Abstract
In this paper, a generalized synchronization (GS) framework for identical hyperchaotic systems is presented. The main objective is to achieve generalized synchronization with guaranteed global stability and effective convergence, which remains a key challenge in synchronization-based secure communication systems. The proposed controller is systematically derived to ensure global asymptotic convergence of the synchronization errors for arbitrary initial conditions and distinct scaling factors. This formulation unifies complete, anti-, and generalized synchronization within a single control structure. To demonstrate the applicability of the proposed method, it is integrated into an image encryption algorithm, where the hyperchaotic trajectories of the drive system generate highly random permutation and diffusion sequences. Simulation results verify that the designed controller achieves effective generalized synchronization and that the encrypted images exhibit uniform histograms and low pixel correlation, indicating strong security and resistance to statistical attacks.
Keywords:
generalized synchronization (GS); hyperchaotic systems; encrypted image; permutation; diffusion MSC:
37N35; 34D06; 34H10
1. Introduction
The study of hyperchaotic systems has attracted significant attention over the past few decades due to their complex nonlinear dynamics and wide-ranging applications in science and engineering. Since the pioneering work of Pecora and Carroll [1], who first introduced the concept of chaos synchronization, researchers have extensively explored synchronization phenomena in nonlinear dynamical systems. These efforts have led to the development of several synchronization types, including complete synchronization, anti-synchronization, projective synchronization, and generalized synchronization [2,3,4,5,6,7,8,9,10,11,12,13,14,15]. Among them, generalized synchronization (GS) is regarded as the most comprehensive form, as it allows for a relationship between the drive and response systems. Hyperchaotic systems, which possess more than one positive Lyapunov exponent, provide even richer dynamic behavior and higher sensitivity to initial conditions compared to simple chaotic systems. Such properties make them especially attractive for secure communication and cryptographic applications, where unpredictability and sensitivity are key requirements [16,17,18,19,20,21,22,23]. Several recent studies have investigated advanced synchronization strategies and their applications in secure communication and encryption. Generalized modified projective synchronization has been employed in secure communication schemes based on newly proposed four-dimensional fractional-order hyperchaotic systems, highlighting the effectiveness of scaling-based synchronization in fractional-order settings [24]. Some studies have addressed synchronization and the FPGA implementation of multiscroll Hopfield neural networks using non-polynomial memristors [25]. Recent work has addressed fixed-time interlayer synchronization in voltage-flux time-delayed memristive neural networks using Lyapunov-based control and demonstrated its effectiveness in secure communication applications [26]. In addition, Mittag–Leffler synchronization of fractional-order chaotic neural networks with time-varying delays has been studied using hybrid control techniques and applied to biometric image encryption. These works highlight the role of advanced control designs in enhancing synchronization robustness and encryption performance [27].
Although these studies provide valuable contributions by addressing specific synchronization types, control strategies, or implementation platforms, they are typically restricted to fractional-order models, neural network-based systems, hardware-oriented realizations, or particular synchronization objectives. In contrast, the present work considers a continuous-time hyperchaotic system and develops a generalized synchronization framework within a unified analytical setting, which is subsequently applied to secure communication.
The main contributions of this paper are summarized as follows:
- A generalized synchronization framework is rigorously formulated for identical hyperchaotic systems by defining appropriate error dynamics with diagonal scaling matrices. This formulation provides a unified mathematical setting that encompasses complete and anti-synchronization as special cases.
- A control law is analytically derived to stabilize the resulting error system. By constructing a quadratic Lyapunov function, sufficient conditions are established to ensure that the synchronization error dynamics are globally asymptotically stable for arbitrary initial conditions and nonzero scaling factors.
- The proposed synchronization framework is further exploited to generate high-quality chaotic sequences from the drive-system trajectories. These sequences are systematically incorporated into a permutation diffusion image encryption algorithm, thereby demonstrating the practical applicability of the theoretical results.
The contents of this paper are organized as follows: Section 2 defines the novel hyperchaotic system. Section 3 proposes the methodology of generalized synchronization. The chaos-generalized synchronization of the introduced chaotic system with itself as a drive response system is investigated in Section 4. A numerical example is provided to show the effectiveness of the method in Section 5. The implementation of the proposed method is presented in Section 6, where secure image encryption is achieved using the drive system’s trajectories to generate permutation and diffusion keys. Moreover, statistical evaluations, including histogram and pixel correlation analysis, confirm that the proposed scheme ensures strong security and robustness against cryptanalytic attacks. Finally, the paper is concluded in Section 7.
