Abstract
The performance of a quality of service (QoS) control scheme in a multi-hop wireless body area network (WBAN) based on the IEEE Std. 802.15.6 is evaluated. In medical Internet of Things systems, WBANs are an important technology. In a previous study, an optimal quality of service control scheme that employs a multiplexing layer for priority scheduling and a decomposable error control coding scheme for WBANs were proposed. However, the two-hop extension supported by IEEE Std.802.15.6 has not been considered. Here, the two-hop extension is applied. Then, the packet error ratio, number of transmissions, and energy efficiency of our previously proposed system are compared to a standard scheme under several conditions. Also, novel evaluations based on communication distance are conducted. Numerical results demonstrate that our proposed scheme, in which coding rates change relative to channel conditions, outperforms standard schemes in many aspects. In addition, those systems show the best performance when the communication distance of the first hop equals that of the second hop. In addition, the above result is theoretically clarified.
1. Introduction
Health monitoring systems that employ wearable vital sign sensors and wireless communication (referred to as medical Internet of Things (m-IoT) systems) have received significant attention recently [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16]. Wireless body area networks (WBAN) are an important key technology in the m-IoT field. WBAN sensors can sample, monitor, process, and communicate a significant amount of various vital data [14]. In addition, they can provide real-time feedback [14]. It is expected that WBANs will be implemented to monitor patient health. In particular, they are expected to monitor elderly people in hospitals, nursing homes, and their own homes [15].
Recently, there have been various attempts to develop standards for WBAN systems [17,18]. In 2011, IEEE Std. 802.15.4a was issued as a standard for wireless personal area networks (WPAN) assuming a wide range of applications [19]. However, IEEE Std. 802.15.4a has not been optimized for medical and healthcare applications. Therefore, IEEE Std. 802.15.6 was published as a standard specialized mainly for implant and wearable WBAN assuming medical-healthcare uses (but not limited to them). In WBAN systems, a wearable vital sign sensor node can include various types of sensors with different data rates. In addition, the allowable communication error ratio and delay depend on the application. IEEE Std. 802.15.6 aims to provide an international standard for low power, short range, and extremely dependable wireless communication within the surrounding area of the human body, supporting a vast range of data rates [14]. Additionally, IEEE Std. 802.15.6 defines eight user priority levels. Quality of Service (QoS) control must ensure that different data types are communicated effectively and efficiently. Therefore, optimal QoS control for input data is an important feature in sensor data transmission procedures. To address this requirement, an optimal QoS control scheme that employs a multiplexing layer for priority scheduling and a decomposable error control coding scheme that adapts to varying channel conditions or QoS requirements have been proposed [20,21,22]. Here, the target WBAN consists of a wearable sensor device that includes multiple sensors whose output data are transmitted using a common medium access control (MAC) and the physical layer (PHY). In those studies, simulations and a theoretical analysis were performed to evaluate the performance of the proposed system by comparing it to an IEEE Std.802.15.6-based system [20,21,22].
Note that IEEE Std. 802.15.6 supports a two-hop extension. In this study, the performance of an error control scheme for a multi-hop WBAN based on IEEE Std. 802.15.6 is evaluated. Specifically, the packet delivery failure ratio (PDFR), number of transmissions as a replacement for delay, and energy efficiency which is throughput considering energy consumption of our previously proposed error control scheme and IEEE Std. 802.15.6 are evaluated relative to this standard’s two-hop extension [20,21,22] like under multi-path fading channel of ultra-wideband (UWB) PHY. The main contribution and novelty of the manuscript are as follows:
- The performance of our previously proposed QoS control scheme is improved by appropriately determining the coding rate using channel estimation. With this improvement, data packets can be relayed to the hub with a small number of transmissions even when the maximum number of retransmissions is limited by a two-hop extension.
- Novel performance evaluations are conducted as a function of the distance between transmitter and receiver assuming a real environment, which were not considered in our previous work [20,21,22]. Through these evaluations, we confirm that our proposed QoS control method is effective even assuming a real environment. It is also clear that it is better to perform two-hop expansion than one-hop case by setting the distance between transmitter and receiver in each hop appropriately. In addition, this paper contributes to theoretically clarifying the relevant optimum setting.
The remainder of this paper is organized as follows. Section 2 introduces the related research in the field of this manuscript. In Section 3, the related descriptions of IEEE Std. 802.15.6 are explained. Section 4 shows our previously proposed error control method. The system model is described in Section 5. Computer simulated performance evaluations and theoretical analysis of the results are presented in Section 6. Section 7 concludes the paper.
2. Related State of the Art Research
This section introduces the latest research related to this manuscript.
WBANs extended to multi-hop communication have been studied to increase their lifetime. Many studies on multi-hop WBANs have focused on energy-efficient MAC or routing protocols [23,24,25,26,27,28,29,30]. For example, previous studies have focused on a cross-layer technique that includes a MAC layer to reduce delay and improve energy efficiency [23,24,25]. In [23], a network tree in a distributed manner has been used to guarantee collision free access to the medium and to route data towards the sink. Computer simulation results have shown that the protocol offers low delay and good resilience to mobility. The proposed solution of [24] extended the cooperation at the MAC layer to a cross-layered gradient based routing solution that allows interaction between WBAN and environmental sensors to ensure data delivery from WBANs to a distant gateway. The MAC layer of [25] provided the network layer with local information about the quality of on-body links to enable the WBAN to identify the most reliable links in a distributed manner. Results of [25] have shown the effectiveness of the proposed design which takes advantage of dynamic scheduling and multi-hop relays as warranted by the link conditions. An energy-efficient and low-delay relay selection method for multi-hop WBANs has also been discussed [26,27]. In [26], a game-theory approach has been proposed to investigate the problem of relay selection and power control with QoS constraints in multiple-access WBANs. Reference [27] considered adaptive power control and routing in multi-hop WBANs, and developed a low overhead energy-efficient routing scheme. The proposed routing protocol has established an energy-efficient end-to-end path as well as adaptively choosing transmission power for sensor nodes. Path loss models have also been considered to evaluate the energy efficiency of multi-hop WBAN topologies in [28]. Ref. [28] has discussed the propagation channel between two half-wavelength dipoles at 2.45 GHz placed near a human body, and then presented an application for cross-layer design to optimize the energy consumption of different topologies. In addition, a security scheme based on PHY characteristics for multi-hop WBANs has been described [29,30]. The game-theory framework of [29] was proposed, wherein wearable sensor devices interact in the presence of wiretappers and under fading channel conditions to find the most secure multi-hop path to the hub, while adhering to the end-to-end delay requirements. Reference [30] proposed MASK-BAN, a lightweight fast authenticated secret key extraction scheme for intra-WBAN communication. However, those studies did not focus on an error control scheme.
