Abstract
In a peer-to-peer complex environment, information is permanently diffused. Such an environment can be modeled as a graph, where there are flows of information. The interest of such modeling is that (1) one can describe the exchanges through time from an initial state of the network, (2) the description can be used through the fit of a real-world case and to perform further forecasts, and (3) it can be used to trace information through time. In this paper, we review the methodology for describing diffusion processes on a network in the context of exchange of information in a crypto (Bitcoin) peer-to-peer network. Necessary definitions are posed, and the diffusion equation is derived by considering two different types of Laplacian operators. Equilibrium conditions are discussed, and analytical solutions are derived, particularly in the context of a directed graph, which constitutes the main innovation of this paper. Further innovations follow as the inclusion of boundary conditions, as well as the implementation of delay in the diffusion equation, followed by a discussion when doing approximations useful for the implementation. Numerous numerical simulations additionally illustrate the theory developed all along the paper. Specifically, we validated, through simple examples, the derived analytic solutions, and implemented them in more sophisticated graphs, e.g., the ring graph, particularly important in crypto peer-to-peer networks. As a conclusion for this article, we further developed a theory useful for fitting purposes in order to gain more information on its diffusivity, and through a modeling which the scientific community is aware of.
1. Introduction
This document aims at describing the diffusion of information in the peer-to-peer (P2P) network related to a crypto, for instance Bitcoin, through a fundamental diffusion approach. The information could be anything, but the object of communication between agents (i.e., miners and users), and, to add context, it could be the hash calculation. This designates the processes which calculate hashes for mining blocks, given relevant remaining transactions to hash. More specifically, miners have the purpose of hash transactions within a list of transactions—the memory pool—which appear in the next block in the blockchain (). Each transaction circulates from node to node in the memory pool used for remembering all new transactions, and miners receiving new transaction lists, supposing no double spending, start to generate hashes to create the new block. To this extent, the hash calculation starts as long as miners receive the list of transactions, thus the hash calculation can be seen as the information of transactions diffusing along the network (see () for a more theoretical discussion). The more a miner receives transactions to be mined, the more he/she is likely to calculate hashes, i.e., the stronger the hash calculation. On the contrary, if there is a low amount of information, i.e., not so many transactions to hash, then the lower the amount of transactions are to be hashed, and the lower the hash calculation. Conversely, if the hash calculation is high, this means that the miner has likely received a long list of transactions ready to be hashed. The hash calculation is intimately linked to the hash rate, so we will name this type of diffusion: diffusion of hash rate. In another more economical context, the diffused information could simply be Bitcoin cash flows.
This is true only if all miners have equal power of computing hashes, which we know is not realistic. This is not an issue: the diffusion model should depend on each node, and we will need to incorporate a rate of creation of hashes to assign to each node. In essence, not only do we have a diffusion of hash rate, but also the creation of hashes, increasing the hash rate for each miner. Being able to derive the hash rate with respect to time and node is being able to predict such an evolution for all nodes, at a given time and context, which is one main motivation for this approach.
A simple but fundamental physics model of diffusion is given by the famous diffusion equation,
where h is the hash rate (or more generally, a ‘rate’ of information), t is the time variable, D is the diffusion coefficient throughout the network, and is the local hash creation rate. The operator is called the Laplacian operator. One may think we could handle this approach and solve the equation for h. However, what do spatial coordinates represent? It seems that the majority of physics fields where this equation applies contains spatial coordinates, which are real numbers with respect to a pre-defined coordinate system. This is not the case for a proper network.
This means we need to handle the diffusion theory on a graph. There have already been established approaches somehow related to the diffusion description on a graph, with many applications (e.g., ; ; ; ). We discuss some of the approaches for modeling diffusion on a network.
The paper () specifies an optimality approach for minimizing the maximum regret due to decision taken in an uncertainty environment, and specifically calculates the maximal regret through a linear program. This program has the advantage of considering the connectivity of the network, and the evolution of the information diffusion should be a relevant complement to describe the structure of the network. The paper () defends Hayek’s theory of private money, which, once applied to a state, should avoid a significant amount of private money within the population of this state and reduce the inequalities by means of further regulations through central banks digital currencies (CBDC). This imposes a certain structure in the network of exchanges: the current Bitcoin P2P network is distributed, and the application of this theory would make it change into a more centralized network. The diffusion properties may significantly change from one type to the other (see Section 7 for numerical illustrations), and our approach applies to both different types. The authors in the paper () model a P2P network as a bipartite graph, where one family is the set of files, and the other is the set of peers. This way of modeling allows to find an ‘S’ shape in the dynamic of the information diffusion, and such a shape is a strong expectation of the social networks community. The equations guiding the evolution are through the susceptible/infectious (SI) equations. There are underlying assumptions, such as the strong one: the constancy of population. The paper () engages a probabilistic approach of diffusion of files into a P2P network. In (), the diffusion methodologies applied to a P2P network are explicitly reviewed. If not based on the SI approach, the models are essentially probabilistic. Finally, the authors in () see the blockchain as a kind of Markov chain.
Interestingly, all the mentioned approaches overall focus on probabilistic modeling for the diffusion processes on a graph. This present study proposes to focus on the more fundamental aspects of the diffusion behavior, mainly governed by an equation of the style of Equation (1). It is worth stressing that the operator is very general, and can be the source of randomness through, for instance, non-linearities, bringing chaos into the system. However, one possibly can also include probability in , which would make the present study very general. More conceptually, can gather any network specificity, such as its consensus, since it is related to sources of information.
However, some definitions already introduced in some of the previous studies, and including the Laplacian operator, may need to be further discussed, especially from a more intuitive and fundamental view of sharing information between two vertices of a graph. This is especially true when the graph is directed. Thus, in the context of diffusion on a P2P network, we need, for deriving the appropriate diffusion equation, to introduce the derivative and the integration on a graph, for a function f defined on each node x at a given time t. The Laplacian operator will follow. One understands that deriving the appropriate diffusion equation is a task in itself. Then, once derived, we need to solve the equation, which represents another task. In addition, we will see that there are different possible Laplacian operators for a diffusion theory (at least two), and we will focus on them separately. We will need some linear algebra tools to do it, as a graph is equivalent to its adjacency matrix, and, conversely, any matrix gives a (weighted) graph.
We now discuss the two hypotheses made (and mitigated) in this study. The first one is that graphs are undirectional. This is a strong assumption, as it means that once a vertex agent receives information that it did not previously have, then it will give back part of it to the source. Although this might be convenient in the context of bitcoin exchange (Alice sends some bitcoins to Bob, but also to herself, i.e., she generates new addresses she owns to send part of the total amount of bitcoins), a piece of information, whatever its type, has no reason to come back to its source. Considering that a directed graph is essential if we need to describe the interactions within a P2P network, this is what we do in this paper, and this constitutes the main innovation of the present study.
Another hypothesis is made in this modeling: when a vertex agent receives a piece of information, he/she immediately treats it and diffuses it to its neighbors. In other words, the response to the information reception is immediate. This is also a strong assumption, as, for instance, cash flows are performed in a delayed manner. Thus, Alice sends some bitcoins to Bob, but Bob does not immediately send a part (or more) of it to Charlie. In fact, the immediate response is the straightforward consequence of the structure of the diffusion equation, whose solutions are a differentiable function of time. It turns out that one way to make a non-differentiable solution at some given times is to introduce time dependency in the Laplacian operator, and the Heaviside function (whose value is 0 below a given time, and 1 above it) is a relevant candidate for differentiability breaking at selected points in time. Introducing Heaviside functions in the Laplacian operator is a much easier task in the context of graph modeling, for the reason that there are no discontinuity issues for the variable x, usually continuous, and here being discrete (and representing the node index). We engage this point of view at the end of the study.
