Abstract
Broadcast-style downlinks (e.g., PONs and satellites) expose physical waveforms despite transport-layer cryptography, motivating physical-layer encryption (PLE). Digital chaotic encryption is appealing for its noise-like spectra, sensitivity, and DSP-friendly implementation, but in low-CSPR KK-SSB systems, common embeddings disrupt minimum-phase requirements and raise PAPR/SSBI near 1 dB CSPR, while finite-precision effects can leak correlation after KK reconstruction. We bridge this gap by integrating 3D Lorenz-based PLE into our low-CSPR KK-SSB receiver. A KK-compatible embedding applies a Lorenz-driven XOR mapping to I/Q bitstreams before PAM4-to-16QAM modulation, preserving the minimum phase and avoiding spectral zeros. Co-design of chaotic strength and subband usage with the KK SSBI-suppression method maintains SSBI mitigation with negligible PAPR growth. We further adopt digitization settings and fractional-digit-parity-based key derivation to suppress short periods and remove key-revealing synchronization cues. Experiments demonstrate a 1091 key space without degrading transmission quality, enabling secure, key-concealed operation on shared downlinks and offering a practical path for chaotic PLE in near-minimum-CSPR SSB systems.
1. Introduction
With the rapid growth of multimodal communication, security is especially challenging in broadcast-style architectures where many receivers observe the same downlink (e.g., PONs and satellite group broadcasting) [1,2,3]. Transport-layer cryptography protects packets end-to-end but does not conceal the physical waveform or prevent signal-level interception. This motivates physical-layer encryption (PLE), which embeds confidentiality at signal generation and propagation and is inherently aligned with shared downlinks [4,5,6].
Within PLE, digital chaotic encryption is compelling: it leverages deterministic dynamical systems (e.g., Lorenz and hyperchaos) exhibiting pseudo-random behavior, strong parameter/initial-condition sensitivity, and broadband noise-like spectra to realize key-controlled masking, scrambling, or modulation mapping [7]. It offers (i) large key spaces that raise brute-force complexity; (ii) noise-like outputs that hinder interception and traffic analysis; (iii) DSP-friendly, low-cost implementations without specialized hardware; and (iv) compatibility with OFDM, FBMC/OQAM, and SSB/KK with modest adjustments. Practical deployment requires careful model selection and digitization to avoid short-period degradation, robust key management under known-/chosen-plaintext adversaries, embeddings co-designed for PAPR/BER/equalizer stability, synchronization aids that do not leak keys, and joint PHY processing [8].
In 2022, we proposed a low-carrier signal power ratio (CSPR) KK receiver that effectively eliminates SSBI [9], enabling single-sideband demodulation when the CSPR is close to 1 dB and attracting widespread attention. Yet most digital chaotic encryption schemes cannot be directly transplanted into low-CSPR KK-SSB systems despite their favorable secrecy properties. The main obstacles are that common chaotic embeddings—such as additive masking, symbol remapping, or amplitude/phase scrambling—tend to perturb the minimum-phase condition required by KK phase retrieval and thereby aggravate phase reconstruction errors; in addition, the induced envelope fluctuations and intermodulation components elevate PAPR and exacerbate SSBI at a low CSPR, undermining KK’s SSBI immunity. Conventional synchronization and key-aided training can also leave identifiable side features on shared downlinks, risking exposure of key structures, while finite-precision digitization of chaotic maps may introduce short-period artifacts that, after KK reconstruction, leak correlation and facilitate traffic analysis or known-/chosen-plaintext attacks. Together, these factors have impeded the use of chaotic PLE in KK-based SSB systems operating near the lowest CSPR regime.
In this work, we bridge this gap by integrating a 3D Lorenz-based PLE scheme into our previously proposed low-CSPR KK SSB system. We design a KK-compatible embedding that applies Lorenz-driven key generation to the I/Q streams via lightweight XOR mapping before PAM4-to-16QAM modulation, thereby preserving the signal’s minimum-phase property and avoiding spectral zeros detrimental to KK invertibility. We further co-design the chaotic strength and subband usage with the low-CSPR KK SSBI-suppression method in [10] to keep SSBI mitigation effective while keeping PAPR growth negligible. In parallel, we adopt digitization settings and a fractional-digit-parity-based key derivation that suppress short-period effects and eliminate key-revealing synchronization cues, enabling secure deployment in broadcast-style downlinks. Experimental demonstrations show that the scheme achieves a key space of 1091 without degrading transmission quality, ensuring that illegal users cannot crack the correct key in a short time and providing a secure transmission solution for further research and application of this single-sideband communication system.