On the other hand, the analytical expressions for energy efficiency and packet error ratio (PER) have been formulated for two-way relay cooperative communication in [31] which is similar to our work. Then, [31] introduced a hybrid system, which allows switching between the proposed two-way relay, multi-stage one-way relay, and direct link to maximize energy efficiency, and a joint network-channel coding scheme using convolutional and BCH codes. However, [31] did not consider a hybrid automatic repeat request (ARQ), which was applied to our method. In addition, path loss, shadowing, and additive white Gaussian noise (AWGN) have been taken into account, but multi-path or flat fading has not in [31]. On the other hand, this manuscript considers all of them.
3. Related Description of IEEE Std. 802.15.6
3.1. UWB PHY
The IEEE Std. 802.15.6 defines three PHY layers: narrowband (NB), UWB, and human body communications (HBC). This study focused on an impulse radio ultra-wideband PHY layer (IR-UWB-PHY) which offers high data rate transmission, low energy consumption, powerful multi-pass resolution, good coexistence with other wireless communication systems, and so on.
The UWB PHY frame format is formed by the synchronization header (SHR), the physical layer header (PHR), and the physical layer service data unit. (PSDU), respectively, as shown in Figure 1 [17]. The PSDU contains the MAC protocol data unit (MPDU) and the BCH parity bits. The PSDU can therefore be regarded as the payload. The information contained by the PHR includes the data rate of the PSDU and the length of the MAC frame body, and the SHR contains the preamble used for timing synchronization, packet detection, and other purposes, and the start-of-frame delimiter (SFD) for frame synchronization. This research mainly focused on the performance of the payload (PSDU).

Figure 1.
Ultra-wideband physical layer frame format. SFD, SHR, PHR, and PSUD are abbreviations of start-of-frame delimiter, synchronization header, physical layer header, and physical layer service data unit respectively.
3.2. Two-Hop Extension
An example smart health care monitoring system that includes a WBAN with a two-hop extended star network topology is shown in Figure 2. As can be seen, vital information obtained by WBAN nodes is displayed on a monitoring unit through a WBAN hub.
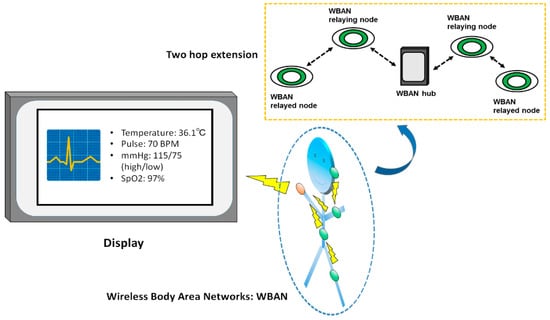
Figure 2.
Example smart health care monitoring system.
In IEEE Std. 802.15.6, a node and a hub can utilize the two-hop extension to exchange frames through another node, except in the medical implant communication service band. In Figure 2, the terminal, intermediate nodes, and the hub function as relayed nodes, relaying nodes, and the target hub of a relayed node, respectively. Here, a relayed node or the target hub can initiate a two-hop extension at times determined by the initiator. Note that a relaying node can exchange its frames with the hub directly.
A relayed node shall not send its frames to a relaying node in contended allocations provided by the target hub [17]. Thus, a scheduled access phase can only be utilized in the case of a two-hop extension. Therefore, the managed access phase as defined in IEEE Std. 802.15.6 is only used in this study.
4. Previously Proposed Error Control Method
In a previous study, an optimal QoS control scheme that employs decomposable error control coding and Weldon’s ARQ scheme was proposed [20,21,22]. As an example of the decomposable code, punctured convolutional code (constraint length ; coding rates are 8/9 to 1/16) is used. The punctured code patterns (codeword 1 and codeword 1’) are generated from a convolutional code whose generator polynomial is [7,5] and the coding rate is = 1/2 as shown in Figure 3.
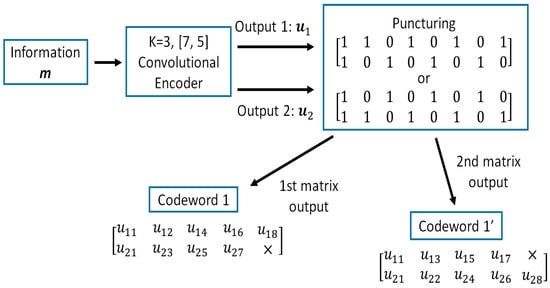
Figure 3.
Punctured convolutional codes .
