Abstract
With the information and communication technologies (ICT) and Internet of Things (IoT) gradually advancing, smart homes have been able to provide home services to users. The user can enjoy a high level of comfort and improve his quality of life by using home services provided by smart devices. However, the smart home has security and privacy problems, since the user and smart devices communicate through an insecure channel. Therefore, a secure authentication protocol should be established between the user and smart devices. In 2020, Xiang and Zheng presented a situation-aware protocol for device authentication in smart grid-enabled smart home environments. However, we demonstrate that their protocol can suffer from stolen smart device, impersonation, and session key disclosure attacks and fails to provide secure mutual authentication. Therefore, we propose a secure and lightweight authentication protocol for IoT-based smart homes to resolve the security flaws of Xiang and Zheng’s protocol. We proved the security of the proposed protocol by performing informal and formal security analyses, using the real or random (ROR) model, Burrows–Abadi–Needham (BAN) logic, and the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool. Moreover, we provide a comparison of performance and security properties between the proposed protocol and related existing protocols. We demonstrate that the proposed protocol ensures better security and lower computational costs than related protocols, and is suitable for practical IoT-based smart home environments.
1. Introduction
With the development of information and communication technologies (ICT) and Internet of Things (IoT), smart home automation systems are receiving a lot of attention. The smart home is a networking environment that connects smart devices (e.g., IoT and sensors) to each other. Based on these smart devices, users can utilize various home services. When the user is inside the home, the user can control all smart devices with a voice commands or applications, granting the user accesses to services such as turning the TV on/off, choosing music, switching lights on/off, and so on. When the user is outside the home, the user can monitor and control various smart devices by checking their status. Thus, users can enjoy a high level of comfort and an increased quality of life through smart home environments.
Generally, smart home environments consist of the user, smart devices, a home gateway, and a registration authority [1,2,3]. A remote user wants to use the data collected by smart devices. However, smart devices are resource limited in terms of computational power, amount of memory, and bandwidth [4]. For these reasons, smart devices communicate through the home gateway. The home gateway acts as a bridge between smart devices and remote users by providing short and long-distance wireless communication interfaces that maintain the connectivity with internal smart devices and remote users [5]. Users can remotely operate smart devices with the help of a home gateway using Internet-enabled mobile phones and tablets anytime and anywhere. Thus, the home gateway plays a crucial role by controlling the data exchange. It manages the communication between internal and external surroundings.
Unfortunately, the smart home has security and privacy problems because the sensitive data collected by smart devices are exchanged through wireless networks. If an adversary obtains the data, the adversary will abuse them for his own purposes. Thus, security and privacy are essential elements to providing secure home services. In addition, the exchanged data should meet confidentiality, integrity, and availability standards. Asymmetric and symmetric key cryptosystems are inappropriate for applying to low-capacity devices because they generate high computational costs. Thus, secure and lightweight authentication protocols are necessary to provide security and privacy in IoT-based smart homes.
In 2020, Xiang and Zheng [6] proposed a situation-aware protocol for device authentication in smart grid-enabled smart home environments. Xiang and Zheng claimed that their protocol can withstand impersonation, man-in-the-middle (MITM), and replay attacks. Xiang and Zheng also demonstrated that their protocol can provide data integrity and mutual authentication. However, herein we prove that their protocol does not prevent stolen smart device, impersonation, and session key disclosure attacks, and fails to ensure mutual authentication. They also mentioned that their protocol concentrates on the security of smart grid-enabled smart home environments. However, they proposed an authentication protocol that is only for smart home environments. Thus, we focus on general smart home environments and present a secure and lightweight authentication protocol for IoT-based smart homes that deals with the security drawbacks of Xiang and Zheng’s protocol [6]. The proposed protocol is efficient for resource-constrained smart devices because we use only one-way hash functions and XOR operations.
1.1. Contributions
This paper has the following main contributions.
- We analyze the security vulnerabilities of Xiang and Zheng’s protocol [6]. To resolve the security drawbacks of their protocol, we propose a secure and lightweight authentication protocol for IoT-based smart homes.
- We demonstrate that our protocol is secure against various kinds of known attacks by reporting on an informal security analysis.
- We conducted formal analysis using the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool [7,8,9], Burrows–Abadi–Needham (BAN) logic [10], and the real or random (ROR) model [11]. With the formal analysis, we proved secure mutual authentication, the session key security, and the resistance against MITM and replay attacks of our protocol.
- We provide a comparison of performance and security properties between our protocol and related protocols. The results show that our protocol provides better security and computational costs compared to related protocols.
1.2. Adversary Model
We adopted the widely-used Dolev–Yao (DY) threat model [12,13,14] and the Canetti and Krawczyk (CK) adversary threat model [15,16] to evaluate the security of the proposed protocol. The capabilities of an adversary can be defined as follows.
- can eavesdrop, intercept, inject, replay, and modify transmitted messages via a public channel and then can perform MITM, replay, impersonation attacks, etc. [17].
- can steal the legal user’s mobile device or smart device and extract secret credentials stored in the memory by performing the power analysis attack [18,19,20,21].
- can access short-term keys, long-term keys, and session states of each party.
In addition, we developed some assumptions for our protocol. cannot feasibly guess the identity and password of the mobile user simultaneously [22,23,24]. cannot extract the data stored in the home gateway’s database, since the home gateway has a secure database.
1.3. Organization
The remaining parts of this paper are structured as follows. In Section 2, we briefly discuss existing proposed protocols in IoT-based smart homes. We suggest the system model of the proposed protocol in Section 3. We review Xiang and Zheng’s protocol in Section 4 and analyze security weaknesses of Xiang and Zheng’s protocol in Section 5. Section 6 proposes a secure and lightweight authentication protocol for IoT-based smart homes to improve the security drawbacks of Xiang and Zheng’s protocol. Section 7 analyzes the security of our protocol through informal and formal analyses with BAN logic, the ROR model, and the AVISPA tool. In Section 8, we present the results of performance and security property comparisons between the proposed protocol and related protocols. Finally, we present the conclusion in Section 9.
2. Related Works
In the last few years, many researchers proposed authentication protocols to provide secure communication between users and smart devices in smart home environments. Santoso and Vun [25] proposed a secure authentication protocol using elliptic curve cryptography (ECC) in IoT-based smart homes. Several authors [26,27] revealed that Santoso and Vun’s protocol [25] is vulnerable to privileged-insider and stolen smart card attacks, and fails to achieve user anonymity and untraceability. Dey and Hossian [28] presented a secure session key establishment protocol for smart home environments using public key cryptosystems. Dey and Hossian [28] proved that their protocol achieves resilience against various attacks. Unfortunately, some researchers [29,30] pointed out that Dey and Hossian’s protocol [28] has various security drawbacks, such as device compromised and known-key attacks, and is unsuccessful in ensuring anonymity and confidentiality. Shuai et al. [31] suggested an ECC-based anonymous authentication protocol for smart home environments. These protocols [25,28,31] use asymmetric key cryptosystems such as ECC for smart home security. However, in terms of costs, symmetric key cryptosystems are more efficient than asymmetric key cryptosystems for deployment on resource-constrained smart devices.
In view of the computational cost for low capacity devices, many authentication protocols have been proposed using symmetric key cryptosystems in smart home environments. Vaidya et al. [32] proposed a robust authentication protocol to provide secure remote access in home environments using symmetric key cryptosystems. Vaidya et al. [32] claimed that their protocol resists synchronization and stolen smart card attacks, and provides forward secrecy and mutual authentication. However, Kim and Kim [33] demonstrated that Vaidya et al.’s protocol [32] does not resist password guessing and smart card loss attacks, and does not provide forward secrecy. To resolve the security problems in Vaidya et al.’s protocol [32], Kim and Kim [33] proposed an improved authentication protocol. Wazid et al. [34] proposed a symmetric key-based secure remote user authentication protocol to provide future secure communications. Wazid et al. [34] proved that their protocol is secure against other possible known attacks. Lyu et al. [35] pointed out that Wazid et al.’s protocol [34] is not secure against desynchronization and compromised server attacks. Poh et al. [36] proposed a privacy-preserving authentication protocol to support data confidentiality. Unfortunately, Irshad et al. [37] pointed out that Poh et al.’s protocol [36] cannot maintain the privacy of authentication parameters. Although these protocols [32,33,34,35,36] use symmetric key cryptosystems considering the low capacity devices, symmetric key cryptosystems are still unacceptable for smart devices with limited resources in terms of computational costs.
