Abstract
Mobile edge computing is critical for improving the user experience of latency-sensitive and freshness-based applications. This paper provides insights into the potential of non-orthogonal multiple access (NOMA) convergence with heterogeneous air–ground collaborative networks to improve system throughput and spectral efficiency. Coordinated resource allocation between UAVs and MEC servers, especially in the NOMA framework, is addressed as a key challenge. Under the unrealistic assumption that edge nodes contribute resources indiscriminately, we introduce a two-stage incentive mechanism. The model is based on contract theory and aims at optimizing the utility of the service provider (SP) under the constraints of individual rationality (IR) and incentive compatibility (IC) of the mobile user. The block coordinate descent method is used to refine the contract design and complemented by a generative diffusion model to improve the efficiency of searching for contracts. During the deployment process, the study emphasizes the positioning of UAVs to maximize SP effectiveness. An improved differential evolutionary algorithm is introduced to optimize the positioning of UAVs. Extensive evaluation shows our approach has excellent effectiveness and robustness in deterministic and unpredictable scenarios.
1. Introduction
The generation of mobile data is growing at an unprecedented rate due to the boom in Internet of Things (IoT) sensors and mobile technologies. This development has led to an influx of mobile tasks that are latency sensitive and computationally intensive, thus highlighting the need for efficient processing mechanisms. Mobile edge computing (MEC) is a new paradigm of innovation. The idea of MEC, which provides computing and storing capabilities directly within the wireless access network, is described in detail in [1]. In addition to reducing congestion in the centralized network, MECs reduce the associated costs, particularly those associated with latency and power consumption for mobile tasks, by offloading the processing of tasks to the edge nodes. Understandably, this has made MECs the center of academic interest, which has spawned a large number of research efforts aimed at refining task offload determination and resource allocation techniques to improve the execution of mobile tasks [2]. However, the great potential of MEC is not without its challenges. In particular, it is constrained by limited computational power and limited spectrum resources. The age of information (AoI) serves as a metric that elegantly quantifies the temporal freshness of data by indicating the length of time since the last update was released. Task offloading decisions that are influenced by the AoI are critical to ensuring the timeliness and relevance of the computation and data processing [3]. Thus, the shortcomings described above are particularly evident for computational tasks that are closely associated with the information age.
With the rapid development of MEC technology, real-time applications have expanded significantly. These include remote monitoring, disaster mitigation, smart agriculture, and urban logistics. There has been a promising integration of unmanned aerial vehicles (UAVs) and non-orthogonal multiple access (NOMA) in the technology domain to address the inherent limitations of multi-spectrum access technologies. This convergence has resulted in an air–ground cooperative heterogeneous network (AGCHN) model [4]. The proposed model not only characterizes the complexity of heterogeneous networks in terms of homogeneous and cross-layer interference, but also explores collaborative research on computational task offloading and resource allocation for HetNet and MEC interconnections [5,6,7,8]. This model is strategically designed to optimize MEC throughput and spectrum resource utilization. In particular, the integration of UAVs has the goal of compensating for the computational limitations of MECs, thus strengthening their computational framework. At the same time, the emergence of NOMA will play a key role in ensuring the maximum utilization of the spectrum resources, thus improving the overall efficiency of the system.
Indeed, the seamless integration of UAVs and NOMA into the MEC architecture is a delicate challenge. This challenge is compounded by the requirements of AoI-based mission offload. The synergy of these technologies is critical to improving the functional efficiency of the MEC, and a judicious mix of resource optimization schemes is required to support AoI-driven mission offloading [4,9]. In practical situations, it is clear that the edge devices will not allocate resources without sufficient incentives. From this operational perspective, using advanced incentivizing schemes becomes particularly important [10,11]. The utilization of artificial intelligence has facilitated the creation of adaptable systems for effectively addressing novel contexts. The utilization of deep learning and deep reinforcement learning techniques accounts for this phenomenon [12]. It is possible to motivate and ensure that these edge nodes contribute resources consistently and optimally by designing well thought-out and tailored incentive mechanisms [13].
The following is a list of the main contributions in this paper.
- This study designs an incentive mechanism that includes both the contract design and the deployment phases. In particular, during the contract design phase, we model the quality of service of users as a function of delay and age of the information, taking into account NOMA communication. Based on this model, we then design the incentive mechanism to account for asymmetric information.
- During the contract design phase, we utilize contract theory to model a contract problem that optimizes the utility of a service provider (SP) while satisfying individual rationality (IR) and incentive compatibility (IC) criteria for mobile users. By reducing constraints and transforming variables, the original contract problem is transformed into a problem that can be solved by the BCD algorithm. To enhance the effectiveness of finding the optimal contract, a new solution based on the generative diffusion mode is proposed.
- During the contract deployment phase, we strive to maximize the utility of the SP contract deployment by optimizing the location of the UAV. To this end, an improved differential evolution algorithm is proposed to identify the optimal UAV locations.
- Compared with the existing methods, our numerical analysis experiment proves that our proposed methods are better and more effective under certain and uncertain environments.
2. Related Work
The domain of MEC has garnered substantial attention within the mobile communication networks realm [14]. This innovation offers a promising avenue to circumvent the constraints of conventional centralized cloud computing by propelling computing and storage resources proximate to end users. The integration of MEC capabilities strategically optimizes offload policies for mobile devices, ushering in an era of elevated service quality and minimal latency in data transmission.
At the same time, AoI has become an important parameter to measure the freshness of data in communication systems. It has gained attention in several applications, such as real-time control, smart agriculture, and healthcare, especially modeling the age problem in wireless networks [15,16]. This has spawned innovative indexing methods and led to intensive research on how to optimize AoI during offloading to improve real-time performance in mobile networks.
Within the sphere of MEC networks, Kuang et al. provided seminal insights into AoI by examining an MEC network model encompassing a single source and server. They arrived at a distinct expression for average AoI and assessed the implications of different MEC offloading strategies [17]. Following this, a study advanced the discussion by analyzing AoI under a partial offloading strategy, emphasizing the significance of optimal offloading ratios [18].
Liu et al. innovatively tackled the challenge of AoI in multi-source, single-server MEC systems by introducing a novel online algorithm that optimally manages task generation, computation offload, and resource distribution [19]. In the realm of MEC-facilitated IoT, Muhammad et al. analyzed the interplay of MEC and AoI, highlighting the pivotal role of variables such as random arrivals and unstable channel conditions [20]. Zhu et al. designed an online optimization algorithm, leveraging both Lyapunov and convex optimization techniques, to ensure optimal online decision making even under partially stale network conditions [21].
