Abstract
Electronic health record (EHR) data breaches create severe concerns for patients’ privacy, safety, and risk of loss for healthcare entities responsible for managing patient health records. EHR systems collect a vast amount of user-sensitive data, requiring integration, implementation, and the application of essential security principles, controls, and strategies to safeguard against persistent adversary attacks. This research is an exploratory study into current integrated EHR cybersecurity attacks using United States Health Insurance Portability and Accountability Act (HIPAA) privacy and security breach reported data. This work investigates if current EHR implementation lacks the requisite security control to prevent a cyber breach and protect user privacy. We conduct descriptive and trend analysis to describe, demonstrate, summarize data points, and predict direction based on current and historical data by covered entity, type of breaches, and point of breaches (examine, attack methods, patterns, and location of breach information). An Autoregressive Integrated Moving Average (ARIMA) model is used to provide a detailed analysis of the data demonstrating breaches caused by hacking and IT incidents show a significant trend (coefficient 0.84, p-value < 2.2 × 10−16 ***). The findings reveal a consistent rise in breaches—particularly from hacking and IT incidents—disproportionately affecting healthcare providers. The study highlights that EHR data breaches often follow recurring patterns, indicating common vulnerabilities, and underlines the need for prioritized, data-driven security investments. These findings validate the hypothesis that most EHR cybersecurity attacks are concentrated using similar attack methodologies and face common vulnerabilities and demonstrate the value of targeted mitigation strategies to strengthen healthcare cybersecurity. The findings highlight the urgent need for healthcare organizations and policymakers to prioritize targeted, data-driven security investments and enforce stricter controls to protect EHR systems from increasingly frequent and predictable cyberattacks.
1. Introduction
Integrated electronic health record (EHR) system is an extensive real-time digital patient-centered health record accessible from many different interoperable automated systems and available instantly and securely to authorized users through standardized health information data format, which supports system functions [1]. Healthcare facilities using EHR systems face enormous and persistent cybersecurity attacks that challenge the integrity of critical EHR infrastructure with dire consequences to patient privacy, patient safety, and risk to an organization’s finances or reputation. As such, confidentiality, integrity, and availability of the EHR system are very crucial, as health providers need to be able to make life-or-death decisions by recording accurate patient hospital-related activities, including but not limited to diagnosis, personally identifying information (PII), and demographic information [1]. The 2019 National Electronic Record survey shows that approximately 89% of USA office-based physicians use EHRs [2]. In addition, over 90% of large, medium, small rural, and critical access hospitals use some form of EHRs [2]. There are four core EHR uses, with increasing subs uses as research and development in technology continue to grow. The four uses include providing healthcare practitioners with history and a potential projected view on patients’ health; aiding healthcare practitioners in enhancing the quality of patient care and efficiency in care by providing access to current health state concerning disease, medication history, medical exams records, from a central location; reducing the cost of care by removing redundancy in procedures, reducing errors (i.e., such as wrong prescription and drug interactions); and serving as a memory bank for practitioners and patients in understanding previous ailments and care [3].
Such core functionalities make EHR systems an essential part of any healthcare information yechnology infrastructure, requiring every measure to guarantee that sensitive patient information such as PII, medical history, diagnosis, medications, treatment plans, immunization dates, allergies, radiology images, laboratory and test results are protected against any adverse threat (either internally or externally). For example, PII collected by a Health custodian during a patient visit, if not safeguarded and subjected to a data breach, can result in identity theft with severe consequences (i.e., impersonation attacks and fraud). Although there are many definitions of what constitutes a data breach, for the purpose of this work, a data breach is limited to any unauthorized access to patients PII, demographic data, diagnosis data, or other EHR system data in a way that compromises the confidentiality of patients or system information.
Unfortunately, there are documented challenges [1,4] in designing and securing EHR systems, including but not limited to how to adequately address security and privacy control requirements for the secure collection, retention, and use of available data. Other difficulties include but are not restricted to protecting data in multiple states (transit, storage, or process); protecting infrastructure to support EHR; access control provisioning to online EHR resources to prevent data breaches; determining the authenticity of an individual during enrollment into the EHR before granting access, privileges, credentials, and services; securing access to other stakeholders to connect to the EHR and how to protect stakeholder’s sensitive data; and providing education to consumers, providers, and employees on the importance of protecting data and somehow introducing incentives [5].
In the past, such challenges have resulted in data breaches in terms of some key organization EHRs. As documented in Table 1, several healthcare facilities across the globe have suffered data breaches. Such Cyber attacks indicate that security measures employed to secure EHRs in most jurisdictions might be subpar and require measured security control and aggressive solutions to address security vulnerabilities that can lead to a successful data breach for EHRs.

Table 1.
Selection of major cyberattacks related to health providers [6,7,8,9,10,11].
As Healthcare data breaches become omnipresent, as depicted in Table 1, patients continuously lose confidence in the security and protection of their health records [4]. Therefore, they are uncomfortable providing information or interest in the fully participating EHR system [12]. Patients’ trust and confidence that Healthcare providers are protecting their private and sensitive information at all costs have dwindled. In a recent global survey, approximately 80% of Americans, 81% of Britons, and 83% of Australians had strong reservations about allowing their paper health record to be migrated into the EHR system because of the risk of identity theft, the possibility of privacy breaches, intrusive privacy violation by nosy healthcare workers, or other employers [12]. Participants from the survey acknowledge a high risk of exposure to privacy threats while their medical records are managed by healthcare organizations [12]. Keeping EHR secure is a challenge that government and healthcare providers around the globe are beginning to grasp in its infancy [13].
The significance of this work focuses on the integrated EHR systems that have revolutionizing healthcare delivery by enabling real-time, patient-centered, and data-driven decision-making across interoperable platforms. These systems serve not only as comprehensive repositories for patient health data, including diagnoses, treatments, medications, and imaging, but also as critical enablers of cost-effective, accurate, and timely healthcare services. As more healthcare institutions adopt EHRs, their role in ensuring continuity of care, reducing medical errors, and improving patient outcomes becomes increasingly indispensable.
However, this growing reliance on EHRs has also made them a prime target for cybersecurity threats. Given the volume and sensitivity of information stored—particularly personally identifiable information (PII) and diagnostic data—any breach can result in severe consequences, including identity theft, medical fraud, and erosion of public trust. The escalating frequency and sophistication of cyberattacks, as evidenced by global incidents involving millions of compromised records, underscores the urgent need for stronger data protection mechanisms in EHR systems.
Despite growing awareness, there remain significant gaps in how EHR systems are secured, particularly within integrated healthcare environments. Existing security frameworks often fail to address the full spectrum of privacy and protection requirements, especially those involving data in various states (in transit, at rest, or in use). Furthermore, current systems lack robust mechanisms for secure identity verification, access provisioning, and stakeholder protection across distributed networks.
This study is an exploratory study into current integrated EHR cybersecurity attacks using United States Health Insurance Portability and Accountability Act (HIPAA) privacy and security breach reported data. This work investigates if current EHR implementation lack the requisite security control to prevent a cyber breach and protect user privacy? A descriptive and trend analysis is conducted to describe, demonstrate, summarize data points, and predict direction based on current and historical data by covered entity, type of breaches, and point of breaches (examine, attack methods, patterns, and location of breach information). Autoregressive Integrated Moving Average (ARIMA) model is used to provide a detailed analysis of the data demonstrating breaches.
In addressing the research question, “Do current Electronic Health Record (EHR) implementations lack the requisite security controls to prevent cyber breaches and adequately protect patient data privacy?” Based on current literature and preliminary work, we hypothesize that:
H1: Most successful EHR cybersecurity breaches exploit similar attack vectors and stem from common security vulnerabilities, indicating that current EHR implementations lack sufficient security controls to prevent unauthorized access and protect patient privacy.
In addressing our stated research question and testing our hypothesis, we assess the current solutions in the literature and conduct an exploratory study on existing HIPAA data breaches between 2010 and 2025. Based on our findings, this work makes two key contributions to the field of health informatics and cybersecurity:
- A literature overview on EHR security
- A statistical and trend analysis of U.S. Healthcare data breaches using reported HIPAA data
This study adopts a mixed-methods approach, including a comprehensive literature review, analysis of major healthcare cyberattacks from 2010 to 2024, and the design of a tailored security framework. The proposed solution integrates encryption, identity verification, anomaly detection, and stakeholder-specific access controls. Its effectiveness is evaluated through theoretical modeling and risk assessment simulations, benchmarked against current industry standards.
The rest of this work is divided into Section 2, background, addressing why EHR security privacy should be of great concern. Section 3 discusses related work. Section 4 presents the methodology. Section 5 and Section 6 presents results, and analysis, Section 7 focuses on the discussion and Section 8 conclusion.
2. Background
The current landscape of EHR system security, privacy, and related safety concerns continues to be critical issues attracting attention in mainstream media as health entities continue to suffer from Cyberattacks. To develop a firm grasp of the security and privacy requirements, we review the background and current EHR security landscape, including but not limited to the following:
2.1. Overview EHR System & Security Requirements
Most advanced countries, such as Canada and the United States, have accepted the importance and significantly benefited from establishing health infrastructure [2]. However, although there are many EHR benefits, complex cybersecurity issues must be resolved to provide privacy and security assurance to stakeholders. Some security issues result from the varied size of EHR data repository and complexity, and the designated strategies of protecting access, securing data and systems, providing the proper access control, and securing physical infrastructure [14]. For example, the universal healthcare system in Canada is homogenous and involves millions of interactions between patients and healthcare professionals. This usually results in over “3.5 million hospital discharges from general and allied special hospitals; over 800 hospitals, some 123,000 in-patient beds; More than 28,000 general practitioners and 27,000 medical specialists; Approximately 230,000 registered nurses in addition to nursing assistants; and More than 9000 pharmacists, 6000 occupational therapists and 9000 physiotherapists” [1]. Figure 1 below shows multiple data sources and possible interactions that can occur within an EHR system and, therefore, require meticulous security controls to protect such complex interactions.
Figure 1.
Multiple EHR Data Sources.
The security of an EHR system must begin with project initiation [15]. It must incorporate EHR system policy application, access control design, data collection security, data transmission, storage security, application security, infrastructure security, and patient privacy. In addition, an adequately secure EHR system should satisfy the following security principles:
- I.