Recently, several lightweight authentication protocols [6,38] have been proposed for smart home environments to solve these problems. Banerjee et al. [38] presented an anonymous and robust authentication protocol for IoT-based smart homes using one-way hash functions, XOR operations, and a fuzzy extractor. Banerjee et al. [38] proved that their protocol resists various attacks. However, AL-Turjman and Deebak [39] pointed out that Banerjee et al.’s protocol [38] does not provide identity protection, traceability, or session secret key agreement. Xiang and Zheng [6] presented a situation-aware protocol for device authentication in smart home environments. Xiang and Zheng [6] claimed that their protocol resists various security threats and ensures data integrity and mutual authentication. However, we prove here that Xiang and Zheng’s protocol [6] cannot ensure secure mutual authentication and is vulnerable to stolen smart device, impersonation, and session key disclosure attacks. Therefore, we propose a secure and lightweight authentication protocol for IoT-based smart homes to improve the security flaws of Xiang and Zheng’s protocol [6].
3. System Model
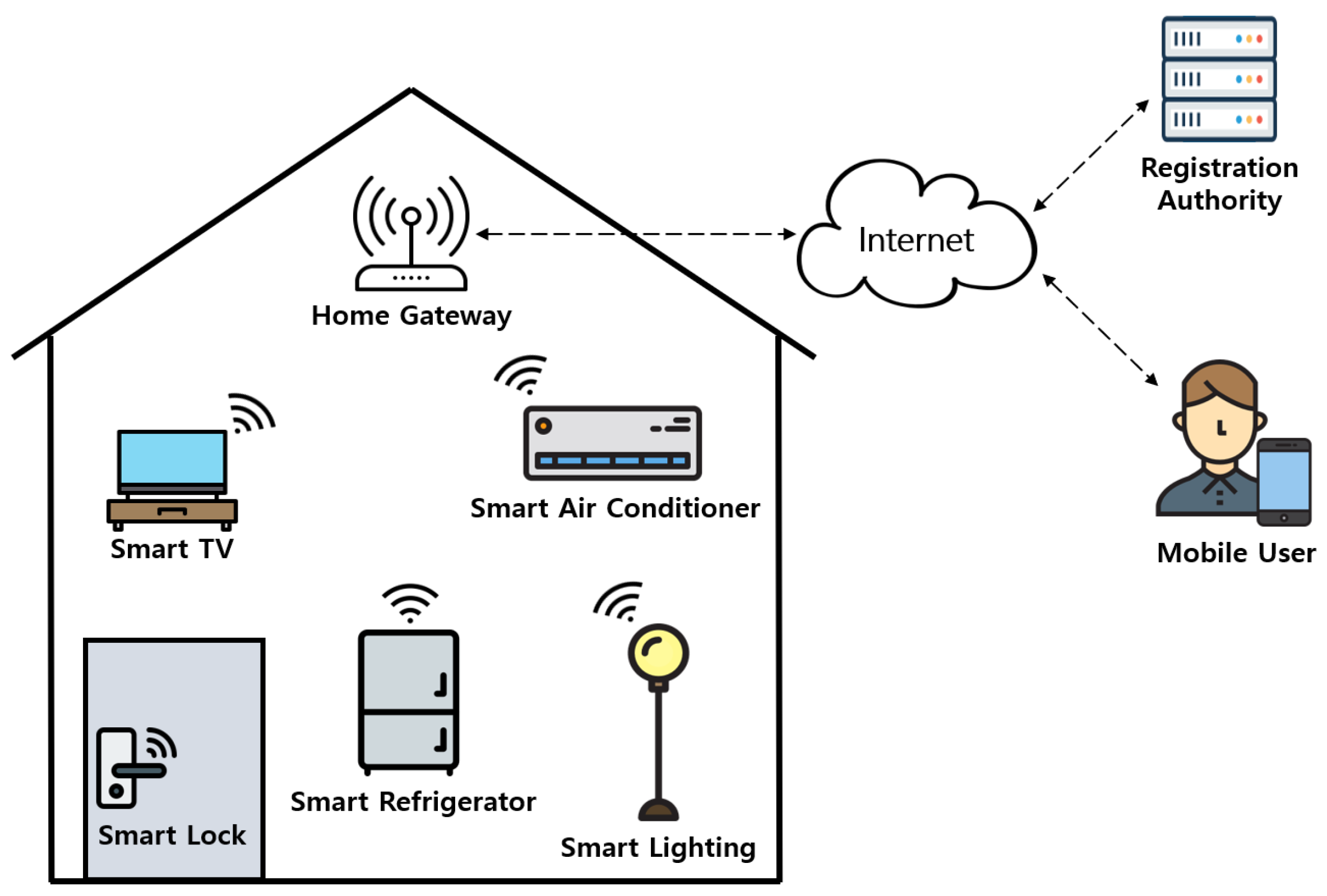
Xiang and Zheng [6] claimed that their protocol concentrates on the security of smart grid-enabled smart home environments, but they proposed an authentication protocol that is only for smart home environments. Therefore, we focus on the architecture of general IoT-based smart home environments. The system model is shown in Figure 1.
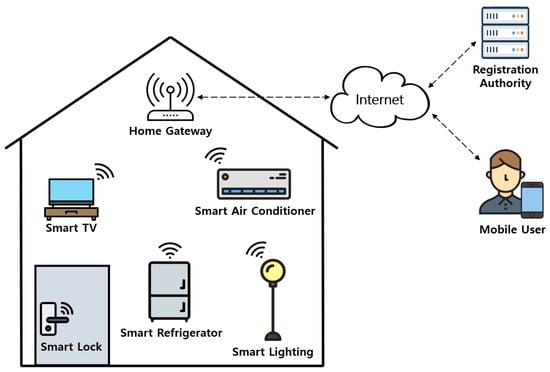
Figure 1.
System model for IoT-based smart homes.
The proposed system is composed of a mobile user (), a smart device (), a home gateway (), and a registration authority (). and are trusted entities in smart home environments. is responsible for initializing the system and registering and . first needs to register at to utilize services. and also need to register at for providing home services. After receiving the registration request message from and , stores the information of each entity in the mobile device of and in the memory of . also stores all information required for the authentication of the and in ’s database. Then, the and perform the mutual authentication and session key agreement with the help of the . With this session key, and can utilize secure smart home services.
4. Review of Xiang and Zheng’s Protocol
This section reviews Xiang and Zheng’s protocol [6]. Xiang and Zheng proposed an authentication protocol according to the security risk level in smart home environments. Their protocol consists of smart device registration, and authentication and key agreement phases. The notation of this paper is described in Table 1.

Table 1.
Notation.
4.1. Smart Device Registration Phase
At the registration phase, generates an identity and a random number for and computes . Then, sends to and to through a secure channel.
4.2. Authentication and Key Agreement Phase
After the registration, sends the message to in the authentication and key agreement phase. is a message header of . Upon getting , receives the current situation from the smart home system regarding whether the security risk level is low or high. According to the security risk level, the authentication phase is divided into low security risk and high security risk.
4.2.1. Low Security Risk
When receives a low-security-risk level report, the authentication phase is described below.
- Step 1:
- computes and extracts current timestamp . Then calculates and . Finally, sends to , where is the header of the message through an insecure channel.
- Step 2:
- Upon receiving the message at timestamp , knows the current security risk level is low from the message header. also computes and checks if and . If it is not equal, the authentication process will be aborted. Then, computes and extracts the current timestamp . also computes and . Finally, sends to , where is the header of the message . computes the session key for the future data communication.
- Step 3:
- After receiving at timestamp , computes , , and . Then, checks if and . If it is correct, computes the session key and adds to the trusted device list.
4.2.2. High Security Risk
If receives a situation report detailing that the current security risk level is high, the authentication phase contains the following steps.
- Step 1:
- computes , and generates a random number . After that, extracts a current timestamp , and computes and . Then, sends the message to , where is the message header of through a public channel.
- Step 2:
- After getting at timestamp , knows the security risk level is high from the header of . then computes and . After that, checks whether and . If the check is failed, the authentication process will be terminated. Otherwise, computes and generates a random number . Then, extracts the current timestamp , and computes and . Finally, sends the message to , where is the message header of , and computes the session key .
- Step 3:
- Upon receiving at timestamp , computes , , and . Then, checks whether and . If it is correct, computes the session key and adds to the trusted device list.
5. Cryptanalysis of Xiang and Zheng’s Protocol
In this section, we discuss the security flaws of Xiang and Zheng’s protocol. We demonstrate that their protocol is vulnerable to various attacks and does not perform secure mutual authentication.
