Channel Allocation for Connected Vehicles in Internet of Things Services
Abstract
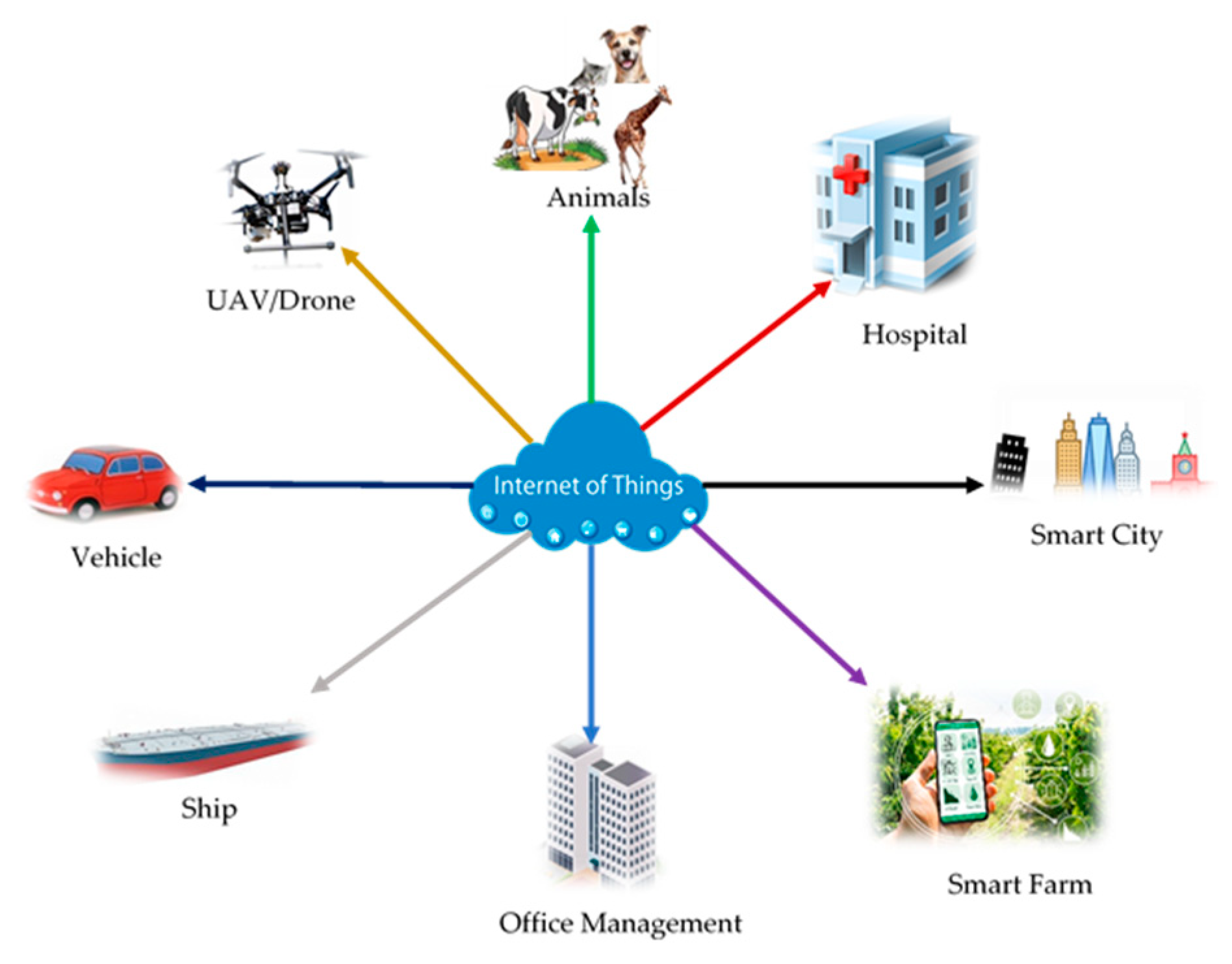
1. Introduction
- This work proposes an ideal access mechanism that considers the optimum target functionality of all traffic.
- This work presents two algorithms with distributed MAC for channel allocation.
- This model maximizes the throughput and reduces the overhead successfully compared with the existed model.
- The proposed model considered varied environments such as city, highway, and rural areas.
2. Literature Review
3. Distributed Medium for Channel Allocation
- Un-Shared Channel
| Algorithm 1 Unshared Channel |
| Step 1. Input set of accessible channel & for vehicles Step 2. For Step 3. . Step 4. If () then Step 5. Obtain , where and are the throughputs before and after channel allocation . Step 6. Else Step 7. Obtain . Step 8. End If Step 9. End For Step 10. . Step 11. Allocate channel to vehicle . Step 12. Update . Step 13. If is empty, terminate the process. Step 14. Else, go to step 2. |
- Shared Channel
| Algorithm 2 Shared Channel |
| Step 1. Input set of assigned channels vehicles for and Step 2. Execute Algorithm 1 to get channel allocated for a single vehicle. Step 3. Let the set of channels that are shared by vehicles be and be the group of vehicles which share channel and set . Step 4. ; ; . Step 5. While do Step 6. Obtain the set of channels shared by vehicles Step 7. For Step 8. For Step 9. If then Step 10. . Step 11. Else Step 12. User computes considering that channel is assigned to vehicle . Step 13. End If Step 14. End For Step 15. . Step 16. End For Step 17. . Step 18. If and then Step 19. Set . Step 20. Go to step 35. Step 21. End If Step 22. If then Step 23. Provisionally allocate channel to vehicle , i.e., update . Step 24. Compute and . Step 25. If then Step 26. . Step 27. Return to Step 7 using the updated . Step 28. Else Step 29. Update (i.e., allocate channel to vehicle ), compute & with , & update . Step 30. Update . Step 31. End If. Step 32. End If. Step 33. Return to step 7. Step 34. . Step 35. End While |
- Contention window computation
4. Results
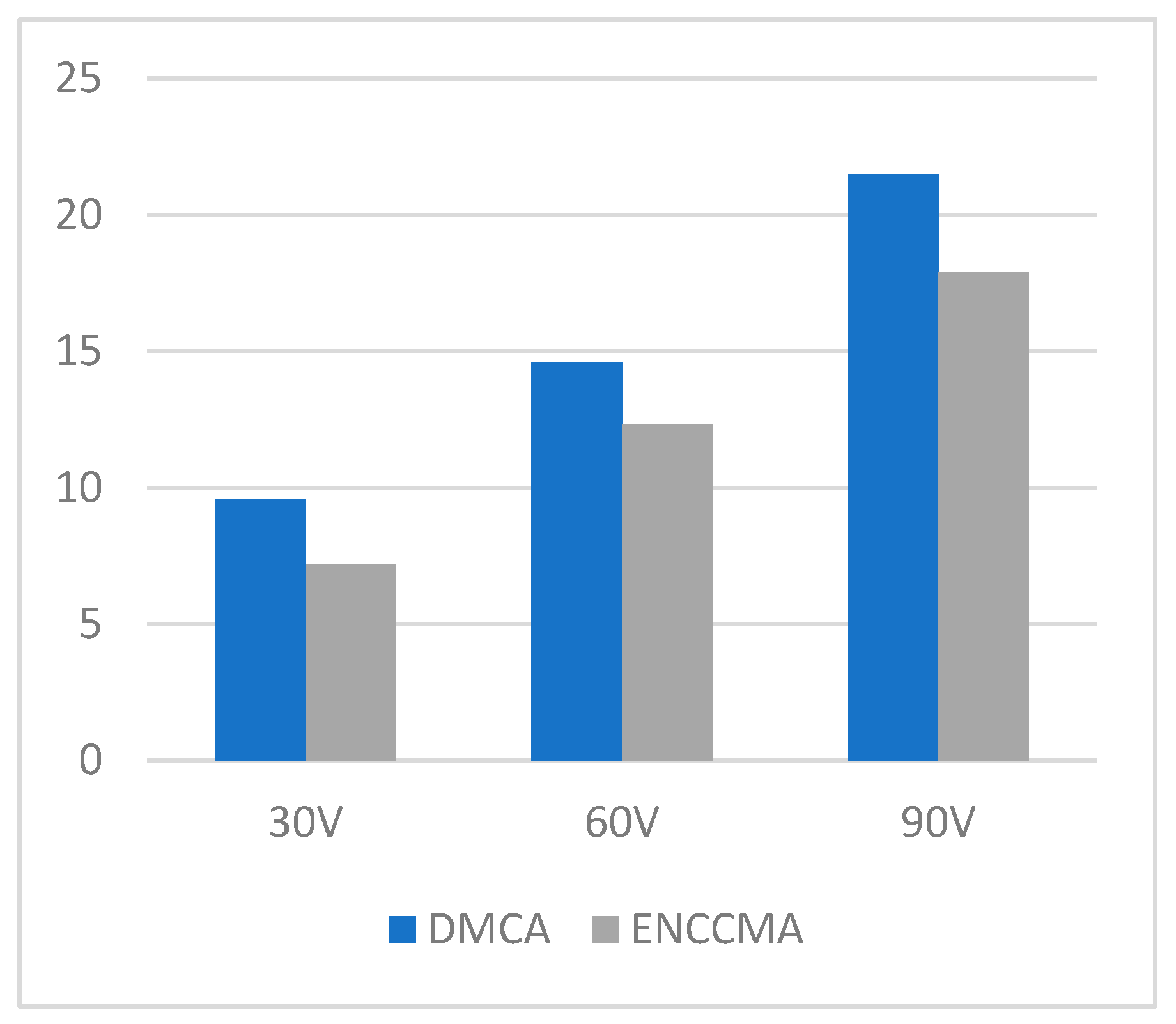
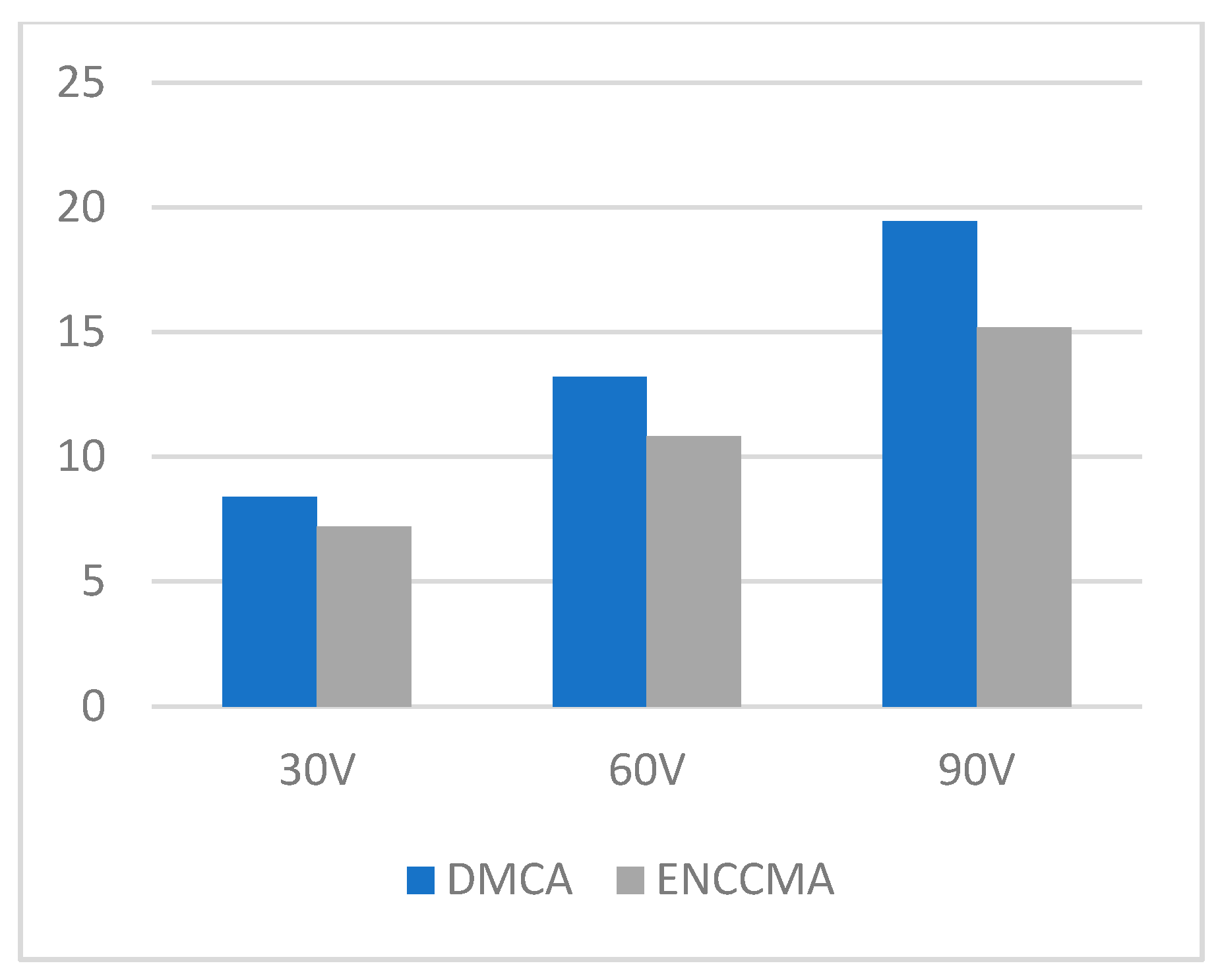
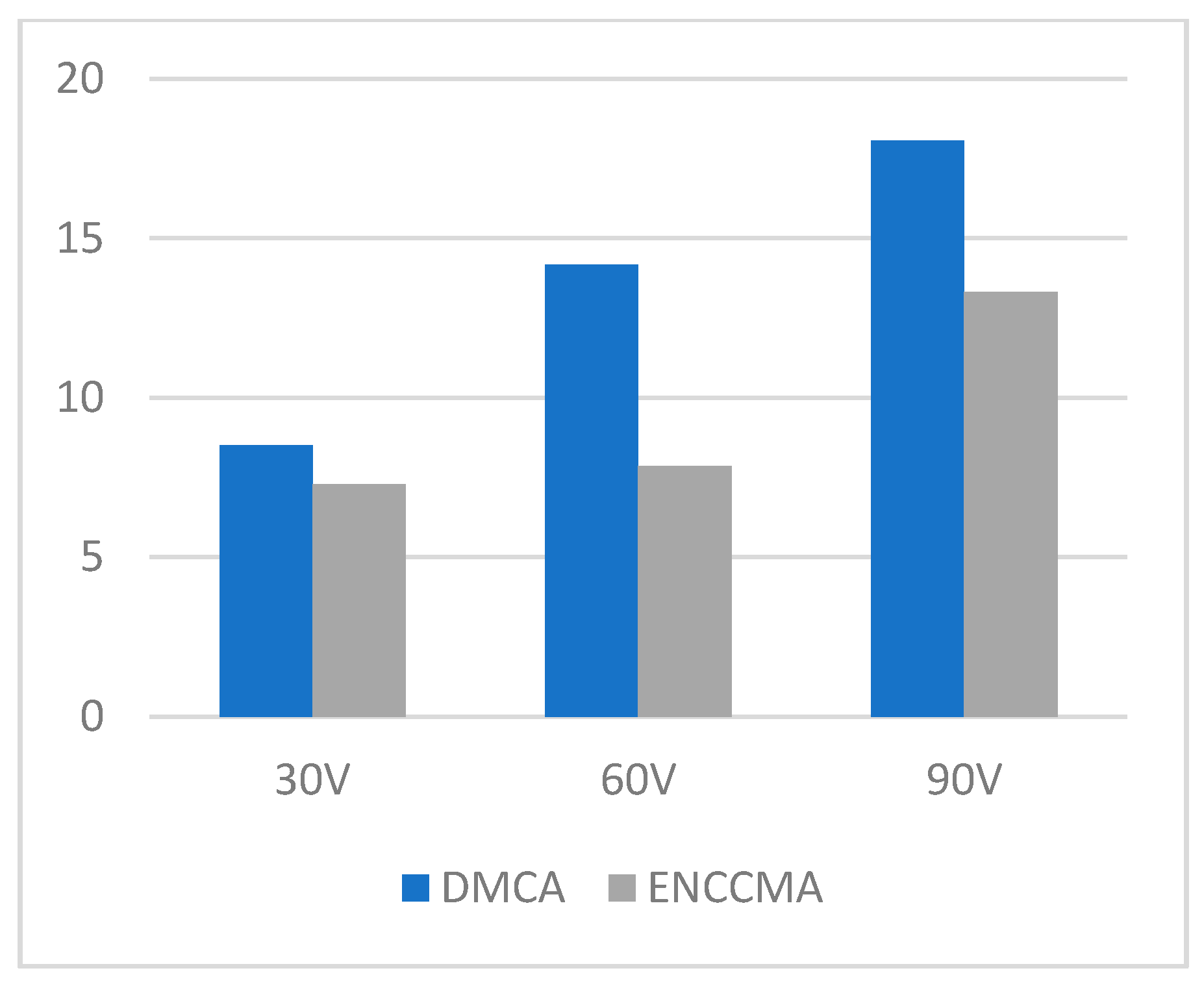
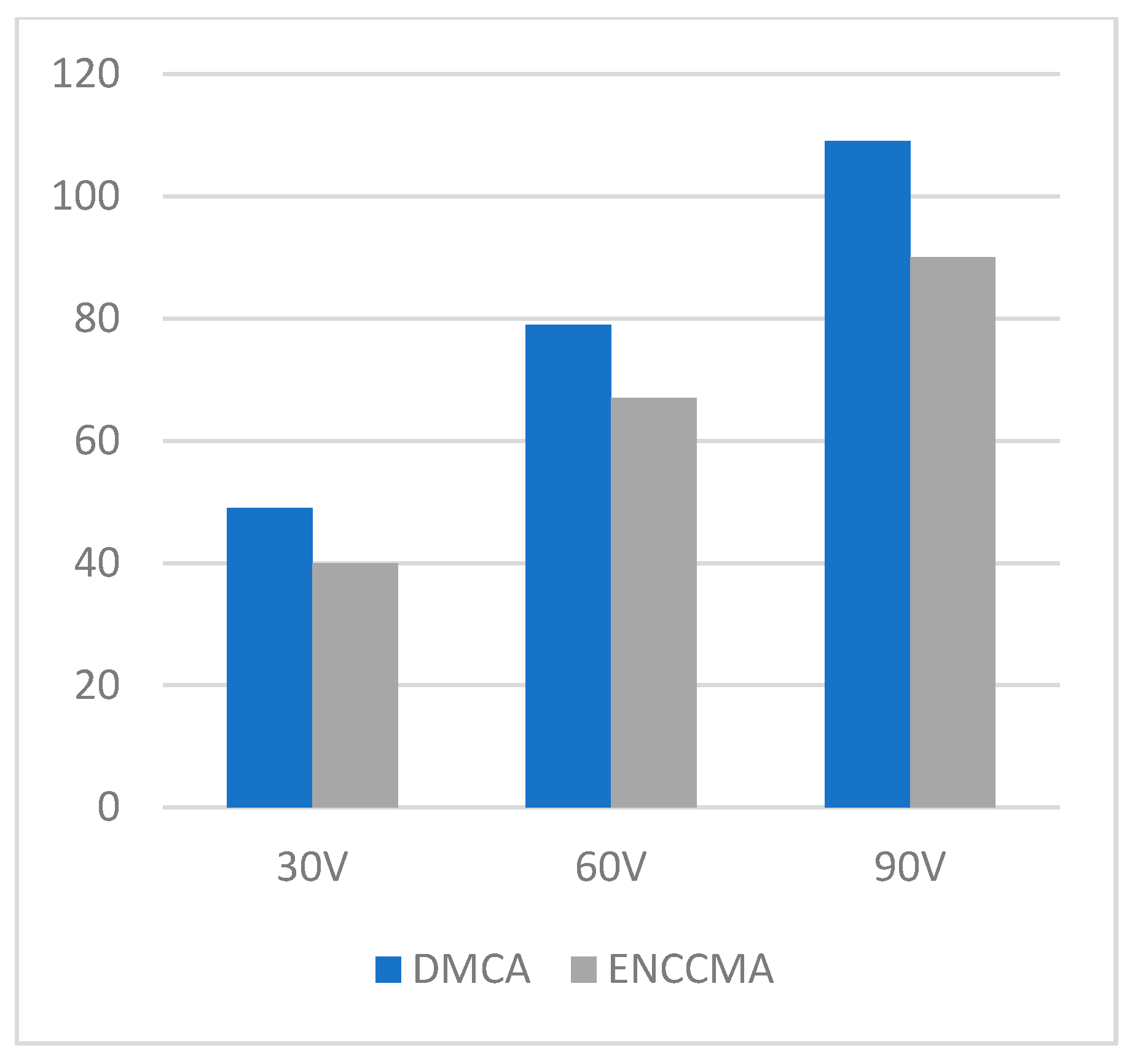
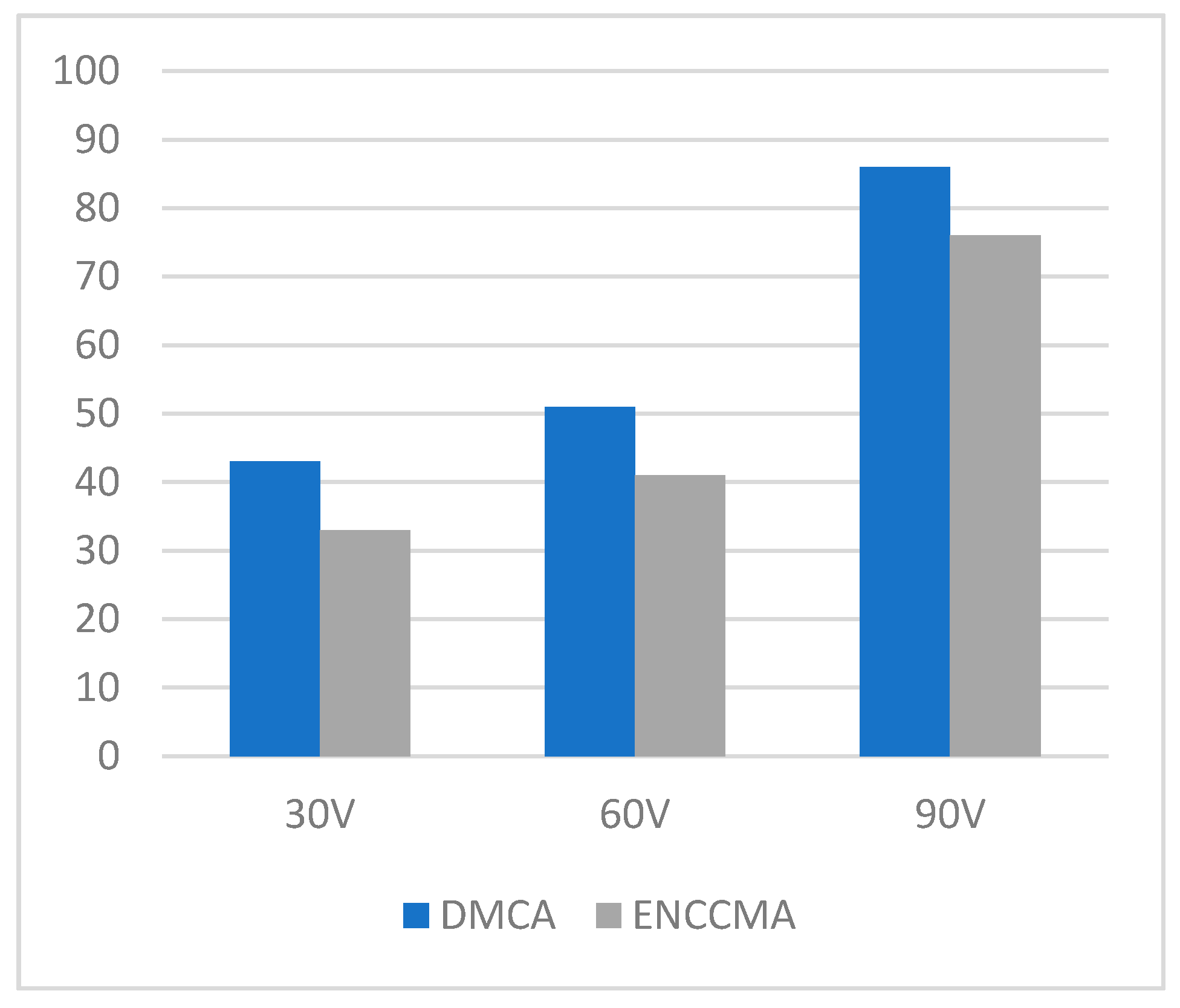
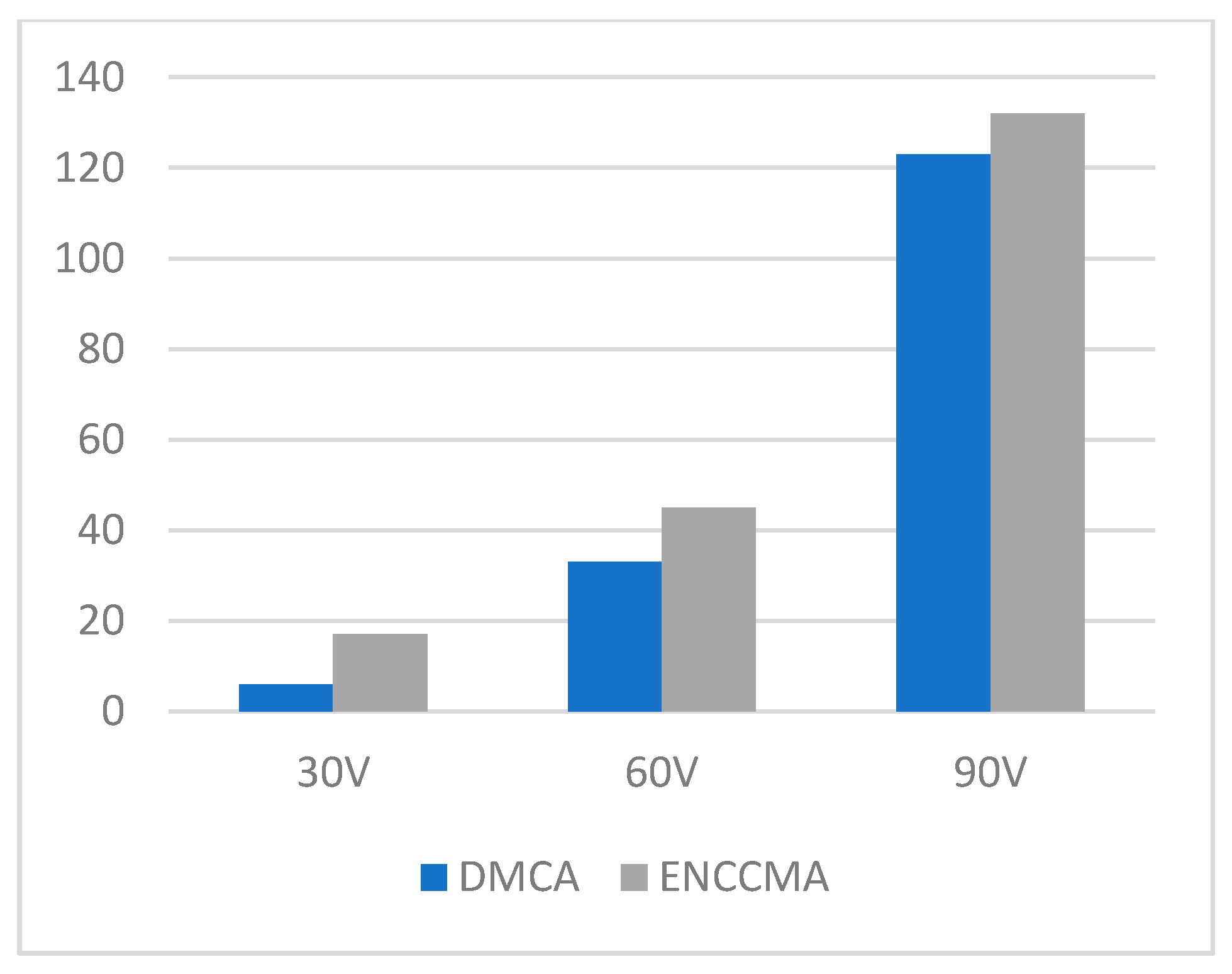
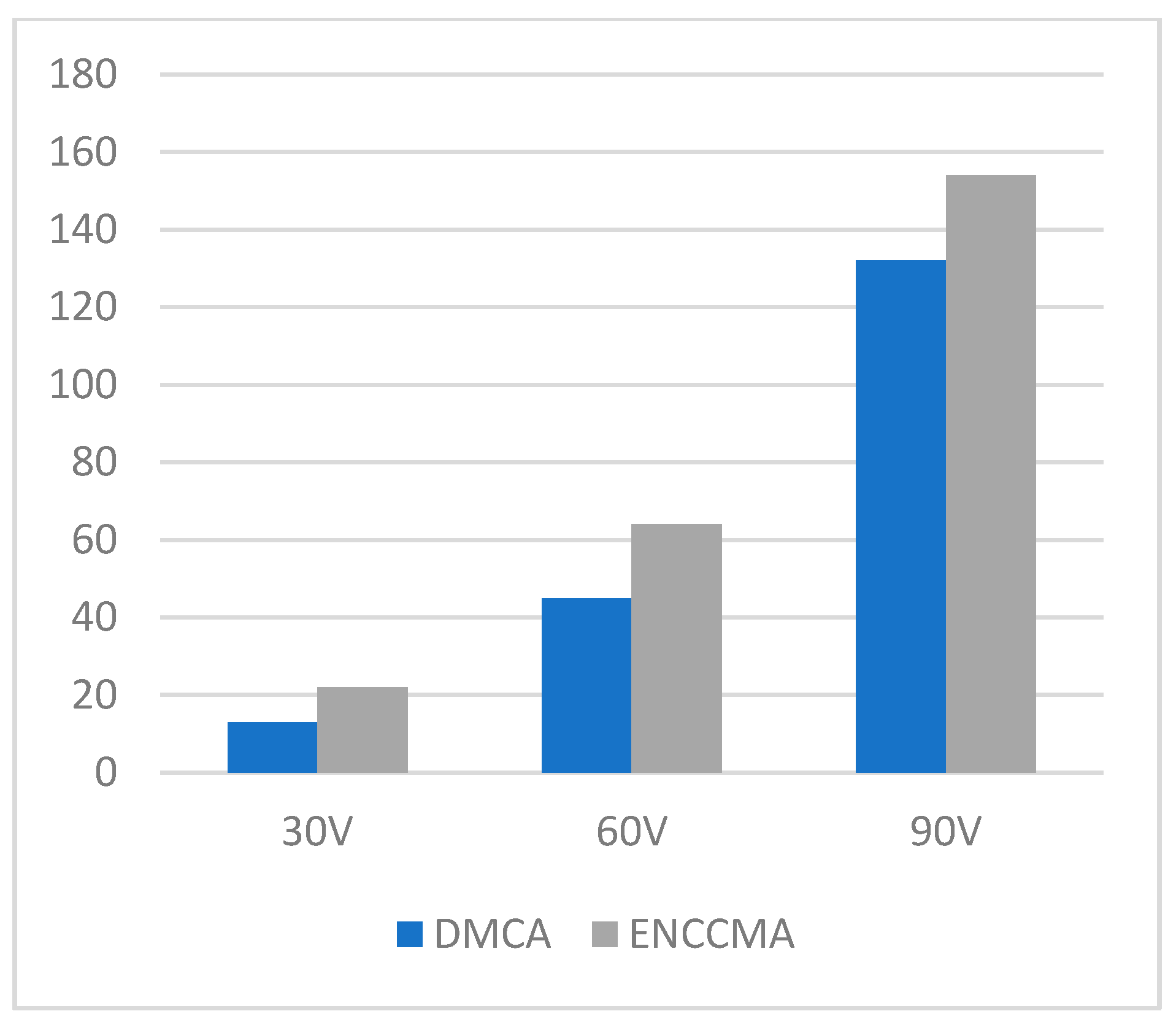
4.1. Throughput, Data Transmission, and Collision Performance of the DMCA Model
4.2. State of the Art Technology Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kostrzewski, M.; Varjan, P.; Gnap, J. Solutions Dedicated to Internal Logistics 4.0. In The Energy Consumption in Refrigerated Warehouses; J.B. Metzler: Stuttgart, Germany, 2019; pp. 243–262. [Google Scholar]
- Manyika, J.; Chui, M. By 2025, Internet of Things Applications Could have $11 Trillion Impact; McKinsey Global Institute: San Francisco, CA, USA, 2015. [Google Scholar]
- Shen, S.; Wei, Z.-Q.; Sun, L.-J.; Su, Y.-Q.; Wang, R.-C.; Jiang, H.-M. The Shared Bicycle and Its Network—Internet of Shared Bicycle (IoSB): A Review and Survey. Sensors 2018, 18, 2581. [Google Scholar] [CrossRef] [PubMed]
- Rodrigues, M.J.; Postolache, O.; Cercas, F. Physiological and Behavior Monitoring Systems for Smart Healthcare Environments: A Review. Sensors 2020, 20, 2186. [Google Scholar] [CrossRef]
