Abstract
Secret image sharing technology is a strategy for jointly protecting secret images. The (n, n) secret image sharing problem can be solved by conventional Boolean calculation easily. However, how to recover secret images with progressive steps is not addressed. In this study, we proposed an XOR-based (m, t, Ti) multi-secret image sharing scheme that shares m secret images among m participants and recovers m shared images progressively with t thresholds. The proposed secret images partition strategy (SIPS) partitions m secret images to generate intermediate images for different thresholds in the sharing procedure. Based on progressive recovery property, the proposed recovery method recovers parts of the secret images by gathering consecutive shared images. Moreover, gathering all shared images can perfectly recover all secret images. The experimental results show that the proposed XOR-based multi-secret image sharing method has high security and efficiency.
1. Introduction
With the development of digital multimedia and the Internet, the sharing of multimedia content through the Internet has become more popular, and intellectual property rights and personal privacy have also become increasingly important. The secret image sharing technique is one of the protection methods that aim to protect multimedia content and has become an important field of recent research [1].
Thien and Lin [2] first proposed a secret image sharing scheme based on the Shamir-Lagrange method [3,4], and then a number of functional secret image sharing schemes have been proposed, such as sharing a secret image among host images [5,6], sharing using Boolean operations [7,8], progressive sharing [9,10,11], visual cryptography with secret image sharing [12], and scalable sharing [13]. Since most of the approaches perform only for sharing one secret image, they cannot share multiple secret images simultaneously in real circumstances.
Over the past few years, a number of approaches for multi-secret image sharing have been proposed. Chen and Chien [14] proposed sharing numerous images secretly with the reduced possessing load. The concept of the method is to generate a random number image with the same size as the secret image, and the random number image and the secret image are processed separately, and then the calculation is made public. Then use secret image sharing technology to share images containing random noise with all participants. Chen and Wu [15] proposed an efficient multi-secret image sharing method that used n − 1 secret images to generate n shared images based on Boolean operations. However, it is necessary to collect all the shared images to recover the secret images. Chen and Wu [16] improved the multi-secret image sharing method proposed in Chen and Wu [15] and proposed a random number image generation function, which used secret images or shared images to perform XOR operations and bit-shifting operations to obtain the random image. Since the random image does not need to be shared as shared images, the sharing capacity is increased. Chen et al. [17] proposed a method that also used the random number image generation function to generate images containing random noise but will perform further bit shift processing on the generated random images. Kabirirad and Eslami [18] proposed a multi secret image sharing scheme based on Boolean operations. Although their approach is efficient, it requires that the size of the generated shared image must be the same as the secret image. Azza and Lian [19] present a cellular automaton-based multi-secret image sharing scheme with steganography. Chen and Wu [20] proposed a Boolean-based multi-secret sharing scheme with the general access structure. The proposed scheme does not necessarily collect all the shared images to recover the secret images by the predefined access structure. In addition, since image secret sharing schemes are widely used in watermarking, access control, identity authentication and so on, a number of image secret sharing schemes were proposed and applied in various practical applications, such as biometric privacy [21], share authentication [22,23], and e-voting [24]. Notice that most of the previous schemes are mainly for low computational complexity. How to process the secret images to achieve progressively secret image sharing and recovery is still not solved by them [25,26,27,28,29,30,31].
This paper proposed a secure XOR-based (m, t, Ti) multiple secret image sharing approach that shares m secret images among m participants and recovers m shared images progressively with t thresholds. The proposed method uses the random number image generation function to generate images containing random noise and further process the secret images to achieve progressively secret image sharing and recovery. The experimental results show the novel properties of our proposed approach.
2. Review of Related Literature
This section briefly reviews the state-of-art in secret sharing of multiple images based on Boolean function. Section 2.1 introduces the secret sharing of multiple images based on the Boolean function proposed by Chen and Wu [15]. Section 2.2 introduces the method proposed by Chen and Wu [16]. Section 2.3 introduces the method proposed by Chen et al. [17].
2.1. Boolean Based Scheme of Chen and Wu
Chen and Wu [15] proposed a method of secretly sharing and restoring n − 1 secret images through n shared images. The sharing steps are as follows:
- Select n − 1 secret images and a random number image R of the same size. The secret images are marked as Gi (i = 1, …, n − 1) in order;
- Using Equation (1), perform an XOR operation on each of n − 1 secret images and R to obtain noise images of n−1 secret images, labeled Bi (i = 1, …, n − 1);
- Use Equation (2) to generate shared images, labeled Si (i = 1, …, n);
The recovery steps are as follows:
- Collect all n shared images, and perform XOR operation S1 ⊕ S2 ⊕ … ⊕ Sn on all shared images to restore G1. Moreover, restore the random number image R through S1 ⊕ G1;
- Use Equation (3) to recover n − 1 noise images;
- Using Equation (4), use n − 1 noise images and images containing random noise R to restore all secret images.
