Abstract
The Internet of Things (IoT) is a complex ecosystem of connected devices that exchange data over a wired or wireless network and whose final aim is to provide services either to humans or machines. The IoT has seen rapid development over the past decade. The total number of installed connected devices is expected to grow exponentially in the near future, since more and more domains are looking for IoT solutions. As a consequence, an increasing number of developers are approaching IoT technology for the first time. Unfortunately, the number of IoT-related studies published every year is becoming huge, with the obvious consequence that it would be impossible for anyone to predict the time that could be necessary to find a paper talking about a given problem at hand. This is the reason why IoT-related discussions have become predominant in various practitioners’ forums, which moderate thousands of posts each month. The present paper’s contribution is twofold. First, it aims at providing a holistic overview of the heterogeneous IoT world by taking into account a technology perspective and a business perspective. For each topic taken into account, a tutorial introduction (deliberately devoid of technical content to make this document within the reach of non-technical readers as well) is provided. Then, a table of very recent review papers is given for each topic, as the result of a systematic mapping study.
Keywords:
Internet of Things; IoT conceptual model; IoT security; IoT privacy; IoT blockchain; IoT communication; IoT fog computing; IoT edge computing; IoT cloud computing; IoT servitization; IoT business models; IoT taxonomies; IoT architectures; middleware; IoT digital twins; IoT software architecture; IoT application domains; IoT ecosystem 1. Introduction
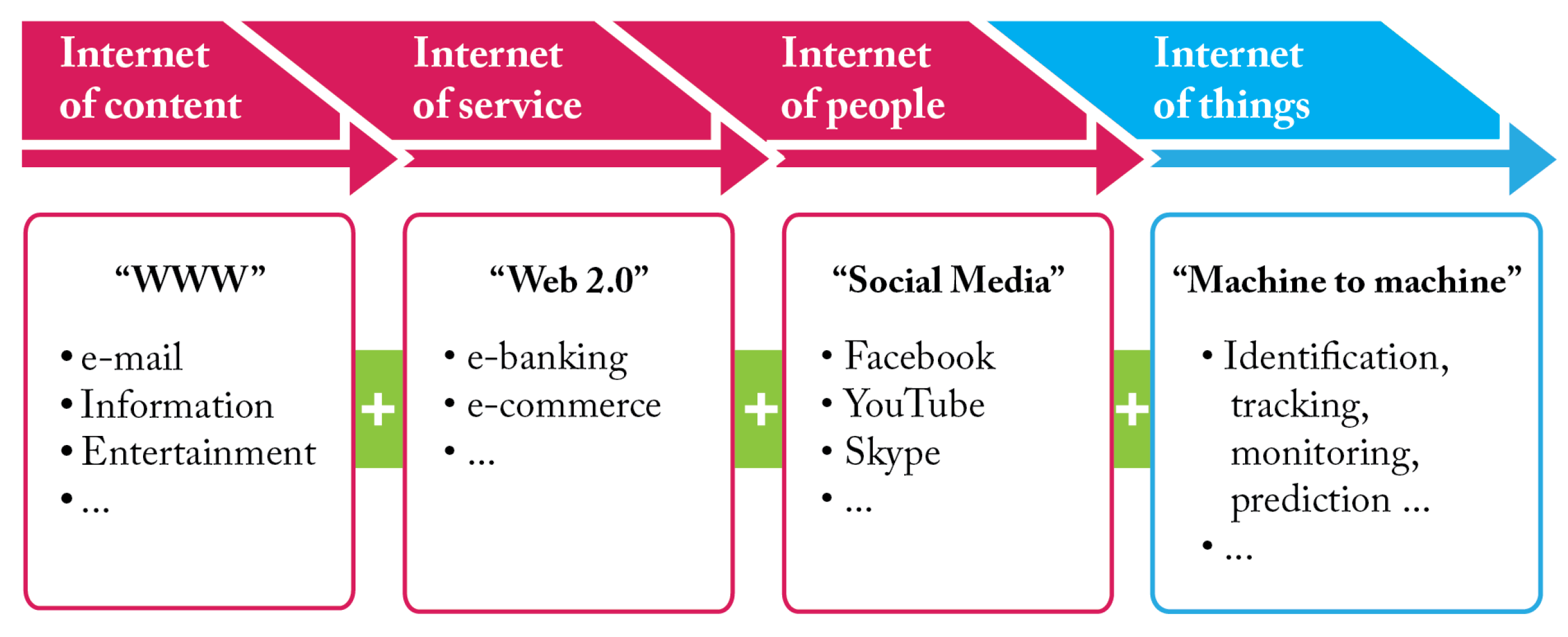
Figure 1 depicts the transformation phases of the Internet up to the Internet of Things (IoT). The IoT is an ecosystem of physical objects (the “things”) that connect to the Internet and to other things. These physical objects could be any device tagged with sensors (e.g., smartphones, smart electric appliances, smart office equipment, cars, and so on). The number of IoT devices worldwide is forecast to almost triple from 8.74 billion in 2020 to more than 25.4 billion IoT devices in 2030 (https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/ (accessed on 5 July 2022)). Data generated by the devices are then shared (over a wired or wireless network) with servers located in cloud or on-premise, where it is processed to gain insights that help in making decisions. The IoT ecosystem can be established not only within small areas such as, for example, a building, but also over larger areas like cities. The IoT is redefining the way we interact, communicate, and go about our daily work. From homes to maintenance to cities, the IoT ecosystem is making our world smarter and more efficient.
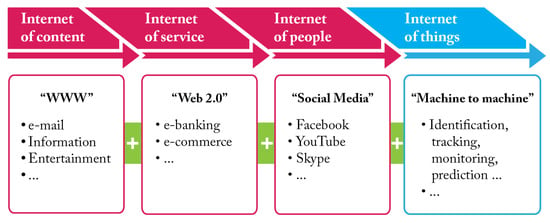
Figure 1.
The evolution of the Internet.
Wang et al. in [1] conducted a bibliometric study of 3523 IoT-related articles published in 2000–2019. According to that study, the development of the IoT has gone through three stages. During the first stage, from 2002 to 2009, just nine papers were published. The second stage spans from 2009 to 2015. In those years, many countries issued action plans on the IoT. “Internet of Things—An action plan for Europe” is an example [2]. The third stage spans from 2015 to 2019, when 2999 publications were published in Web of Science, with an annual increase in publications of about 85%.
This huge knowledge asset has generated a fragmented picture and a lack of consensus about IoT systems, their basic constituents, their qualities, and in some cases even inconsistent terminologies and definitions. A long list of surveys (i.e., articles that in [3] are called secondary studies) have been written with the aim of overcoming this issue. Despite the relevance and soundness of most of these studies, they suffer two severe drawbacks: (a) their scope does not cover all the aspects connected with the IoT domain; (b) they are structured according to a limited number of research questions. Such a common structure of articles does not fit the needs of practitioners looking for suitable answers to overcome the daily challenges they face. That is the reason why IoT-related discussions have become predominant in various domains’ forums, which moderate thousands of posts each month from practitioners with a heterogeneous background and skill.
In 2021, [4] reported on a study that investigated the questions asked by IoT practitioners on one of the relevant domains of the Internet of Things ecosystem, namely “IoT/Industry 4.0”. In such a study, authors mined 176819 publicly available posts (on IoT/Industry 4.0-related questions) retrieved from Stack Exchange (the largest—it has millions of active users—and the most trusted online community of developers). The results of the analysis pointed out that the IoT-related questions concerned 100 topics, which the authors grouped into five general categories: software development, platform development (including debugging and analytics), hardware management (including monitoring and testing), network management (including automation and security), and system management (including debugging and security).
These findings tell us that to develop successful projects within a single IoT domain, IoT practitioners need to acquire knowledge about several topics, usually treated in distinct surveys. The situation becomes more tricky when the IoT practitioner aspires to capture a global picture of the composite IoT ecosystem. In fact, in that case, he has to read independent studies and then harmonize the treated concepts into a unifying frame. This accomplishment is hard to reach, especially by practitioners without an adequate background and technical expertise.
Relative to the existing literature on IoT, the present paper’s contribution is twofold. First, it aims at providing a holistic overview of the heterogeneous IoT world by taking into account a technology perspective and a business perspective. For each topic taken into account, a tutorial introduction (deliberately devoid of technical content to make this document within the reach of non-technical readers as well) is provided. Then, a table of pertinent review papers (published between 2019 and April 2022) is given for each topic. We restricted the attention to a short time interval because, as we will see later, the number of review papers is very high.
According to [3], the present paper is a systematic mapping study dealing with topics concerning the IoT ecosystem. As pointed out above, such a domain is extraordinarily broad and, moreover, a very long list of systematic reviews are already available; therefore “a systematic mapping study is more appropriate than a systematic review”, [3] (p. 5). “Systematic mapping studies (…) are designed to provide a wide overview of a research area” [3] (p. 44), this paper aims to coherently act as the table of contents does in handbooks; indeed, by reading it, a developer can find recently published relevant studies on the concepts underlying the IoT ecosystem (usually the subject of distinct and distant reviews) which he wants to learn about. In light of what has been said above, it follows that this work is not a systematic review; thus, it does not overlap with any of the 119 review studies it cites and to which the reader is referred.
The remaining part of the paper is structured as follows. Section 2 introduces the background necessary to understand the other sections. Specifically, the following topics are introduced: an IoT conceptual model; an IoT reference model; fog computing and edge computing models; middleware; and blockchain. Section 3 describes the articulation of the research process and then the bibliographic search we have carried out. A total of 119 reviews were selected from 62 distinct Scopus-indexed journals. Section 4 reports on the way the 18 topics extracted from the 119 reviews were classified. A brief introduction to each of those topics is also part of the section. Section 5 introduces a definition of the IoT ecosystem that merges a technology perspective and a business perspective. Section 6 introduces the notion of IoT taxonomy and recalls a few recent studies which have made their own proposal. Section 7 ends the paper. Three appendices are an integral part of the paper. They collect a map of the 119 review papers that appeared from 2019 to April 2022.
2. Background
This section collects the following topics: an IoT conceptual model; an IoT reference model; IoT computing models (specifically, fog computing and edge computing); middleware, and blockchain. Given the objectives of the paper, each topic is briefly introduced in a dedicated sub-section without entering into technicalities that interested readers can find in the linked references.
The first step in understanding the IoT ecosystem is to study its architecture [5]. The (keyword thematic evolution and the keyword co-occurrence network) numerical results given in [1] confirm that the IoT architecture is a first-class research topic. Unfortunately, today, there is no one reference architecture model that is universally used. This wealth represents an obstacle for practitioners approaching the IoT ecosystem for the first time. To smooth out these difficulties, it is necessary to introduce first the basic concepts of IoT systems. We refer to the approved International Standard ISO/IEC 30141 [6]. Such a document has four merits: (a) it collects advices for the IoT architect; (b) it is technology-neutral; (c) it gives a clear picture of IoT systems to the involved stakeholders (namely, device manufacturers, application developers, users, and so on); (d) it facilitates the communication between them. Ref. [6] begins by listing the basic characteristics of IoT systems; then it abstracts them into an IoT conceptual model (CM) describing the key concepts of IoT systems; hence, a high-level reference model (RM) is derived. Overall, the ISO/IEC 30141 document serves as a base from which context-specific IoT architectures, and hence actual systems, can be defined.
2.1. IoT Conceptual Model
The IoT CM in [6] is generic, abstract and simple. It introduces a minimum vocabulary about IoT systems, contains the basic concepts to be known about, and describes how they relate to each other logically. The CM is presented by means of a certain number of UML class diagrams where two different types of relationships between classes are used: generalization (the “is-a” relationship) and association (the association names are verbs). To keep the diagrams readable, classes have no attributes, and the cardinality constraints on association ends are omitted.
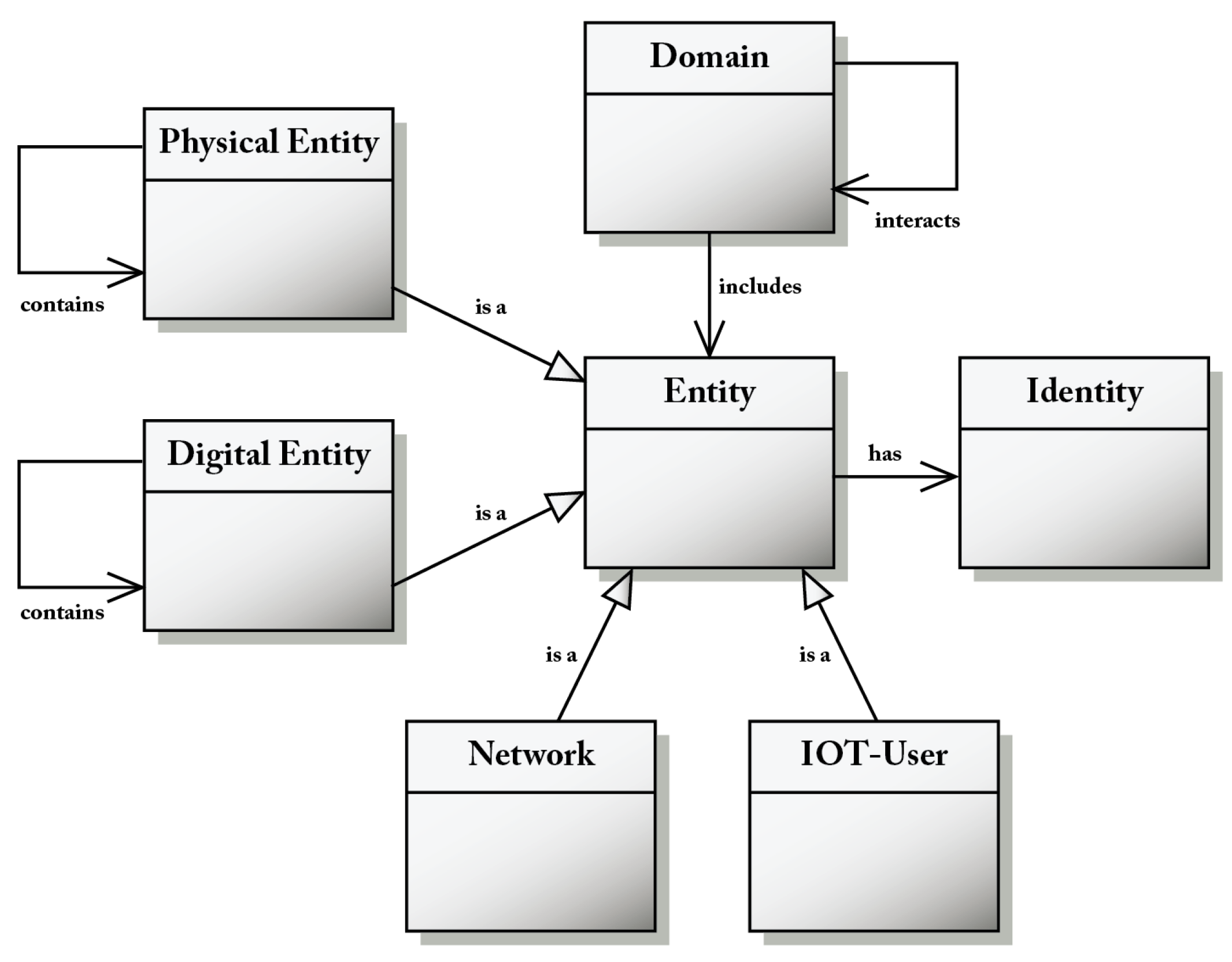
Figure 2 collects the four fundamental entities of the IoT CM: the digital entity, the physical entity, the IoT user, and the communication network. These four entities are a specialization of (the class) entity. Entities have an identity provided by a unique identifier. Each entity participates in at least a domain and is said to be contained by that domain. The notion of domain allows one to decompose complex IoT systems into smaller sub-systems.