In wireless sensor networks (WSNs), Zhang et al. [22] wrestled with AoI-aware scheduling. They jointly optimized sampling rate, computing schedule, and transmit power, tackling a non-convex average AoI minimization problem using geometric programming and sequential convex approximation techniques.
In the context of UAV-aided IoT networks and to quantify the freshness of information, AoI has been widely used in some recent work. Reference [23] in UAV-enabled edge computing focuses on optimizing computational offloading. Employing a Stackelberg multi-layer game, the study aligns interests of base stations, drones, and users, emphasizing time delay and energy consumption. Simulations underscore the Stackelberg game algorithm (SGA) as surpassing conventional methods. Chen et al. [24] delve into AoI perceptual resource management within UAV-assisted mobile electronic device systems orchestrated by an infrastructure provider (InP). Highlighting non-cooperative dynamics, their work models interactions as a stochastic game, with mobile users (MUs) vying for constrained resources. The researchers pioneer an online deep reinforcement learning (DRL) methodology, deploying dual deep Q-networks for individual MUs. Numerical evaluations underscore the DRL’s prowess in harmonizing AoI with energy utilization. Recent exploration ventured into the air–ground collaborative mobile edge computing (AGC-MEC) network, wherein Qin et al. [25] jointly optimized task scheduling, computational resource allocation, and unmanned aerial vehicle (UAV) trajectory to reduce ground user devices’ (UEs) weighted AoI. The approach dynamically tailored offloading design, safeguarding computational output freshness, while optimizing scheduling to enhance performance.
As NOMA rises to prominence as a method to amplify network capacity, integrating it with MEC has spurred a wealth of research. Zhu and Liu both offered insights into this integration, with Zhu emphasizing spectrum utilization in a single-user multi-edge server MEC system [26] and Liu scrutinizing the AoI performance of a NOMA-informed MEC offloading strategy [27].
Recent literature also underscores various approaches to mobile device offloading in NOMA-anchored MEC networks. For instance, game theory has been a popular tool, and Yang et al. addresses channel access issues through the ordinary potential game [28]. The study by Lv et al. highlights the criticality of resource constraints in edge computing, proposing a novel online auction mechanism [29].
Recent trends highlight the growing role of contract theory in wireless networks [30]. This theory aids in crafting incentives to motivate user participation in activities like mobile offloading. Its application promises better network performance and equitable user rewards. Lim et al. proposed a contract-theoretic scheme, taking into account varying AoI requirements across tasks [31]. This method adapts to diverse AoI and latency preferences, as confirmed by experiments.
Recently, reinforcement learning has been used by certain academics to address the challenge of mobile edge computing resource optimization, strengthening the effectiveness of the incentive mechanism. Li et al. harnessed DRL and game theory for computation offloading in MEC systems [32]. Their strategy, built on proximal policy optimization (PPO), optimizes data offload size, pricing, and MEC server selection. This results in enhanced stability and faster convergence in simulations. Xu et al. focused on incentive design for mobile crowd sensing, integrating the AoI metric for data freshness [33]. Their two-tiered Stackelberg game-based approach offers AoI-centric incentives and a DRL-driven method for uncertain utility parameters. Both strategies demonstrate effectiveness in real-world tests.
The research arena of mobile edge computing task offloading with an emphasis on AoI is emerging. Notably, some scholars have ventured into joint optimizations of AoI with other critical performance indicators, including delay and energy consumption. Nevertheless, the prevalent trend in this research is a systemic optimization approach, with limited exploration from the perspective of incentive mechanisms. Furthermore, an evident oversight in current studies, as highlighted in Table 1, is the disregard for interference dynamics in air–ground cooperative heterogeneous network settings. Efforts to design optimal offloading strategies for mobile devices in air–ground collaboration scenarios utilizing NOMA, contract theory, and MEC do face some inherent challenges. These challenges include the AoI variability of mission information, different user requirements, and the complexity associated with contract design. Overall, explorting AoI in conjunction with reinforcement learning to augment heterogeneous networks for air–ground cooperation, particularly through NOMA and MEC offloading frameworks infused with contract theory, is still a nascent field. Undoubtedly, this area requires deeper and broader research efforts.

Table 1.
Optimization of each metric by computational tasks in MEC.
3. System Model
Section 3 describes the underlying framework of the study. Section 3.1 details the utility of mobile terminals (MT). Section 3.2 describes the service provider’s utility. Section 3.3, Contract Formulation, describes the methodology for reaching agreements between stakeholders. Together, these subsections provide a concise overview of system operation, stakeholder interests, and contract strategies.
3.1. Utility of Mobile Terminal
In the presence of a single SP, we depict in Figure 1 an air–ground cooperative heterogeneous network model in which ground-based MEC servers and UAVs jointly provide computational power at the network edge. The network consists of a macro base station, M micro base stations containing MEC servers, macro users, and V UAVs. A device served by the MEC server m is defined as , where . Each MEC server is connected to a group of . A device served by the UAV in the MEC server m is defined as , where . Each UAV is connected to a group of . For ease of reference, Table 2 summarizes the key notations.
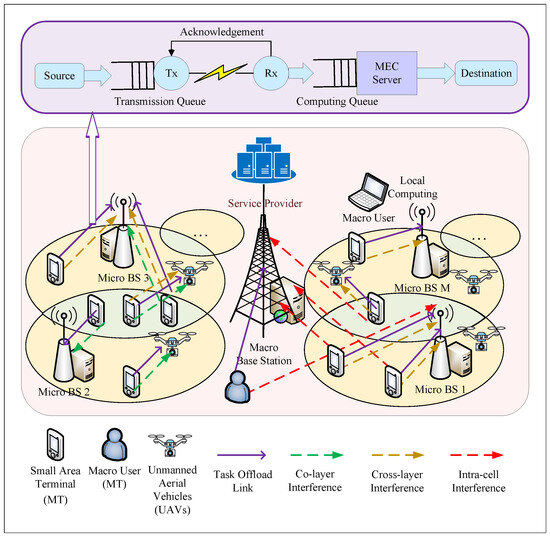
Figure 1.
Heterogeneous network model (HNM).

Table 2.
Key notations.
The SP and MEC servers are connected by high-speed fiber optic cables for reliable communication. The MT interacts with the MEC servers using non-orthogonal NOMA technology over wireless channels. Each UAV functions as a dedicated parallel computing server, which boosts the network’s computational prowess and responsiveness. In this instance, factors including intra-cell interference, cross-layer interference, and co-layer interference must be taken into account.
Figure 1 shows a dual-node cascaded model with two cascaded queues: the transmission queue and the MEC computation queue.
Assuming that the service times of both queues follow an exponential distribution, with service rates denoted as and , respectively, the queue utilization for for edge node (MEC server m or UAV ) is denoted by
In order to maintain queue stability, it is stipulated and .