- Confidentiality: The patient record during the collection, storage, and access stages must be private and confidential so that no unauthorized person or entity may be able to inspect the content of the patient record [3].
- II.
- Integrity: Good data integrity must be defined so that only authorized persons can modify patient records, and proper auditing is put in place to enforce nonrepudiation. A data integrity policy must be implemented and enforced since a patient’s previous record is paramount to their care [3].
- III.
- Availability: Necessary care, ensuring systems are robust and redundant, is taken. First, it must be guaranteed that EHR systems are available anytime, any day. Second, the EHR system must have close to 0% downtime due to its critical role during patient care. Third, all necessary efforts must be implemented to defend against attacks such as Denial of Service, Distributed Denial of Service, and others. Lastly, the hosting server must have the redundant capability to accommodate hardware failure and ensure healthcare providers have continuous access to health records [3].
Other fundamental EHR security principles must be critically analyzed to address shortfalls in maintaining the security of EHR systems and data. Such principles are required to provide holistic EHR security integration to address systems components and interactions ranging from the issue of data classification, data ownership, data confidentiality, data access, data integrity, and data maintenance requirements in EHR systems [16]. These principles must be closely monitored to provide optimum data security for various data states (e.g., storage, transit, etc.) within any EHR system or any user interaction with data within the EHR system.
2.2. Data Ownership
There is fierce debate on the ownership of data in healthcare in various jurisdictions [17]. The ownership of information on patient activities, such as prescriptions taken and diagnoses at hospitals, is a complex issue in many jurisdictions worldwide [18]. Healthcare data ownership is inconsistent globally compared to other fields, such as banking. The data collected, such as transactions on credit cards and spending behavior, is clearly defined as directly owned by the bank that issued the credit card [19]. Although patient records can be similar to information collected by financial institutions, there is consistent complexity in defining the Information owner when the law, medicine, and technology (electronic) intersect [20]. For example, in 1992, Canada’s Supreme Court, in a case dealing with this complex issue regarding a patient’s medical record ownership, set ownership to primarily physicians of health records, with only the patients have access rights to them. Quiet, unfortunately, such a comparison view of electronic data ownership and hard copy ownership introduces challenges considering that electronic records deal with the elusive nature of information (data existing on multiple mediums at the same time), blurring of public and private spaces, and actual physical security [21]. In the past, such a definition of data ownership and security responsibility was based on much speculation and points to the fact that EHR data cannot be monetized. Further, such thinking has led hospitals or healthcare providers not to take all necessary to protect EHR [14].
Further, for countries that enjoy publicly funded Healthcare (e.g., Canada or the UK), providers do not have to deal with losing clientele due to electronic health data breaches [22]. First, this results from the fact that most Universal Healthcare is based on jurisdiction. This means that regardless of how poorly a hospital protects patient health records. Patients have no option but to attend the same hospital if it is the closest provider to their home address. Secondly, funding is not directed at several patients seen in such jurisdiction but rather a complex and intertwined aggregate. Finally, there is not much financial loss to hospitals that disregard protecting patients electronically [16]. For example, in the province of Ontario, Canada, “funding is based primarily on a principle of global (or base) funding where a set budget is provided to each hospital annually” [16].
To address the issue of who owns data in a secure EHR, the designer must clearly define data ownership and assign data accountability to the owner. This means either through legislation or internal EHR information protection policy. There must be a way to trace any issues regarding data breaches to the data owner and investigate to ensure that prudent security measures are in place. In a nutshell, implementing punitive measures can easily act as a catalyst to ensure that hospitals (data owners) of EHR data continuously invest in the security of patient data. With this said, any established data-sharing agreement should not impede a health professional’s ability to comply with the obligations regarding medical records in performing their responsibilities or access such records and, where required, transition the data to another service. The healthcare provider should ensure that health professionals comply with their obligations to secure patient data, irrespective of any nuisances that may affect the EHR system [23]. Therefore, the data-sharing agreement should focus on looking for avenues where the health professional has only required access to PHI but at the same time can provide access to patients requiring access to the PHI without having to burden the health professional’s ability to conduct his core responsibility patient care within the EHR.
2.3. Confidentiality and Privacy of Data
Providing confidentiality for data and patient privacy is complex and involves several moving parts that must be synchronized. These include but are not limited to employee training on confidentiality, tools and a measure to ensure confidentiality, and information security policies to enforce the behavior of information owners and ensure confidentiality. The confidentiality and privacy of EHRs can range from a curious healthcare worker trying to snoop on a new boyfriend’s health record to a more severe breach of patient privacy, including illegal access to patient records through an adversary. The confidentiality principle within EHR is essential, as it ensures compliance initiatives established by health or related patient privacy laws. However, confidentiality and privacy principles can be daunting as they are intertwined with human factors or error-prone processes. Human factors can contribute to undesirable failures ranging from lack of training and understanding of confidentiality by healthcare workers. The lack of adequate measures to ensure employee access is properly logged to establish accountability of access records is essential. Also, there are no adequate punitive measures on information security policy violations by employees to deter preventable errors such as copying and transferring unencrypted data, and inadequate technological solutions to provide automatic safeguards to deal with minimal human errors [24]. It is imperative to note that confidentiality issues such as unauthorized disclosure may harm reputation, credibility, privacy, or regulatory Compliance with the health system.
In dealing with the human factors that negatively affect data security in any EHR deployment, the Healthcare organization must develop an end-to-end personnel practice starting from job posting, hiring, training, and background checks. Therefore, much emphasis must be placed on employees’ training and development. In reference to the employee training, we are not limiting it to employees or stakeholders who directly interact with the EHR but rather expanding the scope of employees to include janitors, hospital aides, and others who have physical access to the EHR system or through login. In addition, we must understand that intentional breaches of an EHR system can be performed through social engineering attacks, where any hospital employee can be a point of contact. Social engineering attacks involve deceiving people into breaching their security practices and allowing unauthorized access to their network, and the success of professional hackers sometimes depends on such human error [24]. For example, for “eleven months, Frank Abagnale impersonated a Chief Resident Pediatrician in a Georgia hospital under the alias Frank Conners” [25]. He gained access to this role and the health records of Georgia Hospital after becoming a friend’s doctor, his neighbor. However, without a proper background check, he was subsequently offered a temporary Supervisor of Resident interns’ position after tricking the real doctor into thinking he was qualified [25].
3. Related Work
3.1. EHR System Security and Data Breaches
The growing digitization of healthcare systems has increased the reliance on electronic health records (EHRs), making data privacy, integrity, and access control critical challenges. We present current research on the privacy and security of EHR system and provides details on unique research work that significantly contributes to privacy and security-related patient data issues. To date, various proposed architectural designs have either run short of required security principles or missed the details with the necessary and critical data protection schemes required for protecting EHR systems in storage, processing, or transit. Most solutions proposed a data security framework, which is not fully inclusive through the EHR system development life cycle and implementation. Several works [26,27,28,29,30,31] have looked at EHR security and privacy challenges, but currently, a limited number of works focus on defining a holistic solution. Most of these authors proposed work that lack consideration of security at the forefront of development of deployment. Rather in most of these works cited most EHR system development, security and privacy integration is an afterthought, fragmented, and improperly thought through [26,28]. Most of the published materials or recently deployed EHR system within Canada and the United States does not provide or recommend solutions that can address the issue of data security concerning design, implementation, and the entire system life cycle. Current works do not fully address patient privacy compliance requirements and issues surrounding developing stakeholder training or cybersecurity policies.
The current electronic health record infrastructure (EHR) privacy and security conceptual architecture “ref. [32] proposes privacy and security conceptual architecture”. It takes a stab at a framework that mitigates patient data breaches in an EHR system. Their work focuses on the business and technical architecture for interoperable EHR systems. The conceptual architecture only illustrates high-level services, data storehouses, and data presented within the enterprise. The author’s [32] blueprint focuses on interoperability within the systems but does not focus and lacks requisite security principles in the architecture. This work [32] fell short in addressing direct patient data privacy compliance challenges to regulations such as PHIPA or HIPPA. The authors [32] fail to propose solutions to the technical specificities required to provide data security within any EHR system. The proposed framework and recommendations did not adequately address unique data security within the EHR system. This does not include several services necessary to ensure the privacy and security of personal health information (PHI) stored or accessed by EHR system users. For this work, a more functional design or model of EHR security architecture is necessary to focus on making security a key component of all interactions within an EHR system. The emphasis of their architecture should not just strictly focus on the interoperability of the various key services and their functionalities but rather incorporate the security of those services and all other interactions between the services. Although the authors proposed conceptual architecture as a roadmap for designing and implementing common services within EHR, security integration is required at the grassroots level.
Several other research works are looking at ways to protect data within EHR [1,3,26,32]. For example, a recent work published by Camps et al. [3], “Security Requirements for a Lifelong Electronic Health Record System: An Opinion”, describes the security requirements for EHR and emphasizes the principles of confidentiality, integrity, and legal value. The authors’ [3] work compared localized patient health records (PHR) and centralized EHR. The authors [3] looked at the various security principles required for both systems to provide health data protection and access vulnerabilities and essential security requirements needed to implement EHR and proposed fourteen principles for securing EHR [3]. Although the authors’ [3] work provided good contributions in addressing EHR security, their work has a research gap by narrowly focused on integrity and legal guidelines. The second gap is that the authors [3] did not offer substantial technical details to potentially make a significant difference in solving the problem, leaving out some critical administrative controls such as policies and technical controls.
The authors [1], in their review of some of the other works, provided a better blanket support EHR system developed in the USA. Upon a close look at that system reviewed by the authors [1], it was immediately apparent that there was no focus on integrating data security within EHR. In a nutshell, their EHR development only focused on eight identifiable critical activities [1]. Similarly, the “Data Breach Battle” survey [12] conducted by SailPoint Market Pulse of adults in the United States, Great Britain, and Australia evaluated the impact of security breaches from the consumer perspective. The authors [12] provided several statistics regarding users’ electronic health record security concerns. It provided critical statistical information on the seriousness of this issue for ordinary citizens.