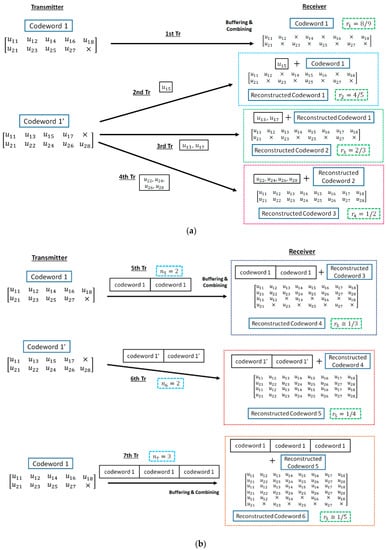
Figure 4.
Method of reconstructing decomposable codes. (a) (b) [20,21,22].
- Firstly, the information bit sequence is encoded via the punctured convolutional code, and codeword 1 is transmitted.
- If bit errors are detected after decoding codeword 1, the receiver stores the transmitted codeword 1, and the transmitter re-sends the sub-codeword of codeword 1′ times if . At the receiver, the received sub-codeword and stored codeword are combined, and the reconstructed codeword is decoded.
- After the third retransmission, codeword 1 is sent times and combined with a buffered codeword at the receiver. If bit errors are detected after decoding reconstructed codeword, the codeword 1 is buffered in the receiver, and codeword 1′ is transmitted times and combined with a stored codeword.
- After that, codeword 1 and 1′ are sent alternately times and stored. Then, a receiver reconstructs and decodes low-rate decomposable codes by changing the number of data copies in Weldon’s ARQ protocol. At this time, a buffered old codeword is updated to a transmitted new codeword.
- This operation continues until no bit errors are detected or the maximum number of transmissions is achieved.
Figure 5 shows a flowchart of the protocol of our proposed error correcting scheme.
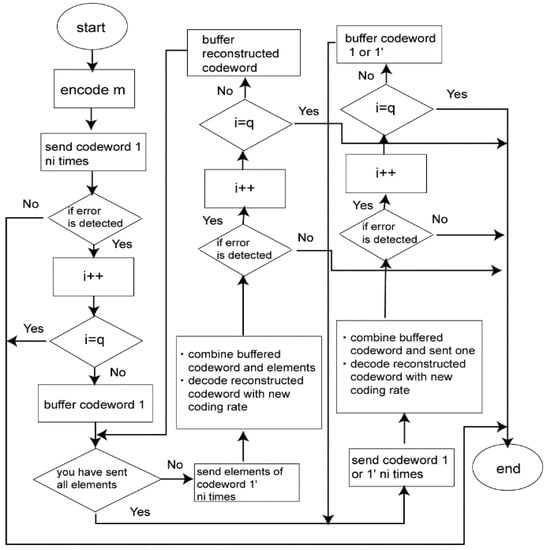
Figure 5.
Flowchart of the proposed automatic repeat request (ARQ) protocol [20,21,22].
This scheme has the following advantages [21,22]. The first one is that the coding rate is very wide. Hence, bit (or packet) errors can be sufficiently eliminated by the coding rate of = 8/9 under very good channel conditions, while very low coding rates can remove bit errors under bad channel conditions. As for the second advantage, in the case of a small number of retransmissions, it is sufficient to transmit a small number of redundant bits. This characteristic leads to improvement of energy efficiency and reduction of transmission delay on retransmission. Finally, combining characteristics of Weldon’s ARQ protocol makes it possible to perform wider QoS control. That is, by controlling the number of data copies in Weldon’s ARQ protocol for transmission, the error correcting capability can be changed even if an error correcting code with the same coding rate is used.
5. System Model in Two-Hop Case
5.1. System Model and QoS Requirement
It is assumed that a sensor node (N1) includes multiple sensors that produce different data types that are transmitted via a relaying node (N2) to the target hub (H) (Figure 6). Here, is the number of transmissions from nodes A to B and is the maximum number of transmissions from nodes A to B. If bit errors are detected, the system retransmits until the maximum number of retransmissions is reached. Then, the transmission is considered to have failed if the data from a sensor node do not reach the target hub.
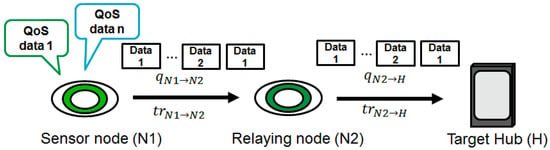
Figure 6.
System model.
The average number of transmissions from node A to node B is expressed as follows:
Here, is the probability of transmission failure in the th transmission. In this study, [21] is the same as PER because packet collisions in the MAC layer are not considered. Hence, bit errors are taken into account due to noise and multipath fading. Then, the average number of transmissions in a two-hop case is expressed as follows:
Here, is the probability of transmission failure at the first hop.
In this study, two data (Data A and Data B) with different types of QoS requirements are considered. Here, it is assumed that a low PER is desired for Data A and high energy efficiency is important for Data B as an example [20,21,22]. As the first reason for selecting those QoSs, this paper particularly focused on an error controlling scheme utilizing a hybrid ARQ, and then PER and the energy efficiency are very important parameters for evaluation of such a scheme. Secondly, those two parameters are related to a trade-off. Hence, we also aimed to show the relationship in some evaluations. Data A is assumed to be a physiological parameter with a low data rate, for example blood pressure, SpO2, or temperature, and Data B to be a waveform, such as an ECG output [20,21,22]. The transmission order and error control process of different types of data packets depend on such QoS requirements. The characteristics of different data types are summarized in Table 1 [13,14,22].

Table 1.
QoS requirements of different data types.
Then, each is set as shown in Table 2. The maximum number of retransmissions is four in high QoS mode in the IR-UWB (impulse radio ultra-wideband) PHY of the standard. However, the default mode in the IR-UWB PHY, the narrowband PHY, and the Human Body Communication PHY in IEEE Std. 802.15.6 do not define a maximum number of retransmissions. Thus, in the current study, this parameter was set according to the QoS requirements of the data in our previous work [20,21,22]. Figure 7 shows examples of each . and denote the probability of transmission failure at the th transmission of the first and second hop, respectively. With Data A, increases steeply under high conditions, especially in low cases, because increases towards as increases. On the other hand, increases gradually with Data B because and are constant.