The rest of this paper is depicted as follows. Section 2 is an introduction to the modeling, with many fundamental definitions which will imply the Laplacian ones, as well as the diffusion theory. Section 3 derives and solves the diffusion equation defined on an undirected graph. It is worth pointing out that the two previous sections are strongly inspired from (). The rest of this paper constitutes the main innovations. Section 4 introduces two different types of equilibrium notion, the standard one () and the blockchain one ( min for Bitcoin), as well as some conceptual links between both. Section 5 shows the implementation of the derived solution in Section 3. Section 6 is an important generalization of the approach done thus far: it introduces the diffusion equation and its resolution in a directed graph, very important properties of the P2P network as already discussed above. Section 7 shows numerical illustrations of the previous section for several famous networks (including the Erdos–Reyni network, or the binary tree). Section 8 is the direct implication of the previous directed graph case when there are boundary conditions, typically certain vertices constantly sending information to the rest of the network. Finally, Section 9 includes delay in the response of nodes when they receive information. The last section concludes the study.
2. Modelling the P2P Network
2.1. Introduction to Graph Theory
Let be a graph, that is a set of nodes E and a set of hedges V, composed of pairs of nodes in E. Thus, if , i.e., x is a node of G, and is another node of G; if , we say that the nodes x and y are connected in G. We suppose that G is connected (that is, there exists a connection between any two nodes of G), unoriented (x to y or y to x is the same) and unweighted (all the paths are equally effective); this last hypothesis may be relaxed in the future. An example of such a graph is shown in Figure 1.
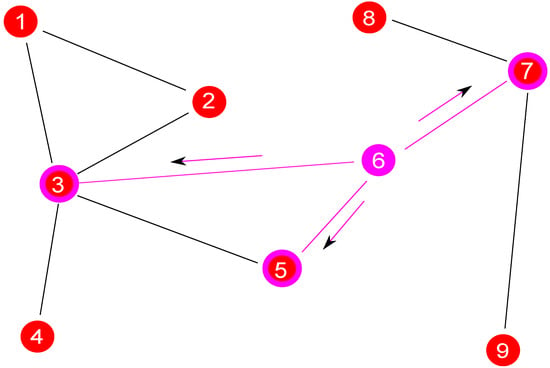
Figure 1.
Illustration of a graph. The balls are nodes, which are connected by edges, the segments. Here, nodes have between one and four neighbors. In particular, node 6 diffuses information (e.g., list of transactions) to its neighbors, i.e., nodes 3, 5, and 7.
There is a matrix equivalence for such a graph. Node 1 is connected to nodes 2 and 3, in Figure 1, but not to any other node. We can represent the graph G by a matrix A, which is named the adjacency matrix. If we arbitrarily label nodes with numbers, the adjacency matrix for the graph G in Figure 1 is given by
The first row corresponds to the connections of node 1. Node 1 is connected to nodes 2 and 3 only, so columns 2 and 3 for the first row prints 1; otherwise, it prints 0, and so on. The diagonal (from top left to bottom right) of this matrix is composed of zeroes. It actually turns out the this matrix is symmetric (i.e., with respect to its diagonal). In this example, E is isomorphic to —we will identify both sets if there is no ambiguity—and the element of A is 1 if for .
Studying the matrix A or the graph G is therefore equivalent, and the P2P network could indeed be represented this way. In addition, in Figure 1, node 6 spreads the information of new transactions to nodes 3, 5, and 7. Node 6 starts to hash first, and then nodes 3, 5, and 7 start once they receive the information: the ‘hash rate’ propagates. Here, node 6 firstly computes hashes (purple), and secondly nodes 3, 5, and 7 compute hashes (they become purple). This approach generalizes to all the nodes that create hashes, i.e., diffuses list of transactions to other nodes as well as starting to compute hashes, and therefore will make its neighbors compute hashes.
The arising question is, how is the diffusive process of such hash information, i.e., can we describe it and thus allow a prediction? The answer is yes.
2.2. Derivative
We need to introduce the derivative and the integration properly before doing anything else. It is worth noting that significant effort has been made to get closer to the notations involved in the differential calculus. From now on, the sequence of this paper will be mathematical, unless specified otherwise. The diffusive quantity of interest, here the hash rate, is given by the function f, function of nodes and time .
In the following, we focus on a graph with associated adjacency matrix ( nodes). The graph G is connected, unoriented and unweighted so that the matrix A is symmetrical, and its elements are in . We finally call the set of all neighbors of , and we write the degree of x, i.e., number of neighbors of x, and we call the volume of the graph G. We write or equivalently in the sequence.
Definition 1
(Derivative). Let f be a function of in .1 The directional derivative of f from to is given by
The operator is a linear map of f, for any .
Figure 2 represents the derivative. The rest of the definitions depend on this, so it is important to well understand this last one.
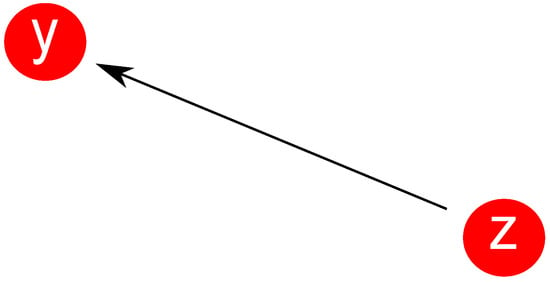
Figure 2.
The of f from z to y. This actually represents the (finite) variation of f for the information going from node z to node y. It is positive if y gets more information than z, and negative otherwise. This concept makes sense only if y and z are neighbors; hence, the presence of in the definition.
Definition 2
(Gradient). Let . The gradient of f at is the vector given by 2
The gradient at a node is the collection of directional derivatives toward this node.
Definition 3
(Laplacians). Let . The normalized Laplacian of f from to is given by
while the non-normalized Laplacian of f from to is given by
The global normalized Laplacian of f at x is given by
while the global non-normalized Laplacian of f at x is given by
(or ) is said to be the Laplacian of f.
The Laplacian of f is the average of the second directional derivative of f at node x, while the Laplacian L of f is the average of the second directional derivative of f at node x. We then could define the following operator:
Definition 4
(Divergence). Let and , be functions. Define the vectorial function . The divergence of f at is given by
or
depending on whether we choose L or Δ.
This is the sum (or average) value of f for a given node, the average being taken at each of the considered node’s neighbors.
Proposition 1
(Div of grad is Laplacian). For any , we have
depending on whether we choose or for the definition of the divergence.
Proof.
Note that, for all , we have
Since , we therefore have that . It turns out that , or . □
Thus, we note that , and it turns out that , for any . A straightforward but essential property for the Laplacian is depicted as follows.
Proposition 2.
Let . The Laplacians of f at satisfy the following property:
Thus, the Laplacian of f at x is the value of f at x, minus the average value of f taken by all its neighbors.
Proof.
From the definition, and since if and only if , we have
which implies the results. □
This actually allows to introduce the Laplacian matrix.
