Abstract
We propose a general approximation method for the determination of optimal trading strategies in markets with proportional transaction costs, with a polynomial approximation of the residual value function. The method is exemplified by several problems, from optimally tracking benchmarks and hedging the log contract to maximizing utility from terminal wealth. Strategies are also approximated by practically executable, discrete trades. We identify the necessary trade-off between the trading frequency and trade size to ensure satisfactory agreement with the theoretically optimal, continuous strategies of infinite activity.
MSC:
91G10; 91G80
1. Introduction
It was explained to me that the effects on which one was working were so vanishingly small that without the greatest possible precision in computation they might have been missed altogether.Norbert Wiener1
Optimal trading strategies in a Black–Scholes market or its extensions face challenges when applied to realistic markets with friction, including transaction costs, price impacts, or margin requirements. For instance, employing a constant proportion trading strategy or a standard Delta hedge in the Black–Scholes model becomes practically infeasible in the presence of a relative bid–ask spread , as it may lead to immediate bankruptcy due to trading policies of infinite variation. In order to maintain solvency in markets with proportional transaction costs, the trading frequency is adjusted to finite variation, involving the minimal trades necessary to stay close to the target exposures. The deviation from this target exposure is of order , while the impact on the transaction costs is of the second order (that is, of magnitude , cf. Shreve and Soner (1994); Gerhold et al. (2014); Kallsen and Muhle-Karbe (2017); Rogers (2004)). Determining long-run optimal trading strategies or solutions to infinite horizon problems involves solving specific free boundary problems. These problems define the boundaries that limit the maximum deviation of a portfolio statistic from the target, where these statistics commonly represent the proportion of wealth in the risky asset, the risky–safe ratio, or transformed variants. For constant investment opportunities, an investor refrains from trading when is outside a constant region , engaging in minimal trading only at the boundaries to maintain the statistic within the interval. This strategy is embodied by a diffusion with two reflecting boundaries and is referred to as a control limit policy Taksar et al. (1988). The parameterization of the involved equations and the methods to solve them are customized for each specific setup. However, the analytical methods are highly technical, making them suitable for an expert audience. Moreover, the resulting optimal trading policies are reflected diffusions (cf. Tanaka (1979)), making them impractical for implementation as they entail infinite activity.
The aim of this paper is to address these challenges by introducing asymptotic methods, both for the approximation of the value functions in various problems and the design of asymptotically optimal trading policies that can be executed in real trading environments. Asymptotic methods have proved instrumental in understanding the sensitivity of trading boundaries and welfare to different market and risk aversion parameters (cf. the ingenious insights of Constantinides (1986) based on numerical computation, with the financial interpretation of the asymptotic expansions derived in Kallsen and Muhle-Karbe (2017); Gerhold et al. (2012, 2014).
First, we employ finite activity strategies to approximate control limit policies. In contrast to reflected diffusions, these strategies can be implemented in a real trading environment. They involve trades of fixed size aimed at re-aligning a portfolio statistic with its frictionless target, such as adjusting the proportion of wealth in the risky asset when reaching . Acknowledging the insightful contribution of Shreve and Soner (1994, Appendix B), which highlights that no-trade regions typically scale with a size proportional to , discrete trades in this context must be of the same or higher order as the bid–ask spread. The findings of this paper offer an alternative answer to the question of Rogers (2004) regarding the effect of proportional transaction costs on welfare. Approximating the control limit policy with trades of fixed size reveals that the transaction costs, at the leading order, are a product of the bid–ask spread (), trade size ( for ), and trading frequency (proportional to ), resulting in the same cost of order , irrespective of the smallness of the trades (dictated by the parameter ) or the objective under consideration.
Second, we put forward a general approximation method for pertinent free boundary problems, which often2 can be expressed as
Here, an unknown scalar representing the proportion of wealth in the risky asset is involved. The function g must satisfy a second-order ODE (1) between the buy and sell boundaries and and boundary conditions (2) and (3). While the latter are universal, the ODE (1) identifies the specific objective under consideration. The approximation method relies on a polynomial expansion of the scalar function g and an asymptotic Ansatz for the trading boundaries .
The parameter in the condition (2) represents the relative bid–ask spread of the risky asset S, where one purchases the asset at time t at the ask price and sells it at the slightly lower price (ibid). This boundary condition’s specific form lends itself to the financial interpretation of a frictionless price with a functional form expressed as . This serves as a potential shadow price, which is a fictitious risky asset evolving within the bid–ask spread and which aligns precisely with the bid or ask of S whenever the optimal strategy for involves executing trades. This asset is indeed a shadow price for power and log-utility, as noted in previous studies by Gerhold et al. (2013, 2014); Guasoni and Muhle-Karbe (2013). However, for certain local criteria, it might only serve as an asymptotic shadow price (or none at all), as discussed in Kallsen and Muhle-Karbe (2017); Mayerhofer (2024). Notwithstanding this issue, our method is applicable for equations both in the original markets and in potential shadow markets. A distinctive aspect of this paper lies in its examination of Neuberger’s log contract Neuberger (1994) and its dynamic hedge under proportional transaction costs, supplementing the well-explored objectives with known solutions in the literature. Due to the straightforward form of its free boundary problem, our analysis may serve as a valuable introductory example for graduate students delving into the realm of optimization under proportional transaction costs.
Program of Paper
The paper’s structure is organized as follows. Section 2 introduces the market model, encompassing a risky Black–Scholes asset with transaction costs, along with the presentation of relevant admissible strategies for this study. Section 3 comprises three distinct parts.
Section 3.1 investigates three strategies and evaluates their performance in terms of the trading frequency and long-run cost. This includes the examination of minimal trades (control limit policies; see Section 3.1.1), maximal trades (discrete trades directly to the target; see Section 3.1.2), and small trades (sufficiently small trades to closely align with control limit policies; see Section 3.1.3). Section 3.2 is dedicated to optimization problems related to tracking specific targets. It includes the computation of asymptotic approximations for the free boundary problem for leveraged ETFs (see Section 3.2.1) and optimally hedging a log contract (see Section 3.2.4). Section 3.3 examines classical objectives with a long-run horizon, featuring the risk-averse investor (Section 3.3.1), the log-utility investor (Section 3.3.2), and the risk-neutral investor (Section 3.3.3). The interpretation and discussion of these results are presented in Section 4.