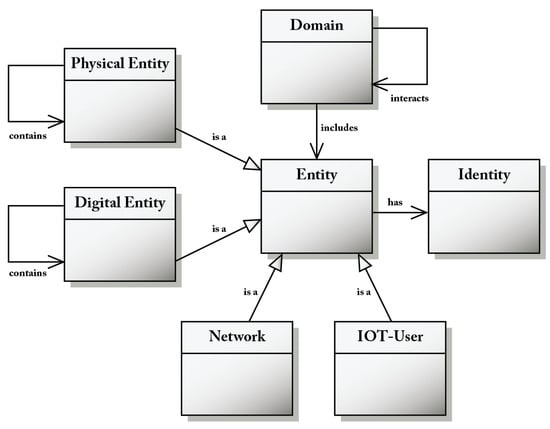
Figure 2.
Entities of the IoT CM.
A digital entity is a computational or data element of an IoT system (applications, services, data stores, IoT devices, and IoT gateways are examples of digital entities), while a physical entity (a real-world “thing”) is a discrete, identifiable and observable part of the physical environment (humans, animals, cars, buildings, and open spaces are physical entities).
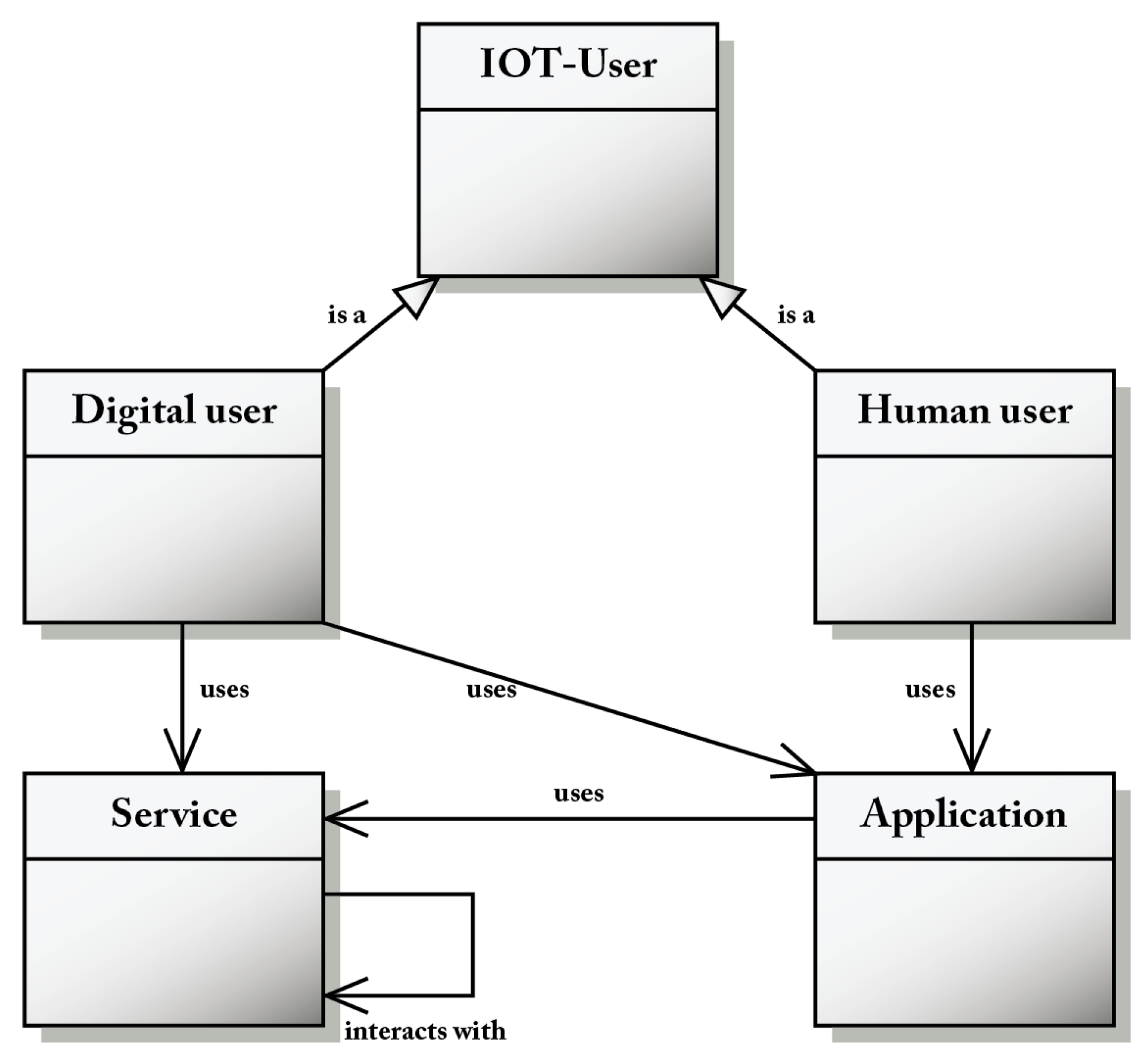
An IoT user may be human or digital; both use applications that, in turn, use a service (Figure 3). An application is a software designed to help IoT users to carry out specific tasks. Service is an abstract concept that is usually implemented as software.
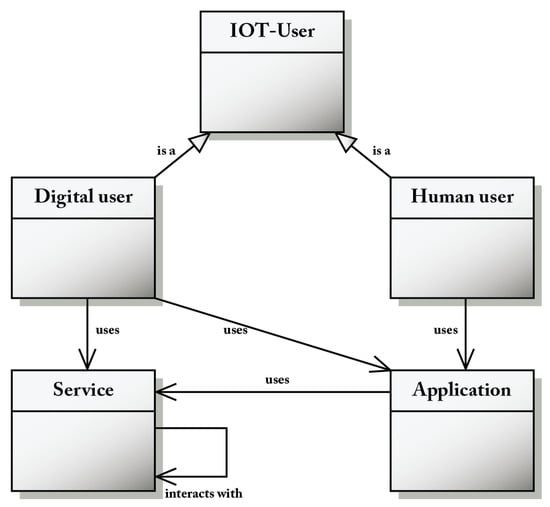
Figure 3.
The IoT user class diagram.
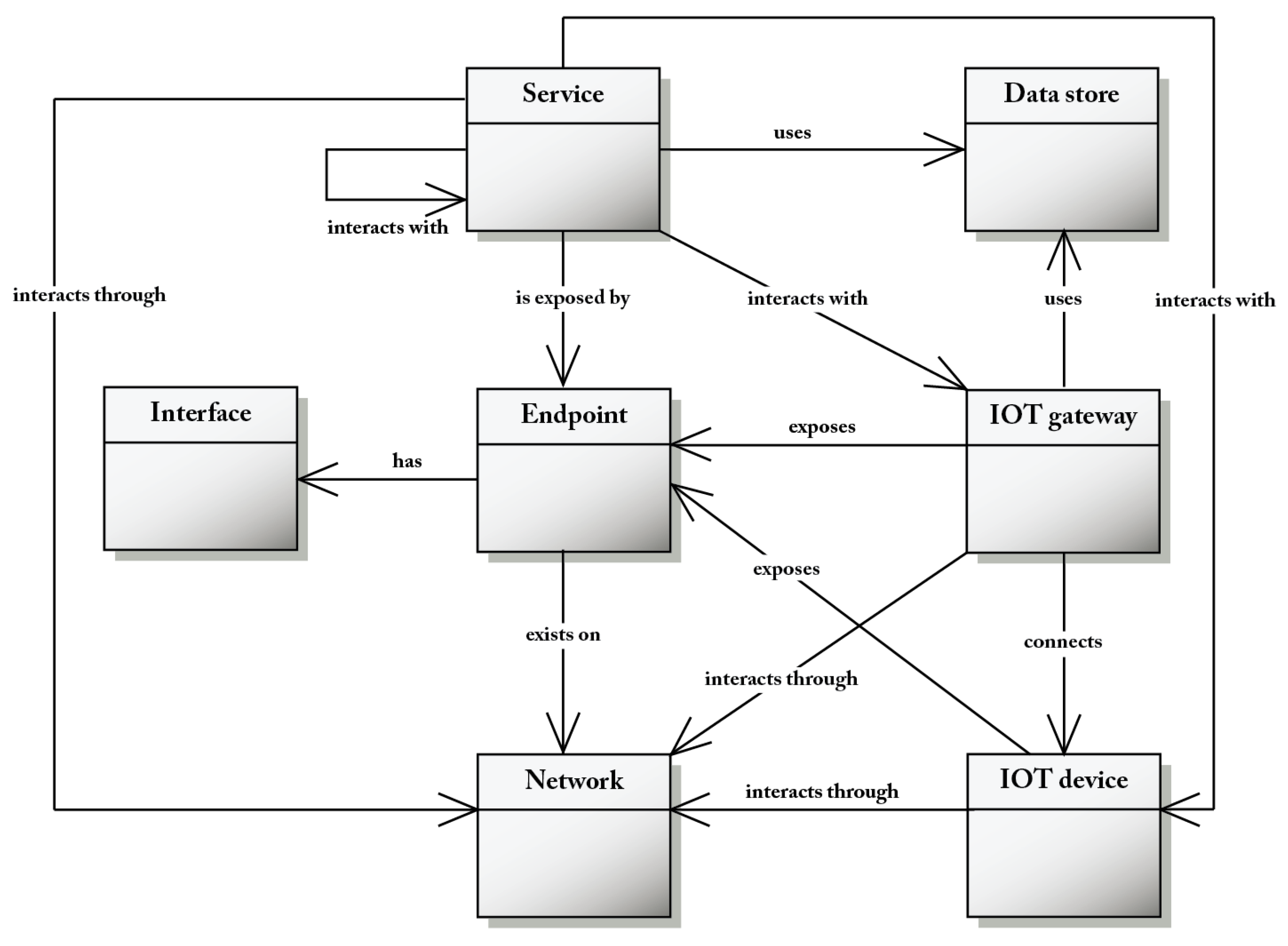
Figure 4 shows the relationship between services and IoT devices through IoT gateways that form a bridge between the networks that connect them. A service exposes at least an endpoint by which it can be invoked. An endpoint has one or more network interfaces. An interface is a set of operations and associated parameters. Data associated with services, IoT devices and IoT gateways are archived in data stores that several entities can access. An IoT device interacts with at least a network in order to communicate with other entities in the same IoT system; moreover, it exposes at least an endpoint, can have computational capabilities and can use local data stores.
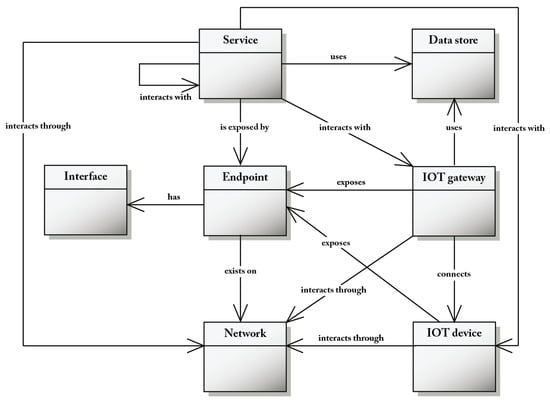
Figure 4.
The service, network, IoT device and IoT gateway concepts of the CM.
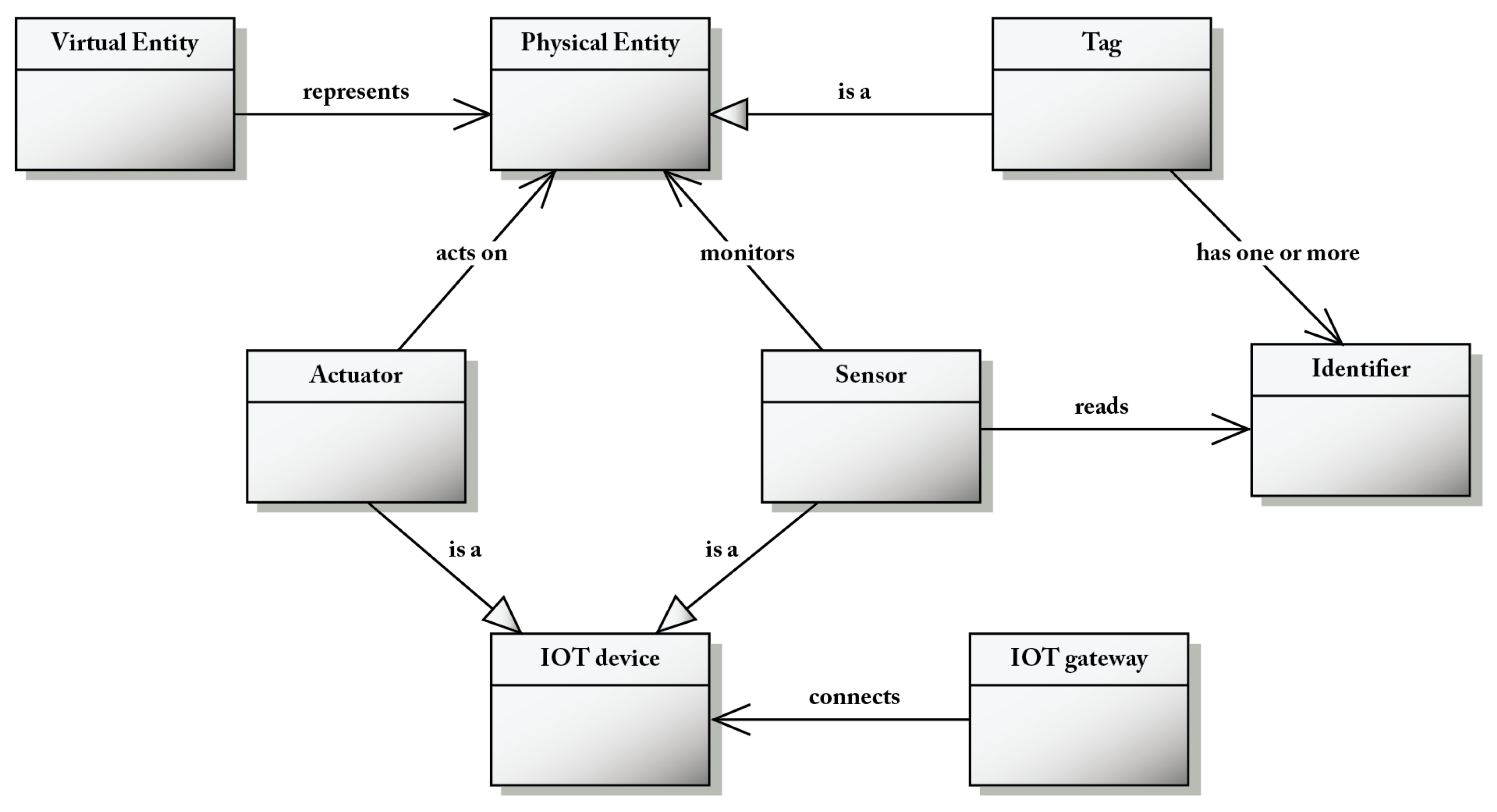
Figure 5 shows the relationship between a virtual entity, a physical entity and an IoT device. Actuators and sensors are IoT devices that have a direct contact with a physical entity, or they interact with it indirectly through the associated tag. A sensor is a device that measures some property of a physical entity and outputs digital data representing the measurement that can be transmitted over a network. An actuator is a device that accepts digital inputs and, on the basis of those inputs, changes one or more properties of a physical entity. A physical entity can have one or more tags attached to it, and sensors can monitor the tag rather than the physical entity itself. A tag is a physical entity that is attached to another physical entity in order to assist in identifying and tracking that physical entity. Barcodes and RFID are common tags. A virtual entity is a digital representation of a physical entity; it is contained in a service.