5.1. Stolen Smart Device Attack
We suppose that an adversary can obtain secret credentials of using the power analysis according to Section 1.2. Xiang and Zheng’s protocol sends the authentication request message as plaintext. can obtain from of the previous session. Then, can make the message anytime and perform various attacks with secret credentials. In conclusion, their protocol does not prevent the stolen smart device attack.
5.2. Impersonation Attack
According to Section 1.2, can perform an impersonation attack at low and low-security-risk levels. The detailed processes are below.
5.2.1. Low Security Risk
can perform the impersonation attack with the following steps.
- Step 1:
- With the obtained secret credentials from and from the previous session, can send the message .
- Step 2:
- Upon getting , computes and extracts the current timestamp . After that, computes and , and sends the message .
- Step 3:
- After receiving , computes and . Then, verifies the validity of and . If it is equal, computes and generates the current timestamp . After that, computes and . Finally, sends the message to and computes the session key .
- Step 4:
- Upon getting , computes , , and . After that, checks the validity of and . If it is equal, computes .
Thus, can impersonate successfully, and Xiang and Zheng’s protocol cannot prevent the impersonation attack at the low-security-risk level.
5.2.2. High Security Risk
With the obtained secret credentials , can disguise as , and the detailed steps are below.
- Step 1:
- can send to using obtained secret credentials and .
- Step 2:
- Upon getting , calculates and generates a random number . After that, extracts the current timestamp , and computes and . Then, sends .
- Step 3:
- After receiving , computes and . Then, verifies the validity of and . If all checks pass, computes , generates a random number , and extracts the current timestamp . After that, computes , , and . Finally, sends to .
- Step 4:
- Upon getting , computes , , and . Then, checks the validity of and . If it is equal, computes .
In conclusion, Xiang and Zheng’s protocol cannot prevent the impersonation attack at the low-security-risk level because can impersonate successfully.
5.3. Session Key Disclosure Attack
As mentioned in Section 1.2, can extract secret credentials . In addition, according to Section 5.2, can obtain the session key between and at the both low-security-risk and high-security-risk levels. With the obtained session key, can communicate with and misinform for ’s own purpose. Therefore, Xiang and Zheng’s protocol is vulnerable to the session key disclosure attack.
5.4. Mutual Authentication
Xiang and Zheng claimed that their protocol supports the mutual authentication between and because and cannot be obtained from the eavesdropped messages. However, in accordance with Section 5.2, can generate an authentication request message and calculate session key and at low security and low security phases, respectively. Thus, Xiang and Zheng’s protocol does not satisfy secure mutual authentication between and .
6. Proposed Protocol
In this section, we present a secure and lightweight authentication protocol for IoT-based smart homes to improve the security drawbacks of Xiang and Zheng’s protocol [6]. The proposed protocol consists of four phases: initialization, registration, authentication and key agreement, and password update.
6.1. Initialization Phase
Before and are deployed in the smart home, generates a master key . has a unique identity , and has a unique identity and secret key .
6.2. Registration Phase
The detailed registration phases for the smart device and user are below.
6.2.1. Smart Device Registration Phase
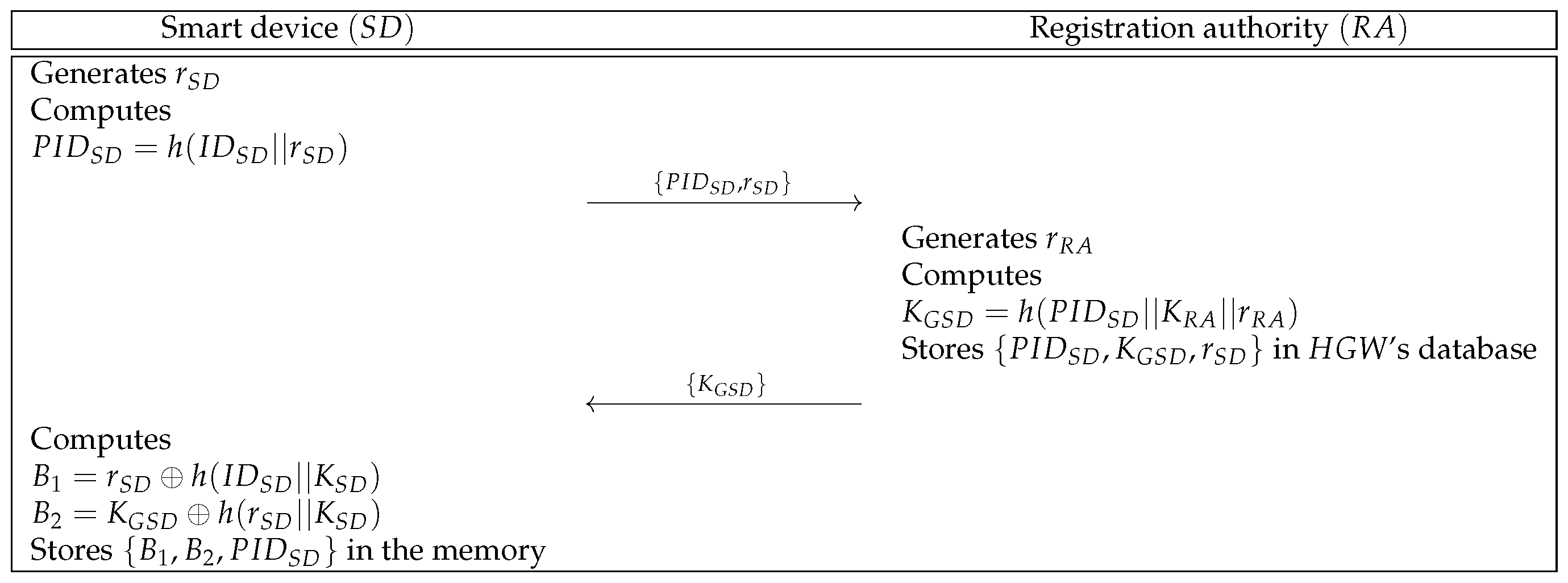
To provide home services to , must register at . We indicate the registration phase of and in Figure 2, and detailed steps are described below.
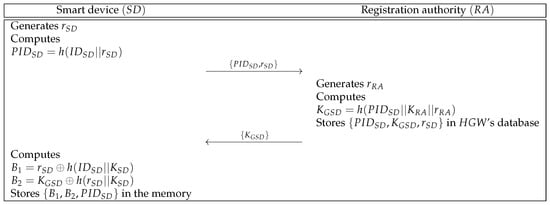
Figure 2.
Smart device registration phase of the proposed protocol.
- Step 1:
- generates a random number and computes . Then, sends to through a secure channel.
- Step 2:
- Upon getting the message, generates and computes . Then, stores in ’s database and sends to over a secure channel. After that, makes public.
- Step 3:
- After receiving the message, computes and . Then, stores in the memory.
6.2.2. Mobile User Registration Phase
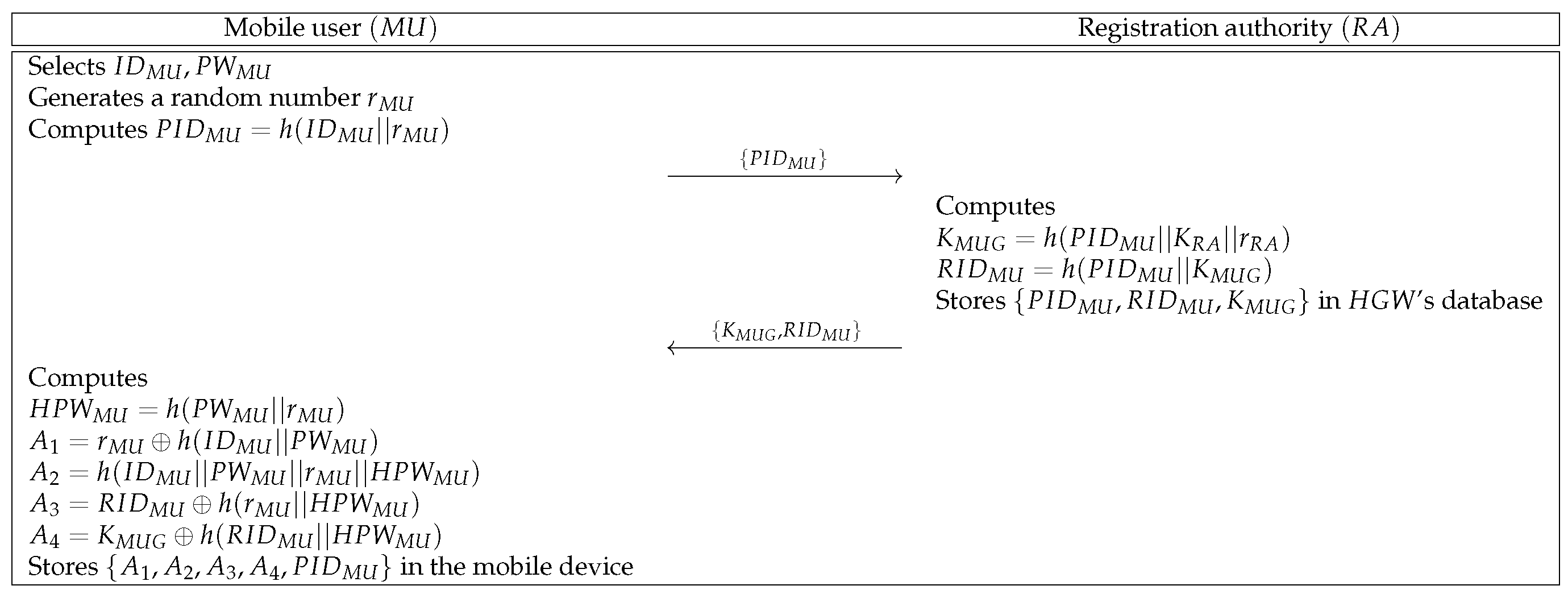
must register at to use the data transmitted from . Figure 3 shows the registration phase of and . This phase is described as follows.