2. Materials and Methods
In our financial market model, there are two tradable assets: a risk-free asset with continuous compounding at a rate and a risky asset S with ask price , governed by the dynamics
where B denotes a standard Brownian motion. We introduce a relative bid–ask spread , ensuring that the risky asset is sold at .
In markets with friction, the trading strategies need to be modified so as to ensure solvency. In the presence of transaction costs, solvency constraints dictate that only finite-variation trading strategies are viable.3 Let be the safe position and the risky position. Furthermore, denote by and the cumulative number of shares bought and sold, respectively. The total wealth, assessed at the ask, is given by , where .
In this paper, we study two types of trading strategies. For continuous , the self-financing condition reads
If is a finite activity jumps process of the pure jump type, such that
then the self-financing condition reads
The following defines admissible strategies.
Definition 1.
The trading policy is admissible if
- (i)
- and are right-continuous, increasing, and non-anticipating processes;
- (ii)
The collection of admissible trading policies is denoted by Φ.
Depending on the specific optimization criterion, some extra integrability or solvency conditions may apply. (Since we focus on asymptotic methods to solve a range of free boundary problems, we refrain from formulating them explicitly.)
The next statement elaborates the dynamics of wealth, its fraction in the risky asset, and the ratio of risky and safe investment.
Lemma 1.
For any admissible, continuous trading strategy φ, we have
If is of the pure jump type (cf. (6)), the same statistics satisfy similar equations, perhaps most rigorously stated in integral form:
3. Results
3.1. Transaction Cost Asymptotics
Reflected diffusions are continuous processes and of finite variation by construction; therefore, strategies of this kind are admissible in the presence of proportional transaction costs. While optimal across a range of optimization criteria in theory, they are practically unrealized due to actual trades occurring discretely in time. In this section, we approximate continuous trading policies with those that trade fixed amounts of the risky asset, thus introducing jumps. The primary challenge lies in quantifying the minimal trade size required to achieve nearly optimal performance. While larger trades align better with a target, they also incur greater costs (cf. Figure 1).
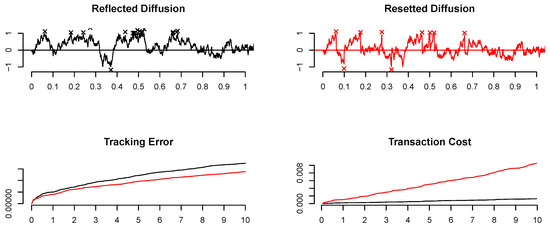
Figure 1.
The upper panel plots illustrate reflected (black line) and resetted (red line) centred Brownian motions with a standard deviation of 10%. Reflected diffusions execute minimal trades—here approximated with small trades—while maximal trades are characteristic of resetted diffusions (as depicted in the second plot). Crosses on the graphs mark trading dates and positions. Notably, over a ten-year period, the annualized tracking error tends to be smaller for resetted diffusions, whereas the transaction costs are generally lower for minimal trades (lower panel).
In this section, we investigate the transaction costs and trading frequency associated with three strategies aimed at maintaining a portfolio statistic near a target. These strategies include the following.
- (i)
- Minimal trades: These strategies operate continuously, engaging in minimal trading at the boundaries of specific no-trade regions (cf. the first plot of Figure 1 (black lines)).
- (ii)
- Maximal trades: These strategies reset a portfolio statistic to its target value once it reaches these boundaries (cf. the first second plot in Figure 1 (red lines)).
- (iii)
- Small trades: These involve smaller trades than (ii) made in the direction of the target value.
The general framework involves a geometric Brownian motion with a drift parameter M and diffusion parameter evolving in an interval , reflected at its boundaries . The financial interpretation of varies among examples, representing either the risky–safe ratio or the risky position . Similarly, the processes that confine the GBM within vary, influencing the definition of the transaction costs.
Each subsection begins by outlining this general setup of a reflected or resetted geometric Brownian motion. We introduce two types of transaction costs: the average transaction costs (ATC), measuring the negative contribution to infinitesimal returns due to a non-zero bid–ask spread, and the transaction costs (TRC), which quantify the actual long-term cost per time unit. The ATC arises for leveraged ETFs in Section 3.2.1 and for the risk-neutral investor in Section 3.3.3 as a penalty in the objective4, whereas the TRC provides the penalty for the log contract in Section 3.2.4.
3.1.1. Minimal Trades
The dynamics of a reflected GBM are
where L resp. U are local times, with the only points of increase (resp. decrease) on (resp. ).
We shall need the stationary density of a reflected diffusion (Guasoni and Mayerhofer 2019, Lemma B.5).
Lemma 2.
Let . Then, there exists an admissible trading strategy such that the risky–safe ratio satisfies SDE (7). Moreover, is a reflected diffusion on the interval . In particular, if , then has stationary density that equals
and, if , then
The trading strategy in Lemma 2 is called the “control limit policy”, cf. Taksar et al. (1988); Mayerhofer (2024).
We start with the following.
Lemma 3.
Proof.
(cf. Gerhold et al. 2014, Lemma C.2, which is a slightly different version, with a different proof.) For convenience, we perform a logarithm transformation. The process is a reflected Brownian motion on , where , with dynamics
To extract , we apply Itô’s formula to the function . As , and , we obtain
Dividing by T and letting it tend to infinity, we have
The limit on the right side can be computed by the Ergodic Theorem (Borodin and Salminen 2002, Chapter II) such that
where the stationary density g of follows from Lemma 2
In total,
from which (10) follows. A similar argument produces (11). □
We consider now two important examples, which both are encountered in this paper. The first one trades, so as to keep the risky position approximately constant, a strategy that is required in the optimal replication of a log contract.
Proposition 1.
For , consider the strategy that trades minimally, by only buying at and selling at as much as necessary to keep the risky position in the interval . If the trading boundaries are of the form5
with , and , then the long-run, average transaction costs are
For sufficiently small ε, we have the following asymptotic formula:
Proof.
The next strategy trades so as to keep the proportion of wealth approximately constant.
Proposition 2.