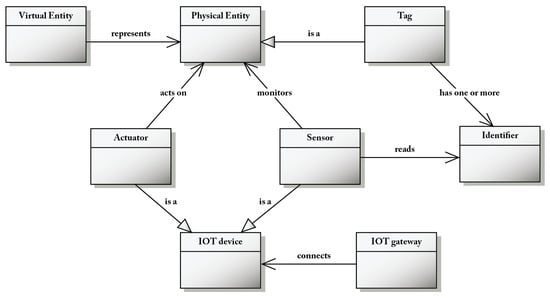
Figure 5.
Virtual entity, physical entity, and IoT device concepts of the CM.
2.2. IoT Reference Model (RM)
This sub-section recalls the structure of the IoT RM introduced in [6]. Two complementary perspectives are taken into account in sequence: the first (perspective) is entity-based (Figure 6), while the second is domain-based (Figure 7).
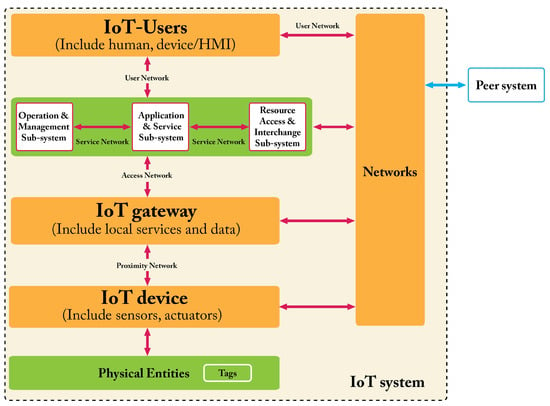
Figure 6.
The entity-based IoT RM.
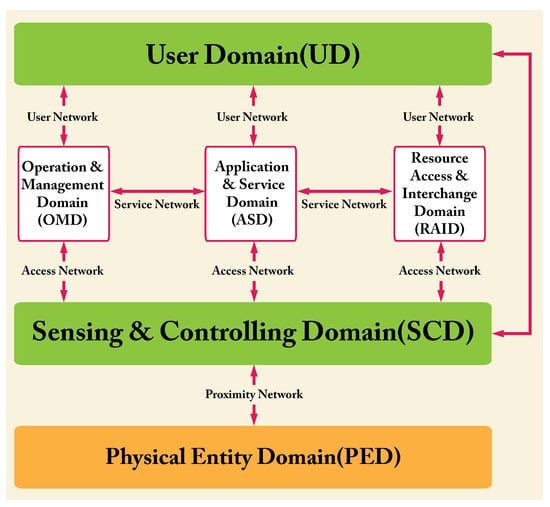
Figure 7.
The domain-based IoT RM.
2.2.1. Entity-Based RM
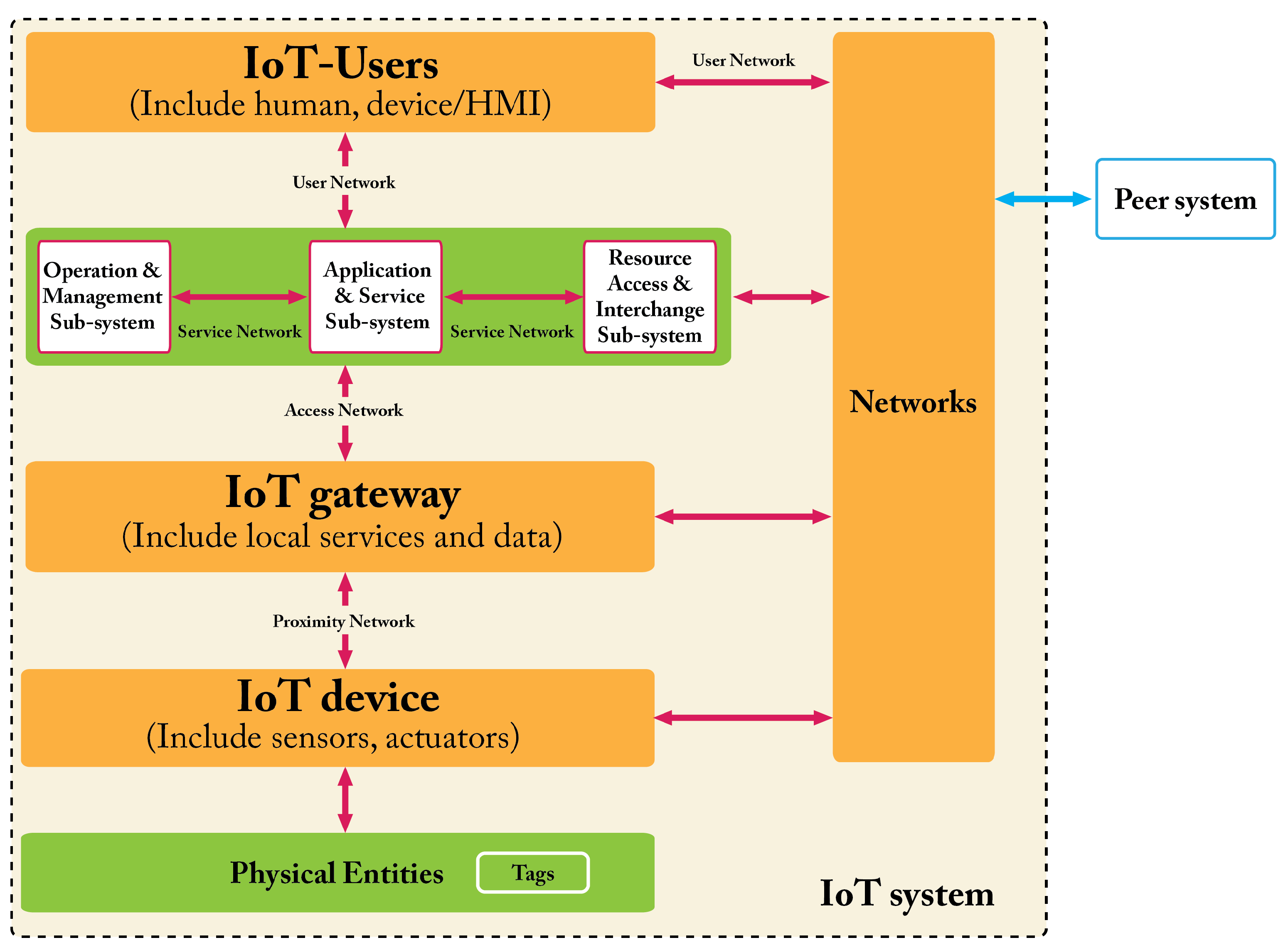
Most of the entities in Figure 6 have been already introduced in Section 2.1, so hereafter, we limit the presentation to the three sub-systems and the (physical) connections. A much more detailed description is given in [6].
IoT devices communicate with the other entities (e.g., IoT users) taking part to IoT systems via the networks. Forward, it will be said that in IoT systems, there are the following four kinds of networks: proximity network, access network, services network, and user network (Figure 6).
The operation and management sub-system includes the device registry database and an associated device identity service, which provides lookup capabilities for applications and services. Various kinds of applications and service sub-systems exist in most IoT systems, with associated data stores. The resource access and interchange sub-system exhibits the interfaces through which both users and peer systems can access the (service/administration/business) capabilities of the IoT system.
Human users typically interact with the IoT system using smartphones, personal computers, etc. Digital users interact with IoT systems by means of APIs. Peer systems interact with the IoT system through the Internet.
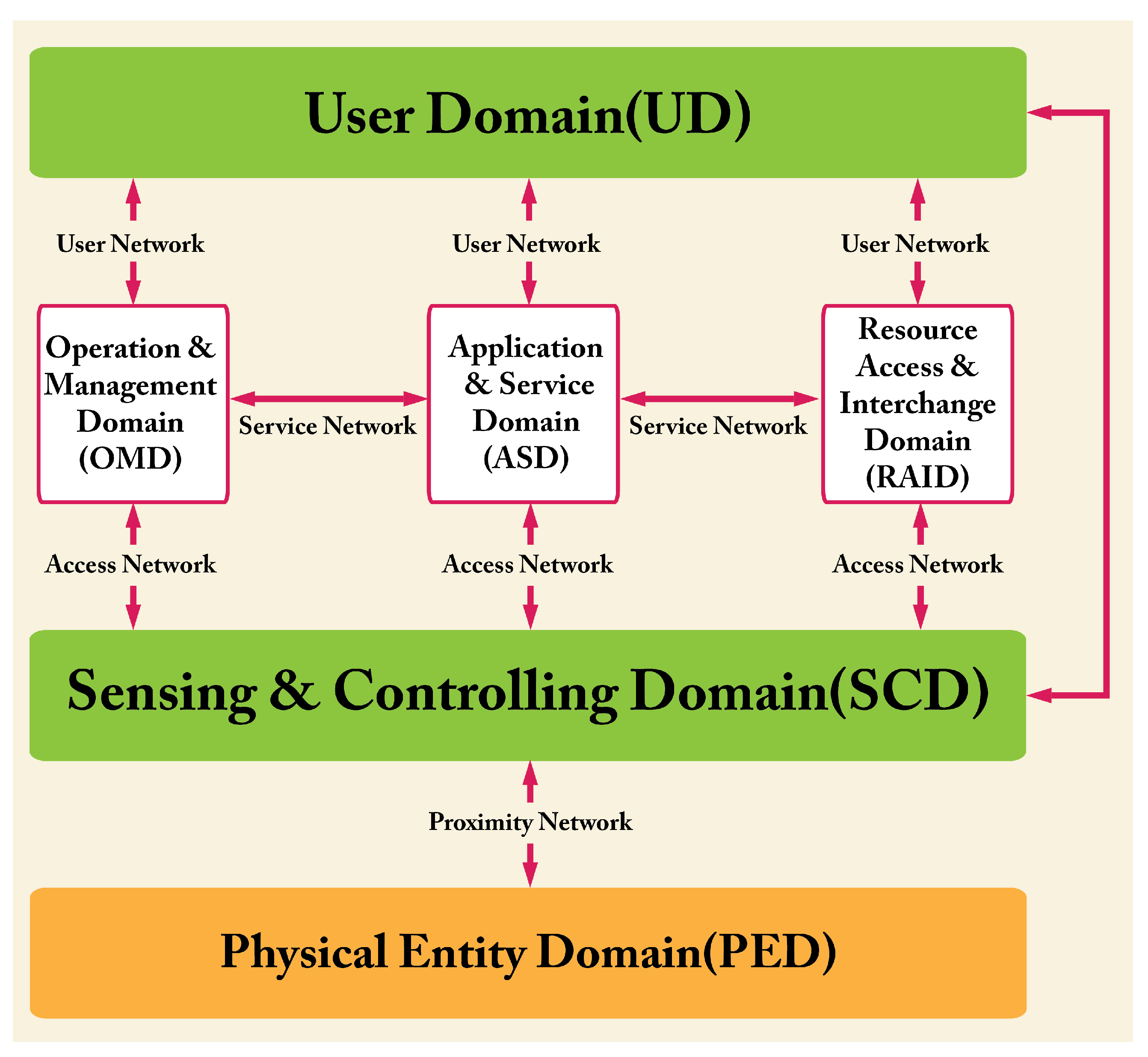
2.2.2. Domain-Based RM
This representation focuses on the tasks that have to be performed. The domain-based RM identifies six mutually exclusive domains (Figure 7). Their meaning is intuitive at this point of the summary of the ISO/ICE:2018 document [6], so we say nothing more about them.
The domains of the IoT RM (and hence the entities inside them) interact by means of four different communication networks (Figure 6 and Figure 7). They are briefly described in the following. The key role played by those networks is to support communication and data exchange activities and interactions between pairs of entities, pairs of domains, or pairs of IoT systems.
Proximity network—The role of this network is to connect sensors and actuators (belonging to the SCD) to the gateways of the IoT system. Proximity networks are necessary because of power and processing limitations of sensors and actuators. As a consequence, their scope is limited to the sensing & controlling domain. IPv6 is an example of a proximity network.
Access network—This network connects IoT gateways (and hence sensors and actuators) to the OMD and the ASD. Such a connection enables the transfer of sensor/actuator data (frequently called “edge data”) to operations logic (from OMD) or to application logic (from ASD). Either wired connections (e.g., broadband, ADSL, Fibre) or wireless connections (e.g., LANs, mobile networks, etc.) are common technologies used in access networks.
Service network—It connects the applications and services in the OMD, the ASD and the RAID.
User network—It connects the user domain with the OMD and ASD; it also connects peer IoT systems and non-IoT systems with the RAID. This network is typically based on the Internet.
