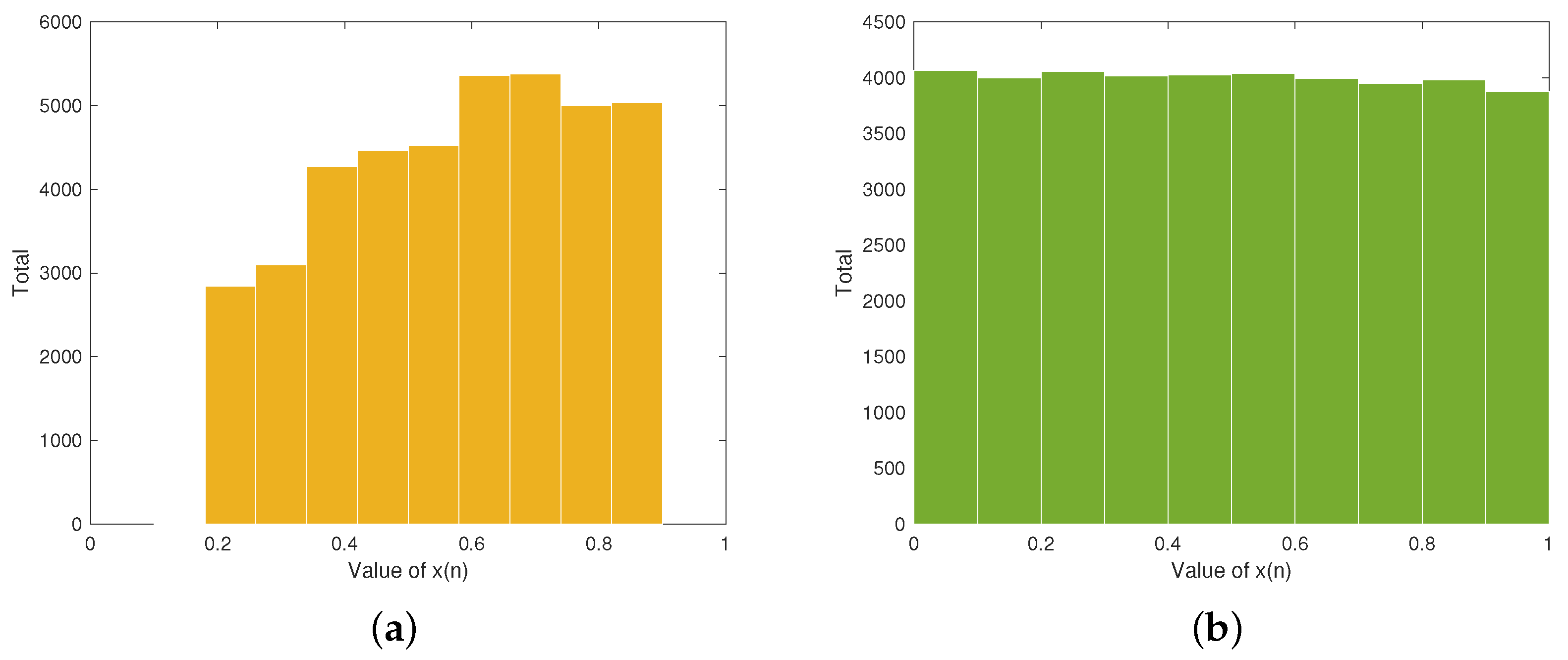1. Introduction
The extensive progress in digital communication and multimedia applications has made the protection of image data increasingly important [
1,
2]. Images carrying sensitive data are frequently transmitted over insecure channels, such as the internet. Due to its large size and high redundancy, traditional encryption methods designed for text may not be efficient or suitable for image data [
3]. Consequently, specialized IEAs have been developed to guarantee data confidentiality, integrity, and secure transmission [
4,
5]. These methods are widely used in medical imaging, military surveillance, cloud storage, and social media. However, existing encryption algorithms still have problems of weak security and low encryption efficiency. Therefore, there is an urgent need to design an exceptionally efficient and secure IEA.
Chaotic maps have the ability to produce highly unpredictable sequences, rendering them effective tools for disrupting the original structure of images. Because of their inherent sensitivity to initial conditions, unpredictability, and complex dynamic behavior, chaotic maps have garnered increasing attention and are anticipated to have a significant impact on modern image cryptosystems [
6,
7]. Naskar et al. introduced a robust IEA using a Tent map and cellular automata. This algorithm uses a Tent map and generates a dynamic key stream to encrypt image blocks, which enhances the overall security of the IEA [
8]. Wang et al. developed a new 2D chaotic system using a Sine map to enhance performance. However, this algorithm requires multiple iterations, which is time-consuming [
9]. Ghebleh et al. proposed an efficient IEA using chained skew Tent maps, in which the image is partitioned into multiple parts for encryption. This approach effectively disrupts the image data and improves the security [
10]. Sneha et al. developed an IEA using the Arnold map, Tent map, and Walsh–Hadamard transform. The Walsh–Hadamard transform is first applied to the image to spread the pixel values, thereby enhancing the diffusion effect. Then, the Arnold and Tent maps are used to permute the image, resulting in a desirable permuted effect [
11]. Mondal et al. integrated the skew Tent map with cellular automata as a key generator. Three pseudo-random numbers are generated for initializing cellular automata and the diffuse process [
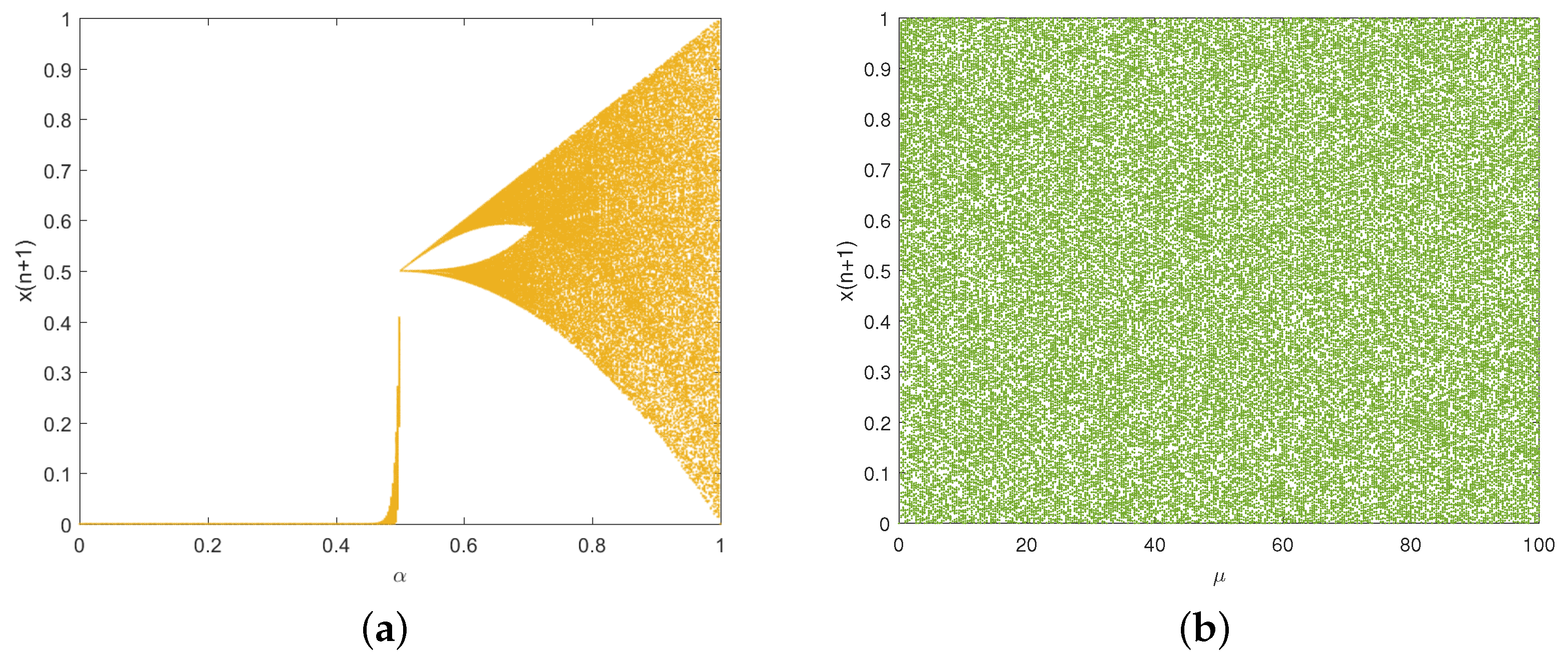
12]. However, the Tent map used in the above algorithm faces challenges such as discontinuity of chaotic intervals and the narrow chaotic range. To address these problems, we propose an improved Tent map that demonstrates continuous chaotic intervals and a broad chaotic range.