Definition 5
(Laplacian matrix). The non-normalized Laplacian matrix is given by
where A is the adjacency matrix, and is the diagonal matrix of degrees.
The Laplacian matrix is given by
where 1 is the identity matrix.
Contrary to any other field in mathematics, there are no criteria of derivability. The function just needs to be defined at the two considered points.
2.3. Integration
After having defined the derivatives, we have to define the integration.
Definition 6.
Let . We introduce the map scalar product of f by h on any sub-graph of G, as follows:
The following proposition is straightforward, but fundamental.
Proposition 3
(Scalar product). The map is a bilinear form from to , for any . This justifies its name scalar product. Thus, the family is said to be a Euclidean graph.
In the following, the graph G is always considered a Euclidean graph.
Definition 7
(Integration). Let . We introduce the integration of f on any sub-graph of G, as follows:
is a measure on G by .
Here again, the function, to be integrable in g, just needs to be defined on g. The previous and following properties are still satisfied for a function .
The above definition actually is consistent with integration by parts.
Proposition 4
(Integration by parts). Let . We have
Proof.
We calculate
We now have all the tools to develop the diffusion theory on a network, which is the object of the next session.
3. The Diffusion Equation
3.1. Derivation of the Equation
In order to derive the diffusion equation, we need the following essential proposition. In the sequence, we call the number of hashes produced per miner, as a function of nodes and time.
Proposition 5.
The density of the current of hashes from at at time t is given by the following law of diffusion:
where is the diffusion coefficient of information.
We indeed assume that D is constant and is a network characteristic. Despite the fact that this law is very intuitive and is a typical Fick law (the information goes toward where there is not any information yet and hence the negative sign), further developments need to be made to rigorously justify this equation in the context of the network. Let us write the vector j at x and t. Thus, represents the flow of information from z to x.
Here is the first important result of the paper.
Theorem 1.
Let represent the information function. If D is the diffusion coefficient and the creation function of the information, the following diffusion equation holds for any and :
Separately, the following diffusion equation also is valid
As long as one remembers that it is local, these equations can simply be written as
The minus sign is actually a necessity for the system to be described as diffusive, and not an explosive one, contrary to standard math and physics systems.
Proof.
On the one hand, let be the quantity of hashes produced during the infinitesimal variation of time , at node . The hash rate is the flux of rates given by , and the number of such hashes produced per neighbors, for node , from time t and , is . It turns out that
On the other hand, node x (i) receives the diffused information from its neighbor, implying hashes, and (ii) can create (or destruct) information, implying hashes. We therefore must have the following conservation of information:
On point (i), the quantity of information entering into node x is provided from all its neighbors, and thus . On point (ii), we introduce the creation rate per node at node x and time t, which is the rate per node per second hashes are calculated. We therefore have .
Bearing all the above in mind, Equation (23) becomes
Equivalently,
or
According to Proposition 5, we have or , which does conclude the proof. □
3.2. Laplacian Matrix: Eigenvalues/Eigenvectors
3.2.1. Quick reminder: Eigenvalues/Eigenvectors
Let be a graph, with nodes and the adjacency matrix A, and . We say that is an eigenvalue of F if the function ( is the identity map) is not injective, which means that there exists a vector , named eigenvector, such that , or component-wise for . The function F has n eigenvalues, which we write , , …, , the index being chosen such that . To each eigenvalue , we associate its eigenvector , for all .
Separately, the function F can be seen as a matrix M, and the above equation is thus written as , or component-wise . We adapt to the matrix viewpoint in the following. If M is symmetric, then it is diagonalizable and is an orthonormal basis of , that is
where is the Kronecker symbol.
3.2.2. Laplacian: Eigenvalues/Eigenvectors
The above applies to the Laplacian matrix (see Definition 5). For instance, the non-normalized Laplacian matrix for Figure 1 writes as
The matrix L is symmetric and positive (semi-)definite. We write the eigenvalues of the matrix L such that with the associated eigenvalues , forming an orthonormal basis of . The normalized Laplacian matrix writes
The matrix is only positive semi-definite.
In the sequence, we focus our attention on the matrix . This matrix is positive semi-definite, but also, since , it is symmetric. As an example, we have
We write the eigenvalues of the matrix such that with the associated eigenvalues , forming an orthonormal basis of . The graph G is fully connected; therefore .
It is interesting to further develop the eigenvector associated with the eigenvalue . Set as the eigenvector of L associated with the eigenvalue (same common eigenvalue between L and ). In addition, we have ; hence, , which implies that with the appropriate normalization.
Actually, we easily can establish that
It turns out that , and with the appropriate normalization, we finally have
Two additional points to bear in mind are that is equivalent to by construction; therefore, both matrices have the same eigenvalues. Finally, since , then, according to Sylvester’s inertia theorem, and L, and thus , have the same number of negative, zero, and positive eigenvalues. Further developments can be done here.
3.3. Resolution of the Equation
We need the following lemma
Lemma 1.
The operator L is self-adjoint, in the sense that
In addition, the operator also is self-adjoint
Proof.
The first two equations have proofs very similar to the one for Proposition 4. We thus focus on and .
First we note, for any , that
It turns out that
Bearing this in mind, we calculate
Here is the second important result of the paper. We have the following analytical expression for the hash rate per node.
Theorem 2.
The solution for the diffusion Equation (21) is given by
with .
The solution for the diffusion Equation (22) is given by
with .
It is worth pointing out that these analytical solutions easily are implementable in a computer.
Proof.
We first focus on the solution for Equation (21). We decompose into the basis of made of eigenvectors of the matrix L.
where, for all , we have
We have
Implementing Equation (35), we have
We can easily solve this differential equation, and we have
We obtain the final result by placing the previous equation to Equation (35).
We now focus on the solution for Equation (22). We decompose into the basis of made of eigenvectors of the matrix . The rest of the calculation remains exactly the same as below, with the additional trick . □
We note that , for any and . It turns out that if , using L or leads to the exact same result.
Corollary 1.
The solution for the diffusion Equation (21) is written as
where is the diffusion propagator for the matrix L, and is such that
We also have
The advantage of this last expression is the explicit dependency of f with respect to the initial condition on all the nodes of G, i.e., with for all .
Proof.
We derive the expression for the matrix . From the general solution expression, we have
Therefore, we have
Implementing into the main solution expression, we have
Some re-ordering leads to
This explicitly is what we are looking for. A variable change will lead to the result. □
Remark 1.
We have
where if and 0 otherwise: the same for matrix L. We also have
in which case does not depend on x. We also found an interesting interpretation for the eigenvector . Indeed, we have
Therefore, represents the propagation of information due to the diffusion, to node y.
The next two sections deal with further developments on the implications of the facts established above. This also holds for the operator L.
4. Standard Equilibrium and Blockchain Equilibrium
The equilibrium is an important aspect of the current paper. We identified two types of equilibrium, which we further develop here. The zero eigenvalue as well as its eigenvector will play an important role, as we are going to see.
4.1. Standard Equilibrium
4.1.1. Integrable Creation Destruction Function
The standard equilibrium corresponds to the steady state, i.e., when . It is expected to have permanent exchanges between nodes at the same rate, which is exactly equivalent to the fact that each node keeps having the same quantity of information, i.e., the same quantity of hash generation.
More specifically, we have the following proposition.
Theorem 3
(Standard Equilibrium Framework). Let f be solution of the diffusion Equation (1). We assume that is integrable on for any , and
Then the standard equilibrium state corresponds to:
We have a similar result by considering the matrix L.
