Asymptotic Methods for Transaction Costs
Abstract
1. Introduction
It was explained to me that the effects on which one was working were so vanishingly small that without the greatest possible precision in computation they might have been missed altogether.Norbert Wiener1
Program of Paper
2. Materials and Methods
- (i)
- and are right-continuous, increasing, and non-anticipating processes;
- (ii)
3. Results
3.1. Transaction Cost Asymptotics
- (i)
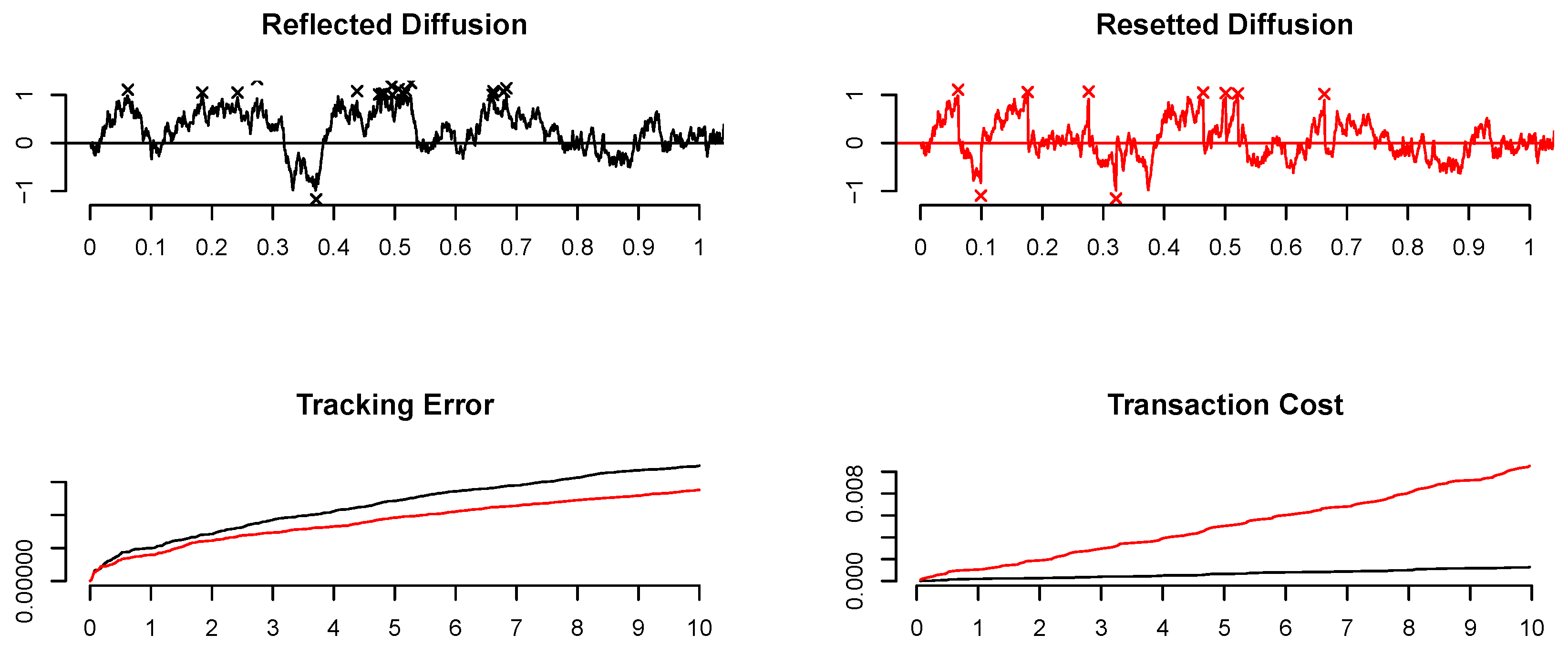
- Minimal trades: These strategies operate continuously, engaging in minimal trading at the boundaries of specific no-trade regions (cf. the first plot of Figure 1 (black lines)).
