Abstract
Ciphertext policy–attribute-based encryption (CP-ABE), which provides fine-grained access control and ensures data confidentiality, is widely used in data sharing. However, traditional CP-ABE schemes often choose to outsource data to untrusted third-party cloud service providers for storage or to verify users’ access rights through third parties, which increases the risk of privacy leakage and also suffers from the problem of opaque permission verification. This paper proposes an access control scheme based on blockchain and CP-ABE, which is based on multiple authorization centers and supports policy updating. In addition, blockchain technology’s distributed, decentralized, and tamper-proof features are utilized to solve the trust crisis problem in the data-sharing process. Security analysis and performance evaluation show that the proposed scheme improves the computational efficiency by 18%, 26%, and 68% compared to previous references. The proposed scheme also satisfies the indistinguishability under chosen-plaintext attack (IND-CPA).
1. Introduction
With the advent of the big data era, data have become an important economic asset and a new factor of production permeating all walks of life. With increasing data resource sharing, incidents such as data theft and information leakage have occurred repeatedly. In May 2022, General Motors released a statement saying that some online customers had suspicious logins and that hackers had accessed some of their personal information through an online mobile application, including names, email addresses, mailing addresses, interest collections, search history, etc. In December of the same year, Azalea Motors suffered a server misconfiguration that led to the leakage of millions of user information and was subjected to a ransom demand of USD 2.25 million in Bitcoin equivalent. To prevent incidents like these, data owners often want to keep their data under control after they have been shared. Access control is an effective means to protect data security and control the flow and sharing of data. It explicitly allows or restricts the subject’s access to the object in a certain way, allowing users to access data within their legitimate permissions. If not, their operations are prohibited. Traditional access control cannot cope with the characteristics of a high degree of sharing and fast data circulation in the big data environment, and problems such as a single point of failure, difficulty in meeting the principle of minimum authorization, difficulty in dynamically adapting to changes in the environment, and difficulty in verifying policy authority have brought “shackles” to the development of access control technology.
The emergence of Attribute-Based Encryption (ABE) [1] brings a new solution to the above problem, which was first proposed by Sahai et al. in 2005, and subsequently developed into Key Policy–Attribute-Based Encryption (KP-ABE) [2] and Ciphertext Policy–Attribute-Based Encryption (CP-ABE) [3]. Data owners can customize access policies in CP-ABE and embed them in ciphertext. This approach not only realizes fine-grained and flexible access control but also solves the problems of traditional access control, which is challenging to satisfy the principle of minimum authorization and dynamically adapt to environmental changes. However, traditional CP-ABE schemes still have some drawbacks in practical applications. For example, in most CP-ABE schemes, with the help of a fully trusted attribute authorization authority, a single authorization authority needs to manage all users’ attributes and be responsible for the key generation and distribution process, which is a considerable workload. Moreover, if the single authorization center in these schemes fails or is maliciously attacked, many user attribute data will be exposed, and the whole system will be affected [4].
Blockchain technology [5], a widely emerging distributed-ledger-based technology, has become a reasonable choice for conducting trusted access control due to its decentralization, data tampering, traceability, non-falsification, and programmability. However, blockchain’s open and transparent nature makes the security and regulation of data stored in blockchain face a series of challenges [6,7]. If blockchain technology is combined with CP-ABE, the cryptographic mechanism of CP-ABE can ensure the confidentiality, privacy, and security of the data stored on the blockchain. In contrast, blockchain technology can provide functions like trusted authority verification and effective auditing for the existing CP-ABE-based schemes. For example, the programs in reference [8] achieve privacy protection and support the accountability of historical protocols through CP-ABE and blockchain technology. Reference [9] considers the advantages of CP-ABE and blockchain combined with cloud storage systems to share medical information effectively. Still, cloud servers storing a large amount of data can lead to privacy leakage and access control that policy permissions cannot credibly verify.
The leading platforms for blockchain applications are Bitcoin, Ethereum, and Hyperledger Fabric. Bitcoin is the blockchain technology’s prototype but lacks privacy protection and smart contracts. As a result, it cannot be used in complex situations. Ethereum is the public blockchain. However, any transaction on Ethereum requires payment. The public blockchain also has no restrictions on participants, who usually participate anonymously, making the public chain quite difficult to regulate. Fabric, as a representative of the consortium blockchain, requires participants to have explicit identifiers so that a malicious participant can be found directly. Therefore, Fabric is more secure than Ethereum. In addition, Fabric provides strong flexibility, pluggability, and scalability by modularizing the technologies of rights management, authentication, consensus mechanism, etc. Fabric can be more easily applied to complex scenarios by designing and developing smart contracts to execute various business logic.
Fabric can also design and develop smart contracts to implement different business logic, making it easier to apply to complex environments.
In summary, the existing schemes still have problems in access control, such as data leakage caused by semi-trusted cloud service providers, a non-transparent and untrustworthy verification of access privileges, an over-concentration of risk in single authorization centers, and overloaded computation. To solve the above problems, this paper proposes an access control scheme based on blockchain and CP-ABE, based on the characteristics of blockchain being de-trusted, decentralized, non-tamperable, and non-forgeable. The main contributions of this paper are as follows:
- A new blockchain-based attribute-based cryptographic access control model is proposed. The introduction of blockchain in this model realizes the auditability of key parameter transmission and the trusted verification of data integrity, decryption correctness, etc., and solves the opaque verification problem of access rights caused by untrusted third parties. The combination of attribute-based encryption and blockchain guarantees that the data owner autonomously and effectively controls the circulation of shared data and protects the security of shared data.