Regarding the problem discussed within the article, the authors focused on users’ high-level concerns and did not dig deep to discover the burden and legal liability that can be put on governments in countries with Universal healthcare systems like Canada and Great Britain. The authors pinpoint direct causation to an average everyday taxpayer within any Universal Health system and show how such data breaches within an EHR affect their pocketbook. Citizens must understand the trickledown effect of legal liability that can be brought against the government when EHR data is continuously breached.
Zhang et al. [33] propose a secure and efficient data auditing scheme for cloud-based electronic health records (EHRs). As EHRs are commonly stored on cloud servers, ensuring data integrity and privacy is a major concern, especially given the possibility that cloud providers may conceal data loss to protect their reputation. Zhang et al. identify security vulnerabilities in an existing privacy-preserving auditing approach and enhance it by introducing improved masking techniques and new cryptographic algorithms. Their proposed scheme supports both recoverability and batch auditing. Formal security proofs and experimental results demonstrate that the scheme effectively protects user privacy, is resistant to forgery and malicious attacks, and significantly reduces computational overhead.
Tahir et al. [34] propose a blockchain-based EHR management framework that focuses on security, interoperability, and user-centric control. Their design incorporates ABAC and privacy-preserving mechanisms and demonstrates applicability through empirical evaluation. The study underscores the value of decentralized systems in reducing single points of failure while empowering patients with greater control over their medical data.
Young et al.’s [26] research on “Electronic Health Records-Privacy and Security issue” discusses the benefits of EHR to patient care and the challenges EHR poses to all stakeholders. The authors [26] describe several characteristics of EHR and question current privacy laws’ ability to address strong enough measures to protect EHR systems. Their work highlights core issues of conflicting privacy laws as EHR data across multi-jurisdictions. For example, in a country like Canada with multi-jurisdiction privacy laws, individual provinces like Ontario, Manitoba, Saskatchewan, and Alberta have adopted individual-specific health sector privacy legislation to protect against the conflicting application of these laws as various EHR systems exchange data. Although most of the issues were discussed in Young et al., the authors [26] did not propose a mechanism to address conflicting privacy policies or establish control to protect the EHR system. Other authors such as Rao et al. work focus designing a secure and efficient method for exchanging electronic health records (EHRs) using blockchain and cryptographic techniques such as identity-based signcryption and bilinear pairings [35]. The authors [35] with this work intend to eliminate reliance on third parties while preserving data integrity, privacy, and trust in a decentralized healthcare data-sharing network. The proposed system uses a tamperproof, distributed ledger where each health record is cryptographically hashed, timestamped, and securely shared across nodes, ensuring secure access control and data confidentiality [36]. Similar work focuses on Blockchain-Based framework for interoperable EHR for an Improved system [36]. The authors [36] address research gap within this domain by developing an interoperable blockchain-based EHR framework that can fulfill the requirements defined by various national and international EHR standards such as HIPAA and HL7 [36].
Shultz et al. [37] investigated the challenges of protecting data within EHR. The authors provided an overview of recent electronic health record security breaches and their impact on healthcare providers and patients [30]. Their work highlighted the impacts of health data breaches and related consequences from EHR breaches. They investigated two cases, the rationale of why hacking of electronic records is on the rise, and the challenges healthcare workers and regulators face [30]. Although their work shed light on the recent surge of interest in EHR data breaches, they did not address or provide solutions to any challenges facing EHRs or propose any mitigation technique that can be used in any given EHR to deal with data theft or data protection [30].
The “Guide to Privacy and Security of Health Information” [31] provides detailed knowledge on the importance of Privacy and Security within an EHR system. The authors [31] made the case that the security of EHR is paramount to the delivery of care, and users should trust that the system’s security does not disclose important medical information. The work [31] analyzes EHR security from the point of view that expects the government to be instrumental in providing a mandate established through government policies as a recourse for a liable lawsuit where necessary due care and due diligence are not exercised to protect EHR data security and privacy. The authors discuss the concept of “meaningful use” to show the importance of providing access to any EHR based on the need-to-know concept, addressing the core objective of protecting EHR through technical means and conducting security analysis following sound security principles to address Information security risk. Although the authors [38] provided sound work in EHR security, they failed to propose comprehensive technical controls or tools to address gaps in EHR security. Secondly, the authors did not provide administrative safeguards or address human factors challenges, which renders most EHR security vulnerable and susceptible to attack.
In the review of the security of EHR, Khin [39] analyzes a research question of whether the current information security technologies are adequate for EHRs. The author [39] reviewed the most up-to-date electronic health record security breaches resulting from inadequate security tools. The authors [39] deduced that although current information technology security tools are in place, their adequacy is questionable in addressing private and public interests to achieve maximum usage of EHR security. All the authors [39] analyzed incidents of security breaches within EHR, information security, and technology; they failed to propose any solutions for mitigating or minimizing risk related to EHR data security.
3.2. AIoT Integrated Healthcare Security and Privacy
In the journal article, “Enabling Artificial Intelligence of Things (AIoT) Healthcare Architectures and Listing Security Issues”, Anil Audumbar Pise [40] and other researchers were able to validate and support the severity of their problem statement effectively [40]. To exemplify, through their expansive research, they discovered various security and privacy concerns in AIoT (this would include systems, applications, and devices), which can consist of cell phones and wearable sensor devices. It is imperative to understand that these devices produce sensitive data, and improper handling of this sensitive data can lead to a “major impact on the overall system’s and its stakeholders’ privacy and security” [40]. It exemplifies how critical it is to properly and efficiently handle sensitive data as this would not significantly impact the Healthcare system and the stakeholders having privacy and security issues. In this case, these stakeholders would refer to internal people. To be more specific, this would refer to patients. To expand on privacy issues, this would include improper sharing of sensitive data (e.g., Heart rate, location), and it also ties in the violation of confidentiality, which means giving the data to unauthorized personnel. As for security issues, this would refer to a lack of encryption or weak encryption since this would refer to the data between the wearable device and the server. Without or having weak encryption, attackers (e.g., hackers) can see the traffic between these two components. Overall, Anil Audumbar Pise and other researchers [40] had an effective and logical argument since they could explain thoroughly the privacy and security issues of AIoT.
In “Security issues and challenges in cloud-of-things-based applications for industrial automation”, Neeraj Kumar Pandey and other researchers [41] were able to support the validity and severity of their problem statement. The researchers were able to address various security issues and challenges of AIoT. Their study found that “AIoT is used in the healthcare system, so most attacks are performed using HTTPS and DNS tunnels, ransomware, and BOTNETS. The radiology data is attacked more, so the storage servers of hospitals are soft targets” [41]. This shows that despite the certain security measures (e.g., firewalls) that were in place in EHR, the attackers were able to penetrate through the network. The authors [41] show that the severe impact on sensitive data and servers was also not secure. The authors [41] also found that “most hospital chains share diagnostic data over the network for remote consultancy and expert opinion” [41]. This exemplifies weakness in the healthcare center’s overall network based on the lack of encryption or weak encryption. Ultimately, the authors [41] and other researchers had a solid and logical argument and provided many details regarding the security issues/challenges of AIoT.
In the research “Artificial Intelligence of Things for Smarter Healthcare: A Survey of Advancements, Challenges, and Opportunities”, Stephanie Baker and Wei Xiang [42] proved the validity and security issues in AIoT. The authors [42] discussed various challenges that AIoT brings to healthcare. One of the major challenges that the authors [42] assessed was security laboratory and clinical components. They demonstrated how availability, one of the components of Confidentiality, Integrity, and Availability (CIA) triad, was negatively impacted. The authors [42] showed that, for example, people with limited access could potentially include medical professionals, lab technicians, and biomedical engineers.
Unavailability would disrupt their productivity and result in financial and operational loss for the hospital. Not only that, other companies that have a relationship with the hospital would also see the hospital as untrustworthy if they do not see any value. Hence, there is reputational loss. As for privacy concerns, the authors discussed one of their approaches to privacy. To amplify, this would include federated learning. This would allow various hospitals to train an ML (Machine learning) model without revealing sensitive patient information. The authors showed that federated learning could create a single point of failure for a single server for learning. In short, the authors argued that if the central server compromises, the other nodes will also be affected [42].
The authors [43] Rajeswari and Ponnusamy, in their work “Internet of Things and Artificial Intelligence in Biomedical Systems”, proved the validity and severity of security and privacy concerns in AIoT. The authors [43] explained how biomedical systems incorporating IoT and AI can positively impact hospitals. Such includes “remote health monitoring, disease prediction and diagnosis, and treatment” [43]. However, it is important to note that there are many challenges to these biomedical systems, including significant challenges that would include security and privacy. The authors identify such concerns, including tampering with the original data and modifying is the nightmare of any technology, ease of access to AIoT system datasets and computational power (Graphics Processing Unit) have been considered severe threats to growing AIoT technology [43].
4. Methodology
We complemented the findings from a literature overview with an examination and analysis of current Health Information Protection Portability Act (HIPPA) breach data. The research adopts a mixed-methods approach combining:
- Literature Review: Comprehensive analysis of existing frameworks, breach records, and industry standards.
- Case Study Analysis: In-depth review of selected high-profile healthcare cyberattacks from 2010 to 2025 to identify patterns and vulnerabilities.
- Empirical Observation and Pattern Analysis: The research involved collecting, analyzing, and interpreting data on real-world EHR systems to identify observable phenomena and recurring patterns in data breaches. This helped determine the relative importance of each factor contributing to cyberattacks.
The focus of this work is on AI integrated EHR devices with potential to collect, process, and store PHI. To address the research question, we conducted an exploratory study into currently reported attacks on hospitals and related healthcare entities from 2010 to 2025, utilizing HIPPA breach reporting data. HIPPA breach reporting data is a multi-stage, specific self-reporting electronic form survey filled out by health entities within the United States who discover a breach of unsecured protected health information. For a breach affecting 500 or more individuals, covered entities must notify the Secretary of Health and Human Services within 60 days following the breach. However, covered entities can report a breach that affects less than 500 individuals within a year and sixty days. All the data are publicly available online: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf (accessed on 15 June 2025).
Based on this data, we assess the type of Cyberattack, trends, and impact in healthcare institutes required to meet HIPPA security and privacy compliance. This exploratory study evaluates the current HIPPA breach reported data to analyze it and interpret observations about commonly known attacks, adversary attack patterns in healthcare, and how affected companies differ by type, state, technical control, etc. In addition, we sought to identify the main security vulnerabilities, failure in technical controls, and different threat agents that learned to breach EHR systems, impacting user privacy violations or affecting critical healthcare operations and patient safety. The empirical study complements the gaps from a literature overview to identify potential new issues in EHR security. The main method processes involve:
- I.