Table 2.
Maximum number of transmissions.
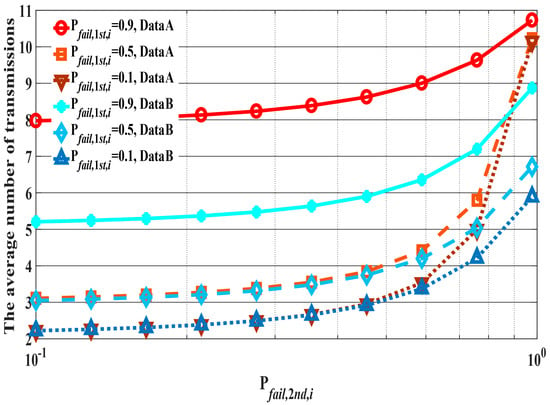
Figure 7.
Examples of . and 0.1. is in the range 0.1–0.9.
5.2. Two Proposed Schemes
In this study, two proposed schemes are assumed. The first scheme (Scheme 1) transmits data depending on preset parameters, which was used in our previous study [20,21,22]. On the other hand, in the second scheme (Scheme 2), coding rates are varied with the SNR estimated using a preamble signal according to each QoS requirement (e.g., desired bit error ratio (BER)), which is introduced for the first time in this manuscript. The operation example is shown in Figure 8. Firstly, the channel SNR is estimated by using the preamble of the beacon or the T-Poll received from the hub or the relaying node. Next, the relayed node or the relaying node determines the coding rate according to the estimated channel SNR and transmits data to the relaying node or the hub. If a bit error is detected, elements of the encoded data (codeword) are transmitted to increase error correcting capability after receiving negative-acknowledgement (NACK). Then, if data are transmitted successfully, the channel SNR is estimated by using the returned acknowledgement (ACK) preamble, the coding rate is determined, and the next data are sent. Since Scheme 2 uses an existing preamble, extra overhead is not required.
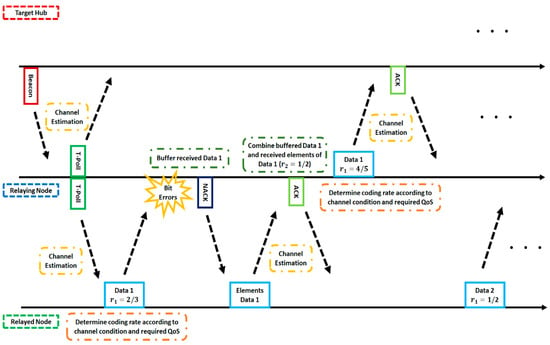
Figure 8.
Operation example of Scheme 2. ACK, NACK, and QoS are abbreviations of acknowledgement, negative-acknowledgement, and quality of service respectively.
Then, the channel SNR is estimated using the following equations [32]:
Here, is the estimated SNR, is a correlation coefficient, is a preamble signal with noise , and is a preamble signal that consists of a signal and unknown constant c without noise or interference. Then, we explain why Equation (3) becomes the SNR. Let’s substitute Equation (4) into Equation (3):
Here, can be expanded as follows:
Here, since noise and a preamble signal are uncorrelated. Then, can be expanded as follows:
For the same reason, . Then, Equation (8) can be modified from Equations (9) and (10) as follows:
Additionally, as follows:
Finally, Equation (11) is summarized as follows, indicating that the SNR can be derived:
where and are signal power and noise power, respectively.
In Scheme 2, the criteria to determine the coding rate are expressed as follows:
where is length of information bits. Hence, the desired BER is calculated from the desired PER such as Table 1 and . The coding rate is determined based on that and the estimated SNR from Figure 9. As the reason for using the desired PER and , it is possible to accurately obtain the desired BER for determining the coding rate from the Equation (14) since the required QoS (desired PER) is used. For example, in a case where the desired PER is and is 400 bits, the desired BER is calculated as . Here, if the estimated SNR is 5 dB, the coding rate is determined to be = 1/2 as shown in Figure 9.
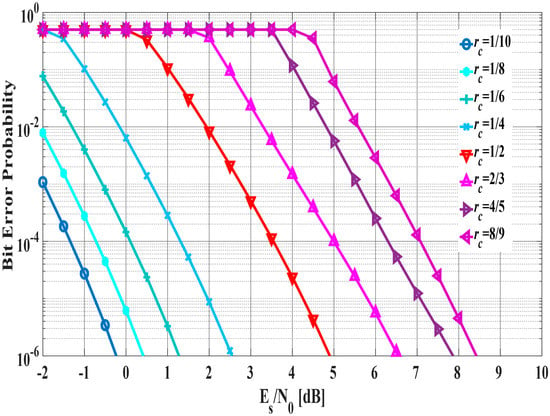
Figure 9.
Bit error probability in each coding rate.
6. Results and Discussion
6.1. Performance Evaluation by Computer Simulation
In this section, the proposed and standard schemes with two-hop extension are evaluated based on communication distance by computer simulations. The computer simulator was built by us with MATLAB. The main simulation parameters are listed in Table 3 and refer to our previous work [20,21,22]. Table 4 shows the preset parameters of Weldon’s ARQ protocol at the th transmission for Scheme 1 [20,21,22]. The computer simulation assumes that there is no error in SHR and PHR. That is, only the characteristics of PSDU are evaluated. In computer simulations of the compared schemes, Data A was transmitted using the default mode with (63, 51) BCH code in IEEE Std. 802.15.6 and the error control scheme utilizing the (63, 55) Reed-Solomon code in IEEE Std. 802.15.4a with ordinary ARQ, whereas Data B was transmitted using the high QoS mode with (126, 63) shortened BCH code and type-II hybrid ARQ, and then the error control scheme utilizing the concatenated code consisting of the (63, 55) Reed–Solomon code and the convolutional code whose constraint length is three and coding rate is 1/2 in IEEE Std. 802.15.4a with ordinary ARQ [17,19]. In these computer simulations, the IEEE model CM 3 is applied as a channel model, which is targeted for wearable WBAN and includes multi-path fading [33]. Then, a hospital room case in the IEEE model CM3 is utilized as a path loss model [33]. The path loss is expressed as follows:

Table 3.
