Empowering End-Users with Cybersecurity Situational Awareness: Findings from IoT-Health Table-Top Exercises
Abstract
1. Introduction
- RQ1. What aspects of security metadata are useful to end-users in an IoT-Health architecture?
- RQ2. How can they help empower users’ cybersecurity situational awareness and design future systems?
2. Background
3. Research Method
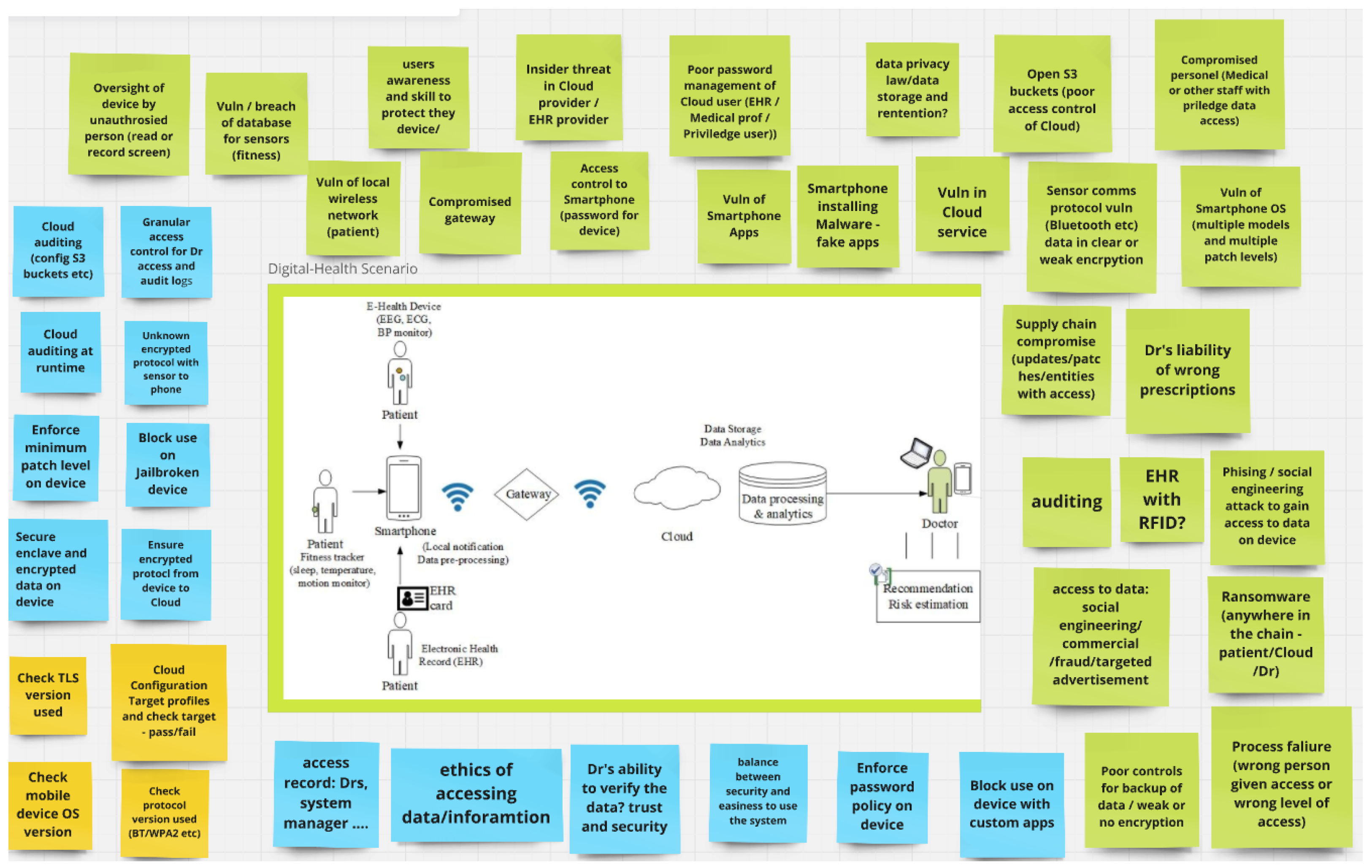
3.1. IoT-Health Scenario
3.2. Structure of Table-Top Exercise
- Task-1: Discuss the scenario with your peers to identify the possible points of attack in the overall scenario. (Assume yourself as an attacker)
- Task-2: What kinds of security controls would need to be in place to prevent these attacks? (Switch each participant’s role from an attacker to a protector of the system, and rethink the cases)
- Task-3: What kind of security evidence/security metadata can be gathered to prove that they (the identified security controls) are in place?