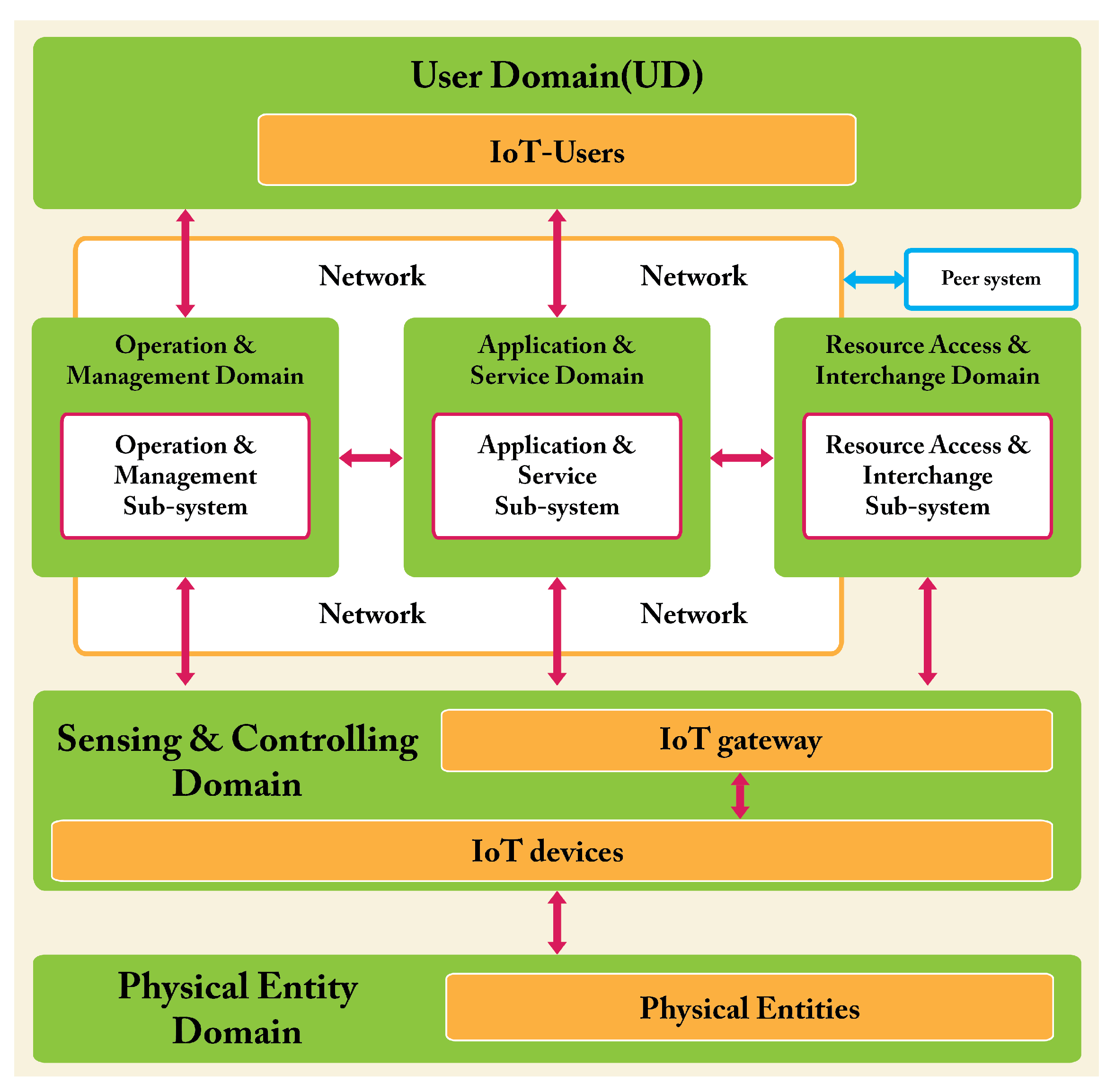
Figure 8 shows that the two representations of the RM are consistent.
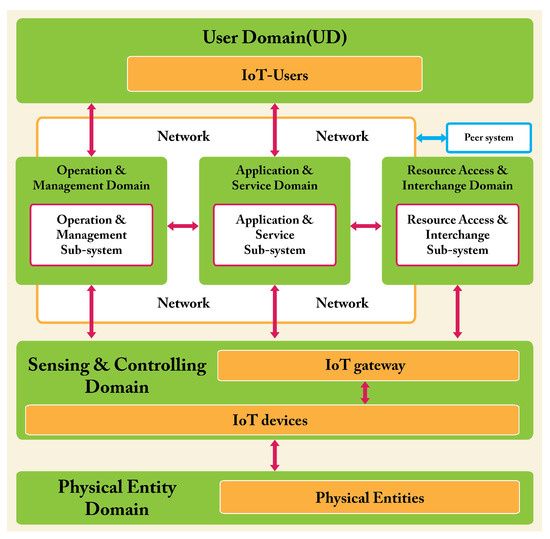
Figure 8.
Entity-based RM vs. domain-based RM.
2.3. IoT Computing Models
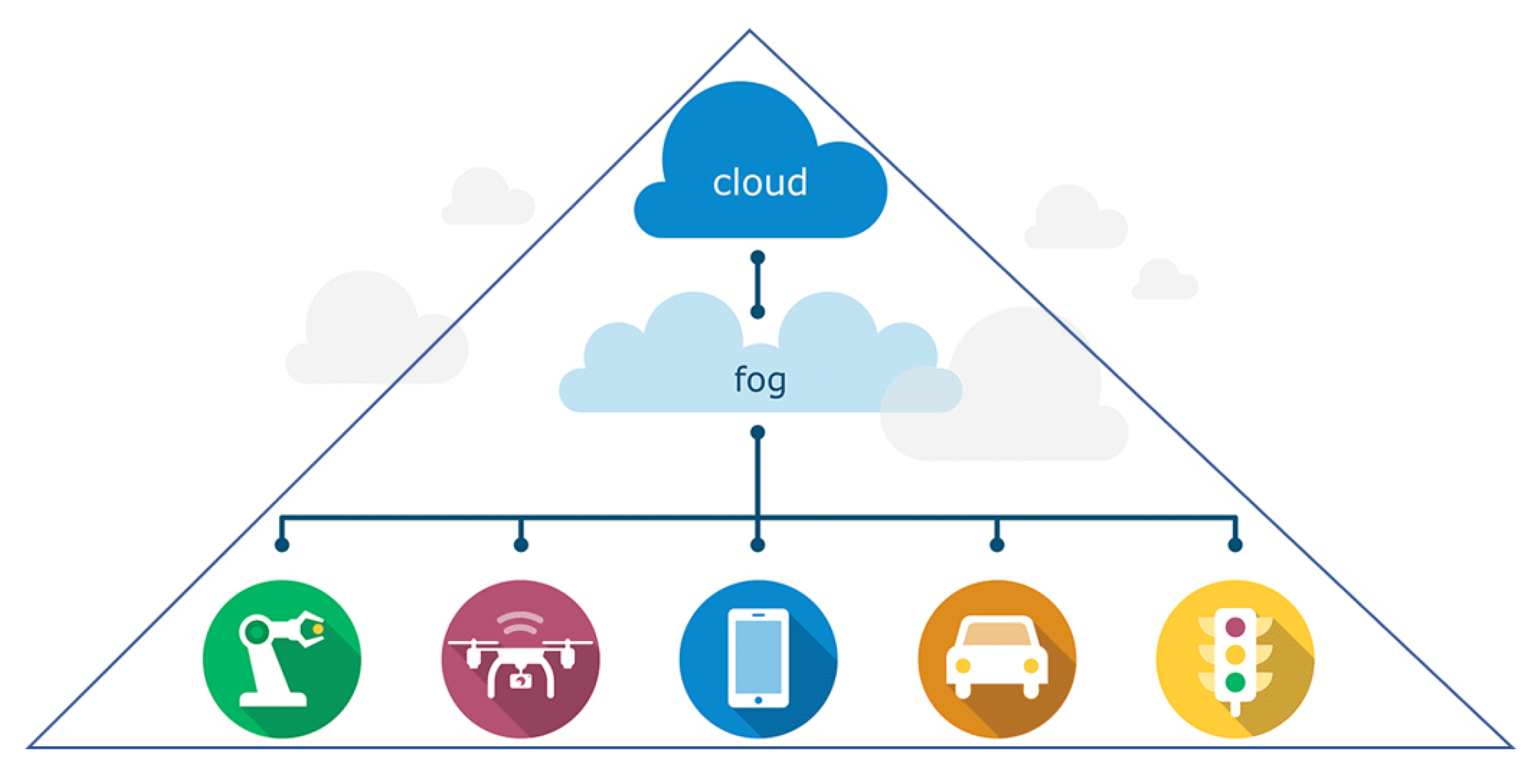
Up until recently, the mandatory deployment model of IoT systems has been the cloud, which offers powerful services, unlimited storage, and computing capacity on-demand; unfortunately, connecting smart devices to the cloud poses severe issues. First of all, connected devices create large volumes of data, which will inevitably result in performance and network congestion challenges. Secondly, there are performance, security, bandwidth, and reliability concerns that make the cloud-only solution not suitable for all the potential real-world applications. The fog-edge computing paradigms have been introduced to bridge the gap between the cloud and IoT devices [5,7,8].
In [5,9], it is stressed that fog and edge computing are often used interchangeably, but both studies agree that these two concepts should be kept distinct. In this paper, we adopt the same point of view. According to [5], fog computing (FC) is a concept that envisions pushing computing power and storage capabilities down to the local network up to reach the gateway level, while EC brings cloud intelligence and storage capabilities at the device level.
2.3.1. Fog Computing
An example can clarify this approach. Let us refer to a high-speed train embedded with hundreds of sensors controlling its journey (besides all the internal parameters). All the sensor readings can be sent to the cloud (for instance, by using expensive satellite links), where the readings will be processed to detect abnormal conditions and send commands back to the train. There are several problems with this scenario: the bandwidth to transport the sensor and actuator data to and from the cloud is expensive; the connections could be susceptible to hackers; it may take several hundred milliseconds to react to an abnormal sensor reading; and if the connection to the cloud is down, or the cloud is overloaded, the control of the train is lost. As an alternative scenario, let us consider placing a hierarchy of local “fog nodes” inside the train. Those nodes can connect to sensors and actuators with inexpensive local networking facilities. Moreover, the fog nodes can be highly secure. Fog nodes can react to abnormal conditions in milliseconds. Moving most of the decision-making functions of this control system to the fog and only contacting the cloud occasionally to report status or receive commands creates a superior control system.
To overcome the mentioned issues, the OpenFog Consortium (www.openfogconsor-tium.org) delivered an architecture which offers the so-called SCALE (security, cognition, agility, latency, and efficiency) advantages over the cloud-only model [10]. The IEEE Standards Association has approved the OpenFog proposal as the official standard for FC and called it “IEEE 1934 in August 2018”. This standard is introduced with the following words (https://standards.ieee.org/ieee/1934/7137/ (accessed on 5 July 2022).): “OpenFog Reference Architecture is a structural and functional prescription of an open, interoperable, horizontal system architecture for distributing computing, storage, control and networking functions closer to the users along a cloud-to-thing continuum of communicating, computing, sensing and actuating entities.”
We can add that cloud and fog computing are on a mutually beneficial, inter-dependent continuum, where certain functions are more advantageous to carry out in fog nodes, while others are better suited to the cloud. The segmentation of what tasks go to fog nodes and what goes to the cloud is application-dependent.
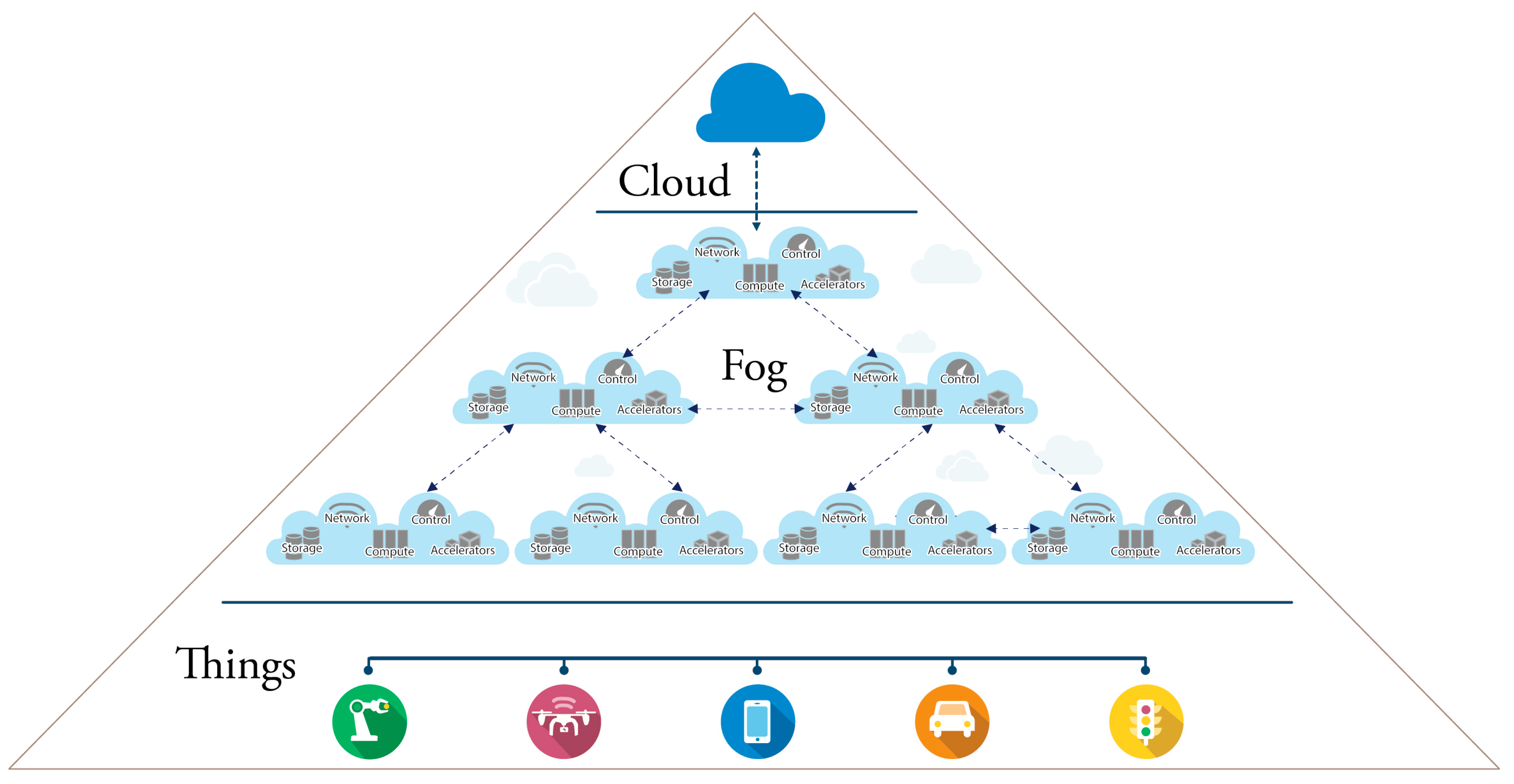
FC architectures are commonly abstracted as a three-layer infrastructure (Figure 9) composed of: (a) IoT devices (e.g., sensors, actuators, smart devices, etc., which represent the front end of whole IoT system and, at the same time, the bottom layer of the architecture. The main purpose of this layer is to sense and capture data. The data are then usually offloaded to the higher layer for the necessary computation); (b) the fog layer (the middle tier); and (c) the cloud layer. The fog layer, in turn, is a network structured as an N-level hierarchy of fog nodes (Figure 10).
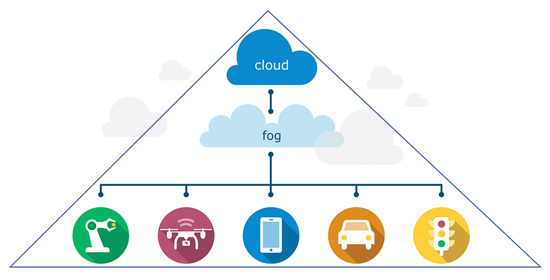
Figure 9.