- An improved CP-ABE algorithm supporting access policy updates is proposed. This algorithm updates the access policy without disclosing the original encrypted data and realizes finer-grained and more flexible one-to-many access control with high efficiency and low overhead.
- Using the threshold secret sharing algorithm to split the private key parameters of data visitors, the user private key needs to be calculated by multiple authorization centers collaboratively. Therefore, a single authorization center does not have the ability to generate user private keys. This method not only solves the problems of poor security, heavy computational burden, and unguaranteed data integrity of a single authorization organization, but also improves user privacy and key security.
2. Related Works
Currently, some research focuses on using a single authorization center for access control of attribute-based encryption in cloud computing environments. For instance, Li et al. [10] suggested a safe data-sharing system based on attribute encryption for users with restricted resources. By boosting the system’s public parameters and transferring a portion of the encrypted calculations to an offline state, this approach removed the majority of the calculation jobs. However, this scheme’s access strategy was limited to a description of positive and negative characteristics, leaving out the overall access control framework. Since we must completely rely on the single authorization center, if it is attacked, all the attributes will be accessed, thus lowering the security of the data stored in the cloud.
A solution with numerous authorization centers was created on the foundation of the conventional centralized single authorization agency solution in order to address the issues of low efficiency and inadequate security of a single authorization center. By expanding attribute sources and decentralizing the central master key, the attribute-based encryption scheme of the authorization center increased the variety of access tactics and encryption security. Sharma et al. [11] resolved the key escrow problems by using two authorities in the key generation process. Data owners and attribute authorities manage the key-related and user access policy details in a distributed manner. A new CP-ABE technique for multi-authorization agencies was also created by Gao et al. [12], which enhances user privacy and key security while significantly reducing the possibility of a single point of failure. A method called T-DPU-MCP-ABE (Traceable and Dynamic Policy Updating Multiauthority Attribute-based Encryption) was proposed by Ling et al. [13] in 2021. Data owners may frequently need to adjust the ciphertext access policy to meet diverse requirements. Updates to rules give data owners flexibility and enable them to fine-tune their encrypted data access restrictions for more precise control. A multi-authorization attribute-based encryption system with policy updating and concealing was suggested by Zhang et al. [14]. The untrusted issue with single attribute authorization is likewise resolved by multiple attribute authorities. Data owners can also easily and affordably adjust the access control policy. However, the above scenario relies on a fully trusted agent or a third-party central authority in addition to a semi-trusted multi-authorization center. In practical scenarios, fully trusted agents and third-party central organizations do not exist, and semi-trusted third parties bring new privacy issues. The multi-authorization center scheme proposed in this paper does not rely on a third party and can solve the trust problem in practical applications.
Blockchain technology [5] is an evolving technology with the advantage of decentralization, which is based on a distributed ledger. The issue of data in cloud storage that can be tampered with and whose integrity cannot be guaranteed has been resolved with the creation of blockchain technology [15]. Additionally, this technology is ideally suited to address issues related to ABE. Therefore, to better realize the secure and dependable large-scale exchange of vast data, researchers have recently integrated blockchain and attribute-based encryption technology. An independently revised key strategy ABE system was put forth by Guo et al. [16]. In addition, utilizing blockchain and distributed database technology protected the integrity of private healthcare data stored in the public cloud, preventing nefarious users or authorizers from tampering with private data from the internal cloud, thereby reducing misdiagnosis caused by tampered electronic health records. This scheme was managed by multiple attribute authorization centers, which was closer to the actual situation. To accomplish fine-grained access control to data, Zuo et al. [17] integrated blockchain with attribute-based encryption technology, making all user operations on the chain immutable and permanently maintained. In order to enable cloud security sharing without the usage of a trusted third party, blockchain was employed to authenticate user identities and manage their access privileges. This system prevented unauthorized users from accessing the data until user identification verification was complete. To protect data and attribute privacy, Gao et al. [18] introduced the ABE approach to the blockchain. Due to the strategy’s limited applicability to the compound order group, efficiency was low. A decentralized architecture was proposed by Vasishta et al. [19] to validate access requests through numerous authorities in a decentralized way using Hyperledger Fabric and Attribute-Based Access Control (ABAC). Reference [20] suggested putting ABAC into practice for decentralized authorization across numerous entities. Each organization in this implementation has a separate smart contract to add properties. A blockchain-based cloud data access authorization updating mechanism that supports keyword retrieval was proposed by Lei et al. [21]. According to reference [22], an industrial client can also validate the legitimacy of an IoT device’s distributor and manufacturer and grant permission for the IoT device to join their IoT network by issuing a network certificate. In reference [23], a multi-layer strategy uses blockchain technology for IoT device authentication and authorization. Some of the above research solutions use blockchain to solve only the cloud storage problem, and some only use blockchain for authorization, which does not involve whether the data owner can control the users who access the data. The proposed scheme in this paper uses the consortium blockchain fabric to verify the data in a trustworthy way and realizes transparent pre-verification of access rights by deploying smart contracts on the blockchain so that the data owner has the right to decide who can access the data and realizes true data security.
