Abstract
Edge computing has been introduced to the Internet of Things (IoT) to meet the requirements of IoT applications. At the same time, data aggregation is widely used in data processing to reduce the communication overhead and energy consumption in IoT. Most existing schemes aggregate the overall data without filtering. In addition, aggregation schemes also face huge challenges, such as the privacy of the individual IoT device’s data or the fault-tolerant and lightweight requirements of the schemes. In this paper, we present a privacy-preserving and lightweight selective aggregation scheme with fault tolerance (PLSA-FT) for edge computing-enhanced IoT. In PLSA-FT, selective aggregation can be achieved by constructing Boolean responses and numerical responses according to specific query conditions of the cloud center. Furthermore, we modified the basic Paillier homomorphic encryption to guarantee data privacy and support fault tolerance of IoT devices’ malfunctions. An online/offline signature mechanism is utilized to reduce computation costs. The system characteristic analyses prove that the PLSA-FT scheme achieves confidentiality, privacy preservation, source authentication, integrity verification, fault tolerance, and dynamic membership management. Moreover, performance evaluation results show that PLSA-FT is lightweight with low computation costs and communication overheads.
1. Introduction
The rapid development of Internet of Things (IoT) technology has made a considerable impact on our lives, such as smart home [1], smart healthcare [2], and smart grid [3]. More and more IoT devices connect to the Internet, and the cloud center analyzes all sensing data in traditional cloud computing, wherein it is difficult to provide real-time services to meet the requirements of IoT applications [4]. Edge computing is used to preprocess the data at the network edge and then transmit these preprocessed data to the cloud center [5]. Thus, it is introduced into IoT to overcome the bottleneck mentioned above (also regarded as an edge computing-enhanced IoT system) [6]. Owing to the distributed architecture of edge computing, sensitive information can be directly stored and processed on edge devices. Nevertheless, the capacity of the edge device is limited, and edge devices are easily captured by adversaries, resulting in the unreliability of edge devices [7]. Therefore, edge computing may increase the possibility of sensitive information leakage [8].
As an essential data processing technique, data aggregation can reduce energy and bandwidth consumption and gain accurate information by merging redundancy data. Although data aggregation is beneficial to edge computing-enhanced IoT, the adversaries can eavesdrop on messages during the transmission between the entities, and even modify messages and forge signatures. Consequently, the authenticity of aggregated data cannot be guaranteed, and the decision of the cloud center may be disturbed. Therefore, privacy-preserving data aggregation (PPDA) has emerged as a significant research area [9].
Most existing aggregation schemes do not process data before the aggregation to avoid revealing data privacy, i.e., overall aggregation [10,11,12,13,14,15]. However, the overall aggregation will aggregate massive unrelated data, which increases the difficulty of both data analysis and data storage. Aggregating the data selectively within the scope of the query will be more beneficial to reduce response latency. Therefore, many selective aggregation schemes have already been proposed [16,17,18,19,20,21,22]. Nonetheless, both overall aggregation and selective aggregation schemes face the following challenges. Firstly, the accuracy of the aggregated data is likely to have a decrease since some unrelated data are also involved in the data aggregation and influence the final decisions. Secondly, a few schemes do not achieve source authentication and integrity verification, and the messages and signatures may be modified or tempered. Thirdly, the huge computation costs bring challenges to resource-constrained IoT devices. Fourthly, fault tolerance should be taken into account to enhance the availability of the aggregation schemes.
We present PLSA-FT, a privacy-preserving and lightweight selective aggregation scheme with fault tolerance for edge computing-enhanced IoT. Our main contributions are as follows:
- In PLSA-FT, the cloud center can set filtering conditions for the data source to avoid aggregating unrelated data. Hence, selective data aggregation can be achieved by constructing Boolean responses and numerical responses according to the attributes of the data source.
- We have constructed the encryption, the aggregation, and the decryption process on the basis of the modified Paillier homomorphic cryptosystem to ensure the confidentiality and privacy of the individual IoT device’s data.
- The PLSA-FT is fault-tolerant, which means that the cloud center could obtain the aggregated data uploaded by all the working IoT devices, even if some IoT devices fail to upload reports.
- We have analyzed the system characteristics to prove that the PLSA-FT scheme achieves confidentiality, privacy preservation, source authentication, integrity verification, fault tolerance, and dynamic membership management. Furthermore, we have evaluated the performance of the scheme to show that the PLSA-FT is lightweight.
The outline of this paper is as follows. The Section 2 introduces related works. The Section 3 presents the system model, the security model, and design goals. In the Section 4, we describe the proposed PLSA-FT scheme in detail. The Section 5 and the Section 6 demonstrate the system characteristic analyses and the performance evaluation. Finally, we provide a conclusion in the Section 7.
2. Related Work
Privacy-preserving data aggregation has attracted much attention in recent years. To protect the sensitive information of users, the homomorphic encryption technology [11,13,16,17,18,19,23,24,25,26,27,28,29,30], the differential privacy technology [17,26,27,31], and the pseudonym technology [12,15,32,33] have mainly been used in aggregation schemes [34].
In [15], Guan et al. utilized pseudonyms and pseudonym certificates to perform secure data aggregation and guaranteed the anonymity of the devices. Nonetheless, the certificate generations and updates were time-consuming. Qian et al. [17] adopted the differential privacy technique to ensure vital privacy preservation and supported selective aggregation to provide online user behavior analysis based on the BGN homomorphic cryptosystem. Mahdikhani et al. [18] employed the Paillier homomorphic encryption to encrypt the reports to avoid the leakage of sensitive information. Moreover, selective aggregation was achieved by computing the inner product similarity to identify the aggregation subset. Zhang et al. [24] constructed a lightweight and verifiable PPDA scheme, called LVPDA, which was proved to be existentially unforgeable under the chosen message attack. LVPDA introduced the edge computing paradigm for efficient data storage and computing services. Nonetheless, the overall interaction of the scheme was complicated, and the signature verification did not support batch verification. In [32], Wang et al. proposed the first anonymous and secure aggregation scheme. In this scheme, the introduction of fog computing transferred storage and computing from the cloud center to fog nodes in order to solve high latency and lack of support for mobility. Moreover, pseudonyms were used for protecting the identities of terminal devices, and homomorphic encryption was employed for guaranteeing data security in fog-based public cloud computing. However, a large number of time-consuming bilinear pairs were used for signature verification, which leads to relatively large computation costs. The security model of this scheme considered that the cloud center was entirely believable, and that the assumption of security needed to be lowered in future work.
However, these schemes mainly focused on privacy, anonymity, and selective aggregation, while the fault tolerance of the scheme was ignored. This could be a large problem because IoT devices are prone to malfunctions. The fault tolerance characteristic was especially significant in [28,29]. Li et al. [28] set the sum of all devices’ secret parameter to 0 in order to enhance the security of plaintext . Nonetheless, would not be able to decrypt the aggregated ciphertexts if one or more IoT devices malfunctioned, since the sum of was no longer 0.
