Highlights
What are the main findings?
- A new attack method, the Common Factor Substitution Attack, is introduced, showing that a broad class of existing pairing-free certificateless signature (PF-CLS) schemes share a common vulnerability and cannot resist Type I adversary forgeries—even after certain prior improvements.
- A new PF-CLS scheme is proposed that securely binds both parts of a user’s public key to the system public key via a hash function, eliminating the Type II attack vulnerability in Ma et al.’s scheme, and is proven secure against both Type I and Type II adversaries under the Random Oracle Model while offering higher computational efficiency than comparable schemes.
What is the implication of the main finding?
- The results underscore that many PF-CLS schemes in current use for resource-constrained environments like IoT remain insecure against forged signature attacks unless both Type I and Type II threats are systematically addressed in their design.
- The proposed scheme’s combined security and efficiency make it a strong candidate for real-world IoT deployments, improving trust in data integrity and identity authentication without imposing heavy computational or communication costs.
Abstract
Pairing-free certificateless signature (PF-CLS) schemes are ideal authentication solutions for resource-constrained environments like the Internet of Things (IoT) due to their low computational, storage, and communication resource requirements. However, it has come to light that many PF-CLS schemes are vulnerable to forged signature attacks. In this paper, we use a novel attack method to prove that a class of PF-CLS schemes with the same security vulnerabilities cannot resist Type I adversary attacks, and we find that, even if some schemes are improved to invalidate existing attack methods, they still cannot defend against the new attack method proposed in this paper. Subsequently, we introduce an enhanced scheme proven to be resilient against both types of adversary attacks under the random oracle model (ROM). Performance analysis shows that, compared with several existing PF-CLS schemes, our scheme offers higher computational efficiency.
1. Introduction
The IoT is used broadly and, because of its openness, transmits most data over the public Internet, exposing it to eavesdropping, tampering, forgery, and other attacks. Consequently, data security is paramount for IoT. Digital signature technology, ensuring the authentication, unforgeability, and non-repudiation of messages, is ideal for IoT environments.
In a traditional public key cryptosystem, an entity’s public key’s authenticity and validity require a digital certificate from a trusted third-party, the Certificate Authority (CA). Managing certificates in IoT environments is challenging because of the substantial overhead for storing, distributing, verifying, and revoking them. In Identity-Based Cryptography (IBC), a user’s public key is generated based on identifiable public information, like a phone number, email address, or IP address. A trusted third-party Private Key Generator (PKG) creates the user’s Private Key, eliminating the need for CAs and digital certificates and addressing the certificate management issue. However, since the PKG fully generates the user’s private key, this raises concerns over potential signature forgeries, undermining the unforgeability of the system. Certificateless Public Key Cryptography (CL-PKC) solves the key escrow issue in IBC by having a Key Generation Center (KGC) create a partial private key for the user. The user then combines this with their own data to generate a full private key.
Consequently, CLS amalgamates the strengths of traditional public key cryptosystem and IBC, addressing their respective drawbacks and proving more effective for ensuring data integrity and identity authentication in IoT’s distributed, flexible, and resource-limited environments.