When unloading, MTs offload computing tasks that require (Mcycles) CPU cycles and have a data packet size of s (MBits) through a wireless channel to an edge node with a computational capability of . Let represent the channel power gain between the edge node and MT .
Referring to [34], is defined as , where represents the channel power at the reference distance, is the location of the MEC server m or UAV , and is the location of MT . Let denote the MTs’ transmission power and B denote the available system bandwidth. Therefore, when MT uploads its computational task to an edge node, we adopt NOMA [35] technology to define the achievable transmission rate
where is the power spectral density of Gaussian white noise and with . Thus, for the transfer queue, its service rate can be rewritten as
For the computation queue, its service rate can be rewritten as
In addition, the average service delay is defined as
Referring to [36], the gain obtained is defined as the saved delay, and AoI by unloading the task of MT is
where is the maximum tolerated AoI and is the trade-off parameter between the saved delay and saved AOI. The utility of MT is the difference between the gained satisfaction and its cost and of offloading its task to the SP or UAV. Thus, the utility of MT is
where is the satisfaction of the performance of the saved delay.
It is noted that the MTs’ type belonging to their privacy is not visible to edge nodes, namely information asymmetry. Various satisfaction categories can be used to categorize MTs according to their composition. These are the definitions that apply. The set of variables is defined as the collection of for every i such that . Consequently, the number of classes of MTs can be denoted as . The probability distribution for each category is denoted as , where m, v, and i represent specific indices. The corresponding number for each category is given by the product of and , that is, . In other words, the sum of all the products over the set of indices i in is equal to . Sequences of MTs that are not degenerate are organized based on their kind.
A higher indicates the higher satisfaction of the performance of the computation task. In this case, is the contract for MTs of type . Each edge node will offer different contracts based on the of the MTs instead of offering the same contract to all of the MTs. We assume that the MT signs a contract of if the MT rejects any contract.
The utility of a MT of type is then redefined as follows:
3.2. Utility of Service Provider
The expense to finish the computation task that the MT offloaded is borne by the MEC service provider. Referring to [37], in order to coordinate with other MTs to lessen the effects of interference and to enable the MT to send data with power, the SP pays a unit cost of for these offloaded computation tasks, i.e., the cost is . Referring to [38], the cost of computing to complete a task is denoted by the formula , where denotes the unit cost expenditure for computational energy consumption and is an effective switching capacitor. Thus, the utility obtained by the edge node is as follows:
As a result, the utility of the SP is as follows for all types of MTs:
To simply the expression, we define the unit transmission rate as the following:
Furthermore, based on (3) and (4), we have
where . When is fixed, is monotonically increasing in terms of , which indicates that and have one-to-one correspondence. For the sake of later analysis, we replace with in (10) and obtain
Then, the SP’s utility is rewritten as
where ,
, and .
3.3. Contract Formulation
It is noted that the MTs’ type belonging to their privacy is not visible to the SP, namely information asymmetry. Considering this information asymmetry, the SP can apply contract theory to find out the best MTs. Here, the SP is the principal of the design contract, and the MTs are agents who select the contract item fitting their own corresponding type. The contract item can be denoted as , where is made for type- MTs. Under the two-tuple asymmetric information, we introduce the following IR conditions and IC conditions to design a feasible contract. The IR condition encourages the participation of MTs while ensuring the non-negative utility of the MT that participates in the computation task. Thus, the IR conditions for the MT of type- will be
The IC conditions ensure that each type of MT can achieve its maximum utility when selecting the contract item based on its own corresponding type. In other words, any item , cannot maximize the utility of type- MT except the contract item .
Thus, the IC conditions for type- MT can be denoted as
Our objective is to maximize the utility of the SP under IR and IC constraints, which is formulated into a contract optimization problem as
Problem 1.
In the next section, we will simplify the constraints in the optimization problem and provide an analysis for solving the simplified optimization problem.
4. Optimal Contract Design and Contract Deployment
We begin by exploring mathematical contract design in Section 4.1 of this section. In Section 4.2, AI-generated contract design introduces an AI-centric approach. Finally, in Section 4.3, we emphasize the practicality of using contracts in the real world.
4.1. Mathematical Based Contract Design
Since there are IR constraints and IC constraints in Problem 1, it is difficult to directly solve Problem 1 with complicated constraints. Specifically, it refers to the challenges posed by the large number of constraints associated with the increasing number of contracts. As the number of contracts increases, the constraints grow exponentially, and their non-convexity increases the complexity of the formula. Thus, we first reduce the number of attached constraints to reformulate Problem 1. Then, we further derive the solution theoretically.
Proof.
Please refer to [39]. □
Constraint (C1) related to the IR constraints ensures that the utility of each worker receiving the contract item of its type is non-negative. Constraints (C2), (C3), and (C4) are related to the IC constraints. Constraints (C2) and (C3) show that the IC constraints can be reduced as local downward incentive compatibility (LDIC) and local upward incentive compatibility (LUIC) with monotonicity, respectively [40]. Constraint (C4) indicates that a worker type with a lower cost can provide the SP with a higher update frequency. From Equation (20), we can know that when the lowest-type workers satisfy the IR constraints, the other types of workers will automatically hold the IR constraints. When type- and type- workers satisfy the IC constraints, the type- and the other types of workers will automatically hold the IC constraints. Thus, the original IR and IC constraints are transformed into constraints, and Problem 1 can be reformulated as
Problem 2.
Based on the first two constraints of (21), the optimal reward is calculated by the iterative method in a subsequent way. Thus, we can obtain as
where , .
By substituting (22) into in Problem 1, Problem 2 is reformulated as
Problem 3.
where
Since the optimization variables are coupled together, the functions and constraints are non-convex.
When is fixed and , the following Problem 4 is a convex problem in terms of . Problem 4 is defined as the following:
Problem 4.
where ,
.
It is noted that the only difference between Problem 3 and Problem 4 is that the objective function differs by a negative sign.
Proof.
First, we compute the second-order derivatives of in terms of and have
where ,
- and .
When and is fixed, is strictly convex on . Therefore, is a block multi-convex function in terms of [41]. Second, constraints (Problem 4 C1) is obviously the set of linear constraints. Thus, when is fixed, Problem 4 is a convex problem in terms of . □
Referring to [41], a block coordinate descent (BCD) method is used to solve Problem 4 and get . When the monotonicity cannot be met, we can utilize the infeasible sub-sequence replacing algorithm [42] to meet the monotonicity. Finally, we derive by substituting into Equation (22).