Shi et al. [31] proposed a fault-tolerant protocol based on diverse groups. Grining et al. [35] proposed a provable level of privacy even if massive devices malfunctioned. Nonetheless, the above traditional PPDA schemes did not adopt the architecture of edge-computing/fog-computing and suffered from latency problems.
Lu et al. proposed a lightweight PPDA scheme to achieve data aggregation and filter fake data, based on the Paillier homomorphic cryptosystem and the Chinese Remainder Theorem [13]. Even if some devices were malfunctioning, their scheme could support fault tolerance. In [30], Zeng et al. presented a data aggregation scheme, which could support column aggregation and support an additional row aggregation. Furthermore, MMDA was fault-tolerant. However, not all the data was useful, as the aggregation of multi-dimensional data from two directions exacerbated the waste of resources. The schemes mentioned above took advantage of the computational capacity of fog computing/edge computing, whereas selective aggregation was not considered. Selective aggregation was beneficial to the recourse-constrained IoT because it could avoid spending massive resources on the aggregation and storage of unrelated data. However, there is seldom any work aiming to support the fault tolerance for selective data aggregation schemes.
In addition to fault tolerance and selective aggregation, dynamic membership management was also significant for practical application scenarios. In schemes without dynamic membership management, all the entities should be reset when there is any membership updating. It would cost considerable computation and communication overheads. Hence, we proposed the PLSA-FT system to aggregate data according to data source attributes and support the IoT devices’ dynamic membership.
3. Models and Design Goals
3.1. System Model
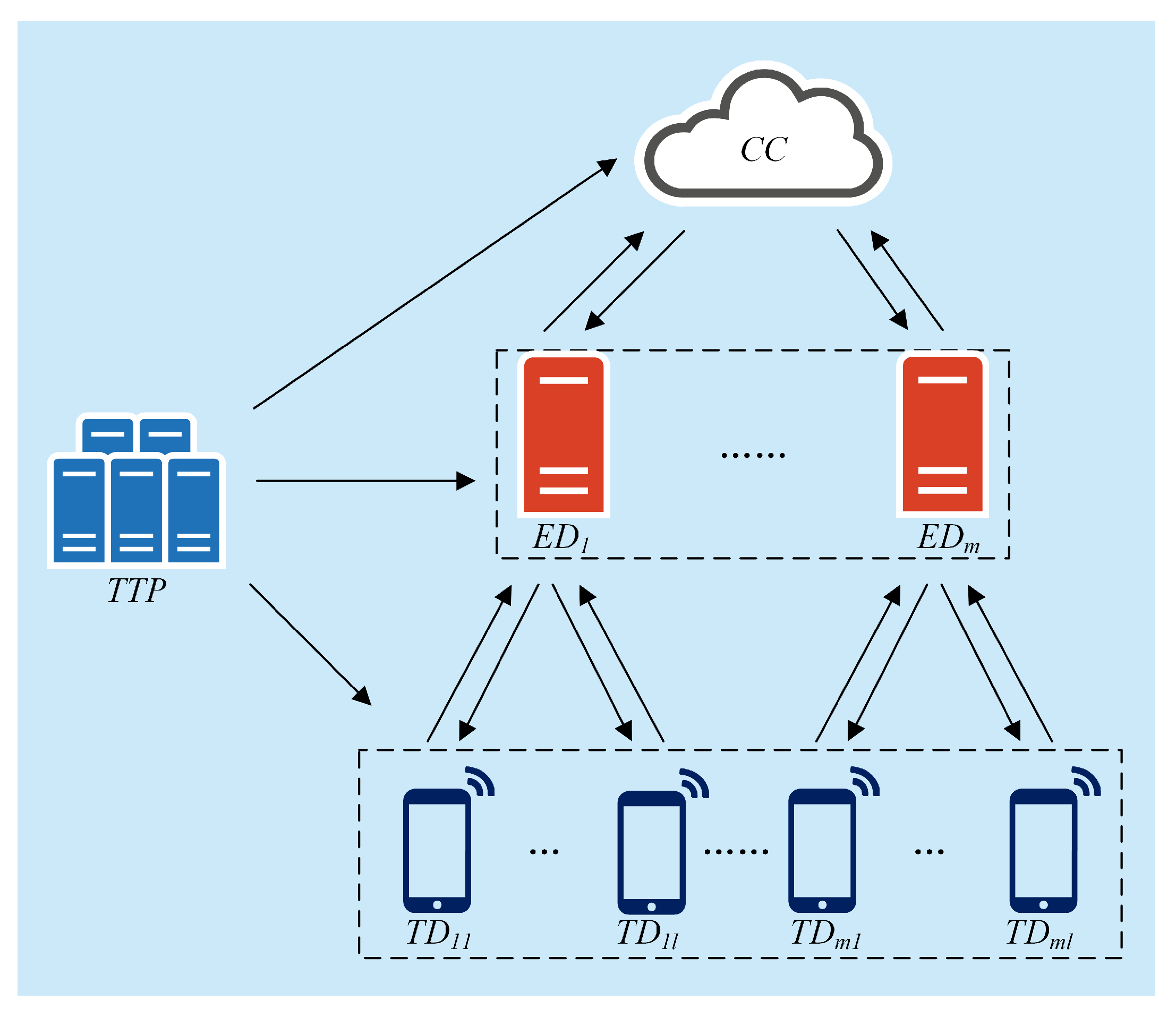
In our scheme, we consider a trusted third party, a cloud center, edge devices, and IoT, which are shown in Figure 1.
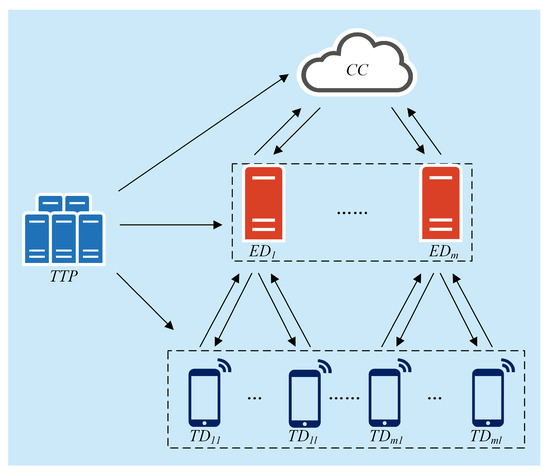
Figure 1.
The system model of the proposed PLSA-FT scheme.
The trusted third-party : The is responsible for initialization and assigning keys for all entities in a secure way. If an IoT device participates in or exits the system, the value of the secret parameter in the ’s database will update. also helps in case of IoT devices’ malfunctioning.
IoT devices : generates responses according to collected data and sends encrypted reports to the corresponding edge device .
Edge devices : The generally refers to the edge server. Specifically, transmits messages between the cloud center and IoT devices.
Cloud center : The broadcasts queries to s via corresponding edge devices, aggregates ciphertexts from s, and analyzes data after decryption.
3.2. Security Model
We assume that the trusted third-party is fully trusted, while the cloud center and edge devices are honest but curious, which means that the cloud center and edge devices would try to gain information by analyzing received data without any modification. Each IoT device is considered to be honest in our scheme.
