Abstract
In this paper, we investigate simultaneous wireless power transfer and secure multicasting via cooperative decode-and-forward (DF) relays in the presence of multiple energy receivers and eavesdroppers. Two scenarios are considered under a total power budget: maximizing the minimum harvested energy among the energy receivers under a multicast secrecy rate constraint; and maximizing the multicast secrecy rate under a minimum harvested energy constraint. For both scenarios, we solve the transmit power allocation and relay beamformer design problems by using semidefinite relaxation and bisection technique. We present numerical results to analyze the energy harvesting and secure multicasting performances in cooperative DF relay networks.
1. Introduction
As a promising technique for energy-constrained wireless communication systems, simultaneous wireless information and power transfer (SWIPT) techniques have been extensively investigated to provide a cost-effective solution for self-sustainability of energy-limited wireless devices [1,2]. The SWIPT schemes have been utilized in various wireless networks [3,4]. In [3], SWIPT-enabled small cells are deployed in heterogeneous cloud small cell networks and energy harvesting revenues have been considered in interference management problems. In particular, references [5,6,7,8] have focused on security issues in SWIPT sytstems and exploited physical layer security techniques to enable simultaneous secure communication and wireless power transfer. In [5], secure beamforming design for a multi-antenna amplify-and-forward (AF) relay was proposed for SWIPT systems. In multiuser multiple-input single-output (MISO) systems, Ng et al. [6] proposed beamforming design to minimize the total transmit power of the system for simultaneous secure communication and power transfer, whereas [7] maximized secrecy rates satisfying given energy harvesting and overall power constraints. It is noteworthy that a single source-destination pair is considered in [5,6,7,8] for secure communication in SWIPT systems.
In this work, secure broadcasting scenarios [9] are considered in SWIPT systems, where an individual secure message is sent to each destination [8] or a common secure message is sent to multiple destinations (i.e., secure multicasting) [10,11]. In particular, we focus on the secure multicasting scenario with wireless power transfer. A common secure message is sent from a source to its desired destinations, while multiple eavesdroppers also exist to overhear the secure message. In general, a rate at which secure messages can be sent from a source to its intended receiver without being leaked to eavesdroppers is termed an achievable secrecy rate. The maximum achievable secrecy rate is defined as the secrecy capacity. In our scenario, energy receivers also exist in the system to harvest energy from the RF transmission. While a source equipped with multiple antennas is considered in [10,11], we consider that a source equipped with a single antenna performs simultaneous secure multicasting and wireless power transfer with the help of multiple decode-and-forward (DF) single-antenna relays located between the source and the receiver nodes [12]. In this work, multiple relays are designed to operate cooperatively to improve the multicast secrecy rate as well as to enlarge the harvested energy at the energy receivers. It is worth mentioning that the exploitation of cooperative relays for SWIPT systems is also shown in [13,14], but a single source-destination pair is considered for secure communication and amplify-and-forward (AF) relays are utilized.
For simultaneous wireless power transfer and secure multicasting in cooperative DF relay networks, we investigate transmit power allocation and relay beamformer design problems under a total power budget, where the overall power consumed by the source and the relays does not exceed a given limit, in the following two scenarios: (1) maximize the minimum harvested energy achieving a given multicast secrecy rate; and (2) maximize the multicast secrecy rate under a minimum harvested energy constraint. Our contribution in this paper is to show that the optimization problems for both scenarios can be solved by a unified framework consisting of semidefinite relaxation [15] and bisection technique [16].
2. System Model
As shown in Figure 1, we consider that one source node, M trusted relays, I destination nodes, J eavesdroppers, and K energy receivers are deployed in a wireless relay network. All nodes are assumed to have a single antenna and each relay operates in the DF mode. The cooperative relays R’s support the source node S to send a common secure message to the destination nodes D’s. The eavesdroppers E’s try to overhear the information message and the energy receivers G’s perform energy harvesting from the RF transmission of S and R’s.