3. Access-Control-Scheme-Based Blockchain and CP-ABE
3.1. Main Parameters and Definitions
The main parameters involved in the scheme of this paper are shown in Table 1.

Table 1.
Main parameters and definitions.
3.2. System Model
The system model proposed in this paper is shown in Figure 1, which includes four types of entities: Data Owner (), Data Visitor (), Attribute Authorization Center (), and Blockchain ().
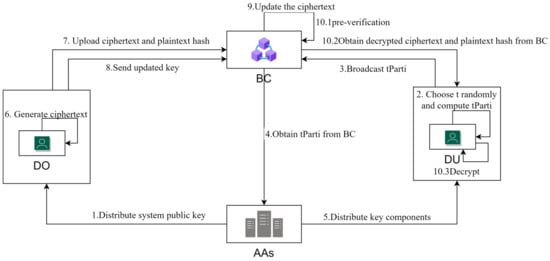
Figure 1.
System model.
1. computes the system public key and system master key and distributes the system public key to . 2. randomly selects the t-value and computes . 3. broadcasts the computed to nodes. 4. When the data visitor needs to obtain its private key, the attribute authorization center obtains from . 5. distributes the private key component of obtained by substituting to . 6. generates the ciphertext by specifying a specific access policy. 7. then uploads the ciphertext and the hash value of the plaintext to . 8. If the access policy needs to be updated, sends the updated key to . 9. updates the ciphertext based on the updated key. 10.1 After obtains the key component from , pre-verifies whether has the access right to the data uploaded by . 10.2 If the verification passes, can obtain the ciphertext and the hash value of the plaintext from . 10.3 decrypts the ciphertext with its private key. In the above process, the entities undertake the following tasks (see Figure 1):
- : Organizations that manage attributes in the system. It manages the respective attributes and generates the master key MSK and system public key PK in step 1. In step 4, it obtains the slice of t, , from the computation nodes in the blockchain and distributes the private key component of to the in step 5.
- : Users who want to access the data uploaded by the . In steps two and three, DU is responsible for computing and broadcasting it to the blockchain. obtains the pre-verification result from the blockchain in part 10.1 of step 10. And if the has access to the data, the obtains the ciphertext and the hash values of the plaintext in part 10.2 of step 10, decrypts them, and verifies the correctness of using the private key of the in part 10.3. If required, can verify the correctness of decryption by querying the blockchain transaction.
- : The user who owns the data and specifies the attributes the visitor requires. The data owner encrypts the plaintext data using a symmetric key, specifies the access policy for the data, encrypts the symmetric key to generate the ciphertext in step 6, and uploads the ciphertext and the data digest to the blockchain through a transaction in step 7. Based on the running results of the policy comparison algorithm deployed on the smart contract, selects the corresponding update key to send to the blockchain via the transaction in step 8.
- : Consortium blockchain fabric, a platform that ensures that data are stored and shared in a trusted manner. Users can publish and query transactions on the blockchain, providing storage services to secure data ( and ciphertext) and services for trusted authentication. In step 9, the blockchain performs the ciphertext update. The blockchain also does the 10.1 pre-verification part of the decryption phase.
3.3. Security Model
Choice Plaintext Attack (CPA) means that the attacker can select a plaintext message in addition to knowing the encryption algorithm to obtain the encrypted ciphertext, i.e., the attacker knows the chosen plaintext and the encrypted ciphertext. Still, they cannot directly break the key. Proof of security is performed by choosing a game of indistinguishability under a plaintext attack, and a game between an adversary and a challenger describes this game.
- Initialization phase. Challenger runs the system initialization algorithm, inputs the security parameter , outputs the system public key PK and sends it to adversary , and saves the system master key MSK. Adversary selects the old access policy and the new access policy that it wishes to attack.
- Querying private key phase 1. Adversary adaptively submits a series of attribute sets that do not satisfy the old and new access policies to challenger . runs the key generation algorithm to generate the corresponding key SK to sends it to adversary .
- Challenge phase. Adversary submits two equal-length messages and to challenger . randomly selects and runs a cryptographic algorithm to encrypt under the old access policy ; challenger performs a dynamic update of the access policy and generates an updated ciphertext based on the determination result of the old and the new access policies; sends the updated ciphertext to adversary .
- Querying private key phase 2. Similar to Phase 1, adversary continues to submit attribute to challenger for querying other attribute keys, with the stipulation that still does not satisfy the access policy .
- Guessing phase. Adversary gives a guess for . The adversary wins the game if , since any inactive adversary can win this game with a probability by making a random guess on . ’s advantage in this game is defined as
The goal of the adversary is to guess the value of with a probability greater than . If the above can be ignored, this cryptosystem is considered indistinguishable under a chosen-plaintext attack and is called IND-CPA secure.
3.4. Operation Flow
The operation flow of the data access control scheme based on blockchain and attribute-based encryption is shown in Figure 2, and the specific implementation details of this scheme are as follows.
