Abstract
Studying the faster and more efficient method of solving the uncertain security-constrained unit commitment (SCUC) problem is an urgent need for the development of power systems under the background of large-scale wind power access and power dispatching. This study proposes an improved constrained order optimization (COO) algorithm to solve the uncertain SCUC problem. First, the data-driven discrete variable identification strategy is incorporated into the COO rough model, and then, the invalid security constraints identification strategy is incorporated into the COO accurate model. Finally, the improved COO algorithm combines the discrete variable identification with the invalid security constraint identification to make the uncertain SCUC decision. The results of the IEEE 118-bus test system showed that, compared with the traditional COO algorithm, the improved COO algorithm proposed has higher accuracy and better efficiency.
1. Introduction
The security-constrained unit commitment (SCUC) considering uncertain factors has become the most significant and hottest research topic in the power market, given large-scale wind power access [1,2,3]. The uncertain SCUC model has always been considered as a high-dimensional, strongly random, nonlinear NP-hard problem due to the integration of uncertain factors, discrete variables, and safety constraints, including power flow calculations [4,5,6]. Therefore, it is difficult to solve the problem accurately and efficiently. Currently, the problem of solving accurately and efficiently has become a key technical bottleneck in the field of SCUC decision-making [7]. Thus, it is of great theoretical and practical significance to research a more efficient method for solving the uncertain SCUC models.
In recent years, the idea of combining the benders decomposition method with a mature mixed integer programming algorithm has gradually become the mainstream solution of the SCUC problem [8,9,10]. The method first decouples the SCUC model and then solves the decoupled subproblems by utilizing a mixed integer programming algorithm. Benders decomposition method achieves good results in solving the deterministic SCUC model. The difficulty of solving the SCUC model is reduced by decoupling the complex constraints into independent optimization subproblems in the benders decomposition method. However, the effect is not obvious for the problem of scene explosion in SCUC solution caused by the uncertainties. Therefore, its advantages are not obvious when this method is used to solve the uncertain SCUC problem. The constrained order optimization (COO) algorithm [11] was introduced first for the problem of SCUC solving in [12], and a solution of the uncertain SCUC was proposed based on the COO algorithm. From the perspective of the solution space, the feasible region scale of the SCUC model is reduced by constructing the COO rough model. On the basis of the COO rough model, a COO accurate model is constructed to find a good enough solution for the SCUC problem. Compared with the traditional benders decomposition method, the efficiency of the COO algorithm is enhanced to nearly 10 times [12]. Based on the existing researches, the COO algorithm has been proven to be an effective method to solve uncertain SCUC problems rapidly. Although the traditional COO algorithm reduces the scale of the feasible region from the perspective of solution space, elimination and discrimination of the redundant information in the model itself are neglected. Therefore, the traditional COO algorithm can still be improved in terms of the solving efficiency, as described below.
1) When the SCUC model is solved by the traditional COO algorithm, the COO rough model should be constructed first, and then it is used to screen out the feasible solution space for the start–stop state of all units. However, there are many units in large-scale power systems, so the solving efficiency of the COO rough model is not high. The maximum load usually reaches 70% or higher of the installed capacity in the real large power grids, which means some units are always on or off during the scheduling period. Actually, there is no need to consider these constant units during the solving process. Consequently, if the constant units are identified first in the COO rough model, the efficiency of the COO algorithm will be improved. The problem of discrete variable identification has been studied. A linear screening model was constructed to identify the constant units in [13]. The constant units were identified through the priority method in [14,15]. In reference [16], the constant units are identified according to the relationship between the calculated active power output value and the identification rate parameter value. On the whole, the existing methods of the SCUC discrete variable identification are mainly based on the physical model driver idea, that is, constructing a complex mathematical model based on physical principles. However, it is difficult to construct an accurate mathematical model, and the identification results in the existing methods often have the problems of strong subjectivity and low accuracy. In fact, a large amount of structured historical data can be accumulated once the SCUC decision-making scheme is utilized in real power systems. In the long run, the accumulated historical SCUC decision-making scheme also has a guiding significance for the identification of the constant units. Therefore, the idea based on a data-driven method is a feasible way to address the problems of low accuracy and low objectivity of the discrete variable identification strategy.
2) Checking and computing network security constraints are one of the most computationally intensive tasks in solving SCUC problems. The strategy of checking all lines one by one was adopted in the COO accurate model in reference [11]. This strategy will have a serious impact on the computational efficiency of the COO algorithm as the number of nodes and checked lines increases sharply with the expansion of the power grid scale. Reference [17] showed that only a few of the network security constraints are effective that play a role in limiting the feasible region. Furthermore, a fast identification strategy for the invalid security constraints was also proposed. The method in [17] reduces the invalid security constraints by more than 85% without affecting the calculation accuracy of the model. Thus, the identification strategy for the invalid security constraints can reduce the redundancy of the SCUC model. If this method can be introduced in the COO accurate model, the computational efficiency of the COO algorithm will be improved greatly.
In summary, a data-driven discrete variable identification strategy for the SCUC model is proposed in this paper. This strategy and the invalid security constraint identification strategy are used to improve the traditional COO algorithm [12]. Finally, an improved COO algorithm for uncertain SCUC problem solving is proposed. This study is following three steps: construct a COO rough model with the discrete variable identification, construct an accurate COO model with the invalid safety constraint identification, solve the two models separately. The results based on IEEE 118-bus show that the redundancy of the uncertain SCUC model can be reduced effectively, and the computational efficiency can be further improved for the proposed improved strategy.
The main contributions in this study are as follows.
(1) A data-driven strategy of the SCUC discrete variable identification is proposed, and a COO rough model is constructed based on this strategy.
(2) A COO accurate model is constructed based on an identification strategy of the invalid security constraints.
(3) An improved COO algorithm suitable for the problem of SCUC solving is proposed based on the discrete variable identification strategy and the invalid security constraints identification strategy.