1.1. Related Work
In 2003, AI-Riyami and Paterson proposed the first certificateless signature scheme [1]. This scheme, which does not require digital certificates, allows the user and the KGC to jointly generate both public and private keys. The KGC only holds a portion of the user’s private keys, effectively solving the key escrow problem inherent in IBC. In 2004, Yum et al. proposed a general construction for CLS schemes [2]. This led to the development of numerous CLS schemes [3,4]. However, these schemes all relied on bilinear pairings, which are known for their high computational complexity and low efficiency. In 2011, He et al. introduced the first CLS scheme that does not use bilinear pairings [5]. However, Tian and Tsai later pointed out that He’s scheme was vulnerable to Type II adversary attacks [6,7]. In 2013, Gong et al. proposed a pairing-free CLS scheme [8], but Yeh et al. pointed out that it could not resist Type I adversary attacks and proposed an improved version [9]. In 2015, Wang et al. introduced a more efficient variant of Yeh et al.’s scheme [10]. In 2017, Yeh et al. discovered vulnerabilities in Wang’s improved scheme regarding forged signatures and subsequently developed a new scheme [11]. However, Jia et al. later revealed that Yeh’s new scheme was still vulnerable to Type II adversary attacks involving public key replacement [12]. In 2018, Karati et al. independently proposed a new scheme that does not use bilinear pairings and claimed that it can resist both Type I and Type II adversary attacks under the ROM [13]. Later, Pakniat et al. successfully demonstrated that Karati et al.’s scheme can be attacked by Type I adversaries, and they improved the scheme [14]. Shim et al. found that Karati et al.’s scheme allows for forging arbitrary message signatures without obtaining any secret information, and that Pakniat et al.’s scheme still cannot resist Type I adversary attacks [15]. In the same year, Du et al. pointed out that Jia et al.’s improved scheme cannot resist Type I adversary attacks and subsequently developed an enhanced version [16]. Thumbur et al. independently proposed a new pairing-free certificateless signature scheme [17], but it was later pointed out by Xu et al. [18] that it cannot resist Type I adversary public key replacement attacks. By 2022, Xiang et al. successfully demonstrated a specific Type II adversary attack method targeting Jia et al.’s scheme and improved it based on identified vulnerabilities [19]. In 2023, Ma et al. pointed out that both Du et al.’s and Xiang et al.’s schemes are susceptible to Type I adversary attacks, and proposed new attack methods and improvements [20]. However, Feng et al. [21] found that Ma et al.’s scheme still could not resist Type II adversary attacks the following year.
1.2. Our Contributions
This paper’s primary contributions are as follows:
1. We analyze a class of PF-CLS schemes with the same security vulnerabilities and use a new attack method to show that all schemes in this class cannot resist Type I adversary attacks.
2. We introduce a new pairing-free certificateless signature scheme, which tightly binds the two parts of the user’s public key ( and ) to the system’s public key () via a hash function, avoiding the vulnerability of Type II adversary attack due to independent generation of public keys in the scheme of Ma et al. [20]. Moreover, our scheme proves its security against both Type I and Type II adversary attacks under the Random Oracle Model (ROM).
3. Performance evaluations demonstrate that our scheme has higher computational efficiency compared to other people’s schemes, making it more suitable for IoT environments.
2. Preliminaries
2.1. Complexity Assumption
Consider q as a large prime number, with representing an additive group of order q over the elliptic curve , where P is a generator of . The Elliptic Curve Discrete Logarithm Problem (ECDLP) means that, for any instance , if are known, finding the solution yields a.
The difficult hypothesis for the Elliptic Curve Discrete Logarithm Problem is that there is no probabilistic polynomial algorithm A that can solve ECDLP with a non-negligible probability in polynomial time.
2.2. Security Model
Certificateless signature schemes face two types of attacks from adversaries. An adversary of Type I () has the capability to substitute the user’s public key without requiring access to the system master key. On the other hand, an adversary of Type II () holds possession of the system master key but does not possess authority to alter or replace the user’s public key. The security model is represented as a gaming scenario involving both challengers and their respective adaptive adversaries
Game 1: This game is played between an adaptive adversary and the challenger . maintains a list that stores information about users. The game consists of the following phases:
Initialization: Challenger enters a security parameter k, generates system parameters , and sends them to , while saves the system master key s itself.
Query phase: In this phase, the following queries can be submitted adaptively by . That is, the adversary will issue a new query based on the received response.
1. : Enter user identity (); queries list . If the user has been created, returns its corresponding user public key (); otherwise, performs three algorithms, , , and , to create a user and returns the . It then adds the , partial private key (), secret value (), and to list for maintenance.
2. : Enter ; queries table . If the user exists, then updates the corresponding public key in the record table as , and records the secret value as ⊥; otherwise, executes the first, and then performs the update.