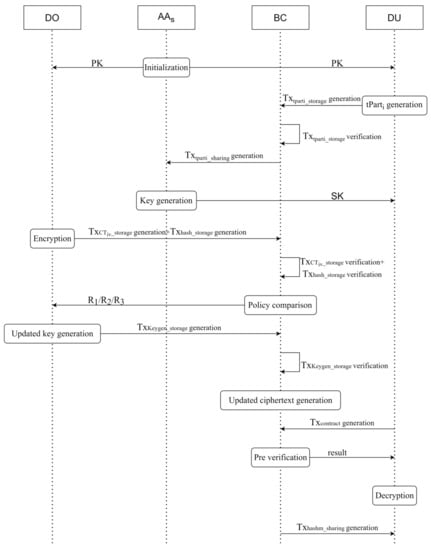
Figure 2.
Scheme operation flow.
3.5. Scheme Construction
3.5.1. Initialization Stage
executes the algorithm. The algorithm inputs the security parameter and outputs the system public key and the system master key with randomly chosen . The bilinear mapping , where and are cyclic groups of primes order , and is the generator of . The hash function maps an attribute in the system to an element in . denotes the set of attributes managed by the .
3.5.2. Generation Stage
The algorithm is executed by . The inputs random numbers and , and uses the threshold secret sharing algorithm to divide into slices of , .
broadcasts the slices of to the blockchain via the storage transaction, and nodes in the blockchain verify the transaction.
3.5.3. Generation Stage
When Fabric processes each transaction, each link needs to verify the authority of the transaction information, and the application client invokes the certificate service through the for registration and enrollment and obtains the identity certificate. So, , , and also have their public–private key pairs in Fabric.
After generating the storage transaction shown in Algorithm 1, broadcasts the transaction to other nodes in the blockchain to verify it.
| Algorithm 1 generation transaction. |
| Input: transaction , , public key of in the blockchain, the address of nodes , private key of in the blockchain Output: transaction |
| /* encrypt _ with their public keys in the blockchain*/ /* compute the hash value of the transaction , and the address of the nodes .*/ /* sign with their private keys in the blockchain*/ |
3.5.4. Verification Stage
Each node receives the transaction; obtains the transaction , , and from it; and compares it with the signed digest by computing the hash value of the three, as shown in Algorithm 2. If it returns , it means the verification passes, and nodes in the blockchain will obtain from the transaction to keep it on behalf of the .
| Algorithm 2 verification transaction. |
| Input:, public key of in the blockchain Output: verification results |
| /*Nodes compute the hash value of the transaction , and the address of the nodes .*/ /*Countersign*/ |
3.5.5. generation Stage
In Algorithm 3, obtains through the transaction and decrypts with its own private key to obtain . The above three transactions coordinate with transferring from to and, at the same time, record the transmission process of the actual key parameter on the blockchain. It reduces the security risks faced by in the process and realizes the traceability of key parameters.
| Algorithm 3 generation transaction. |
| Input: transaction , , the address of the , private key of the nodes in the blockchain Output: transaction |
| /*Nodes in the blockchain compute hash value*/ /*Nodes sign with their private keys in the blockchain*/ |
3.5.6. Key Generation Stage
The algorithm is executed by the that keep the . The algorithm takes the set of user attributes , , , and as inputs, and outputs the user’s private key . The firstly reconstructs the value secretly, and for each , the respective attribute authorization center computes the private key component .
The user combines the above four key components to obtain . The above private key generation stage has at least threshold value attribute authorization centers for collaborative computation to secretly reconstruct the value . Therefore, a single does not have the ability to generate key components. When a single authorization center suffers from the attack, the security of the whole system will not be affected, which ensures that the private key will not be leaked.
3.5.7. Encryption Stage
The encryption phase is performed by . This paper adopts the linear secret sharing schemes (LSSS) access structure. The algorithm takes , plaintext , and access matrix as inputs, where maps each row of the matrix to an attribute. The output is the ciphertext associated with the access structure . The algorithm chooses the random vector , for sharing the secret . is calculated. The random vector is chosen and is chosen, where represents the vector corresponding to the xth row of matrix . is defined, is chosen at random, and the following is computed:
In this paper, the shared data are subjected to a blockchain-based decentralized trusted verification of access rights and encryption/decryption correctness, and the ciphertext components are classified into two categories: pre-verification ciphertext and decryption ciphertext . The ciphertext is uploaded to the blockchain and verified through the generation transaction. In the encryption phase, also needs to calculate the hash value of the plaintext , upload it to the blockchain through the transaction, and verify it. The generation transaction and generation transaction are similar to the generation transaction and verification transaction, respectively; and the verification transaction is similar to the verification transaction.
3.5.8. Policy Comparison Stage
In Algorithm 4, if the needs to update the access policy, the invokes the policy comparison algorithm deployed in the smart contract, and this algorithm outputs the results , , and by determining the type of the new policy attribute .
| Algorithm 4 Policy comparison algorithm. |
| Input: old policy , new policy |
| exist in and , add into delete from else , add into else add into |
3.5.9. Updated Key Generation Stage
At the updated key generation stage, inputs , selects the updated key according to the output of the policy comparison algorithm, and constructs new random vectors and , where the first terms are and respectively. computes and . The generated policy updated key is sent to the blockchain and verified by the transaction, which is similar to the transaction.
where , and
3.5.10. Updated Ciphertext Generation Stage
After receiving the policy updated key , the blockchain inputs the and the old ciphertext and updates the ciphertext as follows.