We considered an external adversary who may eavesdrop on the sensitive information during data transmission, initiate reply attacks, and launch active attacks to modify the messages or forge the signatures. Note that PPDA is the focus of this paper. Other active attacks, i.e., denial of service (DoS) attacks and internal adversaries, are beyond the scope of this paper.
3.3. Design Goals
The main goal of our scheme is to aggregate data without revealing individual IoT device’s data. At the same time, we hope that the scheme supports fault tolerance and dynamic membership management. Specifically, the design goals can be summarized as follows:
Confidentiality and privacy preservation: Adversaries cannot infer any data from ciphertexts without the decryption key. The cloud center can only recover all IoT devices’ aggregated data, and the individual IoT device’s data are protected.
Source authentication and integrity verification: Every legal entity has a unique identity, and the reports generated from illegal devices could be detected. Meanwhile, if the adversaries modify the data or forge signatures, malicious operations would be detected.
Fault tolerance: Even if one or more IoT devices malfunction, the proposed PLSA-FT scheme can still work as usual.
Dynamic membership management: When new IoT devices join or old ones exit the system, any parameters of other devices need not be updated.
4. Our Proposed Scheme
4.1. System Initialization
We assume that the will bootstrap the whole system. Given two security parameters , first chooses two random large prime numbers with length and . Then, let , choose a generator and Then, define a function , output public key , and private key for encryption and decryption. Then, generates a bilinear map of prime order , where . Then, chooses four secure hash functions , , , and a chameleon hash function . Finally, the publishes the public parameters to all entities in the system, and keeps available to .
4.2. Registration
The chooses a random number as ’s private key and computes Then, the publishes the public key and sends the private key to , and keeps its private key secretly. Similarly, selects an identity and a random number for then computes . Then, stores in ’s database. keeps its private key secret. Considering there are IoT devices, generates , as ’s private key and computes such that
Only the and IoT devices know the private key . The also computes the corresponding for each IoT device in the system and stores in the ’s database and in the corresponding ’s database. When an IoT device joins in the system, it should apply the registration to . When an IoT device exits the system, it should send a message to notify to update the value of secret parameter . also regularly inquires of edge devices to obtain the information of working IoT devices to avoid that does not receive the message from the IoT device because of power outages or network fadings.
further chooses and computes
stores the personal information , where and are trapdoor keys. Then, calculates
and the offline signature
Finally, sends message and verification key to the corresponding , where denotes the current timestamp.
After receiving the message packet from , first checks the validity of and the freshness of . Then, performs batch verification , significantly reducing the computation costs of . If the equation holds, is valid. Otherwise, is invalid and rejects ’s responses later.
4.3. Query Broadcasting
Whenever desires, it broadcasts query to all IoT devices via intermediate edge devices. The query is formally defined as , where contains all query conditions of the data source attributes in the current query, denotes ’s basic query condition, and denotes the concatenation function. A query is defined as , whose query conditions of the data source attribute are “female” and “age > 60”, and the basic query condition is “heart rate”. uses its private key to sign query as
to guarantee that the query is not altered, where denotes the current timestamp. Then, sends to all IoT devices via corresponding edge devices.
4.4. IoT Devices Responses
After each IoT device receives the query, it first checks the freshness of Then, each IoT device checks the validity of signature through the equation . The query is accepted when the equation holds. Otherwise, the signature is invalid, and the query is rejected. If the query is accepted, each IoT device constructs the response on the basis of query . Each ’s response is formally defined as
can be computed as (, and is the Boolean response to the corresponding query condition of the data source attribute . denotes numerical response to basic query condition . Each runs the Algorithm 1 to obtaian the output . We define . Note that, the range is still a small message space in comparison with .
| Algorithm 1: IoT devices responses |
| Input: ’s Boolean response and numerical response |
| Output: |
| 1: for each do |
| 2: |
| 3: if then |
| 4: |
| 5: else |
| 6: |
| 7: end if |
| 8: end for |
| 9: return |
computes
where denotes the current timestamp. When is computed in advance, only needs to perform multiplication operations. Then, computes online signature on the basis of as follows:
randomly chooses , and the online signature is formed. Finally, sends message to .
4.5. Edge Device Aggregation
Upon receiving the message from , first checks the timestamp and the validity of . Then, uses verification key to check if
The correctness of above equation can be proved as follows:
If the equation holds, the message sent by is valid. Otherwise, the message is invalid. If the message is valid, aggregates the ciphertext by computing
Then, calculates signature
Finally, sends message to Note that if the set indicates that the devices in the set do not upload the reports, computes
and the corresponding signature is
Finally, sends message to
4.6. Edge Device Aggregation
After receiving the message packet from , first checks the validity of and the freshness of the timestamps . Then, performs batch verification , which significantly reduces the computation costs of . If the equation holds, is valid. Otherwise, is invalid and checks to identify the invalid message.
If the message is valid, sends decryption requirements to , returns to . Then, aggregates the ciphertexts by computing
can obtain the aggregated plaintext by computing
counts the number of IoT devices that satisfy ’s query conditions. denotes the sum of numerical responses that satisfy ’s query conditions. can further gain the mean of aggregated data by computing
The correctness of the ciphertext’s aggregation can be proved as follows:
4.7. Fault Tolerance Handling
If some IoT device cannot work, aggregates the ciphertexts as follows:
Even if the equation mod does not hold, can still use private key to obtain aggregated plaintexts . computes
The aggregated plaintexts can be recovered by
Similarly, can obtain the corresponding mean .
4.8. Extension to Support Dynamic Membership
Since the IoT devices in the edge computing-enhanced IoT system may change, our scheme can provide dynamic membership management. If some new IoT devices participate in the system or some old ones exit, will update the value of and replace with . can be computed as
If some new IoT devices participate in the system, they need to apply the registration to , and the detailed registration operations are described in Section 4.2. If some old IoT devices exit, needs to notify and the corresponding to delete the corresponding record . The cost of our extension is much less than that of other schemes, which need to update IoT device’s private key.
