-EV—AESIN. Available online: https://aesin.org.uk/cybertwin-ev/ (accessed on 30 October 2025).
- A Digital Twin Demonstration for EV Charging Stations Within The TriLab-Trialog. Available online: https://www.trialog.com/en/a-digital-twin-demonstration-for-ev-charging-stations-within-the-trilab/ (accessed on 30 October 2025).
- Kaur, A.; Valizadeh, N.; Jha, D.N.; Szydlo, T.; Rajasekaran, J.R.K.; Kumar, V.; Barika, M.; Liang, J.; Ranjan, R.; Rana, O.; et al. Cybersecurity Challenges in the EV Charging Ecosystem. ACM Comput. Surv. 2023, 58, 14. [Google Scholar] [CrossRef]
- Passos, D.; De Sousa, C.; Gomes, R.C.; Assis, D.F.; Passos, F.G.O.; Albuquerque, C. A Tutorial and Security Overview on the IEEE 2030.5-2018 Standard. IEEE Commun. Surv. Tutor. 2025. [Google Scholar] [CrossRef]
- Alcaraz, C.; Lopez, J. Digital Twin Security: A Perspective on Efforts From Standardization Bodies. IEEE Secur. Priv. 2025, 23, 83–90. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, L.; Li, C.; Bai, J.; Lv, H.; Lv, Z. Blockchain-Based Secure Communication of Intelligent Transportation Digital Twins System. IEEE Trans. Intell. Transp. Syst. 2022, 23, 22630–22640. [Google Scholar] [CrossRef]
- Terrance, W.; Kouadio, K.; Youssef, T. Understanding Open Charge Point Protocol. In Proceedings of the SoutheastCon 2023, Orlando, FL, USA, 1–16 April 2023; Volume 2023, pp. 559–564. [Google Scholar] [CrossRef]
- Kaariainen, T.P.; Kortesniemi, Y. Building Trustworthy Twin-based Systems with Self-Sovereign Identities. IEEE Access 2024, 12, 182101–182123. [Google Scholar] [CrossRef]
- Hoofnagle, C.J.; van der Sloot, B.; Borgesius, F.Z. The European Union general data protection regulation: What it is and what it means. Inf. Commun. Technol. Law 2019, 28, 65–98. [Google Scholar] [CrossRef]
- Baik, J. Data privacy against innovation or against discrimination: The case of the California Consumer Privacy Act (CCPA). Telemat. Inform. 2020, 52, 101431. [Google Scholar] [CrossRef]
- Gaie, C.; Mueck, M. Introduction to the Networks and Information Systems 2 (NIS2) Directive. Intell. Syst. Ref. Libr. 2025, 265, 161–180. [Google Scholar] [CrossRef]
- Custers, B.; Heijne, A.S. The right of access in automated decision-making: The scope of article 15(1)(h) GDPR in theory and practice. Comput. Law Secur. Rev. 2022, 46, 105727. [Google Scholar] [CrossRef]
- Issa, R.; Badr, M.M.; Shalash, O.; Othman, A.A.; Hamdan, E.; Hamad, M.S.; Abdel-Khalik, A.S.; Ahmed, S.; Imam, S.M. A Data-Driven Digital Twin of Electric Vehicle Li-Ion Battery State-of-Charge Estimation Enabled by Driving Behavior Application Programming Interfaces. Batteries 2023, 9, 521. [Google Scholar] [CrossRef]
- Rajesh, P.K.; Soundarya, T.; Jithin, K.V. Driving sustainability—The role of digital twin in enhancing battery performance for electric vehicles. J. Power Sources 2024, 604, 234464. [Google Scholar] [CrossRef]
- Reyes-Acosta, R.E.; Mendoza-González, R.; Diaz, E.O.; Vargas Martin, M.; Luna Rosas, F.J.; Martínez Romo, J.C.; Mendoza-González, A. Cybersecurity Conceptual Framework Applied to Edge Computing and Internet of Things Environments. Electronics 2025, 14, 2109. [Google Scholar] [CrossRef]
- Heiden, P.Z.; Priefer, J.; Beverungen, D. Predictive Maintenance on the Energy Distribution Grid-Design and Evaluation of a Digital Industrial Platform in the Context of a Smart Service System. IEEE Trans. Eng. Manag. 2024, 71, 3641–3655. [Google Scholar] [CrossRef]
- Zaguir, N.A.; De Magalhaes, G.H.; De Mesquita Spinola, M. Challenges and Enablers for GDPR Compliance: Systematic Literature Review and Future Research Directions. IEEE Access 2024, 12, 81608–81630. [Google Scholar] [CrossRef]
- Ferrão, S.É.R.; Silva, G.R.S.; Canedo, E.D.; Mendes, F.F. Towards a taxonomy of privacy requirements based on the LGPD and ISO/IEC 29100. Inf. Softw. Technol. 2024, 168, 107396. [Google Scholar] [CrossRef]