- (ii)
- Maximal trades: These strategies reset a portfolio statistic to its target value once it reaches these boundaries (cf. the first second plot in Figure 1 (red lines)).
- (iii)
- Small trades: These involve smaller trades than (ii) made in the direction of the target value.
3.1.1. Minimal Trades
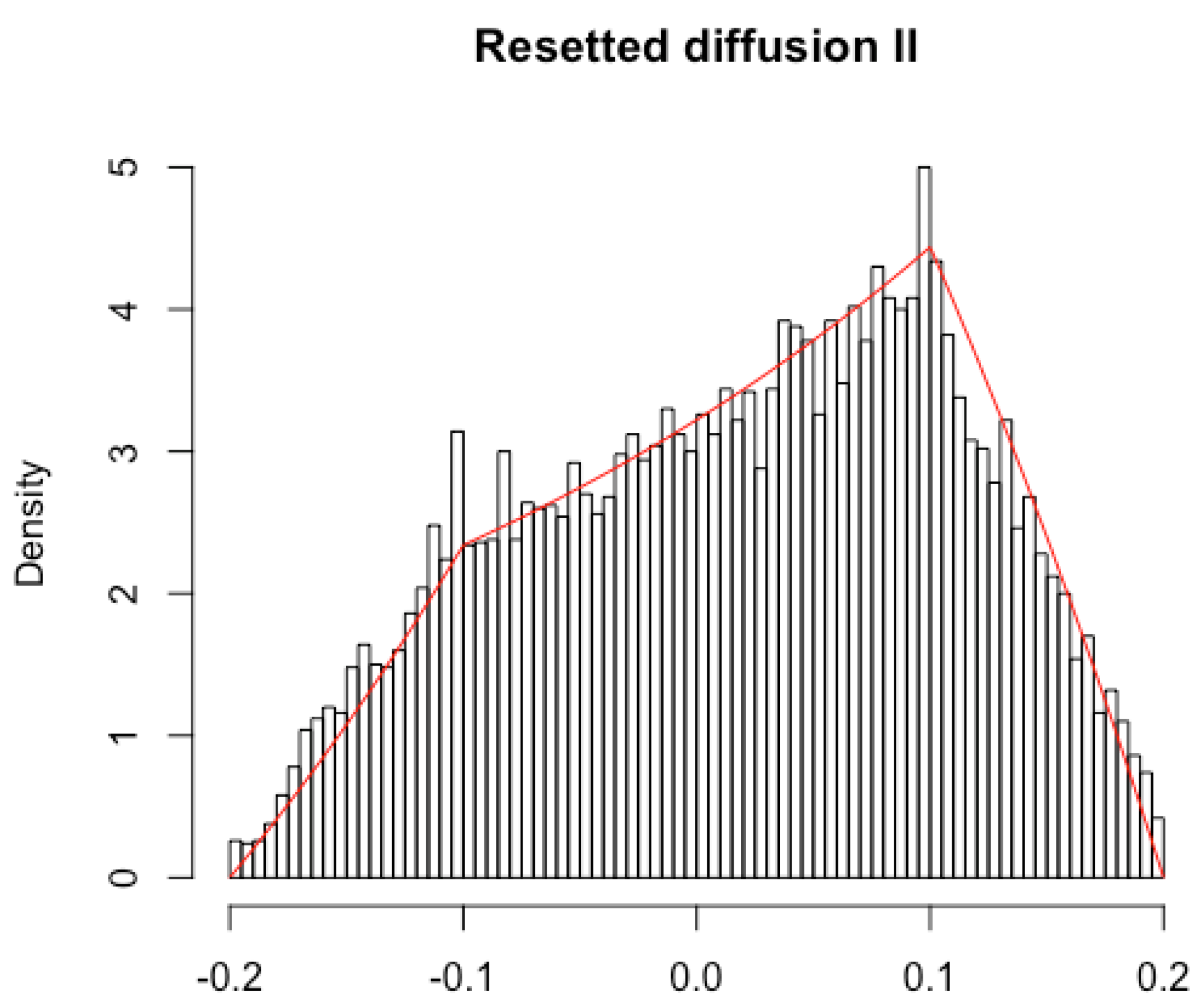
3.1.2. Maximal Trades
- (i)
- (Selling Frequency) The long-run selling frequency per unit time satisfies the asymptotics
- (ii)
- (Average Cost) The average transaction costs satisfy the asymptoticsand thus, at leading order, are twice the cost of the control limit policy (that is, Equation (16) of Proposition 2).