- Collect, analyze, and interpret observations about current EHR systems, design to look for specific phenomena in EHR data breaches, and look for patterns to determine relative importance to Cyberattack.
- II.
- Identify shows that EHR systems serve as a goldmine for an attacker, lack sufficient control to guarantee patient privacy and hospital operation continuity during a Cyberattack, and require integration, implementation, and application of essential security principles, controls, and strategies necessary to safeguard patient data generated through the EHR systems life cycle.
- III.
- To understand why a particular type of attack occurs, how the attack is conducted, whom it affects, how it impacts stakeholders, the mood of the attack, affected systems, period of attack (if IT staff is around), location of breached information on the Network/System, type of breach, and the number of affected records, and privacy of safety impact.
Data Description
We downloaded a copy of the 2016 to 2025 breach reporting data from the USA Department of Health and Human Services data download portal: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf (accessed on 15 June 2025). As required by Section 13402(e)(4) of the HITECH Act, the US Secretary of Health and Human Service must post a list of breaches of unsecured protected health information affecting 500 or more individuals [44]. In addition, we downloaded 24 months of all health data breaches reported within the last 24 months that are currently under investigation by the Office for Civil Rights.
As illustrated in Table 2, we organize the download Excel file column into “Name of Covered Entity”, “Breach Submission Date”, “Individual Affected”, State, “Covered Entity Type”, “Number of Individual Affected”, “Type of Breach”, “Location of Breached Information”, “Business Associate Present”.

Table 2.
Curated HIPPA breach Information.
5. Descriptive Analysis
5.1. Covered Entities
The covered entities in the dataset include business associates, health plans, healthcare clearinghouses, and healthcare providers. Figure 2 shows the frequency distribution of the number of individuals involved in data breach incidents for each category of the covered entity. The vertical axis is on a logarithmic scale for better illustration. From the figure, it is evident that the distributions of the number of individual records in breach incidents on all categories of covered entities are skewed toward zero, meaning that most of the incidents involved a low number of personal health records and all categories, except healthcare clearing houses, have a significant number of outliers with incidents involving a high number of personal health records.
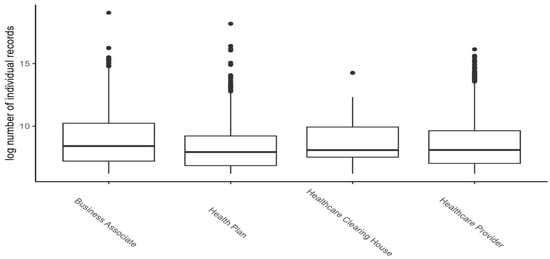
Figure 2.
Distribution of the number of individuals involved in data breaches for each category of the covered entity.
A deeper insight can be gained from Figure 3, which shows histograms of each category where the vertical axis represents the number of data breach incidents in each bracket of the number of compromised individual records. The figure shows that skewness toward zero is more significant for the healthcare provider category, while health plans and business associate categories seem to have a more uniformly distributed number of records. This figure also shows that the category healthcare clearing house does not have a meaningful number of incidents, with only twelve data points.
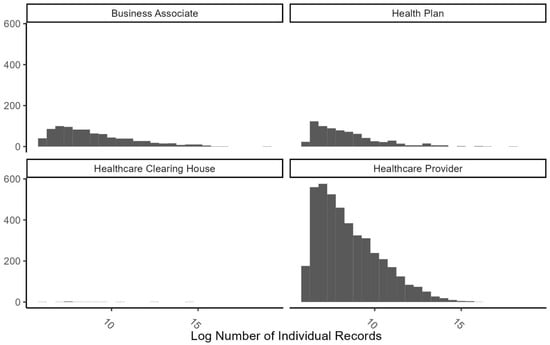
Figure 3.
Frequency of the number of individuals involved in data breaches for each category of the covered entity.
Although the dataset used for this analysis describes the period between 2010 and 2025, Figure 4 shows trends in terms of the number of incidents by covered entity type from 2016 to 2025 due to size restriction of the figure. As illustrated, healthcare providers are consistently on top in terms of the number of breach incidents during the period analyzed, and the trend has consistently been increasing. Healthcare clearinghouses had negligible incidents attributable to them. The health plan category seems to have a constant share of all incidents throughout the period. The most interesting pattern in this figure is the increasing trend in the number of incidents involving business associates. This is likely due to regulatory pressure from the FTC on hospitals contracting with businesses [45] or consumer pressure on business associates. What is interesting for all categories is an increased number of incidents which peak in 2022, declined 2023 and begin rising again as demonstrated in Figure 4.
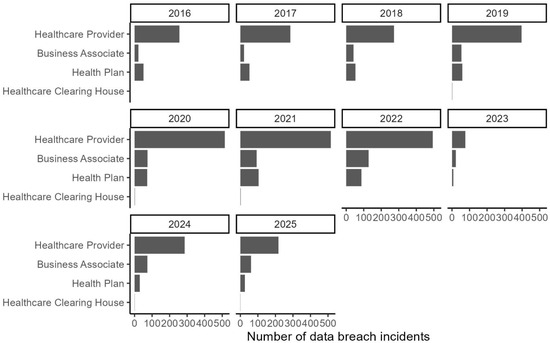
Figure 4.
A few incidents by the covered entity.
5.2. Type of Breaches
The type of breach is inconsistently reported in the original dataset. For example, the type of incident is recorded as theft/improper access/Hacking. We cleaned the dataset and recategorized the type of incidents based on the content in the description column. We identified five main categories of types of breaches, which include hacking/IT incident, improper disposal, loss, theft, unauthorized access/disclosure. Figure 5 illustrates the frequency distribution of the size of breach incidents for each type of breach. It is evident from the figure that most of most incidents belong to the Hacking/IT incidents category. The distribution of all categories is skewed towards zero, meaning that most incidents involved a low number of individual records. However, the distribution of the Hacking/IT incidents category is less skewed and includes more incidents with a high number of individual records involved. The implication is that, while incidents such as theft of devices or unauthorized access usually occur in settings with a small number of individual records, such as small hospitals and healthcare providers, Hacking and IT incidents occur in high-stakes settings with large numbers of individuals involved.
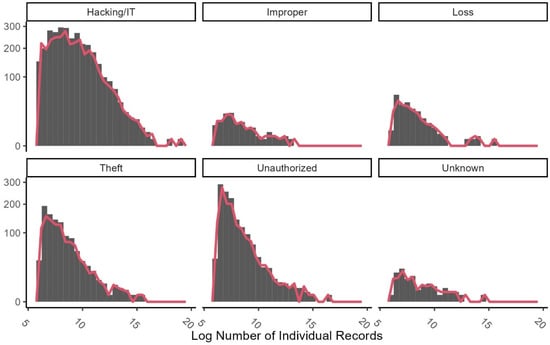
Figure 5.
Frequency of breach size by breach type.
Figure 6 displays the annual number of data breach incidents in the healthcare sector from 2016 to 2025, categorized by breach types: Hacking/IT, Unauthorized Access, Theft, Loss, and Improper Disposal. The horizontal bar charts for each year show a clear upward trend in Hacking/IT incidents, particularly from 2018 onward, peaking between 2020 and 2022. This trend from 2020 to 2022 underscores a growing vulnerability in digital infrastructures, where malicious actors increasingly exploit network and server systems to access sensitive health data [46]. Although there was a dip in 2023; Subsequently, Figure 6 shows a dip in activity, but a continuous rise from 2023–2025.
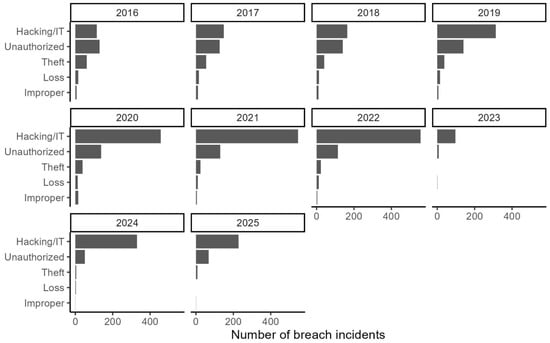
Figure 6.
Number of incidents by type of breach.
While Hacking/IT breaches have dominated in recent years, Unauthorized Access incidents remain relatively steady across the period, highlighting persistent internal or semi-internal security issues. In contrast, physical breaches such as Theft, Loss, and Improper Disposal show a notable decline over time, suggesting either improved handling of physical data or a shift in focus to digital threats. This visualization emphasizes the evolving nature of data security threats in healthcare, with cyberattacks emerging as the primary concern, calling for robust IT security frameworks and proactive risk mitigation strategies.
5.3. Point of Breaches-Distribution and Trends
Figure 7 displays the distribution of breach incident sizes, measured by the (log-transformed) number of individual health records compromised, across six types of breach points: Electronic Medical Record, Email, Laptop, Network Server, Other, and Paper/Films. The histograms reveal that most breach incidents involve a relatively small number of affected records, with distributions heavily skewed to the right. This skewness indicates that most breaches, regardless of type, impact fewer than 20,000 records. However, two breach points—Network Server and Email—stand out for their broader distributions and greater frequency of high-impact incidents. These categories exhibit a longer tail and a higher proportion of breaches involving many compromised records, underscoring their growing relevance in large-scale data exposures. This suggests that breaches at these points are more likely to result from systematic or infrastructure-level vulnerabilities, such as compromised authentication or malware attacks, rather than isolated or accidental incidents.
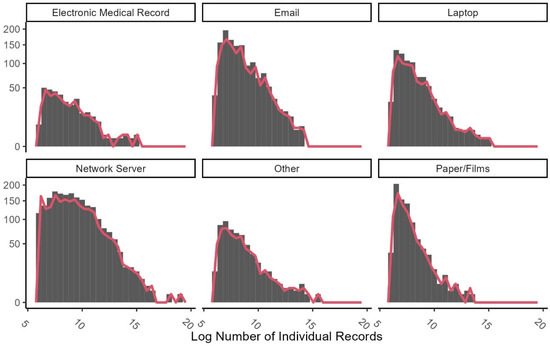
Figure 7.