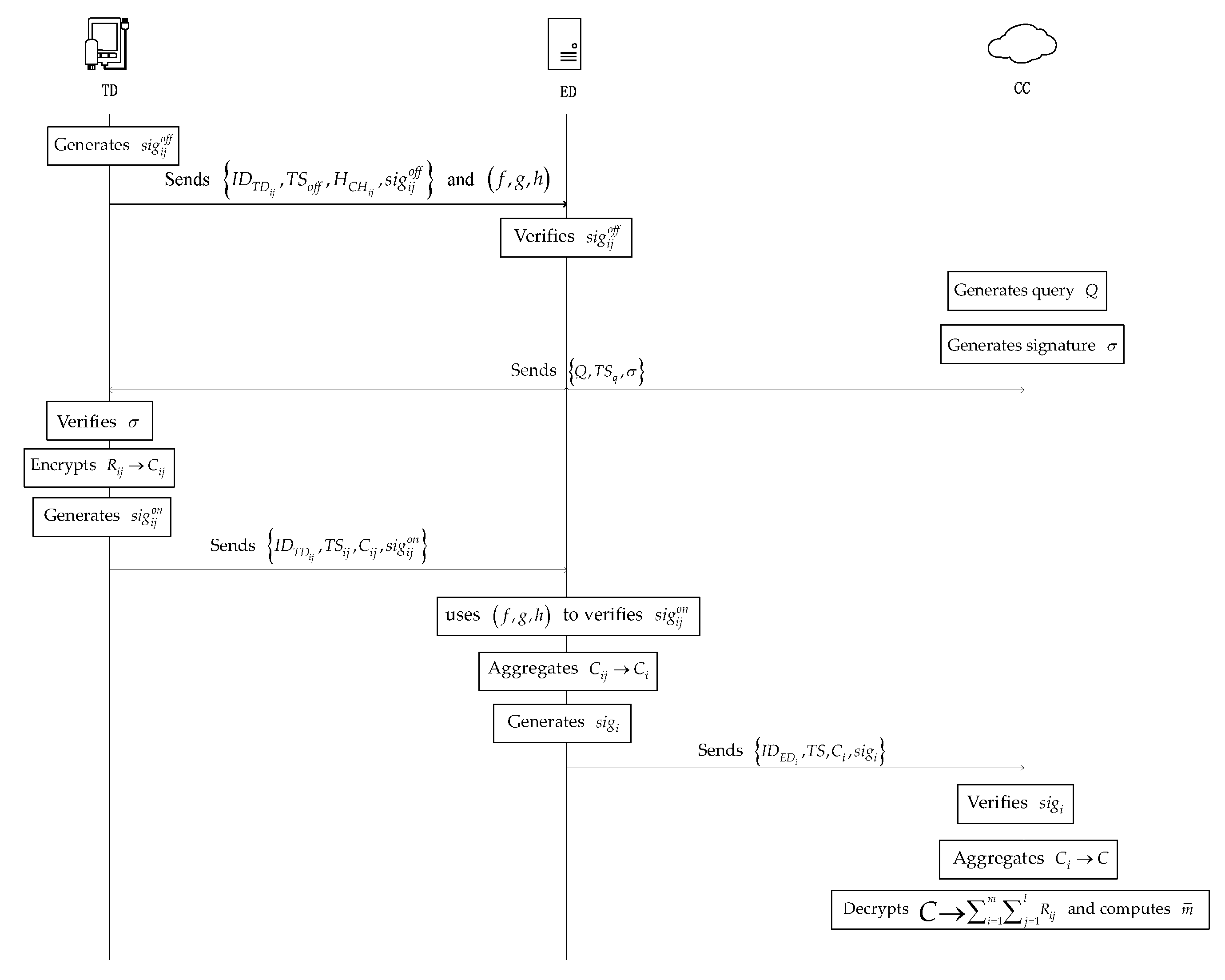
The high-level description of the main phase of the PLSA-FT scheme is shown in Figure 2.
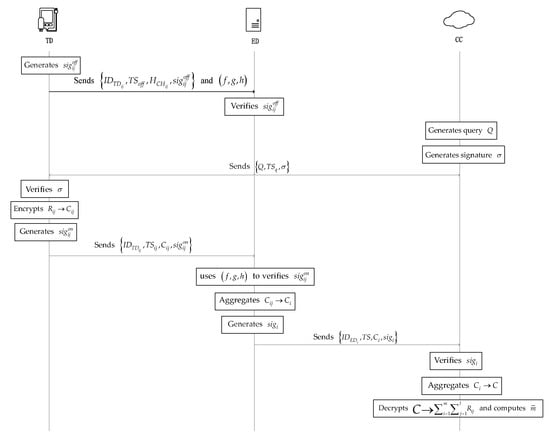
Figure 2.
High-level description of the main phase of the PLSA-FT scheme.
We also show the main phases of our proposed PLSA-FA scheme in Table 1.

Table 1.
The proposed PLSA-FA scheme.
5. System Characteristic Analyses
5.1. Confidentiality and Privacy Preservation
Theorem 1.
The privacy of the individual IoT device’s data cannot be compromised by an external adversary.
Proof of Theorem 1.
If an external adversary eavesdrops on the communication between and to obtain the report . In PLSA-FT, the reports its data in the form of . According to the property under Module , i.e., , will become . If we let , , and , then the ciphertext will become and is still a valid Paillier ciphertext. Since the Paillier encryption algorithm has been proved to be semantically secure against chosen plaintext attacks, an external adversary cannot gain without private key . □
Theorem 2.
The privacy of remaining IoT devices is protected, even if a set of IoT devices is comprised.
Proof of Theorem 2.
If a set of IoT devices are compromised, their corresponding secret keys will be leaked. In PLSA-FT, the randomly generates secret parameters , and there is no correlation between them. In other words, even if an adversary compromises some IoT devices, it has no chance to reveal the secret keys of the remaining IoT devices and the privacy of the remaining IoT devices’ data.
In an extreme case, an adversary successfully compromises IoT devices and obtains their corresponding secret keys ,,(). Recalling Equation (1), the expression for all IoT devices can be expressed in the form of . If we let denote the obtained secret keys, then the above equation will become . This means that only when the adversary obtains the secret parameter and the secret key of will it be able to gain . Therefore, we can conclude that, no matter how many IoT devices are compromised, the privacy of other IoT devices is protected. □
Theorem 3.
If the is compromised, the privacy of individual IoT device’s data and aggregated datais preserved.
Proof of Theorem 3.
If the is compromised, the adversary can obtain multiple ’s ciphertexts . Similarly, the adversary can obtain the aggregated ciphertext . According to the proof of Theorem 1, both the ciphertext and the aggregated ciphertext are valid Paillier ciphertexts, which are indistinguishable under chosen plaintext attacks. The does not have the Paillier algorithm’s secret key to perform the decryption. Thus, even if the adversary has compromised , the privacy of the individual device’s data and the privacy of the aggregated data are both protected. □
Theorem 4.
If is compromised, the privacy of the individual IoT device’s data is protected.
Proof of Theorem 4.
If a strong adversary compromises the , it can only reveal the aggregated data. Since can only obtain aggregated ciphertexts from s, the adversary cannot infer the individual IoT device’s data from the aggregated data. Therefore, even though the adversary compromised the , the privacy of the individual IoT device is still preserved. □
5.2. Source Authentication and Data Integrity
Theorem 5.
Source authentication and integrity verification of the data are guaranteed in proposed PLSA-FT scheme.
Proof of Theorem 5.
After receives the message packet from , first checks the freshness of timestamp and the validity of . can confirm the message packet generated from which and further check if the entity is legal. Then, checks if the equation holds to verify the integrity of data. In our scheme, an online/offline signature is adopted, which has been proved to be is existential unforgeable under chosen message attacks in [24]. Only the adversary with trapdoor keys can easily achieve the collision according to the trapdoor collision property [36]. Thus, an adversary cannot pass ’s integrity verification without trapdoor keys.