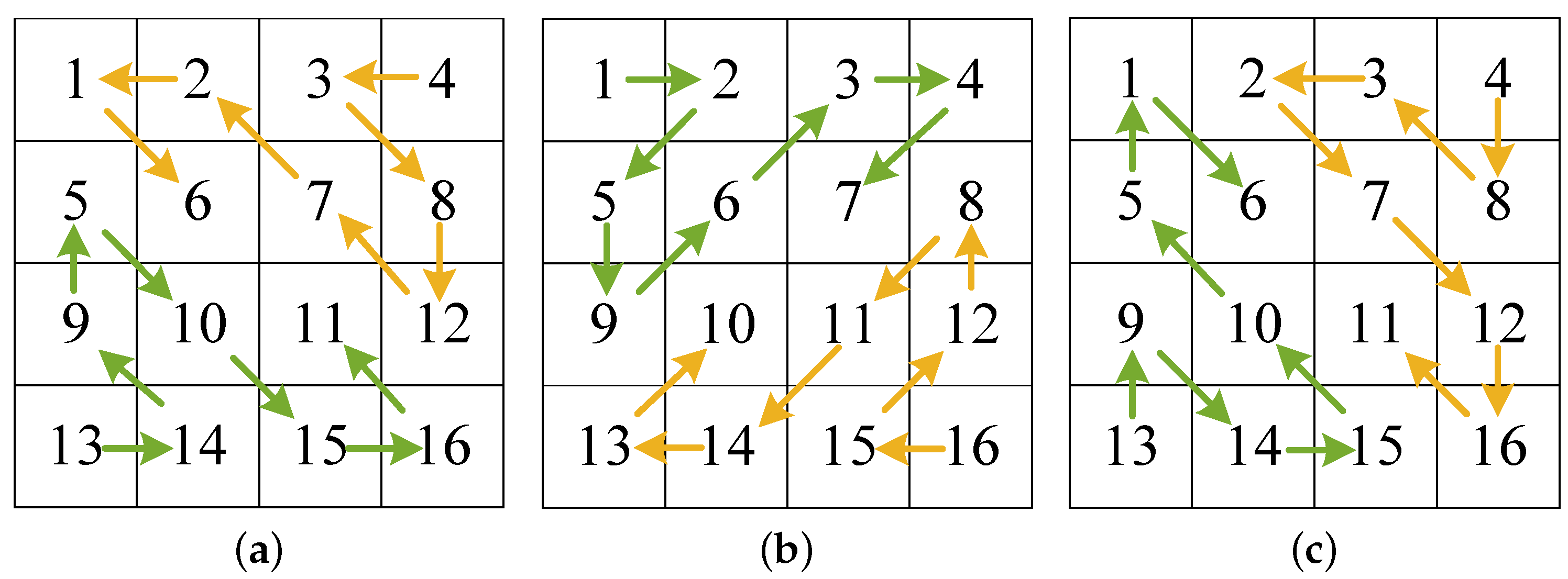
Permutation involves rearranging the pixel locations within an image, thereby disrupting its original structure and patterns [
13], which makes the image difficult to recognize. Permutation is essential in image cryptosystems because it obscures visual information, thereby enhancing security, unpredictability, and resistance to statistical analysis. Wang et al. provided an IEA using the Zigzag transform and dynamic row scrambling. This algorithm uses index sequences produced by the two designed 1D chaotic maps to scramble plain images. The Zigzag transform is applied to the lower and upper triangular sections of the permuted image to further improve the permutation effect [
14]. Hua et al. introduced a novel IEA that integrates an enhanced Zigzag transform with a value-differencing transform, which strengthens the algorithm’s security. The enhanced Zigzag transform uses chaotic sequences to generate a random scanning order, which enables more efficient pixel rearrangement [
15]. Wang et al. designed an IEA that first scrambles the image using an extended Zigzag confusion scheme. Then, RNA operations are applied to the scrambled image, where the RNA encoding and decoding processes are realized using chaotic sequences [
16]. Wang et al. segment the plain image into many blocks, and different Zigzag transforms are randomly selected for each block by using a cascaded chaotic map, thereby improving the randomness of the encrypted image [
17]. Although researchers have provided many improved versions of the Zigzag transform, the scrambled image still exhibits a strong correlation in the horizontal direction. To address this issue, this paper designs an improved Zigzag transform and its three variants through bidirectional scanning and cross methods.