Frequency of breach size by point of breach.
Figure 8 illustrates the temporal trends in the number of breach incidents for each breach location from 2016 to 2025. Notably, Network Server and Email consistently account for the highest number of incidents throughout the observed period, with a marked increase beginning around 2020 and persisting through 2025. This upward trend likely reflects both the growing digitization of healthcare operations and the increased targeting of communication and storage systems by cyberattackers. By contrast, other breach points, such as Paper/Films, Laptop, Other, and Electronic Medical Record systems, remain relatively stable or decline slightly over time. These patterns suggest that physical breaches and endpoint device compromises are being better managed, while systemic vulnerabilities in digital infrastructure remain a significant and growing threat vector.
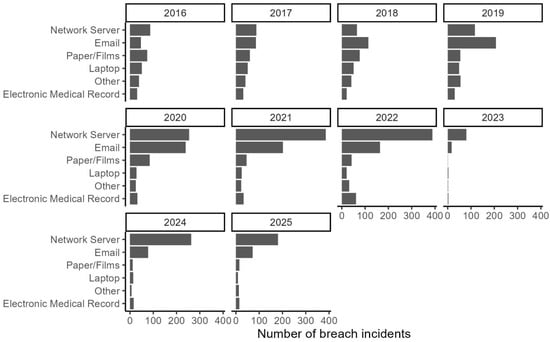
Figure 8.
Number of incidents by point of breach.
Together, Figure 7 and Figure 8 emphasize the shifting landscape of health data security, where infrastructure-related breaches, particularly involving email systems and network servers, represent the most significant and increasing risk. This trend reinforces the urgent need for robust cybersecurity policies, encryption practices, and continuous monitoring of digital communication and storage systems.
6. Trend Analysis of Data Breaches by Type and Point of Breach
This section examines data breach trends across different types and points of breach from 2010 to 2025, focusing on both the frequency of incidents and the scale of personal records affected. We extended the period from 2016 to 2025 to 2010–2025 to have a longer period for our analysis. The findings reveal significant shifts in the data breach landscape, with hacking and IT-related incidents showing the most dramatic increases in both frequency and impact.
6.1. Type of Breach Analysis
Our examination of breach incident trends by type reveals distinct patterns across the 15-year analysis period. Figure 8 illustrates the monthly number of breach incidents across different breach categories, with LOESS smoothing curves highlighting underlying trends. The most striking finding is the consistent and substantial increase in “Hacking/IT” incidents throughout the analysis period. Beginning with relatively low numbers in 2010, hacking-related breaches experienced exponential growth, becoming the dominant breach type by 2025. This trend reflects the increasing digitization of healthcare systems and the corresponding growth in sophisticated cyberattacks targeting these environments.
In contrast, traditional breach types, including improper use of devices, loss of data or devices, theft, and unauthorized access, have remained relatively stable throughout the analysis period. These patterns suggest that while organizational security practices for physical assets and access controls have matured, cybersecurity defenses have struggled to keep pace with evolving digital threats.
Analyzing the average number of personal records breached (number of affected individuals) provides a better view of the trends. Figure 9 illustrates the monthly average personal records reported in the dataset grouped by the types of breaches. The logged total number of affected individuals is relatively low and stays constant during the analysis period for all groups. There is one exception, which is incidents caused by hacking. The average number of individuals has grown from 20,000 to 160,000 individuals for incidents caused by hacking, while for other groups, the number is around 3000 and remains constant. For more detailed analysis, we fit the data into the ARIMA model and reported the coefficients and their significance in Table 3 and Table 4. ARIMA model was employed due to its effectiveness in modeling and forecasting univariate time series data. Given the chronological structure of HIPAA-reported EHR data breaches. ARIMA is well-suited to capture underlying trends, account for non-stationarity, and project future breach occurrences. The model’s interpretability and established use in healthcare analytics make it appropriate for analyzing breach frequencies and identifying evolving threat patterns.
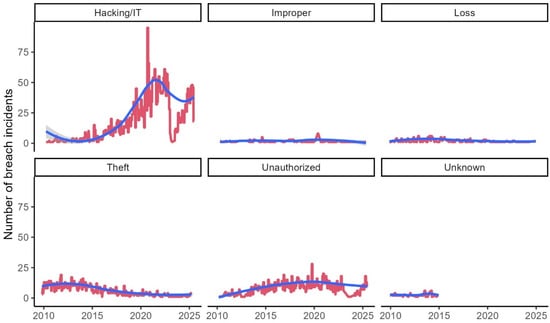
Figure 9.
Monthly number of breach incidents by the type of breach.

Table 3.
Estimated coefficient of trends in the number of breach incidents for each type of breach.

Table 4.
Estimated coefficient of trends in the median size of data breaches for each type of breach.
6.2. Scale of Impact Analysis
The analysis of average personal records affected provides crucial insights into the severity trends across breach types. Figure 9 presents the monthly average of personal records compromised, grouped by breach type, revealing significant disparities in the impact scale. Hacking incidents demonstrate not only an increasing frequency but also a dramatically expanding scope of impact. The average number of individuals affected by hacking incidents has grown from approximately 20,000 in 2010 to over 160,000 by 2025—an eight-fold increase. This trend indicates that successful cyberattacks are becoming increasingly sophisticated and capable of accessing larger data repositories. Other breach types have maintained relatively constant impact scales, with average affected individuals remaining around 3000 throughout the analysis period. This stability suggests that the scope of physical breaches (theft, loss, unauthorized access) is naturally limited by the physical constraints of the compromised media or access points.
Consistent with the visualization, breaches caused by hacking and IT incidents show a significant trend (coefficient 0.84, p-value < 2.2 × 10−16 ***). Interestingly, the Theft and Unauthorized types are also significant and increasing. However, these two types have much smaller coefficients. Unlike visuals, the results of ARIMA models for the trends of median size of the breaches show that all types of breaches have no significant trends. This indicates the high amount of noise in breach-size data that could have originated from measurement errors, inconsistent reports to Health and Human Services, and misattribution of records. These results partially support our H0 hypothesis indicating a significant increasing trend in the number of incidents but inadequate evidence of the increased number of individual records lost in each breach incident. In other words, although the median size of data breach incidents remained unchanged the frequency of the occurrence of those breaches has increased significantly. These trends show that current EHR implementations lack sufficient security controls, thus compromising patient privacy, safety, and hospital operation continuity during a cyberattack.
6.3. Statiscal Model Result
To quantify these trends more precisely, we fitted ARIMA models to the data and analyzed the statistical significance of trend coefficients. The statistical analysis confirms our visual observations with high precision. Hacking/IT incidents show the strongest significant upward trend (coefficient 0.84, p-value < 2.2 × 10−16 ***), indicating robust statistical evidence for the increasing frequency of cyberattacks. Notably, theft and unauthorized access also demonstrate statistically significant increasing trends, though with smaller coefficients (0.633 and 0.492, respectively), suggesting these traditional breach types are also experiencing growth, albeit at lower rates.
Interestingly, the analysis of median breach sizes as shown in Figure 10 reveals no statistically significant trends across any breach type. This finding contrasts with the clear trends observed in average breach sizes and suggests high variability in breach impact within each category. The lack of significant trends in median values indicates substantial noise in breach size data, which may originate from several sources including measurement errors, inconsistent reporting practices to regulatory bodies, and potential misattribution of affected records.
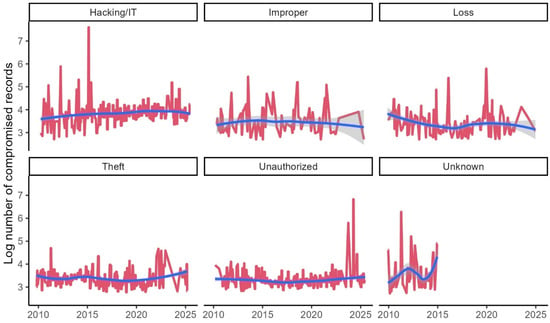
Figure 10.
Monthly median size of breach incidents by the type of breach.
6.4. Key Findings and Implications
Cyber threat dominance emerges as the most significant pattern, with hacking/IT incidents becoming the predominant breach type while showing both the highest frequency growth and largest impact scale increases. Traditional breach stability characterizes physical security breaches such as loss and improper disposal, which have remained relatively constant, suggesting effective traditional security controls have been implemented and maintained. Emerging patterns include theft and unauthorized access, showing statistically significant increases, potentially reflecting new attack vectors or improved detection capabilities within organizations. Impact variance reveals high variability in breach sizes within categories, suggesting inconsistent reporting standards and diverse attack sophistication levels across the healthcare sector.
6.5. Data Quality Consideration
The analysis reveals important data quality challenges that affect trend interpretation. The significant noise in breach size measurements, as evidenced by the lack of trends in median values despite clear trends in averages, indicates several potential issues affecting data reliability and interpretation. Reporting inconsistencies manifest through variations in how organizations count, and report affected individuals, creating challenges for accurate trend analysis. Detection delays between breach occurrence and discovery may affect size estimations, while attribution challenges create difficulty in accurately attributing records to specific incidents in complex breaches involving multiple systems or attack vectors.
These findings have significant implications for healthcare data security strategies across multiple dimensions. Resource allocation decisions should reflect the dominance of hacking/IT trends, suggesting organizations should prioritize cybersecurity investments over traditional physical security measures while maintaining baseline physical protection. Preparedness planning must account for the increasing scale of cyber incidents, requiring enhanced incident response capabilities and larger-scale breach notification processes to handle the growing impact of successful attacks. Regulatory focus appears warranted given the trend data supporting increased regulatory attention on cybersecurity standards and requirements for healthcare organizations. Industry collaboration becomes increasingly important as the sophisticated nature of increasing cyber threats suggests a need for enhanced information sharing and coordinated defense strategies among healthcare organizations and with government agencies.
6.6. Methodlogy Notes
This analysis employs LOESS (locally estimated scatterplot smoothing) for trend visualization and ARIMA (Autoregressive Integrated Moving Average) models for statistical trend analysis. The combination of visual and statistical approaches provides both an intuitive understanding and rigorous quantification of observed trends while accounting for the time series nature of the data. The significance levels reported follow standard statistical conventions, with three asterisks indicating p-values less than 0.001, representing extremely strong evidence for the reported trends. This analytical framework ensures both accessibility for stakeholders and statistical rigor for research and policy applications.