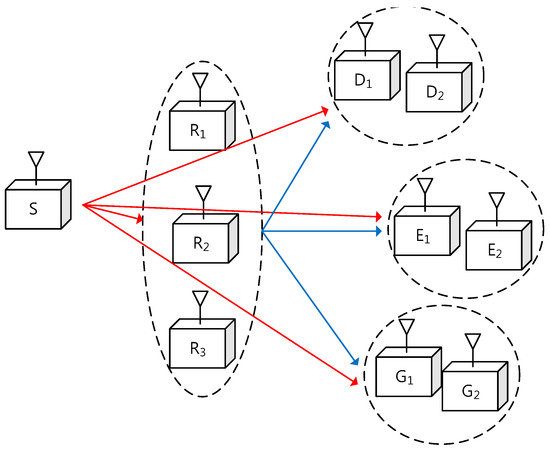
Figure 1.
System model for simultaneous wireless power transfer and secure multicasting via cooperative relays ( and ), where S, , , , and represent the source, the mth relay, the ith destination, the jth eavesdropper, and the kth energy receiver, respectively.
In the first time slot, S sends s and the other nodes listen. We denote , , , and as the received signals at the ith D, the jth E, the kth G, and the mth R, respectively, which are given as
where , , , and are the complex channel gains from S to the ith D, the jth E, the kth G, and the mth R, respectively, and is the transmit power of S. Moreover, , , , and are complex additive white Gaussian noises with zero-mean and variance . In the second time slot, we assume that R decode s successfully and send the weighted version of the re-encoded symbol. Then, the received signals at D’s, E’s, and K’s can be expressed as
where M relay weights are stacked in a vector and , , and denote complex channel vectors from R’s to the ith D, the jth E, and the kth G, respectively.
Let each D and E perform maximal ratio combining using the received signals during two time slots. Then, the rates at the ith D and the jth E are computed as
where
and denotes the conjugated transpose. Here, we compute the achievable multicast secrecy rate as [17]
The rate at the mth R is given as
where . Further, the harvested energy at the kth G is proportional to [5]
where , , and is the energy harvesting efficiency.
In this work, let us assume that global channel state information (CSI) is available. This assumption is valid when we can monitor the transmission of E’s since they are also active in the network [18]. In this scenario, E’s are low-level users such that they are allowed to access less information than D’s. If the global CSI is not available, we may use artificial noise (AN) techniques [19,20], where we consume some portion of the total power budget to transmit artificially generated noises. We expect that our proposed schemes derived in the following can be extended to exploit the AN techniques for simultaneous wireless power transfer and secure multicasting in cooperative DF relay networks.
3. Energy Harvesting Maximization with Secure Multicasting Constraints
Our objective in this section is to maximize the minimum harvested energy among K energy receivers while guaranteeing that the multicast secrecy rate is greater than or equal to the given threshold (i.e., ). Because the common information rate for multicasting is determined by the rate of the weakest S-D link [17,21], we let the rate at each relay be equal to or greater than the minimum rate among D’s (i.e., for all m) such that each R correctly decodes and forwards the common secure message. The optimization problem under a total power budget and the DF relaying constraints for secure multicasting is given as
Substituting (3), (6), and (7) into (8), we have
where and . Let us rewrite (9) as
where , tr(.) denotes the trace of a matrix, and represents that is a Hermitian positive semidefinite matrix.
In (10), let us ignore the rank constraint using semidefinite relaxation [15]. Then, we use the concept of bisection technique [16] as follows. At first, we set an initial interval , where the maximum value of in (10) is assumed to exist. At the midpoint of the given interval , the following feasibility problem is solved by using SeDuMi [22] and Yalmip [23]:
If (11) is infeasible, we update . If (11) is feasible such that we can obtain the solutions , , , and , we check the rank of . If the rank of is one, we update . Otherwise, we exploit the penalty function method (PFM) in [24] with , , , and to confirm the existence of a rank-one solution. The PFM consists of the initialization and optimization steps, which are both an iterative process. In this work, we use as a starting point in the initialization step of the PFM. After the iteration of the initialization step is terminated, we may obtain with . Then, we use as a starting point in the optimization step of the PFM. In the initialization and optimization steps of the PFM, the following semidefinite programming problem is solved at the lth iteration:
where is the maximum eigenvalue of and denotes the eigenvector of corresponding to the maximum eigenvalue. If we can obtain a rank-one solution using the PFM, we update . Otherwise, we update . Until the width of the updated interval is small enough, the above process continues. The initial interval for the above bisection technique is derived in Appendix A.