- Urban Infrastructure: Keeping Economies and People Healthy. Available online: https://theonebrief.com/urban-infrastructure-keeping-economies-and-people-healthy/ (accessed on 15 February 2021).
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and Security: Challenges and Solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.-S. IoT Elements, Layered Architectures and Security Issues: A Comprehensive Survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [PubMed]
- Masood, A.; Lakew, D.S.; Cho, S. Security and Privacy Challenges in Connected Vehicular Cloud Computing. IEEE Commun. Surv. Tutor. 2020, 22, 2725–2764. [Google Scholar] [CrossRef]
- Chen, X.; Xu, B.; Qin, X.; Bian, Y.; Hu, M.; Sun, N. Non-Signalized Intersection Network Management With Connected and Automated Vehicles. IEEE Access 2020, 8, 122065–122077. [Google Scholar] [CrossRef]
- Nimalsiri, N.I.; Mediwaththe, C.P.; Ratnam, E.L.; Shaw, M.; Smith, D.B.; Halgamuge, S.K. A Survey of Algorithms for Distributed Charging Control of Electric Vehicles in Smart Grid. IEEE Trans. Intell. Transp. Syst. 2020, 21, 4497–4515. [Google Scholar] [CrossRef]
- Chatzikomis, C.; Sorniotti, A.; Gruber, P.; Zanchetta, M.; Willans, D.; Balcombe, B. Comparison of Path Tracking and Torque-Vectoring Controllers for Autonomous Electric Vehicles. IEEE Trans. Intell. Veh. 2018, 3, 559–570. [Google Scholar] [CrossRef]
- Thunberg, J.; Lyamin, N.; Sjoberg, K.; Vinel, A. Vehicle-to-Vehicle Communications for Platooning: Safety Analysis. IEEE Netw. Lett. 2019, 1, 168–172. [Google Scholar] [CrossRef]
- Bisoy, S.K.; Pattnaik, P.K.; Sain, M.; Jeong, D.-U. A Self-Tuning Congestion Tracking Control for TCP/AQM Network for Single and Multiple Bottleneck Topology. IEEE Access 2021, 9, 27723–27735. [Google Scholar] [CrossRef]
- Bilstrup, K.; Uhlemann, E.; Storm, E.G. Medium access control in vehicular networks based-on the upcoming IEEE 802.11p standard. In Proceedings of the 15th World Congress on Intelligent Transport Systems (ITS’08), New York, NY, USA, 20 November 2008; pp. 1–12. [Google Scholar]
- Seijo, O.; Lopez-Fernandez, J.A.; Bernhard, H.-P.; Val, I. Enhanced Timestamping Method for Subnanosecond Time Synchronization in IEEE 802.11 Over WLAN Standard Conditions. IEEE Trans. Ind. Inform. 2020, 16, 5792–5805. [Google Scholar] [CrossRef]
- Khairnar, V.D.; Kotecha, K. Performance of Vehicle-to-Vehicle Communication using IEEE 802.11p in Vehicular Ad-hoc Network Environment. Int. J. Netw. Secur. Its Appl. 2013, 5, 143–170. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef] [PubMed]
- Bilstrup, K. A Survey Regarding Wireless Communication Standards Intended Fora High-Speed Vehicle Environment; Technical Report IDE 0712; Halmstad University: Halmstad, Sweden, 2007. [Google Scholar]
- Stibor, L.; Zang, Y.; Reumerman, H.-J. Evaluation of communicationdistance of broadcast messages in a vehicular ad-hoc network using IEEE 802.11p. In Proceedings of the IEEE Wireless Communications Networking Conference, Hong Kong, China, 11–15 March 2007; pp. 254–257. [Google Scholar]
- Wellen, M.; Westphal, B.; Mahonen, P. Performance evaluation of IEEE 802.11based WLANs in vehicular scenarios. In Proceedings of the IEEE Vehicular Technology, Dublin, Ireland, 22–25 April 2007; pp. 1167–1171. [Google Scholar]