In addition, after receives the message packet from , first checks the freshness of timestamp and the validity of . Therefore, can confirm the message packet generated from which and further verify if the entity is legal. This ensures that every packet is from a legal entity and cannot be tampered. can performs batch verification , which greatly reduces the ’s computation costs. If the above equation does not hold, at least one message reported by is invalid, and can check to find invalid messages. If an adversary modifies or forges the data, the above equation would not hold. Thereby, our scheme ensures the source authentication and integrity verification of the data. □
5.3. Fault Tolerance
Theorem 6.
Suppose at some time slot, certain IoT devices cannot successfully upload the reports, can still obtain aggregated data of the rest of normal IoT devices.
Proof of Theorem 6.
In case certain IoT devices in subset are malfunctioning, these devices cannot successfully upload the reports to the corresponding . After aggregating the reports from s, the can obtain the aggregated report , which only includes the normal IoT devices’ reports. Even if the equation mod does not hold, the can still perform the decryption to obtain aggregated data by computing .
According to the properties under Moduln , e.g., , mod and , the aggregated ciphertext can be computed as follows:
Hence, can compute to obtain aggregated data .
Therefore, the proposed PLSA-FT scheme is well functioning, even if certain IoT devices malfunction. We can conclude that the PLSA-FT is fault-tolerant. □
5.4. Dynamic Membership Management
In PLSA-FT, when a new IoT device joins in the system, the IoT device applies to . Then, assigns the IoT device a secret key and updates the value of secret parameter to , which can be computed as . When exits the system, updates the value of secret parameter to , which can be computed as . At the same time, needs to notify the and the corresponding to delete the record .
It can be seen that the joining or exit of IoT devices does not concern other IoT devices, which requires low computation and communication costs.
6. Performance Evaluation
We evaluated the performance of the proposed PLSA-FT scheme in the aspects of the computation costs and the communication overheads. We considered other related aggregation schemes [24,25,30,32] as a comparison. We adopted the Java Pairing Based Cryptography Library (JPBC) to estimate the time costs. We used the Type-A curves as defined in the PBC library for the implementation because the Type-A curves offer the highest efficiency among all types of curves. Table 2 shows the symbol and the meaning of the operations and corresponding time costs. The security parameter is 160 bits, and the RSA modulus n is set to 1024 bits. In addition, we considered that there are s and each corresponds to s. Additionally, the length of timestamp and identity are all 160 bits. All experiments were implemented on Intel Core i7-4790 CPU @ 2.5 GHz, with 4 GB memory with Ubuntu16.04 operating system.

Table 2.
Time costs of the operations.
6.1. Computation Costs
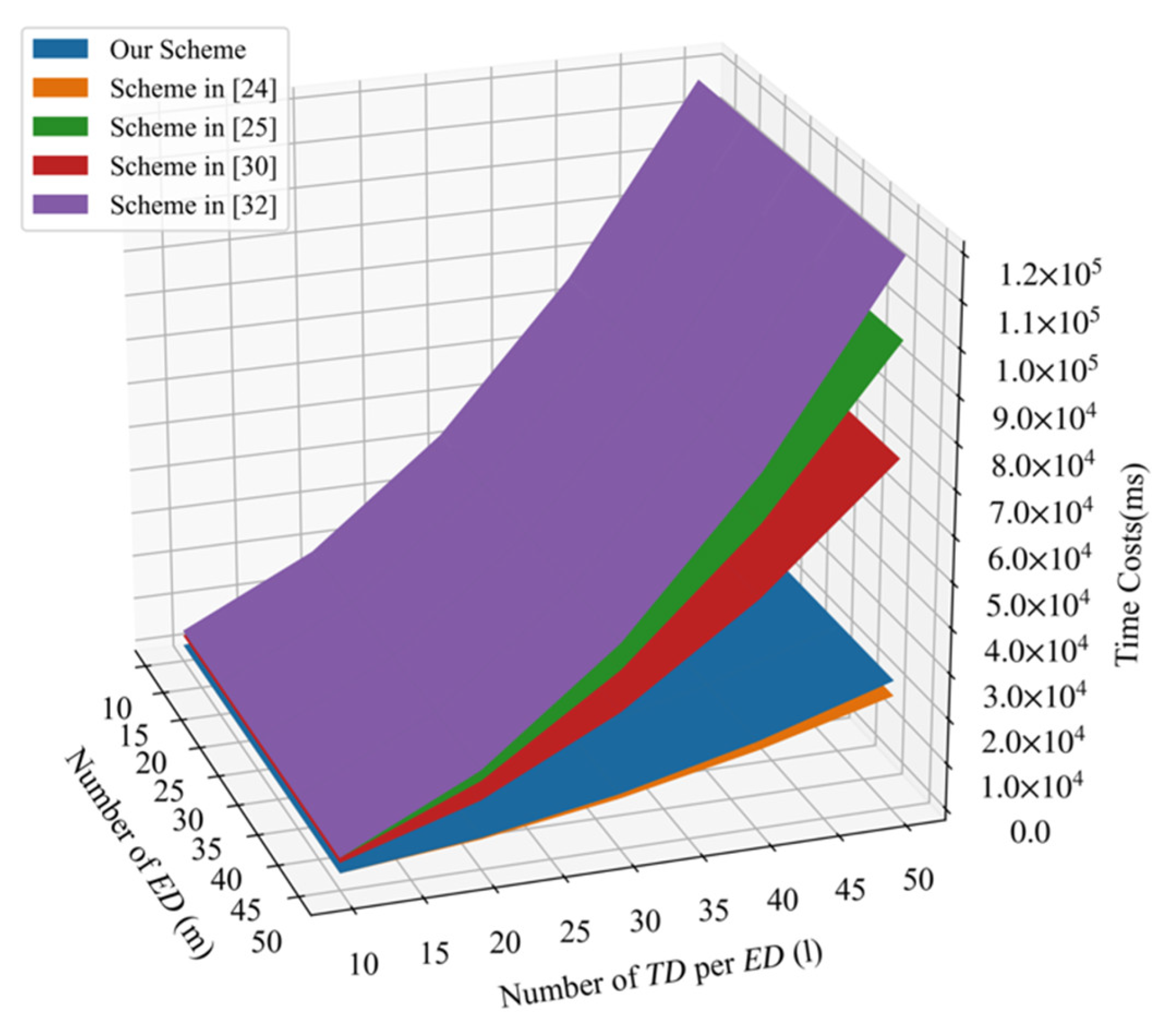
In PLSA-FT, requires one exponentiation operation in , one hash operation, and three multiplication operations to generate the ciphertext and three multiplication operations in to calculate the signature. requires 3 exponentiation operations in and 2 multiplication operations to verify the signature and multiplication operations in to aggregate ciphertext , one exponentiation operation, and a hash operation in to generate signature . requires multiplication operations bilinear pairing operations, hash operations, and one exponentiation operation in to verify the signatures and recover the plaintexts. We list a comparative summary of overall computation costs for five schemes in Table 3. From Table 3, we can find that our scheme requires the least operations that are the most time-consuming operations. When the number of edge devices increases, the cloud center needs to verify a large number of signatures; thus, the advantage of our scheme will become more evident. Figure 3 shows that the comparison of overall computation costs in terms of the number of per and the number of . It shows that our proposed PLSA-FA scheme greatly reduced the overall communication costs. Although the overall computation costs of the scheme [24] are fewer than that of our scheme, our scheme provides more functional properties than that of the scheme [24]. Table 4 further shows the comparison of functionalities achieved by five schemes.