The rest of this paper is organized as follows. The SCUC model considering the uncertainty of wind power output is constructed in Section 2. An overall framework for an improved COO algorithm is proposed in Section 3. An improved strategy for the COO algorithm is proposed in Section 4. The simulation analysis is shown in Section 5. Finally, the conclusions are provided in Section 6.
2. The SCUC Model Considering the Uncertainty of Wind Power Output
2.1. Description of the Uncertainty of Wind Power Output
The confidence interval of active power for wind power output is adopted to characterize the uncertainty of wind power output in this study. The interval can be calculated according to the prediction values and error distribution for the wind power output. The specific mathematical expressions are as follows:
The relationship between K and ζ is as follows, according to the central limit theorem [18].
where PW represents the active power output from wind power unit. PWjt represents the real value of active power output from unit j at time t. PWjt* represents the expected value of active power output from unit j at time t. PWjt- and PWjt+ represent the lower limit and upper limit respectively of active power output from unit j at time t. ζ represents the confidence probability of wind power output interval. K represents the coefficient relating to confidence probability ζ. σjt represents the standard deviation of predicted error of active power output from unit j at time t. Φ-1 represents the inverse function of the probability density function of the wind power output.
2.2. SCUC Model Based on the Robust Optimization
The uncertainty of wind power output is considered based on the robust optimization. Decisions of the start–stop state and the output scheme of generating units are made to ensure the lowest total cost under the worst case of wind power output. The objective function is as follows:
The operation cost of thermal power units is shown in (6).
The total start–stop cost of thermal power units is shown in equation (7) if the shut-down cost of units is ignored.
where F(UG,PG) represents the total scheduling cost of all thermal power units. PGit represents the active power output of unit i at time t. UGit represents the start–stop states of unit i at time t. RGit(PGit) represents the operation cost of unit i at time t. SGit(τti) represents the start–up cost at time t of thermal power unit i. ai, bi, ci represents the operation cost parameter of unit i. αi represents the start-up and maintenance cost of unit i. βi represents the cooling environment start-up cost of the unit i. τti represents the continuous shut-down time of unit i at time t. ωi represents the time constant of cooling speed of unit i. H represents the scheduling period. M represents the total number of schedulable thermal power units.
For the min–max model, the inner maximization (max) problem indicates the worst impact of uncertain active power output from wind power for SCUC decision-making, and the outer minimization (min) problem indicates the minimum total cost of the system under the worst case of SCUC decision-making.
The following constraints must be met for the decision variables (UGit and PGit) of the SCUC model, in order to ensure the run safety and reliability of the system.
(1) The power balance of the power system is defined as follows:
(2) The capacity constraints of the unit can be expressed as follows:
(3) The constraints of the maximum start–stop number are defined as follows:
(4) The constraints of minimum start–stop time are defined as follows:
(5) The constraints of unit ramping up/down are as follows:
(6) The constraints of network security are as follows:
where W represents the total number of schedulable wind power units. PDt represents the active load of the system at time t. PGimax and PGimin represents the upper limit and lower limit, respectively, of active power output from unit i. ni represents the maximum start–stop times of unit i in a scheduling period. MUTGi and MDTGi represent the minimum start-up and shut-down time respectively of unit i. and represent the maximum ramping up and ramping down limits respectively of unit i in one hour. Pl represents the active power on the transmission line l. Plmax represents the maximum active power capacity on the transmission line l. D represents the total number of load nodes. PDkt represents the active load of the system on node k at time t. KGli, KWlj, and KDlk represent the shift factor matrix of thermal power unit, wind power unit, and load, respectively.
3. An Overall Framework for the Improved COO Algorithm
The COO [6,11,12] is an efficient algorithm suitable for the SCUC model solution, and its main idea is as follows. A COO rough model is constructed first. The solution number in the solution space is reduced greatly by quickly prescreening the solution space. In addition, the feasible solutions in the solution space are preliminarily sorted, and the selected set is formed based on the certain strategy. Then, a COO accurate model is constructed to sort the solutions further in the selected set to obtain the optimal solution.
The SCUC model itself is a mixed integer programming problem with relatively independent decision variables. Therefore, the COO rough models and the COO accurate models for the discrete decision variables UGit and continuous decision variables PGit are constructed in the COO algorithm, respectively. In addition, the following improvements are made on the basis of the traditional COO algorithm [12].
(1) The discrete variable identification strategy is added to the COO rough model. First, the data-driven discrete variable identification strategy is used to identify the constant units, and then, the COO rough model is adopted to solve the remaining units. Its purpose is to reduce the dimensions of the variables used in the COO rough model and to improve its computational efficiency.
(2) The identification strategy of the invalid security constraints is added to the COO accurate model, eliminating the invalid security constraints, and reducing the number of network security constraints that need to be checked for the COO accurate model. It can also reduce the complexity of solving the COO accurate model.
The overall idea of the improved COO algorithm is shown in Figure 1. As shown in Figure 1, the improved COO algorithm consists of three main steps as follows.
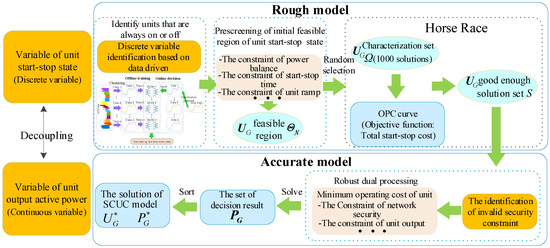
Figure 1.
The overall idea of the improved constrained order optimization (COO) algorithm.