4. Multicast Secrecy Rate Maximization with Energy Harvesting Constraints
Now, we aim to maximize the achievable multicast secrecy rate [17], while guaranteeing that the minimum harvested energy among K energy receivers is greater than or equal to the given threshold (i.e., ) shown as
which can be considered as an extended version of [17] for cooperative DF relay networks including the energy harvesting constraints. Substituting (3), (6), and (7) into (13), we have
Let us rewrite (14) as
As in Section 3, we also exploit the semidefinite relaxation and bisection technique to solve (15). The rank constraint in (15) is ignored and the bisection technique begins with an initial interval , where the maximum value of is assumed to exist. At the midpoint of the given interval , the following feasibility problem is solved by using SeDuMi [22] and Yalmip [23]:
The bisection process is the same as that described in Section 3. We update when (16) is infeasible. If (16) is feasible, we can obtain , , , and . If the rank of is one, we update . Otherwise, the PFM is performed to confirm the existence of a rank-one for the given , , and . If we obtain a rank-one solution via the PFM, we update . Otherwise, we update . Until the width of the updated interval is small enough, the above process continues. The initial interval is also derived in Appendix B.
5. Numerical Results
In this section, we present numerical results to verify the energy harvesting and secure multicasting performance of the proposed schemes. As shown in Figure 2, we assume that R’s are located randomly within a circle with a radius of and the center of the circle for R’s is located away from S. Further, the radius of a circle, where D’s, E’s, and G’s are located randomly, is and the center of this circle is on the line formed by S and the center of the circle for R’s. The center of the circle for D’s, E’s, and G’s is located away from S. In our simulation, we set m, m, m, and varied for R’s to be located between S and the receiver nodes D’s, E’s, and G’s as in [12]. We adopt a line-of-sight channel model [12] such that the channel gain between any two nodes is evaluated by , where d is the distance between the nodes, denotes the path loss exponent, and follows a uniform distribution on . For simplicity, we set dBm and dBm. We performed Monte Carlo simulations with independent channel realizations and random node locations to obtain the average results.
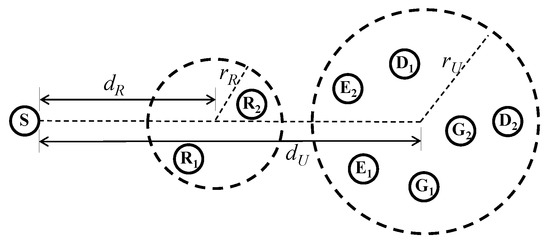
Figure 2.
Simulation model.
Let us first consider maximizing the minimum harvested energy under a multicast secrecy rate constraint described in Section 3. In Figure 3, we present [7] as a function of for different values of when and , where denotes the average of and the upper bound is the average of the minimum harvested energy without the secure multicast constraints as in Appendix A. Note that only wireless power transfer is performed when there is no secure multicasting constraint, which is equivalent to . In this case, it is beneficial for energy harvesting that R’s are located close to G’s, because the harvested energy at G depends on the received signal strength as shown in (7) and G can easily harvest the energy from the RF transmission of the closely located R’s. Therefore, the upper bound in Figure 3 increases as R’s move closer to the nodes (i.e., increases). Now, we focus on a simultaneous wireless power transfer and secure multicasting case with . In this case, R’s in the DF mode should decode a secure message from S correctly and forward it to D’s. Obviously, moving close to S is beneficial for R’s to decode the secure message from S without errors and R’s should be located more closely to S for larger values of . Here, we find a tradeoff for the R’s location in simultaneous wireless power transfer and secure multicasting scenarios. In our simulation, we do not allow the RF transmission of S and R’s for a certain channel realization and random location of the nodes, where the given cannot be achieved (i.e., the optimization problem in (8) is infeasible for the given ). For smaller values of , the wireless power transfer is more dominant than the secure multicasting such that the average of the minimum harvested energy still increases as increases. However, for larger values of , is found to decrease drastically for larger values of . This implies that, when R’s are located close to the receiver nodes, it is hard to achieve the given for lots of channel realizations and random node locations such that S and R’s do not perform the RF transmission more frequently and the harvested energy at G’s reduces.