Diffusion disperses the pixel values throughout the entire image, making it visually hard to recognize and preventing decryption through statistical or other analytical methods [
18,
19]. Teng et al. applied DNA diffusion to the facial region identified through face recognition, enhancing the diffusion of the image data, thereby significantly strengthening the overall encryption robustness [
20]. Zheng et al. developed an IEA that utilizes the Sine and Logistic maps. The image undergoes permutation using the Zigzag transform, followed by DNA addition and XOR operations for diffusion [
21]. Nezhad et al. cross-reconstructed the bit planes of images to make the distribution of image data more even. To strengthen the encryption effect, DNA subtraction, addition, and XOR operations can be dynamically selected using an operation control sequence [
22]. Lai et al. employed an integer wavelet transform and DNA coding for medical images. Then, the produced DNA sequence is shuffled using specialized DNA cubes to improve the security [
23]. Anisha et al. combine DNA coding with an 8D hyperchaotic system to encrypt patient image data. The plain image is subjected to block scrambling, followed by dynamic DNA coding and XOR operations, where the coding and operations processes are controlled by a chaotic sequence [
24]. However, using DNA coding alone as the diffusion method cannot provide sufficiently desirable diffusion effect. Therefore, this paper designs two new DNA operation rules and combines them with pixel-level diffusion method to enhance the diffusion effect.
In addition to the design of novel image encryption schemes, recent studies have also focused on analyzing their vulnerabilities through cryptanalysis. Chen et al. demonstrated that a DNA-based encryption scheme for DICOM images fails to withstand chosen-plaintext attacks [
25]. Feng et al. demonstrated that the 2D Logistic-adjusted-Sine-map-based scheme suffers from weak key sensitivity, improper key stream generation, and a flawed permutation process, allowing chosen-plaintext attacks to fully recover the original image without access to secret keys [
26]. Feng et al. conducted a detailed cryptanalysis of an image encryption scheme based on Feistel network and dynamic DNA encoding. They identify weaknesses in the secret key structure and encryption procedure and propose a targeted chosen-plaintext attack capable of fully recovering the plain image without secret keys [
27]. Therefore, our proposed algorithm enhances resistance to plaintext attacks by employing a redesigned chaotic map with a broader chaotic range, an improved Zigzag transform and its three variants, and dynamically DNA operations.
Despite significant advancements in image encryption algorithms, several limitations remain unresolved. Many existing schemes still suffer from weak diffusion mechanisms, insufficient permutation strength, and limited chaotic behavior, which compromises their robustness against statistical and differential attacks. In particular, conventional chaotic maps often demonstrate narrow chaotic intervals and low key sensitivity, while standard Zigzag-based permutation methods leave strong directional correlations. Similarly, DNA-based diffusion techniques, though promising, are typically constrained by a small set of fixed operation rules, reducing unpredictability. These challenges highlight a pressing need for more adaptive and secure encryption strategies.
