Abstract
Non-orthogonal multiple access (NOMA) is a promising technology for future beyond-5G wireless networks, whose fundamental information-theoretic limits are yet to be fully explored. Considering regular sparse code-domain NOMA (with a fixed and finite number of orthogonal resources allocated to any designated user and vice versa), this paper extends previous results by the authors to a setting comprising two classes of users with different power constraints. Explicit rigorous closed-form analytical inner and outer bounds on the achievable rate (total class throughput) region in the large-system limit are derived and comparatively investigated in extreme-SNR regimes. The inner bound is based on the conditional vector entropy power inequality (EPI), while the outer bound relies on a recent strengthened version of the EPI. Valuable insights are provided into the potential performance gains of regular sparse NOMA in practically oriented settings, comprising, e.g., a combination of low-complexity devices and broadband users with higher transmit power capabilities, or combinations of cell-edge and cell-center users. The conditions for superior performance over dense code-domain NOMA (taking the form of randomly spread code-division multiple access), as well as a relatively small gap to the ultimate performance limits, are identified. The proposed bounds are also applicable for the analysis of interference networks, e.g., Wyner-type cellular models.
1. Introduction
Non-orthogonal multiple access (NOMA) is a key enabler in the design of future overloaded beyond-5G communication systems with many more designated users than available physical resources, precluding the conventional orthogonal multiple access (OMA) paradigm [1,2,3,4] (see also [5] for a very recent technology review). The main potential appeal of NOMA over OMA stems from either supporting more simultaneous users or, in lieu, facilitating higher user throughputs when orthogonality is practically unsustainable. NOMA technologies generally comprise two main manifestations, power-domain NOMA and code-domain NOMA. Power-domain NOMA essentially relies on direct superposition of the transmitted signals, successive interference cancellation (SIC) at the receivers and appropriate power allocation to different users in order to achieve desired performance objectives [1,2,6,7]. Under the code-domain NOMA paradigm, the users’ signals are distinguished by different spreading signatures chosen to facilitate efficient multiuser detection (MUD) at the receivers (see, e.g., [2,8]). In particular, sparse NOMA, or low-density code-domain (LDCD) NOMA, has gained considerable interest in recent years due to its appealing attributes. Relying on sparse spreading signatures, sparse NOMA potentially facilitates enhanced spectral efficiency with practical receiver implementation based on sparsity exploiting iterative message passing algorithms (MPAs), similarly to the ones empowering the efficient decoding of low-density parity-check (LDPC) codes. The interested reader is referred to the insightful surveys [1,2] for details about the utilization of MPAs in NOMA, along with their concrete application for sparse NOMA [9,10,11], including sparse-code multiple access (SCMA) [12]. Different designs of sparse spreading signatures and their impact on MUD error-rate performance are discussed, e.g., in [11,13,14] and references therein.
Transmission schemes combining power-domain NOMA and SCMA were also recently proposed, e.g., in [15,16] for the cellular downlink channel and in [17,18,19,20,21] for the uplink channel. Therein, the main objective is to identify efficient centralized algorithms for joint resource and power allocation, that attempt to maximize the SCMA achievable throughput under independent Rayleigh fading and certain simplifying assumptions (viz., independent Gaussian signaling over each utilized physical resource, full synchronization and perfect channel state information). Fairness and quality-of-service constraints may also be incorporated into the optimization algorithm (e.g., [19,20,21]). The performance of the proposed algorithms is then evaluated by means of numerical simulations. More involved network configurations have also been considered recently, e.g., system models encompassing relays (see [22] and references therein for an exhaustive literature survey). Relaying may either appear in the form of dedicated network elements, e.g., [22,23] or, alternatively, by means of user cooperation, e.g., [24,25,26,27]. In this framework, focusing on power-domain NOMA with SIC, the notion of virtual full-duplex (VFD) relaying [28] has gained particular interest as means to circumvent the implementation challenges of true full-duplex operation; see, e.g., [22,25,26,27]. The impact of imperfect SIC and residual inter-relay interference in this framework was also recently considered in [26].
Notwithstanding their great practical promise and potential, sparse NOMA techniques often pose serious analytical challenges and their information-theoretic performance limits are not easily tractable even in the simplest settings. Typically, tools from random matrix theory or statistical physics are harnessed for their analysis [29,30,31,32], while considering the asymptotic large-system limit, where both the number of users and the number of available resources grow large, while retaining a fixed ratio (see, e.g., [33,34,35]). The obtained results typically yield excellent approximations for the expected performance with finite (and quite moderate) system dimensions [29,30].
Sparse NOMA is dubbed: regular when a fixed (and finite) number of orthogonal resources is allocated to any designated user and each resource is used by a fixed number of users; irregular when the respective numbers are random and only kept fixed on average [33]. In the literature, one can also find a partly regular version of the sparse NOMA setup where each user occupies a fixed number of resources and each resource is used by a random, yet fixed on average, number of users (or vice versa) [34,36].
In a recent line of works by the authors [37,38,39], the particular manifestation of code-domain NOMA known as regular sparse NOMA has been investigated and its asymptotic spectral efficiency has been derived in closed form [38,39] (see Section 2 for a precise characterization of the underlying asymptotic large-system limit and [38,39] for a discussion on what distinguishes this particular setting from previous analyses). Therein, a generic setup of a (non-fading) Gaussian vector multiple-access channel (MAC) with equal-power users was considered, representing the case of a single-cell uplink model with fully coordinated grant-based access, and the scheme was analytically proven to substantially decrease the gap to the ultimate capacity limit of overloaded systems. Furthermore, regular sparse NOMA was proven by the authors to outperform the dense code-domain NOMA alternative [40,41], along with its irregular and partly regular sparse counterparts [33,34]. Hence, regular sparse NOMA seems to exhibit a rare combination of information-theoretic superiority and computational feasibility (dense code-domain NOMA is operationally equivalent to randomly spread code-division multiple access (RS-CDMA) [40,41], for which achieving the optimal spectral efficiency becomes prohibitively complex in large systems [42]). However, analyzing the merits of regular sparse NOMA beyond the generic equal-power Gaussian vector MAC setting is still a challenging, yet of utmost importance, open problem, which does not seem to lend itself to closed-form characterization, as in [38,39].
Motivated by this noteworthy challenge, the current paper takes a step further towards a generalization of the fundamental result of [38,39]. To this end, the focus remains on regular sparse NOMA within a single-cell Gaussian uplink (MAC) model, but the single-class information-theoretic analysis of [37,38,39] is extended to a looser, yet more realistic, setting comprising two user classes distinguished by their received powers. Again, the large-system limit is considered and our main contribution is the derivation of closed-form bounds on the achievable class-rate (total throughput) region, which are both insightful and analytically tractable. An inner bound is first derived based on the standard conditional vector entropy power inequality (EPI) [43]. A derivation of an outer bound follows, while relying on a recent strengthened version of the EPI by Courtade [44,45]. Both bounds are tight with respect to the individual achievable class-throughput constraints and only differ in the achievable sum-rate (total throughput) constraint. The key tool in the derivations is a noise-split “trick”, that, when combined with the EPI, induces closed-form bounds expressed in terms of single-class achievable throughputs [38,39]. A simplified outer bound, which does not rely on the EPI, is then presented for load-symmetric settings (under some mild technical assumptions). This bound turns out to be tighter in certain cases. An in-depth elucidative investigation of the corresponding lower and upper bounds on the achievable sum rate in extreme-SNR regimes is also provided, which, by means of appropriate approximations [41], identifies conditions under which the bounds are useful and a superior performance over dense code-domain NOMA is guaranteed. Conditions for attaining a relatively small gap to the ultimate performance limits are also discussed.