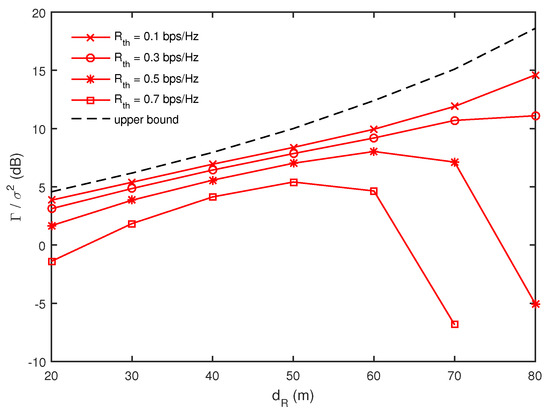
Figure 3.
Comparison of minimum harvested energy as a function of for different values of when and .
Figure 4 presents as a function of K for different values of and I when , , and m. As expected, the minimum harvest energy decreases as K increases and also becomes smaller for larger values of in all ranges of K. However, it is observed that the decrease of the minimum harvested energy according to increasing K does not become steeper even though is larger. Further, for a given , the minimum harvested energy with is greater than that with in all ranges of K and the gap between them becomes larger with an increase of . Since the multicast secrecy rate depends on the minimum rate among D’s as shown in (5), it becomes harder to achieve the given as I increases. Then, the solution for and in (8) becomes more oriented to the secure multicasting for achieving than the energy harvesting, as I becomes larger. This phenomenon becomes severe as increases.
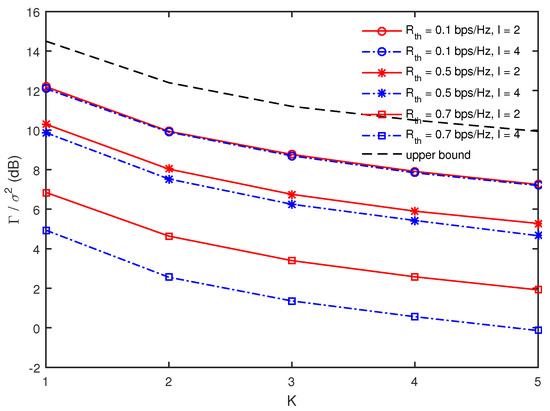
Figure 4.
Comparison of minimum harvested energy as a function of K for different values of and I when , , and m.
Now, we focus on maximizing multicast secrecy rates under a minimum energy harvesting constraint investigated in Section 4. Figure 5 shows the multicast secrecy rate as a function of for different values of when and . We evaluated the upper bound in Figure 5 as in Appendix B, which is the multicast rate in the absence of E’s without the energy harvesting constraints. Note that R’s should decode the signal from S correctly as well as forward it to D’s thoroughly. In order to decode the signal from S correctly, R’s should be close to S, while it is beneficial for the signal forwarding that R’s are located close to D. As a compromise, it is optimal for the multicast rate to let R’s be in the middle range between S and the receiver nodes as shown in the curve for the upper bound in Figure 5. This observation is still valid for simultaneous wireless power transfer and secure multicasting cases. It is seen that the optimal position of R’s to provide the maximum multicast secrecy rate is m until dB, while m is found to be optimal when dB. As discussed in Figure 3, it is advantageous for energy harvesting that R’s are close to G’s. For larger values of , the energy harvesting becomes more dominant, such that the optimal position of R’s move closer to the receiver nodes. Moreover, the multicast secrecy rate decreases in all ranges of as increases. In particular for smaller values of , the secrecy rate decrease with an increase of is more severe. This implies that, as R’s are located farther from G’s, it becomes more difficult to satisfy the given energy harvesting constraint.