Motivated by these limitations, we introduce a comprehensive IEA that integrates an improved chaotic map, enhanced Zigzag permutation techniques, and dynamic DNA operations. The proposed approach aims to generate highly unpredictable encryption sequences, thoroughly disrupt spatial pixel correlations, and enrich diffusion behavior. Through the joint use of a redesigned Tent map, a set of four Zigzag variants, and novel compound DNA operation rules, the method ensures strong resistance to various types of attacks while maintaining encryption efficiency.
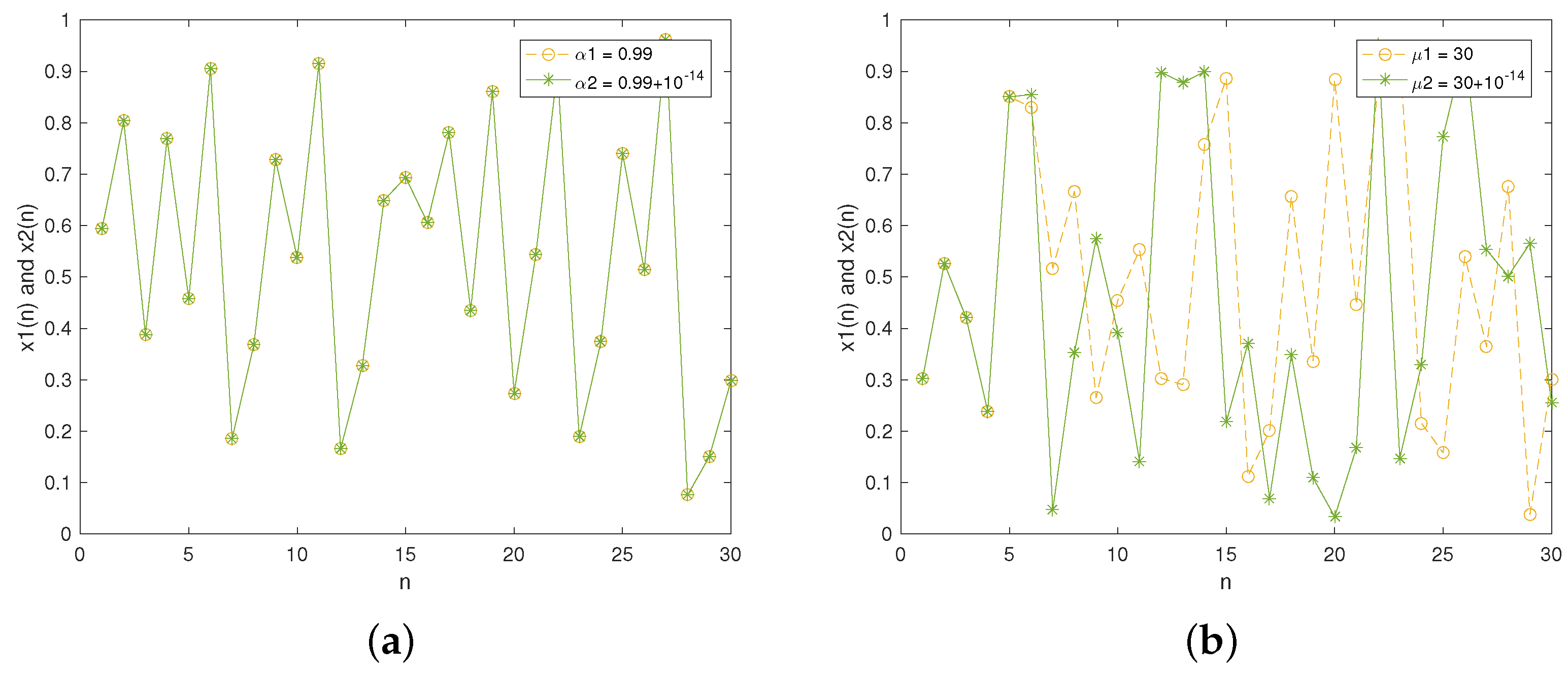
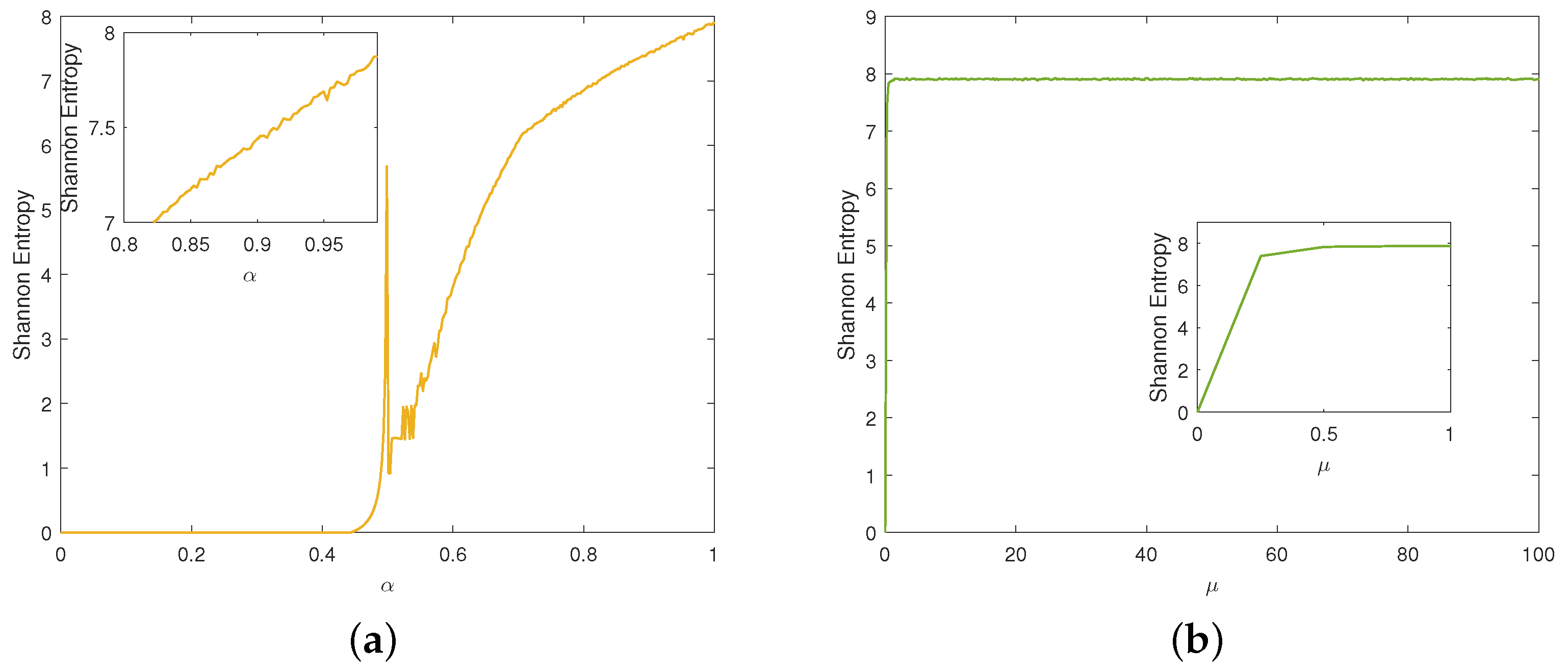
The contributions of our work include the following: (1) We design an improved Tent map by cascading the traditional Tent map and exponential function. Dynamics analyses demonstrate that it offers excellent randomness and complex chaotic behaviors. (2) To eliminate the limitations of the traditional Zigzag transform, we design an improved Zigzag transform and its three variants to enhance the scrambling effect. (3) To enrich the diversity of DNA operation rules, we design two novel DNA operations by compounding DNA addition and subtraction operations. (4) A two-layer IEA is proposed by combining the improved Tent map, improved Zigzag transform, and dynamic DNA coding, which can provide high-level security and efficiency. Through these innovations, our scheme achieves strong resistance against various plaintext and statistical attacks while maintaining computational efficiency.
The structure of this paper is as follows.
Section 2 introduces the improved Tent map and its dynamics analyses.
Section 3 presents the improved Zigzag transforms and our newly designed DNA operations.
Section 4 describes the proposed encryption and decryption algorithms.
Section 5 shows the experimental results and the security analyses. The conclusions are shown in
Section 6.
4. Proposed Encryption Algorithm
To ensure both strong security and high efficiency, we propose a novel IEA that integrates an improved Tent map, four variants of improved Zigzag transforms, and newly designed compound DNA operations. The improved Tent map provides continuous chaotic intervals, a broad chaotic range, and uniform sequence distribution. The Zigzag transform variants significantly enhance permutation complexity, while the compound DNA operations increase diffusion effectiveness.
4.1. Key Generation
The plain image is converted into a 256-bit binary hash value based on the SHA-256 algorithm. Next, the 256-bit binary is divided into groups of 8 bits, and each group is converted into its corresponding decimal form, resulting in 32 decimal hash values
. These values are then combined with three externally provided secret keys
and
to generate the initial values and control parameters of the improved Tent map. This hybrid method of key derivation enhances key sensitivity and expands the key space while preserving simplicity in hardware and software implementation. The key generation formula is provided in Equation (
7).
where ⊕ and
represent XOR and modulo operations, respectively.