For , consider the strategy that trades minimally, by only buying at and selling at as much as necessary to keep the proportion of wealth in the risky asset in the interval . If the trading boundaries are of the form
with , and , then the long-run, average transaction costs are
For sufficiently small ε, we have the following asymptotic formula:
Proof.
We change to the risky–safe ratio , such that the new trading boundaries have asymptotics
The risky–safe ratio satisfies the dynamics (7) and thus is a geometric Brownian motion of the form (9), where and , while
The rest of the proof is similar to that of Proposition 1. □
Remark 1.
The second-order coefficients of the trading boundaries (15) only enter the third-order term of the average trading costs (16), and their impact depends on the difference . For a range of criteria, including the ones in the present paper, we have , whence these coefficients do not impact the average trading costs at the third order.
3.1.2. Maximal Trades
In this section, we consider the process on that satisfies
with fixed jump sizes, such that we reset to some point , whenever it hits . We compute the average, long-run jump sizes, and then compute the transaction costs for constant proportion trading strategies, similar to Section 3.1.1. By taking logarithms, we obtain , which is a resetted Brownian motion on , where , satisfying the dynamics
Whenever hits (resp. ), it is reset to . Thus, we have , and . Define the differential operator
By construction, is a Markov process on .6 By Itô’s formula, for any ,
Thus, solves the martingale problem for , where constitutes those functions for which and thus is a martingale.
Lemma 4.
The process η is ergodic, with stationary density
where and
The ergodic theorem applies, such that, for any bounded continuous7 function f,
Proof.
To derive the stationary density , we solve the adjoint equation
for on and for on , where (). The constants and are determined by insisting on continuity (), vanishing density at the boundaries (), and mass one ().
To prove the ergodicity, we assume, for brevity of exposition, that and that (the general case can be proven similarly but is more tedious due to the lengthy formulas). Furthermore, by shifting the process, we can assume, without loss of generality, that . In this case, the stationary density takes the specific form
To compute the limit on the left side of (21), the starting point is irrelevant, as the diffusion is reset every time it hits the boundary (the integral up to the first hitting time gives a vanishing contribution to the overall limit), thus starting from . Therefore, we may, without loss of generality, start the process also initially at . Denote the consecutive exit times
Since is Markovian, the inter-exit times () are independent and identically distributed with first moment
Thus, by the strong law of large numbers (SLLN), almost surely,
Similarly, the random variables are independent, identically distributed with mean and thus by the SLLN, almost surely,
The expectation on the right-hand side of (24) is computed in the following. Let w be the unique solution of the Dirichlet problem
By Itô’s formula, for ,
Since , , and by (25), we obtain, by optimal stopping,
The explicit solution of (25) is given by
Comparing this with the stationary density (22) reveals that
and thus, by (24),
A combination with (23) and (24) yields
Note that this limit involves annualizing over random horizons the . It remains to show that this limit is the same for annualizing with deterministic time T. For each , let be the first passage time of t, for the renewal process , where . That is,
A combination of (Gut 2009, Theorems 4.1 and 3.4.2) yields that, almost surely,
and
Therefore,
where, because of (27), (28), and (26), the first term converges to the desired limit, whereas the second term, bounded by
converges due to (28) to zero, as . Recalling (26) confirms this claim. □
In Figure 2, the histogram of the (approximate) distribution of for years is given, along with the exact stationary distribution provided by Lemma 4. The fit of this asymmetric distribution appears to be excellent, reflecting that daily sampling is sufficient for financial data with reasonable parameter ranges, and that approaches stationarity for a finite time horizon of five years.
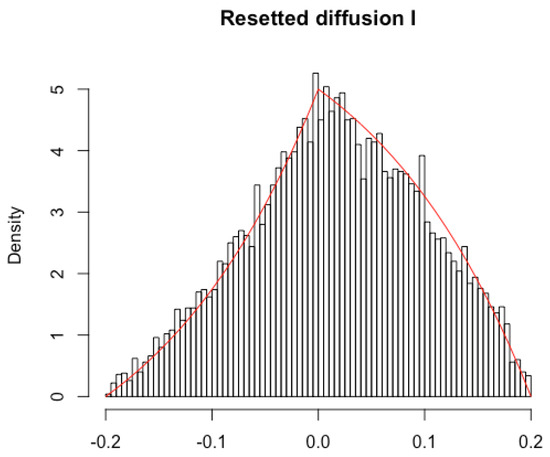
Figure 2.
For and , and , , and , we plot the stationary density of the resetted process . The histogram gives the value of for years, from ten thousand simulated paths (daily frequency).
We are able to count the number of downward jumps of by appealing to the ergodic theorem.
Proposition 3.
where
Proof.
Let f be the quadratic function
As, , and , and
we obtain, by Equation (19), after division by T and letting ,
It remains to evaluate the almost sure limit on the right side, by appealing to the ergodic theorem. Since
we have
By Lemma 4, and using the stationary density (20) of , we obtain and thus (29). □
We revisit the strategy that keeps the proportion of wealth approximately constant. The proof of the following is similar to that of Proposition 2 and thus omitted. Note that we do not give the explicit formula, which can easily be derived from the previous statements but would take up too much space here. For the same reason, we only provide asymptotics of the leading order.
Proposition 4.
For and , consider the strategy that buys at and sells at as much as necessary to bring the proportion of wealth in the risky asset back to Λ. If the trading boundaries are of the form
with , then the average transaction costs satisfy, for sufficiently small ε, the following.
- (i)
- (Selling Frequency) The long-run selling frequency per unit time satisfies the asymptotics
- (ii)
- (Average Cost) The average transaction costs satisfy the asymptoticsand thus, at leading order, are twice the cost of the control limit policy (that is, Equation (16) of Proposition 2).
3.1.3. Small Trades
The cumulative number of shares bought or sold lacks absolute continuity, necessitating approximation for real-world trade applications through trades of fixed size. However, executing discrete trades toward the midpoint of the no-trade region proves suboptimal, incurring twice the transaction costs compared to control limit policies (Proposition 4 (ii)). Using the methods developed in this section, a similar outcome can be demonstrated for trades of any order comparable to the size of the no-trade region (approximately , as indicated in Remark 2).