The above is the introduction of the Chen and Wu [15] method. If the number of shared secret images divided by the number of shared images is defined as the sharing rate, the sharing rate is n − 1/n. However, a shared image Si is calculated by Equation (5), and it is quite insufficient in security, as shown in Figure 1.
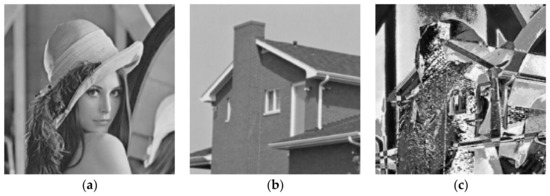
Figure 1.
The results of XOR operation: (a) Lena, (b) house, (c) XOR result of (a,b).
2.2. The Improved Scheme of Chen and Wu
Chen and Wu [16] improved their work [15] by using the proposed random number image generation function F to generate a random number image R. F contains two sub-functions F1 and F2. The function is defined as F(x)= F2 (F1(x)), where F1 is calculated by Equation (6), performs XOR operation on all images, F2 then marks the image after F1 operation as . For each pixel value, it is converted into a binary bit, and the bit is transposed, and the processed result is marked as and expressed by Equation (7).
where x, y represent the pixel position in the image, and b (0 ≤ b ≤ 7) represents the pixel bit converted to binary. The sharing steps are introduced as follows:
- Select n secret images and mark them as G1, G2, …, Gn in sequence;
- Using Equation (8), the random number image generation function obtains the random number image R;
- Using Equation (9), n secret images and images containing random noise R are used to generate n noise images, which are labeled Ni (i = 1, 2, …, n);
- Using Equation (10), generate n shared images and share them with all participants, labeled Si (i = 1, …, n).
The recovery procedure is described as follows:
- Using Equation (11), from the shared images S1, S2, S3, …, Sn, restore all the noise images N1, N2, …, Nn in sequence;
- Using Equation (12), the generated when sharing is obtained from the noise image. Then use Equation (7) to substitute into the sub-function F2 of the random number, the image generating function, and the random number image R generated during sharing can be recovered;
- According to Equation (13), the noise image and random number image R are recovered to the corresponding secret image.
2.3. Scheme of Chen et al.
The sharing steps of the secret image sharing scheme proposed by Chen et al. are introduced as follows:
- Prepare n secret images and mark them as Ii (i = 0, …, n − 1) in sequence;
- After performing the XOR operation on all the secret images I, the Hash method is performed on the result to generate the matrix h;
- The matrix h is reorganized to generate the image SI;
- Performing XOR operation on all secret images I0–In−1 and then bit shifting to generate the image and then performing XOR operation with the SI to generate random image R;
- Using Equation (17), n random images R0–Rn−1 are generated by n secret images performing bit shifting, where x, y represents the pixel positions in the image;
- After all the secret images I0–In−1 and images containing random noise R0–Rn−1 are calculated according to Equation (18), n shared images Oi (i = 0,…, n − 1) can be obtained.
The recovery procedure is described as follows:
- Collect all n shared images, and perform XOR operation on all shared images . In this way, the result of is obtained;
- Obtain h by Equation (14), and then obtain SI by Equation (15);
- After obtaining the noise image R by Equation (16), then obtain the noise image by Equation (17);
- Then, by Equation (19), n noise images R0, …, Rn−1 are used to restore all the secret images.
Based on Chen et al.’s proposed algorithm [17], the sharing rate of this method is n/n.
3. The Proposed Approach
This section introduces our proposed XOR-based (m, t, Ti) multi-secret image sharing scheme, in which m secret images are shared among m participants with t different thresholds T0 to Tt−1 satisfying T0 < … < Tt−1. Moreover, the highest threshold Tt−1 should be equal to m.
Section 3.1 introduces the proposed secret image segmentation strategy (SIPS) method to partition m secret images into t groups of intermediate images for t thresholds. Section 3.2 introduces the proposed sharing algorithm, and Section 3.3 introduces the recovery algorithm. Examples of sharing and recovery with thresholds (4, 3, {2, 3, 4}) are demonstrated in Section 3.4.