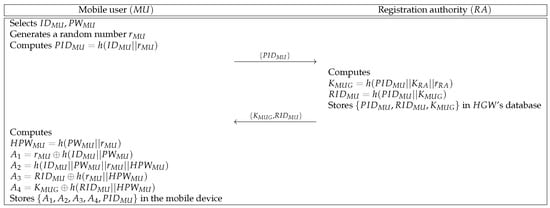
Figure 3.
Mobile user registration phase of the proposed protocol.
- Step 1:
- selects identity and password and generates a random number . Then, computes and sends to through a secure channel.
- Step 2:
- Upon receiving the message, computes and . Then, stores in ’s database and sends to via a secure channel.
- Step 3:
- After receiving the message, computes , , , , and . Then, stores in the mobile device.
6.3. Authentication and Key Agreement Phase
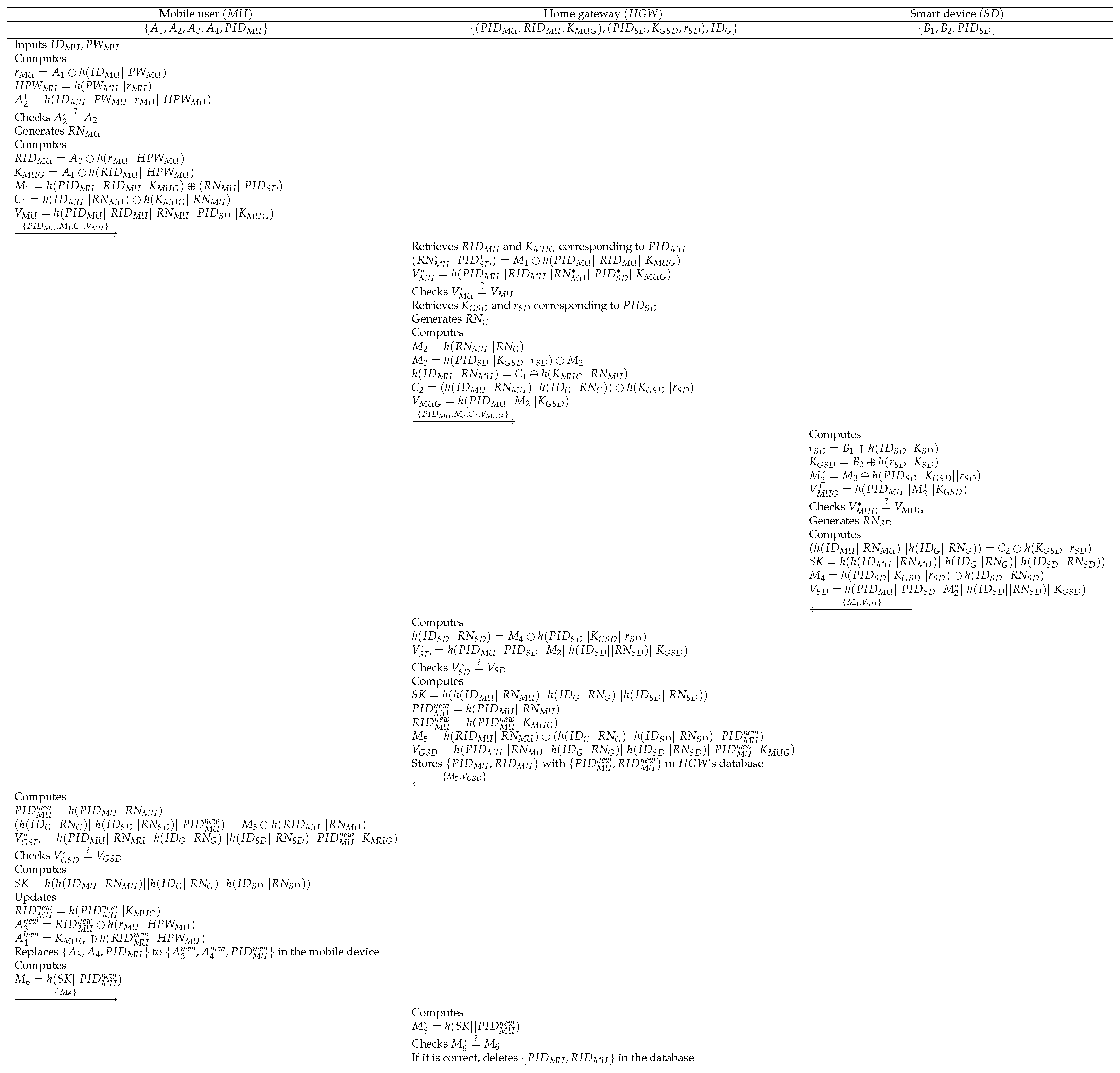
To utilize secure home services, and establish a session key with the help of . We indicate the detailed steps below, and a summarized version of this phase is in Figure 4.

Figure 4.
Authentication and key agreement phase of the proposed protocol.
- Step 1:
- inputs identity and password and computes , , and . Then, checks if . If this condition is satisfied, generates a random nonce and computes , , , , and . After that, sends to through a public channel.
- Step 2:
- Upon getting the message, retrieves and corresponding to , and computes and . checks if . If it is equal, retrieves and corresponding to . Then, generates a random nonce and computes , , , , and . Finally, sends to .
- Step 3:
- After receiving the message, computes , , , and . checks if . If this condition is valid, generates a random nonce . Then, computes , , , and . Finally, sends to .
- Step 4:
- Upon receiving the message, computes and . checks if . Then, computes , , and , and computes and .stores with in ’s database. Finally, sends to .
- Step 5:
- After receiving the message, computes , and . checks if . After that, computes . Then, updates , , and . Then, replaces to in the mobile device. computes and sends to .
- Step 6:
- After receiving the message from , computes and checks if . If it is correct, deletes {} in the database.