2. Related Works
Currently, many scholars have proposed different chaotic encryption schemes for PONs. Liu, Zhao et al. proposed a 4D chaotic encryption scheme for orthogonal frequency division multiplexing (OFDM)–PON systems [11]; Liu, Ren et al. proposed a physical-layer encryption scheme based on a 4D hyperchaotic system for probabilistic shaping OFDM-PON systems [12]; Tang, Ren et al. proposed a filter-bank multicarrier/offset quadrature amplitude modulation (FBMC/OQAM) physical-layer encrypted transmission system based on chaotic encryption [13]. Wang, Zhiyi et al. proposed a PS-based constellation encryption system for OFDM–RoF. Hyperchaotic sequences and SHA–512 hashes drive two bit-level encryption steps. Probabilistic shaping is then applied using PS–16QAM. A constellation encryption stage maintains the shaping distribution while improving security. The encrypted signal was transmitted over a 50 km SSMF and a 5 m wireless link. The scheme achieves a key space of 10121, resisting brute-force attacks. It also provides a ~2.4 dB SNR gain at BER = 10−3 versus conventional OFDM [14]. Liu, L. et al. proposed a physical-layer encryption system for CO–OFDM based on disturbing data clusters via a color--seeking chaotic mechanism. The chaotic sequence is generated from key-driven Brownian motion, labeled with two primary colors, and reordered through sorting and seeking. Data disturbance follows this color-seeking process, and PAPR is optimized simultaneously. The scheme provides a key space of 1090 and reduces PAPR by about 0.5 dB. In a 40 GHz 16QAM CO–OFDM system over an 80 km SSMF, authorized users decrypt successfully, while eavesdroppers see BER ≈ 0.5 [15]. Li, Y. et al. proposed a camera projection-based physical-layer encryption system for CO–OFDM. A camera projection module maps data to new positions and is driven by keys from a 5D hyperchaotic system. In a simulated 16QAM CO–OFDM over an 80 km SSMF, the scheme yields a key space of about 9 × 1090, thwarting eavesdroppers. It also reduces PAPR by ~0.8 dB [16]. Chen, Q. et al. proposed dual chaotic encryption for OTFS–IM, securing both index and data bits. They also introduced a PAPR-optimized encryption system using random interleaved partitioning time segmentation (RIPTS) to lower autocorrelation and ICI. In B2B and 80 km SSMF PON tests, RIPTS improves PAPR by 4.3 dB over no optimization and by 0.8/0.6/0.5 dB over PTS/IPTS/RPTS, respectively. The dual-chaos system uses six parameters, yielding a key space up to 1090 [17]. Wang, Zhang et al. proposed an efficient data security enhancement scheme for NOMA-PON, addressing primary-user interference and third-party eavesdropping by combining a fixed-point extended logistic chaotic map with a cascaded 2D cellular automata–Turing pattern scrambling (CA-TPCS) algorithm. The method uses FE chaos to construct 2D-CA for dynamic bit diffusion, extracts a Turing symbol substitution matrix via index sorting for 2D symbol scrambling, and employs a dual-key mechanism with uplink data as a private key [18]. Wang, Pan et al. proposed a 4D chaotic IM encryption system for CO-OFDM-PON, combining a 1D cubic map and a 3D T–S fuzzy chaotic system to generate four dynamic scrambling factors that secure index bits, data bits, intra-subcarrier blocks, and inter-subcarrier blocks. The design builds a chaotic many-to-many mapping between index bits and SAPs for index-bit encryption, as well as heterodynes data bits with chaotic bits for data encryption, and applies a chaotic shuffling algorithm to rearrange symbols within and across subcarrier blocks for secondary OFDM-IM encryption [19]. As shown in Table 1, we list and compare representative chaotic PLE schemes, highlighting the PAPR impact, BER/sensitivity performance, and implementation complexity.

Table 1.
Comparative analysis of chaotic physical-layer encryption schemes in terms of PAPR impact, BER/sensitivity performance, and implementation complexity.