3.3. Experts Diversity
3.4. Data Collection and Analysis
3.5. Ethics Approval
4. Findings
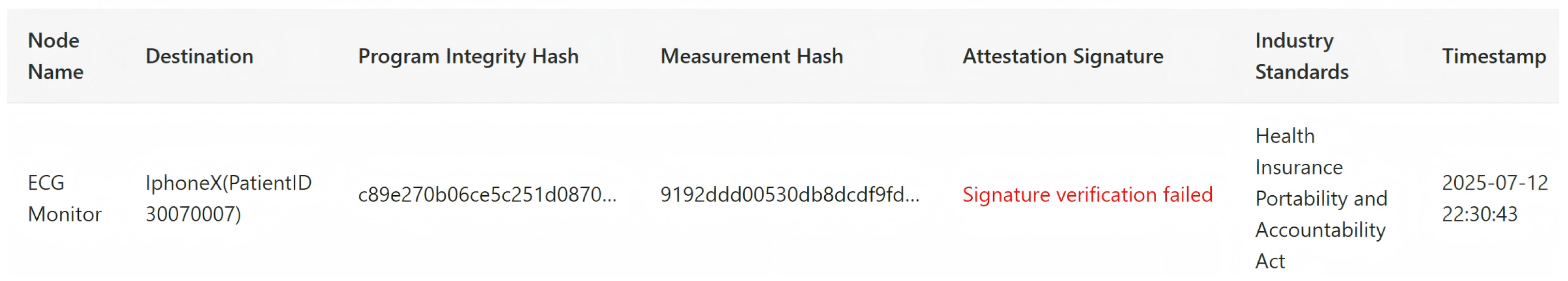
4.1. Providing Security Metadata
“I think the simplest solution is a digital signature. In every five minutes, data will be aggregated and assigned either by the device itself or from the smartphone, and then it will pass on to the nearest endpoint for the doctors…”
“So basically, I think all the health data need to be processed in the trusted room. Furthermore, if they are not being processed, they have to be staying in encrypted form always so that it will be the cipher-text, and there will be no use for other apps or attackers. Hence, the key for encrypting this host data must always be stored in this secure enclave.”
“When you want to open up that app, that app should not function, it should immediately alert that your phone is not secured.”
“You can have your point of view, you can do background checking, like police checks and clearance. Furthermore, from a technological point of view, you can do significant activity monitoring for behavioral analytics over time.”
4.2. Providing Concerns and Proposals by Experts (for System Design)
“I think the only thing that we can assume is that any kind of protection software on smartphones breaks the security of the smartphone. I have not seen any proof of anti-malware software strengthening security. However, I have seen many issues with this…"
“So if you’ve got a compromised individual anywhere in the chain, then he can gain system access, and that does not require any vulnerability…”Expert-4
“I would build something like a Virtual Private Network (VPN) connection through a vendor. Maybe we can channel through them (the vendor) without them able to process it. However, this vendor specifically knows what kind of traffic should go in and out. He can decide whether the traffic is okay or not”.
“I like the idea that certain data, especially health data can only flow through certain channels. Furthermore, that happens to be a VPN or some private network. In that case, we can skip encryption and make sure that health data pass through these channels is ending up in a secured channel from an information flow perspective. They should not just be going through public networks”.