- Xiang, W.; Richardson, P.; Guo, J. Introduction andpreliminary experimental results of wireless access for vehicular environments (WAVE) systems. In Proceedings of the International Confrance Mobile and Ubiquitous Systems: Network and Services, San Jose, CA, USA, 22–24 July 2007; pp. 1–8. [Google Scholar]
- Qureshi, K.N.; Islam, F.U.; Kaiwartya, O.; Kumar, A.; Lloret, J. Improved Road Segment-Based Geographical Routing Protocol for Vehicular Ad-hoc Networks. Electronics 2020, 9, 1248. [Google Scholar] [CrossRef]
- Al-Absi, M.A.; Al-Absi, A.A.; Lee, H.J. Varied density of vehicles under city, highway, rural environments in V2V communication. Int. J. Sens. Netw. 2020, 33, 148–158. [Google Scholar] [CrossRef]
- Mohammed, A.A.; Ahmed, A.A.; R’bigui, H.; Lee, H.J. A Novel Throughput andCollision for City Environment in V2V Communication. In Proceedings of the 10th IEEE International Conf ICTC Convergence, Jeju Island, Korea, 16–18 October 2019; pp. 1413–1415. [Google Scholar]
- Al-Absi, M.A.; Al-Absi, A.A.; Sain, M.; Lee, H.J. A State of the Art: Future Possibility of 5G with IoT and Other Challenges. In Smart Healthcare Analytics in IoT Enabled Environment; Pattnaik, P., Mohanty, S., Mohanty, S., Eds.; Springer: Cham, Switzerland, 2020; Volume 178, pp. 35–65. [Google Scholar] [CrossRef]
- Bilstrup, K.; Uhlemann, E.; Strom, E.G.; Bilstrup, U. On the ability of the 802.11p MAC method and STDMA to support realtime vehicle-to-vehicle communication. EURASIP J. Wirel. Commun. Netw. 2009, 2009, 902414. [Google Scholar]
- Bilstrup, K.; Uhlemann, E.; Strom, E.G.; Bilstrup, U. Evaluation of the IEEE 802.11p MAC method for vehicleto-vehicle communication. In Proceedings of the IEEE 68th Vehicular Technology Conference (VTC ’08), Calgary, AB, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Sjoberg-Bilstrup, K.; Uhlemann, E.; Strom, E.G. Scalability issues of the MAC methods STDMA and CSMA of IEEE 802.11p when used in VANETs. In Proceedings of the IEEE International Conference on Communications Workshops (ICC ’10), Capetown, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar]
- Gomez, A.A.; Mecklenbrauker, C.F. Dependability of Decentralized Congestion Control for Varying VANET Density. IEEE Trans. Veh. Technol. 2016, 65, 9153–9167. [Google Scholar] [CrossRef]
- Paier, A.; Karedal, J.; Czink, N.; Hofstetter, H.; Dumard, C.; Zemen, T.; Tufvesson, F.; Molisch, A.F.; Mecklenbrauker, C.F. Car-to-car radio channel measurements at 5 GHz: Pathloss, power-delay profile, and delay-Doppler spectrum. In Proceedings of the 2007 4th International Symposium on Wireless Communication Systems, Trondheim, Norway, 16–19 October 2007; pp. 224–228. [Google Scholar]
- Research and Innovative Technology Administration (Intelligent Transportation Systems). 2020. Available online: https://www.its.dot.gov/ (accessed on 10 December 2020).
- Liu, L.; Xia, W.; Shen, L. An adaptive multi-channelMAC Protocol with Dynamic interval division in vehicular environment. In Proceedings of the 2009 First International Conference on Information Science and Engineering, Nanjing, China, 26–28 December 2009; pp. 2534–2537. [Google Scholar]
- Cao, H.; Cai, J. Distributed opportunistic spectrum access in anunknown and dynamic environment: A stochastic learning approach. IEEE Trans. Veh. Technol. 2018, 67, 4454–4465. [Google Scholar] [CrossRef]