Main simulation parameters.

Table 4.
Preset number of data copies in Weldon’s ARQ .
Here, and are linear fitting coefficients, is the communication distance (millimeter, mm) between a transmitter and a receiver, and is a normally distributed variable with zero mean and standard deviation . Details about these parameters can be found in the literature [33]. Using , the signal to noise ratio (SNR) at a receiver can be expressed as follows:
where is transmission power and is thermal noise. The average path loss is shown in Figure 10. It is assumed that the channel condition does not change until the two-hop relay is completed or the two-hop relay fails beyond the maximum number of retransmissions.
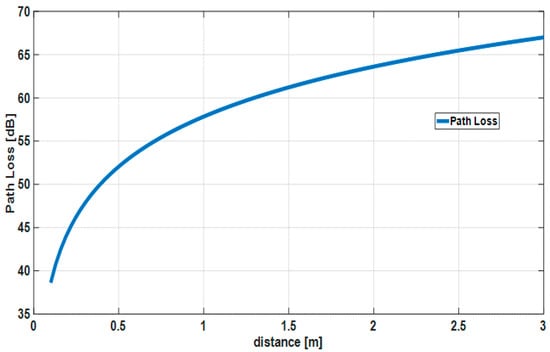
Figure 10.
Average path loss in IEEE model CM3.
In addition, each case of the proposed scheme in each hop is summarized in Table 5.

Table 5.
Cases for the proposed scheme of each hop.
Then, energy efficiency is derived from our previous work [22] as follows:
Here, is the energy consumption of the communication link at each hop and is the transmission success ratio, is the total duration of packet transmission, is the duration of ACK, is the length of PSDU, is the number of transmission, is the transmitter RF power consumption, is the transmitter circuitry power consumption, is the receiver power consumption, and and are the encoding and decoding energies, respectively [34,35,36,37].
Figure 11, Figure 12 and Figure 13 show the performance results when the distance of the first hop is changed from 10 centimeters (cm) to 3 m and the distance of the second hop is constant ( = 40 cm). In this scenario, it can be said that the performance in the range in which the WBAN mainly operates (10 cm~1.5 m) and certain limitations of the WBAN system (1.5 m~2.3 m) are evaluated. PDFR means the ratio at which the two-hop relay failed beyond the maximum number of retransmissions. As can be seen, the proposed scheme satisfies the QoS requirements for data A and B as shown in Table 1, while IEEE Std. 802.15.6 and 15.4a do not. Hence, the proposed method can improve PER of Data A more, while it can improve the energy efficiency and the number of transmissions of Data B more. Conversely, Data B has better performances with respect to both standard schemes. The reason is that those standard schemes are not basically designed so that any QoSs can be satisfied. Hence, it can be considered that the performances of each mode of IEEE Std. 802.15.6 and error control schemes of IEEE Std. 802.15.4a were simply expressed. Also, that is one of problems of these standard schemes. Cases 2 and 3 show better energy efficiency and average number of transmissions than Case 1, because the coding rate of Case 2 and Case 3 is set appropriately for the channel SNR and the number of retransmissions is reduced by utilizing Scheme 2, while Case 1 uses only Scheme 1 and it requires a larger number of retransmissions. However, there is not a large difference between Cases 2 and 3 because is short and the error correcting capability of coding rate = 8/9 at the first transmission can reduce bit errors sufficiently. That is, there is no large difference between Schemes 1 and 2 with respect to the second hop.
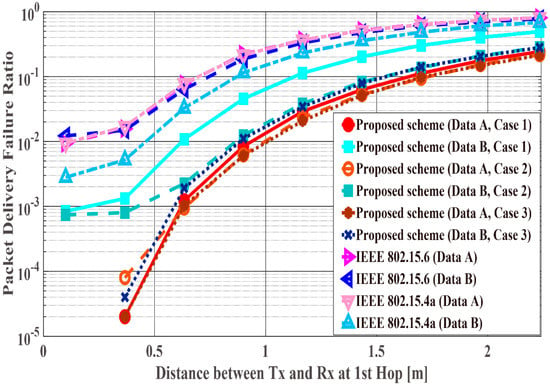
Figure 11.
Packet delivery failure ratio with constant .
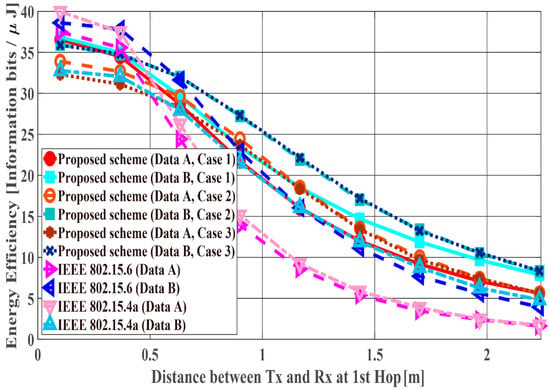
Figure 12.
Energy efficiency with constant .