Proof.
From the expression
we see that all the terms cancel since , except the last one. Thus
This does not depend on x. We then start from the following equation
Hence,
The previous equation is the most general one. We come to the factor between parenthesis. The previous equation is then
We now focus on the Equations (40). We will prove that , for all and , which will prove Equation (41). A variable change gives
Bearing this in mind, for , we have
that is
Hence with C function from G to , and , for any . It turns out that for any , we have
Hence, for any and , we have
Hence
By a variable change and using triangular inequality, we have
In other words, we have
Suppose now that is such that
Then we have
Therefore,
which concludes the proof. □
For example, set , where P is a polynomial and with some restrictions that we need to discover.
Let . A quick calculation allows to establish that
If we set , then we deduce that
We deduce that, for to be finite, we need to have , while without restriction, and the degree of P is in . However, if , then we necessarily need to have . The less negligible function is thus , which is the only form giving a nonzero .
Remark 2.
Equation (40) is actually close to the one found by applying the mean value theorem, provided is continuous for any : there exists such that
Thus, , with .
Remark 3.
General function theory might be interesting if one decides to break the assumption that is continuous.
4.1.2. Continuous-by-Parts Creation Destruction Function
If we require the solution f to be continuous at all times, then, according to the diffusion equation, must be at least continuous by parts. In this case, the function is continuous by parts, for any , i.e., there are some points on the time axis where the function is not continuous (discontinuity of first kind). In this case, for any , the function still is integrable on .
4.2. Blockchain Equilibrium (Approximation)
In fact, we have to consider that time is discretized, i.e., subdivided into interval of time which are of length 10 min approximately. Ten minutes is the average time needed for a miner to mine a new block in the Bitoin blockchain (), and this could be changed to 15 s for the Ethereum blockchain. We will go to deeper detail to this point in the future, but approximately every 10 min, the blockchain equilibrium equation is satisfied. The following are functions of interest:
- —b-block reward;
- c—cost per hash, supposed to be constant;
- —price of one Bitcoin, in USD, at time t;
- —fee for transaction , where I is the set of all transactions that will be stacked into block b;
- —number of hashes in the network, for block b.
From these five variables, we can easily compute the revenues for block b, as follows.
We can compose the costs, more precisely the expected costs , for block b, as well:
We have the blockchain equilibrium equation:
Thus, is connected to , which gives the cost for forming a block. We can, in fact, make the assumption that the circulation of transaction lists within miners is very fast: it takes approximately 1 millisecond for the nodes to receive the transaction list from an original list. It is relevant to assume that the diffusion happens very fast once one miner has a transaction list to be sent, and that the diffusion coefficient D is very high. This is the blockchain equilibrium approximation: , for any time t.
In other words, is so high that , for any . Only the term corresponding to survives.
Proposition 6
(Blockchain Equilibirum Approximation). Let f be solution of the diffusion Equation (1). We focus on , where T is set to be 10 min. Then the blockchain equilibrium state corresponds to
We have a similar result by considering the matrix L.
It turns out that , which does not depend on x, is the same for all the nodes.
Proof.
We have
and
We deduce the equation from
which concludes the proof. □
Thus, is to be associated to . Finally, in essence, the standard equilibrium and blockchain equilibrium give the same results. In the following, ‘’ refers to the function at the equilibrium state.
5. Undirected Graph: Case Studies
5.1. 2 Nodes
As a quick application, suppose , only two nodes, and , one connection. Suppose , , . We have , , and
We can calculate the eigenvalues and eigenvectors for the network. The non-normalized Laplacian matrix is given by
and the Laplacian matrix by . The eigenvalues are and , and the eigenvectors are and . We finally obtain
See Figure 3 for a plot of these two solutions.
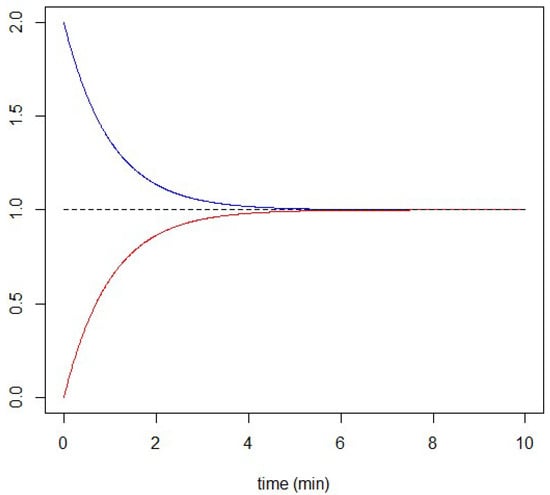
Figure 3.
Illustration of the diffusion information for 2 nodes. The initial conditions are , , and . We set , and . Blue is for , while red is for .
The equilibrium is therefore given by
Finally, due to the diffusion effect, both nodes share the same information at the equilibrium.
5.2. 3 Nodes
We set that and . The non-normalized Laplacian of such a matrix is
and is
The eigenvalues of are the roots of the polynomial , that is , , and . The eigenvectors are , , and .
We set . In order to be very explicit, the propagators are written as, for ,
for
and for
Therefore, we have
Figure 4 plots the evolution of the three functions.
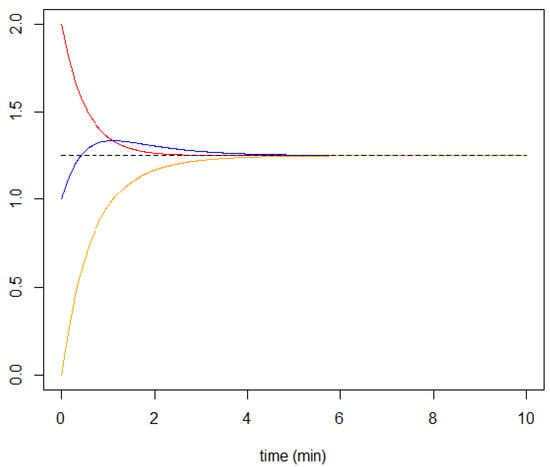
Figure 4.
Illustration of the diffusion information for 3 nodes. Node 2 is connected to nodes 1 and 3, but nodes 1 and 3 are not connected. The initial conditions are , , and . We set . Blue is for , red is for , and yellow is for .
The equilibrium state corresponds to the following expressions.
We are now going to propose the solutions for specific P2P networks. It is worth stressing that implementation of the above in a prototype is in progress.
6. Generalization to Directed Graphs
This section focuses on the generalization of what has been seen so far, but applied to a directed graph. Concretely, information between different layers of the whole Bitcoin network is directed. A very simple example is that the users layer is sending information to the P2P network as transaction lists, and they do not expect any information back to them since they are not miners. The diffusion is thus directed. This breaks the symmetry of the adjacency matrix, which is not diagonalizable anymore. Thus, we could handle a more general framework to perform the diffusion. So far, we may handle with straight numerical solutions for the implementation, but we are going to see that we can derive an analytical solution base on the singular value decomposition (SVD).
Definition 8
(SVD). Let be a matrix of size , with . Then, A admits the following decomposition:
where U and V are orthogonal square matrices of size n and m, respectively, and is a 0 matrix, except its diagonal elements, which are non-negative numbers.
If , we have
If is a diagonal matrix . The numbers are the singular values of A. The columns of matrices U and V are the singular vectors of A.