- Li, R.; Zhu, P. Spectrum Allocation Strategies Basedon QoS in Cognitive Vehicle Networks. IEEE Access 2020, 8, 99922–99933. [Google Scholar] [CrossRef]
- Sarker, A.; Qiu, C.; Shen, H. Connectivity Maintenance for Next-Generation Decentralized Vehicle Platoon Networks. IEEE/ACM Trans. Netw. 2020, 28, 1449–1462. [Google Scholar] [CrossRef]
- Abbas, F.; Fan, P.; Khan, Z. A Novel Low-Latency V2V Resource Allocation Scheme Based on Cellular V2X Communications. IEEE Trans. Intell. Transp. Syst. 2019, 20, 2185–2197. [Google Scholar] [CrossRef]
- You, H.; Ekici, E.; Kremo, H.; Altintas, O. Throughput-Efficient ChannelAllocation Algorithms in Multi-Channel Cognitive Vehicular Networks. IEEE Trans. Wirel. Commun. 2017, 16, 757–770. [Google Scholar]
- Hossain, E.; Rasti, M.; Tabassum, H.; Abdelnasser, A. Evolution toward 5G multi-tier cellular wireless networks: An interference management perspective. IEEE Wirel. Commun. 2014, 21, 118–127. [Google Scholar] [CrossRef]
- Zeng, F.; Zhang, R.; Cheng, X.; Yang, L. Channel prediction based scheduling fordata dissemination in VANETs. IEEE Commun. Lett. 2017, 21, 1409–1412. [Google Scholar] [CrossRef]
- Abboud, K.; Zhuang, W. Stochastic analysis of a single-hop communication link invehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2014, 5, 2297–2307. [Google Scholar] [CrossRef]
- Al-Absi, M.A.; Kamolov, A.; Al-Absi, A.A.; Sain, M.; Lee, H.J. IoT Technology with Marine Environment Protection and Monitoring. In Proceedings of the International Conference on Smart Computing and Cyber Security; Pattnaik, P.K., Sain, M., Al-Absi, A.A., Kumar, P., Eds.; Springer: Singapore, 2021; pp. 81–89. [Google Scholar] [CrossRef]
- Zhang, Y.; Ye, M.; Guan, L. QoS-aware Link Scheduling Strategy for Data Transmission in SDVN. arXiv 2021, arXiv:2102.00953. [Google Scholar]
- Sehrawat, S.; Bora, R.P.; Harihar, D. Performance analysis of QoS supported by Enhanced Distributed Channel Access (EDCA) mechanism in IEEE 802.11e. IAENG Int. J. Comput. Sci. 2007, 33, 943–948. [Google Scholar]
- Manzano, M.; Bravo-Santos, Á.M.; Santiso, E.; Espinosa, F.; Bravo, I.; Garcia, D. Dynamic Cognitive Self-Organized TDMA for Medium Access Control in Real-Time Vehicle to Vehicle Communications. Math. Probl. Eng. 2013, 2013, 1–13. [Google Scholar] [CrossRef]
- Ma, X.; Yin, X.; Wilson, M.; Trivedi, K.S. MAC and application-level broadcast reliability in vanets with channel fading. In Proceedings of the 2013 International Conference on Computing, Networking and Communications (ICNC), San Diego, CA, USA, 28–31 January 2013; pp. 756–761. [Google Scholar]
- Soltani, M.D.; Alimadadi, M.; Seyedi, Y.; Amindavar, H. Modeling of Doppler spectrum in V2V urban canyon oncoming environment. In Proceedings of the 7’th International Symposium on Telecommunications (IST’2014), Tehran, Iran, 9–11 September 2014; pp. 1155–1160. [Google Scholar]
- Drigo, M.; Zhang, W.; Baldessari, R.; Le, L.; Festag, A.; Zorzi, M. Distributed rate control algorithm for VANETs (DRCV). In Proceedings of the Sixth ACM International Workshop on Underwater Networks—WUWNet ’11, Berkeley, CA, USA, 3 November 2009; pp. 119–120. [Google Scholar] [CrossRef]
- Mitola, J.; Maguire, G. Cognitive radio: Making software radios more personal. IEEE Wirel. Commun. 1999, 6, 13–18. [Google Scholar] [CrossRef]