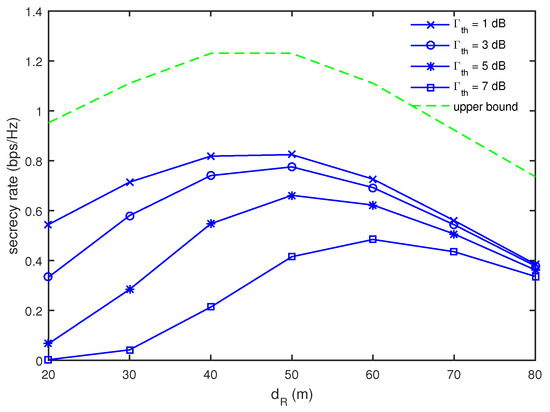
Figure 5.
Comparison of multicast secrecy rate as a function of for different values of when and .
From the observations in Figure 3 and Figure 5, we found that the location of R’s is an important factor to figure out the tradeoff between energy harvesting and secure multicasting in simultaneous wireless power transfer and secure multicasting via cooperative DF relays. In Figure 3, we observed that R’s should be close to G’s for energy harvesting, while it is advantageous for secure multicasting that R’s is located in the middle range of S and the receiver nodes as shown in Figure 5. For simultaneous wireless power transfer and secure multicasting in cooperative DF relay networks, we may choose the location of R’s to be close to the receiver nodes when the harvested energy is more required than the multicast secrecy rates, while the location of R’s may be chosen to be in the middle range between S and the receiver nodes when more multicast secrecy rates are needed.
The multicast secrecy rates are compared in Figure 6 as a function of J for different values of and K when , , and m. As expected, the multicast secrecy rate is found to decrease with an increase of J. It also becomes smaller for larger values of K in all ranges of J. Further, it is also observed that the gap between the multicast secrecy rates for and 4 becomes more significant as becomes larger. Since is the requirement for the minimum harvested energy among G’s, it becomes more difficult to achieve as K increases. Therefore, with an increase of K, the solution for and in (13) becomes more oriented to the energy harvesting for achieving than the secure multicasting. Further, the increase of brings about the aggravation of this effect.
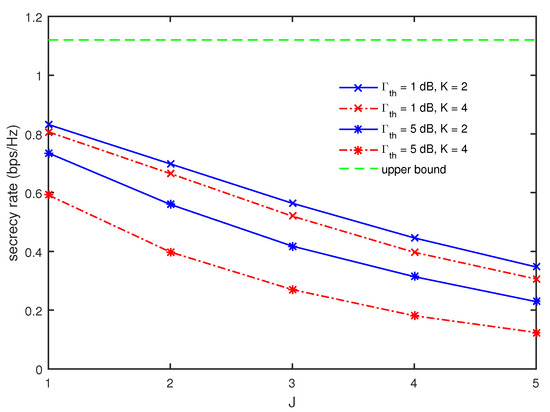
Figure 6.
Comparison of multicast secrecy rate as a function of J for different values of and K when , , and m.
6. Conclusions
In this paper, we considered simultaneous wireless power transfer and secure multicasting in cooperative DF relay networks, where multiple energy receivers and eavesdroppers are deployed. Two different scenarios were investigated such as maximizing the minimum harvested energy under a multicast secrecy rate constraint and maximizing the multicast secrecy rate under a minimum harvested energy constraint. For both scenarios, we showed that the transmit power allocation and relay weight design problems under a total power budget can be solved by a unified framework using semidefinite relaxation and bisection technique. We also presented numerical results to analyze the simultaneous energy harvesting and secure multicasting performances attained by the proposed schemes in cooperative DF relay networks.