Step 1. First, the SCUC discrete variable identification model for the start–stop state of the units is constructed based on the deep learning idea, and the constant units are identified in discrete variable space. Then, the initial feasible region of the start–stop state (UGit) is formed by eliminating the constant units. Moreover, the SCUC model is decoupled, and the variable UGit is taken to construct a COO rough model with its related constraints and start–stop cost. The initial feasible region of the start–stop state of the units is prescreened, and the feasible region ΘN is obtained. Select N feasible solutions from feasible region ΘN according to a uniform distribution to form a characterization set Ω. The number of N is closely related to the size of the solution space. Reference [19] showed that the number of N is generally 1000, as the solution space is less than 108.
Step 2. Z solutions are selected further from the characterization set Ω as the selected set S based on the Horse Race method [11,20]. In set S, it must be guaranteed that at least α% of the probability contains k good enough solutions. The specific selection rule of the Horse Race method is as follows.
Firstly, the COO rough model is utilized to evaluate and sort the solutions in the characterization set Ω, and the order performance curve (OPC) is formed. Secondly, the type of OPC curve generated is determined based on the standard OPC curve. Thirdly, the optimization parameter in equation (6) [20] is determined according to the type of the OPC, and the value of Z is obtained. Finally, the previous Z solutions are selected from the sorted characterization set Ω to form the selected set S. The Z solution model is as follows.
The meanings of all the symbols in (16) are shown in [20].
Step 3. The identification model of the invalid security constraints is constructed first to eliminate the invalid security constraints. Second, the minimum total cost of units is taken as an objective function. Then, a COO accurate model of continuous variable PGit is constructed under the condition of considering the constraints related to the active power output. Solving the unit output scheme and operation cost corresponding to the unit start–stop state in selected set S. Finally, the COO accurate model is employed to sort the set S to obtain the optimal solution.
4. Improved Strategy for the COO Algorithm
4.1. Improved Strategy for the COO Rough Model
The key to ensuring the efficiency and accuracy of the COO algorithm is to construct a reasonable COO rough model. The solution of the COO rough model needs to be simpler than that of the COO accurate model to ensure the rapid prescreening of the solution space. In addition, the COO rough model should be able to reflect the relative merits and demerits of the solutions accurately to preliminarily sort the solution space.
Some constant units during the short time scale of day-ahead scheduling are affected by the load level and the installed capacity of the system. Therefore, the computational efficiency of the COO rough model can be improved greatly if the constant units before the COO rough model are screened. A novel data-driven SCUC discrete variable identification method is first proposed in this paper to improve the COO rough model.
4.1.1. The Data-Driven SCUC Discrete Variable Identification Strategy
A deep learning model is constructed by using Long Short-Term Memory (LSTM), which can accept the input of a time series structure. The mapping relationship of deep learning between the system load and the start–stop state of the units is created through massive historical data training. Based on the deep learning model, the constant units are identified.
In the real power system, the similarity of the daily load curve is relatively higher in the short period and in the same period each year. However, the load curve varies sharply in different months and seasons due to environmental and climatic factors. These historical data will easily lead to overfitting and reduce the calculation accuracy if they are directly used to train the deep learning model without distinction. Thus, it is necessary to preprocess the historical data by clustering and constructing a deep learning model for each type of historical data. The type of load data input is first determined, and then, the corresponding mapping model is used to solve the problem as the decision-making step. The process is shown in Figure 2. The structure of the deep learning model based on LSTM is shown in Figure 3.
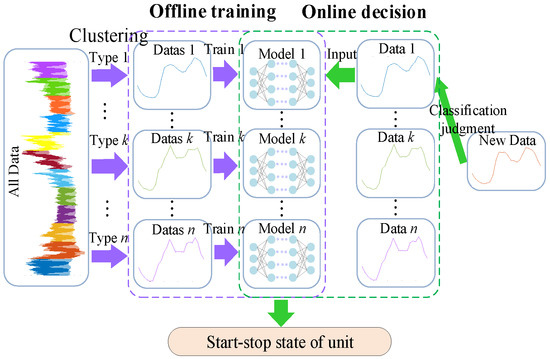
Figure 2.
Deep learning model for the discrete variable identification.
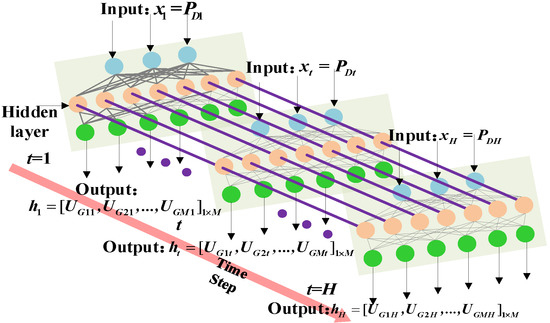
Figure 3.
The structure of the deep learning model.
The parameter xt represents the load data input to the deep learning model at time t in Figure 3, and xt is equal to PDt. The symbol ht is the start–stop state vector of all units output by the deep learning model at time t, and ht equals [UG1t,UG2t,…,UGMt]1×M. The total number of units is M. The hidden layer is composed of LSTM neurons. Its depth is set after the size of data input, the structure factors, and the training test results are all considered. The training process of the deep learning model can be found in [21].
The internal structure of the LSTM neuron is shown in Figure 4.
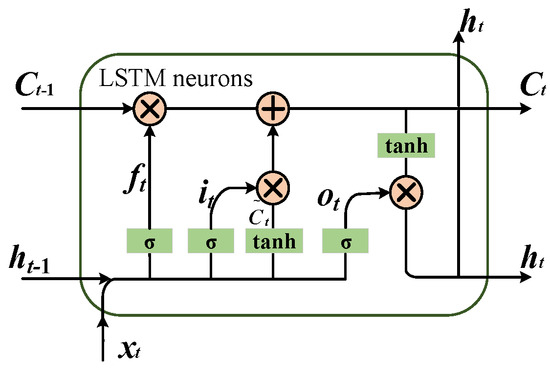
Figure 4.
Internal structure of using Long Short-Term Memory (LSTM) neuron.