- Di Felice, M.; Chowdhury, K.R.; Bononi, L. Analyzing the potential of cooperative Cognitive Radio technology on inter-vehicle communication. 2010 IFIP Wirel. Days 2010, 1–6. [Google Scholar] [CrossRef]
- Chung, S.-E.; Yoo, J.; Kim, C.-K. A cognitive MAC for VANET based on the WAVE systems. In Proceedings of the 11th International Conference on (ICACT ’09), Dublin, Ireland, 1 February 2009; pp. 41–46. [Google Scholar]
- Gräfling, S.; Mähönen, P.; Riihijärvi, J. Performance evaluation of IEEE 1609 WAVE and IEEE 802.11p for vehicular communications. In Proceedings of the 2010 Second International Conference on Ubiquitous and Future Networks (ICUFN), Jeju, Korea, 16–18 June 2010; pp. 344–348. [Google Scholar]
- Krishna, P.V.; Misra, S.; Obaidat, M.S.; Saritha, V. Virtual Backoff Algorithm: An Enhancement to 802.11 Medium-Access Control to Improve the Performance of Wireless Networks. IEEE Trans. Veh. Technol. 2010, 59, 1068–1075. [Google Scholar] [CrossRef]
- Roberts, L.G. ALOHA packet system with and without slots and capture. ACM SIGCOMM Comput. Commun. Rev. 1975, 5, 28–42. [Google Scholar] [CrossRef]
- Hossain, E.; Niyato, D.; Han, Z. Dynamic Spectrum Access and Management in Cognitive Radio Networks; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar]
- Yuan, Y.; Bahl, P.; Chandra, R.; Moscibroda, T.; Wu, Y. Allocating dynamic time-spectrum blocks in cognitive radio networks. In Proceedings of the 8th ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc ’07), Montreal, QC, Canada, 9–14 September 2007; pp. 130–139. [Google Scholar]
- Parsapoor, M.; Bilstrup, U. Imperialist competitive algorithm for DSA in cognitive radio networks. In Proceedings of the 8th International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM ’12), Shanghai, China, 21–23 September 2012; pp. 1–4. [Google Scholar]
- Manzano, M.; Espinosa, F.; Bravo-Santos, Á.M.; Gardel-Vicente, A. Cognitive Self-Scheduled Mechanism forAccess Control in Noisy Vehicular Ad Hoc Networks. Mathemarical Probl. Eng. 2015, 2015, 354292. [Google Scholar]
- Lee, J.; Al-Absi, M.A.; Al-Absi, A.A. Performance Enriching Channel Allocation Algorithm for Vehicle-to-Vehicle City, Highway and Rural Network. Sensors 2019, 19, 3283. [Google Scholar] [CrossRef]
- Al-Absi, M.A.; Lee, H.J.; Al-Absi, A.A. A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication. Sensors 2020, 20, 1000. [Google Scholar] [CrossRef] [PubMed]
- Mohammed, A.A.; Ahmed, A.A.; Kim, T.; Lee, H.J. An Environmental Channel Throughput and Radio Propagation Modeling for Vehicle-to-Vehicle Communication. Int. J. Distrib. Sens. Netw. 2018, 14, 1–10. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Lee, H.J. V2V communication modeling for environmental channel throughput and radio propagation. In Proceedings of the 8th IEEE International Conference on ICTC Convergence, Jeju Island, Korea, 18–20 October 2017; pp. 507–512. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Kang, Y.J.; Lee, H.J. Obstacles Effects on Signal Attenuation in Line of Sight for Different Environments in V2V. In Proceedings of the 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon-si, Korea, 11–14 February 2018; pp. 17–20. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Lee, H.J. Performance Analysis for City, Highway and Rural Area in Vehicle-to-Vehicle Network. In Proceedings of the 8th IEEE International Conference on ICTC Convergence, Jeju Island, Korea, 18–20 October 2017. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Lee, H.J. Comparison between DSRC and other Short-Range Wireless Communication Technologies. In Proceedings of the 2020 22nd International Conference on Advanced Communication Technology (ICACT) Phoenix Park, PyeongChang, Korea, 16–19 February 2020; pp. 1–5. [Google Scholar]