In this subsection, we lay the groundwork for an in-depth exploration of nuanced contract formulation by anchoring our approach to an established analytical methodology. Next, we move from the traditional paradigm to the AI paradigm.
4.2. AI-Generated Contract Design
The presence of distinct variables among users and the intricate nature of the wireless environment contribute to the intricacy of the contract structure, thus requiring periodic modifications using established mathematical methodologies. Therefore, we use a methodology based on diffusion models to tackle the above dilemmas.
In order to build a contract design, our AI-generated contract algorithm uses a denoising technique. It also incorporates exploration noise to gain experience in the exploration process. As shown in Figure 2, the processes taken by the algorithm to produce an AI-generated contract are as follows:
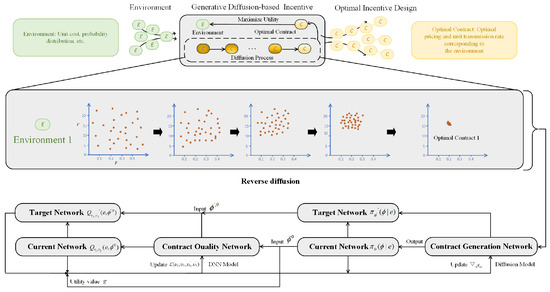
Figure 2.
Process of producing an AI-generated contract.
The diffusion-generated contract algorithm is designed to create optimal contracts through a blend of denoising methods, exploration noise, and policy optimization. It starts by defining a vector that encapsulates the current status of the contract service sector. The latent policy space, represented as , is explored using a conditional diffusion model. This exploration seeks the best contract based on the given state. Gaussian noise is introduced to and then iteratively denoised to yield to , allowing for precise contract adjustments. The specific mathematical form is as follows:
where can be modeled as a Gaussian distribution. This is specifically represented as: .
According to [43], the covariance matrix is defined as , and the mean constructed as . The training phase begins with setting key parameters such as batch size, exploration noise, and number of diffusion steps K. The contract generation network with weights and contract quality network with weights are initialized. According to [13], using double Q-learning, the best contract generation policy may be derived by minimizing the loss function :
where is the contract design policy. We construct two networks, namely and , with target networks, namely and , to learn the contract quality network in a conventional way, minimizing the Bellman operator with the double Q-learning technique [44]. We then optimize for by minimizing the objective
where is the target contract generation network. In each iteration, the environment’s state is observed, and actions are generated by denoising and adding exploration noise. Rewards are determined by the utility function, updating the replay buffer. Critic networks are improved using policy gradient and loss calculations, and the target networks are also updated to enhance performance over time. The final stage centers on crafting the best contract. Trained networks and environmental states are employed to deduce the contract. Gaussian noise is denoised using reverse diffusion to obtain an optimal contract , ensuring efficient resource allocation and maximizing utility based on the current conditions. Overall, the AI-generated contract algorithm seamlessly combines policy optimization and denoising methods to progressively refine contract representations, optimizing resource allocation and utility even under changing environmental circumstances.
The basic elements of the AI algorithm used to generate the contract are contained in the pseudocode provided. We will provide a brief review of the text for consistency.
- Training Phase: focuses on training AI-generated contracts. It initializes key components such as replay buffer, contract generation and quality networks, and target networks. The main loop iterates through episodes and steps, where the agent interacts with the environment, generates contracts, and learns to optimize contract quality. The training process involves computing rewards, updating networks, and performing target network updates, which are core elements of reinforcement learning (RL).
- Looping Pseudo-code: indicates the inference phase. In this phase, the trained AI-generated contract is used to generate the optimal contract design based on the given environment vectors. It utilizes the network, which has learned from the training phase to produce effective contracts.
In general, the pseudo-code provides a systematic description of the algorithm. This is consistent with RL frameworks that are often used to train agents to perform complex decision-making tasks such as contract generation. In addition, the parameters of the resource allocation scheme generated by Algorithm 1 during the process are shown in Table 3 and Table 4.
| Algorithm 1 The algorithm for diffusion-generated contract. |
|

Table 3.
Algorithm network parameters.

Table 4.
Algorithm training parameters.
In this subsection, the evolution of contracting strategies is demonstrated through the convergence of classical principles with cutting-edge AI techniques. However, there is still a need to discuss the implications of real-world scenarios. The practicalities and nuances of contract deployment are explored below.
4.3. Deployment of Contracts
In the intricate framework of mobile edge networks, the precise location of MTs is of paramount importance. The effectiveness of the SP is intrinsically linked to the assurance that each MT carefully selects an optimal contract item that is a good fit for its specific type. Intriguingly, the positioning of the microbase station, which hosts the MEC server, is static, underscoring its intransigent nature. Given this inflexibility, an optimal strategy pivots towards modulating a more adaptable entity: the UAV entrusted with the MEC server. By optimizing the spatial coordinates of the UAV, we can generate precision in the contract item delineation process. Upon the ratification of the contract selection across the MT spectrum, two salient parameters emerge into the limelight: the transmission rate inherent to each UAV and its concomitant reward. An astute observation at this juncture elucidates that the SP, armed with this newly found knowledge, discerns the precise location of each UAV. Such enlightenment precipitates a complex optimization conundrum: how to augment the SP’s utility by finessing the locational parameters of the edge nodes? This optimization enigma is elegantly captured as Problem 5:
Problem 5.
where . We also define , . And is the maximum communication range of the edge node.
Within this mathematical formulation, epitomizes the holistic utility derived by the SP. This metric is an amalgamation of a panoply of variables, encompassing the fiscal dynamics associated with diverse transmission rates and a confluence of incentives vis-à-vis the spatial dynamics of MTs.
Nevertheless, the inherent nonconvexity of Problem 5 augments the problem’s complexity. To navigate this intricate maze, our strategic pivot leans towards the meta-heuristic paradigm, notably harnessing the prowess of the improved differential evolution (DE) algorithm. We propose finding optimal location using differential evolution algorithm, and the specific process is represented by Algorithm 2.
| Algorithm 2 Finding optimal location using differential evolution algorithm. |
|
5. Simulation Results
We perform simulations in MATLAB to verify that the proposed incentive mechanism is effective. The numerical results show that the proposed incentive mechanism has a great advantage in improving the utility of the system when compared with other benchmark incentives. We consider that the probability of each type is uniform in . Referring to [45,46,47,48], other parameters are summarized in Table 5.

Table 5.
Parameter settings in the simulation.