- If ,
- If ,
- If ,
The blockchain is authorized to re-encrypt the ciphertext, and the policy updated key only reveals the relationship between the old and new access policies. It does not disclose any information about the encrypted data.
3.5.11. Decryption Stage
The decryption phase consists of two parts: pre-verification and decryption. Pre-verification verifies whether the has access rights to the data, and the invokes the smart contract through the contract generation transaction and obtains the partial ciphertext before decryption to verify the access rights. If the attribute sets satisfy the access policy, the algorithm will output the correct result. Otherwise, it will output , as shown in Algorithm 5.
| Algorithm 5 Pre-verification algorithm. |
| , , , or |
| |
After verifying the access rights, the fully trusted receives the , obtains the decrypted ciphertext from the blockchain through the transaction, and decrypts it with the private key. In the decryption phase, inputs , ’s private key , and value . If the value of is the same as the value of after collaborative computation by attribute authorization centers in phase, the following computation is performed:
In the above process, proves that semi-trusted attribute authorizations correctly compute the value , and the legitimate obtains the correct key component. If ), then chooses the constant that satisfies and computes
This process generates plaintext . The user encrypts the plaintext obtained from the decryption algorithm with the help of the SHA256 algorithm and compares its hash value with the obtained through the blockchain transaction. If , then the decryption is correct and the data are complete.
4. Proof of Security
Definition 1.
(The Decisional q-Parallel Bilinear Diffie–Hellman Exponent problem): Choose a group of prime order p according to the security parameter. Let be chosen at random and be a generator of . If an adversary is given,
It must remain difficult to distinguish from a random element in . An algorithm that outputs has an advantage in solving the decisional q-parallel BDHE in if
We say that the (decision) q parallel-BDHE assumption holds if no polytime algorithm has a non-negligible advantage in solving the decisional q-parallel BDHE problem.
Theorem 1.
Suppose an adversary can attack this scheme with a non-negligible advantage ε; in probabilistic polynomial time. Then, a challenger can solve the q-Parallel BDHE hypothesis with an advantage of .
Proof of Theorem 1.
The challenger picks two multiplicative cyclic groups and , the generator , and the bilinear mapping . Set a q-Parallel BDHE challenge with randomly chosen , , and take if ; otherwise, take .
- Initialization phase.
The challenger obtains the access structure that the adversary wishes to challenge, and is a matrix. chooses the random number such that , with the implication that .
For each in , chooses at random. Let be the set of satisfying . It can be sought that
The above expression is randomly distributed, so is also randomly distributed. If , .
- Querying private key phase 1.
Adversary adaptively submits a set of attributes not satisfying to ask for the private key. Challenger chooses the random number and finds the vector with the first term , for . Define , where .
Challenger cannot model the unknown term , so it must be ensured that the expression does not contain a term of the form . Challenger computes .
If and there is no such that , one can make .
If , there is more than one such that , and all equations of the form can be cancelled out by . Let be the set of satisfying . constructs according to the following equation:
- Challenge phase.
The adversary submits two equal-length challenge messages and to the challenger . chooses at random and the random numbers and uses for secret sharing on .
In addition, randomly selects to generate the challenge ciphertext as follows:
- Querying private key phase 2.
Similar to Phase 1.
- Guessing phase.
The adversary outputs a guess for . If , challenger outputs , denoting ; otherwise, challenger outputs , denoting . ’s advantage in that game is defined as .
If , obtains a valid ciphertext and ;
guesses that when and ;
If , obtains invalid information and ;
guesses that when and .
Thus, the advantage of in solving the deterministic hypothesis q-Parallel BDHE problem is
Based on the q-Parallel BDHE hypothesis, the challenger has a non-negligible advantage, proving that the scheme proposed in this paper is IND-CPA-safe under the q-Parallel BDHE hypothesis.
5. Performance Analysis
5.1. Functional Comparison
This section presents a comparative analysis of the schemes of reference [3,14,24] and this paper in terms of six aspects: access structure, multiple authorization centers, policy update, pre-validation, correctness verification, and blockchain, as shown in Table 2. The symbols × and √ represent whether the scheme has the function. Table 2 shows that reference [14] implements decryption correctness verification, and this paper and reference [24] implement decentralized trusted verification based on blockchain, which implements a pre-verification of access rights and verification of decryption correctness, respectively. Among these three schemes, reference [24] has only one authorization center to manage all users’ attributes and key distribution, which is a heavy workload and faces trust crises. Zhang et al. [14] and the scheme proposed in this paper also implement the access policy update function under the premise of multiple authorization centers. However, the access structure of reference [14] adopts a simple AND gate, which supports only the AND form when expressing the access policy and cannot express access policies with more complex logical structures, and is also limited in realizing fine-grained access control. Meanwhile, the multi-authorization center in the system designed in reference [14] needs a fully trusted third-party central authority to distribute global parameters for it, but in some application scenarios, the fully trusted third party does not exist, in which case the semi-trusted multi-authorization center may distribute incorrect private keys to legitimate data visitors, and the practical application scenarios of reference [14] are greatly limited. This is the reason why this paper designs the data visitor to provide the t-value in advance, which ensures that the semi-trusted multi-authorization center still generates the correct private key for the legitimate user in the absence of a third-party fully trusted central authority. In addition, the blockchain introduced in this paper’s scheme also guarantees that the data delivered under the de-trusted condition are not tampered with. In summary, the scheme in this paper realizes the above essential features simultaneously, solves the trust problem of access control systems in practical application scenarios, and is functionally superior to other schemes.