- Zhou, J.; Fu, W.; Hu, W.; Sun, Z.; He, T.; Zhang, Z. Challenges and Advances in Analyzing TLS 1.3-Encrypted Traffic: A Comprehensive Survey. Electronics 2024, 13, 4000. [Google Scholar] [CrossRef]
- Briongos, S.; Malagón, P.; de Goyeneche, J.M.; Moya, J.M. Cache Misses and the Recovery of the Full AES 256 Key. Appl. Sci. 2019, 9, 944. [Google Scholar] [CrossRef]
- Cruz, J.P.; Kaji, Y.; Yanai, N. RBAC-SC: Role-based access control using smart contract. IEEE Access 2018, 6, 12240–12251. [Google Scholar] [CrossRef]
- Hameed, K.; Barika, M.; Garg, S.; Amin, M.B.; Kang, B. A taxonomy study on securing Blockchain-based Industrial applications: An overview, application perspectives, requirements, attacks, countermeasures, and open issues. J. Ind. Inf. Integr. 2022, 26, 100312. [Google Scholar] [CrossRef]
- Jiang, L.; Xia, Z.; Sun, X. Review on privacy-preserving data comparison protocols in cloud computing. Adv. Comput. 2021, 120, 81–119. [Google Scholar] [CrossRef]
- Zhou, I.; Tofigh, F.; Piccardi, M.; Abolhasan, M.; Franklin, D.; Lipman, J. Secure Multi-Party Computation for Machine Learning: A Survey. IEEE Access 2024, 12, 53881–53899. [Google Scholar] [CrossRef]
- Wairimu, S.; Iwaya, L.H.; Fritsch, L.; Lindskog, S. On the Evaluation of Privacy Impact Assessment and Privacy Risk Assessment Methodologies: A Systematic Literature Review. IEEE Access 2024, 12, 19625–19650. [Google Scholar] [CrossRef]
- Al Nasar, M.R.; Mohd, M.; Ali, N.M. Personal information management systems and interfaces: An overview. In Proceedings of the 2011 International Conference on Semantic Technology and Information Retrieval, STAIR 2011, Putrajaya, Malaysia, 28–29 June 2011; pp. 197–202. [Google Scholar] [CrossRef]
- NIST IR 8356; Considerations for Digital Twin Technology and Emerging Standards. NIST: Gaithersburg, MD, USA, 2021. [CrossRef]
- Murtaza, A.A.; Saher, A.; Zafar, M.H.; Moosavi, S.K.R.; Aftab, M.F.; Sanfilippo, F. Paradigm shift for predictive maintenance and condition monitoring from Industry 4.0 to Industry 5.0: A systematic review, challenges and case study. Results Eng. 2024, 24, 102935. [Google Scholar] [CrossRef]
- Banafaa, M.; Shayea, I.; Din, J.; Azmi, M.H.; Alashbi, A.; Daradkeh, Y.I.; Alhammadi, A. 6G Mobile Communication Technology: Requirements, Targets, Applications, Challenges, Advantages, and Opportunities. Alex. Eng. J. 2023, 64, 245–274. [Google Scholar] [CrossRef]
- Smith, M.; Castellano, J. Costs Associated with Non-Residential Electric Vehicle Supply Equipment: Factors to Consider in the Implementation of Electric Vehicle Charging Stations; U.S. Department of Energy Vehicle Technologies Office: Washington, DC, USA, 2015. [Google Scholar]
- A Review of the Economic Costs of Cyber Incidents: Annex-Number of Disclosed Cyber Incidents Per Country 2014–2022. Available online: https://documents.worldbank.org/en/publication/documents-reports/documentdetail/099092324164513733/p1787691fbc9980d19c891b7e706e6f352 (accessed on 6 August 2025).
- Khalid, M. Smart grids and renewable energy systems: Perspectives and grid integration challenges. Energy Strategy Rev. 2024, 51, 101299. [Google Scholar] [CrossRef]
- Jetson Orin Nano Super Developer Kit NVIDIA. Available online: https://www.nvidia.com/en-us/autonomous-machines/embedded-systems/jetson-orin/nano-super-developer-kit/ (accessed on 6 August 2025).
- HIL101-HIL Simulator System-Typhoon HIL. Available online: https://www.typhoon-hil.com/products/hil-simulator/hil101/ (accessed on 6 August 2025).
- OPAL-RT Launched the New OP4500 Real-Time Power Grid Simulator, Starting from $20,000. Available online: https://www.prnewswire.com/news-releases/opal-rt-launched-the-new-op4500-real-time-power-grid-simulator-starting-from-20000-229565311.html (accessed on 2 June 2025).