2. The Novel Hyperchaotic System
The considered novel hyperchaotic system defined in [28] is expressed as follows:
where the system parameters are given by The corresponding phase portraits and projections of the system variables are illustrated in Figure 1, where subfigures (a)–(h) represent different two dimensional projections and three-dimensional attractors of the novel hyperchaotic system.
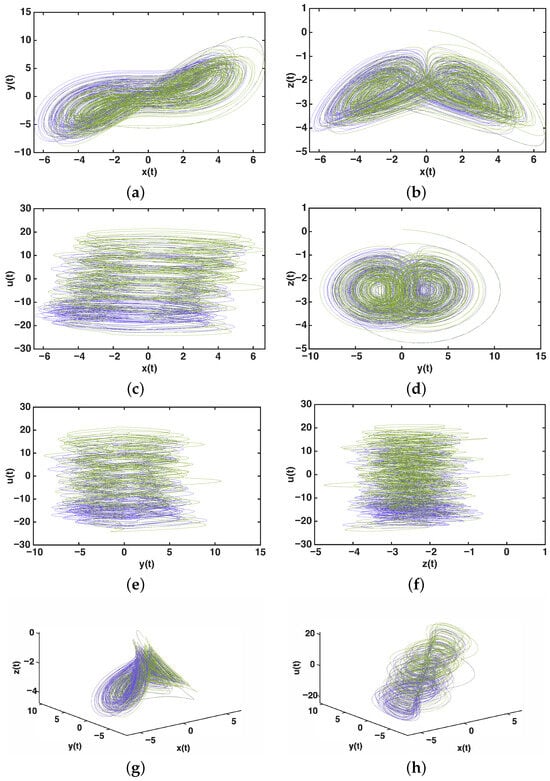
Figure 1.
Phase portraits of the novel hyperchaotic system: (a) trajectory in the plane; (b) trajectory in the plane; (c) trajectory in the plane; (d) trajectory in the plane; (e) trajectory in the plane; (f) trajectory in the plane; (g) 3D attractor ; (h) 3D attractor . The green trajectory represents the numerical solution obtained using the default settings of the ODE45 solver, while the purple trajectory corresponds to the solution computed with a higher relative tolerance (RelTol = 10−6).
3. The Scheme of General Synchronization
We consider the drive and response systems shown in the following form:
where and are state vectors, are continuous nonlinear functions, and is the controller vector to be designed [29].
Definition 1.
It is said that the drive and response systems achieve generalized synchronization if the following equation holds:
where the diagonal matrix () is a scaling factor that can be chosen to realize different types of synchronization.
Remark 1.
The generalized synchronization framework includes several classical synchronization schemes as special cases, depending on the choice of the scaling matrix (Λ).
- If , where denotes the identity matrix, the generalized synchronization reduces to complete synchronization, that is,
- If , the generalized synchronization becomes anti-synchronization, where the state variables of the drive and response systems evolve in opposite directions, i.e.,
4. Generalized Synchronization Between Two Identical Systems
Here, we present the novel hyperchaotic dynamical system with generalized synchronization. The novel hyperchaotic drive system is described as follows:
where , and denote the drive states. The corresponding response system, including the control input (), is given by
where , and denote the response states and is the control signal to be designed.
To establish generalized synchronization between the drive (1) and response (2) systems, we define the error vectors as follows:
Then, by differentiating the error variables (3), we obtain
The main purpose is to determine controllers () that could stabilize the error variables of the system. For this, the following theorem is presented:
Theorem 1.
For a given nonzero scaling factor (, where ), the generalized synchronization among the drive and response systems will occur with the following control inputs chosen.
where are design parameters.
Proof.