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2016R1D1A1B03930599).
Author Contributions
J.-H. Lee and Y.-H. Kim conceived the idea of the proposed scheme and performed the modeling and simulation. I. Sohn provided substantial comments on the performance analysis of the proposed scheme.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
We derive the initial interval for the bisection technique in Section 3. We simply set the lower value of the initial interval as zero. For the upper value of the initial interval, it is reasonable to assume that the harvested energy with the secure multicasting constraint cannot exceed that without the constraint. In this viewpoint, we consider an optimization problem to maximize the minimum harvested energy among K energy receivers without the secure multicasting constraints shown as
Ignoring the rank constraint in (A1), we can obtain the solution , , and using SeDuMi [22] and Yalmip [23]. Here, we have to check the rank of . If the rank is one, is set to the initial upper value. Otherwise, we use the PFM to confirm the existence of a rank-one solution. As in Section 3, is used as a starting point for the iterative process of the PFM associated with the following semidefinite programming problem:
If the PFM provides a certificate to confirm that a rank-one solution is feasible, is set to the initial upper value. Otherwise, let us begin the bisection technique with the initial interval of . For the given interval , is chosen and the following feasibility problem is solved by using SeDuMi [22] and Yalmip [23]:
If (A3) is infeasible, we update . Otherwise, we check the rank of the solution for . If the rank is one, we update . Otherwise, we use the PFM to confirm the existence of a rank-one solution. If we can obtain a rank-one solution via the PFM, we update . Otherwise, we update . Until the width of the interval is small enough, the above process continues. After the iteration is terminated, we can obtain our initial upper value.
Appendix B
For the initial interval of the bisection technique in Section 4, the initial lower value is simply set to one. For the initial upper value, let us consider the multicast rate without the energy harvesting constraints in the absence of the eavesdroppers. Here, we solve the following optimization problem:
Let us ignore the rank constraint in (A4) to obtain the solution , , and using SeDuMi [22] and Yalmip [23]. Then, we check the rank of . If the rank is one, is set to the initial upper value. Otherwise, we perform the PFM for the given , , and . If the PFM provides a certificate to confirm that a rank-one is feasible, we set as the initial upper value. Otherwise, we begin the bisection technique with the initial interval of as in Appendix A. For the given interval , is chosen and the following feasibility problem is solved by using SeDuMi [22] and Yalmip [23]:
If (A5) is infeasible, we update . Otherwise, we check the rank of the solution for . If the rank is one, we update . Otherwise, we perform the PFM to confirm the existence of a rank-one solution. If we can obtain a rank-one solution via the PFM, we update . Otherwise, we update . Until the width of the interval is small enough, this process continues. After the iteration is terminated, we can obtain our initial upper value.
References
- Zhang, R.; Ho, C.K. MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless networks with RF energy harvesting: A contemporary survey. IEEE Commun. Surv. Tutor. 2015, 17, 757–789. [Google Scholar] [CrossRef]
- Zhang, H.; Du, J.; Cheng, J.; Leung, V.C.M. Resource allocation in SWIPT enabled heterogeneous cloud small cell networks with incomplete CSI. In Proceedings of the IEEE Global Communications Conference, Washington, DC, USA, 4–8 December 2016; pp. 1–5. [Google Scholar]
- Zhang, H.; Huang, S.; Jiang, C.; Long, K.; Leung, V.C.M.; Poor, H.V. Energy Efficient User Association and Power Allocation in Millimeter Wave Based Ultra Dense Networks with Energy Harvesting Base Stations. arXiv, 2017; arXiv:1704.07037v1. [Google Scholar]