Combined with historical sample data of SCUC, mathematical models of the LSTM neuron are constructed as follows.
where “·” represents the element multiplication in the matrix. “*” represents matrix multiplication. Wf, Wi, WC, Wo, Wh represents the weight value of the input parameter. bf, bi, bC, bo, bh represents the offset value of each input parameter. A detailed description of the symbols can be found in [14].
4.1.2. Construction and Solution of the COO Rough Model
The COO rough model is constructed according to the constraints related to the start–stop state variables UGit. The main constraints include the power balance constraint, unit climbing constraint, and minimum start–stop time constraint. The mathematical model is shown in (18).
where ΔPDt represents the active power reserved by the system at time t.
First, the data-driven SCUC discrete variable identification strategy is utilized to determine constant units. Then, equation (18) is used to screen the solution space, and the feasible region ΘN of unit start–stop variable UGit can be obtained. The N feasible solutions are selected randomly and uniformly in the feasible region ΘN, and the cost F1 for all start–stop units is taken as the objective function. Meanwhile, the OPC is drawn, and the set S of unit start–stop variable UGit is sequenced further. The objective function is shown in (19).
4.2. Improved Strategy for the COO Accurate Model
The scale of modern power systems is huge, and there are many nodes. Therefore, solving the equation of power flow and checking network security constraints are some of the most time-consuming parts in the process of solving SCUC problems. Only a small part of the constraints is effective, which could restrict the formation of the feasible region among all the network security constraints shown in [17]. From this viewpoint, the invalid security constraints identification strategy is introduced first, and the accurate COO model is improved on this basis.
4.2.1. The Invalid Security Constraints Identification Strategy
The invalid constraint is defined as follows. The constraint is an invalid constraint if the feasible region is the same, no matter if the constraint is removed or not. The principle is shown in Figure 5.
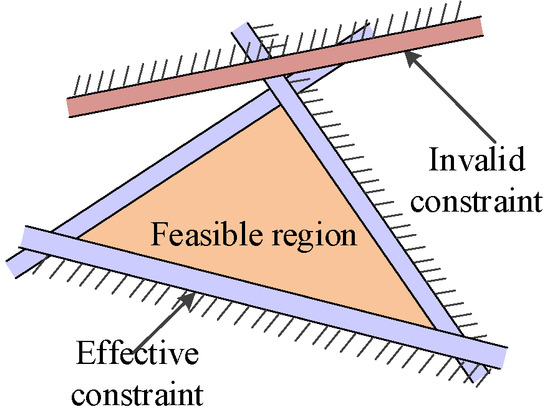
Figure 5.
Definition of the invalid constraint.
The network security constraint condition of the power system, which is a bilateral constraint, is shown in (15). The bilateral constraint condition can be judged as an invalid constraint if both unilateral constraints in (15) are invalid constraints. The bilateral constraints in (15) are divided into the unilateral constraints in (20):
Two identification models with the unilateral invalid constraints are established according to (20).
The minimum is solved by (21), (23), and (24). The minimum is also solved by (22)–(24). It indicates that the lth security constraint is invalid if both and satisfy the conditions.
4.2.2. Construction and Solution of the COO Accurate Model
The COO accurate model is constructed based on the invalid security constraints identification strategy. The COO accurate model sets the unit output PGit as the variable and takes the systems start–stop costs and operation costs as the objective function. Meanwhile, the set S is evaluated accurately to obtain the optimal solution. The variable UGit is a constant for the COO accurate model, and the corresponding start–stop cost F1 is also a constant. Therefore, the decision variables are only PGit in the COO accurate model. The COO accurate model is shown in (25) to minimize the total SCUC cost.
Equation (25) is a min–max model that cannot be solved directly. Thus, dual transformation is first needed to process it. Equation (25) is the linear objective function and the constraint condition of the uncertain variable PW for the inner max model. Therefore, the duality model of the inner model is directly obtained according to the linear duality theorem. Combining the outer max model, the final form (26) of the dual transformation model is obtained.
where Pl(l) represents the active power on the remaining line after removing the invalid constraint on the line l.
where PG represents the matrix of active power output from thermal power units. λ represents the dual variable of the PW. φ1 represents the equation constraints containing PG and PW. φ2 represents the inequality constraint containing only PG. φ3 represents the inequality constraints containing PG and PW.
5. Numerical Simulation
5.1. The Test System
The numerical tests are performed on a modified IEEE 118-bus system, which includes 54 thermal units, 91 demand sides, and 3 wind farms. The three wind farms in which the rated powers are 100, 200, and 250 MW, are accessed at the bus 14, 54, and 95, respectively. The load data is based on the actual load data of 365 typical days in a certain area of Hunan Province in 2014, and it is reduced by 4.4 times. The scheduling period is H = 24 h. The related calculations are done on the Intel Core i5-7500 processor 3.40 GHz, 8G memory computer. The improved COO algorithm in this paper is implemented using Matlab 9.0 and CPLEX 12.4, but the discrete variable identification process is implemented in the Python 3.6 environment.
In this paper, the training and test sample data in the deep learning model are generated by using the decision-making method in [9]. The above data are calculated based on load data from the Hunan power grid. The load data are divided into four types by cluster analysis. Under each type, 6% of the data are selected randomly as the test data, and the remaining 94% are left as training data. The size of the training and test samples is shown in Table 1.

Table 1.
Sample size.
5.2. SCUC Decision Process and Results based on the Improved COO Algorithm
The specific solving process in the improved COO algorithm is analyzed by taking the first test sample in the beginning type of data as an example. The load data of the test sample and the predicted expected value for the wind power output are shown in Table A1 of the Appendix A.
The COO rough model is used to calculate and form the feasible region ΘN. Then, a method of simple random sampling is used to select 1000 solution sets from the feasible region ΘN to form the characterization set Ω. The start–stop cost corresponding to each feasible solution is solved according to (19). The OPC is shown in Figure 6.