- Digital Twin Cost for Development Explained Toobler. Available online: https://www.toobler.com/blog/digital-twin-cost-development (accessed on 6 August 2025).
- Su, S.; Nassehi, A.; McClenaghan, A.; Langridge, A.; Hicks, B. A methodology for estimating the cost of a digital twin. J. Manuf. Syst. 2025, 80, 841–858. [Google Scholar] [CrossRef]
- Pricing AI Applications Google Cloud. Available online: https://cloud.google.com/generative-ai-app-builder/pricing (accessed on 6 August 2025).
- Chen, X.; Zhou, X.; Zhang, H.; Sun, M.; Zhao, T. Cost-Effective Federated Learning: A Unified Approach to Device and Training Scheduling. In Proceedings of the IEEE International Conference on Communications, Denver, CO, USA, 9–13 June 2024; pp. 3488–3493. [Google Scholar] [CrossRef]
- Cirrascale Cloud Services. Available online: https://www.cirrascale.com/ai-innovation-cloud/nvidia-ai (accessed on 6 August 2025).
- Hyperstack AI Cloud Pricing|On-Demand, Reserved and Spot GPU VMs. Available online: https://www.hyperstack.cloud/gpu-pricing (accessed on 6 August 2025).
- Predictive Analytics For Cybersecurity. Available online: https://www.meegle.com/en_us/topics/predictive-analytics/predictive-analytics-for-cybersecurity (accessed on 6 August 2025).
- Baker, M.; Fard, A.Y.; Althuwaini, H.; Shadmand, M.B. Real-Time AI-Based Anomaly Detection and Classification in Power Electronics Dominated Grids. IEEE J. Emerg. Sel. Top. Ind. Electron. 2022, 4, 549–559. [Google Scholar] [CrossRef]
- Bhatia, M.P.S.; Sangwan, S.R. Soft computing for anomaly detection and prediction to mitigate IoT-based real-time abuse. Pers. Ubiquitous Comput. 2024, 28, 123–133. [Google Scholar] [CrossRef]
- Can Public EV Fast-Charging Stations Be Profitable in the United States?|McKinsey. Available online: https://www.mckinsey.com/features/mckinsey-center-for-future-mobility/our-insights/can-public-ev-fast-charging-stations-be-profitable-in-the-united-states (accessed on 6 August 2025).
- How Digital Twins Are Transforming Cybersecurity Defense and Threat Detection|RSA Conference. Available online: https://www.rsaconference.com/library/blog/how-digital-twins-are-transforming-cybersecurity-defense-and-threat-detection (accessed on 6 August 2025).
- Energy and Power Data Loggers and Recorders—Measuring and Logging Power and Energy for Load Analysis, Quality and Metering. Available online: https://microdaq.com/data-loggers/energy-power.php?srsltid=AfmBOorjkMwMTX4hnflalrVAd6mvC2lSgWUjqs7STopX4GUP8MEfCvj8 (accessed on 2 June 2025).
- Buy the Latest Jetson Products|NVIDIA Developer. Available online: https://developer.nvidia.com/buy-jetson (accessed on 2 June 2025).
- Raspberry Pi 5 16GB. Available online: https://www.seeedstudio.com/Raspberry-Pi-5-16GB-p-6319.html (accessed on 2 June 2025).
- Typhoon HIL—Solutions. Available online: https://www.typhoon-hil.com/solutions/ (accessed on 2 June 2025).
- IoT Gateways. Available online: https://buy.advantech.com/IoT-Gateways/Industrial-IoT-Gateways-Devices-IoT-Gateways/AUS_32213.products.htm (accessed on 2 June 2025).
- RTDS Simulator|Powerful Hardware for World-Class Simulation. Available online: https://www.rtds.com/technology/simulation-hardware (accessed on 2 June 2025).
- Eser, S.; Storek, T.; Wüllhorst, F.; Dähling, S.; Gall, J.; Stoffel, P.; Müller, D. A modular Python framework for rapid development of advanced control algorithms for energy systems. Appl. Energy 2025, 385, 125496. [Google Scholar] [CrossRef]
- GPU Pricing Google Cloud. Available online: https://cloud.google.com/compute/gpus-pricing?hl=en (accessed on 2 June 2025).
- Abdessadak, A.; Ghennioui, H.; Thirion-Moreau, N.; Elbhiri, B.; Abraim, M.; Merzouk, S. Digital twin technology and artificial intelligence in energy transition: A comprehensive systematic review of applications. Energy Rep. 2025, 13, 5196–5218. [Google Scholar] [CrossRef]
- AI Pricing: How Much Does AI Implementation Cost. Available online: https://www.neurond.com/blog/how-much-does-ai-cost (accessed on 2 June 2025).