3. : Enter ; first queries table . If the user does not exist, then executes and returns the corresponding secret value ; if the user exists and the public key is not replaced, outputs the corresponding secret value . Otherwise, output ⊥.
4. : Enter ; queries table . If the user is present, returns the corresponding partial private key . Otherwise, first executes the and then returns .
5. : Input ; outputs a signature . The signature can be verified by the corresponding message plaintext m, system parameter , and user public key . The is the last updated public key corresponding to the in list , that is, the public key may not be original.
Forgery: After successfully executing all queries, adversary generates a counterfeit signature . The victory condition for is as follows: 1. has never queried the super signature for ; 2. has never performed an for ; 3. for is a verifiable valid signature, and the public key may not be original.
Game 2: This game is played between an adaptive adversary and the challenger . maintains a list that stores information about users. The game consists of the following phases:
Initialization: Challenger enters a security parameter k, generates system parameters , and sends them to , while sends the system master key s to .
Query phase: In this phase, the following queries can be submitted adaptively by .
1. : Enter user identity (); queries list . If the user has been created, returns its corresponding user public key (); otherwise, performs three algorithms, , , and , to create a user and returns the , and then adds the , partial private key (), secret value (), and to list for maintenance.
2. : Enter ; first queries table . If the user does not exist, then executes and returns the corresponding secret value ; if the user exists and the public key is not replaced, outputs the corresponding secret value . Otherwise, output ⊥.
3. : Enter ; queries table . If the user is present, returns the corresponding partial private key . Otherwise, first executes the and then returns .
4. : Input ; outputs a signature . The signature can be verified by the corresponding message plaintext m, system parameter , and user public key . The is the last updated public key corresponding to the in list , that is, the public key may not be original.
Forgery: After successfully executing all queries, adversary generates a counterfeit signature . The victory condition for is as follows: 1. has never queried the super signature for ; 2. never performs an on ; 3. is a verifiable valid signature for , and the public key remains intact.
For a CLS scheme, if the super Type I or Type II adversary cannot win Game 1 or Game 2 by a significant advantage in polynomial time, we say that the scheme is unfalsifiable against adaptive chosen plaintext attacks and identity attacks.
3. Review of Four PF-CLS Schemes
In this section, we review the four PF-CLS schemes [13,14,16,19]. The four PF-CLS schemes contain six basic process algorithms: , , , , , and .
3.1. Xiang et al.’s Scheme
Xiang et al.’s scheme [19] contains the following six algorithms:
1. : The KGC generates an elliptic curve additive group of order q and selects as the generator of group . The KGC randomly chooses as the system master key, computes , and selects three functions: . Subsequently, the KGC publishes the system parameters and keeps the master key s secret.
2. : The KGC takes the system parameters and identity as input. Then, it randomly selects , computes , , and . KGC sends the partial private key to the user over a secure channel.
3. : The user randomly picks as his/her secret value and calculates .
4. : The user sets as the public key and as the private key.
5. : The signer takes the message m, , , , and as input, then generates a signature on message m as follows:
(i) Randomly select a value , and compute ;
(ii) Compute , , and ;
(iii) Output as a signature.
6. : The verifier takes the message–signature tuple , , , and as input, then verifies the signature as follows:
(i) Compute , , ;
(ii) Output “Accept” if holds, and “Reject” otherwise.
3.2. Du et al.’s Scheme
The , , , and algorithms in Du et al.’s scheme [16] are basically the same as those in Xiang et al.’s scheme [19], with the only difference being the value of .
: Given the message m, , , , and as input, the signature generation process is as follows:
1. Randomly select a value , and compute .
2. Compute , , and .
3. Output as the signature.
: Given m, , , , and as input, the verification process is as follows:
1. Compute , , .
2. Output "Accept" if holds, and "Reject" otherwise.
3.3. Karati et al.’s Scheme
Karati et al.’s scheme [13] contains the following six algorithms:
1. : The KGC generates an elliptic curve additive group of order q and selects as the generator of group . The KGC randomly chooses as the master key, computes , and selects two functions: . Subsequently, the KGC publishes the system parameters and keeps the master key s secretly.