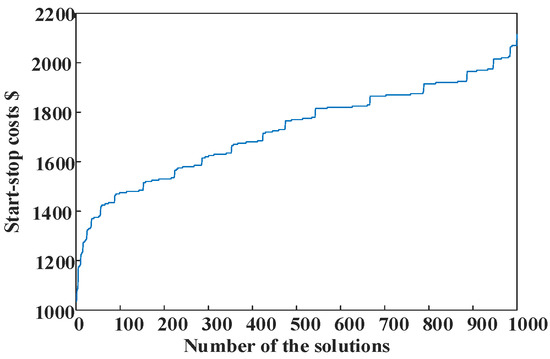
Figure 6.
The OPC of solutions.
The OPC in Figure 6 is stepped because the start–stop costs of different units may be the same under different start–stop schemes. The OPC type obtained by the improved COO algorithm is determined to be bell-shaped compared with the standard curve of the OPC in [20]. The probability that at least one solution from the set S belongs to the accurate solution set of the original problem is set to 95%. The parameters in (17) are determined as follows: Z0 = 8.1998, ρ = 1.9164, γ = –2.0250, η = 10, g = 20, and k = 1 according to [20]. The above parameters are substituted into (16), and the solutions number in the set S is 19. The COO accurate model solves the set S accurately of the COO rough model, and the results are shown in Figure 7.
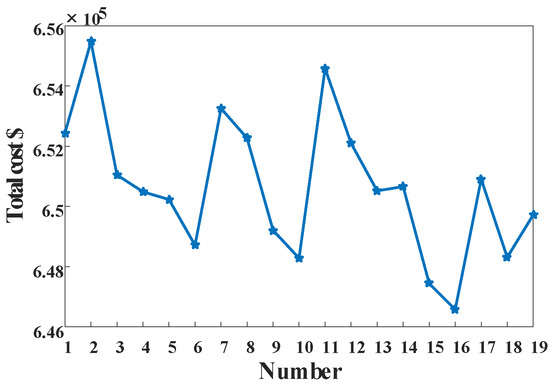
Figure 7.
The results of the COO accurate model.
The start–stop and output scheme (No. 16) with the lowest total cost is selected as the decision result. In this study, the output scheme of each unit is shown in Table A2 of the Appendix A.
5.3. Validation of the Improved COO Rough Model
Compared with [16], the effectiveness of the discrete variable identification method in this paper is verified. Compared with the traditional COO rough model [12], the effectiveness of the improved COO rough model is verified.
5.3.1. Effectiveness of the Discrete Variable Identification Method
The SCUC training sample data are utilized for training the LSTM-based deep learning model in this paper. The network parameters of the constructed deep learning model are shown in Table 2.

Table 2.
Parameter of the deep learning model.
Figure 8 shows that the training error in the deep learning model decreases as the number of training increases for each type of training sample. In other words, the constructed deep learning model proposed in this paper converges.
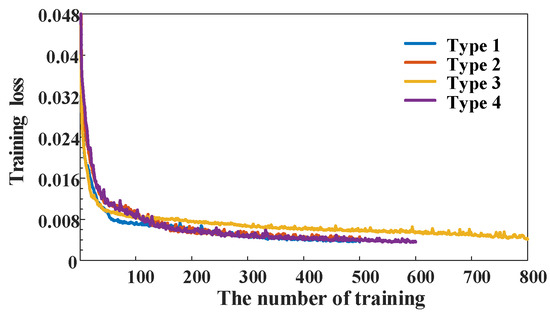
Figure 8.
Training error of the deep learning model.
The discrete variable identification results based on the clustered data of load test samples, and the identification results are compared with real start–stop state data. The Precision and Recall evaluation indexes are used to verify the correctness of the data-driven discrete variable identification strategy. The specific calculation of Precision and Recall are as follows.
where PRE represents Precision. REC represents Recall. TP represents among the units that have been identified, the number of correct identification units. FP represents among the units that have been identified, the number of units that are misidentified. FN represents among the units that have been identified, the number of units that should have been identified but missing.
A Precision of 100% means that the identification results are all correct, and there is no erroneous recognition unit. A Recall of 100% indicates that the identified results are all correct, and there is no missing unit. The COO algorithm can correct the missing units in the COO accurate model stage. Nevertheless, it has no ability to correct incorrect identification units. Thus, the discrete variable identification model must guarantee a Precision of 100%, and the higher the Recall is, the better it is. However, a Recall of 100% is not mandatory.
As seen in Figure 9, the Precision is 100%. It is the same as the method in [16] for all samples. This result indicates that there is no error identification result. The Recall in the proposed algorithm is higher than that in [16], which means that it can greatly improve the Recall of the unit start–stop states under the condition of ensuring no error identification.
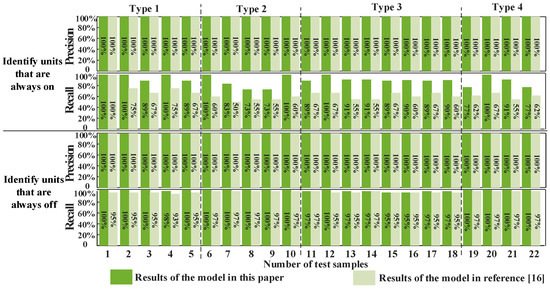
Figure 9.
Comparison diagram of the discrete variable identification results.
Compared with the real unit output, it is found that the active power output value of some units in the scheduling scheme solved by this method fluctuates sharply. Therefore, reference [16] set the identification rate parameter directly through subjective judgment, which is not enough to identify as many constant units as possible. Consequently, the Recall is relatively higher. The method of this paper uses the massive historical data to train the deep learning model, and creates the mapping relationship between the load and the constant units directly, which has a stronger objectivity and a higher accuracy.
Comparing the computational time of the COO rough model with that of [16], the results of each test sample are shown in Table 3.