Our contribution provides valuable insights into the potential performance gains of regular sparse NOMA in several timely use cases of interest. One particular example represents a 5G-and-beyond scenario, where the two user classes respectively correspond, say, to low-complexity devices with stringent power constraints (e.g., Internet-of-Things applications) and to broadband users with higher transmit power capabilities. Another applicable use case is a single cell with users located at the extremes of either the cell center or the cell edge. Our analysis is also applicable to a compelling combination of power-domain NOMA [2,6] and code-domain NOMA, which has only recently started to attract attention in the literature [15,16,17,18,19,20,21], as discussed above. Accordingly, the corner points of the achievable region bounds correspond to a SIC scheme between the two user classes, while incorporating near-optimal joint iterative decoding (MPA) within each class. In fact, by this interpretation, our analysis provides, in a sense, an analytical benchmark for the setting considered in [20] (see also [18]), under the simplifying assumptions of non-fading channels and full symmetry among the users in each user class. Note that, in the absence of fading, the corresponding regular SCMA achievable sum rate, while assuming independent Gaussian signaling over each utilized resource, trivially coincides with the Cover–Wyner sum capacity (see, e.g., [43] and Section 3.3). Hence, our analytical bounds quantify the gap from the ultimate performance limit induced by employing regular sparse spreading signatures and may serve as reference for practical schemes that aim to approach the sum-capacity limit using the SCMA paradigm, e.g., [17,18,19,20,21]. Note that, in the presence of fading, characterizing the achievable rate region of the two-user-class system considered in this paper is still a formidable open problem yet to be explored; hence, a direct and explicit comparison with practical achievable sum rates reported in works, such as [20], cannot be performed at this stage. Yet another applicable model is a two-cell interference network, where the two user classes represent, respectively, the local cell users and the users operating in the adjacent interfering cell. This may be further extended, e.g., to Wyner-type cellular models with single-cell processing [46,47,48,49].
This paper is organized as follows: Section 2 describes the underlying system model and the random graph models employed to construct the regular sparse spreading signatures. Section 3 presents a general statement of the class-throughput achievable region and the corresponding closed-form analytical inner and outer bounds. Section 4 is devoted to a comparative extreme-SNR characterization of the lower and upper bounds on the total achievable sum rate. Illustrative numerical results are provided in Section 5. Finally, Section 6 ends this paper with some concluding remarks. Detailed proofs and some technical observations are deferred to the appendices.
2. System Model
Notation: We use boldface lower-case letters to denote vectors and boldface uppercase letters to denote matrices. denotes the -th entry of the matrix . denotes the transpose of , while denotes the corresponding conjugate (Hermitian) transpose. ⊗ denotes the Kronecker product. denotes the N-dimensional identity matrix. designates the distribution of a proper circularly symmetric complex Gaussian random vector with mean and covariance matrix . designates the probability distribution of a single mass at x. Equality in distribution is denoted by , stating that the distribution of the random variables on both sides of the equality sign is the same. denotes statistical expectation and designates that the expectation is taken with respect to the distribution of the random variable X. denotes differential entropy and denotes mutual information. For any , we use the notation . Base-2 logarithms are used throughout this paper unless otherwise stated (in which case the base of the logarithm is explicitly designated). For the sake of clarity, we use to denote the natural logarithm.
We consider a MAC, representing a single-cell uplink, where the users belong to either of two different classes distinguished by their received powers (henceforth referred to as “Class 1” and “Class 2”). Within each class, all users are assumed to be received at the same power level. The users’ signals are multiplexed over N shared orthogonal dimensions (resources), which may represent, e.g., orthogonal time–frequency slots. However, it is important to emphasize here that the setting is quite general and applies to any orthogonal coordinate system; therefore, the dimensions are, by no means, restricted to the time–frequency domain. Let and denote the number of users in Class 1 and Class 2, respectively, and let , denote the respective loads (users per resource). The total number of users is denoted by and the total system load reads .
Focusing on a generic non-fading Gaussian channel model, the N-dimensional received signal at some arbitrary time instance reads
where , , is a -dimensional complex vector comprising the coded symbols of the users in Class i. Assuming Gaussian signaling, full symmetry, fixed powers and no cooperation among encoders corresponding to different users, the input vector is distributed as . The matrix represents the sparse signature matrix of Class-i users, where the kth column represents the spreading signature of user k in Class i. The non-zero entries of designate the corresponding user-resource mapping, namely, user k in Class i occupies resource n if . Specifically, we adhere to the regular sparse NOMA paradigm [37,38,39], where, for each Class i, , due to the sparsity of , only a few of the users’ signals collide over any given orthogonal resource. The regularity assumption generally dictates that each column of (respectively, row) has exactly (respectively, ) non-zero entries. However, for notational simplicity, we assume henceforth that , while noting that extension of the analysis to the case where and have a different fixed number of non-zero column entries is straightforward (hence omitted). Therefore, d takes the role of the system’s sparsity parameter. We assume here that is chosen so that , , in order to avoid degenerate settings. The non-zero entries of are assumed to be independent and identically distributed (i.i.d.), but may otherwise arbitrarily reside on the unit circle in the complex plane, in complete adherence to [38,39]. Thus, the normalization in (1) ensures that the columns of have unit norm. We also assume here that the signature matrices and are perfectly known at the receiving end and uniformly chosen, respectively, randomly and independently per each channel use and each user class i, from the set of -regular matrices. This assumption is only introduced here for the sake of concreteness and the setting, in fact, generalizes verbatim to the case where the signature matrix selection process is stationary and ergodic. Finally, denotes the N-dimensional circularly symmetric complex additive white-Gaussian-noise (AWGN) vector at the receiving end. Thus, the parameter in (1), , designates the received signal-to-noise ratio (SNR) of each of the users in Class i.
A key additional underlying assumption, which follows [38,39], is that the signature matrices can be associated with the adjacency matrices of certain random -semiregular bipartite (factor) graphs , with special properties to be stated next. To this end, we first introduce the following two definitions.
Definition 1
(Locally Tree-Like Graphs [50,51]). Let denote the space of rooted isomorphism classes of rooted connected graphs. A sequence of random graphs , , in the space , with a root vertex chosen uniformly at random from the vertex set of , is said to converge locally (weakly) to a certain random rooted tree , if, for each , the sequence of balls with radius r (in graph distance) around converges in law to in the space . A more precise mathematical definition can be found, e.g., in [50,51].
Definition 2
(Bipartite Galton–Watson Tree (BGWT) [50]). A Galton–Watson tree (GWT) with degree distribution is a rooted random tree obtained by a Galton–Watson branching process, where the root has offspring distribution and all other genitors have offspring distribution F, where (assuming )
A BGWT with degree distribution and parameter p is obtained from a Galton–Watson branching process with alternated degree distribution. Namely, with probability p, the root has offspring distribution , all odd generation genitors have an offspring distribution G (related to analogously to F) and all even generation genitors (apart from the root) have an offspring distribution F. Similarly, with probability , the root has offspring distribution and the offspring distributions of all odd and even generation genitors are switched. See [50] for a more elaborate discussion.
We now further assume that the random graphs associated with the signature matrices are locally tree-like and converge in the large-system limit to BGWTs having degree distribution and parameter as a weak limit, where . The term “large-system limit” refers here to the regime where while fixing , . We use henceforth the shorthand notation “” to designate this limiting regime.
From a practical perspective, it is important to note here that the aforementioned locally tree-like property is valid, e.g., for regular LDPC codes [50,52] and it essentially implies that, for large dimensions, short cycles are rare, which facilitates the use of iterative near-optimal multiuser detection algorithms (while applying MPAs over the underlying factor graphs). Moreover, the sparse signature matrices can in fact be constructed as weighted parity-check matrices of regular LDPC codes, which we, in fact, employ using Gallager’s construction [53] to produce the finite dimensional simulation results in Section 5 (see therein).
3. The Achievable Rate Region
3.1. Preliminaries
For the sake of completeness, we first review the main result of [38,39] (adapted to the current system model), which constitutes the basis for the analysis in the sequel. Let us consider a single-class channel model (cf. ( 1)) as follows:
Theorem 1
([38], Theorem 3). Let , , be a sparse random matrix with exactly (respectively, ) non-zero entries in each column (respectively, row), independent and identically arbitrarily distributed over the unit circle in . Assume that the -semiregular bipartite graph associated with is locally tree-like with the limiting properties specified in Section 2. Let and , . Further, let and , . Then, the normalized conditional input–output mutual information
converges, as , to
where (cf. [40])
and, for ,
Let denote the normalized spectral efficiency (total throughput) in bit/sec/Hz of the users in Class i, . Let denote the achievable region of rate pairs for the channel (1). Then, by the standard properties of the MAC capacity region (e.g., [43]), it follows that
In the large-system limit, the two constraints on the (class) individual rates can be characterized explicitly and in closed form by means of Theorem 1. Namely, the two bounds converge to the following limits:
Note that specifies, in the large-system limit, the normalized spectral efficiency with optimum processing in bit/sec/Hz of the users in Class i, given the signals transmitted by the users in Class j, [38,39]. However, unfortunately, a corresponding limiting result for the maximum achievable sum rate is still missing. Furthermore, the limit does not seem amenable to closed-form characterization. Therefore, we proceed, in the following sections, by deriving closed-form analytical lower and upper bounds on this quantity in the large-system limit. These bounds produce, in turn, corresponding inner and outer bounds on the achievable region which, as implied by (9), are tight in their individual rate constraints.