2. : The KGC takes and identity as input, randomly selects , computes , , , and . KGC sends the partial private key to the user over a secure channel.
3. : The user randomly selects as his/her secret value.
4. : The user computes , then sets as the public key and as the private key.
5. : The signer inputs m, , , , and , then generates signature for m as follows:
(i) Randomly select a value , and compute ;
(ii) Compute , and ;
(iii) Output as a signature.
6. : The verifier inputs , , , and , then verifies the signature as follows:
(i) Compute , , and ;
(ii) Output “Accept” if holds, and “Reject” otherwise.
3.4. Pakniat and Vanda’s Scheme
The , , , and algorithms in Pakniat and Vanda’s scheme [14] are basically the same as those in Karati et al.’s scheme [13], except that Pakniat and Vanda’s scheme additionally defines an extra function .
: Given m, , , , and as input, the signature generation process is as follows:
1. Randomly select a value and compute .
2. Compute , , and .
3. Output as a signature.
: Given m, , , , and as input, the verification process is as follows:
1. Compute , , , and .
2. Output “Accept” if holds, and “Reject” otherwise.
4. Novel Attacks on Four Schemes
In this section, we use a novel attack method on the four schemes presented in Section 3 and prove that all four schemes cannot resist Type I adversary attacks.
4.1. Cryptanalysis of Xiang et al.’s and Du et al.’s Schemes
Ma et al. [20] have pointed out that Xiang et al.’s scheme [19] cannot resist Type I adversary attacks, and the specific attack method will not be elaborated here. In this section, we use a new attack method different from Ma et al. to prove that Xiang et al.’s scheme cannot resist Type I adversary attacks. Suppose that there exists a Type I adversary attempting to forge the signature of a user with identity and public key . The process of forging the signature is as follows:
1. selects two random values , , computes , , and replaces the original public key with .
2. Assuming that the message is , randomly selects , and computes , , , , and . Then, outputs the forged signature .
3. Upon receiving the message–signature tuple , , and , the verifier first computes , , , and then verifies the equation .
We can observe that the forged signature can easily pass the verification equation:
Through the above attack method, the attacker can forge a valid signature for any user on any message. Therefore, Xiang et al.’s scheme cannot resist Type I adversary attacks. Moreover, the attack on Du et al.’s scheme [16] is similar to the attack on Xiang et al.’s scheme, and will not be elaborated here.
4.2. Cryptanalysis of Pakniat and Vanda’s and Karati et al.’s Schemes
Shim [15] pointed out that Pakniat and Vanda’s scheme [14] cannot resist Type I adversary attacks, and the specific attack method will not be elaborated here. In this section, we first improve Pakniat and Vanda’s scheme to make Shim’s attack method ineffective. Then, we use the same attack method as in Section 4.1 to demonstrate that the improved Pakniat and Vanda’s scheme still cannot resist Type I adversary attacks.
The method for improving Pakniat and Vanda’s scheme is relatively simple, requiring only a change in the calculation of from to . The improved scheme will not be described in detail here. After this improvement, if we still want to forge , we need to provide the value of to obtain , and, in order to obtain the value of ,we need to first provide the value of . This is contradictory, so we cannot forge and Shim’s attack cannot succeed.
Next, we prove that the improved Pakniat and Vanda’s scheme still cannot resist Type I adversary attacks. Suppose that a Type I adversary attempts to forge the signature of a user with identity and public key . The detailed process is as follows:
1. selects three random values , , , computes , , , and replaces the original public key with .
2. Supposing that the message is , randomly selects , and computes , , , , . Then, outputs the forged signature .
3. After receiving the message–signature pair , , and , the verifier first computes , , , and then verifies the equation .
We can observe that the forged signature can easily pass the verification equation:
Through the above attack method, the attacker can forge a valid signature for any user on any message. Therefore, Pakniat and Vanda’s scheme cannot resist Type I adversary attacks. Moreover, we can use the same attack method to prove that Karati et al.’s scheme [13] cannot resist Type I adversary attacks, and the detailed process can be referred to above, which will not be repeated here.