Table 3.
Comparison of the discrete variable identification efficiency.
Table 3 shows that the computational efficiency of the discrete variable identification method is generally 0.2 seconds for 22 test samples, while the reference [16] is generally 2 seconds. The computational efficiency is improved by approximately 10 times compared with that in [16]. The reason is that the discrete variable identification method in [16] is essentially designed to solve the SCUC model, so the computational efficiency is lower. The proposed discrete variable identification method does not need to solve any optimization model. Instead, the method directly identifies the corresponding constant units according to the load data and the corresponding mapping relationship. The main reason is that the data-driven strategy of offline training and online decision-making is adopted. Thus, the calculation efficiency of this method is higher.
5.3.2. Effectiveness of the Improved COO Rough Model
Comparing the computational time of the COO rough model with that of the traditional COO rough model [12]. The results of each test sample are shown in Table 4.

Table 4.
Comparison of computational efficiency of the COO rough model.
Table 4 shows that in 22 test samples, the computational efficiency of the improved COO rough model has a minimum improvement of approximately nine times, a maximum improvement of approximately 250 times, and an average improvement of approximately 40 times compared with the traditional COO rough model [12]. The reason is that the discrete variable identification method can reduce the dimension of the solution space effectively so that the computational efficiency of the COO rough model is improved as a whole.
5.4. Validation of the Improved COO Accurate Model
Firstly, the effectiveness of the invalid security constraints identification method is verified. Then the computational efficiency of the improved COO accurate model is compared with that of the traditional COO accurate model [12].
5.4.1. Effectiveness of the Invalid Safety Constraint Identification Method
Equations (20)–(24) are used to reduce the invalid security constraints. The number of remaining security constraints after reduction and the time consumed are shown in Table 5 for each test sample.

Table 5.
Identification effect and efficiency comparison of the invalid security constraints model.
Table 5 shows that the number of invalid safety constraints is different for the different test samples. The reason is that the identification effect in the invalid safety constraints identification model is closely related to the load characteristics of each sample. Generally, the proposed strategy can reduce more than 90% of the invalid security constraints, and the time consumed is approximately 50 seconds, which indicates that the security constraints of the SCUC model may be redundant for real power systems. Thus, the identification strategy of invalid security constraints can eliminate redundant information quickly and effectively.
5.4.2. Effectiveness of the Improved COO Accurate Model
Comparing the computational time of the COO accurate model with that of the traditional COO accurate model [12]. The results of each test sample are shown in Table 6.

Table 6.
Comparison of computational efficiency of the COO accurate model.
The computational efficiency of the improved COO accurate model has a minimum improvement of approximately 1.08 times, a maximum improvement of approximately 1.49 times, and an average improvement of approximately 1.28 times compared to the COO accurate model [12]. The main reason is that the invalid security constraints identification strategy is added to the COO accurate model, which can reduce the number of security constraints that need to be checked greatly. Thus, the computational efficiency of the COO accurate model is improved overall.
5.5. The Overall Validation of the Improved COO Algorithm
All 22 test samples are taken as examples in this paper, and the results are compared with those for the traditional COO algorithm [12] and algorithm [9] to verify the effectiveness of the improved COO algorithm. The comparison is shown in Table 7.

Table 7.
Comparison of the solution results.
It can be observed that the SCUC total cost solved in the improved COO algorithm is slightly higher than that in [9], while the total cost in the traditional COO [12] algorithm is the highest in Table 8. The SCUC total cost solved by the two COO algorithms is higher. The average solution precision of the proposed method is about 99.6%, while the traditional COO method is about 88.1%. Compared with the traditional COO method, the accuracy of the proposed method is 1.13 times higher. The main reason is that the COO algorithm is designed to improve the algorithm efficiency greatly by abandoning the search for the optimal solution and instead searching for a good enough solution. The SCUC total cost obtained by the improved COO algorithm is slightly lower than that in the traditional COO algorithm [12]. The reason is that the set S in the improved COO algorithm is not the same as that in the traditional COO screening. This improved COO reduces the dimension of the solution space through a discrete variable identification strategy so as to improve the quality of effective solutions. Therefore, the solution quality of the set S obtained by the improved COO algorithm is higher than the traditional COO algorithm.

Table 8.
Robust and non-robust security-constrained unit commitment (SCUC) model.
The efficiency of the improved COO algorithm has been improved significantly in terms of solving efficiency compared with the other two algorithms. The efficiency of the improved COO algorithm is approximately five times higher than that of the traditional COO [12] algorithm. It is also six times higher than that in [9]. There are two main reasons. The discrete variable identification strategy is introduced into the COO rough model, which reduces the dimension of the solution space effectively and improves the computational efficiency greatly. In addition, the invalid security constraints identification strategy is introduced in the COO accurate model, which eliminates the invalid security constraints and reduces the number of security constraints that need to be checked greatly. Thus, the computational efficiency is sharply improved.
5.6. Validation of the SCUC Model Considering the Uncertainty of Wind Power Output
In order to analyze the influence of wind power uncertainty on power system scheduling, the SCUC problem is solved with the proposed method under the two situations of considering wind power uncertainty and not considering wind power uncertainty. In this paper, the robust optimization method is used to deal with the uncertainty of wind power output. The scheduling cost, calculation efficiency, and over-limited power flow under two different situations of robust optimization and non-robust optimization are shown in Table 8.
It can be seen from Table 8 that the scheduling cost considering the uncertainty of wind power is higher than that not considering the uncertainty of wind power. The reason is that the SCUC decision based on the robust optimization method is to solve the thermal power unit scheduling scheme under the worst scenario of wind power output. The scheme is a conservative uncertainty factor processing method, so the cost is high. Considering the uncertainty of wind power, the calculation efficiency is low. The reason is that the dual optimization process is added to the robust optimization model. The network power flow considering the uncertainty of wind power does not exceed the limit, while the network power flow not considering the uncertainty of wind power exceeds the limit. The reason is that the wind power output is uncertain, and the actual wind power output value is not necessarily equal to the predicted value. The generated scheduling scheme will not guarantee the network security in the worst scenario of actual wind power output if the uncertainty of wind power output is not considered.