- Bilgin, B.E.; Gungor, V.C. Performance Comparison of IEEE 802.11p and IEEE 802.11b for Vehicle-to-Vehicle Communications in Highway, Rural, and Urban Areas. Int. J. Veh. Technol. 2013, 2013, 1–10. [Google Scholar] [CrossRef]
- Bazzi, A.; Zanella, A.; Masini, B.M. An OFDMA-Based MAC Protocol for Next-Generation VANETs. IEEE Trans. Veh. Technol. 2015, 64, 4088–4100. [Google Scholar] [CrossRef]
- Ferreira, N.F.G.C.; Fonseca, J.A.G. Improving safety message delivery through RSU’s coordination in vehicular networks. In Proceedings of theFactory Communication Systems (WFCS), Palma de Mallorca, Spain, 27–29 May 2015; pp. 1–8. [Google Scholar]
- Chang, C.-Y.; Yen, H.-C.; Deng, D.-J. V2V QoS Guaranteed Channel Access in IEEE 802.11p VANETs. Veh. Technol. IEEE Trans. 2015, 13, 5–17. [Google Scholar] [CrossRef]
- Meng, Y.; Dong, Y.; Liu, X.; Zhao, Y. An Interference-Aware Resource Allocation Scheme for Connectivity Improvement in Vehicular Networks. IEEE Access 2018, 6, 51319–51328. [Google Scholar] [CrossRef]
- Zhang, R.; Cheng, X.; Yao, Q.; Wang, C.-X.; Yang, Y.; Jiao, B. Interference Graph-Based Resource-Sharing Schemes for Vehicular Networks. IEEE Trans. Veh. Technol. 2013, 62, 4028–4039. [Google Scholar] [CrossRef]
- Lin, F.; Zhou, Y.; Pau, G.; Collotta, M. Optimization-Oriented Resource Allocation Management for Vehicular Fog Computing. IEEE Access 2018, 6, 69294–69303. [Google Scholar] [CrossRef]
- Sun, W.; Strom, E.G.; Brannstrom, F.; Sou, K.C.; Sui, Y. Radio Resource Management for D2D-Based V2V Communication. IEEE Trans. Veh. Technol. 2015, 65, 6636–6650. [Google Scholar] [CrossRef]
- Wang, R.; Wu, J.; Yan, J. Resource Allocation for D2D-Enabled Communications in Vehicle Platooning. IEEE Access 2018, 6, 50526–50537. [Google Scholar] [CrossRef]
- Liang, L.; Li, G.Y.; Xu, W. Resource Allocation for D2D-Enabled Vehicular Communications. IEEE Trans. Commun. 2017, 65, 3186–3197. [Google Scholar] [CrossRef]
- Sahin, T.; Boban, M. Radio Resource Allocation for Reliable Out-of-Coverage V2V Communications. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018; pp. 1–5. [Google Scholar]
- Zhang, S.; Hou, Y.; Xu, X.; Tao, X. Resource allocation in D2D-based V2V communication for maximizing the number of concurrent transmissions. In Proceedings of the 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–7 September 2016; pp. 1–6. [Google Scholar]
- Guo, C.; Liang, L.; Li, G.Y. Resource Allocation for Low-Latency Vehicular Communications: An Effective Capacity Perspective. IEEE J. Sel. Areas Commun. 2019, 37, 905–917. [Google Scholar] [CrossRef]
- Lin, C.-C.; Deng, D.-J.; Yao, C.-C. Resource Allocation in Vehicular Cloud Computing Systems With Heterogeneous Vehicles and Roadside Units. IEEE Internet Things J. 2017, 5, 3692–3700. [Google Scholar] [CrossRef]
- Noor-A-Rahim, M.; Ali, G.M.N.; Guan, Y.L.; Ayalew, B.; Chong, P.H.J.; Pesch, D. Dirk, Broadcast performance analysis and improvements of the LTE-V2V autonomous mode at road intersection. IEEE Trans. Veh. Technol. 2019, 68, 1. [Google Scholar] [CrossRef]