Definition 1.
In our attack, , , are generated by random values , , , which do not have a relationship with each other, and therefore the verifier cannot detect the forgery of the public key and signature. Compared with the attack method of Ma et al., our attack method is practical. We call this novel attack the Common Factor Substitution Attack.
5. The Proposed CLS Scheme
In this section, we introduce a novel CLS scheme that offers enhanced security and efficiency (Figure 1).
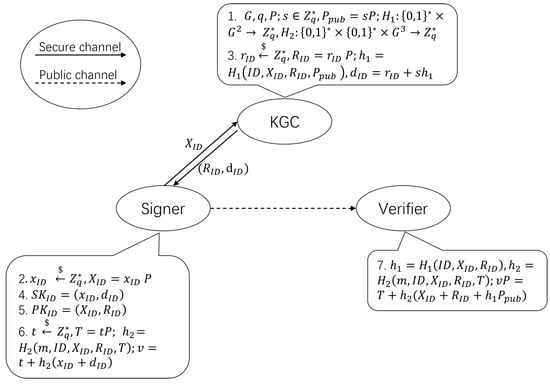
Figure 1.
Our CLS scheme.
1. : KGC takes the security parameter k as input and selects the elliptic curve addition group , where q and P are the order and generator of the group , respectively. KGC chooses two secure hash function , . Then, KGC randomly selects the system master key , and calculates the system public key . will be outputted as the public system parameters.
2. : User identified by randomly chooses the secret value , then computes and transmits it to KGC.
3. : After receiving submitted by the user, KGC randomly selects and calculates as part of the public key, then calculates . Finally, KGC calculates as the partial private key and transmits to the user via a secure communication channel.
4. : The user generates the complete private key .
5. : The user generates the complete public key .
6. : The signer signs the message m. The signer randomly picks and calculates . And then the signer calculates to obtain signature
7. : The verifier receives signature and message m for verification. First, the verifier calculates , and then determines whether the verification equation is valid. It accepts if true, and rejects the signature otherwise.
6. Security Proof
Forking Lemma: In cryptography, the forking lemma is a crucial tool for proving the security of digital signature schemes. Its core idea is as follows: if there exists an adversary capable of successfully forging a valid signature triple (where m denotes the message, denotes the signature value, h denotes the hash value generated by the random oracle H, and it contains a publicly accessible value z), then, by replaying the interaction process between the adversary and the random oracle, the adversary can be forced to generate a different hash output for the same input, thereby obtaining another valid signature .
Specifically, by fixing the adversary’s random tape and resetting the random oracle, the adversary can be compelled to generate two distinct yet valid signatures during repeated executions. These two signatures satisfy , and their existence can be used to construct an algorithm to solve the underlying cryptographic hard problem (such as the discrete logarithm problem) with a non-negligible probability. The advantage probability of the forking lemma is , where denotes the original forgery probability of the adversary, denotes the number of oracle queries, and e denotes the natural constant.
Theorem 1.
Suppose that the probability that a super Type I adversary , being able to produce a valid forged signature in polynomial time, is ε, the maximum number of times that an adversary can query is , and the maximum number of times that an adversary can query the is . The polynomial time algorithm has the advantage of to solve difficult ECDLP problems.
Proof.
Suppose that the super Type I adversary can win Game 1 by a non-negligible advantage in polynomial time. For a given ECDLP hard problem instance , we can construct the algorithm to call as a subroutine and use the power of to solve it. and are two random oracle models. maintains two lists, and , for recording ’s query of and , respectively. , are initially empty. The interaction between and is as follows:
Initialization phase: inputs security parameter k to generate system parameters and sets (a is unknown to ). Then, selects the challenge user and sends the system parameters to the adversary .
Query phase:
1. : enters ; first looks up list . If already exists, returns ; otherwise, carry out the following: (1) If the , randomly selects , calculates , sets , and returns . adds to table . (2) If the , randomly selects , calculates , sets , and returns . adds to list .