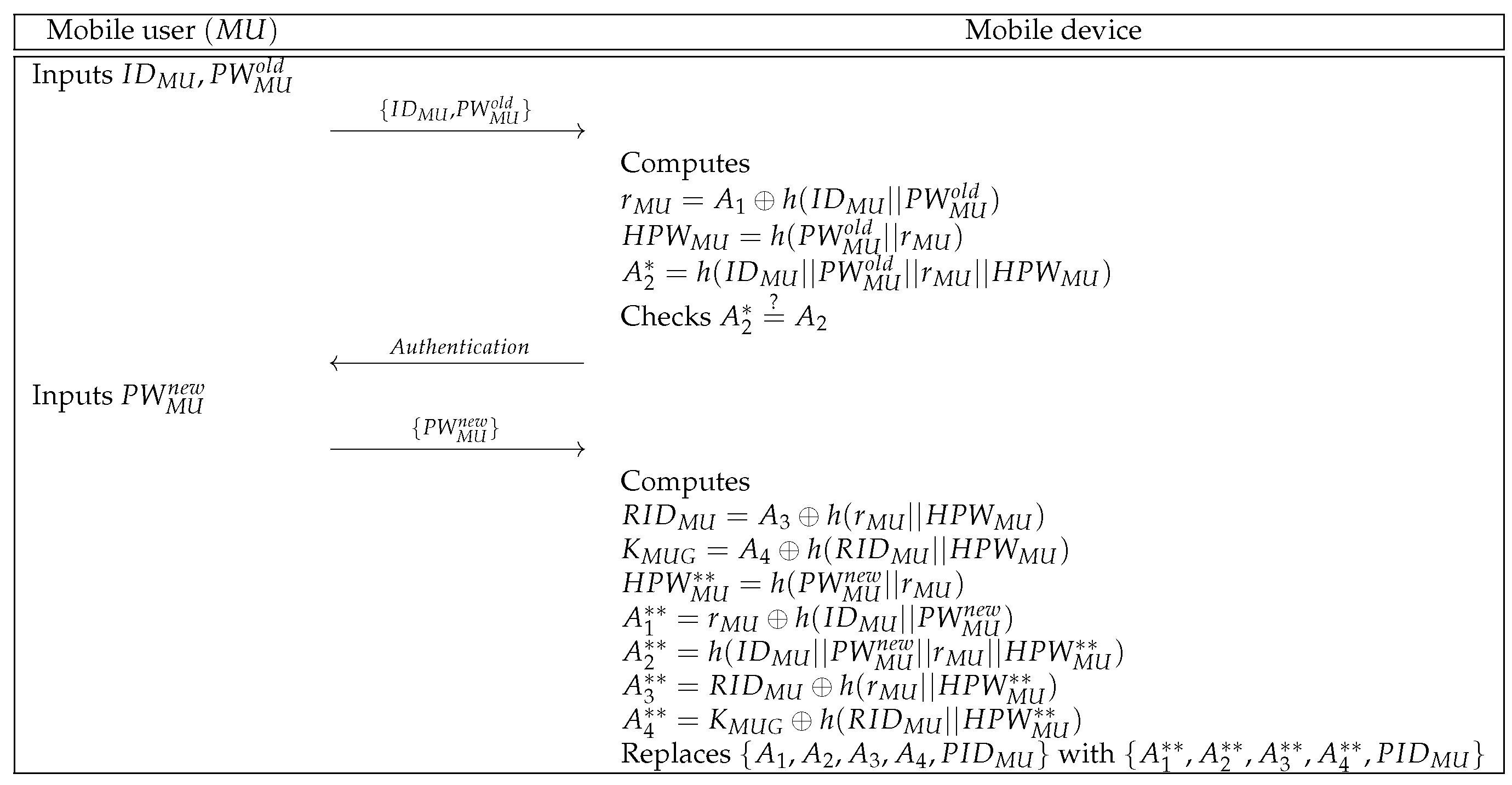
6.4. Password Update Phase
can update the password individually. In Figure 5, we represent the password update phase and the detailed steps are below.
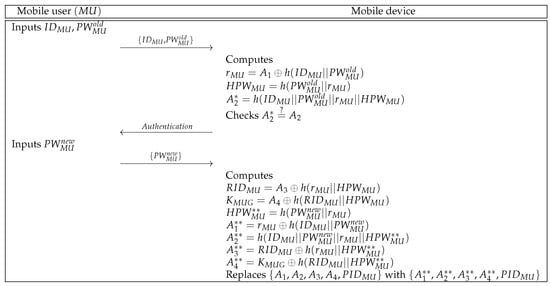
Figure 5.
Password update phase of the proposed protocol.
- Step 1:
- inputs identity and old password to the mobile device over a secure channel.
- Step 2:
- Mobile device computes , , and . Then, the mobile device checks whether . If this condition is met, the mobile device sends the authentication message to .
- Step 3:
- Upon receiving the authentication message, inputs the new password to the mobile device.
- Step 4:
- After getting the new password, the mobile device computes , , , , , , and . Finally, the mobile device replaces with .
7. Security Analysis
This section shows informal and formal security analyses of our protocol using BAN logic, the ROR model, and the AVISPA tool. Through theses analyses, we demonstrate that the proposed protocol prevents various kinds of known attacks.
7.1. Informal Security Analysis
We performed informal analysis to describe how our protocol withstands various attacks and supports perfect forward secrecy and mutual authentication.
7.1.1. Mobile User Impersonation Attack
According to Section 1.2, an adversary can have the lost/stolen mobile device of a legal user , and extract secret credentials using the power analysis [18,19]. With these values, can try to impersonate by intercepting transmitted messages through an insecure channel. However, cannot send a valid authentication request message because cannot calculate without the knowledge of the ’s real identity , password , and a random nonce . Hence, the proposed protocol resists the mobile user impersonation attack.
7.1.2. Home Gateway Impersonation Attack
Suppose that an adversary intercepts messages and over an insecure channel. can try to calculate the other valid messages and . However, cannot compute messages, because has no knowledge of the ’s real identity and a random nonce . In addition, does not know ’s real identity , a random nonce , and the shared secret key . Thus, the proposed protocol withstands the home gateway impersonation attack.
7.1.3. Smart Device Impersonation Attack
An adversary can try to impersonate using the exchanged message . According to Section 1.2, can extract stored values in the lost/stolen smart device. However, cannot compute the message because does not know the ’s unique identity , secret key , and a random nonce . Therefore, our protocol prevents the smart device impersonation attack.
7.1.4. Session Key Disclosure Attack
In accordance with Section 1.2, an adversary can extract secret credentials and of and , respectively. To calculate the session key, should know real identities and random nonces of , , and . However, cannot obtain and from transmitted messages because these are encrypted with secret keys . Thus, the proposed protocol withstands the session key disclosure attack.
7.1.5. Replay and MITM Attack
We assume that an adversary intercepts and resends the previous authentication request message to for the purpose of disguising . detects is not fresh by checking the validity of . In addition, even if tries to modify the authentication request message, cannot modify without the knowledge of the ’s real identity , password , a random nonce , and shared secret key . In conclusion, our protocol prevents replay and MITM attacks.
7.1.6. Offline Guessing Attack
After extracting the information from the ’s mobile device, can obtain , , , and . All of these values are encrypted with and . If wants to compromise the security of our protocol, needs to guess both and . However, it is a computationally infeasible problem to according to Section 1.2. As a result, our protocol resists the offline guessing attack.
7.1.7. Stolen Smart Device Attack
Assume that an adversary obtains and extracts secret credentials stored in the memory through the power analysis attack [20,21]. Although obtains these values, cannot get sensitive information of because all information stored in the memory is masked with ’s unique identity and secret key . Thus, the proposed protocol withstands the stolen smart device attack.
7.1.8. Privileged-Insider Attack
In this attack, a privileged-insider adversary is able to get during the ’s registration phase. Then, can extract secret credentials stored in the mobile device. However, since does not know the ’s real identity , password , and a random number , cannot calculate the session key . Hence, our protocol prevents the privileged-insider attack.
7.1.9. Known Session-Secret Temporary Information Attack
An adversary can obtain session specific random nonces to conduct the known session-secret temporary information attack under the CK-adversary model. Even if knows these secrets, cannot calculate the session key , because consists of , , and ’s identities. Thus, our protocol withstands the known session-secret temporary information attack.
7.1.10. Desynchronization Attack
A desynchronization attack is when an adversary can modify and block the transmitted messages to make , , and unable to authenticate in the future. Assume that tries to modify the messages for desynchronizing the next session. However, as mentioned in Section 7.1.5, cannot modify the exchanged messages because has no knowledge about ’s secret credentials. In addition, we assume that blocks the transmitted messages to disturb the synchronization. calculates , generates a verification message using , and sends it to . stores the with , and checks . If the is correct, updates . sends the message to to describe that authentication is complete. Then, checks the validation of . If is validated, deletes the old and . Otherwise, stores them. Through these things, and always have synchronized values. Consequently, a desynchronization attack is impossible in our protocol.
7.1.11. Perfect Forward Secrecy
We assume that an adversary knows long-term secret keys . can try to calculate the session key . However, cannot affect on the confidentiality of past communications because is composed of the random nonces which is generated for each session. Thus, the proposed protocol provides the perfect forward secrecy.
7.1.12. Mutual Authentication
At the authentication and key agreement phase, , , and check the message validity. checks the validity of , verifies and , and checks whether . If the values are correct, each entity authenticates each other. Therefore, our protocol achieves the mutual authentication.
7.1.13. Anonymity and Untraceability
An adversary can obtain exchanged messages in the authentication and key agreement phase. However, cannot obtain real identities of , , and because these are dependent on . In addition, and update to for every session. It makes all messages are dynamic at every session. Consequently, the proposed protocol provides anonymity and untraceability.
7.2. BAN Logic
We performed the formal security analysis with BAN logic to evaluate the secure mutual authentication of the proposed protocol [10,40]. We present the notation of BAN logic in Table 2.

Table 2.
BAN logic notation.
7.2.1. Rules
We describe the rules of BAN logic in the following.