This prompts the question of determining the optimal trade size for a satisfactory approximation of the optimal trading policy. In the computation of the average trading costs, a crucial factor is the stationary density of the resetted or reflected diffusions (e.g., ). Hence, smaller trades contribute to a better approximation of the stationary density of the control limit policy, as illustrated in Figure 3. In this section, we substantiate this intuition by approximating the somewhat abstract reflected diffusion discussed in Section 3.1.1. We achieve this by employing adequately small trades, ensuring that the transaction costs align at the leading order with the control limit policy (Proposition 2).
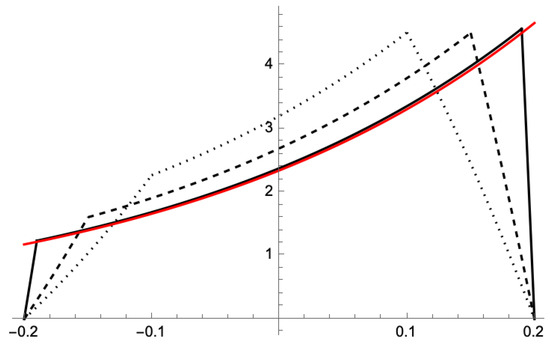
Figure 3.
The stationary densities converge, for smaller and smaller trades, to the stationary density of a reflected diffusion (red line). Here, , (dotted line), (dashed line), and (solid line). The parameters are and .
This section is analogous to the previous one, with the modification that we trade from to , and from to , where
Define again ; then, for any function f, we obtain the dynamics
To extract the downward jumps , we use , for which , and
Furthermore,
By dividing (31) by T and letting , we obtain
a limit that exists almost surely and can be computed by appealing to a suitably tailored ergodic theorem, knowing the stationary density. (The proof is similar to the one in Section 3.1.2 but results in more tedious computations and longer proofs and thus is omitted.) The simulation in Figure 4 demonstrates the satisfactory agreement of the empirically computed stationary density of ( years) with its exact counterpart .
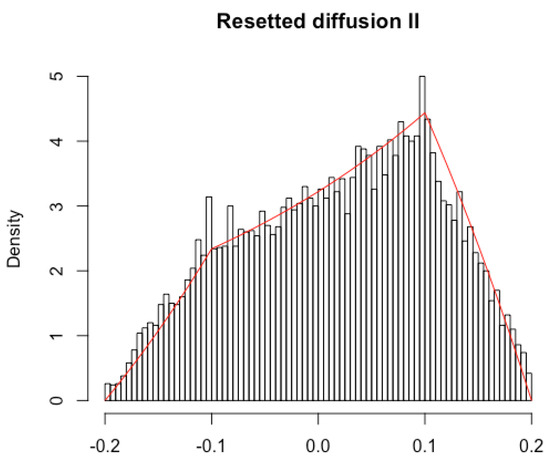
Figure 4.
Small trades of fixed size. For and , and , , , and , we plot the stationary density of the resetted process . The histogram gives the value of for years, from ten thousand simulated paths (daily frequency).
The sizes of the no-trade regions in all our examples are proportional to ; thus, sufficiently small trades must be of the second order. We summarize the trading frequency and long-run transaction costs.8
Proposition 5.
For and , consider the strategy that buys at resp. sells at as much as necessary to bring the proportion of wealth in the risky asset to resp. . If the trading boundaries are of the form (30) with , and if
with , or sufficiently small ε, the following must apply.
- (i)
- (Selling Frequency) The long-run selling frequency per unit time satisfies the asymptotics
- (ii)
- (Average Cost) The average transaction costs satisfy the asymptoticsand thus agree, at leading order, with the cost of the control limit policy (that is, Equation (16) of Proposition 2).
Remark 2.
If, instead of (33), one would use significantly larger trades, to
then the selling frequency is given by
and the transaction costs are
For , we recover the trades to some point Λ in the no-trade region (Proposition 4), and, for any , we obtain an ATC slightly larger at leading order than the original one. This means that such trading strategies never match the trading costs of the control limit policy at the relevant second order.
3.2. Tracking Frictionless Targets
3.2.1. Levered Funds
The manager of a leveraged (or inverse) exchange traded fund (LIETF) has to maintain a constant exposure to a constant multiple of the benchmark’s S return with dynamics (4). For this section, we take the conservative view that the annualized average excess returns of S vanish, which is in line with the objective of a levered ETF manager to track a multiple of a benchmark’s return rather than to outperform it.9
Due to the fact that frequent trading incurs transaction costs, it is impossible to trade by perfectly matching the target leverage—such a strategy would lead to immediate bankruptcy, as it is of infinite variation. To measure the discrepancy between a fund’s excess returns (with wealth w, trading strategy ) and the multiple of the underlying excess return (the target), we use the (cumulative) difference
The most relevant statistics of D, the tracking distance (TrD) and tracking error (TrE), are defined by
with the quadratic variation of D being .
The explicit expression on the right side of (34) reveals that the negative tracking distance is equal to the average tracking costs (ATC) (cf. Guasoni and Mayerhofer (2019)). Thus, managing an LIETF means finding an optimal trade-off between the tracking distance TrD (or ATC) and tracking error TrE (for a more detailed explanation of this objective, cf. Guasoni and Mayerhofer (2023)).
Maximizing the tracking distance for a fixed tracking error can be summarized as minimizing the long-run equivalent expense ratio (EER):
where the Lagrange multiplier is interpreted as an aversion to the tracking error.
By (Guasoni and Mayerhofer 2023, Theorem 3.1), for sufficiently small , the problem
over all admissible strategies , is well posed. There exists such that the trading strategy that buys at and sells at to keep the risky weight within the interval is optimal. Furthermore, the minimum equivalent expense ratio is
and the optimal tracking difference and tracking error are
The trading boundaries have the series expansion
In this section, we put forward an approximation method that allows us to obtain the above trading boundaries and performance measures, at high precision. First, we study the shadow market approach; second, we consider the associated HJB equations.
3.2.2. The Shadow Market
We assume that a shadow price is a continuous semimartingale with absolutely continuous differential characteristics, that is,
In the shadow market, the cumulative tracking difference is of the form
which results in the shadow equivalent expense ratio
This objective is optimized by trading so that, at all times, the fraction of wealth in equals the Merton fraction
Assume a shadow price of the form , where the function g is assumed to be twice differentiable, satisfying , , and the smooth pasting condition . This implies that
and
The proportion of wealth in the shadow asset is
By equating (40) with (37), using (38) and (39), we obtain the following free boundary problem for g,
subject to (2) and (3).