Table 3.
The overall computation costs comparison.
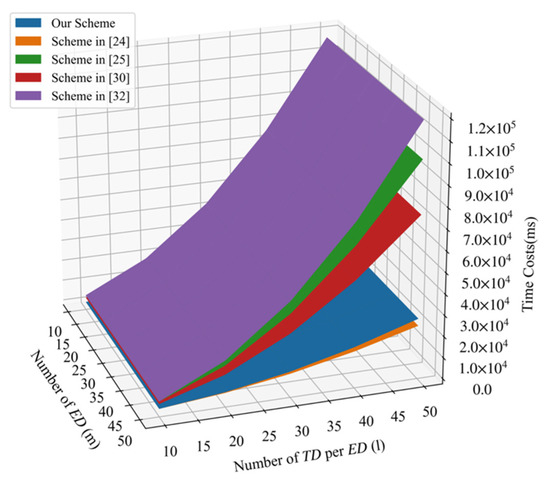
Figure 3.
Comparison of overall computation costs.

Table 4.
Comparison of overall computation costs.
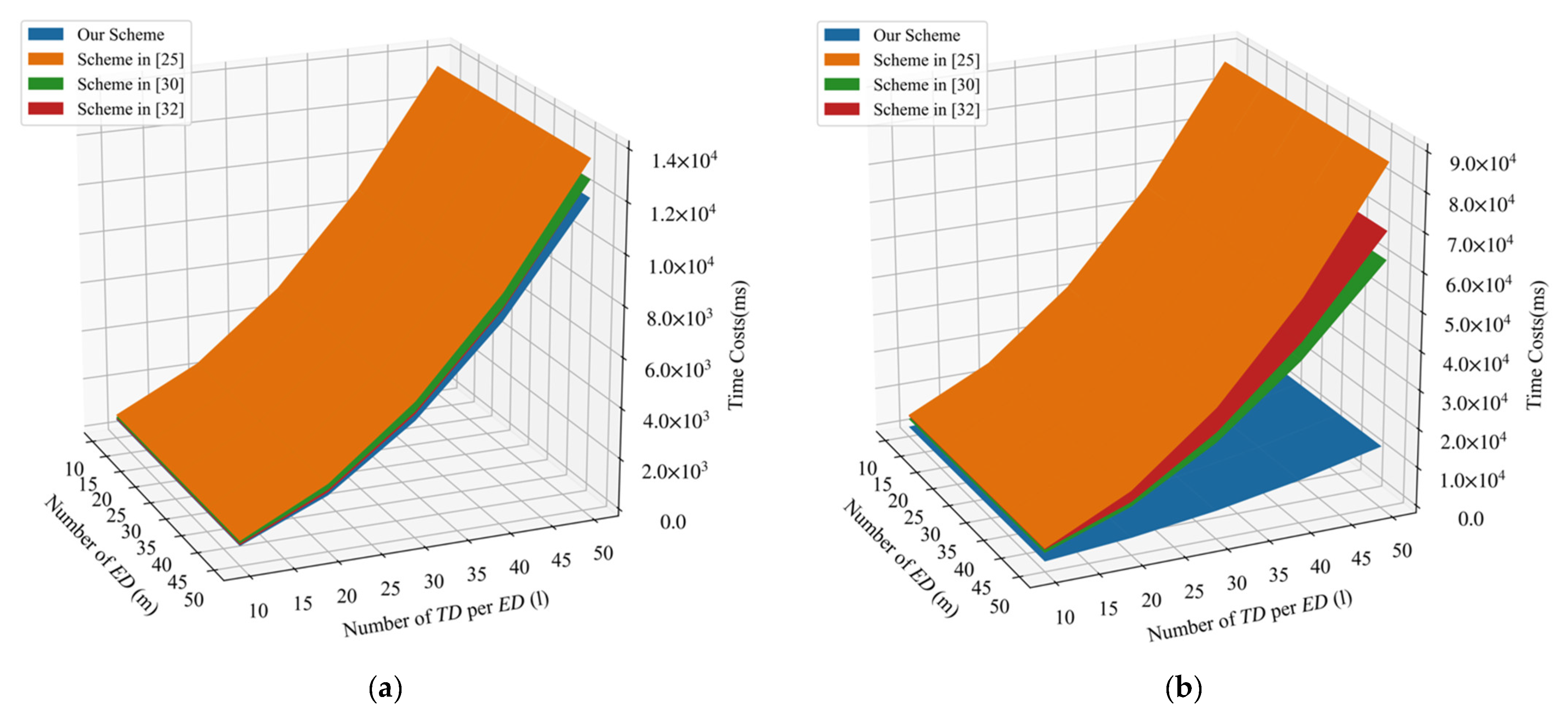
We also compared the computation costs during the aggregation phase in Figure 4a. It can be seen that our scheme requires the least computation costs during aggregation phrase. Figure 4b further depicts the signature and verification costs in terms of the number of per and the number of . The time costs of the signature and verification in our proposed PLSA-FA scheme were found to be the least among the four schemes discussed.
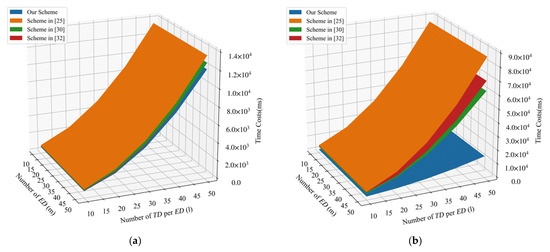
Figure 4.
(a) Comparison of aggregation costs. (b) Comparison of signature and verification costs.
6.2. Communication Overheads
The communication process of PLSA-FT consists of two processes. One is the communication process from to , and the other one is the communication process from to . In the phase of IoT devices responses, each sent a message packet to , and the corresponding communication overheads were 160 + 160 + 2048 + 160 = 2528 bits. Moreover, in the phase of edge device aggregation, each sent message packet to , and the corresponding communication overheads were 160 + 160 + 2048 + 160 = 2528 bits. Considering that there were edge devices and each corresponded to IoT devices, the total communication overheads in the scheme were 2528+ 2528 bits.