Meanwhile, in 2016, Mecozzi proposed the Kramer–Kronig (KK) receiver scheme, which theoretically proved that after adding a sufficiently large continuous wave, the KK receiver can eliminate the influence of signal–signal beat interference (SSBI) on single-sideband (SSB) signals [20]. Li, Erkılınç et al. evaluated DD-SSB 16QAM WDM systems with receiver-side electronic dispersion compensation plus DSP linearization (net O-ISD 2.8 b/s/Hz), showing that receiver-based compensation can match transmitter-based methods; the Kramers–Kronig receiver performed best [21]. Chen, Antonelli et al. demonstrated a 218 Gb/s direct-detection receiver using Kramers-Kronig phase reconstruction and chromatic-dispersion compensation with a single photodiode, enabling single-span 125 km SSMF transmission at 1550 nm [22]. Le, Schuh et al. show low-complexity SSB DD transmission by adding a digital (virtual) carrier with the complex signal using only two DACs. Combined with KK field reconstruction or two-stage SSBI cancelation, eight-channel WDM achieves 1.72 Tb/s net over 200 km at 1550 nm [23]. Kong, Da Silva et al. demonstrate KK detection of a 909.5 Tbit/s DSDM/WDM signal over a single-mode 37-core fiber [24]. Hoang, Sowailem et al. propose 4D modulation with direct detection via a Stokes-vector KK transceiver. Using a digital carrier plus KK detection enables polarization de-rotation without an LO [10]. Che, Sun, and Shieh propose an SSB Stokes-vector receiver to demultiplex 4D POL-MUX signals, fundamentally resolving carrier fading in direct detection. It was validated with 60 Gbaud POL–MUX 16QAM over an 80 km SSMF using digital post-compensation of dispersion [25]. Zhu, Zou et al. demonstrate 448 Gb/s single channels and 1.792 Tb/s WDM Nyquist PDM–16QAM using heterodyne detection with single-ended photodiodes [26]. Li, Galdino et al. present the first use of digital back-propagation for fiber nonlinearity compensation in KK direct-detection receivers, improving 112 Gb/s/λ WDM single-span SSMF transmission up to 160 km [27].
3. Principle
Three-dimensional Lorenz chaos is a three-dimensional chaotic phenomenon generated based on the Lorenz system, which is one of the most classic models in chaos theory. It was proposed by the American meteorologist Edward Lorenz in 1963 when he was studying atmospheric convection problems. It reveals the intrinsic randomness that may appear in deterministic systems and is a typical representative of the “butterfly effect”.
The Lorenz system is a dynamic system composed of three coupled nonlinear ordinary differential equations, and its expression is
where are the state variables of the system (which can be understood as physical quantities describing fluid motion, such as velocity, temperature, etc.); t is time, represented as a positive step value in this paper; and α (Prandtl number), γ (Rayleigh number), and β (geometric parameter) are the control parameters of the system. Among them, γ is the key to determining the transition of the system from order to chaos. Its chaotic range is related to the values of α and β, and the calculation formula of its critical value γc is as follows:
Chaos begins to emerge when parameters take specific values (the classic values are α = 10 and β = 8/3). As ρ continues to increase (such as ρ = 28, 30, 100, etc.), the chaotic characteristics still exist, with only slight changes in the structure of the attractor (such as the degree of stretch of the “wings” and the frequency of trajectory jumps). α (Prandtl number) is a physical quantity describing the ratio of fluid viscosity to thermal diffusivity, and its value is usually related to specific physical scenarios, with a practical range of α ∈ [5,21]. (Ten, sixteen, etc., are commonly used in research). β is a parameter related to the geometric structure of the system (such as the thickness of the fluid layer), and its value is relatively fixed, with a classic practical range of β ∈ [1,12] (the most classic value is β = 8/3 ≈ 2.6667). When the parameters take specific values (the classic values are α = 10, γ = 28, and β = 8/3), the system will exhibit the optimal chaotic characteristics. The phase diagram of its chaotic mapping model is shown in Figure 1.
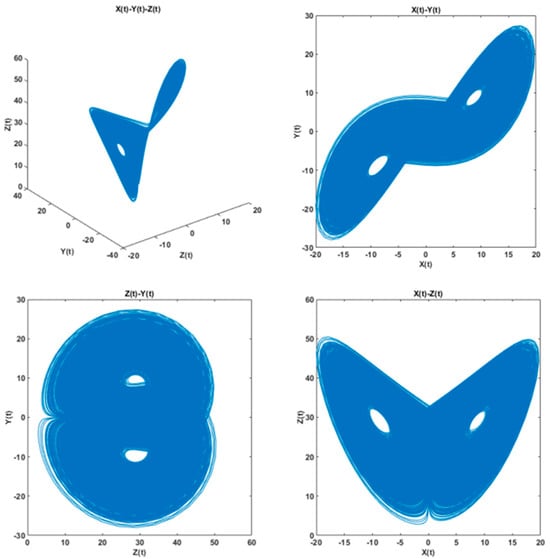
Figure 1.
Phase diagram of the 3D Lorenz chaotic map model.
There are a total of 6 variables () in Equation (1). Different initial values and different control parameters will generate three different chaotic sequences . To ensure the chaotic characteristics of the system, the value range of the control parameters in this paper does not exceed ±0.5 compared with the classic values.
In three-dimensional space, the trajectory of the Lorenz attractor behaves as follows: it winds repeatedly around two symmetric “vortex centers” and randomly “jumps” from one vortex region to another, with the timing and number of jumps being completely unpredictable. The overall trajectory never intersects or repeats itself, forming a complex yet ordered chaotic structure.