- Message meaning rule ():
- Nonce verification rule ():
- Jurisdiction rule ():
- Freshness rule ():
- Belief rule ():
7.2.2. Goals
The following are the main goals to demonstrate that our protocol satisfies the secure mutual authentication.
- Goal 1:
- .
- Goal 2:
- .
- Goal 3:
- .
- Goal 4:
- .
7.2.3. Assumptions
We assume the following to initiate states of the proposed protocol.
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
7.2.4. Idealized Forms
We present ideal forms of our protocol as below.
- :
- :
- :
- :
7.2.5. Proof
We conducted the BAN logic test, and detailed steps are described as follows.
- Step 1:
- From , we can obtain .
- Step 2:
- Using and with , we can get .
- Step 3:
- can obtained using and with .
- Step 4:
- Using and with , we can get .
- Step 5:
- We can obtain from .
- Step 6:
- can obtained using and with .
- Step 7:
- Utilizing and with , we can get .
- Step 8:
- For obtaining , we can use and with .
- Step 9:
- From , we can obtain .
- Step 10:
- For getting , we can utilize and with .
- Step 11:
- For obtaining , we can use and with .
- Step 12:
- Using and with , we can get .
- Step 13:
- We can get from .
- Step 14:
- can obtained using and with .
- Step 15:
- can obtained using and with .
- Step 16:
- Using and with , we can get .
- Step 17:
- Since the session key is , we can obtain from , , and .
- Step 18:
- From , , and , we can get .
- Step 19:
- can obtained from and .
- Step 20:
- can obtained using and .
Therefore, , , and can perform the secure mutual authentication in our protocol.
7.3. ROR Model
The session key security of the proposed protocol is demonstrated using the ROR model [11]. We interpret the ROR model before proving the session key security of the proposed protocol. In the authentication and key agreement phase of the proposed protocol, we have three participants , which are mobile user , home gateway , and smart device . These are instances , , and for , , and , respectively. can eavesdrop, intercept, or modify transmitted messages through an insecure channel. In addition, can simulate active and passive attacks by executing various queries defined in the ROR model, such as , , , , and queries. Detailed instructions of the queries are below.
- : performs this query to obtain transmitted messages over a public channel between , , and .
- : This query represents that can extract sensitive information stored in the mobile device of .
- : This query is that reveals the current session key between and . If an adversary cannot reveal the session key between and using the query, then is secure.
- : With this query, can send the message M to and receive a response message.
- : Before the start of the game, a fair coin is tossed and the result becomes only known to . uses this result to make a decision of the query. If runs the query and the session key is fresh, returns for = 1 or a random number for = 0. Otherwise, it returns a null (⊥).
After performs the query on , must distinguish the result value. uses the output of the query for checking the consistency of the random bit . wins the game when the guessed bit is equal to . Moreover, all participants have access to a collision-resistant cryptographic one-way hash function . We model as a random oracle, .
7.3.1. Security Proof
We prove the session key security of the proposed protocol using Zipf’s law [41].
Theorem 1.
can break the session key security of the proposed protocol. We denote the advantage of running in polynomial time as . Then, we obtain the following.
Here, is the number of queries, is the range space of the hash function , and is the number of queries. In addition, C and s denote Zipf’s parameters [41].
Proof.
The proof of Theorem 1 is similar as presented in [42,43]. We prove the session key security through a sequence of four games, , where . indicates the event that wins by guessing the random bit correctly. We denote the advantage of winning the game as . In the following, we describe each game.
- : This game allows to execute the real attack against the proposed protocol. chooses a random bit at the beginning of . Then, we obtain the following in accordance with this game.
- : In this game, runs the query and eavesdrops transmitted messages , , , and . Then, executes and queries to validate whether the derived session key is real or not. In our protocol, the session key is constructed as . To derive the session key, needs to know the identities and random nonces of , , and . Consequently, there are no instances in which increases ’s winning probability. Therefore, and turn out to be indistinguishable, and we can obtain the following.
- : To obtain the session key, performs and queries in this game. can perform an active attack by modifying exchanged messages. However, all exchanged messages are constructed with secret credentials and random nonces, and protected using one-way hash function . In addition, is difficult to derive secret credentials and random nonces because it is a computationally infeasible problem according to the property of . Hence, we can get the following result through the use of birthday paradox [44].
- : In the final game , can try to get the session key with the query. By the query, can extract sensitive values stored in the mobile device of . Sensitive values are expressed as , , , and . Since has no knowledge of and , cannot derive secret values and from the extracted values. Besides, it is a computationally infeasible task for to guess and simultaneously. In conclusion, and are indistinguishable. By utilizing Zipf’s law, the following result can be obtained.As all games have been run, must guess the bit for winning the game. Therefore, we can obtain the following result.From Equations (1) and (2), we obtain the result as follows.With Equations (5) and (6), we derive the below equation.By using the triangular inequality, we can have the following result with Equations (4), (5), and (7).Finally, by multiplying both sides of Equation (8) by two, we can obtain the required result.
Therefore, we prove Theorem 1. □
7.4. AVISPA Tool
We utilized the AVISPA tool [7,8,9] to verify the security of our protocol against MITM and replay attacks. The AVISPA tool uses a role based language, High-Level Protocols Specification Language (HLPSL), to specify actions of each protocol participant [45]. For the security analysis, the HLPSL is entered and translated into the Intermediate Format (IF) in the AVISPA tool. If the IF becomes the input of the back-end, the back-end outputs the security analysis result as the Output Format (OF). The back-end of the AVISPA tool consists of four components, including SAT-based Model-Checker (SATMC), Tree-Automata-based Protocol Analyzer (TA4SP), On-the-Fly-Model-Checker (OFMC), and CL-based Attack Searcher (CL-AtSe). If the OF is SAFE for the back-end, the proposed protocol prevents MITM and replay attacks. We use OFMC and CL-AtSe for the proposed protocol, since SATMC and TA4SP do not support XOR operations.
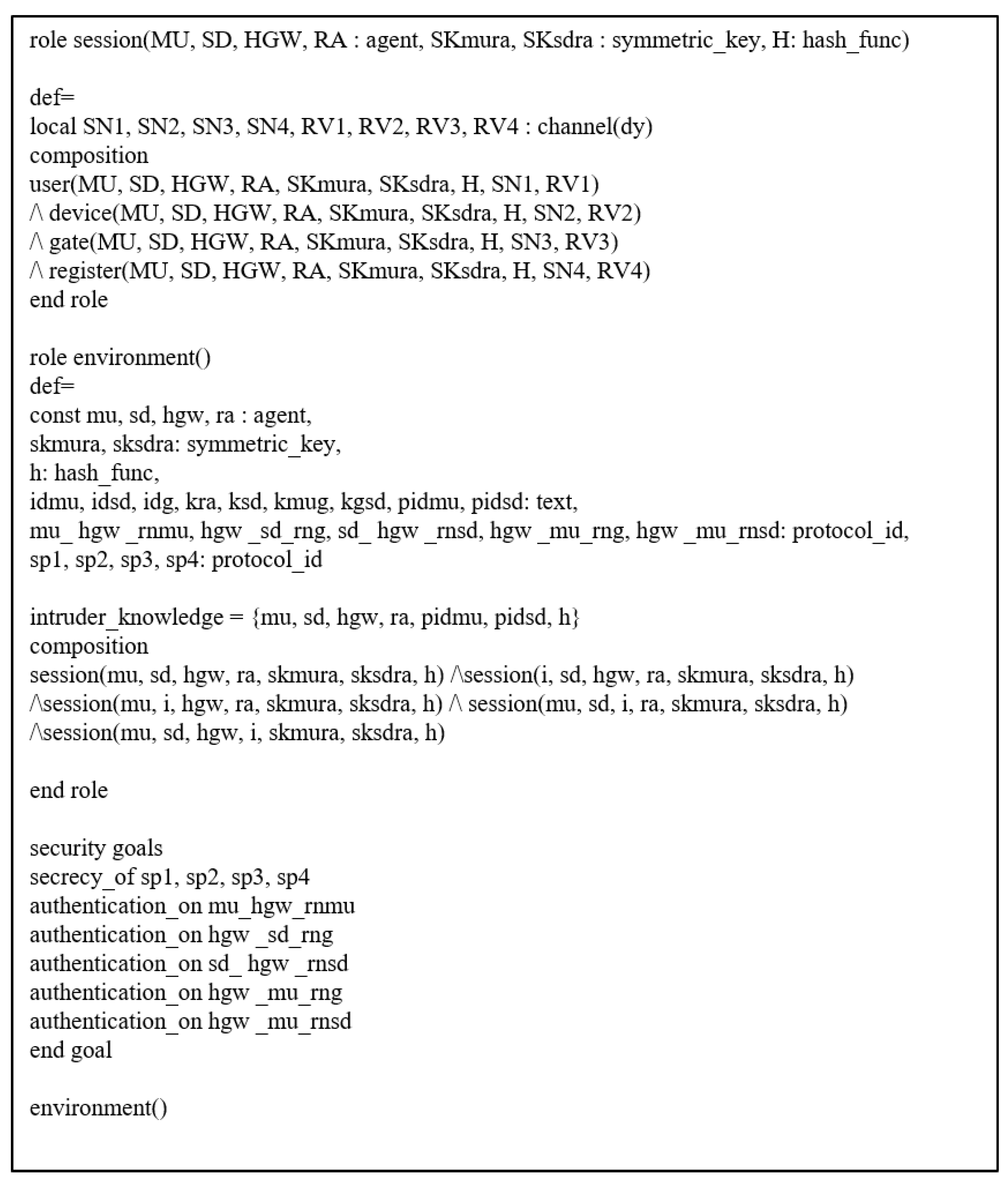
7.4.1. Specifications of the Proposed Protocol
We set up the session, environment, and security goals using the HLPSL language. Details of these are shown in Figure 6. In and , we specify instances of each role and construct the whole protocol session. In addition, we state the security goals of the proposed protocol. is used to check secret values are explicitly undisclosed and is used to verify the validity of secret values between entities. Through and , we can confirm that the proposed protocol is resistant to MITM and replay attacks.