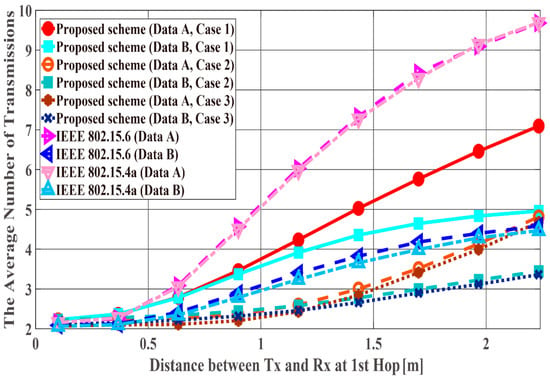
Figure 13.
Average number of transmissions with constant .
Figure 14, Figure 15 and Figure 16 show the performance results for fixed communication distance in two hops + (1.5 m) and varying the and values. For = 1.5 m, data are transmitted using only a single hop. Thus, the proposed scheme satisfies the QoS requirements for Data A and B, while both standard schemes approach do not, like in the first scenario. Also, when comparing the standard schemes and the proposed scheme, the performances of both standards are worse than the proposed one. For example, Data A of the proposed scheme satisfies PDFR <, while that of both standards do not satisfy PDFR <. This is because the correcting capability of error correcting codes used in those standards is lower than that of the proposed scheme. In other words, the standard schemes do not have sufficient correcting capability in a hop with poor channel conditions. Comparing Case 1 and Case 2, it is understood that Case 2 has better characteristics. The reason is that Case 2 can select a coding rate suitable for the channel condition by using Scheme 2 at the second hop. On the other hand, regarding Case 1, since Scheme 1 is used at both hops, it is considered that a hop having a bad channel condition is greatly affected. Then, Case 3 shows the best performance because Scheme 2 is used at both hops. In addition, all systems except Case 2 of the proposed scheme show the best performance when the communication distance of the first hop equals that of the second hop because or becomes long (unlike the previous condition) and the long-distance communication influences performance in other cases.
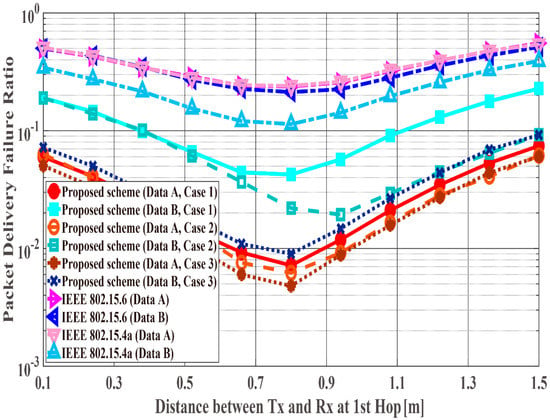
Figure 14.
Packet delivery failure ratio with constant .
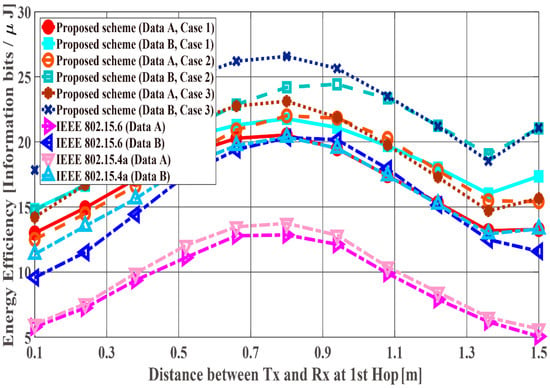
Figure 15.
Energy efficiency with constant .
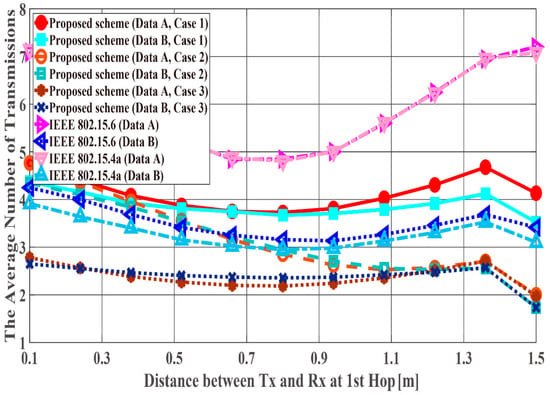
Figure 16.
Average number of transmissions with constant .
6.2. Theoretical Analysis of Constant
Here, we present a theoretical analysis when is fixed because this scenario appears to show the optimal point in Figure 14, Figure 15 and Figure 16. The reason for the optimized performances, except for Case 2, when = = is described in this section.
The probability of transmission failure in the two-hop case is expressed using the probability of transmission failure at each hop , as follows:
Here, = and = . The communication distance in two hops is defined as follows:
is differentiated by as follows:
Here, the case that (30) = 0 is considered. Equation (30) is modified by the following equation:
Both sides of (31) are integrated by as follows:
Here, where is considered. Under this condition, . Thus, (32) is rewritten as follows:
and that satisfies (33) are considered. Here, it is assumed that . Under this condition, (33) is satisfied when in the computer simulations (except for Case 2) because, when , (27) is modified as follows:
When (26) is satisfied,
or
However, due to (27)–(29), (35) and (36) are not satisfied. Thus, it can be said that . On the other hand, for Case 2, (33) is not satisfied when because . From Figure 14, Figure 15 and Figure 16, it can be observed that all cases (except Case 2) achieve optimal performance under the above conditions; thus, .
7. Conclusions
In this paper, the performance of our proposed QoS control scheme in the case of two-hop extension was evaluated. The PDFR, number of transmissions, and energy efficiency of our previously proposed system, IEEE Std. 802.15.6, and 15.4a were evaluated for this case. Also, two schemes (Schemes 1 and 2) were compared for the proposed method. The numerical results show that the proposed scheme outperforms the standard scheme in terms of the PDFR, number of transmissions, and energy efficiency. In addition, Case 3 (i.e., the coding rates change depending on the channel’s condition) showed better performance than the other cases at both hops. When was fixed, it was shown that performance became optimal when (except Case 2) from computer simulations and theoretical analysis. This result is expected to greatly contribute to the optimization of how nodes and hubs are arranged when designing a WBAN.