The encryption scheme proposed in this paper is as shown in Figure 2. First, we determine the initial values and control parameters of the transmission key for this transmission to generate chaotic sequences . According to Equation (3), the parity of the 13th digit after the decimal point is used to generate corresponding perturbation sequences m/n and l. It should be noted that choosing k = 13 (the 13th fractional digit) balances stability and security: it lies beyond low-order digits that are susceptible to quantization/synchronization bias yet avoids the rounding-dominated tail near the precision limit, yielding stable, near-balanced bits across platforms. Then, m/n and l are generated into keys Key1 and Key2 according to Equation (4).
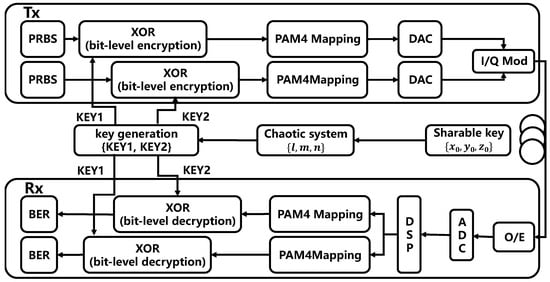
Figure 2.
The encryption scheme proposed in this paper.
After the sender and receiver confirm the transmission of encrypted information, the sequences of the I and Q signals are XORed with the keys according to Equation (5).
The encrypted I and Q signals are modulated by PAM4, and then enter the IQ modulator to complete the modulation of 16QAM signals. After that, the encrypted signals are transmitted according to the method for generating and receiving low-CSPR SSB signals in reference [15]. After the receiver completes the equalization of the low-CSPR single-sideband signal, the legitimate ONU user will generate the correct keys Key1 and Key2 based on the initial values and control parameters of the transmission key and will obtain the information before encryption after performing the XOR operation with the I and Q signals.
4. Experiments and Result Analysis
4.1. Experiment Setup
Figure 3 shows the experimental setup of 3D Lorenz-encrypted SSB-16QAM coherent optical communication systems that remove SSBI to achieve low-CSPR detection. CWs are generated by external cavity lasers (ECLs) with a line width of less than 100 kHz and an output power of less than 15 dBm. The 1550 nm light source is then modulated by the I/Q modulator to realize photoelectric conversion. The I/Q modulator has a 3 dB bandwidth of 33 GHz and an insertion loss of 6 dB.
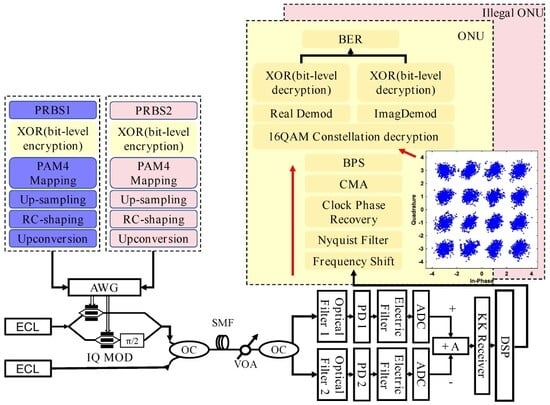
Figure 3.
Experiment setup.
The input of initial values and control parameters for the chaotic sequence at the system’s transmitting end is . A 64 GSa/s AWG is used to convert the two encrypted digital symbol sequences into I/Q analog 10 Gbaud PAM4 signals (with a raised cosine IQ filter and roll-off = 0.2), which are then converted into a 16QAM optical signal via an I/Q modulator. An EDFA with a noise value of 5.5 dB and a variable optical attenuator (VOA) is used to adjust the transmitted signal power into a 1 × 2 OC. CW light is generated by another external cavity laser (ECL 2) that can adjust the frequency to provide a guard band between the CW and 16QAM signals.
The output power of ECL 2 is adjusted by another VOA, and it is then coupled to the other side of the 1 × 2 coupler. The transmission link is composed of a 10 km SMF. The bandwidth of the OBPF1 is 20 GHz, including the 16QAM signal and CW. The bandwidth of OBPF2 is 12 GHz, and the center frequency domain is the same as that of the 16QAM signal. A four-channel digital phosphor oscilloscope with a bandwidth of 100 GSa/s and 20 GHz as ADC is used to receive the signal. The offline digital signal is then processed by MATLAB R2024b.
Offline DSP includes the KK algorithm, resampling, CD, a Nyquist filter, frequency shifts, clock phase recovery, MMA, and BPS. The KK chain is dominated by a block Hilbert transform implemented via two FFTs per -sample block, yielding complexity; timing recovery and equalization are . The Lorenz-driven XOR mapping (and its inverse) is per symbol with no extra buffering, so end-to-end latency is governed by one DSP block ( samples) plus filter transients, with negligible additional delay from the PLE layer. We have set up two types of Optical Network Units (ONUs) at the receiving end. One is a legitimate ONU that knows the initial values and control parameters, enabling it to generate the key at the receiving end and correctly decrypt the received information. The other is an illegal ONU that does not know the key but is aware of the encryption scheme and can use the exhaustive method to brute-force crack the encrypted signal.