In view of Formula (36) and the results in Mayerhofer (2024), we conjecture that the trading boundaries agree for small transaction costs with (59) at the first order; furthermore, we anticipate a minor discrepancy in the second-order terms. Therefore, we conjecture that the free boundaries are of the form
with unknown constant and multiplier . Furthermore, being deprived of an explicit solution to the ODE (41), we derive an Ansatz for a polynomial approximation
where the choice acknowledges that the expansions of the trading boundaries (42) are formal power series in .
Next, we outline how to identify the unknown constants in (42) and (43). By construction, and at the third order. To satisfy at the second order, we must set
and
and to have up to the second order, we need to insist on . Next, if g satisfies the ODE (41) at , we obtain the coefficients (lengthy expressions in terms of , , ) and they satisfy
If we insist on at the third order, we obtain as a function of , , and . At the moment, the ODE is satisfied at the second order only at . We finally insist that the ODE is asymptotically satisfied at any z in the interval, which can be represented as a convex combination of the free boundaries
In the interior of the interval, g satisfies the ODE at the second order only if
Furthermore, to have the ODE satisfied at the third order, we obtain
and
and, similarly, if g satisfies the ODE (41) at , we obtain . These computations are summarized in the following result.
3.2.3. The Original Market
Due to (Guasoni and Mayerhofer 2023, Theorem 3.1), for a small enough bid–ask spread , there exist some trading boundaries such that the policy that buys minimally at and sells minimally at so as to maintain the fraction of wealth between and is optimal.
The trading boundaries are obtained in terms of the risky–safe ratio . These are of the form , where are part of the solution to the free boundary problem for the triple (W, ), with a scalar function W satisfying
which has a unique solution for which . To allow the adoption of the method of Section 3.2.2, we use the transformation
which translates (45) and (46) into the following problem for (, )
subject to (2) and (3).
We use again the general Ansatz for g in (43) and the Ansatz (42) for the trading boundaries, relabeling them as . Since the boundary conditions are the same as in Section 3.2.2, we obtain the exact same coefficients and .
Since the ODE is different, we have to compute the remaining coefficients again. If g satisfies the ODE (41) at , we have the coefficients (lengthy expressions in terms of , , , but different from the shadow market) and they satisfy also
If we insist on at the third order, we have as a function of , , and . If we finally insist on the ODE being satisfied at any z in the no-trade region, then g satisfies the ODE only if
This sign is opposite to the shadow market solution. This provides an alternative proof to Guasoni and Mayerhofer (2023) of the asymptotics of the optimal policy (36). We finally discuss the transaction costs.
Remark 3.
For the trading boundaries (36) (optimal in the original market) and (44) (optimal in a potential shadow market), we have the transaction costs
Note that this is precisely the asymptotic expansion of the negative tracking difference (35), which may be found in (Guasoni and Mayerhofer 2023, Theorem 3.1, Equation (17)).
3.2.4. Neuberger’s Log Contract
In a frictionless market with a risky asset S that is a continuous semimartingale, and cash earning zero interest (),11 a variance swap can be perfectly replicated by the combination of a static hedge in options to replicate the log contract and a dynamic hedge with an exposure in a risky position constant at all times to some . Such a strategy results in insolvency under proportional costs.
Let us again assume that the ask price is given by (4), and the proportional costs are equal to . Because investment opportunities are constant, the variance swap is trivial, with a vanishing net cashflow upon maturity T. Since
we consider instead dynamic hedging units of the log contract that pays at time .12 This is a non-trivial question in itself as it requires us to modify the frictionless strategy to remain solvent. This task can be attempted by finding a non-anticipating, finite-variation strategy that minimizes the squared hedging error
while keeping the annualized transaction costs
acceptable. With , the aversion to the hedging error, we minimize
Please note that even when the transaction costs are zero, a self-financing strategy that maintains at a constant value of may, with low probability, necessitate excessively large funds by time T to cover the rebalancing costs, rendering the strategy potentially insolvent. This issue arises because the fair value of a log contract is given by
thus being a Brownian motion with drift. This challenge is addressed by entering in futures positions on the underlying S rather than trading S itself and linking the futures position to the shorted log contract, which is also futures traded with as the settlement price. This results in changes in the futures positions being immediately offset by the log contract, providing a perfect hedge (cf. Neuberger 1994, p. 78). In the following, we only implicitly adopt these mechanics, by ignoring the solvency issue.
For tractability reasons, we resort to an infinite time horizon, and thus minimize
over all admissible strategies. For time horizons such as five years, and daily hedging, the strategies typically approximate well those for the finite horizon objective (48). (cf. the robustness checks in (Guasoni and Mayerhofer 2023, Section 6.2 and Figure 6)). For shorter maturities, such as those aligning with the expiry of European calls or inputs, the slight adjustment of the analysis may be necessary. This adjustment yields time-dependent strategies instead of the steady-state solutions discussed earlier. The rigorous treatment of the finite time horizon remains a subject for future research.
We introduce now the hedging exercise. Knowing the perfect target, we conjecture that it is optimal to not engage in trading, as long as ranges in , where , and to trade minimally at the boundaries , so as to keep the risky position Y inside the interval. In other words, Y is a stationary process, realized by the reflected diffusion
with being supported on , and being supported on . In a similar manner as in Lemma 2, we obtain the following.
Lemma 5.
For , there exists an admissible trading strategy such that the risky position satisfies SDE (48). Moreover, is a reflected diffusion on the interval . In particular, has a stationary density that equals
Next, we give a heuristic derivation of the HJB equations, which will allow us to identify an optimal strategy. While the heuristics provided here to derive the free boundary problem follow the arguments of Guasoni and Mayerhofer (2019) for local mean variance, the resulting equations are different.