3.2. Inner Bound
Proposition 1.
Let us fix , , and let be defined as
Then, the rate region is achievable for the channel (1) in the large-system limit, as .
Proof.
See Appendix A. □
As shown in Appendix A, the parameter is introduced by a noise-split step required for applying Theorem 1 (see (A2)). The inner bound (10) can then be tightened by maximizing the sum-rate constraint over (which can be easily accomplished, e.g., by a straightforward grid-search over ). As a simple example, consider the extreme case where the receive SNR of either of the user classes vanishes. In such case, the optimized sum-rate constraint can be set arbitrarily close to the actual achievable sum rate. Specifically, assume, without loss of generality, that (with and fixed). Clearly, in such case, the achievable throughput of Class 2 users trivially satisfies . The sum-rate constraint in (10) then approaches the limit
which is indeed the maximum achievable sum rate in this extreme setting. In fact, the optimization with respect to turns out to be rather crucial, since poor choices of may lead to cases where not all rate constraints in (10) are active and the inner bound no longer specifies a pentagon in the -plane. As indicated by numerical investigations, this may occur in underloaded settings, which are of lesser interest in view of the expected use cases of the underlying NOMA setting.
3.3. Outer Bound
Proposition 2.
Let us fix such that , let , , and let satisfy
Then, the rate region includes the achievable region for the channel (1) in the large-system limit, as .
Proof.
See Appendix B. □
Analogously to the proof of Proposition 1, a noise-split step introducing the parameters is required for the applicability of Theorem 1 (see (A13)–(A15)) and the outer bound (12) can be tightened by minimizing the sum-rate constraint over the choice of , while satisfying . Here as well, a proper choice of and is crucial, as, otherwise, the sum-rate constraint may turn out too loose and become inactive.
To obtain more insight, it is also useful to consider the Cover–Wyner region, specifying the ultimate MAC capacity region (without any random-spreading constraint). In the current setting, the Cover–Wyner region reads [40]
and constitutes a trivial outer bound on the achievable region. A comparison to (13) can thus be used to identify settings where the outer bound of Proposition 2 is indeed useful. Note that (13) is also, in fact, the achievable region with a corresponding idealized SCMA scheme, where each user transmits independent Gaussian symbols over each of the utilized orthogonal resources; see, e.g., [20].
3.4. Alternative Outer Bound for Symmetric Loading
To complete the characterization of the achievable region, we further introduce an alternative outer bound, which applies to a particular symmetric construction of the signature matrices (henceforth dubbed, for conciseness, “symmetric construction”). The bound relies on a simple upper bound on the maximum achievable sum rate . Let us consider the case where and thus . With some abuse of notation, let us assume now that, in addition to the underlying assumptions of Theorem 1, the signature matrices and are constructed such that the matrix can be associated with the adjacency matrix of a locally tree-like -semiregular bipartite graph (see Definitions 1 and 2). Additionally, let have a BGWT with degree distribution and parameter as a weak limit. Analogously to Section 2, we assume here that the pair of matrices is randomly chosen uniformly and independently per each channel use from the set of matrices satisfying the above properties. Then, the following proposition holds.
Proposition 3.
Let the two user classes have equal sizes, corresponding each to a load . Let the signature matrices and be chosen according to the “symmetric construction”. Let be defined as
where is specified in (5). Then, the rate region includes the achievable region for the channel (1) in the large-system limit, as .
Proof.
Focusing on the sum-rate constraint, the underlying assumptions of the “symmetric construction” imply that the maximum achievable sum rate satisfies
where
is a random permutation matrix satisfying
and follows by symmetry with respect to and . Next, applying Jensen’s inequality, while relying on the convexity of the function, we obtain
where we define the average SNR as
yielding for the “symmetric construction”. The limit in (18) follows from Theorem 1. Combining (18) with (9) finally yields (14), which completes the proof. □
4. Extreme-SNR Characterization
To complement the analytical characterization of the achievable rate region by means of the bounds in Propositions 1–3, we focus on the achievable sum rate and provide, in this section, an in-depth investigation of the respective bounds in extreme-SNR regimes. Although all bounds take an explicit closed form, the corresponding expressions are still rather involved. Therefore, the main advantage of the extreme-SNR characterization is that, by means of certain simplifying approximations (appropriate for extreme SNRs), it leads to valuable insights that are otherwise hard to obtain, as is shown in the sequel. In particular, this characterization demonstrates the impact of the parameters used in Propositions 1 and 2 on the tightness of the respective lower and upper bounds on the achievable sum rate. For symmetric settings (see Section 3.4), it further allows us to identify which of the two upper bounds on the achievable sum rate stated in Propositions 2 and 3 is tighter; hence, the corresponding outer bound is more useful for characterizing the achievable region in extreme-SNR regimes. For the low-SNR regime, we specify conditions under which the former bound of Proposition 2 is tighter, while, for the high-SNR regime, it turns out that Proposition 3 generally provides a tighter bound in symmetric overloaded settings.
Our analysis examines the achievable sum rate as a function of (the average SNR), as defined in (19). Furthermore, without loss of generality, we assume henceforth that for some . This immediately implies (cf. (19)) that
where
Starting with the low-SNR regime, the achievable sum rate is approximated as
where denotes the low-SNR slope, is the minimum system average that enables reliable communications and [41]. The average SNR and are related via
Let denote the achievable sum rate expressed as a function of in nats/channel use per dimension. Then, the minimum that enables reliable communications and the low-SNR slope read [41]
where and denote the first and second derivatives at zero of (note that (22), (24) and (25) tacitly assume that the minimum corresponds to the point of vanishing rate; a short discussion on this aspect is provided in Appendix D).
Turning to the high-SNR regime, we approximate the achievable sum rate as [41]
where denotes the high-SNR slope (multiplexing gain) and denotes the high-SNR power offset. Note that we use here a slightly different high-SNR approximation than the one originally proposed in [41], in the sense that it relies on approximating the sum rate as a function of (rather than ); consequently, the resulting high-SNR power offset differs by a term when compared to [41].
In the following sections, we employ the above approximations for the lower and upper bounds on the achievable sum rate and derive the corresponding extreme-SNR parameters. Specifically, we consider the sum-rate bounds in (10) and (12), which, when rewritten as functions of , read
where we introduce the notation
For symmetric settings, we additionally rely on ([38], Proposition 5; see also [39], Proposition 4) for the extreme-SNR characterization of the sum-rate bound in (14).
Furthermore, note that the sum capacity (specifying the ultimate performance limit) is given by the sum-rate constraint in (13), which, when expressed as a function of , boils down to
Hence, the corresponding low-SNR parameters are
while the high-SNR parameters read
4.1. The low-SNR Regime
Starting with the sum-rate lower bound (27), its low-SNR characterization is summarized in the following proposition.
Proposition 4.
The low-SNR parameters of the asymptotic sum-rate lower bound (27) read
where, as in Proposition 1, and .
Proof.
See Appendix C. □
As implied by Proposition 4, the sum-rate lower bound optimization with respect to (see Section 3.2) takes a more explicit form in the low-SNR regime. Specifically, the low-SNR slope (34) can be optimized by choosing such that the denominator therein is minimized; namely, by setting
To demonstrate the usefulness of this observation, while simplifying the discussion, let us consider the symmetric setting where . Then, the optimal choice for reduces to
which yields
Substituting back into (34), while accounting for the class-symmetry and setting
we obtain (following some algebra)
Note that is strictly lower, for all , than the corresponding low-SNR slope of the optimum spectral efficiency (total throughput) in a single-class setting with load and an SNR that equals , as specified in Theorem 1, which reads ([38], Proposition 5; see also [39], Proposition 4)
In fact, (40) also specifies the low-SNR slope of the sum-rate upper bound for the “symmetric construction”, as stated in Proposition 3 (cf. (14)). Hence, (39) and (40) provide compact lower and upper bounds on the low-SNR slope of the achievable sum rate under class symmetry. Another interesting comparison is with the low-SNR slope of the maximum achievable sum rate with RS-CDMA, representing a practical manifestation of random dense NOMA (see Appendix G for a derivation of the RS-CDMA achievable region). For the symmetric setting, this slope reads (following (A110), (A114) and ([41], Equation (147)))
which lets us conclude that , as long as
hence, regular sparse NOMA is guaranteed to strictly outperform RS-CDMA in the low-SNR regime as long as (42) is satisfied. Note, e.g., that setting immediately implies that (42) is satisfied for all .