3.1. Secret Images Partition Strategy (SIPS)
Since the proposed scheme obtains the progressive recovery property, the following partition method is, therefore, presented to generate intermediate images for different thresholds. For sharing m secret images with the property of t thresholds, the first step in SIPS partitions the lowest 4 bit-planes (LSB0–3) of m secret images, which denoted by PSt−1 as group partition and the remaining highest 4 bit-planes (LSB4–7) are partitioning to PS0–PSt−2 by bit sequence. Since any modification under LSB2 is hard to be noticed by human eyes, therefore, lowest and highest 4 bit-planes are determined. Figure 2 shows two examples of sharing a 5 pixels block to PSi (0 ≤ i ≤ t − 1) two different thresholds of (a) t = 3 and (b) t = 4 by the proposed SIPS.
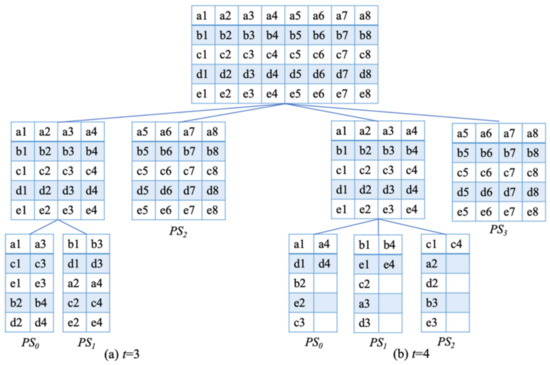
Figure 2.
Example of sharing 5 pixels by the proposed secret image partition strategy (SIPS), (a) shares to 3 groups of PS0, PS1, PS2, (b) shares to 4 groups of PS0, PS1, PS2, PS3.
Figure 3 shows the results of only part PSi being recovered by filling the un-recovered PSi by random or 0/1 bits under threshold t = 3. Figure 3a shows the original Barbara image, and Figure 3b–d shows the recovery by PS0 with compensating by 0/1 and random bit, respectively. Moreover, Figure 3e–g shows the recovery by {PS0, PS1} with compensating by 0/1 and random bit, respectively. Figure 3 shows that compensating by 0 leads to a darker recovery. On the contrary, compensating by 1 acquires a brighter recovery. However, since the compensation by 0/1 mainly changes the brightness of the recovery result, the proposed strategy adopting the compensation by random bits, as shown in Figure 3d,g.

Figure 3.
Results of an image by part of group partitions under threshold t = 3, (a) the original image: Barbara, (b–d) recovery by PS0 with compensating by 0/1 and random bit, respectively, (e–g) recovery by {PS0, PS1} with compensating by 0/1 and random bit, respectively.
Since each secret image has its group partitions PSi(0 ≤ i ≤ t − 1), sharing m secret images acquires m multiples of their PSi. The second step in SPIS is to generate intermediate images from PSi. The lowest 4 bit-planes (LSB0–3) of PSt−1 construct the intermediate images Pt−1,j (0 ≤ j ≤ Tt−1) for group t − 1. The 4 bits higher planes (LSB4–7) of PS0–PSt−2 are shared to t − 1 groups, as shown in Figure 2, and the size of these intermediate images will reduce to of the original image size. Each PSi(0 ≤ i < t − 1) is then reorganized to intermediate images Pi,k (0 ≤ k ≤ Ti−1) for further sharing processing.
By applying the proposed SIPS and the predefined (m, t, Ti) thresholds, secret images with size M × N obtains the following intermediate images.
- 4 lowest bit-planes (LSB0–3) of m secret images (4mMN bits) are reconstructed to m intermediate images with the size of pixels for threshold Tt−1 (=m);
- Total bits from m secret images in highest bit-planes (LSB4–7) are re-shaped to Ti (0 ≤ i < t − 1) intermediate images for different Ti thresholds, respectively. Therefore, sizes of intermediate images are ;
- Finally, the size of the shared image is
Table 1 shows the sizes of shared images in the proposed SIPS with different thresholds under the size of secret images being 300 × 300.

Table 1.
Sizes of shared images in the proposed secret image partition strategy (SIPS).