2. : inputs . first queries list . If already exists, then returns to ; otherwise, performs the and then returns .
3. : inputs ; first inquires about . If already exists, then returns ; otherwise, randomly selects and returns to . Then, updates to list .
4. : inputs . If , aborts the program and outputs ⊥; otherwise, checks list and returns . If does not exist in table , the will be executed first and then will be returned.
5. : enters . queries list and returns . If does not exist in list , executes and then returns . In addition, if the public key is not the original one, then outputs ⊥.
6. : inputs . looks up list and updates in the table corresponding to the content as .
7. : inputs . checks whether is contained in list . If not, executes first and then performs the following: (1) if the and (the public key has not been replaced), randomly selects , calculates , and outputs signature ; (2) if or (the public key is replaced), randomly selects , calculates , and outputs signature . Then, updates to list .
Forgery: Upon completing all queries, adversary outputs a forged signature for . If , will abort and output ⊥. In line with the forking lemma, when replays , produces another forged signature , resulting in two signatures sharing . According to the signature calculation, there are two equations:
Considering the potential for public key replacement, remains unknown to . The equation involves three unknown variables: . The value of a can be determined using simultaneous equations as . This approach enables to successfully employ as a subroutine to solve the ECDLP.
Next, we calculate the probability that will win Game 1. First, we define three events: indicates that does not exit during the query phase; indicates that does not exit during the forgery; indicates that successfully forges a valid signature. Therefore, the following are true:
1. The probability that does not perform the for during the query phase is ;
2. The probability that does not exit in the forgery stage is the probability that outputs the signature corresponding to in the forgery stage: ;
3. The probability of forging one valid signature is , and the probability of forging two valid signatures is . Thus, , and challenger can solve an ECDLP hard problem with non-negligible probability. And because the difficult problem is actually unsolvable, the adversary cannot forge the signature. □
Theorem 2.
If the ECDLP hardness assumption cannot be solved in polynomial time, then our proposed enhanced scheme can effectively resist Type II attackers . Specifically, suppose that the probability that a super Type II adversary , being able to produce a valid forged signature in polynomial time, is ε. The maximum number of times that an adversary can query is , the maximum number that an adversary can query is , and the maximum number that an adversary can query is . The polynomial time algorithm has the advantage of to solve difficult ECDLP problems.
The proof steps of Theorems 2 and 1 are similar. However, it is necessary to mention that, in the proof of Theorem 2, and will not be initiated by .
7. Performance Evaluation
In the previous section, we established the complete security and unforgeability of our proposed new scheme. We now turn our attention to the performance analysis of this new solution. To match the security level of the 1024-bit RSA algorithm, we employ the elliptic curve , with being the order-q additive cyclic group on . Here, p is a 512-bit prime, q is a 160-bit prime, and P serves as the generator of . The implementation utilizes the open-source cryptography library MIRACL, running on a device equipped with an Intel(R) Core(TM) i5-3470 CPU @ 3.20 GHz x4 processor, 4GB of memory, and the 64-bit Ubuntu 22.04.3 LTS operating system. Table 1 presents the average running time of each basic cryptographic operation, measured over 1000 repeated experiments.

Table 1.
Running time of cryptographic operations.
In the IoT environment, where device resources are limited and computing capacities are modest, there are stringent requirements for both computational efficiency and communication efficiency. In CLS schemes, computational efficiency is primarily determined by the computational load during the signing and verification phases, whereas communication efficiency largely depends on the size of the signature.
As illustrated in Table 2 and Figure 2, in terms of computational efficiency, during the signature phase, our scheme has a calculation time comparable to those of Feng, Ma et al.’s scheme, and is slightly lower than those of Karati, Pakniat, Du, Xiang, and other schemes. However, in the verification phase, our scheme has a calculation time of , which is lower than Feng, Ma et al.’s calculation time of , and Du, Xiang et al.’s calculation time of , and is comparable to Karati et al.’s scheme. The total calculation time of our scheme is slightly lower than that of Karati et al.’s scheme, about 19.76% lower than Feng et al. and Ma et al.’s scheme, about 19.80% lower than Du et al. and Xiang et al.’s schemes, and about 20.05% lower than Pakniat et al.’s scheme, marking a significant improvement in computational efficiency.