4.2. Security Analysis Under Known-/Chosen-Plaintext and Side-Channel Models
We analyze the proposed scheme as a synchronous stream cipher acting on the I/Q bitstreams prior to PAM4-to-16QAM mapping. Let denote the plaintext bits, and let
denote the encrypted bits, where represents key stream bits derived from the Lorenz system by numerical integration with the secret seed
followed by burn-in, stride- sub-sampling, extraction of the 13th fractional-digit parity, and coordinate mixing, as shown in Equations (3)–(5). The adversary is passive, observes the broadcast downlink, and knows all algorithms (Kerckhoffs’s principle) but not . To preclude keystream reuse, we evolve the initial conditions across frames within the allowed parameter windows (Section 3), applying the same parity mechanism to derive small, deterministic offsets; extraction always follows a burn-in and sub-sampling stage. This design removes key-aided pilots or tones and avoids any key-dependent synchronization markers on the physical waveform.
Under known-plaintext or chosen-plaintext conditions, the attacker can recover for the queried positions within a frame via Equation (7). However, predicting unseen key stream bits or recovering from such samples requires inverting highly nonlinear, quantized, and aliased observations—parities of deep fractional digits—of a continuous chaotic system at – precision across six dimensions. No efficient method is known for this inversion, and our per-frame evolution ensures statistical independence across frames. Consequently, KPA/CPA provide only instantaneous key stream exposure and do not compromise future symbols in the same frame or any subsequent frames when key stream reuse is avoided.
The residual attack reduces to a parameter-space search constrained by observed key stream bits. Even with optimistic pruning, discretizing four variables at and at within windows yields approximately . We also consider side-channel avenues pertinent to low-CSPR KK-SSB. Because XOR is applied at the bit level before PAM4-to-16QAM modulation, the minimum-phase condition required by KK phase retrieval is preserved, spectral zeros are not introduced, and co-design with our SSBI mitigation maintains negligible PAPR growth. The absence of key-dependent pilots or tones eliminates simple spectral or timing markers on the downlink. Further, double-precision integration, burn-in, stride- sub-sampling, and coordinate mixing suppress finite-precision short-period effects that could otherwise re-emerge after KK reconstruction. These measures collectively raise the bar against side-channel exploitation while keeping transmission performance identical to the non-encrypted baseline shown in Figure 4 and Figure 5.
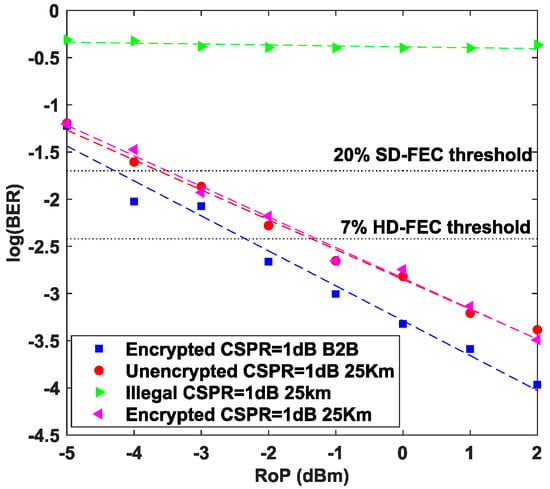
Figure 4.
Comparison of transmission results among legitimate ONUs (using correct keys and incorrect keys), illegal ONUs, and non-encrypted systems.
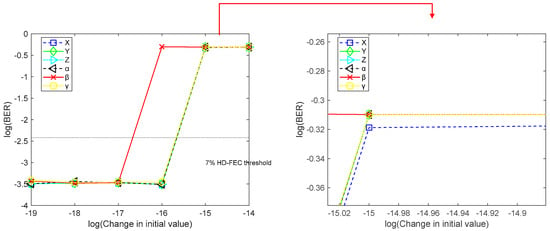
Figure 5.
BER curve when there is a slight change in the initial value among the key parameters.
4.3. Results Analysis
Figure 4 shows a comparison between the proposed encrypted low-CSPR KK receiving system and the non-encrypted system. As can be seen from the experimental results in the figure, the ONU using the legitimate key achieves a bit error rate below the 7% HD-FEC threshold under the back-to-back condition with a received power of approximately −2.3 dBm. After 25 km of fiber transmission, the bit error rate curve of the ONU using the legitimate key nearly overlaps with that of the non-encrypted system. It can achieve a bit error rate below the 7% HD-FEC threshold at a received power of approximately −1.4 dBm and a bit error rate below the 20% SD-FEC threshold at a received power of approximately −3.7 dBm. Since the illegal ONU does not use the correct key (e.g., using or ), its bit error rate is much higher than 10−1.