The FC architecture.
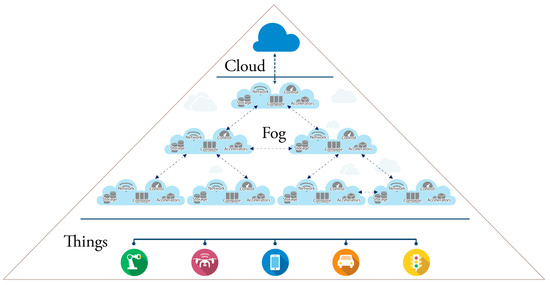
Figure 10.
Details regarding the fog layer.
The number of tiers composing the fog layer depends on many factors, including: (a) the number of sensors involved; (b) the capabilities of the fog nodes at each tier; (c) the amount and type of work required by each tier; (d) the latency constraints to be satisfied.
In IoT systems so organized, each node contributes somehow to the overall service, but its role largely depends on its position in the pyramid. In general, each level of the hierarchy examines and extracts relevant data to create more intelligence while moving towards the root. The mode of communication between the things and the fog devices is wireless in nature, while the fog can communicate with the cloud using both wired and wireless means of communication. Notice that fog nodes communicate with each other both vertically and horizontally according to the load of the IoT system and the requirements of the application.
As stressed by OpenFog [10], the nodes of fog computing networks (a) satisfy requirements for security (security is essential to the overall security of the system. This includes protection for interfaces and computation); (b) supports the management of interfaces; (c) are able to communicate through the network; (d) can store data; (e) utilize accelerators (e.g., FPGA, GPGPU, …) to satisfy both latency and power constraints; (f) have general purpose computing capabilities. Moreover, standard/open-source software runs on them, which is a precondition of interoperability between fog nodes.
2.3.2. Edge Computing
According to [9,11], the architecture of modern IoT systems should consist of four layers: a things layer; an EC layer; an FC layer; and a cloud computing (CC) layer. Such an architecture is a consolidation of the FC architecture.
The things layer consists of fixed-place devices (e.g., smart fridges, smart TVs, surveillance cameras, etc.) and/or mobile devices (e.g., smart vehicles, smart wearable devices, smartphones, etc.) that relate to specific applications (e.g., traffic monitoring, healthcare, smart building, and agriculture). Those devices embed micro-controllers and sensors, so they can carry out some degree of computation. This paradigm is called mist computing. Such an augmented computing capability enables IoT devices to constitute a mesh-like network.
The EC layer is equipped with dedicated routers and switches located close to the IoT devices to act as the gateway to the fog or cloud layer. This proximity minimizes the network traffic. Such a layer can also be equipped with micro-data centers (the so-called cloudlets), able to gather the sensed data of the smart devices, filter, and only send the reduced analyzed data to the fog or cloud for the sake of bandwidth preservation. The concept of a cloudlet was the de facto birth of the mobile edge computing (MEC) paradigm as the integration of mobile computing and EC.
The EC has been widely adopted in various application domains, and Market Research Future expects that the global EC market size is likely to touch USD 168.59 billion between 2020–2030 (Market Research Future, Global edge computing market. Forecast till 2030 February 2020. URL: https://www.marketresearchfuture.com/reports/edge-computing-market-3239 (accessed on 26 May 2022)).
2.4. Middleware
Middleware is the core layer of the architecture of modern IoT systems, where it acts as a bridge between applications and smart devices. Middleware masks the heterogeneity and complexity of the devices, solving many IoT issues and, consequently, simplifying the application development. An appropriate middleware layer is a determinant factor to meet the following requirements: functional-, heterogeneous-, and network-scalability; interoperability; light-weightness; real-timeness; self-adaptability; and service reliability [12].
Ref. [12] is an up-to-date survey on middleware. In the study, the authors summarize the requirements of IoT middleware by analyzing the main features of the following five application domains: environment, healthcare, industry, social, and transportation. In the same paper, the following taxonomies of IoT middleware are proposed: the service-based approach, the event-based approach, the virtual machine-based approach, the database-based approach, and the agent-based approach. Those five approaches are presented and then compared with respect to the six requirements recalled above.
Ref. [13] provides an overview of the proprietary and open-source middleware solutions currently available. The IoT middleware platforms are classified into four types (service-oriented, cloud-based, actor-based, and event-based) and compared from different aspects. The following platforms are taken into account. Cloud-based IoT middleware includes: AWS IoT, Azure IoT Hub, IBM Watson IoT, Google Cloud IoT, Xively, and Oracle IoT. Service-based IoT middleware includes: LinkSmart (Hydra), Kaa (open-source), Global Sensor Networks (GSN), ThingSpeak IoT (open-source), and Aura. Actor-based IoT middleware includes: Calvin (open-source), Node-RED (open-source), Ptolemy Accessor Host (open-source), and Akka (open-source). Event-based IoT middleware: Hermes, Gryphon, Rebeca, and FiWare (open-source).
2.5. Blockchain
Below, we touch on this topic by taking inspiration from [14], which:
- Describes the fundamental components of blockchain technologies (i.e., transactions, digital signatures, blocks, consensus mechanisms, and blockchain types) and their pros/cons when applied in the IoT domain (including eHealth, smart home and smart vehicular networks);
- Reviews almost every recent research work about blockchain;
- Identifies research gaps and challenges in those studies and discusses possible solutions.
In IoT systems, the entire network linking things to the cloud requires protection against malicious attacks and threats that, otherwise, can obstruct IoT services as well as endanger the data security, users’ privacy and confidentiality. Blockchain (invented by Nakamoto in 2008 as the underlying technology of the Bitcoin cryptocurrency) seems to be destined to become the secure- and privacy-preserving technology for IoT applications. Blockchain is a transparent, trusted, and distributed database (called a ledger) on a peer-to-peer network of participants able to provide a secure method to store and process data crossing it. The data unit on the blockchain is called a transaction; sets of transactions are grouped into blocks; confirmed blocks are stored into the (blockchain) ledger. Sequential blocks in the ledger are linked through a cryptographic hash code.
The implementation of the blockchain method implies high computing costs which, today, represent the biggest challenge to its adoption for IoT systems (typically suffering limitations in the power and storage capacities). Indeed, every node/participant keeps a copy of the ledger. Upon the confirmation of a new block, it is relayed throughout the network, and every node appends the confirmed block to its local ledger. Ref. [14] states that it has been calculated that a blockchain node would need about 730 GB of (data) storage per year if 1000 participants exchange an image of 2 MB per day in a blockchain application.
3. The Research Methodology
Our research methodology is based on the well-known guidelines defined in [3] for conducting systematic mapping studies. Those guidelines are structured in terms of three stages: planning, conducting, and reporting. The third stage is self-explanatory, while the second stage consists in the implementation of the first one. Therefore, below, we detail the conducting stage. It has been articulated in terms of three activities: (a) Definition of the study need; (b) Definition of the research question; and (c) Definition of the mapping protocol.
The study need. The need for the study is motivated by the lack of consensus about IoT systems, their basic constituents, and their qualities that have been pointed out in Section 1 as the result of the preliminary investigation we have accomplished. The study aims at providing a holistic overview of the heterogeneous IoT world by taking into account a technology perspective and a business one, that, as far as we know, so far are kept distinct since they are the topic of independent research communities. The target audience are the developers who are interested in better understanding the characteristics of IoT systems in order to take them into consideration when designing and developing IoT systems.
The Research Question (RQ). To achieve the goals of the study, we investigated the following RQ:
What are the available review studies about IoT systems?
Objective: By answering this question, we aim to download review studies about topics connected with issues pertinent to the IoT ecosystem, either from the technology perspective or from the business persepctive.
Output: A set of pertinent review studies.
The mapping protocol. This activity included the four sub-activities described below.
- Search Process. We implemented it as a manual search of articles in the Scopus repository. Scopus, created by Elsevier in 2004, is the largest curated scientific database. In these days, it has achieved 195 million references (http://www.elsevier.com/solutions/scopus/content (accessed on 5 July 2022)). All major publishers (e.g., ACM, IEEE, Springer, Whiley, Elsevier, …) are indexed in Scopus. About 99.11% of the journals indexed in Web of Science are also indexed in Scopus [15]. That is the reason why we queried only Scopus.
- Inclusion criteria. The initial search string was the following (the Scopus engine is case sensitive):”Internet Of Thing” OR “Internet Of Thing (IOT)” OR “Internet Of Things” OR “Internet Of Things (IOT)” OR “Internet Of Things (IoT)” OR “Inter net Of Things (IOT)” OR IOT OR IoT.
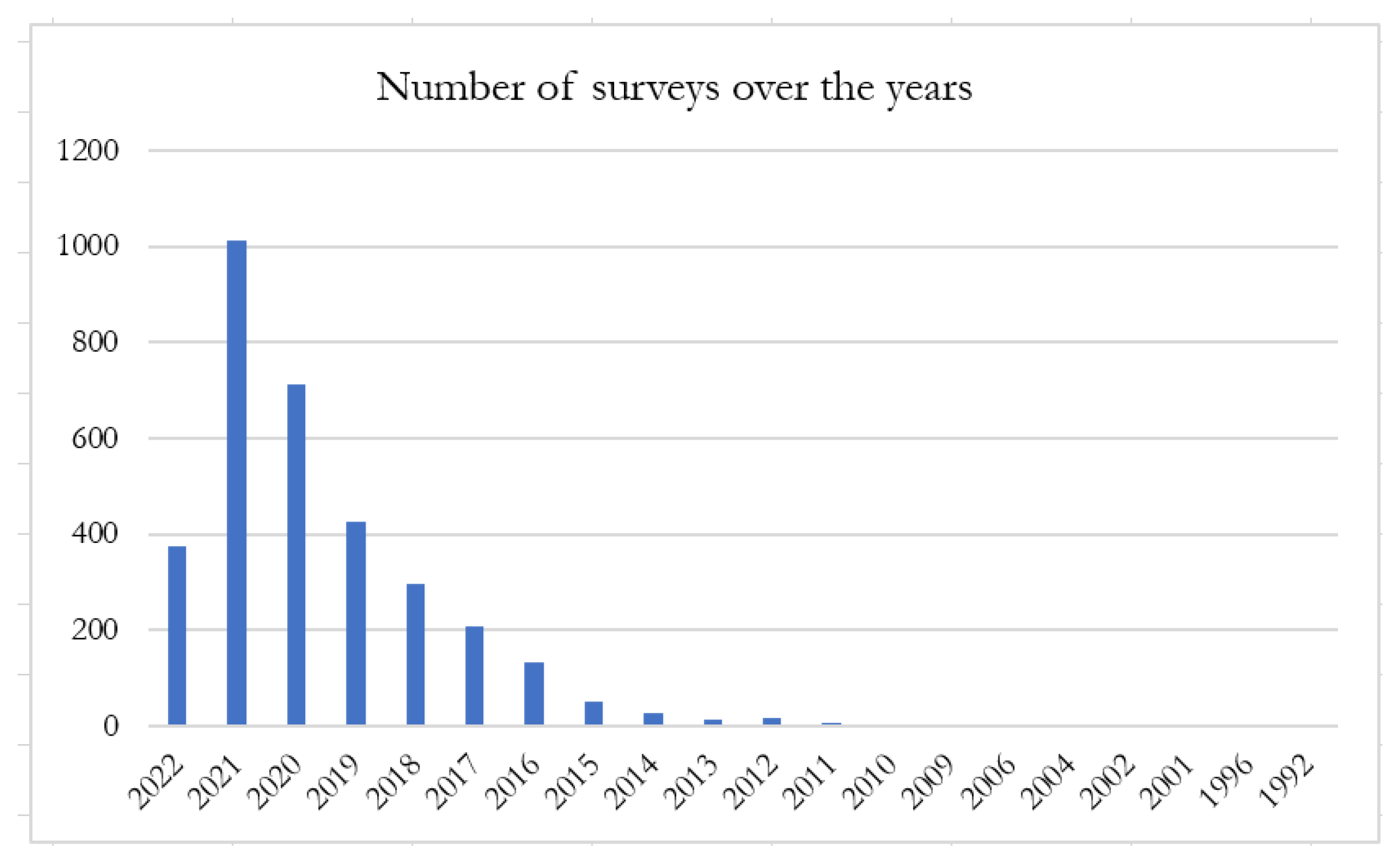
- Exclusion Criteria. As output, we received 148,773 documents. Scopus offers several ways to refine the result of a search. We restricted the output, definitely too large to be investigated, by adding the following three filters: (a) Language: English; (b) Document type: Review; (c) Source type: Journal. The bibliographic search has been restricted to journals as they are the natural destination of review studies, unlike research papers, which very often are made public at conferences. The number of items returned by the search was 3286. Table 1 and Figure 11 show the distribution of these reviews over the years.
 Table 1. Total number of reviews archived into Scopus.
Table 1. Total number of reviews archived into Scopus. Figure 11. The graph of the reviews archived into Scopus.Through the “Source title” item exposed by Scopus, we found that the 3286 reviews came from 160 distinct journals. A large number of them have focuses distant from the IoT, which explains why the papers published in these journals have a mild connection with the IoT ecosystem. A partial list of journals that fall into this category, and which, therefore, were excluded from the research, follows: Advanced Engineering Materials; Advanced Functional Materials; Advanced Healthcare Materials; Advanced Materials; Advanced Materials Technologies; Advanced Optical Materials; Advances in Physics: X; Aggression and Violent Behavior; Chemical Reviews; Current Opinion in Neurology; International Journal of Epidemiology; International Materials Reviews; Journal of Advanced Research in Dynamical and Control Systems; Materials Today; Nano Energy; Nature Communications; Nature Materials; Semiconductor Science and Technology; and Sensors and Materials.To overcome the aforementioned criticality, the initial search was restricted to the 62 journals listed below: IEEE Access; Journal of Network and Computer Applications; IEEE Internet of Things Journal; IEEE Communications Surveys and Tutorials; Internet of Things Netherlands; ACM Computing Surveys; Computer Communications; Future Internet; Wireless Communications and Mobile Computing; Computer Networks; International Journal of Distributed Sensor Networks; Journal of Sensor and Actuator Networks; Security and Communication Networks; Computer Science Review; IEEE Communications Magazine; Proceedings of the IEEE; Computer; Sustainable Cities and Society; Computers in Industry; IEEE Internet Computing; Computers and Security; Journal of Medical Internet Research; Journal of Theoretical and Applied Information Technology; Computers and Electronics in Agriculture; IEEE Pervasive Computing; IEEE Wireless Communications; Journal of Industrial Information Integration; Digital Communications and Networks; IEEE Transactions on Industrial Informatics; International Journal of Environmental Research and Public Health; Journal of Management Analytics; Pervasive and Mobile Computing; Annals of Emerging Technologies in Computing; Communications of the ACM; Health and Technology; IEEE Cloud Computing; Journal of Healthcare Engineering; Smart Cities; Trends in Food Science and Technology; Applied Sciences, Array; Blockchain: Research and Applications; Computer & Security; Digital Signal Processing; Future Generation Computer Systems; Industrial Marketing Management; Information Sciences; Information Systems; Information; Intelligent Systems with Applications; International Journal of Wireless Information Networks; Journal of Ambient Intelligence and Humanized Computing; Journal of Business Research; Journal of Parallel and Distributed Computing; Journal of Retailing and Consumer Services; Journal of Retailing; Journal of Systems Architecture; Journal of Open Innovation: Technology, Market, and Complexity; Mobile Networks and Applications; Sensors; Telematics and Informatics; and Wireless Personal Communications.Five journals (namely the Journal of Business Research; Industrial Marketing Management; Journal of Open Innovation: Technology, Market, and Complexity; Journal of Retailing and Consumer Services; and Journal of Retailing), among the 62 listed above are business-oriented. They have been selected in order to complement the IoT technology perspective with the IoT business perspective.The number of items returned by the new search was 953. This number confirms the great ferment of research about the IoT ecosystem, interest substantiated by the large number and heterogeneity of the topics with a greater or lesser connection with such a domain. Given that the first objective of this work is to offer a tutorial introduction to the IoT ecosystem (Section 1), we carried out a further filter. It consisted of limiting the attention to the reviews published between 2019 and April 2022. As a result, we retrieved 119 articles; this is a manageable number which, at the same time, is definitely significant.