For finite horizon T, we have the objective
Assuming that the value function V depends on and time t only, the objective’s conditional value is
Applying the Itô formula, we have
and thus satisfies the dynamics
The martingale principle of optimal control implies that the process is a supermartingale for any strategy but a martingale for the optimal one. Thus,
Similarly, it follows that
In order to obtain a steady-state solution, we assume that for a constant , which represents the average long-run performance. With this assumption, the previous inequalities become
We conjecture now, similarly as in Guasoni and Mayerhofer (2019), that the first is an inequality on some interval , which becomes an equality at the boundary of the interval, and thus
This problem is a second-order ODE with two free boundaries and two unknown constants. To identify the latter, we use the smooth pasting conditions
Let . The initial conditions identify , and thus the ODE becomes
The solution of the corresponding initial value problem (which can be found by the variation of constants) is given by
Insisting on the terminal conditions, and , we obtain the following system of non-linear equations for ():
Lemma 6.
Proof.
We set . We derive the following Ansatz for the asymptotic expansions of the boundaries
For , the integral on the right-hand side of the equations vanishes. We develop this integral asymptotically for small . To this end, observe that
Developing this expression as a formal power series in and then integrating once yields the asymptotic expansion of the left side of the Equations (51) and (52). (Alternatively, one can integrate explicitly. The present method has the advantage of being applicable to general functions h, not only the quadratic one considered here.) Developing also the right sides shows that the first equation’s leading term is of the third order, and the second one has a second-order term. To make them vanish, we use the following system of equations,
which implies
Next, to satisfy (51) at the fourth order, we equate the fourth-order term to zero, obtaining
and, to satisfy (52) at the third order, we must have . This establishes the asymptotics (53). □
We now proceed to the asymptotic method, to provide the following.
Alternative Proof of Lemma 6.
For , the free boundary problem (49) and (50) takes the form
which is essentially of the form (1)–(3) except that g is a function of the risky position Y, instead of . We use an Ansatz similar to (43) for g but with (otherwise, the ODE cannot be satisfied at the third order in the interior of the interval), and we assume (guided by the previous two problems). Noting that the variable z is interpreted as the risky position y, rather than its proportion of wealth,
Moreover, we use the Ansatz (54) for the trading boundaries, assuming knowledge of the first-order terms.13 Thus, we only need to identify the coefficients in
By construction, and at the third order. To satisfy at the second order, we must set
Similarly, to have at the second order, we need . Next, if g satisfies the ODE (55) at , we have
and if g satisfies the ODE (55) at , we have
If we insist on at the third order, we have
Next, we insist that the ODE is satisfied at any y in the interior of the no-trade region , i.e., for any
g satisfies the ODE at the second order only if
We set , anticipating the same asymmetry in the second-order expansion, as in other problems14 Thus, in the interior of the interval, g satisfies the ODE at the third order only if and satisfy a system of four linear equations; its Jacobian is non-singular with determinant
thus leading to a unique solution. The unique solution of this system ensures that the free boundary problem is satisfied at the third order, which completes this independent proof of Lemma 6. □
3.3. Risk and Returns
3.3.1. Power Utility
Long-run power utility investors with risk aversion maximize the equivalent safe rate
over all admissible strategies . The shadow price, which yields an optimal trading policy, is of the form (Gerhold et al. 2012, Lemma B.2)
with
where w satisfies the ODE
As
g satisfies the free boundary problem
subject to (2) and (3). We are again using the Ansatz (43) for the polynomial approximation of g, and, inspired by the asymptotics in Mayerhofer (2024), derive the Ansatz for the trading boundaries
with unknown constants . By construction, and at the third order. To satisfy at the second order, we must set
and
and, to have up to the second order, we need to insist on .
Next, if g satisfies the ODE (41) at at the second order, we obtain the coefficients (lengthy expressions in terms of , , ) and they satisfy
If we insist on at the third order, we have as a function of , , and .
Note that, at the moment, the ODE is satisfied at at the second order only. We finally insist on the ODE being satisfied at any z in the interval, i.e.,
In the interior of the interval, g satisfies the ODE only if
In other words, the asymptotics of the trading boundaries lack the second-order terms and thus are of the form
Remark 4.
Thus, we have an alternative proof of (Gerhold et al. 2012, Equation (2.9) of Theorem 2.2). Note that this is different from the two strategies for the myopic investor, where both the shadow market strategy, which is suboptimal, and the optimal portfolio have non-vanishing second-order terms. In fact, the optimal strategy for the myopic investor in Guasoni and Mayerhofer (2019) satisfies , and the shadow market strategy satisfies and is suboptimal (cf. (Mayerhofer 2024, Theorem 3.3), unless .
Remark 5.
For power utility investors, the trading boundaries are of the form (56), implying that the second terms even vanish (, cf. Remark 1). The trading boundaries for local mean variance investors are similar, with . Moreover, for the associated asymptotic shadow, we have the same coefficients of the second order, albeit of different sign, cf. Mayerhofer (2024). Therefore, for these three strategies, the average trading costs agree for a small bid–ask spread ε up to the third order and are of the form
3.3.2. Logarithmic Utility
A long-run log-utility investor maximizes the logarithmic utility of terminal wealth for an infinite time horizon,
over all admissible strategies . For , an optimal strategy is derived in Taksar et al. (1988), with the asymptotics established in Gerhold et al. (2012), and independently by Guasoni and Mayerhofer (2019) (the latter discusses, more generally, a local mean variance objective for any risk aversion , which agrees with log-utility for and includes leverage, in particular ). In the parameterization of Mayerhofer (2024), the shadow price put forward by Gerhold et al. (2012) is
where solve
subject to (2) and (3). Note that this equation can also be obtained from the value function—more precisely, (Guasoni and Mayerhofer 2019, Theorem 3.1, Equations (3.1)–(3.5)) with the transformation (47).
Using the Ansatz (43) for a polynomial approximation of g, and the Ansatz for the trading boundaries
with unknown constants . Now, the same computations as in Section 3.3.1 deliver and all constants in the approximation (43) of g (they are as in Section 3.3.1, with the exception that one needs to set the specific value .)
3.3.3. Risk Neutrality
By Guasoni and Mayerhofer (2019), maximizing the long-run returns, ignorant to risk,
over all admissible strategies , is well posed, because the transaction costs take the role of a penalty, which, typically, the variance of returns does.