6.7. Point of Breach Analysis
The analysis of trends for groups of data breaches based on the point of breach provides deeper insights into recent developments in health records security. Understanding where breaches originate within healthcare systems is crucial for developing targeted security strategies and allocating resources effectively to protect patient information. Figure 11 illustrates the monthly number of data breach incidents during the analysis period for each category of incidents based on the point of breach. The visualization reveals significant patterns in how breach points have evolved over the study period, reflecting the changing landscape of healthcare technology infrastructure and attack methodologies. Note that for this section, we integrated Desktop and Laptop into one category because of the small number of incidents and similarity between them.
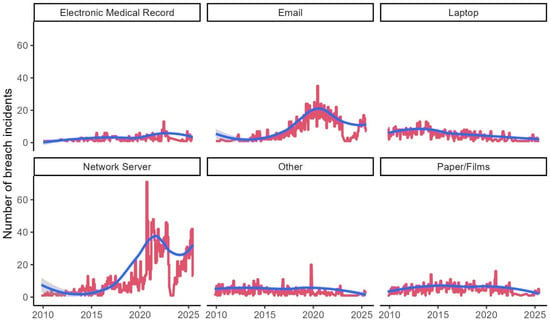
Figure 11.
Monthly number of breach incidents by the point of breach.
Analyzing trends for groups of data breaches based on the point of the breach could provide deeper insights into recent developments in health records security. The number of breaches that occurred via network servers, email, and electronic health record management systems show increasing trends. For further investigation, we ran an ARIMA model to see if the trends were statistically significant. The results are shown in Table 5. Consistent with visuals, ARIMA coefficients for all types of breach are statistically significant except for the groups Desktop and Other. The largest coefficients belong to Network Servers and Email groups, indicating the increasing usage of these platforms for communication and inappropriate access to health records. Changes in the median size of breach incidents in terms of the number of personal health records are illustrated in Figure 12. In line with our discussion in the previous section, due to the large noise in the report of the size of data breaches, we cannot identify any meaningful trend in this variable for any point of the breach. Table 4 provides further evidence of this issue. The results show that, historically, most prevalent points of vulnerabilities have been via emails, network servers, papers/films, and laptops. From these points of breach, however, the frequency of incidents has significantly been increasing for emails, electronic medial records, network servers, and laptops but not for other groups. The median size of breach for different points of breach incidents do not show any significant trends. These results support our H1 indicating that most EHR cybersecurity attacks are concentrated using similar attack methodologies and face common vulnerabilities.

Table 5.
Trend analysis—Number of breach incidents by point of breach.
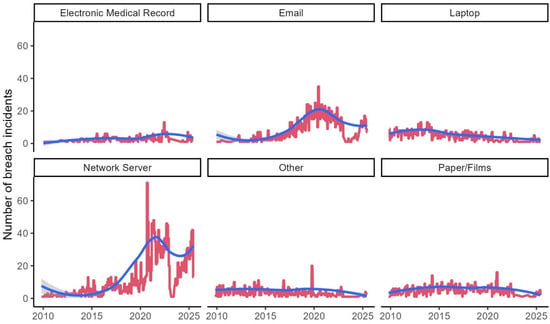
Figure 12.
Monthly median size of breach incidents by the point of breach.
The number of breaches that occurred via network servers, email, and electronic health record management systems shows increasing trends throughout the analysis period. Network servers demonstrate the most pronounced upward trajectory, reflecting the increasing centralization of healthcare data storage and the corresponding expansion of attack surfaces as healthcare organizations migrate to digital systems. Email-based breaches also exhibit substantial growth, indicating that email remains a primary vector for both targeted attacks and inadvertent data exposure despite widespread awareness of email security risks.
Electronic health record management systems show a concerning upward trend in breach incidents, which is particularly significant given the central role these systems play in modern healthcare delivery. This trend suggests that while EHR adoption has improved care coordination and efficiency, it has also created new vulnerabilities that attackers are increasingly exploiting.
6.8. Statistical Significance Analysis
To validate these visual observations and quantify the trends more precisely, we applied ARIMA modeling to assess the statistical significance of observed patterns. Table 5 presents the comprehensive results of this analysis, revealing which trend coefficients represent statistically significant changes rather than random variation. The ARIMA analysis confirms that coefficients for most types of breach points are statistically significant, with notable exceptions being Desktop and Other categories. Network servers exhibit the highest coefficient (0.797, p < 2.2 × 10−16 ***), indicating the strongest upward trend and highlighting the critical importance of server security in modern healthcare environments. This finding aligns with broader cybersecurity research indicating that centralized data repositories have become primary targets for sophisticated attackers seeking to maximize the impact of successful breaches [46,47].
Email breaches show the second-highest coefficient (0.724, p < 2.2 × 10−16), reflecting the persistent vulnerability of email systems to both technical attacks and social engineering. This trend is consistent with industry reports indicating that email remains one of the most common initial attack vectors in healthcare breaches [48]. The statistical significance of this trend underscores the need for enhanced email security measures, including advanced threat protection, user training, and secure communication alternatives.
Laptop-related breaches demonstrate a substantial and statistically significant upward trend (coefficient 0.548, p < 2.2 × 10−16), reflecting the increasing mobility of healthcare workers and the corresponding challenges of securing mobile endpoints. This finding is particularly relevant in the context of increased remote work patterns accelerated by the COVID-19 pandemic, which expanded the attack surface for healthcare organizations significantly.
Electronic Medical Records systems show a moderate but statistically significant increasing trend (coefficient 0.297, p < 0.001), indicating growing targeting of these critical systems. While the coefficient is smaller than network servers or email, the statistical significance suggests a consistent pattern of increasing EHR-focused attacks, which concerns the centrality of these systems to healthcare operations. Interestingly, Paper/Films breaches also show statistical significance (coefficient 0.268, p < 0.001), suggesting that traditional physical security challenges persist even as organizations digitize their operations. This finding indicates that comprehensive security strategies must continue to address both digital and physical threat vectors.
6.9. Breach Size Analysis
Figure 12 above presents changes in the median size of breach incidents measured by the number of personal health records affected, displayed on a logarithmic scale to accommodate the wide range of breach sizes across different points of breach. The logarithmic transformation helps reveal patterns that might be obscured by the extreme values that characterize large-scale cyber incidents. Consistent with our previous analysis of breach types, the examination of breach sizes by point of breach reveals significant data quality challenges that limit our ability to identify meaningful trends. The high variability in reported breach sizes creates substantial noise that obscures underlying patterns, reflecting the complex challenges organizations face in accurately quantifying the scope of data breaches.
Table 6 presents estimated coefficient of trends in the log median size of data breaches for each point of breach. The statistical analysis of median breach sizes confirms the limited presence of significant trends, with only laptop-related breaches showing statistical significance (coefficient −0.203, p = 0.007). Interestingly, this coefficient is negative, suggesting that while laptop breaches are becoming more frequent, their median size may be decreasing. This pattern could reflect improved detection capabilities leading to earlier discovery of laptop-based breaches, or it might indicate that laptop breaches tend to involve more limited datasets compared to server-based incidents. The lack of significant trends in breach sizes for most categories provides further evidence of the substantial measurement challenges in breach size reporting. These challenges likely stem from several factors, including inconsistent methodology for counting affected individuals, variations in breach discovery timing, and the complex technical challenges of determining the full scope of sophisticated cyberattacks [4].

Table 6.
Estimated coefficient of trends in the log median size of data breaches for each point of breach.
6.10. Implications for Healthcare Security Strategy
The analysis reveals critical insights into healthcare security strategy development and resource allocation. The dominance of network server breaches in both frequency and statistical significance indicates that healthcare organizations must prioritize server security infrastructure including robust access controls, network segmentation, and advanced threat detection capabilities.
The persistent growth in email-based breaches suggests that current email security measures are insufficient to address evolving threats. Healthcare organizations should consider implementing advanced email security solutions, including zero-trust architectures, enhanced user authentication, and comprehensive security awareness training programs that specifically address healthcare-relevant attack scenarios. The significant trend in laptop breaches highlights the ongoing challenges of mobile security in healthcare environments. This finding suggests that organizations need robust mobile device management solutions, enhanced endpoint protection, and clear policies governing the use of mobile devices for accessing patient data.
The continued significance of EHR breaches indicates that these critical systems require enhanced security attention despite their central role in care delivery. Healthcare organizations should prioritize EHR security through regular security assessments, robust access controls, and integration with broader security monitoring systems. Even the persistence of paper/film breaches underscores the importance of maintaining comprehensive security programs that address both digital and physical threats. Healthcare organizations cannot focus exclusively on cybersecurity while neglecting traditional physical security measures.
6.11. Data Quality Considerations
The analysis reveals significant data quality challenges that affect our understanding of breach impact patterns. The high noise levels in breach size data suggest several areas where the healthcare industry could improve breach reporting and analysis capabilities. Standardized reporting methodologies would improve the quality and comparability of breach data across organizations and time periods. Currently, variations in how organizations count affected individuals and attribute records to specific incidents create substantial noise in trend analysis.
Enhanced detection and forensic capabilities could improve the accuracy of breach size estimates by providing better tools for determining the actual scope of data compromise. Investment in these capabilities would benefit both individual organizations and industry-wide understanding of breach patterns. Improved incident attribution methods would help distinguish between different types of breaches and improve the accuracy of trend analysis by breach point. Current challenges in definitively attributing breaches to specific systems or attack vectors limit the precision of analytical insights.
The point of breach analysis reveals a healthcare security landscape increasingly dominated by digital threats, with network servers and email emerging as the most significant and rapidly growing attack vectors. While traditional physical security challenges persist, the statistical evidence clearly indicates that healthcare organizations must prioritize digital security infrastructure to address the most pressing and rapidly evolving threats to patient data protection. The persistence of measurement challenges in breach size reporting highlights the need for industry-wide improvements in incident response and forensic capabilities. Enhanced standardization and improved technical capabilities for breach assessment would significantly improve the healthcare industry’s ability to understand and respond to evolving security threats.