Turning to the sum-rate upper bound (28), its low-SNR characterization is summarized in the following proposition.
Proposition 5.
Proof.
See Appendix D. □
Analogously to the characterization of the lower bound in Proposition 4, the low-SNR slope (45) can be optimized by choosing such that the denominator therein is maximized; namely, by setting
Note that, for , the low-SNR slope is strictly smaller than (recall that ); hence, the upper bound (28) is useful in this region of the parameters.
Additional insight can be gained by focusing again on the symmetric setting . In such case, we obtain that the optimal choice for simplifies to the following:
Note that, in fact, for , the condition that specifies the set simplifies to . Then, rewriting the low-SNR slope (45) as
we conclude that the sum-rate upper bound (28) implied by Proposition 2 is tighter in the low-SNR regime than the corresponding simple “symmetric construction“ bound in (14), as long as there exists a pair of constants such that (cf. (40))
Note that the existence of such constants is not guaranteed for all choices of the underlying parameters. To see this, let and let us recall that, since , the ratio must satisfy . Then, (49) can be rewritten as
or, equivalently,
where and
Now, a careful examination of the constants , and reveals that a necessary condition for (51) to hold is
That is, the sum-rate upper bound (28) can be tighter than the corresponding “symmetric construction“ upper bound in (14) only if is relatively low. To determine sufficiency, let us consider the polynomial . Then, it can be verified that, subject to condition (55), the coefficients , and satisfy
Let and denote the roots of , namely,
Then (noting that ),
and it turns out that, in addition to (55), condition (51) can only hold if the following additional conditions are satisfied:
4.2. The High-SNR Regime
As in Section 4.1, we start with the sum-rate lower bound (27) and derive its high-SNR characterization while focusing on the case where at least one of the two user classes is overloaded. For concreteness, we assume henceforth that . Our main observations are summarized in the following proposition.
Proposition 6.
Assume that . Then, the high-SNR parameters of the asymptotic sum-rate lower bound (27) read
and
where , , denotes the high-SNR power offset of a single-class setting with load (corresponding to Theorem 1), which reads ([38], Proposition 5)
Proof.
See Appendix E. □
Remark 1.
Analogous results for the case where the load is constrained to satisfy , as well as the case where , can be straightforwardly derived following similar lines to the proof in Appendix E. The details are omitted for conciseness. Note also that, for the case where both user classes are underloaded (i.e., ), the corresponding derivation indicates that the sum-rate lower bound is too loose in the high-SNR regime and fails to capture the correct high-SNR slope.
Remark 2.
The high-SNR characterization of the sum-rate upper bound (28) is summarized next.
Proposition 7.
Proof.
See Appendix F. □
Remark 3.
Note that, for , the high-SNR parameters of the sum-rate upper bound turn out to be independent of the choice of . Derivations along the lines of Appendix F reveal that, for , the sum-rate upper bound follows the correct high-SNR slope only if , namely, when the (overall) system operates in the underloaded (or fully loaded) regime, which is of lesser interest in the NOMA framework. Furthermore, the analysis shows that, for all other choices of and (expect for ), the sum-rate upper bound (28) becomes too loose for the high-SNR regime and does not capture the correct high-SNR slope.
To gain more insight, let us consider the symmetric overloaded setting where . In such case, the high-SNR slope equals unity for both the lower and upper sum-rate bounds, namely,
Turning to the high-SNR power offset, note that, in the symmetric overloaded setting, one obtains (cf. (21))
while
Hence, we conclude, from (61) and (67), that
Similarly, considering the high-SNR power offset of the sum-rate upper bound (64), we obtain
The difference between the offsets (68) and (69) specifies the horizontal gap (in logarithmic scale) between these lower and upper bounds on the achievable sum rate in the high-SNR regime. However, it is also insightful to compare to the corresponding high-SNR power offset induced by the “symmetric construction” outer bound of Proposition 3 (see (14)). This offset is simply given by (62), while substituting instead of , and reads
Note that
which can be verified to always take on negative values for and (in fact, in such case, is even strictly smaller than (32)). Hence, we conclude that the “symmetric construction” sum-rate upper bound is tighter in the high-SNR regime for symmetric settings, when . This observation is corroborated by the numerical results presented in Section 5.
5. Numerical Results
In this section, we present some numerical results that demonstrate the effectiveness of the inner and outer bounds derived in Section 3 for assessing the potential performance gains of regular sparse NOMA. The focus here is on overloaded settings (), corresponding to use cases where NOMA is of particular interest, while noting that the bounds also generally apply to underloaded regimes. The sparsity parameter d of the signature matrices was set throughout to , since, as shown in [38,39], it induces the highest achievable individual (per class) throughputs for regular sparse NOMA. Our numerical investigation complements the analytical observations of Section 4, by considering more general SNR regimes.
Figure 1 depicts the inner and outer bounds on the achievable region (8) in the large-system limit, for the case where and (cf. (10) and (12)). The corresponding noise-split parameters were set to , and (these values were numerically verified to be close to optimal). The SNRs of the two user classes were fixed to and . The cautious reader should note that this choice for the noise split parameters is, by no means, a contradiction to the condition specified in Proposition 5 for the usefulness of the outer bound (see (43)). This is since Proposition 5 only applies to the low-SNR regime, while, in Figure 1, the two SNRs do not yield a low average SNR setting. In fact, it can be numerically verified that choosing in the low-SNR regime, which falls outside the region in (43), leads to a very loose upper bound on the achievable sum rate, significantly higher than the corresponding Cover–Wyner sum-rate upper bound in (13). Hence, this choice is not useful in the low-SNR regime as predicted by Proposition 5 (see also the discussion in Section 4.1). The boundary of the inner bound is represented Figure 1 by the dashed black line, while the boundary of the outer bound is designated by the dash–dotted black line. Note that the two bounds differ only in the sum-rate constraint, while sharing the class–individual rate constraints (which are characterized in full via Theorem 1, as discussed in Section 3.1). To assess the tightness of the bounds, Figure 1 also shows an estimation of the boundary of the achievable region (8) for a regular sparse NOMA system with a large but finite number of orthogonal dimensions . Here, all rate constraints of the corresponding region were evaluated based on Monte Carlo (MC) simulations of 1000 sparse matrix realizations using Gallager’s construction for parity-check matrices of LDPC codes [38,39,53] (let us recall that the main motivation for the derivation of the inner and outer bounds on the achievable region is the fact that an exact analytical asymptotic result for the sum-rate constraint of this region is still lacking; hence, we resorted to MC simulations). The boundary of this region is represented by the solid blue line. Note that both inner and outer bounds are rather tight and provide a very good assessment of the achievable region (specifically, the limiting upper bound on the sum-rate constraint is higher than the simulated constraint by about only , while the corresponding lower bound is lower by less than ). Figure 1 also indicates that the asymptotic class–individual rate constraints provide an extremely tight assessment of the corresponding throughputs in large finite-dimensional systems, as already shown in [38,39]. We further note that extensive numerical investigations indicate that the EPI-based bounds become tighter as the powers allocated to each class of users become more unbalanced, which stems from the nature of the EPIs. This observation is further demonstrated in the sequel.
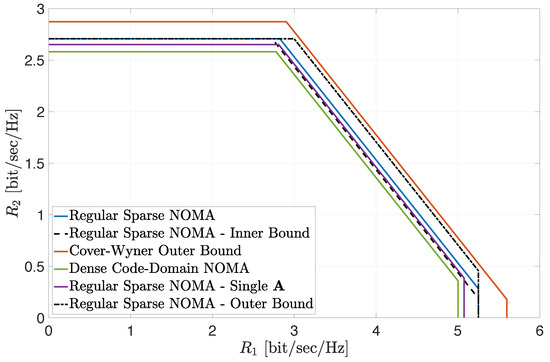
Figure 1.
Achievable regions for , , , and .