3.1.3. Small Trades
- (i)
- (Selling Frequency) The long-run selling frequency per unit time satisfies the asymptotics
- (ii)
- (Average Cost) The average transaction costs satisfy the asymptoticsand thus agree, at leading order, with the cost of the control limit policy (that is, Equation (16) of Proposition 2).
3.2. Tracking Frictionless Targets
3.2.1. Levered Funds
3.2.2. The Shadow Market
3.2.3. The Original Market
3.2.4. Neuberger’s Log Contract
3.3. Risk and Returns
3.3.1. Power Utility
3.3.2. Logarithmic Utility
3.3.3. Risk Neutrality
4. Discussion
Funding
Data Availability Statement
Conflicts of Interest
| 1 | Norbert Wiener about the Manhattan project, in “I am a mathematician”, MIT Press 1964. |
| 2 | For the log contract, we use another parameterization. |
| 3 | Discrete trades occur in the context of fixed transaction costs Altarovici et al. (2015), where only a fixed number of trades maintains solvency. Finite trading speed—that is, the absolute continuity of the number of shares of the risky asset—occurs in market impact models, cf. Guasoni and Weber (2020) and the references therein. See also Bruhn et al. (2016). |
| 4 | In fact, for the log-utility, the same penalty also appears: we rewrite the finite-horizon version of objective (57), using Itô’s formula. |
| 5 | For cosmetic reasons, which shall be clear later, we subtract the second-order term from each boundary. However, since may be any real number, our choice does not lead to a loss of generality. |
| 6 | In fact, is the unique strong solution to (18). |
| 7 | This results holds for all essentially bounded, Borel-measurable functions. |
| 8 | The majority of the computations were performed by Wolfram Mathematica, using (32). |
| 9 | Moreover, this assumption yields explicit formulas. Risk premia, stochastic interest rates, and stochastic volatility are included in the more general theory of the performance evaluation of LIETFs in Guasoni and Mayerhofer (2023). |
| 10 | |
| 11 | A small modification for a non-zero interest rate applies. |
| 12 | |
| 13 | The approximation can be performed without knowing the coefficients . Moreover, one can obtain higher-order coefficients with this method. |
| 14 | See the situation for leveraged ETFs in the previous section, or the local mean variance criteria Mayerhofer (2024). |
| 15 | The paper Guasoni and Mayerhofer (2019) states that , which is a typing error, having no implications for their paper. |
References
- Altarovici, Albert, Johannes Muhle-Karbe, and Halil Mete Soner. 2015. Asymptotics for fixed transaction costs. Finance and Stochastics 19: 363–414. [Google Scholar] [CrossRef]
- Borodin, Andrei N., and Paavo Salminen. 2002. Handbook of Brownian Motion: Facts and Formulae. Berlin/Heidelberg: Springer. [Google Scholar]
- Bruhn, Kenneth, Ninna Reitzel Jensen, and Mogens Steffensen. 2016. Smooth investment. Annals of Finance 12: 335–61. [Google Scholar] [CrossRef]
- Constantinides, George M. 1986. Capital market equilibrium with transaction costs. Journal of Political Economy 94: 842–62. [Google Scholar] [CrossRef]
- Gerhold, Stefan, Johannes Muhle-Karbe, and Walter Schachermayer. 2012. Asymptotics and duality for the Davis and Norman problem. Stochastics An International Journal of Probability and Stochastic Processes 84: 625–41. [Google Scholar] [CrossRef]