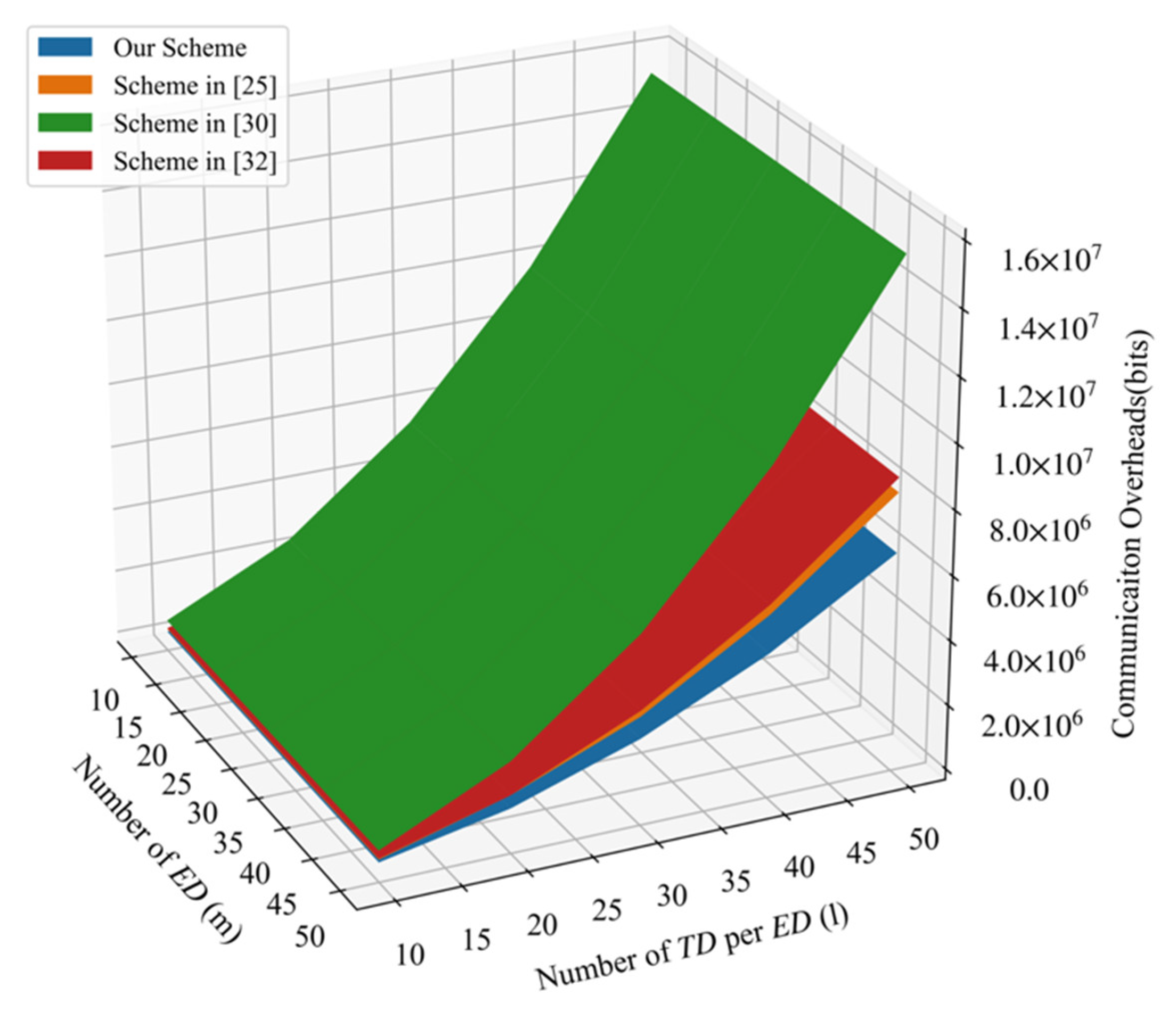
Figure 5 shows the comparison of total communication overheads among four schemes. We can conclude that the PLSA-FT scheme requires the least communication overheads.
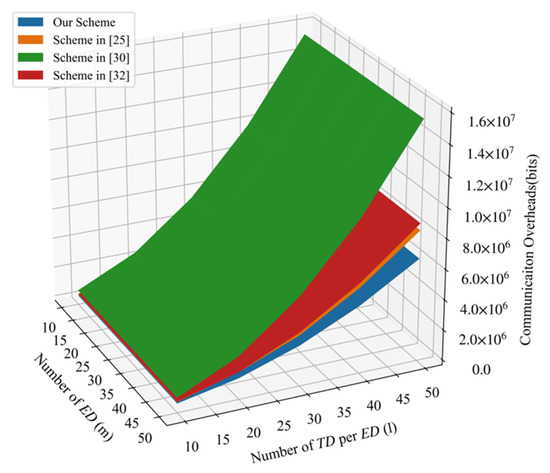
Figure 5.
Comparison of communication overheads.
7. Conclusions
In this paper, we present a privacy-preserving and lightweight selective aggregation scheme with fault tolerance (PLSA-FT) for edge computing-enhanced IoT. PLSA-FT can filter data according to data source attribute to achieve selective aggregation and provide fault tolerance and dynamic membership management. Moreover, benefiting from edge computing, PLSA-FT transfers time-consuming operations to edge devices while reducing the online computatiDon costs. Detailed system characteristic analyses illustrate that the proposed PLSA-FT scheme is secure. Moreover, performance analysis results showed that it is lightweight in both computation costs and communication overheads. However, PLSA-FT is vulnerable to the collusion attacks of edge devices and malicious IoT devices, which exposes the data privacy of a single IoT device. In our future work, we plan to extend our scheme to cope with collusion attacks. Moreover, we also prepare to improve the security properties under more powerful adversaries and active attack models.
Author Contributions
Conceptualization, Q.W.; methodology, Q.W.; validation, H.M.; investigation, Q.W.; writing—original draft preparation, Q.W.; writing—review and editing, H.M. All authors have read and agreed to the published version of the manuscript.