For the sake of comparison, Figure 1 also includes the achievable regions of two other system settings of interest. The first region corresponds to dense code-domain NOMA, represented here by RS-CDMA. The corresponding boundary of the achievable region in the large-system limit is designated by the solid green line (see (A119) in Appendix G). The second region corresponds to a setting where the signatures of individual users are taken as the columns of a single regular sparse matrix, where each user occupies resources and each resource is utilized by exactly users. No regularity is imposed within either of the two classes of users and the signature columns are allocated to the users in each class uniformly at random. The induced signature matrices and for each class of users (after reordering of the columns) are therefore no longer row-regular. The boundary of the corresponding achievable region, based on MC simulations (while fixing ), is designated by the solid purple line (referred to as ‘Single ’). Finally, Figure 1 also shows the Cover–Wyner region (13). The boundary of this region is designated by the solid red line.
A comparison of all achievable regions in Figure 1 lets us conclude the following (with the aid of additional investigations omitted for conciseness): Irregularity induces a loss in the achievable rate region. This is clearly observed when comparing the achievable region with a single regular sparse signature matrix construction (‘Single ’) and the MC-based achievable region with two separate regular constructions of the signature matrices for the two classes of users. The superiority of separate constructions is also observed for the class–individual rate constraints when considering the inner bound (10). Comparing the regular sparse construction in (1) and dense code-domain NOMA (here, RS-CDMA), the MC simulation results indicate that the corresponding achievable region strictly includes the achievable region with dense code-domain NOMA, in full agreement with the analytical observations made in [38,39] with respect to single-class systems. Furthermore, when the class-powers are far enough apart, this even holds for the inner bound (10), as shown in Figure 1, implying that regular sparse NOMA indeed strictly outperformed dense code-domain NOMA (RS-CDMA) in this setting. Finally, considering the outer bound on the achievable region (12), Figure 1 shows that, for power-unbalanced settings, it provides a good assessment of the gap to the ultimate performance limits, as designated by the Cover–Wyner capacity region.
The impact of the SNR balance between the two classes of users is illustrated in Figure 2. A load-symmetric setting is considered where and the received SNR of Class 1 users was set to . The received SNR of Class 2 users was set to , where . The figure depicts the sum-rate constraint of the rate region for the settings and bounds considered in Figure 1 as a function of . The lower and upper bounds, according to (10) and (12), were numerically optimized, respectively, by fine-tuning the values of , and . In view of the load-symmetry in this example, the “symmetric construction” upper bound in (14) is also included in the figure (designated by the dotted line). Similar conclusions to the ones discussed with respect to Figure 1 can be reached. The tightness of all three bounds is clearly demonstrated in the low region. In particular, note that a threshold value for is observed, below which the sum-rate lower bound in (10) already surpasses the dense code-domain NOMA achievable sum rate (thus guaranteeing the superiority of regular sparse NOMA). The results also indicate that the sum-rate upper bound in (12) is meaningful and resides below the Cover–Wyner sum capacity, when lies below a threshold (while, otherwise, it becomes too loose and ceases to be useful). Note that, in this load-symmetric setting, the simple “symmetric construction” upper bound in (14) turns out to be the tightest for most values of . In fact, by Jensen’s inequality, it also provides here a tight upper bound for the ‘Single ’ construction. However, neither of the two upper bounds (in (12) or (14)) is universally superior. Although Figure 2 does not represent an extreme-SNR regime per se, the main observations qualitatively corroborate the conclusions of the analytical examination in Section 4.
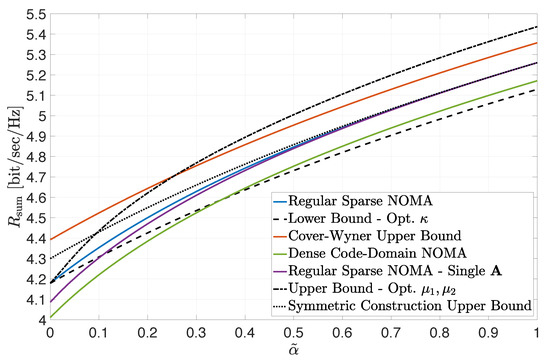
Figure 2.
Achievable sum rate for , (), , and . Bounds are plotted for numerically optimized , , .
Finally, the preceding observations are further corroborated in Figure 3, where a setting with , and is considered (similarly to Figure 1). Here, the sum-rate constraints depicted in Figure 2 (excluding the “symmetric construction” upper bound (14)) are plotted as a function of the system average (see (19) and (23)). The tightness of the derived bounds over a wide range of values is clearly demonstrated, as well as the superior performance of regular sparse NOMA compared to dense code-domain NOMA (which yields lower sum rates for all values). Again, the results are in full agreement with the conclusions of Section 4 regarding extreme-SNR regimes.
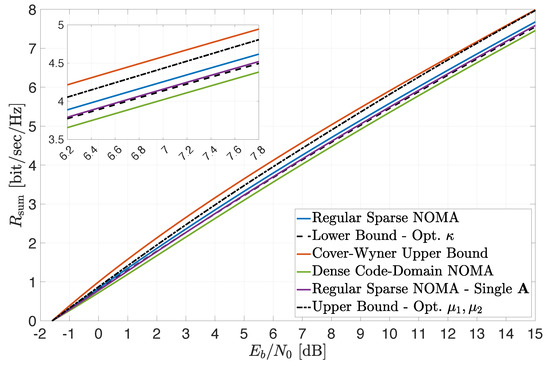
Figure 3.
Achievable sum rate for , , and . Bounds are plotted for numerically optimized , , .
6. Conclusions
We investigate, in this paper, the achievable rate region in the large-system limit of regular sparse NOMA with two user classes. The analytical challenges induced by the underlying random matrix model were circumvented by deriving closed-form inner and outer bounds on the achievable region. These bounds provide a valuable assessment of the potential performance gains of regular sparse NOMA in use cases of interest beyond the equal-power setting previously considered in [38,39]. The superiority of regular sparse NOMA compared with highly complex dense alternatives is demonstrated. The analytical characterization of the bounds in extreme-SNR regimes further elucidates their usefulness, while exhibiting the benefits of their closed-form expressions.
It is important to recall, at this point, that regular sparse NOMA requires fully coordinated signatures (to retain the regular structure of the signature matrices); therefore, it might be inapplicable to massive connectivity use cases with sporadic user activity, where such coordination cannot be practically accomplished. Hence, to complement the current analysis, a similar setting with two mixed classes of users, where one class employs regular sparse NOMA and the second class employs random dense NOMA, was recently considered in [54]. For this representation of a mixture of fully coordinated and lightly coordinated users, the achievable region was completely and rigorously characterized using fundamental tools from free probability theory [30,55]. Potential extensions of both lines of work to account for multiple user classes and multicell networks, as well as the impact of fading and additional channel impairments, are the subject of current and future planned investigations.
Author Contributions
Conceptualization, B.M.Z., O.S. and S.S.; methodology, B.M.Z., O.S. and S.S.; software, B.M.Z. and O.S.; validation, B.M.Z. and O.S.; formal analysis, B.M.Z., O.S. and S.S.; investigation, B.M.Z., O.S. and S.S.; writing—original draft preparation, B.M.Z.; writing—review and editing, B.M.Z., O.S. and S.S.; visualization, B.M.Z. and O.S.; supervision, B.M.Z., O.S. and S.S.; project administration, B.M.Z. and S.S.; funding acquisition, B.M.Z. and S.S. All authors have read and agreed to the published version of the manuscript.