7. Discussion
To look for avenues for addressing data security issues within EHR, it must be established, understood, and agreed on that EHR data must be treated differently, and priority must be set to protect it at all costs. EHR data is about people, usually people’s health data. It is unique in finding ways, tools, and methodology to prevent it from getting into the hands of the wrong people or being used for non-intended purposes. In addressing the inherent problem with data breaches, the crucial part focuses on the understanding that once patient data confidentiality is breached and the data is within the public sphere, it can not be retracted. Its effects can be more significant and far-reaching than ever imagined. Again, this makes EHR data unique and requires very stringent mechanisms and rules to protect it within the EHR.
This study aimed to investigate the trends and characteristics of data breaches in the U.S. healthcare system, with a specific focus on breach frequency, size, type, and point of compromise. Through a combination of descriptive statistics and time-series modeling, our analysis offers several important insights into the evolving cybersecurity landscape of electronic health records (EHRs). The descriptive analysis presented in Section 5 and Section 6 serves a crucial foundational role in informing the statistical inference and modeling efforts of this study. By visualizing the distribution, frequency, and trends of breach incidents across covered entities, breach types, and points of entry, we identify underlying patterns, outliers, and data characteristics such as skewness and variability. These insights are not merely illustrative but essential in guiding the subsequent use of inferential techniques such as ARIMA modeling. For instance, the consistently increasing frequency of breaches in specific categories, such as Hacking/IT and Network Server incidents, highlighted in the descriptive figures, provided the rationale for modeling time-dependent trends in breach frequency. Additionally, the observed data skewness and variability across groups justify the need for log transformation and trend decomposition in the inferential phase. Thus, the descriptive statistics do not stand alone; they lay the groundwork for robust statistical inference by validating assumptions, informing model selection, and contextualizing the significance of estimated trend.
The descriptive findings revealed that most breach incidents involved a relatively small number of individual records, with distributions heavily skewed toward zero across most categories. However, exceptions were noted in the Hacking/IT incident type and breaches involving network servers and email categories that showed more frequent and higher-volume breaches. These results suggest that while most breaches may be minor in scale, a small but growing subset poses significant risk due to the large number of patient records compromised.
Trend analysis using ARIMA modeling confirmed that the frequency of Hacking/IT-related breaches has significantly increased over the past decade, with the average number of individuals affected by such incidents growing substantially. This trend highlights a clear shift in the cybersecurity threat landscape, where attackers are increasingly targeting large-scale systems such as hospital servers and email platforms. Similarly, breaches through network servers and emails have shown statistically significant upward trends, indicating a growing vulnerability in these critical points of EHR infrastructure.
Interestingly, while the frequency of breaches has increased across several categories, the median size of breach incidents has not shown a significant upward trend. This divergence suggests that although breaches are becoming more frequent, the number of records affected in each incident remains relatively stable—likely due to reporting inconsistencies, measurement errors, or mitigation efforts that limit breach scope. This finding partially supports our hypothesis (H0), indicating a significant increase in the number of breach incidents, but not in their median size.
The implications of these findings are substantial. First, the increasing trend in hacking and network-based breaches signals the need for healthcare organizations to prioritize investments in cybersecurity, particularly in email security, server protections, and intrusion detection systems. Second, the lack of growth in breach size may reflect improvements in containment practices or reporting inconsistencies that warrant further investigation. Third, the concentration of breaches among certain covered entities, particularly healthcare providers and business associates, underscores potential policy gaps in vendor and third-party risk management.
Taking together, our results provide empirical evidence that EHR data breaches are not only becoming more frequent but are increasingly associated with digital attack vectors. These patterns raise critical concerns about the adequacy of current security protocols and call for a reevaluation of regulatory standards, staff training, and IT infrastructure in the healthcare sector.
The contribution of this work is centered around the provision of descriptive analysis of PHI breach data, emphasizing the individual entities covered and the impact of cyberattack breaches. Such information is important for other researchers in understanding the various data breach risks associated with each covered entity and required targeted solution that can be applied. Similarly, these entities can garner information from this work to understand where within their infrastructure they should be spending the limited security budget in addressing risks. Overall, the detailed analysis of current health data breaches to demonstrate common modes of attacks highly breach area assets within the EHR infrastructure, allowing health entities to invest in solutions that focus on identified areas.
Second, the contribution made through the analysis of frequency of type of breach, and points of breaches, is an important one in understanding the most occurring breach type, method use by adversary. This contribution allows stakeholders within the healthcare domain to understand the requisite controls needed to address the most occurring breach type with maximum impact. Such information allows organization to prioritize risk and required effort needed to address them. Descriptive and trend analysis is used to describe, demonstrate, and summarize data points, and also to predict the direction of EHR data breaches based on current and historical data from a covered entity, allowing other researchers to build on our work.
8. Conclusions
In this work, we demonstrated that electronic health record (EHR) data breaches create severe concerns about patients’ privacy and safety, as well as about a risk of loss for healthcare entities responsible for managing patient health records. This explorative work into integrated EHR cybersecurity attacks using United States Health Insurance Portability and Accountability Act (HIPAA) privacy and security breach data reported shows, through descriptive and trend analysis, breaches caused by hacking, and IT incidents show a significant trend (coefficient 0.84, p-value < 2.2 × 10−16 ***) over the duration of the data collection. The finding indicates that individual records in breach incidents on all categories of covered entities are skewed toward zero, demonstrating that healthcare providers are consistently at the top in the number of breaches. Further, the trend is increasing, with the number of breach incidents attributed to “Hacking/IT” increasing consistently from 2010 to 2025. The analysis validated that some EHR implementations lack sufficient security controls to guarantee patient privacy, safety, and hospital operation continuity during a cyberattack. The analysis proved that attacks on integrated EHR systems are concentrated using similar attack methodologies and face common vulnerabilities. The reliability of this explorative research work was confirmed through retesting and reanalyzing the HIPAA breach data. The result achieved was consistent with the initial result and analysis. What is interesting for all categories is an increased number of incidents which peaked in 2022, declined 2023 and began rising again as demonstrated in Figure 4 and Figure 6.
Based on the findings of this study, there are several important implications for healthcare organizations and policymakers. First, the analysis underscores the urgent need to treat electronic health record (EHR) data as a uniquely sensitive and high-risk asset. Unlike other forms of data, once personal health information is breached and exposed to the public, the consequences are irreversible and potentially far-reaching—impacting not just on individual privacy but also public trust in healthcare systems. As such, healthcare organizations must prioritize the implementation of more stringent, proactive security measures to prevent unauthorized access and mitigate the risk of cyberattacks. The study’s descriptive and trend analysis of HIPAA-reported breaches reveals that most incidents stem from consistent and predictable attack methods—particularly hacking and IT incidents—suggesting that many healthcare entities face common vulnerabilities. This insight provides a roadmap for organizations to make data-driven, risk-based decisions in allocating limited cybersecurity resources toward the most vulnerable areas of their EHR infrastructure.
For policymakers, the findings emphasize the need to strengthen regulatory oversight and enforce standardized security controls that address the unique challenges integrated EHR systems. Additionally, given the study’s limitation regarding the completeness of breach reporting, there is a clear need for the development of automated and mandatory reporting mechanisms to ensure accurate national breach data. Ultimately, both healthcare leaders and regulators must work collaboratively to adopt targeted solutions, enhance breach reporting transparency, and implement adaptive security frameworks that evolve alongside technological advancements in healthcare.
The limitation of this work relate the authors’ inability to validate if companies are reporting all data breaches to US Health and Human services. As such, feature work should evaluate and explore automated breach reporting options to ensure a level of accurate data reporting.
Author Contributions
Conceptualization, B.Y. and R.B.; methodology, M.B. and R.M.; software, M.B.; validation, B.Y. and R.B.; formal analysis, B.Y.; investigation, B.Y.; resources, R.M.; data curation, M.B.; writing—original draft preparation, B.Y., R.B., M.B. and R.M.; writing—review and editing, R.B.; visualization, M.B.; supervision, B.Y.; project administration, B.Y. and R.B.; funding acquisition, B. Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
HIPAA breach data download for this project can be found https://drive.google.com/file/d/1bQNqQi_pPdFON8jYgr6arLs-vGEKacHu/view?usp=sharing (accessed on 22 May 2025).
Acknowledgments
The authors would like to express their sincere gratitude to Ariel Pinto and the University at Albany’s Cyber Cascade Risk (CCR) Lab (https://www.albany.edu/cehc/cyber-cascade-risk-lab (accessed on 22 May 2025)) for providing the funding that supported Rebecca Bondzie, whose contributions were vital to the successful progress and completion of this research. The authors would also like to acknowledge the University at Albany’s HackIoT & PCCRT Assessment Lab (https://www.albany.edu/cehc/cybersecurity/hackiot-pccrt-assessment-lab (accessed on 22 May 2025)) for supporting Ram Madani. This combined financial and academic support has been instrumental in advancing the objectives and outcomes of this study.
Conflicts of Interest
The authors have no conflicts of interest to declare. All co-authors have seen and agree with the manuscript’s contents, and there is no financial interest to report. We certify that the submission is original work and is not under review at any other publication.
References
- Sherman, G.; Health Canada: Office of Health and the Information Highway. Towards Electronic Health Record. 2001. Available online: https://publications.gc.ca/collections/Collection/H21-166-2001E.pdf (accessed on 5 December 2021).
- CDC. Electronic Medical Records/Electronic Health Records. Available online: https://www.cdc.gov/nchs/fastats/electronic-medical-records.htm (accessed on 5 December 2021).
- Camps, C.J.R.; Wainer, J.; Salinas, M.D.U.; Sigulem, D. Security Requirements for a Lifelong Electronic Health Record System: An Opinion. Open Med. Inform. J. 2008, 2, 160–165. Available online: http://www.ncbi.nlm.nih.gov/pmc/articles/PMC2669643/ (accessed on 5 December 2021).
- Barati, M.; Yankson, B. Predicting the occurrence of a data breach. Int. J. Inf. Manag. Data Insights 2022, 2, 100128. [Google Scholar] [CrossRef]
- Frampton, S.; Guastello, S. Patient-Centered Care Guide. Available online: http://www.patient-centeredcare.org/inside/practical.html (accessed on 5 December 2021).