Consider the following Lyapunov function:
The time derivative of the Lyapunov function (5) is
substituting the above control input (4) to cancel cross terms and ensure negative definiteness:
Then, we obtain
since , and and the matrix (P) is positive definite, which implies that is negative definite. Consequently, the error system is globally asymptotically stable, and generalized synchronization between the identical hyperchaotic systems is achieved. □
5. Numerical Simulations
To substantiate the analytical results and assess the effectiveness of the proposed synchronization schemes, a series of numerical simulations was carried out using the designed novel hyperchaotic drive response systems. The synchronization performance is evaluated through the temporal evolution of the error variables (), which are defined as follows:
We assume that the initial conditions are given by
In the first case, the complete synchronization behavior was achieved by setting all scaling factors to , as presented in Figure 2. In the second case, the anti-synchronization phenomenon appears in Figure 3 when , as the state variables of the response system evolved in an opposite phase to those of the drive system. Finally, for the generalized synchronization, different scaling factors of were considered to demonstrate the system’s ability to achieve stable convergence, even under non-identical mappings, as illustrated in Figure 4. These results demonstrate that the proposed controller provides a unified and effective synchronization mechanism for multiple synchronization modes.
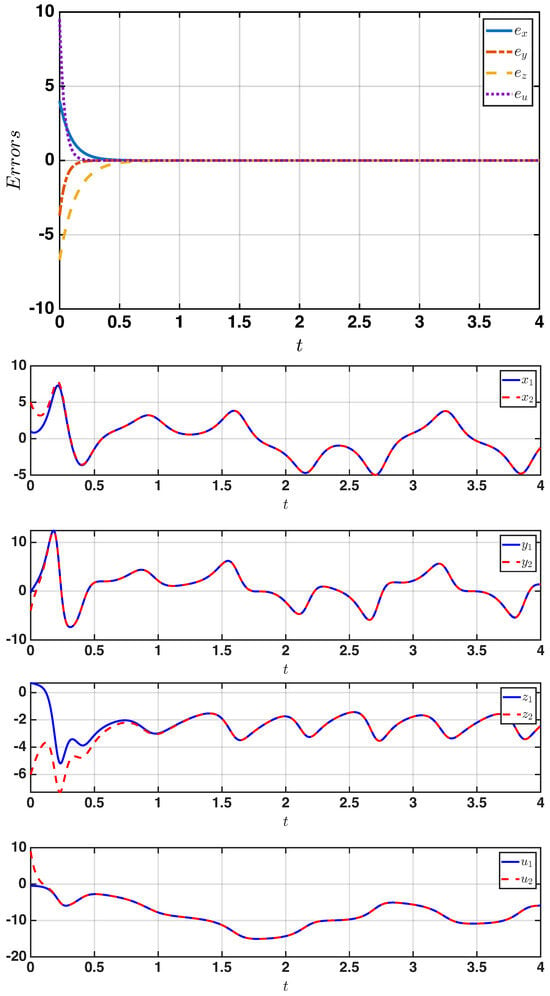
Figure 2.
Complete synchronization results showing (top) drive response trajectories, and (bottom) phase portraits under .
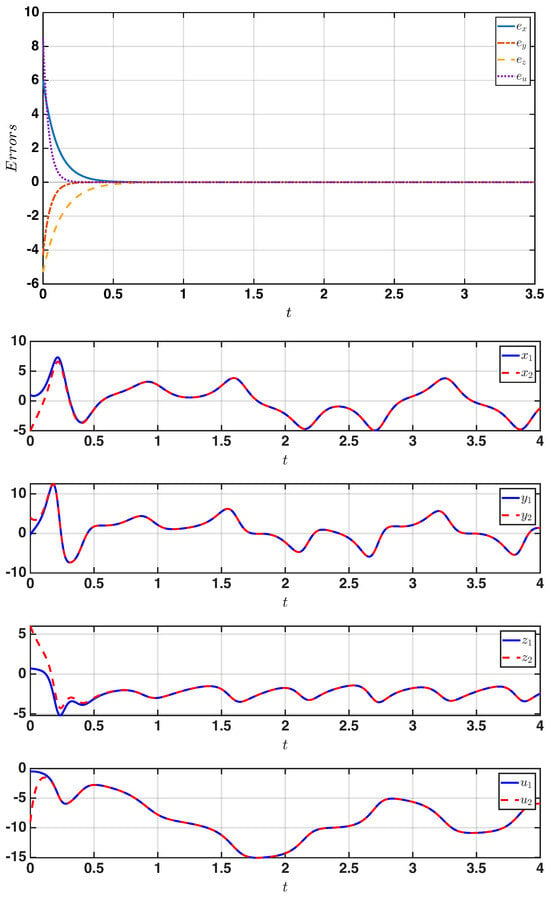
Figure 3.