Funding
The work of B. M. Zaidel and S. Shamai (Shitz) was supported by the ISRAEL SCIENCE FOUNDATION (grant No. 1897/19).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AWGN | Additive white Gaussian noise |
| BGWT | Bipartite Galton–Watson tree |
| CDMA | Code-division multiple access |
| EPI | Entropy power inequality |
| GWT | Galton–Watson tree |
| i.i.d. | Independent identically distributed |
| LDCD | Low-density code-domain |
| LDPC | Low-density parity-check |
| MAC | Multiple access channel |
| MC | Monte Carlo |
| MPA | Message-passing algorithm |
| MUD | Multiuser detection |
| NOMA | Non-orthogonal multiple access |
| RHS | Right-hand side |
| RS | Randomly spread |
| SIC | Successive interference cancellation |
| SNR | Signal-to-noise ratio |
Appendix A. Proof of Proposition 1
By the fundamental properties of mutual information, the sum-rate constraint in (8) can be decomposed as
Now, let us fix and let , . Then, the channel output (cf. (1)) is statistically equivalent to
where , and and are independent. The vectors
are thus statistically independent conditional on the signature matrices and have a corresponding multivariate complex Gaussian density. Hence, since
it follows, by the conditional EPI [43] and (A2), that
Considering the exponential terms on the right-hand side (RHS) of the inequality in (A5), we have
where follows from Theorem 1 (note that the introduction of the parameter in the open interval , as part of the noise-split step (A2), is necessary for the applicability of Theorem 1). Then, considering the large-system limit and substituting (A6) back into (A5), while relying on the continuity of the exponential and logarithmic functions, we obtain the following lower bound:
Appendix B. Proof of Proposition 2
Analogously to the proof of Proposition 1 in Appendix A, we aim to upper-bound the sum-rate constraint in (8). Towards this end, we employ a strengthened version of the EPI, recently derived in [45] (see also [44]), which is adapted here to the complex setting.
Theorem A1
([45], Corollary 2). Suppose that and are random vectors in , conditionally independent given Q; moreover, suppose that is conditionally Gaussian given Q. Define . For any satisfying ,
Theorem A1 immediately implies the following conditional EPI for three random summands (one of which is Gaussian).
Corollary A1
([45], Theorem 3). Let , and be three random vectors in , conditionally independent given Q, with finite second moments. Moreover, conditional on Q, let be distributed as . Then,
Proof.
The Corollary follows from Theorem A1 by letting and rearranging the exponents [45]. □
Now, let us fix , such that
and let us consider the following three independent random vectors:
where , , are independent complex Gaussian vectors, independent also of , and . Note that , and are independent conditional on the signature matrices as well. Then, observing that
hence,
Theorem A1 and Corollary A1 can be applied to yield the upper bound
where take the role of Q and all differential entropies are neither ∞ nor −∞ by construction.
Starting with the Gaussian vector , its normalized differential entropy reads
Next, considering each exponential term inside the parentheses in the RHS of (A18), we obtain, for the first term,
where is due to (A12) and follows from Theorem 1. Treating the remaining terms in an analogous manner, we obtain
Appendix C. Proof of Proposition 4
Let denote the lower bound on the achievable sum rate (27), when expressed in nats/channel use per dimension as a function of . Then,
where we use to denote the function converted to nats/channel use, (cf. (5)). The minimum that enables reliable communications and the low-SNR slope of the sum-rate lower bound then read (cf. (24)–(25))
Starting with the first derivative of (A27), we obtain
which, using the fact that and recalling that , yields
Now, as shown in [38,39] (see the proof of Theorem 3 therein), the asymptotic normalized spectral efficiency , (cf. (5) and (9)), coincides with the Shannon transform of the asymptotic empirical eigenvalue distribution of , whose density reads ([38], Theorem 2) (see also [39])
where , , is a unit point mass at and . Let be a probability distribution defined on . The Shannon transform of is defined for as [30], Definition 3.2 (see also [29], Definition
2.12). Hence, the derivative at zero , , reads
Thus, we conclude, from (A30) and (21), that
Turning to the second derivative, we have
Since the denominators of all three terms in (A34) approach unity as , we focus on the numerators. Starting with the first term, note that
In a completely analogous manner, the numerator of the second term in (A34) takes the following form as :
Appendix D. Proof of Proposition 5
Following similar steps to the proof in Appendix C, while retaining the notation therein, let denote the sum-rate upper bound (28) in nats/channel use per dimension. Then,
It is important to note, at this point, that, in contrast to the sum-rate lower bound (27), the sum-rate upper bound (A40) may exhibit a bowl-shaped form when plotted as a function of in dB (see, e.g., the discussion in ([56], p. 1341)). This behavior depends on the system load parameters and the particular choice of the constants and . That said, insights on the low-SNR characteristics of this upper bound can still be obtained by deriving its low-SNR parameters. One should only bear in mind that the value of corresponding to does not necessarily represent the minimum above which the upper bound is positive. In fact, the latter may be attained at a lower, as discussed in [56]. In such case, the low-SNR slope turns out to be negative, as shall be made clear in the sequel.
The low-SNR parameters of are given by
with the subscript in (A41) designating that corresponds to . Hence, we proceed by taking the first derivative of ,
which, letting and using (A32), yields
Therefore, it is concluded, from (A41), that, as (implying ), the corresponding approaches
which, as said, does not necessarily correspond to the minimum above which the sum-rate upper bound is positive.
To derive the slope of the sum-rate upper bound at , we take the second derivative of . From (A43), we obtain
In view of (A44), the last term in (A46) converges to as , while the denominators of the first two terms converge to . Therefore, it is left to calculate the limit of the respective numerators at . Starting with the first term in (A46), we have
where
Relying on (A32) and (A36), we then finally obtain (following some algebra)
Similarly to (A49), this yields
Finally, substituting (A49) and (A52) into (A46) while taking , we obtain
Hence, we conclude, from (A42), that the low-SNR slope is given by
Note that setting yields , which is the low-SNR slope of the single-user AWGN channel, as well as the Cover–Wyner sum capacity. Furthermore, let denote the set
Then, recalling that (see Section 2), the low-SNR slope (A54) is positive and lower than 2 as long as . Hence, for the sum-rate upper bound (28) to be useful, the parameters should be restricted in the low-SNR regime only to the set . The fact that the low-SNR slope is positive over immediately implies that (A45) is indeed the minimum over which the upper bound is positive in this setting. This completes the proof of Proposition 5. We further note that, for , the low-SNR slope may turn out negative and it may exhibit discontinuity if and are chosen so that
The bound is obviously not useful in this regime.
Appendix E. Proof of Proposition 6
Let denote an achievable rate in bit/sec/Hz expressed as a function of . Let us recall that the high-SNR approximation of reads
where denotes the high-SNR slope and denotes the high-SNR power offset. Then, for any constant , can be characterized for as
Hence, any scaling of by a factor corresponds to a shift in the high-SNR power offset by .
Rewriting the lower bound on the achievable sum rate (27), we obtain
where we use the identities and . Let and , , denote the high-SNR parameters characterizing as in ([38], Proposition 5; see also [39], Proposition 4). Specifically, for ,
and is given in (62). Then, the term outside the logarithm in (A59) can be approximated for as
Therefore, it is left to examine the different term in the exponent inside the logarithm in (A59), which we denote as
Note that, accordingly, the sum-rate lower-bound (A59) can be compactly rewritten as
We thus proceed with the analysis of (A63), while distinguishing among three possible cases and relying on the observations made in Appendix H.
Appendix E.1. Case I: β 1,β 2 >1
Using (A133), we obtain, for ,
where should be interpreted here as the corresponding expression in (62) for . Similarly, we obtain
The substitution back into (A62) then yields
where
Hence, for , it can be shown (following some algebra) that
where
and, finally (cf. (A63)),
This lets us conclude that the high-SNR slope of the sum-rate lower bound reads
and the respective high-SNR power offset satisfies
Using (A70), we finally conclude that
Appendix E.2. Case II: β 1 >1,β 2 =1
Using (A126), we obtain, for ,
Combining (A75) with (A64) and substituting back into (A62), we obtain (while considering only small terms of leading order)
where
This yields, for ,
where
and, finally,
Note that, although apparently takes the same form as in (A70), these two constants are not identical, since differs for (cf. (62)); to emphasize this, we use a different notation.
Therefore, we conclude that the high-SNR slope of the sum-rate lower bound satisfies
and the high-SNR power offset is given by
Using (A80), we then obtain
Appendix E.3. Case III: β 1 >1,2 d≤β 2 <1
For , we start from (A140) and obtain, for ,
Using (A64) and substituting back into (A62), we then obtain
where
This yields
hence,
We finally conclude that the high-SNR slope for and reads
while the high-SNR power offset reads
Appendix F. Proof of Proposition 7
Starting from (28), we obtain, following some algebra,
Next, relying on (A58), (A60) and (62), we conclude that the terms outside the logarithm in (A93) can be approximated, for , as
Our next step is to investigate the different terms in the exponent inside the logarithm in (A93), which we compactly denote as
Focusing on , we resort to Appendix H and obtain, from (A133), that, for ,
This yields
hence, for ,
where we used the approximation , and
Next, considering the term in (A93), it is concluded (following some algebra) that, for ,
Appendix G. RS-CDMA: Achievable Region for Two User Classes
In this appendix, we derive the achievable region for RS-CDMA in the large-system limit following the analysis in [41]. The system model for RS-CDMA can still be described via (1), where we now assume that the entries of the signature matrices are i.i.d. random variables with zero mean, unit variance and finite fourth moment. We also set to comply with the setting considered in [41]. Referring to (8) and starting with the individual rate constraints, we have, from ([41], Section IV), that
where
and is defined in (6) [40].