Table 2.
Comparative analysis of performance.
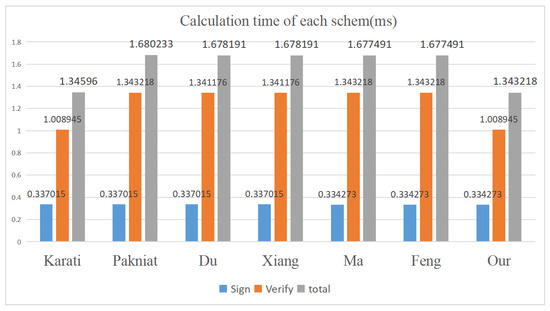
Figure 2.
Calculation time of each scheme.
Regarding communication efficiency, our scheme’s output signature size, , is comparable to Feng, Ma, Karati, Du, and Xiang et al. Compared to Pakniat et al.’s scheme’s output signature size, , our scheme is more efficient in communication efficiency.
Our performance analysis shows that our scheme offers higher security and computational efficiency compared to Ma, Karati, Pakniat, Du, and Xiang et al.’s schemes. Compared with Feng et al.’s scheme, our scheme has improved computational efficiency while maintaining the original security level. Therefore, our scheme is a more suitable solution for the IoT environment.
8. Conclusions
The design of lightweight, secure, efficient, and reliable signature schemes for the IoT has become a hot research topic. Certificateless signature schemes have become an important solution for providing security services such as identity authentication, data integrity protection, and non-repudiation for the IoT due to their advantages of not requiring certificates and avoiding the key escrow problem. We review four PF-CLS schemes and use a novel attack method to attack the existing ones on four PF-CLS schemes with the same security vulnerabilities to prove that none of the four schemes can protect against Type I adversary forgery attacks. Subsequently, we propose an improved scheme, which is proven to be secure, reliable, and unforgeable under the ROM. Finally, the performance analysis of the new scheme shows that our scheme offers higher computational efficiency compared to the other PF-CLS schemes, making it more suitable for resource-constrained IoT environments.
Future research will focus on the following directions: (1) Existing schemes may expose user identities, and anonymous signatures can instead be realized by combining zero-knowledge proof (ZKP) or ring signature technologies. (2) Deploy the new scheme in practical resource-constrained IoT environment applications, and evaluate its feasibility during actual deployment, as well as its resistance to side-channel attacks such as timing attacks and power analysis.
Author Contributions
Writing—original draft, X.L. and B.L.; Supervision, Z.W., H.Z. and Z.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Beijing Natural Science Foundation (No. L251067) and Fundamental Research Funds for the Central Universities (No. 3282024052, No. 3282024058).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author(s).