5.1. Evaluation of the Proposed Contract Design under Certain Environment
5.1.1. Efficiency of Contract Design
In Figure 3, we evaluate the IR and the IC conditions of our proposed algorithm. Figure 3 shows the utilities of type-1, type-2, type-3, type-4, and type-5 MTs when selecting all the contracts offered by MEC servers. For example, for type 1, it can be seen that each MT can maximize its utility when selecting the contract that fits its own types, which means that the IC constraints are satisfied. Furthermore, each type of MTs receives a positive utility value when selecting the contract that fits their types, which suggests that the IR constraints are satisfied. Therefore, after choosing the best contract that is designed for its own type, the types of the MTs will be revealed to the MEC server. Therefore, by applying the proposed scheme, each MEC server is able to be aware of the exact types of the MTs, which means that the asymmetric information between the MEC server and the MTs is overcome. Moreover, the utilities of higher type of MTs are larger than those of lower type of MTs.
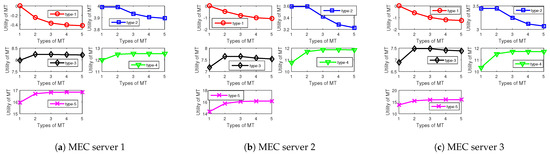
Figure 3.
Types of MT versus utilities of MTs under different MEC servers.
5.1.2. Impact of Interference on System Performance
Figure 4 shows the performance system versus maximum delay under different interference strategies. Details of these interference strategies are listed as follows:
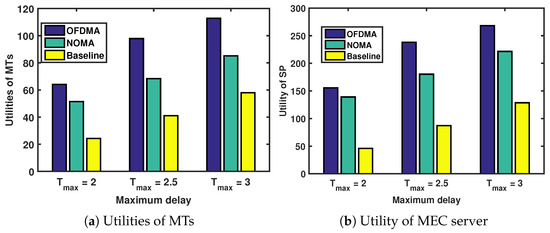
Figure 4.
Utilities of MTs and MEC server versus number of MT types under different interference strategies.
- OFDMA: Each MT in cross-layer and co-layer adopts orthogonal frequency-division multiple access (OFDMA) to offload computation tasks. OFDMA optimizes bandwidth via orthogonal subcarriers, ensuring interference-free transmission. Users on different subcarriers achieve mutual orthogonality, enhancing communication efficiency.
- NOMA: In both cross-layer and co-layer scenarios, each MT employs NOMA as a means to offload computational chores. NOMA permits multiple users to share the same subchannel, boosting spectral efficiency and ensuring rapid transmission. Unlike OFDMA, NOMA has less of the near–far effect and works best in dynamic link states, maintaining a strong rate performance even when there are problems with multi-access interference.
- Baseline: Each MT in both cross-layer and co-layer settings shares the same channel for computational task offloading.
5.1.3. Performance Comparison
We compare the proposed contract-based incentive mechanism under asymmetric information (CA) with other incentive mechanisms, including the Stackelberg game-based incentive mechanism under asymmetric information (SA) [33]. For the SA mechanism, the utilities of MTs and the SP are as follows:
and
where .
Figure 5 depicts the relationship between the utilities of the MTs (and the SP) and maximum delay under different incentive mechanisms.
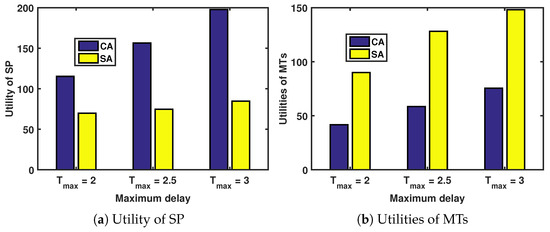
Figure 5.
Utilities of MTs and the SP versus maximum delay under different incentives.
The utilities of the SP and the MTs increase with the maximum delay, as shown in Figure 5a and Figure 5b, respectively. Additionally, we analyze the utilities of the SP and the MTs under different incentive mechanisms when the maximum delay is fixed. Since the research objective is to maximize the utility of SP, it is necessary to ensure that the SP utility is maximized when the MT utility is non-negative.
In Figure 5a, the CA approach achieves the best performance among the two approaches. This is because the CA approach aims to collect as much revenue from the MTs as possible while satisfying both the IR and IC constraints, leaving only a small share of revenue for the MTs. In contrast, the SG strategy aims to maximize the combined utility of the SP and the MTs, allowing for more revenue to be allocated to the MTs. In Figure 5b, the CA approach provides better utilities for the MTs than the SA approach. This is due to the same reasons mentioned in Figure 5a.
5.1.4. Impact of System Parameters on System Performance
When and , Figure 6 shows the performance system versus trade-off parameter. As increases, the utility of the MTs and SP decreases.
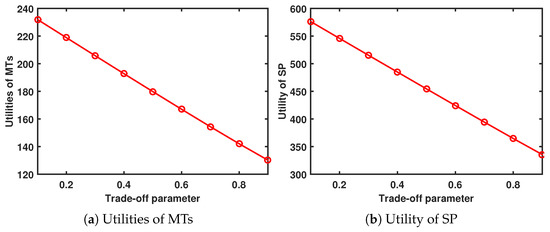
Figure 6.
Performance system versus trade-off parameter.
When and , Figure 7 shows the performance system versus the trade-off parameter. As increases, the utility of the MTs and SP increases.
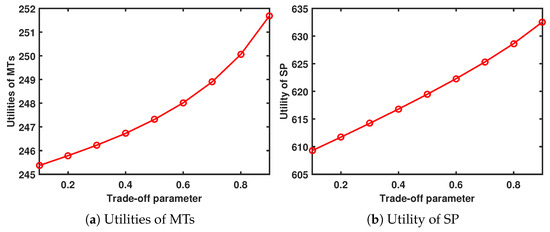
Figure 7.
Performance system versus trade-off parameter.
When and , Figure 8 shows the performance system versus trade-off parameter. As increases, the utility of the MTs and SP first decreases and then decreases.
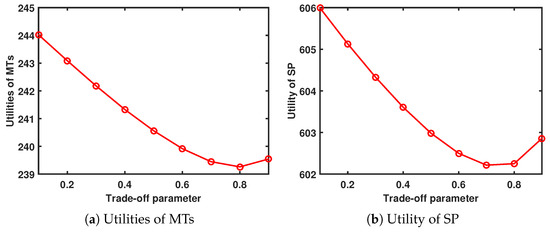
Figure 8.
Performance system versus trade-off parameter.
When and , Figure 9 shows the performance system versus maximum delay. As increases, the utility of the MTs and SP increases. The increase in increases the gain for the MTs, so the MTs are willing to pay more rewards for the SP, which means that the utility of the SP also increases.
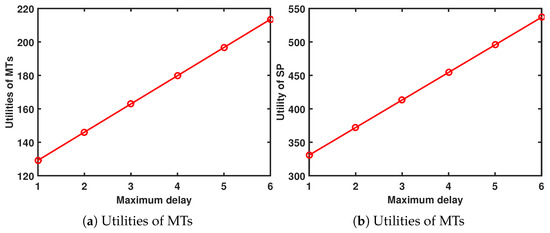
Figure 9.