6.1. Matrix Exponential and Adjoint of the Laplacian Operator
As a reminder, we need the following three definitions.
Definition 9
(Exponential of Matrix). Let for . The of the matrix A is given by
We write for .
Definition 10
(Hyperbolic Cosine and Sine of Matrix). Let for . The hyperbolic cosine of the matrix A is given by
The hyperbolic sine of the matrix M is given by
It turns out that
Definition 11.
Let T be a (linear) operator and be a subgraph. The operator of T is such that
for any . The adjoint operator is the transposed of the associated matrix.
6.2. Solution for the Directed Diffusion Involving the Operator L
6.2.1. Intuition
In case of the directed network, the diffusion also is oriented. To gain intuition, suppose there are two nodes x and y, so that x is connected to y, but not the converse. In this case, the adjacency matrix writes
so that the non-normalized Laplacian matrix is
In addition, the node x loses information, while y gains the same amount of information that x loses. Therefore, at any time , the conservation of total information is satisfied:
Since x loses information but in a diffusive effect such that the more information it has, the more it gives, we must have
Solving this equation leads to
so that
This is the solution of the differential equation:
Introducing the vector , we thus obtain the following system of differential equations:
6.2.2. The Directed Diffusion Equation Involving L
Definition 12.
Let representing the information function for a graph with n nodes. If D is the diffusion coefficient and the creation function of the information, the following directed diffusion equation holds, for any :
We have the same Equation (21) if and only if , that is, if and only if A is symmetrical.
6.2.3. Solution Involving L
From Equation (12), we can use the Cauchy theorem to obtain the following solution.
Theorem 4
(Application of the Cauchy Theorem). The solution of the related Cauchy problem associated with Equation (12) is given by
This expression is straightforwardly implementable in a computer. As a tip, we would rather use the following equation:
The advantage of this equation is to force step-by-step dependency of configuration at time , for any time t, for the increment . See Section 8.3 for a practical implementation from this equation.
6.2.4. Analytical Solution Involving L
The reader may find it useful to derive an analytical solution based on SVD.
Theorem 5.
Let be the SVD of L (here is indeed square), and let and be the columns of the matrices u and v, respectively. The solution for the directed diffusion Equation (52) is given by
where
with , and
Proof.
From the SVD , we deduce that and . This means that u and v are the matrices of eigenvectors of the symmetric matrices and , respectively, which thus are diagonalizable matrices. Therefore the columns of u and v form an orthonormal basis of . We can decompose the function f on those two bases:
Set . On the one hand, we have
The left-hand-side gives
The right-hand-side gives, after some calculations
This leads to
On the other hand, we have
The left-hand-side gives
The right-hand-side gives
There is the supplement term . We calculate it below.
We have
Let . Some calculations lead to
Finally, we obtain
The system to solve is, therefore,
We are now facing a system of differential equations, first order, non-homogeneous, with constant coefficients. In fact, we can solve this system of equations using a matrix approach.
First, we note that
Next, we set
also
and
The system of differential equations then becomes
The Cauchy theorem leads to
We can go further. We are calculating the powers of the matrix , as follows. In fact, we can prove by mathematical induction that
Therefore
which we can write as
This achieves the proof. □
As a simple verification, what does this theorem become if we set L to be symmetric? We would then have , for any , and , so that and . In addition would be diagonal and , i.e., . Then
and, if , we have
This conforms to the previous theorem’s relevance and truth.
6.3. Solution for the Directed Diffusion Involving the Operator
6.3.1. The Directed Diffusion Equation Involving
Definition 13.
Let represent the information function for a graph with n nodes. If D is the diffusion coefficient and the creation function of the information, the following directed diffusion equation holds for any :
We have the same Equation (22) if and only if , that is if and only if A is symmetrical.
6.3.2. Solution Involving
Theorem 6
(Application of the Cauchy Theorem). The solution of the related Cauchy problem associated with Equation (13) is given by
This expression is straightforwardly implementable in a computer.
6.3.3. Analytical Solution Involving
Similarly, we can prove the following theorem.
Theorem 7.
Let be the SVD of (here Σ is indeed square), and let and be the columns of the matrices U and V, respectively. The solution for the directed diffusion Equation (57) is given by
where
with , and
7. Directed Graph: Case Studies
This section shows simulations for important graphs.
7.1. Erdos–Reyni
The Erdos–Reyni graph is uniformly random: fix the number of nodes and edges. Then the connections are all random. Figure 5 shows a simulation.
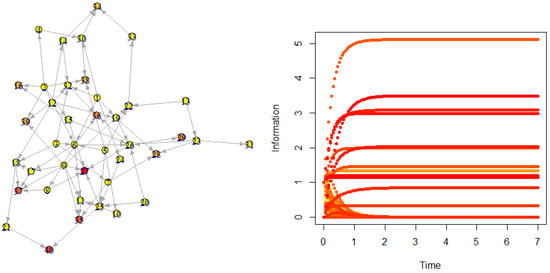
Figure 5.
Diffusion on a directed Erdos–Reyni graph.
There might be counter-intuitive facts, e.g., the node which has a high number of neighbors is not necessarily the most influential in the network. The influence depends on connectivity, but also on a given network configuration, as distribution of information among all the nodes.
7.2. Binary Tree
The binary graph is the simplest hierarchical structure on graphs: every node has two children. Figure 6 shows a simulation.
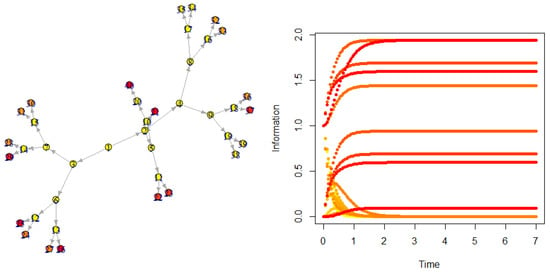
Figure 6.
Diffusion on a directed binary tree.
In the standard configuration as in Figure 6, the information is circulating from parents to children. We, however, observed (as in Mandala networks) the other possible direction.
7.3. 4-Tree
Figure 7 shows a simulation.
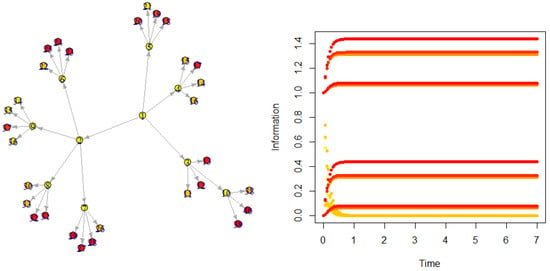
Figure 7.
Diffusion on a 4-tree.
7.4. Ring Graph
The ring graph is the simplest cycle on a network. Cycles are a very important aspect of graphs: they allow to extract seasonality patterns for a given context. Figure 8 shows a simulation.
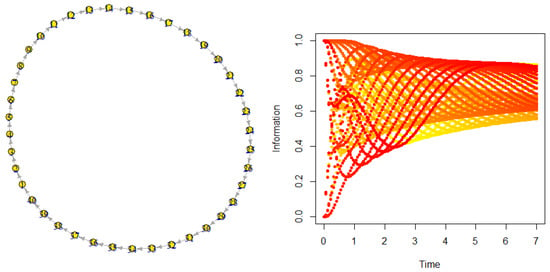
Figure 8.