Funding
The research of the authors was supported by Industrial Internet innovation and development project of MIIT, China.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors wish to thank the reviewers for their valuable comments and suggestions concerning this manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Khan, M.; Silva, N.S.; Han, K. Internet of Things Based Energy Aware Smart Home Control System. IEEE Access 2016, 4, 7556–7566. [Google Scholar] [CrossRef]
- Ara, A.; Al-rodhaan, M.; Tian, Y.; Al-rodhaan, A. A Secure Privacy-Preserving Data Aggregation Scheme Based on Bilinear ElGamal Cryptosystem for Remote Health Monitoring Systems. IEEE Access 2017, 5, 12601–12617. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Zeadally, S.; Vinel, A.; Yang, L.T. Efficient and Privacy-Preserving Data Aggregation Scheme for Smart Grid against Internal Adversaries. IEEE Trans. Smart Grid 2017, 8, 2411–2419. [Google Scholar] [CrossRef]
- Botta, A.; Donato, D.W.; Persico, V.; Pescapé, A. Integration of Cloud computing and Internet of Things: A survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Sun, X.; Ansari, N. EdgeIoT: Mobile Edge Computing for the Internet of Things. IEEE Commun. Mag. 2016, 54, 22–29. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile Edge Computing, Fog et al: A Survey and Analysis of Security Threats and Challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef] [Green Version]
- Zhang, J.; Chen, B.; Zhao, Y.; Cheng, X.; Hu, F. Data Security and Privacy-Preserving in Edge Computing Paradigm: Survey and Open Issues. IEEE Access 2018, 6, 18209–18237. [Google Scholar] [CrossRef]
- He, J.; Cai, L.; Cheng, P.; Pan, J.; Shi, L. Distributed Privacy-Preserving Data Aggregation Against Dishonest Nodes in Network Systems. IEEE Internet Things J. 2019, 6, 1462–1470. [Google Scholar] [CrossRef]
- Fan, C.I.; Huang, S.Y.; Lai, Y.L. Privacy-Enhanced Data Aggregation Scheme against Internal Attackers in Smart Grid. IEEE Trans. Industr. Inform. 2013, 10, 666–675. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, Q.; Ji, S.; Bai, W. PVF-DA: Privacy-Preserving, Verifiable and Fault-Tolerant Data Aggregation in MEC. China Commun. 2020, 17, 58–69. [Google Scholar] [CrossRef]
- Guan, Z.; Si, G.; Zhang, X.; Wu, L.; Guizani, N.; Du, X.; Ma, Y. Privacy-Preserving and Efficient Aggregation Based on Blockchain for Power Grid Communications in Smart Communities. IEEE Commun. Mag. 2018, 56, 82–88. [Google Scholar] [CrossRef] [Green Version]
- Lu, R.; Heung, K.; Lashkari, A.H.; Ghorbani, A.A. A Lightweight Privacy-Preserving Data Aggregation Scheme for Fog Computing-Enhanced IoT. IEEE Access 2017, 5, 3302–3312. [Google Scholar] [CrossRef]
- Song, J.; Liu, Y.; Shao, J.; Tang, C. A Dynamic Membership Data Aggregation (DMDA) Protocol for Smart Grid. IEEE Syst. J. 2020, 14, 900–908. [Google Scholar] [CrossRef]
- Guan, Z.; Zhang, Y.; Wu, L.; Wu, J.; Li, J.; Ma, Y.; Hu, J. APPA: An Anonymous and Privacy Preserving Data Aggregation Scheme for Fog-Enhanced IoT. J. Netw. Comput. Appl. 2019, 125, 82–92. [Google Scholar] [CrossRef]
- Zhu, H.; Gao, L.; Li, H. Secure and Privacy-Preserving Body Sensor Data Collection and Query Scheme. Sensors 2019, 16, 179. [Google Scholar] [CrossRef]
- Qian, J.; Qiu, F.; Wu, F.; Ruan, N.; Chen, G.; Tang, S. Privacy-Preserving Selective Aggregation of Online User Behavior Data. IEEE Trans. Comput. 2017, 66, 326–338. [Google Scholar] [CrossRef]
- Mahdikhani, H.; Mahdavifar, S.; Lu, R.; Zhu, H.; Ghorbani, A.A. Achieving Privacy-Preserving Subset Aggregation in Fog-Enhanced IoT. IEEE Access 2019, 7, 184438–184447. [Google Scholar] [CrossRef]
- Manzano, L.G.; Fuentes, J.M.; Pastrana, S.; Lopez, P.P.; Encinas, L.H. PAgIoT-Privacy-Preserving Aggregation Protocol for Internet of Things. J. Netw. Comput. Appl. 2016, 71, 59–71. [Google Scholar] [CrossRef] [Green Version]
- Lu, R. A New Communication-Efficient Privacy-Preserving Range Query Scheme in Fog-Enhanced IoT. IEEE Internet Things J. 2019, 6, 2497–2505. [Google Scholar] [CrossRef]
- Mahdikhani, H.; Lu, R. Achieving Privacy-Preserving Multi Dot-Product Query in Fog Computing-Enhanced IoT. In Proceedings of the GLOBECOM 2017–2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; IEEE: New York, NY, USA, 2017. [Google Scholar]
- Datta, A.; Joye, M.; Fawaz, N. Private Data Aggregation over Selected Subsets of Users. In Proceedings of the 18th International Conference on Cryptology and Network Security, Fuzhou, China, 25–27 October 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 375–391. [Google Scholar]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
- Zhang, J.; Zhao, Y.; Wu, J.; Chen, B. LVPDA: A Lightweight and Verifiable Privacy-Preserving Data Aggregation Scheme for Edge-Enabled IoT. IEEE Internet Things J. 2020, 7, 4016–4027. [Google Scholar] [CrossRef]
- Wang, Z. An Identity-Based Data Aggregation Protocol for the Smart Grid. IEEE Trans. Industr. Inform. 2017, 13, 2428–2435. [Google Scholar] [CrossRef]
- Lyu, L.; Nandakumar, K.; Rubinstein, B.; Jin, J.; Bedo, J.; Palaniswami, M. PPFA: Privacy Preserving Fog-Enabled Aggregation in Smart Grid. IEEE Trans. Industr. Inform. 2018, 14, 3733–3744. [Google Scholar] [CrossRef]
- Bao, H.; Lu, R. A New Differentially Private Data Aggregation with Fault Tolerance for Smart Grid Communications. IEEE Internet Things J. 2015, 2, 248–258. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.; Wu, F.; Kumari, S.; Rodrigues, J.J.P.C. Privacy Preserving Data Aggregation Scheme for Mobile Edge Computing Assisted IoT Applications. IEEE Internet Things J. 2019, 6, 4755–4763. [Google Scholar] [CrossRef]
- Liu, Y.; Guo, W.; Fan, C.I.; Chang, L.; Cheng, C. A Practical Privacy-Preserving Data Aggregation (3PDA) Scheme for Smart Grid. IEEE Trans. Industr. Inform. 2019, 15, 1767–1774. [Google Scholar] [CrossRef]
- Zeng, P.; Pan, B.; Choo, K.R.; Liu, H. MMDA: Multidimensional and Multidirectional Data Aggregation for Edge Computing-Enhanced IoT. J. Syst. Archit. 2020, 106, 101713. [Google Scholar] [CrossRef]
- Shi, Z.; Sun, R.; Lu, R.; Chen, L.; Chen, J.; Shen, X.S. Diverse Grouping-Based Aggregation Protocol with Error Detection for Smart Grid Communications. IEEE Trans. Smart Grid. 2015, 6, 2856–2868. [Google Scholar] [CrossRef]
- Wang, H.; Wang, Z.; Domingo, F.J. Anonymous and Secure Aggregation Scheme in Fog-Based Public Cloud Computing. Future Gener. Comput. Syst. 2018, 78, 712–719. [Google Scholar] [CrossRef]
- Shen, X.; Zhu, L.; Xu, C.; Sharif, K.; Lu, R. A Privacy-Preserving Data Aggregation Scheme for Dynamic Groups in Fog Computing. Inf. Sci. 2020, 514, 118–130. [Google Scholar] [CrossRef]
- Liu, D.; Zheng, Y.; Ding, W.; Atiquzzaman, M. A Survey on Secure Data Analytics in Edge Computing. IEEE Internet Things J. 2019, 6, 4946–4967. [Google Scholar] [CrossRef] [Green Version]
- Grining, K.; Klonowski, M.; Syga, P. On Practical Privacy-Preserving Fault-Tolerant Data Aggregation. Int. J. Inf. Secur. 2019, 8, 285–304. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, Z.; Guo, F. Online/Offline Verification of Short Signatures. In Proceedings of the Information Security and Cryptology, Inscrypt 2010, Shanghai, China, 20–24 October 2010; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).