Figure 11. The graph of the reviews archived into Scopus.Through the “Source title” item exposed by Scopus, we found that the 3286 reviews came from 160 distinct journals. A large number of them have focuses distant from the IoT, which explains why the papers published in these journals have a mild connection with the IoT ecosystem. A partial list of journals that fall into this category, and which, therefore, were excluded from the research, follows: Advanced Engineering Materials; Advanced Functional Materials; Advanced Healthcare Materials; Advanced Materials; Advanced Materials Technologies; Advanced Optical Materials; Advances in Physics: X; Aggression and Violent Behavior; Chemical Reviews; Current Opinion in Neurology; International Journal of Epidemiology; International Materials Reviews; Journal of Advanced Research in Dynamical and Control Systems; Materials Today; Nano Energy; Nature Communications; Nature Materials; Semiconductor Science and Technology; and Sensors and Materials.To overcome the aforementioned criticality, the initial search was restricted to the 62 journals listed below: IEEE Access; Journal of Network and Computer Applications; IEEE Internet of Things Journal; IEEE Communications Surveys and Tutorials; Internet of Things Netherlands; ACM Computing Surveys; Computer Communications; Future Internet; Wireless Communications and Mobile Computing; Computer Networks; International Journal of Distributed Sensor Networks; Journal of Sensor and Actuator Networks; Security and Communication Networks; Computer Science Review; IEEE Communications Magazine; Proceedings of the IEEE; Computer; Sustainable Cities and Society; Computers in Industry; IEEE Internet Computing; Computers and Security; Journal of Medical Internet Research; Journal of Theoretical and Applied Information Technology; Computers and Electronics in Agriculture; IEEE Pervasive Computing; IEEE Wireless Communications; Journal of Industrial Information Integration; Digital Communications and Networks; IEEE Transactions on Industrial Informatics; International Journal of Environmental Research and Public Health; Journal of Management Analytics; Pervasive and Mobile Computing; Annals of Emerging Technologies in Computing; Communications of the ACM; Health and Technology; IEEE Cloud Computing; Journal of Healthcare Engineering; Smart Cities; Trends in Food Science and Technology; Applied Sciences, Array; Blockchain: Research and Applications; Computer & Security; Digital Signal Processing; Future Generation Computer Systems; Industrial Marketing Management; Information Sciences; Information Systems; Information; Intelligent Systems with Applications; International Journal of Wireless Information Networks; Journal of Ambient Intelligence and Humanized Computing; Journal of Business Research; Journal of Parallel and Distributed Computing; Journal of Retailing and Consumer Services; Journal of Retailing; Journal of Systems Architecture; Journal of Open Innovation: Technology, Market, and Complexity; Mobile Networks and Applications; Sensors; Telematics and Informatics; and Wireless Personal Communications.Five journals (namely the Journal of Business Research; Industrial Marketing Management; Journal of Open Innovation: Technology, Market, and Complexity; Journal of Retailing and Consumer Services; and Journal of Retailing), among the 62 listed above are business-oriented. They have been selected in order to complement the IoT technology perspective with the IoT business perspective.The number of items returned by the new search was 953. This number confirms the great ferment of research about the IoT ecosystem, interest substantiated by the large number and heterogeneity of the topics with a greater or lesser connection with such a domain. Given that the first objective of this work is to offer a tutorial introduction to the IoT ecosystem (Section 1), we carried out a further filter. It consisted of limiting the attention to the reviews published between 2019 and April 2022. As a result, we retrieved 119 articles; this is a manageable number which, at the same time, is definitely significant. - Data Collection. We downloaded (as a PDF file) the title, authors’ name, keywords, abstract and DOI for each article belonging to the set of items returned by Scopus.
- Data Analysis. At this stage the title, keywords, and abstract of the 119 reviews were read by three authors of the present paper. Despite the fact that, in systematic mapping studies, the investigation is usually limited to taking into account the title and abstract of each selected item, we downloaded the PDF of the 119 reviews to give a correct answer to the RQ. The other three authors read the introduction and conclusion sections of those articles. Periodic meetings were organized among the authors to make alignments regarding the proper classification of the reviews. This approach was applied iteratively until all the reviews had been explored and mapped.
4. A Map of Recent IoT Review Studies
“The data extraction process for mapping studies (…) can (…) be termed a classification (…) stage.” [3] (p. 44); accordingly, the topics covered in the 119 review articles were grouped as three distinct dimensions (Table 2): (a) functional blocks (sometimes also called the constituent components) of the IoT systems (the first column), (b) their qualities— i.e., their non-functional characteristics (the second column), and (c) other topics (the third column). The six functional blocks are as in [5], the six qualities come from [16], while the six items in the last column complete those in the other two columns of the table.

Table 2.
Dimensions and topics of the IoT ecosystem.
4.1. IoT Functional Blocks
Below, the six functional blocks in Table 2 are briefly described ([5] discusses them meticulously) and linked to the concepts introduced in Section 2. Appendix A lists the reviews (published from 2019 to April 2022) where these concepts are deepened.
- Identification It has been already said that IoT systems are complex systems composed of physical entities, sensors, actuators, network components, and software components. It is essential that each entity in an IoT system is distinguishable from each other in order to make it possible for the system to monitor and communicate with specific entities. The identification of the entities is done by attaching tags to them (Section 2.1). In this way, a unique identification code is associated unambiguously to the “things”. In the domain-based RM (Section 2) the identification block belongs to the SCD (Figure 7).
- Sensing IoT networks sense, aggregate, and broadcast data from smart objects located in a given area. IoT sensors can be deployed as individual devices (smart sensors, smart wearables, actuators) or as a network of devices (such as WSN) that execute a function collectively. A wide range of sensors are currently available on the market place and used in IoT applications [5,17,18]. In the domain-based RM (Section 2) the sensing block belongs to the SCD (Figure 7).
- Networking IoT networks are a combination of heterogeneous smart devices, communication technologies, and protocols that all together perform application-specific tasks. Communication protocols provide instructions on data coding, transmission and flow controls, sequencing, and error correction. There are a bulk of technologies for IoT communication [19]. Communication technologies usually used in IoT networks include near-field communication, narrowband IoT, ultra-wide bandwidth, LTE-A, WiMax, WiFi and LoRa. A comparison among largely utilized communication technologies in IoT networks may be found in [5]. As said in Section 2, there are four different kinds of networks to connect the physical components in the six domains of an IoT system: proximity networks, access networks, service networks, and user networks (Figure 7). The networking functional block also corresponds to the networks block in the entity-based RM (Figure 6).
- Computation Standard computation is performed by the CPU and is managed by the hardware’s operating system. Unfortunately, such a paradigm is not suitable in the IoT domain where, as the number of IoT devices grows, a heterogeneous approach is required. The findings from many recent studies have shown that future IoT systems need hybrid computing capabilities ranging from low-power IoT nodes to mid-end gateways to high-computing cloud networks [20,21]. Section 2.3 has introduced the most relevant IoT computing models. Computation in IoT systems takes place at each layer of the RM (Figure 6 and Figure 7).
- Services Service is an abstract concept (Section 2) that is usually implemented as software. IoT systems can provide an increasing number of ubiquitous services with different performances and functionalities. A service in the IoT environment can be invoked by a user to perform specific tasks, such as, for instance, returning the humidity of a room [22]. Several types of services are implemented inside the operation and management sub-system, the application and service sub-systems, and the resource access and interchange sub-system (Figure 6).
- Analytics IoT systems sense and convey a huge volume of heterogeneous data that have to be stored and later processed by efficient algorithms to get benefit from them. Analytics services of various types are usually provided by the application and service sub-systems (Figure 6) and the ASD (Figure 7). Analytics services are also supported by the IoT gateway, typically operating on data coming from the IoT devices or from the device data store. Ref. [23] stressed the primary role that will be played by the technologies, frameworks, and platforms for big data analytics.
Ref. [5] is a rigorous systematic literature review that proposes an IoT technological stack, which has the merit of decoupling the enabling technologies, the underlying infrastructure, and vendor implementations concerning the IoT ecosystem. In the paper, the IoT functional blocks are thoroughly investigated at each layer of the stack. Table 6 in [5] associates the IoT functional blocks briefly recalled in this sub-section with the pertinent technologies.
4.2. IoT Qualities
Quality aspects are non-functional characteristics of IoT systems. As said at the beginning of Section 4, the IoT qualities we refer to come from [16]. With respect to the original taxonomy, we merged trust into security (similarly to what is done in [6]). Below, we briefly introduce the six qualities in Table 2 and link them to the concepts introduced in Section 2. Appendix B collects the pertinent reviews.
- Security: Information security is a major concern of any ICT system, and IoT systems are no exception. IoT systems present particular challenges for information security because they are distributed and involve a large number of diverse components. As in [6], hereinafter, security (of an IoT system) is defined as the combination of availability, confidentiality, and integrity. Availability means that the IoT system is accessible and usable on demand by an authorized entity; the latter includes both human users and service components. Availability is a characteristic of devices, data and services. Confidentiality means that information is not disclosed to unauthorized individuals, entities, or processes. Integrity means that the data to be used for decision-making processes are accurate and complete. Therefore, integrity ensures that the data have not been altered by faulty or unauthorized devices, by malicious actors, or by environmental causes. An increasing number of scholars are investigating the security improvements that can be achieved in IoT systems using a blockchain-based approach (Section 2.5) (e.g., [24,25]). The security issue spans the four different categories of IoT networks of Figure 6.
- Privacy: privacy characterizes aspects related to the protection of the data of an IoT system. The privacy requirement spans all layers of IoT systems from the bottom to the top, that is, from the sensing of data, to its storage, to the processing (Figure 6). Security functions in IoT systems assure the authenticity, availability, confidentiality, and integrity of information travelling the networks. The concept of privacy overlaps the concept of protection of personally identifiable information (PII). If PII is stolen or is misused, the people identified by the information may be harmed somehow. ISO/IEC 29100 details the principles to protect PII. Task offloading is one of the key enabling ECs, (which, as has been mentioned in Section 2.3.2, continues to grow at a steep pace). Because of the vulnerability of edge servers and the wireless transmission features, serious privacy concerns come along with offloading. Ref. [26] is a comprehensive survey that systematically reviews recent studies about privacy-preserving offloading methods.
- Interoperability: interoperability (called heterogeneity in [6]) is the ability of IoT systems to seamlessly communicate and use each other’s services. The IoT is typically cross-system, cross-product and cross-domain. Realizing the full potential of IoT requires interoperability between heterogeneous components and systems. A certain number of temperature sensors from different manufacturers and with different specifications integrated into a single IoT system is a simple, and at the same time common, example of heterogeneity. Middleware is the core component of the IoT systems devoted to enhance the interoperability (Section 2.4).
- Scalability: Let us refer to a smart city IoT system where the number of the attached sensors increase constantly over a time. The growth will determine an increase in the volume of sensor data flowing in the system, in the volume of data being stored in the database, in the number of devices handled by the management system, and in the number of temperature readings processed by services and applications. It is important that the IoT system continues to function effectively despite its growth. Ref. [12] distinguishes among functional scalability, heterogeneous scalability, and network scalability. Functional scalability means that a functionality can be added to, modified from, or removed from the IoT system without affecting existing activities. Heterogeneous scalability denotes the ability to add heterogeneous components and resources. Lastly, network scalability is the ability to add or remove network nodes without the need to restart the whole system. Middleware is the core component of the IoT systems devoted to enhancing the scalability (Section 2.4).
- Latency. Latency concerns the time an IoT system needs before responding to an external stimulus (e.g., a user request via a smartphone). Obviously, transferring large volumes of data from the environment to the cloud (the most common architecture thus far) increases energy consumption, resource consumption, and network latency, which is not suitable for time-critical applications. To address this issue, the edge and fog computing paradigms have been proposed. They allow data storage and processing at network edges rather than on a distant cloud data center (Section 2.3).
- Reliability: reliability is a property of consistent, intended behavior and results [6]. Reliability is relevant with respect to communications, data, and computing. Reliability of data is of great importance for the decision-making processes of many IoT systems, while reliability of communication networks is important for ensuring the availability and correct operation of IoT systems. Health-related applications, industrial manufacturing operations and time-critical applications are examples of applications that pose stringent requirements on the reliability. Edge-fog computing and middleware enhance the reliability of IoT systems (Section 2.3 and Section 2.4).