5. Simulation
5.1. System Setup
5.2. Simulation Use Cases
5.3. Results
6. Discussion
6.1. Significance of Security Metadata
6.2. Empowering End-Users with Cybersecurity Situational Awareness
6.3. Design for Security-Aware Provenance-Based Approach and Implications for Future
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Catarinucci, L.; De Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-Aware Architecture for Smart Healthcare Systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Bhuiyan, M.N.; Rahman, M.M.; Billah, M.M.; Saha, D. Internet of things (IoT): A review of its enabling technologies in healthcare applications, standards protocols, security, and market opportunities. IEEE Internet Things J. 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Jaigirdar, F.T.; Rudolph, C.; Bain, C. Can I Trust the Data I See? A Physician’s Concern on Medical Data in IoT Health Architectures. In Proceedings of the Australasian Computer Science Week Multiconference, Sydney, Australia, 29–31 January 2019; pp. 1–10. [Google Scholar]
- Somasundaram, R.; Thirugnanam, M. Review of security challenges in healthcare internet of things. Wirel. Netw. 2021, 27, 5503–5509. [Google Scholar] [CrossRef]
- Affia, A.A.O.; Finch, H.; Jung, W.; Samori, I.A.; Potter, L.; Palmer, X.L. IoT health devices: Exploring security risks in the connected landscape. IoT 2023, 4, 150–182. [Google Scholar] [CrossRef]
- Butt, S.A.; Diaz-Martinez, J.L.; Jamal, T.; Ali, A.; De-La-Hoz-Franco, E.; Shoaib, M. IoT smart health security threats. In Proceedings of the 2019 19th International Conference on Computational Science and Its Applications (ICCSA), St. Petersburg, Russia, 1–4 July 2019; pp. 26–31. [Google Scholar]
- Clinton, U.B.; Hoque, N.; Robindro Singh, K. Classification of DDoS attack traffic on SDN network environment using deep learning. Cybersecurity 2024, 7, 23. [Google Scholar] [CrossRef]
- Addula, S.R.; Ali, A. A Novel Permissioned Blockchain Approach for Scalable and Privacy-Preserving IoT Authentication. J. Cyber Secur. Risk Audit. 2025, 2025, 222–237. [Google Scholar] [CrossRef]
- Jaigirdar, F.T.; Rudolph, C.; Bain, C. Risk and Compliance in IoT- Health Data Propagation: A Security-Aware Provenance based Approach. In Proceedings of the 2021 IEEE International Conference on Digital Health (ICDH), Chicago, IL, USA, 5–10 September 2021; pp. 27–37. [Google Scholar]
- Jaigirdar, F.T. Provenance for Secure Propagation of IoT Data. Ph.D. Thesis, Monash University, Melbourne, Australia, 2021. [Google Scholar] [CrossRef]
- Almuqren, A.A. Cybersecurity threats, countermeasures and mitigation techniques on the IoT: Future research directions. J. Cyber Secur. Risk Audit. 2025, 1, 1–11. [Google Scholar] [CrossRef]
- Jaigirdar, F.T.; Rudolph, C.; Oliver, G.; Watts, D.; Bain, C. What information is required for explainable AI?: A provenance-based research agenda and future challenges. In Proceedings of the 2020 IEEE 6th International Conference on Collaboration and Internet Computing (CIC), Atlanta, GA, USA, 1–3 December 2020; pp. 177–183. [Google Scholar]
- Liu, J.; Yang, H.; Qu, Q.; Liu, Z.; Cao, Y. Research on distribution automation security situational awareness technology based on risk transmission path and multi-source information fusion. Cybersecurity 2024, 7, 57. [Google Scholar] [CrossRef]
- Reveraert, M.; Sauer, T. A four-part typology to assess organizational and individual security awareness. Inf. Secur. J. A Glob. Perspect. 2022, 31, 64–82. [Google Scholar] [CrossRef]
- Jaigirdar, F.T.; Rudolph, C.; Bain, C. Prov-IoT: A security-aware IoT provenance model. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 1360–1367. [Google Scholar]
- Jaigirdar, F.T.; Tan, B.; Rudolph, C.; Bain, C. Security-Aware Provenance for Transparency in IoT Data Propagation. IEEE Access 2023, 11, 55677–55691. [Google Scholar] [CrossRef]
- Sukhodolia, O. Training as a Tool of Fostering CIP Concept Implementation: Results of a Table Top Exercise on Critical Energy Infrastructure Resilience. Inf. Secur. Int. J. 2018, 40, 120–128. [Google Scholar] [CrossRef]
- Shaikh, A. Smartphones Usage at Workplace: Assessing Information Security Risks from Accessibility Perspective. Available online: http://hdl.handle.net/2142/106547 (accessed on 20 July 2025).
- Fietkiewicz, K.J.; Ilhan, A. How Do Users of Activity Tracking Technologies Perceive the Data Privacy Environment in the EU? Available online: http://hdl.handle.net/2142/106603 (accessed on 20 July 2025).