Despite the trading costs, for small bid–ask spreads , excessive leverage, around , can be obtained. Due to (Guasoni and Mayerhofer 2023, Theorem 3.2), for a small enough bid–ask spread , there exist some such that the policy that minimally buys at and minimally sells at to keep the fraction of wealth invested in the risky asset between and is optimal. The long-run expected return of this policy is given by
and the trading boundaries have the series expansions
with being the unique zero of
in the unit interval.
It is important to note that the trading boundaries specified in Equation (59) exhibit singularity in their expansion, with the leading term experiencing explosive growth. Due to this characteristic, these boundaries do not align with the approach that we have employed for other optimization problems. Additionally, according to (Mayerhofer 2024, Theorem 3.10), there is no shadow price for this particular problem, not even an asymptotically optimal one, as opposed to the situation with positive risk aversion, where a shadow price exists, being optimal up to the third order (Mayerhofer 2024, Theorems 3.1 and 3.3).
Let and with be the unique solution (according to (Guasoni and Mayerhofer 2019, Theorem 3.2) of the free boundary problem
We regularize the problem with the transformation
to obtain the following free boundary problem for the scalar function and boundaries
Note that, by the chain rule,
which implies (64). We now obtain the Ansatz for an approximation of the solution of (60),
We have the following.
Proof.
We expand (60) formally in powers of (only those up to the second order appear as coefficients), giving the equation associated with ,
the linear term associated with
and the constant term
The last one gives the general solution , and Equation (67) gives . Finally, Equation (66) gives
□
Assume that
then
and thus
We first ensure that the zero-order term satisfies, by default, the left boundary conditions (61) and (62). This implies that
For condition (62) to be satisfied at the first order, we have . However, then, to ensure that (61) is satisfied at the first order, we need . We further set to satisfy the same conditions at the second order. We thus have
Next, to have (63) and (64) satisfied at zero order, must satisfy the system of equations
Note that these equations recover the ones in (Guasoni and Mayerhofer 2019, D.5). By (Guasoni and Mayerhofer 2019, Lemma D.1.), the unique solution of the system (69) is
where is the unique solution of (69).
To have (63) and (64) satisfied at the first order, we equate the respective coefficients to zero,
which yields the constants15
We must ultimately verify that the approximation of the value function and trading strategy has been carried out to a satisfactory order. To achieve this, we begin by determining the order of the average transaction costs. Since the trading boundaries experience explosive behavior as the bid–ask spread approaches zero, we anticipate a corresponding escalation in the transaction costs. This expectation is corroborated by the following analysis.
Lemma 8.
The risk-neutral investor faces average transaction costs
Proof.
Since, by (58) and (59), the equivalent safe rate adheres to the asymptotics
we infer that the impact of the transaction costs on welfare is of a similar order. Notably, this situation contrasts many other problems, where the size of the no-trade region is strictly of larger order than the impact of the transaction costs on welfare (as discussed in Section 1 and referenced therein). As the coefficients only contribute to the zeroth order, as seen in (72), our approximation is deemed satisfactory. This suggests that the essential effects of the transaction costs on welfare are adequately captured by the simplified analysis.
4. Discussion
In this paper, we provide asymptotic methods for a continuous-time portfolio choice under proportional transaction costs.
The first results pertain to the trading frequency and incurred cost. While, for long-run or infinite horizon optimization problems, it is typically optimal to trade such that several portfolio statistics follow a reflected diffusion, these strategies cannot be realized in a real-world trading setup. The trading is of infinite activity and thus requires not only continuous monitoring but also the execution of trades of infinitesimal size. This inspired us to develop realistic, discrete trades. In terms of the proportion of wealth in the risky asset, if the trading boundaries satisfy
bulk trades to some target incur average transaction costs that are twice the optimal strategy’s (Proposition 4 vs. Proposition 2), rendering them strictly suboptimal. For maximal trades (Section 3.1.2 and Remark 2), where reasonable trade sizes must be of order (no larger than the size of the no-trade region), the trading frequency (TF) is of order . A moment’s reflection on Proposition 4 reveals that the annualized transaction costs are, precisely at the first order, the product of the relative bid–ask spread, trading frequency, and trade size:
The same formula can be inferred for small trades (Proposition 5), where the trading frequency is much higher (order ) but the annualized transaction costs are smaller (of the order ). This process can be iterated, yielding the scaling law (73) (cf. Golub et al. (2018) and the references therein), for trade sizes of order and associated trading frequency , where , resulting in the same order of the average trading costs, namely . This scaling law provides a complementary answer to the question in Rogers (2004) concerning the effect of the proportional transaction costs being of the second order, as the annualized transaction costs of nearly optimal strategies are precisely of this order. For , we recover the control limit policy, which is continuous. Our result is applicable to any control limit policy, irrespective of the objective in use, whereas Rogers (2004) reaches his conclusion only for the maximization of the power utility from consumption in an investment problem on an infinite horizon.
Section 3.1 offers a novel insight into the question of why the ATC may agree up to the third (!) order, despite the varying, problem-specific, second-order terms in the trading boundaries (Remark 1). If the second-order coefficients of the lower and upper trading boundaries agree, they do not contribute to the asymptotics (16) of the ATC, as only their difference (here zero) gives a non-zero contribution. A notable example is the (candidate) shadow price strategy in (44) vs. the optimal strategy (36) for leveraged ETFs: the respective no-trade regions are small shifts—in opposing directions—in a symmetric region with boundaries
Note that the latter trading boundaries do not correspond to any optimization problem mentioned here or in the literature (they lack second-order terms). However, in the analogous situation for local mean variance criteria Mayerhofer (2024), a symmetric no-trade region around the Merton fraction identifies the optimal strategy for a power utility investor Gerhold et al. (2014) (see Remark 5). In this case, three different problems, whose trading policies disagree at the second order, enjoy the same equivalent safe rate up to the third order.
In Section 3.2 and Section 3.3, we introduce a novel approximation approach addressing free boundary problems. Employing a universal polynomial Ansatz for the value function enables the resolution of the free boundary problems associated with the power utility of terminal wealth, leveraged ETF objectives, and the computation of a solvent hedge for the log contract. Remarkably, our solutions exhibit precision up to the third order, with the trading boundaries’ precision reaching the second order. This high level of precision becomes particularly relevant given that the transaction costs’ primary contribution to the objective is of the second order. These costs are solely influenced by the first-order coefficients of the trading boundaries. Consequently, the polynomial method excels in providing precision beyond what is strictly necessary.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study (Only imulations are used to produce the plots).