On the whole, considering the uncertainty of wind power output, the scheduling cost increases slightly and the calculation efficiency decreases slightly. Nevertheless, the network security is improved.
6. Conclusions
An improved COO algorithm for solving the SCUC problem was proposed in this paper. The SCUC problem was solved rapidly and effectively considering the uncertainty of wind power output. Simulations based on the IEEE 118-bus example were executed. First, the data-driven discrete variable identification strategy was incorporated into the COO rough model, and then, the invalid security constraints identification strategy was incorporated into the COO accurate model. Finally, the improved COO algorithm combined the discrete variable identification with the invalid security constraint identification to make the uncertain SCUC decision. The conclusions are as follows.
(1) A deep learning model based on LSTM was constructed, and then a data-driven SCUC discrete variable identification strategy was proposed. This strategy was applicated to the COO rough model. The proposed improvement strategy can enhance the computational efficiency greatly of the rough COO model under the premise of ensuring the solution accuracy.
(2) The invalid security constraints identification strategy can identify more than 90% of the invalid security constraints in a short period of time. The strategy introduced to the COO accurate model can effectively reduce the computational redundancy of the COO accurate model and improve its computational efficiency.
(3) The data-driven SCUC discrete variable identification strategy and the invalid security constraint identification strategy were introduced based on the COO algorithm. These strategies effectively improved the compactness and the overall efficiency of the COO algorithm. Compared with the traditional COO, the accuracy and efficiency of the proposed method were improved by nearly 1.13 times and 5 times, respectively.
On the whole, the actual situation, which is common in the SCUC problem, was considered in the method of this paper. By reducing the complexity of the solution space and the model, the purpose of improving the accuracy and efficiency of the solution was achieved.
Author Contributions
Data curation, J.J.; funding acquisition, N.Y.; project administration, C.X.; resources, Y.H.; validation, H.C. and B.Z.; writing—original draft, J.J.; writing—review and editing, S.L.
Funding
This research was funded by the National Natural Science Foundation of China No. 51607104.
Acknowledgments
The authors would like to thank the National Natural Science Foundation of China (Project No.: 51607104) for providing funding to conduct this study.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A

Table A1.
Load data and output prediction of wind power for the first test sample in the first type (MW).
Table A1.
Load data and output prediction of wind power for the first test sample in the first type (MW).
| Time Period | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Load | 2094 | 1748 | 1566 | 1463 | 1478 | 1498 | 1640 | 1861 | 2486 | 2706 | 2678 | 2638 | 2607 | 2420 | 2335 | 2240 | 2311 | 2497 | 2537 | 2985 | 3061 | 2948 | 2856 | 2716 |
| PW1 | 44 | 70 | 76 | 82 | 84 | 84 | 100 | 100 | 78 | 64 | 100 | 92 | 84 | 80 | 78 | 32 | 4 | 0 | 10 | 0 | 6 | 56 | 82 | 52 |
| PW2 | 72 | 71 | 80 | 67 | 70 | 66 | 46 | 36 | 32 | 44 | 40 | 30 | 23 | 27 | 33 | 16 | 29 | 32 | 35 | 26 | 53 | 68 | 75 | 66 |
| PW3 | 95 | 94 | 69 | 86 | 73 | 88 | 51 | 35 | 30 | 72 | 50 | 41 | 29 | 39 | 43 | 22 | 26 | 32 | 24 | 25 | 60 | 81 | 82 | 83 |

Table A2.
Solution results of the SCUC model based on improved COO (taking the first sample in the first type as an example) (MW).
Table A2.
Solution results of the SCUC model based on improved COO (taking the first sample in the first type as an example) (MW).
| Time Period | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| G1–G4 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G5 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 100 | 100 | 106 | 138 | 135 | 112 | 100 | 100 | 100 | 100 | 100 | 100 | 104 | 105 | 118 | 102 | 0 |
| G6–G9 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G10 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 100 | 100 | 100 | 100 | 100 | 104 | 105 | 118 | 102 | 119 |
| G11 | 350 | 350 | 322 | 289 | 298 | 302 | 347 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 | 350 |
| G12–G19 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G20 | 250 | 134 | 75 | 50 | 50 | 51 | 107 | 165 | 250 | 250 | 250 | 250 | 250 | 250 | 221 | 217 | 250 | 250 | 250 | 250 | 250 | 250 | 250 | 250 |
| G21 | 250 | 134 | 75 | 50 | 50 | 51 | 107 | 165 | 250 | 250 | 250 | 250 | 250 | 250 | 221 | 217 | 250 | 250 | 250 | 250 | 250 | 250 | 250 | 250 |
| G22–G23 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G24 | 73 | 50 | 50 | 50 | 50 | 50 | 50 | 50 | 185 | 200 | 200 | 200 | 200 | 101 | 50 | 50 | 50 | 127 | 99 | 200 | 200 | 0 | 0 | 0 |
| G25 | 73 | 50 | 50 | 50 | 50 | 50 | 50 | 50 | 185 | 200 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 99 | 200 | 200 | 200 | 200 | 200 |