- Wilbanks, L.R. CyberSecurity Privacy Risks. In Advances in Human Factors in Robots, Unmanned Systems and Cybersecurity, Proceedings of the AHFE 2021 Virtual Conferences on Human Factors in Robots, Drones and Unmanned Systems, and Human Factors in Cybersecurity, Online, July 25–29 2021; Springer: Cham, Switzerland, 2021; pp. 191–198. [Google Scholar]
- Cilliers, L. Wearable devices in healthcare: Privacy and information security issues. Health Inf. Manag. J. 2020, 49, 150–156. [Google Scholar] [CrossRef] [PubMed]
- Bada, M.; Sasse, A.M.; Nurse, J.R. Cyber security awareness campaigns: Why do they fail to change behaviour? arXiv 2019. [Google Scholar] [CrossRef]
- Abawajy, J. User preference of cyber security awareness delivery methods. Behav. Inf. Technol. 2014, 33, 237–248. [Google Scholar] [CrossRef]
- Thomas, J. Individual cyber security: Empowering employees to resist spear phishing to prevent identity theft and ransomware attacks. Int. J. Bus. Manag. 2018, 12, 1–23. [Google Scholar] [CrossRef]
- Lamprinakos, G.; Kosmatos, E.; Kaklamani, D.; Venieris, I. An integrated architecture for remote healthcare monitoring. In Proceedings of the 2010 14th Panhellenic Conference on Informatics, Tripoli, Greece, 10–12 September 2010; pp. 12–15. [Google Scholar]
- Gutzwiller, R.; Dykstra, J.; Payne, B. Gaps and opportunities in situational awareness for cybersecurity. Digit. Threat. Res. Pract. 2020, 1, 1–6. [Google Scholar] [CrossRef]
- Braun, U.; Shinnar, A.; Seltzer, M. Securing provenance. In Proceedings of the 3rd Conference on Hot Topics in Security (HOTSEC’08), San Jose, CA, USA, 29 July 2008; pp. 1–5. [Google Scholar]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Moreau, L.; Clifford, B.; Freire, J.; Futrelle, J.; Gil, Y.; Groth, P.; Kwasnikowska, N.; Miles, S.; Missier, P.; Myers, J.; et al. The open provenance model core specification (v1.1). Future Gener. Comput. Syst. 2011, 27, 743–756. [Google Scholar] [CrossRef]
- Sultana, S.; Bertino, E. A comprehensive model for provenance. In Provenance and Annotation of Data and Processes; Springer: Berlin/Heidelberg, Germany, 2012; pp. 243–245. [Google Scholar]
- Forero, C.A.M. Tabletop Exercise For Cybersecurity Educational Training; Theoretical Grounding Furthermore, Development. Master’s Thesis, University of Tartu, Tartu, Estonia, 2016. [Google Scholar]
- Conklin, A.; White, G.B. E-government and cyber security: The role of cyber security exercises. In Proceedings of the 39th Annual Hawaii International Conference on System Sciences (HICSS’06), Kauai, HI, USA, 4–7 January 2006; Volume 4, p. 79b. [Google Scholar]
- Aoyama, T.; Nakano, T.; Koshijima, I.; Hashimoto, Y.; Watanabe, K. On the complexity of cybersecurity exercises proportional to preparedness. J. Disaster Res. 2017, 12, 1081–1090. [Google Scholar] [CrossRef]
- Miro Whiteboard. Available online: https://miro.com/ (accessed on 3 June 2025).
- Richards, L. Using NVivo in Qualitative Research. Available online: https://help-nv11.qsrinternational.com/desktop/concepts/using_nvivo_for_qualitative_research.htm (accessed on 3 June 2025).
- Frederick, N.; Ali, A. Enhancing DDoS attack detection and mitigation in SDN using advanced machine learning techniques. J. Cyber Secur. Risk Audit. 2024, 2024, 23–37. [Google Scholar] [CrossRef]
- Hyla, T.; Fabisiak, L. Measuring cyber security awareness within groups of medical professionals in Poland. In Proceedings of the 53rd Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2020. [Google Scholar]
- Eminağaoğlu, M.; Uçar, E.; Eren, Ş. The positive outcomes of information security awareness training in companies—A case study. Inf. Secur. Tech. Rep. 2009, 14, 223–229. [Google Scholar] [CrossRef]
- Moustafa, A.A.; Bello, A.; Maurushat, A. The role of user behaviour in improving cyber security management. Front. Psychol. 2021, 12, 561011. [Google Scholar] [CrossRef] [PubMed]
- Mitchell, C. Trusted Computing, The Institution of Engineering and Technology (IET): London, UK, 2005; Volume 6, 1.