Performance system versus maximum delay.
When and , Figure 10 illustrates the performance system in relation to the maximum AoI. As the maximum AoI increases, the utilities of both the MTs and the SP increase. The MTs gain more when the maximum AoI is higher, so they are willing to offer more rewards to the SP, thus increasing the SP’s utility.
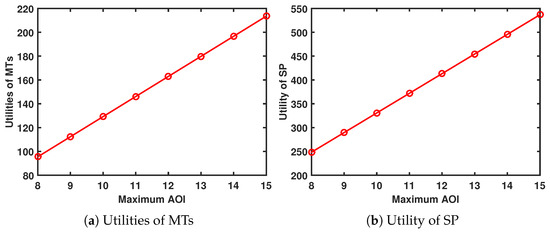
Figure 10.
Performance system versus maximum AoI.
5.2. Evaluation of the Proposed Generative AI-Aided Contract Design under Uncertain Environment
We conducted a comparative analysis of our suggested artificial intelligence (AI)-generated contract algorithm and two traditional DRL algorithms, namely SAC and proximal PPO. The training process, as depicted in Figure 11, demonstrates that the PPO algorithm requires a greater number of iteration steps in order to achieve convergence. Although the SAC method exhibits a relatively rapid stabilization at a higher reward level, it is important to note that both its convergence rate and final reward value are comparatively worse when compared to the AI-generated contract approach. This phenomenon can be attributed to two factors:
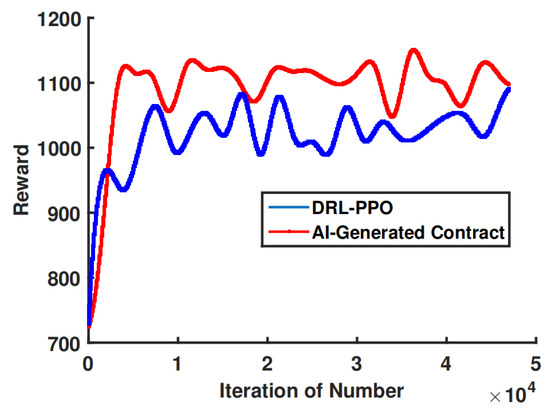
Figure 11.
Training process.
- Our algorithm produces higher-quality samples by utilizing diffusion models and fine-tuning multiple times. By setting the diffusion step to 10 and gradually adjusting the model’s output with each fine tuning, the impact of uncertainty and noise is reduced, resulting in improved sampling accuracy.
- Our approach is better able to handle long-term dependencies. In contrast to traditional neural network generation models that solely take into account the input at the present time step, the diffusion model undergoes numerous fine-tuning iterations to produce samples including a greater number of time steps. This phenomenon leads to an enhanced capacity for long-term reliance processing.
Figure 12 shows the comparison of the trained models’ capacity for optimal contract design. For type-3 MTs, when given a particular environment state, the AI-generated contract algorithm can generate a contract design that yields a higher utility than the utility obtained by the DRL-PPO.
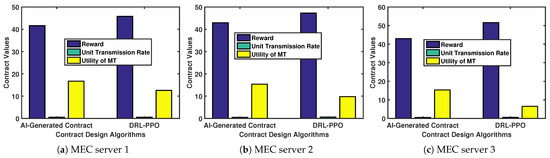
Figure 12.
Contract design algorithms.
5.3. Contract Deployment Optimal Design
We consider a scenario in which there are three MEC servers, and every MEC server located within a 100 m radius has its own UAV. We set the location of three MEC severs as (−100 m, −100 m), (100 m, −100 m), and (0, 100 m). Then, 20 users are randomly generated within the 100 m radius of each MEC server. Fifteen of these users are served by each MEC server, and five are served by the UAV. We show in Figure 13 that the service delivery of MT is enhanced by optimizing the location coordinates of the UAVs, the result of which leads to an optimal contract deployment design. Figure 14 shows the utility of the SP versus different interference strategies under the optimal location of UVAs. Since there is no interference in the OFDMA strategy, the SP allows MTs to use the lowest power to achieve a transmission rate that meets the delay and AOI requirements, which reduces the SP cost and maximizes the utility of the SP. Interference with the baseline strategy causes MTs to use more power to meet latency and AOI requirements, increasing the SP cost and minimizing the utility of the SP.
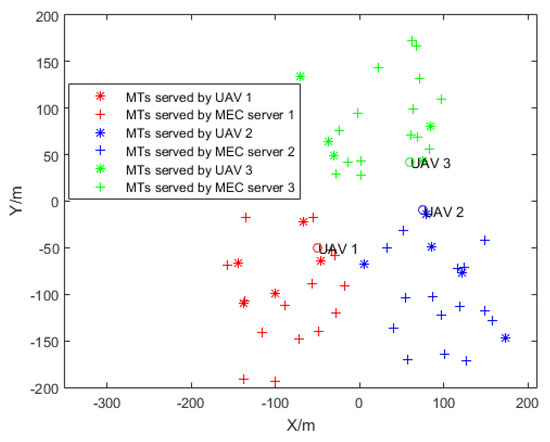
Figure 13.
Optimal location of UVAs in different MEC servers.
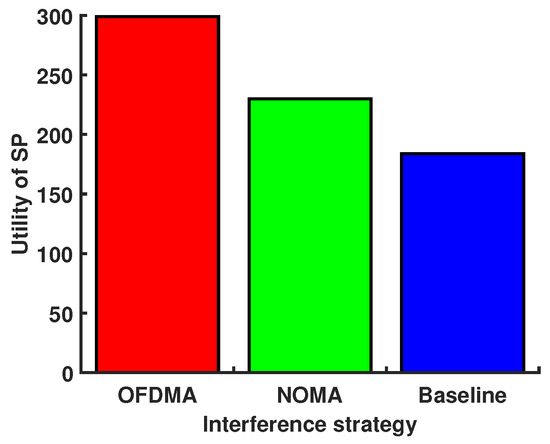
Figure 14.
Utility of the SP versus different interference strategies under the optimal location of UVAs.