Diffusion on a directed ring.
The most important characteristics we observe is the envelope: the cycle behaves as two distinct sub-systems which interact continuously up to the dissipation level. One sub-system gives the information to the other, which receives it, and vice versa.
8. Layers Constantly Giving Information
8.1. Motivations
This section deals with an important aspect of the Bitcoin network. There are different families (layers) of nodes in this network. In fact, the P2P network is a subnetwork of the whole system. There is, in addition, the layer of users which may send information (e.g., a transaction) to the miners so that they mine it. There also is the layer of exchanges, which sends in the blockchain any information which may be about public key diffusion, or even collects prices from different exchanges. In particular, an exchange needs to be in the center of the whole network, communicating to nodes of all the layers by sending and receiving all types of information. Such a complex system could in fact be simplified and illustrated in Figure 9. If the related graph is directed, then the layers are said to be directed, and the layer which receives information from others, and whose nodes exchange information with each other, is named the main layer. A graph configuration where the main layer is the layer of miners could represent all the list of transactions diffusion from users to miners, and also between miners (see Figure 9), whereas if the main layer is the layer of exchanges, the resulting diffusion model would describe all the interactions (i.e., emission/reception) of data from users, exchanges, and miners, the exchanges could have. In particular, this graphical representation of an exchange should genuinely reveal, in a clear way, the whole flow of information dealing with the exchange. The diffusion model, for a given time condition, should predict the evolution of information propagation all around the network. Modeling this is the object of the current section. Surprisingly, bearing in mind the previous section, the result is simple.
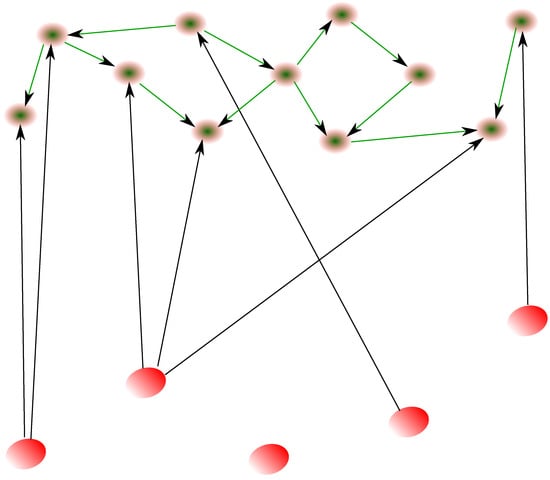
Figure 9.
Two directed layers, i.e., families of nodes. The red layer sends information toward the green layer, while nodes of the last layer send information to each other. Thus, the green layer could represent the layer of miners, while the red layer could represent the layer of exchanges. In such a model, the miners are the main layer. We could easily change the configuration so that exchanges are the main layer, and the following theory also applies.
8.2. Directed Diffusion with Boundary Conditions—Analytical Expression
Let be the main layer (the green layer in Figure 9), and (the red layer in Figure 9) such that and . We keep the notations in the previous sections. The following theorem is the Theorem 5, with an additional boundary condition.
Theorem 8.
Suppose L is written as
where, in particular, is the Laplacian of the sub-graph S with singular vectors and . Suppose , fixed and known, for any (boundary condition). Then, Theorem 5 applies to the sub-graph S, by replacing with , and with , where
Proof.
Let be the singular values for , and let and be the singular vector matrices for . In fact, we set if , idem for , for any , so that and are n-dimensional vectors.
Bearing in mind the proof for Theorem 5, we need to set
On the one hand, we have
Thus
Identically, we have
In particular, the last term is written as
The same calculations performed as in the proof for Theorem 5 actually allow to conclude. □
Remark 4.
When the exchanges constitute the main layer S, two other layers could be of interest, the layers of users (customers) and the layers of miners , so that the whole network G is such that , and . Setting , we deduce that Theorem 8 applies to the layer S of exchanges, and, considering the two distinct sources , we specifically have
8.3. Directed Diffusion with Boundary Conditions—Practical Case
The previous section demonstrates that any boundary condition must be considered as a constraint to the nodes whose neighbors are boundary nodes, multiplied by the diffusion coefficient D. Figure 9 thus becomes the object of Figure 10.
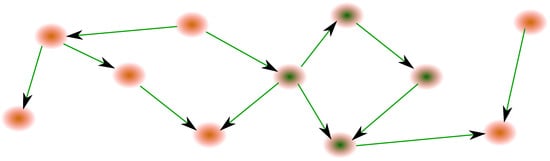
Figure 10.
Provided that the red-nodes layer plays the role of boundary condition layer in Figure 9, the two directed layers network is mathematically equivalent to one unique network, whose node neighbors with the boundary layer nodes have a reaction term applied for the diffusion of information.
Basically, each contrainst node has a stronger diffusive effect toward the rest of the network. More specifically, since (supposing sufficiently small)
and from Equation (54), we can set
where is the error committed by the approximation. In practice, the approximation is sufficiently good if second such that we set . Provided that is of class , we indeed have an error of
If the function is sufficiently smooth, then
In practice, we shall have so that the error never exceeds such that the equality is justified, for any x.
Figure 11 plots a diffusion without the creation/destruction () of a graph, where the information is provided by node 1, and diffuses up to node 10 (without ever reaching 11). Note that nodes 2 and 3 (respectively, 5, 6, and 7) play symmetrical roles and have the same information amount through time.
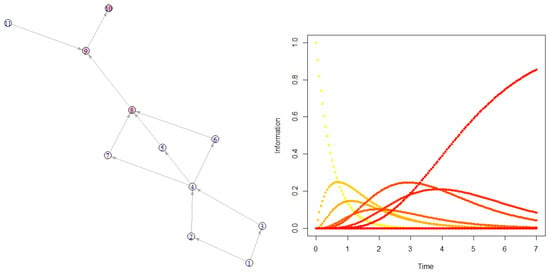
Figure 11.
The information diffuses from node 1 ( while for any ) to node 10. Here, and .
We now add the constraint such that
In words, node 2 is constantly fed by external layers with a rate of r (creation) if it does not have a sufficient resource, while node 10 is constantly feeding external layers with a rate of (destruction) if it does have too much of a resource. We choose rates .
With a cubic spline smoothing, we may observe that so that .
Figure 12 shows the simulation.
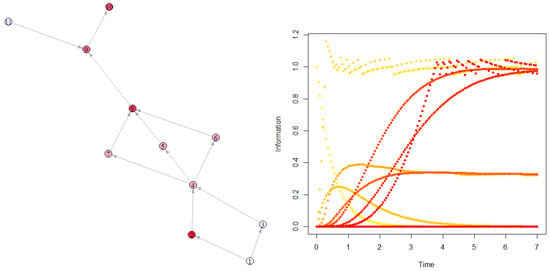
Figure 12.
The information diffuses from node 1 ( while for any ) to node 10 with additional creation (to node 2) and destruction (to node 10) added. Here .
It is interesting to note the literal change of behavior by applying such constraints. Node 2 is submitted to permanent oscillations around 1 with a frequency-decreasing transition regime, so node 10 once it reaches information higher than 1. The oscillations induced at node 2 transfer visible oscillations to node 4, but the diffusion is not sufficiently strong to see them.
We therefore increase the diffusion coefficient D from 1 to 5, then to 10, and Figure 13 shows the simulations.