3.2. The Proposed Sharing Algorithm
The sharing algorithm of the proposed XOR-based (m, t, Ti) multiple secret image sharing scheme shares m secret images among m participants with the progressive property of t different thresholds Ti (0 ≤ i ≤ t − 1) and m = Tt−1. These t thresholds must fit the requirement of . Figure 4 shows the proposed sharing structure. The intermediate images Pj,k (0 ≤ j ≤ t − 1, 0 ≤ k < Tj) are acquired from the proposed SIPS introduced in Section 3.1. The following steps adopt Chen et al.’s method [17] with consecutive modification on thresholds Ti, 0 ≤ i < t − 1. This modification also means that in the Pt−1,k intermediate images, the threshold is Tt−1, and Chen et al.’s method [17] is directly applied. However, other thresholds Ti (0 ≤ i < t − 1) should give some modification to Chen et al.’s method [17]. Our proposed structure obtains the property of consecutive recovery on threshold Ti (0 ≤ i < t − 1). For example, if Ti = 3 and m = 4, four shared images (denoted by S1, S2, S3, S4) are generated and collecting 3 consecutive shared images like S1, S2, S3 or S2, S3, S4 can perfectly recover secret images of the threshold Ti = 3.
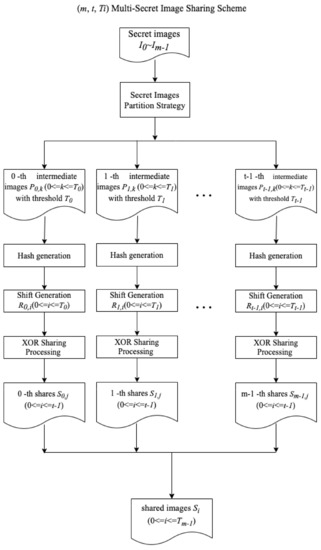
Figure 4.
The proposed sharing algorithm.
The sharing algorithm is introduced as follows:
- Using the proposed secret images partition strategy (SIPS) to generate intermediate images Pj,k (0 ≤ j ≤ t − 1, 0 ≤ k < Tj) from m secret images;
- Apply the XOR function, the SHA-256 hash function H, the image_synthesis(h) function, and the bit_reverse(x) function on these intermediate images Pj,k by Equations (20) and (21) to generate random image Rj for each threshold;where the image_synthesis(h) function synthesizes the image from the seed h, and the bit_reverse(X) function reverses each bit of all pixels in an image X;
- Generate a series of random images from circular pixel shift processing on Rj as defined in Equation (22);
- Generate a series of intermediate shares Si,j by Equation (23);
- Concatenate all the intermediate shares Si,j to acquire shared image Si for participant i by Equation (24).
3.3. The Proposed Recovery Algorithm
The recovery algorithm of the proposed XOR-based multiple secret image sharing scheme is introduced in this section. Enough shared images should be acquired for meeting the threshold criterium. In the proposed XOR-based (m, t, Ti) multiple secret image sharing scheme, the acquirement of consecutive k shared images recovers all thresholds Ti with Ti ≤ k. The recovery algorithm is introduced as follows:
- Acquire the consecutive k shared images. Without loss of generality, these shared images are denoted by ;
- Split for obtaining intermediate shares ;
- Assume the number of collected shared images k is equal to one threshold Tm . For each threshold , apply the following steps to recover the intermediate image ;
- 3.1.
- Applying to Equations (20) and (21) acquire and , respectively;
- 3.2.
- Generate a series of random images from ;
- 3.3.
- Acquire intermediate images from Equation (25)
- Apply the reverse processing of the proposed SIPS from the intermediate images to recover the bit-plane shares PSi (0 ≤ i ≤ t − 1);
- Combine all the recovered bit-plane shares PSi (0 ≤ i ≤ t − 1) and replace the un-recovered bits with random bits for recovering all secret images.
3.4. Discussion of a Sharing Example
This section shows an example of sharing four secret images I0–I3 with size 300 × 300 by the proposed (4, 3, {2, 3, 4}) XOR-based multi-secret image sharing scheme. The detailed information for each step is introduced as follows:
- Partition four secret images I0–I3 to group partition;
- 1.1.
- Four highest bit planes of size 150 × 300 are partitioned to group partitions PS0,i (0 ≤ i ≤ 3) and PS1,i (0 ≤ i ≤ 3) with size 75 × 300;
- 1.2.
- Four lowest bit planes construct the PS2,i (0 ≤ i ≤ 3) with size 150 × 300;
- Acquire the intermediate images Pi,j (0 ≤ i ≤ 3, 0 ≤ j ≤ 2) from PSi (0 ≤ i ≤ 2);
- 2.1.