6. Conclusions
We suggest implementing an incentive system that comprises two distinct stages: contract design and deployment. During the contract design phase, we create a mechanism using contract theory. It optimizes the utility of the SP while satisfying the IR and IC requirements of the mobile customer. We use the block coordinate descent method to discover the most favorable contract and introduce a new strategy based on the generative diffusion model to improve the efficiency of finding the best contract. During the contract deployment phase, the effectiveness of SP contract deployment is enhanced by optimizing the positioning of UAVs. To do this, a refined differential evolutionary algorithm is introduced to determine the most optimum site for the UAVs. The rigorous empirical evaluation shows that under incentive-consistent conditions, our approach has improved over the baseline approach (each MT in both cross-layer and co-layer settings shares the same channel for computational task offloading) by nearly 100%. When NOMA is employed, the incentive methods we use nearly double the SP efficiency on average.
In the next step of our research, we will discuss how UAV trajectories and UAV speeds affect resource allocation strategies.
Author Contributions
Conceptualization, Z.S.; methodology, Z.S.; validation, Z.S.; data curation, Z.S.; writing—original draft preparation, Z.S.; writing—review and editing, G.C.; visualization, Z.S.; project administration, Z.S.; funding acquisition, G.C. All authors have read and agreed to the published version of the manuscript.
Funding
Special Industrial Technology Research Project of Jilin Province, Research on Self-organizing Network System of Unmanned Platform for Optoelectronic Composite Communication, No.2022C047-8; Supported by “Thirteenth Five-Year Plan” of Provincial Science and Technology of Education Department of Jilin Province, Research on Large-scale D2D Access and Traffic Balancing Technology for Heterogeneous Wireless Networks (JJKH20181130KJ).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Chen, M.; Hao, Y. Task offloading for mobile edge computing in software defined ultra-dense network. IEEE J. Sel. Areas Commun. 2018, 36, 587–597. [Google Scholar] [CrossRef]
- Yates, R.D.; Sun, Y.; Brown, D.R.; Kaul, S.K.; Modiano, E.; Ulukus, S. Age of information: An introduction and survey. IEEE J. Sel. Areas Commun. 2021, 39, 1183–1210. [Google Scholar] [CrossRef]
- Chen, X.; Wu, C.; Chen, T.; Liu, Z.; Zhang, H.; Bennis, M.; Liu, H.; Ji, Y. Information freshness-aware task offloading in air-ground integrated edge computing systems. IEEE J. Sel. Areas Commun. 2021, 40, 243–258. [Google Scholar] [CrossRef]
- Singh, S.; Andrews, J.G. Joint resource partitioning and offloading in heterogeneous cellular networks. IEEE Trans. Wirel. Commun. 2013, 13, 888–901. [Google Scholar] [CrossRef]
- Al-Zahrani, A.Y.; Yu, F.R. An energy-efficient resource allocation and interference management scheme in green heterogeneous networks using game theory. IEEE Trans. Veh. Technol. 2015, 65, 5384–5396. [Google Scholar] [CrossRef]
- Xu, C.; Zheng, G.; Zhao, X. Energy-minimization task offloading and resource allocation for mobile edge computing in noma heterogeneous networks. IEEE Trans. Veh. Technol. 2020, 69, 16001–16016. [Google Scholar] [CrossRef]
- Fan, W.; Han, J.; Su, Y.; Liu, X.; Wu, F.; Tang, B.; Liu, Y. Joint task offloading and service caching for multi-access edge computing in wifi-cellular heterogeneous networks. IEEE Trans. Wirel. Commun. 2022, 21, 9653–9667. [Google Scholar] [CrossRef]
- Ma, X.; Zhou, A.; Sun, Q.; Wang, S. Freshness-aware information update and computation offloading in mobile-edge computing. IEEE Internet Things J. 2021, 8, 13115–13125. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Yu, H.; Liang, Y.-C.; Kim, D.I. Incentive design for efficient federated learning in mobile networks: A contract theory approach. In 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS); IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Zhu, P.; Hu, J.; Li, X.; Zhu, Q. Using blockchain technology to enhance the traceability of original achievements. IEEE Trans. Eng. Manag. 2023, 70, 1693–1707. [Google Scholar] [CrossRef]
- Cai, Y.; Ke, W.; Cui, E.; Yu, F. A deep recommendation model of cross-grained sentiments of user reviews and ratings. Inf. Process. Manag. 2022, 59, 102842. [Google Scholar] [CrossRef]
- Du, H.; Wang, J.; Niyato, D.; Kang, J.; Xiong, Z.; Kim, D.I. Ai-generated incentive mechanism and full-duplex semantic communications for information sharing. IEEE J. Sel. Areas Commun. 2023, 41, 2981–2997. [Google Scholar] [CrossRef]
- Park, C.; Lee, J. Mobile edge computing-enabled heterogeneous networks. IEEE Trans. Wirel. Commun. 2020, 20, 1038–1051. [Google Scholar] [CrossRef]
- Wu, H.; Tian, H.; Fan, S.; Ren, J. Data age aware scheduling for wireless powered mobile-edge computing in industrial internet of things. IEEE Trans. Ind. Inform. 2020, 17, 398–408. [Google Scholar] [CrossRef]
- Sun, J.; Jiang, Z.; Krishnamachari, B.; Zhou, S.; Niu, Z. Closed-form whittle’s index-enabled random access for timely status update. IEEE Trans. Commun. 2019, 68, 1538–1551. [Google Scholar] [CrossRef]
- Kuang, Q.; Gong, J.; Chen, X.; Ma, X. Age-of-information for computation-intensive messages in mobile edge computing. In Proceedings of the 2019 11th International Conference on Wireless Communications and Signal Processing (WCSP), Xi’an, China, 23–25 October 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Kuang, Q.; Gong, J.; Chen, X.; Ma, X. Analysis on computation-intensive status update in mobile edge computing. IEEE Trans. Veh. Technol. 2020, 69, 4353–4366. [Google Scholar] [CrossRef]
- Liu, L.; Qin, X.; Zhang, Z.; Zhang, P. Joint task offloading and resource allocation for obtaining fresh status updates in multi-device mec systems. IEEE Access 2020, 8, 38248–38261. [Google Scholar] [CrossRef]
- Muhammad, A.; Sorkhoh, I.; Samir, M.; Ebrahimi, D.; Assi, C. Minimizing age of information in multiaccess-edge-computing-assisted iot networks. IEEE Internet Things J. 2021, 9, 13052–13066. [Google Scholar] [CrossRef]