| ID | Role | Industry Sector | Expertise |
|---|---|---|---|
| 1 | Professor | Information and Communication Technology | Critical infrastructure security, remote condition monitoring, mobile and sensor network, information processing. |
| 2 | Senior Lecturer | Criminology | Cybercrime, fake news, information operation. |
| 3 | Senior Lecturer | Software Systems and Cybersecurity | Data security and privacy, trusted computing, secure networked system. |
| 4 | Head of research and capacity building–industry and academia | Cybersecurity Policy and Strategy | Public health, information security management, pharmacology, neuroscience. |
| 5 | Professor | Computer Security and Reliability | Cybersecurity, digital evidence, trusted computing, network security. |
| 6 | Researcher-industry and academia | Secure Information Technology | Trusted computing, formal methods, distributed systems. |
| 7 | Lecturer | Cybersecurity | Information security, privacy, Blockchain. |
| 8 | Professor | Computer Security and Reliability | Cryptography, information security, network security. |
| 9 | Digital Health expert-industry and academia | Digital Health and IT | Health informatics, usability, software design and evaluation. |
| 10 | Professor | Software Systems and Cybersecurity | Security, digital health, cryptographic protocols, trusted computing. |
| Attack Points | Security Controls | Topic-Based Security Evidence | Relevant Security Metadata |
|---|---|---|---|
| Smartphone, Electronic Health Record (EHR), Fitness Tracker, Bluetooth, Gateway | Access control, Authentication device identity, Security of apps, Anti-malware software, Authentication mechanisms | Trusted computing, Encryption, Policy and human-centric | Programmable system on a chip (PSoC6), Trusted Platform Module (TPM), secure boot, secure attestation, secure enclave, trusted room, trustable logs, HTTPS, digital signature, restricted key management, time-specific data (timestamp), demographic information, device configuration information, law/regulation information |
| End-to-end system | Protocols (with version and parameters): 802.1AR, S/MIME, PGP, TLS, etc., multi-factor authentication (2FA, MFA), AI-based authentication, authentication chip, antivirus, OS version and update status, encryption validation, telemetry data, safety info | ||
| At any point (general) | Auditing service | Professional auditing service | Configuration target, output from auditing service |
| Cloud | Cloud security, Certificate authority (CA) | Cloud security | Contractual specifications or policies, security engineering auditing, CA-related evidence |
| Device-specific | Device standard or update | Device standard | Industry/government standards, HIPAA/FDA/TGA regulations |
| Concerns | Discussion Points | Representative Quotes |
|---|---|---|
|
| “Avoiding cloud is the best thing. Cloud security is contractual security. …As long as you believe the contract, it’s fine.” Expert-5 “I think ‘clouds’ are monitored continuously and managed by professional security experts. Expert-1 “If you are actually assuming that the cloud operator is malicious, you havebigger problems.” Expert-6 “However, I think it is very challenging for attackers to launch side channel attacks inside the cloud right now. I think they still have very strong protection.” Expert-3 |
|
| “With some antivirus software on the device, we are running into a very tough update issue, …as soon as any kind of software decides this device is infected. We need to remediation processes.” Expert-5 “Whenever you work in the health industry, you should maintain a certain security, for the hardware and for the software.” Expert-7 |
|
| “How to define a situation when somebody approaches me looks like a doctor or health professional? I will believe them and maybe even transfer some of the credentials or if they want to replace my device…” Expert-7 “…even for a secure system, the patient might not have any awareness, …For example, they might simply not be able to keep their phone in a safe place. Furthermore, for the doctor, it will be the same.” Expert-2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jaigirdar, F.T.; Rudolph, C.; Anwar, M.; Tan, B. Empowering End-Users with Cybersecurity Situational Awareness: Findings from IoT-Health Table-Top Exercises. J. Cybersecur. Priv. 2025, 5, 49. https://doi.org/10.3390/jcp5030049
Jaigirdar FT, Rudolph C, Anwar M, Tan B. Empowering End-Users with Cybersecurity Situational Awareness: Findings from IoT-Health Table-Top Exercises. Journal of Cybersecurity and Privacy. 2025; 5(3):49. https://doi.org/10.3390/jcp5030049
Chicago/Turabian StyleJaigirdar, Fariha Tasmin, Carsten Rudolph, Misita Anwar, and Boyu Tan. 2025. "Empowering End-Users with Cybersecurity Situational Awareness: Findings from IoT-Health Table-Top Exercises" Journal of Cybersecurity and Privacy 5, no. 3: 49. https://doi.org/10.3390/jcp5030049
APA StyleJaigirdar, F. T., Rudolph, C., Anwar, M., & Tan, B. (2025). Empowering End-Users with Cybersecurity Situational Awareness: Findings from IoT-Health Table-Top Exercises. Journal of Cybersecurity and Privacy, 5(3), 49. https://doi.org/10.3390/jcp5030049