4.2. Encryption Algorithm
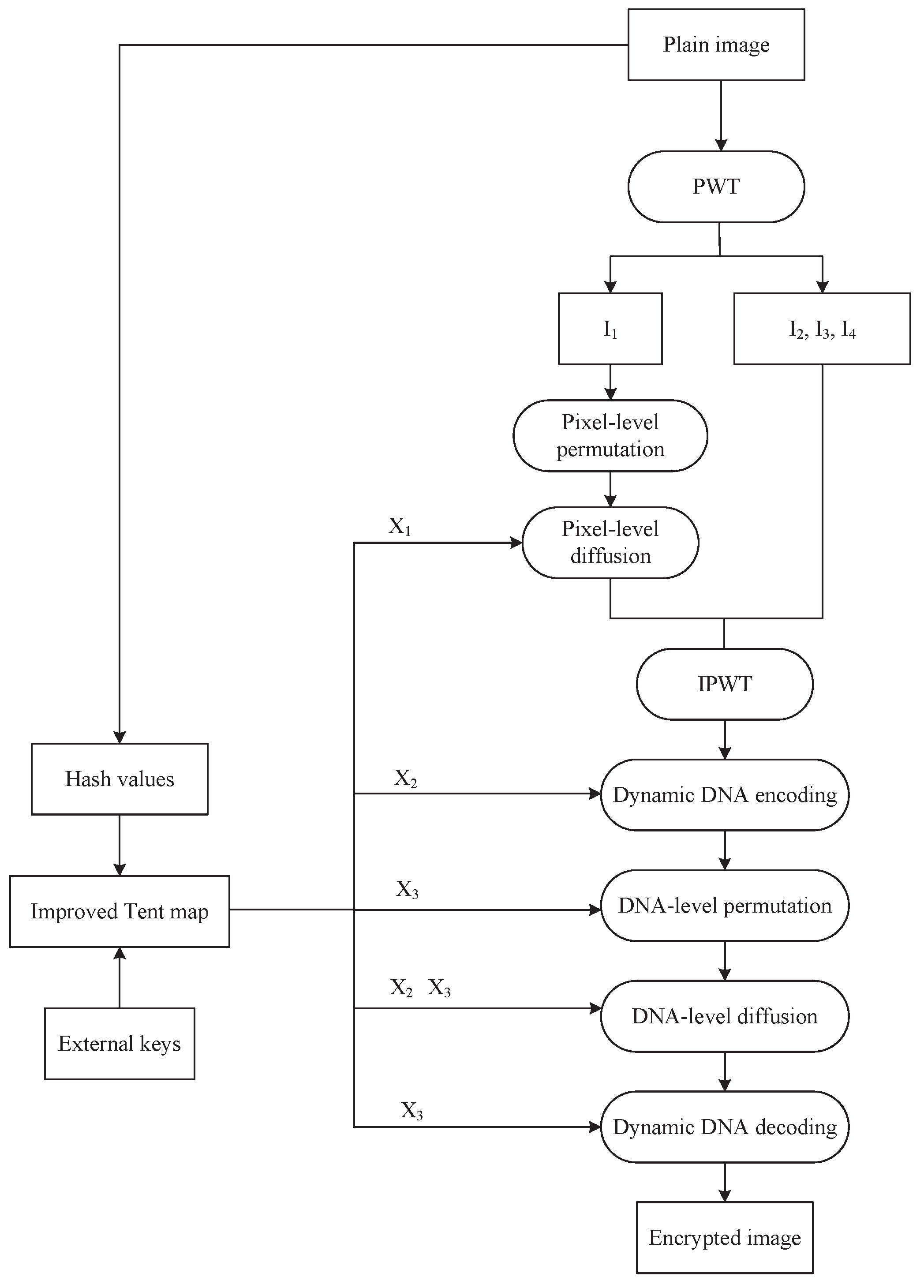
The encryption procedure is constructed in two layers—pixel-level and DNA-level encryption—to maximize entropy and enhance obfuscation. The proposed IEA begins with the application of the pseudo-wavelet transform (PWT) [
33]. Subsequently, pixel-level permutation and diffusion are performed to obtain a semi-encrypted image. Following that, we apply DNA-level permutation and diffusion to generate the encrypted image. The encryption process is depicted in
Figure 10.
- Step 1:
Chaotic sequence generation
We generate the initial values and control parameters
, and
according to Equation (
7). And then, three chaotic sequences
,
, and
are produced using the improved Tent map. The length of
is
, while the lengths of
and
are both
.
- Step 2:
PWT
Image P is decomposed using PWT to obtain four sub-images , , and , each of size .
- Step 3:
Pixel-level permutation
We randomly select one of the four improved Zigzag transforms using a chaotic sequence. The selection process involves calculating the mean value
x of
P, defined by Equation (
8). Then, we convert
x into
by Equation (9).
where
. Next, we permute the sub-image
using the improved Zigzag transform to generate
, which has a size of
.
- Step 4:
Pixel-level diffusion
We apply Equation (
10) to convert
into a pixel sequence
C. According to Equation (11), the diffused sub-image
D is obtained by XORing
with
C.
Subsequently, an inverse pseudo-wavelet transform (IPWT) is applied to
D,
,
, and
to generate image
, which has a size of
.
- Step 5:
Dynamic DNA encoding
We generate the encoding rule
according to Equation (
12).
where
denotes the absolute value function, and
denotes the round-down function. We perform dynamic DNA encoding on
to produce a DNA sequence
of length
.
- Step 6:
DNA-level permutation
is sorted to generate an index sequence
. Then,
is permuted according to Equation (
13) to generate a permuted DNA sequence
.
- Step 7:
DNA-level diffusion
We convert the chaotic sequence
into a DNA sequence
according to Equation (
14). The operation process utilizes four DNA operation rules: DNA addition and subtraction operations specified in
Table 3 and
Table 4, DNA ASC operation, and DNA SAC operation from
Table 5 and
Table 6. The inclusion of DNA-level operations significantly improves the diffusion strength and further increases the unpredictability of the encrypted image. The dynamic DNA operation rule
is generated from the chaotic sequence
, provided by Equation (15).
Dynamic DNA operations are performed using Equation (
16) and
is the DNA sequence after operations.
- Step 8:
Dynamic DNA decoding
We generate the decoding rule
according to Equation (
17).
Then, dynamic DNA decoding is performed on to generate a binary sequence of length 4 mn. After that, we convert into a decimal sequence of length . Finally, is reshaped into an encrypted image .
4.3. Decryption Algorithm
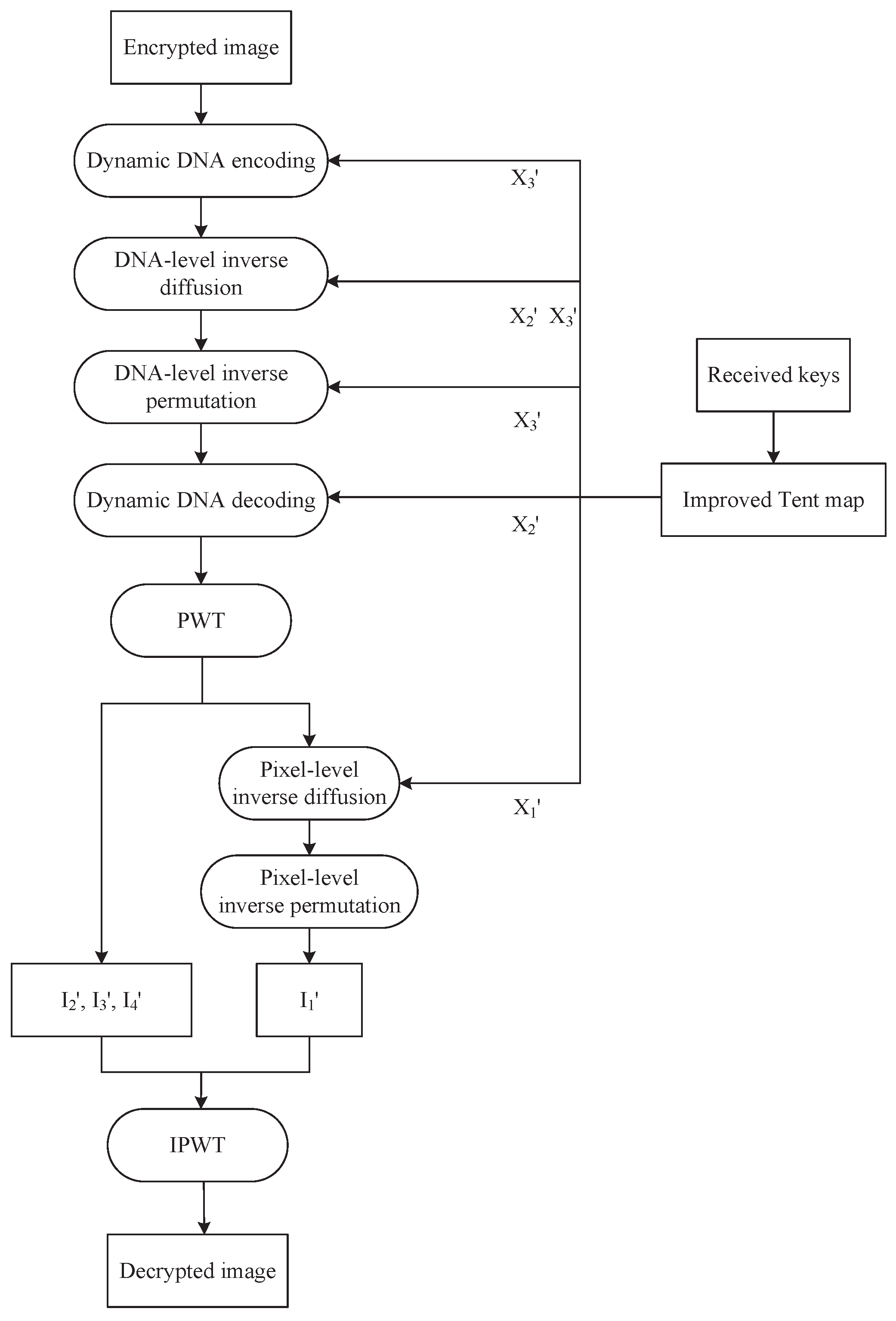
The decryption process is completely reversible, provided the keys and rules are correctly matched. This ensures both high security and lossless recovery of the original image.