- Zhu, Z.; Wan, S.; Fan, P.; Letaief, K.B. An edge federated marl approach for timeliness maintenance in mec collaboration. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–6. [Google Scholar]
- Zhang, G.; Shen, C.; Shi, Q.; Ai, B.; Zhong, Z. Aoi minimization for wsn data collection with periodic updating scheme. IEEE Trans. Wirel. Commun. 2023, 22, 32–46. [Google Scholar] [CrossRef]
- Yuan, X.; Xie, Z.; Tan, X. Computation offloading in uav-enabled edge computing: A stackelberg game approach. Sensors 2022, 22, 3854. [Google Scholar] [CrossRef]
- Chen, X.; Wu, C.; Chen, T.; Liu, Z.; Bennis, M.; Ji, Y. Age of information-aware resource management in uav-assisted mobile-edge computing systems. In Proceedings of the GLOBECOM 2020-2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Qin, Z.; Wei, Z.; Qu, Y.; Zhou, F.; Wang, H.; Ng, D.W.K.; Chae, C.-B. Aoi-aware scheduling for air-ground collaborative mobile edge computing. IEEE Trans. Wirel. Commun. 2023, 22, 2989–3005. [Google Scholar] [CrossRef]
- Zhu, B.; Chi, K.; Liu, J.; Yu, K.; Mumtaz, S. Efficient offloading for minimizing task computation delay of noma-based multiaccess edge computing. IEEE Trans. Commun. 2022, 70, 3186–3203. [Google Scholar] [CrossRef]
- Liu, L.; Qiang, J.; Wang, Y.; Jiang, F. Age of information analysis of noma-mec offloading with dynamic task arrivals. In Proceedings of the 2022 14th International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 14–17 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 181–186. [Google Scholar]
- Yang, Y.; Wang, W.; Xu, R.; Srivastava, G.; Alazab, M.; Gadekallu, T.R.; Su, C. Aoi optimization for uav-aided mec networks under channel access attacks: A game theoretic viewpoint. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Lv, H.; Zheng, Z.; Wu, F.; Chen, G. Strategy-proof online mechanisms for weighted aoi minimization in edge computing. IEEE J. Sel. Areas Commun. 2021, 39, 1277–1292. [Google Scholar] [CrossRef]
- Su, C.; Ye, F.; Liu, T.; Tian, Y.; Han, Z. Computation offloading in hierarchical multi-access edge computing based on contract theory and bayesian matching game. IEEE Trans. Veh. Technol. 2020, 69, 13686–13701. [Google Scholar] [CrossRef]
- Lim, W.Y.B.; Xiong, Z.; Kang, J.; Niyato, D.; Leung, C.; Miao, C.; Shen, X. When information freshness meets service latency in federated learning: A task-aware incentive scheme for smart industries. IEEE Trans. Ind. Inform. 2022, 18, 457–466. [Google Scholar] [CrossRef]
- Li, S.; Hu, X.; Du, Y. Deep reinforcement learning and game theory for computation offloading in dynamic edge computing markets. IEEE Access 2021, 9, 121456–121466. [Google Scholar] [CrossRef]
- Xu, Y.; Xiao, M.; Zhu, Y.; Wu, J.; Zhang, S.; Zhou, J. Aoi-guaranteed incentive mechanism for mobile crowdsensing with freshness concerns. IEEE Trans. Mob. Comput. 2023, 1–17. [Google Scholar] [CrossRef]
- Diao, X.; Zheng, J.; Wu, Y.; Cai, Y.; Anpalagan, A. Joint trajectory design, task data, and computing resource allocations for noma-based and uav-assisted mobile edge computing. IEEE Access 2019, 7, 117448–117459. [Google Scholar] [CrossRef]
- Makki, B.; Chitti, K.; Behravan, A.; Alouini, M.-S. A survey of noma: Current status and open research challenges. IEEE Open J. Commun. Soc. 2020, 1, 179–189. [Google Scholar] [CrossRef]
- Li, C.; Wang, S.; Huang, X.; Li, X.; Yu, R.; Zhao, F. Parked vehicular computing for energy-efficient internet of vehicles: A contract theoretic approach. IEEE Internet Things J. 2018, 6, 6079–6088. [Google Scholar] [CrossRef]
- Sun, Z.; Chen, G. Contract-optimization approach (coa): A new approach for optimizing service caching, computation offloading, and resource allocation in mobile edge computing network. Sensors 2023, 23, 4806. [Google Scholar] [CrossRef] [PubMed]
- Zhou, Z.; Liu, P.; Feng, J.; Zhang, Y.; Mumtaz, S.; Rodriguez, J. Computation resource allocation and task assignment optimization in vehicular fog computing: A contract-matching approach. IEEE Trans. Veh. Technol. 2019, 68, 3113–3125. [Google Scholar] [CrossRef]
- Zhang, K.; Mao, Y.; Leng, S.; Maharjan, S.; Vinel, A.; Zhang, Y. Contract-theoretic approach for delay constrained offloading in vehicular edge computing networks. Mob. Netw. Appl. 2019, 24, 1003–1014. [Google Scholar] [CrossRef]
- Hou, Z.; Chen, H.; Li, Y.; Vucetic, B. Incentive mechanism design for wireless energy harvesting-based internet of things. IEEE Internet Things J. 2017, 5, 2620–2632. [Google Scholar] [CrossRef]
- Xu, Y. Block Coordinate Descent for Regularized Multi-Convex Optimization; Rice University: Houston, TX, USA, 2013. [Google Scholar]
- Gao, L.; Wang, X.; Xu, Y.; Zhang, Q. Spectrum trading in cognitive radio networks: A contract-theoretic modeling approach. IEEE J. Sel. Areas Commun. 2011, 29, 843–855. [Google Scholar] [CrossRef]
- Ho, J.; Jain, A.; Abbeel, P. Denoising diffusion probabilistic models. Adv. Neural Inf. Process. Syst. 2020, 33, 6840–6851. [Google Scholar]
- Hasselt, H. Double q-learning. In Advances in Neural Information Processing Systems 23; Neural Information Processing Systems Foundation, Inc. (NeurIPS): La Jolla, CA, USA, 2010. [Google Scholar]
- Liu, M.; Liu, Y. Price-based distributed offloading for mobile-edge computing with computation capacity constraints. IEEE Wirel. Commun. Lett. 2017, 7, 420–423. [Google Scholar] [CrossRef]
- Wang, S.; Ye, D.; Huang, X.; Yu, R.; Wang, Y.; Zhang, Y. Consortium blockchain for secure resource sharing in vehicular edge computing: A contract-based approach. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1189–1201. [Google Scholar] [CrossRef]
- Xiao, H.; Zhao, J.; Pei, Q.; Feng, J.; Liu, L.; Shi, W. Vehicle selection and resource optimization for federated learning in vehicular edge computing. IEEE Trans. Intell. Transp. Syst. 2021, 23, 11073–11087. [Google Scholar] [CrossRef]
- Feng, J.; Zhang, W.; Pei, Q.; Wu, J.; Lin, X. Heterogeneous computation and resource allocation for wireless powered federated edge learning systems. IEEE Trans. Commun. 2022, 70, 3220–3233. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).