Anti-synchronization results showing (top) drive response trajectories and (bottom) phase portraits under .
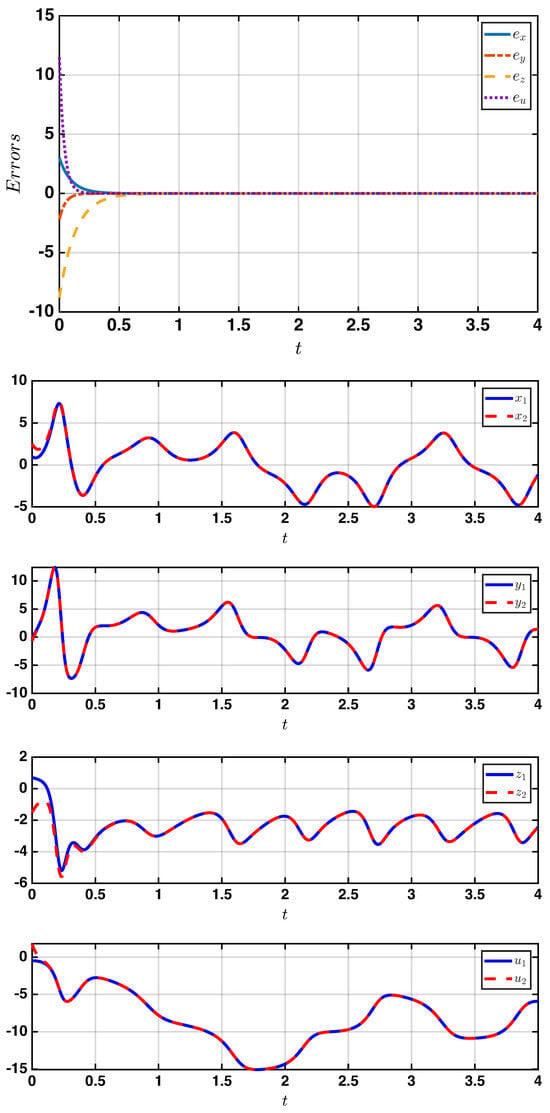
Figure 4.
Generalized synchronization results showing the drive response trajectories (top) and phase portraits (bottom).
6. Chaotic Image Encryption and Decryption Process
This section describes the proposed chaotic image encryption scheme, which combines permutation and diffusion mechanisms driven by a hyperchaotic synchronization system. Figure 5 illustrates a schematic depiction of the proposed encoding technique. Below are the procedures followed during encryption.
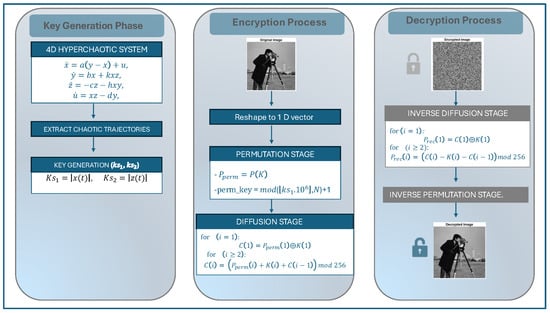
Figure 5.
Proposed permutation diffusion-based image encryption and decryption scheme.
6.1. Novel Hyperchaotic System Modeling
We consider a four-dimensional novel hyperchaotic system defined as follows:
The system generates chaotic trajectories , which are obtained using numerical integration with the fourth-order Runge–Kutta solver (ode45)and a sufficiently small step size of . From the obtained chaotic trajectories, two state variables of the drive system are extracted, namely
which serve as the sources of chaotic key streams. To guarantee sufficient length for image encryption, the generated sequences are extended when necessary.