Figure 11 shows the flowchart of the decryption process. We first apply dynamic DNA coding, DNA-level inverse diffusion, and permutation to obtain the semi-decrypted image. And then, pixel-level inverse diffusion and permutation are performed to generate the final decrypted image.
- Step 1:
Chaotic sequence generation
We generate three chaotic sequences , and using the improved Tent map and the received keys , and , where the length of is , the lengths of and are both .
- Step 2:
Dynamic DNA encoding
We reshape the encrypted image
into a vector
of length
and then convert
into a binary sequence
. The encoding rule
is generated according to Equation (
18).
Afterwards, dynamic DNA encoding is performed on
to generate a DNA sequence
.
- Step 3:
DNA-level inverse diffusion
is converted into a chaotic DNA sequence
according to Equation (
19).
The dynamic DNA operation rule
is generated from
, as illustrated in Equation (
20).
is the DNA sequence after inverse diffusion, and the inverse diffusion is performed using Equation (
21).
- Step 4:
DNA-level inverse permutation
We sort
to generate an index sequence
. Then,
is scrambled using DNA-level inverse permutation in Equation (
22), resulting in a DNA sequence
.
- Step 5:
Dynamic DNA decoding
The decoding rule
is generated by Equation (
23).
We perform dynamic DNA decoding on sequence to generate a decoded sequence of length .