Figure 5 shows the BER curve when the initial values and initial parameters undergo slight changes at a received optical power of 0 dBm after 25 km of fiber transmission, verifying the initial value sensitivity of the chaotic system and the security of the proposed encryption system. Among them, the initial values and control parameters of the legitimate ONU user in the chaotic system are set as . It can be found from the figure that when only a tiny change of 10–15 occurs in any of the above six parameters (such as ), the BER rises sharply, and the parameter β will have a significant change even with a 10−16 variation.
Since the control parameters of the chaotic model are generally selected around typical values, the considered value ranges of α, γ, and β are within ±0.5 of the typical values. If the above six parameters are taken into account, the step range of t is assumed to be [1, 103].
We bound the key space using the actual admissible domains and quantization applied in our system. Control parameters are restricted to robust-chaos windows around the canonical values, and initial conditions to States are generated in single precision and deterministically quantized so that the parity of the 13th fractional digit is well-defined. Counting distinguishable seeds on these grids and including the time-step index and the per-segment counter (mixed into the seed) yield an effective brute-force space on the order of while retaining KK compatibility (no spectral zeros, negligible PAPR growth, and preserved SSBI mitigation).
5. Discussion
At higher symbol rates, the KK-SSB receiver remains computationally tractable because the FFT-based Hilbert transform and timing/equalization stages scale as O(N log N) and O(N), respectively. The dominant challenges arise from hardware and waveform margins: tighter analog front-end bandwidth, DAC/ADC ENOB limits, and increased sensitivity to laser phase noise and the excess phase. Preserving the minimum-phase condition over wider spectra requires careful CSPR tuning, digital pre-emphasis to manage PAPR, and consistent biasing of the modulator. The proposed PLE layer is rate-agnostic—its XOR mapping is O(1) per symbol and does not add buffering—so the principal rate-scaling risks are practical ones such as key/chaotic-seed synchronization at very short symbol periods, which we mitigate using lightweight frame markers and periodic seed re-alignment.
For longer fiber spans, chromatic dispersion and OSNR degradation become the primary constraints, followed by residual nonlinearities (SPM/XPM). KK detection is resilient to linear impairments when minimum-phase conditions hold, but accumulated dispersion broadens the signal spectrum and can shrink that margin if compensation is imperfect or if CSPR is set too low under amplified noise. Our DSP already includes CD compensation; for extended reaches, we anticipate modest enhancements—adaptive CD estimation per burst, tighter CSPR control versus OSNR, and, if needed, single-step digital back-propagation or a Volterra equalizer—to maintain performance without modifying the PLE layer. Since PLE operates on mapped bits rather than the analog waveform, it neither exacerbates fiber nonlinearity nor interferes with KK phase reconstruction; latency continues to be governed by one DSP block plus filter transients.
In multi-user settings such as WDM or PON, penalties are dominated by inter-channel crosstalk, relative frequency offsets, and timing skew, which appear as excess EVM and an increased cycle-slip risk in timing recovery. With independent seeds, the PLE masks are orthogonal across users, so interference manifests in the optical/electrical domains rather than through cryptographic coupling. Per-channel CSPR optimization, conventional guard-band planning, and narrowband optical filtering are effective in maintaining KK stability in the presence of adjacent-channel leakage typical of 50–100 GHz grids; for denser packing, slightly raised CSPR or sharper filters restore the minimum-phase condition at the cost of modest OSNR.
Overall, the scalability limits are governed by the familiar KK-SSB trade-offs among CSPR, OSNR, bandwidth, and front-end linearity and not by the PLE itself. Future work will report systematic measurements across baud rates (e.g., 32/64/96 Gbd), spans representative of metro–regional links with EDFA chains, and multi-user experiments in a WDM-PON emulator to map the operating envelope and quantify the minimal overhead introduced by the PLE under each regime.
6. Conclusions
We have experimentally demonstrated that the low-CSPR SSB transmission system, after adopting 3D Lorenz chaotic encryption, not only does not affect its transmission quality but also achieves a key space of 1091. This ensures that illegal users cannot crack the correct information in a short time, greatly enhancing its security. Chaotic encryption enables single-sideband systems to achieve extremely high security while maintaining high spectral resource utilization, which allows them to play a significant role in future applications such as large-capacity multi-user optical communication networks in data centers.