- Re-shape PS0,i (0 ≤ i ≤ 3) to acquire P0,0, P0,1 with size 150 × 300 for sharing with threshold 2;
- 2.2.
- Re-shape PS1,i (0 ≤ i ≤ 3) to acquire P1,0, P1,1, P1,2 with size 100 × 300 for sharing with threshold 3;
- 2.3.
- Re-shape 4 lower bit planes PS2,i (0 ≤ i ≤ 3) to acquire Pj,2 (0 ≤ j ≤ 3) with size 150 × 300 for sharing with threshold 4;
- In first threshold 2, R0 is acquired by applying P0,0, P0,1 to Equation (20). Applying R0 and Equation (21) generates R0,0 and R0,1. Four intermediate shares with the size of 150 × 300 are acquired from the following:
- In second threshold 3, R1 is acquired by applying P1,0, P1,1, P1,2 to Equation (20). Applying R1 and Equation (21) generates R1,0, R1,1 and R1,2. Four intermediate shares with the size of 100 × 300 are acquired from the following:
- In the last threshold 4, R2 is acquired by applying P2,0, P2,1, P2,2, P2,3 to Equation (20). Applying R2 and Equation (21) generates R2,0, R2,1, R2,2 and R2,3. Four intermediate shares with the size of 150 × 300 are acquired from the following:
- All shared images , , , and with the size of 400 × 300 are obtained from the following concatenation processing:
The recovery example is explained as follows: The proposed XOR-based multi-secret image sharing scheme should be recovered by collecting consecutive shared images. In the proposed (4, 3, {2, 3, 4}) XOR-based multi-secret image sharing scheme, the collections of , , or meet the requirement of threshold 2 and the consecutive requirement. Moreover, the collections of or meet the requirement of threshold 3 and the consecutive requirement. The following introduces the recovery of three different collections of shared images.
- The collection of ;
- 1.1.
- Splitting and acquire intermediate shares , , and , , , respectively;
- 1.2.
- Since and , and can also be acquired by and , respectively;
- 1.3.
- Directly applying acquires , and can be obtained by Equation (20);
- 1.4.
- and are then acquired from Equations (21) and (22);
- 1.5.
- By using , , , and , the intermediate images and can be then obtained;
- 1.6.
- Finally, the reverse processing of the SIPS can obtain half bits of higher bit planes (LSB4–7) to have the rough image result;
- The collection of ;
- 2.1.
- Similar to the process in the previous collection, can also be split into intermediate shares , and , respectively;
- 2.2.
- Directly applying acquires the same result of ;
- 2.3.
- can be then obtained by Equation (20) so as to acquire , and
- 2.4.
- From , , , , , and reverse processing of the SIPS, another half bits of a higher bit planes (LSB4–7) are then acquired;
- 2.5.
- Therefore, recovers all bits under higher bit planes (LSB4–7);
- The collection of ;
- 3.1.
- Since includes and , all bits in a higher bit planes (LSB4–7) are perfectly recovered;
- 3.2.
- Splitting acquires , , , and , respectively;
- 3.3.
- Using , , the , , , , and are orderly calculated for obtaining the lower bit planes (LSB0–3);
- 3.4.
- The collection of recovers the secret images information of two half bits of a higher bit planes (LSB4–7) from and , and the lower bit planes (LSB0–3) from . Therefore, all secret images can then be perfectly recovered.
4. Experimental Results and Discussions
This section demonstrates the experimental results of our proposed approach. Section 4.1 presents the experimental results of the proposed approach to share four and five secret images. All experiments are run on a PC with an Intel i5-4210 CPU and 12G RAM, using the MATLAB R2019b software. The size of all experimental secret images is 256 × 256. Section 4.2 presents the performance of the proposed approach by comparing other multiple secret image sharing methods.
4.1. Experimental Results
Figure 5 shows the experimental results of sharing by thresholds (4, 3, {2, 3, 4}) with sharing four secret images and 3 recovery thresholds by collecting 2, 3, or 4 consecutive shared images. Figure 5a–d shows the four secret images: Airplane, Baboon, Barbara, and Boat. Figure 5e shows the result of XOR of all pictures, and there are still afterimages of secret images. Figure 5f shows the generated random image R, which is obtained by hash and bit reverse calculation in Figure 5e. Figure 5g–j show four shared images with size 342 × 256, in which the size is acquired from the concatenation for three thresholds {2, 3, 4} by the equation as 128 × 256, 86 × 256, 128 × 256, respectively. Figure 5k–n are the recovery results by gathering consecutive shared images in Figure 5g–h of satisfying the first threshold 2. Moreover, gathering three consecutive shared images in Figure 5g–i recover the results shown in Figure 5o–r, which are a little different comparing with the original secret images in Figure 5a–d. Gathering all four secret images recovers the secret images perfectly, as shown in Figure 5a–d.