Table 2.
Comparison of the performance of different schemes.
5.2. Comparison of Computation
Table 3 demonstrates the computational overhead of [3,14,24] and this paper, where and represent the number of attributes and the number of policies, respectively; and represent the exponential operation in and , respectively; and is the bilinear operation. Table 3 shows that this paper’s scheme has the lowest total computational overhead in key generation, encryption, and decryption.

Table 3.
The computational overhead of different schemes.
5.3. Efficiency Analysis
This experiment is based on Ubuntu 22.04.2 LTS and the Charm-crypto library, running on a computer (Intel(R) Core(TM) i5-7300HQ CPU @ 2.50 GHz,8.00 GB RAM). In this paper, we use a 160-bit group of elliptic curves in hyper-singular curve over a 512-bit finite field. The experimental data are taken as the average value of the data obtained from 20 runs. This section compares this scheme with the existing schemes mainly in key generation time, encryption time, and decryption time.
Figure 3 shows the variation in key generation time with the number of attributes in [3,14,24] and the proposed scheme in this paper. Since reference [24] needs to create the vector for decryption, it has the highest computational overhead and the longest key generation time. The key generation time of this paper’s scheme is very low and basically does not vary with the number of attributes, which is close to that of reference [3]. However, the key generation process in reference [3] is managed by only one authorization center, which is inefficient and less secure.
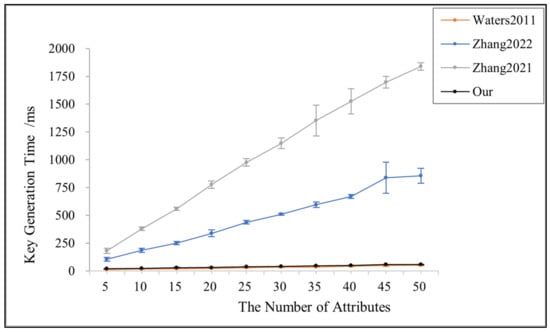
Figure 3.
Key generation time for references [3,14,24] and this paper.
Figure 4 illustrates the variation in encryption time with the number of attributes in [3,14,24] and the proposed scheme in this paper. All the results are linearly related to the number of attributes. Reference [14] is based on the AND gate access structure; its scheme sacrifices more fine-grained access policies for a lower cost encryption time. Reference [3] does not support the policy update function that facilitates the data owner to perform access control. However, in the actual access process, to dynamically adapt to changes in the environment and keep the shared data in a controllable range, the data owner must be able to formulate and update the access policy according to the demand dynamically and flexibly. This paper uses the linear secret sharing scheme, which is practical in that it can be implemented in any monotonic access structure despite the slightly higher encryption cost and can be used for policy updates without compromising user privacy.
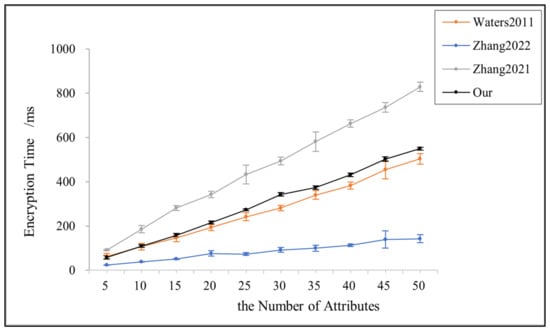
Figure 4.
Encryption time for references [3,14,24] and this paper.
Compared with the existing schemes, this paper, in order to ensure that legitimate users will not obtain the wrong key components provided by the semi-trusted attribute authorization centers, chooses to verify the correctness of the computed by the m attribute authorization centers by the value provided by the in the decryption phase, increasing the operation and making the decryption stage slightly more computationally intensive than in reference [14] and reference [24], as shown in Figure 5. However, in reference [14], only linear operations are required for decryption because this scheme supports only AND gate structures. Reference [24], on the other hand, outsources most of the decryption computation to the blockchain, which significantly increases the cost of using the blockchain.
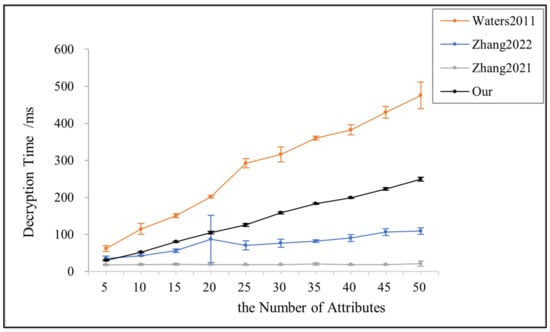
Figure 5.