In the future, an effective error control scheme for multi-hop WBANs should be considered. In addition, PHY evaluation indexes were mainly considered. Hence, evaluating the system delay and throughput in the network layer should be considered for multi-hop cases. As an extension of IEEE Std. 802.15.6, cases with greater than three hops should also be evaluated and analyzed theoretically.
Author Contributions
K.T. and H.T. conceived and designed the study. K.T. performed the computer simulations. K.T. provided the theoretical analysis of the proposed method. K.T. wrote the manuscript. H.T., C.S., K.S. and R.K. reviewed and edited the manuscript. All authors read and approved the manuscript
Funding
The APC was funded by Japan Society for the Promotion of Science under Grant-in-Aid for Scientific Research (C) (KAKENHI No. 16K06363) and Wesco Scientific Promotion Foundation
Acknowledgments
The first author would like to thank members of Kohno laboratory, Yokohama National University, Japan for their great inspiration and kindness.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chen, M.; Gonzalez, S.; Vasilakos, A.V.; Cao, H. VCM Leung, Body Area Networks: A Survey. Mob. Netw. Appl. 2010, 16, 171–193. [Google Scholar] [CrossRef]
- Acampora, G.; Cook, D.J.; Rashidi, P.; Vasilakos, A.V. A Survey on Ambient Intelligence in Healthcare. Proc. IEEE 2013, 101, 2470–2494. [Google Scholar] [CrossRef] [PubMed]
- Hayajneh, T.; Almashaqbeh, G.; Ullah, S.; Vasilakos, A.V. A survey of wireless technologies coexistence in WBAN: Analysis and open research issues. Wirel. Netw. 2014, 20, 2165–2199. [Google Scholar] [CrossRef]
- Fortino, G.; Fatta, G.D.; Pathan, M.; Vasilakos, A.V. Cloud-assisted body area networks: State-of-the-art and future challenges. Wirel. Netw. 2014, 20, 1925–1938. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Lin, X.; Vasilakos, A.V. Securing m-healthcare social networks: Challenges, countermeasures and future directions. IEEE Wirel. Commun. 2013, 20, 12–21. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Xiong, N.; Vasilakos, A.V. 4S: A secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Inf. Sci. 2014, 314, 255–276. [Google Scholar] [CrossRef]
- Cao, H.; Leung, V.; Chow, C.; Chan, H. Enabling technologies for wireless body area networks: A survey and outlook. IEEE Commun. Mag. 2009, 47, 84–93. [Google Scholar] [CrossRef]
- Viswanathan, H.; Chen, B.; Pompili, D. Research challenges in computation, communication, and context awareness for ubiquitous healthcare. IEEE Commun. Mag. 2012, 50, 92–99. [Google Scholar] [CrossRef]
- Bachmann, C.; Ashouei, M.; Pop, V.; Vidojkovic, M.; Groot, H.D.; Gyselinckx, B. Low-power wireless sensor nodes for ubiquitous long-term biomedical signal monitoring. IEEE Commun. Mag. 2012, 50, 20–27. [Google Scholar] [CrossRef]
- Caldeira, J.M.L.P.; Rodrigues, J.J.P.C.; Lorenz, P. Toward ubiquitous mobility solutions for body sensor networks on healthcare. IEEE Commun. Mag. 2012, 50, 108–115. [Google Scholar] [CrossRef]
- Boulis, A.; Smith, D.; Miniutti, D.; Libman, L.; Tselishchev, Y. Challenges in body area networks for healthcare: The MAC. IEEE Commun. Mag. 2012, 50, 100–106. [Google Scholar] [CrossRef]
- Suzuki, T.; Tanaka, H.; Minami, S.; Yamada, H.; Miyata, T. Wearable Wireless Vital Monitoring Technology for Smart Health Care. In Proceedings of the 7th International Symposium on Medical Information and Communication Technology (ISMICT), Tokyo, Japan, 6–8 March 2013. [Google Scholar]
- Cavallari, R.; Martelli, F.; Rosini, R.; Buratti, C.; Verdone, R. A Survey on Wireless Body Area Networks: Technologies and Design Challenges. IEEE Commun. Surv. Tutor. 2014, 16, 1635–1657. [Google Scholar] [CrossRef]
- Movassaghi, S.; Abolhasan, M.; Lipman, J.; Smith, D.; Jamalipour, A. Wireless Body Area Networks: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1658–1686. [Google Scholar] [CrossRef]
- Patel, M.; Wang, J. Applications, challenges, and prospective in emerging body area networking technologies. IEEE Wirel. Commun. 2010, 17, 80–88. [Google Scholar] [CrossRef]
- Rodrigues, J.J.P.C. Digital Advances in Medicine, E-Health, and Communication Technologies; IGI Global: Hershey, PA, USA, 2013; ISBN 978-1-466-62794-9. [Google Scholar]
- IEEE Standard for Information Technology—Telecommunications and Information Exchange between Systems-Local and Metropolitan Area Networks-Specific Requirements: Part 15.6: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Wireless Personal Area Networks (WPANs) Used in or 12 around a Body. IEEE, 2012. Available online: https://ieeexplore.ieee.org/document/6161600 (accessed on 28 September 2018).
- Smart Body Area Network (SmartBAN); Low Complexity Medium Access Control (MAC) for SmartBAN, ETSI TC Smart BAN TS 103 325 V1.1.1. 2015. Available online: http://www.etsi.org/deliver/etsi_ts/103300_103399/103325/01.01.01_60/ts_103325v010101p.pdf (accessed on 28 September 2018).