Figure 5.
A (4, 3, {2, 3, 4}) XOR-based progressively secret image sharing example, (a–d) the secret images, (e) XOR result of (a–d), (f) the generated random image, (g–j) shared images, (k–n) recovery results by using (g–h), (o–r) recovery results by using (g–i).
Figure 6 shows another example of sharing five secret images by thresholds (5, 4, {2, 3, 4, 5}) consisting of 4 progressive recovery steps. Collecting 2, 3, 4, or 5 consecutive shared images recover high noise (Figure 6m–q), light noise (Figure 6r–v), clear (like Figure 5o–r), or perfect recovery (like Figure 6a–e), respectively. Figure 6h–l shows five shared images with size 361 × 256, in which the size is acquired from the concatenation for four thresholds {2, 3, 4, 5} by the equation as 107 × 256, 72 × 256, 54 × 256, and 128 × 256, respectively. However, the size of shared images may not be a square integer due to the proposed SIPS method and compensation with bit 0 is needed. Moreover, the number of compensation bits is limited and will not have a visual effect. The progressive recovery property of the proposed XOR-based (m, t, Ti) multi-secret image sharing scheme is clearly demonstrated in Figure 5 and Figure 6.
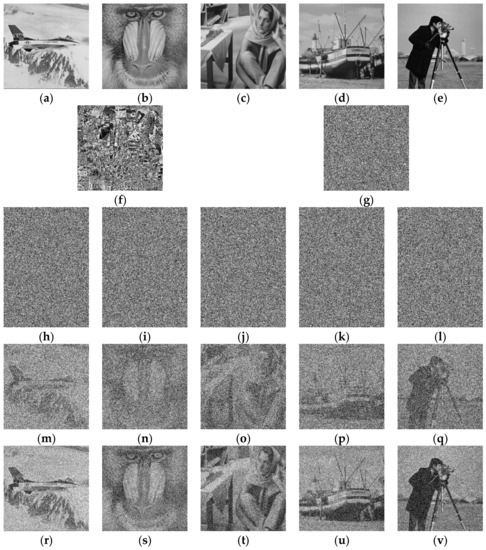
Figure 6.
A (5, 4, {2, 3, 4, 5}) XOR-based progressively secret image sharing example, (a–e) the secret images, (f) XOR result of (a–e), (g) the generated random image, (h–l) shared images, (m–q) recovery results by using (h–i), (r–v) recovery results by using (h–j).
Figure 7 shows an experiment of collecting all 5 shared images in a (5, 4, {2, 3, 4, 5}) XOR-based progressively secret image sharing, in which one shared image Figure 7a is under attacked. In our proposed scheme, collecting 5 shared images with no attacked shared image leads to perfect recovery. In Figure 7a, a region with black pixels is replaced at the center of the shared image, and the attacked region modifies the data required to recover in threshold 2. Therefore, the recovery of threshold 2 cannot be fulfilled. However, the data required to recover in threshold 3, 4, or 5 are still correct. Thus, the recovery results in Figure 7f–j exhibit the property of gathering satisfying the thresholds 3, 4 and 5.
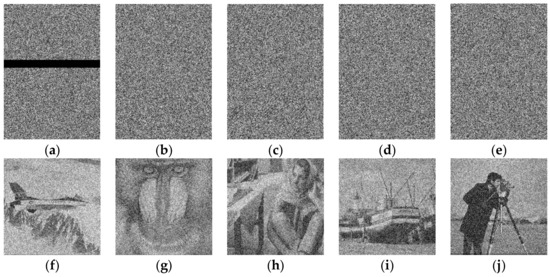
Figure 7.
An example of collecting 5 shared images with one attacked shared image in a (5, 4, {2, 3, 4, 5}) XOR-based progressively secret image sharing, (a) the attacked shared image, (b–e) the correct shared images, (f–j) the recover results by using (a–e).
Figure 8 shows another attack experiment. In Figure 8a, the attacked region covers the data required to satisfy thresholds 2, 3, 4, and 5. Therefore, no correct secret images can be recovered, and the recovered images shown in Figure 8f–j all look like noised images.