- Chromium, P. The Chromium Projects: System Hardening. Available online: http://www.chromium.org/chromium-os/chromiumos-design-docs/system-hardening (accessed on 28 March 2021).
- Humphries, M. AI Leaks Over 2.5M Medical Records. Available online: https://uk.pcmag.com/encryption/128228/report-ai-company-leaks-over-25m-medical-records (accessed on 21 November 2021).
- Clmpanu, C. AMCA Data Breach Has Now Gone Over The 20 Million Mark. Available online: https://www.zdnet.com/article/amca-data-breach-has-now-gone-over-the-20-million-mark (accessed on 20 November 2021).
- Tidy, J. Hackers Threaten to Leak Plastic Surgery Pictures. Available online: https://www.bbc.com/news/technology-55439190 (accessed on 1 November 2021).
- Murphy, H. Why a Dat Breach at a Genealogy Site Has Privacy Expert Worried. Available online: https://www.nytimes.com/2020/08/01/technology/gedmatch-breach-privacy.html?referringSource=articleShare (accessed on 20 October 2021).
- Iwin, L. Breach at Norway’s Largest Healthcare Authority Was a Disaster Waiting to Happen. Available online: https://www.itgovernance.eu/blog/en/breach-at-norways-largest-healthcare-authority-was-a-disaster-waiting-to-happen (accessed on 24 October 2021).
- Sailpoint. SailPoint Market Pulse Survey: The Data Breach Battle. Available online: http://assets.fiercemarkets.net/public/newsletter/fierceemr/sailpoint.pdf (accessed on 5 November 2021).
- Khalil, E.-K. Biometric, Access Control, and Smart Card Technology: Lecture 1; University of Ontario Institute of Technology: Oshawa, ON, Canada, 2012; p. 15. [Google Scholar]
- Yankson, B.; Ottah, A. Investigating HIPAA Cybersecurity & Privacy Breach Compliance Reporting During COVID-19. In Proceedings of the 18th Annual Symposium on Information Assurance, New York, NY, USA, 6–7 June 2023; Volume 18, pp. 14–21. [Google Scholar]
- Implementation of Electronic Records. Available online: http://openonlinecourses.com/ehr/ImplementationOfInformationSystems.asp (accessed on 14 August 2021).
- Health Services in Your Community. Available online: https://www.ontario.ca/page/public-health-unit-locations (accessed on 23 August 2021).
- Available online: https://www.onespan.com/topics/biometric-authentication (accessed on 14 August 2021).
- Sharma, R. Who Really Owns You’re Your Health Data? Available online: https://www.forbes.com/sites/forbestechcouncil/2018/04/23/who-really-owns-your-health-data/?sh=3bf0587c6d62 (accessed on 23 November 2021).
- Canadian Medical Protective Association. How to Manage Your Medical Records: Retention, Access, Security, Storage, Disposal, and Transfer. The Canadian Medical Protective Association December 2011. Available online: https://www.cmpa-acpm.ca/en/advice-publications/browse-articles/2003/a-matter-of-records-retention-and-transfer-of-clinical-records (accessed on 23 October 2021).
- King, M. Who Owns Your Banking Data? Available online: https://iveybusinessjournal.com/who-owns-your-banking-data (accessed on 4 September 2021).
- Takach, G. Computer Law, 2nd ed.; Irwin Law: Toronto, ON, Canada, 2003; p. 515. [Google Scholar]
- Healthcare in Digital Age: Who Owns Data. The Wall Street Journal. Available online: https://www.wsj.com/video/health-care-in-the-digital-age-who-owns-the-data/28B6E0AD-8506-40B2-A659-20A9B696F524 (accessed on 5 December 2021).
- Data Sharing Principles. The Canadian Medical Protective Association. Available online: https://www.cmpa-acpm.ca/static-assets/pdf/advice-and-publications/handbooks/com_electronic_records_handbook-e.pdf (accessed on 15 October 2021).
- Valerius, J.D. The Electronic Health Record: What Every Information Manager Should Know. Inf. Manag. J. 2007, 41, 56–60. [Google Scholar]
- Wikipedia. Frank Abagnale. Available online: http://en.wikipedia.org/wiki/Frank_Abagnale (accessed on 16 February 2013).
- Young, D. Electronic Health Records-Privacy and Security Issues. McMillan. 2010. Available online: https://www.lexology.com/library/detail.aspx?g=ac5b1631-835b-44e8-9f8d-4590ece77a21 (accessed on 12 June 2012).
- Office of the Auditor General of Canada. Electronic Health Records in Canada: An Overview of Federal and Provincial Reports. April 2010. Available online: https://www.oag.bc.ca/app/uploads/sites/963/2024/08/OAGBC-2010-02-03a-15008-e-health-records-report-en.pdf (accessed on 2 July 2012).
- Yankson, B. Ubiquitous Biometrics NOW: Identity Management Solution for the Canadian Government, Canadian Business, and You [Unpublished Course Project]; Ontario Tech University Library: Oshawa, ON, Canada, 12 December 2011. [Google Scholar]
- Hospital Treating Kate Middleton Falls for a Prank Call. Toronto Star, 5 December 2012. Available online: https://www.thestar.com/news/world/hospital-treating-kate-middleton-falls-for-prank-call-gives-out-health-information/article_e2b32615-eeeb-5fb2-b122-dedd48e57e40.html (accessed on 18 January 2013).
- McMurch, T. Ehealth Saskatchewan Security Reviews Under Way Following Computer Disposal Error. Government of Saskatchewan. 27 March 2012. Available online: https://www.saskatchewan.ca/government/news-and-media/2012/march/27/ehealth-saskatchewan-security-review-under-way-following-computer-disposal-error (accessed on 15 January 2013).
- Priest, L. A Sickening Side-Effect of the eHealth Revolution Globe and Mail. 6 September 2012. Available online: https://www.theglobeandmail.com/news/politics/a-sickening-side-effect-of-the-ehealth-revolution/article1359796/ (accessed on 17 January 2013).
- Health Canada Infoway. Electronic Health Record Infostructure (EHRi): Privacy and Security Conceptual Architecture. June 2005. Available online: https://canadacommons.ca/artifacts/21650824/electronic-health-record-infostructure-ehri-privacy-and-security-conceptual-architecture/22551013/ (accessed on 15 July 2012).
- Tahir, N.U.A.; Rashid, U.; Hadi, H.J.; Ahmad, N.; Cao, Y.; Alshara, M.A.; Javed, Y. A blockchain-based healthcare records management framework. Sensors 2024, 24, 1022. [Google Scholar]
- Saksena, N.; Matthan, R.; Bhan, A.; Balsari, S. Rebooting consent in the digital age: A governance framework for health data exchange. BMJ Glob. Health 2021, 6, e005057. [Google Scholar] [CrossRef] [PubMed]
- Rao, K.R.; Naganjaneyulu, S. Designing a Block Chain Based Network for the Secure Exchange of Medical Data in Healthcare Systems. Appl. Artif. Intell. 2024, 38, 2318164. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, X.A.; Jiang, W.; Zhou, M.; Xu, X.; Liu, H. An efficient and secure data audit scheme for cloud-based EHRs with recoverable and batch auditing. Comput. Mater. Contin. 2025, 83, 1533–1553. [Google Scholar] [CrossRef]
- Shultz, D. As Patients’ Records Go Digital, Theft and Hacking Problem Grow. Kaiser Health News, 3 June 2012. Available online: http://www.kaiserhealthnews.org/Stories/2012/June/04/electronic-health-records-theft-hacking.aspx (accessed on 20 July 2012).
- The Office of the National Coordinator for Health Information Technology. Guide to Privacy and Security of Health Information. Available online: http://www.healthit.gov/sites/default/files/pdf/privacy/privacy-and-security-guide.pdf (accessed on 2 July 2012).
- Khin, T.W. A Review of Security of Electronic Health Records. Health Inf. Manag. 2005, 34, 13–17. Available online: https://www.cs.uwaterloo.ca/twiki/pub/Main/MaxwellYoung/Review_Win.pdf (accessed on 12 August 2012).
- Pise, A.A.; Almuzaini, K.K.; Ahanger, T.A.; Farouk, A.; Pant, K.; Pareek, P.K.; Nuagah, S.J. Enabling artificial intelligence of Things (AIoT) healthcare architectures and listing security issues. Comput. Intell. Neurosci. 2022, 8421434. [Google Scholar] [CrossRef] [PubMed]
- Pandey, N.K.; Kumar, K.; Saini, G.; Mishra, A.K. Security issues and challenges in cloud of things-based applications for industrial automation. Ann. Oper. Res. 2023, 342, 565–584. [Google Scholar] [CrossRef] [PubMed]
- Baker, S.; Xiang, W. Artificial intelligence of things for smarter Healthcare: A survey of advancements, challenges, and opportunities. IEEE Commun. Surv. Tutor. 2023, 25, 1261–1293. [Google Scholar] [CrossRef]
- Rajeswari, S.V.K.R.; Ponnusamy, V. Internet of Things and artificial intelligence in biomedical systems. In Artificial Intelligence for Innovative Healthcare Informatics; Springer International Publishing: Berlin/Heidelberg, Germany, 2022; pp. 153–177. [Google Scholar]
- Available online: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf (accessed on 15 July 2025).
- Federal Trade Commission. FTC Enforcement Action to Bar GoodRx from Sharing Consumers’ Sensitive Health Info for Advertising. 1 February 2023. Available online: https://www.ftc.gov/news-events/news/press-releases/2023/02/ftc-enforcement-action-bar-goodrx-sharing-consumers-sensitive-health-info-advertising (accessed on 22 May 2025).
- Kruse, C.; Frederick, B.; Jacobson, T.; Monticone, D. Cybersecurity in healthcare: A systematic review of modern threats and trends. PubMed. 2017. Available online: https://pubmed.ncbi.nlm.nih.gov/27689562/ (accessed on 22 May 2025).
- Lee, I. Analyzing Web Descriptions of Cybersecurity Breaches in the Healthcare Provider Sector: A Content Analytics Research Method. Comput. Secur. 2023, 129, 103185. [Google Scholar] [CrossRef]
- Verizon Business. 2025 Data Breach Investigations Report. 22 April 2025. Available online: https://www.verizon.com/business/resources/reports/dbir/ (accessed on 22 May 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).