To proceed with the analysis of the sum-rate constraint in (8), we introduce the probability mass function (pmf) as
where, as in (19),
Then, in the large-system limit, while relying on the strong law of large numbers (SLLN), the received signal in (1) is well represented by
where the matrix has i.i.d. zero-mean entries with unit variance and finite fourth moment, is a diagonal random matrix with i.i.d. entries distributed according to (A110), denotes the input vector comprising both classes of users and denotes the AWGN. Next, by ([41], Theorem IV.1), we have
where
and is the positive solution to
The explicit dependence of , and on was omitted here for notational simplicity. Note that (A116) boils down to the 3rd order polynomial equation
where
Appendix H. The High-SNR Regime: Some Fundamental Observations
In this appendix, we pursue a somewhat refined high-SNR approximation of , as given by (5) (we omit subscripts in the following since the analysis holds for either or ). The observations made here serve as a fundamental tool for the high-SNR analysis of the sum-rate lower and upper bounds of Propositions 1 and 2 (see Appendices Appendix E and Appendix F, respectively).
Appendix H.1. β = 1
We start by considering the case where ; hence, (cf. Theorem 1) , and , yielding
Note that
while
Substituting (A121) back into the first logarithmic term in (A120) yields (following some algebra)
where we use the following approximation:
Similarly, using (A122), we obtain, for the second logarithmic term in (A120),
Substituting the above high-SNR approximations back into (A120), we finally obtain
Appendix H.2. β > 1
For , we investigate by directly considering its integral form (see [39], ([38], Theorems 2 and 3), (A31) and the corresponding discussion and notation in Appendix C)
where
Note that, for , the density has a finite strictly positive support ; hence, can be equivalently expressed as
Therefore, we approximate in the high-SNR regime as
Appendix H.3. 2 d≤ β < 1
Using the subscript to designate quantities corresponding to an underloaded setting (), we start by noting that, in the underloaded regime, can be shown to satisfy the relation
where we additionally define and . Here, specifies the achievable throughput in an overloaded single-class setting with the corresponding parameters (see the discussion in Section 3.1). Hence, can be expressed in an integral form as
where is as in (A128) with the obvious change in parameters. Since , the density has a finite strictly positive support and can be equivalently rewritten as
Hence, we approximate in the high-SNR regime as
The two integrals in (A137) can be solved in closed form, yielding
and the high-SNR approximation for thus reads
References
- Ding, Z.; Lei, X.; Karagiannidis, G.J.; Schober, R.; Yuan, J.; Bhargava, V.K. A Survey on Non-Orthogonal Multiple Access for 5G Networks: Research Challenges and Future Trends. IEEE J. Sel. Areas Commun. 2017, 35, 2181–2195. [Google Scholar] [CrossRef] [Green Version]
- Dai, L.; Wang, B.; Ding, Z.; Wang, Z.; Chen, S.; Hanzo, L. A Survey of Non-Orthogonal Multiple Access for 5G. IEEE Commun. Surv. Tutor. 2018, 20, 2294–2323. [Google Scholar] [CrossRef] [Green Version]
- Makki, B.; Chitti, K.; Behravan, A.; Alouini, M.S. A Survey of NOMA: Current Status and Open Research Challenges. IEEE Open Commun. Soc. 2020, 1, 179–189. [Google Scholar] [CrossRef] [Green Version]
- Yuan, Y.; Wang, S.; Wu, Y.; Poor, H.V.; Ding, Z.; You, X.; Hanzo, L. NOMA for Next-Generation Massive IoT: Performance Potential and Technology Directions. IEEE Commun. Mag. 2021, 59, 115–121. [Google Scholar] [CrossRef]
- Dangi, R.; Lalwani, P.; Choudhary, G.; You, I.; Pau, G. Study and Investigation on 5G Technology: A Systematic Review. Sensors 2022, 22, 26. [Google Scholar] [CrossRef]
- Maraqa, O.; Rajasekaran, A.S.; Al-Ahmadi, S.; Yanikomeroglu, H.; Sait, S.M. A Survey of Rate-Optimal Power Domain NOMA With Enabling Technologies of Future Wireless Networks. IEEE Commun. Surv. Tutor. 2020, 22, 2192–2235. [Google Scholar] [CrossRef]
- Iswarya, N.; Jayashree, L.S. A Survey on Successive Interference Cancellation Schemes in Non-Orthogonal Multiple Access for Future Radio Access. Wirel. Pers. Commun. 2021, 120, 1057–1078. [Google Scholar] [CrossRef]
- Jamali, M.H.; Mahdavifar, H. Massive Coded-NOMA for Low-Capacity Channels: A Low-Complexity Recursive Approach. IEEE Trans. Commun. 2021, 69, 3664–3681. [Google Scholar] [CrossRef]
- Hoshyar, R.; Wathan, F.P.; Tafazolli, R. Novel Low-Density Signature for Synchronous CDMA Systems Over AWGN Channel. IEEE Trans. Signal Process. 2008, 56, 1616–1626. [Google Scholar] [CrossRef] [Green Version]
- Hoshyar, R.; Razavi, R.; Al-Imari, M. LDS-OFDM an Efficient Multiple Access Technique. In Proceedings of the 2010 IEEE 71st Vehicular Technology Conference, Taipei, Taiwan, 16–19 May 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Qi, T.; Feng, W.; Chen, Y.; Wang, Y. When NOMA Meets Sparse Signal Processing: Asymptotic Performance Analysis and Optimal Sequence Design. IEEE Access 2017, 5, 18516–18525. [Google Scholar] [CrossRef]
- Nikopour, H.; Baligh, H. Sparse Code Multiple Access. In Proceedings of the 2013 IEEE 24th International Symposium on Personal, Indoor and Mobile Radio Communications, London, UK, 8–11 September 2013; pp. 332–336. [Google Scholar] [CrossRef]
- Van de Beek, J.; Popović, B.M. Multiple Access with Low-Density Signatures. In Proceedings of the 2009 IEEE GLOBECOM, Honolulu, Hawaii, 30 November–4 December 2009. [Google Scholar]
- Millar, G.; Kulhandjian, M.; Alaca, A.; Alaca, S.; D’Amours, C.; Yanikomeroglu, H. Low-Density Spreading Design Based on an Algebraic Scheme for NOMA Systems. IEEE Wireless Commun. Lett. 2022. [Google Scholar] [CrossRef]
- Moltafet, M.; Mokari, N.; Javan, M.R.; Saeedi, H.; Pishro-Nik, H. A New Multiple Access Technique for 5G: Power Domain Sparse Code Multiple Access (PSMA). IEEE Access 2018, 6, 747–759. [Google Scholar] [CrossRef]
- Sharma, S.; Deka, K.; Bhatia, V.; Gupta, A. Joint Power-Domain and SCMA-Based NOMA System for Downlink in 5G and Beyond. IEEE Commun. Lett. 2019, 23, 971–974. [Google Scholar] [CrossRef]
- Li, Z.; Chen, W.; Wei, F.; Wang, F.; Xu, X.; Chen, Y. Joint Codebook Assignment and Power Allocation for SCMA Based on Capacity With Gaussian Input. In Proceedings of the 2016 IEEE/CIC International Conference on Communications in China, Chengdu, China, 27–29 July 2016; pp. 1–6. [Google Scholar]
- Balasubramanya, N.M.; Gupta, A.; Sellathurai, M. Combining Code-domain and Power-domain NOMA for Supporting Higher Number of Users. In Proceedings of the 2018 IEEE GLOBECOM, Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Evangelista, J.V.C.; Sattar, Z.; Kaddoum, G.; Chaaban, A. Fairness and Sum-Rate Maximization via Joint Subcarrier and Power Allocation in Uplink SCMA Transmission. IEEE Trans. Wireless Commun. 2019, 18, 5855–5867. [Google Scholar] [CrossRef]