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Yum, D.H.; Lee, P.J. Generic construction of certificateless signature. In Proceedings of the Australasian Conference on Information Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2004; pp. 200–211. [Google Scholar]
- Huang, X.; Susilo, W.; Mu, Y.; Zhang, F. On the security of certificateless signature schemes from Asiacrypt 2003. In Proceedings of the Cryptology and Network Security: 4th International Conference, CANS 2005, Xiamen, China, 14–16 December 2005; Proceedings 4. Springer: Berlin/Heidelberg, Germany, 2005; pp. 13–25. [Google Scholar]
- Choi, K.Y.; Park, J.H.; Lee, D.H. A new provably secure certificateless short signature scheme. Comput. Math. Appl. 2011, 61, 1760–1768. [Google Scholar] [CrossRef]
- He, D.; Chen, J.; Zhang, R. An efficient and provably-secure certificateless signature scheme without bilinear pairings. Int. J. Commun. Syst. 2012, 25, 1432–1442. [Google Scholar] [CrossRef]
- Tian, M.; Huang, L. Cryptanalysis of a certificateless signature scheme without pairings. Int. J. Commun. Syst. 2013, 26, 1375–1381. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W.; Wu, T.C. Weaknesses and improvements of an efficient certificateless signature scheme without using bilinear pairings. Int. J. Commun. Syst. 2014, 27, 1083–1090. [Google Scholar] [CrossRef]
- Gong, P.; Li, P. Further improvement of a certificateless signature scheme without pairing. Int. J. Commun. Syst. 2014, 27, 2083–2091. [Google Scholar] [CrossRef]
- Yeh, K.H.; Tsai, K.Y.; Kuo, R.Z.; Wu, T.C. Robust certificateless signature scheme without bilinear pairings. In Proceedings of the 2013 International Conference on IT Convergence and Security (ICITCS), Macao, China, 16–18 December 2013; pp. 1–4. [Google Scholar]
- Wang, L.; Chen, K.; Long, Y.; Mao, X.; Wang, H. A modified efficient certificateless signature scheme without bilinear pairings. In Proceedings of the 2015 International Conference on Intelligent Networking and Collaborative Systems, Taipei, Taiwan, 2–4 September 2015; pp. 82–85. [Google Scholar]
- Yeh, K.H.; Su, C.; Choo, K.K.R.; Chiu, W. A novel certificateless signature scheme for smart objects in the Internet-of-Things. Sensors 2017, 17, 1001. [Google Scholar] [CrossRef] [PubMed]
- Jia, X.; He, D.; Liu, Q.; Choo, K.K.R. An efficient provably-secure certificateless signature scheme for Internet-of-Things deployment. Ad Hoc Netw. 2018, 71, 78–87. [Google Scholar] [CrossRef]
- Karati, A.; Hafizul Islam, S.; Biswas, G. A pairing-free and provably secure certificateless signature scheme. Inf. Sci. 2018, 450, 378–391. [Google Scholar] [CrossRef]
- Pakniat, N.; Vanda, B.A. Cryptanalysis and Improvement of a Pairing-Free Certificateless Signature Scheme. In Proceedings of the 2018 15th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Tehran, Iran, 28–29 August 2018; pp. 1–5. [Google Scholar]
- Shim, K.A. Forgery attacks on two provably secure certificateless signature schemes. Inf. Sci. 2020, 521, 81–87. [Google Scholar] [CrossRef]
- Du, H.; Wen, Q.; Zhang, S.; Gao, M. A new provably secure certificateless signature scheme for Internet of Things. Ad Hoc Netw. 2020, 100, 102074. [Google Scholar] [CrossRef]
- Thumbur, G.; Rao, G.S.; Reddy, P.V.; Gayathri, N.B.; Reddy, D.V.R.K. Efficient Pairing-Free Certificateless Signature Scheme for Secure Communication in Resource-Constrained Devices. IEEE Commun. Lett. 2020, 24, 1641–1645. [Google Scholar] [CrossRef]
- Xu, Z.; Luo, M.; Khan, M.K.; Choo, K.K.R.; He, D. Analysis and Improvement of a Certificateless Signature Scheme for Resource-Constrained Scenarios. IEEE Commun. Lett. 2021, 25, 1074–1078. [Google Scholar] [CrossRef]
- Xiang, D.; Li, X.; Gao, J.; Zhang, X. A secure and efficient certificateless signature scheme for Internet of Things. Ad Hoc Netw. 2022, 124, 102702. [Google Scholar] [CrossRef]
- Ma, K.; Zhou, Y.; Wang, Y.; Dong, C.; Xia, Z.; Yang, B.; Zhang, M. An Efficient Certificateless Signature Scheme with Provably Security and Its Applications. IEEE Syst. J. 2023, 17, 5636–5647. [Google Scholar] [CrossRef]
- Feng, T.; Wang, J.; Zheng, L. Blockchain-enhanced efficient and anonymous certificateless signature scheme and its application. Pervasive Mob. Comput. 2024, 105, 101990. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).