Author Contributions
Conceptualization, C.Y. and Y.L. (Yuanfeng Li); methodology, C.Y., A.Z. and H.Y.; software, C.Y. and H.Y.; validation, C.Y., M.Y., Y.L. (Yue Liu) and H.Z.; formal analysis, C.Y., X.Z. and D.Z.; investigation, X.C., H.Q., D.W. and P.H.; resources, C.Y. and X.Z.; data curation, Y.Q.; writing—original draft preparation, C.Y. and A.Z.; writing—review and editing, C.Y.; visualization, Y.Q.; supervision, C.Y. and X.Z.; project administration, D.Z.; funding acquisition, Y.L. (Yue Liu). All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key R&D Program of China “6G satellite communication access networking technology” (No. 2020YFB1808000).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All data included in this study are available upon request by contact with the corresponding author.
Conflicts of Interest
All authors were employed by China’s Telecom Satellite Communications Satellite Application Technology Research Institute Branch during the course of this work. The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Chen, T.; Rao, R.R. Audio-visual integration in multimodal communication. Proc. IEEE 1998, 86, 837–852. [Google Scholar] [CrossRef]
- Almadani, B.; Mostafa, S.M. IIoT Based Multimodal Communication Model for Agriculture and Agro-Industries. IEEE Access 2021, 9, 10070–10088. [Google Scholar] [CrossRef]
- Ren, C.; Gong, C.; Liu, L. Task-Oriented Multimodal Communication Based on Cloud–Edge–UAV Collaboration. IEEE Internet Things J. 2024, 11, 125–136. [Google Scholar] [CrossRef]
- Kanter, G.S.; Reilly, D.; Smith, N. Practical physical-layer encryption: The marriage of optical noise with traditional cryptography. IEEE Commun. Mag. 2009, 47, 74–81. [Google Scholar] [CrossRef]
- Zhang, J.; Marshall, A.; Woods, R.; Duong, T.Q. Design of an OFDM Physical Layer Encryption Scheme. IEEE Trans. Veh. Technol. 2017, 66, 2114–2127. [Google Scholar] [CrossRef]
- Zhang, C.; Yue, J.; Jiao, L.; Shi, J.; Wang, S. A Novel Physical Layer Encryption Algorithm for LoRa. IEEE Commun. Lett. 2021, 25, 2512–2516. [Google Scholar] [CrossRef]
- Li, S.; Zheng, X.; Mou, X.; Cai, Y.L. Chaotic encryption scheme for real-time digital video. In Proceedings of the IS&T/SPIE 14th Annual Symposium on Electronic Imaging, San Jose, CA, USA, 20–25 January 2002; SPIE: Bellingham, WA, USA, 2002; Volume 4666, pp. 149–160. [Google Scholar]
- Dai, S.; Sun, K.; Ai, W.; Peng, Y. Novel discrete chaotic system via fractal transformation and its DSP implementation. Mod. Phys. Lett. B 2020, 34 (Suppl. S1), 2050429. [Google Scholar] [CrossRef]
- Yu, C.; Gao, R.; Wang, F.; Li, Z.; Guo, D.; Chang, H.; Zhou, S.; Liu, X.; Wang, F.; Gao, Y.; et al. Modified low CSPR Kramer–Kronig receivers based on a signal–signal beat interference estimation. Opt. Express 2022, 30, 28251–28267. [Google Scholar]
- Hoang, T.M.; Sowailem, M.Y.S.; Zhuge, Q.; Xing, Z.; Morsy-Osman, M.; El-Fiky, E.; Fan, S.; Xiang, M.; Plant, D.V. Single wavelength 480 Gb/s direct detection over 80km SSMF enabled by Stokes vector Kramers Kronig transceiver. Opt. Express 2017, 25, 33534–33542. [Google Scholar] [CrossRef]
- Zhao, J.; Liu, B.; Mao, Y.; Ullah, R.; Ren, J.; Chen, S.; Jiang, L.; Han, S.; Zhang, J.; Shen, J. High security OFDM-PON with a physical layer encryption based on 4D-hyperchaos and dimension coordination optimization. Opt. Express 2020, 28, 21236–21246. [Google Scholar]
- Ren, J.; Liu, B.; Zhao, D.; Han, S.; Chen, S.; Mao, Y.; Wu, Y.; Song, X.; Zhao, J.; Liu, X.; et al. Chaotic constant composition distribution matching for physical layer security in a PS-OFDM-PON. Opt. Express 2020, 28, 39266–39276. [Google Scholar] [CrossRef]
- Tang, R.; Ren, J.; Fang, J.; Mao, Y.; Han, Y.; Shen, J.; Zhong, Q.; Wu, X.; Tian, F.; Liu, B. Security strategy of parallel bit interleaved FBMC/OQAM based on four-dimensional chaos. Opt. Express 2021, 29, 24561–24575. [Google Scholar] [CrossRef]