6.2. Key Generation
The absolute-valued chaotic sequences are defined as
where N denotes the total number of pixels in each image channel. These sequences are normalized and mapped as follows:
Image Preprocessing
The plaintext image is resized to pixels. For grayscale images, the image is directly reshaped into a one-dimensional pixel vector. For color images, the encryption process is applied independently to each RGB channel. Each channel is reshaped into a one-dimensional vector:
where denotes the intensity value of the i-th pixel in the plaintext image and N is the total number of pixels in each channel.
- Permutation Key GenerationA permutation key is generated from the chaotic sequence () as follows:By sorting the permutation key in ascending order, a permutation index vector () is obtained, which determines the scrambling order of pixel positions. The permuted pixel sequence is given byThis permutation stage effectively disrupts the strong spatial correlation among adjacent pixels in the original image.
- Diffusion Key GenerationA diffusion key stream is derived from the second chaotic sequence aswhere is an 8-bit integer sequence used to modify pixel intensities during the diffusion process.
6.3. Diffusion Stage
The diffusion process is performed sequentially to enhance sensitivity to plaintext changes. The first encrypted pixel is computed using the bitwise XOR operation:
For the remaining pixels, a feedback-based diffusion rule is applied:
This chained diffusion mechanism ensures that a slight change in any pixel propagates throughout the entire ciphertext image.
6.4. Decryption Process
Decryption applies the inverse operations:
- Inverse Diffusion:
- Inverse Permutation: Construct the inverse index such that
The reconstructed image matches the original, with no information loss.
6.5. Validation
The encryption scheme is validated using the following metrics:
- Histogram Analysis: Encrypted images exhibit uniform distributions.
- Correlation Coefficient: Near-zero correlation for adjacent pixels in encrypted images.
The successful reconstruction of the original images, along with uniform histograms and low pixel correlation, confirms that the proposed framework provides a reliable and secure foundation for the encryption process.
Figure 6 presents visual and statistical analyses of the image encryption process using the proposed chaotic system. The top section illustrates the grayscale image encryption results, including the original, encrypted, and decrypted images, along with their corresponding histograms and pixel correlation plots. The bottom section presents the same evaluation for a colored (RGB) image, demonstrating consistent encryption performance across different image types.
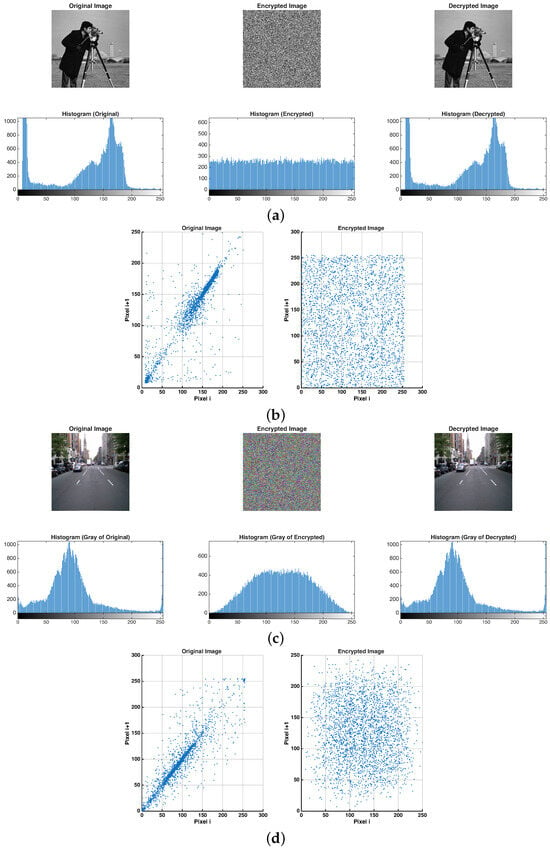
Figure 6.
Subfigures (a,b) show the grayscale case, including the original, encrypted, and decrypted images with their corresponding histograms and pixel correlation plots, while (c,d) represent the corresponding results for the colored case.