Conflicts of Interest
The author declares no conflicts of interest.
Notes
| 1 | Norbert Wiener about the Manhattan project, in “I am a mathematician”, MIT Press 1964. |
| 2 | For the log contract, we use another parameterization. |
| 3 | Discrete trades occur in the context of fixed transaction costs Altarovici et al. (2015), where only a fixed number of trades maintains solvency. Finite trading speed—that is, the absolute continuity of the number of shares of the risky asset—occurs in market impact models, cf. Guasoni and Weber (2020) and the references therein. See also Bruhn et al. (2016). |
| 4 | In fact, for the log-utility, the same penalty also appears: we rewrite the finite-horizon version of objective (57), using Itô’s formula. |
| 5 | For cosmetic reasons, which shall be clear later, we subtract the second-order term from each boundary. However, since may be any real number, our choice does not lead to a loss of generality. |
| 6 | In fact, is the unique strong solution to (18). |
| 7 | This results holds for all essentially bounded, Borel-measurable functions. |
| 8 | The majority of the computations were performed by Wolfram Mathematica, using (32). |
| 9 | Moreover, this assumption yields explicit formulas. Risk premia, stochastic interest rates, and stochastic volatility are included in the more general theory of the performance evaluation of LIETFs in Guasoni and Mayerhofer (2023). |
| 10 | |
| 11 | A small modification for a non-zero interest rate applies. |
| 12 | In practice, this should be done by trading futures on S, tied to the log contract, cf. Neuberger (1994). |
| 13 | The approximation can be performed without knowing the coefficients . Moreover, one can obtain higher-order coefficients with this method. |
| 14 | See the situation for leveraged ETFs in the previous section, or the local mean variance criteria Mayerhofer (2024). |
| 15 | The paper Guasoni and Mayerhofer (2019) states that , which is a typing error, having no implications for their paper. |
References
- Altarovici, Albert, Johannes Muhle-Karbe, and Halil Mete Soner. 2015. Asymptotics for fixed transaction costs. Finance and Stochastics 19: 363–414. [Google Scholar] [CrossRef]
- Borodin, Andrei N., and Paavo Salminen. 2002. Handbook of Brownian Motion: Facts and Formulae. Berlin/Heidelberg: Springer. [Google Scholar]
- Bruhn, Kenneth, Ninna Reitzel Jensen, and Mogens Steffensen. 2016. Smooth investment. Annals of Finance 12: 335–61. [Google Scholar] [CrossRef]
- Constantinides, George M. 1986. Capital market equilibrium with transaction costs. Journal of Political Economy 94: 842–62. [Google Scholar] [CrossRef]
- Gerhold, Stefan, Johannes Muhle-Karbe, and Walter Schachermayer. 2012. Asymptotics and duality for the Davis and Norman problem. Stochastics An International Journal of Probability and Stochastic Processes 84: 625–41. [Google Scholar] [CrossRef]
- Gerhold, Stefan, Johannes Muhle-Karbe, and Walter Schachermayer. 2013. The dual optimizer for the growth-optimal portfolio under transaction costs. Finance and Stochastics 17: 325–54. [Google Scholar] [CrossRef][Green Version]
- Gerhold, Stefan, Stefan Guasoni, Johannes Muhle-Karbe, and Walter Schachermayer. 2014. Transaction costs, trading volume, and the liquidity premium. Finance and Stochastics 18: 1–37. [Google Scholar] [CrossRef]
- Golub, Anton, James B. Glattfelder, and Richard B. Olsen. 2018. The alpha engine: Designing an automated trading algorithm. In tHigh-Performance Computing in Finance. Boca Raton: Chapman and Hall/CRC, pp. 49–76. [Google Scholar]
- Guasoni, Paolo, and Eberhard Mayerhofer. 2019. The limits of leverage. Mathematical Finance 29: 249–84. [Google Scholar] [CrossRef]
- Guasoni, Paolo, and Eberhard Mayerhofer. 2023. Leveraged funds: Robust replication and performance evaluation. Quantitative Finance 23: 1155–76. [Google Scholar] [CrossRef]
- Guasoni, Paolo, and Johannes Muhle-Karbe. 2013. Portfolio choice with transaction costs: A user’s guide. In Paris-Princeton Lectures on Mathematical Finance. Edited by Vicky Henderson and Ronnie Sircar. Cham: Springer, pp. 169–201. [Google Scholar]
- Guasoni, Paolo, and Marko Hans Weber. 2020. Nonlinear price impact and portfolio choice. Mathematical Finance 30: 341–76. [Google Scholar] [CrossRef]
- Gut, Allan. 2009. Stopped Random Walks. Limit Theorems and Applications. Springer Series in Operations Research and Financial Engineering; New York: Springer. [Google Scholar]
- Kallsen, Jan, and Johannes Muhle-Karbe. 2017. The general structure of optimal investment and consumption with small transaction costs. Mathematical Finance 27: 695–703. [Google Scholar] [CrossRef]
- Mayerhofer, Eberhard. 2024. Almost perfect shadow prices. Journal of Risk and Financial Management 17: 70. [Google Scholar] [CrossRef]
- Neuberger, Anthony. 1994. The log contract. Journal of Portfolio Management 20: 74–80. [Google Scholar] [CrossRef]
- Rogers, L. C. G. 2004. Why is the effect of proportional transaction costs δ2/3? Mathematics of Finance 351: 303–8. [Google Scholar]
- Shreve, S. E., and H. M. Soner. 1994. Optimal investment and consumption with transaction costs. The Annals of Applied Probability 4: 609–92. [Google Scholar] [CrossRef]
- Taksar, Michael, Michael J. Klass, and David Assaf. 1988. A diffusion model for optimal portfolio selection in the presence of brokerage fees. Mathematics of Operations Research 13: 277–94. [Google Scholar] [CrossRef]
- Tanaka, Hiroshi. 1979. Stochastic differential equations with reflecting boundary condition in convex regions. Hiroshima Mathematical Journal 9: 163–77. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).