- Quan, C.; Yadav, A.; Geng, B.; Varshney, P.K.; Poor, H.V. A Novel Spectrally-Efficient Uplink Hybrid-Domain NOMA System. IEEE Commun. Lett. 2020, 24, 2609–2613. [Google Scholar] [CrossRef]
- Yadav, A.; Quan, C.; Varshney, P.K.; Poor, H.V. On Performance Comparison of Multi-Antenna HD-NOMA, SCMA, and PD-NOMA Schemes. IEEE Wireless Commun. Lett. 2021, 10, 715–719. [Google Scholar] [CrossRef]
- Kim, Y.B.; Yamazaki, K.; Jung, B.C. Virtual Full-Duplex Cooperative NOMA: Relay Selection and Interference Cancellation. IEEE Trans. Wirel. Commun. 2019, 18, 5882–5893. [Google Scholar] [CrossRef]
- Ding, Z.; Dai, H.; Poor, H.V. Relay Selection for Cooperative NOMA. IEEE Wireless Commun. Lett. 2016, 5, 416–419. [Google Scholar] [CrossRef] [Green Version]
- Zhang, L.; Liu, J.; Xiao, M.; Wu, G.; Liang, Y.C.; Li, S. Performance Analysis and Optimization in Downlink NOMA Systems with Cooperative Full-Duplex Relaying. IEEE J. Sel. Areas Commun. 2017, 35, 2398–2412. [Google Scholar] [CrossRef]
- Liau, Q.Y.; Leow, C.Y. Cooperative NOMA System with Virtual Full Duplex User Relaying. IEEE Access 2019, 7, 2502–2511. [Google Scholar] [CrossRef]
- Jose, J.; Shaik, P.; Bhatia, C. VFD-NOMA under Imperfect SIC and Residual Inter-Relay Interference Over Generalized Nakagami-m Fading Channels. IEEE Commun. Lett. 2021, 25, 646–650. [Google Scholar] [CrossRef]
- Jose, J.; Shaik, P.; Bhatia, V. Performance of Cooperative NOMA with Virtual Full-Duplex based DF Relaying in Nakagami-m Fading. In Proceedings of the VTC-Spring 2021—2021 IEEE 93rd Vehicular Technology Conference, Helsinki, Finland, 25–28 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Hong, S.N.; Caire, G. Virtual Full-Duplex Relaying With Half-Duplex Relays. IEEE Trans. Inf. Theory 2015, 61, 4700–4720. [Google Scholar] [CrossRef]
- Tulino, A.M.; Verdú, S. Random Matrix Theory and Wireless Communications. Found. Trends Commun. Inf. Theory 2004, 1, 1–182. [Google Scholar] [CrossRef]
- Couillet, R.; Debbah, M. Random Matrix Methods for Wireless Communications; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Nishimori, H. Statistical Physics of Spin Glasses and Information Processing: An Introduction; Oxford University Press: Oxford, UK, 2001. [Google Scholar]
- Mézard, M.; Montanari, A. Information, Physics, and Computation; Oxford University Press: Oxford, UK, 2009. [Google Scholar]
- Yoshida, M.; Tanaka, T. Analysis of Sparsely-Spread CDMA via Statistical Mechanics. In Proceedings of the 2006 IEEE International. Symposium of Information Theory (ISIT), Seatle, Washington, 11–15 June 2006; pp. 2378–2382. [Google Scholar] [CrossRef]
- Ferrante, G.C.; Di Benedetto, M.G. Spectral Efficiency of Random Time-Hopping CDMA. IEEE Trans. Inf. Theory 2015, 61, 6643–6662. [Google Scholar] [CrossRef] [Green Version]
- Asgharimoghaddam, H.; Kaleva, J.; Tölli, A. Capacity Approaching Low Density Spreading in Uplink NOMA via Asymptotic Analysis. IEEE Trans. Commun. 2021, 69, 1635–1647. [Google Scholar] [CrossRef]
- Le, M.T.P.; Ferrante, G.C.; Caso, G.; Di Benedetto, M.G. On Information-Theoretic Limits of Code-Domain NOMA for 5G. IET Commun. 2018, 12, 1864–1871. [Google Scholar] [CrossRef]
- Shental, O.; Zaidel, B.M.; Shamai (Shitz), S. Low-Density Code-Domain NOMA: Better Be Regular. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 2633–2637. [Google Scholar]
- Zaidel, B.M.; Shental, O.; Shamai (Shitz), S. Sparse NOMA: A Closed-Form Characterization. In Proceedings of the 2018 IEEE International Symposium on Information Theory (ISIT), Vail, CO, USA, 17–23 June 2018; pp. 1106–1110. [Google Scholar]
- Zaidel, B.M.; Shental, O.; Shamai (Shitz), S. Regular Sparse NOMA: Ultimate Performance in Closed Form. IEEE J. Sel. Areas Inf. 2022. submitted for publication. [Google Scholar]
- Verdú, S.; Shamai (Shitz), S. Spectral Efficiency of CDMA with Random Spreading. IEEE Trans. Inf. Theory 1999, 45, 622–640. [Google Scholar] [CrossRef]
- Shamai (Shitz), S.; Verdú, S. The Impact of Frequency-Flat Fading on the Spectral Efficiency of CDMA. IEEE Trans. Inf. Theory 2001, 47, 1302–1327. [Google Scholar] [CrossRef]
- Hu, J.; Duman, T.M. Graph-Based Detection Algorithms for Layered Space-Time Architectures. IEEE J. Sel. Areas Commun. 2008, 26, 269–280. [Google Scholar]
- El Gamal, A.; Kim, Y.H. Network Information Theory; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Courtade, T.A. Strengthening the Entropy Power Inequality. In Proceedings of the 2016 IEEE International Symposium on Information Theory (ISIT), Barcelona, Spain, 10–15 July 2016; pp. 2294–2298. [Google Scholar]
- Courtade, T.A. A Strong Entropy Power Inequality. IEEE Trans. Inf. Theory 2018, 64, 2173–2192. [Google Scholar] [CrossRef]
- Wyner, A.D. Shannon-Theoretic Approach to a Gaussian Cellular Multiple-Access Channel. IEEE Trans. Inf. Theory 1994, 40, 1713–1727. [Google Scholar] [CrossRef]
- Zaidel, B.M.; Shamai (Shitz), S.; Verdú, S. Multi-Cell Uplink Spectral Efficiency of Coded DS-CDMA with Random Signatures. IEEE J. Sel. Areas Commun. 2001, 19, 1556–1569. [Google Scholar] [CrossRef]
- Somekh, O.; Zaidel, B.M.; Shamai (Shitz), S. Sum Rate Characterization of Joint Multiple Cell-Site Processing. IEEE Trans. Inf. Theory 2007, 53, 4473–4497. [Google Scholar] [CrossRef] [Green Version]
- Simeone, O.; Levy, N.; Sanderovich, A.; Somekh, O.; Zaidel, B.M.; Poor, H.V.; Shamai (Shitz), S. Cooperative Wireless Cellular Systems: An Information-Theoretic View. Found. Trends Commun. Inf. Theory 2012, 8, 1–177. [Google Scholar] [CrossRef]
- Bordenave, C.; Lelarge, M. Resolvent of Large Random Graphs. Random Struct. Alg. 2010, 37, 332–352. [Google Scholar] [CrossRef] [Green Version]
- Dembo, A.; Montanari, A.; Sun, N. Factor Models on Locally Tree-Like Graphs. Ann. Probab. 2013, 41, 4162–4213. [Google Scholar] [CrossRef]
- Richardson, T.; Urbanke, R. Modern Coding Theory; Cambridge University Press: Cambridge, UK, 2008. [Google Scholar]
- Gallager, R.G. Low-Density Parity-Check Codes; MIT Press: Cambridge, MA, USA, 1963. [Google Scholar]
- Zaidel, B.M.; Shamai (Shitz), S. Sparse and Dense: An Achievable Region for Code-Domain NOMA with Mixed Users. In Proceedings of the 2021 IEEE International Symposium on Information Theory (ISIT), Melbourne, Australia, 12–20 June 2021; pp. 2942–2947. [Google Scholar]
- Mingo, J.A.; Speicher, R. Free Probability and Random Matrices; Springer: New York, NY, USA, 2017. [Google Scholar]
- Verdú, S. Spectral Efficiency in the Wideband Regime. IEEE Trans. Inf. Theory 2002, 48, 1319–1343. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).