7. Conclusions
In this study, a generalized synchronization scheme for identical hyperchaotic systems was successfully presented and systematically analyzed. The proposed method guarantees global asymptotic convergence of synchronization errors based on Lyapunov stability analysis and extends the synchronization capability to cases with distinct scaling factors (). Numerical simulations confirm the effectiveness of the designed controllers, showing that the synchronization errors rapidly approach zero for complete, anti-, and generalized synchronization cases. Furthermore, the developed synchronization framework was applied to image encryption, where the hyperchaotic trajectories of the drive system provide secure and highly sensitive keys. The encrypted images exhibit uniform histograms, low pixel correlations, and perfect reconstruction upon decryption, confirming the robustness and efficiency of the proposed scheme. This approach demonstrates that generalized synchronization not only stabilizes complex hyperchaotic systems but also provides a powerful and reliable foundation for secure communication and information protection applications.
Author Contributions
Conceptualization, M.M.E.-D. and N.A.; methodology, M.M.E.-D. and N.A.; software, M.M.E.-D. and N.A.; validation, M.M.E.-D. and N.A.; formal analysis, M.M.E.-D. and N.A.; investigation, M.M.E.-D. and N.A.; resources, M.M.E.-D.; data curation, M.M.E.-D. and N.A.; writing—original draft preparation, M.M.E.-D. and N.A.; writing—review and editing, M.A.; visualization, M.M.E.-D. and N.A.; supervision, M.M.E.-D. and M.A.; project administration, M.M.E.-D.; funding acquisition, M.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding authors.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Pecora, L.M.; Carroll, T.L. Synchronization in chaotic systems. Phys. Rev. Lett. 1990, 64, 821–824. [Google Scholar] [CrossRef]
- Park, J.H. Adaptive modified projective synchronization of a unified chaotic system with an uncertain parameter. Chaos Solitons Fractals 2007, 34, 1552–1559. [Google Scholar] [CrossRef]
- Huang, J. Adaptive synchronization between different hyperchaotic systems with fully uncertain parameters. Phys. Lett. A 2008, 372, 4799–4804. [Google Scholar] [CrossRef]
- Runzi, L.; Zhengmin, W. Adaptive function projective synchronization of unified chaotic systems with uncertain parameters. Chaos Solitons Fractals 2009, 42, 1266–1272. [Google Scholar] [CrossRef]
- Yu, Y.; Li, H.X. Adaptive generalized function projective synchronization of uncertain chaotic systems. Nonlinear Anal. Real World Appl. 2010, 11, 2456–2464. [Google Scholar] [CrossRef]
- Zheng, S.; Dong, G.; Bi, Q. Adaptive modified function projective synchronization of hyperchaotic systems with unknown parameters. Commun. Nonlinear Sci. Numer. Simul. 2010, 15, 3547–3556. [Google Scholar] [CrossRef]
- Zheng, S. Adaptive modified function projective synchronization of unknown chaotic systems with different order. Appl. Math. Comput. 2012, 218, 5891–5899. [Google Scholar] [CrossRef]
- El-Dessoky, M.M.; Alzahrani, E.; Almohammadi, N. Function projective synchronization for four scroll attractor by nonlinear control. Appl. Math. Sci. 2017, 11, 1247–1259. [Google Scholar] [CrossRef]
- El-Dessoky, M.M.; Alzahrani, E.; Almohammadi, N. Control and adaptive modified function projective synchronization of Liu chaotic dynamical system. J. Appl. Anal. Comput. 2019, 9, 601–614. [Google Scholar] [CrossRef]
- Almohammadi, N.; Alzahrani, E.; El-Dessoky, M.M. Combined modified function projective synchronization of different systems through adaptive control. Arch. Control Sci. 2019, 29, 133–146. [Google Scholar] [CrossRef]
- El-Dessoky, M.M.; Alzahrani, E.; Almohammadi, N. Adaptive modified function projective synchronization of chaotic dynamical system with different order. J. Comput. Anal. Appl. 2020, 28, 354–363. [Google Scholar]