Figure 6.
Roles of session, environment, and security goals.
As shown in Figure 7, if the registration process is started at state 0, generates identity and password , and calculates at state 1. Then, sends the registration request message to . After receiving secret values from , updates the state from 1 to 2. Then, stores secret values encrypted with the and in the mobile device. Then, transmits the authentication request message to . Upon receiving the message in state 2, updates the state from 2 to 3 and checks . If the condition is met, authenticates successfully. Then, computes and sends it to . The roles of , , and are similar to the roles of .

Figure 7.
Roles of .
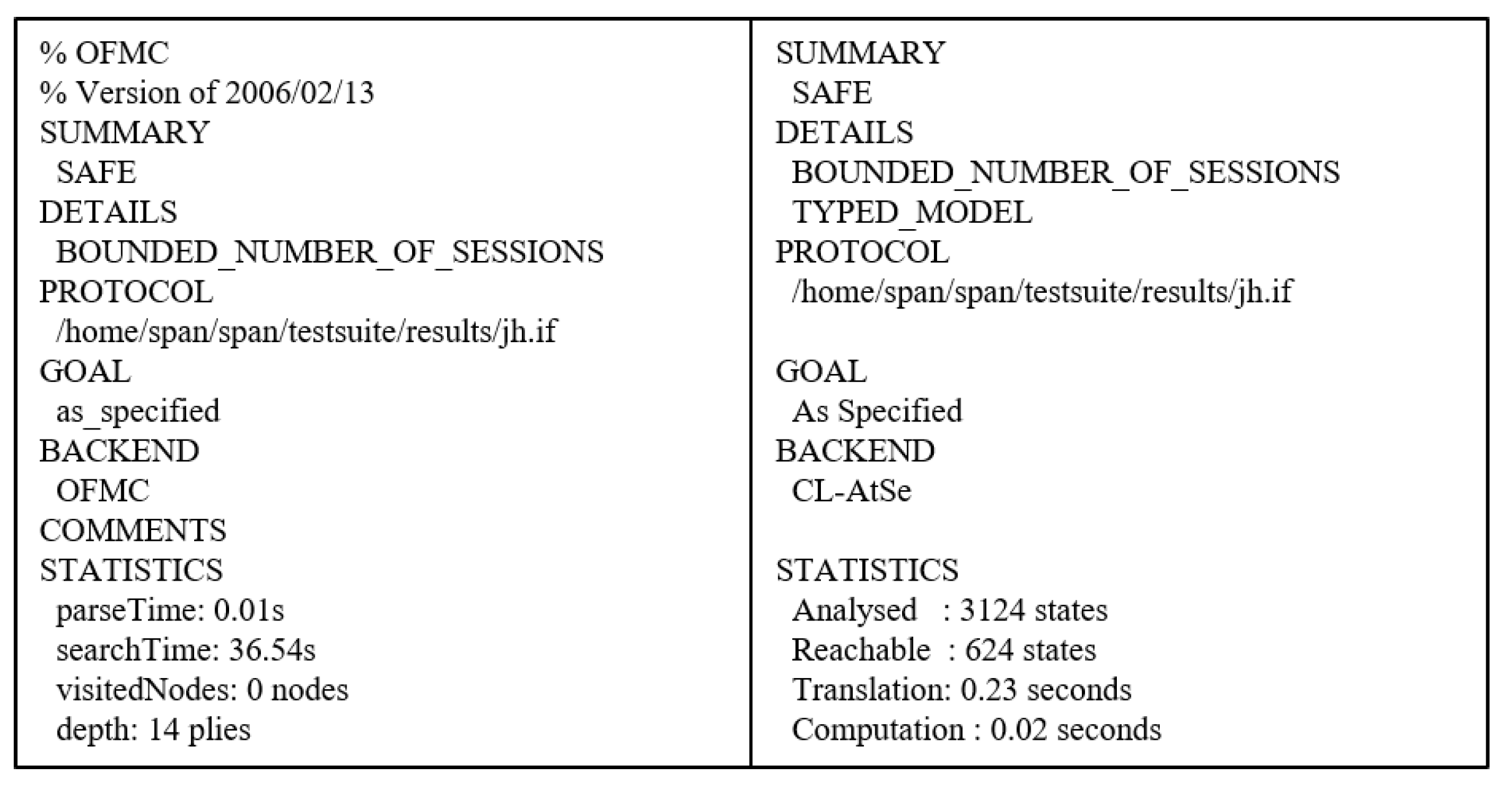
7.4.2. Result of AVISPA
We use OFMC and CL-AtSe for XOR operations to show the security analysis result. The OFMC estimates that the proposed protocol withstands the MITM attack, and CL-AtSe assesses our protocol is resistant to the replay attack. Figure 8 shows the OF of OFMC and CL-AtSe back-ends for the proposed protocol. The output shows that the proposed protocol is SAFE in OFMC and CL-AtSe back-ends. Thus, our protocol successfully satisfies the specified security goals. In other words, our protocol withstands MITM and replay attacks.
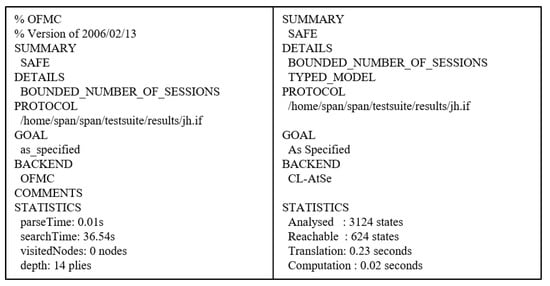
Figure 8.
Results of analysis using OFMC and CL-AtSe.
8. Performance and Security Analyses
This section shows the comparison results of the proposed protocol with similar protocols [6,31,34,38], including computational and communication costs, and security properties.
8.1. Computational Costs
The computational costs are analyzed for our protocol and related existing protocols [6,31,34,38]. For comparison, we refer to the work [46]. , , , and denote the execution times of an ECC point multiplication (≈7.3529 ms), fuzzy extractor function (≈7.3529 ms), a hash function (≈0.0004 ms), and symmetric key encryption/decryption (≈0.1303 ms), respectively. Table 3 contains the result of the computational costs comparison. Although the proposed protocol has a slightly higher computational cost than the low-security-risk path of Xiang and Zheng’s protocol [6], our protocol provides more robust security. Moreover, the proposed protocol has a lower computational cost compared with the other related protocols, except for the low-security-risk path of Xiang and Zheng’s protocol [6].

Table 3.
Computational costs comparison.
8.2. Communication Costs
The communication cost of our protocol is compared to those costs of other related protocols [6,31,34,38]. Referring to the paper [31], we define that an ECC point, symmetric key encryption/decryption, hash function, random number, identity, and timestamp are 320, 256, 160, 160, 128, and 32 bits. We estimate the message header as Internet Protocol version 4 (IPv4) packet header, 4 bits. In the authentication and key agreement phase of the proposed protocol, exchanged messages , , , , and need 640, 640, 320, 20, and 160 bits, respectively. Consequently, our protocol has 2080 bits as the total communication cost. In Table 4, we show the results of the communication costs comparison. Although our protocol has a higher communication cost than some of the existing protocols [6,31,38], it provides more efficient computational costs and security.