| G26 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G27 | 264 | 219 | 206 | 196 | 199 | 200 | 213 | 226 | 311 | 323 | 356 | 354 | 330 | 276 | 239 | 238 | 245 | 287 | 275 | 321 | 322 | 336 | 320 | 337 |
| G28 | 264 | 219 | 206 | 196 | 199 | 200 | 213 | 226 | 311 | 323 | 356 | 354 | 330 | 276 | 239 | 238 | 245 | 287 | 275 | 321 | 322 | 336 | 320 | 337 |
| G29 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 104 | 105 | 118 | 102 | 119 |
| G30–G38 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G39 | 300 | 300 | 300 | 289 | 298 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 | 300 |
| G40 | 50 | 50 | 50 | 50 | 50 | 50 | 50 | 50 | 93 | 106 | 138 | 135 | 112 | 60 | 50 | 50 | 50 | 70 | 59 | 104 | 105 | 118 | 102 | 119 |
| G41–G42 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| G43 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 106 | 138 | 135 | 112 | 100 | 100 | 100 | 100 | 100 | 100 | 104 | 105 | 118 | 102 | 0 |
| G44 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 100 | 100 | 100 | 100 | 100 | 100 | 104 | 105 | 0 | 0 | 0 |
| G45 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 112 | 100 | 100 | 100 | 100 | 100 | 100 | 104 | 105 | 118 | 102 | 119 |
| G46–G54 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
References
- Ye, H.; Wang, J.; Li, Z. MIP Reformulation for max-min problems in Two-stage robust SCUC. IEEE Trans. Power Syst. 2017, 32, 1237–1247. [Google Scholar] [CrossRef]
- Li, Z.; Ye, L.; Zhao, Y.; Song, X.; Teng, J.; Jin, J. Short-term wind power prediction based on extreme learning machine with error correction. Prot. Control Mod. Power Syst. 2017, 3, 95–100. [Google Scholar] [CrossRef]
- Ai, Q.; Fan, S.; Piao, L. Optimal scheduling strategy for virtual power plants based on credibility theory. Prot. Control Mod. Power Syst. 2016, 1, 1–8. [Google Scholar] [CrossRef]
- Abujarad, S.Y.; Mustafa, M.W.; Jamian, J.J. Recent approaches of unit commitment in the presence of intermittent renewable energy resources: A Review. Renew. Sustain. Energy Rev. 2017, 70, 215–223. [Google Scholar] [CrossRef]
- Zheng, Q.P.; Wang, J.; Liu, A.L. Stochastic optimization for unit commitment—A review. IEEE Trans. Power Syst. 2015, 30, 1913–1924. [Google Scholar] [CrossRef]
- Guan, X.; Song, C.; Ho, Y.C.; Zhao, Q. Constrained ordinal optimization—A feasibility model based approach. Discret. Event Dyn. Syst. 2006, 16, 279–299. [Google Scholar] [CrossRef]
- Yang, N.; Ye, D.; Zhou, Z.; Cui, J.; Chen, D.; Wang, X. Research on modelling and solution of stochastic SCUC under AC power flow constraints. IET Gener. Transm. Distrib. 2018, 12, 3618–3625. [Google Scholar]
- Alemany, J.; Kasprzyk, L.; Magnago, F. Effects of binary variables in mixed integer linear programming based unit commitment in large-scale electricity markets. Electr. Power Syst. Res. 2018, 160, 429–438. [Google Scholar] [CrossRef]
- Zhang, Z.; Chen, Y.; Liu, X.; Wang, W. Two-Stage robust Security-Constrained Unit Commitment model considering time autocorrelation of wind/load prediction error and outage contingency probability of units. IEEE Access 2019, 7, 25398–25408. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, J.; Zeng, B. Chance-constrained two-stage unit commitment under uncertain load and wind power output using bilinear benders decomposition. IEEE Trans. Power Syst. 2017, 32, 3637–3647. [Google Scholar] [CrossRef]
- Jia, Q.S.; Ho, Y.C.; Zhao, Q.C. Comparison of selection rules for ordinal optimization. Math. Comput. Model. 2006, 43, 1150–1171. [Google Scholar] [CrossRef]
- Wu, H.; Shahidehpour, M. Stochastic SCUC solution with variable wind energy using constrained ordinal optimization. IEEE Trans. Sustain. Energy 2014, 5, 379–388. [Google Scholar] [CrossRef]
- Ouyang, Z.; Shahidehpour, S.M. An intelligent dynamic programming for unit commitment application. IEEE Trans. Power Syst. 1991, 6, 1203–1209. [Google Scholar] [CrossRef]
- Wang, S.; Xu, X.; Kong, X.; Zheng, Y. Extended priority list and discrete heuristic search for multi-objective unit commitment. Int. Trans. Electr. Energy Syst. 2017, 28, e2486. [Google Scholar] [CrossRef]
- Shahbazitabar, M.; Abdi, H. A novel priority-based stochastic unit commitment considering renewable energy sources and parking lot cooperation. Energy 2018, 161, 308–324. [Google Scholar] [CrossRef]
- Wang, Y.; Xia, Q.; Kang, C.Q. Identification of the active integer variables in security constrained unit commitment. Proc. CSEE 2010, 30, 46–52. [Google Scholar]
- Zhai, Q.; Guan, X.; Cheng, J.; Wu, H. Fast identification of inactive security constraints in SCUC problems. IEEE Trans. Power Syst. 2010, 25, 1946–1954. [Google Scholar] [CrossRef]
- Berckmoes, B.; Molenberghs, G. Approximate central limit theorems. J. Probab. 2017, 31, 1590–1605. [Google Scholar] [CrossRef]
- Lee, L.H.; Lau, T.W.E.; Ho, Y.C. Explanation of goal softening in ordinal optimization. IEEE Trans. Autom. Control 1999, 44, 94–99. [Google Scholar] [CrossRef]
- Lau, T.W.E.; Ho, Y.C. Universal alignment probabilities and subset selection for ordinal optimization. J. Optim. Theory Appl. 1997, 93, 455–489. [Google Scholar] [CrossRef]
- Klaus, G.; Rupesh, K.S.; Jan Koutník, J.; Steunebrink, B.R.; Schmidhube, J. LSTM: A search space odyssey. IEEE Trans. Neural Netw. Learn. Syst. 2017, 28, 2222–2232. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).