- Yang, W.; Zhang, R.; Chen, C.; Cheng, X. Secrecy-Based Resource Allocation for Vehicular Communication Networks with Outdated CSI. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–5. [Google Scholar]
- Ahmed, K.J.; Lee, M.J. Secure Resource Allocation for LTE-Based V2X Service. IEEE Trans. Veh. Technol. 2018, 67, 11324–11331. [Google Scholar] [CrossRef]
- Meng, Y.; Dong, Y.; Wu, C.; Liu, X. A Low-Cost Resource Re-Allocation Scheme for Increasing the Number of Guaranteed Services in Resource-Limited Vehicular Networks. Sensors 2018, 18, 3846. [Google Scholar] [CrossRef]
- Hung, S.-C.; Zhang, X.; Festag, A.; Chen, K.-C.; Fettweis, G. An Efficient Radio Resource Re-Allocation Scheme for Delay Guaranteed Vehicle-to-Vehicle Network. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–6. [Google Scholar]
- González, A.; Franchi, N.; Fettweis, G. A feasibility study of LTE-V2X semi-persistent scheduling for string stable CACC. In Proceedings of the IEEE Wireless Communications and Networking Conference, Marrakesh, Morocco, 15–19 April 2019. [Google Scholar]
- Scheuvens, L.; Hobler, T.; Barreto, A.N.; Fettweis, G.P. Wireless Control Communications Co-Design via Application-Adaptive Resource Management. In Proceedings of the 2019 IEEE 2nd 5G World Forum (5GWF), Dresden, Germany, 30 September–2 October 2019; pp. 298–303. [Google Scholar]
- Peng, H.; Li, D.; Ye, Q.; Abboud, K.; Zhao, H.; Zhuang, W.; Shen, X. Resource Allocation for Cellular-based Inter-Vehicle Communications in Autonomous Multiplatoons. IEEE Trans. Veh. Technol. 2017, 66, 11249–11263. [Google Scholar] [CrossRef]



| Notation | Meaning |
|---|---|
| Vehicle | |
| Throughput Achieved | |
| Channel | |
| accessibility | |
| accessibility for atmost one channel | |
| is not accessible | |
| Throughput increment | |
| Input set of accessible channels | |
| Throughput before channel allocation . | |
| . | |
| channel allocation | |
| MAC Overhead | |
| Number of vehicles | |
| Vehicle | |
| vehicle | |
| contention window | |
| User minimum pay cost from time to time | |
| Reduction function of | |
| total number of channels in the network | |
| time slot | |
| Roadside unit | |
| Roadside unit after | |
| Data packet |
| Parameters | Network | MAC | Modulation Scheme | Mobility | Bandwidth | Frequency Channels | Vehicles | Time Slots | Environment |
|---|---|---|---|---|---|---|---|---|---|
| Value | 10 km × 10 km | ENCCMA & DMCA | 64-QAM | 20 Per Frame | 27 Mbps | 7 | 30, 60 & 90 | 8 μs | Rural, city & highway |
| Environment | City | Highway | Rural |
|---|---|---|---|
| Path loss | 1.61 | 1.85 | 1.79 |
| Shadowing deviation | 3.4 | 3.2 | 3.3 |
| DMCA (Ours) | ENCCMA | MS-ALOHA | SLOP | EDF-CSMA | |
|---|---|---|---|---|---|
| Environment | C.H.R | flowing vehicles freely | highway and urban | driver intelligent | NA |
| Algorithm | DMCA | (NCC-FDMA-TDMA) | MS-ALOHA | Wave-Slotted aloha | EDF-CSMA |
| Vehicle varied Density | Yes | No | No | No | No |
| Simulator used | SIMITS | SIMITS | VISSIM | YES (NA) | NS-3 |
| MAC USED | 802.11p MAC | 802.11p MAC | 802.11p MAC | 802.11p MAC | 802.11p MAC |
| Mobility | Yes | Yes | Yes | Yes | Yes |
| Channel sharing available | Yes | Yes | No | No | No |
| Reference | (Ours) | [57] | [66] | [67] | [68] |