Table 4.
Communication costs comparison.
8.3. Security Properties
In Table 5, we present security properties of the proposed protocol and those of models by Shuai et al. [31], Wazid et al. [34], Banerjee et al. [38], and Xiang and Zheng [6]. In contrast with the other protocols [6,31,34,38], our protocol prevents more attacks. Thus, the proposed protocol meets more security requirements compared to related protocols.

Table 5.
Security properties.
9. Conclusions
We proved that Xiang and Zheng’s protocol does not perform secure mutual authentication. We also discovered that their protocol is vulnerable to impersonation, stolen smart device, and session key disclosure attacks. To deal with the security threats to Xiang and Zheng’s protocol, we proposed a secure and lightweight authentication protocol for IoT-based smart homes. We demonstrated that the proposed protocol is secure against various attacks, including impersonation, replay, MITM, and session key disclosure attacks. We performed the BAN logic test to show that our protocol ensures secure mutual authentication. Furthermore, we demonstrated that the proposed protocol provides session key security and resists replay and MITM attacks by utilizing the ROR model and the AVISPA tool. We compared our protocol with associated existing protocols in terms of security properties, and computational and communication costs. In conclusion, our protocol provides better security and low computational costs. When we consider all perspectives of security and costs, our protocol is suitable for practical IoT-based smart home environments. In the future, we will develop a better protocol and implement it in an actual environment.
Author Contributions
Conceptualization, J.O.; formal analysis, J.L., S.S. and M.K.; investigation, S.Y.; methodology, J.O.; software, S.Y. and J.L.; supervision, Y.P.; validation, S.S., M.K. and Y.P.; writing—original draft, J.O.; writing—review and editing, S.Y., J.L., S.S., and Y.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported in part by the Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education under grant 2020R1I1A3058605, and in part by the BK21 FOUR project funded by the Ministry of Education, Korea under grant 4199990113966.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Shin, S.; Kwon, T. A lightweight three-factor authentication and key agreement scheme in wireless sensor networks for smart homes. Sensors 2019, 19, 2012. [Google Scholar] [CrossRef] [PubMed]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Lightweight and secure password based smart home authentication protocol: LSP-SHAP. J. Netw. Syst. Manag. 2019, 27, 1020–1042. [Google Scholar] [CrossRef]
- Baruah, B.; Dhal, S. A two-factor authentication scheme against FDM attack in IFTTT based smart home system. Comput. Secur. 2018, 77, 21–35. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Iinatti, J.; Ylianttila, M.; Sain, M. Lightweight and secure session-key establishment scheme in smart home environments. IEEE Sens. J. 2015, 16, 254–264. [Google Scholar] [CrossRef]
- Kumar, P.; Braeken, A.; Gurtov, A.; Iinatti, J.; Ha, P.H. Anonymous secure framework in connected smart home environments. IEEE Trans. Inf. Forensics Secur. 2017, 12, 968–979. [Google Scholar] [CrossRef]
- Xiang, A.; Zheng, J. A situation-aware scheme for efficient device authentication in smart grid-enabled home area networks. Electronics 2020, 9, 989. [Google Scholar] [CrossRef]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 10 November 2020).
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 10 November 2020).
- Mandal, S.; Bera, B.; Sutrala, A.K.; Das, A.K.; Choo, K.R.; Park, Y. Certificateless-signcryption-based three-factor user access control scheme for IoT environment. IEEE Internet Things J. 2020, 7, 3184–3197. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password based authenticated key exchange in the three-party setting. In Public Key Cryptgraphy; Springer: Les Diablerets, Switzerland, 2005; pp. 65–84. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Kim, M.; Park, Y.; Das, A.K. On the design of secure and efficient three-factor authentication protocol using honey list for wireless sensor networks. IEEE Access 2020, 8, 107046–107062. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef] [PubMed]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In International Conference on the Theory and Applications of Cryptographic Thechniques (EUROCRYPT’02); Springer: Amsterdam, The Netherlands, 2002; pp. 337–351. [Google Scholar]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.P.C.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. A secure and efficient three-factor authentication protocol in global mobility networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. On the design of provably secure lightweight remote user authentication scheme for mobile cloud computing services. IEEE Access 2017, 5, 25808–25825. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Das, A.K. 2PAKEP: Provably secure and efficient two-party authenticated key exchange protocol for mobile environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Alhakami, H.; Baz, A.; Al-Turjman, F. Securing demand response management: A certificate-based access control in smart grid edge computing infrastructure. IEEE Access 2020, 8, 101235–101243. [Google Scholar] [CrossRef]
- Park, K.; Noh, S.; Lee, H.; Das, A.K.; Kim, M.; Park, Y.; Wazid, M. LAKS-NVT: Provably secure and lightweight authentication and key agreement scheme without verification table in medical internet of things. IEEE Access 2020, 8, 119387–119404. [Google Scholar] [CrossRef]
- Ul Haq, I.; Wang, J.; Zhu, Y. Secure two-factor lightweight authentication protocol using self-certified public key cryptography for multi-server 5G networks. J. Netw. Comput. Appl. 2020, 161, 102660. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Chandrakar, P.; Om, H. A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput. Commun. 2017, 110, 26–34. [Google Scholar] [CrossRef]
- Santoso, F.K.; Vun, N.C.H. Securing IoT for smart home system. In Proceedings of the 2015 International Symposium on Consumer Electronics (ISCE), Madrid, Spain, 24–26 June 2015; pp. 1–2. [Google Scholar]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure remote anonymous user authentication scheme for smart home environment. Internet Things 2020, 9, 100158. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.P.C.; Park, Y. Physically secure lightweight anonymous user authentication protocol for internet of things using physically unclonable functions. IEEE Access 2019, 7, 85627–85644. [Google Scholar] [CrossRef]
- Dey, S.; Hossian, A. Session-key establishment and authentication in a smart home network using public key cryptography. IEEE Sens. Lett. 2019, 3, 7500204. [Google Scholar] [CrossRef]
- Gaba, G.S.; Kumar, G.; Monga, H.; Kim, T.; Kumar, P. Robust and lightweight mutual authentication scheme in distributed smart environments. IEEE Access 2020, 8, 69722–69733. [Google Scholar] [CrossRef]
- Kumar, P.; Chouhan, L. A privacy and session key based authentication scheme for medical IoT networks. Comput. Commun. 2021, 166, 154–164. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Vaidya, B.; Park, J.H.; Yeo, S.S.; Rodrigues, J.J. Robust one-time password authentication scheme using smart card for home network environment. Comput. Commun. 2011, 34, 326–336. [Google Scholar] [CrossRef]
- Kim, H.J.; Kim, H.S. AUTH HOTP-HOTP based authentication scheme over home network environment. In International Conference on Computational Science and Its Applications; Springer: Berlin/Heidelberg, Germany, 2011; pp. 622–637. [Google Scholar]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Lyu, Q.; Zheng, N.; Liu, H.; Gao, C.; Chen, S.; Liu, J. Remotely access “my” smart home in private: An anti-tracking authentication and key agreement scheme. IEEE Access 2019, 7, 41835–41851. [Google Scholar] [CrossRef]
- Poh, G.S.; Gope, P.; Ning, J. Privhome: Privacy-preserving authenticated communication in smart home environment. IEEE Trans. Dependable Secur. Comput. 2019. [Google Scholar] [CrossRef]
- Irshad, A.; Usman, M.; Chaudry, S.A.; Bashir, A.K.; Jolfaei, A.; Srivastava, G. Fuzzy-in-the-loop-driven low-cost and secure biometric user access to server. IEEE Trans. Reliab. 2020. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An efficient, anonymous and robust authentication scheme for smart home environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef]
- AL-Turjman, F.; Deebak, D.B. Seamless authentication: For IoT-big data technologies in smart industrial application systems. IEEE Trans. Ind. Inf. 2020. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [PubMed]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Das, A.K.; Yu, S.; Lee, J.; Park, Y. A dynamic privacy-preserving key management protocol for V2G in social internet of things. IEEE Access 2019, 7, 76812–76832. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, K.; Das, A.K.; Park, Y. IoV-SMAP: Secure and efficient message authentication protocol for IoV in smart city environment. IEEE Access 2020, 8, 167875–167886. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]
- Vigano, L. Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Mo, J.; Chen, H. A lightweight secure user authentication and key agreement protocol for wireless sensor networks. Secur. Commun. Netw. 2019, 2019, 2136506. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).