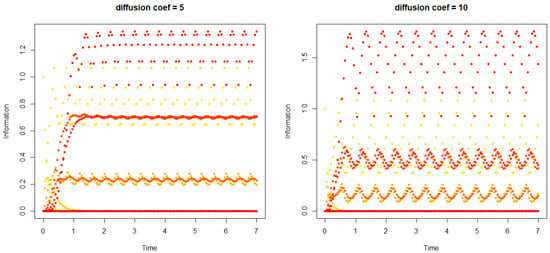
Figure 13.
The information diffuses from node 1 ( while for any ) to node 10 with additional creation (to node 2) and destruction (to node 10) added. Here (left panel) and (right panel).
For all intermediate nodes, oscillations of information are observed at a frequency identical to the one imposed by node 2 reception. Concretely, it means that one node providing constant information to the others without exceeding its resources is governing the dynamics of the network. The shift of the minimum and maximum values at the permanent regime is due to the delay to obtain the information, and the shift is higher if the node is more distant from node 2.
In fact, the graph in Figure 12 and Figure 13 behaves as a cycle: nodes 2 and 10 could be connected to each other through an intermediate set of layers. This means that cycles are maintaining oscillations through a permanent regime. These oscillations are importantly induced by one parameter: the diffusion coefficient D, which therefore appears as a bifurcation parameter (its value determines chaotic behavior in the network).
9. Delay in the Differential Equation
So far, there has been an immediate response from a stimulation of the network. However, time lags are essential to consider since response to the information never is automatic: there is a response time to understand the information and find an appropriate answer, from the human as well as machine viewpoints. It is essential to find a way to describe delay in the study.
Generally speaking, a delayed differential equation—an active topic of academic research nowadays—for the above diffusion equation could be written as a delayed-response diffusion equation:
where is the time lag for the answer of the system due to diffusion effects. Usually, the function , for any , is defined on and is given on .
Although there are methods for solving such an equation, we may develop some technics to make an easy implementation in the following. One trick is to make L time dependent, as we are going to see.
9.1. Time Dependent Laplacian
The adjacency matrix may be time dependent, as nodes can change their configuration through time. In the concern of expressing the time-dependent Laplacian matrix with respect to exclusively, we note that
and the Laplacian matrix is rewritten as , which behaves as a functional of the matrix .
Bearing this in mind, a way to introduce delay in a graph system is to make connections at a given time . Without any loss of generality, we suppose that node , for a fixed , is an isolated node at time , then gets connected to, say, (from k to r) in the network, from time .
This makes the adjacency matrix time dependent, since
where is the Heaviside distribution.
Thus, we can prove that the diagonal element of L is , while . In this configuration, we therefore have
where is zero everywhere, except at element , where it is equal to , and at its diagonal element , which is equal to . We actually can generalize the above approach to the following proposition.
Proposition 7.
If nodes are connected to , …, and , respectively, at times , …, and , respectively, then
where is zero except element which is , for all , and either element if the connection is from to , or element otherwise, whose value is , for all , .
Thus, the matrix behaves as a Laplacian matrix whose elements are either 0 or Heaviside distributions.
The idea now is to find a solution with the Heaviside distribution as a kernel.
9.2. Definition Set for the Solution and Its Derivative
From the previous Section 9.1, the diffusion equation is written as
It is worth stressing that the matrix is not defined at times when an evenness occurs, which therefore implies that f is not derivable on those points. It turns out that f is of class almost everywhere (and not everywhere), provided that is continuous almost everywhere as well, but still is required to be continuous at all times. If the study starts at and there is no connection between distant nodes, then and the equation simplifies to
which has the usual form.
9.3. Simple Cases
9.3.1. Heaviside integration
Suppose we would like to calculate
where g is a continuous and integrable function. Let
up to a constant. Then
By integration by parts, we have
true up to a constant , and we thus can write
9.3.2. Simple Case of Two Nodes
Suppose in , the network is composed of two nodes. Without creation/destruction, suppose that node 1 sends information to node 2 from time . The Laplacian matrix is written as
This equation is just from the diffusion equations given by the system:
Note that we can rewrite this function as
Then putting this expression into the second equation and using the fact that , we have
Using again Equation (67) with , we have
This behavior is the one expected.
9.3.3. Simple Case of Three Nodes
The case of three nodes might be of particular interest as well. We could break the symmetry by supposing that node 1 sends information to node 2 at rate from time , and to node 3 at rate from time . The Laplacian matrix is written as
This equation is just from the diffusion equations given by the system:
Deriving is the most complex task here. First of all, we note that , and then we have
We deduce, from Equation (67), that
The continuity of the function at times and allows to find an equation for and one for . We therefore derive the function given by
We now derive expression for . We find that
The resolution leads to
It is interesting to note that the symmetry is broken in the long-run
and, quite importantly, we can demonstrate that
The conservation of information is held at all time.
9.4. Delay in the Differential Equation—Practical Case
We will need the following results, which generalize Definition 12 (specifically Equation (52)) and Theorem 4.
9.4.1. The Time-Dependent Directed Diffusion Equation Involving the Operator
Definition 14.
Let representing the information function for a graph with n nodes. If D is the diffusion coefficient and the creation function of the information, with a time-dependent Laplacian operator , the following directed diffusion equation holds, for any :
Here the main difference is that the Laplacian operator L is a function of time t.
9.4.2. Solution Involving
From Equation (12), we can use the Cauchy theorem to obtain the following solution.
Theorem 9
(Application of the Cauchy Theorem). The solution of the related Cauchy problem associated with Equation (12) is given by
As was done previously, we would rather use the following equation:
which we can reduce again by noticing that and since , so that Equation (64) is also verified:
9.4.3. Practical Case—Committed Error
Here, the error committed due to the approximation being split into two terms, and one has
where
is the error due to the approximation at the diffusion term, and
is the error due to the approximation at the creation/destruction term. We derive an upper bound for these two errors. Regarding the error on the diffusion term, we note that
so that
This proves that . Regarding the error on the creation/destruction term, we introduce
so that
We have
Bearing all above in mind, we have
This proves that . Finally, we have proven that the committed error is such that . Thus, Equation (72) can be implemented by neglecting as this represents a negligible error (see Section 8.3 for numbers).
9.4.4. Practical Case—Implementation
3-Node Case
We implement the model through Equation (72). We took a 3-node graphs as a first step, and wanted to plot the solutions for the case depicted in Section 9.3.3. We set and , with , and we set the adjacency matrix A as
Figure 14 shows the information evolution per node (yellow is node 1; orange is node 2; and red is node 3).
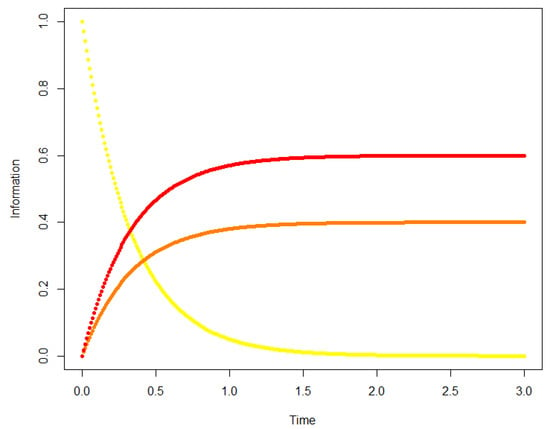
Figure 14.