Decryption time for references [3,14,24] and this paper.
In order to comprehensively and holistically compare the performance of the four schemes, this paper finds the sum of the key generation time, the encryption, and the decryption time of each scheme, as shown in Figure 6. Figure 6 shows that this paper’s scheme spends the lowest sum of time in the key generation, encryption, and decryption stages, consistent with each scheme’s theoretical and computational overhead results demonstrated in Table 3.
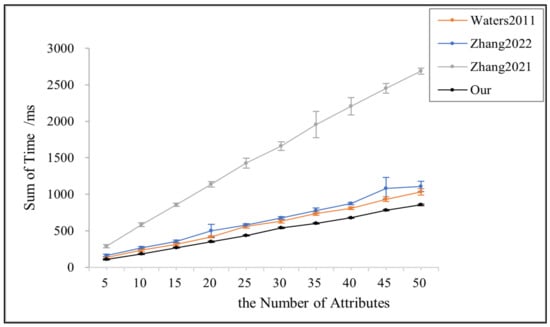
Figure 6.
Time of key generation + encryption + decryption for references [3,14,24] and this papers.
5.4. Blockchain Network Simulation
In the blockchain simulation experiment, this paper builds the Fabric consortium blockchain based on Ubuntu 22.04.2 LTS, which uses the PBFT consensus algorithm. The chaincode used in the scheme is developed with the Golang language. In this paper, the Caliper tool measures the transaction throughput and latency of the generation and verification transactions under different numbers of transactions. The test object of this experiment is a randomly selected node from the blockchain network, and the test content is the generation transaction and the verification transaction with a concurrency of 100–1000.
Throughput is the speed at which the blockchain ledger receives transactions, measured by the number of transactions executed per second. Figure 7 shows the throughput of two types of transactions for different transaction numbers in the blockchain. From Figure 7, as the number of transactions increases, the throughput of a single node remains near 120, indicating that the scheme proposed in this paper has good scalability.
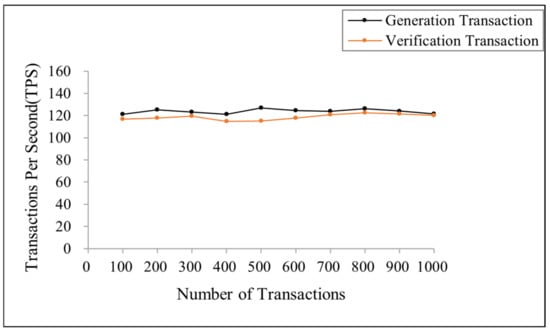
Figure 7.
Throughput of the generation and verification transaction under different transaction numbers.
Figure 8 shows the variation in transaction latency with the number of transactions in the proposed scheme. The results show that the latency of both types of transactions increases linearly with the number of transactions because increasing the number of transactions causes the waiting queue to become longer. Nonetheless, the generation transaction and verification transaction time remain within 10 s with a concurrency of 100–1000. Each node has a faster transaction speed, which provides a high-performance service.
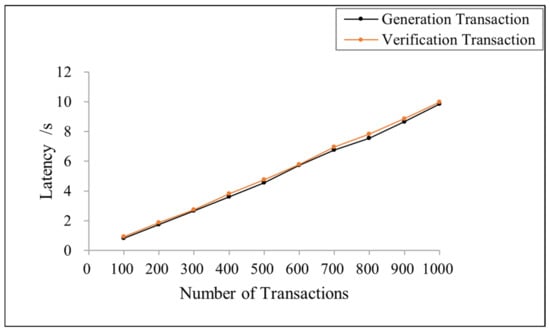
Figure 8.
Latency of the generation and verification transaction under different transaction numbers.
6. Conclusions
This paper proposes a multi-authorization access control scheme based on blockchain and CP-ABE, adopting a matrix access structure and supporting policy update functions to realize flexible and fine-grained access control. In this paper, blockchain is combined with attribute-based encryption, where the data owner embeds the access policy into the ciphertext data through attribute-based encryption and later uploads it to the blockchain. The blockchain records the transmission process of the data visitor’s private key to pre-verify the data visitor’s access rights. The combination of the two not only ensures the confidentiality and security of the data on the blockchain, but also realizes the auditable and highly transparent access process, which solves the problems of traditional access control, such as single-point failure, difficulty in meeting the principle of minimum authorization, difficulty in dynamically adapting to changes in the environment, and difficulty in verifying the access rights of the policy.