| Use Case | Objectives | Method | RSU/BS Assisted | Parameters | Scenario | Mobility | Reference |
|---|---|---|---|---|---|---|---|
| Sheared and Un-sheared nodes channels | Maximizing throughput, Minimizing collision | Distributed Medium Channel Allocation (DMCA) | yes | Bandwidth | City, Highway, Roral | Yes | Ours |
| Generic | Interference Minimizing | Subpool sensing-based algorithm | No | Bandwidth | Urban grid layout | Yes | [69] |
| Generic | Maximizing Connectivity | Graph theory | Yes | Bandwidth | Single-Lane Highway | No | [70] |
| Generic | Maximizing throughput | Graph theory | Yes | Bandwidth | Single-Lane Highway | Yes | [71] |
| Generic | Maximizing sum rate | Hungarian method | Yes | Bandwidth Power | Two-way urban roadway | Yes | [72] |
| Generic | Maximizing sum-rate; minimize latency | Karush-Kuhn-Tucker theory | Yes | Bandwidth Power | Urban grid layout | No | [73] |
| Security | Maximizing secrecy rate | Greedy algorithm | Yes | Bandwidth | Single-lane Highway | Yes | [74] |
| Generic | Maximizing ergodic capacity, reliability | Hungarian method | Yes | Bandwidth Power | Multi-Lane Highway | Yes | [75] |
| Generic | Reliability maximizing | Pre-scheduling | No | Bandwidth | Single-lane Highway | Yes | [76] |
| Generic | Maximizing concurrent reuses | Perron-Frobenius theory | Yes | Bandwidth | Urban grid layout; Single-lane Highway | No | [77] |
| Fog Computing | Maximizing utility model | Langranign algorithm | Yes | Bandwidth | Multi-RSU network | No | [78] |
| Basic Safety Message relaying | interference Minimizing | Exhaustive search algorithm | No | Bandwidth | Intersection | No | [79] |
| Security | Maximizing resource utilization | Dynamic semi-persistent method | Yes | Bandwidth | Highway | Yes | [80] |
| Cloud Computing | Maximizing discount value | Semi-Markov decision process | Yes | Computing resource | Urban area | No | [81] |
| Vehicle Platooning | Maximizing sum rate | Weight matching theory | Yes | Bandwidth | Single-lane Highway | Yes | [82] |
| Automated guided vehicle | QoS Maximizing | Lyapunov optimization | Yes | Bandwidth | Highway | Yes | [83] |
| Vehicle Platooning | Maximizing service guaranteed users | Conflict-Free SPS | Yes | Bandwidth | Highway | Yes | [84] |
| Platooning Vehicle | stability Maximizing | Application-adaptive algorithm | Yes | Bandwidth | Highway | Yes | [85] |
| multi platooning Vehicle | reallocation rate, Minimizing delay | Lyapunov optimization | Yes | Bandwidth Power | Highway | Yes | [86] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Absi, A.A.; Al-Absi, M.A.; Sain, M.; Lee, H.J. Channel Allocation for Connected Vehicles in Internet of Things Services. Sensors 2021, 21, 3646. https://doi.org/10.3390/s21113646
Al-Absi AA, Al-Absi MA, Sain M, Lee HJ. Channel Allocation for Connected Vehicles in Internet of Things Services. Sensors. 2021; 21(11):3646. https://doi.org/10.3390/s21113646
Chicago/Turabian StyleAl-Absi, Ahmed Abdulhakim, Mohammed Abdulhakim Al-Absi, Mangal Sain, and Hoon Jae Lee. 2021. "Channel Allocation for Connected Vehicles in Internet of Things Services" Sensors 21, no. 11: 3646. https://doi.org/10.3390/s21113646
APA StyleAl-Absi, A. A., Al-Absi, M. A., Sain, M., & Lee, H. J. (2021). Channel Allocation for Connected Vehicles in Internet of Things Services. Sensors, 21(11), 3646. https://doi.org/10.3390/s21113646