- Gerhold, Stefan, Johannes Muhle-Karbe, and Walter Schachermayer. 2013. The dual optimizer for the growth-optimal portfolio under transaction costs. Finance and Stochastics 17: 325–54. [Google Scholar] [CrossRef][Green Version]
- Gerhold, Stefan, Stefan Guasoni, Johannes Muhle-Karbe, and Walter Schachermayer. 2014. Transaction costs, trading volume, and the liquidity premium. Finance and Stochastics 18: 1–37. [Google Scholar] [CrossRef]
- Golub, Anton, James B. Glattfelder, and Richard B. Olsen. 2018. The alpha engine: Designing an automated trading algorithm. In tHigh-Performance Computing in Finance. Boca Raton: Chapman and Hall/CRC, pp. 49–76. [Google Scholar]
- Guasoni, Paolo, and Eberhard Mayerhofer. 2019. The limits of leverage. Mathematical Finance 29: 249–84. [Google Scholar] [CrossRef]
- Guasoni, Paolo, and Eberhard Mayerhofer. 2023. Leveraged funds: Robust replication and performance evaluation. Quantitative Finance 23: 1155–76. [Google Scholar] [CrossRef]
- Guasoni, Paolo, and Johannes Muhle-Karbe. 2013. Portfolio choice with transaction costs: A user’s guide. In Paris-Princeton Lectures on Mathematical Finance. Edited by Vicky Henderson and Ronnie Sircar. Cham: Springer, pp. 169–201. [Google Scholar]
- Guasoni, Paolo, and Marko Hans Weber. 2020. Nonlinear price impact and portfolio choice. Mathematical Finance 30: 341–76. [Google Scholar] [CrossRef]
- Gut, Allan. 2009. Stopped Random Walks. Limit Theorems and Applications. Springer Series in Operations Research and Financial Engineering; New York: Springer. [Google Scholar]
- Kallsen, Jan, and Johannes Muhle-Karbe. 2017. The general structure of optimal investment and consumption with small transaction costs. Mathematical Finance 27: 695–703. [Google Scholar] [CrossRef]
- Mayerhofer, Eberhard. 2024. Almost perfect shadow prices. Journal of Risk and Financial Management 17: 70. [Google Scholar] [CrossRef]
- Neuberger, Anthony. 1994. The log contract. Journal of Portfolio Management 20: 74–80. [Google Scholar] [CrossRef]
- Rogers, L. C. G. 2004. Why is the effect of proportional transaction costs δ2/3? Mathematics of Finance 351: 303–8. [Google Scholar]
- Shreve, S. E., and H. M. Soner. 1994. Optimal investment and consumption with transaction costs. The Annals of Applied Probability 4: 609–92. [Google Scholar] [CrossRef]
- Taksar, Michael, Michael J. Klass, and David Assaf. 1988. A diffusion model for optimal portfolio selection in the presence of brokerage fees. Mathematics of Operations Research 13: 277–94. [Google Scholar] [CrossRef]
- Tanaka, Hiroshi. 1979. Stochastic differential equations with reflecting boundary condition in convex regions. Hiroshima Mathematical Journal 9: 163–77. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mayerhofer, E. Asymptotic Methods for Transaction Costs. Risks 2024, 12, 64. https://doi.org/10.3390/risks12040064
Mayerhofer E. Asymptotic Methods for Transaction Costs. Risks. 2024; 12(4):64. https://doi.org/10.3390/risks12040064
Chicago/Turabian StyleMayerhofer, Eberhard. 2024. "Asymptotic Methods for Transaction Costs" Risks 12, no. 4: 64. https://doi.org/10.3390/risks12040064
APA StyleMayerhofer, E. (2024). Asymptotic Methods for Transaction Costs. Risks, 12(4), 64. https://doi.org/10.3390/risks12040064