- Step 6:
Pixel-level inverse diffusion
PWT is used to decompose
into four sub-images:
,
,
, and
, each with size
. Then, we use Equation (
24) to convert
into a chaotic DNA sequence
.
According to Equation (
25),
is obtained by XORing
with sequence
.
- Step 7:
Pixel-level inverse permutation
One of the four improved Zigzag inverse transforms are randomly selected for the inverse permutation. This process involves calculating the mean value
y of
, as shown in Equation (
26). And then, we convert
y into
by using Equation (27).
where
. Then, we permute
using the improved Zigzag inverse transform to generate
, which has a size of
.
- Step 8:
IPWT
IPWT is applied to sub-images , , , and , resulting in the decrypted image P.
6. Conclusions
With the increasing demand for privacy protection in image data transmission and storage, the design of secure and efficient image encryption algorithms remains a significant challenge. Many existing image encryption schemes struggle to achieve a satisfactory balance among security strength, randomness, computational efficiency, and real-time performance. To address these issues, we propose a novel IEA that integrates an improved Tent map, four variants of improved Zigzag transforms, and newly designed compound DNA operations.
The improved Tent map achieves outstanding chaotic performance by providing continuous chaotic intervals, broad chaotic range, and uniform sequence distribution. The improved Zigzag transform and its three variants provide flexible and effective scrambling strategies, significantly enhancing permutation complexity. Additionally, the incorporation of dynamic DNA encoding and two newly designed compound DNA operation rules increases diffusion capability.
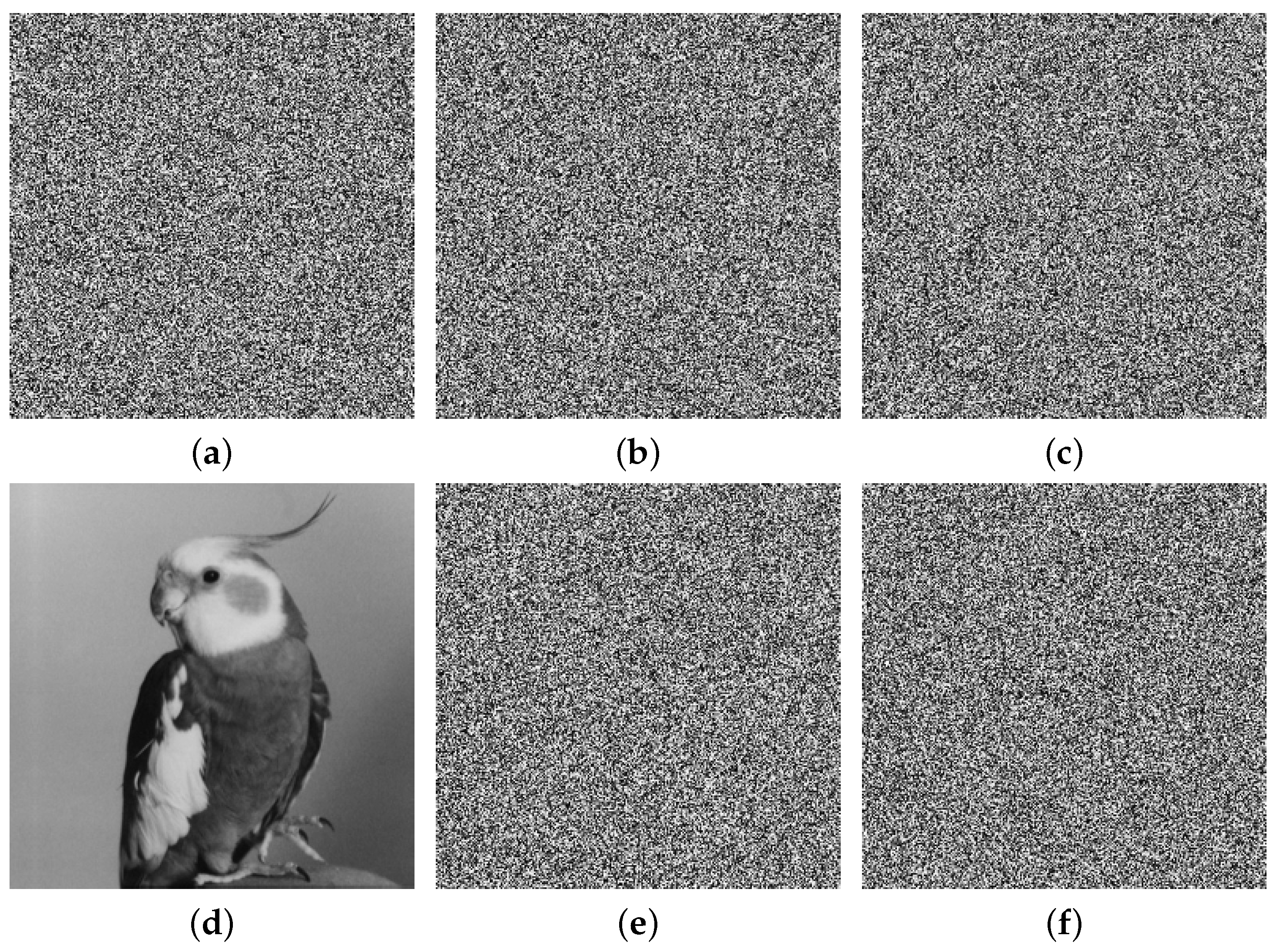
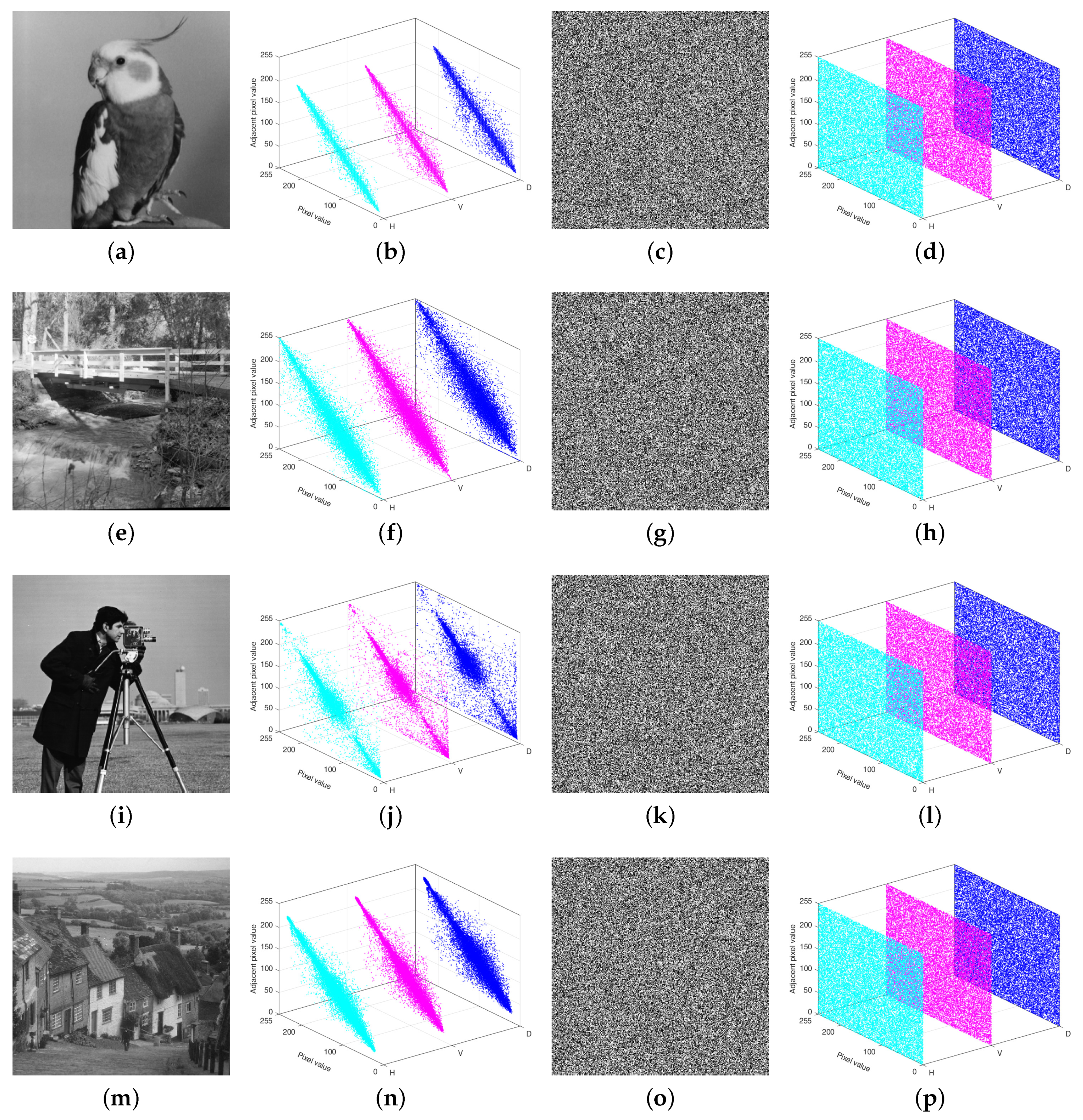
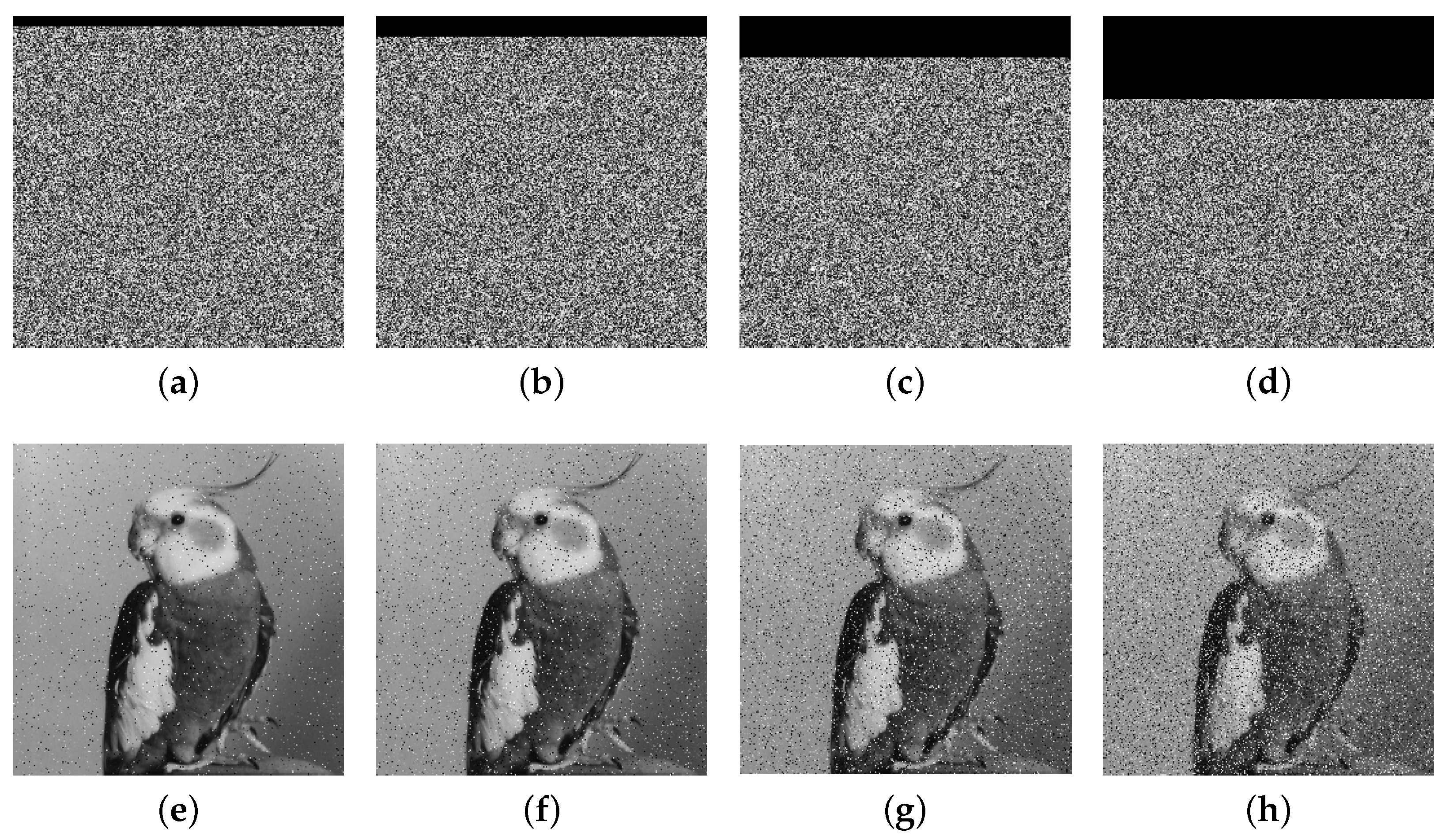
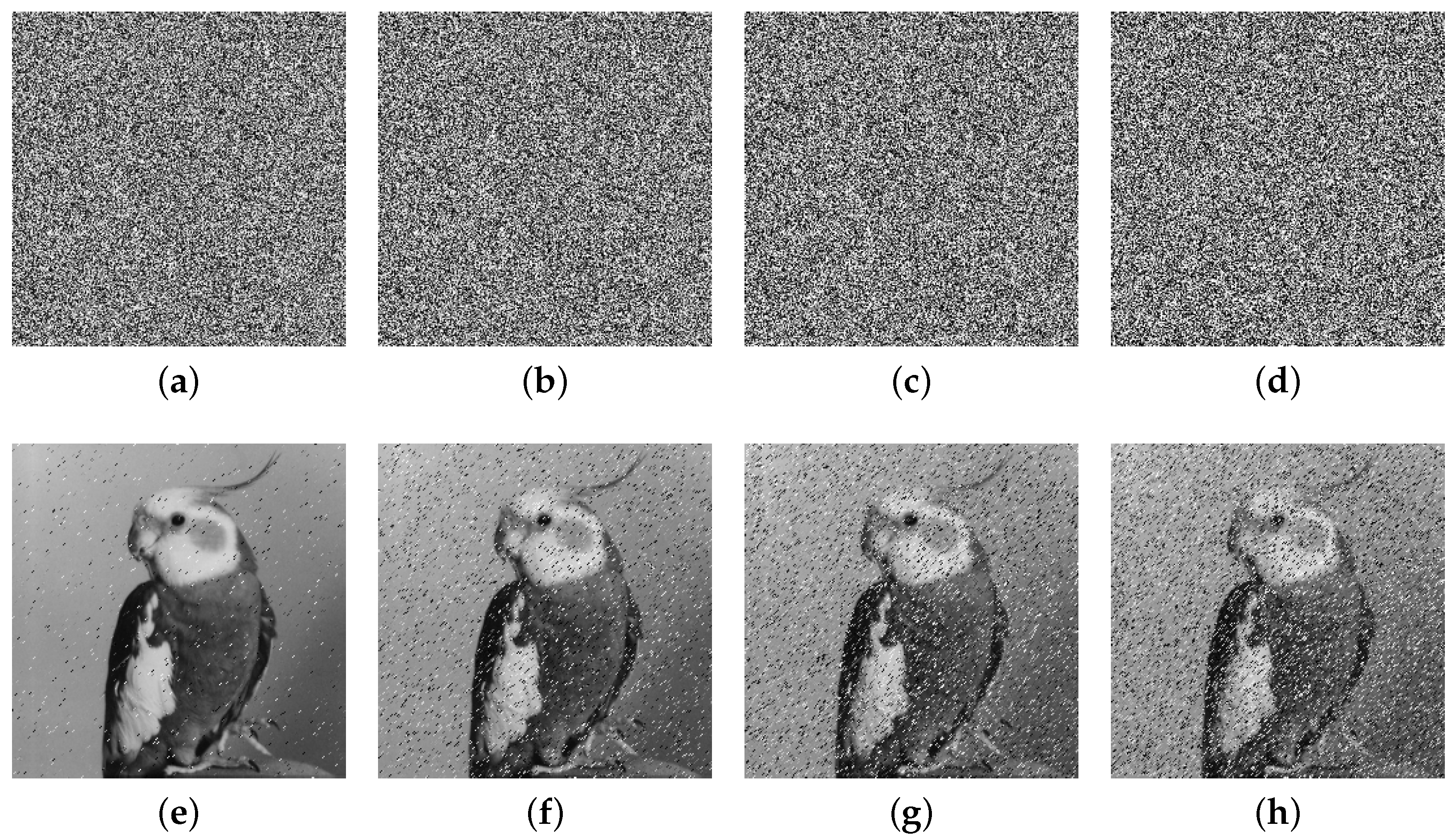
The extensive experimental results and security analyses demonstrate that the proposed IEA achieves excellent performance in terms of key sensitivity, information entropy, pixel correlation, resistance to differential attacks, and robustness under noise and cropping. The encryption time for a gray image is approximately 0.1509 s, confirming the algorithm’s suitability for real-time, high-security applications, such as medical image protection and secure communication in social platforms.
Despite these strengths, the current scheme is primarily validated on gray images. In future work, we plan to extend the algorithm to color images and video encryption, further optimize the execution time on resource-limited devices, and explore its integration with compression and watermarking technologies to support hybrid image security frameworks.