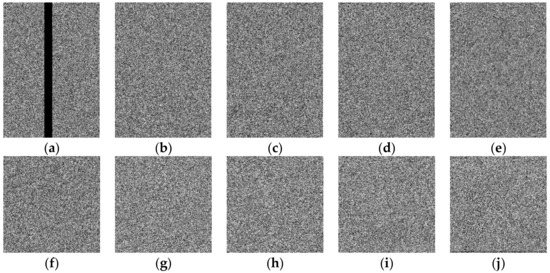
Figure 8.
Another example of collecting 5 shared images with one attacked shared image in a (5, 4, {2, 3, 4, 5}) XOR-based progressively secret image sharing, (a) the attacked shared image, (b–e) the correct shared images, (f–j) the recover results by using (a–e).
Table 2 shows the computation time of the proposed scheme in two thresholds. The proposed Boolean-based scheme requires limited CPU computation time, and the performance of the proposed scheme is, therefore, exhibited.

Table 2.
Performance of sharing and recovery procedures at different thresholds.
4.2. Comparison and Discussion
This section compares the proposed method with other multiple secret image sharing methods. The comparison metrics include recovery results, color levels, recovery methods, sharing types, sharing rates, and progressive or not. The recovery results are divided into recognizable recovery or lossless recovery. The color scales are divided into binary images and grayscale images by secret images. The recovery methods are to superimpose shared images or use a calculation to restore. The sharing rates are the value of the size of secret images divided by the size of shared images. Although the shared image size produced by the proposed method is not fixed, the total size of shared images is larger than the original image due to the presented consecutive recovery strategy. Table 3 shows that the proposed method is the only XOR-based method that can perform progressive sharing with no distortion reduction and grayscale.

Table 3.
Comparisons between the proposed approach and related multiple secret image sharing methods.
5. Conclusions
This paper proposed a high security and efficiency XOR-based (m, t, Ti) multi-secret image sharing scheme. The proposed method only needs to perform XOR operations without recording random images. The proposed secret image partition strategy (SIPS) generates intermediate images for different thresholds in the sharing procedure. Based on the property of progressive recovery, the proposed scheme should be recovered by collecting consecutive shared images. The experimental results and analyses show that the proposed method outperforms previous schemes. In the future, we will study how to limit the sharing rate to further improve our approach.
Author Contributions
Conceptualization, C.-S.L., C.-C.C.; methodology, C.-C.C.; validation, C.-S.L., C.-C.C., Y.-C.C.; formal analysis, C.-S.L., C.-C.C.; investigation, Y.-C.C.; writing—original draft preparation, writing—review and editing, C.-S.L., C.-C.C., Y.-C.C.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chanu, O.B.; Neelima, A. A survey paper on secret image sharing schemes. Int. J. Multimed. Inf. Retr. 2019, 8, 195–215. [Google Scholar] [CrossRef]
- Thien, C.-C.; Lin, J.-C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Blakley, G.R. Safeguarding cryptographic keys. In Proceedings of the 1979 International Workshop on Managing Requirements Knowledge (MARK), New York, NY, USA, 4–6 June 1979; Volume 48, pp. 313–317. [Google Scholar]
- Ulutas, M.; Ulutas, G.; Nabiyev, V.V. Invertible secret image sharing for gray level and dithered cover images. J. Syst. Softw. 2013, 86, 485–500. [Google Scholar] [CrossRef]
- Wu, X.; Ou, D.; Liang, Q.; Sun, W. A user-friendly secret image sharing scheme with reversible steganography based on cellular automata. J. Syst. Softw. 2012, 85, 1852–1863. [Google Scholar] [CrossRef]
- Wang, D.; Zhang, L.; Ma, N.; Li, X. Two secret sharing schemes based on Boolean operations. Pattern Recognit. 2007, 40, 2776–2785. [Google Scholar] [CrossRef]
- Kabirirad, S.; Eslami, Z. Improvement of (n, n)-multi-secret image sharing schemes based on Boolean operations. J. Inf. Secur. Appl. 2019, 47, 16–27. [Google Scholar] [CrossRef]