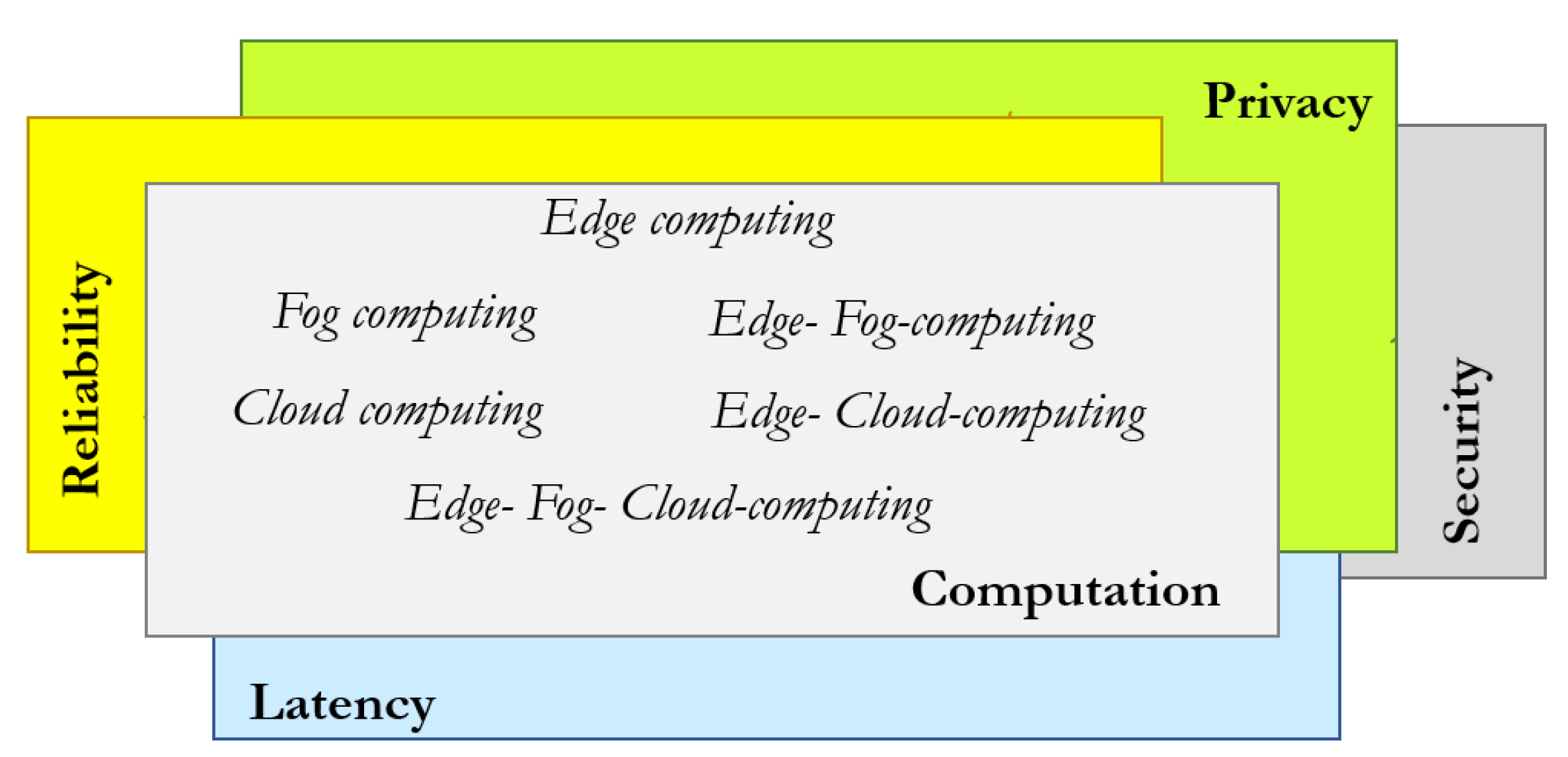
In light of the above discussion about the qualities of IoT systems, it is possible to notice that there exists an overlapping between the computation functional block and the security, privacy, reliability, and latency quality attributes (Figure 12).
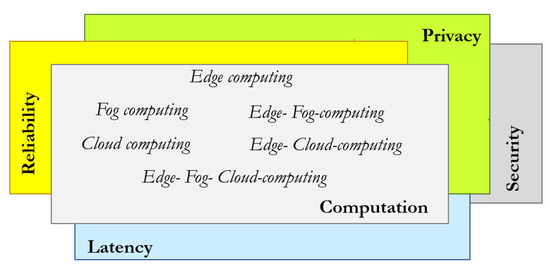
Figure 12.
Overlapping of the computation functional block and four qualities of IoT systems.
4.3. Other Topics
The third column of Table 2 lists the following six items: application domains, business models, customers, servitization, digital twins, and software engineering. These arguments complement those in the first and second column of the same table.
The larger the domain of the IoT applications becomes, the more relevant the topics become concerning business models, customers, and servitization.
The digital twin (DT) is an emerging approach that promotes the softwarization of physical things into logical ones. At present, DT promises to change the way products and systems are made and used.
From the software engineering perspective, IoT applications are distributed over heterogeneous devices, operate in dynamic and uncertain environments, and, in the worst case, they can stop providing their services abruptly. It follows that to be able to provide IoT users (either humans or machines—Section 2) with robust IoT applications is a serious challenge.
Below, we introduce these five topics. Appendix C collects the pertinent reviews where the interested reader may find a suitable deepening.
4.3.1. Application Domains
IoT is becoming popular due to its wide range of applications in healthcare, retail, smart parking, transportation, agriculture, public safety, smart lighting, smart homes, smart buildings, manufacturing, logistics, and disaster management, just to mention a few (Figure 13). The list of industries and businesses using IoT is incredibly long, and the COVID-19 pandemic has forced rapid adoption because it holds the promise of enabling businesses to sail safe in the new normal.
Figure 13.
Examples of IoT application domains.
Ref. [27] summarizes the structure and the methodology of sustainable IoT applications; reviews the most important IoT applications; discusses the major challenges of the sustainable growth of IoT applications; highlights open research directions in the field of IoT; and proposes directives for new business opportunities.
4.3.2. Business Models
Business models are conceptual tools that explain the logic of an organization, the way it operates, and hence, how it creates value. In the meantime, while issues such as security, privacy, reliability, and network instability are solved (Section 2), currnetly, important questions are under investigation about how businesses should innovate their business models in order to create and capture added value thanks to the adoption of the IoT technology. Indeed, the IoT revolution can reshape industries, modify work processes, create new economic benefits, save time, money and ultimately improve the quality of our life. At present, “a practical and effective IoT business model is yet to emerge” [28]. The reviews collected in Appendix C provide insight into the phenomenon of IoT in order to help organizations understand the potential of such a technology and, hence, how value could be created by implementing it. For example, the literature review reported in [29] identifies four groups of articles: the first one contains studies examining the innovation of business models that takes place thanks to the digital/IoT technologies; the second collects studies dealing with the interconnection between business models and strategies in the general context of digitalization; the third group contains studies that focus on digital platforms and how they are shaping business models; eventually, the fourth group collects studies that analyze the relationship between digital/IoT technologies and business models in a servitization perspective.
4.3.3. Customers
IoT innovation impacts the customers’ life in two opposite directions, as is pointed out below. It was not too long time ago when industries and retailers claimed that the key to attract and maintain customers was determined by the quality of the products they sell and their price. Now, things have changed dramatically, as explained by Batat [30], which says that: “today consumers increasingly buy experiences rather than goods or services”. Given that nowadays, customers are tech-savvy, the adoption of IoT technology is becoming mandatory for industries and retailers to meet this goal; indeed, the IoT has the potential to provide personalized services to customers (since IoT is able to bridge the gap between the digital world and the real world).
The other side of the coin concerns the protection of customer identity and personal data. Indeed, the growth of IoT-enabled devices and the developments in artificial intelligence and 5G are intensifying the pressure on privacy. In a very recent review about the state-of-the-art of people-centered distributed ledger technology (DLT) [31], Pinto, da Silva, and Moro conclude that DLT-IoT architectures and the protection of individuals’ interests in the data economy is in an embryonic state. In the same study, those authors conjecture that in the near future, there will be an acceleration in the proposal of reliable people-centered IoT solutions based on DLT.
Ref. [31] gives a picture of people-centered data control milestones starting from the 1960s. Here, we only mention the more recent and relevant initiatives. In 2016, the European Union published the General Data Protection Regulation; in the same year, the Self-Sovereign Identity (SSI) concept emerged. With SSI, people have the opportunity of controlling their personal data, share it or even sell it. In 2018, the MyData Global was created with the objective of empowering individuals by “improving their right to self-determination regarding their personal data”, and California released the California Consumer Privacy Act.
4.3.4. Servitization
Moving from product to service is called servitization. There are a number of reasons why manufacturers and retailers should implement the servitization paradigm:
- Revenue growth and profitability: By adding services to their offering, companies increase their number of revenue streams, and those become recurring. Complimenting the product portfolio with ongoing services to the customers allows their income to become more predictable and secure, which in turn helps insulate the company from unpredictable market conditions.
- Improved customer outcomes: Focusing on solutions instead of products allows companies to think in terms of their customers’ needs, which means companies can adapt products and services to help customers achieve those outcomes; furthermore, this helps companies to respond faster to issues and challenges that may arise. The resulting increase in customer satisfaction builds a stronger relationship and increased loyalty.
- Higher entry barriers: The more established a relationship with customers is, the more difficult it is for someone to come in and steal market share. Servitization means that customers benefit from support and knowledge in real terms, every day.
In the present time, with digitalization advancing rapidly, more and more companies are understanding the benefits of making the final step, that is, implementing the so-called digital servitization [32]. Digitalization and servitization are distinct business model innovations. In fact, manufacturing industries and retailers can invest in digitalization without providing services; vice versa, they can offer services without the support of digital technologies. However, it is worth notice that digitalization is an important enabler of servitization. Specifically, embedding IoT-enabled sensors and devices into physical products makes them intelligent and connected, so it becomes feasible for industries and retailers to achieve closer and better proximity to their customers and, at the same time, reorganize their value chains by expanding the scope of their product–service offerings.
The digital servitization paradigm addresses three relevant requirements of modern industries, that is: agility, connectivity, and decentralization. Additionally, one more point in favor of IoT-based digital servitization derives from the useful insights that can be gained by analyzing the performance of a product and using this information for continuous improvement.
All said, digital servitization can be defined as the process by which a company transforms its product-centered business model to a service-centered business model with the support of IoT/digital technologies, allowing the reorganization of its business processes, capabilities, products, and services to enhance the value for customers and simultaneously increase the company’s performance, [32], p.109. Such a definition gathers technical (i.e., offering and technology) and business perspectives.
The notion of digital servitization coincides with the notion of smart services adopted in [33]: “Smart service is a service whose value and efficiency extends beyond classic, digital service and is delivered through a smart product.”
4.3.5. Digital Twins (DTs)
A severe challenge posed by IoT systems composed of thousands of “things” (such as, for instance, smart cities) concerns how to manage efficiently, and often in real-time, the big data that they produce. To become truly smart/intelligent, IoT systems have to possess, in addition, the following three core characteristics: awareness, response, and prediction. Real-time awareness (of IoT systems) is fundamental in order to keep rapidly changing parameters under constant control (for instance, the pollution level in the downtown of a city). By referring, once again, to the city domain, awareness coupled with quick response time can enhance the quality of life of citizens and, sometimes, even save lives. The ability (of IoT systems) to predict is the precondition for them to proactively respond to events. There is increasing convergence over the DT paradigm as the solution of this problem.
Many definitions of the notion of DTs have been proposed. For instance, [34] lists eight independent definitions coming from as many articles. Three alternative DT definitions, taken from [35], follow. DT refers to the ability to clone a physical object into a software counterpart. The softwarized object (the DT) reflects all the important properties and characteristics of the original object (the twin) within a specific application domain.
A DT is composed of three parts: (a) the physical object in the real space; (b) the virtual object in the virtual space; and (c) connected data that ties the physical and virtual together [36].
A DT of an IoT system consists of (a) a set of models of the system; (b) a set of contextual data traces and/or their aggregation/abstraction collected from the system; and (c) a set of services that allow using the data/models from/of the original system [37].
IoT sensors continuously collect the data necessary for companies to derive value from physical things. This feed of real-time data is what ensures that a DT maintains an actual live copy of an asset, process, or ecosystem. The marriage between the virtual and physical world allows the analysis of data and the monitoring of the IoT system to foresee problems before they occur, prevent downtime, develop new opportunities and even elaborate plans for the future by carrying out simulations.
The DT notion impacts the business model, customer (experience), and (quality of) servitization topics (discussed previously) (the point of view held by Thomas Kaiser, SAP Senior Vice President of IoT, in 2017 explains this statement: “Digital twins are becoming a business imperative, covering the entire lifecycle of an asset or process and forming the foundation for connected products and services. Companies that fail to respond will be left behind.” (https://www.forbes.com/sites/bernardmarr/2017/03/06/what-is-digital-twin-technology-and-why-is-it-so-important/?sh=320198902e2a—accessed on 25 May 2022)) and software engineering (discussed next).
4.3.6. Software Engineering
From a software engineering point of view, IoT applications execute on a network consisting of hundreds to thousands of heterogeneous devices (e.g., sensors, actuators, storage, and user interface devices), operating in dynamic and uncertain environments, and they can fail to provide their services without notice. Consequently, their development differs from the development of traditional applications.
Another difference with the development of traditional software (that has to be taken into account in the development of IoT applications) resides in the multitude of involved stakeholders, namely: software designers, developers, domain experts, and technologists. It follows that, in the process of IoT application development, knowledge from multiple concerns intersects. Moreover, those stakeholders have to address issues belonging to different life cycle phases, including development, deployment, and maintenance.
Scholars are debating whether the model-driven engineering (MDE) paradigm can mitigate the challenges posed by the development of IoT applications, but, so far, the question of whether MDE can play a key role in the future of IoT is still an unanswered research question [38]. Below, we mention two studies that adopt the MDE paradigm.
To reduce IoT development effort, Patel and Cassou [39] suggest: (a) separating this task into different concerns; (b) providing stakeholders with a set of high-level languages to specify them. In detail, their proposal consists of (a) a conceptual model; (b) a development methodology; and (c) the implementation of a development framework. Through the conceptual model, it is possible to address four major concerns for IoT application development, namely domain-specific concepts, functionality-specific concepts, deployment-specific concepts, and platform-specific concepts. In turn, the development framework supports three modeling languages: Srijan Vocabulary Language (to describe domain-specific features of the IoT application), Srijan Architecture Language (to describe application-specific functionality of the IoT application), and Srijan Deployment Language (to describe deployment-specific features consisting information about physical environment where devices have to be deployed).
MontiThings is a modeling infrastructure that facilitates the development of IoT applications by increasing abstraction, separating concerns, and their deployment to heterogeneous devices [40]. Specifically, MontiThings (a) supports the separation of error-handling from the development of business logic; (b) features a model-driven toolchain for generating executable containers; and (c) allows an efficient deployment of them even for large IoT systems. MontiThings specifies architectures of IoT systems as networks of components that exchange data with each other via black box ports. MontiThings is an extension of MontiArc (an Architectural Description Language for the MDE of IoT systems), and is implemented using MontiCore (a language workbench for the engineering of textual Domain Specific Languages) and the template engine Freemarker.
5. IoT Ecosystem
The prevalent number of definitions of the IoT-ecosystem notion comes from a technology perspective. Several scholars have proposed their own definition. Ref. [41], for example, states that an IoT ecosystem connects heterogeneous components in a handled way to build an efficient and secure system, while ref. [42] says that an IoT ecosystem comprises the following four basic components: sensors and actuators, connectivity/gateway, data processing, and the user interface.
In 2012, ref. [43] proposed a definition of the IoT business ecosystem (i.e., a definition of IoT ecosystem from the business perspective) as a metaphor adopted from biology. It is well-known that a natural life ecosystem is a biological community of interacting organisms along with their physical environment, with which they also interact. Similarly, in [43], an IoT business ecosystem is defined as being comprised of the community of interacting individuals and companies along with their socio-economic environment.
We are now able to give a definition of the IoT ecosystem which merges the technology perspective of the IoT domain with the business one. This widening of the perimeter of the definition of the IoT ecosystem is motivated by the fact that, from a commercial point of view, the IoT represents a huge opportunity for most companies to enter new markets and generate increasing revenue.