- Zhang, F.; Zhou, P.; Qin, J.; Mu, C.; Xu, F. Dynamics of a Generalized Lorenz-Like Chaos Dynamical Systems. J. Appl. Anal. Comput. 2021, 11, 1577–1587. [Google Scholar] [CrossRef]
- El-Dessoky, M.M.; Almohammadi, N.; Alzahrani, E. Control and adaptive modified function projective synchronization of different hyperchaotic dynamical systems. AIMS Math. 2023, 8, 23621–23634. [Google Scholar] [CrossRef]
- Chong, Y.; Chen, F. Global Stability, Bifurcations and Chaos Control in a Discrete Amensalism Model With Cover and Saturation Effect. J. Appl. Anal. Comput. 2025, 15, 2977–3003. [Google Scholar] [CrossRef]
- Guan, J.; Chen, S. Feedback Control of Chaos in The Modified KdV–Burgers–Kuramoto Equation Via a Single Time-Delay. J. Appl. Anal. Comput. 2026, 16, 17–33. [Google Scholar] [CrossRef]
- Huang, H.; Yang, S. Image Encryption Technique Combining Compressive Sensing with Double Random-Phase Encoding. Math. Probl. Eng. 2018, 2018, 6764052. [Google Scholar] [CrossRef]
- Wang, J.; Li, J.; Di, X.; Zhou, J.; Man, Z. Image Encryption Algorithm Based on Bit-level Permutation and Dynamic Overlap Diffusion. IEEE Access 2020, 8, 160004–160024. [Google Scholar] [CrossRef]
- Liu, L.; Lei, Y.; Wang, D. A Fast Chaotic Image Encryption Scheme with Simultaneous Permutation and Diffusion. IEEE Access 2020, 8, 27361–27374. [Google Scholar] [CrossRef]
- Li, Z.; Peng, C.; Tan, W.; Li, L. An Effective Chaos-Based Image Encryption Scheme Using Imitating Jigsaw Method. Complexity 2021, 2021, 8824915. [Google Scholar] [CrossRef]
- Raghuvanshi, A.; Budhia, M.; Patro, K.; Acharya, B. FSR-SPD: An efficient chaotic multi-image encryption system based on flip-shift-rotate synchronous-permutation-diffusion operation. Multimed. Tools Appl. 2024, 83, 57011–57057. [Google Scholar] [CrossRef]
- Li, Y.; Jiang, M.; Wei, D.; Deng, Y. A Novel Image Encryption Algorithm Based on Compressive Sensing and a Two-Dimensional Linear Canonical Transform. Fractal Fract. 2024, 8, 92. [Google Scholar] [CrossRef]
- Li, Y.; Deng, Y.; Jiang, M.; Wei, D. Fast Encryption Algorithm Based on Chaotic System and Cyclic Shift in Integer Wavelet Domain. Fractal Fract. 2024, 8, 75. [Google Scholar] [CrossRef]
- Acharya, B.; Sravan, J.V.; Potnuru, D.J.R.; Patro, K.A.K. MIE-SPD: A New and Highly Efficient Chaos-Based Multiple Image Encryption Technique With Synchronous Permutation Diffusion. IEEE Access 2025, 13, 62773–62797. [Google Scholar] [CrossRef]
- Nabil, H.; Tayeb, H. A secure communication scheme based on generalized modified projective synchronization of a new 4-D fractional-order hyperchaotic system. Phys. Scr. 2024, 99, 095203. [Google Scholar] [CrossRef]
- Yu, F.; Kong, X.; Yao, W.; Zhang, J.; Cai, S.; Lin, H.; Jin, J. Dynamics analysis, synchronization and FPGA implementation of multiscroll Hopfield neural networks with non-polynomial memristor. Chaos Solitons Fractals 2024, 179, 114440. [Google Scholar] [CrossRef]
- Tan, F.; Zhou, L.; Zong, G.; Wang, Z.; Zhuang, G.; Shangguan, X. Fixed Time Control for Interlayer Synchronism Under DDMNNs and Application in Secure Communication. IEEE Trans. Autom. Sci. Eng. 2025, 22, 10827–10834. [Google Scholar] [CrossRef]
- Ramaswami, R.; Arumugam, V.; Pathmanaban, S. Mittag–Leffler synchronization of fractional order disturbed chaotic neural networks with varying time-delay using hybrid controller and its application to biometric image encryption. Commun. Nonlinear Sci. Numer. Simul. 2026, 152, 109350. [Google Scholar] [CrossRef]
- Xu, J.; Cai, G.; Zheng, S. A Novel Hyperchaotic System and Its Control. J. Uncertain Syst. 2009, 3, 137–144. [Google Scholar]
- Li, G. Generalized projective synchronization between Lorenz system and Chen’s system. Chaos Solitons Fractals 2007, 32, 1454–1458. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.