- Li, Q.; Zhang, Q.; Qin, J. Secure relay beamforming for simultaneous wireless information and power transfer in nonregenerative relay networks. IEEE Trans. Veh. Technol. 2014, 63, 2462–2467. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Robust beamforming for secure communication in systems with wireless information and power transfer. IEEE Trans. Wirel. Commun. 2014, 13, 4599–4615. [Google Scholar] [CrossRef]
- Feng, R.; Li, Q.; Zhang, Q.; Qin, J. Robust secure transmission in MISO simultaneous wireless information and power transfer system. IEEE Trans. Veh. Technol. 2015, 64, 400–405. [Google Scholar] [CrossRef]
- Zhang, H.; Li, C.; Huang, Y.; Yang, L. Secure beamforming for SWIPT in multiuser MISO broadcast channel with confidential messages. IEEE Commun. Lett. 2015, 19, 1347–1350. [Google Scholar] [CrossRef]
- Khisti, A.; Tchamkerten, A.; Wornell, G.W. Secure broadcasting over fading channels. IEEE Trans. Inf. Theory 2008, 54, 2453–2469. [Google Scholar] [CrossRef]
- Zhu, B.; Ge, J.; Huang, Y.; Yang, Y.; Lin, M. Rank-two beamformed secure multicasting for wireless information and power transfer. IEEE Signal Process. Lett. 2014, 21, 199–203. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Schober, R.; Alnuweiri, H. Secure layered transmission in multicast systems with wireless information and power transfer. In Proceedings of the IEEE International Conference on Communications, Sydney, Australia, 10–14 June 2014; pp. 5389–5395. [Google Scholar]
- Li, J.; Petropulu, A.P.; Weber, S. On cooperative relaying schemes for wireless physical layer security. IEEE Trans. Signal Process. 2011, 59, 4985–4997. [Google Scholar] [CrossRef]
- Xing, H.; Chu, Z.; Ding, Z.; Nallanathan, A. Harvest-and-jam: Improving security for wireless energy harvesting cooperative networks. In Proceedings of the IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 3145–3150. [Google Scholar]
- Zhao, M.; Wang, X.; Feng, S. Joint power splitting and secure beamforming design in the multiple non-regenerative wireless-powered relay networks. IEEE Commun. Lett. 2015, 19, 1540–1543. [Google Scholar] [CrossRef]
- Luo, Z.; Ma, W.; So, A.; Ye, Y.; Zhang, S. Semidefinite relaxation of quadratic optimization problems. IEEE Signal Process. Mag. 2010, 27, 20–34. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Lee, J.-H. Confidential multicasting assisted by multi-hop multi-antenna DF relays in the presence of multiple eavesdroppers. IEEE Trans. Commun. 2016, 64, 4295–4304. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.O.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless information-theoretic security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Lin, P.-H.; Lai, S.-H.; Lin, S.-C.; Su, H.-J. On secrecy rate of the generalized artificial-noise assisted secure beamforming for wiretap channels. IEEE J. Sel. Areas Commun. 2013, 31, 1728–1740. [Google Scholar] [CrossRef]
- Zhang, H.; Xing, H.; Cheng, J.; Nallanathan, A.; Leung, V.C.M. Secure Resource Allocation for OFDMA Two-Way Relay Wireless Sensor Networks without and with Cooperative Jamming. IEEE Trans. Ind. Informat. 2016, 12, 1714–1725. [Google Scholar] [CrossRef]
- Sidiropoulos, N.D.; Davidson, T.N.; Lou, Z. Transmit beamforming for physical-layer multicasting. IEEE Trans. Signal Process. 2006, 54, 2239–2251. [Google Scholar] [CrossRef]
- Sturm, J.F. Using SeDuMi 1.02, a Matlab toolbox for optimization over symmetric cones. Optim. Methods Softw. 1999, 11–12, 625–653. [Google Scholar] [CrossRef]
- Lofberg, J. YALMIP: A toolbox for modeling and optimization in MATLAB. In Proceedings of the IEEE International Symposium on Computer Aided Control Systems Design, Taipei, Taiwan, 2–4 September 2004; pp. 284–289. [Google Scholar]
- Wang, H.-M.; Luo, M.; Yin, Q.; Xia, X.-G. Hybrid cooperative beamforming and jamming for physical-layer security of two-way relay networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 2007–2020. [Google Scholar] [CrossRef]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).