Author Contributions
Conceptualization, R.H. and Z.M.; data curation, J.W.; funding acquisition, R.H.; investigation, S.L.; methodology, X.L.; software, P.Z.; validation, L.L.; writing—original draft, Z.M.; writing—review and editing, R.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Fundamental Research Funds for the Central Universities (Grant Numbers: 328202251, 3282023017). The APC was funded by the Fundamental Research Funds for the Central Universities (Grant Numbers: 328202251, 3282023017).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Advances in Cryptology—EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In Proceedings of the International Workshop on Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Feng, T.; Kong, F.; Liu, C.; Lu, Y. Multi-Authorization Attribute-Based Verifiable Encryption Scheme Based on Blockchain. Mob. Netw. Appl. 2023, 1–8. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 1–9. [Google Scholar]
- Li, T.; Wang, Z.; Chen, Y.; Li, C.; Jia, Y.; Yang, Y. Is semi-selfish mining available without being detected? Int. J. Intell. Syst. 2022, 37, 10576–10597. [Google Scholar] [CrossRef]
- Li, T.; Wang, Z.; Yang, G.; Cui, Y.; Chen, Y.; Yu, X. Semi-selfish mining based on hidden Markov decision process. Int. J. Intell. Syst. 2021, 36, 3596–3612. [Google Scholar] [CrossRef]
- Cheng, L.; Liu, J.; Xu, G.; Zhang, Z.; Wang, H.; Dai, H.-N.; Wu, Y.; Wang, W. SCTSC: A semicentralized traffic signal control mode with attribute-based blockchain in IoVs. IEEE Trans. Comput. Soc. Syst. 2019, 6, 1373–1385. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Bayat, M.; Farjami, Y. MedSBA: A novel and secure scheme to share medical data based on blockchain technology and attribute-based encryption. J. Ambient Intell. Humaniz. Comput. 2020, 11, 4613–4641. [Google Scholar] [CrossRef]
- Li, J.; Zhang, Y.; Chen, X.; Xiang, Y. Secure attribute-based data sharing for resource-limited users in cloud computing. Comput. Secur. 2018, 72, 1–12. [Google Scholar] [CrossRef]
- Sharma, P.; Jindal, R.; Borah, M.D. Blockchain-based cloud storage system with CP-ABE-based access control and revocation process. J. Supercomput. 2022, 78, 7700–7728. [Google Scholar] [CrossRef]
- Gao, J.; Yu, H.; Zhu, X.; Li, X. Blockchain-based digital rights management scheme via multiauthority ciphertext-policy attribute-based encryption and proxy re-encryption. IEEE Syst. J. 2021, 15, 5233–5244. [Google Scholar] [CrossRef]
- Ling, J.; Chen, J.; Chen, J.; Gan, W. Multiauthority attribute-based encryption with traceable and dynamic policy updating. Secur. Commun. Netw. 2021, 2021, 1–13. [Google Scholar] [CrossRef]
- Zhang, J.; Gong, Q.; Wei, Z.; Wang, X.; Yan, X.; Zhang, X. Efficient Multi-Authority Attribute-Based Encryption with Policy Hiding and Updating. In Proceedings of the 2022 IEEE 10th International Conference on Computer Science and Network Technology (ICCSNT), Dalian, China, 22–23 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 34–38. [Google Scholar]
- Gupta, B.B.; Li, K.-C.; Leung, V.C.; Psannis, K.E.; Yamaguchi, S. Blockchain-assisted secure fine-grained searchable encryption for a cloud-based healthcare cyber-physical system. IEEE/CAA J. Autom. Sin. 2021, 8, 1877–1890. [Google Scholar]
- Guo, R.; Shi, H.; Zheng, D.; Jing, C.; Zhuang, C.; Wang, Z. Flexible and efficient blockchain-based ABE scheme with multi-authority for medical on demand in telemedicine system. IEEE Access 2019, 7, 88012–88025. [Google Scholar] [CrossRef]
- Zuo, Y.; Kang, Z.; Xu, J.; Chen, Z. BCAS: A blockchain-based ciphertext-policy attribute-based encryption scheme for cloud data security sharing. Int. J. Distrib. Sens. Netw. 2021, 17, 1550147721999616. [Google Scholar] [CrossRef]
- Gao, S.; Piao, G.; Zhu, J.; Ma, X.; Ma, J. Trustaccess: A trustworthy secure ciphertext-policy and attribute hiding access control scheme based on blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5784–5798. [Google Scholar] [CrossRef]
- Vasishta, M.V.A.; Palanisamy, B.; Sural, S. Decentralized Authorization using Hyperledger Fabric. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 238–243. [Google Scholar]
- Varun, M.; Vasishta, M.V.A.; Palanisamy, B.; Sural, S. Decentralized Authorization in Web Services Using Public Blockchain. In Proceedings of the International Conference on Blockchain, Online, 10–14 December 2021; Springer: Cham, Switzerland, 2021; pp. 27–42. [Google Scholar]
- Lei, Y.; Jia, Z.; Yang, Y.; Cheng, Y.; Fu, J. A cloud data access authorization update scheme based on blockchain. In Proceedings of the 3rd International Conference on Smart BlockChain (SmartBlock), Zhengzhou, China, 20–25 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 33–38. [Google Scholar]
- Singh, R.; Sturley, S.; Sharma, B.; Dhaou, I.B. Blockchain-enabled Device Authentication and Authorisation for Internet of Things. In Proceedings of the 2023 1st International Conference on Advanced Innovations in Smart Cities (ICAISC), Jeddah, Saudi Arabia, 23–25 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Honar Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Multi-Layer Blockchain-Based Security Architecture for Internet of Things. Sensors 2021, 21, 772. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Z.; Zhang, J.; Yuan, Y.; Li, Z. An expressive fully policy-hidden ciphertext policy attribute-based encryption scheme with credible verification based on blockchain. IEEE Internet Things J. 2021, 9, 8681–8692. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).