- IEEE Std 802.15.4-2011 (Revision of IEEE Std 802.15.4-2006)-IEEE Standard for Local and Metropolitan Area Networks—Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs). IEEE, 2011. Available online: https://ieeexplore.ieee.org/document/6012487 (accessed on 28 September 2018).
- Takabayashi, K.; Tanaka, H.; Sugimoto, C.; Kohno, R. Multiplexing and Error Control Scheme for Body Area Network employing IEEE 802.15.6. IEICE Trans. Commun. 2014, 97, 564–570. [Google Scholar] [CrossRef]
- Takabayashi, K.; Tanaka, H.; Sugimoto, C.; Kohno, R. Performance Analysis of Multiplexing and Error Control Scheme for Body Area Networks. EURASIP J. Wirel. Commun. Netw. 2016, 2016, 1–16. [Google Scholar] [CrossRef]
- Takabayashi, K.; Karvonen, H.; Paso, T.; Tanaka, H.; Sugimoto, C.; Kohno, R. Performance Evaluation of a QoS-aware Error Control Scheme for Multiple-WBAN Environment. IEEJ Trans. Electr. Electron. Eng. TEEE C 2017, 12, S146–S157. [Google Scholar] [CrossRef]
- Latre, B.; Braem, B.; Moerman, I.; Blondia, C.; Reusens, E.; Joseph, W.; Demeester, P. A Low-delay Protocol for Multihop Wireless Body Area Networks. In Proceedings of the 2007 Fourth Annual International Conference on Mobile and Ubiquitous Systems: Networking & Services (MobiQuitous), Philadelphia, PA, USA, 6–10 August 2007. [Google Scholar]
- Ivanov, S.; Botvich, D.; Balasubramaniam, S. Cooperative wireless sensor environments supporting body area networks. IEEE Trans. Consum. Electron. 2012, 58, 284–292. [Google Scholar] [CrossRef]
- Torabi, N.; Leung, V.C.M. Cross-Layer Design for Prompt and Reliable Transmissions over Body Area Networks. IEEE J. Biomed. Health Inf. 2014, 18, 1303–1316. [Google Scholar] [CrossRef] [PubMed]
- Moosavi, H.; Bui, F.M. Optimal Relay Selection and Power Control with Quality-of-Service Provisioning in Wireless Body Area Networks. IEEE Trans. Wirel. Commun. 2016, 15, 5497–5510. [Google Scholar] [CrossRef]
- Liang, L.; Ge, Y.; Feng, G.; Ni, W.; Wai, A.A.P. Experimental study on adaptive power control based routing in multi-hop Wireless Body Area Networks. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012. [Google Scholar]
- Reusens, E.; Joseph, W.; Latré, B.; Braem, B.; Vermeeren, G.; Tanghe, E.; Martens, L.; Moerman, I.; Blondia, C. Characterization of On-Body Communication Channel and Energy Efficient Topology Design for Wireless Body Area Networks. IEEE Trans. Inf. Technol. Biomed. 2009, 13, 933–945. [Google Scholar] [CrossRef] [PubMed]
- Moosavi, H.; Bui, F.M. Delay-Aware Optimization of Physical Layer Security in Multi-Hop Wireless Body Area Networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1928–1939. [Google Scholar] [CrossRef]
- Shi, L.; Yuan, J.; Yu, S.; Li, M. MASK-BAN: Movement-Aided Authenticated Secret Key Extraction Utilizing Channel Characteristics in Body Area Networks. IEEE Int. Things J. 2015, 2, 52–62. [Google Scholar] [CrossRef]
- Waheed, M.; Ahmad, R.; Ahmed, W.; Drieberg, M.; Alam, M.M. Towards Efficient Wireless Body Area Network Using Two-Way Relay Cooperation. Sensors 2018, 18, 565. [Google Scholar] [CrossRef] [PubMed]
- Kamiya, Y. Digital Wireless Communication Technologies with MATLAB, 1st ed.; Corona Publishing Co., Ltd.: Tokyo, Japan, 2008; pp. 168–169. ISBN 978-4-339-00800-5. (In Japanese) [Google Scholar]
- Yazdandoost, K.Y.; Sayrafian-Pour, K. Channel Model for Body Area Network (BAN). IEEE P802.15 Working Group for Wireless Personal Area Networks (WPANs), IEEE P802.15-08-0780-10-0006. 2009. Available online: https://mentor.ieee.org/802.15/file/08/15-08-0780-10-0006-tg6-channel-model.pdf (accessed on 28 September 2018).
- Karvonen, H.; Iinatti, J.; Hämäläinen, M. A cross-layer energy efficiency optimization model for WBAN using IR-UWB transceivers. Telecommun. Syst. 2015, 58, 165–177. [Google Scholar] [CrossRef]
- Abughalieh, N.; Steenhaut, K.; Nowé, A.; Anpalagan, A. Turbo codes for multihop wireless sensor networks with decode-and-forward mechanism. EURASIP J. Wirel. Commun. Netw. 2014, 204, 1–13. [Google Scholar]
- Ryckaert, J.; Desset, C.; Fort, A.; Badaroglu, M.; De Heyn, V.; Wambacq, P.; Van der Plas, G.; Donnay, S.; Van Poucke, B.; Gyselinckx, B. Ultra-wide-band transmitter for low-power wireless body area networks: Design and evaluation. IEEE Trans. Circuits Syst. I Regul. Pap. 2005, 52, 2515–2525. [Google Scholar] [CrossRef]
- Zou, Z.; Mendoza, D.S.; Wang, P.; Zhou, Q.; Mao, J.; Jonsson, F.; Tenhunen, H.; Zheng, L.R. A Low-Power and Flexible Energy Detection IR-UWB Receiver for RFID and Wireless Sensor Networks. IEEE Trans. Circuits Syst. I Regul. Pap. 2011, 58, 1470–1482. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).