- Dhara, B.C.; Chanda, B. A fast progressive image transmission scheme using block truncation coding by pattern fitting. J. Vis. Commun. Image Represent. 2012, 23, 313–322. [Google Scholar] [CrossRef]
- Fang, W.-P. Friendly progressive visual secret sharing. Pattern Recognit. 2008, 41, 1410–1414. [Google Scholar] [CrossRef]
- Huang, C.-P.; Hsieh, C.-H.; Huang, P.S. Progressive sharing for a secret image. J. Syst. Softw. 2010, 83, 517–527. [Google Scholar] [CrossRef]
- Lin, S.-J.; Lin, J.-C. VCPSS: A two-in-one two-decoding-options image sharing method combining visual cryptography (VC) and polynomial-style sharing (PSS) approaches. Pattern Recognit. 2007, 40, 3652–3666. [Google Scholar] [CrossRef]
- Wang, R.-Z.; Su, C.-H. Secret image sharing with smaller shadow images. Pattern Recognit. Lett. 2006, 27, 551–555. [Google Scholar] [CrossRef]
- Chen, C.C.; Chien, Y.W. Sharing numerous images secretly with reduced possessing load. Fundam. Inf. 2008, 86, 447–458. [Google Scholar]
- Chen, T.-H.; Wu, C.-S. Efficient multi-secret image sharing based on Boolean operations. Signal Process. 2011, 91, 90–97. [Google Scholar] [CrossRef]
- Chen, C.-C.; Wu, W.-J. A secure Boolean-based multi-secret image sharing scheme. J. Syst. Softw. 2014, 92, 107–114. [Google Scholar] [CrossRef]
- Chen, C.-C.; Wu, W.-J.; Chen, J.-L. Highly efficient and secure multi-secret image sharing scheme. Multimedia Tools Appl. 2015, 75, 7113–7128. [Google Scholar] [CrossRef]
- Kabirirad, S.; Eslami, Z. A(t,n)-multi secret image sharing scheme based on Boolean operations. J. Vis. Commun. Image Represent. 2018, 57, 39–47. [Google Scholar] [CrossRef]
- Azza, A.A.; Lian, S. Multi-secret image sharing based on elementary cellular automata with steganography. Multimed. Tools Appl. 2020, 79, 21241–21264. [Google Scholar] [CrossRef]
- Chen, T.-H.; Wu, X.-W. Multiple secret image sharing with general access structure. Multimed. Tools Appl. 2020, 79, 13247–13265. [Google Scholar] [CrossRef]
- Ross, A.; Othman, A. Visual Cryptography for Biometric Privacy. IEEE Trans. Inf. Forensics Secur. 2011, 6, 70–81. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Yang, C.-N.; Zhang, X.; Wang, S. A Common Method of Share Authentication in Image Secret Sharing. IEEE Trans. Circuits Syst. Video Technol. 2020. [Google Scholar] [CrossRef]
- Yue, J.; Yan, X.; Qi, J.; Lu, Y.; Zhou, X. Secret image sharing with dealer-participatory and non-dealer-participatory mutual shadow authentication capabilities. Mathematics 2020, 8, 234. [Google Scholar]
- Li, J.; Wang, X.; Huang, Z.; Wang, L.; Xiang, Y. Multi-level multi-secret sharing scheme for decentralized e-voting in cloud computing. J. Parallel Distrib. Comput. 2019, 130, 91–97. [Google Scholar] [CrossRef]
- Chen, J.; Chen, Y.S.; Hsu, H.C.; Chen, H.W. New visual cryptography system based on circular shadow image and fixed angle segmentation. J. Electron. Imaging 2005, 14, 033018. [Google Scholar] [CrossRef]
- Shyu, S.J.; Huang, S.-Y.; Lee, Y.-K.; Wang, R.-Z.; Chen, K. Sharing multiple secrets in visual cryptography. Pattern Recognit. 2007, 40, 3633–3651. [Google Scholar] [CrossRef]
- Lin, S.-J.; Chen, S.-K.; Lin, J.-C. Flip visual cryptography (FVC) with perfect security, conditionally-optimal contrast, and no expansion. J. Vis. Commun. Image Represent. 2010, 21, 900–916. [Google Scholar] [CrossRef]
- Chen, C.C.; Fu, W.F. A geometry-based secret image sharing approach. J. Informat. Sci. Eng. 2008, 24, 1567–1577. [Google Scholar]
- Wu, H.C.; Chang, C.C. Sharing visual multi-secrets using circle shares. Comput. Stand. Interfaces 2005, 28, 123–135. [Google Scholar]
- Bhattacharjee, T.; Maity, S.P.; Islam, S.R. Hierarchical secret image sharing scheme in compressed sensing. Signal Process. Image Commun. 2018, 61, 21–32. [Google Scholar] [CrossRef]
- Chanu, O.B.; Neelima, A. A new multi-secret image sharing scheme based on DCT. Vis. Comput. 2019, 36, 939–950. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).