- Wang, Z.; Xiao, Y.; Wang, S.; Yan, Y.; Wang, B.; Chen, Y.; Zhou, Z.; He, J.; Yang, L. Probabilistic shaping based constellation encryption for physical layer security in OFDM RoF system. Opt. Express 2021, 29, 17890–17901. [Google Scholar] [CrossRef] [PubMed]
- Liu, L.; Tang, X.; Li, F.; Xu, Z.; Zhang, X. Enhanced Physical Layer Security and PAPR Performance Based on Disturbance of Data Cluster Under Chaotic Sequence Color Seeking Mechanism in CO-OFDM System. J. Light. Technol. 2023, 41, 6507–6513. [Google Scholar] [CrossRef]
- Li, Y.; Wang, D.; Ding, H.; Li, Z.; Wang, X. Physical Layer Encryption for CO-OFDM Systems Enabled by Camera Projection Scrambler. Mathematics 2024, 12, 1807. [Google Scholar] [CrossRef]
- Chen, Q.; You, W.; Wen, H.; Chen, M.; Ma, J. Dual chaotic encryption scheme for index modulation orthogonal time frequency space PON system. Opt. Express 2025, 33, 30997–31009. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Zhang, Q.; Xin, X.; Sun, M.; Gao, R.; Yao, H.; Tian, F.; Tian, Q.; Wang, Y.; Wang, F.; et al. Security enhancement for NOMA-PON with 2D cellular automata and Turing pattern cascading scramble aided fixed-point extended logistic chaotic encryption. J. Opt. Commun. Netw. 2024, 16, 1204–1217. [Google Scholar] [CrossRef]
- Wang, Y.; Pan, X.; Zhang, Q.; Xin, X.; Gao, R.; Yao, H.; Tian, F.; Wang, F.; Li, Z.; Liu, X.; et al. Chaotic index modulation and subcarrier intra-block-inter-block shuffling for secure CO-OFDM-PON based on a hybrid 4D chaos. Opt. Express 2025, 33, 21217–21235. [Google Scholar] [CrossRef]
- Mecozzi, A.; Antonelli, C.; Shtaif, M. Kramers–Kronig coherent receiver. Optica 2016, 3, 1220–1227. [Google Scholar] [CrossRef]
- Li, Z.; Erkılınç, M.S.; Shi, K.; Sillekens, E.; Galdino, L.; Thomsen, B.C.; Bayvel, P.; Killey, R.I. SSBI mitigation and the Kramers–Kronig scheme in single-sideband direct-detection transmission with receiver-based electronic dispersion compensation. J. Light. Technol. 2017, 35, 1887–1893. [Google Scholar] [CrossRef]
- Chen, X.; Antonelli, C.; Chandrasekhar, S.; Raybon, G.; Sinsky, J.; Mecozzi, A.; Shtaif, M.; Winzer, P. 218-Gb/s single-wavelength, single-polarization, single-photodiode transmission over 125-km of standard singlemode fiber using Kramers-Kronig detection. In Proceedings of the Optical Fiber Communication Conference, Los Angeles, CA, USA, 19–23 March 2017; Optica Publishing Group: Washington, DC, USA, 2017. [Google Scholar]
- Le, S.T.; Schuh, K.; Chagnon, M.; Buchali, F.; Dischler, R.; Aref, V. 1.72-Tb/s virtual-carrier-assisted direct-detection transmission over 200 km. J. Light. Technol. 2018, 36, 1347–1353. [Google Scholar] [CrossRef]
- Kong, D.; da Silva, E.P.; Sasaki, Y.; Aikawa, K.; Da Ros, F.; Galili, M.; Morioka, T.; Oxenløwe, L.K.; Hu, H. Kramers–Kronig detection with adaptive rates for 909.5 Tbit/s dense SDM and WDM data channels. In Proceedings of the 2018 European Conference on Optical Communication (ECOC), Rome, Italy, 23–27 September 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–3. [Google Scholar]
- Che, D.; Sun, C.; Shieh, W. Single-channel 480-Gb/s direct detection of POL-MUX IQ signal using single-sideband Stokes vector receiver. In Proceedings of the Optical Fiber Communication Conference, San Diego, CA, USA, 11–15 March 2018; Optica Publishing Group: Washington, DC, USA, 2018. [Google Scholar]
- Zhu, Y.; Zou, K.; Ruan, X.; Zhang, F. Single carrier 400G transmission with single-ended heterodyne detection. IEEE Photonics Technol. Lett. 2017, 29, 1788–1791. [Google Scholar]
- Li, Z.; Galdino, L.; Xu, T.; Erkılınç, M.; Shi, K.; Sillekens, E.; Thomsen, B.; Bayvel, P.; Killey, R. Performance of digital back-propagation in Kramers-Kronig direct-detection receivers. In Proceedings of the Optical Fiber Communication Conference, San Diego, CA, USA, 11–15 March 2018; Optica Publishing Group: Washington, DC, USA, 2018. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).