An IoT ecosystem connects resource-constrained heterogeneous devices in a handled way to build an efficient and secure system, whose final aim is to deliver services of practical utility to a community comprising a multitude of stakeholders. At a high level of abstraction, the involved stakeholders are: the industries providing the IoT technology, the developers of IoT solutions, and the customers (either individuals, companies, or machines).
6. IoT Taxonomies
The heterogeneity and complexity of the IoT ecosystem originated a huge number of classification of such a domain. Such classifications are usually called taxonomies. Classification of the IoT can be carried out in many ways, as it emerges, for example, from [16], which reports on a mapping study about 73 papers concerning IoT system taxonomies. Ref. [19], for instance, proposes an IoT taxonomy which takes into account protocols, architecture, energy efficiency, scalability, security, social networking, and inter-operability, while [44] proposes taxonomies with respect to communication technologies, operating systems, gateway operating modes, architecture, middleware, platforms, storage techniques, capability and performance, entity and service life cycle, and applications. Another interesting IoT taxonomy is adopted in [41], comprising IoT devices, operating systems, communication interfaces and networks, middleware, platforms, and applications. The present paper, too, has introduced an IoT taxonomy consisting of the 18 topics listed in Table 2.
7. Conclusions
The aim of the paper was to introduce the reader to the IoT ecosystem by providing him with a broad-spectrum description of the many topics that can be traced back to it. The study of the state of the art made it possible to identify 3 distinct dimensions for a total number of 18 topics. For each topic, the link is provided to 119 very recent reviews (from 2019 to April 2022) where technical details are given, details that developers will not find in this manuscript given its introductory nature.
Author Contributions
Conceptualization, P.D.F. and G.P.; methodology, P.D.F.; data curation, R.P., F.P. and D.I.; writing—original draft preparation, F.P.; visualization, M.M.; supervision, G.P.; funding acquisition, G.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Gruppo Software Industriale, Italy.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| IIoT | Industry Internet of Things |
| IoT CM | IoT Conceptual Model |
| IoT RM | IoT Reference Model (RM) |
| PED | Physical Entity Domain |
| OMD | Operation and Management Domain |
| ASD | Application and Service Domain |
| RAID | Resource Access and Interchange Domain |
| UD | User Domain |
| CC | Cloud Computing |
| FC | Fog Computing |
| EC | Edge Computing |
| MEC | Mobile Edge Computing |
| SCD | Sensing and Controlling Interface |
| UML | Unified Modeling Language |
| MDE | Model-Driven Engineering |
| API | Application Programming Interface |
| PII | Personally Identifiable Information |
| SSI | Self-Sovereign Identity |
Appendix A. Recent Review Papers about IoT Functional Blocks
This appendix is composed of six parts as per the number of topics belonging to the functional blocks dimension (Table 2). Each part collects “metadata” about reviews (published between 2019 and April 2022 and indexed in the Scopus database) which deal with the corresponding topic. The metadata describing each survey consists of four items: (a) the reference number (within this paper); (b) the keywords listed in the source file; (c) the summary of the major contributions of the study; and (d) other topics taken into account in the study (if any). The notation “0X-0Y” denotes topic 0Y belonging to dimension 0X.
| Reviews about Identification |
|
| Reviews about Sensing |
|
| Reviews about Networking |
|
| Reviews about Computation |
|
| Reviews about Services |
|
| Reviews about Analytics |
|
Appendix B. Recent Review Papers about IoT Qualities
This appendix is composed of six parts as per the number of topics belonging to the qualities dimension (Table 2). Each part collects “metadata” about reviews (published between 2019 and April 2022 and indexed in the Scopus database) that deal with the corresponding topic. The metadata describing each survey consists of four items, as explained in Appendix A.
| Reviews about Security |
|
| Reviews about Privacy |
|
| Reviews about Interoperability |
|
| Reviews about Scalability |
| Reviews about Latency |
|
| Reviews about Reliability |
Appendix C. Recent Review Papers about IoT Other Topics
This appendix is composed of six parts as per the number of topics belonging to the Other Topics dimension (Table 2). Each part collects “metadata” about reviews (published between 2019 and April 2022 and indexed in the Scopus database) which deal with the corresponding topic. The metadata describing each survey consists of four items, as explained in Appendix A.
| Reviews about Application Domains |
|
| Reviews about Business Models |
|
| Reviews about Customers |
|
| Reviews about Servitization |
|
| Reviews about Digital Twins |
|
| Reviews about Software Engineering |
|
References
- Wang, J.; Lim, M.K.; Wang, C.; Tseng, M.L. The evolution of the Internet of Things (IoT) over the past 20 years. Comput. Ind. Eng. 2021, 155, 107174. [Google Scholar] [CrossRef]
- Internet of Things. An Action Plan for Europe. An-Europe. 2009, Volume 278, pp. 1–15. Available online: https://www.eesc.europa.eu/en/ourwork/opinions-information-reports/opinions/internet-things-action-pl (accessed on 5 July 2022).
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering. EBSE Technical Report EBSE-2007-01. 2007. Available online: https://www.525444systematicreviewsguide.pdf (accessed on 5 July 2022).
- Aly, M.; Khomh, F.; Yacout, S. What Do Practitioners Discuss about IoT and Industry 4.0 Related Technologies? Characterization and Identification of IoT and Industry 4.0 Categories in Stack Overflow Discussions. Internet Things 2021, 14, 100364. [Google Scholar] [CrossRef]
- Ali, O.; Ishak, M.K.; Bhatti, M.K.L.; Khan, I.; Kim, K.-I. A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface. Sensors 2022, 22, 995. [Google Scholar] [CrossRef] [PubMed]
- ISO/IEC 30141:2018, Internet of Things (IoT)—Reference Architecture. Available online: https://standards.iso.org/ittf/PubliclyAvailableStandards/c065695_ISO_IEC_30141_2018(E).zip (accessed on 25 May 2022).
- Alli, A.A.; Alam, M.M. The fog cloud of things: A survey on concepts, architecture, standards, tools, and applications. Internet Things 2020, 9, 100177. [Google Scholar] [CrossRef]
- Firouzi, F.; Farahani, B.; Marinšek, A. The convergence and interplay of edge, fog, and cloud in the AI-driven Internet of Things (IoT). Inf. Syst. 2022, in press. [Google Scholar]
- Aslanpour, M.S.; Gill, S.S.; Toosi, A.N. Performance evaluation metrics for cloud, fog and edge computing: A review, taxonomy, benchmarks and standards for future research. Internet Things 2020, 12, 100273. [Google Scholar] [CrossRef]
- OpenFog: Reference Architecture for Fog Computing. 2017. Available online: https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf (accessed on 27 March 2022).
- Gill, S.S. A Manifesto for Modern Fog and Edge Computing: Vision, New Paradigms, Opportunities, and Future Directions. In Operationalizing Multi-Cloud Environments; Nagarajan, R., Raj, P., Thirunavukarasu, R., Eds.; EAI/Springer Innovations in Communication and Computing; Springer: Cham, Switzerland, 2022. [Google Scholar] [CrossRef]
- Zhang, J.; Ma, M.; Wang, P.; Sun, X.-D. Middleware for the Internet of Things: A survey on requirements, enabling technologies, and solutions. J. Syst. Archit. 2021, 117, 102098. [Google Scholar] [CrossRef]
- Kassab, W.; Darabkh, K.A. A–Z survey of Internet of Things: Architectures, protocols, applications, recent advances, future directions and recommendations. J. Netw. Comput. Appl. 2020, 163, 102663. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in IoT: Challenges and solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Singh, V.K.; Singh, P.; Karmakar, M.; Leta, J.; Mayr, P. The journal coverage of Web of Science, Scopus and Dimensions: A comparative analysis. Scientometrics 2021, 126, 5113–5142. [Google Scholar] [CrossRef]
- Alkhabbas, F.; Spalazzese, R.; Davidsson, P. Characterizing Internet of Things Systems through Taxonomies: A Systematic Mapping Study. Internet Things 2019, 7, 100084. [Google Scholar] [CrossRef]
- Stavropoulos, T.G.; Papastergiou, A.; Mpaltadoros, L.; Nikolopoulos, S.; Kompatsiaris, I. IoT Wearable Sensors and Devices in Elderly Care: A Literature Review. Sensors 2020, 20, 2826. [Google Scholar] [CrossRef]
- Laghari, A.A.; Wu, K.; Laghari, R.A.; Ali, M.; Khan, A.A. A Review and State of Art of Internet of Things (IoT). Arch. Comput. Methods Eng. 2022, 29, 1395–1413. [Google Scholar] [CrossRef]
- Sobin, C.C. A Survey on Architecture, Protocols and Challenges in IoT. Wirel. Pers. Commun. 2020, 112, 1383–1429. [Google Scholar] [CrossRef]
- Jin, X.; Lib, L.; Dang, F.; Chen, X.; Liu, Y. A survey on edge computing for wearable technology. Digit. Signal Process. 2022; in press. [Google Scholar] [CrossRef]
- Rosendo, D.; Costan, A.; Valduriez, P.; Antoniu, G. Distributed Intelligence on the Edge-to-Cloud Continuum:A Systematic Literature Review. J. Parallel Distrib. Comput. 2022; in press. [Google Scholar]
- Achir, M.; Abdelli, A.; Mokdad, L.; Benothman, J. Service discovery and selection in IoT: A survey and a taxonomy. J. Netw. Comput. Appl. 2022, 200, 103331. [Google Scholar] [CrossRef]
- Khan, M.A.; Siddiqui, M.S.; Rahmani, M.K.I.; Husain, S. Investigation of Big Data Analytics for Sustainable Smart City Development: An Emerging Country. IEEE Access 2022, 10, 16028–16036. [Google Scholar] [CrossRef]
- Saxena, S.; Bhushan, B.; Ahad, M.A. Blockchain based solutions to secure IoT: Background, integration trends and a way forward. J. Netw. Comput. Appl. 2021, 181, 103050. [Google Scholar] [CrossRef]
- Kaur, M.; Khan, M.Z.; Gupta, S.; Alsaeedi, A. Adoption of Blockchain With 5G Networks for Industrial IoT: Recent Advances, Challenges, and Potential Solutions. IEEE Access 2022, 10, 3138754. [Google Scholar] [CrossRef]
- Li, T.; He, X.; Jiang, S.; Liu, J. A survey of privacy-preserving offloading methods in mobile-edge computing. J. Netw. Comput. Appl. 2022, 203, 103395. [Google Scholar] [CrossRef]
- Ali, Z.H.; Ali, H.A. Towards sustainable smart IoT applications architectural elements and design: Opportunities, challenges, and open directions. J. Supercomput. 2021, 77, 5668–5725. [Google Scholar] [CrossRef]
- Cranmer, E.E.; Papalexi, M.; tom Dieck, M.C.; Bamford, D. Internet of Things: Aspiration, implementation and contribution. J. Bus. Res. 2022, 139, 69–80. [Google Scholar] [CrossRef]
- Agostini, L.; Nosella, A. Industry 4.0 and business models: A bibliometric literature review. Bus. Process. Manag. J. 2021, 7, 1633–1655. [Google Scholar] [CrossRef]
- Batat, W. Experiential Marketing: Consumer Behavior, Customer Experience and the 7Es; Routeledge, Taylor & Francis Group: London, UK; New York, NY, USA, 2019. [Google Scholar]
- Pinto, F.; da Silva, C.F.; Moro, S. People-centered distributed ledger technology-IoT architectures: A systematic literature review. Telemat. Inform. 2022, 70, 101812. [Google Scholar] [CrossRef]
- Favoretto, C.; Mendes, G.H.S. Oliveira, M.G.; Cauchick-Miguel, P.-A.; Coreynen, W. From servitization to digital servitization: How digitalization transforms companies’ transition towards services. Ind. Mark. Manag. 2022, 102, 104–121. [Google Scholar] [CrossRef]
- Fischer, M.; Heim, D.; Hofmann, A. Christian Janiesch, Christoph Klima, Axel Winkelmann. A taxonomy and archetypes of smart services for smart living. Electron. Mark. 2020, 30, 131–149. [Google Scholar] [CrossRef]
- Lim, K.Y.H.; Zheng, P.; Chen, C.-H. A state-of-the-art survey of Digital Twin: Techniques, engineering product lifecycle management and business innovation perspectives. J. Intell. Manuf. 2020, 31, 1313–1337. [Google Scholar] [CrossRef]
- Ante, L.; Fischer, C.; Strehle, E. A bibliometric review of research on digital identity: Research streams, influential works and future research paths. J. Manuf. Syst. 2022, 62, 523–538. [Google Scholar] [CrossRef]
- Grieves, M. Product Lifecycle Management: Driving the Next Generation of Lean Thinking; McGraw-Hill: New York, NY, USA, 2006. [Google Scholar]
- Kirchhof, J.C.; Michael, J.; Rumpe, B.; Varga, S.; Wortmann, A. Model-driven Digital Twin Construction: Synthesizing the Integration of Cyber-Physical Systems with Their Information Systems. In Proceedings of the ACM/IEEE 23rd Inter. Conference on Model Driven Engineering Languages and Systems (MODELS ’20), Virtual Event, 18–23 October 2020; ACM: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Bucchiarone, A.; Cabot, J.; Paige, R.F.; Pierantonio, A. Grand challenges in model-driven engineering: An analysis of the state of the research. Softw. Syst. Modeling 2020, 19, 5–13. [Google Scholar] [CrossRef]
- Patel, P.; Cassou, D. Enabling high-level application development for the Internet of Things. J. Syst. Softw. 2015, 103, 62–84. [Google Scholar] [CrossRef]
- Kirchhof, J.C.; Rumpe, B.; Schmalzing, D.; Wortmann, A. MontiThings: Model-Driven Development and Deployment of Reliable IoT Applications. J. Syst. Softw. 2022, 183, 111087. [Google Scholar] [CrossRef]
- Bansal, S.; Kumar, D. IoT Ecosystem: A Survey on Devices, Gateways, Operating Systems, Middleware and Communication. Int. J. Wirel. Inf. Netw. 2020, 27, 340–364. [Google Scholar] [CrossRef]
- Raj, A.; Shetty, S.D. IoT Eco-system, Layered Architectures, Security and Advancing Technologies: A Comprehensive Survey. Wirel. Pers. Commun. 2022, 122, 1481–1517. [Google Scholar] [CrossRef]
- Mazhelis, O.; Luoma, E.; Warma, H. Defining an Internet-of-Things Ecosystem. In Internet of Things, Smart Spaces, and Next Generation Networking; Andreev, S., Balandin, S., Koucheryavy, Y., Eds.; ruSMART NEW2AN 2012; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7469, pp. 1–14. [Google Scholar] [CrossRef]
- Sivagami., P.; Illavarason, P.; Harikrishnan, R.; Reddy, G.V.S.R. IoT Ecosystem. A survey on Classification of IoT. In Proceedings of the First International Conference on Advanced Scientific Innovation in Science, Engineering and Technology, ICASISET, Chennai, India, 16–17 May 2020. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).