A 3 node-graph. Node 1 gives information to node 2 (resp. 3) with rate 0.4 (resp. 0.6). There is no delay, and .
We compare these results with the ones obtained from adding delays: node 2 starts receiving the information from time and node 3 from time . The time-dependent adjacency matrix becomes
Figure 15 plots the results.
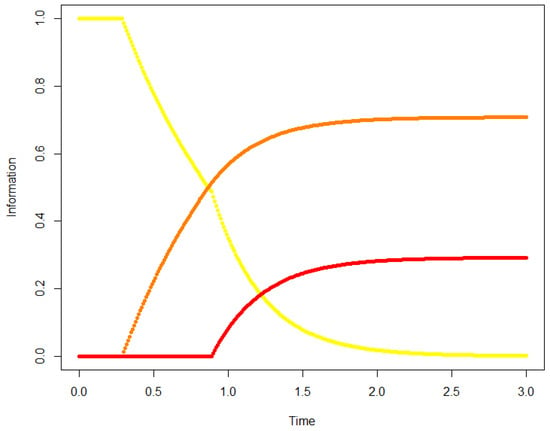
Figure 15.
Same structure as in Figure 14, but with a delay for node 2 and for node 3.
The results are showing expected behaviors, with another interesting aspect: if a node takes too much delay to receive information, even if it has strong affinity, it will receive much less than the expectations. This could modify the whole network configuration and change its dynamical properties.
A last remark is about the obvious discontinuity of the derivative at times where nodes start receiving the information.
Random Walk
Random walk is an important modelization of the propagation of information in a network. It represents the abrupt movement of a bunch of bitcoins (resp. epidemia) among different addresses (resp. people), and is a powerful tool for the traceability of sub-signals of one signal.
From what we have seen above, we can confidently state that random walk actually is a particular case of the above delayed differential equation theory. Indeed, a random walk is obtained by taking the limit , with delay times as a multiple of a fixed delay , marking the time step of the movement of information from node to node (creating a discretization of time from a continuous time environment). It is worth pointing out that, in this case, diffusion becomes propagation. Thus, more generally, on a network, it turns out that a signal propagation is a particular diffusion of it, which is a non-trivial statement (but the converse is incorrect, as the sub-signals are not modified in essence through their propagation throughout the network).
10. Conclusions
In this paper, we studied the process of diffusion on a network, undirected and directed, with boundary conditions and response delays. More specifically, we introduced some fundamental definitions in the context of a crypto’s P2P network, and then derived the diffusion equation, with two different Laplacian operators. The main innovations are the analytic solution derivation (by means of singular value decomposition), with or without boundary conditions. We also have characterized delays into the response of vertices.
It is worth pointing out that a tool, based on the evolution of information within a real blockchain network, could be envisaged through this approach. For instance, a visualization of any kind of exchange in the Bitcoin network could be implemented. The tool can trace any piece of the exchange, from the past to the future, using the forecasting ability, and this at any instant. The forecast, thus, can be updated by feeding the system with all historical information up to the present. We also can imagine a parametrized machine learning process which captures the historical configurations of the Bitcoin network, and suggests likely ones in the future. Thus, the traceability of information is a starting point for further transparency within all the agents, and implies the diminution of money-laundering risk. Modeling the P2P network is useful for any exchange, not only for trading and forecast purposes, but also for compliance duties.
Finally, it is worth stressing that the results developed in this paper are generalizable to any kind of P2P network, except Section 4.2, which is Bitcoin specific, even if the approach could be adapted. No matter what the underlying protocol is, we will systematically find exchange of information between agents, nodes, and users. The structure of the network as well as its underlying consensus mechanism (e.g., proof-of-work and proof-of-stake) are additional data which the general diffusion equation on a directed graph, given by Equation (52), can be a fitting model with parameter D, and, more importantly, with the operator , function of the consensus, as is related to the source of information. One could also make the model even more general by implementing a tensor D as a function of the vertices and of the edges of the network. This is left for further studies.
[custom]
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Notes
| 1 | We write . The function has two variables, i.e., time and node, and takes real values. |
| 2 | numbers 1, 2, etc. designates the neighboring nodes of y. |
References
- An, Jaehyung, Alexey Mikhaylov, and Sang-Uk Jung. 2021. A Linear Programming approach for robust network revenue management in the airline industry. Journal of Air Transport Management 91: 101979. [Google Scholar] [CrossRef]
- Bondy, J. Adrian, and Uppaluri S. R. Murty. 2007. Graph Theory: An Advanced Course (Graduate Texts in Mathematics). Berlin and Heidelberg: Springer. [Google Scholar]
- Chung, Soon-Yeong, Yun-Sung Chung, and Jong-Ho Kim. 2007. Diffusion and Elastic Equations on Networks. Publications of the Research Institute for Mathematical Sciences 43: 699–726. [Google Scholar] [CrossRef] [Green Version]
- Hollanders, Romain, Daniel F. Bernardes, Bivas Mitra, Raphaël M. Jungers, Jean-Charles Delvenne, and Fabien Tarissan. 2014. Data-driven traffic and diffusion modeling in peer-to-peer networks: A real case study. Network Science 2: 341–66. [Google Scholar] [CrossRef] [Green Version]
- Li, Quan-Lin, Jing-Yu Ma, Yan-Xia Chang, Fan-Qi Ma, and Hai-Bo Yu. 2019. Markov processes in blockchain systems. Computational Social Networks 6: 5. [Google Scholar] [CrossRef]
- Lipton, Alexander, and Adrien Treccani. 2021. Blockchain And Distributed Ledgers: Mathematics, Technology, And Economics. Singapore: World Scientific. [Google Scholar]
- Manini, Daniele, and Marco Gribaudo. 2008. An Analytical Study of the Resource Diffusion in Non-homogeneous P2P Networks. Paper presented at International Conference on Analytical and Stochastic Modeling Techniques and Applications, Nicosia, Cyprus, June 4–6; Berlin and Heidelberg: Springer, pp. 88–100. [Google Scholar]
- Mikhaylov, Alexey Yu. 2021. Development of Friedrich von Hayek’s theory of private money and economic implications for digital currencies. Terra Economicus 19: 53–62. [Google Scholar] [CrossRef]
- Musa, Ahmad, Hamad Almohannadi, and Jassim Alhamar. 2018. Malware Propagation Modelling in Peer-to-Peer Networks: A Review. Paper presented at 2018 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Barcelona, Spain, August 6–8; pp. 198–202. [Google Scholar]
- Pacreau, Grégoire, Edmond Lezmi, and Jiali Xu. 2021. Graph Neural Networks for Asset Management. IEEE Transactions on Engineering Management, 1–18. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3976168 (accessed on 15 December 2021).
- Shahsavari, Yahya, Kaiwen Zhang, and Chamseddine Talhi. 2017. A Theoretical Model for Block Propagation Analysis in Bitcoin Network. IEEE Transactions on Engineering Management, 1–18. [Google Scholar] [CrossRef]
- Thanou, Dorina, Xiaowen Dong, Daniel Kressner, and Pascal Frossard. 2017. Learning Heat Diffusion Graphs. IEEE Transactions on Signal and Information Processing over Networks 3: 484–99. [Google Scholar] [CrossRef] [Green Version]
- Viriyasitavat, Wattana, and Danupol Hoonsopon. 2019. Blockchain characteristics and consensus in modern business processes. Journal of Industrial Information Integration 13: 32–39. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).