- Steidl, M.; Felderer, M.; Ramler, R. The pipeline for the continuous development of artificial intelligence models—Current state of research and practice. J. Syst. Softw. 2023, 199, 111615. [Google Scholar] [CrossRef]
- Real-World Gen AI Use Cases from the World’s Leading Organizations|Google Cloud Blog. Available online: https://cloud.google.com/transform/101-real-world-generative-ai-use-cases-from-industry-leaders (accessed on 2 June 2025).
- Kilic, A. TLS-handshake for Plug and Charge in vehicular communications. Comput. Netw. 2024, 243, 110281. [Google Scholar] [CrossRef]
- Hamdare, S.; Brown, D.J.; Kaiwartya, O.; Cao, Y.; Jugran, M. MitM Cyber Risk Analysis in OCPP Enabled EV Charging Stations. In Proceedings of the 2024 4th Intelligent Cybersecurity Conference, ICSC 2024, Valencia, Spain, 17–20 September 2024; pp. 151–157. [Google Scholar] [CrossRef]
- Wanecki, P.; Jasek, R.; Drofova, I. The Contribution of the European NIS2 Directive to the Design of the Cyber Security Model. In Proceedings of the International Conference on Information and Digital Technologies, Zilina, Slovakia, 20–22 June 2023; pp. 149–154. [Google Scholar] [CrossRef]
- California Consumer Privacy Act (CCPA)|State of California—Department of Justice—Office of the Attorney General. Available online: https://oag.ca.gov/privacy/ccpa (accessed on 25 June 2025).
- Chirita, M.; Jørgensen, B.N.; Ma, Z.G. Digital Twin of the European Electricity Grid: A Review of Regulatory Barriers, Technological Challenges, and Economic Opportunities. Appl. Sci. 2025, 15, 6475. [Google Scholar] [CrossRef]
- Badakhshan, E.; Ivanov, D. Integrating digital twin and blockchain for responsive working capital management in supply chains facing financial disruptions. Int. J. Prod. Res. 2025, 63, 7800–7834. [Google Scholar] [CrossRef]
- Al-Banna, A.; Yaqot, M.; Menezes, B.C. Investment strategies in Industry 4.0 for enhanced supply chain resilience: An empirical analysis. Cogent Bus. Manag. 2024, 11, 2298187. [Google Scholar] [CrossRef]
- Qadir, Z.; Le, K.N.; Saeed, N.; Munawar, H.S. Towards 6G Internet of Things: Recent advances, use cases, and open challenges. ICT Express 2023, 9, 296–312. [Google Scholar] [CrossRef]
- Masanet, E.; Shehabi, A.; Lei, N.; Smith, S.; Koomey, J. Recalibrating global data center energy-use estimates. Science 2020, 367, 984–986. [Google Scholar] [CrossRef]
- Li, P.; Fan, J.; Wu, J. Exploring the key technologies and applications of 6G wireless communication network. iScience 2025, 28, 112281. [Google Scholar] [CrossRef]
- Jha, R.; Jha, R.; Islam, M. Forecasting US data center CO2 emissions using AI models: Emissions reduction strategies and policy recommendations. Front. Sustain. 2024, 5, 1507030. [Google Scholar] [CrossRef]
- Acharige, S.S.G.; Fernando, M.A.; Abeyratne, S.K.; Chandima, R.M.; Abeywickrama, S.N. Grid integration of electric vehicles-Impact assessment and remedial measures. J. Power Sources 2025, 650, 236697. [Google Scholar] [CrossRef]
- Hawkins, T.R.; Singh, B.; Majeau-Bettez, G.; Strømman, A.H. Comparative Environmental Life Cycle Assessment of Conventional and Electric Vehicles. J. Ind. Ecol. 2013, 17, 53–64. [Google Scholar] [CrossRef]
- Nwagu, C.N.; Ujah, C.O.; Kallon, D.V.V.; Aigbodion, V.S. Integrating solar and wind energy into the electricity grid for improved power accessibility. Unconv. Resour. 2025, 5, 100129. [Google Scholar] [CrossRef]
- Alsharif, M.H.; Kelechi, A.H.; Jahid, A.; Kannadasan, R.; Singla, M.K.; Gupta, J.; Geem, Z.W. A comprehensive survey of energy-efficient computing to enable sustainable massive IoT networks. Alex. Eng. J. 2024, 91, 12–29. [Google Scholar] [CrossRef]
- Cai, L.; Wang, J.; Li, Y.; Zhang, X.; Liu, H.; Chen, Z. Adaptive frequency optimization control strategy of electric vehicles participation in energy storage considering user active response margin. Int. J. Electr. Power Energy Syst. 2025, 170, 110858. [Google Scholar] [CrossRef]
- Fossen, S.; Fossen, T.I. EXogenous Kalman filter (XKF) for Visualization and Motion Prediction of Ships using Live Automatic Identification System (AIS) Data. Model. Identif. Control 2018, 39, 233–244. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).